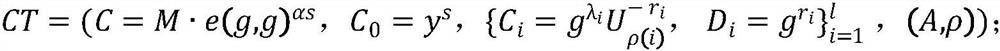Patents
Literature
33results about How to "Guaranteed storage security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Cloud data sharing method based on block chain
ActiveCN112019591AGuaranteed storage securityGuaranteed sharingKey distribution for secure communicationUser identity/authority verificationBlockchainCloud storage
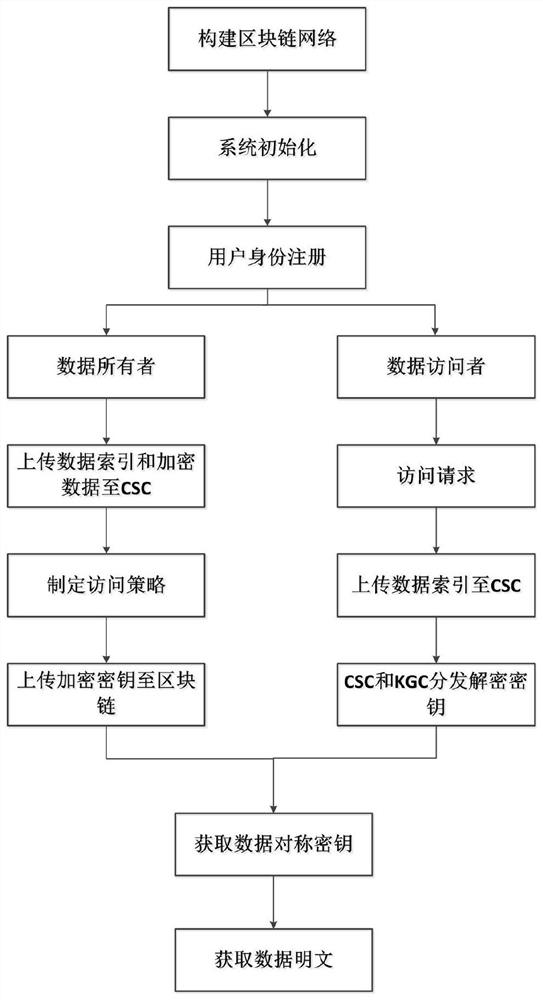
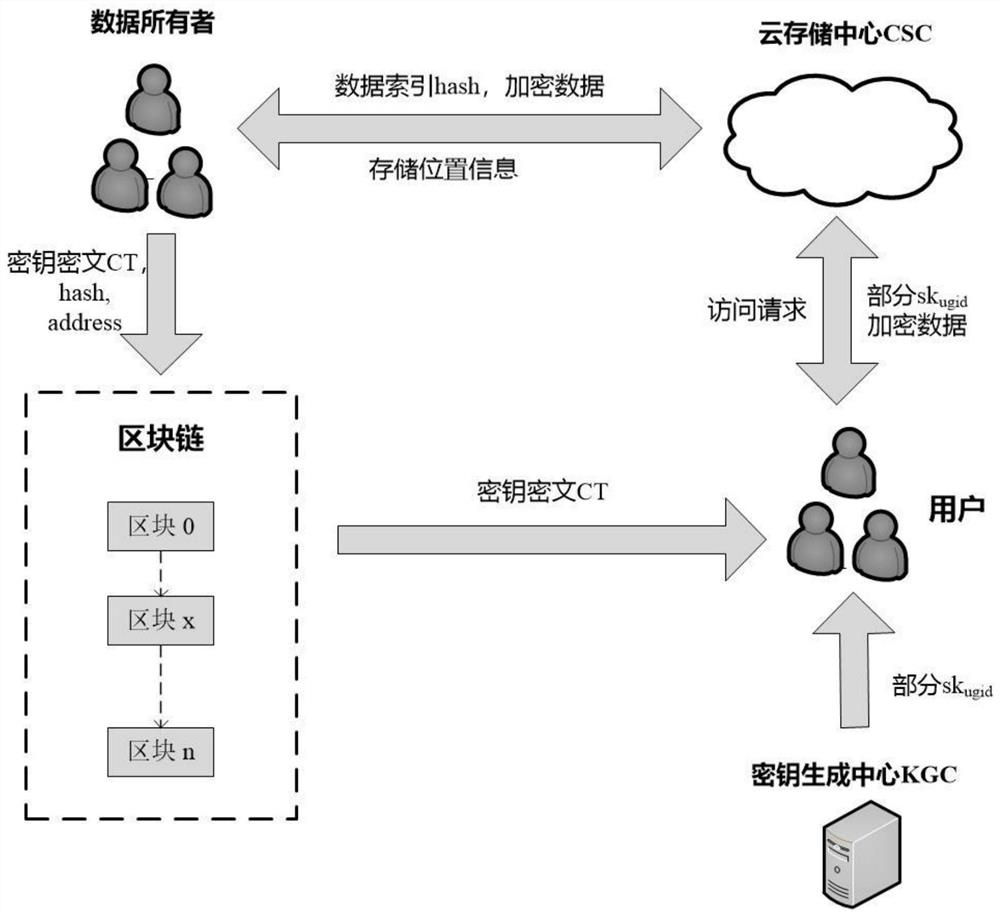
The invention discloses a cloud data sharing method based on a block chain, and the method comprises the steps: the block chain is constructed, an initialization generator is accessed, and the systeminitialization is performed; the user performs identity registration and joins the blockchain network to obtain an identity ID; the data owner uploads the data index and the encrypted data to the CSC;after successful uploading, the cloud storage center CSC stores the encrypted data and the index list; after the shared data is uploaded successfully, the data owner formulates an access strategy, encrypts an owner key, generates a new block in the block chain, and records data uploading information and an encryption key; the user sends an access request to a cloud storage center CSC and uploadsa data index needing to be accessed; the user submits attributes to the KGC and the CSC, and the KGC and the CSC jointly generate and issue a key to the user according to the attributes; and the useracquires the symmetric key ciphertext and decrypts the symmetric key ciphertext. According to the invention, the encryption key of the data owner is managed through the blockchain, an effective key management mechanism is provided, and the problem of secure sharing of cloud data is solved.
Owner:NANJING UNIV OF POSTS & TELECOMM
Establishing and operation method for portable smart password management system
InactiveCN106850228AEnsure safetyImprove management efficiencyUser identity/authority verificationSecurity arrangementNetwork terminationInformation storage
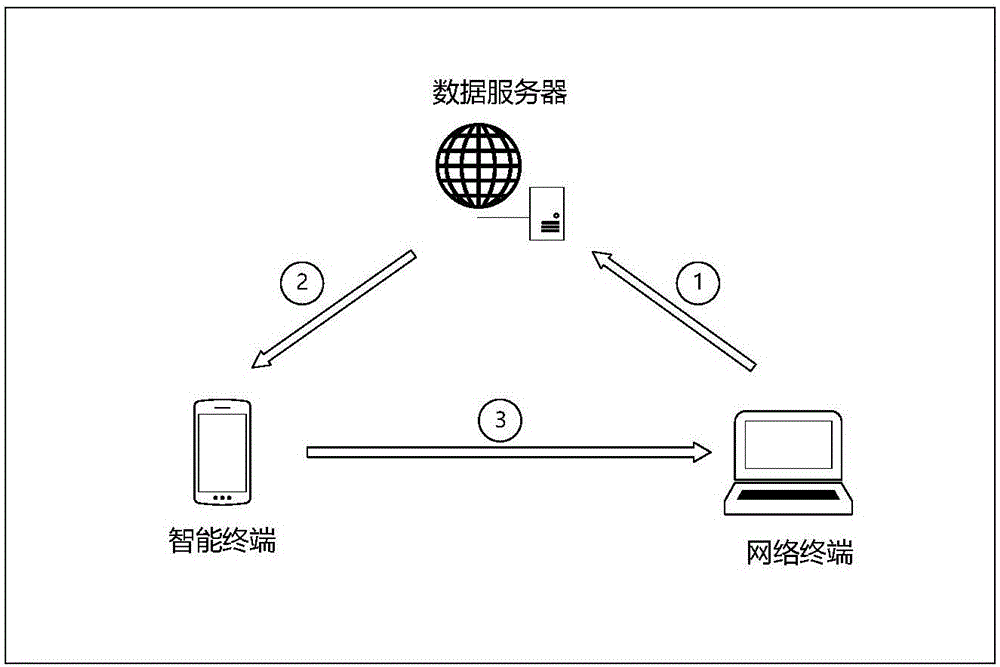
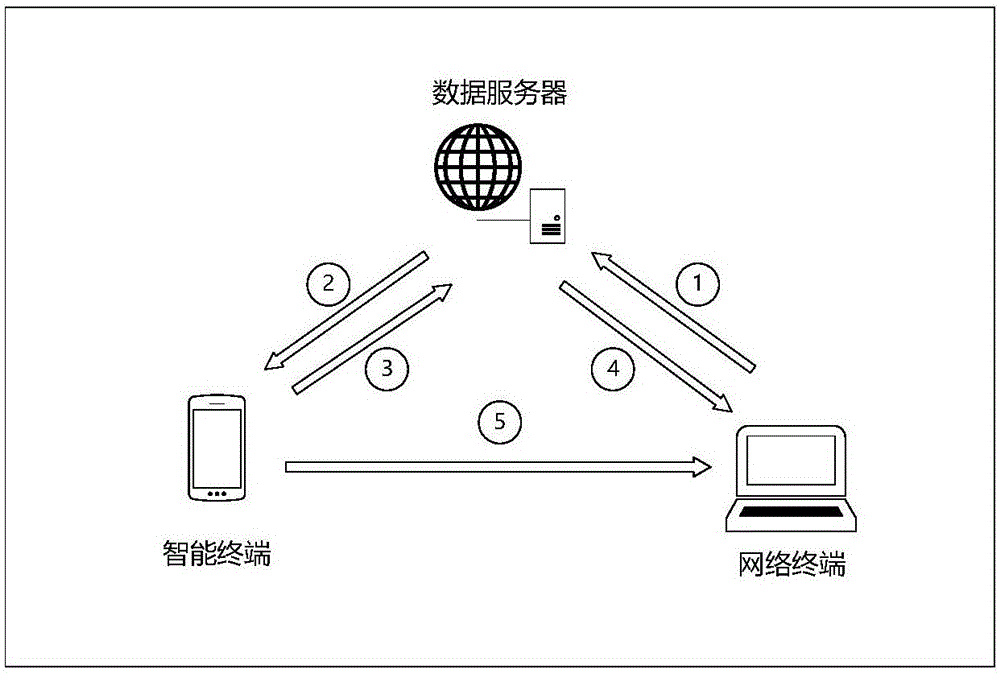
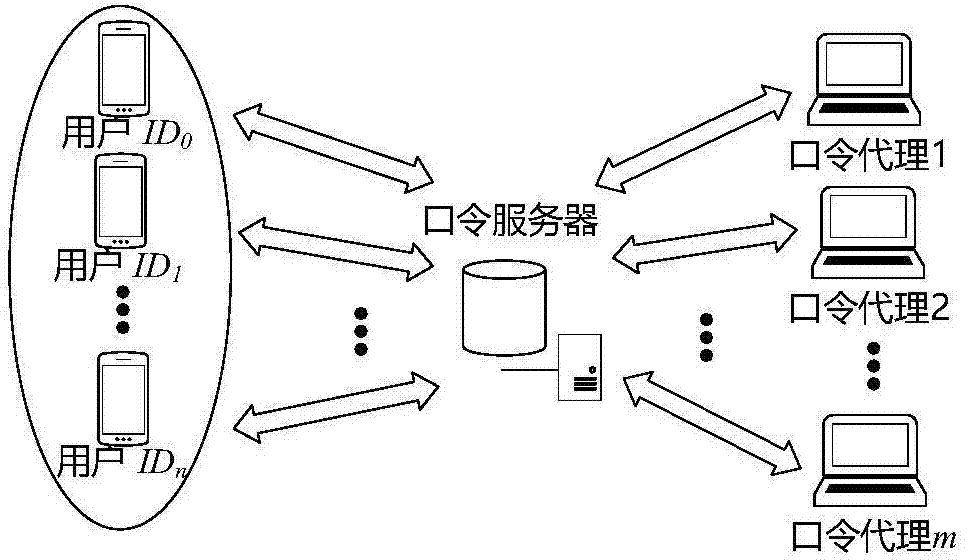
The invention discloses an establishing and operation method for a portable smart password management system. The operation steps comprise 1, registering a system account; 2, generating digital certificate information; 3, transmitting the digital certificate information; 4, generating a master password and inputting user personal information; 5, carrying out secret sharing on the user master password; 6, storing password information in a database; 7, verifying integrity of database information; 8, logging in the system account at a network terminal; 9, recovering the password information from the database; 10, synchronizing the password information to the network terminal; 11, finishing automatic login operation by the network terminal; 12, authorizing other users, thereby enabling the other users to use the password information; 13, inputting the personal information to initiate password finding operation; 14, judging a user identity and recovering the user master password; and 15, modifying a social relationship attribute. According to the method, the password management efficiency is clearly improved, the convenient degree of using the password by the user is increased, the security of the password is improved, and the method has popularization prospect.
Owner:BEIHANG UNIV
Method for establishing and operating intelligent portable password management system
ActiveCN107359998AShorten the timeSimplify traditional login behaviorKey distribution for secure communicationUser identity/authority verificationSecret shareManagement efficiency
The invention discloses a method for establishing and operating an intelligent portable password management system. The method includes the following steps: 1. three types of entities establishing communication channels; 2. a user registering a system account; 3. preparing local password management; 4. the user adding website record; 5. a password management device encrypting a database and generating a message verification code; 6. computing a master password secret sharing portions; 7. encrypting a secrete share and distributively saving secret shares; 8. the user verifying identities from the server; 9. the password management device proves that the operation environment is not changed; 10. the user authorizing an agent usage account; 11. the agent automatically logging in a target website; 12. the user authorizing other users to user his / her account; 13. the user activating an updated password management device; 14. the user initiating the restoration of a password request; 15. the user's mobile phone restoring the information as required by the password; and 16. the user restoring the master password and a website password. According to the invention, the method herein increases password management efficiency, makes password usage much easier, improves password safety, and has great marketing potential.
