Electronic bidding document multilayer encryption and decryption system for electronic bidding
A bidding, encryption and decryption technology, which is applied in the fields of electrical digital data processing, instruments, digital data protection, etc., can solve the problem of low difficulty for hackers to crack, and achieve the effect of ensuring storage security, improving security, and reducing possibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
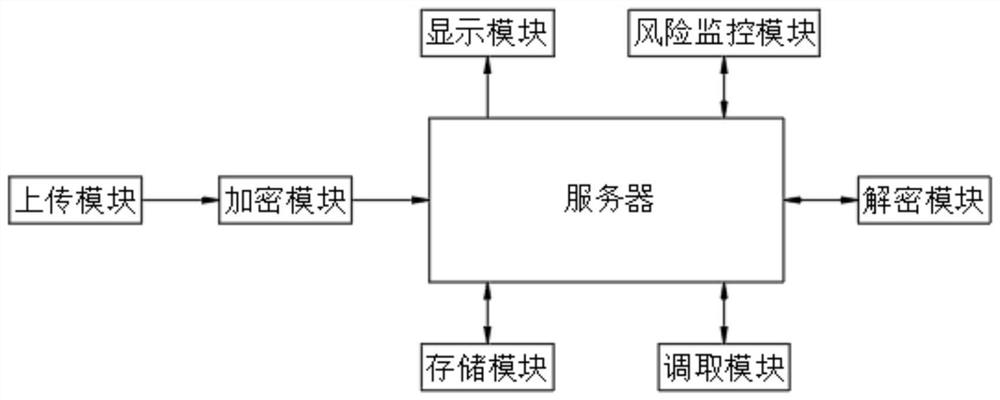
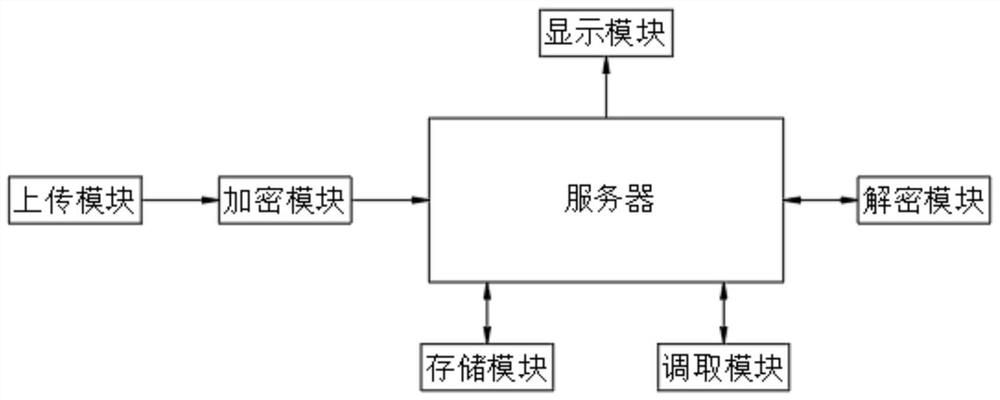
[0037] see figure 2 As shown, the user uploads the electronic bidding document file to be encrypted to the encryption module through the upload module, and the encryption module encrypts the electronic bidding document file after receiving the electronic bidding document file: mark the electronic bidding document file to be encrypted as a processing file, and obtain the processing file Complete pinyin of the first character of the name and mark the first letter as the initial letter A1, obtain the full pinyin of the last word of the processed file name and mark the last letter as the last letter A2, and obtain the total number of characters in the processed file name And mark it as the number of characters B1, get the memory value of the processed file, the unit is Mb, perform octal conversion on the memory value and round the obtained value, mark the obtained value as the memory performance value C1, and generate a call in the form of A-B-C Code fetching, where A is the comb...
Embodiment 2
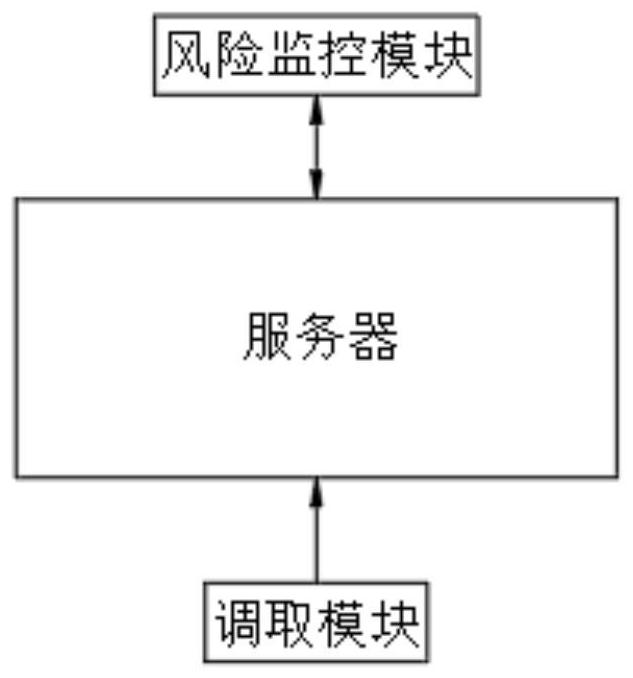
[0042] see image 3 As shown, the risk monitoring module is used to monitor and analyze the risk of file retrieval: the number of times the retrieval personnel enters the retrieval code is marked as DC, the number of times the retrieval module receives a first-level failure signal is marked as YS, and the retrieval The number of times that the fetching module receives the second-level failure signal is marked as ES, and the number of times that the calling module receives the third-level failure signal is marked as SS. It is obtained by the formula FX=α1×DC+α2×YS+α3×ES+α4×SS The risk coefficient FX retrieved from the file, where α1, α2, α3, and α4 are all proportional coefficients, and α1>α2>α3>α4>0; obtain the risk threshold FXmax through the storage module, and compare the risk coefficient FX with the risk threshold FXmax Comparison: If the risk coefficient FX is less than the risk threshold FXmax, it is determined that the file retrieval is safe, and the risk monitoring mod...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com