Authentication method and authentication system among mobile devices
A mobile device and authentication technology, applied in payment systems, payment architectures, data processing applications, etc., can solve problems such as the inability to meet user compatibility and convenience needs, the leakage of bank account-related information, and the exposure of security risks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
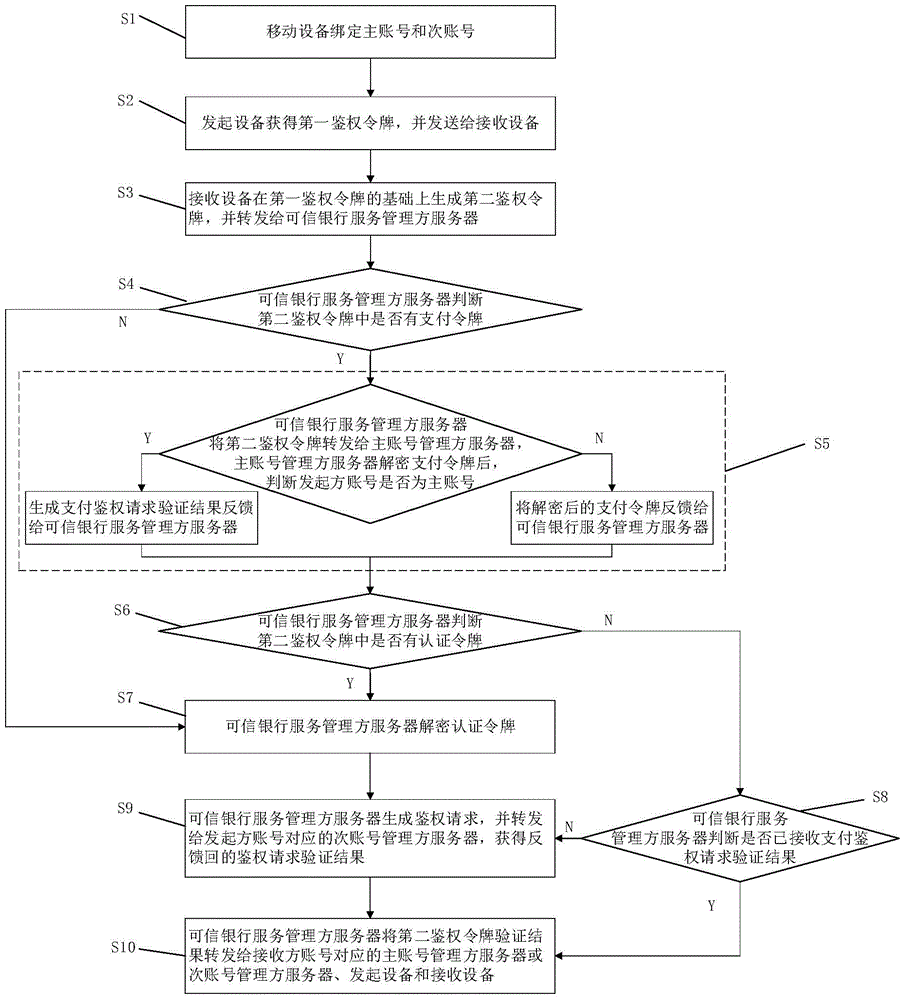
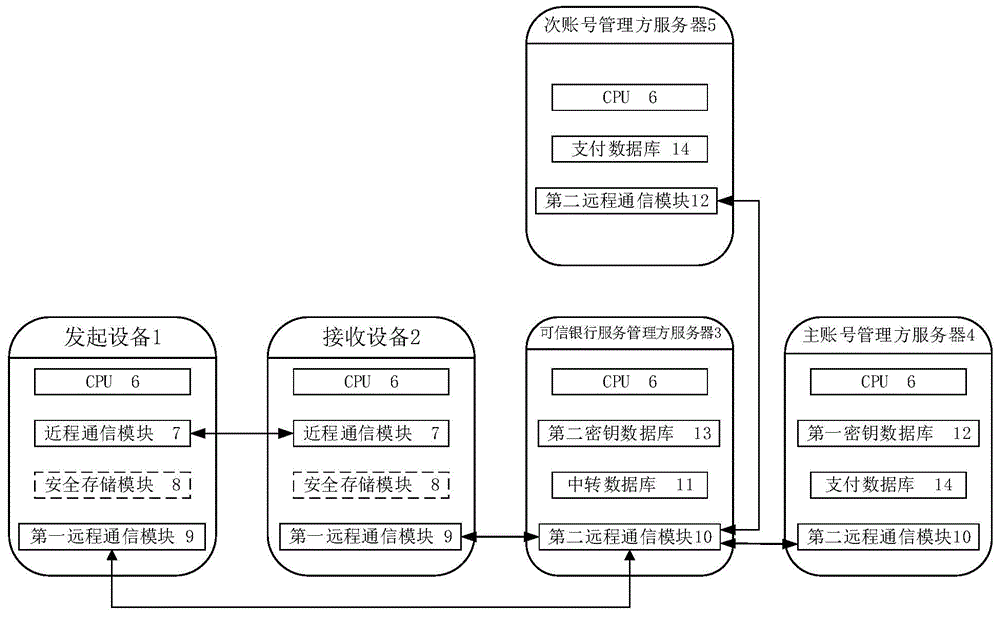
[0093] Such as figure 2 As shown, an authentication system between mobile devices includes:
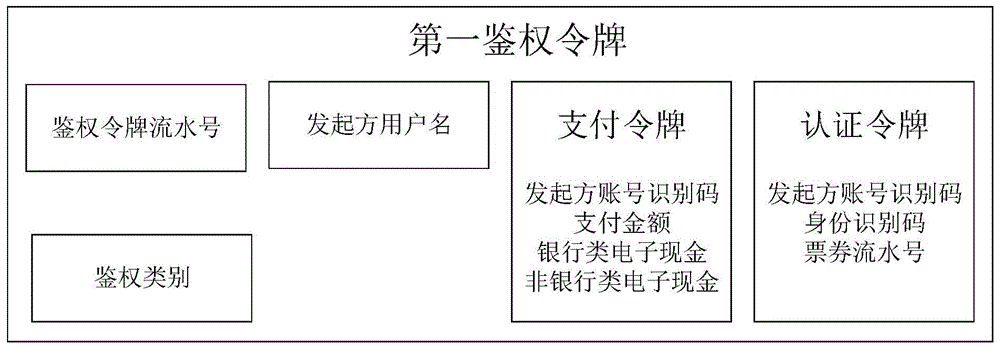
[0094] The initiating device 1 is used to bind a primary account and multiple secondary accounts, and after selecting the bound account as the initiator account, obtain the first authentication order for mobile payment, identity authentication and ticket verification through an encryption method card, and send it to the receiving device 2 through short-distance communication, and at the same time receive the verification result of the second authentication token fed back by the trusted bank service manager server 3, wherein the first authentication token includes but is not limited to authentication Token serial number, authentication category, initiator user name and token information corresponding to the initiator account, token information includes payment token and / or authentication token;
[0095] The receiving device 2 is used to bind a primary account and multiple secondary a...
Embodiment 2