Owner:BEIHANG UNIV
Virtual machine static measurement method and device based on built-in security architecture
ActiveCN111638936AImprove securityEnsure safetySoftware simulation/interpretation/emulationVirtualizationSecurity measurement
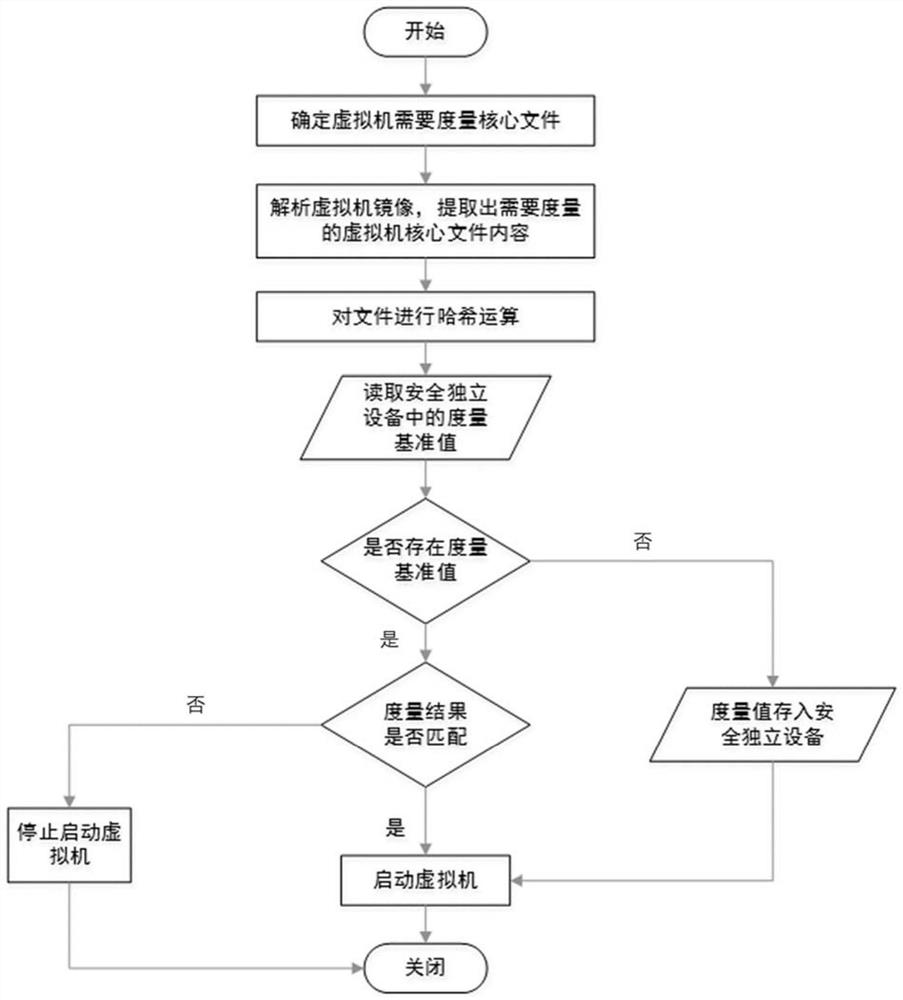
The invention relates to a virtual machine static measurement method and device based on a built-in safe architecture. The method comprises the steps of in the starting process of a physical host, enabling safe independent equipment to carry out safety measurement on a host machine system and virtualization software to ensure credibility of the host machine system and the virtualization software;enabling the host machine system and the virtualization software to determine a to-be-measured virtual machine core file; analyzing the virtual machine mirror image file, extracting the content of theto-be-measured virtual machine core file, performing security measurement on the content, and generating a measurement value; if judging that the virtual machine is started for the first time, indicating that the metric value serves as a reference value to be stored in the safe independent equipment, and the virtual machine is started; and if judging that the virtual machine is not started for the first time, verifying the metric value and a reference value in the safe independent equipment, cancelling starting of the virtual machine if verification fails, and starting the virtual machine ifverification succeeds. According to the invention, the extension of the static measurement mechanism of the virtual machine to the virtual machine can be realized, and the security of the virtual machine is enhanced.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Distributed processing-based urban intelligent traffic guidance system
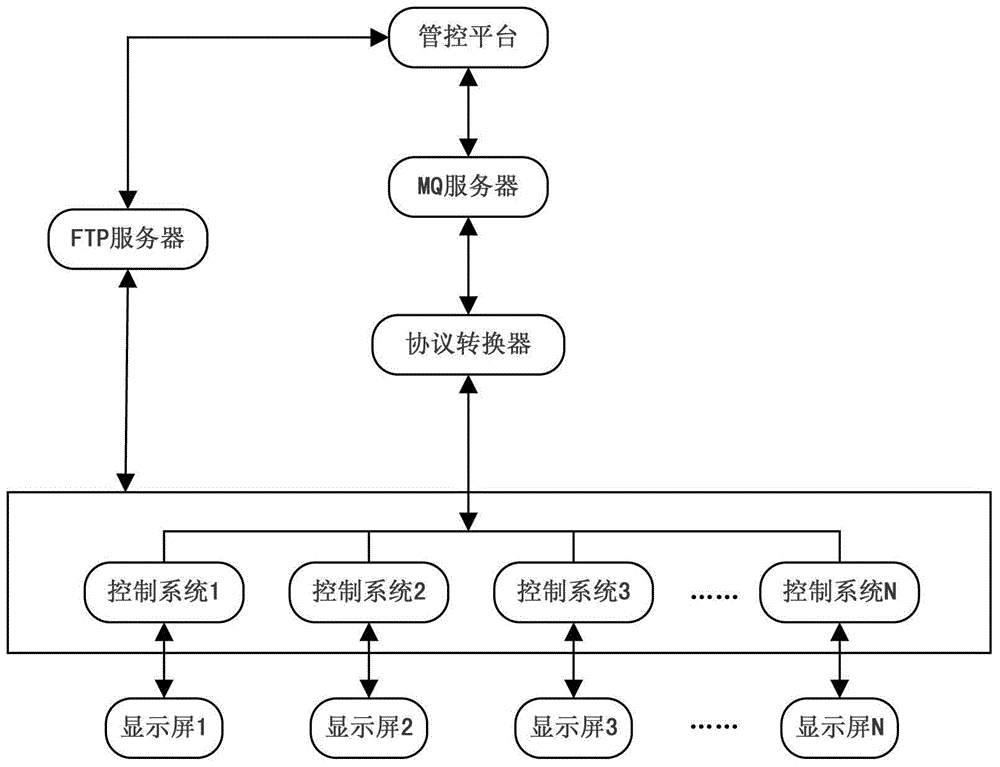
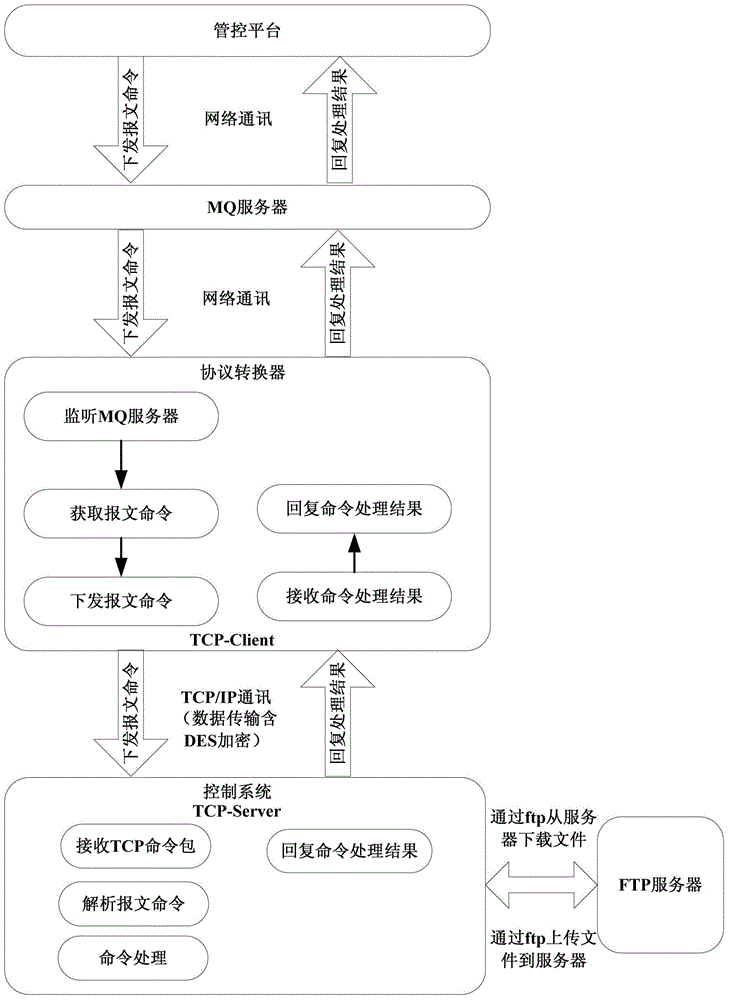
ActiveCN104616512AGuaranteed storage securityGuaranteed normal transmissionArrangements for variable traffic instructionsTransmissionGuidance systemExtensibility
The invention provides a distributed processing-based urban intelligent traffic guidance system. The system comprises a management and control platform, an MQ (Message Queue) server, a protocol converter, an FTP (File Transfer Protocol) server, a control system and a display screen. According to the distributed processing-based urban intelligent traffic guidance system, full support of display screen program editing, management and play can be realized aiming at different industry information, the entire system is designed to be an open modularized structure; the system has a powerful network control function, the display control system has good network communication, remote control and self-detection performance and can realize automatic control and remote network control and display network information; the distributed system layout can realize quicker user connection of a resource, the extensibility is improved, and the safe storage and transmission of the information are guaranteed.
Owner:JIANGSU GENTURE ELECTRONICS INFORMATION SERVICE CO LTD
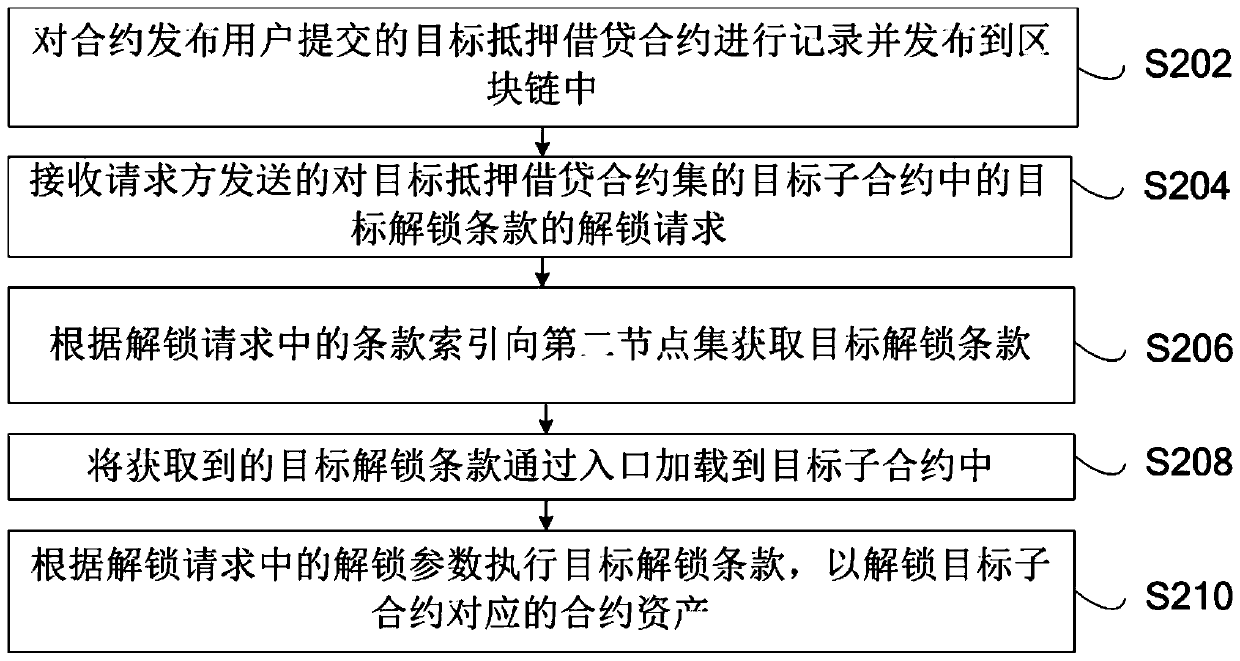
Block chain-based mortgage borrowing method and system, storage medium and computing device
PendingCN111415251AReduce sync pressureGuaranteed storage securityFinancePayment protocolsComputer networkEngineering
The invention relates to a block chain-based mortgage borrowing method, which is applied to a node of a first node set, and is used for recording a target mortgage borrowing contract submitted by a contract publishing user and publishing the target mortgage borrowing contract into a block chain. The target mortgage loan contract comprises at least one sub-contract; the sub-contract comprises at least one term index corresponding to an unlocking term for unlocking the contract asset, and an entrance for loading the unlocking term; an unlocking request for the target unlocking clause sent by therequester is received; a target unlocking term is obtained from the second node set according to the term index in the unlocking request; the obtained target unlocking clause is loaded into the target sub-contract through the entrance; and the target unlocking clause is executed according to the unlocking parameter in the unlocking request so as to unlock the contract asset corresponding to the target sub-contract. The block chain-based mortgage borrowing method provided by the invention can reduce the node synchronization pressure. The invention further provides a block chain-based mortgageborrowing system, a computer readable storage medium and computing equipment.
Owner:杭州时戳信息科技有限公司
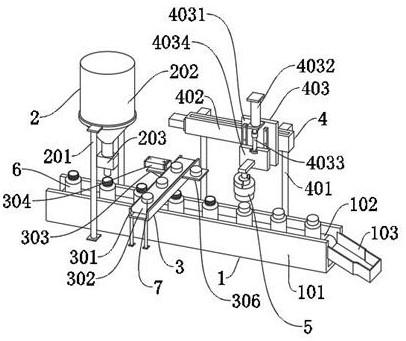
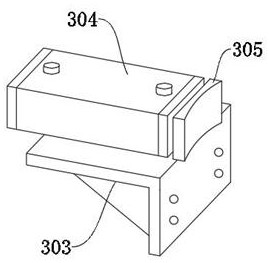
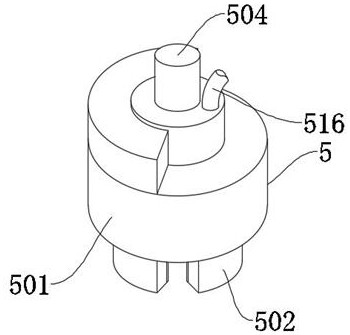
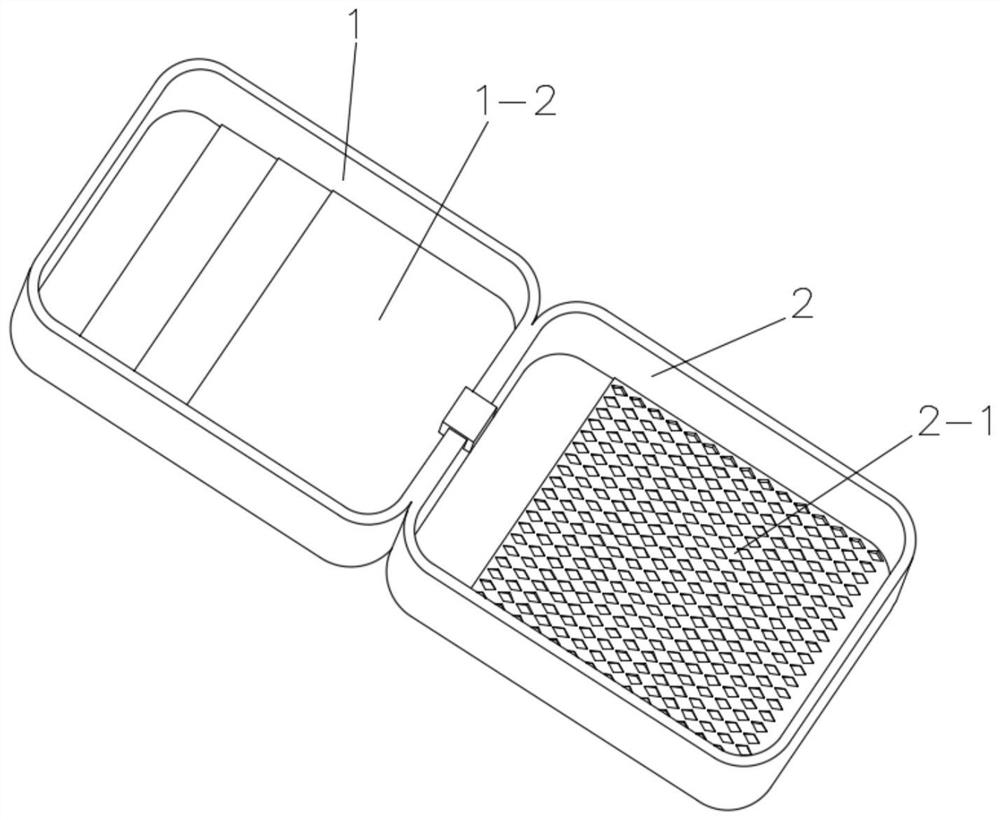
Traditional Chinese medicine tablet filling device
ActiveCN112960201AGuaranteed storage securityImprove work efficiencyCapsThreaded caps applicationEngineeringTraditional Chinese medicine
The invention relates to the technical field of traditional Chinese medicine processing, in particular to a traditional Chinese medicine tablet filling device which comprises an X-axis conveying mechanism, a filling mechanism, medicine bottles and bottle caps, wherein the filling mechanism and a Z-axis conveying mechanism are installed above the X-axis conveying mechanism; the filling mechanism comprises a first supporting frame, and a tablet tank is fixed to the top end of the first supporting frame; a solenoid valve is fixed to the bottom end of the tablet tank, and the Z-axis conveying mechanism comprises a second supporting box; a second conveyor belt is movably connected to the interior of the second supporting box, and the bottle caps are evenly distributed on the second supporting box; an X-axis driving mechanism is arranged behind the right side of the Z-axis conveying mechanism, and comprises a second supporting frame; and an X-axis sliding table is fixed to the top end of the second supporting frame, and the front end of the X-axis sliding table is slidably connected with a Y-axis driving mechanism. According to the filling device, a screw cap and sealing detection integrated structure is adopted, therefore the sealing detection can be carried out while the caps are sealed, and the storage safety of tablets is ensured.
