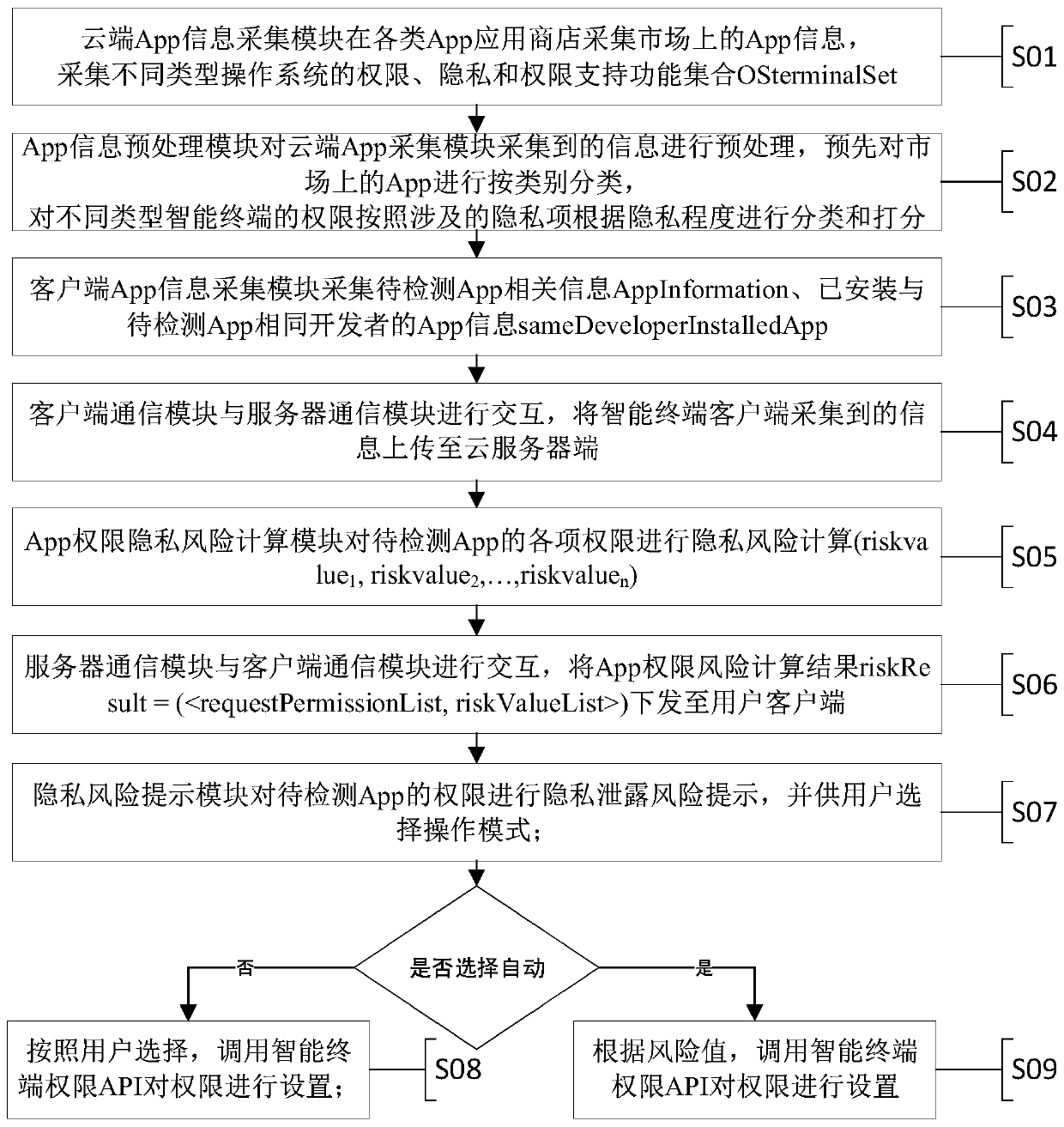
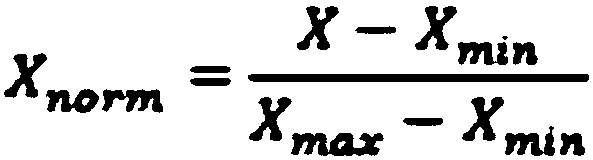Patents
Literature
204 results about "Risk detection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Detection risk is the chance that an auditor will fail to find material misstatements that exist in an entity's financial statements. These misstatements may be due to either fraud or error.
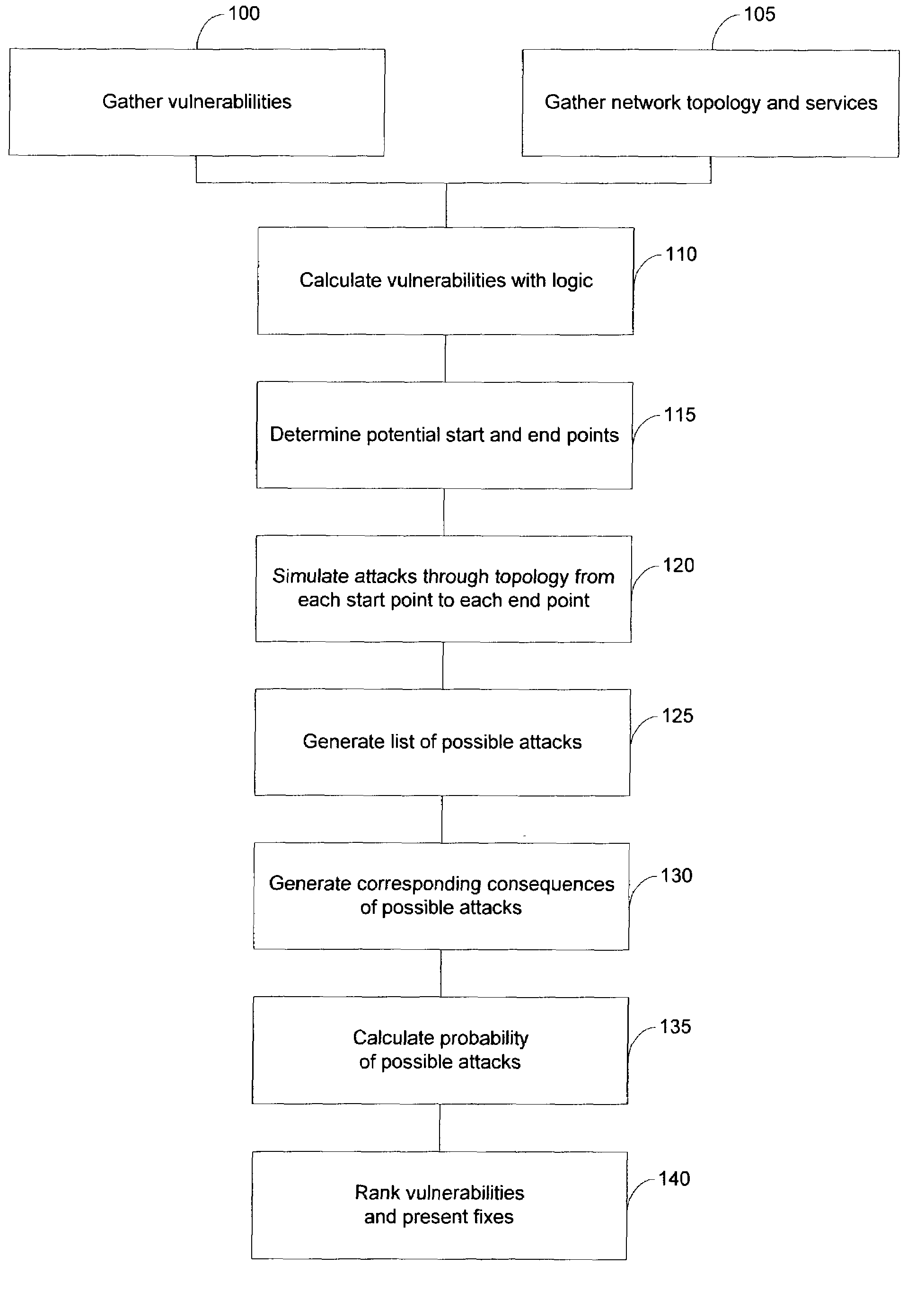
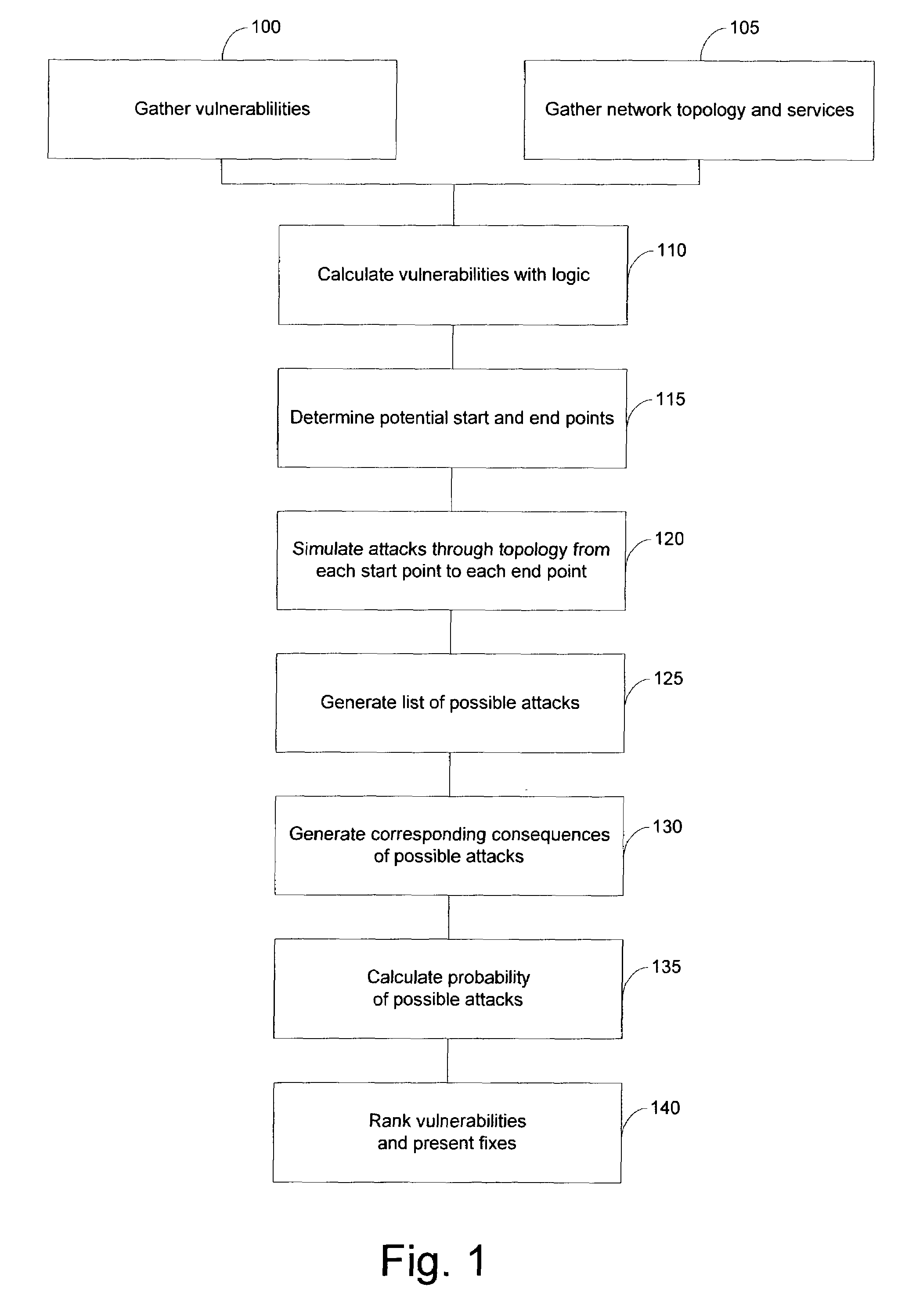
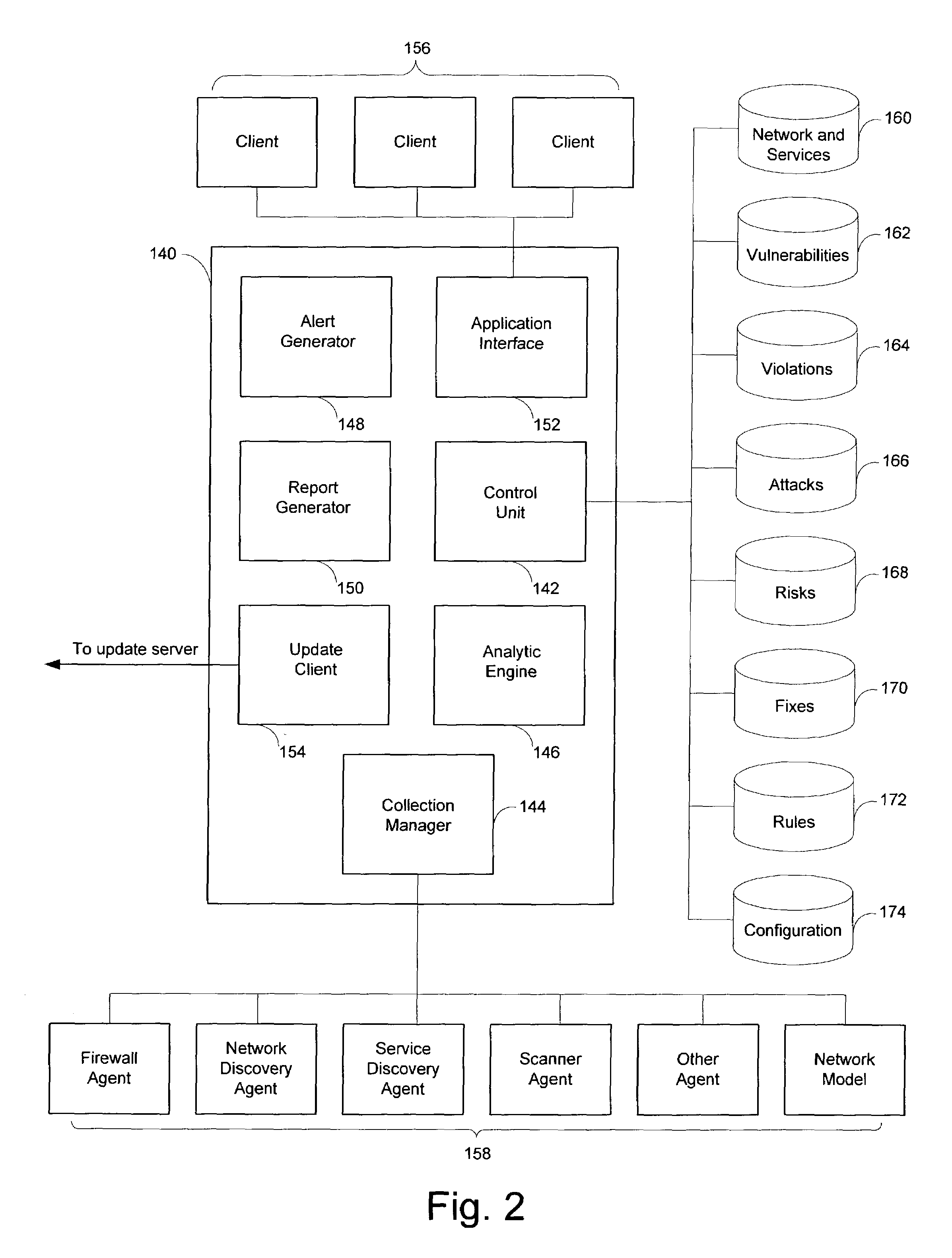
System and method for risk detection and analysis in a computer network
The present invention provides systems and methods for risk detection and analysis in a computer network. Computerized, automated systems and methods can be provided. Raw vulnerability information and network information can be utilized in determining actual vulnerability information associated with network nodes. Methods are provided in which computer networks are modeled, and the models utilized in performing attack simulations and determining risks associated with vulnerabilities. Risks can be evaluated and prioritized, and fix information can be provided.
Owner:SKYBOX SECURITY
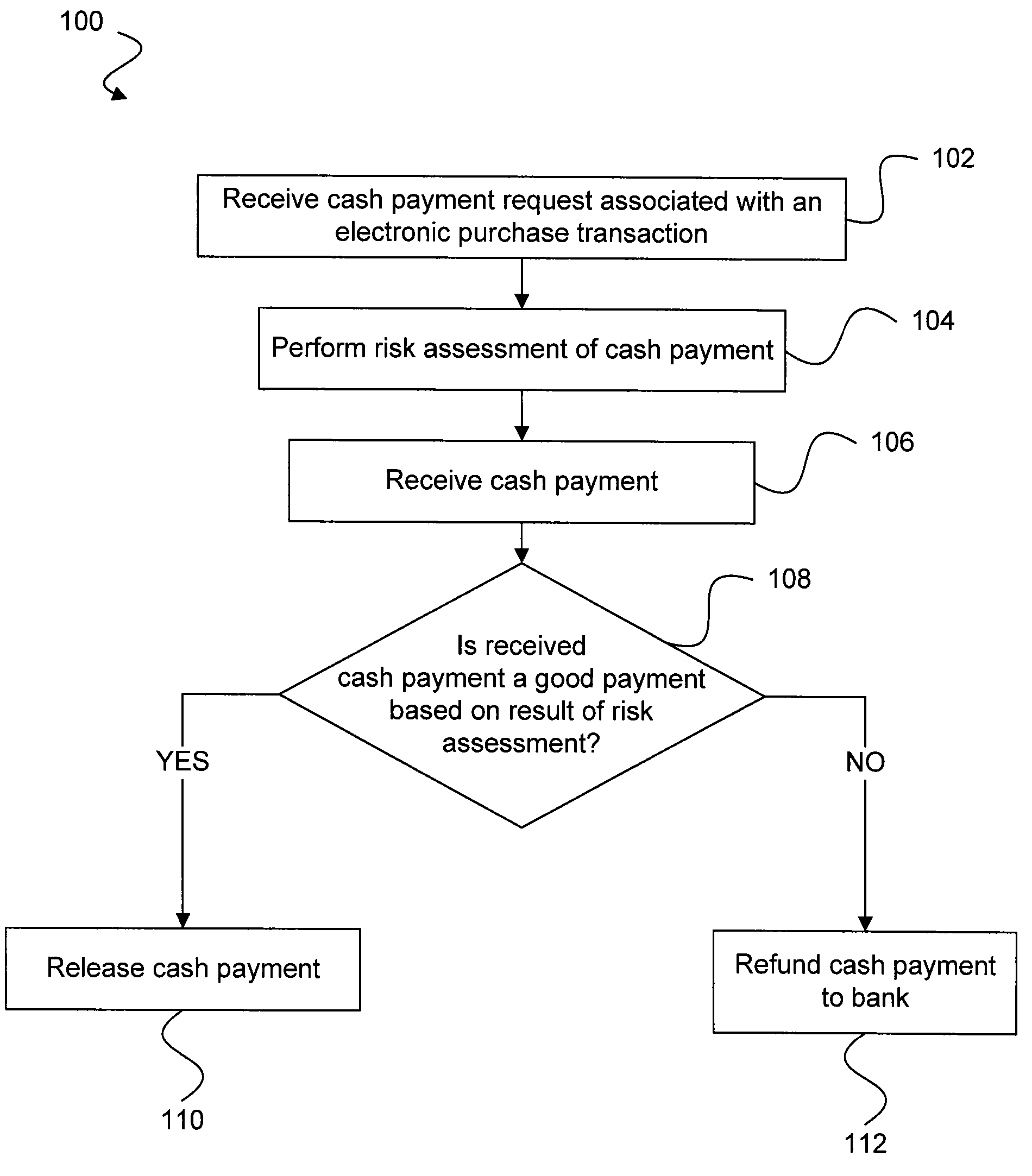
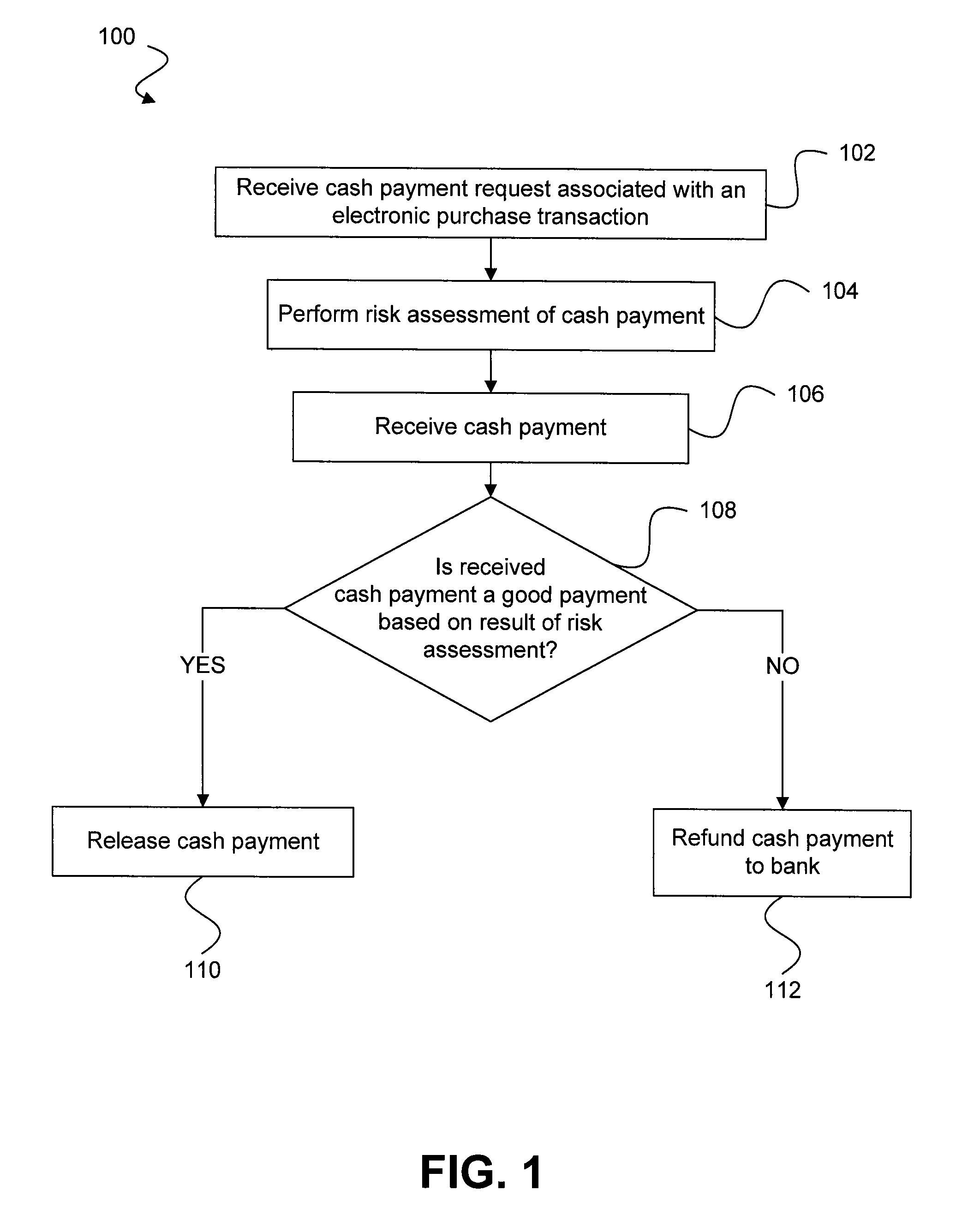
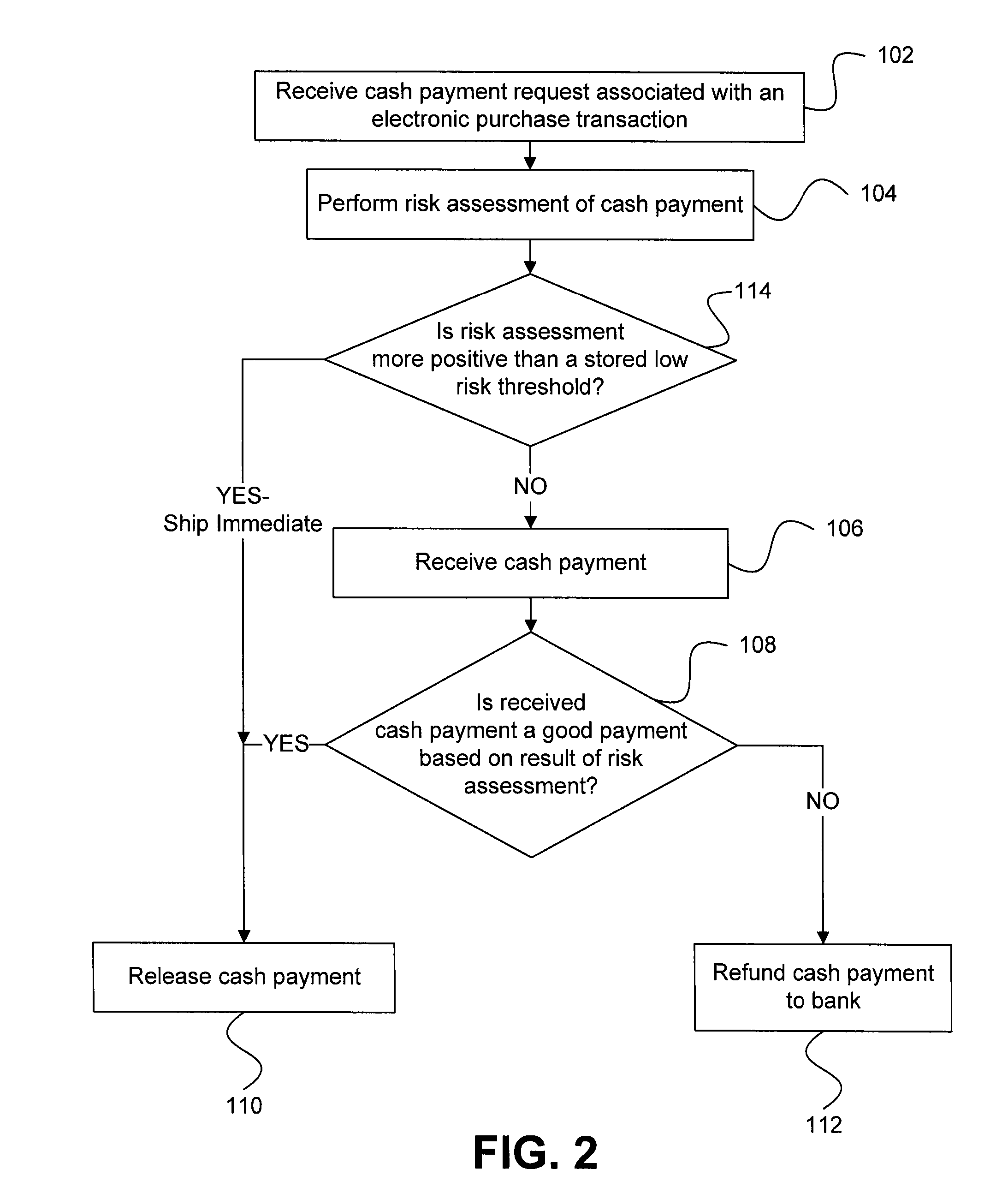
Risk detection and assessment of cash payment for electronic purchase transactions
A system and methods are provided which allow consumers to pay for ecommerce transactions through online bill payment and for merchants to determine that payments are not fraudulent. The system and methods do not rely on personal or confidential customer information relating to credit-cards and / or bank account routing information, date of birth and / or social security number. A risk manager can perform risk assessment for the cash payment based on order information and non-confidential purchaser information included in a cash payment request. In response to receiving an indication of the cash payment from the purchaser, a determination is made whether the cash payment is a good payment based on the risk assessment. The cash payment is released to a merchant in response to a determination that the cash payment is a good payment.
