Patents
Literature
122 results about "Risk category" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Risk category. Definition. Organization of risks in the form of a hierarchical scale that identifies each risk and what that level of risk entails. Some brokerage firms utilize risk categories to identity and categorize the risk associated with a particular investment.
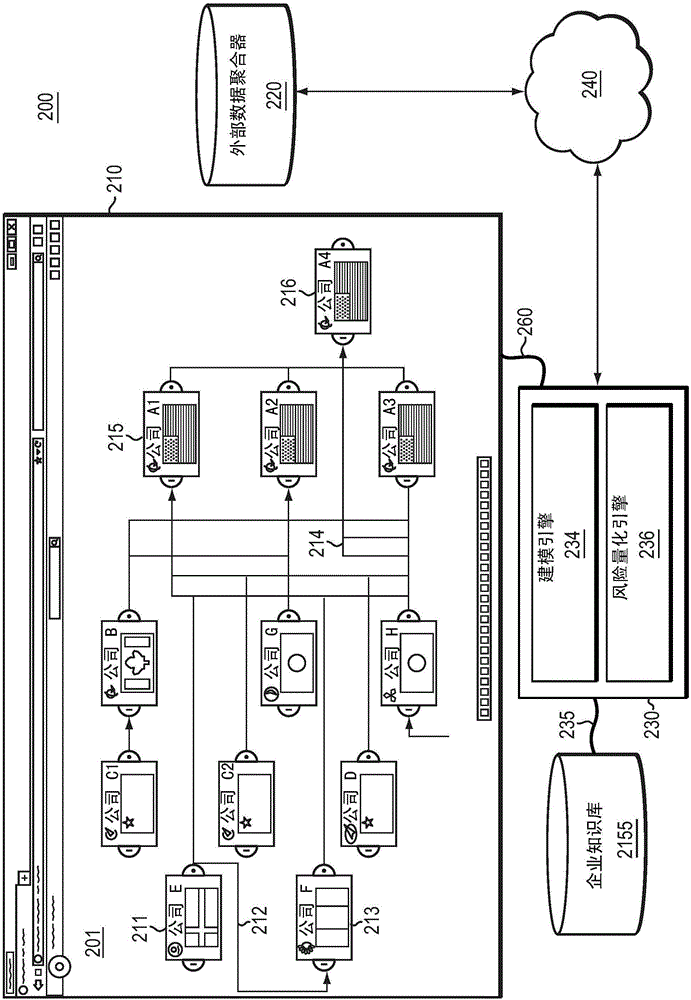
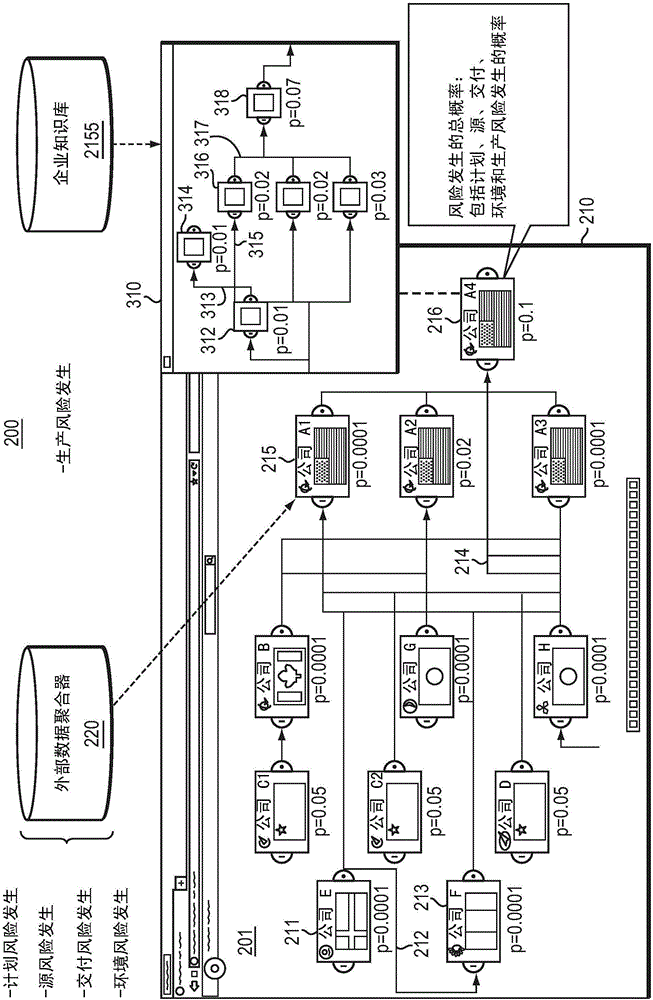
System and method for risk detection reporting and infrastructure
InactiveUS20050021360A1Efficiently monitor riskFlexibility in modifying and updatingFinanceMemory loss protectionPaper documentDocument preparation
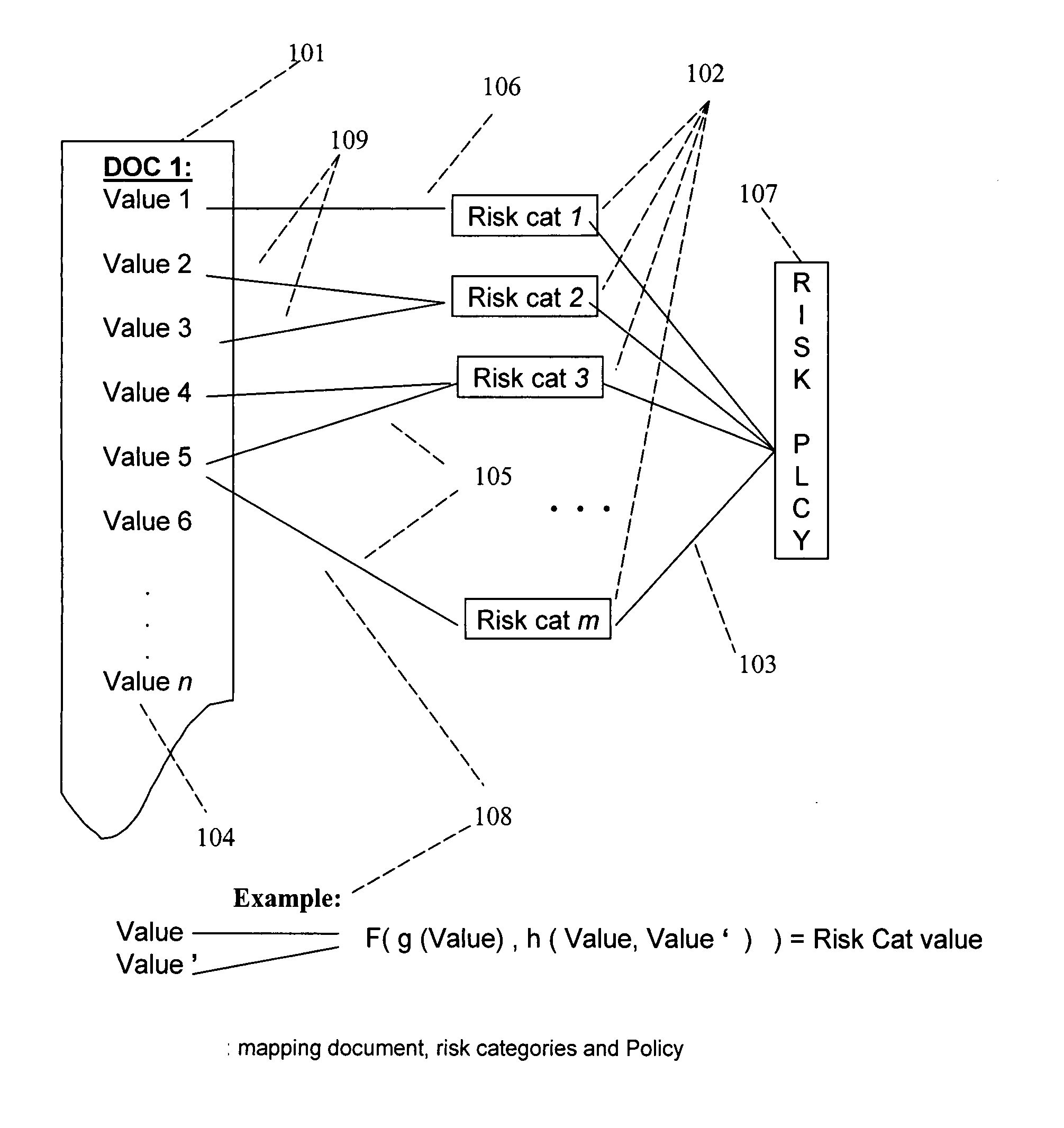
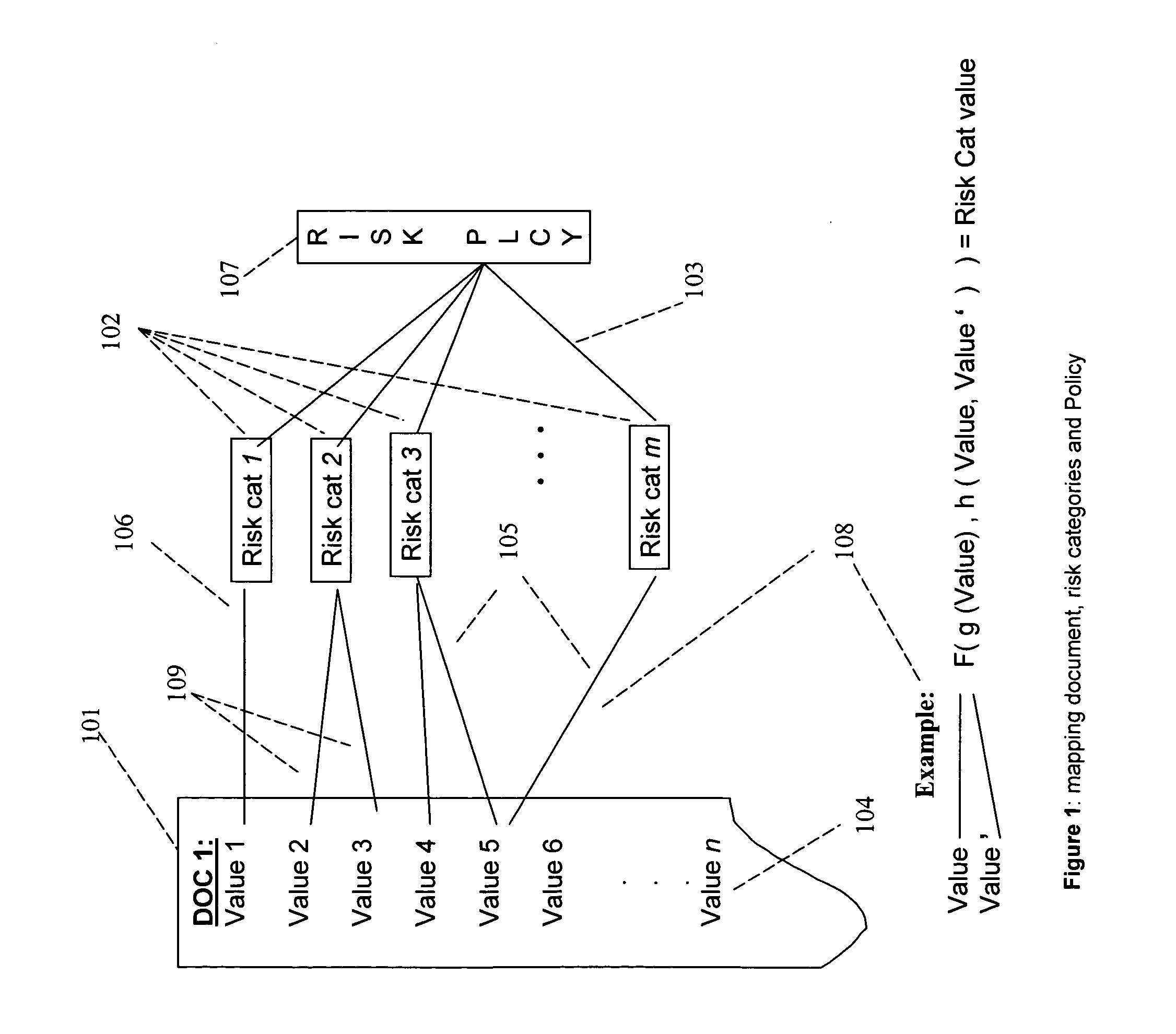
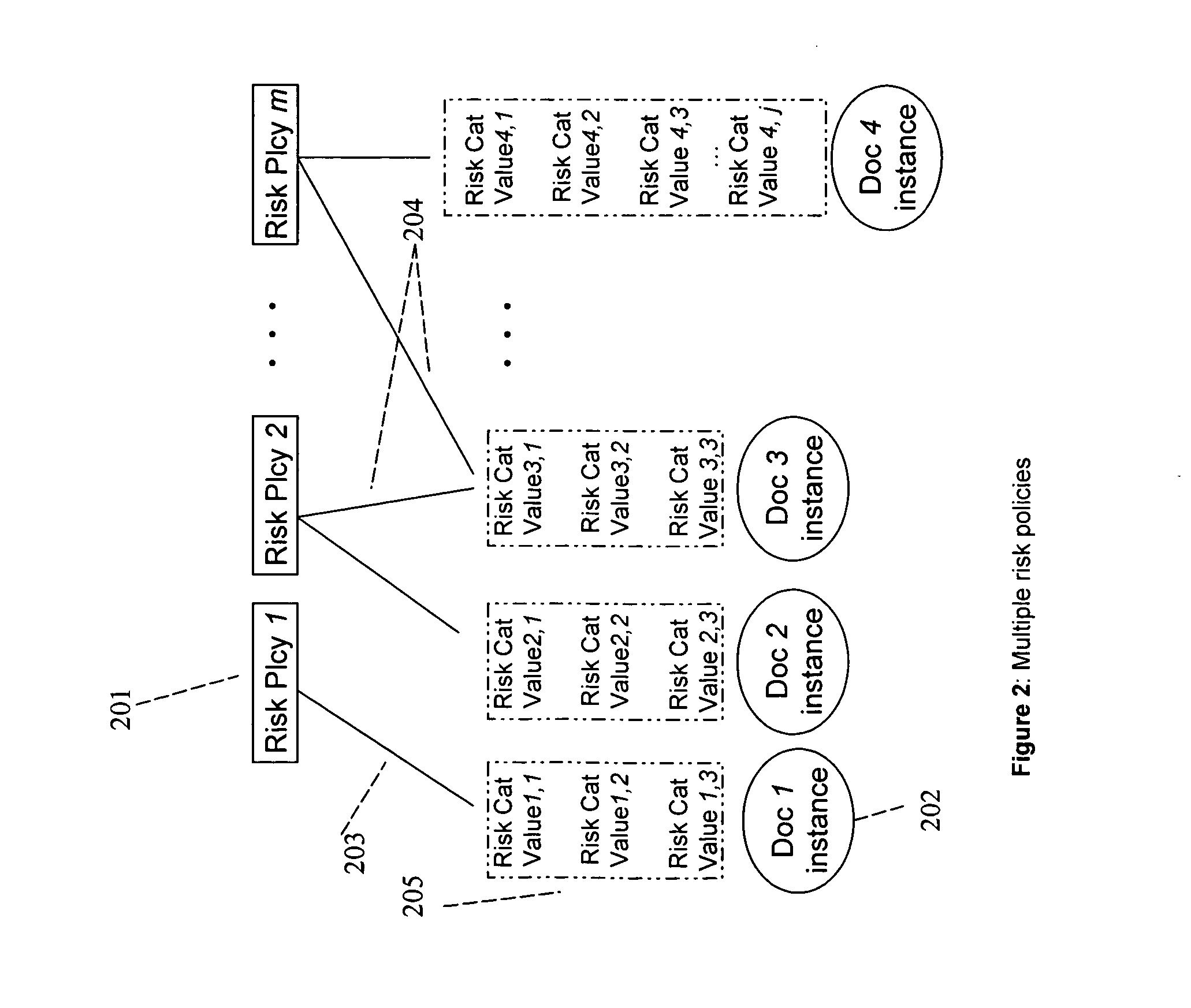
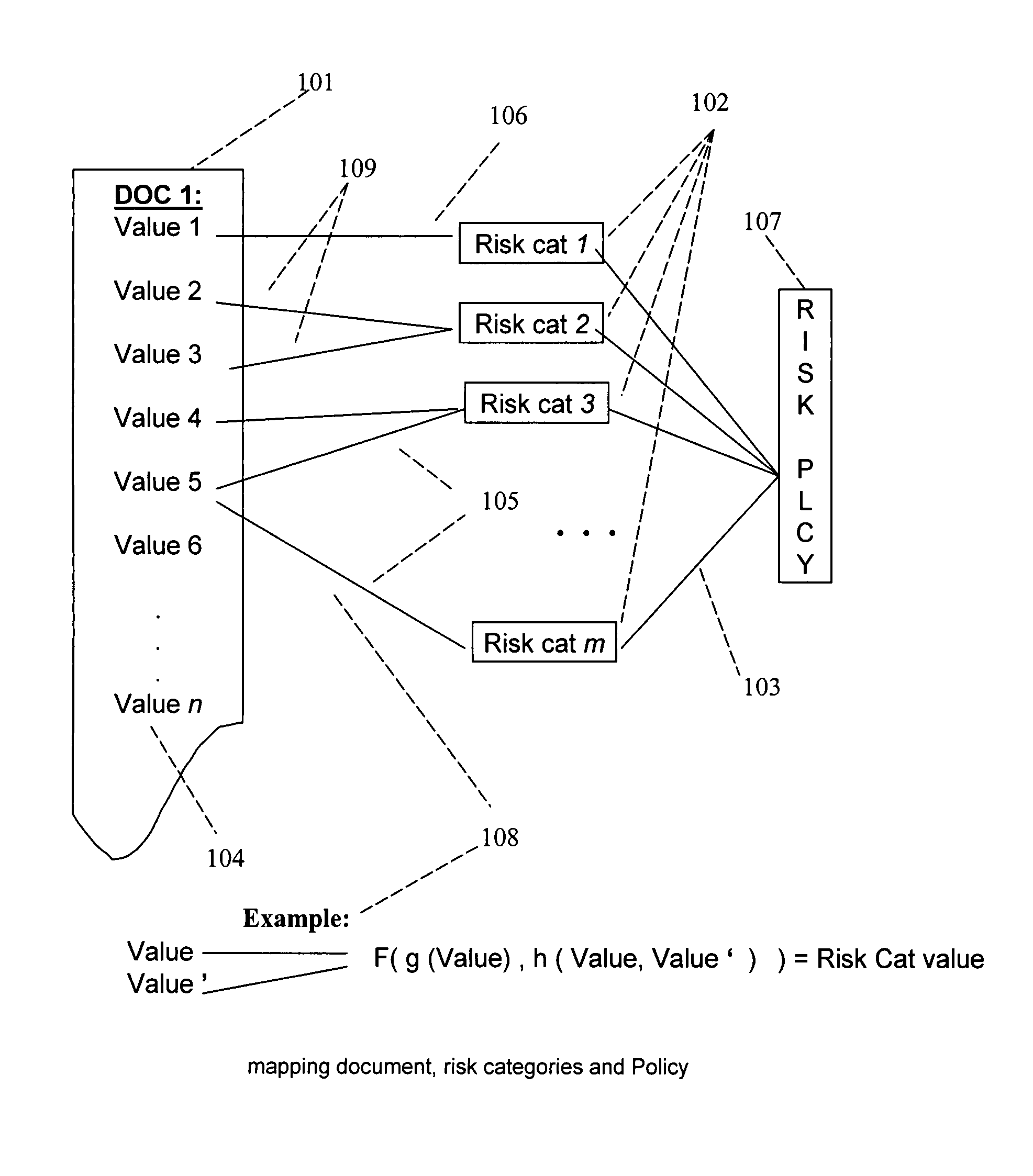
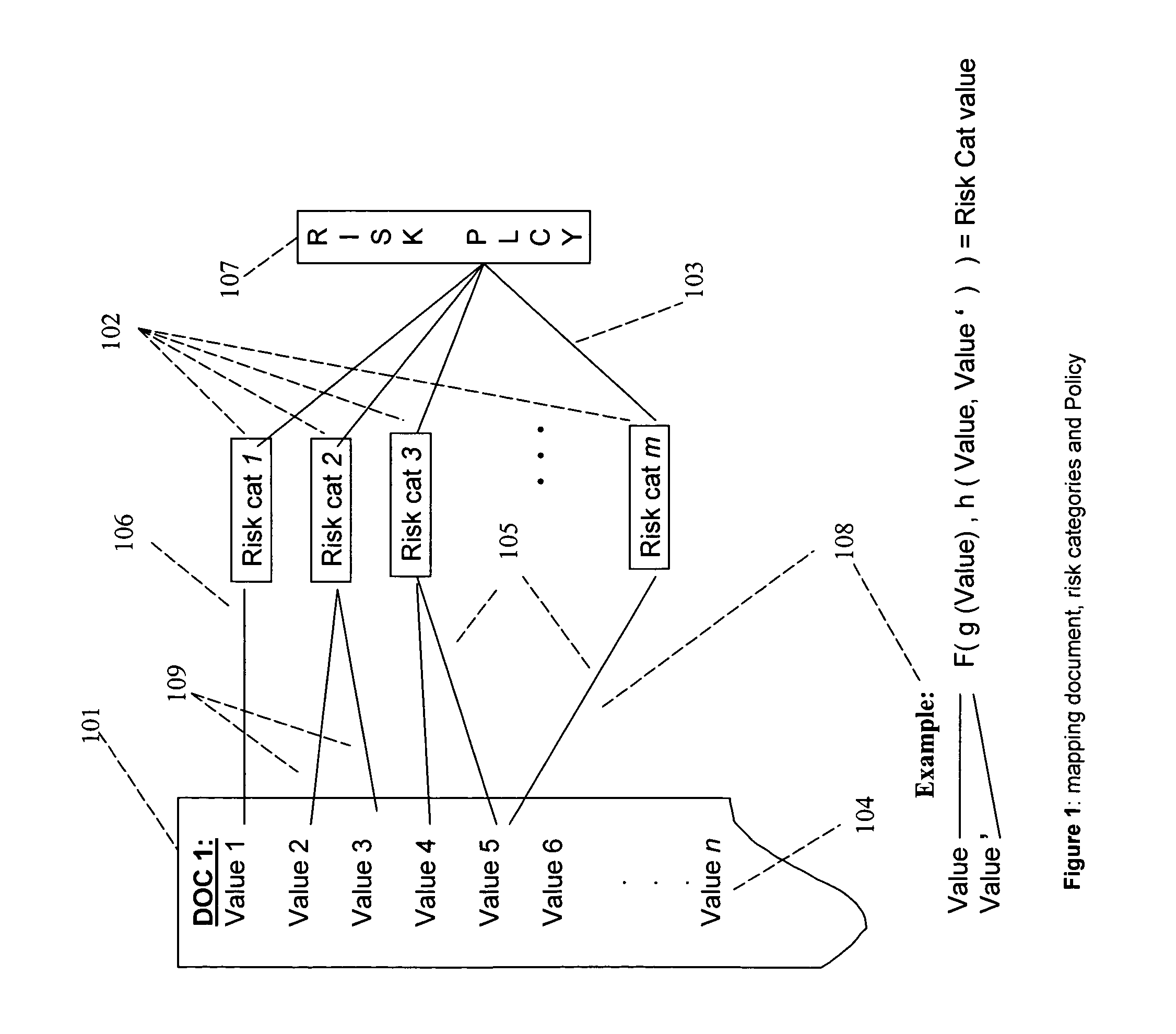
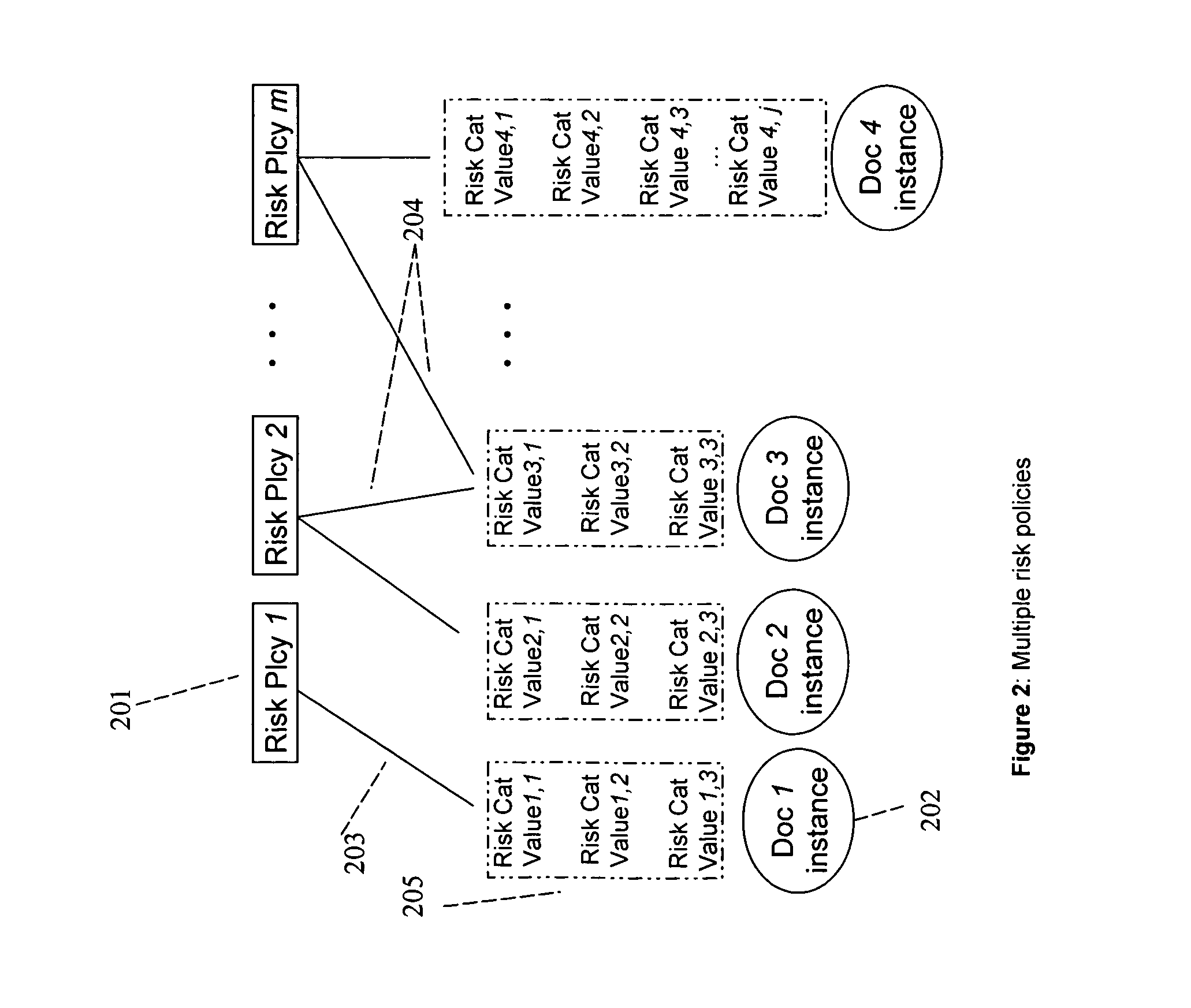
A method, a system, and a device for monitoring risks associated with at least one business process, including: evaluating at least one of a plurality of document instances, wherein each of the document instances includes, in association therewith, a plurality of document values, against a plurality of risk categories; implementing the plurality of risk categories pursuant to at least one acceptable risk policy approved for the at least one business process; and qualifying at least one of the at least one of the plurality of documents pursuant to an approval rating of the at least one document in at least one risk category. The system, method, and device efficiently monitor risk, and allow for flexibility in modifying or updating risk policy.
Owner:SMARTSAFETY SOFTWARE INC
System and method for risk detection reporting and infrastructure
InactiveUS8484066B2Efficiently monitor riskFlexibility in modifying and updatingFinanceMemory loss protectionData miningDocumentation
A method, a system, and a device for monitoring risks associated with at least one business process, including: evaluating at least one of a plurality of document instances, wherein each of the document instances includes, in association therewith, a plurality of document values, against a plurality of risk categories; implementing the plurality of risk categories pursuant to at least one acceptable risk policy approved for the at least one business process; and qualifying at least one of the at least one of the plurality of documents pursuant to an approval rating of the at least one document in at least one risk category. The system, method, and device efficiently monitor risk, and allow for flexibility in modifying or updating risk policy.