[0155] The difference between this embodiment and Embodiment 1 is that, taking the smart watch as the initiating device 1, the smart access control as the receiving device 2, and the Hanting server as the secondary account management server 5 as an example, user A (using a smart watch) needs to register with the Hanting Room 301 of the Shanghai Shimen 2nd Road branch of the hotel (using smart access control) for identity verification. User A selects the Hanting account as the initiator account, and Room 301 of the Hanting Hotel Shanghai Shimen 2nd Road branch selects the Hanting account as the recipient account. Personal identification Voiceprint recognition is used as the method, and Bluetooth is used as the short-distance communication method. In order to simplify the steps, the default validity verification is valid, such as Figure 6 As shown, the authentication method between user A and the mobile device in Room 301 of the Hanting Hotel based on the offline encryption meth...
Embodiment 3
[0162] The difference between this embodiment and Embodiment 1 is that the initiating device 1 is not provided with a secure storage module 8, then in step S2, the initiating device 1 obtains the first authentication token through an online encryption method, and in the online encryption method, the initiating device 1, The trusted bank service manager server 3 and the main account manager server 4 cooperate to realize the encrypted acquisition of the first authentication token, specifically: the initiating device 1 initiates the first authentication token online to the trusted bank service manager server 3 To generate a request, the trusted bank service manager server 3 judges that the first authentication token generation request is valid and then encrypts and generates a corresponding first authentication token. If the first authentication token generation request includes a payment token generation request, Then the trusted bank service manager server 3 requests the primary...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com