Owner:WESTERN UNION FINANCIAL SERVICES
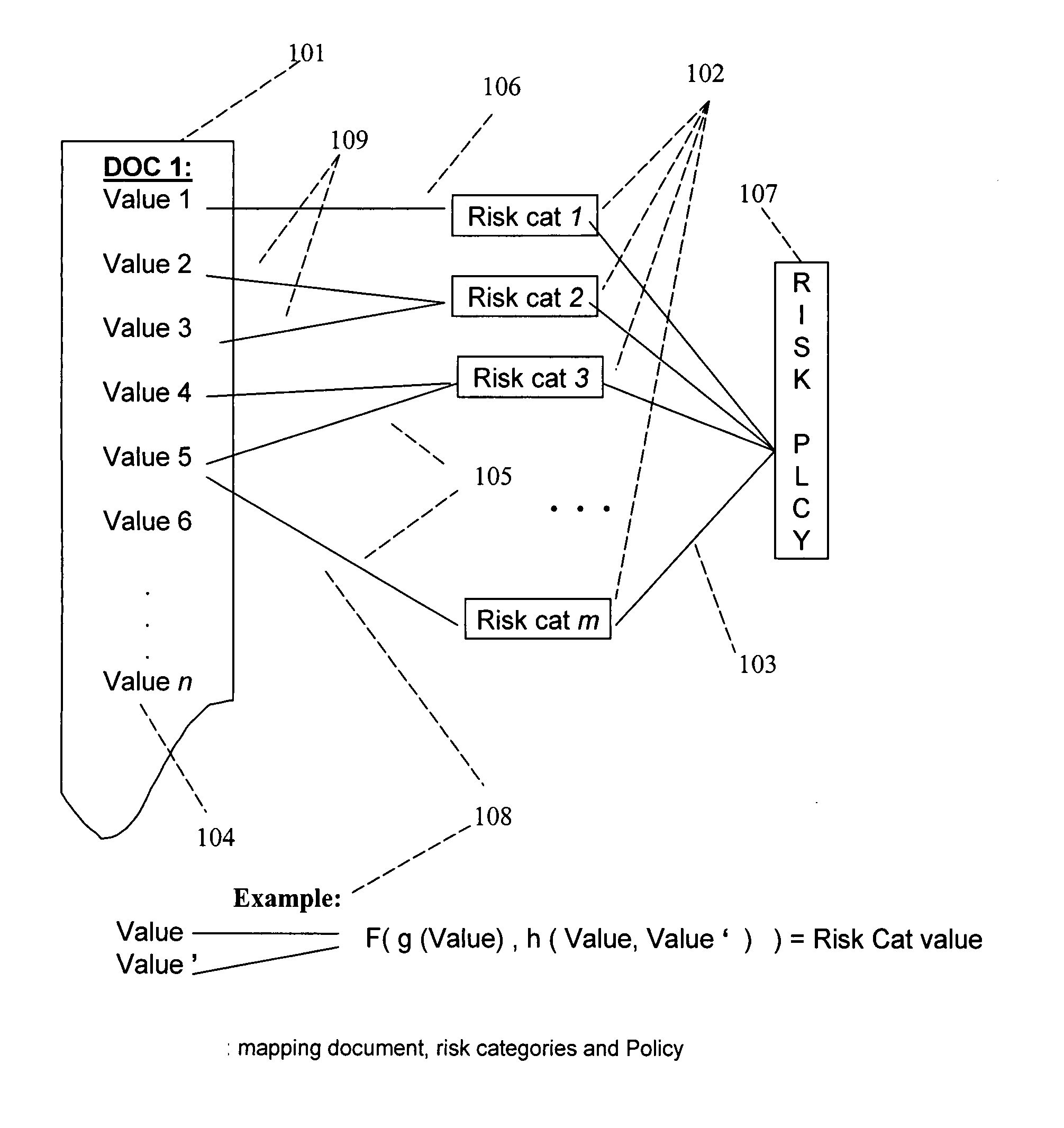
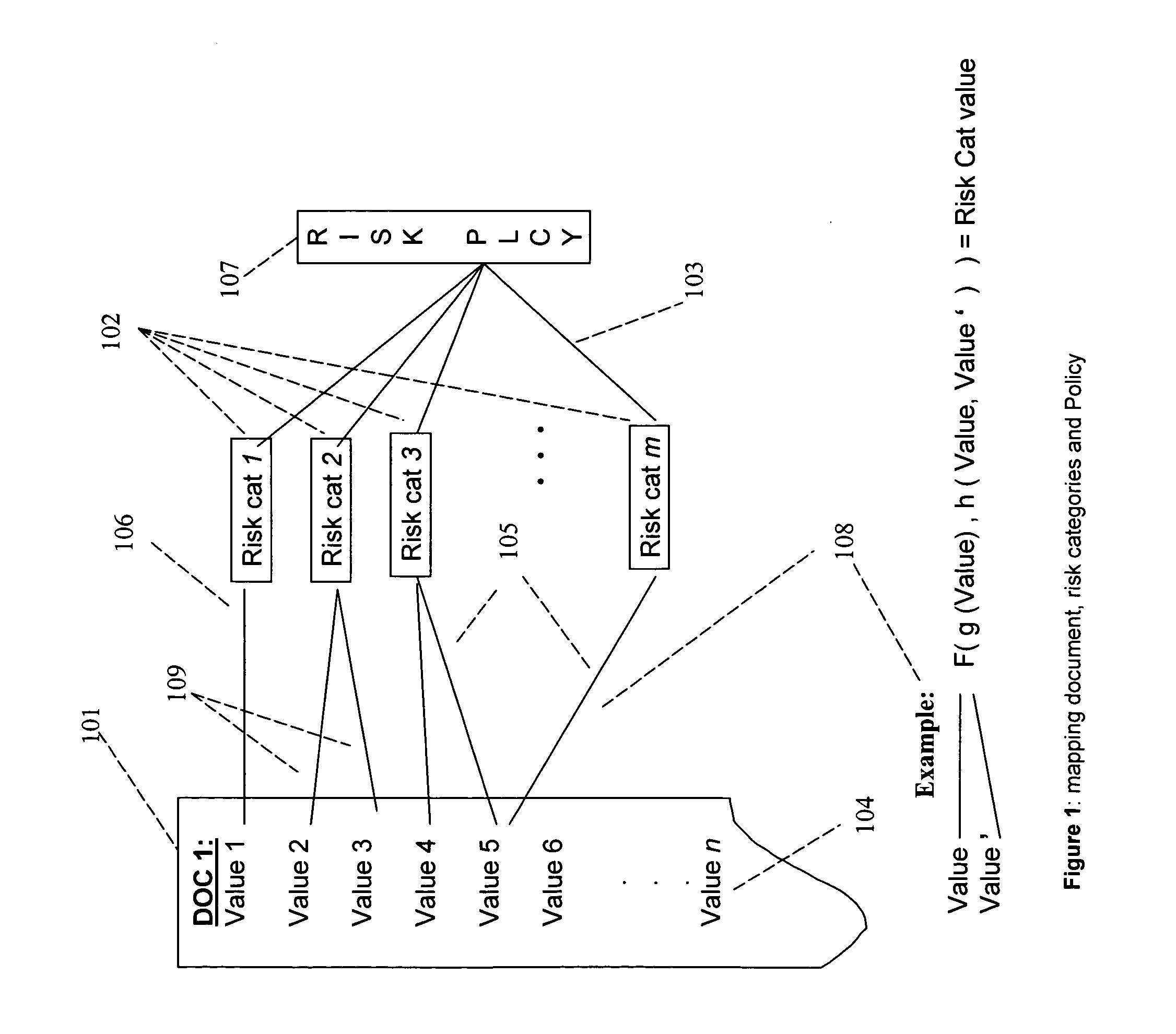
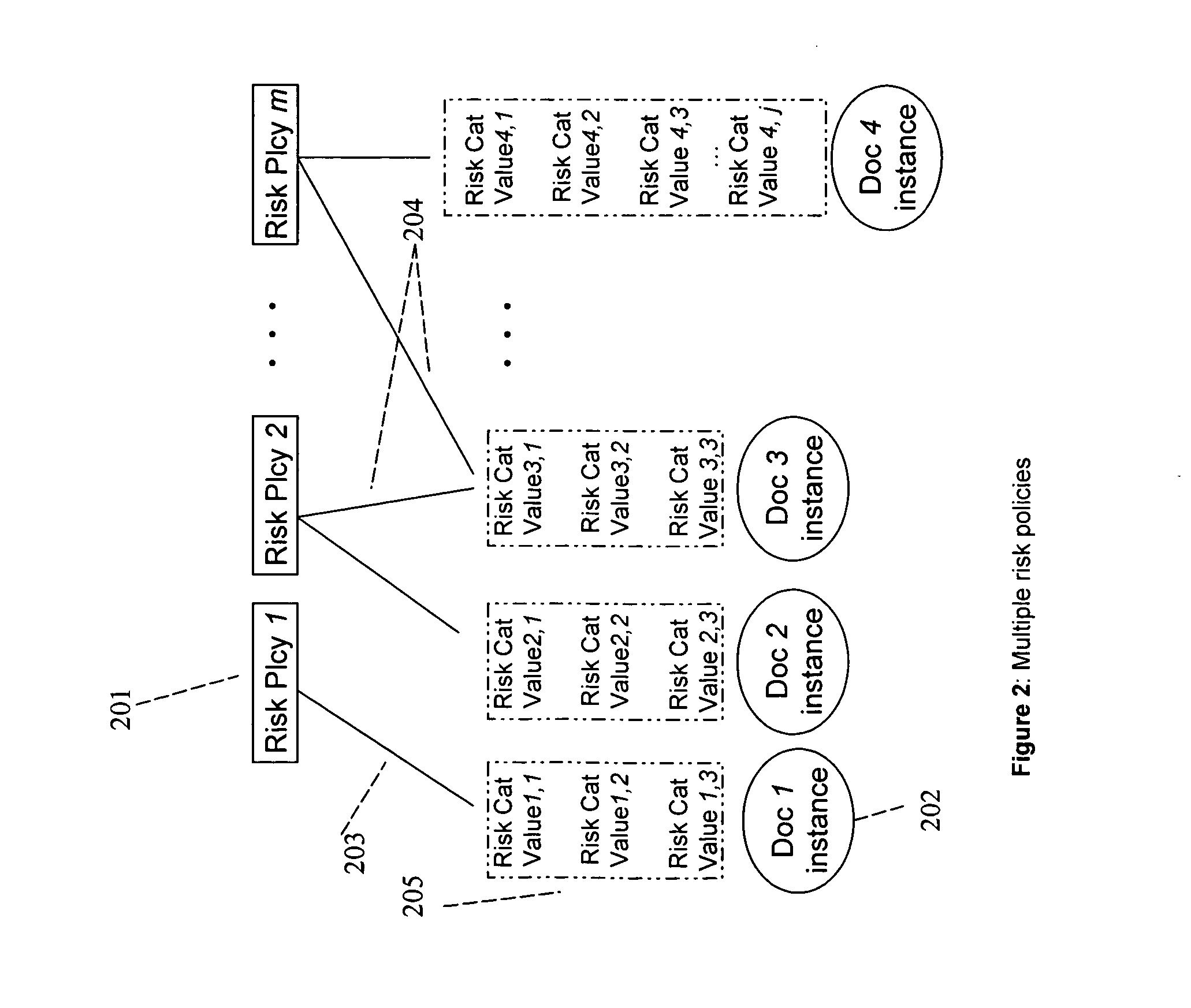
System and method for risk detection reporting and infrastructure
InactiveUS20050021360A1Efficiently monitor riskFlexibility in modifying and updatingFinanceMemory loss protectionPaper documentDocument preparation
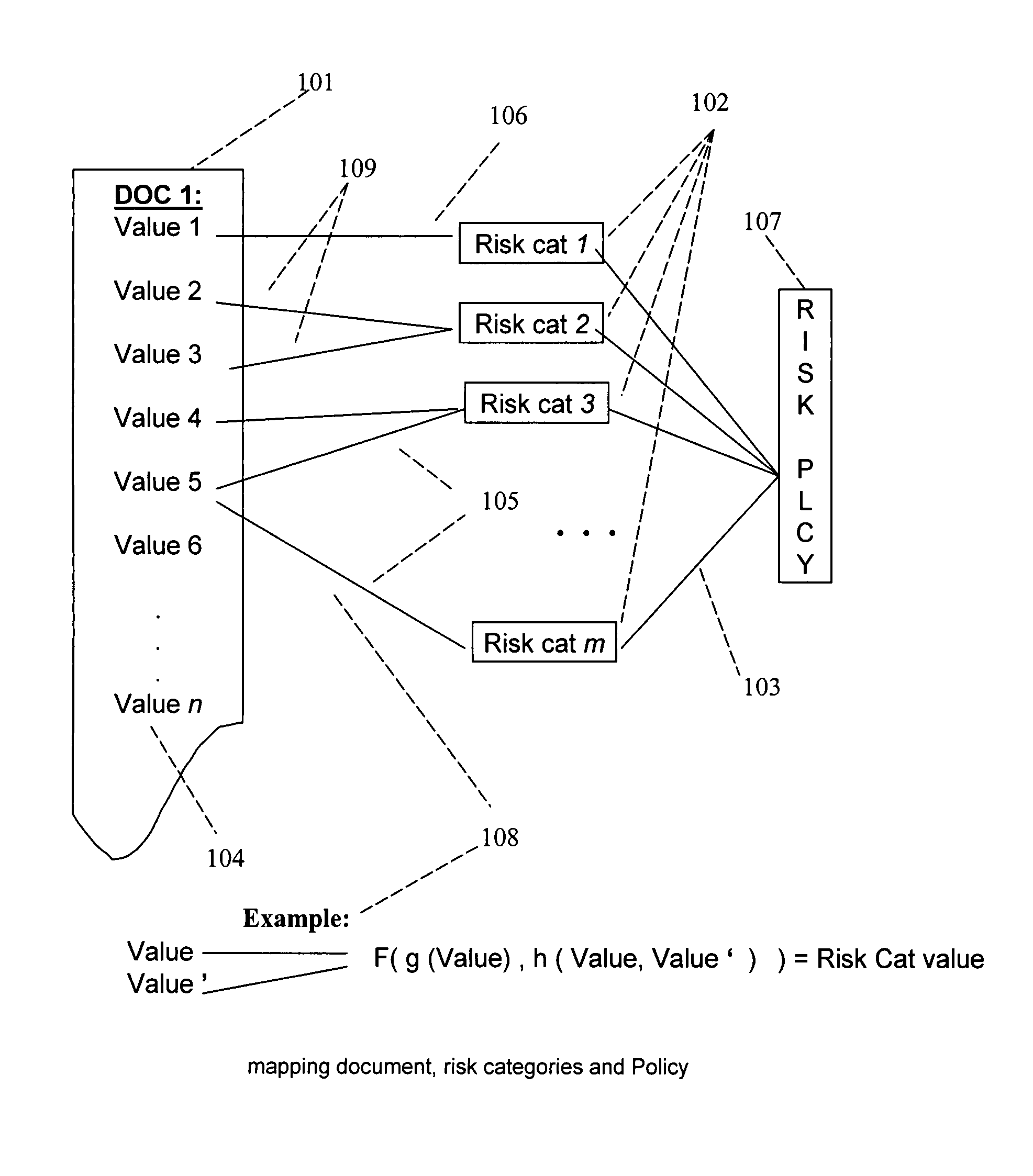
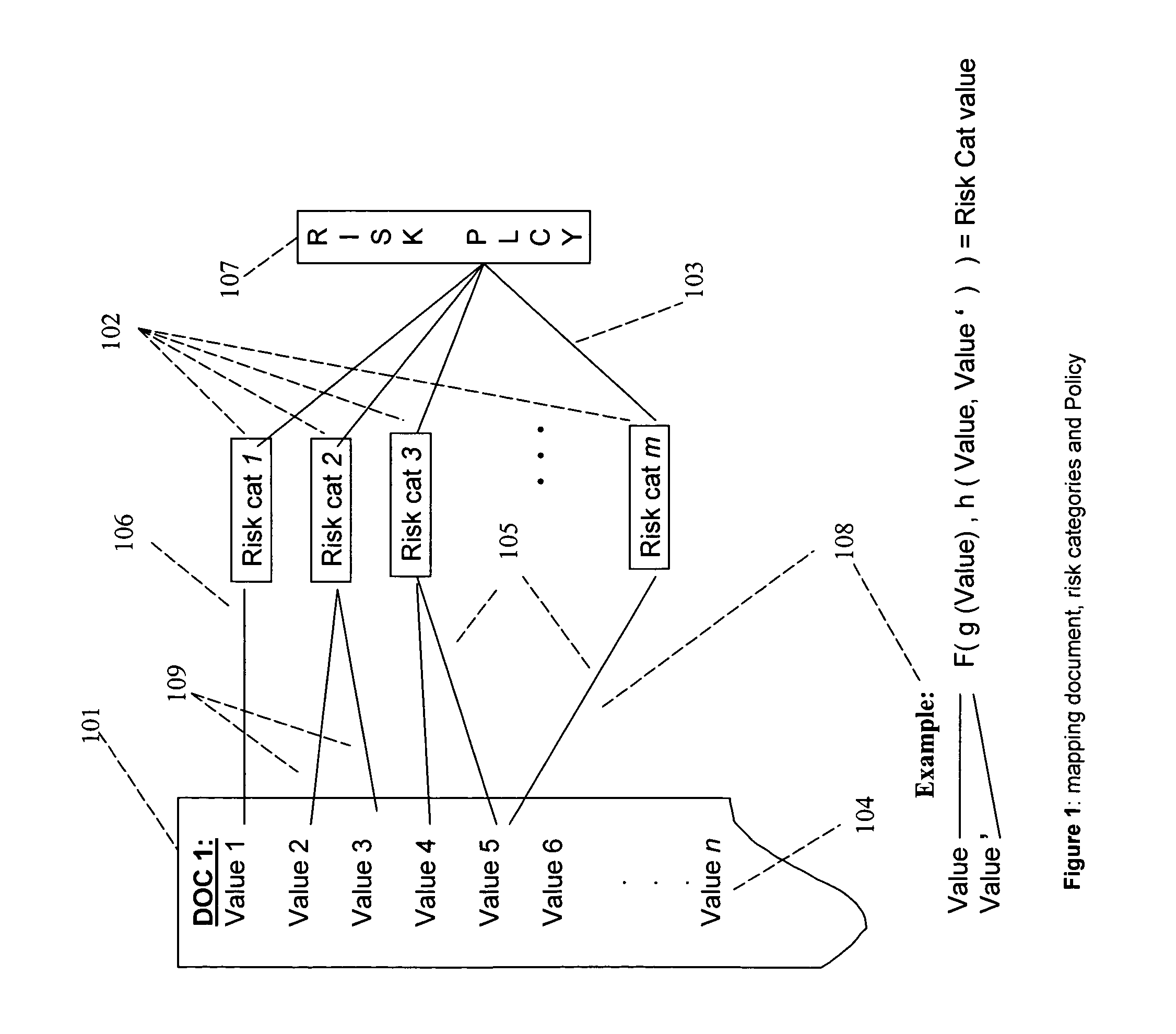
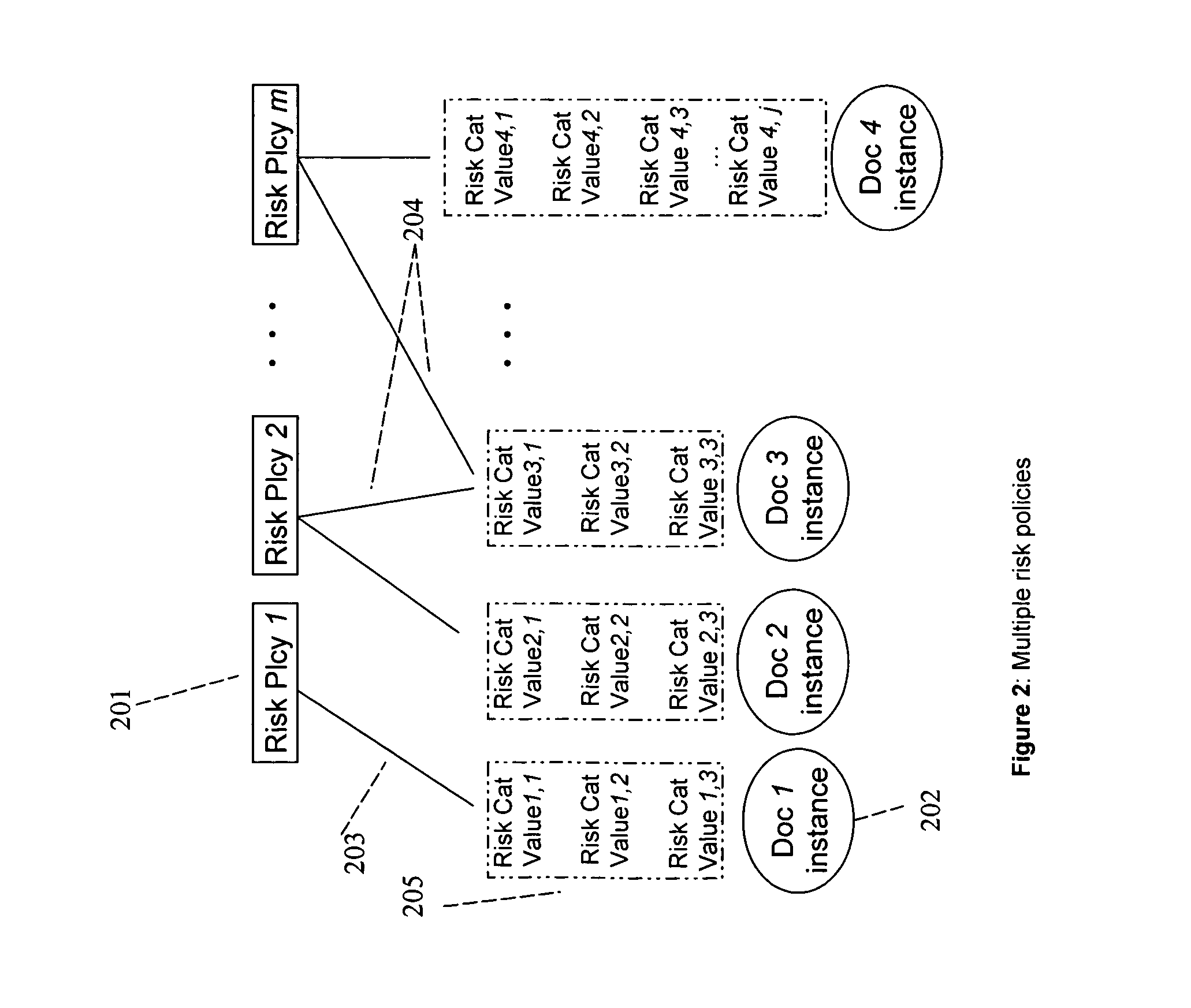
A method, a system, and a device for monitoring risks associated with at least one business process, including: evaluating at least one of a plurality of document instances, wherein each of the document instances includes, in association therewith, a plurality of document values, against a plurality of risk categories; implementing the plurality of risk categories pursuant to at least one acceptable risk policy approved for the at least one business process; and qualifying at least one of the at least one of the plurality of documents pursuant to an approval rating of the at least one document in at least one risk category. The system, method, and device efficiently monitor risk, and allow for flexibility in modifying or updating risk policy.
Owner:SMARTSAFETY SOFTWARE INC
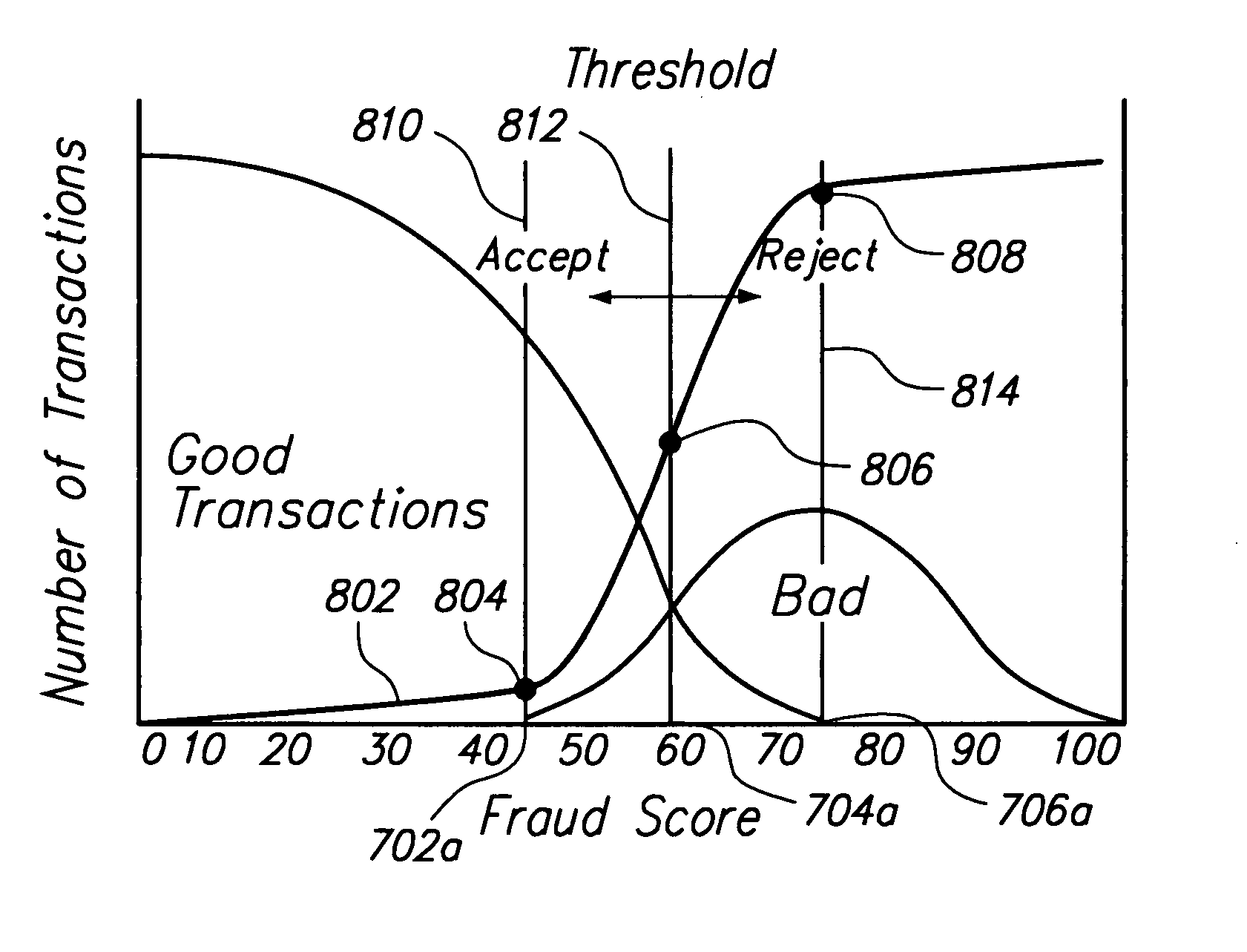
Method and apparatus for evaluating fraud risk in an electronic commerce transaction
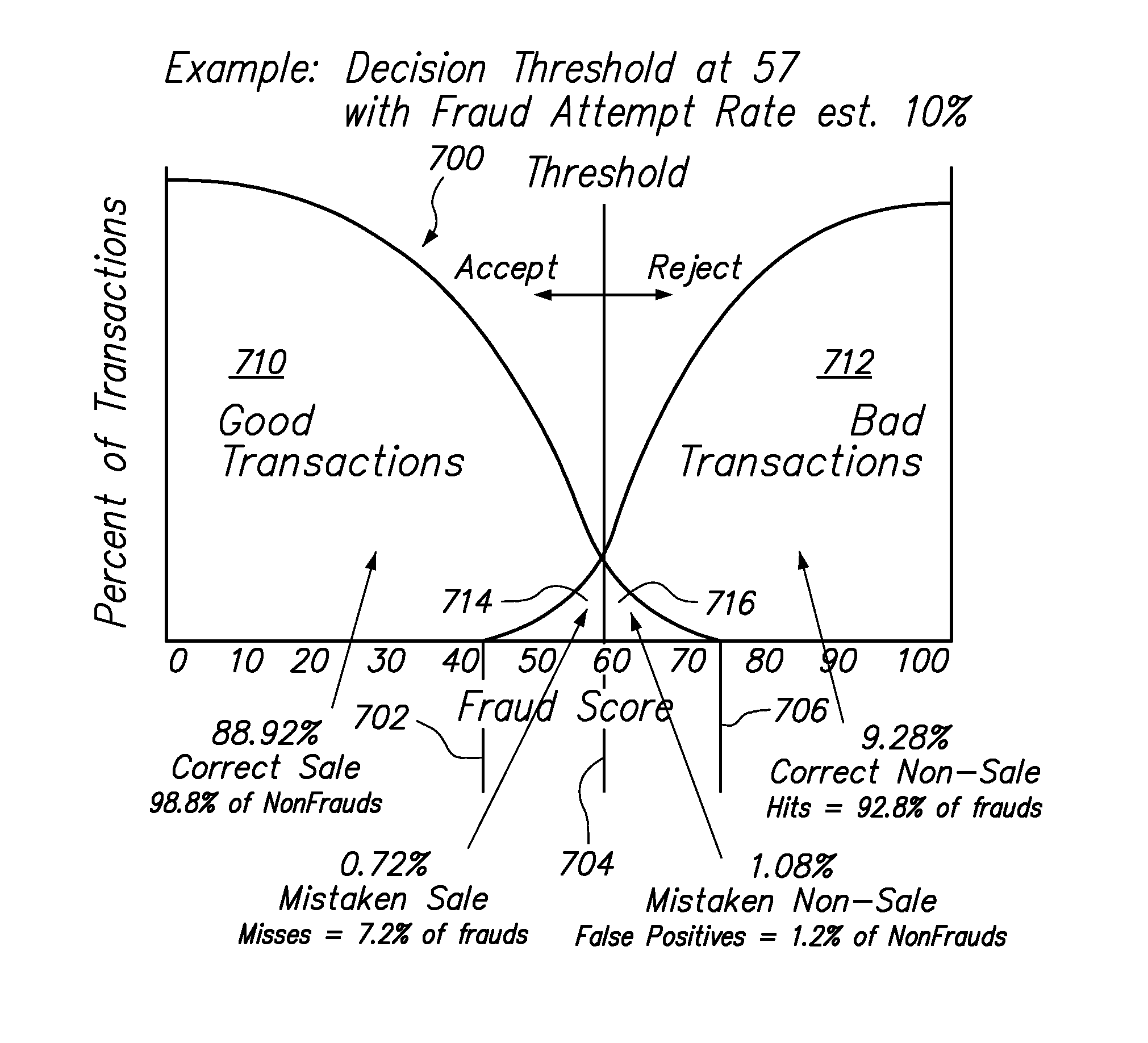
According to one aspect, transaction information is received and applied to multiple fraud risk mathematical models that each produce a respective raw score, which are transformed with respective sigmoidal transform functions to produce optimized likelihood of fraud risk estimates to provide to a merchant. In one embodiment, the respective fraud risk estimates are combined using fusion proportions that are associated with the respective risk estimates, producing a single point risk estimate, which is transformed with a sigmoidal function to produce an optimized single point risk estimate for the transaction. The sigmoidal functions are derived to approximate a relationship between risk estimates produced by fraud risk detection models and a percentage of transactions associated with respective risk estimates, where the relationship is represented in terms of real-world distributions of fraudulent transaction and non-fraudulent transaction. One embodiment is directed to computing respective risk test penalties for multiple risk tests in one or more of the multiple fraud risk mathematical models used to estimate the likelihood of fraud, given a certain pattern of events represented by the transaction information, wherein the respective risk test penalties are computed as the inverse of the sum of one and a false positive ratio for the respective risk test.
