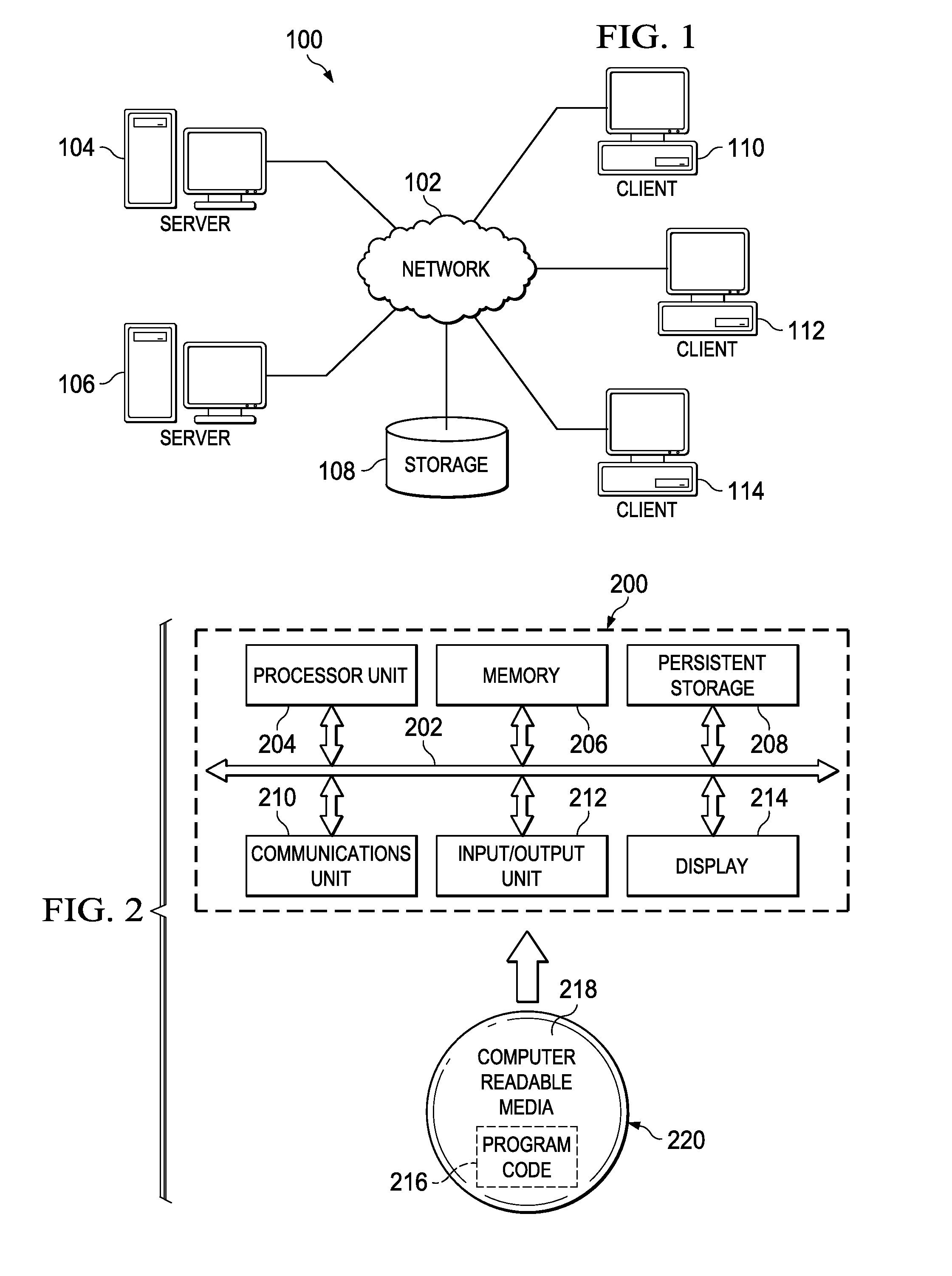
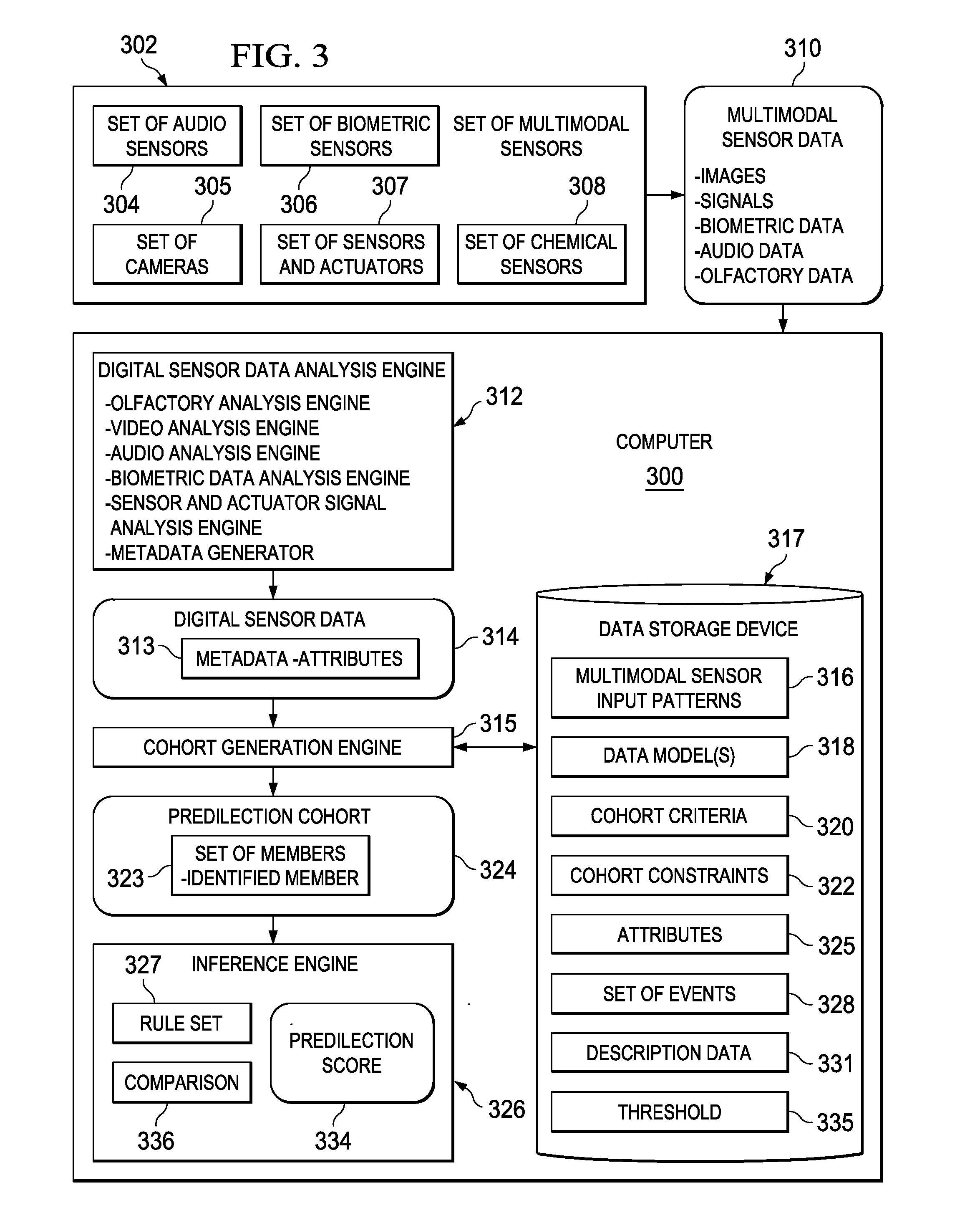
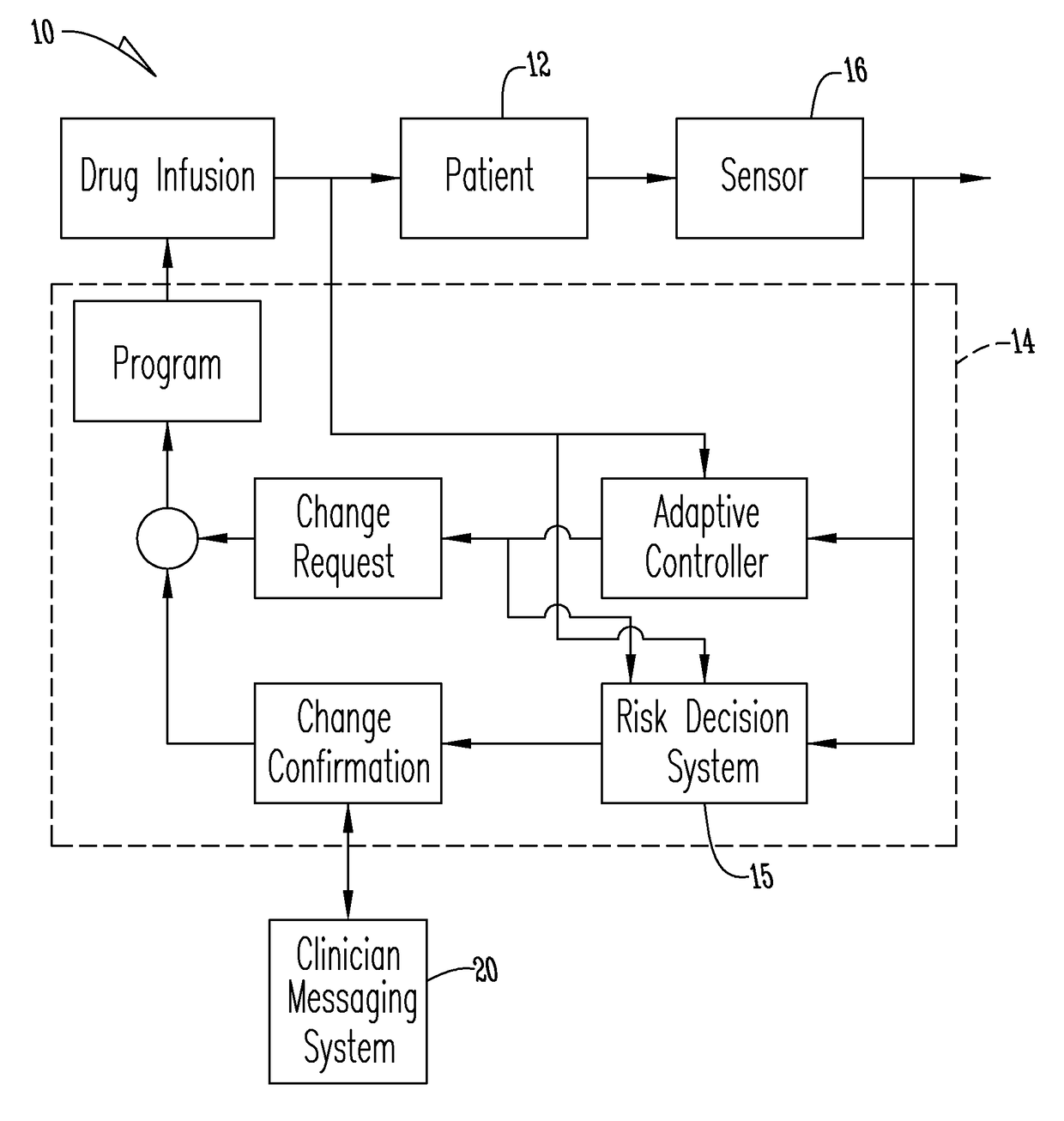
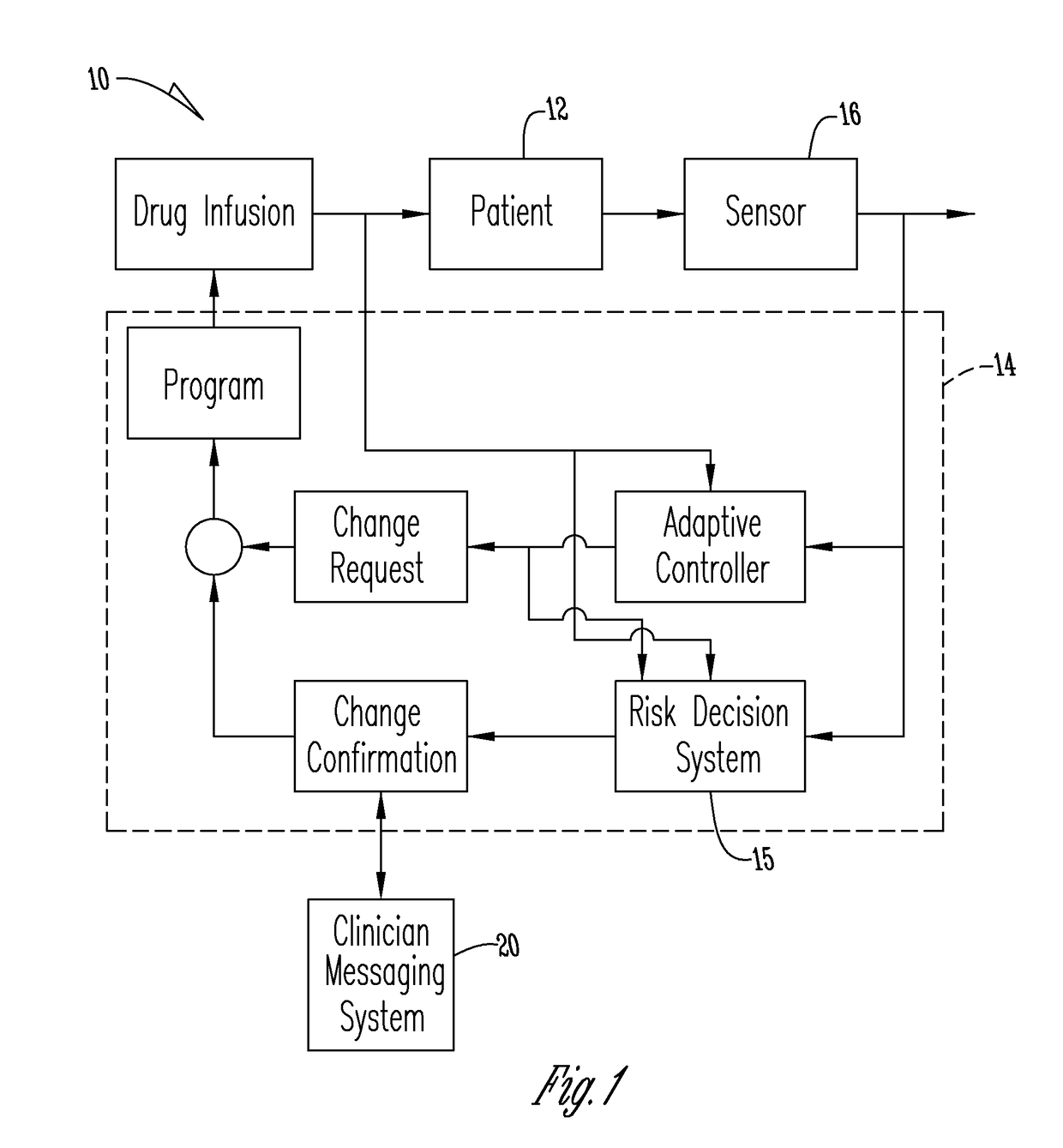
Patents
Literature
216 results about "Risk threshold" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The risk threshold is defined as a project management tool to measure the degree of uncertainty and the level of impact which a stakeholder or organization may have interest. As the name implies, it sets a certain value that the stakeholder or organization will accept a certain risk or not.