Owner:SMARTSAFETY SOFTWARE INC
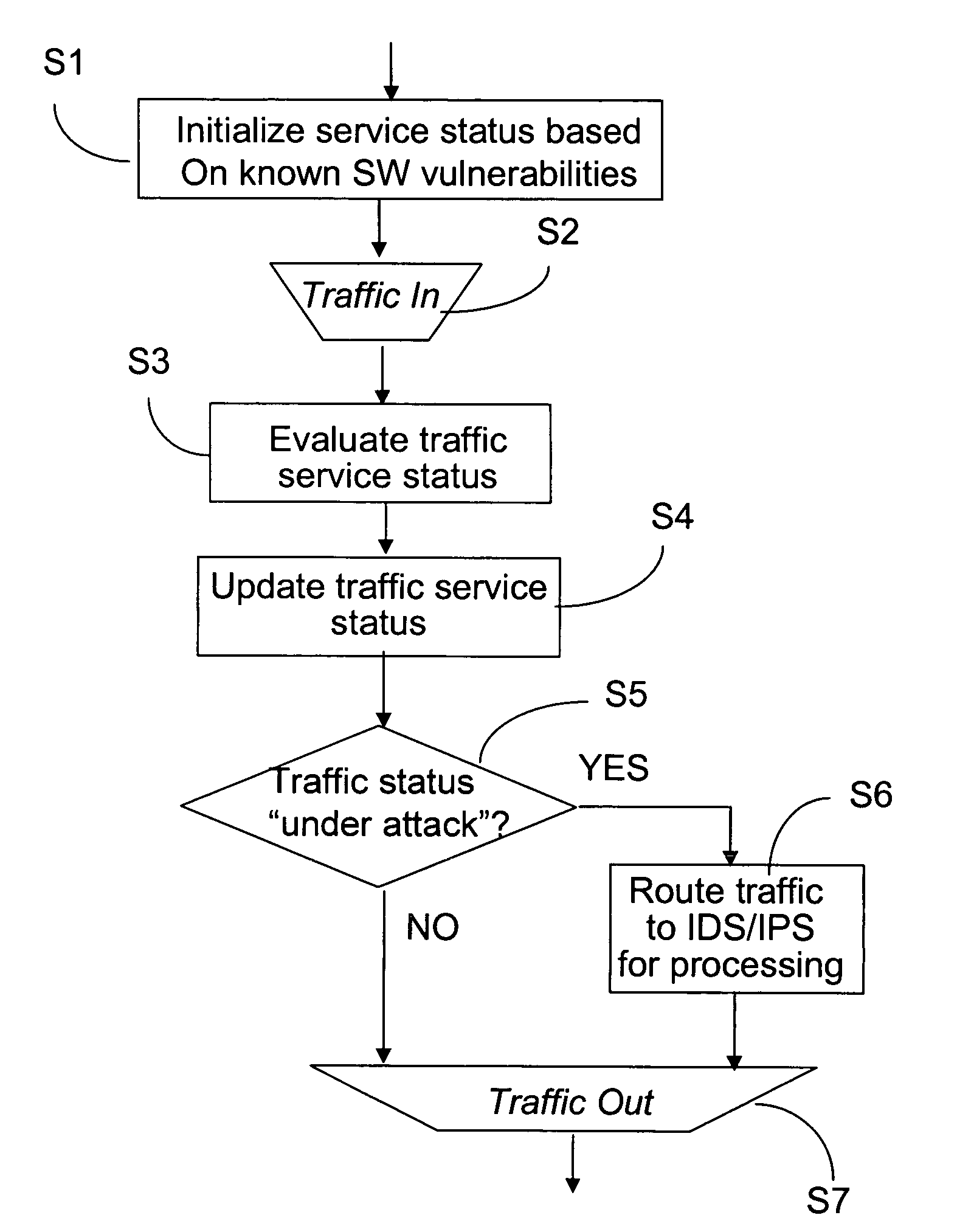
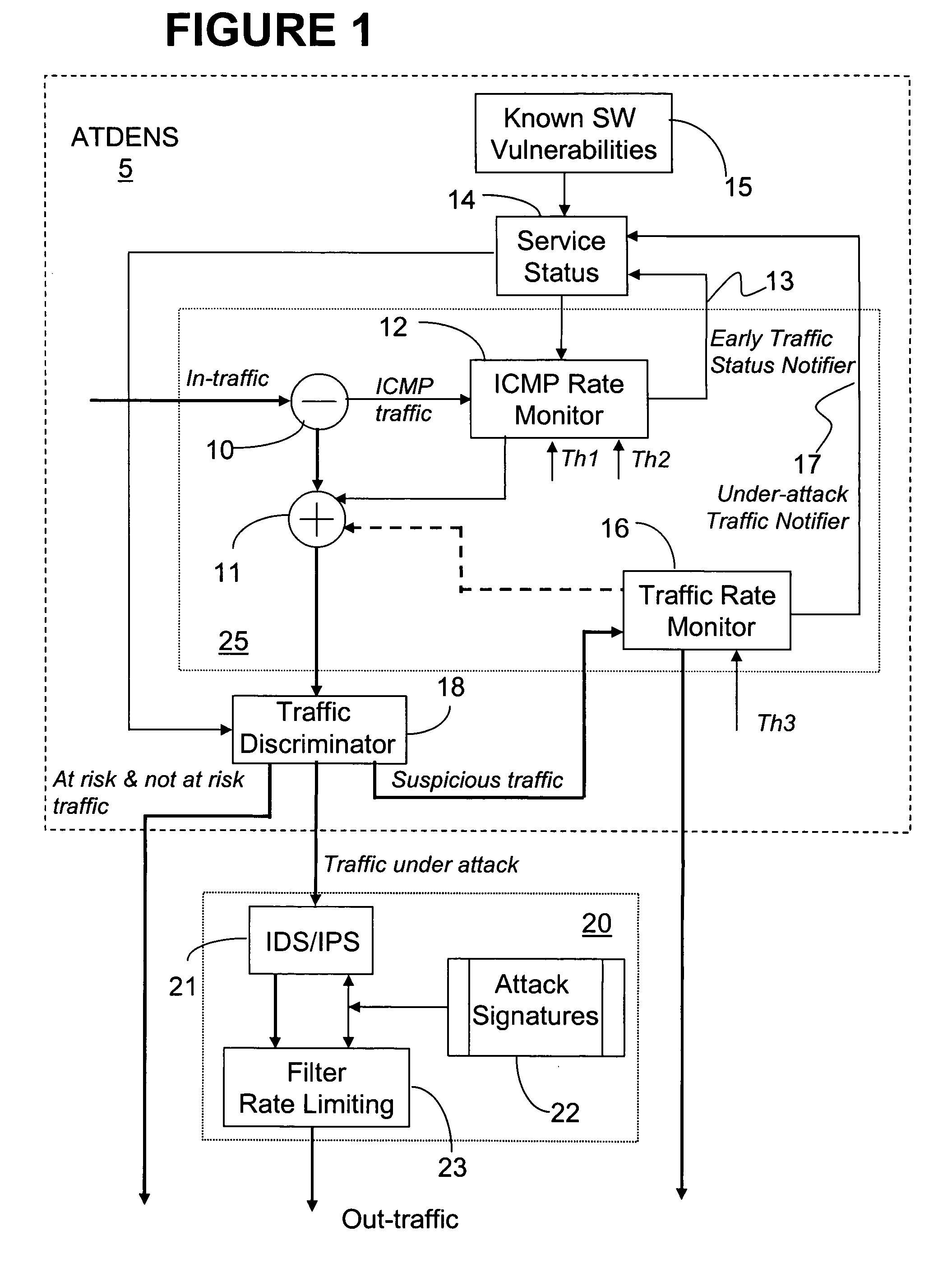
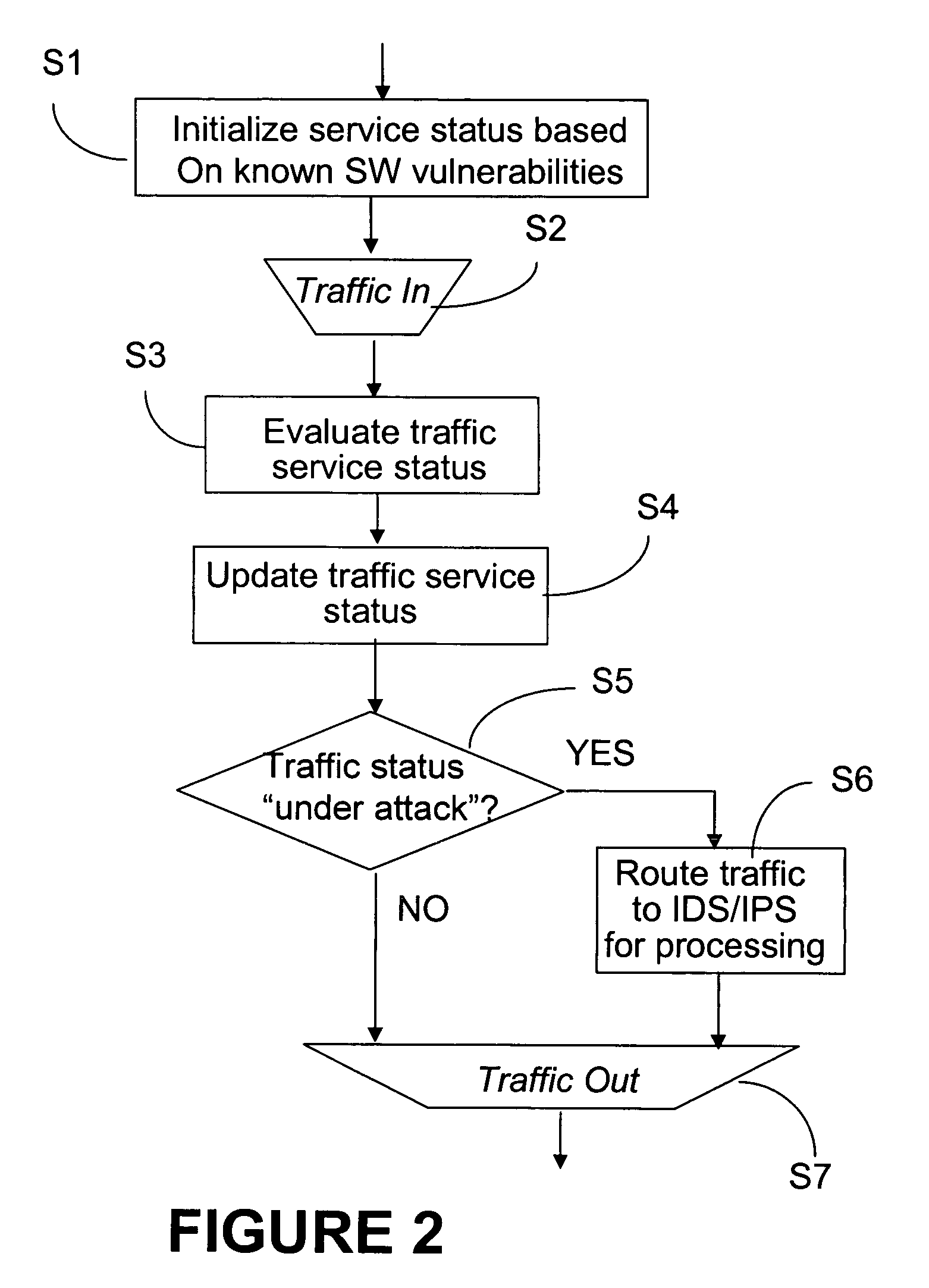
System and method for detecting abnormal traffic based on early notification
ActiveUS20070011741A1Reduce trafficFind quicklyMemory loss protectionError detection/correctionTraffic capacityMalware
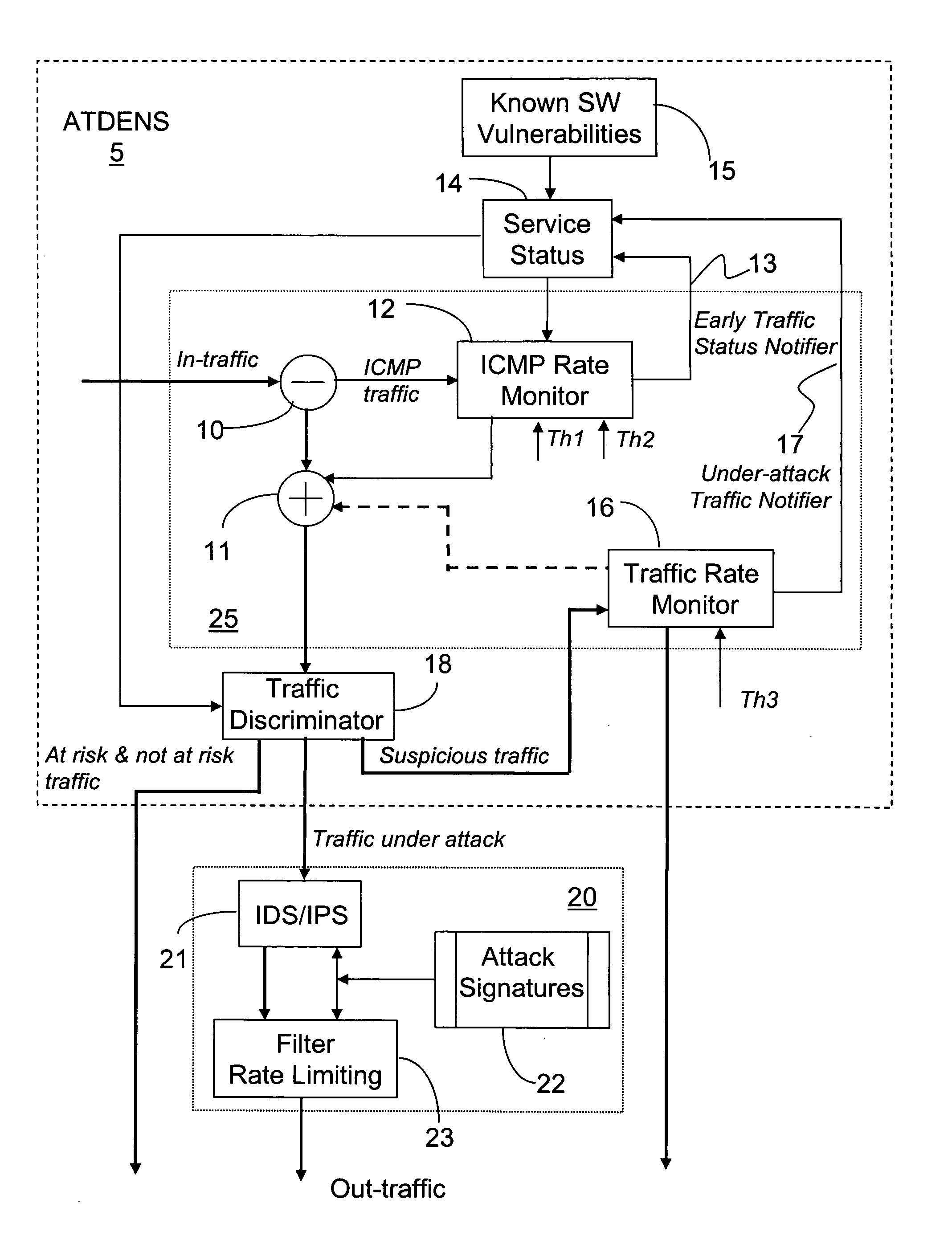
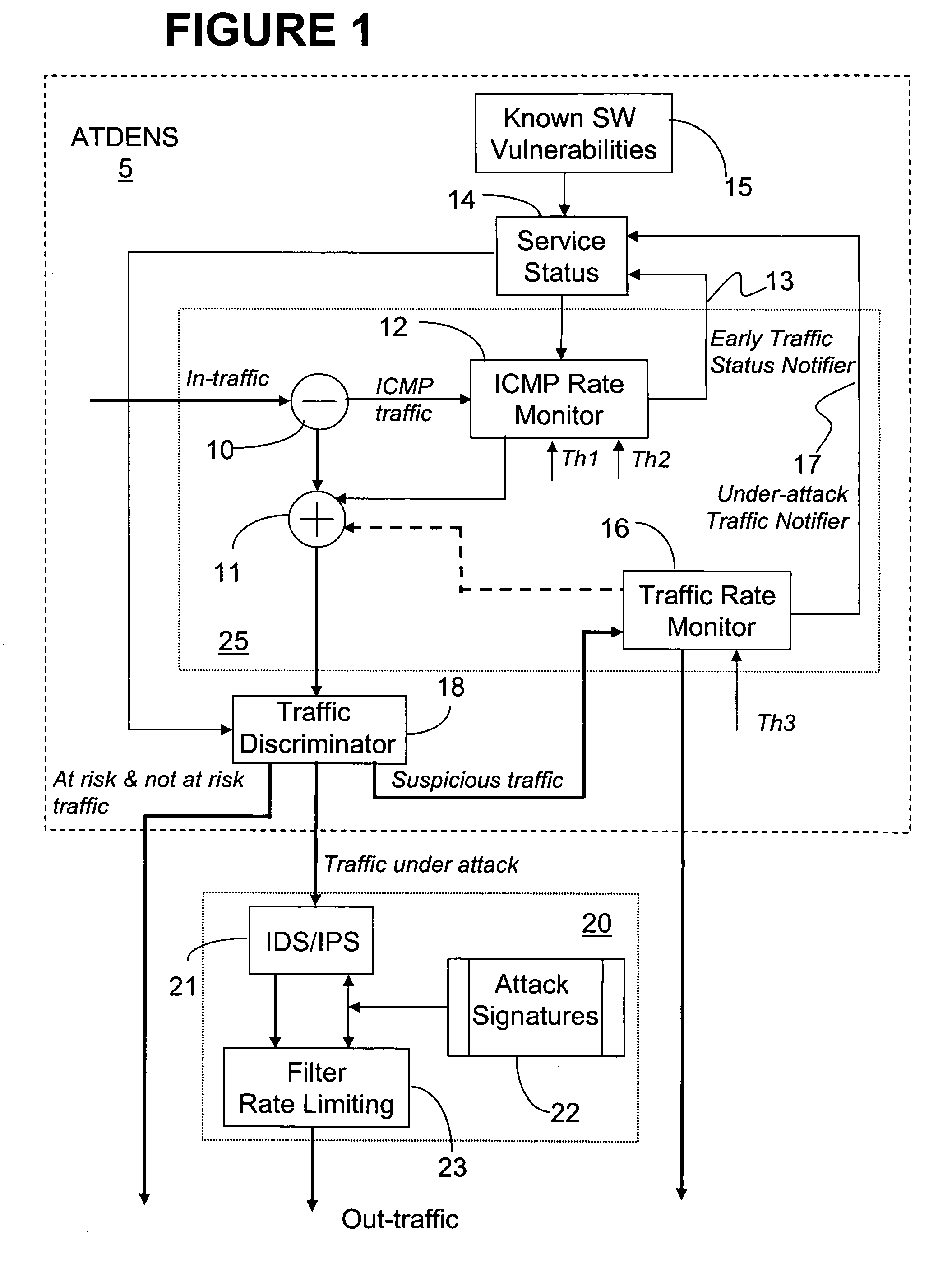
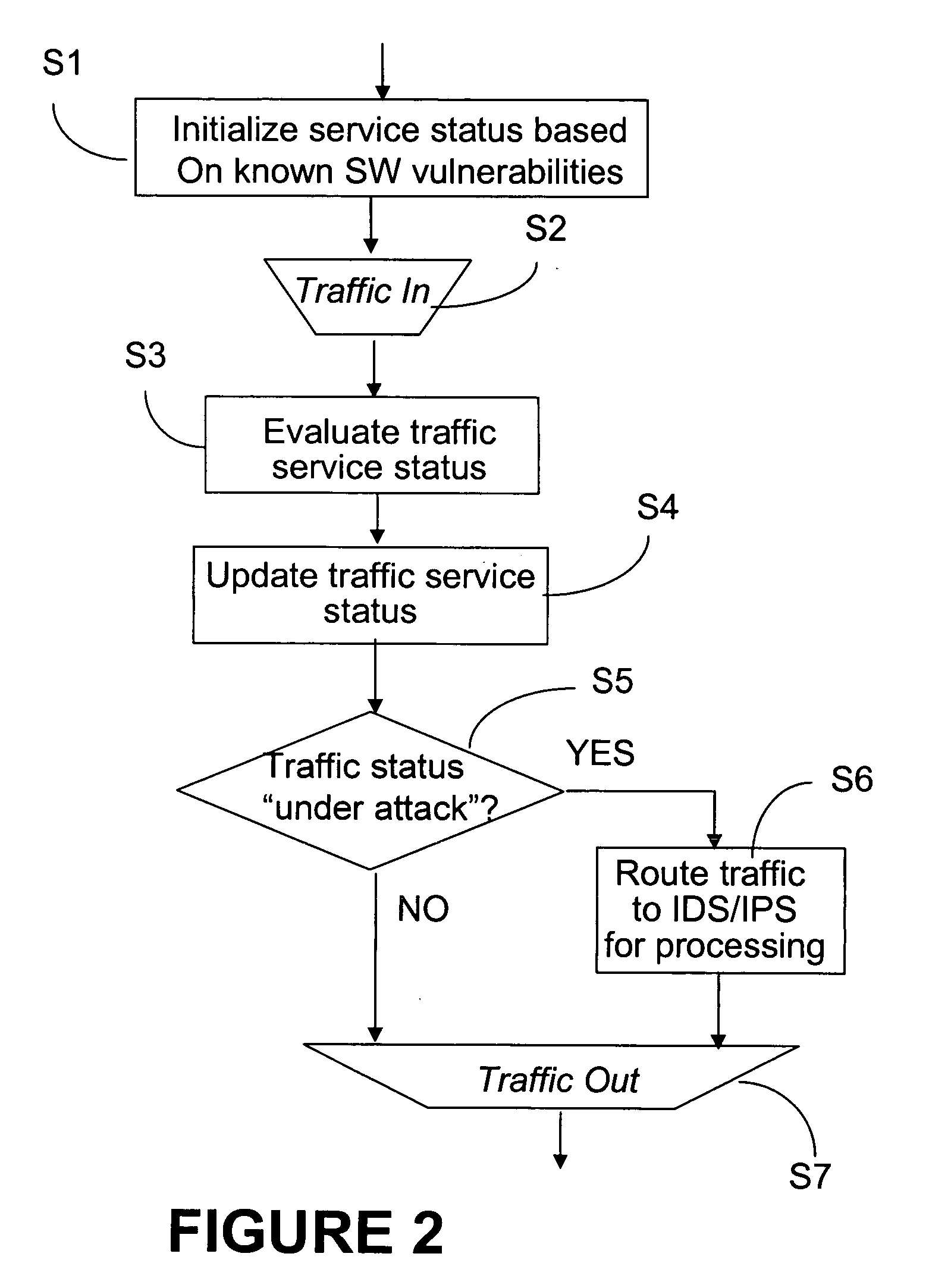
This method and system for detecting abnormal traffic in a communications network is based on classifying the traffic in risk and status categories and maintaining a service status table with this information for each service at a respective node. The risk categories are initially established based on known software vulnerabilities recognized for the respective service. An early notifier enables further processing of services suspected of malware propagation. Status categories enable segregating the traffic with a “under attack status” from the“non under attack” status, so that the intrusion detection system at the respective node only processes the “under attack” traffic. In this way, the time and amount of processing performed by the intrusion detection system is considerably reduced.
Owner:ALCATEL LUCENT SAS
Method of Identifying Myelodysplastic Syndromes
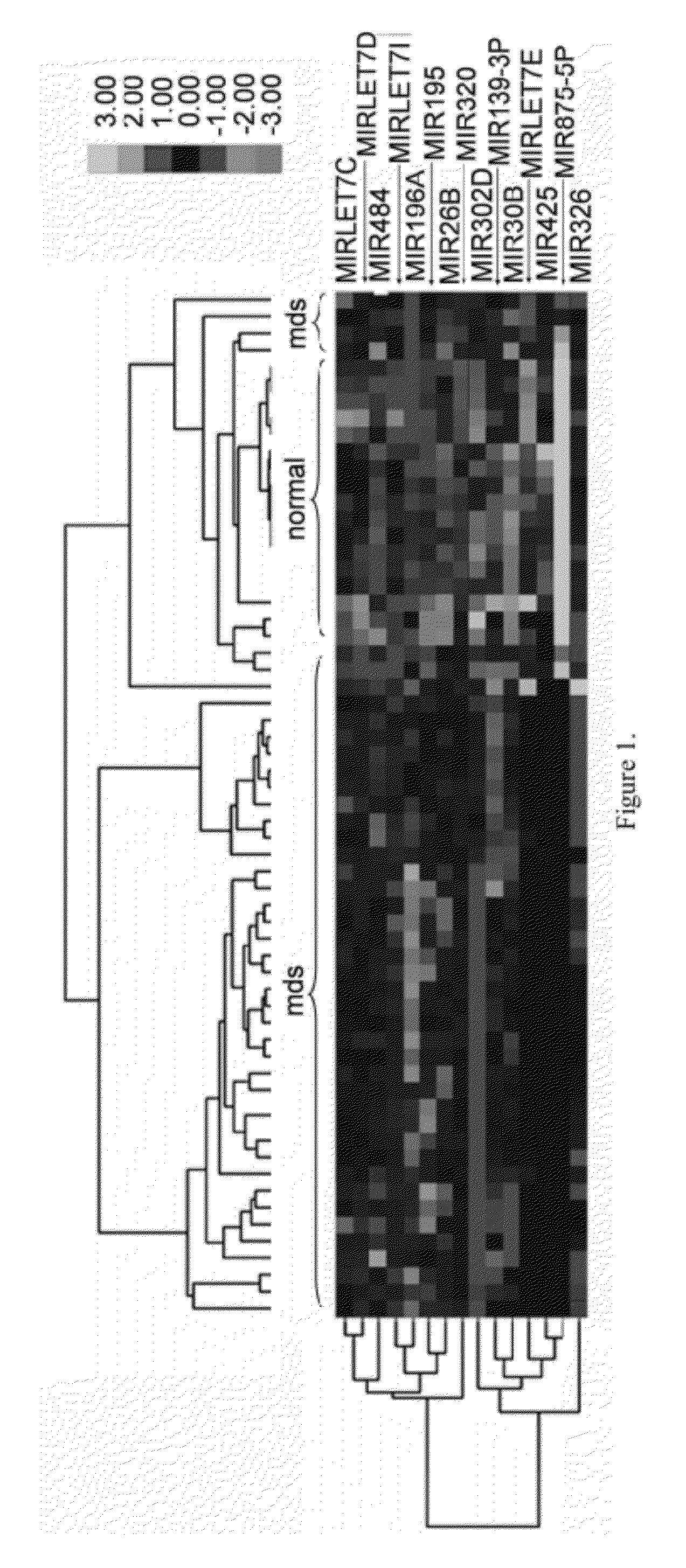
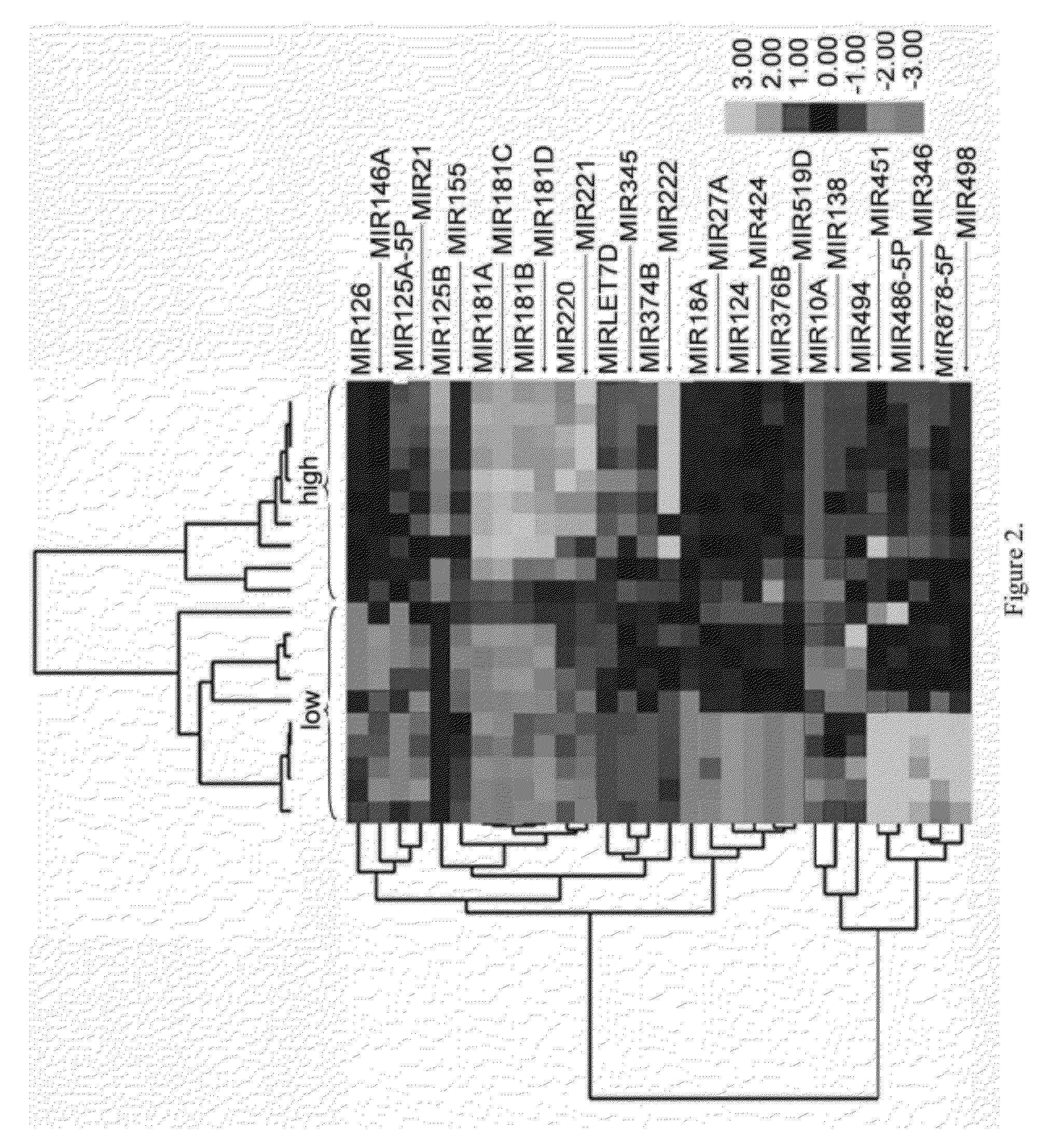
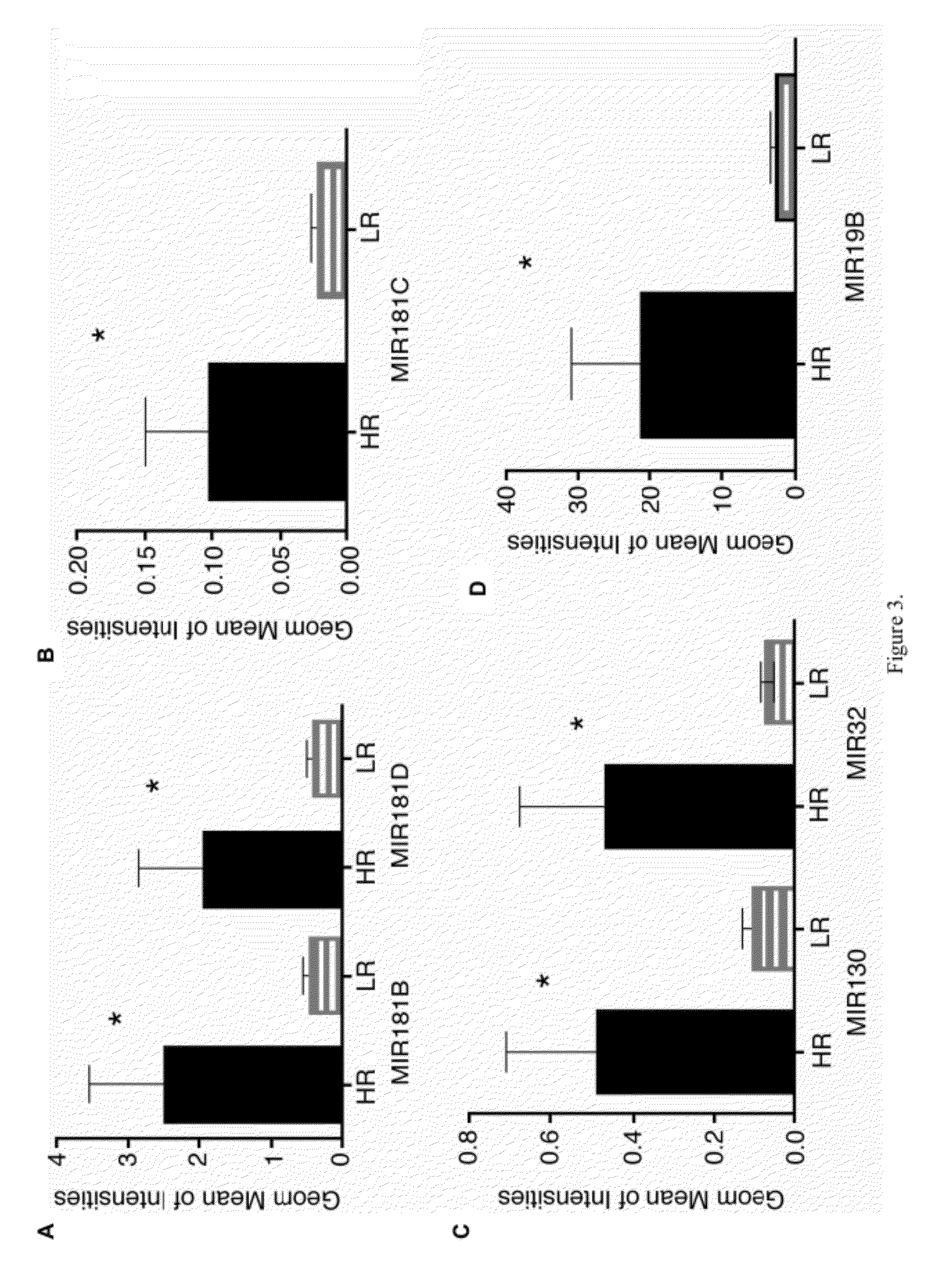
Myelodysplastic syndromes display both hematological and biological heterogeneity with variable leukemia potential. To determine whether microRNAs expression offers diagnostic discrimination or influences malignant potential in MDS, bone marrow miRNA expression was investigated from prognostically distinct MDS subsets using a microarray platform. After background subtraction and normalization, data were analyzed indicating thirteen miRNA signature with statistically significant differential expression, including down-regulation of members of a leukemia associated miRNA family. A unique signature consisting of 10 miRNAs was closely associated with International Prognostic Scoring System risk category permitting discrimination between lower and higher risk disease. Selective overexpression of miRNA-181 family members was detected in higher risk MDS, indicating pathogenetic overlap with acute myeloid leukemia. Analysis of miRNA expression profile offers diagnostic utility, and provides pathogenetic and prognostic discimination in MDS.