Owner:CYBERSOURCE CORP
System and method for risk detection reporting and infrastructure
InactiveUS8484066B2Efficiently monitor riskFlexibility in modifying and updatingFinanceMemory loss protectionData miningDocumentation
A method, a system, and a device for monitoring risks associated with at least one business process, including: evaluating at least one of a plurality of document instances, wherein each of the document instances includes, in association therewith, a plurality of document values, against a plurality of risk categories; implementing the plurality of risk categories pursuant to at least one acceptable risk policy approved for the at least one business process; and qualifying at least one of the at least one of the plurality of documents pursuant to an approval rating of the at least one document in at least one risk category. The system, method, and device efficiently monitor risk, and allow for flexibility in modifying or updating risk policy.
Owner:SMARTSAFETY SOFTWARE INC
Method and Apparatus for Evaluating Fraud Risk in an Electronic Commerce Transaction
Transaction information is received and applied to multiple fraud risk mathematical models that each produce a respective raw score, which are transformed with respective sigmoidal transform functions to produce optimized likelihood of fraud risk estimates to provide to a merchant. Respective fraud risk estimates are combined using fusion proportions associated with the respective risk estimates, producing a single point risk estimate, which is transformed with a sigmoidal function to produce an optimized single point risk estimate. The sigmoidal functions approximate a relationship between risk estimates produced by fraud risk detection models and a percentage of transactions associated with respective risk estimates; the relationship is represented in terms of real-world distributions of fraudulent and non-fraudulent transaction.
Owner:CYBERSOURCE CORP
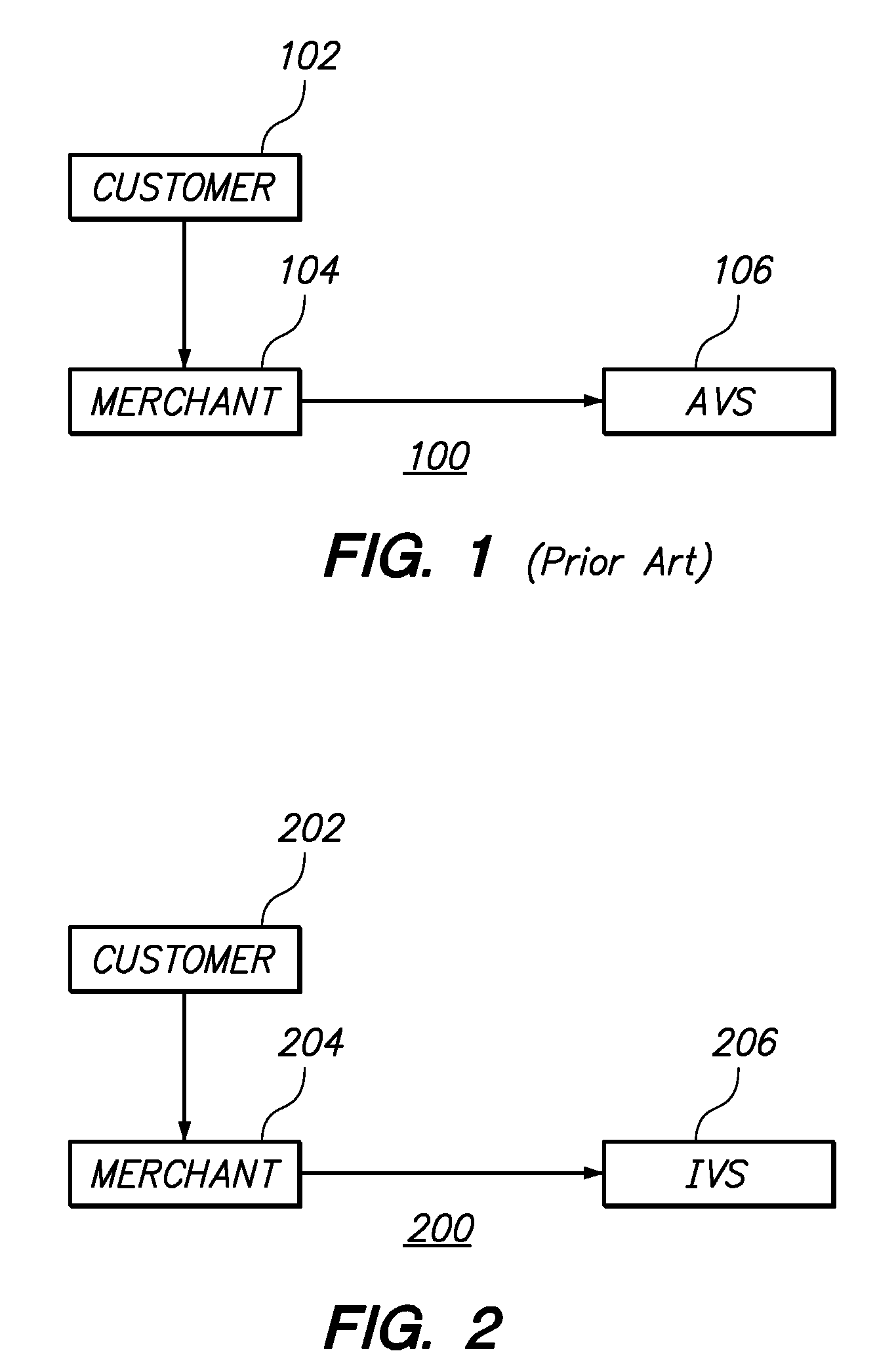
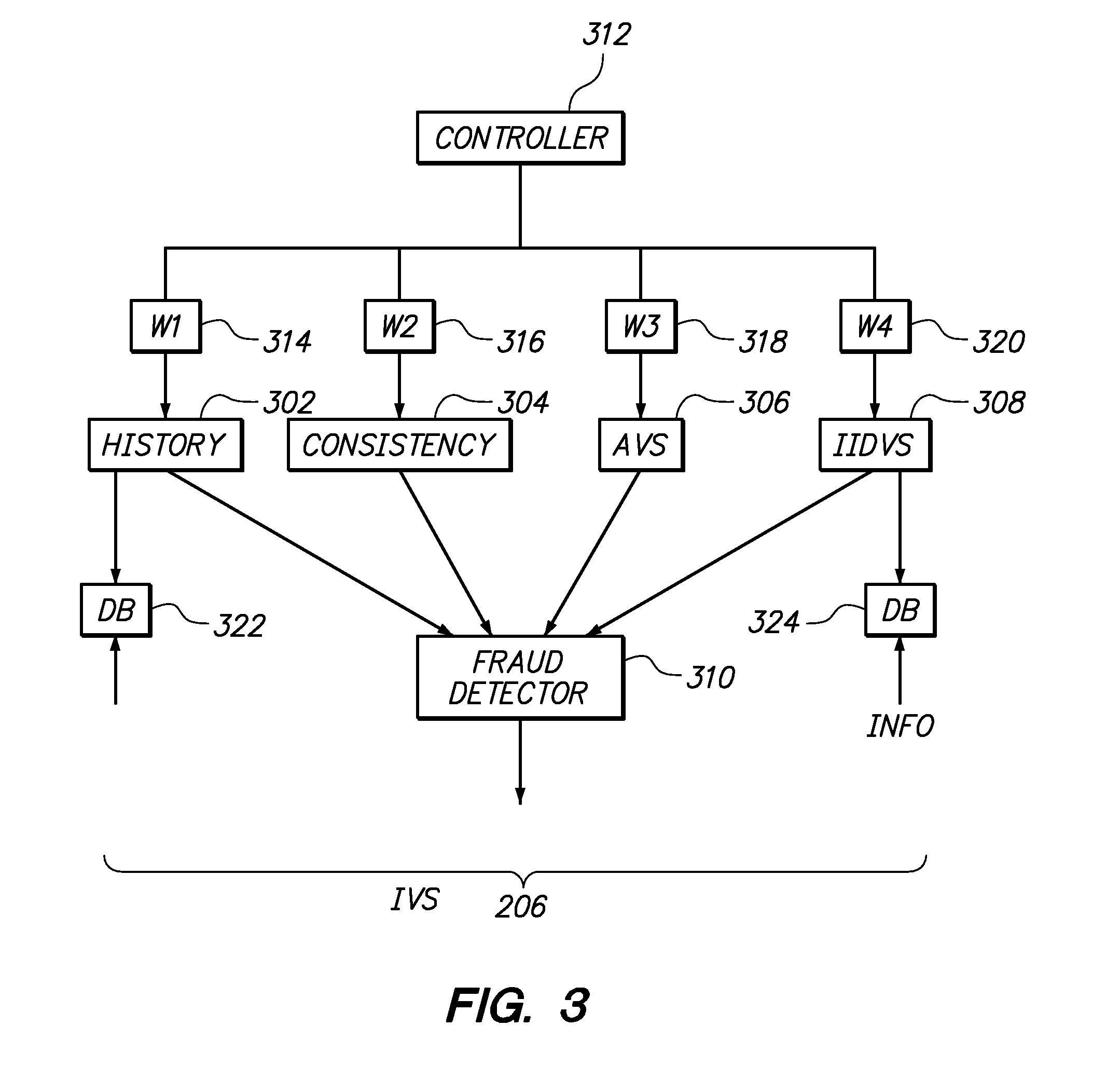
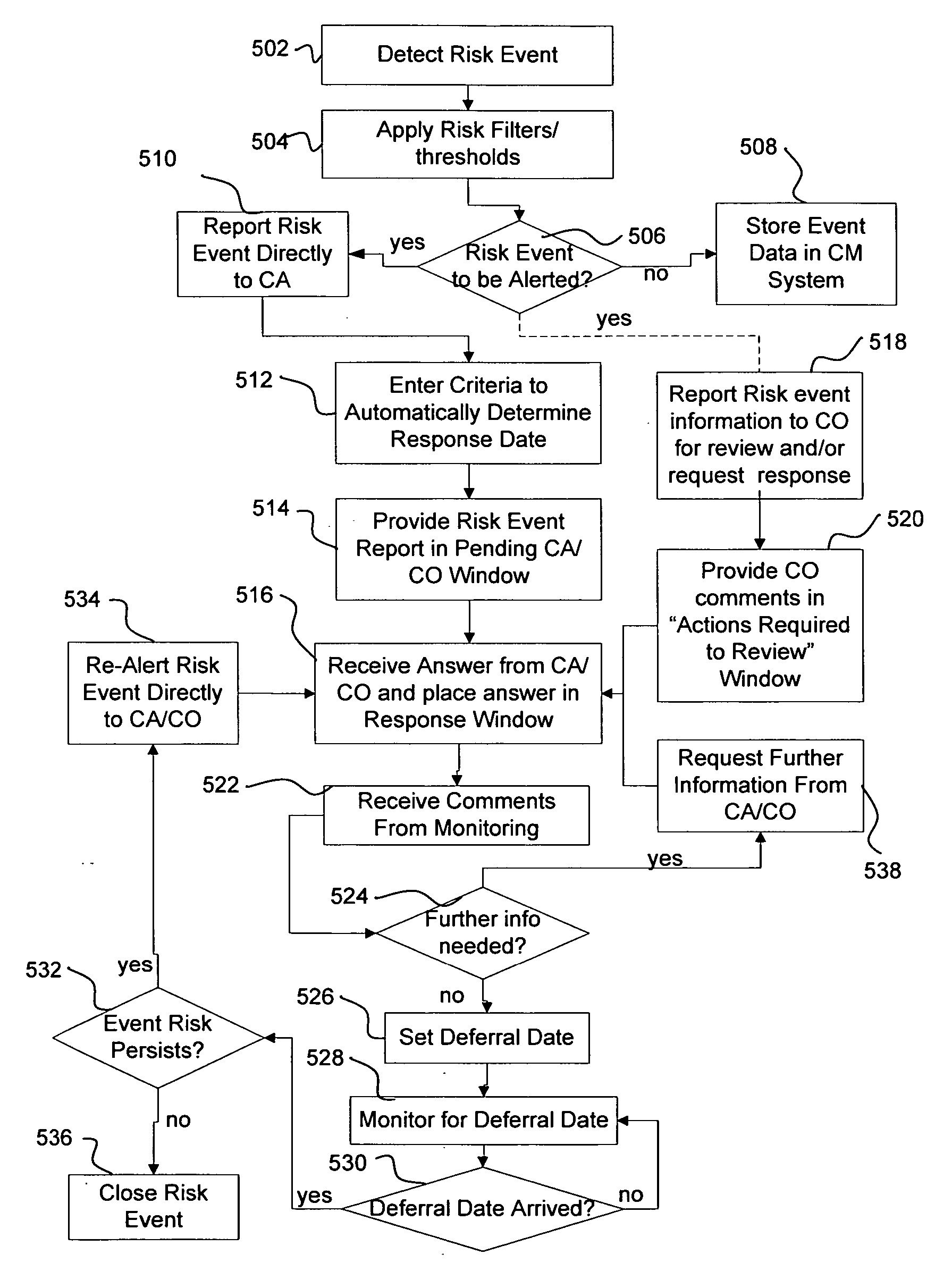
System and method for credit risk detection and monitoring
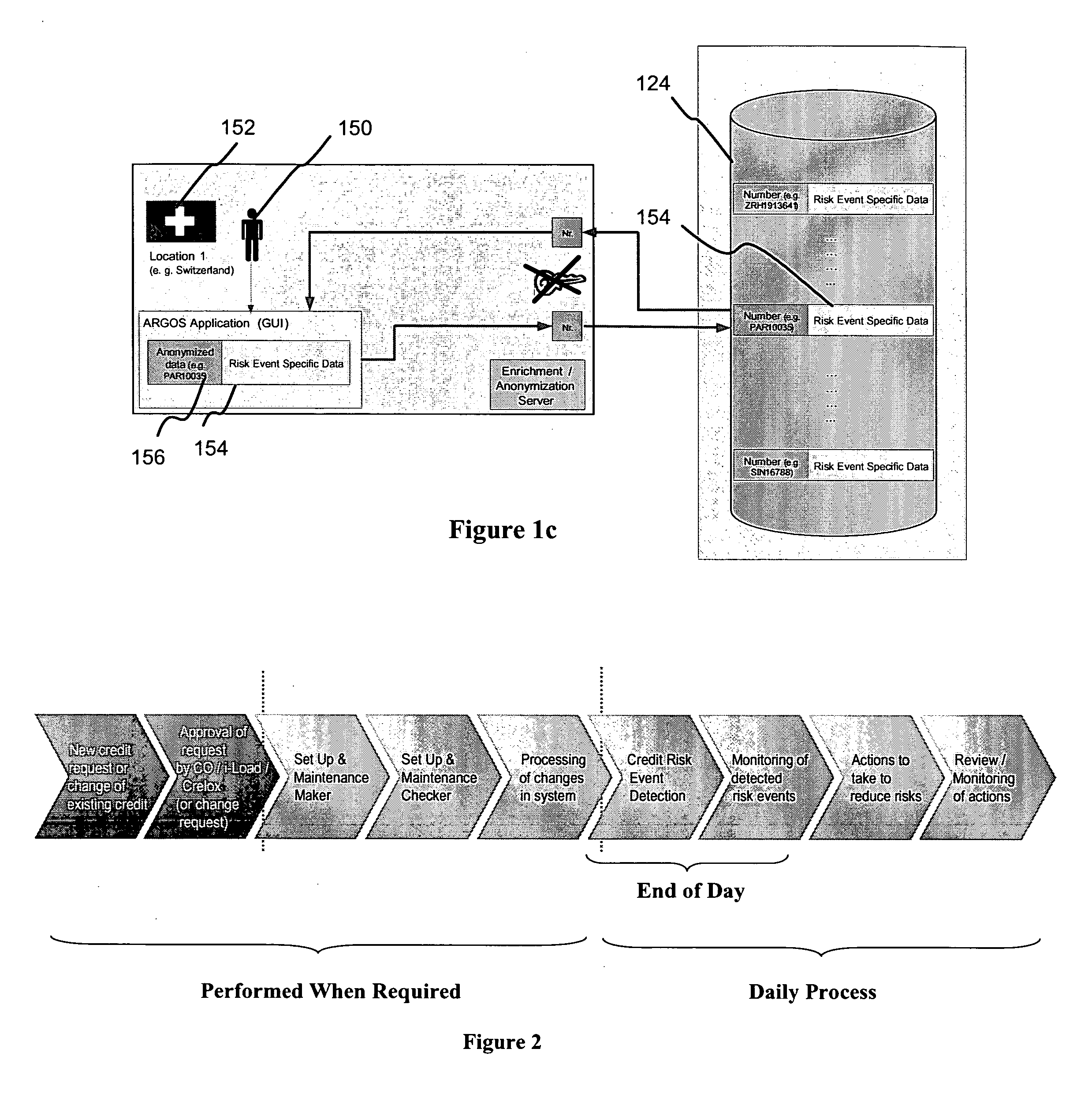
A method for credit risk evaluation includes receiving a set of credit related data associated with a client. Risk events are detected from this set of credit related data according to preset rules, and a set of thresholds and filters is applied to determine whether each detected risk event is to be alerted or not. A risk event qualifying for being alerted can be directly alerted to a client advisor associated with the client. A first answer from the client advisor is received concerning the reported risk event. A response date is set for the alerted risk event. If the risk event persists at the response date, the client advisor is re-alerted as to the risk event according to the set rules.
Owner:UBS AG
Apparatus and method for providing security information on background process
InactiveUS20130055387A1Memory loss protectionError detection/correctionExecution unitBackground process
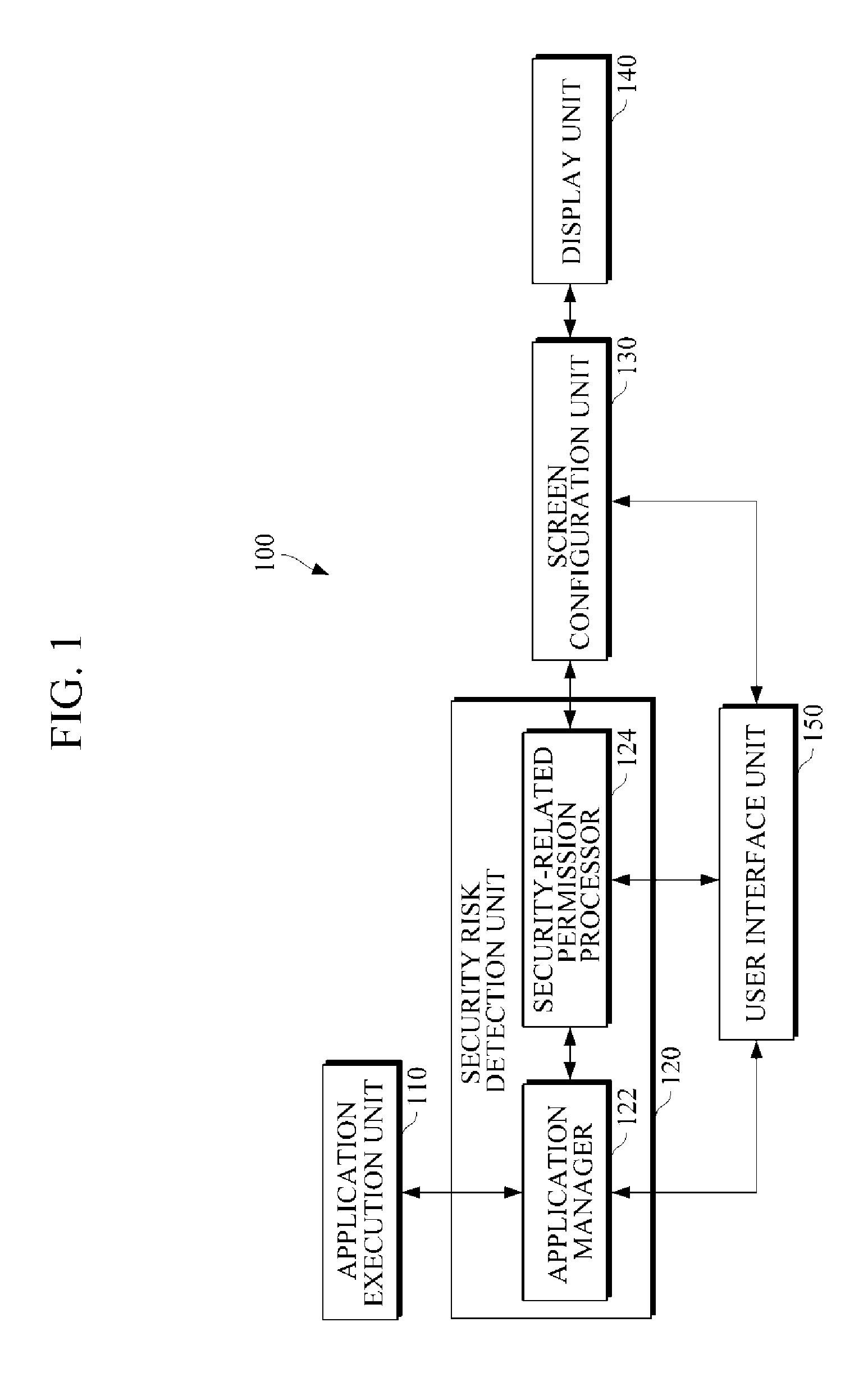
An apparatus and method for providing security information on a background process are provided. The method includes executing an application, detecting an event associated with the execution of the application, identifying a security related permission associated with the application, determining whether the security related permission matches a registered security related permission, determining an application identifier in response to the security related permission matching the registered security related permission, determining whether the event is associated with the background process, and displaying a security risk alert icon based on the detected event. The apparatus includes an application execution unit to execute an application; a security risk detection unit to detect an event associated with a background process of the application; and a screen configuration unit to configure a security risk alert icon to be displayed based on the detected event.
Owner:PANTECH CO LTD
System and method for carrying out safety risk check to computer BIOS firmware
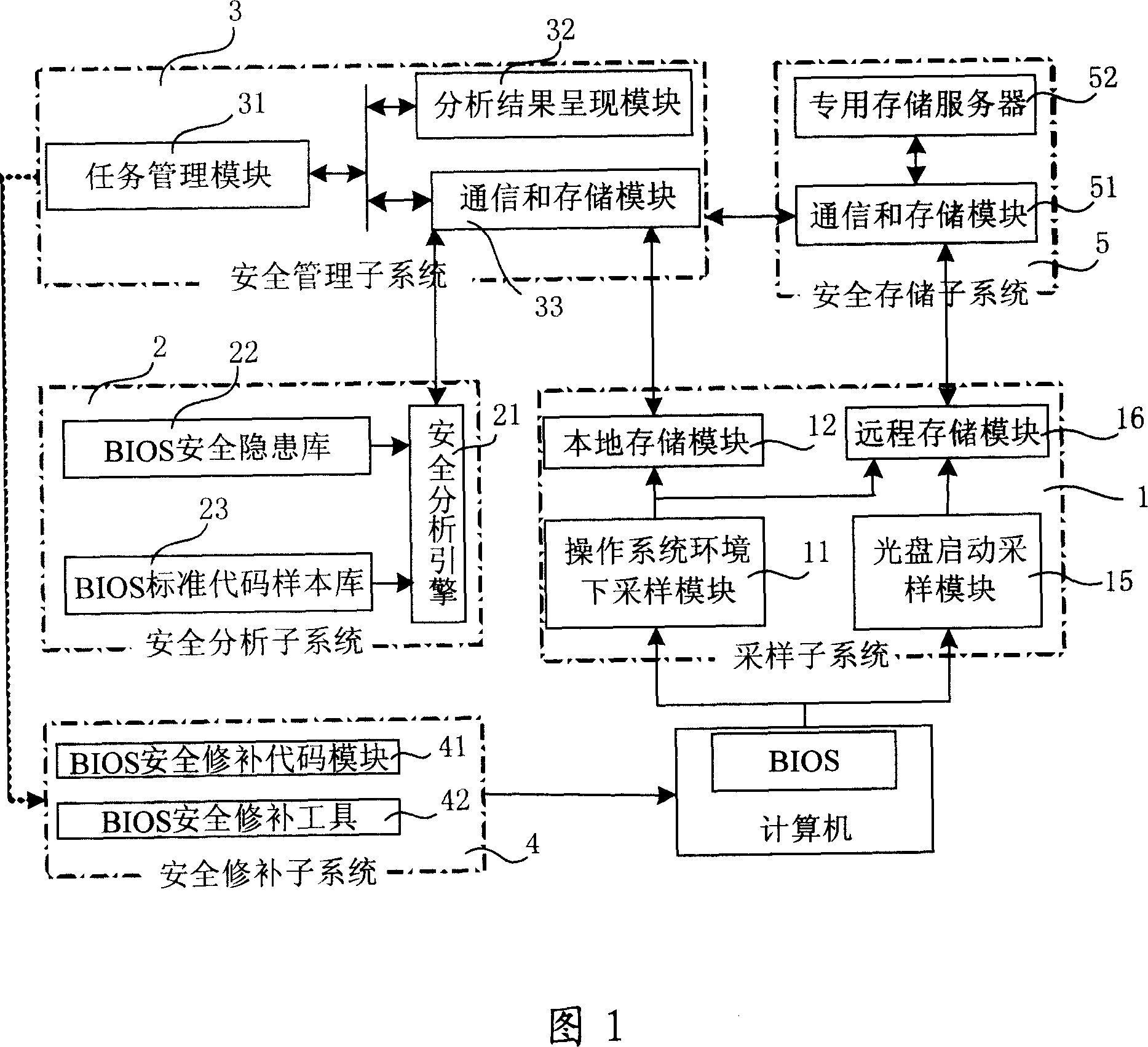
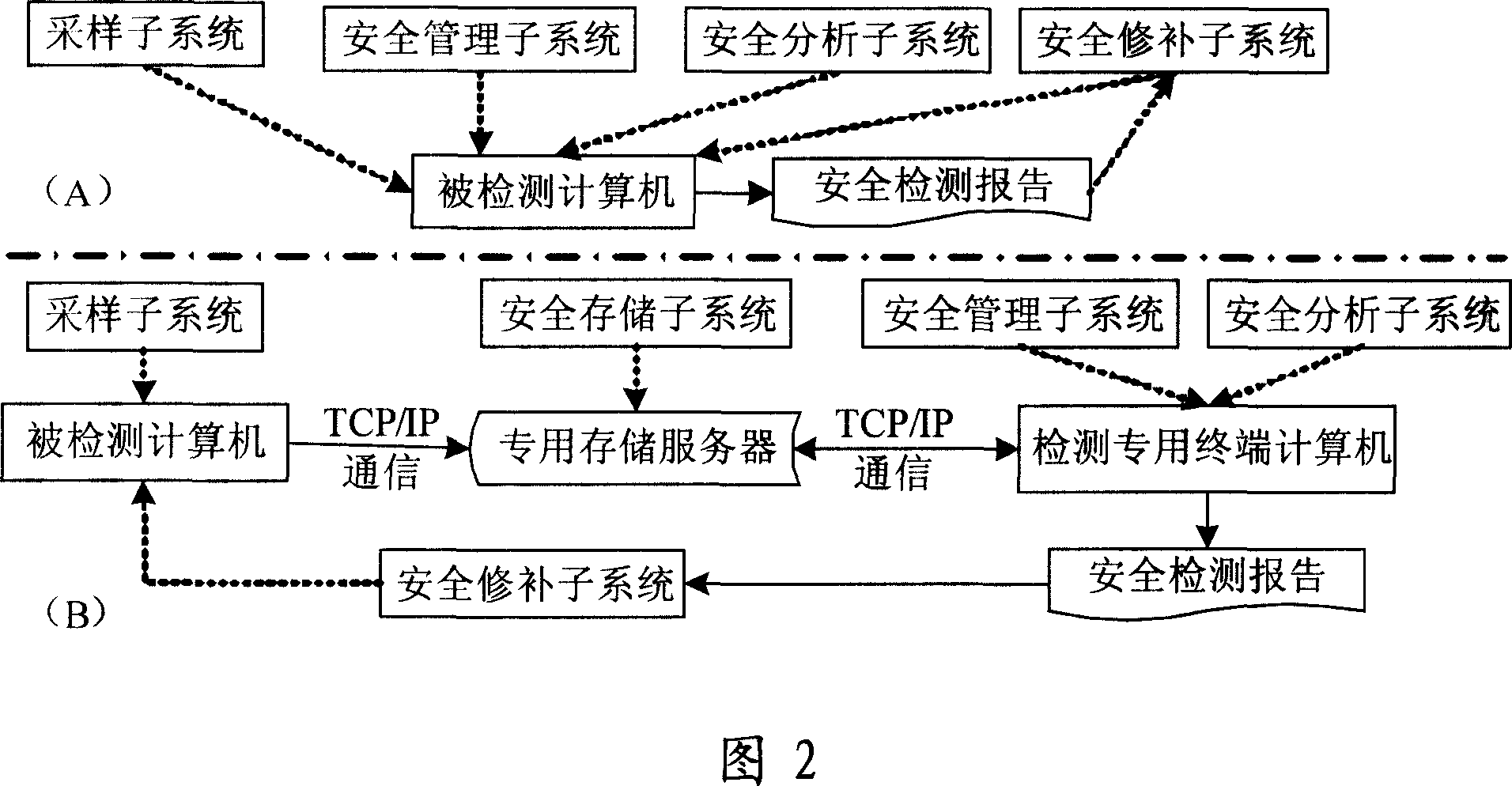
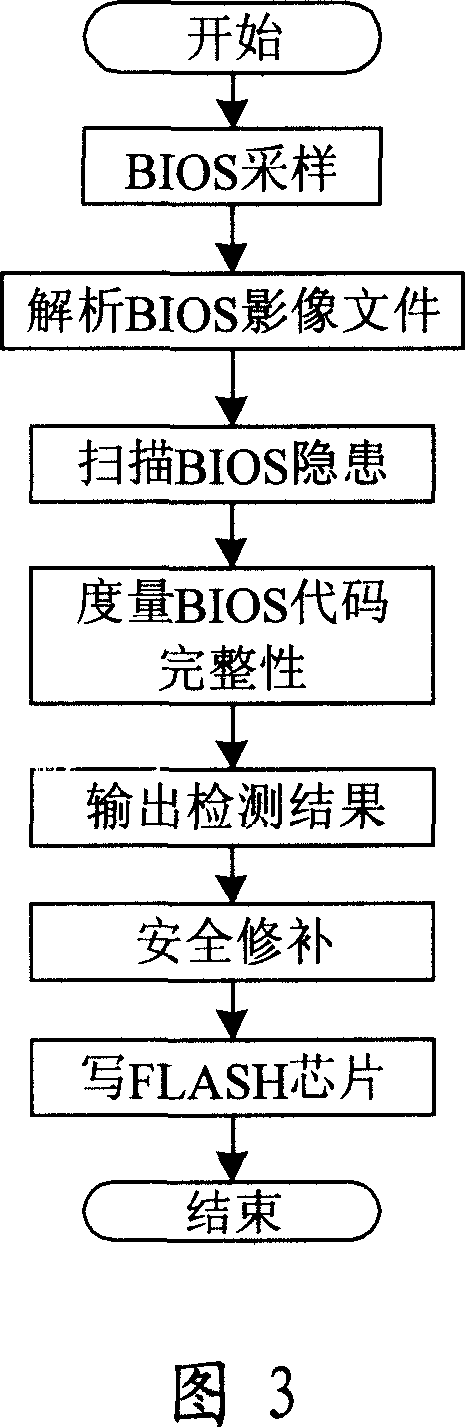
InactiveCN101079003AAvoid lossPrevent crashSoftware testing/debuggingRedundant operation error correctionEngineeringBIOS
The invention discloses a system proceed safe test for computer BIOS firmware and method, which comprises the following steps: initializing; proceeding BIOS sampling; analyzing BIOS image file; scanning various hidden dangers of BIOS; measuring completeness integrity of BIOS code; outputting the testing effect; proceeding safe repair for BIOS. This invention can decrease, reduce and remove safety loophole and hidden danger of computer BIOS, which provides reliable terminal safety prevention and overall protection for computer and network.