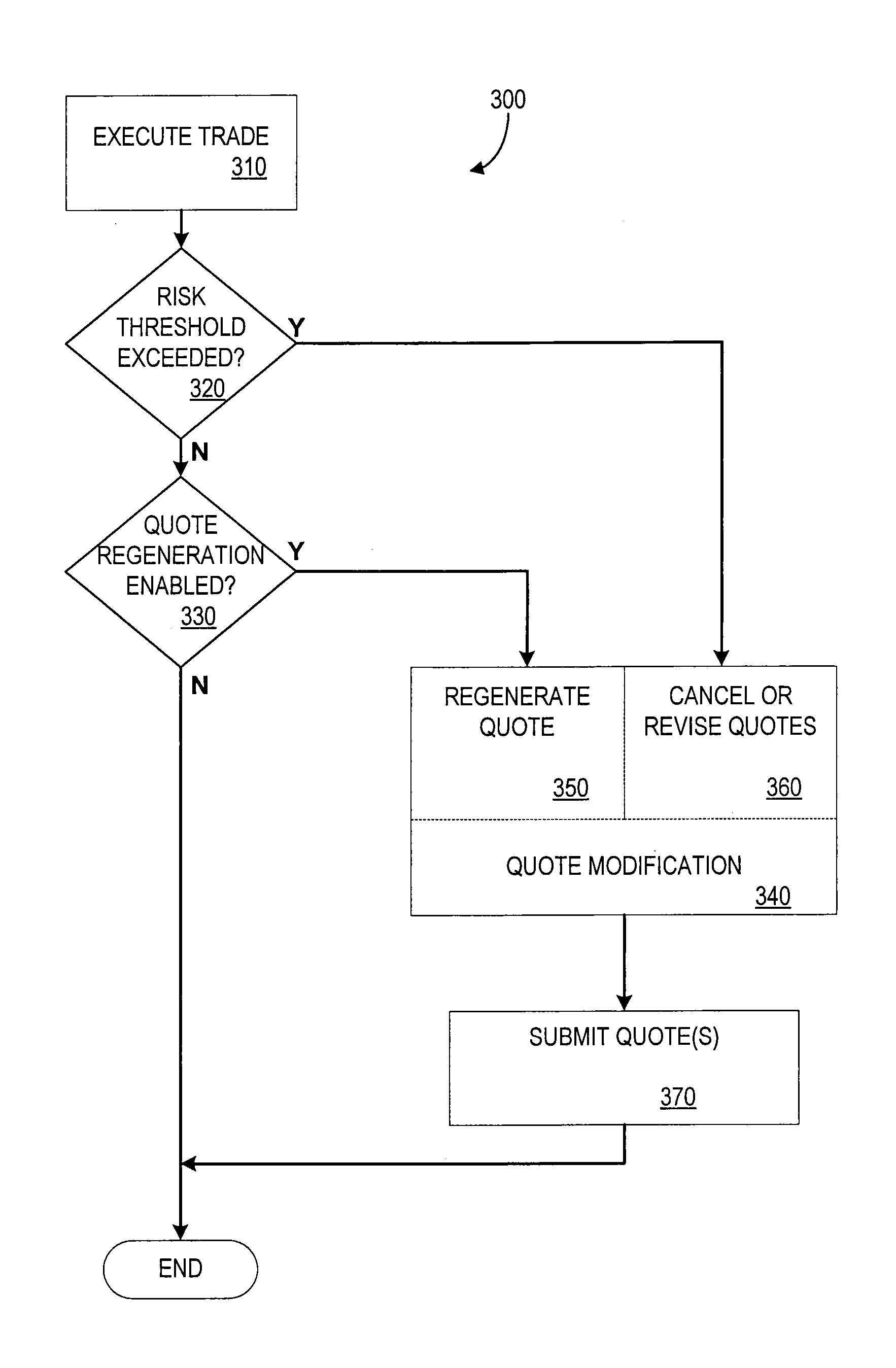
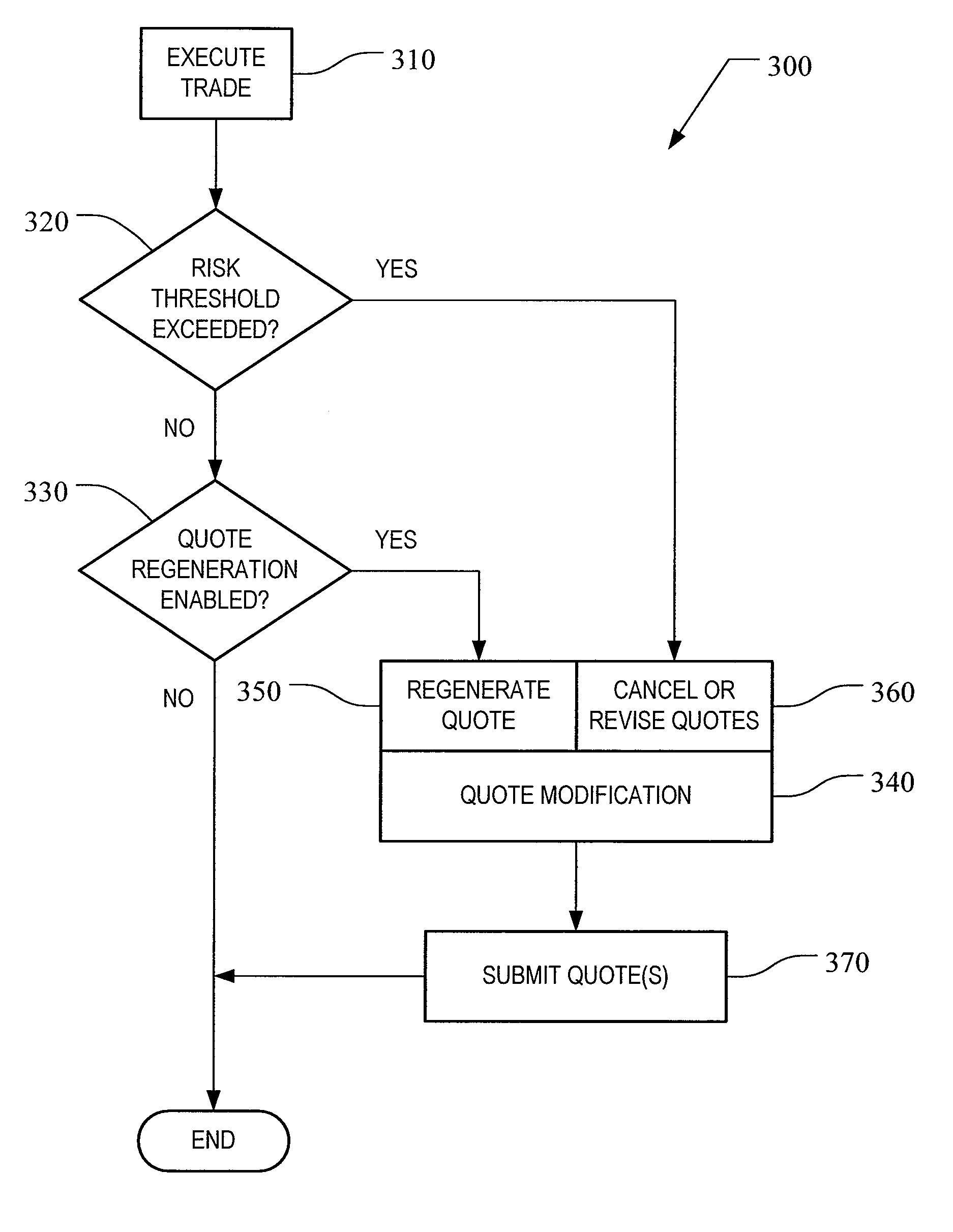
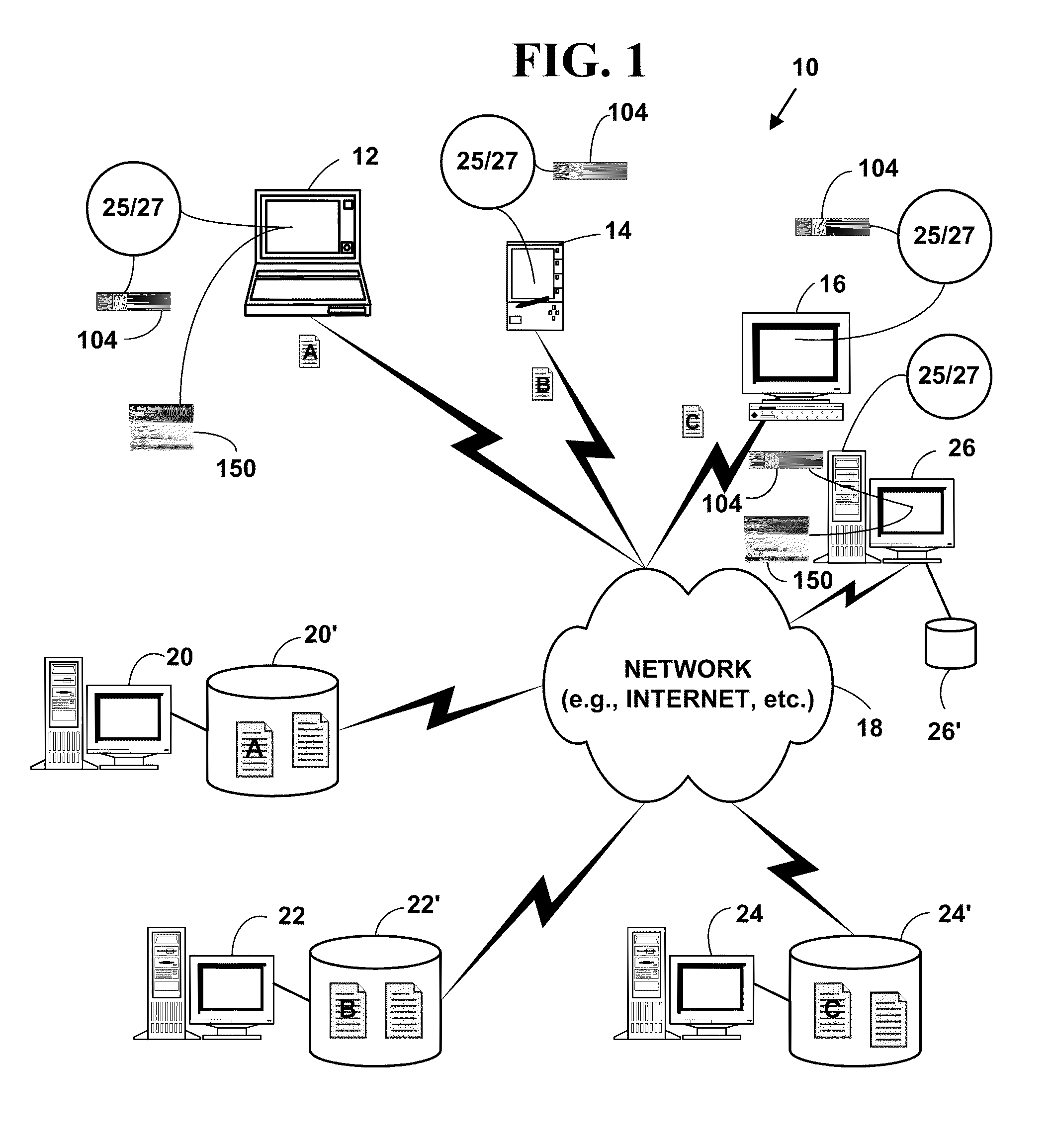
Automated Trading Exchange System Having Integrated Quote Risk Monitoring and Integrated Quote Modification Services
<heading lvl="0">Abstract< / heading> An automated trading exchange having integrated quote risk monitoring and quote modification services. An apparatus is implemented using at least one computer, having memory, and a processor. The computer is configured to receive orders and quotes, wherein specified ones of the quotes are contained in a quote group, and have associated trading parameters such as a risk threshold. Not all received quotes are required to have trading parameters as described herein. Preferably, the quote group contains all the quotes, or a subset of quotes, belonging to an individual market-maker for a given class of options contracts, or possibly the quotes of two or more market-makers that have identified themselves as belonging to a group for the purposes of risk monitoring and quote modification. The computer typically generates a trade by matching the received orders