Big data and trusted computing based information network security self-defense system
A technology of trusted computing and information network, applied in the field of big data, can solve the problem of unsatisfactory processing effect of discrete attributes, and achieve the effect of preventing information security risks, improving clustering stability, and avoiding idleness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
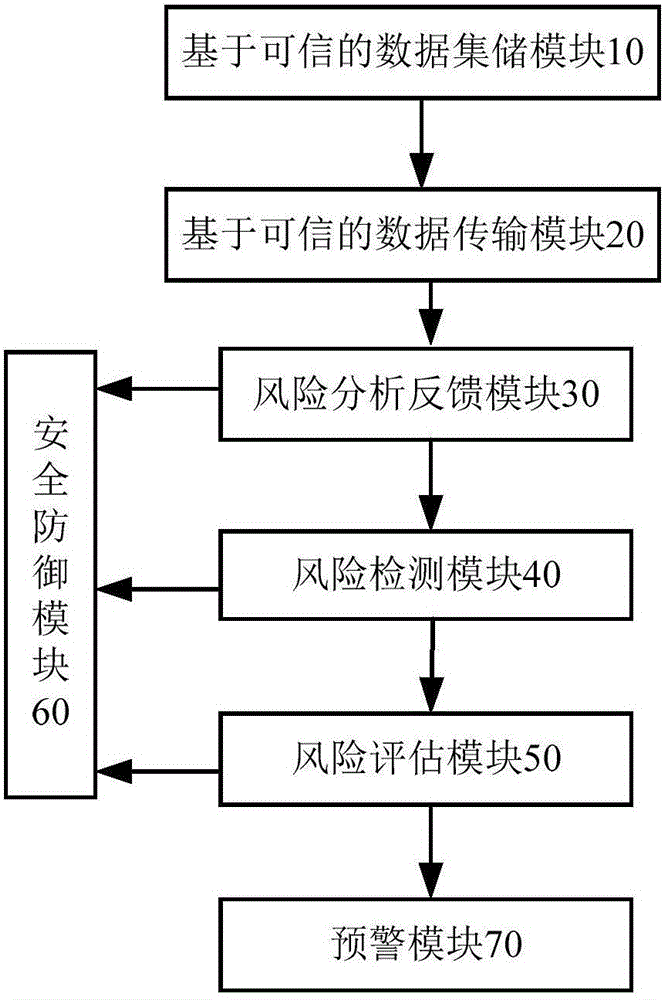
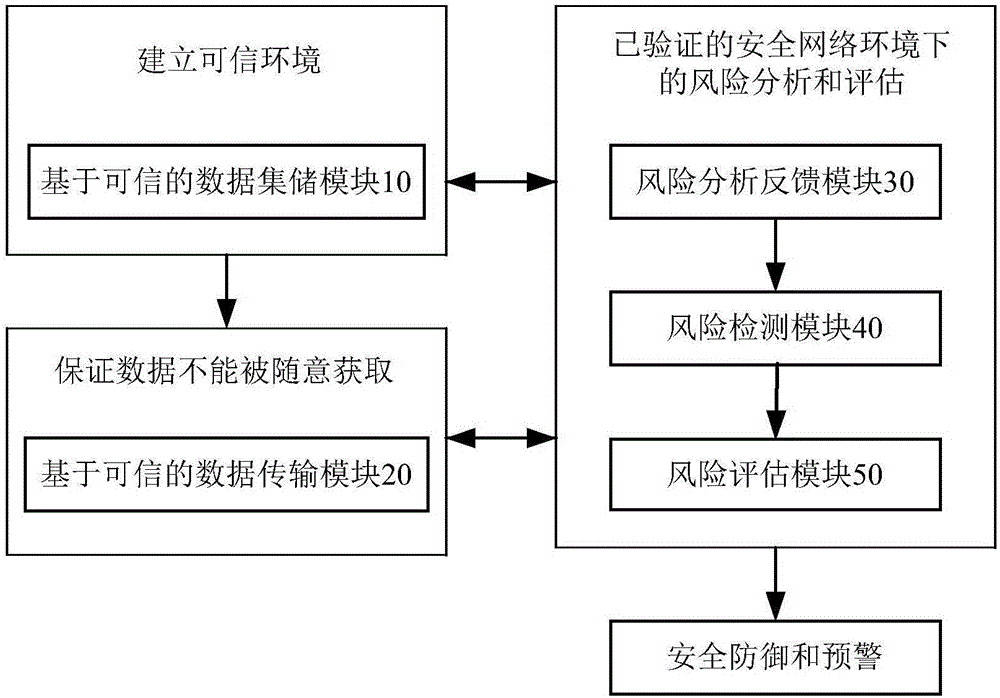
[0047] Embodiment 1: as figure 1 , figure 2 The shown information network security self-defense system based on big data and trusted computing includes a trusted data collection module 10, a trusted data transmission module 20, a risk analysis feedback module 30, a risk detection module 40, a risk Evaluation module 50, security defense module 60 and early warning module 70, the described credible data collection and storage module 10 is used to collect and encrypt the useful data containing user-related information of the storage terminal, when collecting, the network nodes that collect useful data are collected Authentication, to ensure that the data collection environment is trustworthy, and to establish a trust relationship. The trusted data transmission module 20 is used to realize the encrypted transmission of useful data of each module, so as to ensure that useful data will not be obtained arbitrarily;
[0048] The risk detection module 40 is used to perform real-time ...
Embodiment 2
[0077] Embodiment 2: as figure 1 , figure 2 The shown information network security self-defense system based on big data and trusted computing includes a trusted data collection module 10, a trusted data transmission module 20, a risk analysis feedback module 30, a risk detection module 40, a risk Evaluation module 50, security defense module 60 and early warning module 70, the described credible data collection and storage module 10 is used to collect and encrypt the useful data containing user-related information of the storage terminal, when collecting, the network nodes that collect useful data are collected Authentication, to ensure that the data collection environment is trustworthy, and to establish a trust relationship. The trusted data transmission module 20 is used to realize the encrypted transmission of useful data of each module, so as to ensure that useful data will not be obtained arbitrarily;
[0078] The risk detection module 40 is used to perform real-time ...
Embodiment 3
[0107] Embodiment 3: as figure 1 , figure 2 The shown information network security self-defense system based on big data and trusted computing includes a trusted data collection module 10, a trusted data transmission module 20, a risk analysis feedback module 30, a risk detection module 40, a risk Evaluation module 50, security defense module 60 and early warning module 70, the described credible data collection and storage module 10 is used to collect and encrypt the useful data containing user-related information of the storage terminal, and collect the useful data of the network nodes that collect useful data Authentication, to ensure that the data collection environment is trustworthy and to establish a trust relationship, the trusted data transmission module 20 is used to realize the encrypted transmission of useful data of each module, to ensure that useful data will not be obtained arbitrarily;
[0108] The risk detection module 40 is used to detect the running termin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com