Owner:BEIJING JINYUAN LONGMAI INFORMATION TECH
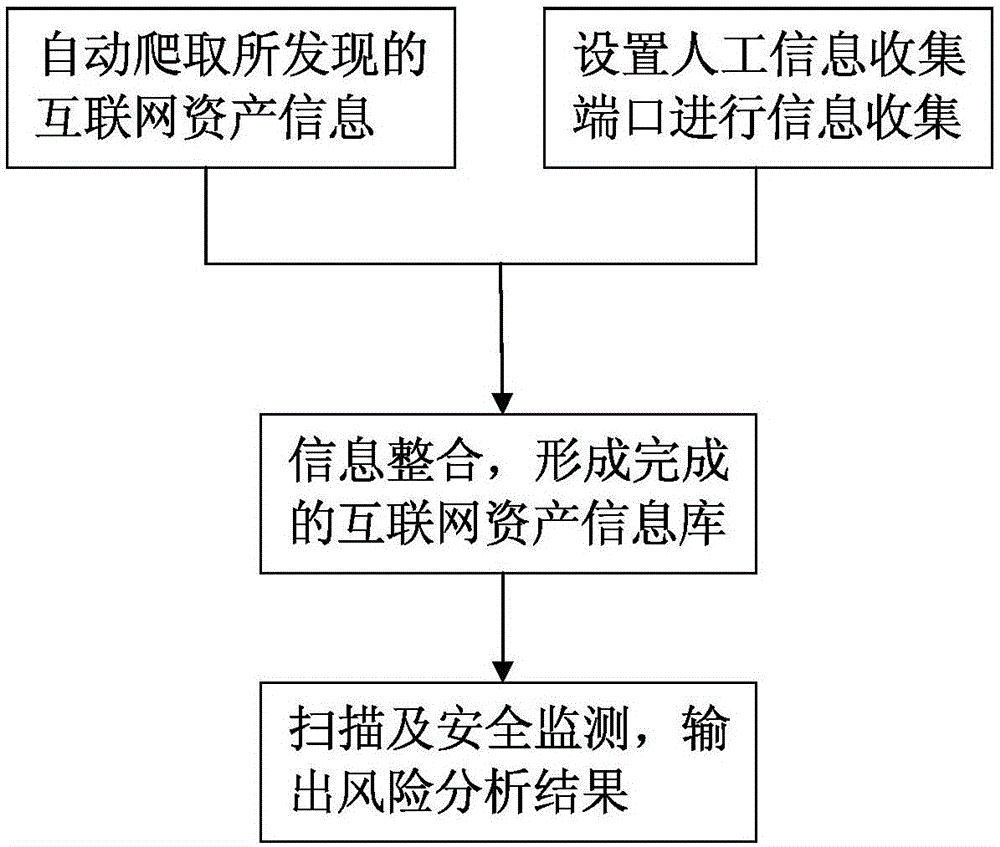
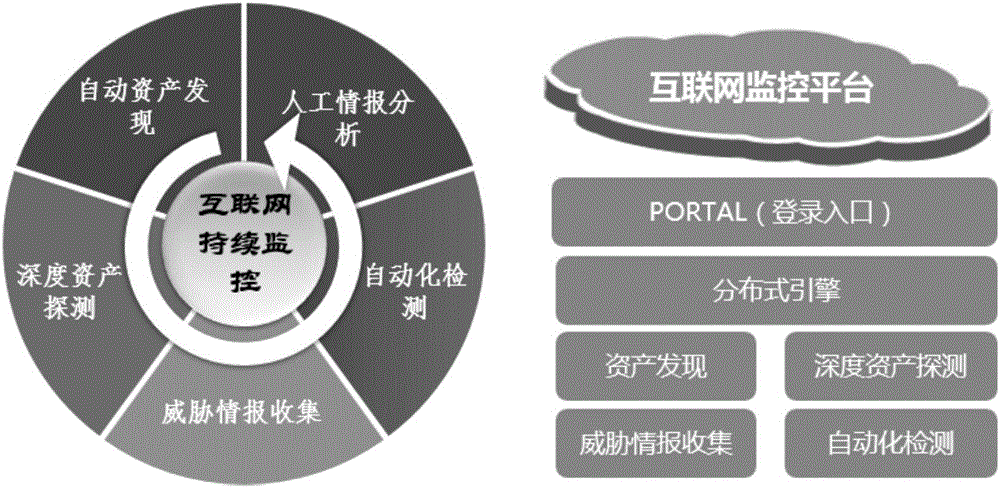
Automatic internet asset monitoring and risk detecting method based on distributed technology
The invention belongs to the technical field of network information security, and relates to an automatic internet asset monitoring and risk detecting method based on a distributed technology. The method comprises the following steps of: discovering and scanning the internet asset exposed at the internet side by utilizing a distributed message queue, analyzing the internet asset information, which is discovered by automatic crawling, by using a crawler technology and a DNS, setting an artificial information collecting port to perform information collection, integrating the automatically crawled information and the artificially collected information, so that a complete internet asset information library is formed, performing scanning and security detection of the internet asset information library, and outputting a risk analysis result. By means of the automatic internet asset monitoring and risk detecting method based on the distributed technology disclosed by the invention, the internet asset can be actively monitored; and the asset risk can be identified.
Owner:深圳市魔方安全科技有限公司
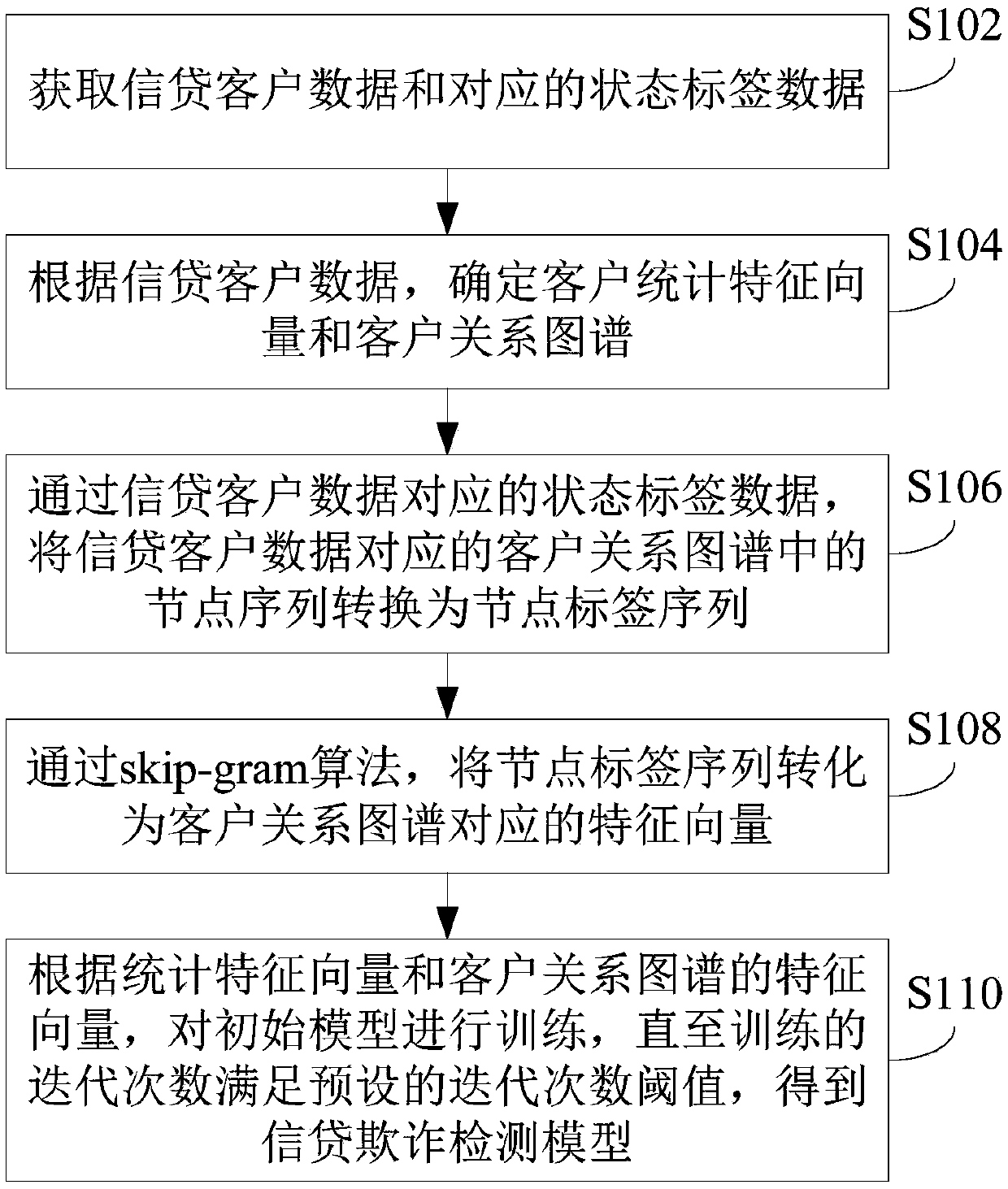
Credit fraud detection method and model training method, device and server thereof
ActiveCN109685647AIdentify fraud risksImprove reliabilityFinanceCharacter and pattern recognitionFeature vectorGram
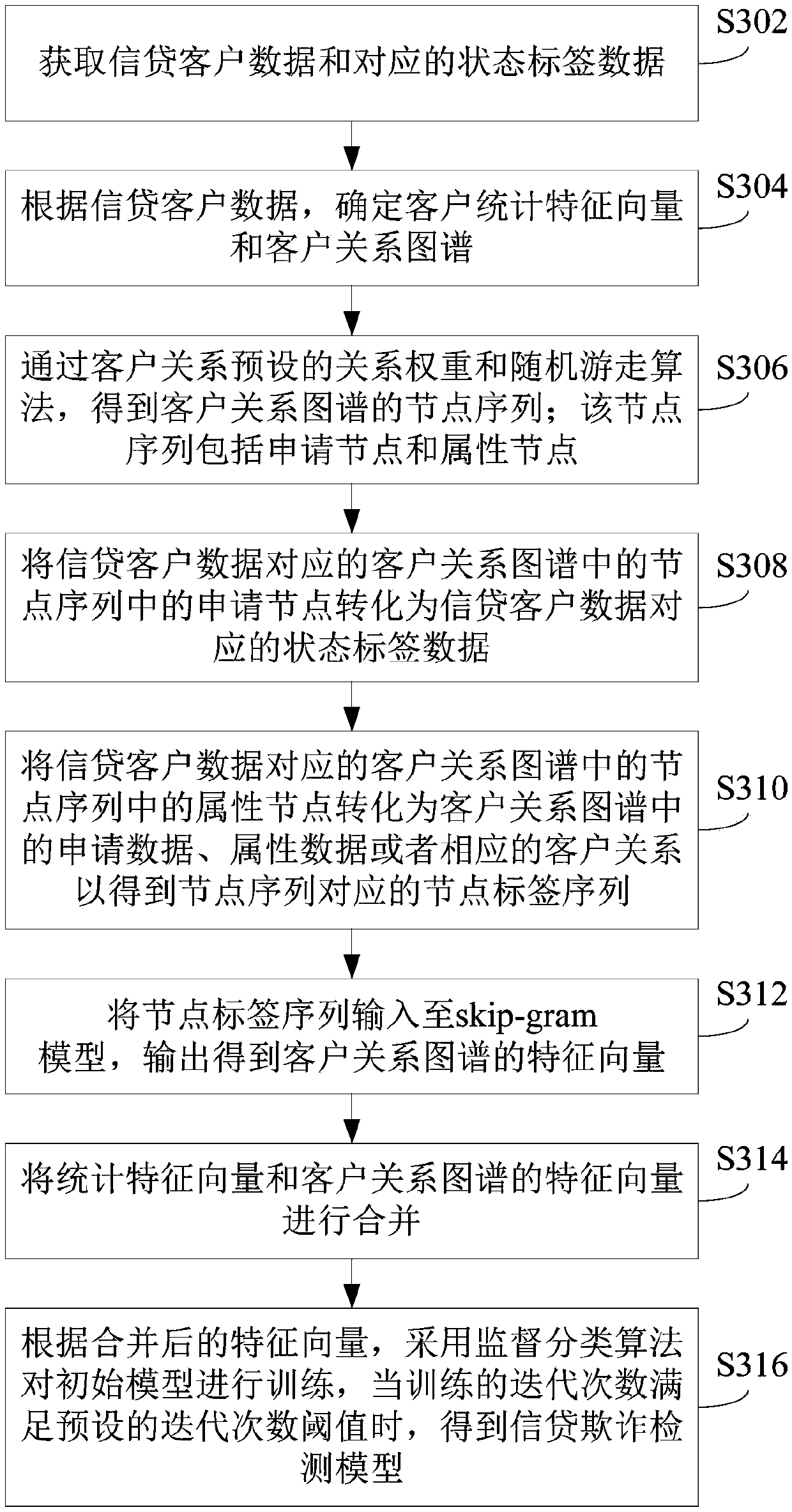
The invention provides a credit fraud detection method, a training method and device of a credit fraud detection model and a server, and the method comprises the steps: determining a client statistical feature vector and a client relation map through the obtained credit client data; Converting the node sequence in the customer relationship map into a node label sequence through the obtained statelabel data corresponding to the credit customer data; using the skip- gram algorithm to convert the node tag sequence into a feature vector corresponding to the customer relationship map; And according to the statistical feature vector and the feature vector of the customer relationship map, training the initial model until the number of iterations of the training meets a preset iteration number threshold, and obtaining a credit fraud detection model. According to the credit fraud detection model obtained by the invention, the relation graph network structure, the label characteristics and thestatistical characteristic vectors are utilized, so that the fraud risk of a client can be better identified, and the reliability of a risk detection result is improved.
Owner:SUNSHINE PROPERTY & CASUALTY INSURANCE CO
Apparatus and method for managing risk based on prediction on social web media
InactiveUS20140172497A1Continuous improvement in performance of systemImprove reliabilityFinanceHardware monitoringManagement unitNetwork media
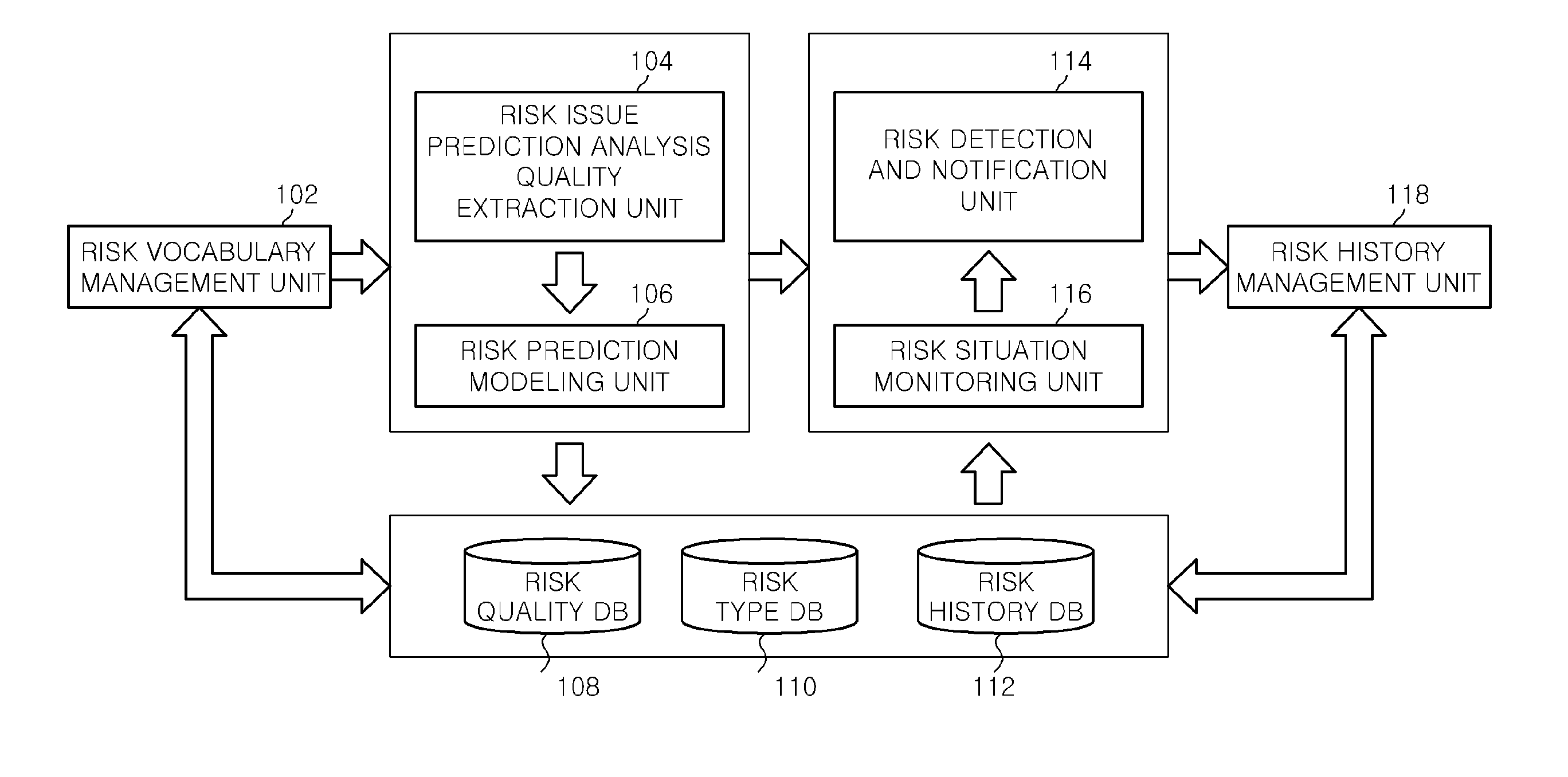
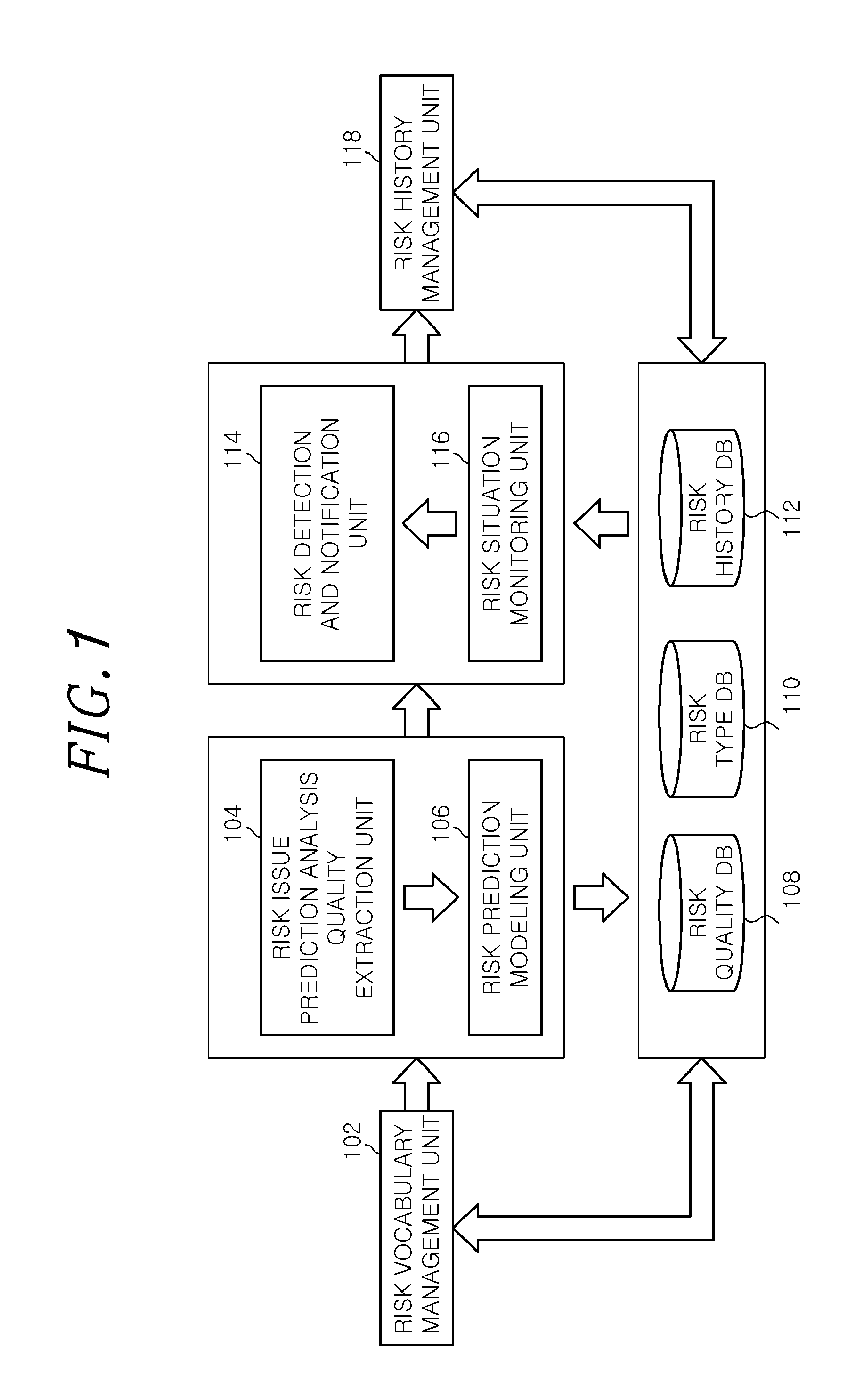
An apparatus for managing risk in social web media in a prediction-based manner is provided, and includes a risk vocabulary management unit, which extracts and manages vocabulary to be managed as pertaining to risk from social web content, a risk issue prediction analysis quality extraction unit, which performs language analysis and sensitivity analysis, a risk prediction modeling unit, which models risk prediction analysis, a risk detection and notification unit, which automatically detects and notifies the risk, a risk situation monitoring unit, which monitors in real time a risk state of a risk entity when an alarm is raised with respect to the detected risk, and a risk history management unit, which receives user feedback for monitored risk information and manages a record of a terminated risk situation.