Owner:烟台康骨堂医药科技有限公司
Gas pressure measuring device with high safety factor and using method of gas pressure measuring device
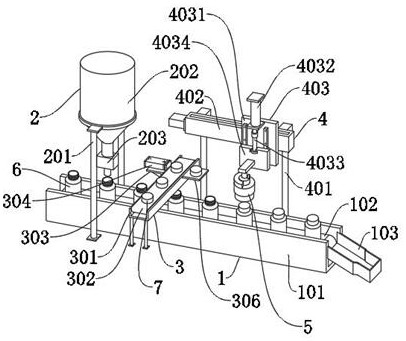
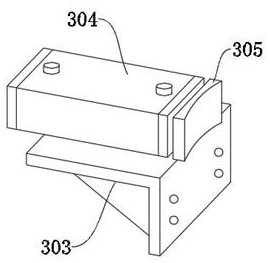
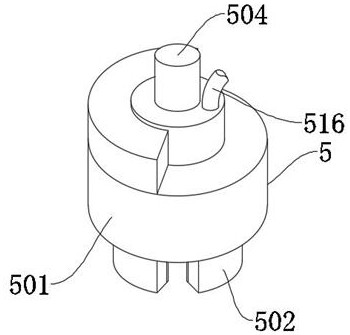
InactiveCN110566185AImprove support stabilityGood for adsorption and retentionSurveyFluid removalData displayProduct gas
The invention provides a gas pressure measuring device with high safety factor. The gas pressure measuring device comprises a gas pressure measuring sensor, a gas storage tank, a measuring data display screen, an exhaust pipe, a gas-pressure meter, a first flanged connecting pipeline, a gas-water separator, a valved drainage pipe, a second flanged connecting pipeline, a third flanged connecting pipeline, a suction pump, an adjustable fixed installation gas pipeline supporting frame, a detachable clearing core structure capable of adsorbing impurities, an explosion-proof auxiliary gas dischargestructure, a gas sampling to-be-inspected bottle structure capable of taking and putting and an explosion-proof auxiliary protective barrel structure. According to the gas pressure measuring device,a metal soft guide pipe, a cone-shaped suction pipe and an eduction pipe are arranged, self bending is advantageously adjusted according to the bending degree of a drilled hole, gas water can be conveniently sucked out, and the smooth progress of the gas pressure measurement work is ensured.
Owner:NORTH CHINA INST OF SCI & TECH
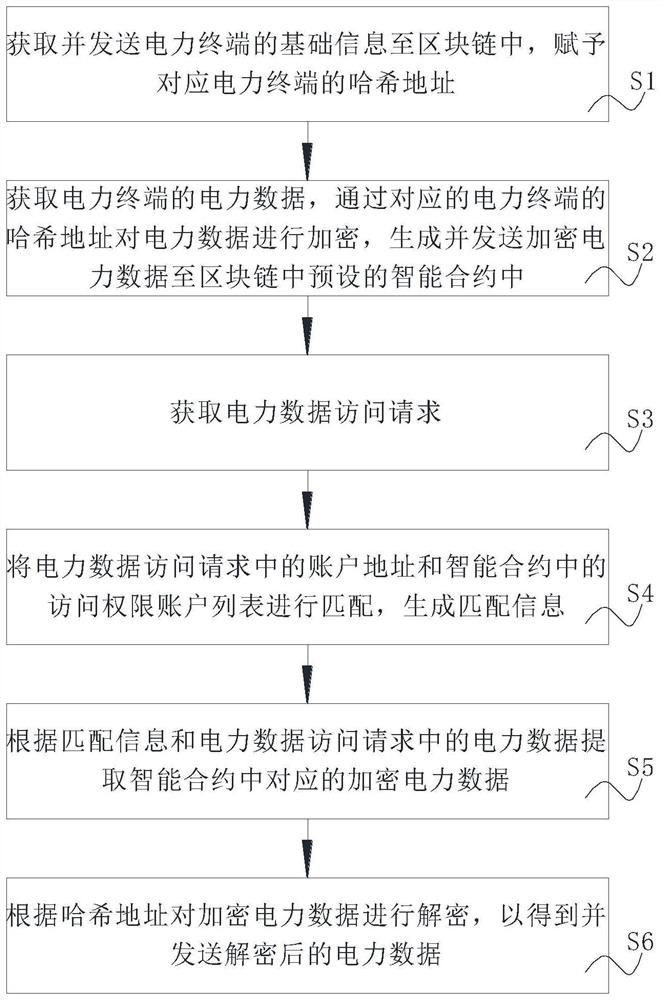
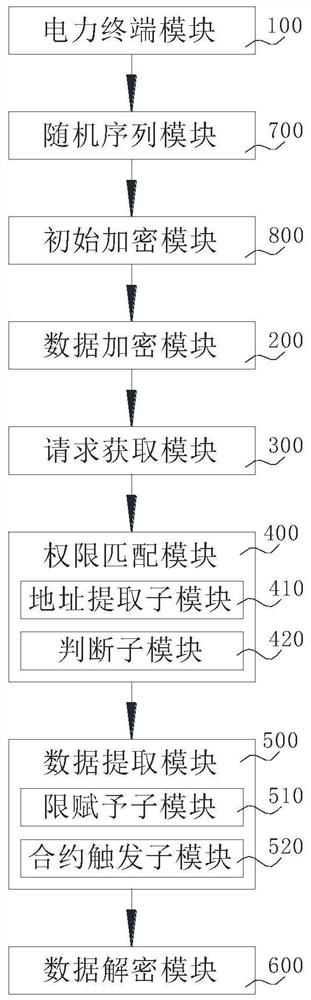
Power data management method and system based on blockchain smart contract
InactiveCN112926985ASafe and effective managementGuaranteed storage securityPayment protocolsInformation technology support systemComputer networkData access
The invention discloses an power data management method based on a blockchain smart contract, and the method comprises the following steps: obtaining and transmitting basic information of a power terminal to a blockchain, and endowing the corresponding power terminal with a hash address; encrypting the power data through the hash address of the corresponding power terminal, and generating and sending the encrypted power data to a preset smart contract in the blockchain; acquiring a power data access request; matching the account address with an access permission account list in the smart contract to generate matching information; extracting corresponding encrypted power data in the smart contract according to the matching information and the power data in the power data access request; and decrypting the encrypted power data according to the hash address. The invention relates to the technical field of power management. The invention further discloses a power data management system based on the blockchain smart contract. The power data is safely and effectively managed based on the intelligent contract, and the management requirement of the power data is met.
Owner:上海和数软件有限公司 +1
Cost management and control system based on collaborative office platform
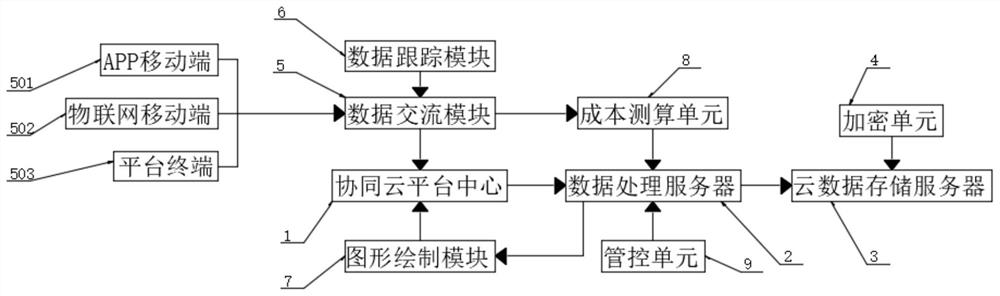
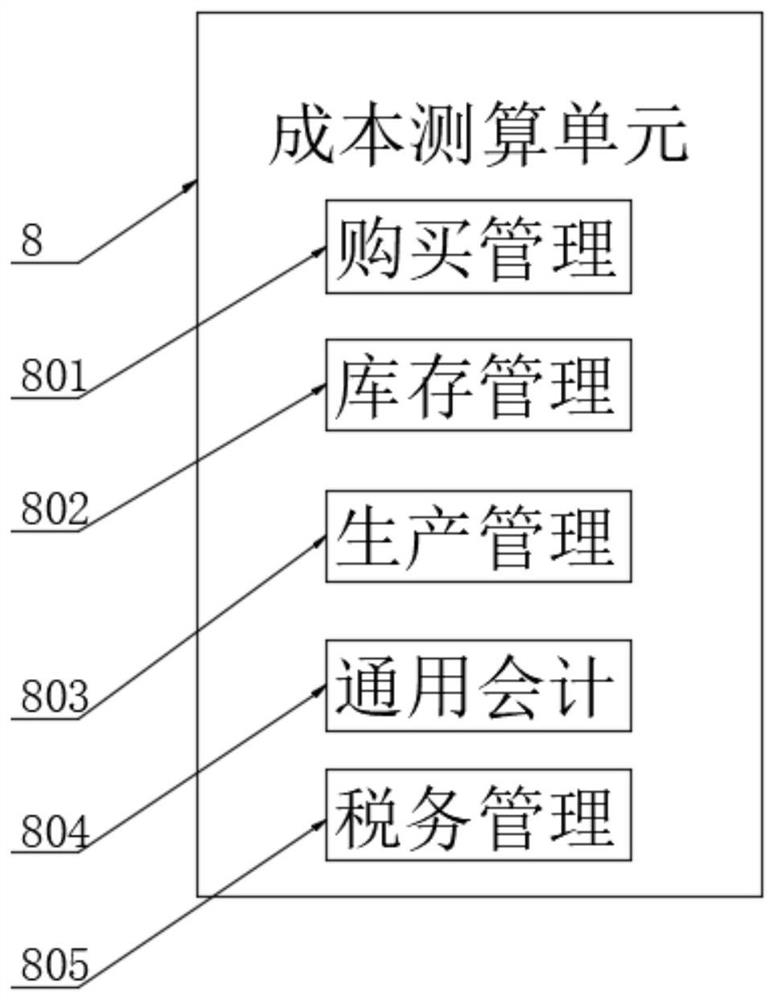
PendingCN112633818AEnsure safetyImprove cost control abilityOffice automationPlatform integrity maintainanceGraphicsControl system
The invention discloses a cost management and control system based on a collaborative office platform, and belongs to the technical field of collaborative office. The system comprises a collaborative flat holder center, wherein the input end of the collaborative flat holder center is connected with a data communication module and a graph drawing module, and the output end of the data communication module is connected with a cost calculation unit; and the cost calculation unit is connected with a data processing server. According to the invention, the dynamic cost rate is compared through the analysis strategy provided by the analysis strategy module, and when the cost rate reaches the early warning value, the dynamic cost early warning is started, so the platform office data can be updated and traced in real time through the data communication module and the data tracking module; and the data can be gathered and stored by cooperating with the cloud platform center, so the instantaneity and security of data communication are ensured, the cost management and control capability of multi-platform office can be improved by the management and control unit and the cost measurement and calculation unit, and the overall management and control requirements are met.
Owner:易筑网络科技(苏州)有限公司
Big data analysis method based on Internet of Things
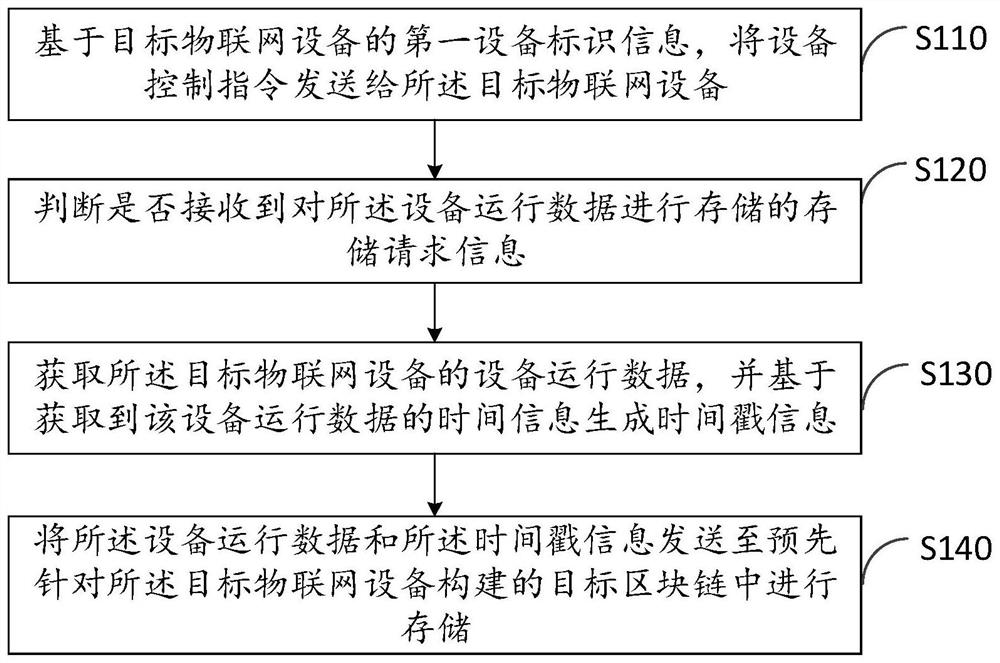
ActiveCN113518072AGuaranteed storage securityImproved safety is lowUser identity/authority verificationTotal factory controlTime informationTimestamp
The invention provides a big data analysis method based on the Internet of Things, and relates to the technical field of the Internet of Things. In the application, the method comprises the steps of: firstly, based on first device identification information of a target Internet-of-Things equipment, sending a device control instruction to the target Internet-of-Things equipment, and enabling a device operation program installed on the target Internet-of-Things equipment to operate according to the device control instruction to generate device operation data; secondly, judging whether storage request information for storing the equipment operation data is received or not; then, if the storage request information is received, obtaining the equipment operation data of the target Internet-of-Things equipment, and generating timestamp information based on the time information of obtaining the equipment operation data; and finally, sending the device operation data and the timestamp information to a target block chain pre-constructed for the target Internet of Things device for storage. Based on the method, the problem that in the prior art, the security of data storage is low can be solved.