Owner:H LEE MOFFITT CANCER CENT & RES INST INC
Method and system for recording carious lesions
InactiveUS7343305B2Efficiently and effectively chartEfficient and reliableTeeth fillingDiagnostic recording/measuringDental patientsDisease
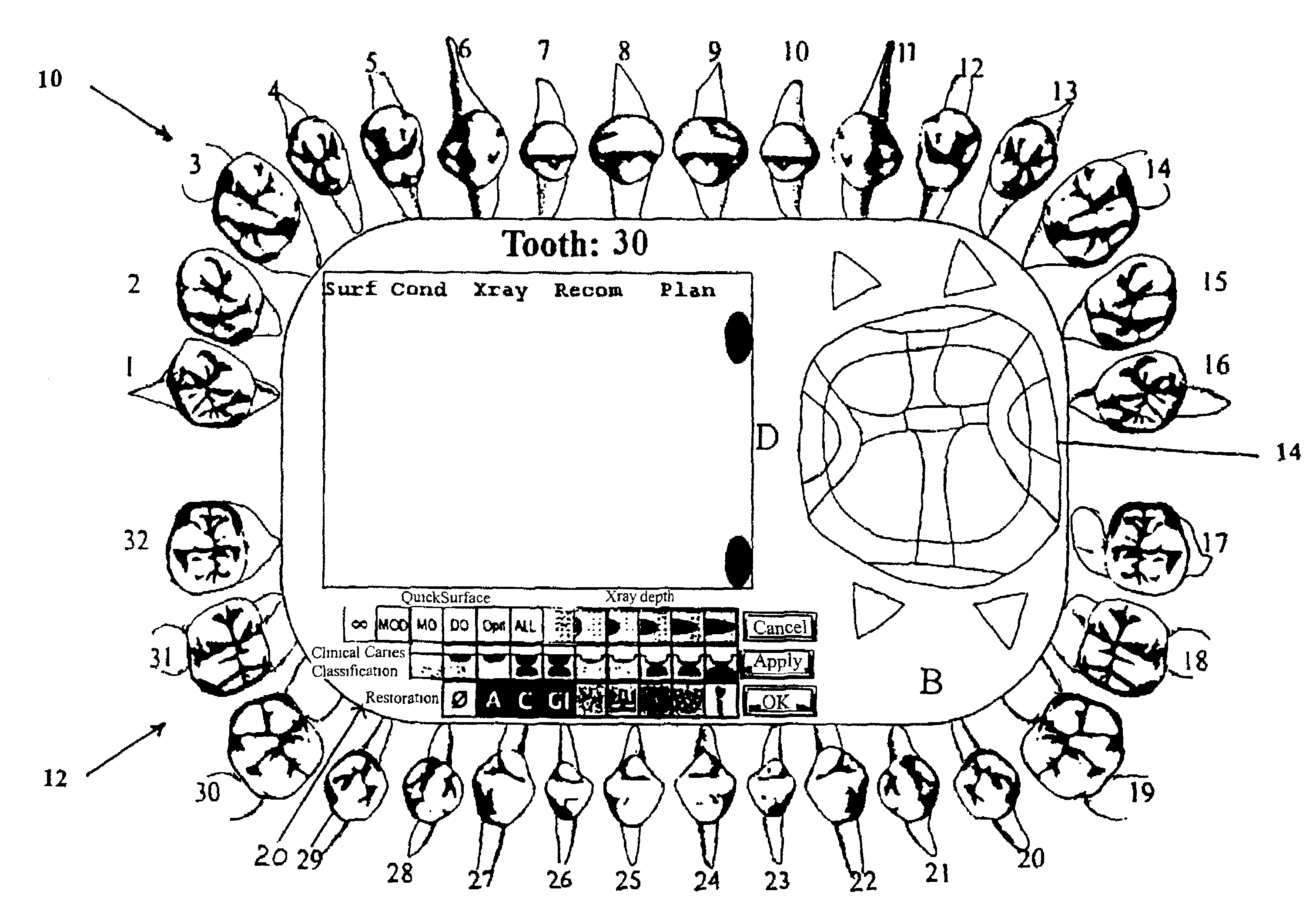
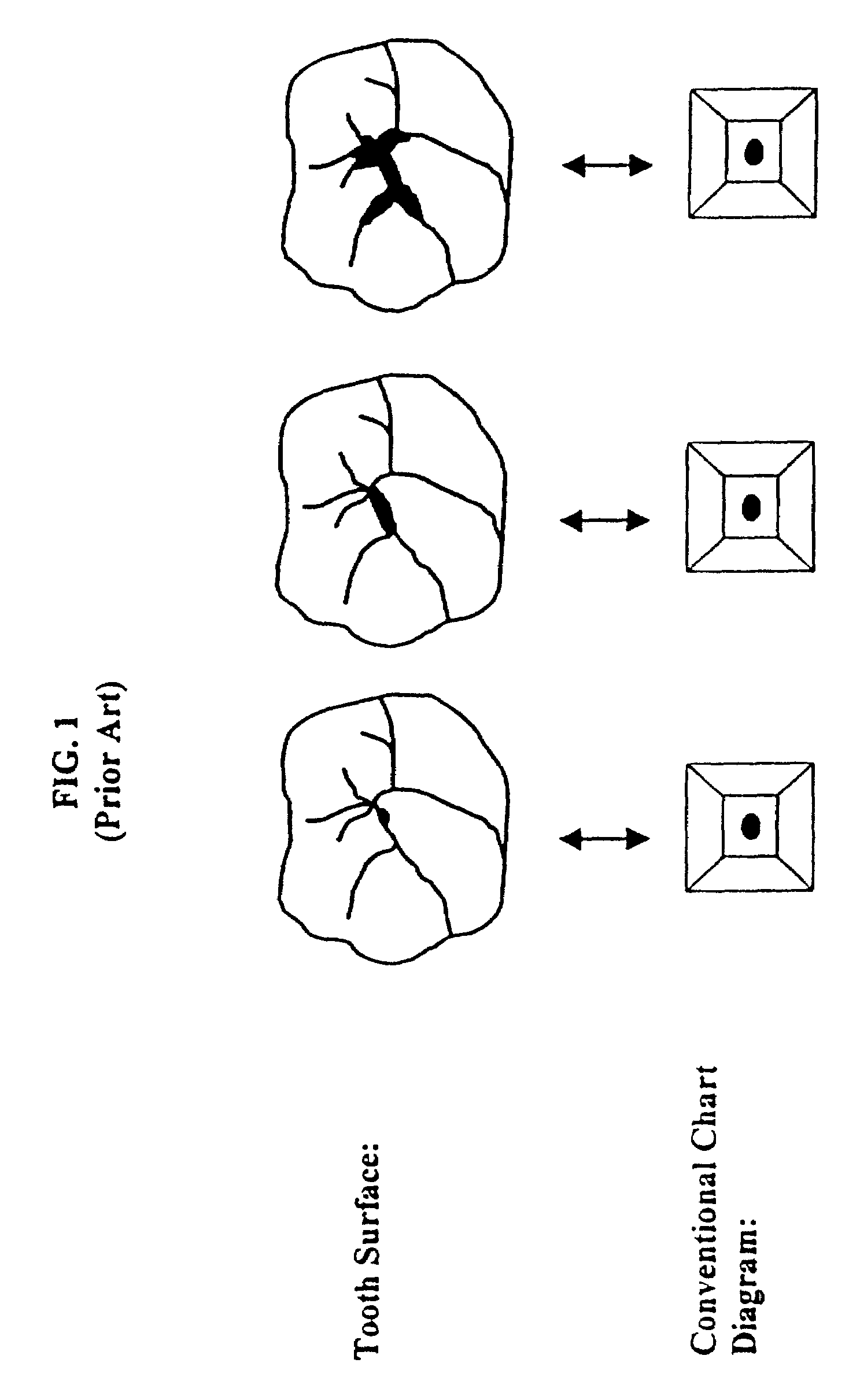
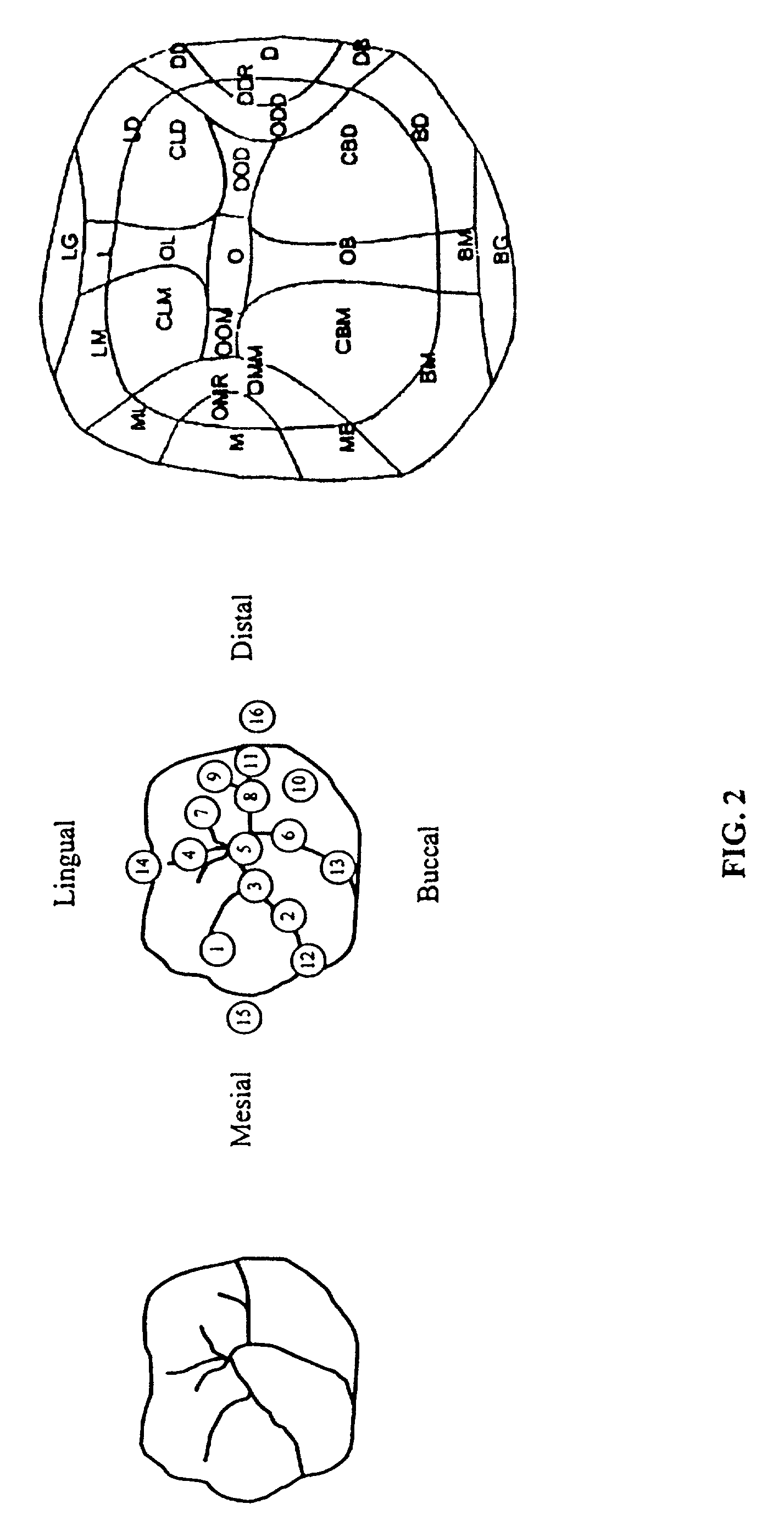
A method and system is provided for charting tooth decay to assist in caries management. Specifically, the invention provides a computer system, a Graphical User Interface(GUI), a method, and associated computer code for presenting an interactive tooth chart comprising selectable, anatomically correct tooth icons corresponding to a dental patient's teeth. The invention allows a user to select regions of each individual tooth icon to record the condition of the selected region. According to the invention, a dental patient is selected from a patient data base, the patent's teeth are examined, and the condition of each tooth region is recorded using selectable icons. The invention further provides automatic characterization of dental conditions based on standard values and previously recorded conditions to indicate progression of disease. In an alternative embodiment, the invention provides a recommended course of clinical management based on the information recorded. In another embodiment the invention automatically classifies patients into risk categories and provides suggested x-ray exam intervals. Thus, particular advantages of the current invention include ease of recording dental conditions, more accurate dental charting, and automatic analysis of recorded dental data, advantageously resulting in better patient care and more efficient use of a dental care provider's time.
Owner:FLORIDA RES FOUND INC THE
Multidimensional risk analysis
InactiveUS20170301024A1Limit number of unnecessaryEconomical environmentDrawing from basic elementsFinanceTime frameRisk category
Owner:DALAL PANKAJ B +1
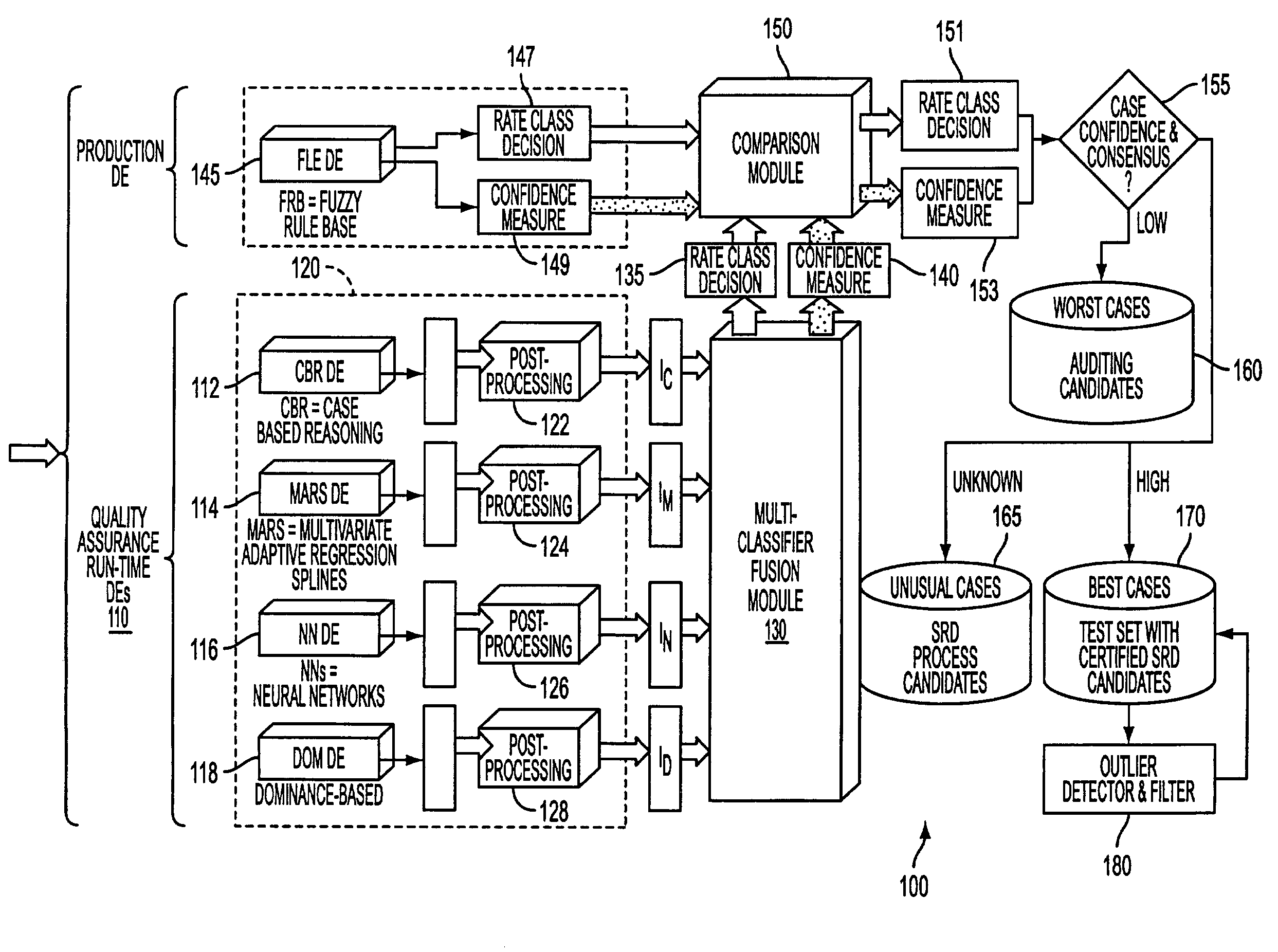
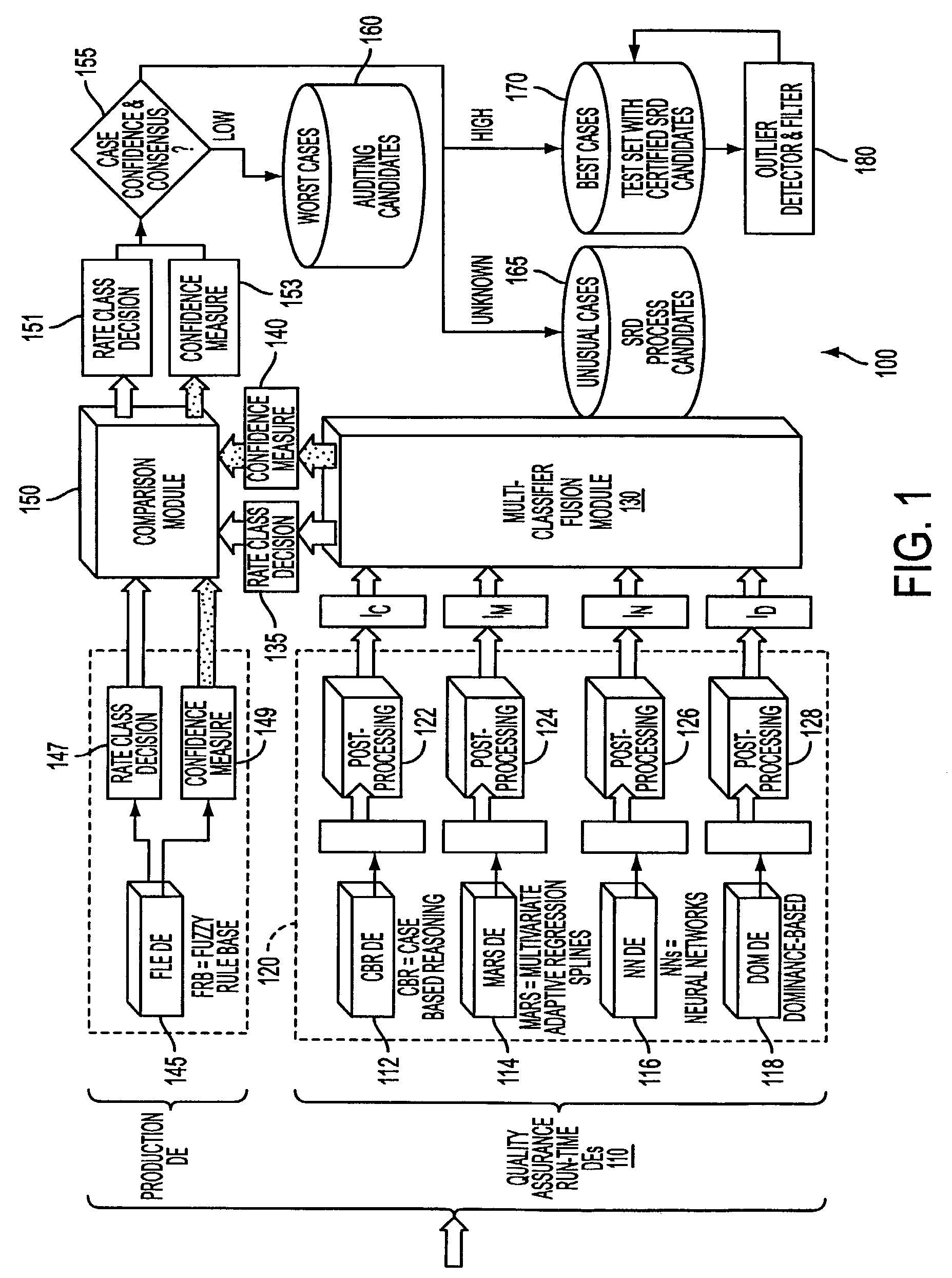
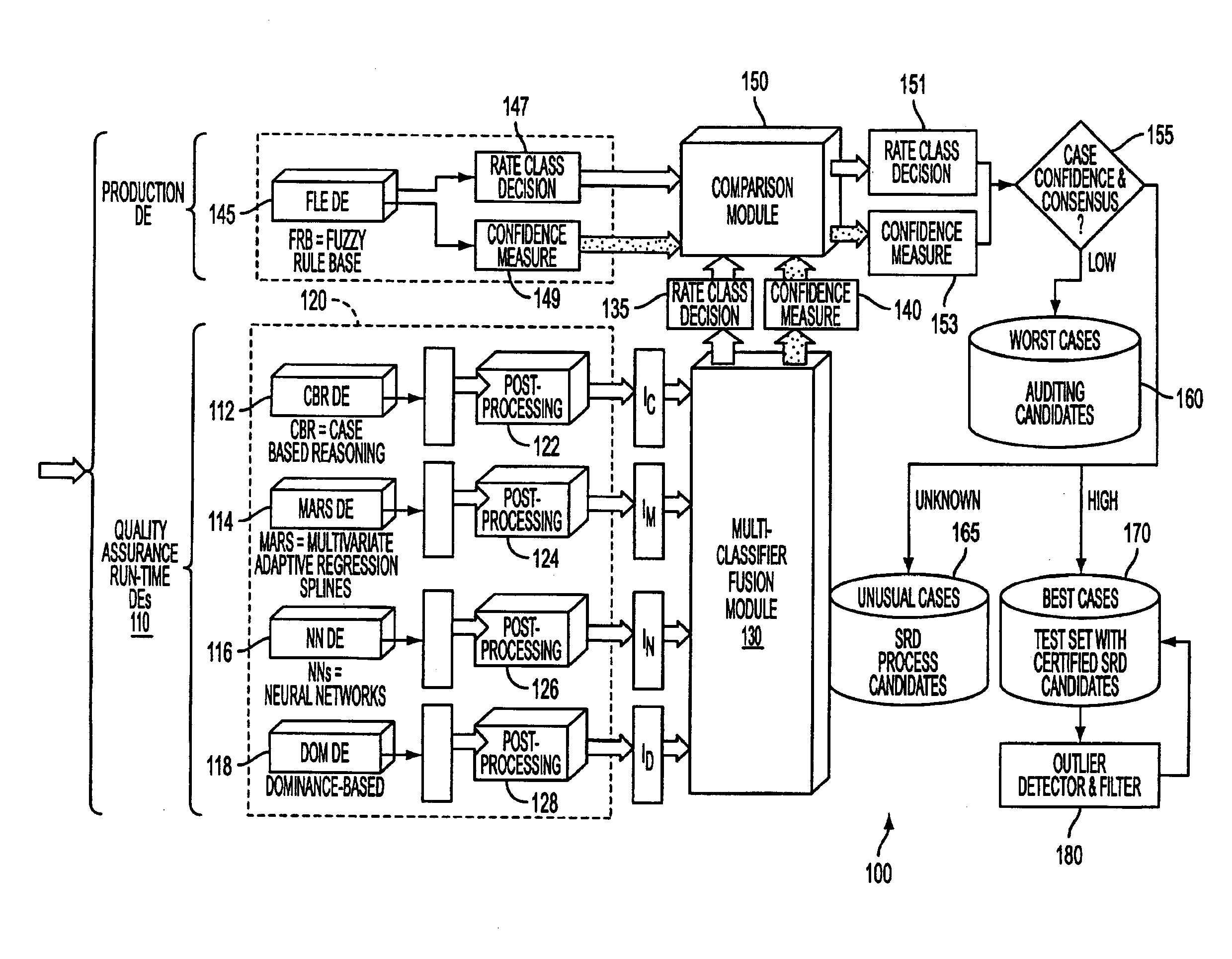
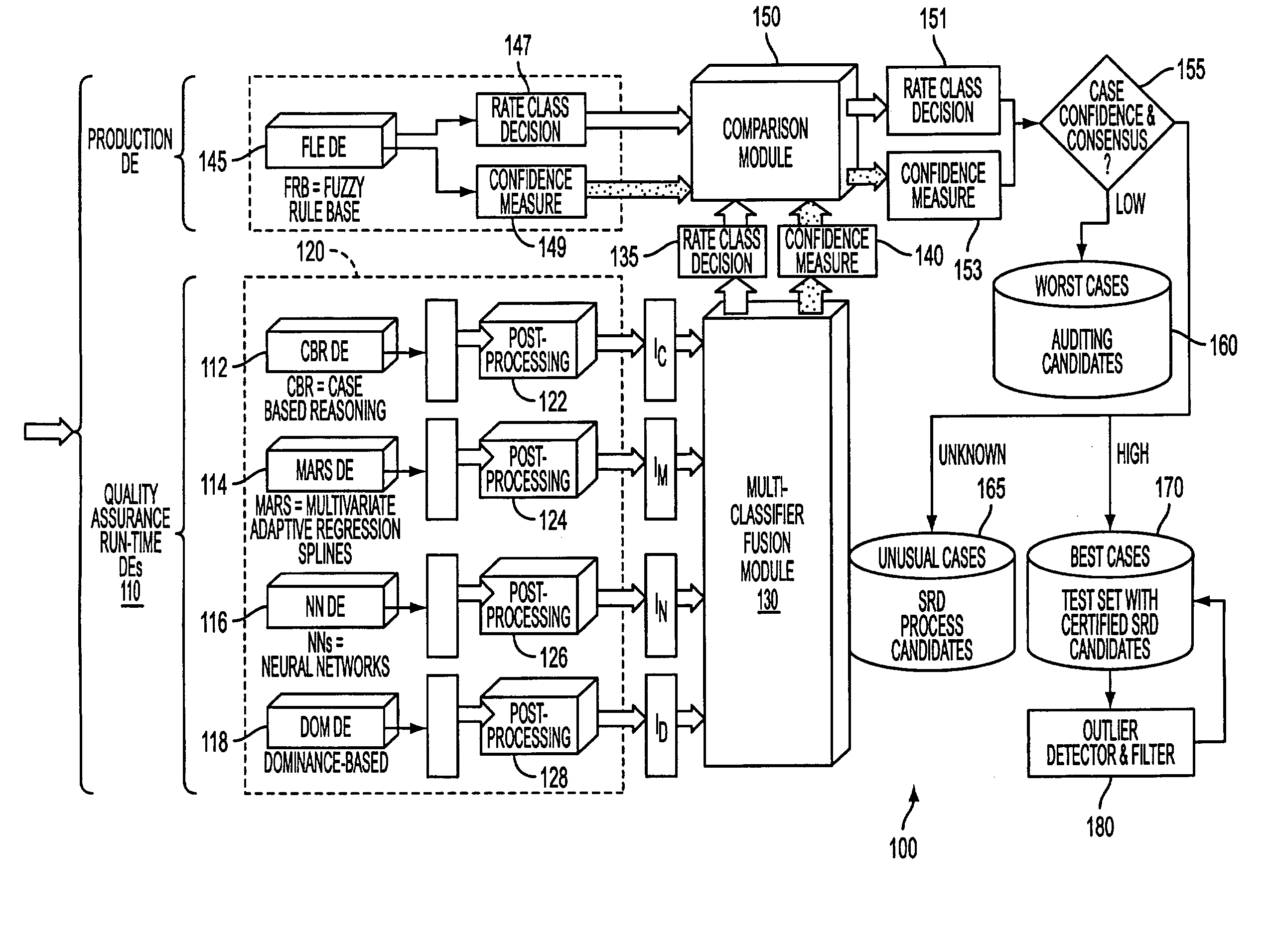
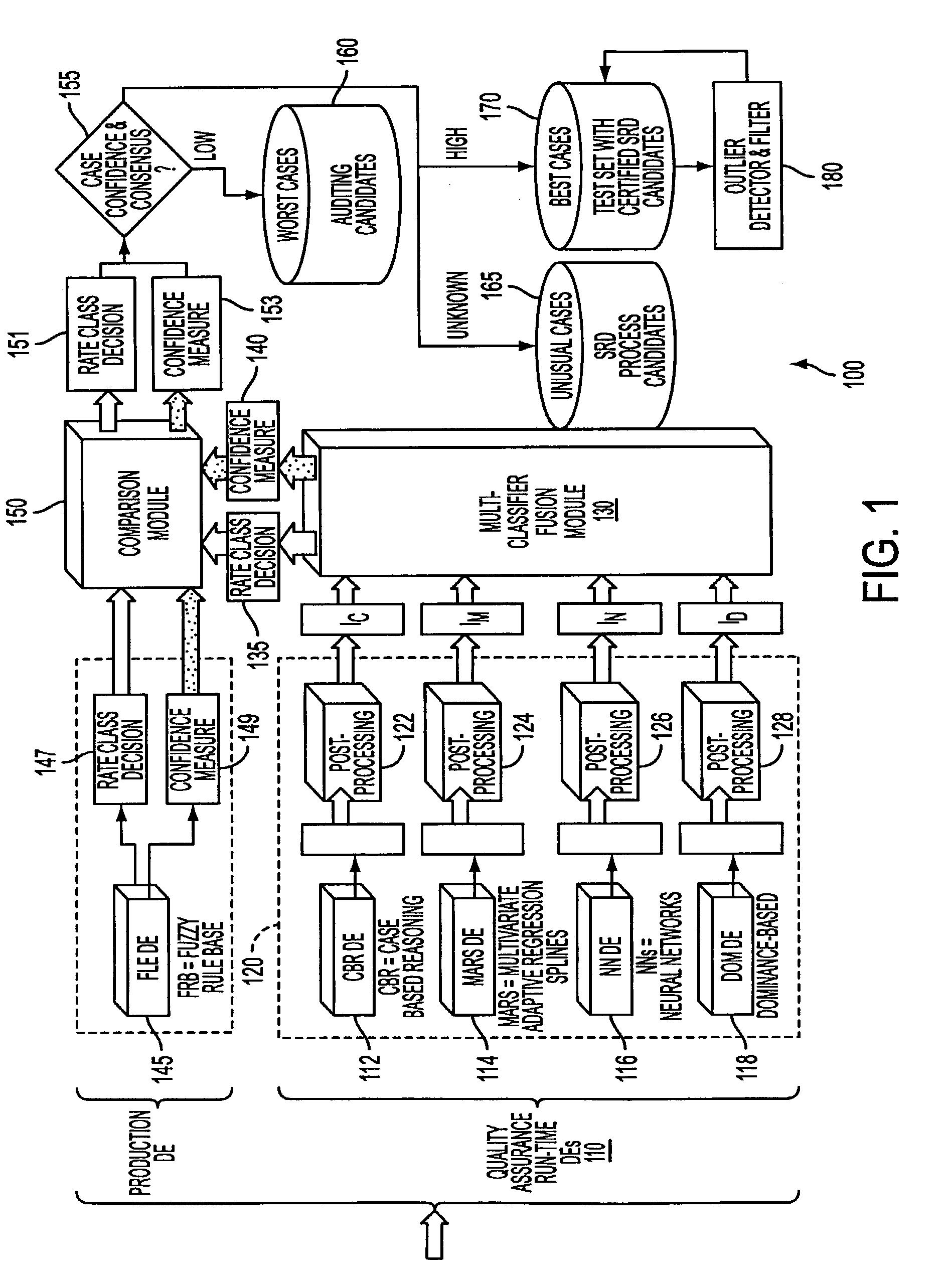
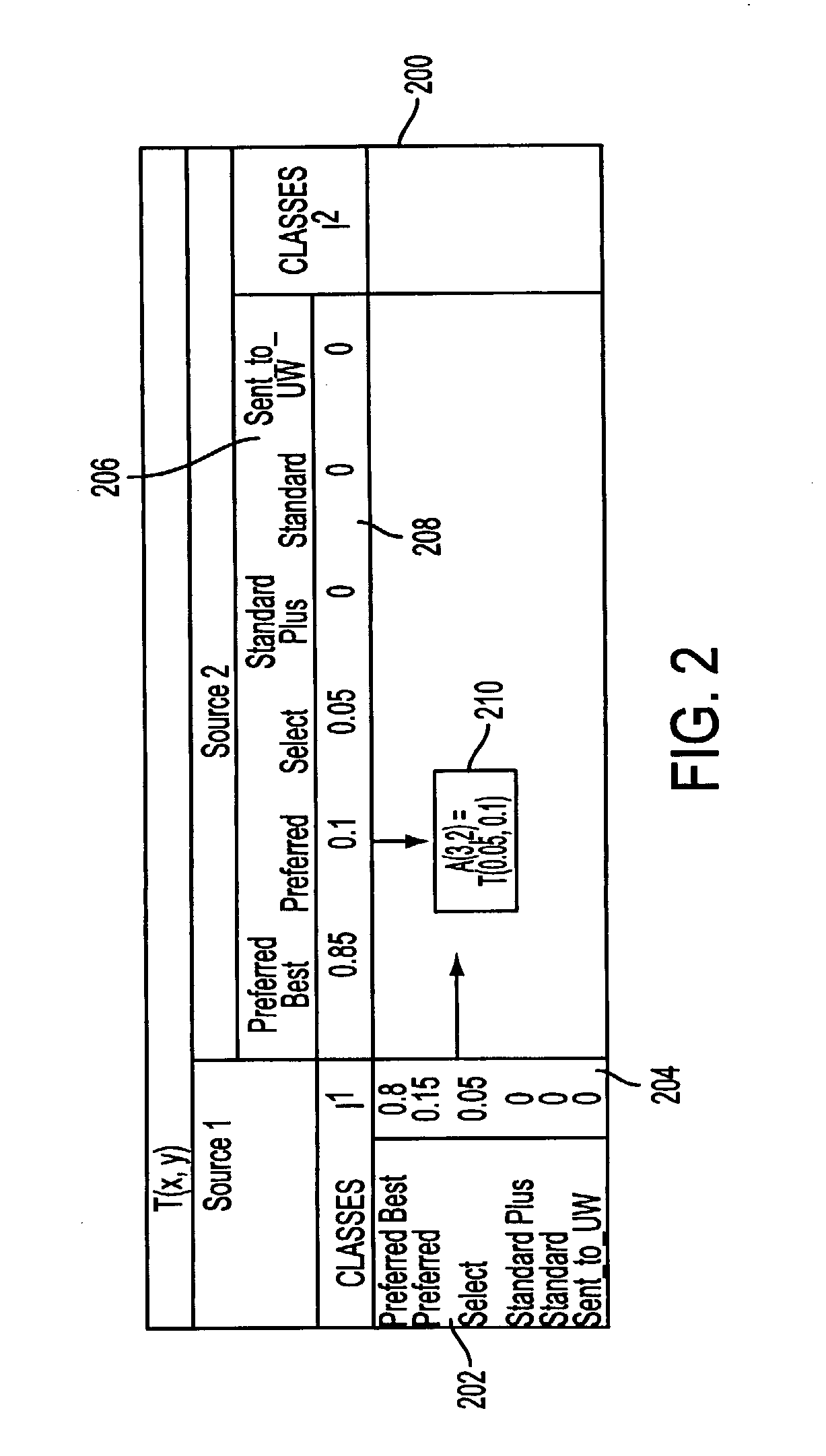
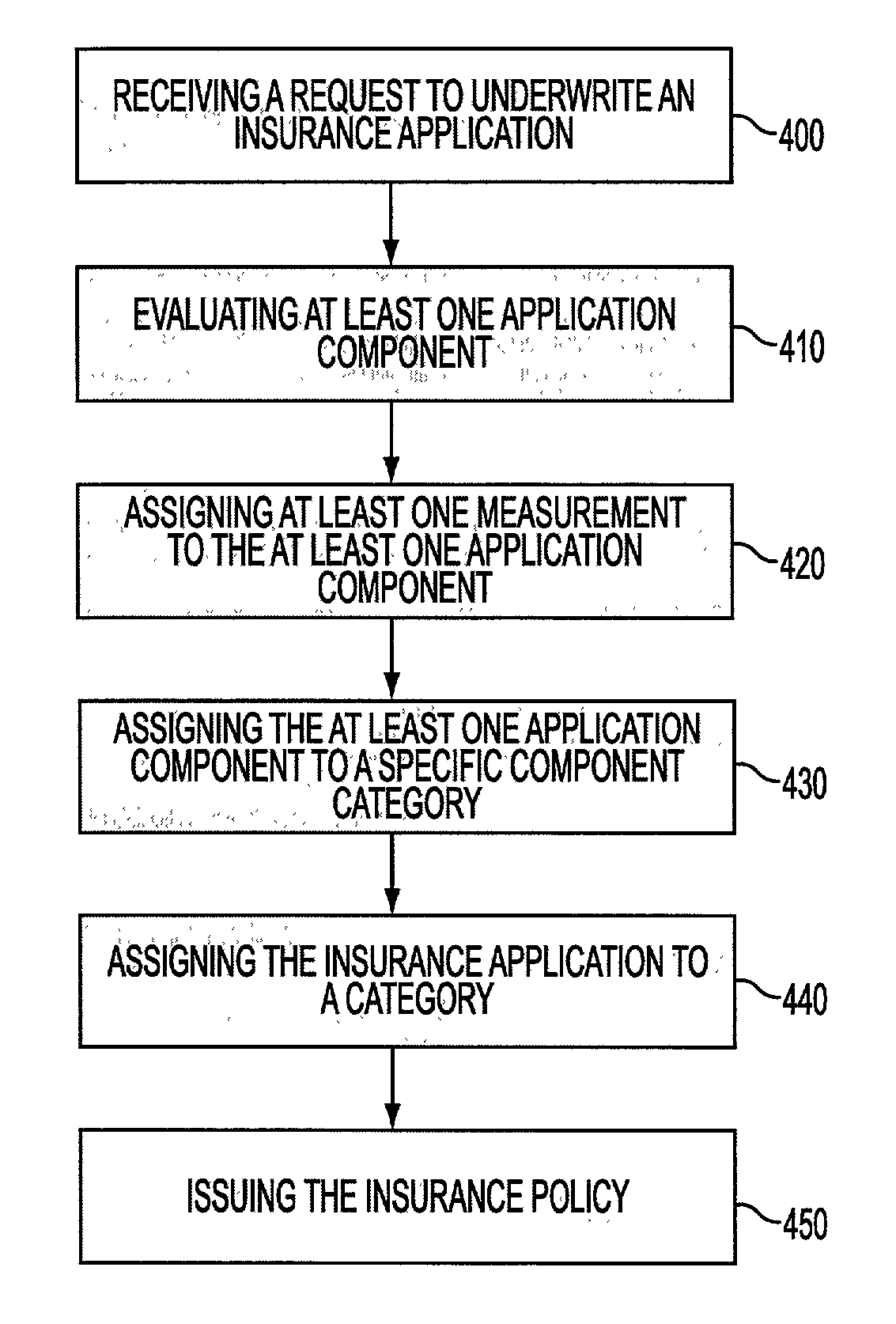
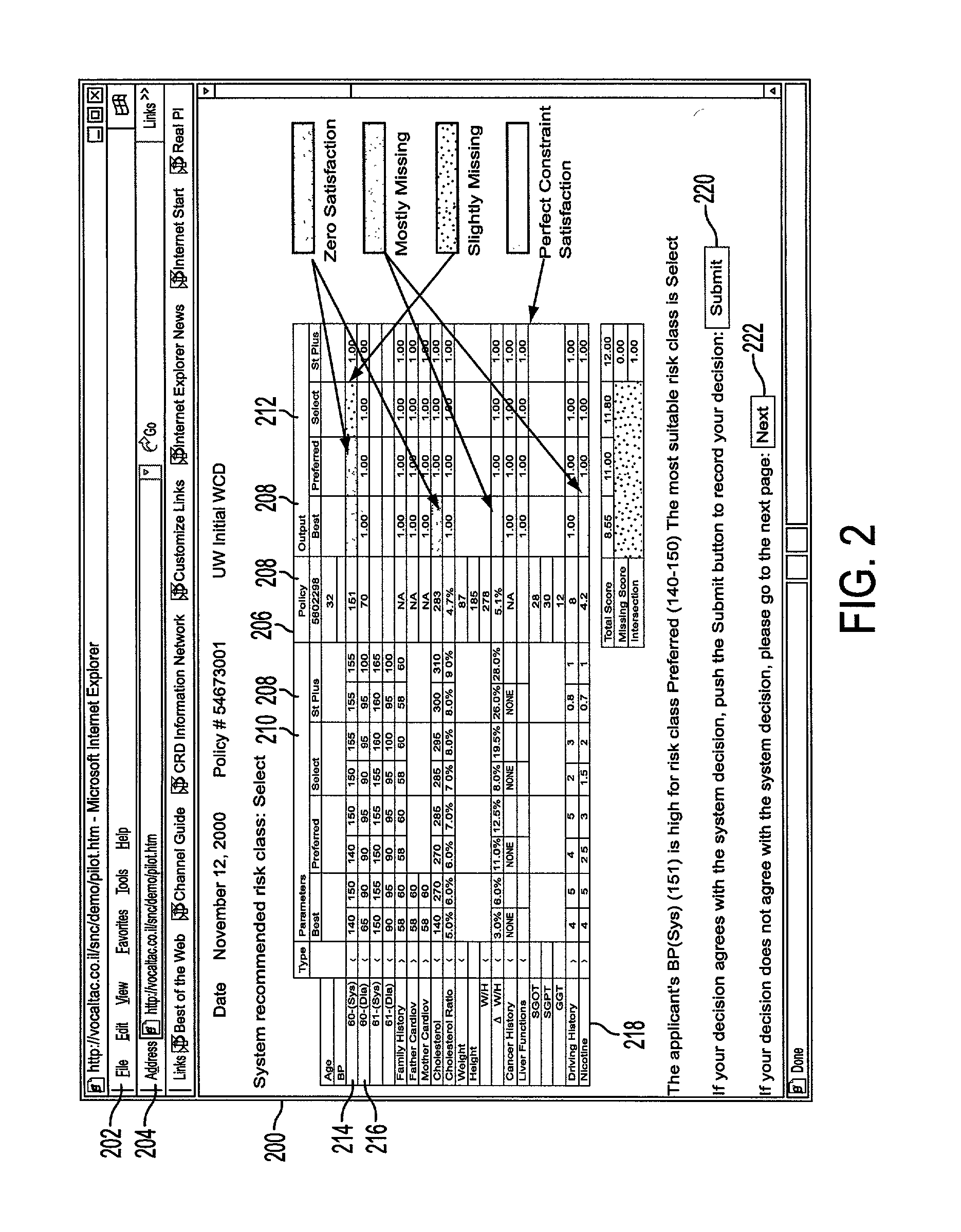
System and process for dominance classification for insurance underwriting suitable for use by an automated system
A risk classification technique that exploits the existing risk structure of the decision problem in order to produce risk categorizations for new candidates is described. The technique makes use of a set of candidates for which risk categories have already been assigned (in the case of insurance underwriting, for example, this would pertain to the premium class assigned to an application). Using this set of labeled candidates, the technique produces two subsets for each risk category: the Pareto-best subset and the Pareto-worst subset by using Dominance. These two subsets can be seen as representing the least risky and the most risky candidates within a given risk category. If there are a sufficient number of candidates in these two subsets, then the candidates in these two subsets can be seen as samples from the two hypothetical risk surfaces in the feature space that bound the risk category from above and below respectively. A new candidate is assigned a risk category by verifying if the candidate lies within these two bounding risk surfaces.