and quotes to previously received orders and quotes, and otherwise stores each of the received orders and quotes if a trade is not generated. The computer then determines whether a quote within the quote group has been filled as a result of the generated trade, and if so, determines a risk level and an aggregate risk level associated with said trade. The computer then compares the aggregate risk level with the market-maker's risk threshold, and if the threshold is exceeded, automatically modifies at least one of the remaining quotes in the quote group. The computer may also automatically regenerate quotes that have been filled.
Owner:CBOE EXCHANGE INC
Automated trading exchange system having integrated quote risk monitoring and integrated quote modification services
An automated trading exchange having integrated quote risk monitoring and quote modification services. An apparatus is implemented using at least one computer, having memory, and a processor. The computer is configured to receive orders and quotes, wherein specified ones of the quotes are contained in a quote group, and have associated trading parameters such as a risk threshold. Not all received quotes are required to have trading parameters as described herein. Preferably, the quote group contains all the quotes, or a subset of quotes, belonging to an individual market-maker for a given class of options contracts, or possibly the quotes of two or more market-makers that have identified themselves as belonging to a group for the purposes of risk monitoring and quote modification. The computer typically generates a trade by matching the received orders and quotes to previously received orders and quotes, and otherwise stores each of the received orders and quotes if a trade is not generated. The computer then determines whether a quote within the quote group has been filled as a result of the generated trade, and if so, determines a risk level and an aggregate risk level associated with said trade. The computer then compares the aggregate risk level with the market-maker's risk threshold, and if the threshold is exceeded, automatically modifies at least one of the remaining quotes in the quote group. The computer may also automatically regenerate quotes that have been filled.