Owner:中乾思创(北京)科技有限公司
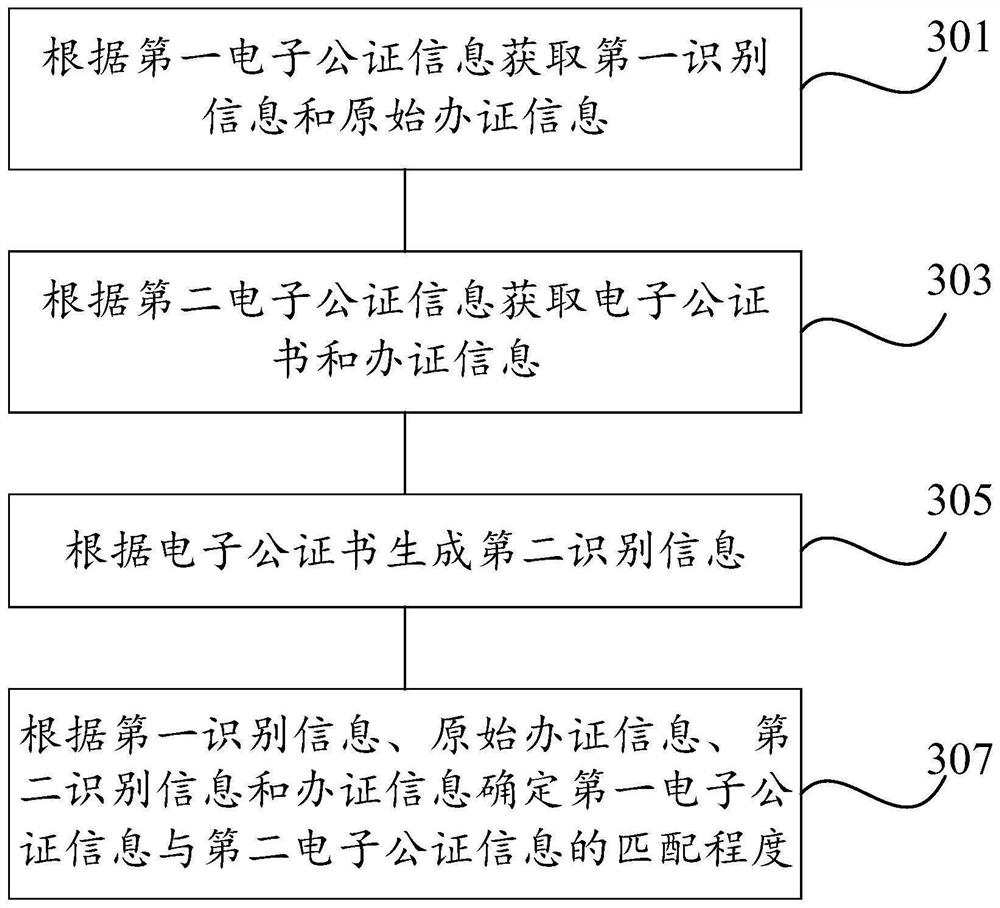
Electronic notarization information processing method, device and system, equipment and storage medium
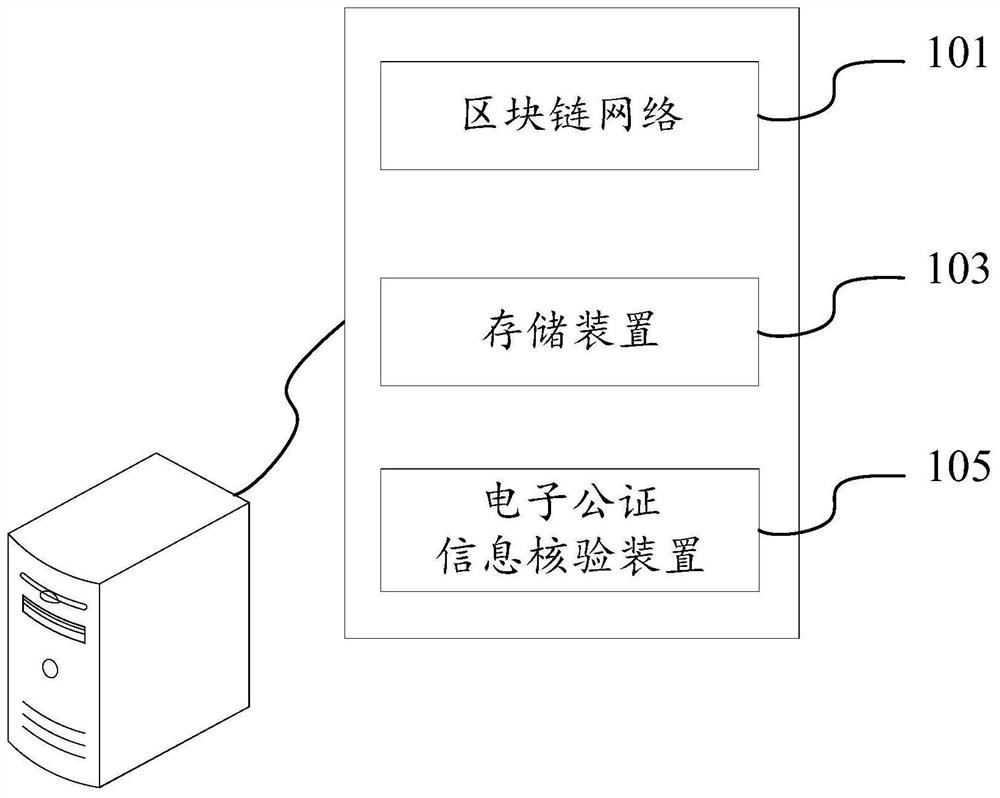
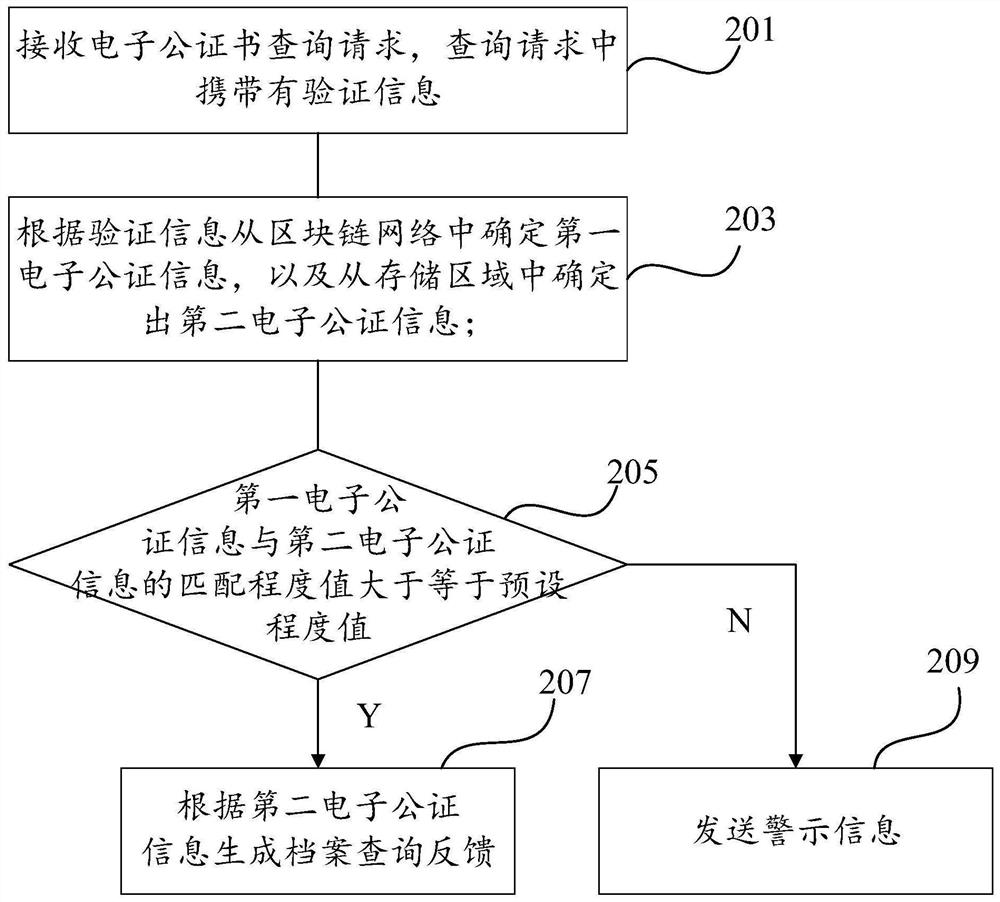
PendingCN112115423ANon-tamperableEasy extractionDigital data protectionProgram/content distribution protectionTamper resistanceInformation processing
The invention relates to the technical field of electronic data processing, in particular to an electronic notarization information processing method, device, system and equipment and a storage medium, and the method comprises the steps: receiving an electronic notarization query request which carries verification information; determining first electronic notarization information from a blockchainnetwork according to the verification information, and determining second electronic notarization information from a storage area; and if the matching degree of the first electronic notarization information and the second electronic notarization information is greater than or equal to a preset degree value, generating file query feedback according to the second electronic notarization information. Original electronic notarization information is stored in a block chain network and a storage area respectively, data in a block chain cannot be tampered, and the data in the storage area is convenient to extract; when the electronic notarization is inquired, the electronic notarization is extracted from the two previous storage paths according to the verification information, so that the electronic notarization is convenient to inquire, and the storage safety, tamper resistance and legality of the electronic notarization are ensured.
Owner:法信公证云(厦门)科技有限公司
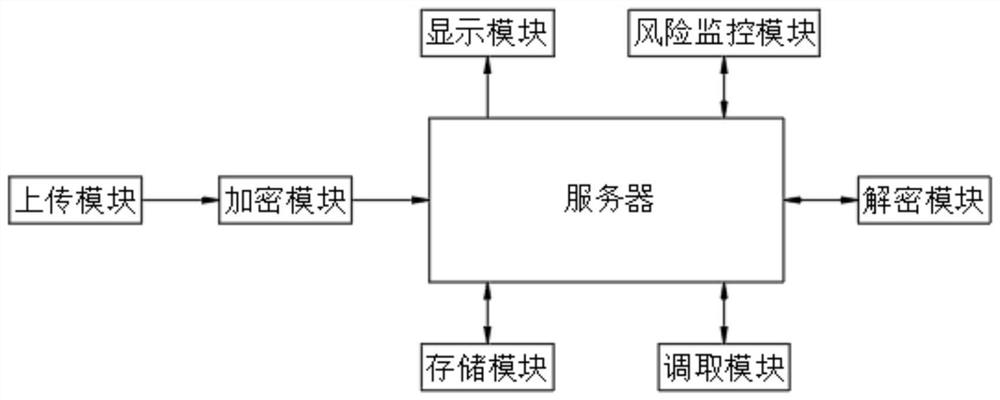
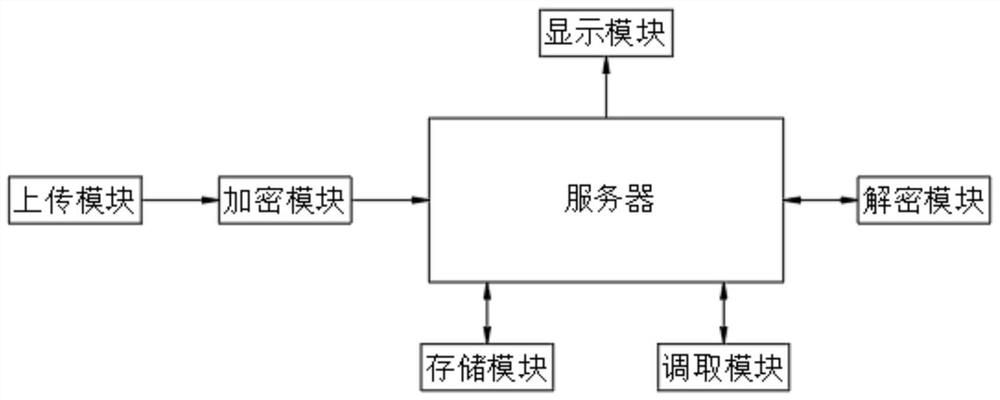
Electronic bidding document multilayer encryption and decryption system for electronic bidding
PendingCN114386077AGuaranteed storage securityImprove securityDigital data protectionEngineeringEncryption
The invention belongs to the field of electronic bidding, relates to a data encryption technology, and is used for solving the problems that an encryption and decryption system for an electronic bidding document does not have a function of carrying out integral defense encryption on all encrypted files, the storage modes of a calling code and a secret key are the same, and the difficulty is very small when a hacker cracks the encryption and decryption system. The electronic bidding document multilayer encryption and decryption system comprises a server, the server is in communication connection with an encryption module, a decryption module, a storage module, a calling module and a risk monitoring module, and the encryption module is in communication connection with an uploading module; parameters of the encrypted files are analyzed through the encryption module, the calling codes are generated, the encrypted files are stored in the storage module, the calling codes need to be input through the calling module when the files are extracted, and the calling codes of all the encrypted files in the storage module can form an integral defense wall. And all encrypted files in the storage module can be defended and protected.