Owner:ELECTRONICS & TELECOMM RES INST
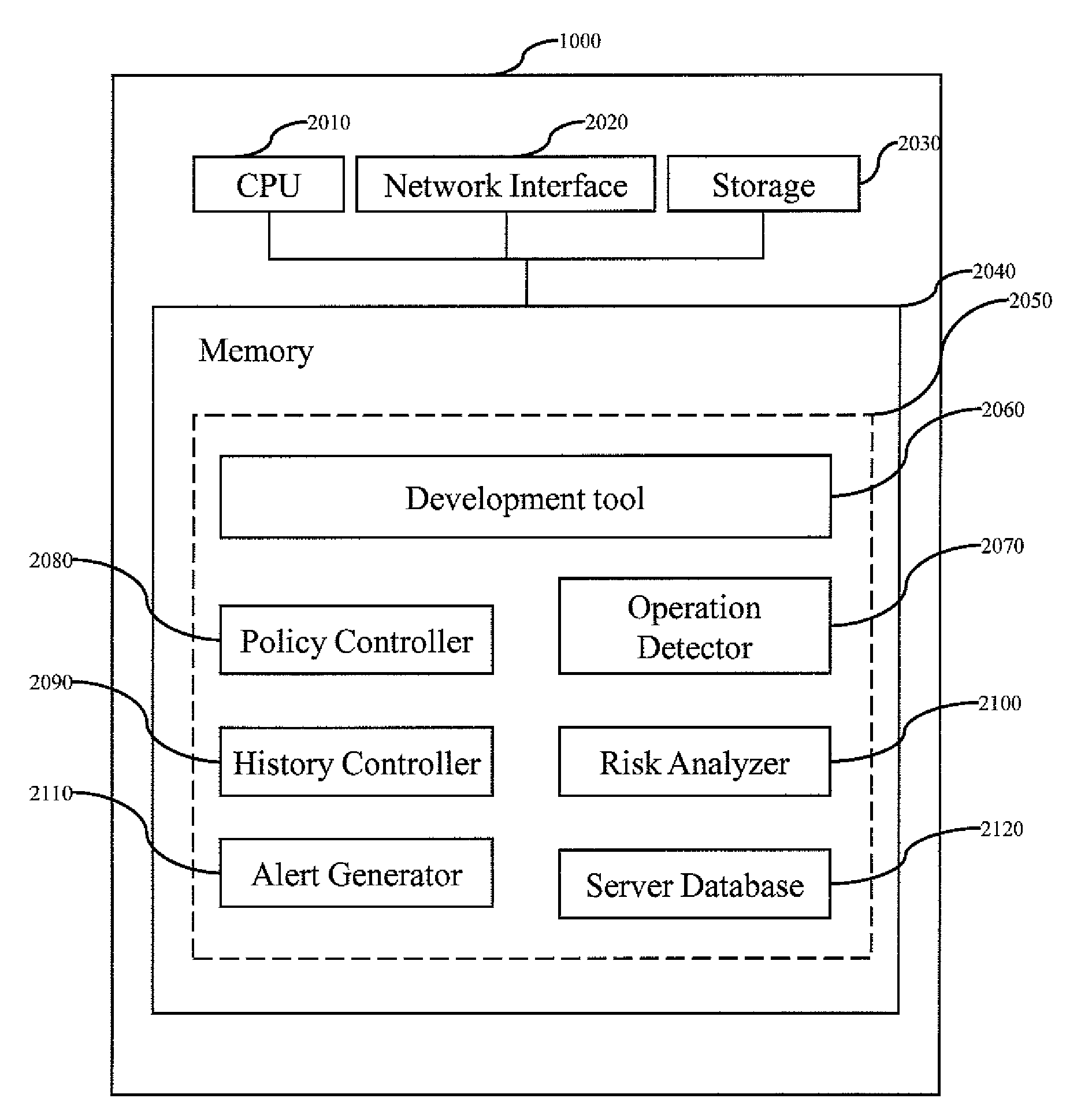
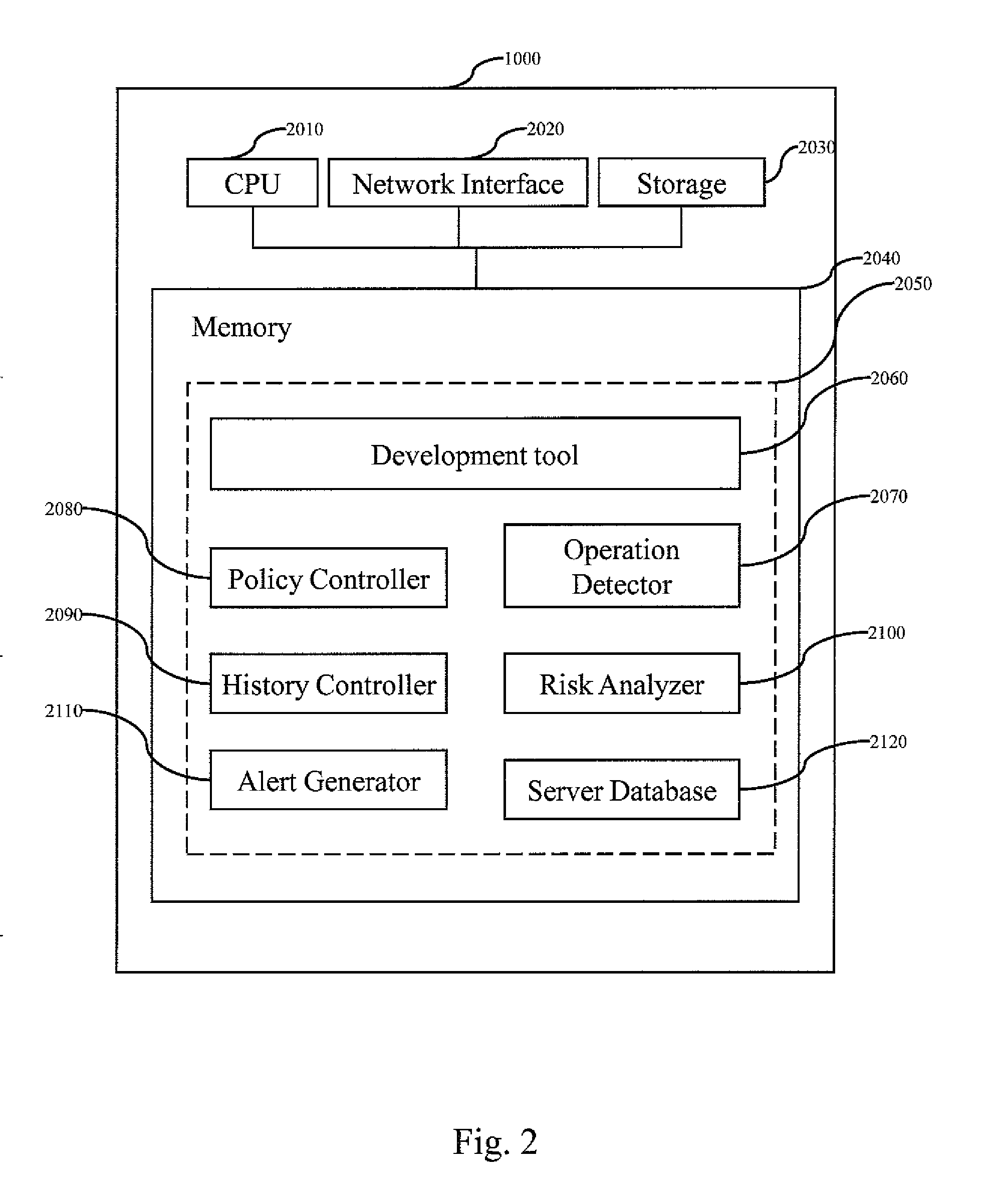
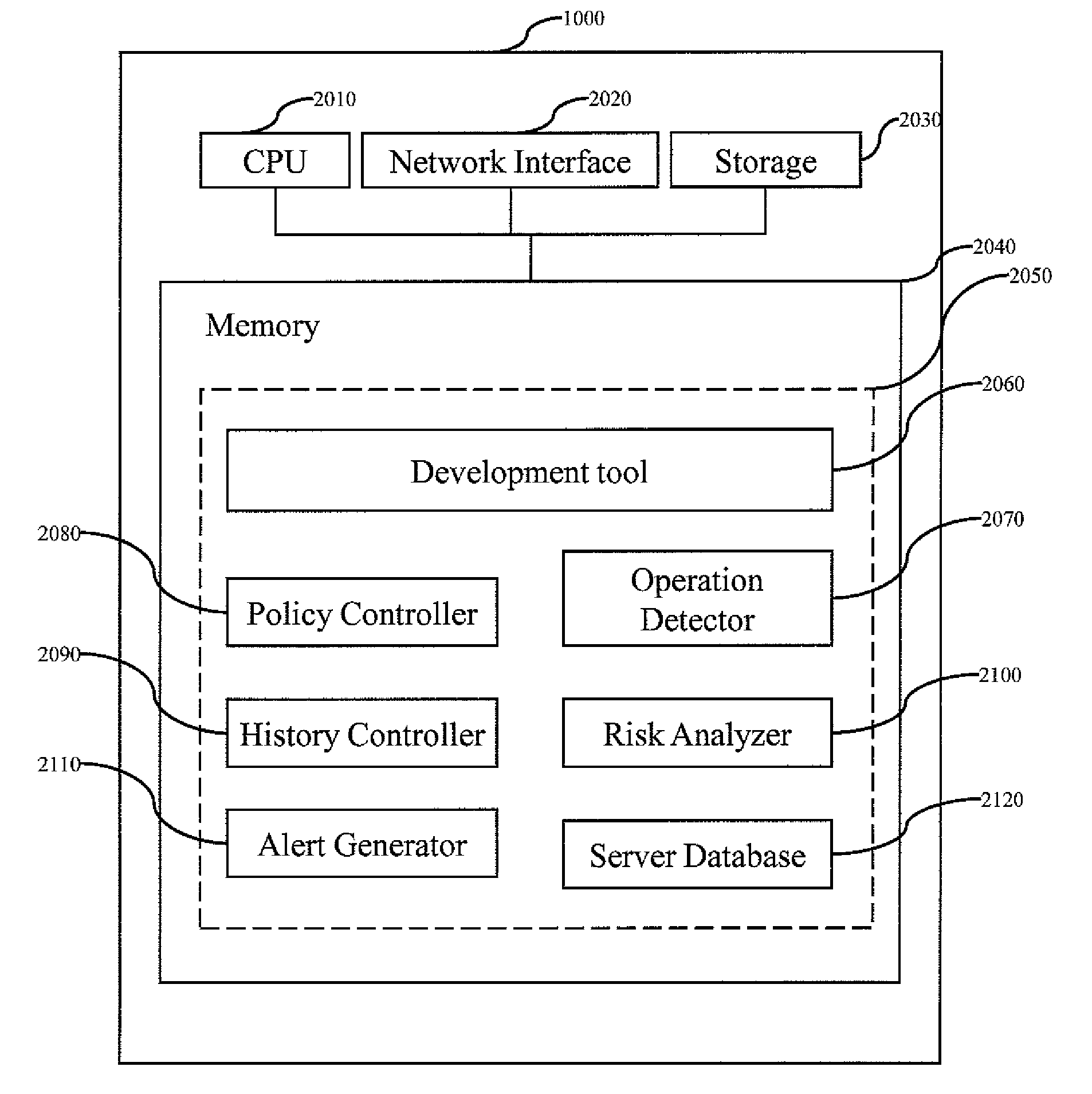
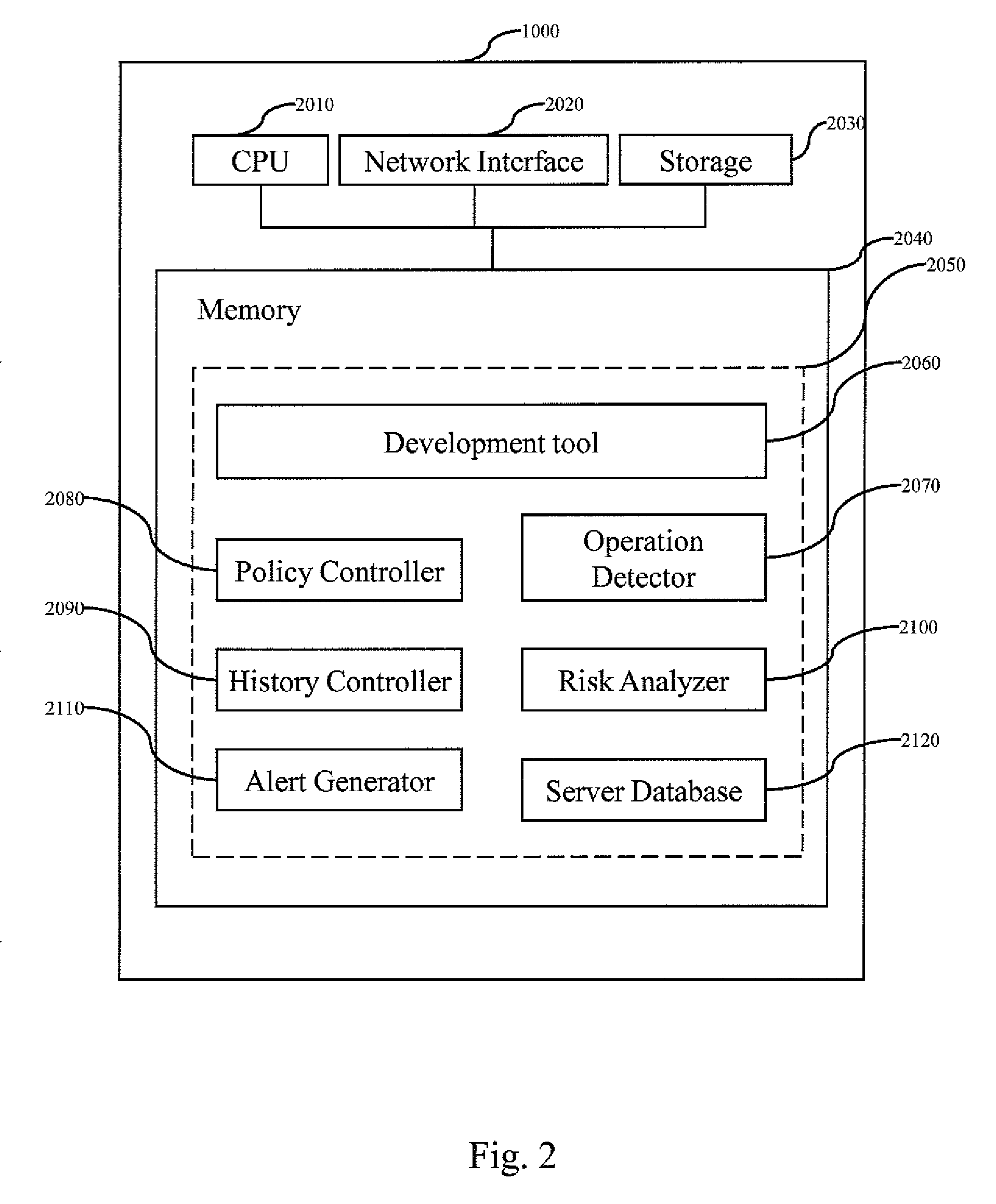
Method for source-related risk detection and alert generation
InactiveUS20100095277A1Burdensome and costlyProcess be accelerated and easilyVersion controlSpecific program execution arrangementsComputer scienceRisk detection
A method and system for detecting a source-related risk and generating an alert concerning the source-related risk are disclosed. Criteria of the source-related risk are defined. Thresholds associated with the source-related risk are defined. Every operation on an object is detected. If an operation on an object satisfies a criterion among the criteria or if the operation causes to exceed a threshold among the thresholds, an alert is generated for the operation.
Owner:SERVICENOW INC
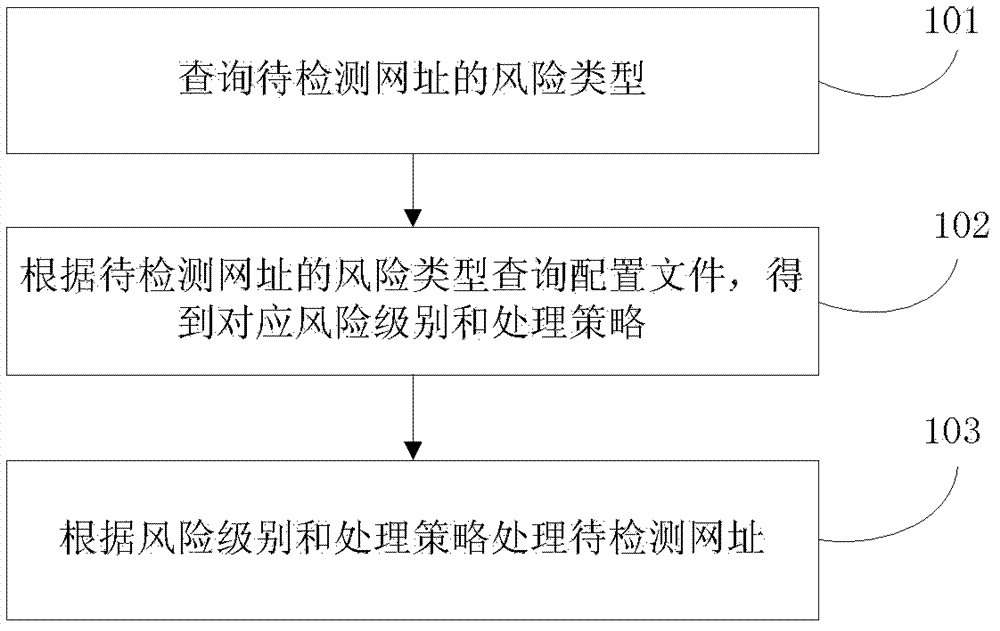
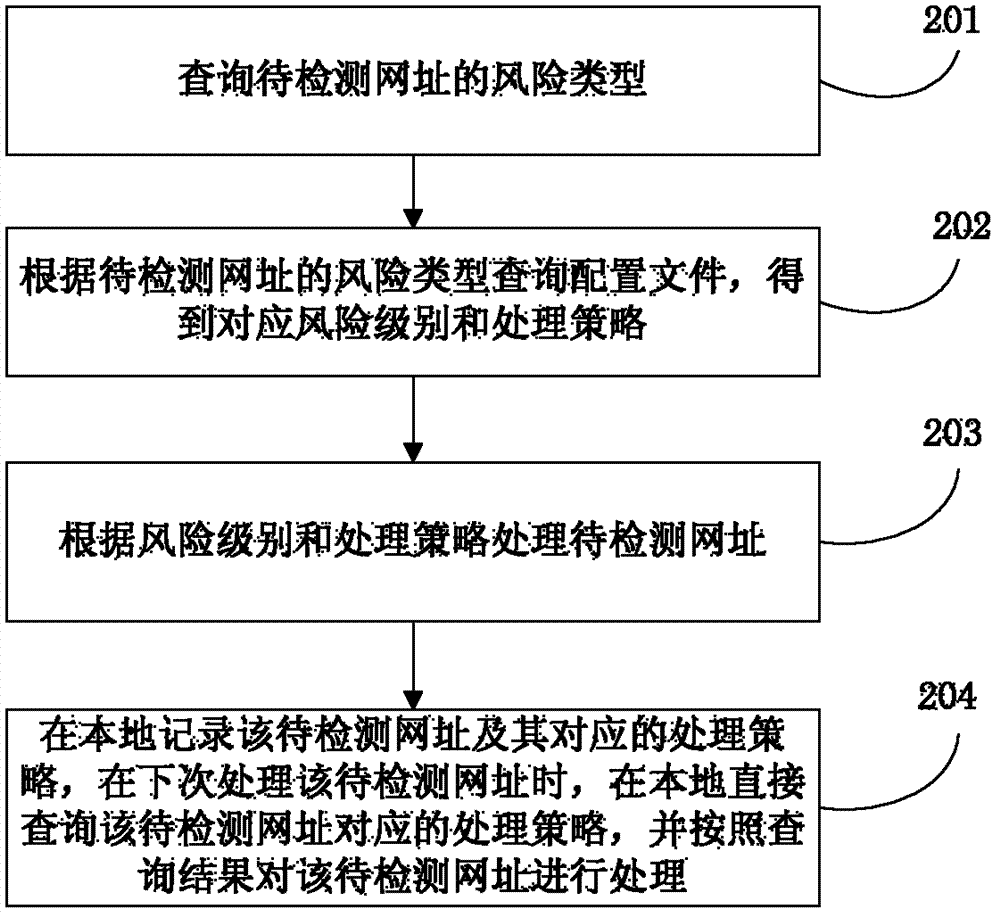
Website risk detection processing method and website risk detection processing device
InactiveCN103092832ARobustReduce the burden onDigital data information retrievalPlatform integrity maintainanceRisk levelInternet privacy
The invention discloses a website risk detection processing method and a website risk detection processing device and belongs to the technical field of computers. The website risk detection processing method includes inquiring a risk type of a website to be detected; inquiring a configuration file according to the risk type of the website to obtain a risk level and a processing strategy correspondingly; and processing the website to be detected according to the risk level and the processing strategy. The corresponding processing strategy can be obtained by determining the risk level according to the risk type of the website to be detected; and different types of the websites are processed according to the different risk levels and the protecting strategies, and accordingly, processing is diversified when the risky websites are intercepted. Further, when the risk types are determined, data in a risk database established in advance are matched to obtain the risk types of the websites to be detected, binding of a website risk monitoring component is omitted, and codes are short, simple and high in robustness.
Owner:TENCENT TECH (SHENZHEN) CO LTD
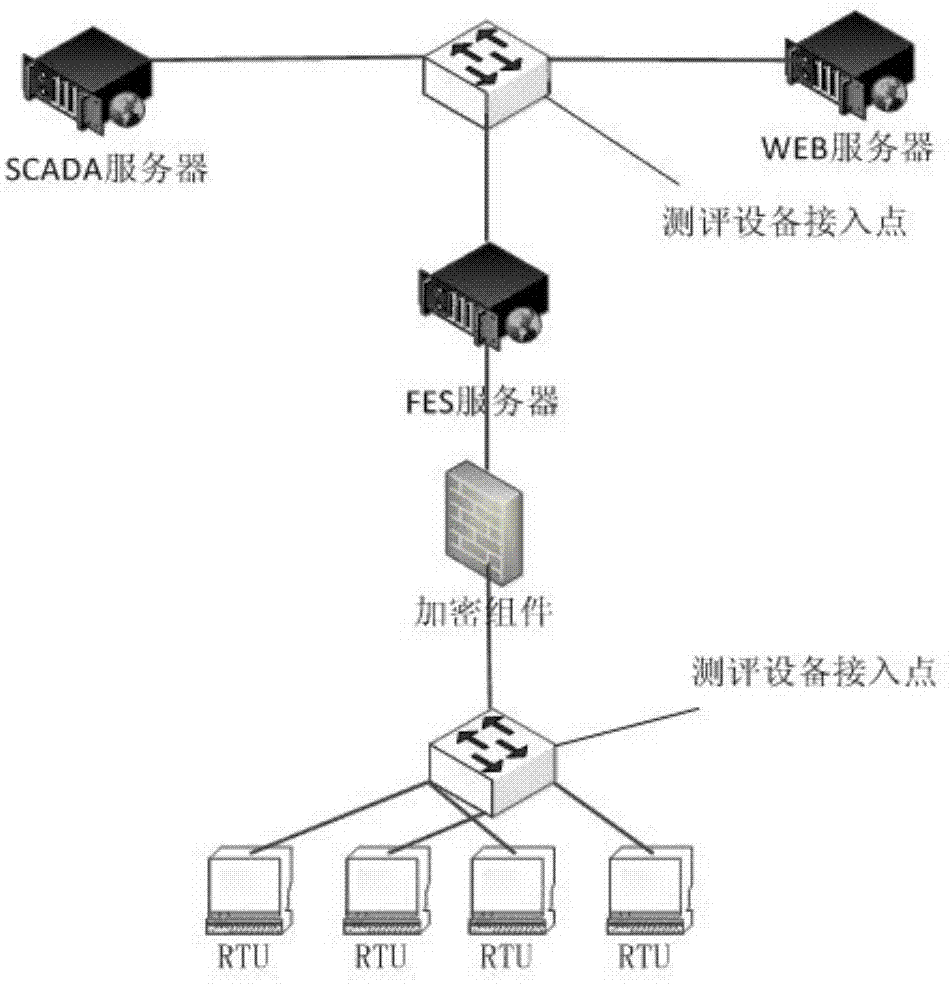
Fast detection method for potential safety hazards of power distribution automation system information
InactiveCN103903187AAchieving Simultaneous DetectionReduce investmentData processing applicationsTransmissionMaster stationAdvanced Distribution Automation
The invention relates to a fast detection method for potential safety hazards of power distribution automation system information. The fast detection method comprises the steps of master station configuration of a power distribution automation system, encryption module configuration, terminal configuration of the power distribution automation system, corresponding testing and evaluating tool selection according to testing and evaluating objects, security risk assessment of the power distribution automation system information, and termination after all the potential safety hazards are solved. According to the fast detection method, all the functions of the power distribution automation system can be simulated, a plurality of power distribution terminals can be detected at the same time, the automation degree in the testing and evaluating process is high, the investment of personnel and equipment in the testing and evaluating process can be effectively reduced, potential safety hazard checking equipment can be selected selectively, and comprehensive safety risk detection of the system can be achieved.
Owner:STATE GRID CORP OF CHINA +1
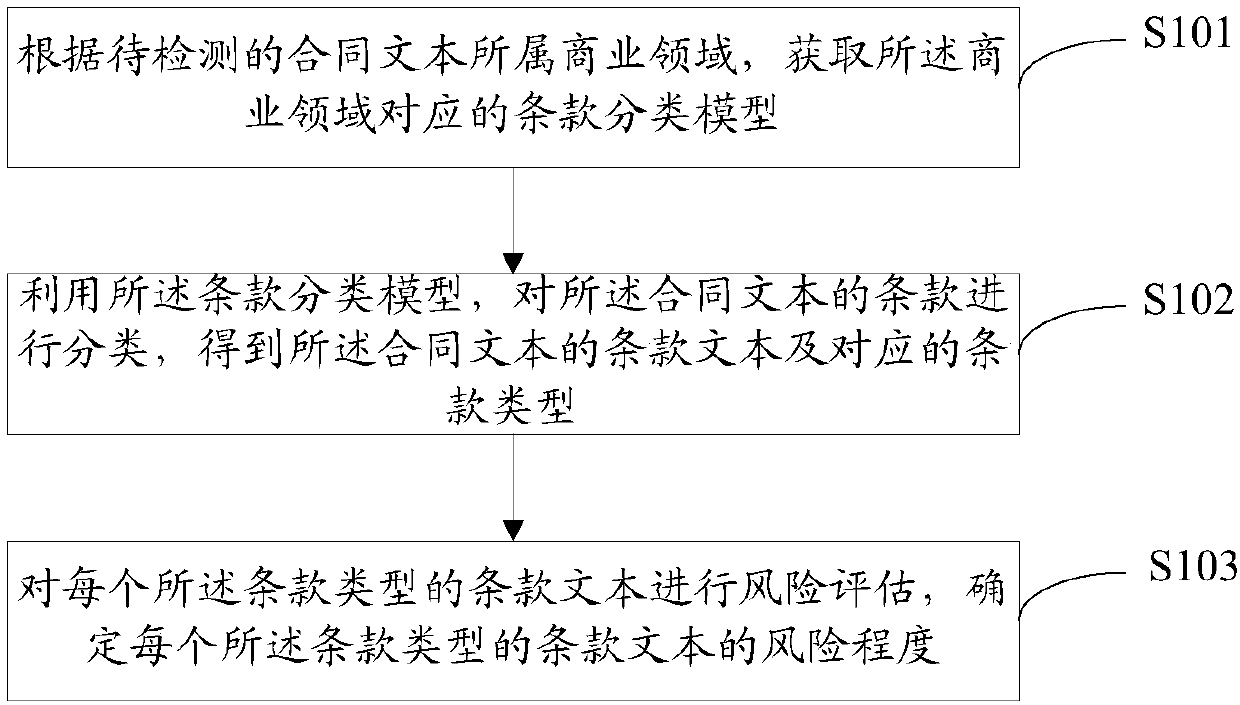
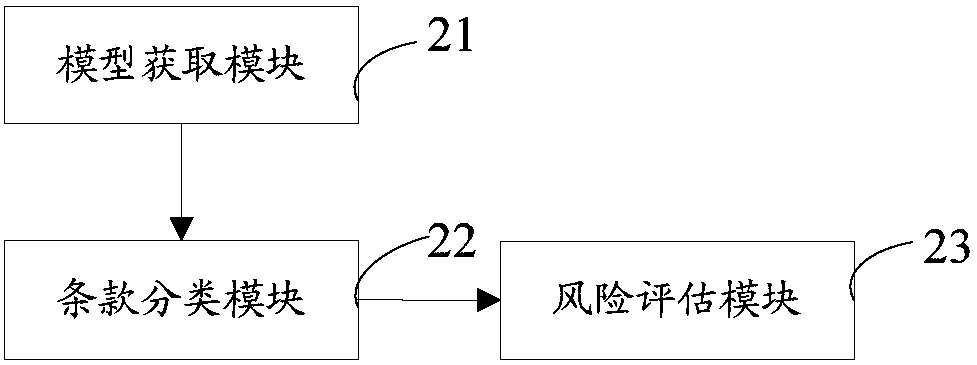
Contract text risk detection method, device and equipment and storage medium
PendingCN109918635AImprove accuracyRealize risk detectionResourcesSpecial data processing applicationsSemantic matchingData mining
The invention discloses a contract text risk detection method, device and equipment and a storage medium, and relates to the fields of natural language processing, semantic calculation and the like, the method comprises the following steps: obtaining a clause classification model corresponding to a business field according to the business field to which a contract text to be detected belongs; using the clause classification model to classify clauses of the contract text to obtain the clause text of the contract text and a corresponding clause type; performing risk assessment on the clause textof each clause type, and determining the risk degree of the clause text of each clause type. According to the embodiment of the invention, the risk detection of the to-be-detected contract text is realized through the classification module and the deep semantic matching model which are obtained through training based on a large number of contract texts, risk reminding is carried out on a client,specific words or phrases and manual setting rules are not needed, and the contract text analysis and risk judgment accuracy is improved.