Owner:GE FINANCIAL ASSURANCE HLDG INC A RICHMOND
Risk identification method and device
InactiveCN106296195AGuaranteed accuracyEfficient identificationFinanceCharacter and pattern recognitionRisk ControlRisk identification
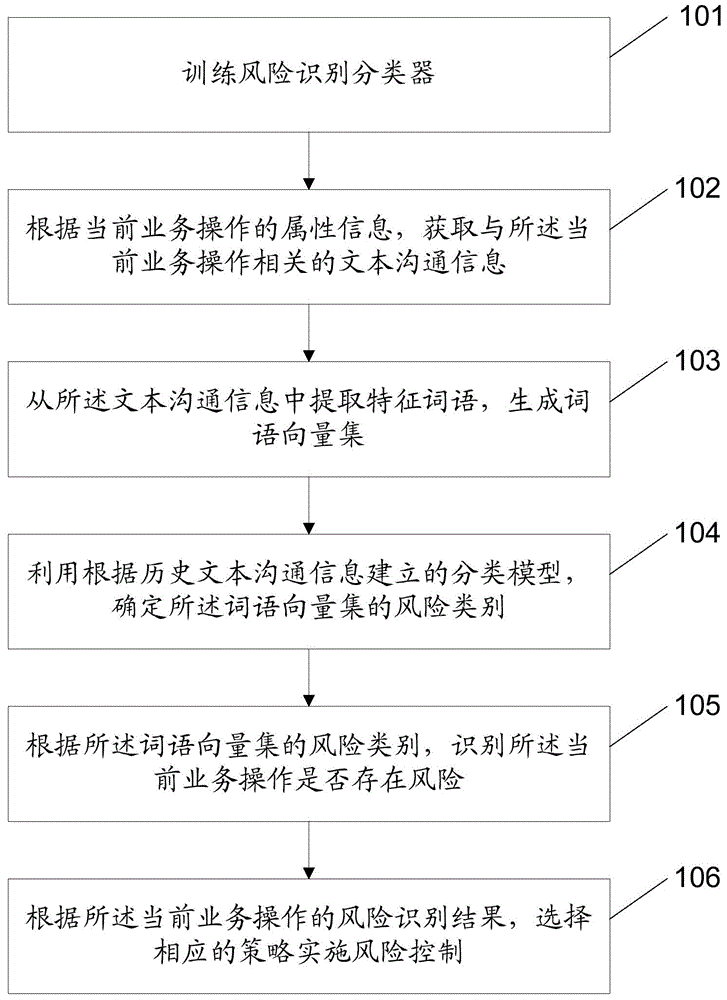
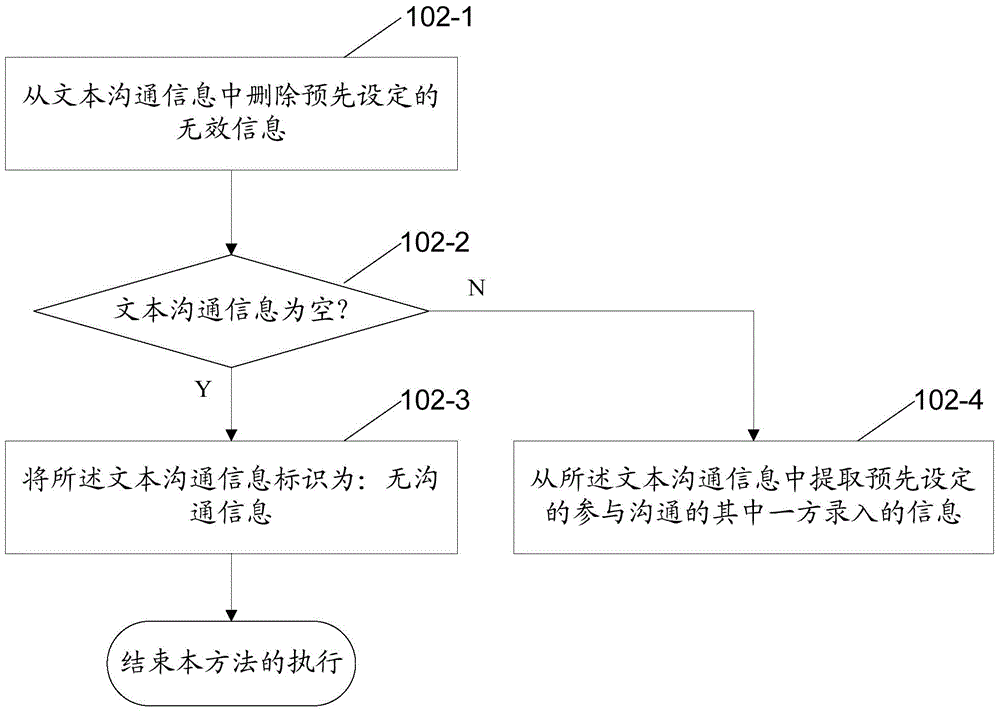
The application discloses a risk identification method comprising the following steps: acquiring text communication information related to a current service operation according to the attribute information of the current service operation; extracting feature words from the text communication information to generate a word vector set; determining the risk category of the word vector set using a classification model built according to historical text communication information; and identifying whether the current service operation is at risk or not according to the risk category of the word vector set. The application further provides a risk identification device. The method provides a new way of service operation risk identification. Through risk identification according to the text communication information related to the current service operation, a service operation which may be at risk can be identified efficiently, and a powerful reference is provided for the subsequent risk control link.
Owner:ADVANCED NEW TECH CO LTD
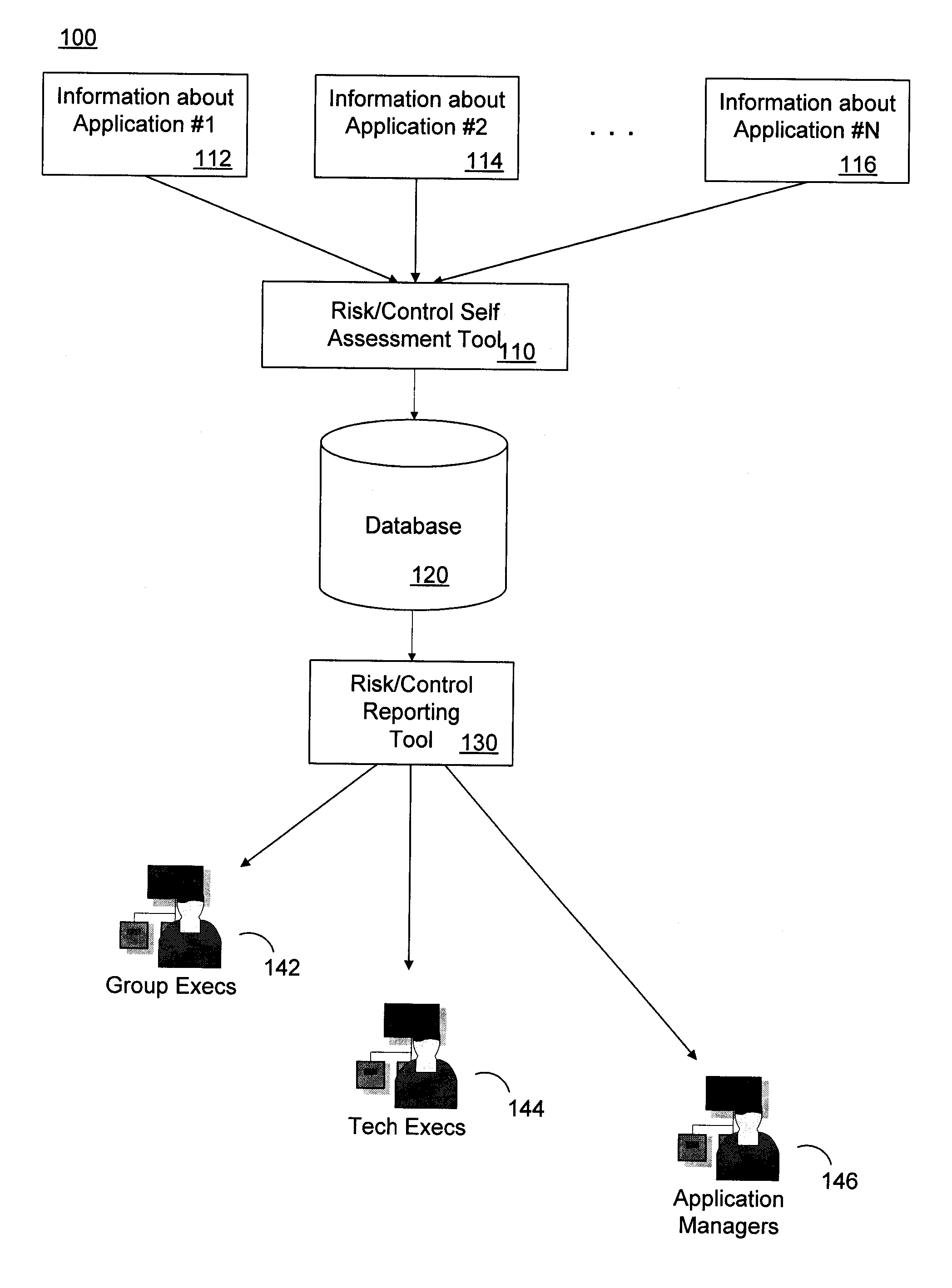
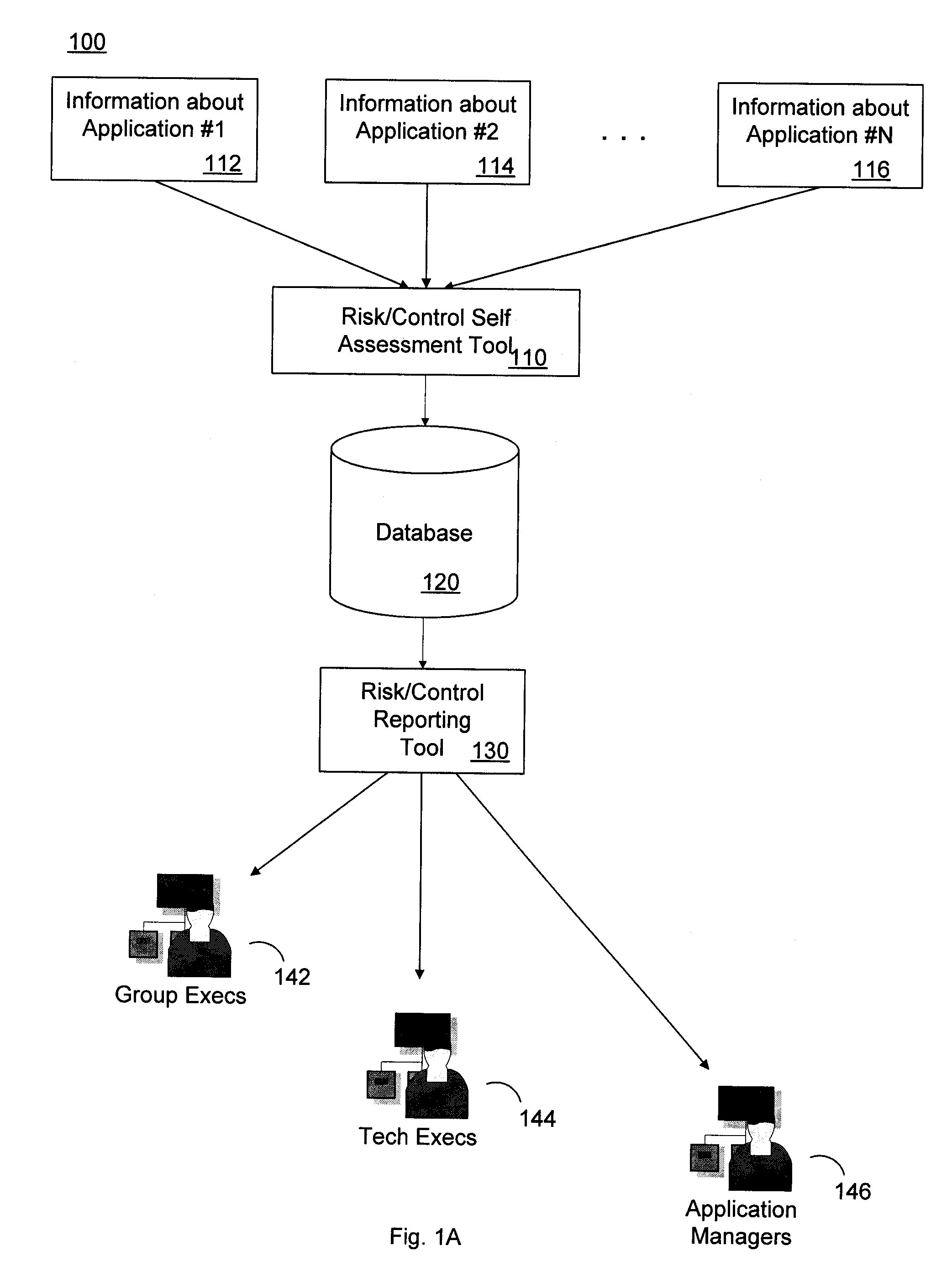
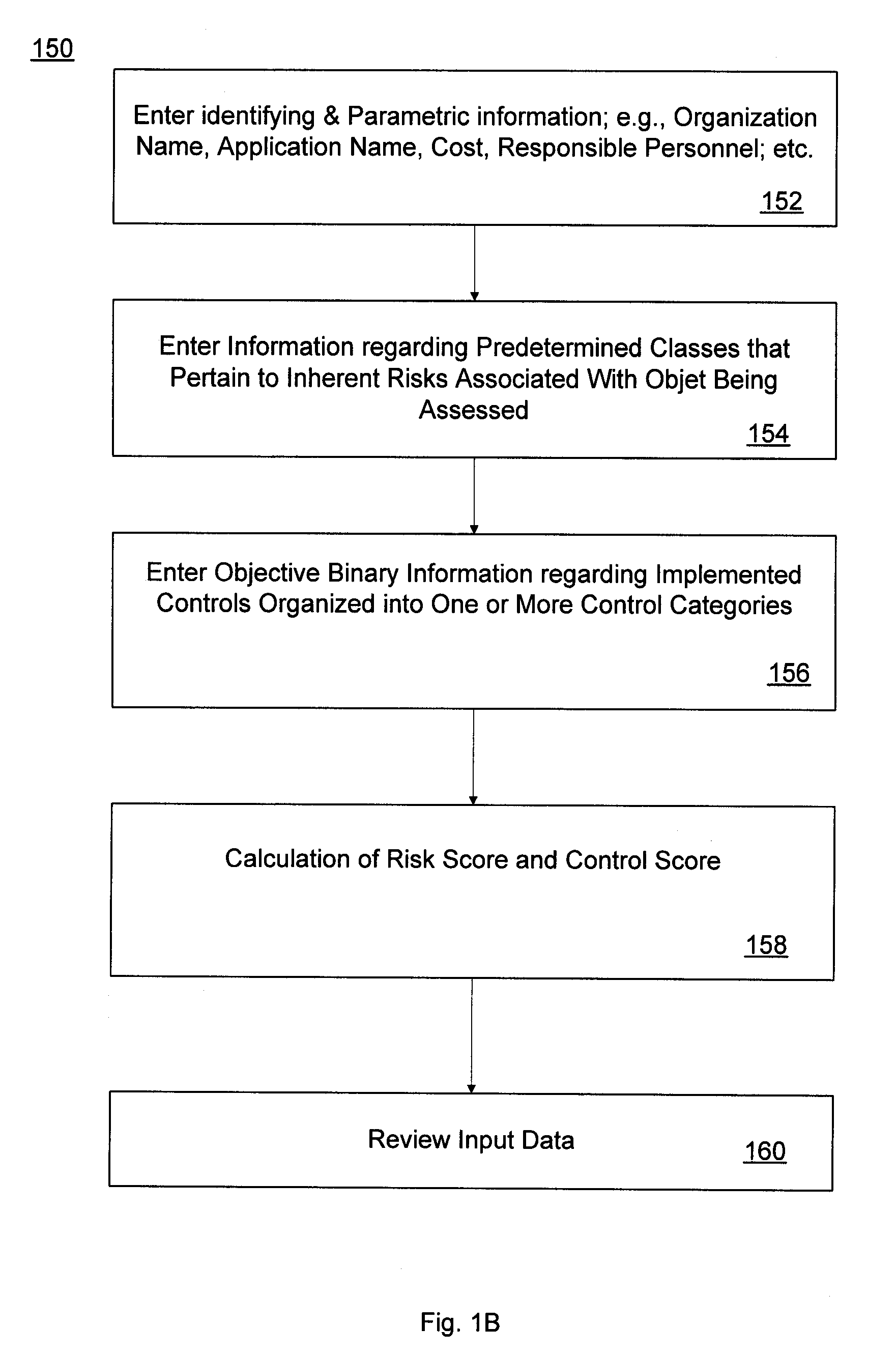
Application Risk and Control Assessment Tool
ActiveUS20070239495A1Reduce riskFinanceSpecial data processing applicationsRisk levelComputer science
A tool to assess risks associated with software applications, and controls implemented to mitigate these risks, includes a first software component configured to gather information about the risks and controls, and a second software component configured to display the gathered information. The first software component includes a self-assessment tool which is invoked by a user to enter information reflective of risk levels over a number of risk categories. These risk levels are used to calculate a risk score associated with a particular application. The user also enters information as to whether or not a number of specific control attributes have been implemented, and this information is used to calculate a control score. This process may be repeated for each of several software applications. The second software component allows one to selectively display various subsets, or even the entire population, of the collected information by invoking various combinations of parametric filters on the compiled information.