Owner:山东标书易信息技术有限公司
Microcontroller object code protection method and system
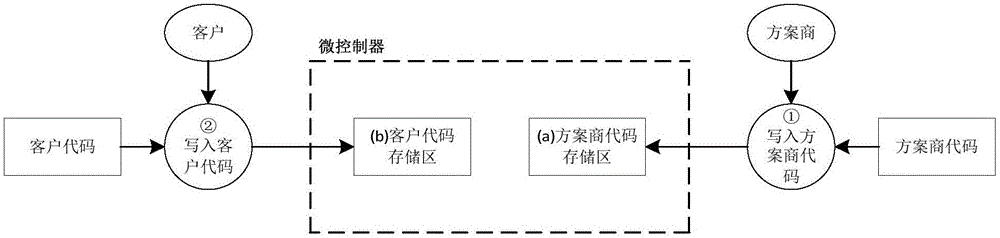
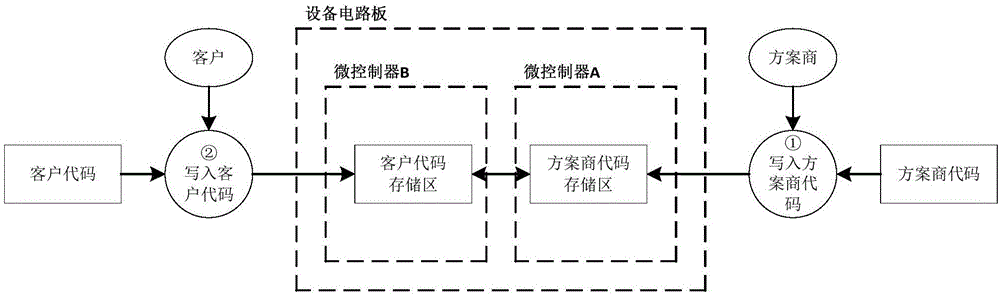
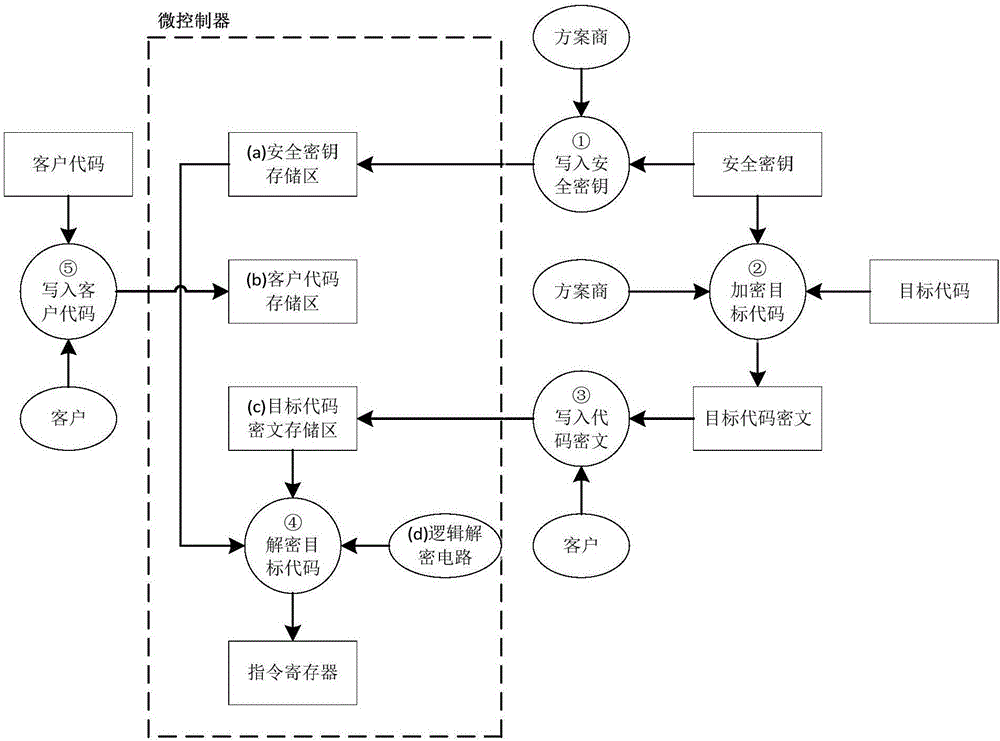
InactiveCN107181593AGuaranteed confidentialityLow cost to manufacture and useKey distribution for secure communicationProgram/content distribution protectionMicrocontrollerConfidentiality
The invention relates to the technical field of microcontroller encryption and, specifically, to a microcontroller object code protection method and system for protecting an object code of an IP supplier. The storage space in a microcontroller is divided into a secure key storage area, an object code ciphertext storage area and a customer code storage area for respectively storing a secure key, an object code ciphertext and a customer code, and the IP supplier encrypts an object code required to be protected by using a secure key and generates an object code ciphertext so that the object code ciphertext must be decrypted through a decryption module in the microcontroller when a program is running. In this way, the confidentiality of the object code is ensured, and the manufacturing and using costs are reduced as the write-in and upgrade processes of the object code ciphertext are operated by customers themselves.
Owner:SHANGHAI AISINOCHIP ELECTRONICS TECH
Self-service bill processing terminal and bill processing method thereof
ActiveCN110415460BSimple mechanical structureReliable mechanical structureTypewritersApparatus for meter-controlled dispensingTicketEmbedded system
In the self-service bill processing terminal and its bill processing method described in the present invention, execution information is input through an input module, and then converted into execution instructions by a main control chip circuit. The bill scanner scans the bills and displays them in the display module. The scanned bills fall into the bill temporary storage component, waiting for the user’s confirmation on the operation component side. The main control chip circuit commands the limit device to perform an opening action, takes out the bill through the bill exit window, and terminates the bill processing flow. If the bills in the bill temporary storage component are correct, the main control chip circuit sends an opening command to the baffle, the baffle opens, and the bills fall into the bill storage platform under the action of gravity for storage. The mechanical structure is simple and reliable. If the bill is found to be wrong, it can be taken out under the control of the user. After the bill is taken out, the bill processing process will be terminated immediately, so as to prevent the process from continuing and the paper bill from being damaged.
Owner:厦门商集网络科技有限责任公司
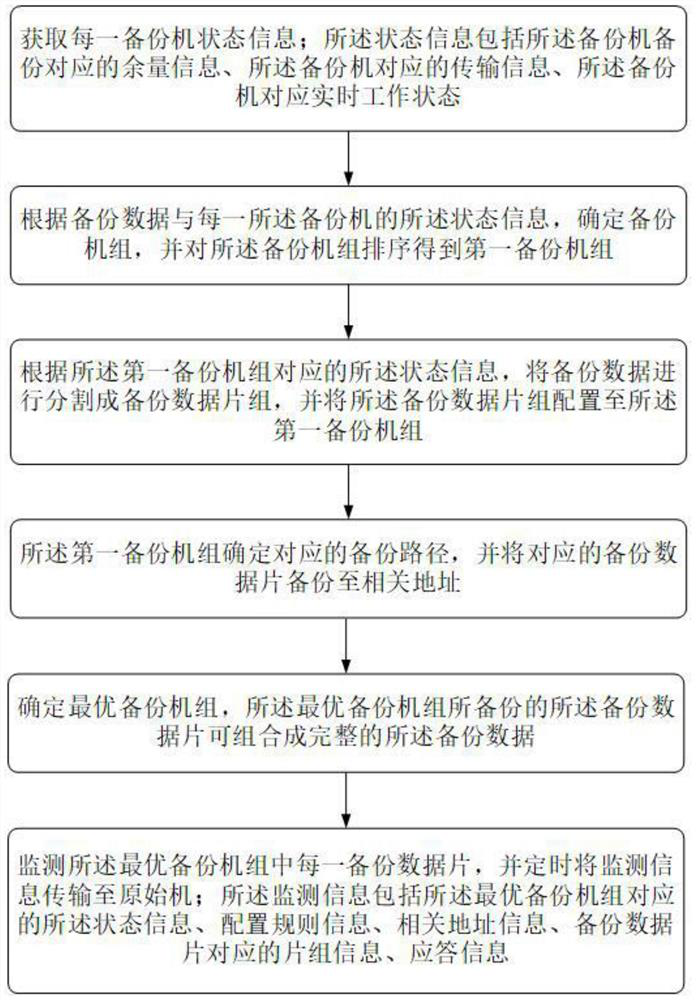
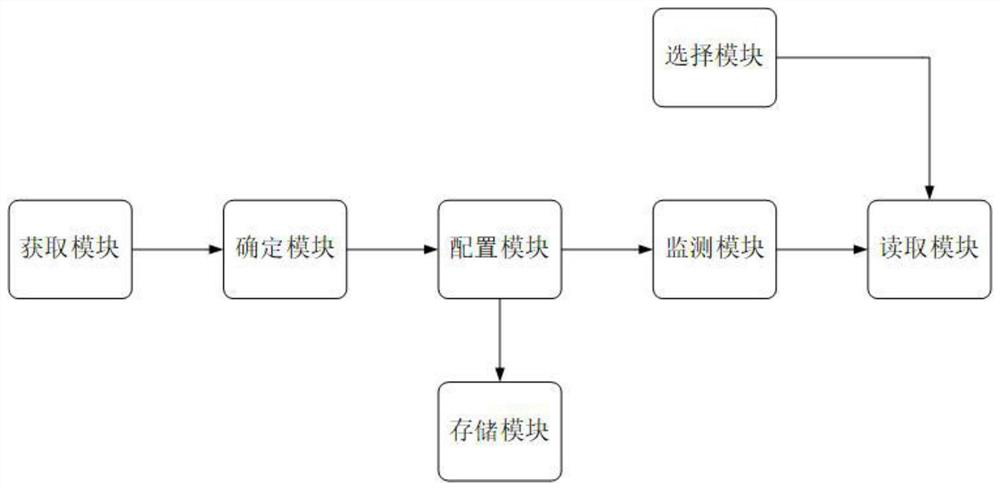
A computer backup data monitoring method and system
ActiveCN112685232BIntegrity guaranteedGuaranteed validityHardware monitoringRedundant operation error correctionStorage securityMonitoring methods
Owner:HENAN UNIVERSITY
File processing method and device, equipment and storage medium
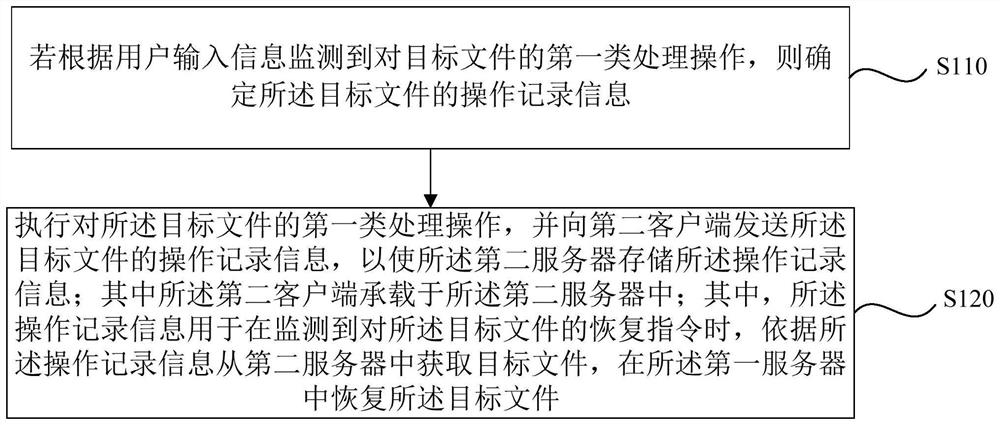
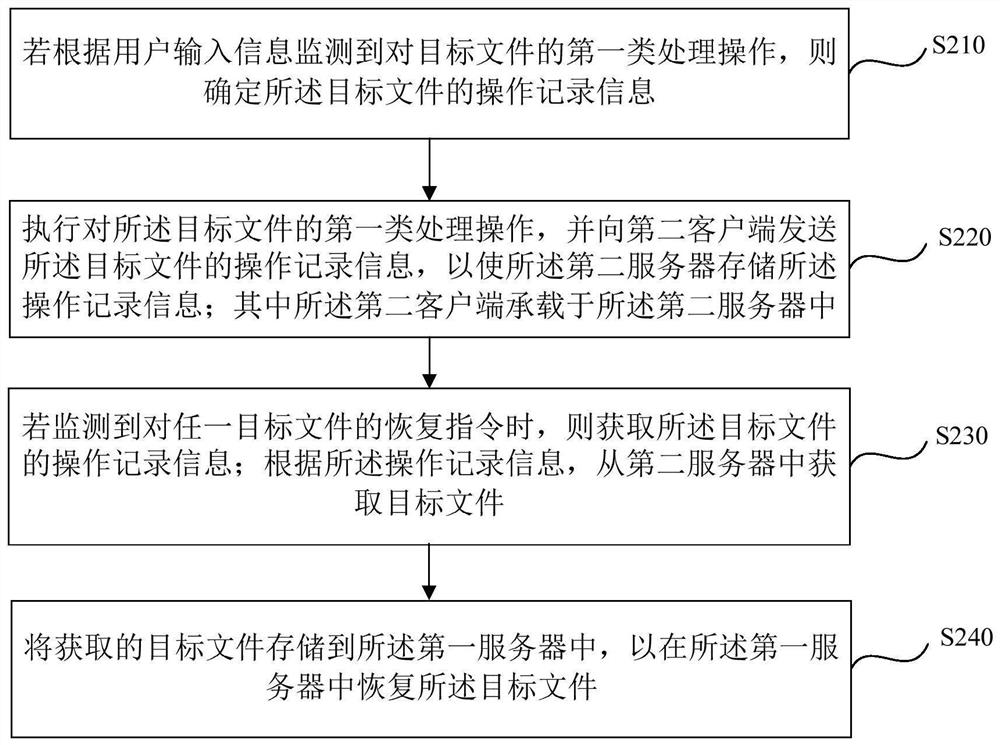
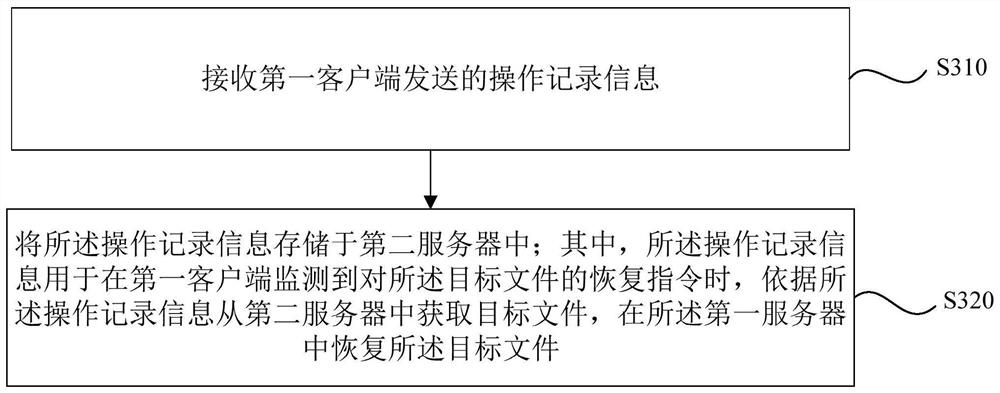
PendingCN113127261AAvoid deletionGuaranteed storage securityFile/folder operationsRedundant operation error correctionStorage securityUser input
The embodiment of the invention discloses a file processing method and device, equipment and a storage medium. The method is executed by a first client associated with a first server, and comprises the following steps: if a high-risk processing operation on a target file is monitored according to user input information, determining operation record information of the target file; executing a high-risk processing operation on the target file, and sending operation record information of the target file to a second client, so that a second server stores the operation record information, wherein the operation record information is used for acquiring the target file from the second server according to the operation record information when a recovery instruction for the target file is monitored, and recovering the target file in the first server. According to the embodiment of the invention, the target file can be recovered in a targeted manner according to the operation record information, and the operation record information is stored in the second server, so that the situation that the operation record information is deleted due to misoperation of the first client can be avoided, and the storage security of the operation record information is ensured.