Owner:ZTE CORP
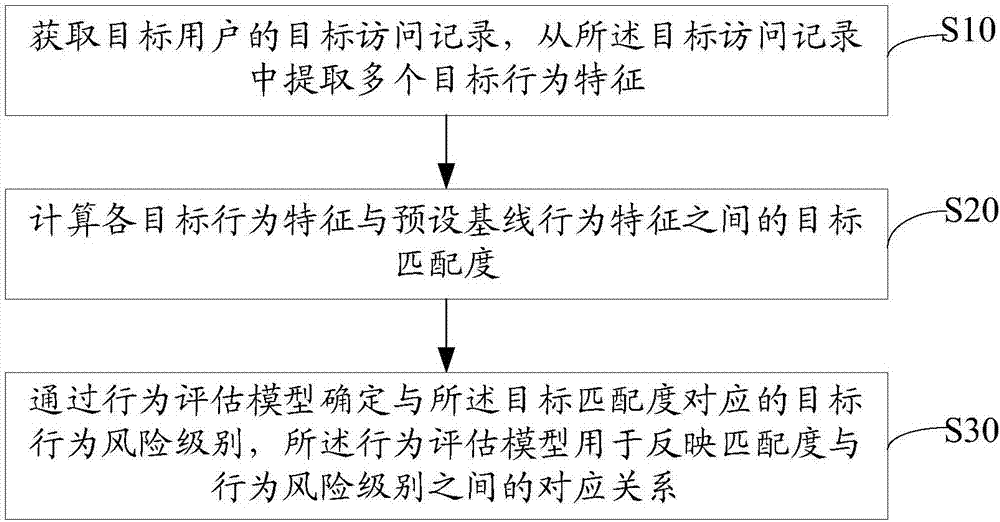
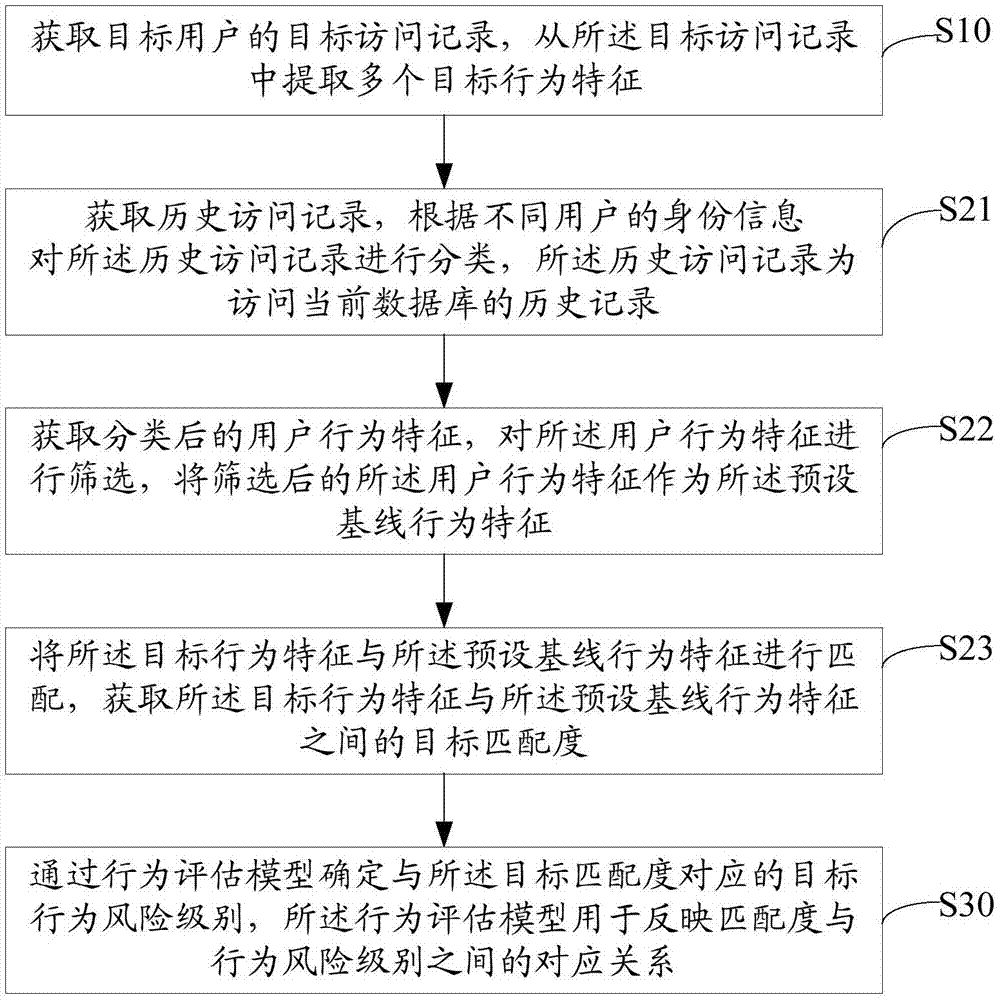
Method for detecting database risk, server and storage medium
The invention discloses a method for detecting a database risk, a server and a storage medium. The method comprises the steps of obtaining a target access record of a target user; extracting multipletarget behavior characteristics from the target access record; calculating a target matching degree between each target behavior characteristic and a preset baseline behavior characteristic; determining a target behavior risk level corresponding to the target matching degree through a behavior estimation model, wherein the behavior estimation model is used for reflecting a corresponding relationship between the matching degree and the behavior risk level. Based on the preset baseline behavior characteristic, the method for detecting the database risk can detect external attacks and internal threats, also can detect variable attacks efficiently without updating the database repeatedly and in real time, avoids data leakage caused by risky behavior of internal personnel, can detect threatening access to the database more comprehensively, can protect the database more efficiently, improves the database risk detection efficiency and accuracy and improves the database security.
Owner:SANGFOR TECH INC
Method for source-related risk detection and alert generation
InactiveUS8171458B2Version controlSpecific program execution arrangementsComputer scienceRisk detection
A method and system for detecting a source-related risk and generating an alert concerning the source-related risk are disclosed. Criteria of the source-related risk are defined. Thresholds associated with the source-related risk are defined. Every operation on an object is detected. If an operation on an object satisfies a criterion among the criteria or if the operation causes to exceed a threshold among the thresholds, an alert is generated for the operation.
Owner:SERVICENOW INC
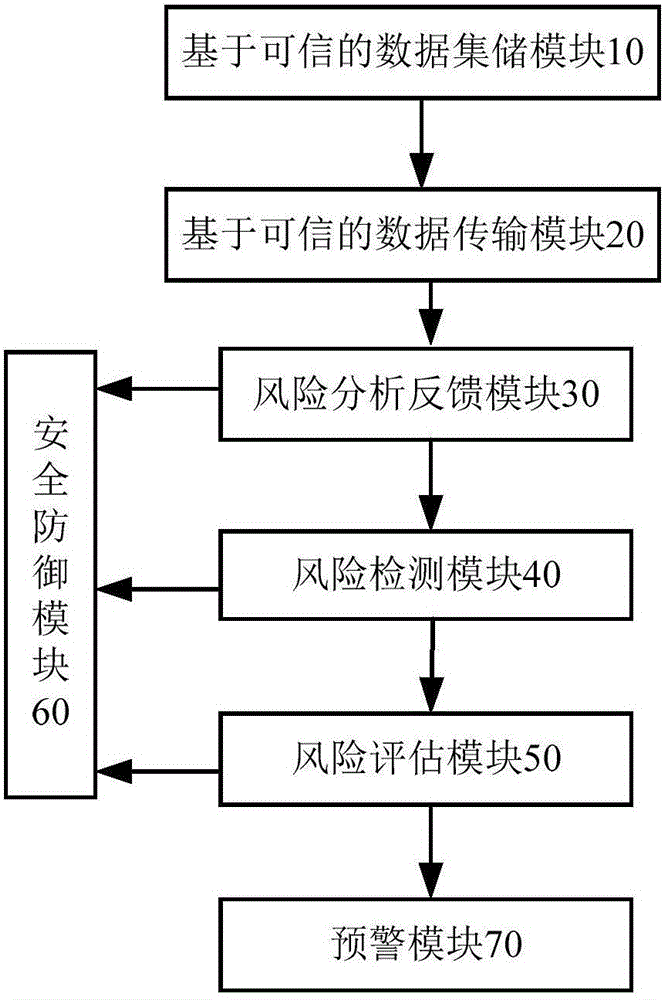
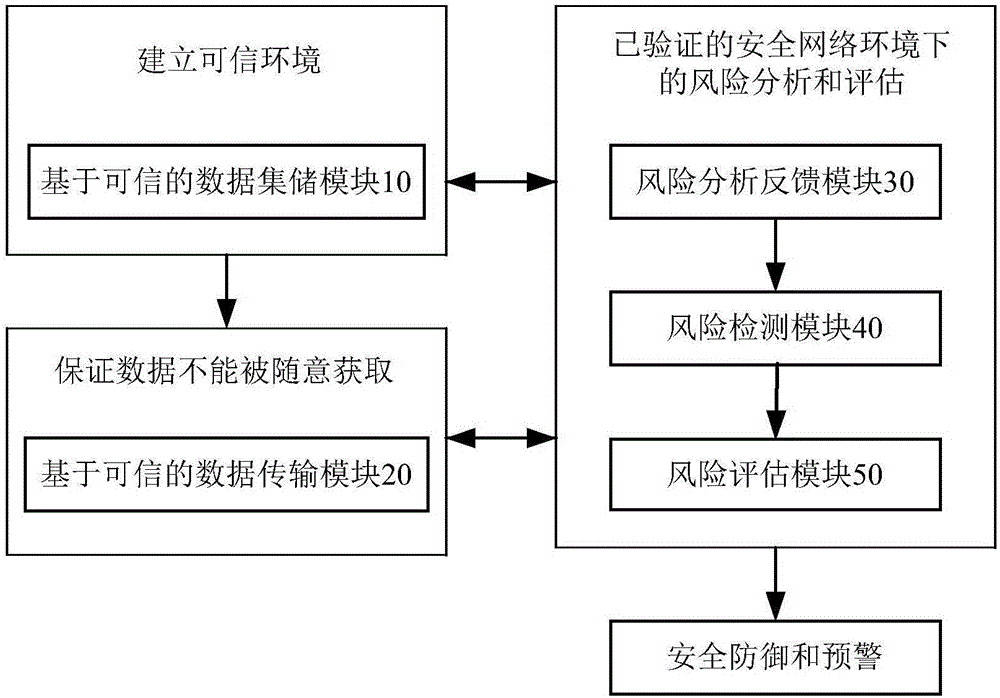
Big data and trusted computing based information network security self-defense system
ActiveCN106209817AGuaranteed storage securityGuaranteed transmission securityTransmissionData setRisk profiling
The invention discloses a big data and trusted computing based information network security self-defense system. The big data and trusted computing based information network security self-defense system comprises a trusted computing based data set storage module, a trusted computing based data transmission module, a risk analysis feedback module, a risk detection module, a risk assessment module, a security defense module and an early warning module. Through brand-new modular combination and an innovative algorithm, the big data analysis and trusted computing technologies are successfully applied to the information network security self-defense system. Starting from the trusted computing based data set storage module and the trusted computing based data transmission module, data assessed by the risk assessment module are trustable; the risk assessment module performs assessment in an authorized secure network environment; a security policy is established on the trusted data and the trusted assessment system; the final behavior is in line with expected design; and the information network defense capability and system credibility are further improved efficiently.
Owner:广东新世立种子技术有限公司
Real-time active detecting and passive monitoring integrated system and method for hidden disasters of mine
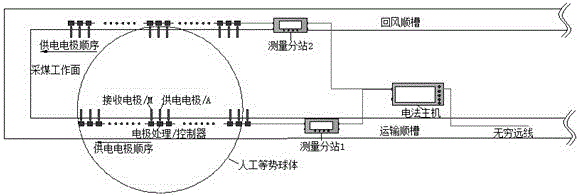
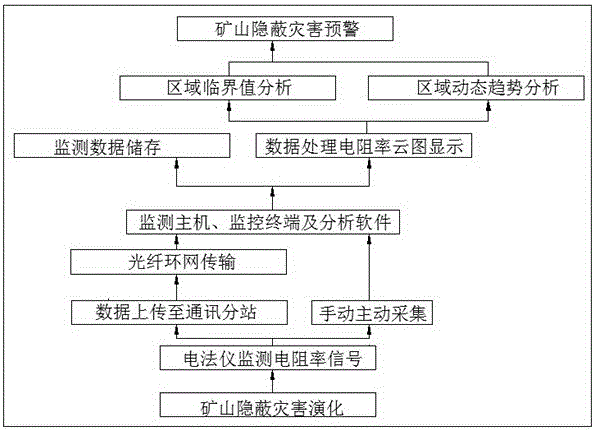
ActiveCN105840239AReal-time detectionReal-time evaluationMining devicesDisaster monitoringEngineering
The invention discloses a real-time active detecting and passive monitoring integrated system and method for hidden disasters of a mine, and belongs to hidden disaster monitoring systems and methods for mines. The system mainly comprises electrodes, electrode treatment controllers, an electrical prospecting apparatus main unit / communication substation, a ring network and a monitoring center. The system performs electrical prospecting active detection regularly, one electrode treatment controller is taken as source emission current through the corresponding electrode, an active electric field is formed in coal and rock mass, the other electrode treatment controllers receive active voltage signals synchronously through the corresponding electrodes, and active emission is performed sequentially one by one; passive potential signal monitoring of the coal and rock mass is performed at other time. An evolutionary process of the hidden disasters of the mine is reflected through coupling of results obtained through active electrical prospecting detection and passive potential monitoring, and meanwhile, real-time risk detection and evaluation of a dynamic disaster region and real-time fusion early-warning of risks before disasters are realized. The system and the method can reflect the evolution information of an internal structure of the coal and rock mass in real time more comprehensively, the anti-interference capability is high, and the early warning accuracy is high.
Owner:CHINA UNIV OF MINING & TECH
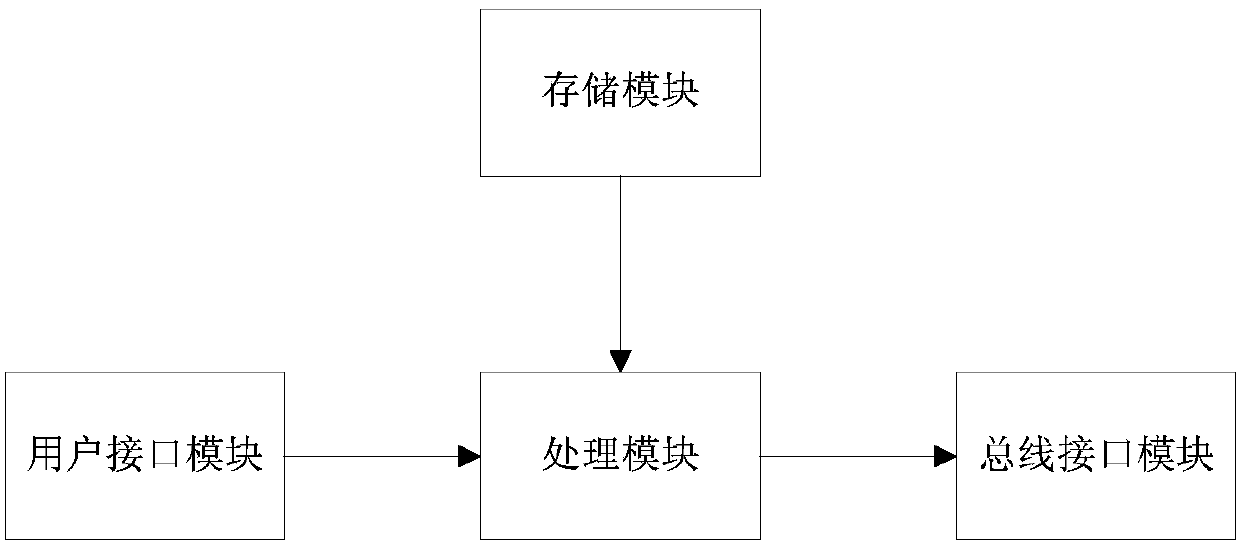
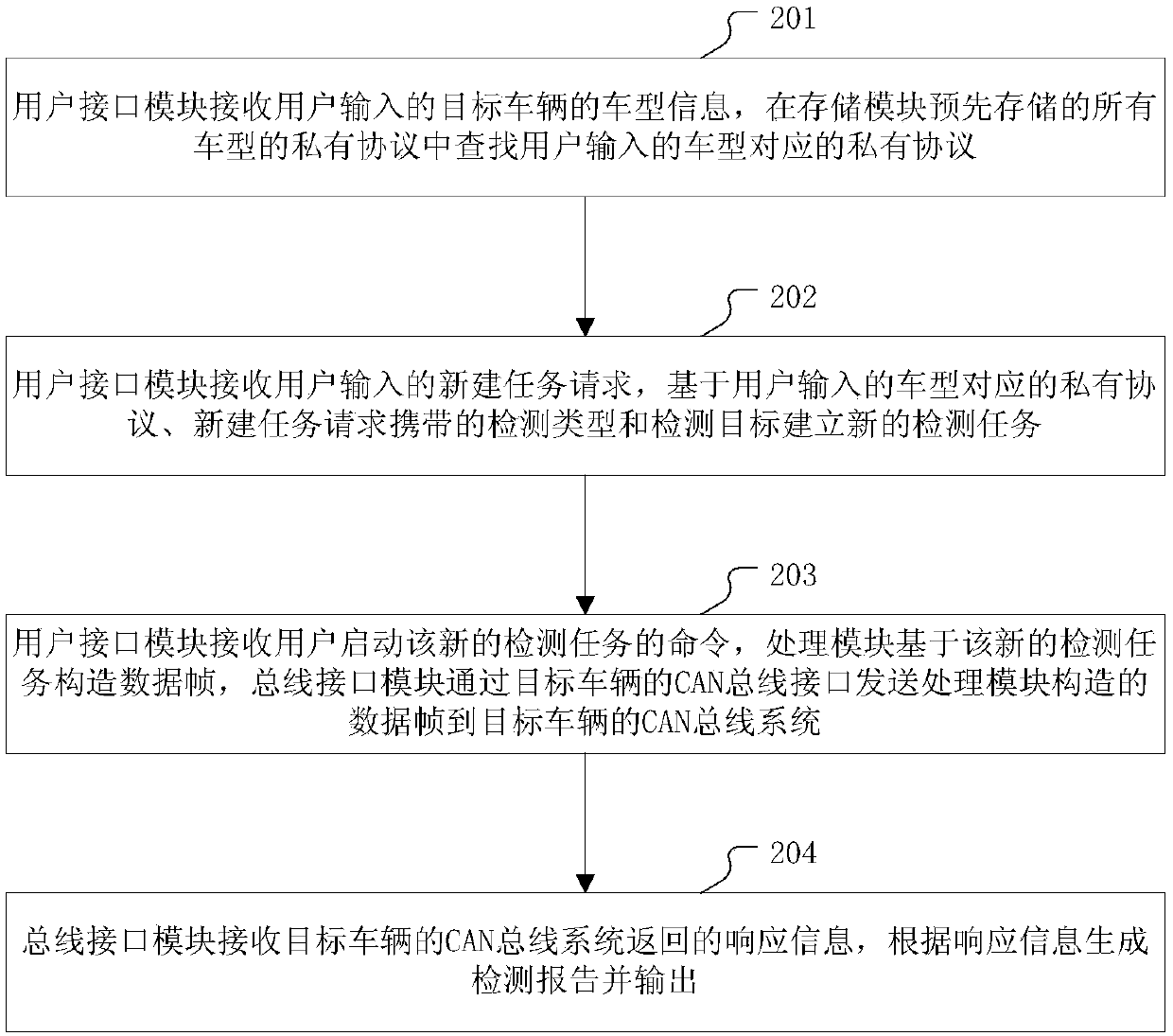
CAN bus risk detection method and device
The present invention provides a CAN bus risk detection method and device. The method is applied to a device connected with the CAN bus interface of a target vehicle and includes the following steps that: the vehicle model information of the target vehicle inputted by a user is received, and a private protocol corresponding to the vehicle model inputted by the user is searched in the private protocols of various pre-stored vehicle models; a task creation request inputted by the user is received, a new detection task is created according to the private protocol corresponding to the vehicle model inputted by the user, a detection type carried by the task creation request, and a detection target; and a data frame is constructed based on the detection task when a command for initiating the detection task is received, and the constructed data frame is sent to the CAN bus system of the target vehicle through the CAN bus interface of the target vehicle; response information returned by the CAN bus system of the target vehicle is received, and a detection report is generated according to the response information and is outputted. With the CAN bus risk detection method and device of the present invention adopted, a safety risk in the CAN bus system of the vehicle is detected.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT
Transaction risk detection method, apparatus and equipment
ActiveCN106875078AAvoid false rejectionReduce maintenance costsBuying/selling/leasing transactionsResourcesRisk typeComputer science
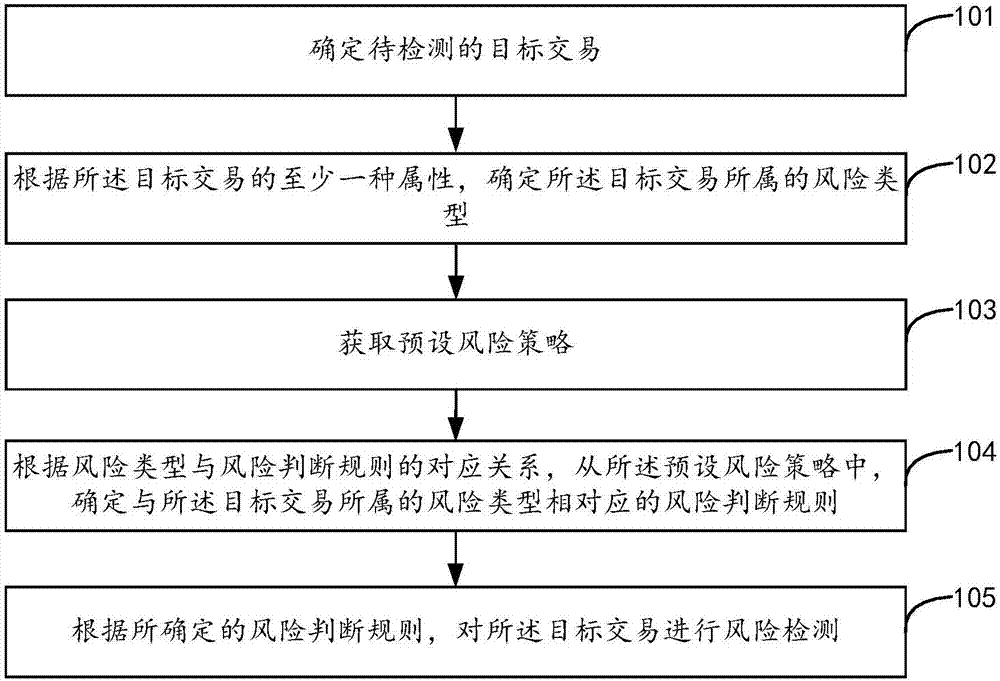
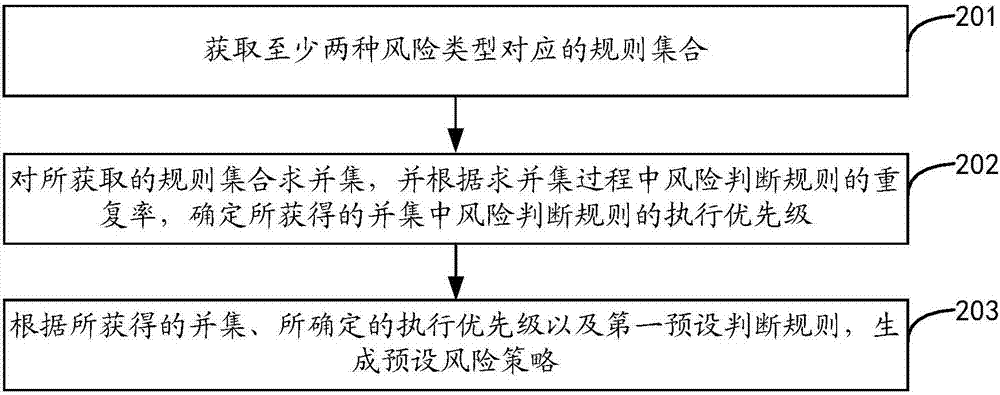
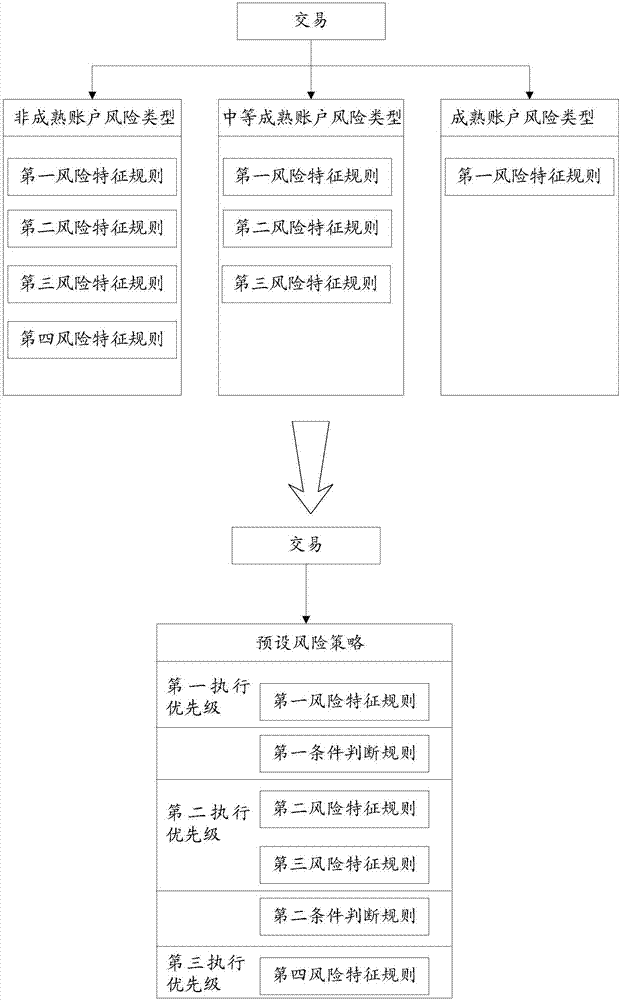
The invention relates to transaction risk detection method, apparatus and equipment. The transaction risk detection method includes the steps: determining the target transaction to be detected; according to at least one attribute of the target transaction, determining the risk type owned by the target transaction; acquiring a preset risk strategy, wherein the preset risk strategy includes at least one risk judgment rule; each risk judgment rule is corresponding to at least one risk type; and at least one risk judgment rule in the risk strategy is corresponding to at least two risk types; according to the corresponding relationship between the risk types and the judgment rules, from the preset risk strategy, determining the risk judgment rule corresponding to the risk type owned by the target transaction; and according to the determined risk judgment rules, performing risk detection on the target transaction. The transaction risk detection method, apparatus and equipment can avoid incorrect rejection and can reduce the maintenance cost.