Owner:BANK OF AMERICA CORP
Risk Governance Model for an Operation or an Information Technology System
A computer system assessing risks for a joint venture. A risk, e.g., a technology or operational risk, may be associated with an infrastructure or an application that supports one or more operations of the joint venture, where the infrastructure or application may encompass an information technology system for the joint venture. A risk assessment computer system obtains risk information for identified risks in the information technology system, where the joint venture may support separate operations for first and second partner businesses on the information technology system. Identified risks may be owned by the joint venture or by one or more partner businesses and assigned accordingly. The risk assessment computer system may prioritize identified risk according to risk scores. When a control that is associated with a high priority risk category is not installed, a mitigation plan may be tracked to eliminate a high risk control gap.
Owner:BANK OF AMERICA CORP
Security control verification and monitoring subsystem for use in a computer information database system
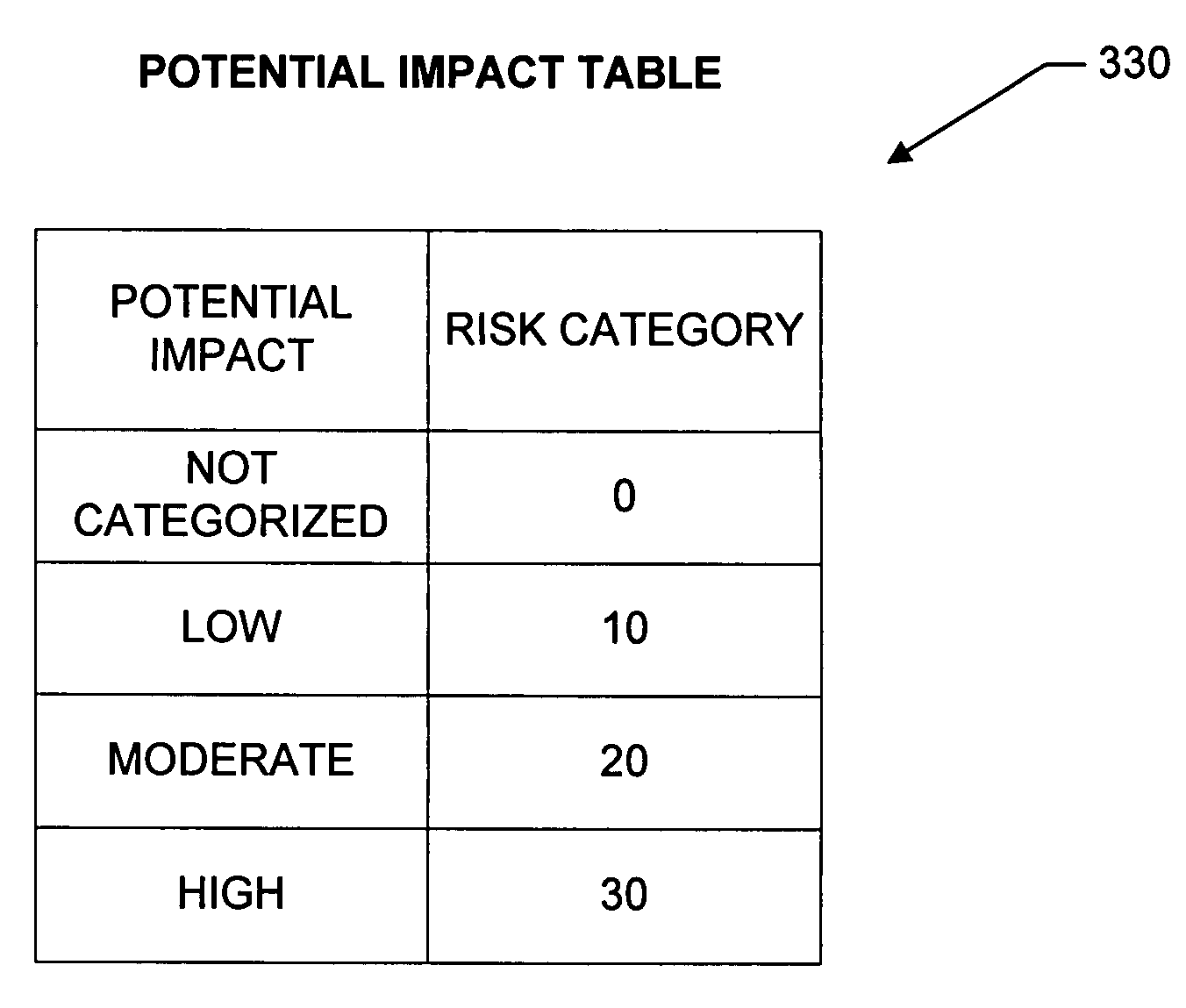
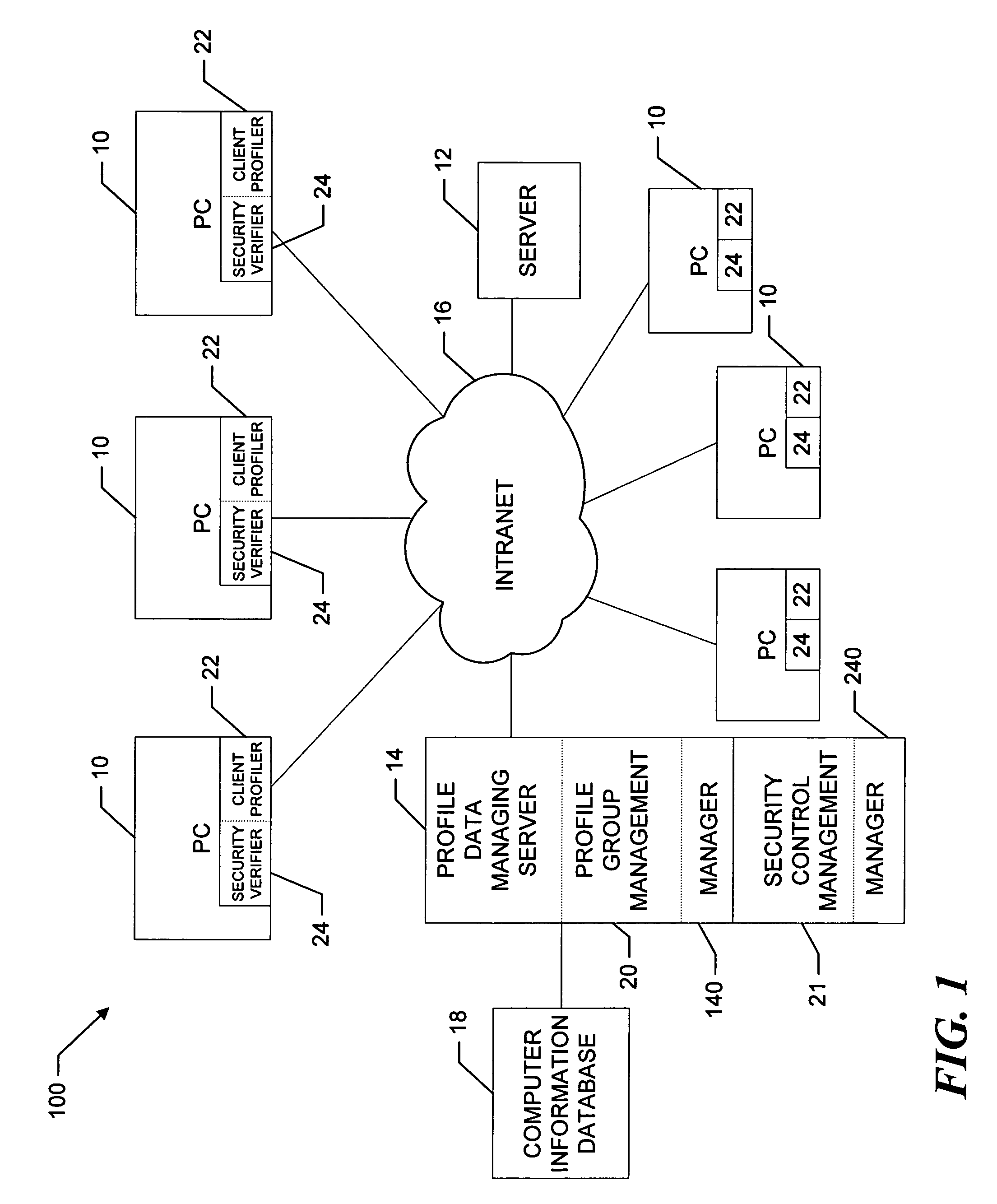
A security control verification and monitoring subsystem of a managed computer system performs security control verification operations regularly and for each security control verification operation determines the applicable security benchmark level for use by a given computer. The subsystem assigns security risk categories to groups of computers based, for example, on overall system or group administrator supplied potential impact settings and / or system type and business or information type selections. The subsystem further associates the security risk categories with security benchmark levels based on mapping information supplied by the overall system or group administrator. The subsystem then directs the computer to benchmark definition files based on the assigned security risk category, the associated security benchmark level and attributes of the computer. The subsystem performs the security control verification operations whenever the computer performs computer profile data update operations, and thus, monitors essentially continuously the security control compliance of the computer. The subsystem stores the results of the security verification operations and includes the results in reports for the system, group or computer.
Owner:BELARC
Healthcare information technology system for predicting development of cardiovascular conditions
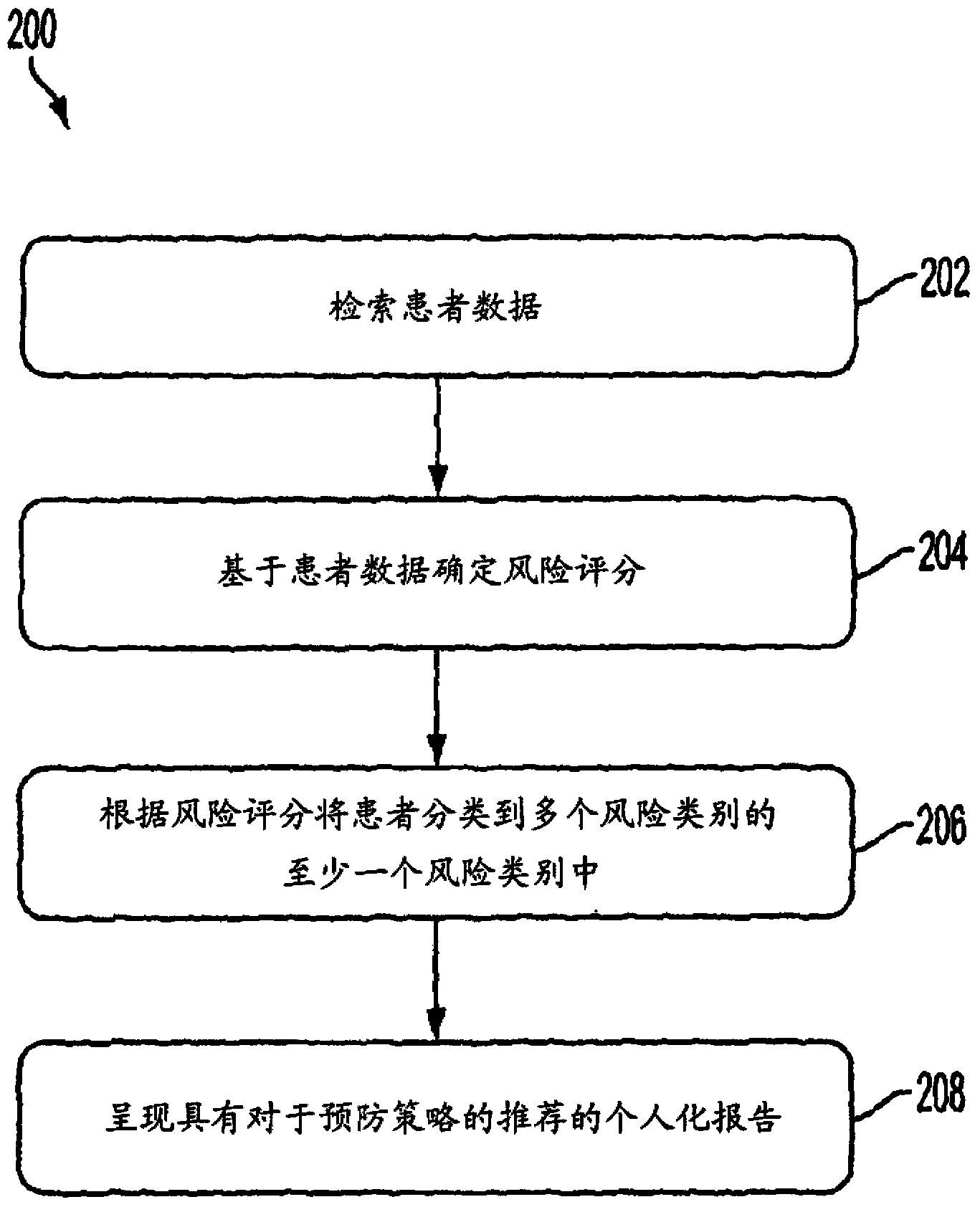
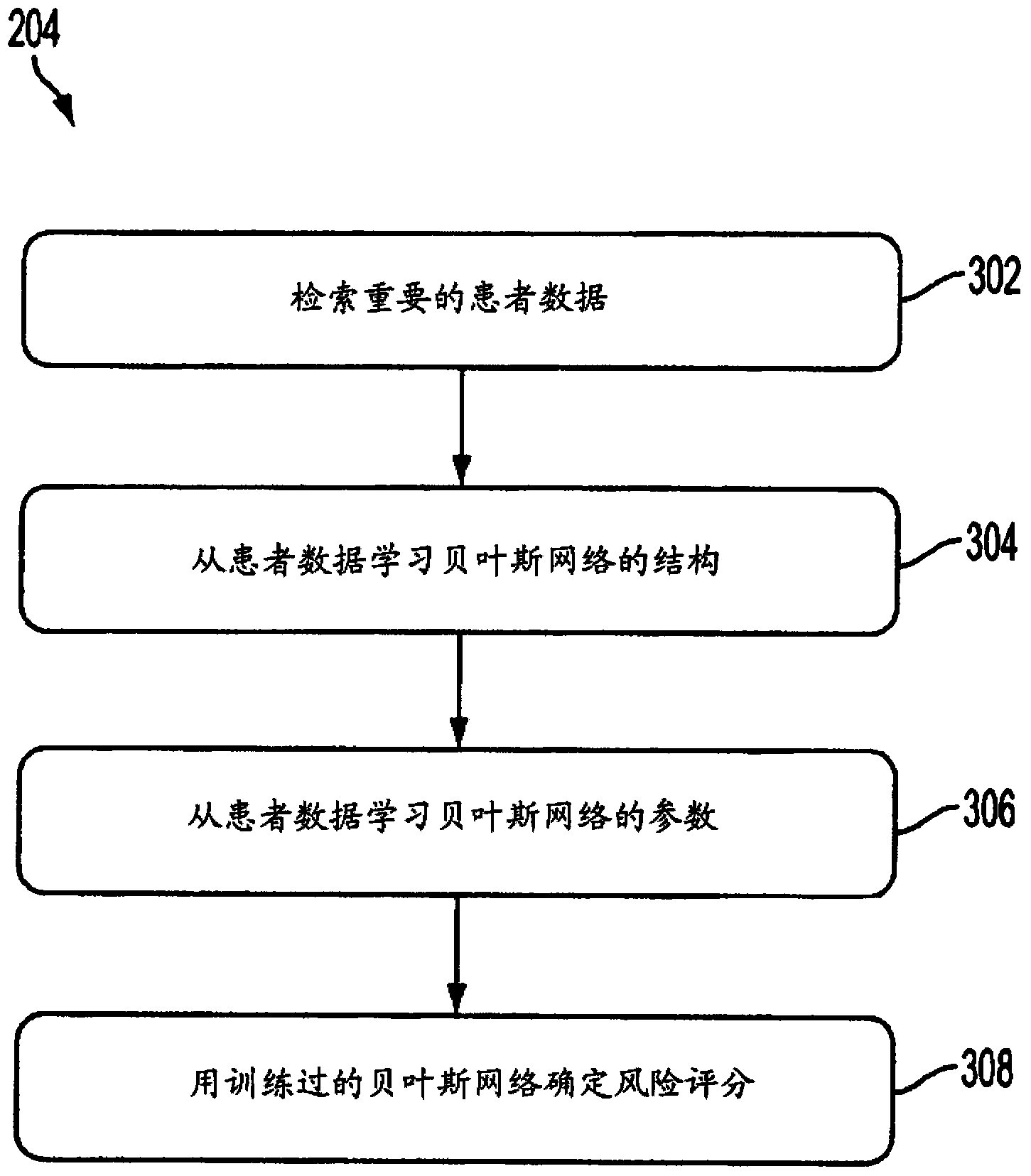
Described herein is a framework for predicting development of a cardiovascular condition of interest in a patient. The framework involves determining, based on prior domain knowledge relating to the cardiovascular condition of interest, a risk score as a function of patient data. The patient data may include both genetic data and non-genetic data. In one implementation, the risk score is used to categorize the patient into at least one of multiple risk categories, the multiple risk categories being associated with different strategies to prevent the onset of the cardiovascular condition. The results generated by the framework may be presented to a physician to facilitate interpretation, risk assessment and / or clinical decision support.
Owner:SIEMENS MEDICAL SOLUTIONS USA INC +1
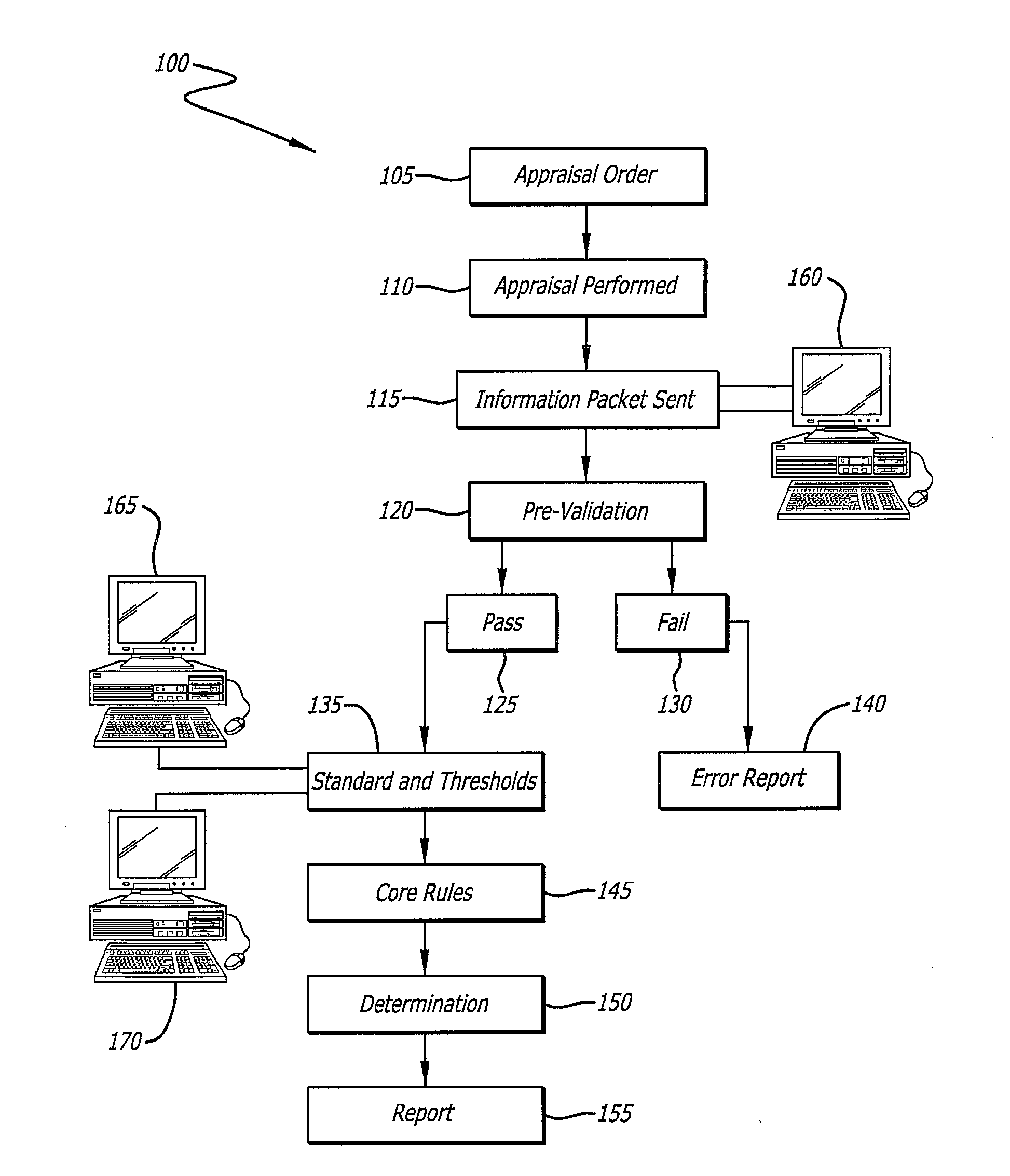
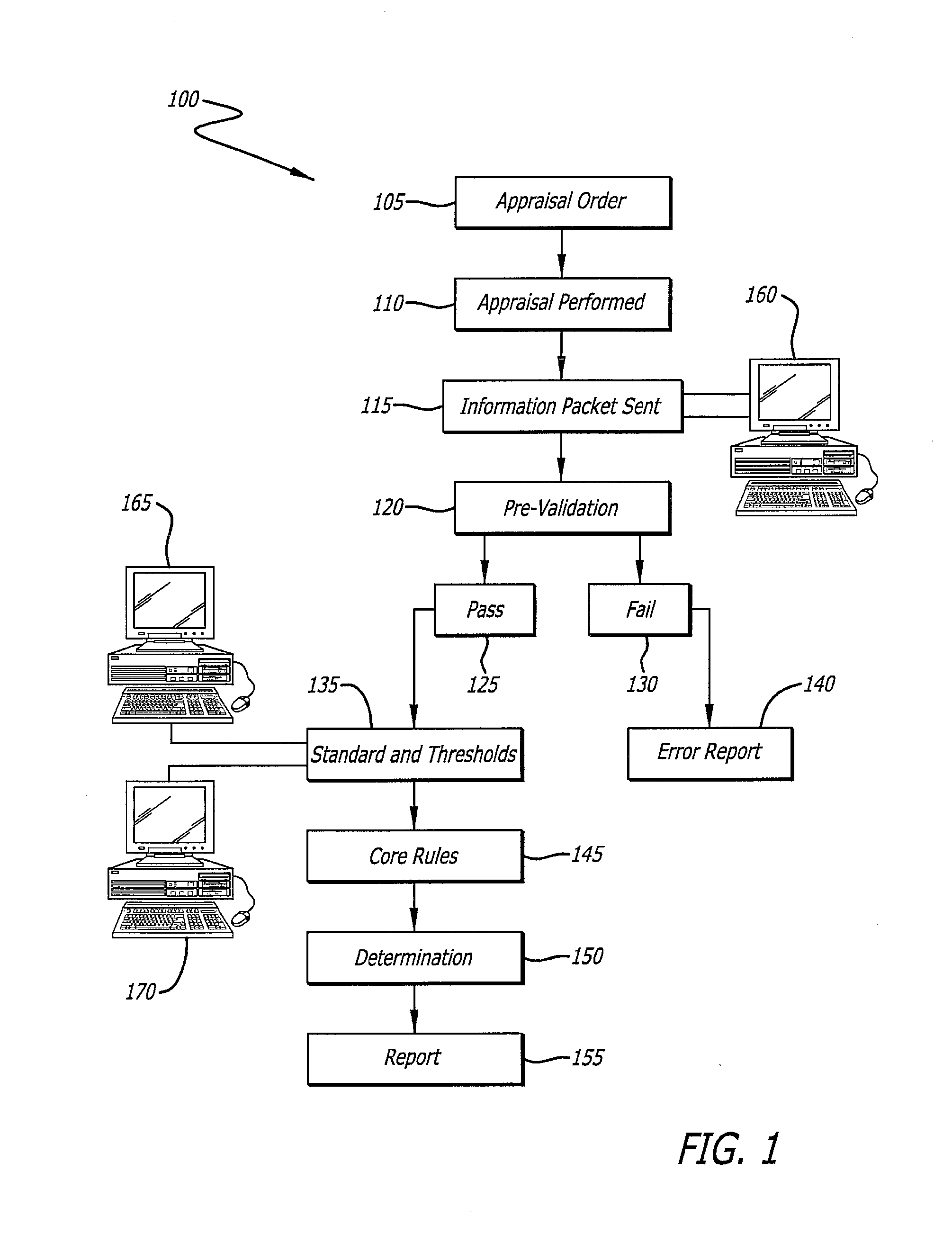
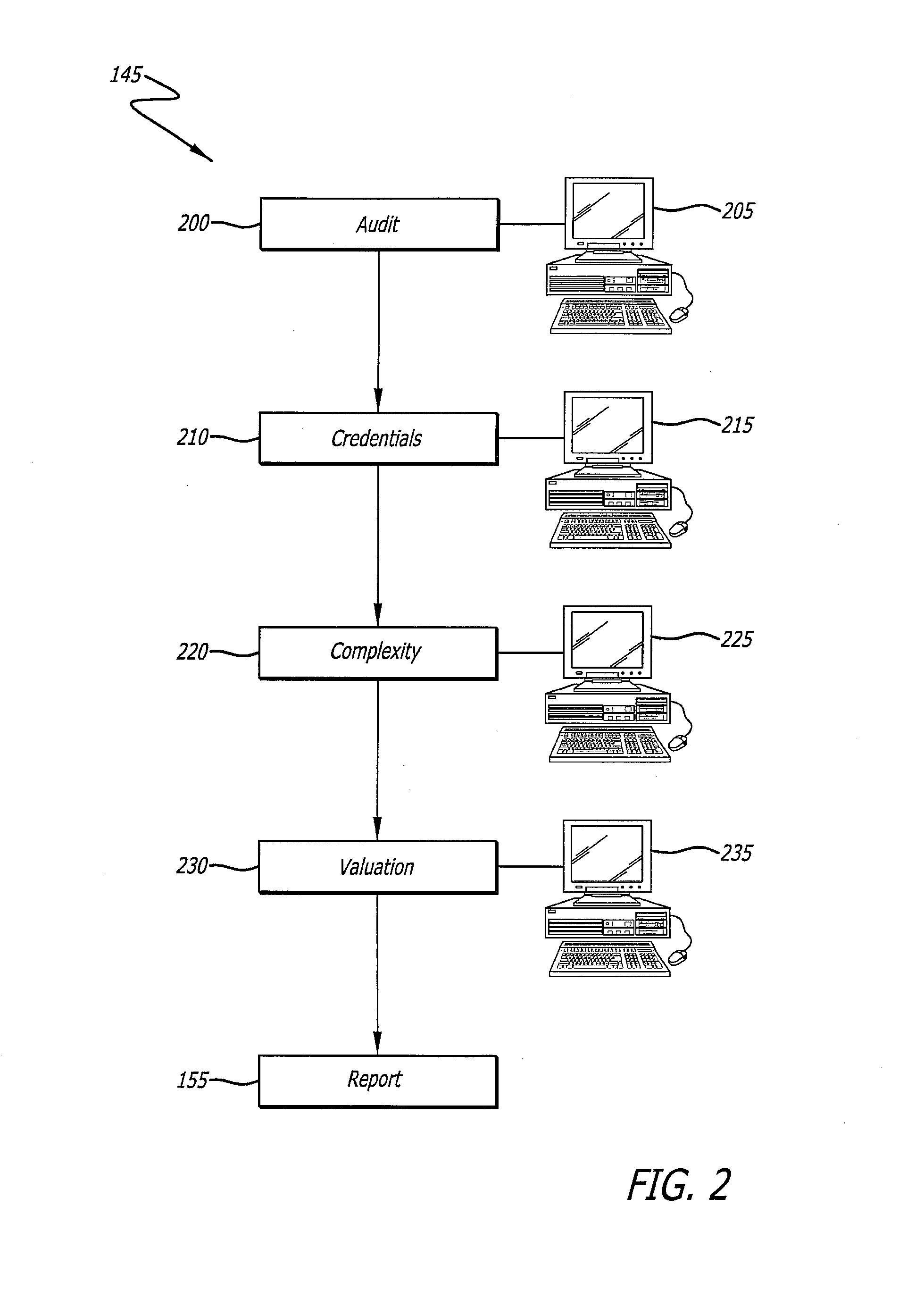
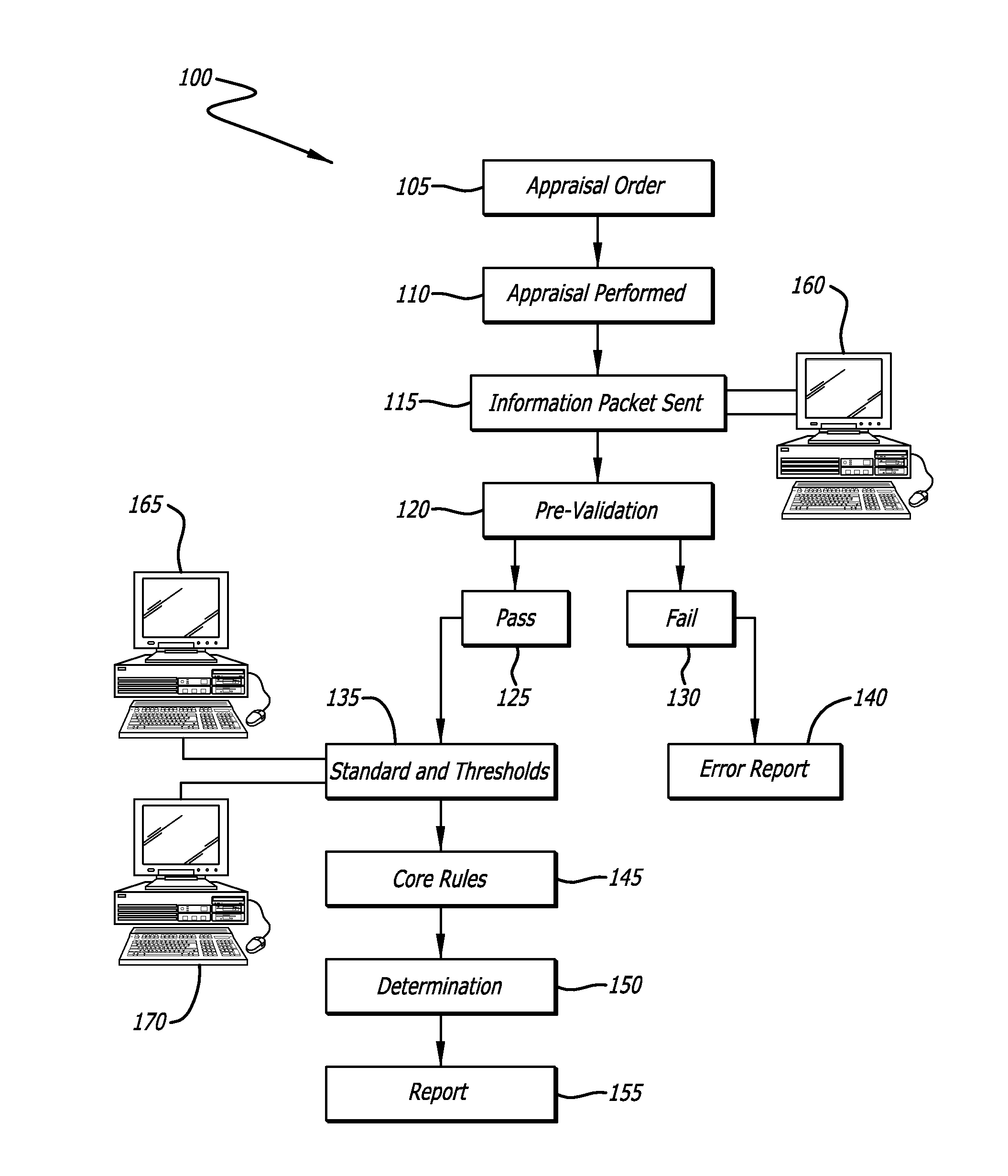
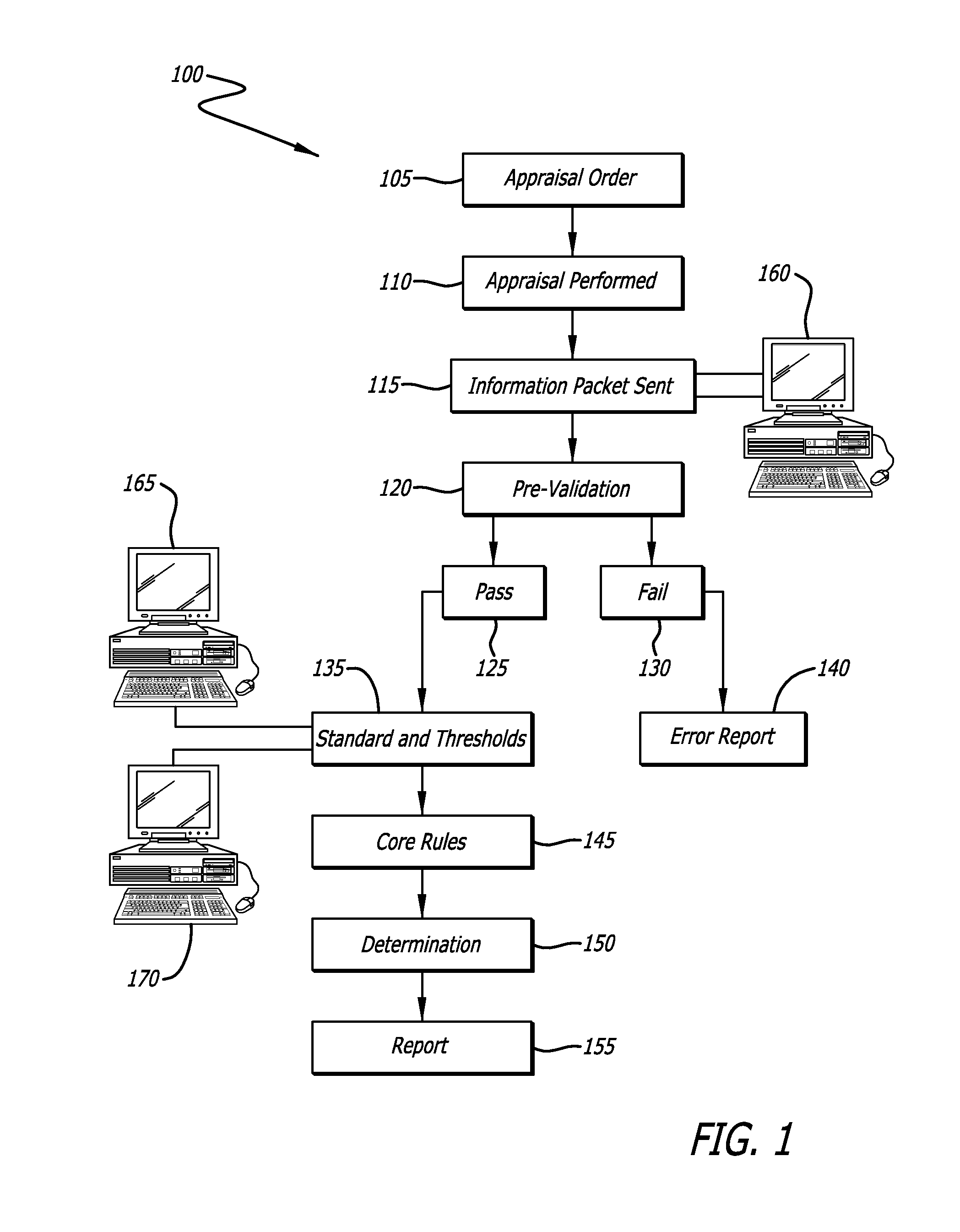
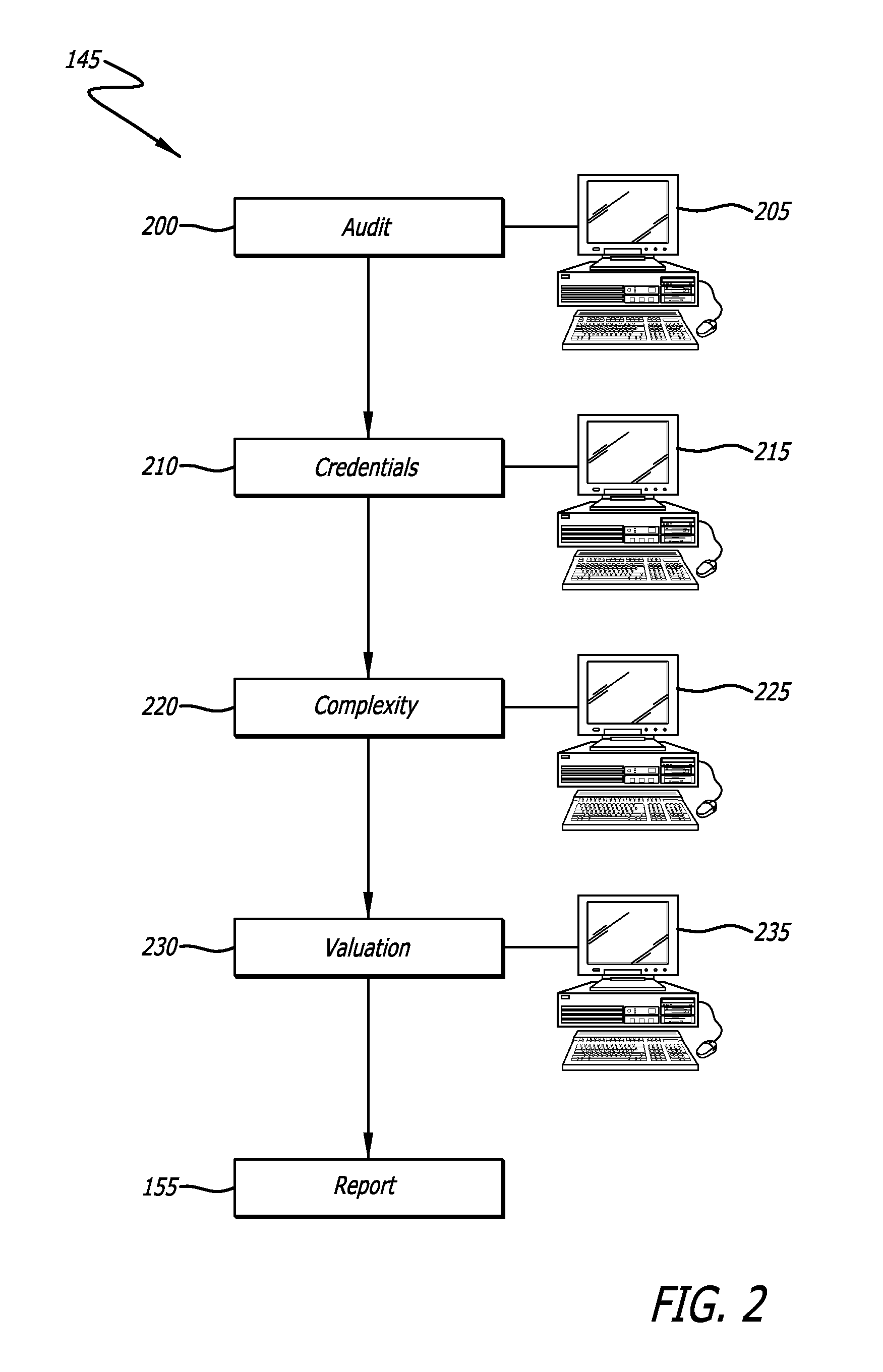
Determination of appraisal accuracy