Owner:ZHEJIANG UNIVIEW TECH CO LTD
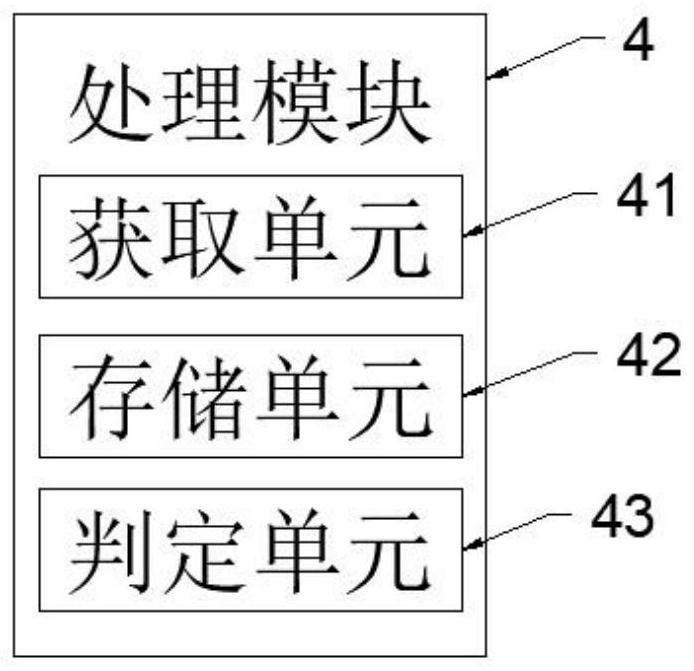
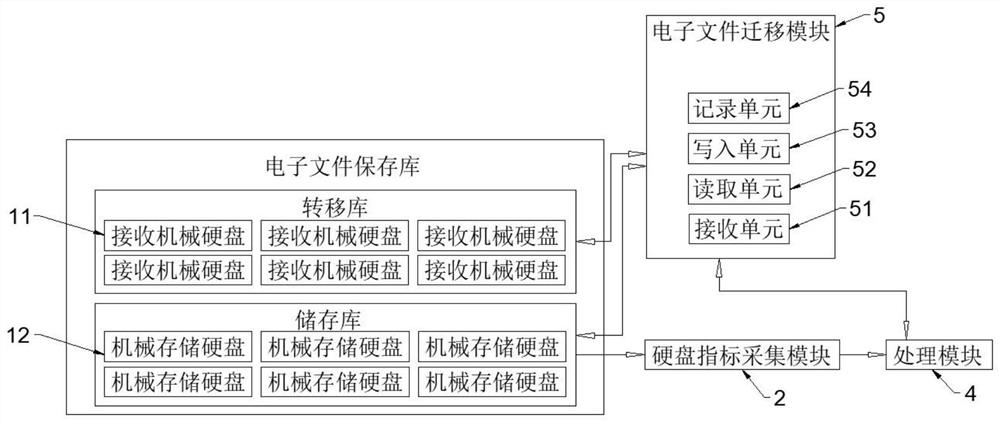
Electronic file long-term storage system
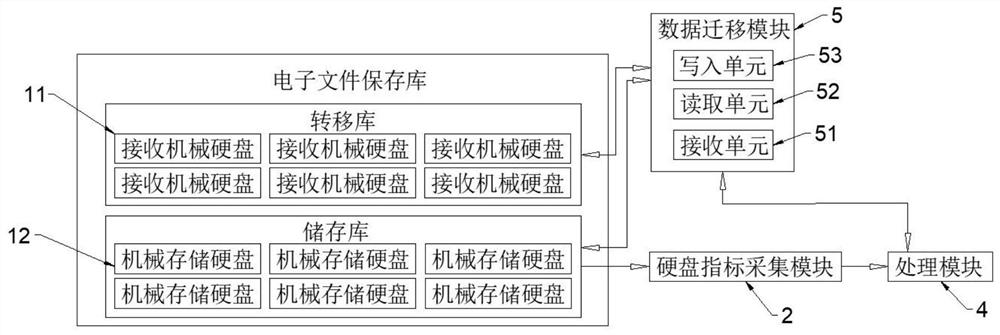
InactiveCN113608673AAvoid Storage Security ImpactsGuaranteed storage securityInput/output to record carriersComputer hardwareElectronic document
The invention provides an electronic file long-term storage system, and relates to the technical field of electronic file long-term storage. The electronic file long-term storage system comprises a mechanical storage hard disk, wherein the mechanical storage hard disk is used for storing electronic files; a hard disk index acquisition module used for acquiring operation indexes of the mechanical storage hard disk and sending the acquired operation indexes to the processing module; the processing module used for carrying out comparative analysis on the obtained operation index and a pre-stored critical value and judging whether an electronic document transfer instruction is generated or not; an electronic file migration module for reading the electronic file from the corresponding mechanical storage hard disk according to the electronic file migration instruction and migrating the electronic file into the receiving mechanical hard disk. By arranging the hard disk index acquisition module and the receiving mechanical hard disk, the system automatically transfers the corresponding electronic file in advance, so that the storage security of the electronic file is prevented from being influenced, the storage security of the electronic file is ensured, and the long-term storage of the electronic file is realized.
Owner:南京科海智博信息技术有限公司
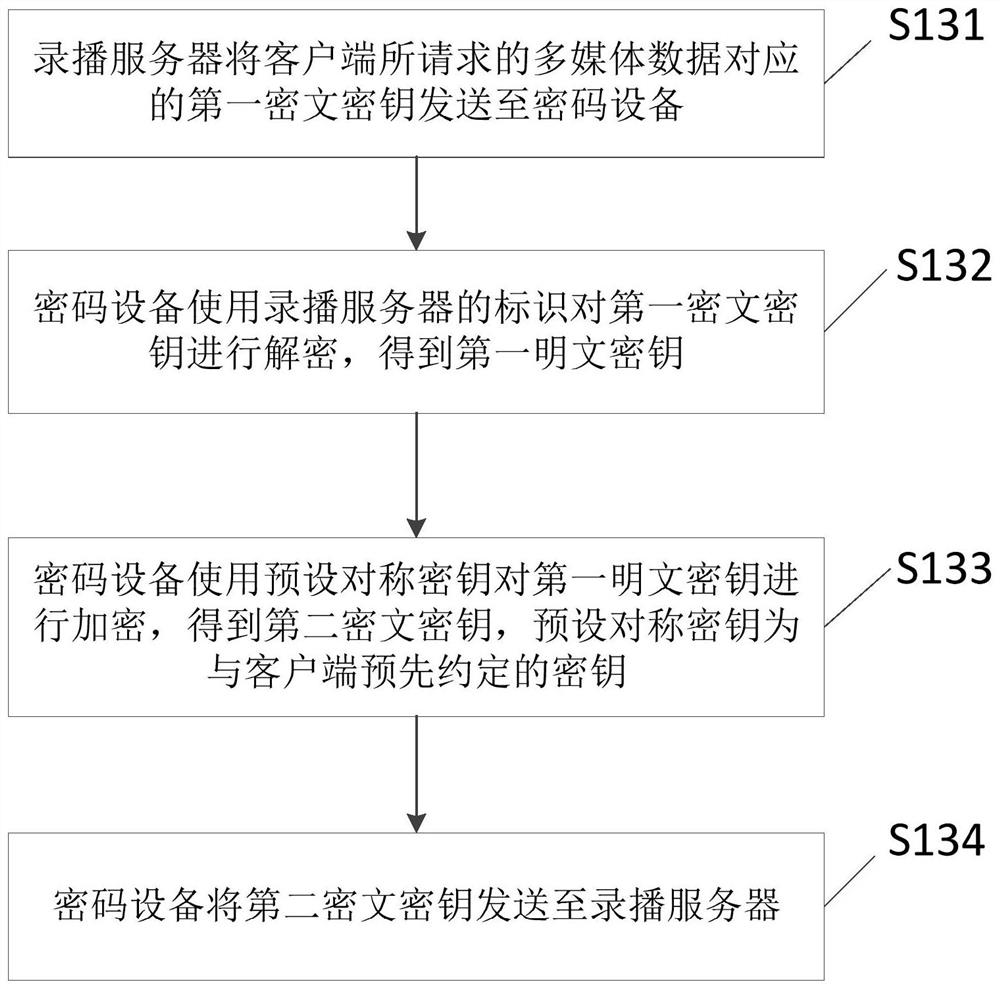
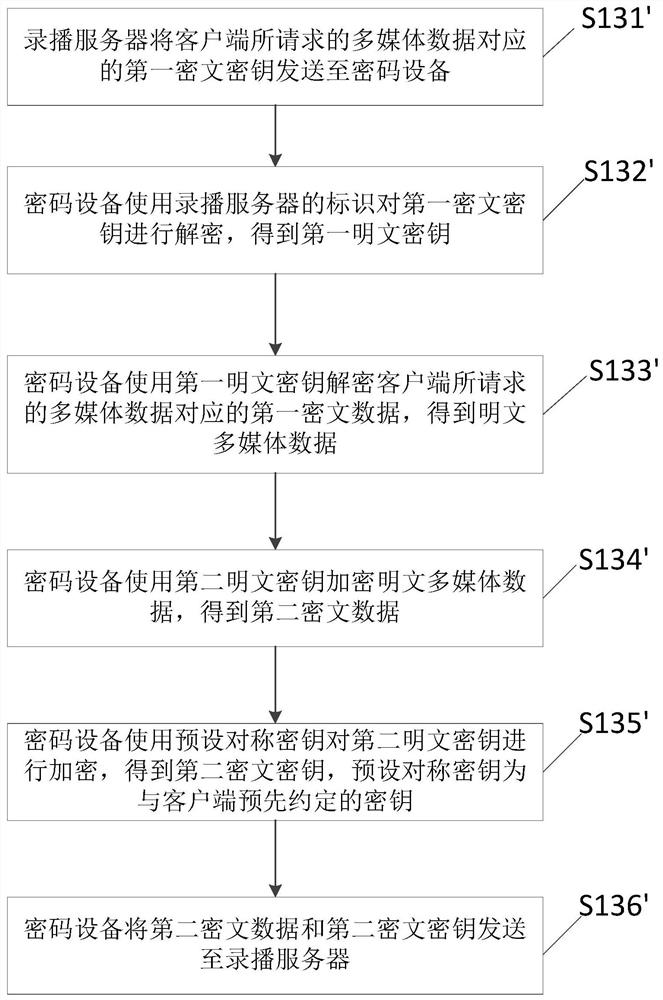
A recording and broadcasting data processing method and device
ActiveCN108768920BEnsure safetyNot easy to attackKey distribution for secure communicationEncryption apparatus with shift registers/memoriesPlaintextMan-in-the-middle attack
The present invention relates to the technical field of recording and broadcasting, and discloses a method and device for processing recording and broadcasting data. The method includes: a recording and broadcasting server receives a playback request from a client; the recording and broadcasting server determines the multimedia data requested by the client and its corresponding An encryption key, wherein the multimedia data stored by the recording and broadcasting server is ciphertext data encrypted by a cryptographic device, and the corresponding encryption key is a ciphertext key after being encrypted by a cryptographic device; the recording and broadcasting server calls the cryptographic device, Use the cryptographic device to perform secondary processing on the multimedia data requested by the client and its corresponding encryption key to obtain the secondary processed multimedia data and its corresponding encryption key; the recording and broadcasting server will process the secondary processed multimedia data sent to the client. During the transmission of recording and broadcasting data, the plain text does not land, ensuring the security of recording and broadcasting data during transmission, and is not easy to be attacked by a middleman.
Owner:SUZHOU KEDA TECH
Chinese herbal medicine tablet filling device
ActiveCN112960201BGuaranteed storage securityGuaranteed sealing performanceCapsThreaded caps applicationSolenoid valveTraditional medicine
Owner:烟台康骨堂医药科技有限公司
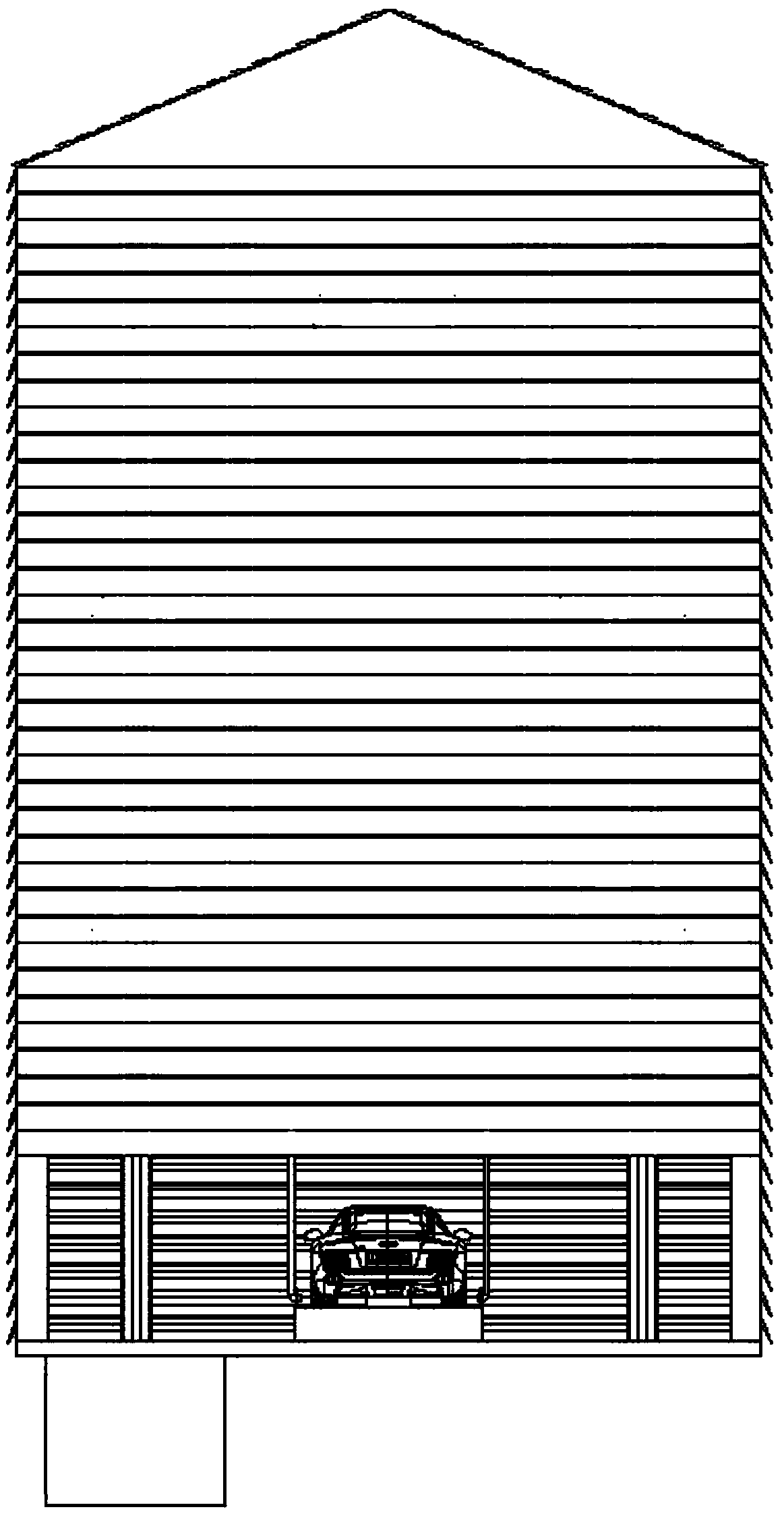
Self-balanced circulating mechanical parking system suitable for new-energy vehicle
InactiveCN109577709AEnsure driving safetyGuaranteed storage securityCharging stationsElectric vehicle charging technologyVehicle frameNew energy
The invention discloses a self-balanced circulating mechanical parking system suitable for new-energy vehicles and belongs to the field of new-energy vehicle parking equipment. The self-balanced circulating mechanical parking system comprises a support, charging interfaces, car carriers, electric rails A and electric rails B; the support is connected with the electric rails A and the electric rails B; the charge interfaces are respectively mounted at one sides of the car carriers, touches the electric rails A when moving to the mounting positions of the electric rails A along with the car carriers, and touches the electric rails B when moving to the mounting positions of the electric rails B along with the car carriers. Vertical contact groups are connected with balance motors, the balancemotors drive counter weights through lead screws to keep the car carriers balanced, horizontal contact groups are connected with sockets, and the new-energy vehicles can be charged through the sockets.
