Anonymous express information security system based on two-dimension code
An information security system and two-dimensional code technology, applied in the fields of instruments, data processing applications, logistics, etc., can solve problems such as information leakage and information security leakage, and achieve the effect of ensuring security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
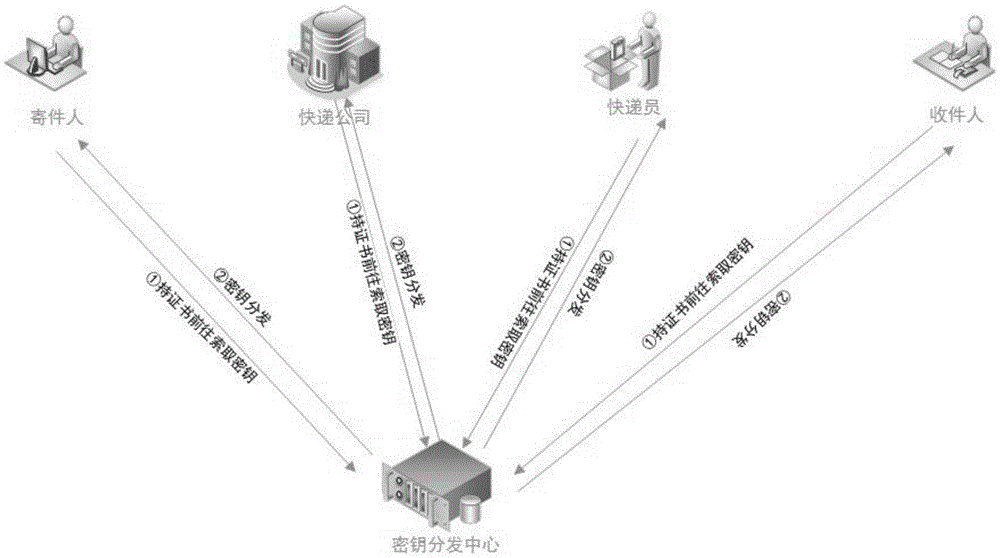
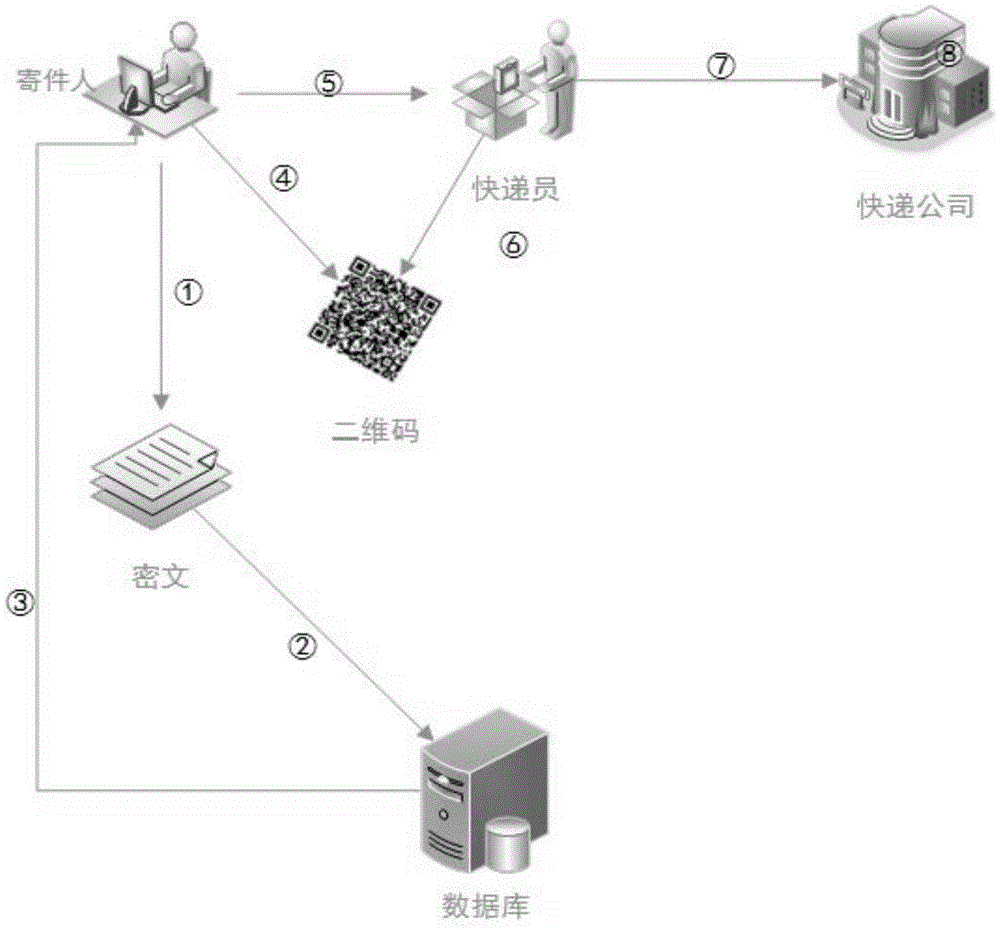
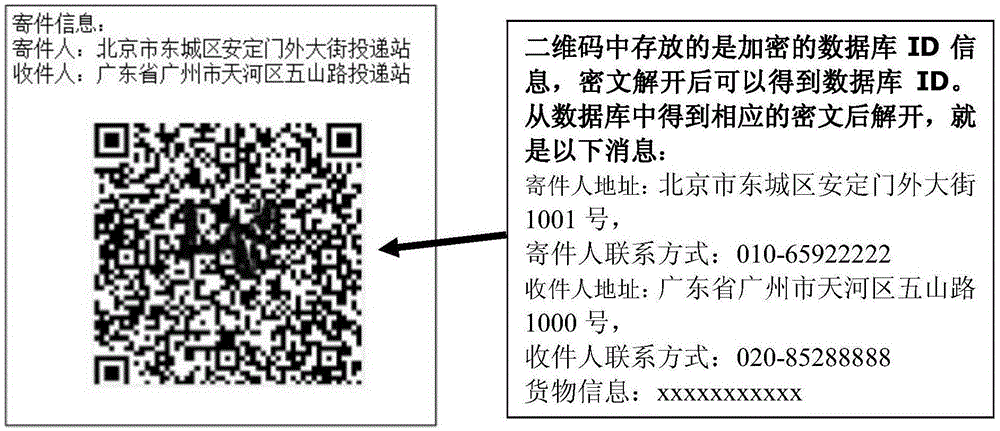
[0046] This system is a privacy protection solution designed for express delivery companies (such as: China Post EMS, SF Express, YTO Express, etc.), which mainly solves the problem of information leakage in the process of sending and receiving express delivery, and protects the privacy of senders and recipients Address information and item information prevent the leakage of personal privacy to the greatest extent and protect personal safety. It mainly involves the following participants, related institutions and media, and their respective meanings are shown in Table 1.
[0047] Table 1 Comparison table of concepts and meanings of system design
[0048]
[0049] like figure 1 As shown, the system of the present invention is composed of a relatively independent key management subsystem and an express information management subsystem. Structure; the express delivery information management subsystem mainly includes five entities of the sender, the recipient, the courier, th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com