A method for determining the accuracy of an appraisal report using a computer implemented application, including pre-validating an appraisal report to determine whether a first set of rules has been satisfied, the appraisal report including N fields to be completed, the first set of rules comprising completion of a pre-determined number of N fields; proceeding to a post-validating step if the first set of rules is satisfied; post-validating an appraisal report to provide an evaluation thereof, the evaluation including a plurality of risk categories including risk level indicators, and a risk-based overall score.
Owner:BLACK KNIGHT IP HLDG COMPANY
Machine-learning concepts for detecting and visualizing healthcare fraud risk
Machine-learning concepts for detecting and visualizing healthcare fraud, waste, and abuse risk using a data driven decision and investigations support system. The concepts comprise an analytic core that processes a large amount of data, generates an overall risk score, and ranks healthcare providers and / or members. The overall risk score is an integrated score encompassing multiple categories of risk. The multiple categories of risk factors include multiple definitions of what defines risk, allowing for a synergistic effect between the risk analytics, where the overall effect of the combination is greater than the sum of the effects of any one definition of risky behavior by a provider or member. Utilizing this approach a unique risk profile of healthcare providers and members is generated and visualized to the user. Various embodiments further encompass a user interface that comprises linked panels that display targeted information regarding providers and members.
Owner:OPTUM SERVICES IRELAND LTD
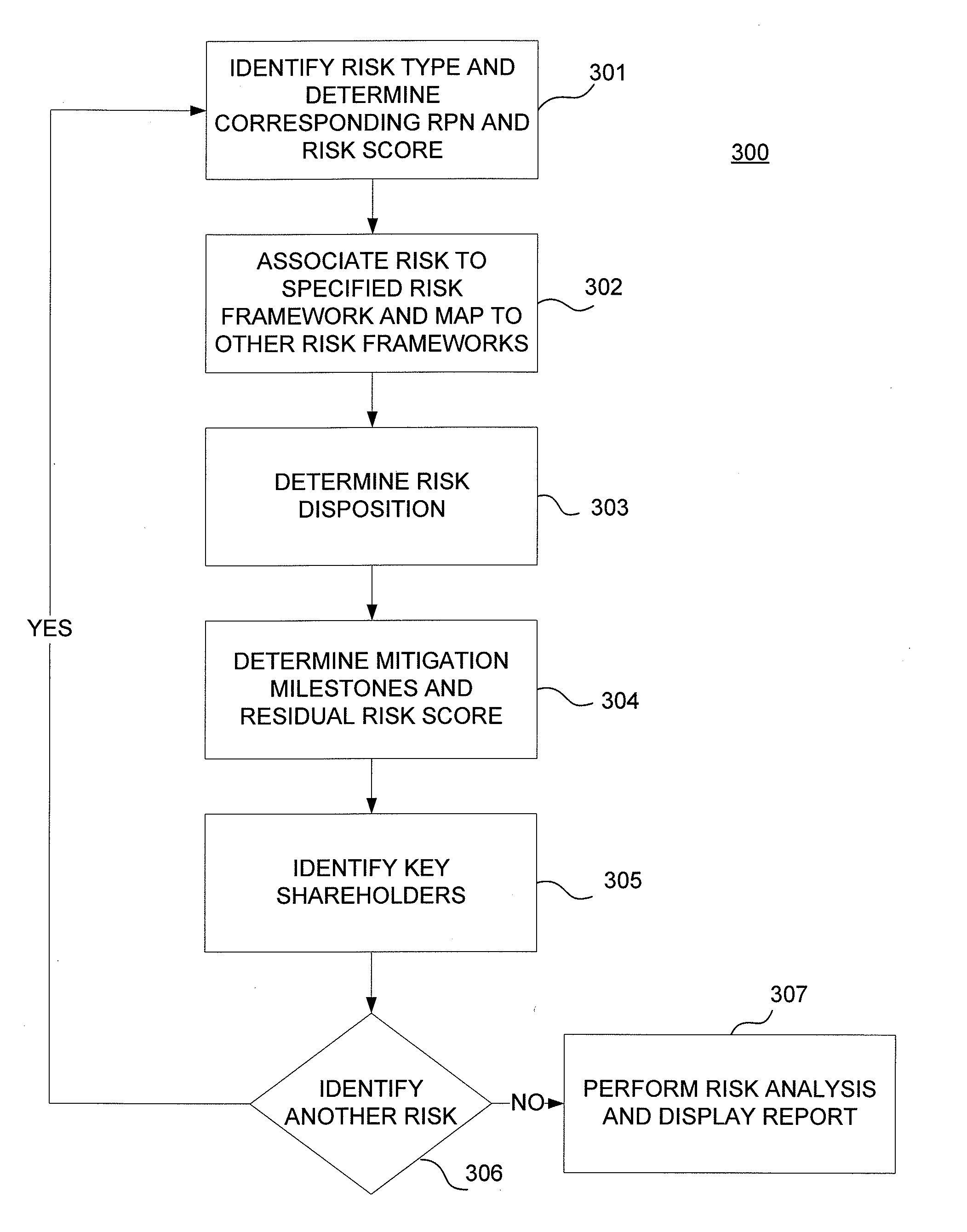
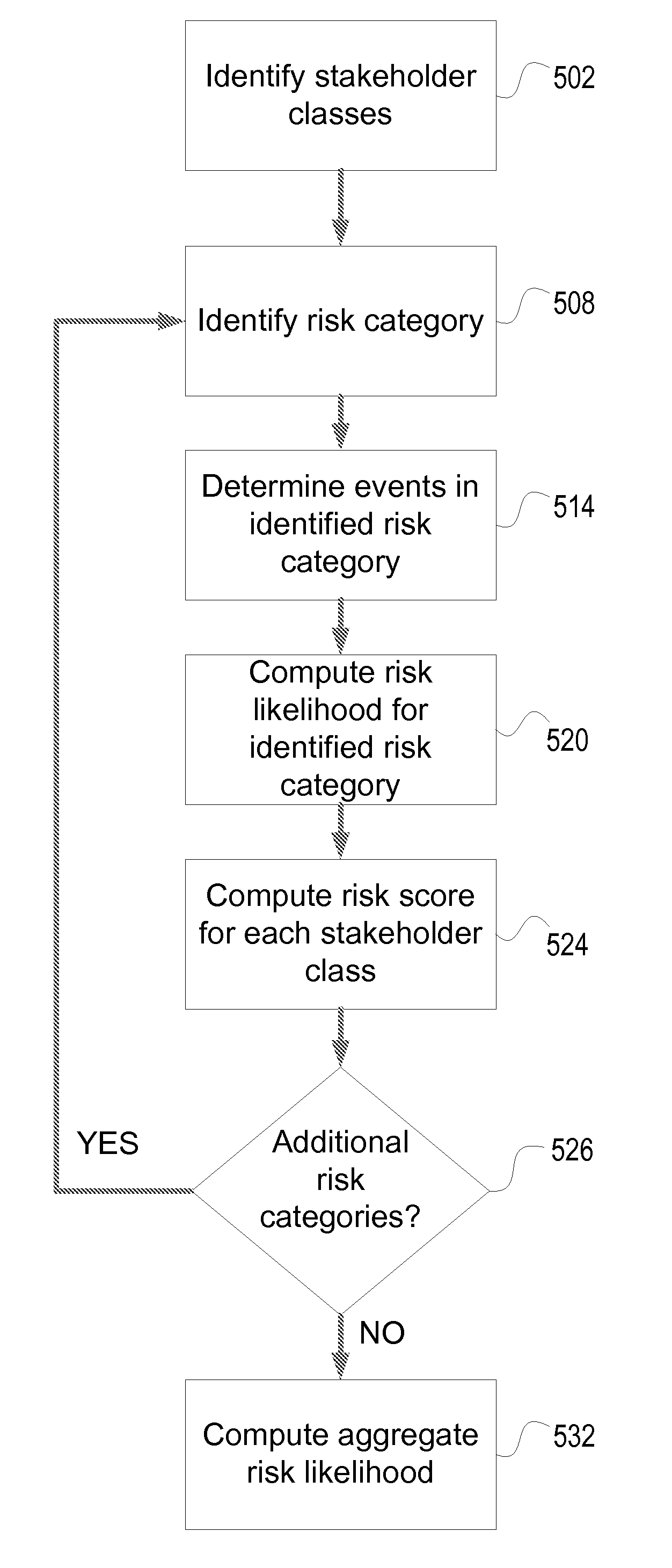
Reputation Risk Framework
A risk framework is described for computing risk. One or more persons may be grouped into classes of stakeholders. Different types of risk may be classified into risk categories. Within each risk category, events contributing to that type of risk may be determined and assigned a weight / severity value and a likelihood of occurrence value. Risk likelihood may be computed for each risk category by summing the products of weight / severity value and likelihood of occurrence value for each event within the risk category. A severity level may be determined and assigned with respect to each class of stakeholders regarding the risk categories, and a risk score may be computed for each stakeholder class and risk category combination. An aggregate risk likelihood may be computed by summing and / or weighting the risk likelihoods computed for each risk category.
Owner:BANK OF AMERICA CORP
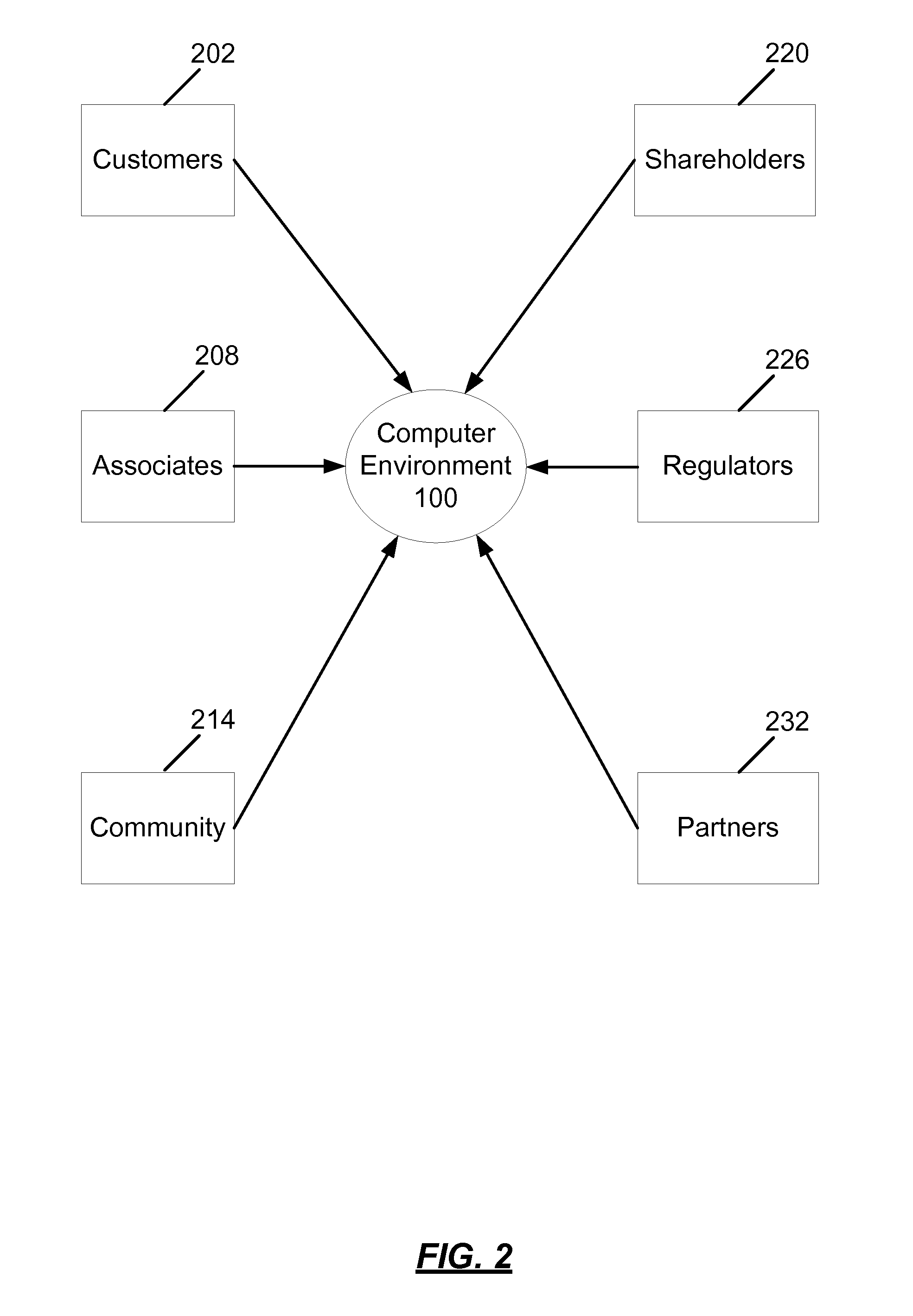
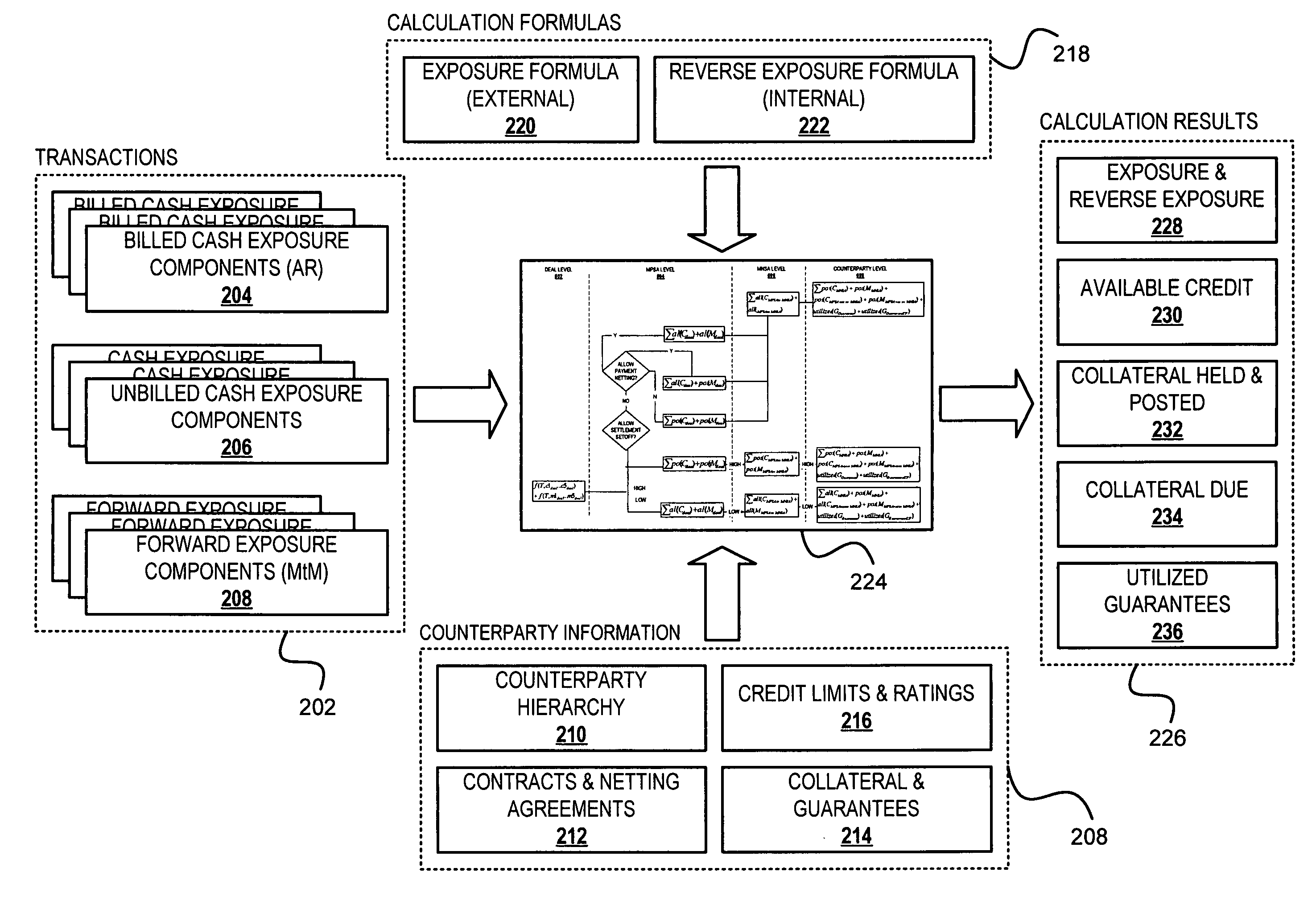
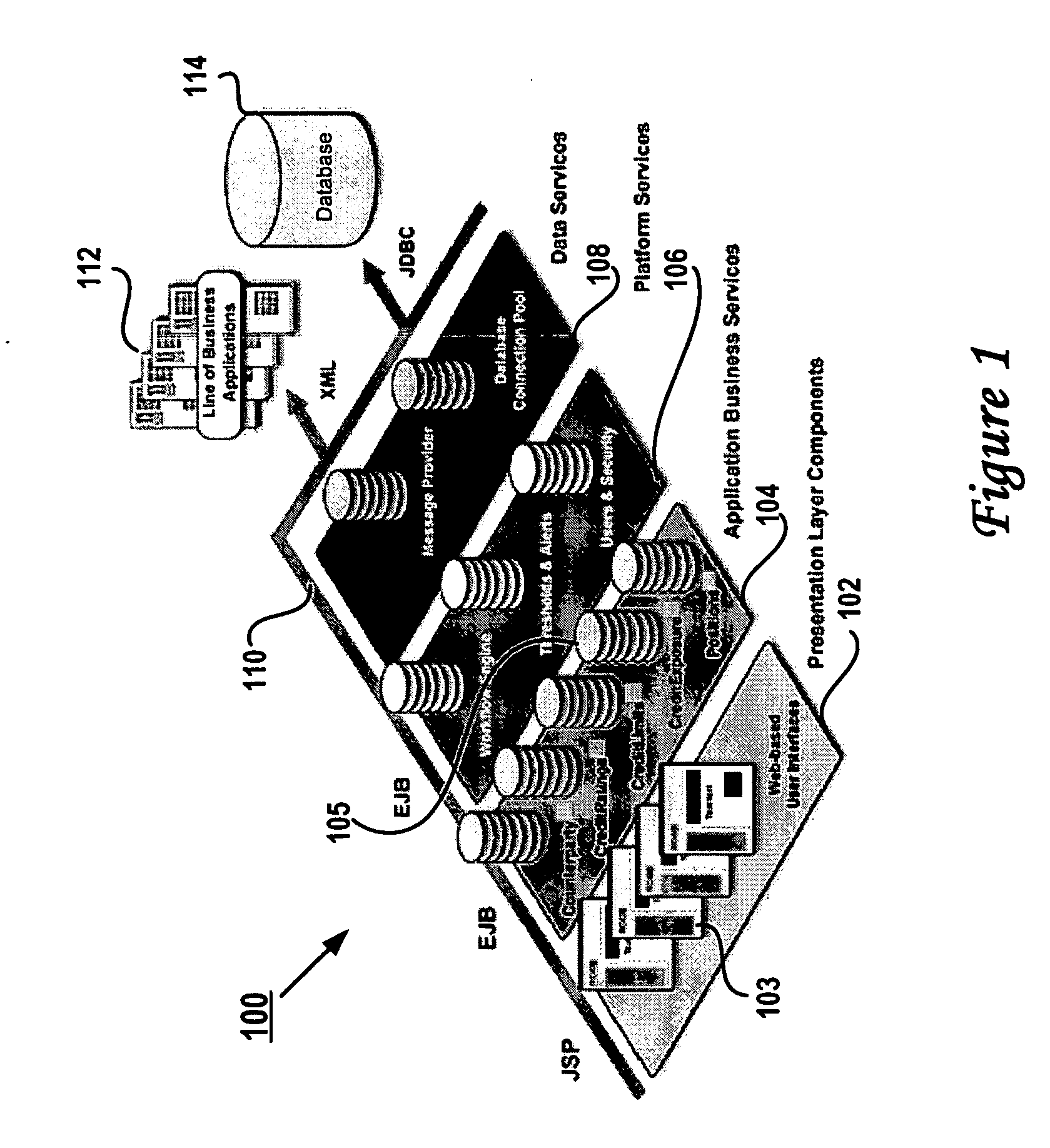
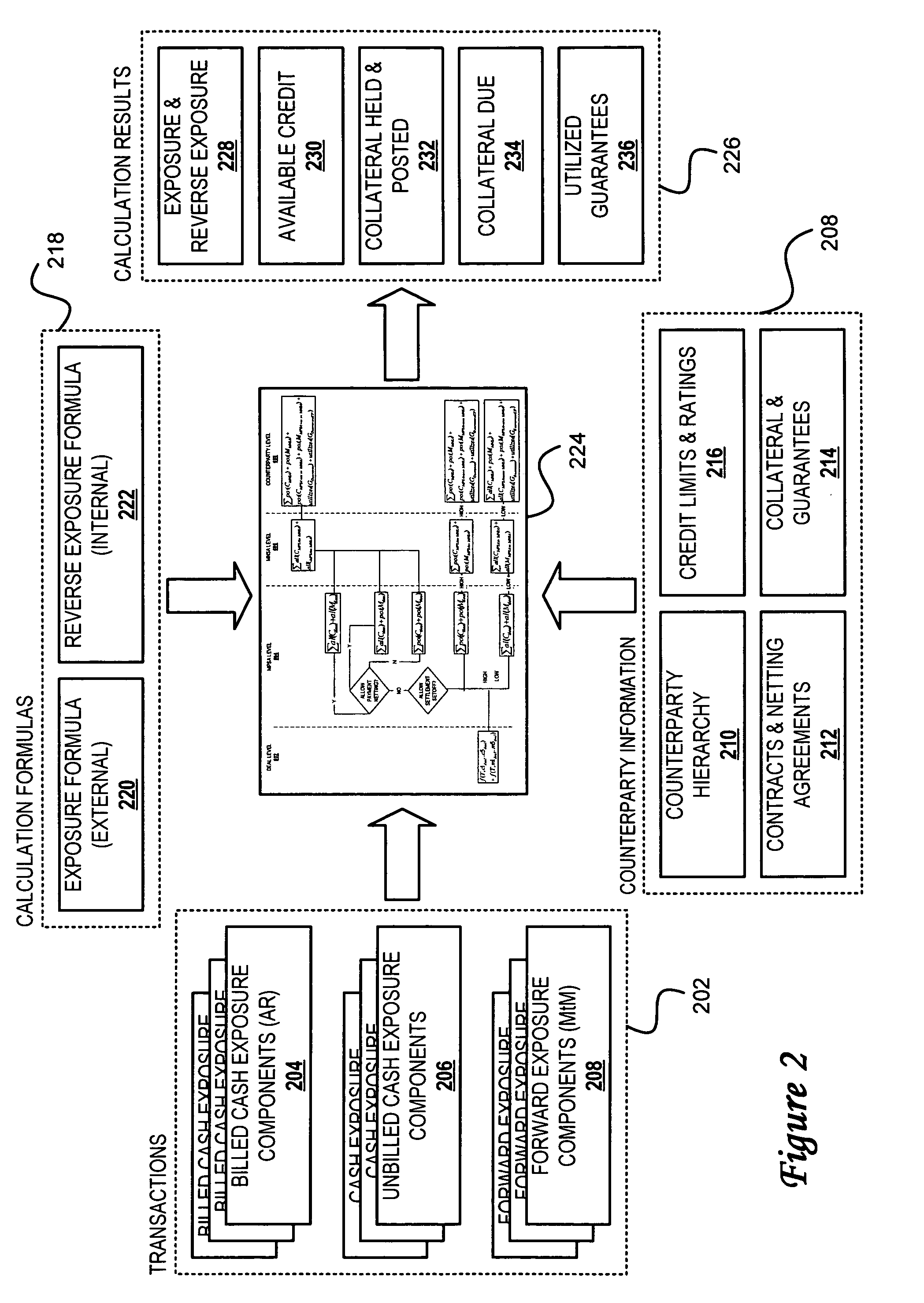
Method, system and program for credit risk management utilizing credit exposure
Software aggregates and integrates credit exposure data across accounting, trading and operational systems within an energy trading organization. A comprehensive model of exposure to all counterparties, across all of their divisions and subsidiaries, is then assembled, enabling the creation of a hierarchical view of each counterparty that models its real-world parent-child relationships, and taking into account netting, setoff, and margin requirements, collateral requirements and contract terms, internal and external views of exposure and liquidity, and risk concentrations based on both system and user-defined risk categories. After aggregating the exposure information, credit, transactions, risk and other properties are determined at any level in the hierarchy and then the system presents a comprehensive, detailed, real-time, enterprise-wide view of current exposure, collateral requirements and outlays for both a company and its counterparties. Walkforward views of potential credit exposure taking into account current and future prices and volumes are also provided.