Owner:ADVANCED NEW TECH CO LTD
Risk detection method and device, equipment and storage medium
ActiveCN110210227ARealize scenario-based risk predictionEasy to understand implementationRelational databasesCharacter and pattern recognitionData miningInformation data
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
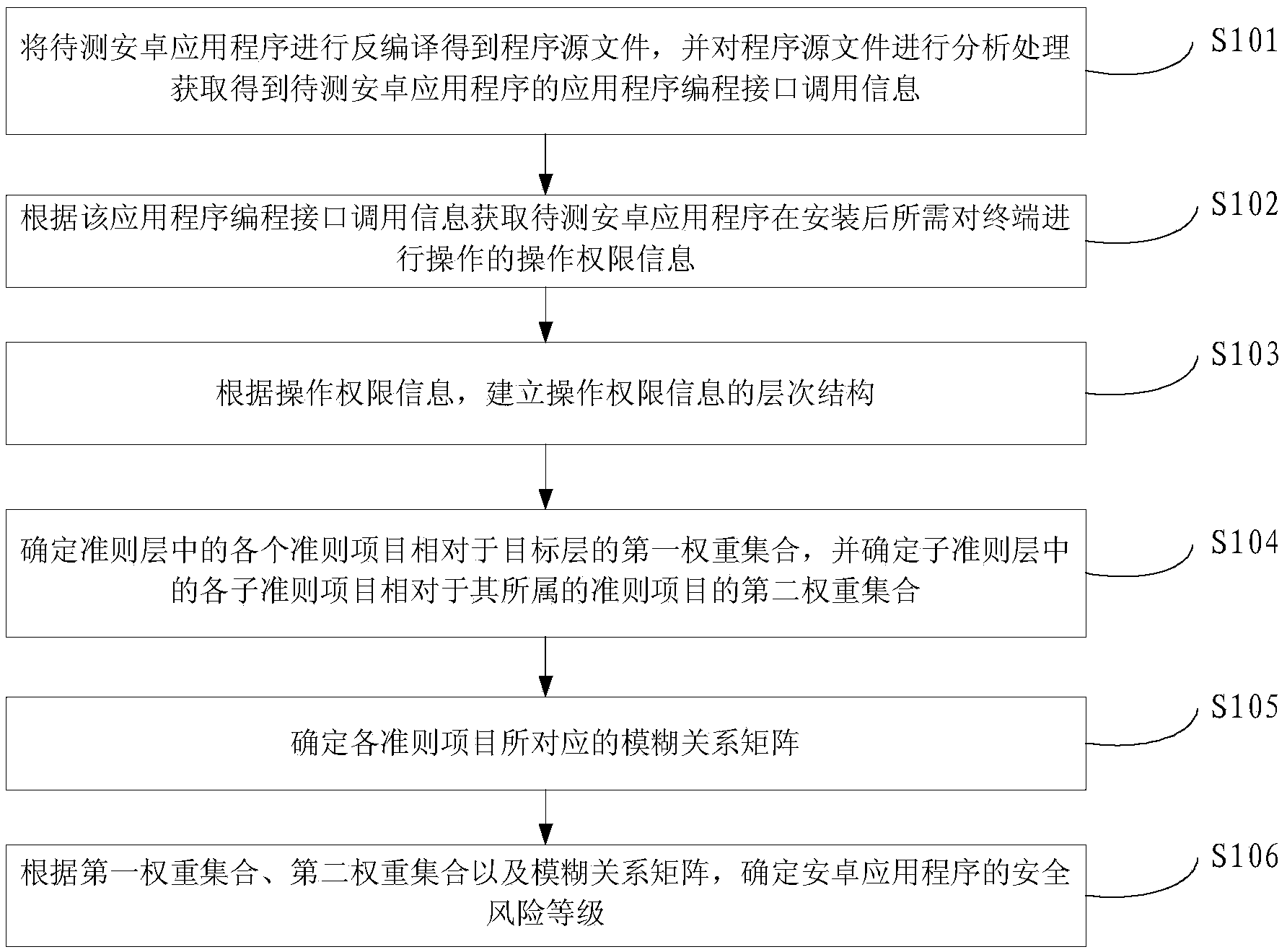
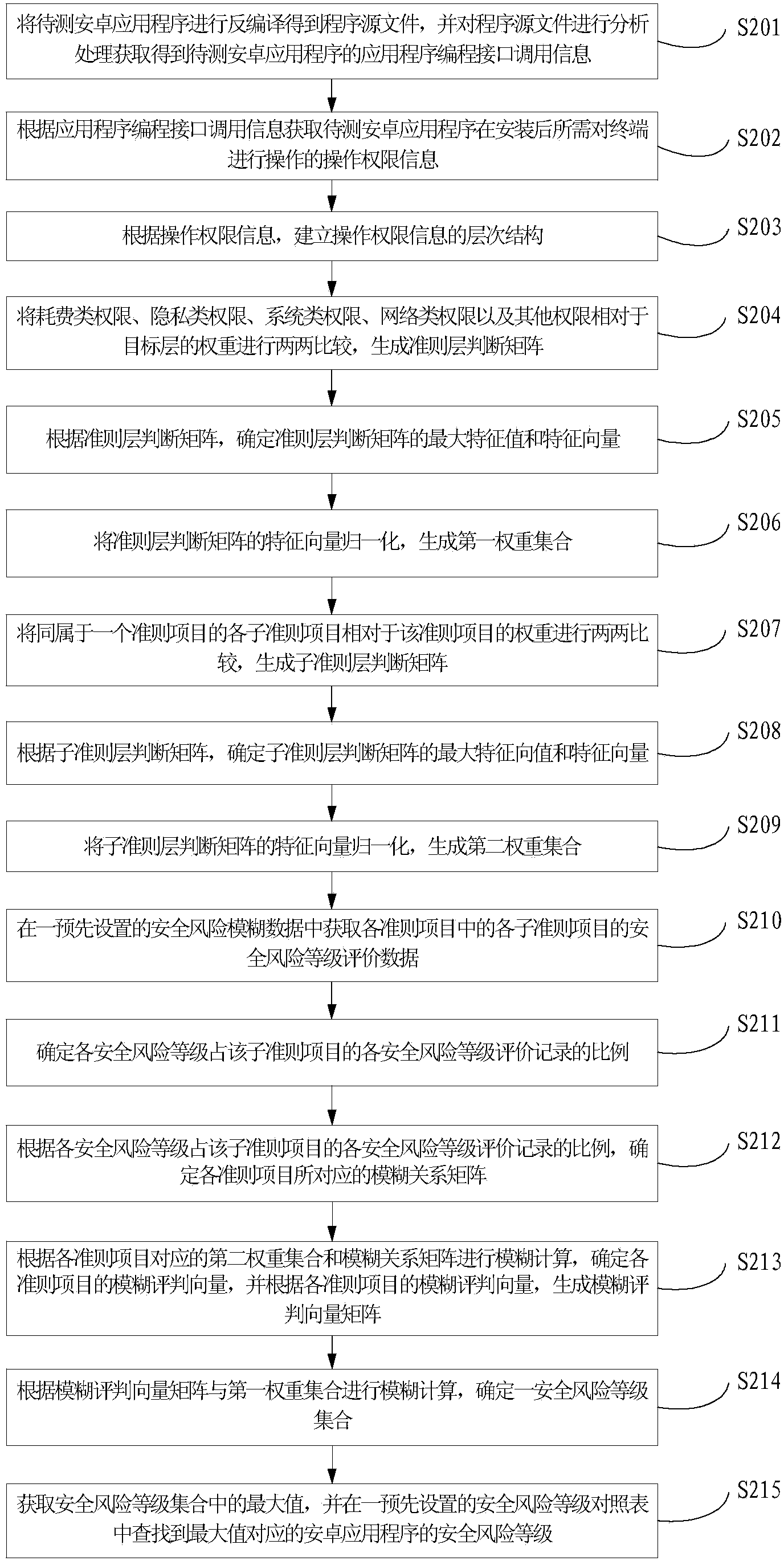
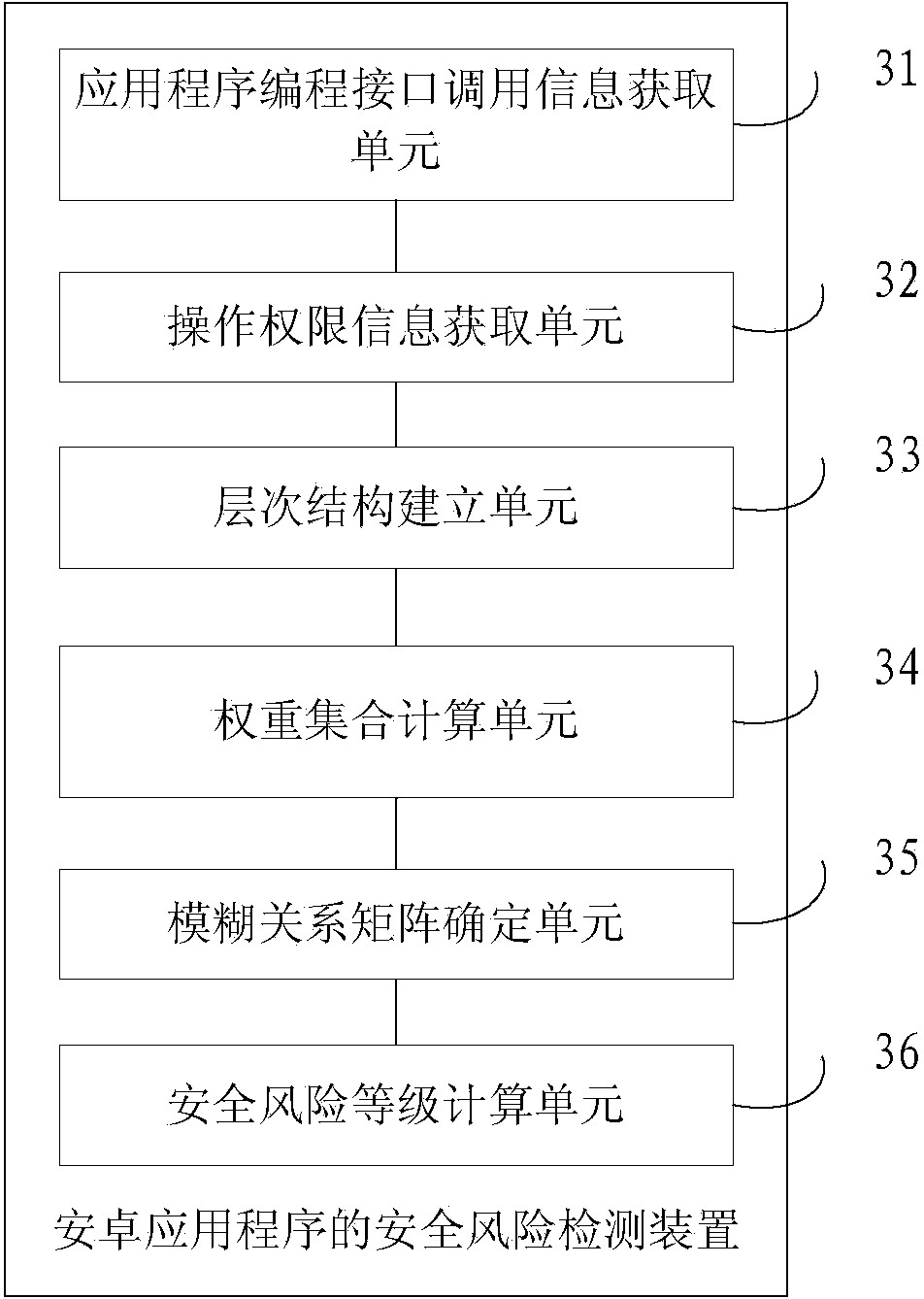
Safety risk detecting method and device for Android application program
ActiveCN104376258APlatform integrity maintainanceApplication programming interfaceSoftware engineering
The invention provides a safety risk detecting method and device for an Android application program and relates to the technical field of Android application detecting. The method comprises the steps that decompiling is carried out on the Android application program to be detected to obtain a program source file, and the program source file is analyzed and processed to obtain application programming interface call information of the Android application program to be detected; according to the application programming interface call information of the Android application program to be detected, operating authorization information of operation needing to be carried out on a terminal by the Android application program to be detected is obtained; according to the operating authorization information, a hierarchical structure is set up; first weight sets of all criterion items in a criterion layer relative to a target layer are determined, and second weight sets of all subsidiary criterion items in a subsidiary criterion layer relative to the criterion items which the subsidiary criterion items belong to are determined; fuzzy relation matrixes corresponding to all the criterion items are determined; according to the first weight sets, the second weight sets and the fuzzy relation matrixes, safety risk grades are determined. The method can solve the problem that a risk detecting mode of a current application program is not accurate.
Owner:CHINA ACADEMY OF INFORMATION & COMM
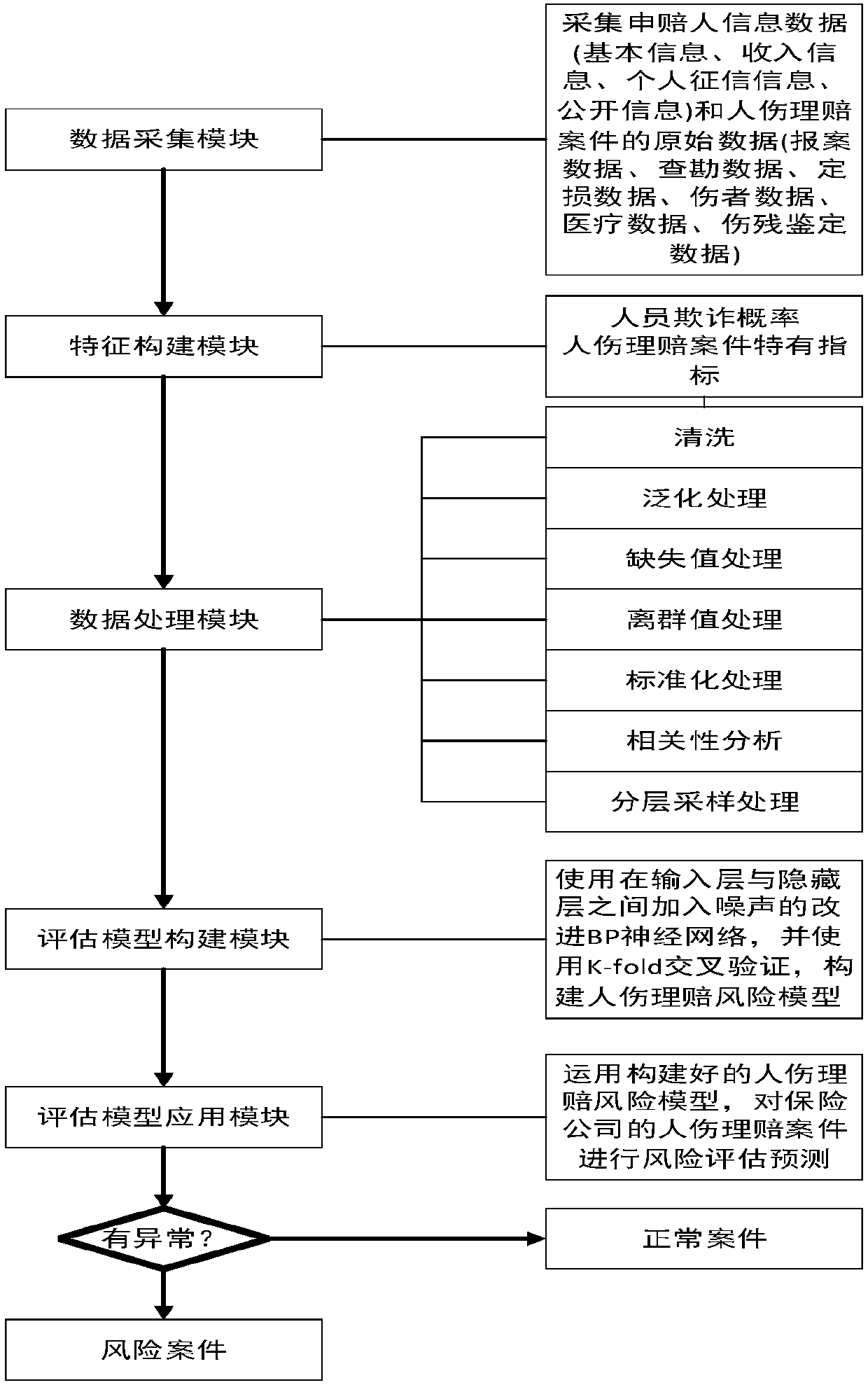
Method and system for detecting human injury claim data risk
ActiveCN107909299AMaintain orderImprove forecast accuracyFinanceResourcesComputer scienceRisk evaluation
The invention relates to a method and a system for detecting human injury claim data risk. The method comprises steps that at least one type of the claimant information, medical data, disability identification data and claim data of human claim data is acquired, a prebuilt human injury claim risk detection modeling algorithm is utilized to carry out data processing, and false frauds and unreasonable expense item results in the claim process are discovered. The method is combined with all the characteristics of human injury claims to construct a human injury claim risk evaluation characteristicsystem, and the unified evaluation standard foundation is laid, moreover, for problems of low evaluation accuracy and incapability of guaranteeing rights of insurance companies and most of normal customers and maintaining the normal social order existing in a system in the prior art, the improved BP neural network algorithm is further constructed as a human injury claim risk evaluation model, andprediction accuracy and generalization performance are improved.
Owner:KAITAIMING BEIJING TECH
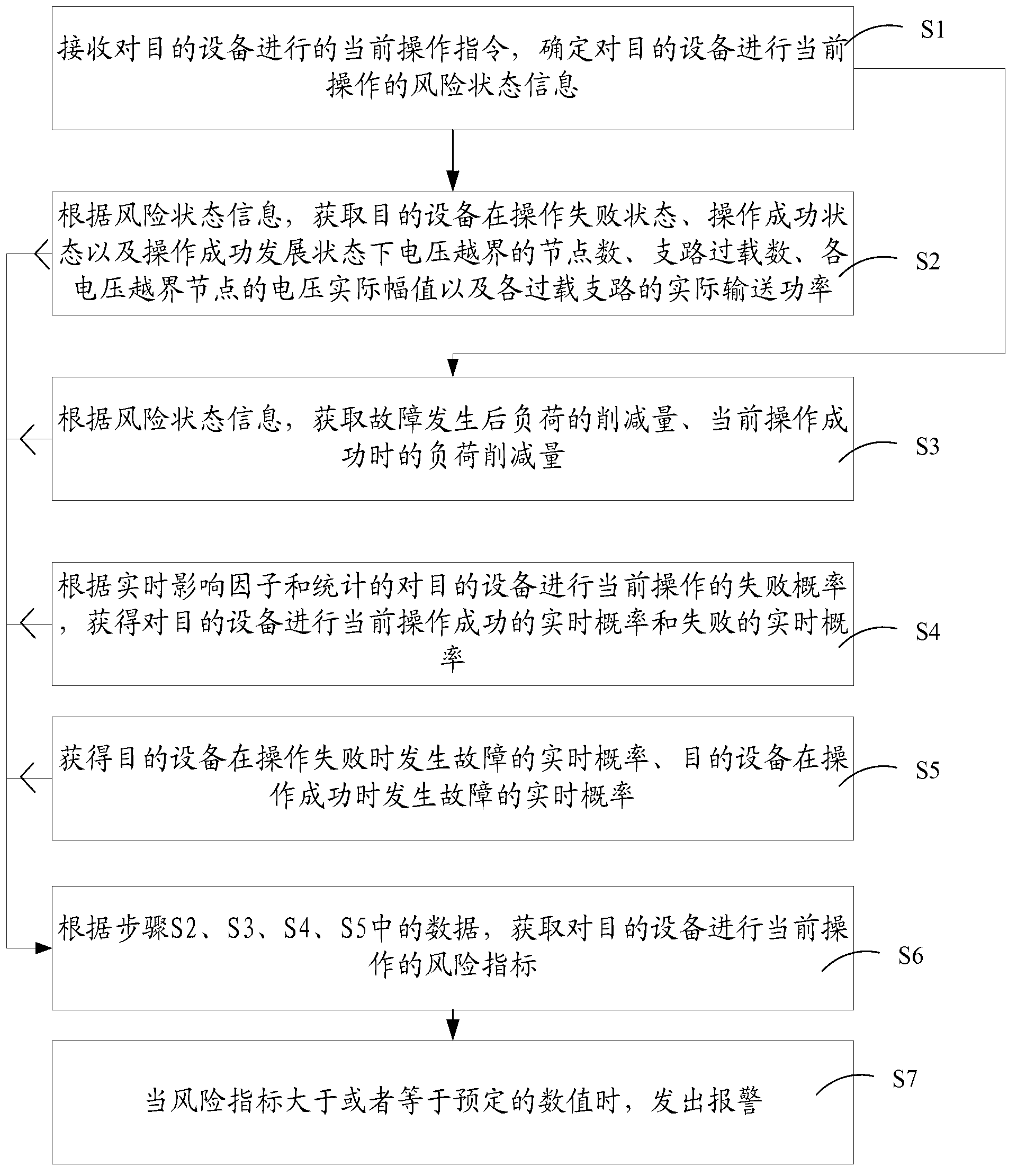
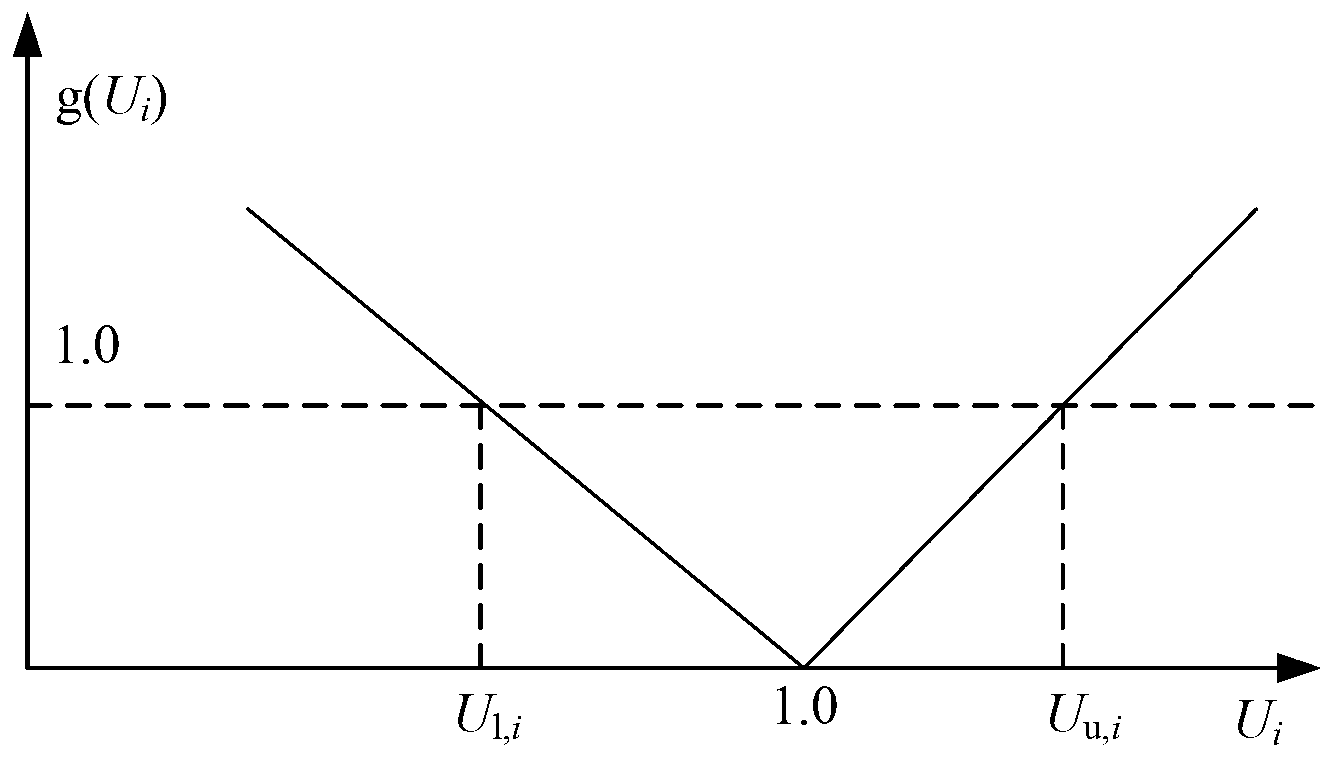
Risk test method and risk test device for power gird dispatching operation
ActiveCN103218754AGuaranteed safe operationData processing applicationsInformation technology support systemVoltage amplitudeTransmitted power
The invention provides a risk test method for power gird dispatching operation. The risk test method for the power gird dispatching operation comprises the steps: receiving a current operation command conducted to target equipment and confirming risk state information; obtaining the number of nodes which are beyond a voltage boundary, overload number of branches, actual voltage amplitude value of each node which is beyond the voltage boundary and actual transmitting power of each overload branch under the states of failed operation, successful operation and successful operation development; obtaining load reduction quantity after failure and load reduction quantity under successful operation; obtaining real-time probabilities when operation succeeds and fails; obtaining real-time probability of failure after operation fails and real-time failure probability of the target equipment when operation succeeds; obtaining a risk indicator of the current operation; and sending an alarm out when the risk indicator is larger than or equal to a preset value. The invention further provides a risk test device for the power gird dispatching operation. The risk test device for the power gird dispatching operation is capable of pre-testing security status of a power gird caused by the power gird dispatching operation and guaranteeing the safe operation of an electrical power system.