Owner:DALIAN NATIONALITIES UNIVERSITY
Park smart cloud all-purpose card platform system based on block chain technology
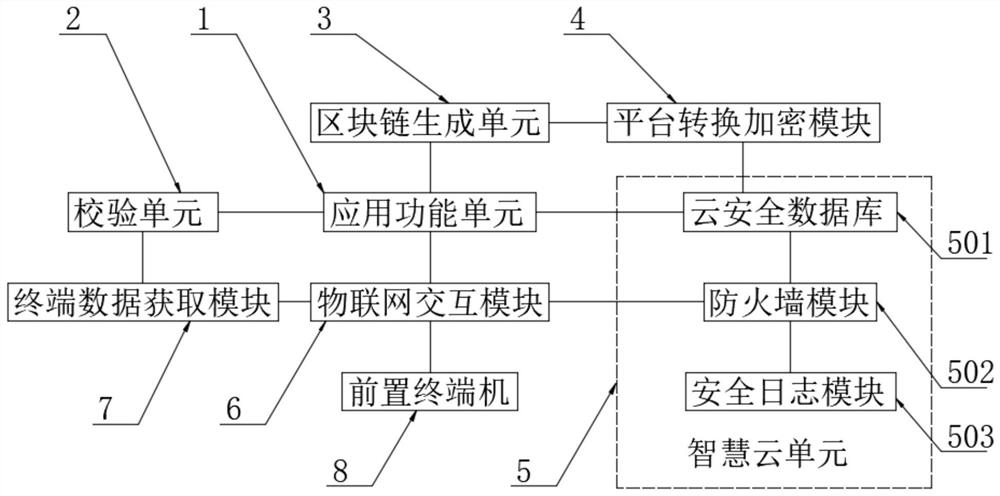
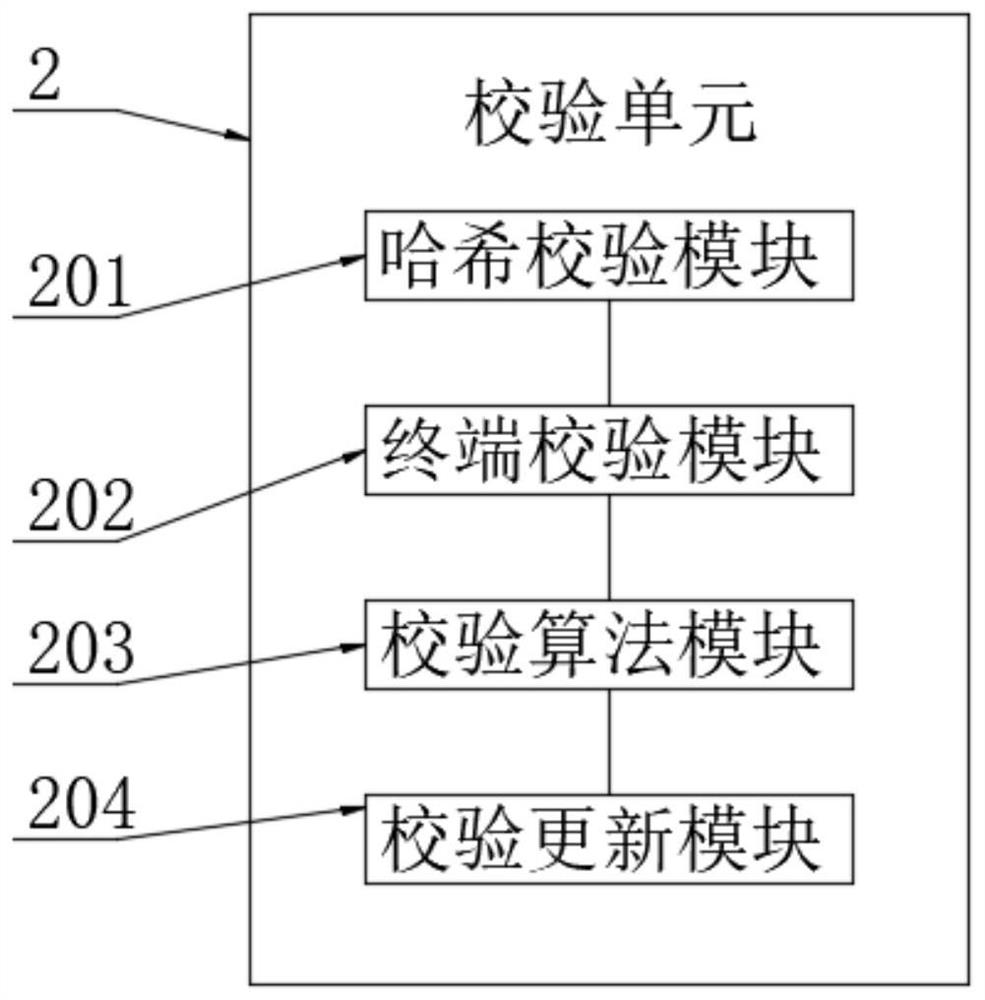
InactiveCN113489715ARealize full traceabilityImplement public lookupSecurity arrangementSecuring communicationThe InternetData acquisition
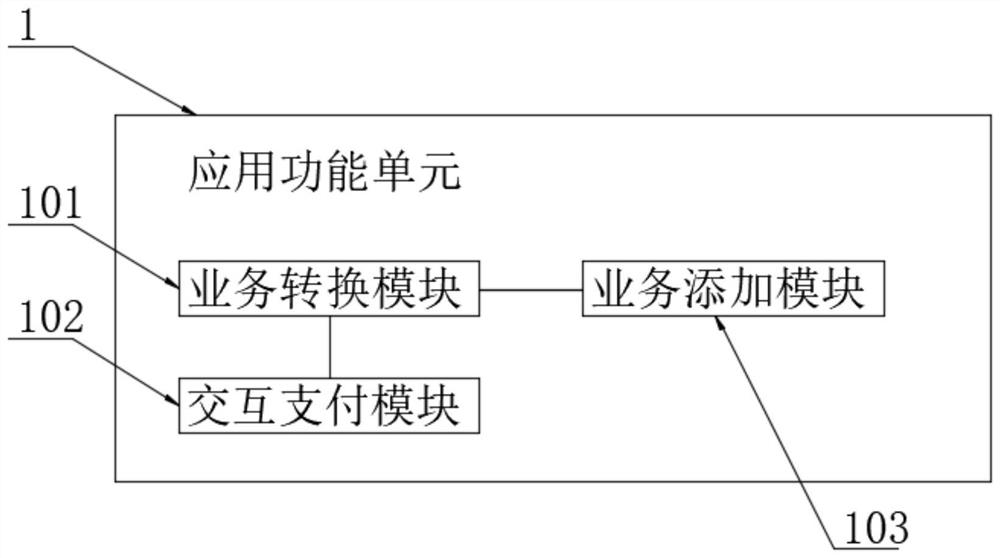
The invention discloses a park smart cloud all-purpose card platform system based on a block chain technology, and belongs to the technical field of campus all-purpose cards, and the system comprises an application function unit, the input end of the application function unit is in bidirectional connection with a verification unit, and the input end of the verification unit is connected with a terminal data acquisition module. The input end of the terminal data acquisition module is connected with an Internet of Things interaction module. According to the invention, the verification and comparison of the block chain data generated by the application function unit through the block chain generation unit can be realized through the Hash verification module of the verification unit, and the block chain sequencing processing is carried out on different applications of the application function unit after the verification; therefore, calibration processing of the Internet of Things interaction module and the front terminal at the blockchain level is facilitated, whole-course tracing and unforgeable public search of a data end are realized, and the data interaction processing capability of different terminal all-purpose card devices in a campus is remarkably improved.
Owner:北京金誉智能科技有限公司
Grain and oil storage device
PendingCN112027372AGuaranteed storage securityImprove storage securityDomestic cooling apparatusLighting and heating apparatusThermodynamicsDisplay device
The invention discloses a grain and oil storage device. The grain and oil storage device comprises a base, wherein a shell is arranged at the upper end of the base, a display is arranged at the outerside of the shell, a storage box is arranged in the shell and a heat insulation belt is arranged between the storage box and the shell; a conduction sheet is arranged in the storage box, and the conduction sheet is movably connected with the storage box in a matched manner; a sealing cover is arranged at the upper end of the shell, the sealing cover is movably connected with the shell in a matchedmanner, and a pressure relief opening is formed in the upper end of the sealing cover; an electric power storage device is arranged at one side of the shell, an oil inlet pipe is arranged at the upper end of the electric power storage device, one end of the oil inlet pipe communicates with the storage box, and a valve is arranged at the other end of the oil inlet pipe and electrically connected with the electric power storage device; a connecting element is arranged at one end, away from a driver, of the shell and fixedly connected with the shell, and a plurality of oil outlet pipes are arranged at the other end of the shell; and a constant temperature device is arranged at the upper end of the connecting element and is fixedly connected with the connecting element. The grain and oil storage device is good in heat insulation performance, capable of monitoring the internal temperature of equipment in real time and high in safety performance.
Owner:贵州四方粮油有限公司
Single-police first-aid kit
PendingCN113813112AEasy to useNo delay in first aidFirst-aid kitsEmergency kitsMechanical engineering
The invention discloses a single-police first-aid kit, which comprises a front kit body and a rear kit body; an accommodating bag with an upward opening is arranged on the front end surface of the front kit body; a fixed panel is detachably arranged on the back surface of the rear kit body; the two ends of the fixed panel are locked through buckles. The top of the fixed panel can be folded to the front end surface of the front kit body and covers the opening part of the accommodating bag; the bottom of the front kit body and the bottom of the rear kit body are sewn, and the front kit body and the rear kit body are opened and closed through a zipper; a whistle fixing part is arranged in the accommodating bag; and an external hanging system is arranged on the back of the fixed panel. According to the invention, the accommodating bag with the upward opening is arranged on the front end face of the front kit body, the whistle fixing part is arranged in the accommodating bag, use of police officers is facilitated, the detachable fixing panel is arranged, the kit body is taken down during first aid, use is very convenient, and the first aid opportunity cannot be delayed.
Owner:国家移民管理局常备力量第二总队
Antibacterial cleaning solution used for preventing and curing bedsores and preparation method thereof
The invention discloses an antibacterial cleaning solution used for preventing and curing bedsores. The antibacterial cleaning solution is characterized by consisting of the following components in proportion by 1000ml of the antibacterial cleaning solution: 2.5-10g of chlorhexidine or chlorhexidine salt, 1.5-4.5ml of organic acid, 50-100ml of propellant, 0.1-0.5ml of penetrant, 2.5-15ml of cationic surfactant, 2.5-5ml of zwitterionic surfactant, 5-10ml of nonionic surfactant and the balance deionized water. The invention further discloses a preparation method for the antibacterial cleaning solution. The antibacterial cleaning solution provided by the invention is safe and non-irritant, and the raw materials are simple and easy to obtain; and the antibacterial cleaning solution can effectively clean sweat stains and oil stains on the surface of skin, can effectively sterilize and inhibit bacteria on the surface of the skin to prevent bedsores, can be prepared into various forms including an aqueous solution, a spray, a liniment, a wet tissue and the like, and is convenient for patients prone to suffer from the bedsores to use in daily life.
Owner:重庆返璞科技有限公司
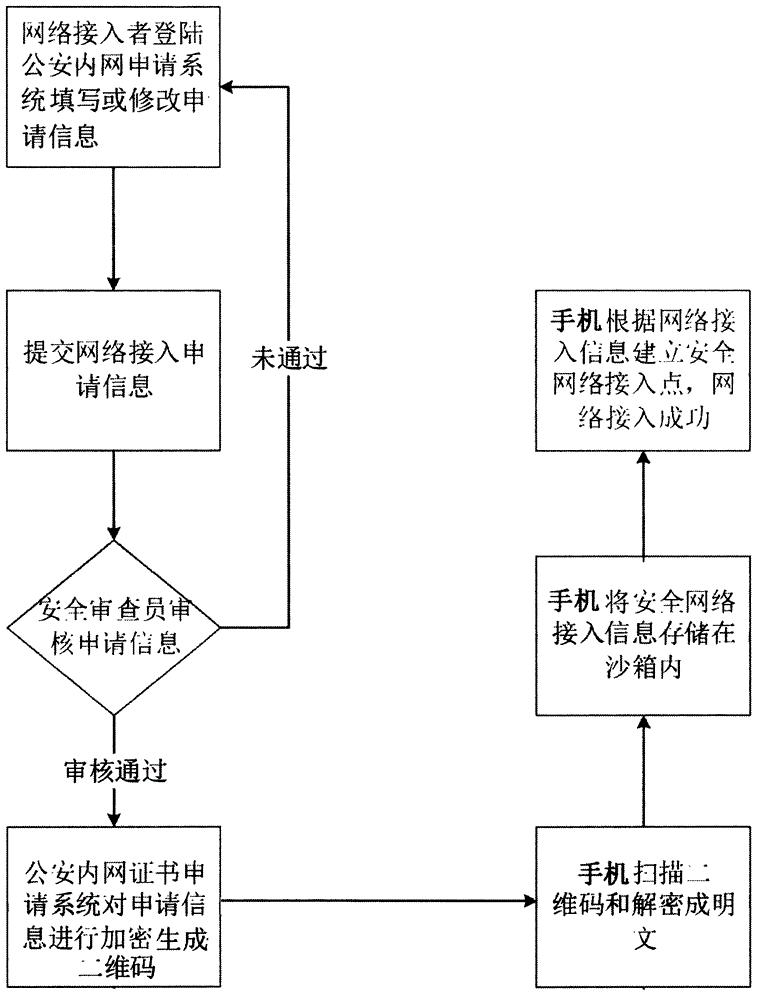
Method for mobile terminal to access to private network
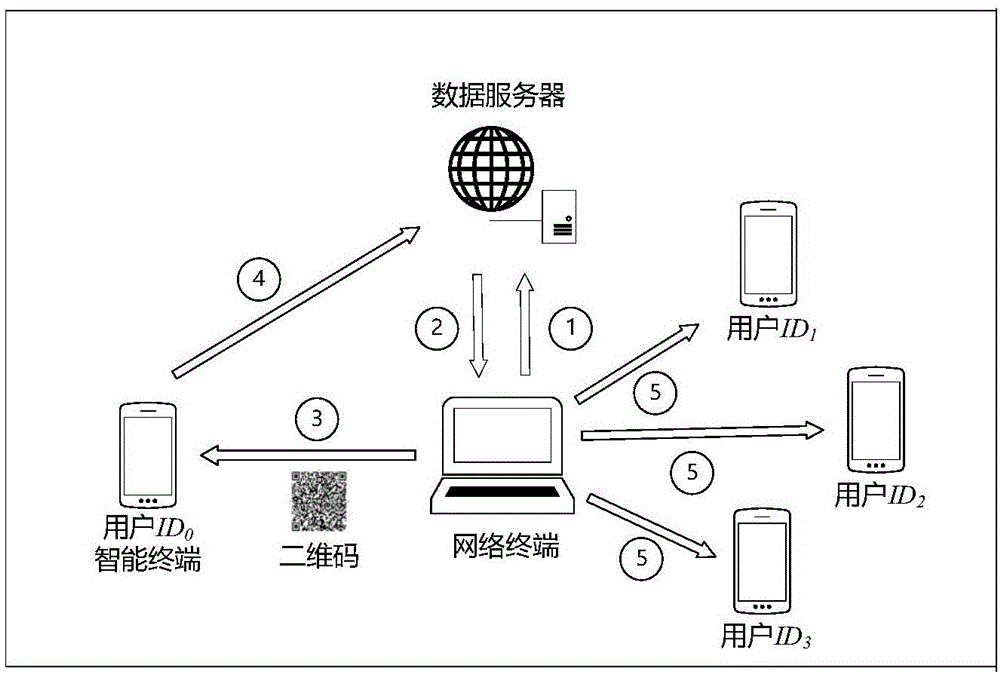
The invention belongs to the technical field of software development and network access, and more particularly relates to a method for a mobile terminal to access to a private network. The method for the mobile terminal to access to the private network comprises the steps that: (1) a mobile terminal user makes a login application to the private network, and the private network checks the login application information manually; (2) the private network encrypts the application information to generate a two-dimensional code after the checking is passed; (3) the mobile terminal scans the two-dimensional code, analyzes the two-dimensional code into plaintext information and saves the information; (4) and the mobile terminal establishes a private network access point according to the saved information. The method establishes network access through combining the manual checking with the two-dimensional code interactively, has good security and is simple in operation.