Owner:ROME CORP
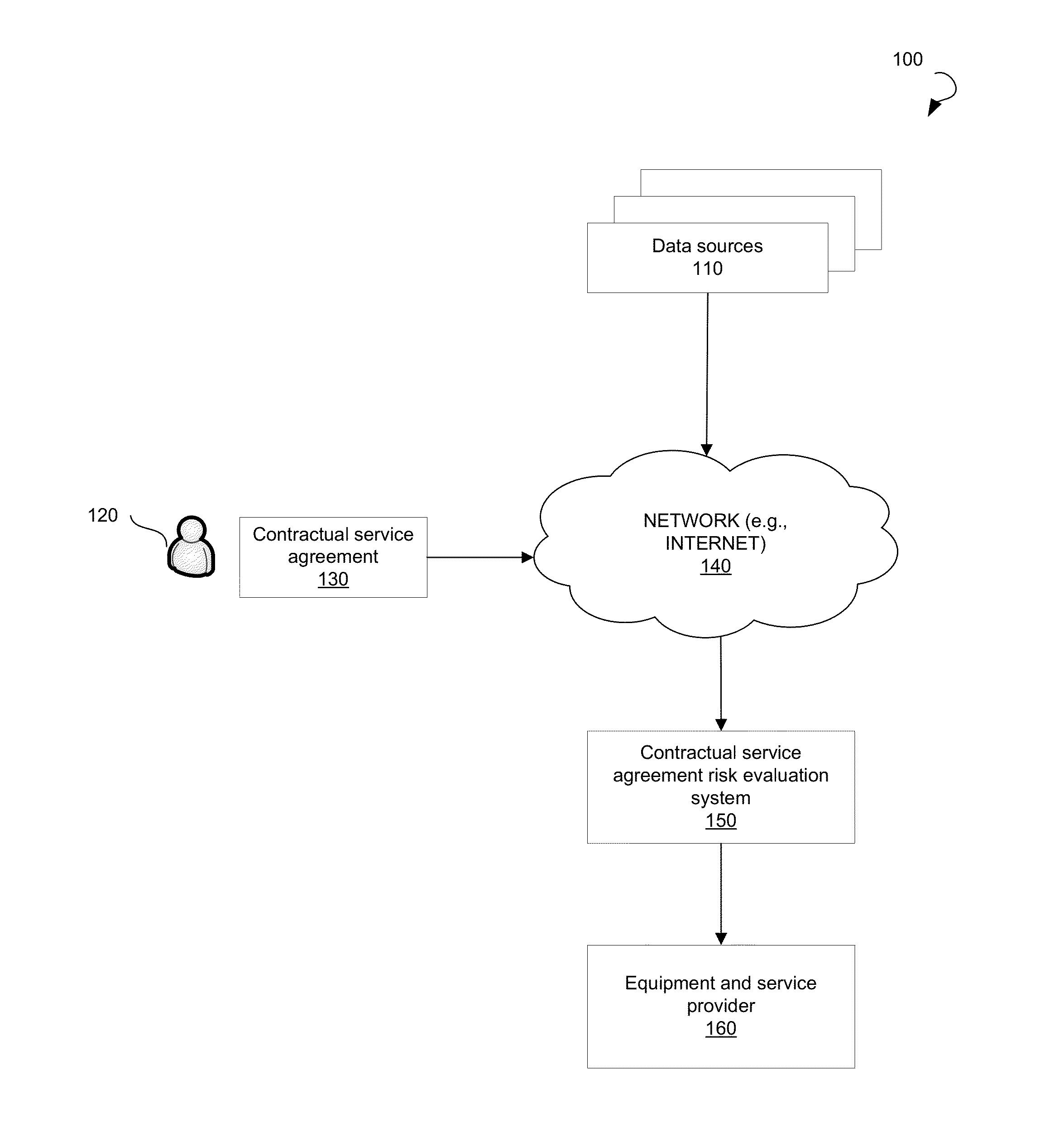
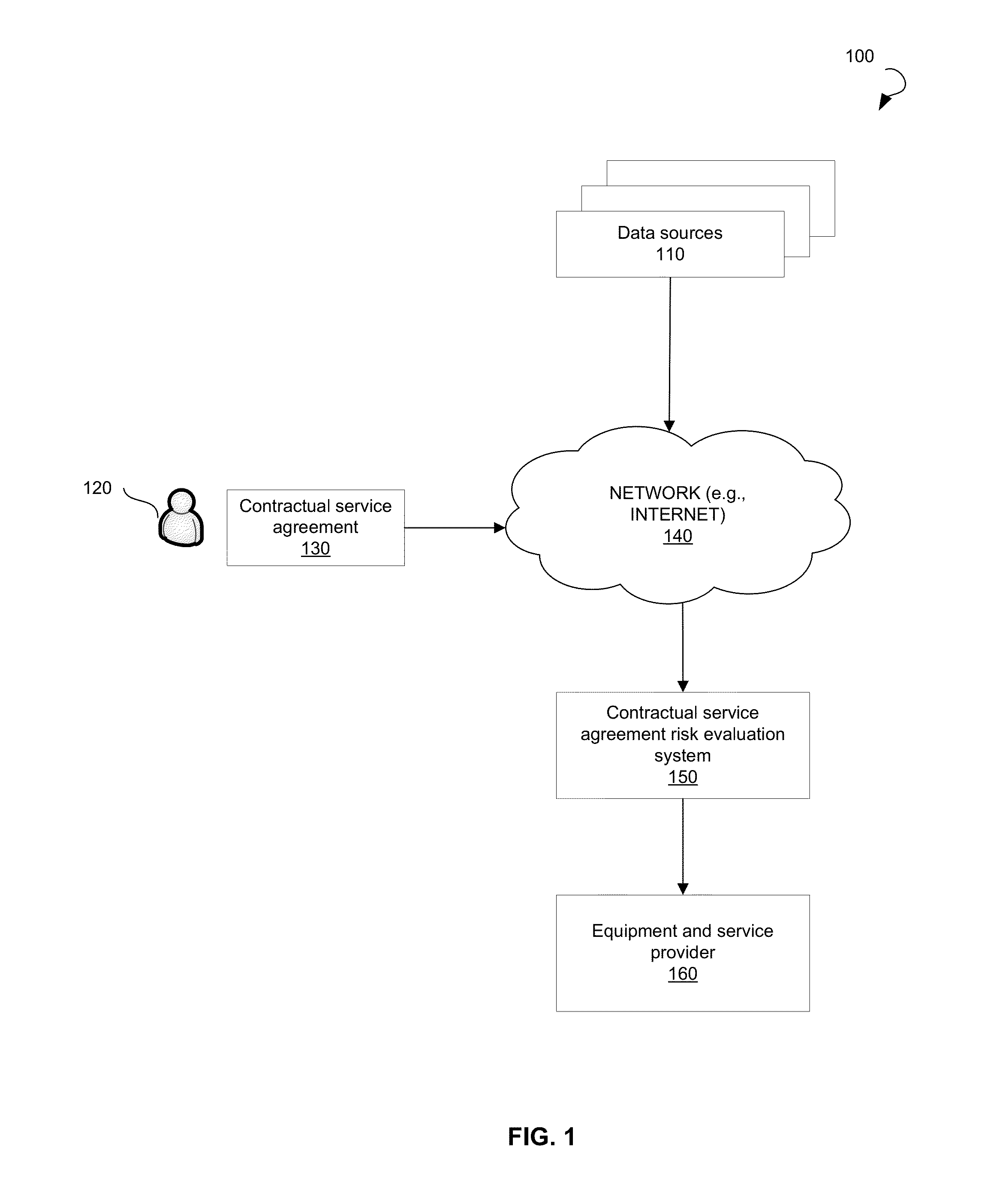
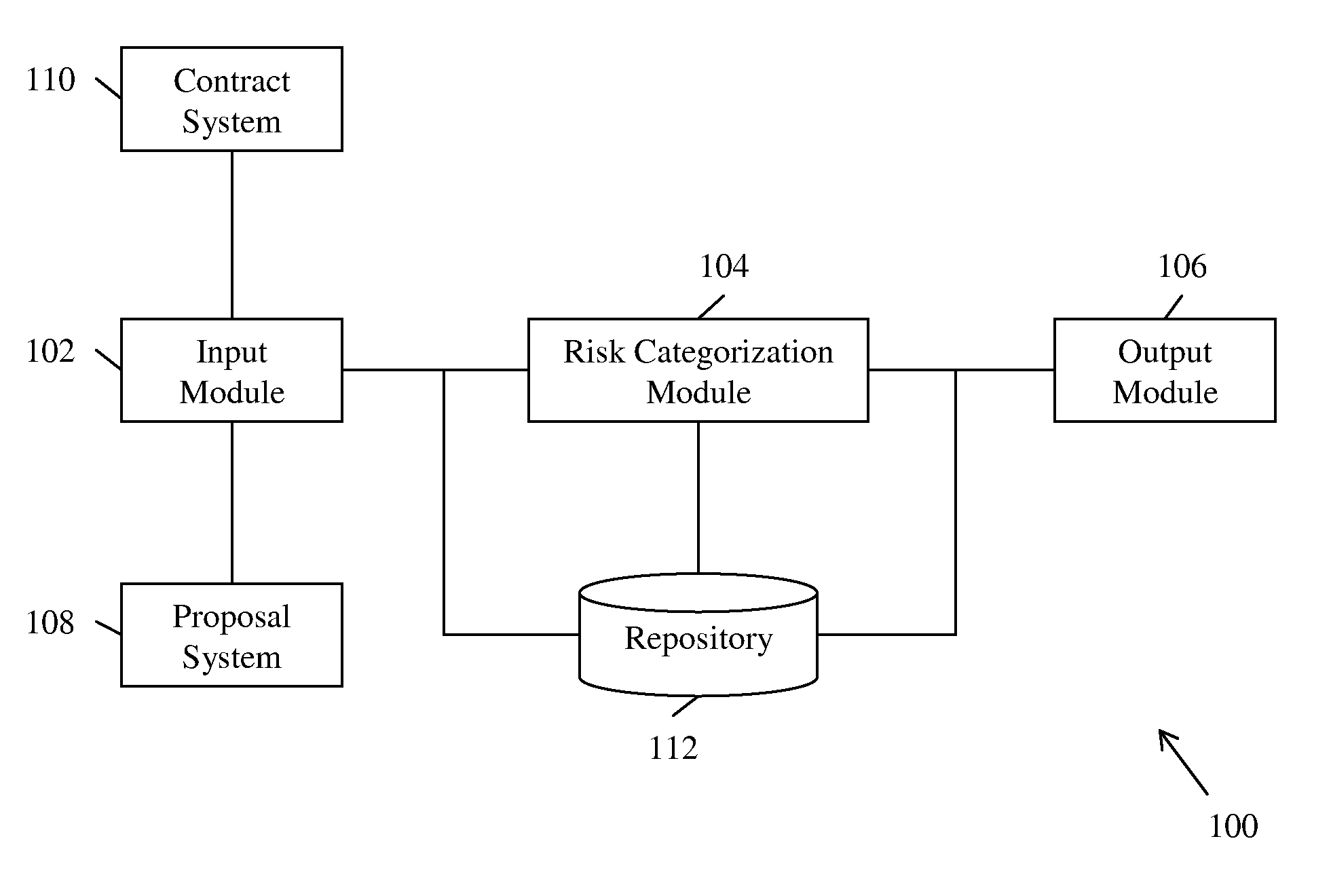
Systems and Methods for Evaluating Risks Associated with a Contractual Service Agreement
Systems and methods for evaluating risks associated with a contractual service agreement are provided. According to one embodiment, a system may include a processor configured to analyze the contractual service agreement to determine risk categories associated with the contractual service agreement. The system may receive risk parameters associated with the one or more risk categories and weights associated with the one or more risk parameters. The weights may be associated with the risk parameters to produce weighted risk parameters. The risk associated with the contractual service agreement may be evaluated by adding the weighted risk parameters.
Owner:GENERAL ELECTRIC CO
System and method for detecting abnormal traffic based on early notification
ActiveUS7757283B2Reduce trafficLarge of attackMemory loss protectionDigital data processing detailsTraffic capacityMalware
Owner:ALCATEL LUCENT SAS
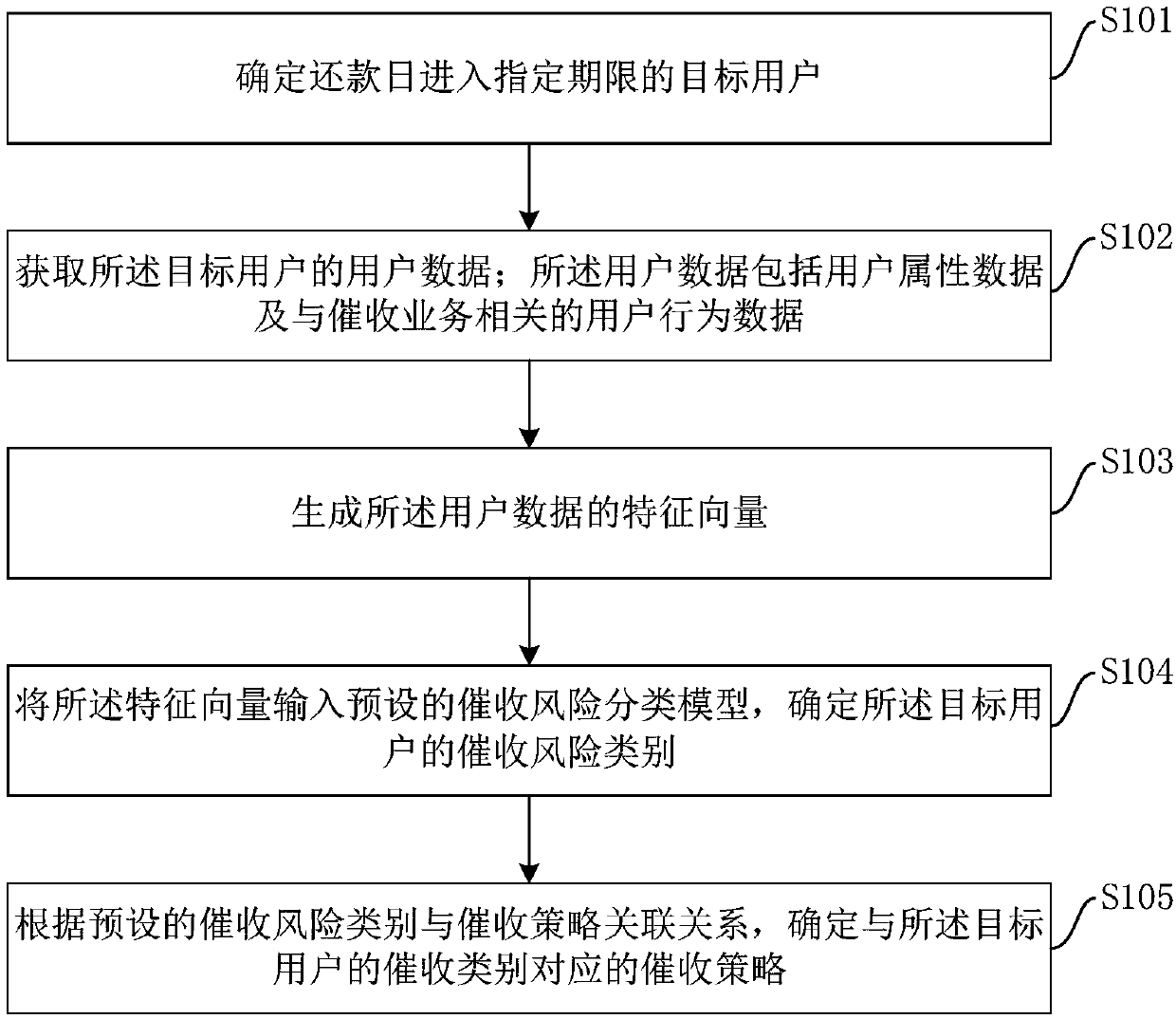
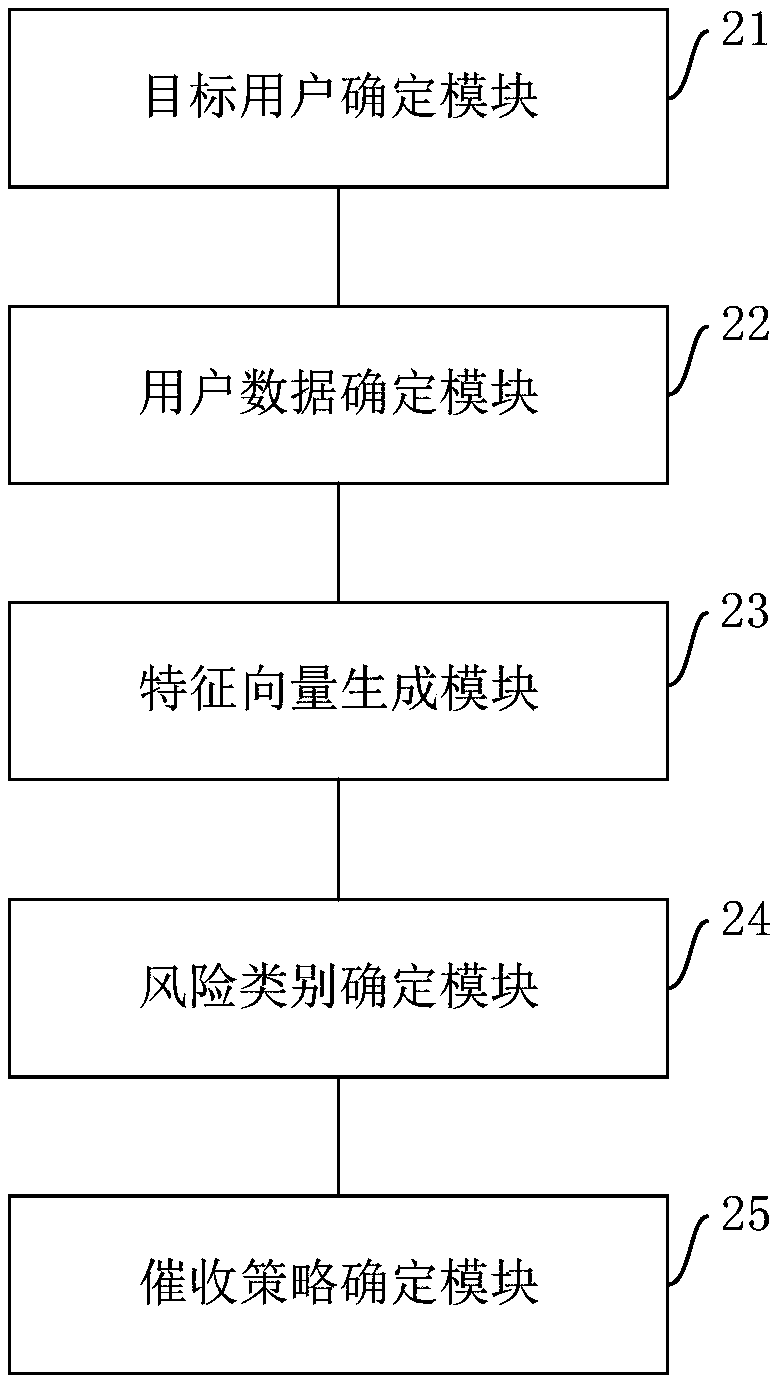
Collection method and device based on user data and storage medium
InactiveCN109559221AImprove collection success rateImprove collection efficiencyFinanceFeature vectorRisk classification
The embodiment of the invention provides a collection method and device based on user data and a storage medium. The method comprises the steps of determining a target user whose repayment day entersan appointed deadline; obtaining user data of the target user, wherein the user data comprises user attribute data and user behavior data related to the collection service; generating a feature vectorof the user data; Inputting the feature vector into a preset collection risk classification model, and determining a collection risk category of the target user; and determining a collection strategycorresponding to the collection category of the target user according to a preset corresponding relation between the collection risk category and the collection strategy. The embodiment of the invention can improve the collection success rate, and is high in efficiency and low in cost.
Owner:BANK OF CHINA
Determination of Appraisal Accuracy
A method for determining the accuracy of an appraisal report using a computer implemented application, including pre-validating an appraisal report to determine whether a first set of rules has been satisfied, the appraisal report including N fields to be completed, the first set of rules comprising completion of a pre-determined number of N fields; proceeding to a post-validating step if the first set of rules is satisfied; post-validating an appraisal report to provide an evaluation thereof, the evaluation including a plurality of risk categories including risk level indicators, and a risk-based overall score.
Owner:BLACK KNIGHT IP HLDG COMPANY
System And Process For Dominance Classification For Insurance Underwriting Suitable For Use By An Automated System
A risk classification technique that exploits the existing risk structure of the decision problem in order to produce risk categorizations for new candidates is described. The technique makes use of a set of candidates for which risk categories have already been assigned (in the case of insurance underwriting, for example, this would pertain to the premium class assigned to an application). Using this set of labeled candidates, the technique produces two subsets for each risk category: the Pareto-best subset and the Pareto-worst subset by using Dominance. These two subsets can be seen as representing the least risky and the most risky candidates within a given risk category. If there are a sufficient number of candidates in these two subsets, then the candidates in these two subsets can be seen as samples from the two hypothetical risk surfaces in the feature space that bound the risk category from above and below respectively. A new candidate is assigned a risk category by verifying if the candidate lies within these two bounding risk surfaces.
