Social privacy protection method of multi-level attribute management center based on characteristic encryption
A technology of management center and attribute characteristics, which is applied in digital data protection, electronic digital data processing, instruments, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
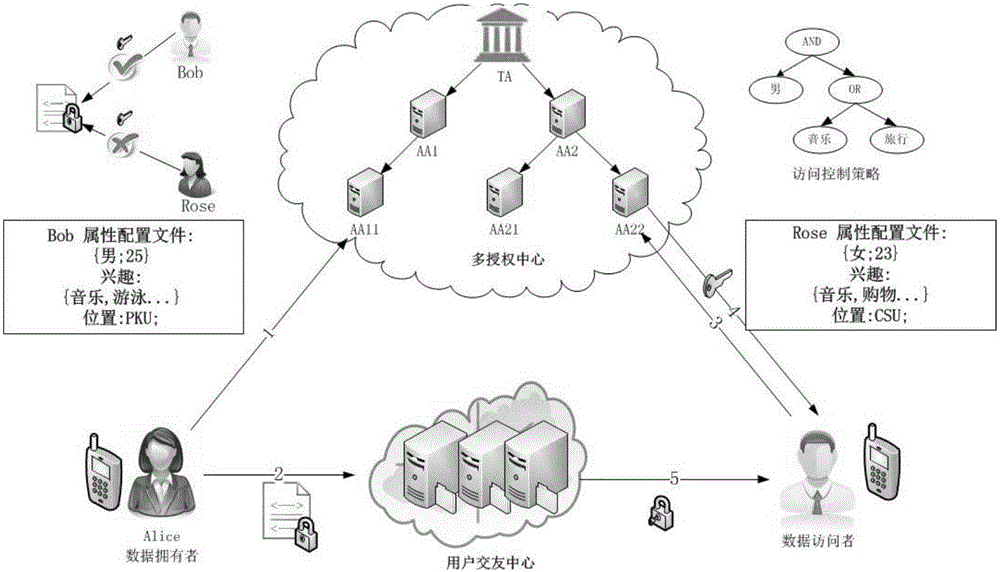
[0046] The overall structure of the friendship process is as follows figure 1 As shown, the friendship process is as follows:
[0047] Step 1: System initialization, generating system public key and system master key.
[0048] The trusted central authorization center TA assigns a unique global GID as a user identity identifier to all dating users, and assigns a unique identifier AID to all attribute management servers AA. GID is usually the user's identity digital signature string, all AAs can verify the authenticity of GID and the user's GID cannot be illegally obtained by other users.
[0049] See Table 1 for the meaning of the relevant character variables in this scheme;
[0050] Table 1 Symbol description table
[0051]
[0052]
[0053] In the system initialization phase, TA specifies the recursion depth dep defined in the key structure, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com