Owner:浙江公共安全技术研究院有限公司
A storage and management device for power grid operation data
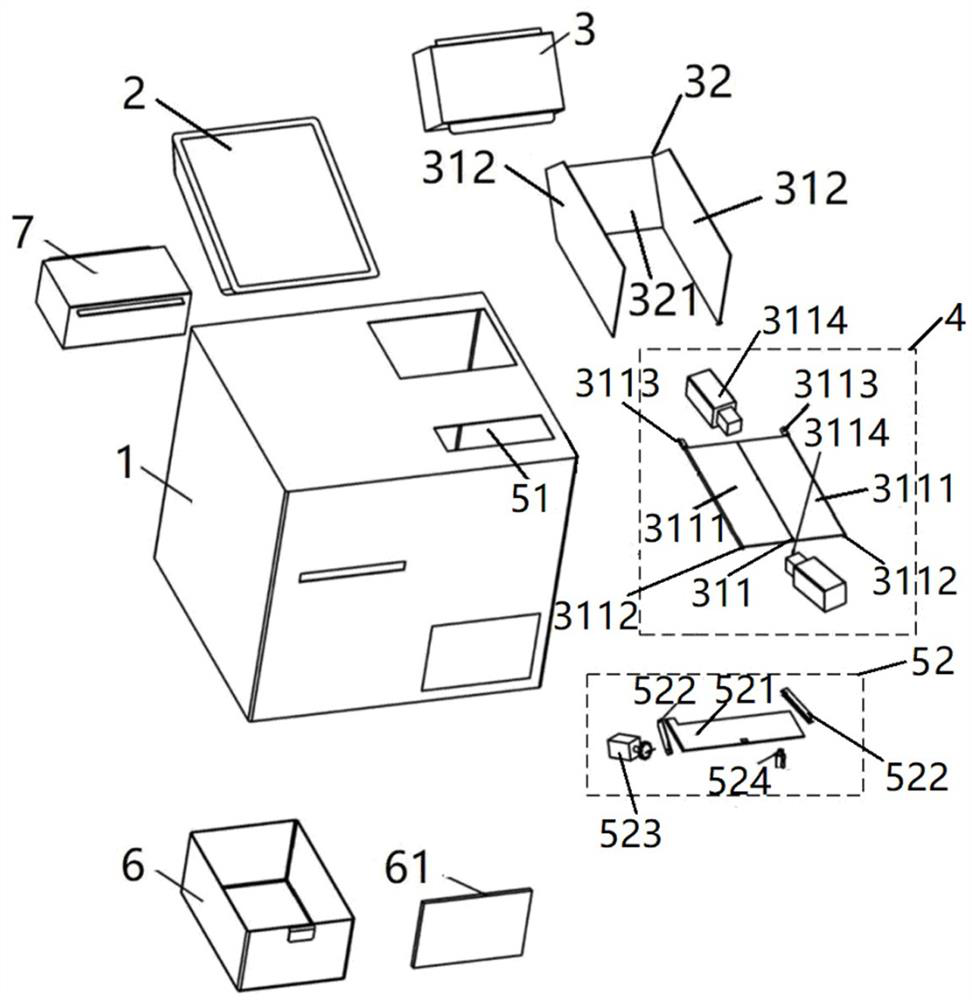
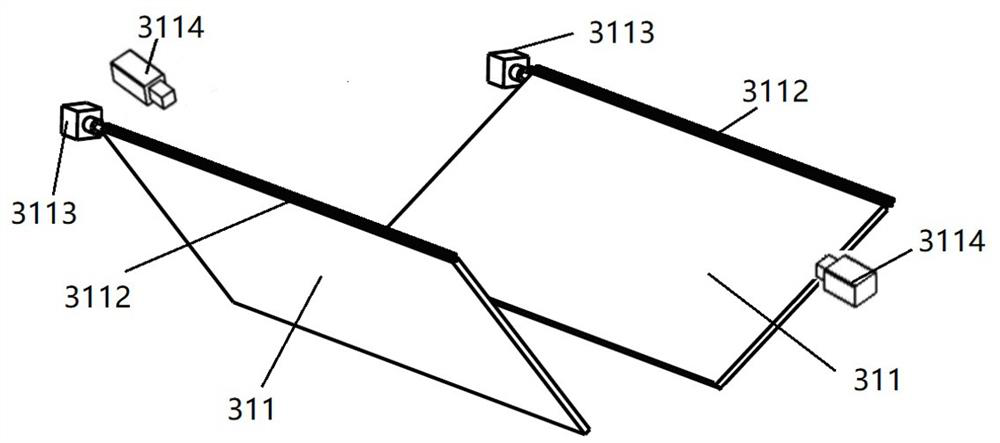
ActiveCN112752456BGuaranteed storage securityGood for structural protectionCasings/cabinets/drawers detailsCouplings bases/casesStorage securityPower grid
Owner:南京佳智飞迅科技有限公司
A cloud service authority authentication method, device, equipment and medium
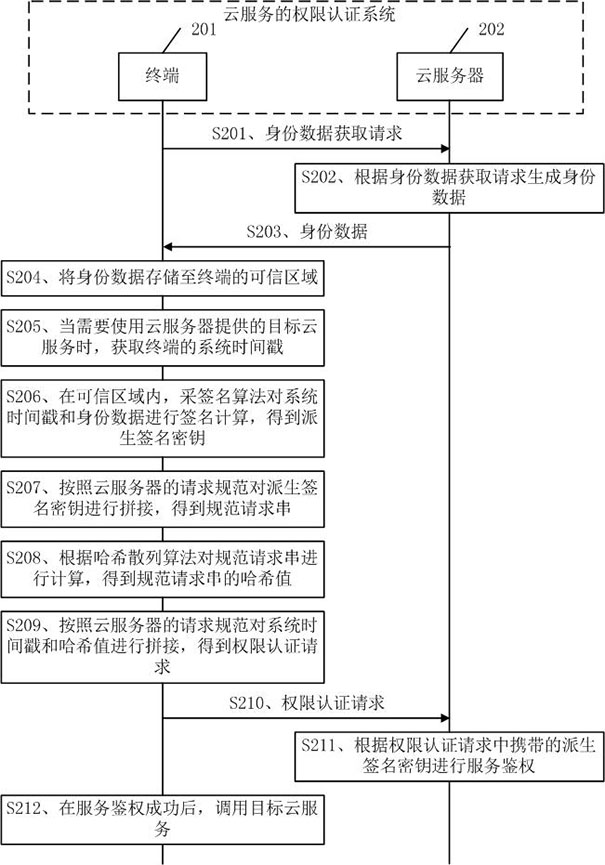
ActiveCN111262889BGuaranteed storage securityImprove securityKey distribution for secure communicationUser identity/authority verificationInternet privacyEngineering
The embodiment of the present application discloses a cloud service authority authentication method, device, equipment, and medium. The cloud service authority authentication method includes: when the target cloud service provided by the cloud server needs to be used, obtain from the trusted area of the terminal Deriving the signature key; the trusted area is one or more secure execution areas divided in the terminal memory; generating an authority authentication request based on the derived signature key, and the authority authentication request carries the derived signature key; sending the authority authentication to the cloud server Request, so that the cloud server performs service authentication according to the derived signature key carried in the permission authentication request; after the service authentication is successful, call the target cloud service. By adopting the embodiment of the present application, by dividing a secure trusted area in the terminal, the trusted area is used to ensure the security of the derived signature key, thereby ensuring the reliability of the authority authentication process based on the derived signature key.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Self-service bill processing terminal and bill processing method thereof
ActiveCN110415460ASimple mechanical structureReliable mechanical structureTypewritersApparatus for meter-controlled dispensingComputer moduleComputer terminal
The invention provides a self-service bill processing terminal and a bill processing method thereof. Execution information is input by an input module, and converted by a main control chip circuit into various execution instructions; a bill scanner scans a bill and displays the bill in a display module, the scanned bill falls into a bill temporary storage assembly to wait user validation on an operation component side, if the bill processing flow needs to be stopped, instruction information for taking out of the bill is input by the input module, the main control chip circuit commands a limiting device to execute the opening activity, the bill is taken out through a bill exit window, and the bill processing flow is stopped; if the bill in the bill temporary storage assembly is accurate, the main control chip circuit sends an opening instruction to a baffle, the baffle is opened, and under the gravity action, the bill falls into a bill storage platform for storage. The mechanism is simple and reliable. If it is found that the bill is accurate, a user can self-control the bill to be taken out, after the bill is taken out, the bill processing flow is stopped immediately, and the situation that the flow continues to be conducted, defect of the paper bill is caused is avoided.
Owner:厦门商集网络科技有限责任公司
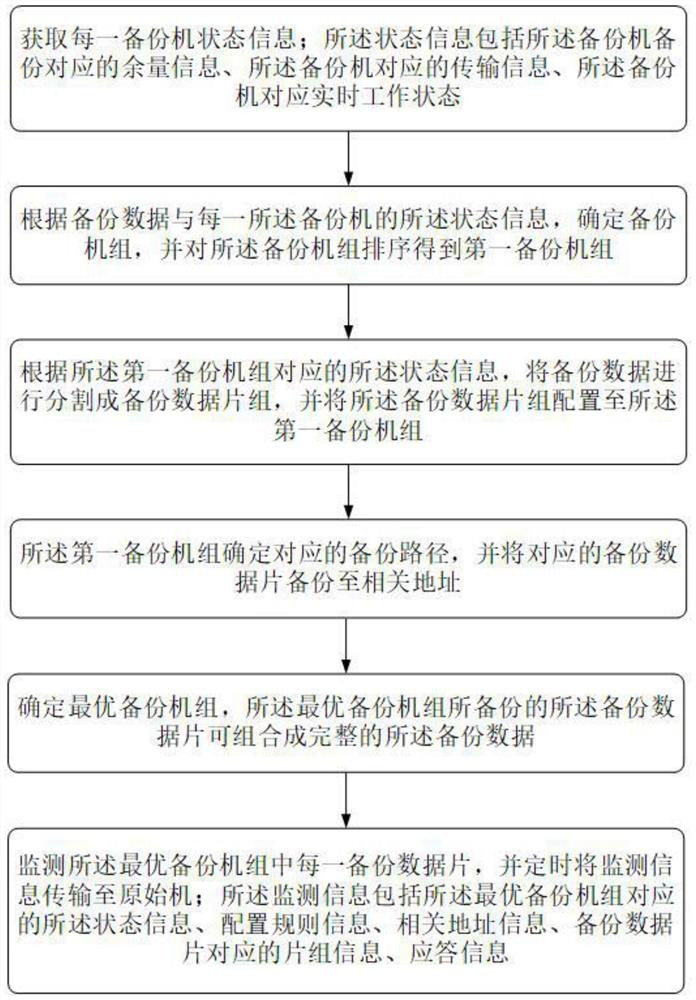
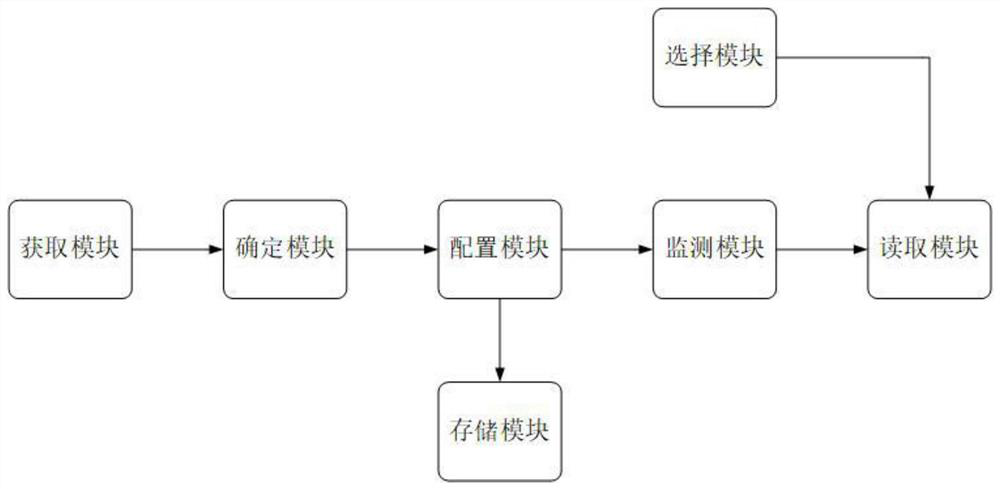
Computer backup data monitoring method and system
ActiveCN112685232AIntegrity guaranteedGuaranteed validityHardware monitoringRedundant operation error correctionStorage securityMonitoring methods
The invention discloses a computer backup data monitoring method and system, and the method comprises the steps: setting a mode of combining k-fold backup and segmented backup, achieving the multi-segment backup on the premise that the integrity and effectiveness of backup data are guaranteed, reducing the backup and reading pressure of a single backup machine, and balancing the performance of the backup machine. By setting a reasonable configuration rule in k backups, on one hand, the storage security of backup data is ensured, random combination and reading cannot be realized, and on the other hand, the fixity and traceability of data backup are ensured.
Owner:HENAN UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com