Owner:POWER DISPATCHING CONTROL CENT OF GUANGDONG POWER GRID CO LTD +1
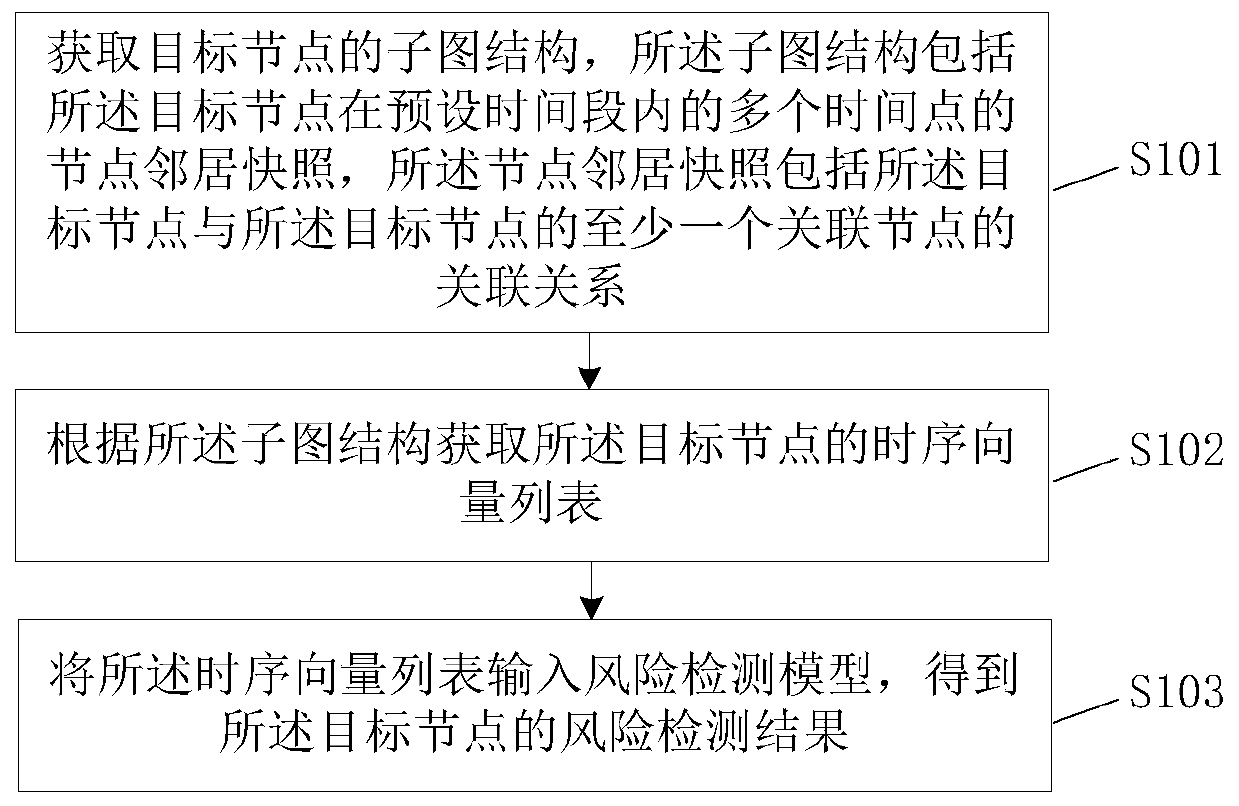
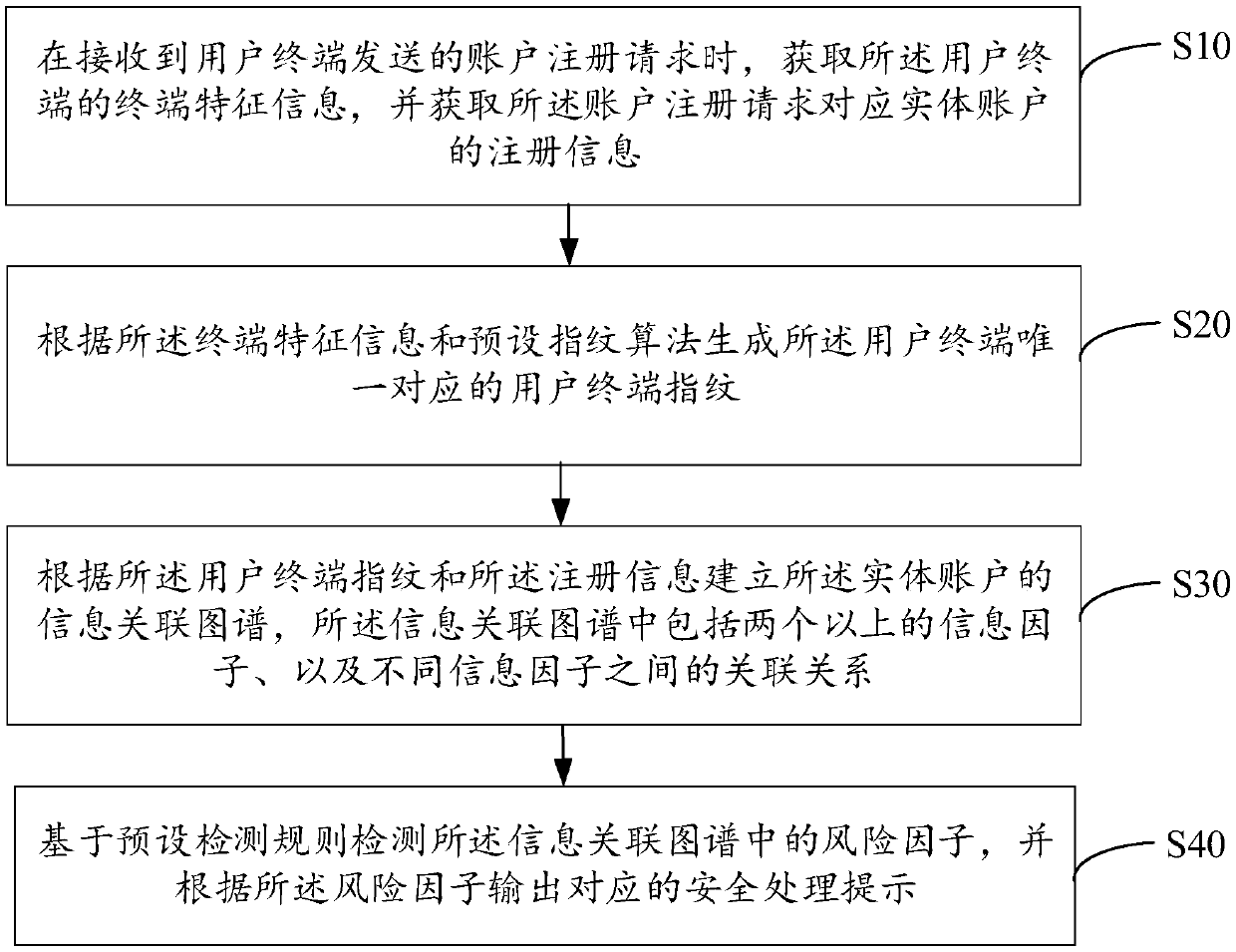
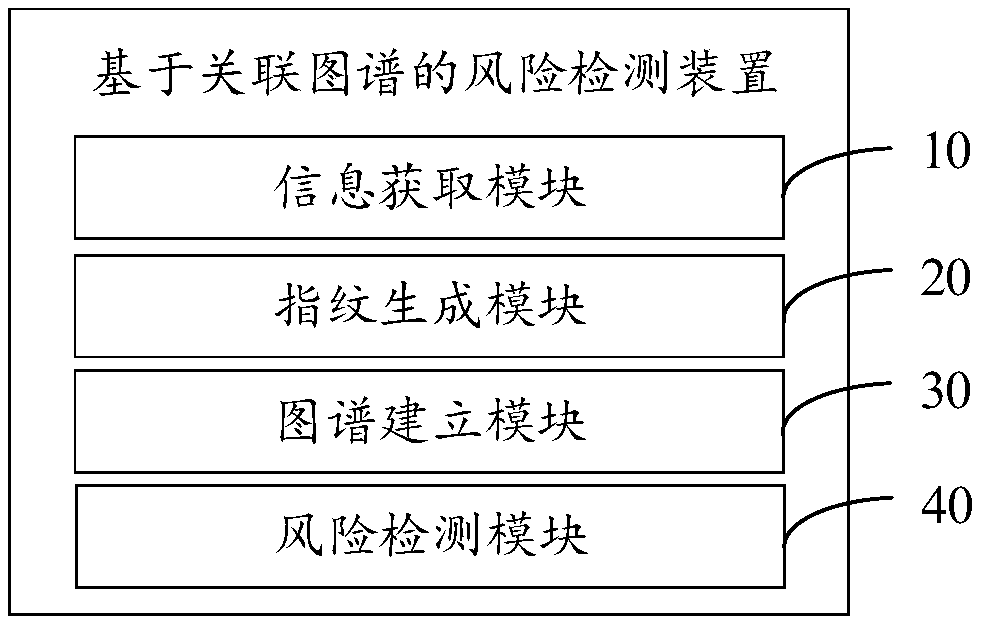
Risk detection method, device and equipment based on association map and storage medium
PendingCN109559192ARealize risk warningEasy to understandBuying/selling/leasing transactionsResourcesRisk ControlE-commerce
The invention provides a risk detection method, device and equipment based on a knowledge graph and a readable storage medium, and the method comprises the steps of collecting related data of a user when the user carries out account registration, and integrating the data through a correlation graph (knowledge graph) mode, so that merchants or risk control personnel can conveniently know the correlation among various information; and then carrying out the risk detection according to the association map, so that the user data is analyzed in a knowledge relation analysis manner, potential business risks are predicted, electronic commerce risk early warning is realized, and the risk detection capability and the business safety are improved.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
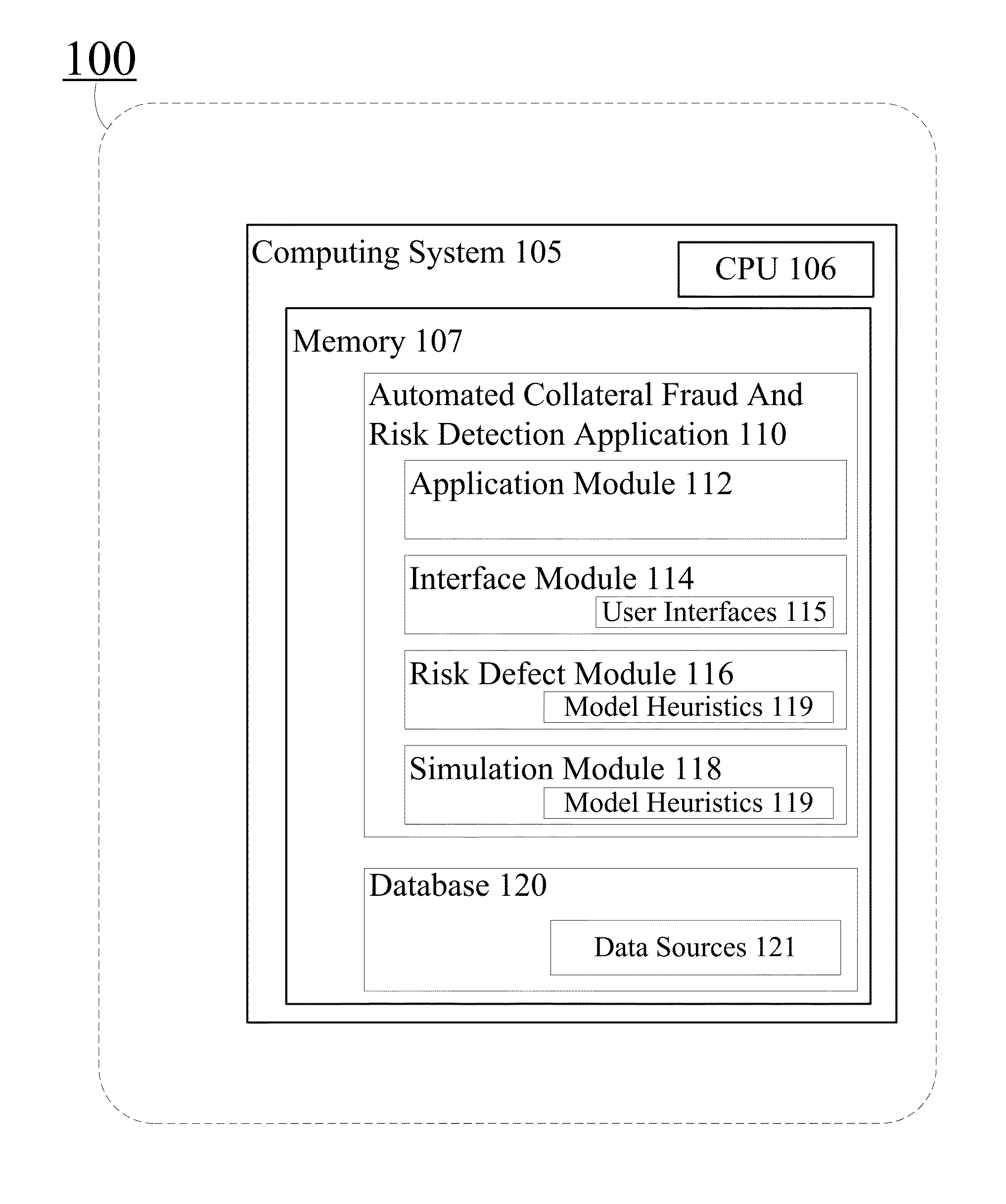
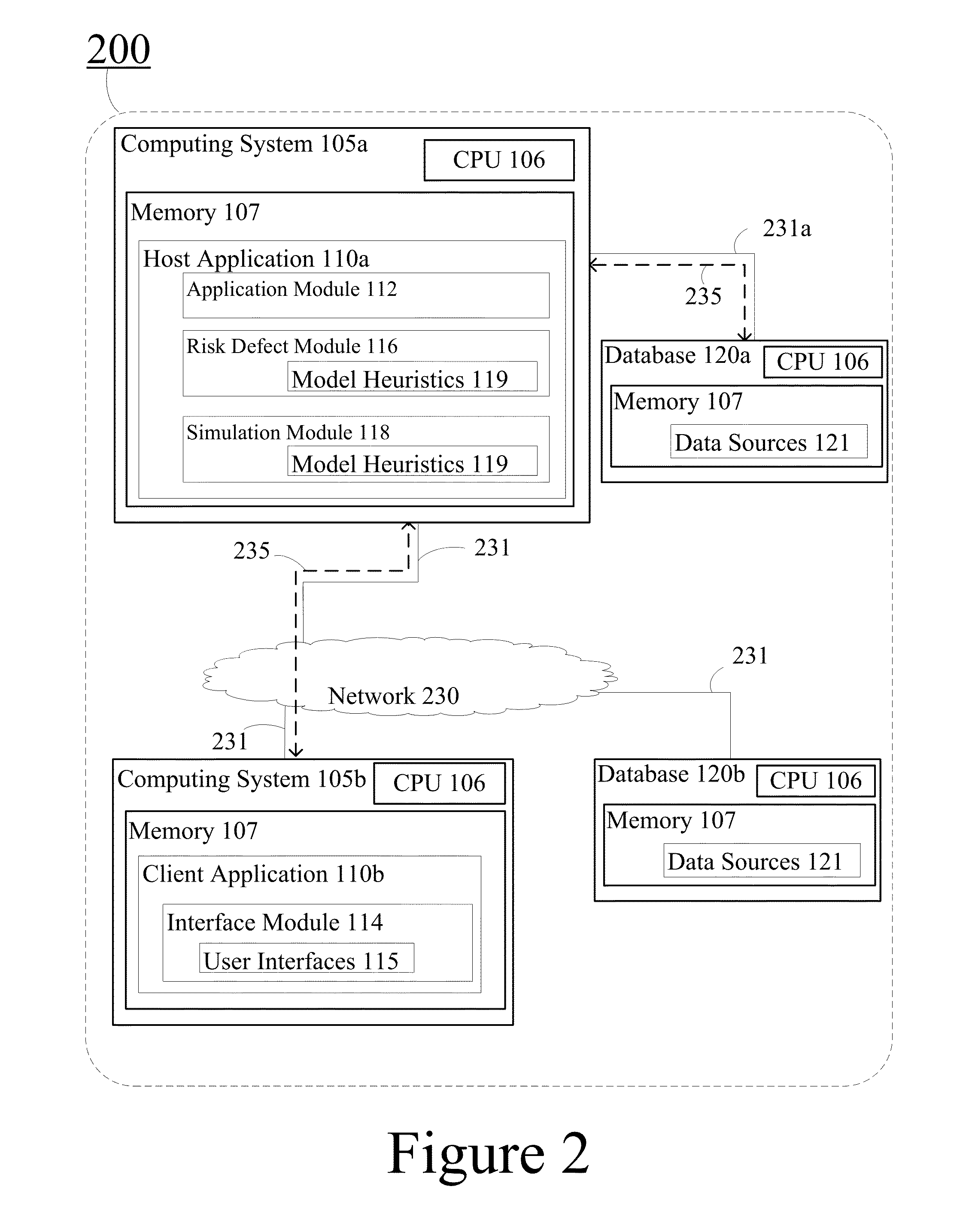
Automated risk evaluation in support of end user decisions
A system comprises a device including a memory with an automated collateral fraud and risk detection application installed thereon, wherein the application evaluates risk in an acquisition in support of end user decisions by accessing at least one database to retrieve documentation corresponding to the acquisition and secondary information corresponding to the documentation, the documentation and secondary information each including data fields; compares the documentation data fields with corresponding secondary information data fields to identify acquisition defects; applies risk heuristics on the acquisition defects to generate a probability estimation for each acquisition defect; and outputs a risk evaluation for the acquisition including a confidence metric based on an aggregation of the probability estimations.
Owner:FANNIE MAE
Failure risk rate calculation method and device based on dam failure function models
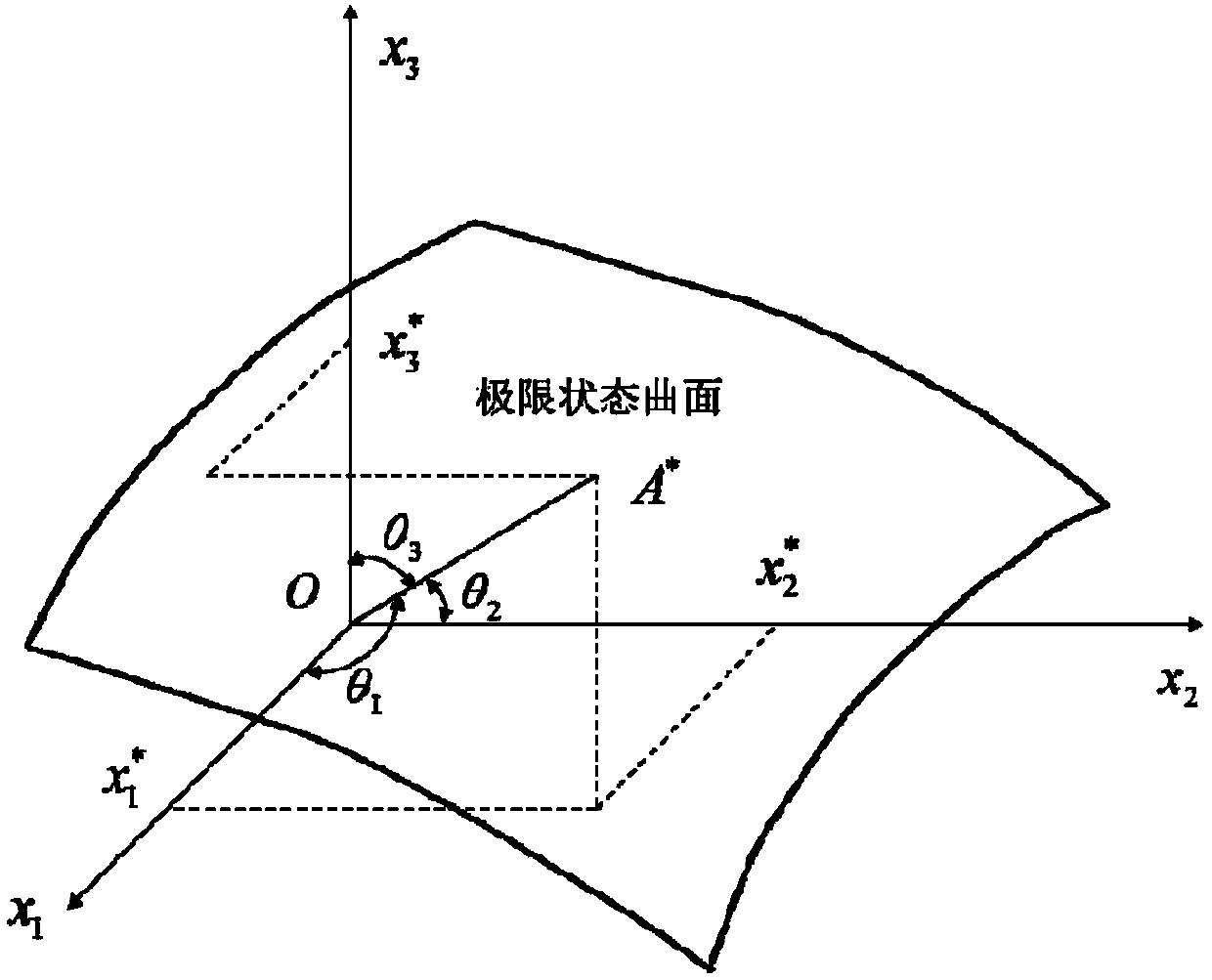
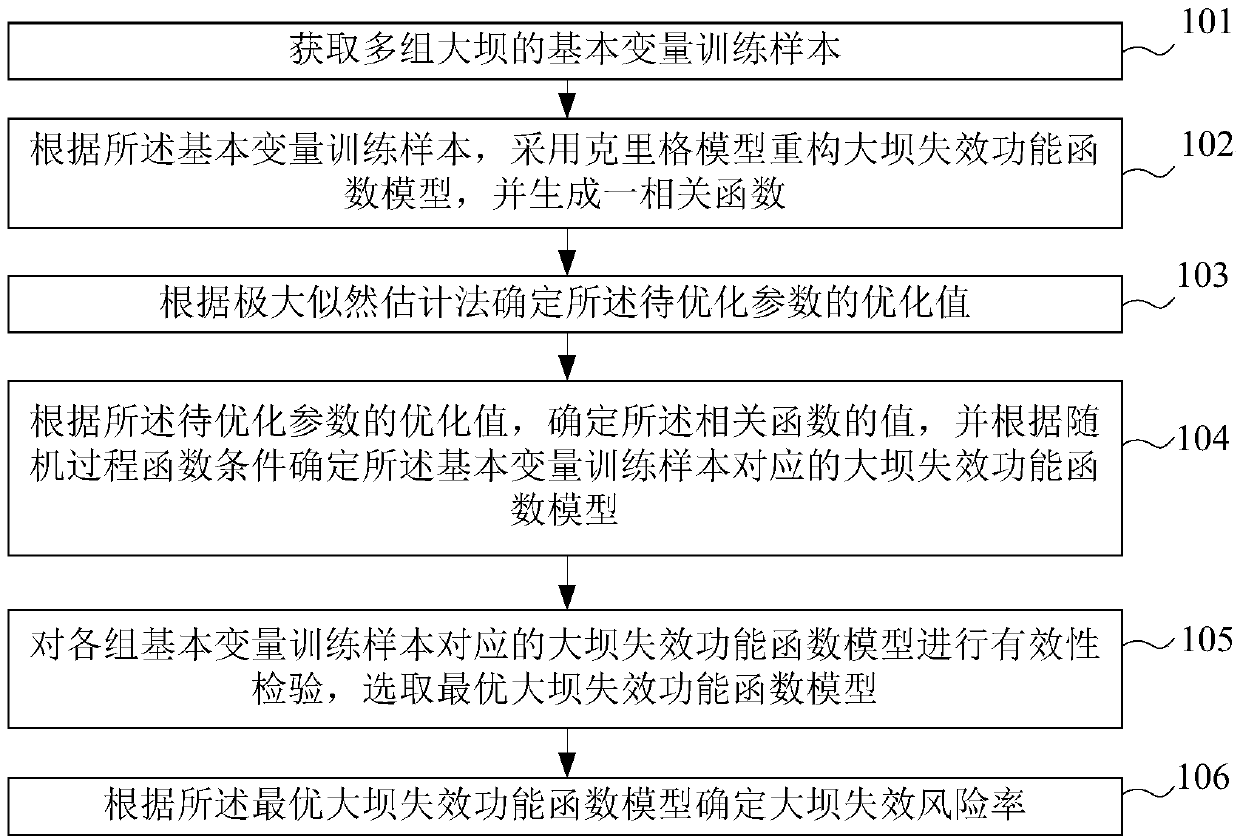
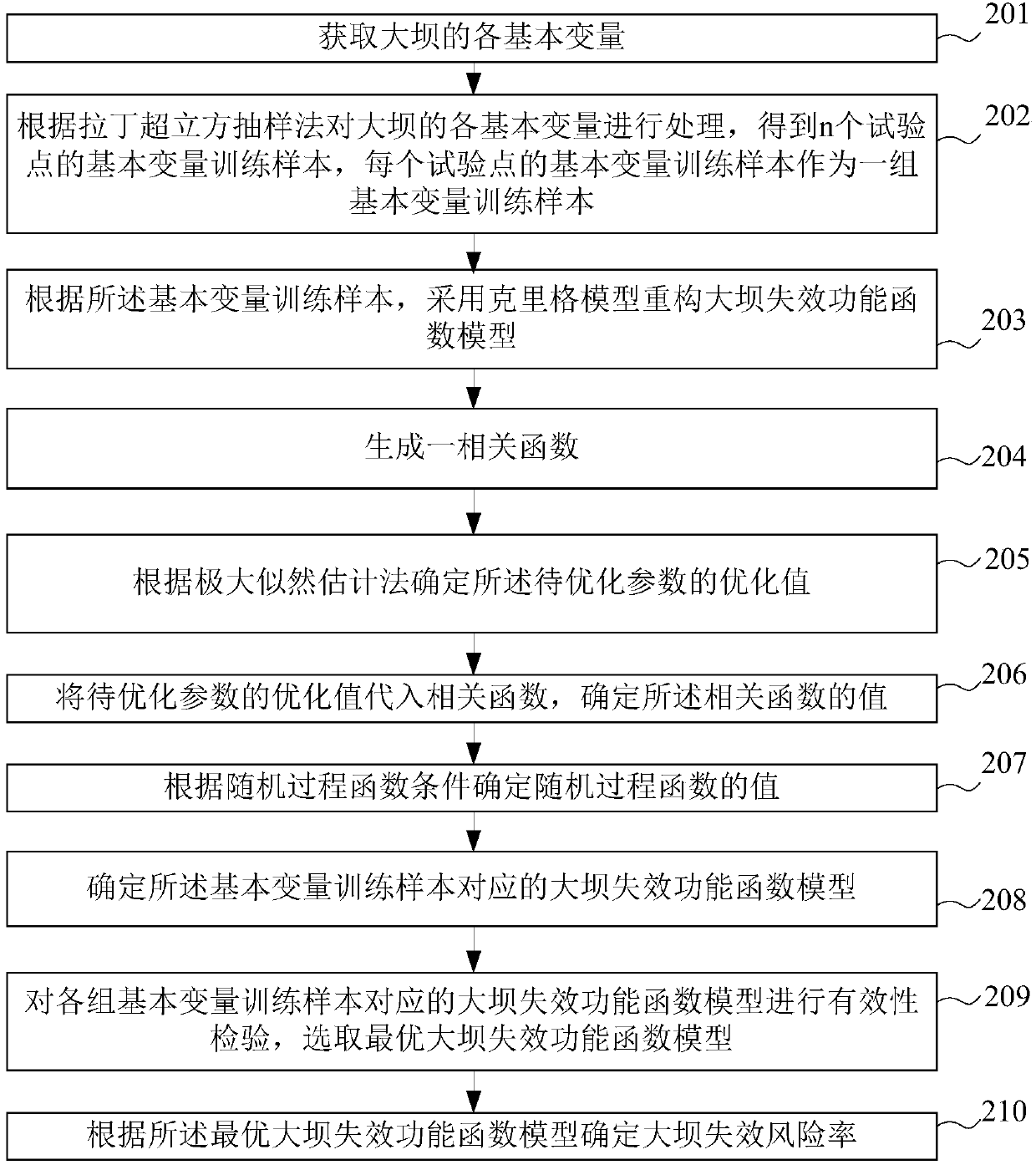
InactiveCN107563046AEasy to operateSpecial data processing applicationsProcess functionCorrelation function
The invention provides a failure risk rate calculation method and device based on dam failure function models, and relates to the technical field of dam safety risk detection. The method comprises thesteps that basic variable training samples of a plurality of groups of dams are acquired; the dam failure function models are reconstructed by using a kriging model, and a correlation function is generated, wherein the correlation function is used for describing spatial correlation among all the basic variable training samples affecting the safety of the dams, and the correlation function comprises a to-be-optimized parameter; an optimization value of the to-be-optimized parameter is determined according to the maximum likelihood estimation method; according to the optimization value of the to-be-optimized parameter, the value of the correlation function is determined, and the dam failure function models corresponding to the basic variable training samples are determined according to a random process function condition; validity check is conducted on the dam failure function models corresponding to each group of basic variable training samples, and the optimal dam failure function model is selected; the dam failure risk rate is determined according to the optimal dam failure function model.
Owner:STATE GRID CORP OF CHINA +2
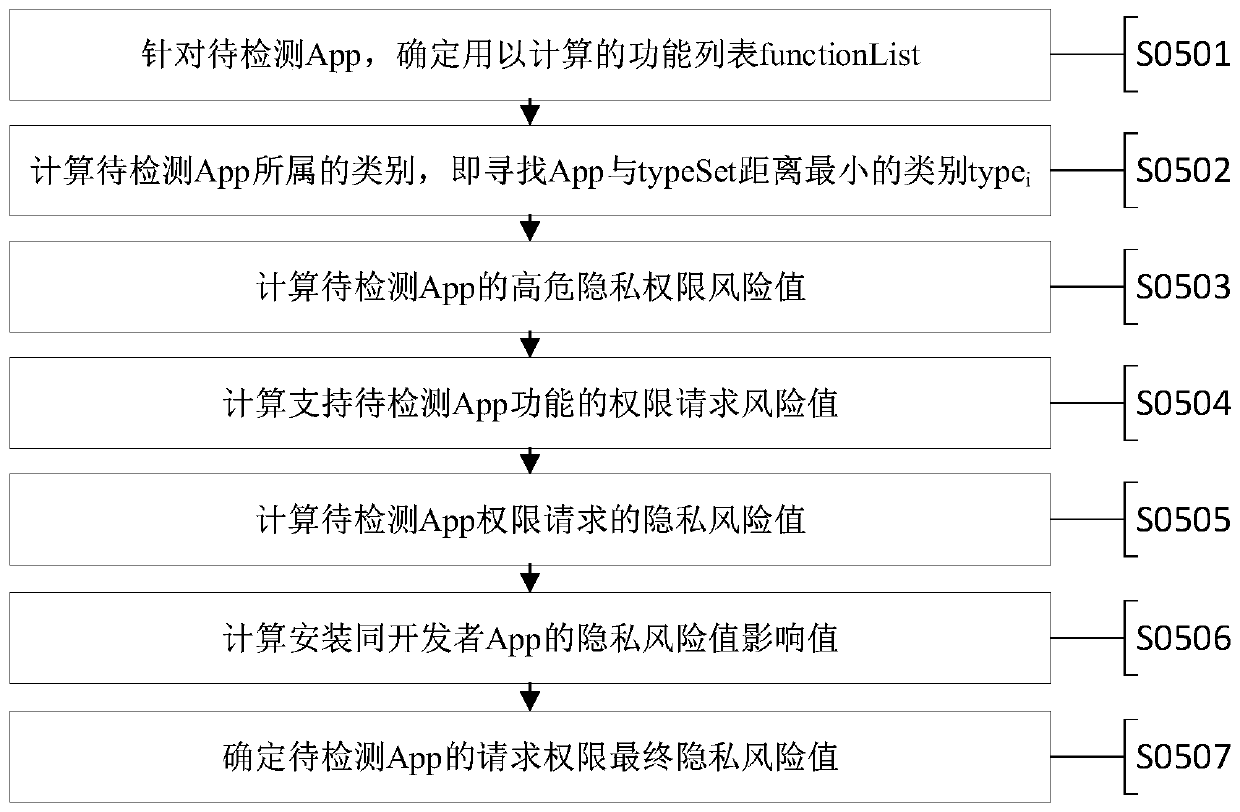
Intelligent terminal App permission privacy risk monitoring and evaluation system and method
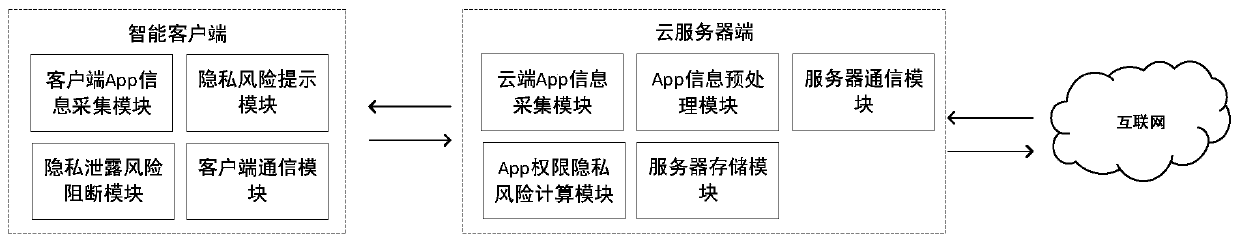
ActiveCN110298176APrivacy protectionDigital data protectionPlatform integrity maintainanceComputation complexityRelevant information
The invention discloses an intelligent terminal App permission privacy risk monitoring and evaluation system and method. Aiming to solve the problem of privacy disclosure of a user caused by user permission abuse in the application process of an existing intelligent terminal App and solve the technical problems of large data acquisition amount, high calculation complexity, high implementation difficulty, easy misjudgment and the like in the prior art, the invention provides an intelligent terminal App permission privacy risk detection and evaluation method and a privacy disclosure blocking system, being characterized by collecting an App permission list and related information; calculating permission analysis of an App to be detected, an App of the same kind, an App of the same function and an App of the same developer and privacy information sensitivity of related permissions, so as to provide the privacy disclosure risk evaluation method for the intelligent terminal App permission, and providing an unloading prompt for blocking high-risk App permission or App according to permission privacy disclosure risk grading, so that efficient, convenient and accurate intelligent terminal App permission privacy disclosure risk evaluation and blocking are realized, and the privacy of a user is protected.
Owner:GUIZHOU UNIVERSITY OF FINANCE AND ECONOMICS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com