Owner:GE FINANCIAL ASSURANCE HLDG INC A RICHMOND
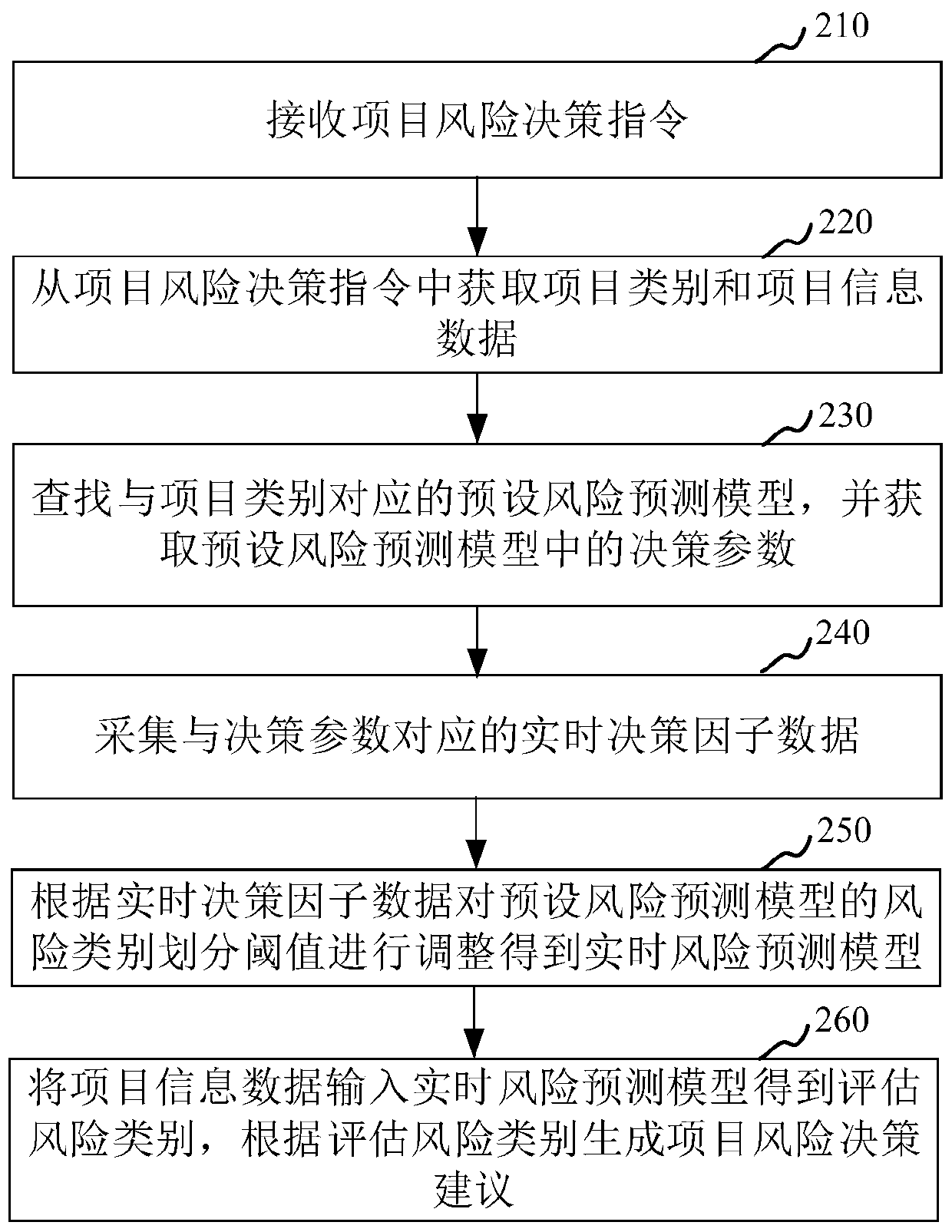
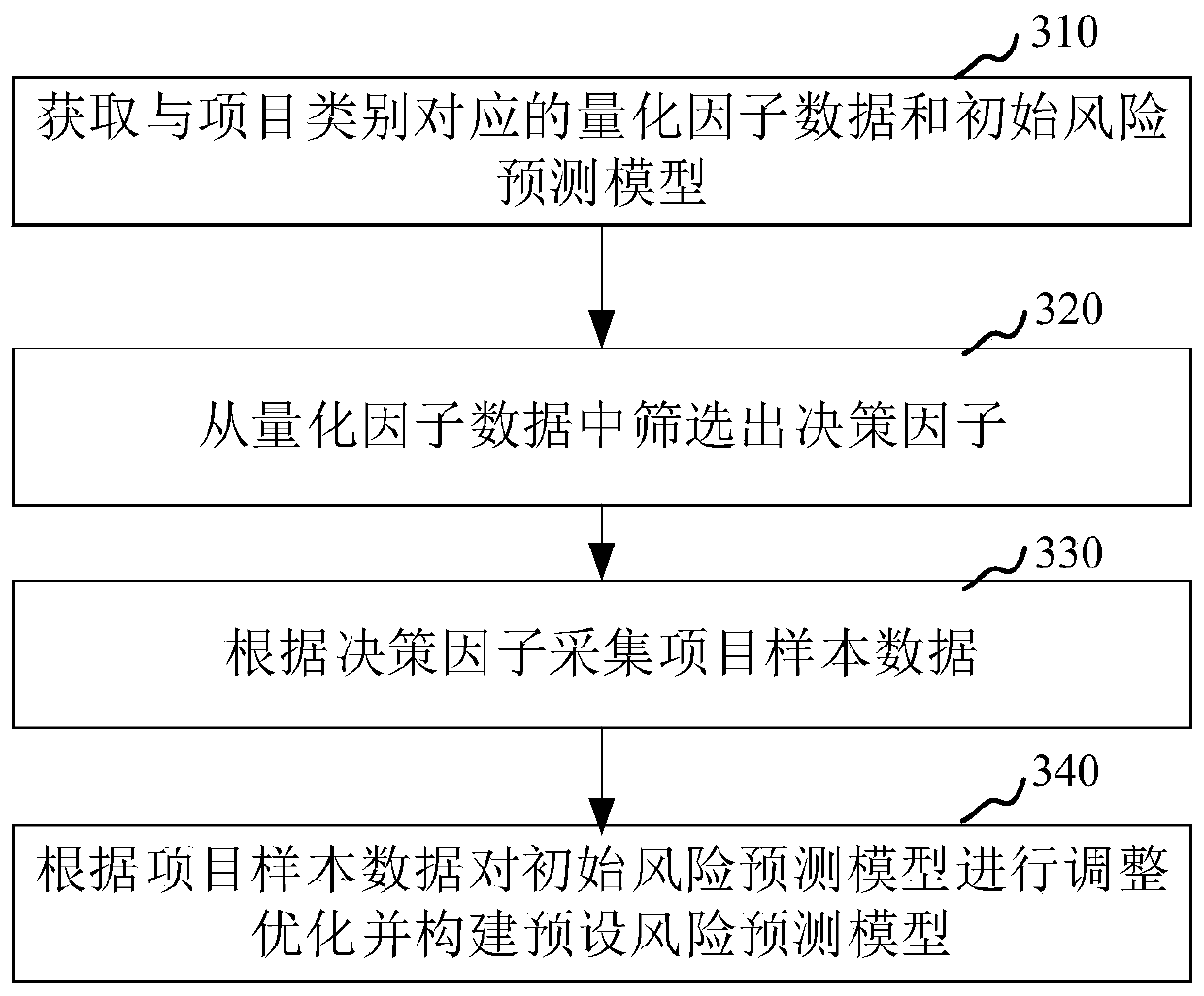
Project risk decision-making method and device, computer equipment and storage medium
PendingCN109816221AImprove the effectiveness of risk classificationThe risk assessment is reasonable and effectiveForecastingResourcesDecision takingData treatment
The invention relates to the field of big data processing, in particular to a project risk decision-making method and device, computer equipment and a storage medium. The method comprises the steps ofreceiving a project risk decision instruction; obtaining a project category and project information data from the project risk decision instruction; searching a preset risk prediction model corresponding to the project category, and obtaining a decision parameter in the preset risk prediction model; collecting real-time decision factor data corresponding to the decision parameters; adjusting a risk category division threshold value of a preset risk prediction model according to the real-time decision factor data to obtain a real-time risk prediction model; inputting the project information data into a real-time risk prediction model to obtain an assessment risk category, and generating project risk decision suggestions according to the assessment risk category. By adopting the method, theproject risk assessment accuracy can be improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
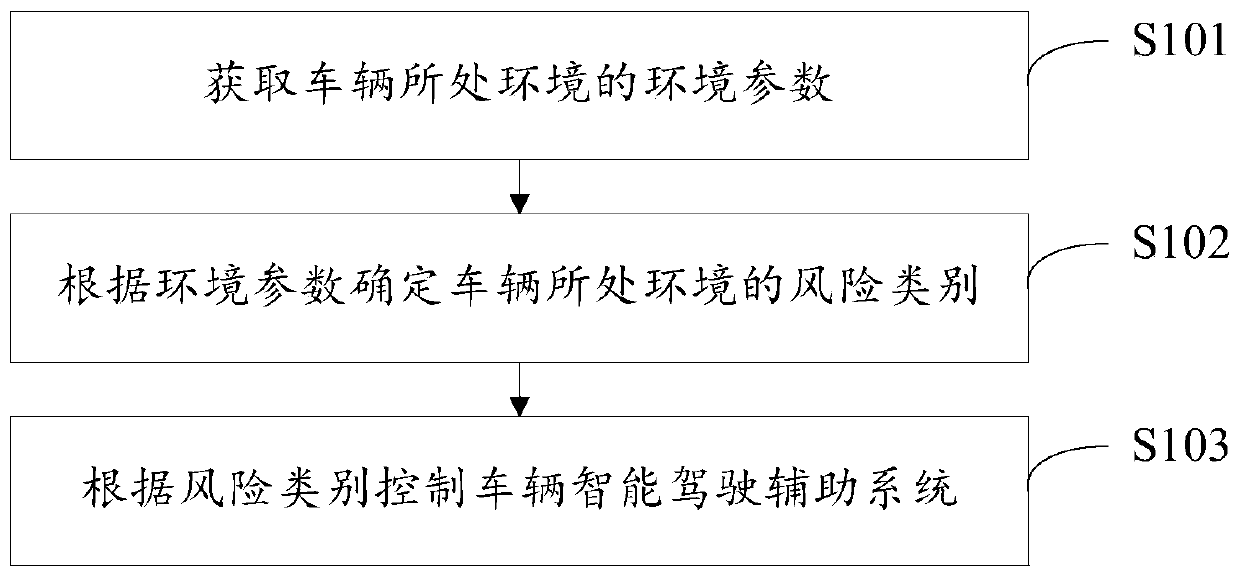
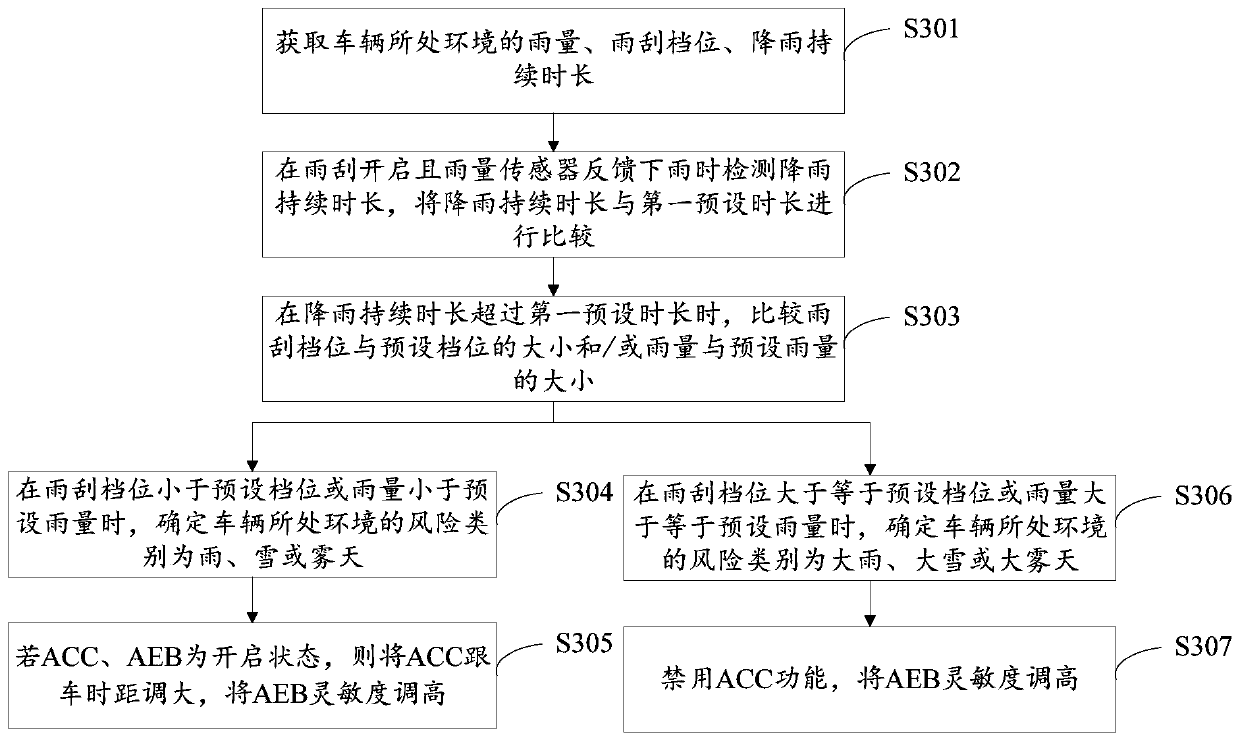
Intelligent driving auxiliary control method and system
The invention discloses an intelligent driving auxiliary control method. The method comprises the steps of obtaining the environmental parameters of the environment where a vehicle is located, whereinthe environmental parameters comprise one or more of the environmental temperature, the rainfall, the wiper gears, the rainfall duration, the illumination intensity and the headlight on-state; determining the risk category of the environment where the vehicle is located according to the environment parameters; controlling the vehicle intelligent driving assistance system according to the risk category, wherein the vehicle intelligent driving assistance system comprises an ACC and / or an AEB. Meanwhile, the invention further discloses the intelligent driving auxiliary control system. Accordingto the invention, a user can be reminded to reasonably use the intelligent driving assistance system, the intelligent driving assistance system is forbidden under the extreme weather conditions, compared with the existing driving assistance system, the safety level of the intelligent driving assistance system can be effectively improved, and no hardware cost is increased.
Owner:ZHEJIANG GEELY AUTOMOBILE RES INST CO LTD +1
System and process for detecting outliers for insurance underwriting suitable for use by an automated system
An outlier detector that exploits the existing risk structure of the decision problem in order to discover risk assignments that are globally inconsistent is described. The technique works on a set of candidates for which risk categories have already been assigned. In the case of insurance underwriting, the invention pertains to the premium class assigned to an application. For this set of labeled candidates, the system finds all such pairs of applications belonging to different risk categories, which violate the principle of dominance. The invention matches the risk ordering of the applications with the ordering imposed by dominance and uses any mismatch during the process to identify applications that were potentially assigned incorrect risk categories.
Owner:GE FINANCIAL ASSURANCE HLDG INC A RICHMOND
Intelligent alarm method and mobile terminal
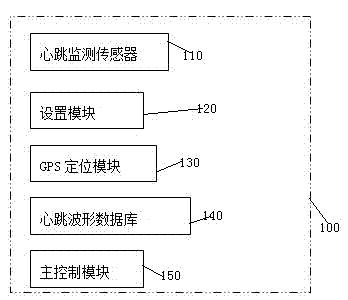
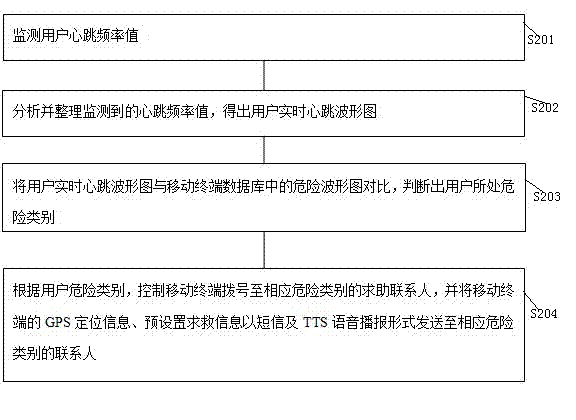
InactiveCN103886712APersonal and property safety protectionAlarmsMeasuring/recording heart/pulse rateComputer terminalBroadcasting
The invention discloses an intelligent alarm method and a mobile terminal. The method includes the steps that user heartbeat frequency values are monitored; the monitored heartbeat frequency values are analyzed and arranged, and a user real-time heartbeat oscillogram is obtained; the user real-time heartbeat oscillogram is compared with risk oscillograms in a database of the mobile terminal, and the user risk category is judged; the mobile terminal is controlled to dial a helping contact person of the corresponding risk category according to the user risk category, and GPS positioning information and preset help information of the mobile terminal are sent to the contact person of the corresponding risk category in a short message and TTS voice broadcasting mode. According to the intelligent alarm method and the mobile terminal, due to the fact that an intelligent alarm method is improved, when the user carries the mobile terminal closely, heartbeats of the user can be monitored at any time, the user risk condition can be judged intelligently according to the heartbeats of the user, an alarm is sent to the corresponding contact person automatically, and therefore the personal and property safety of the user is guaranteed.
Owner:PHICOMM (SHANGHAI) CO LTD
System for optimization of insurance underwriting suitable for use by an automated system
A robust system for automating the tuning and maintenance of decision-making systems is described. A configurable multi-stage mutation-based evolutionary algorithm optimally tunes the decision thresholds and internal parameters of fuzzy rule-based and case-based systems that decide the risk categories of insurance applications. The tunable parameters have a critical impact on the coverage and accuracy of decision-making, and a reliable method to optimally tune these parameters is critical to the quality of decision-making and maintainability of these systems.
Owner:GE FINANCIAL ASSURANCE HLDG INC A RICHMOND
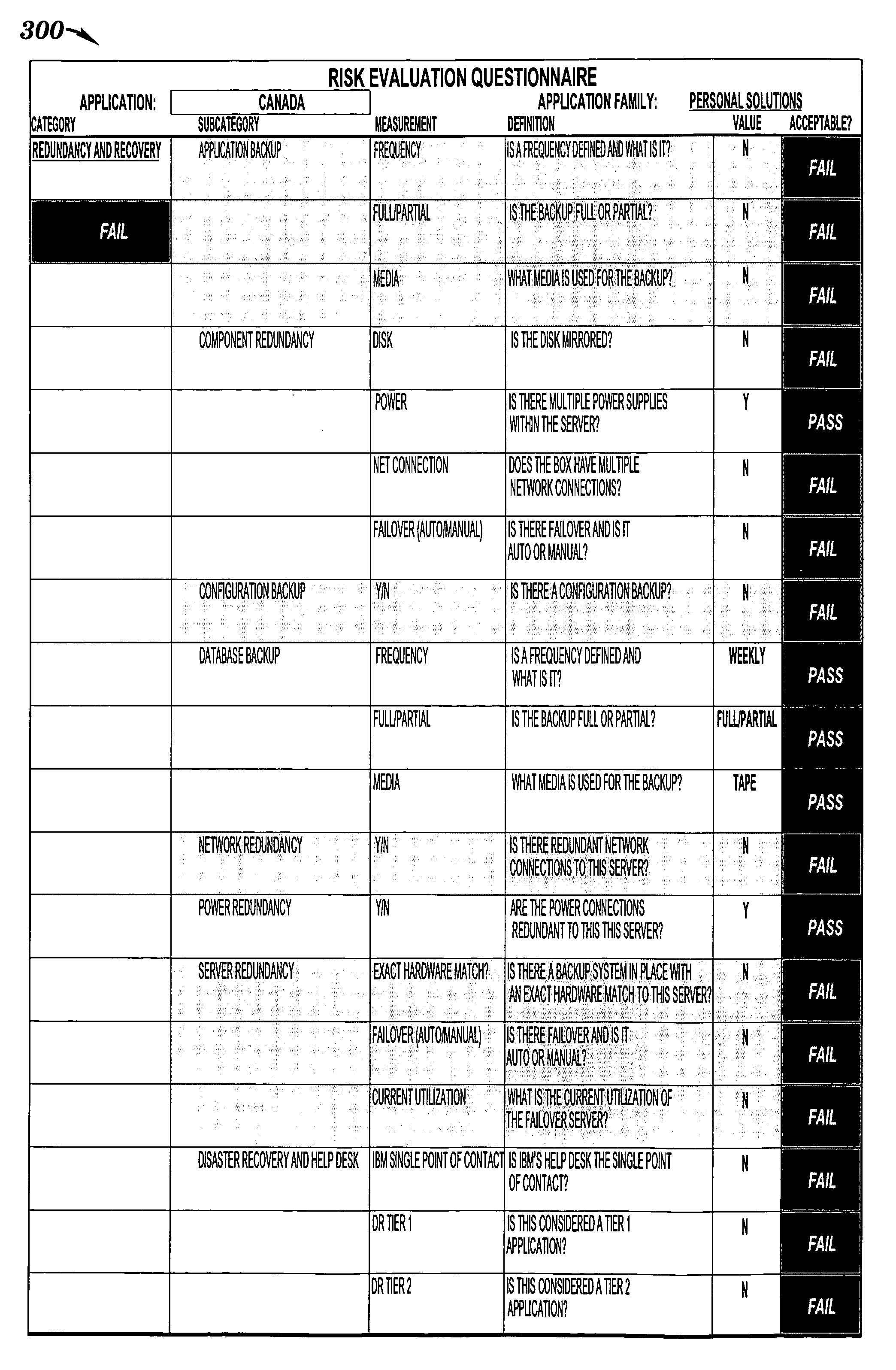
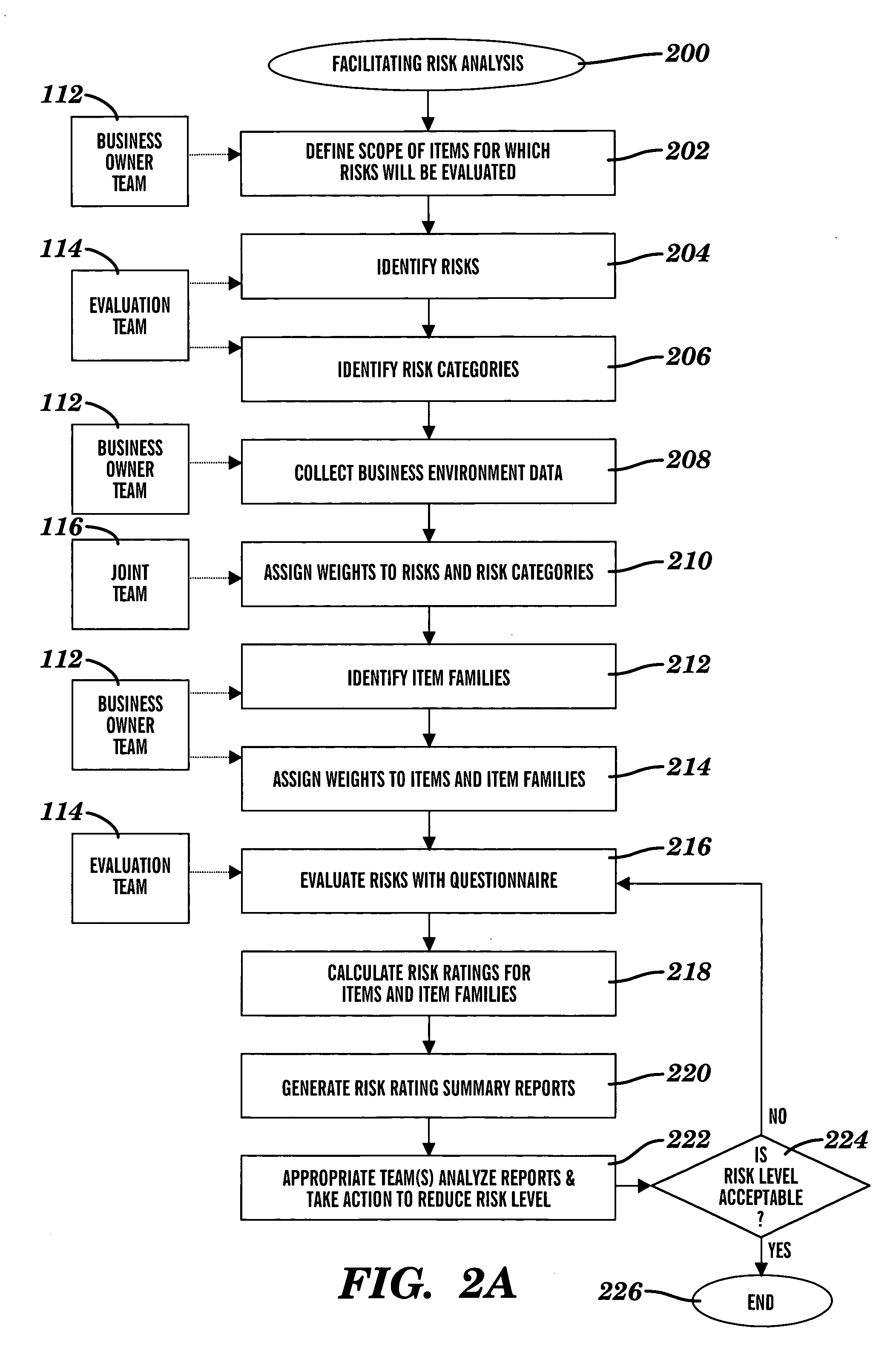
Method and system for facilitating analysis of risks
InactiveUS20060247957A1Facilitates analysis of riskFacilitate risk analysisFinanceSpecific program execution arrangementsRisk ratingRisk evaluation
A method and system for facilitating analysis of risks. Items, families of items, risks, sub-categories of risks, and categories of risks are weighted. Items are related to each other by a common business function. The risks are associated with each item. For each item, each associated risk is evaluated to determine whether the risk is mitigated. Risk ratings associated with the items or families are calculated using at least risk evaluations and weights assigned to risks and items. The risk ratings are summarized in selectable views which are based on the sub-categories or categories, and which are to be analyzed by wide-ranging levels in a business organizational hierarchy.
Owner:SERVICENOW INC
Risk identification in supply chain
Owner:DASSAULT SYST AMERICAS CORP
System and method for predictive categorization of risk
A system and method for predictive categorization of risk of at least one project related activity is provided. The system and method provide categorization of the project related activity into one of a plurality of predetermined risk categories. Further, the risk category of the project related activity is predicted in at least one stage of the project life cycle. The method comprises collecting inputs pertaining to the project related activity being categorized and a predetermined set of details for categorizing the project related activity. The method further comprises categorizing the project related activity by applying discriminant analysis. The application of discriminant analysis comprises constructing a set of functions based on the predetermined set of details. Thereafter, the constructed set of functions are applied on the details collected pertaining to the project related activity, wherein the functions are applied for predicting the risk category of the project related activity.
Owner:INFOSYS LTD
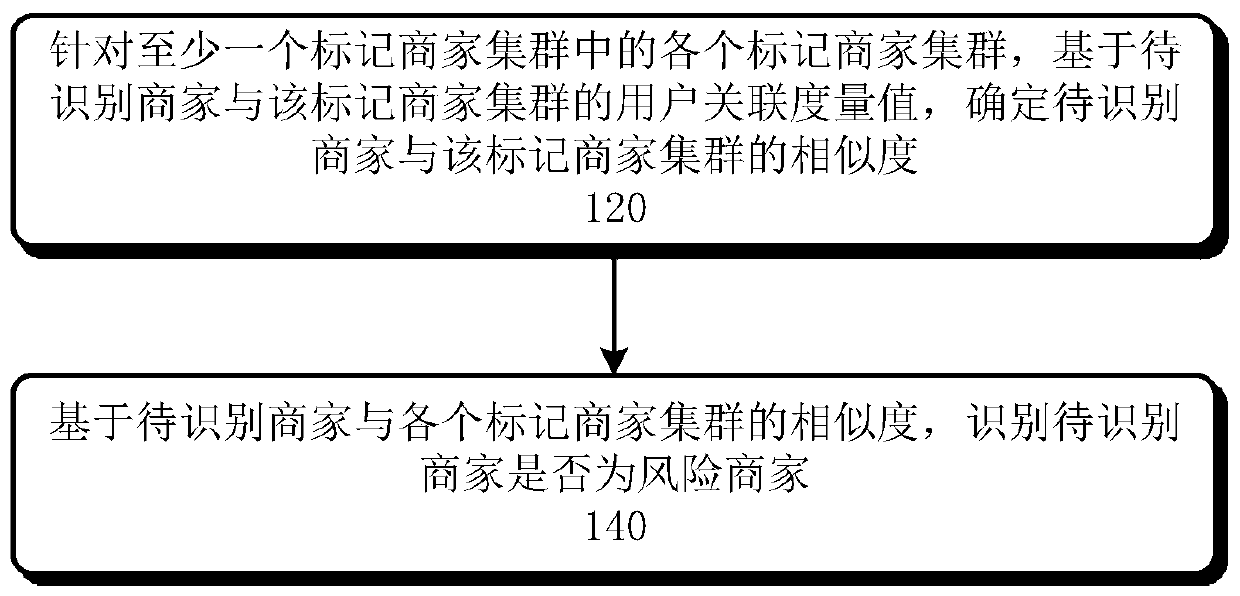
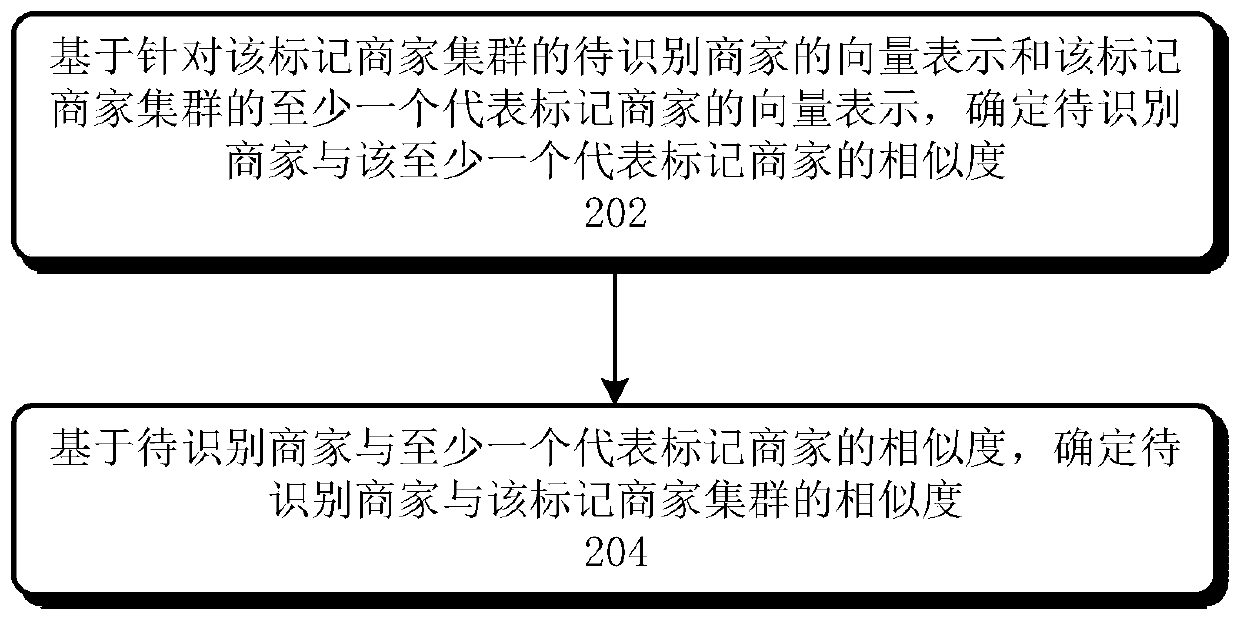
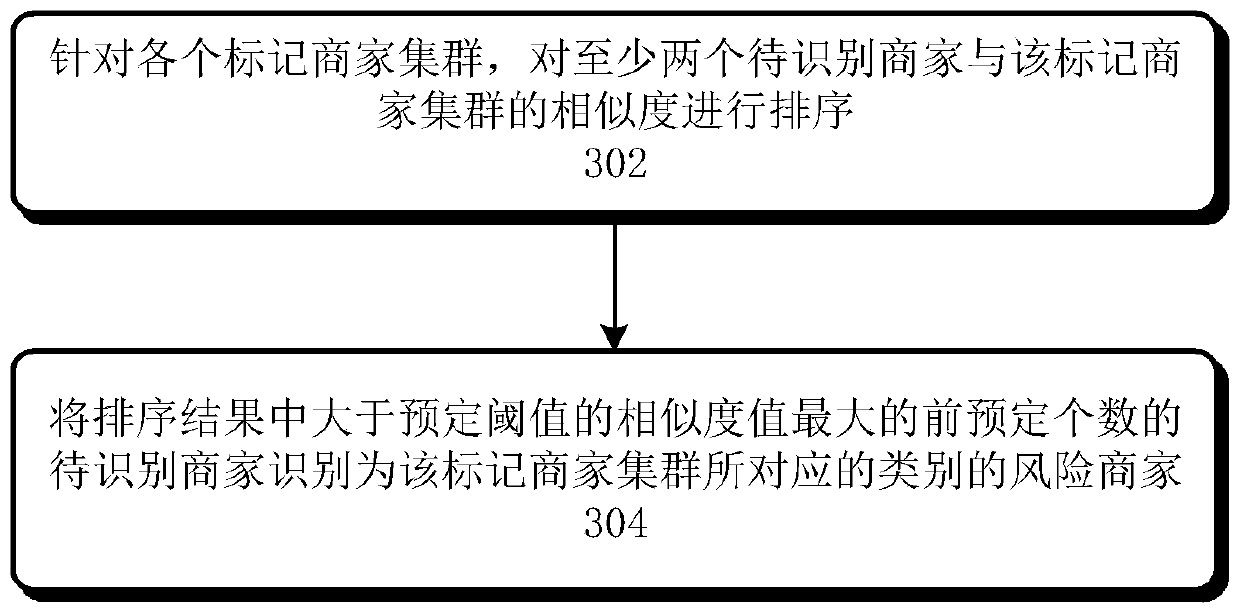
Method and device for identifying risk merchants
ActiveCN110033170AAccurate identificationReduce computationPayment architectureBuying/selling/leasing transactionsCluster basedData mining
The invention relates to a method and device for identifying risk merchants. The method comprises the following steps of aiming at each marked merchant cluster in at least one marked merchant cluster,determining the similarity between the to-be-identified merchant and the marked merchant cluster based on the user correlation degree value of the to-be-identified merchant and the marked merchant cluster, and marking each marked merchant in each marked merchant cluster as a risk merchant of a corresponding risk category; and based on the similarity between the to-be-identified merchant and eachmarked merchant cluster, identifying the risk merchant in the at least one to-be-identified merchant.
Owner:ADVANCED NEW TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com