Owner:CBOE EXCHANGE INC
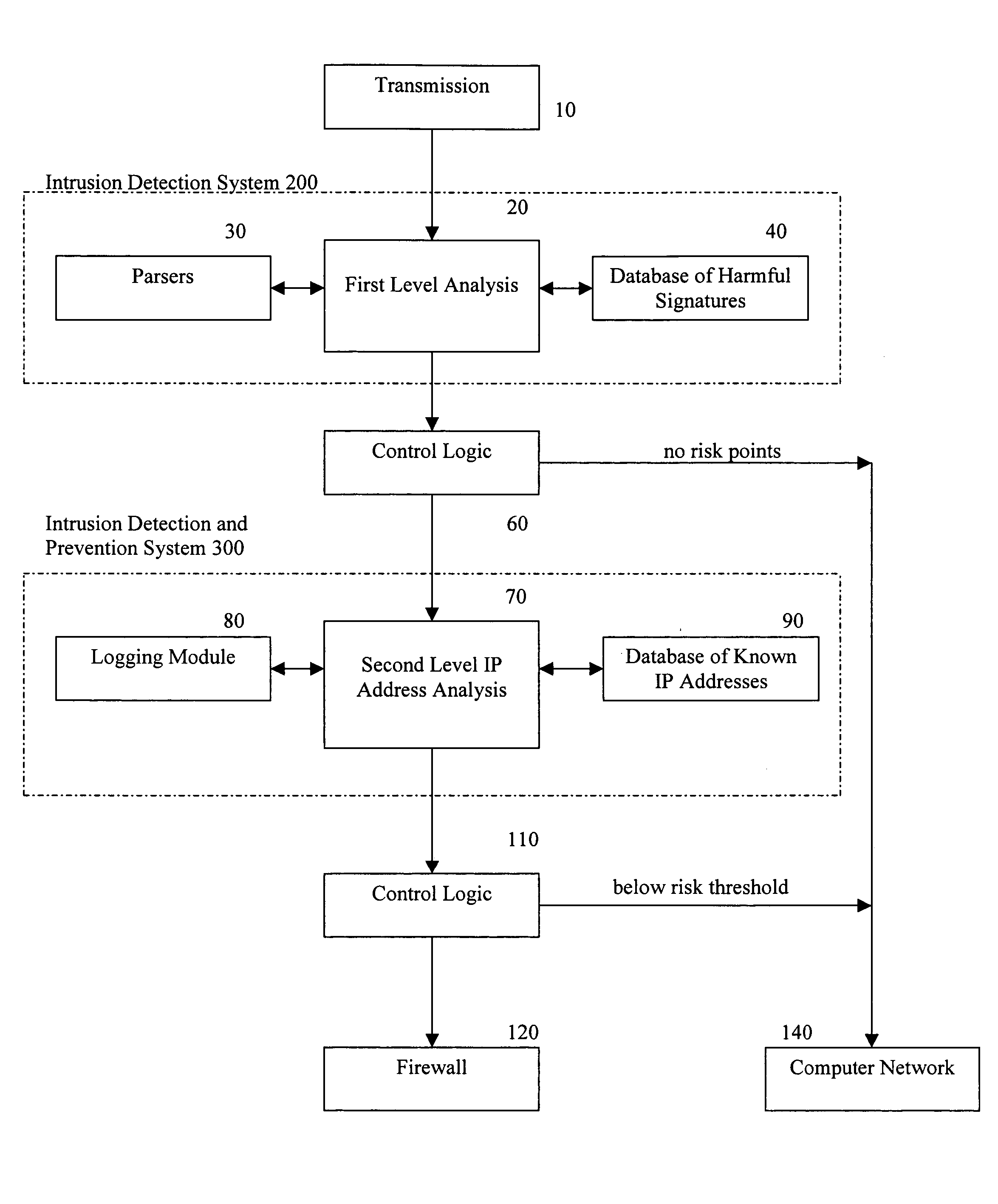
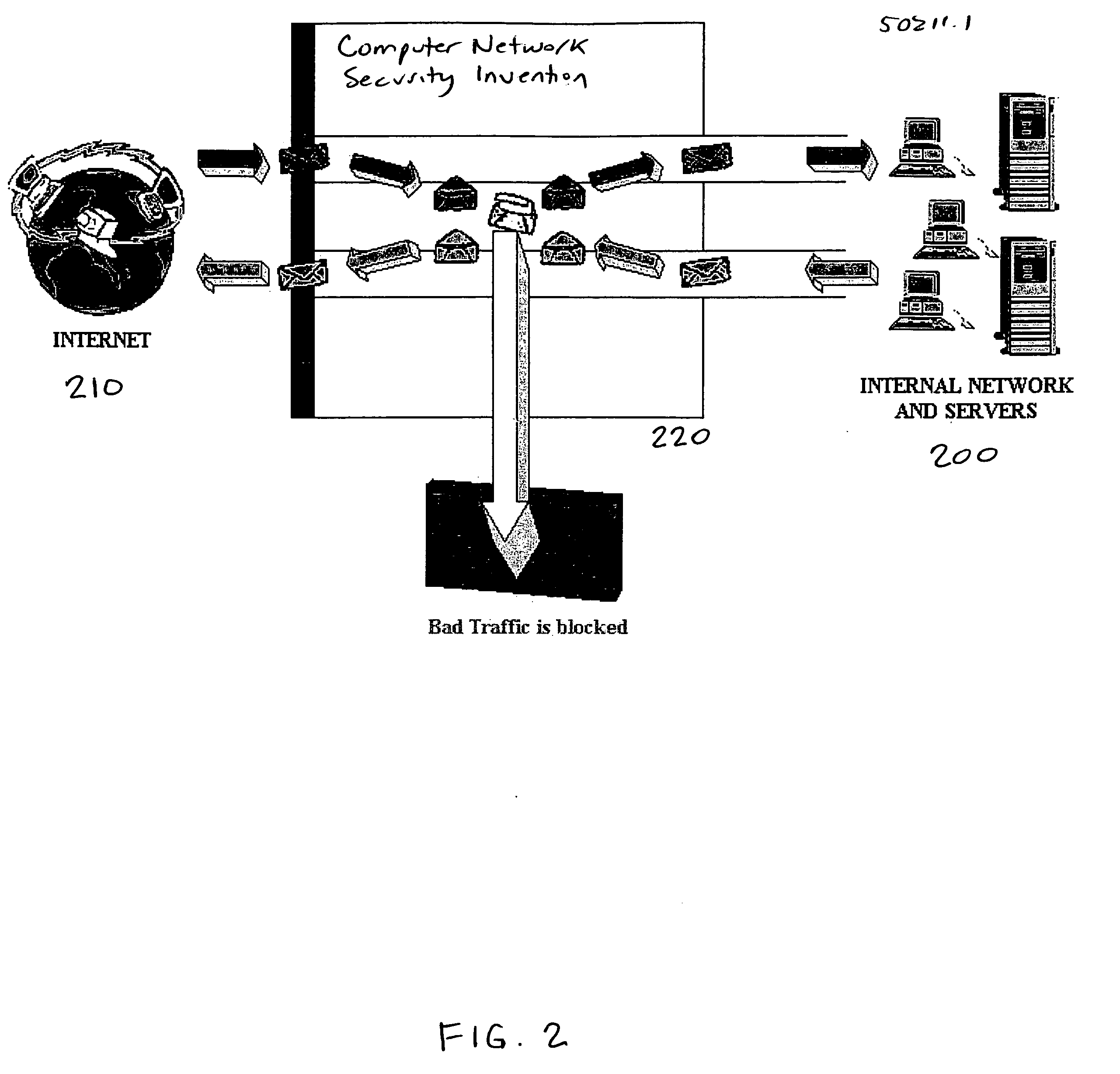
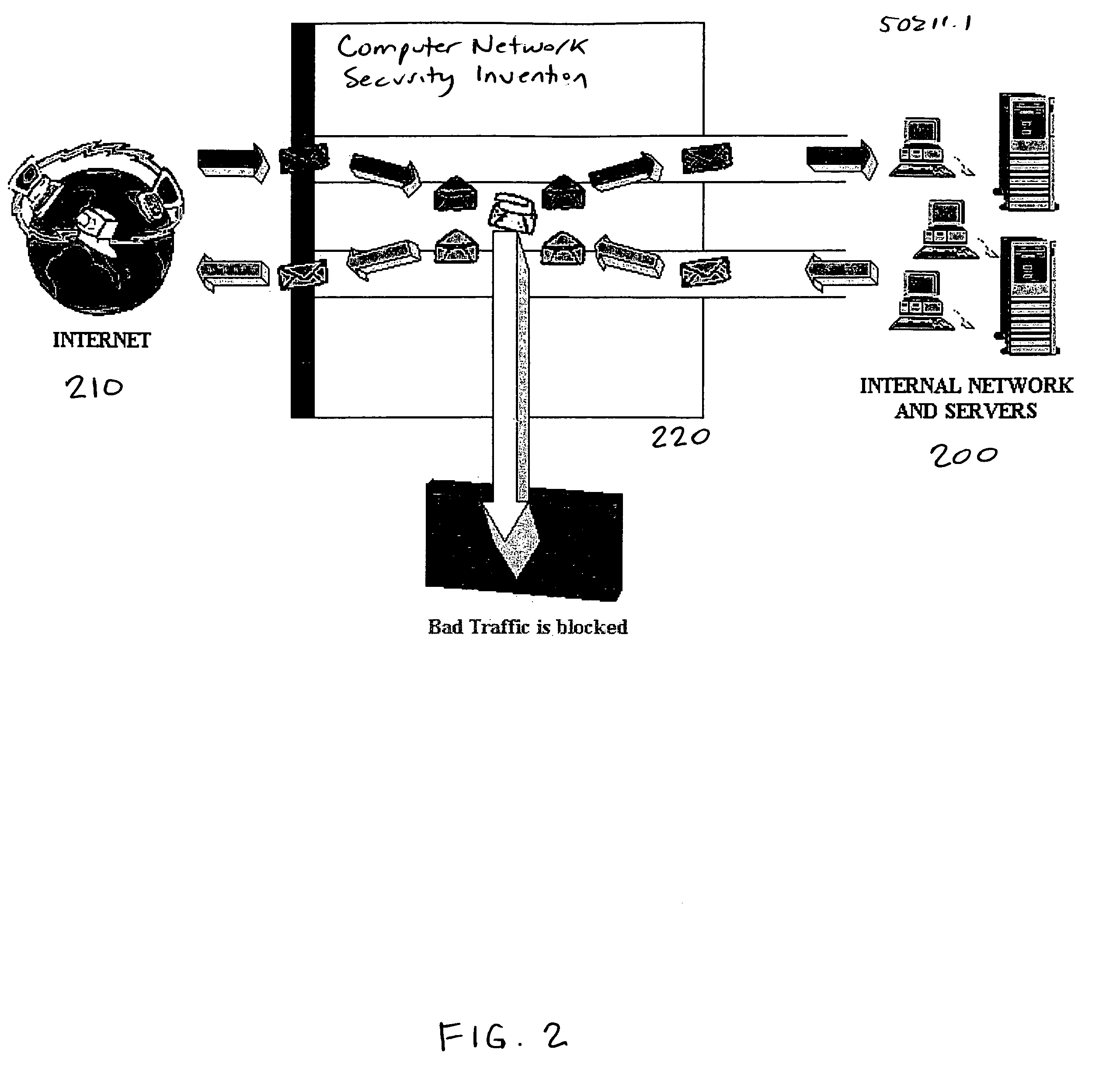
Methods and apparatus for computer network security using intrusion detection and prevention
InactiveUS20050262556A1Overcome disadvantagesMemory loss protectionDigital data processing detailsIp addressIntrusion detection and prevention
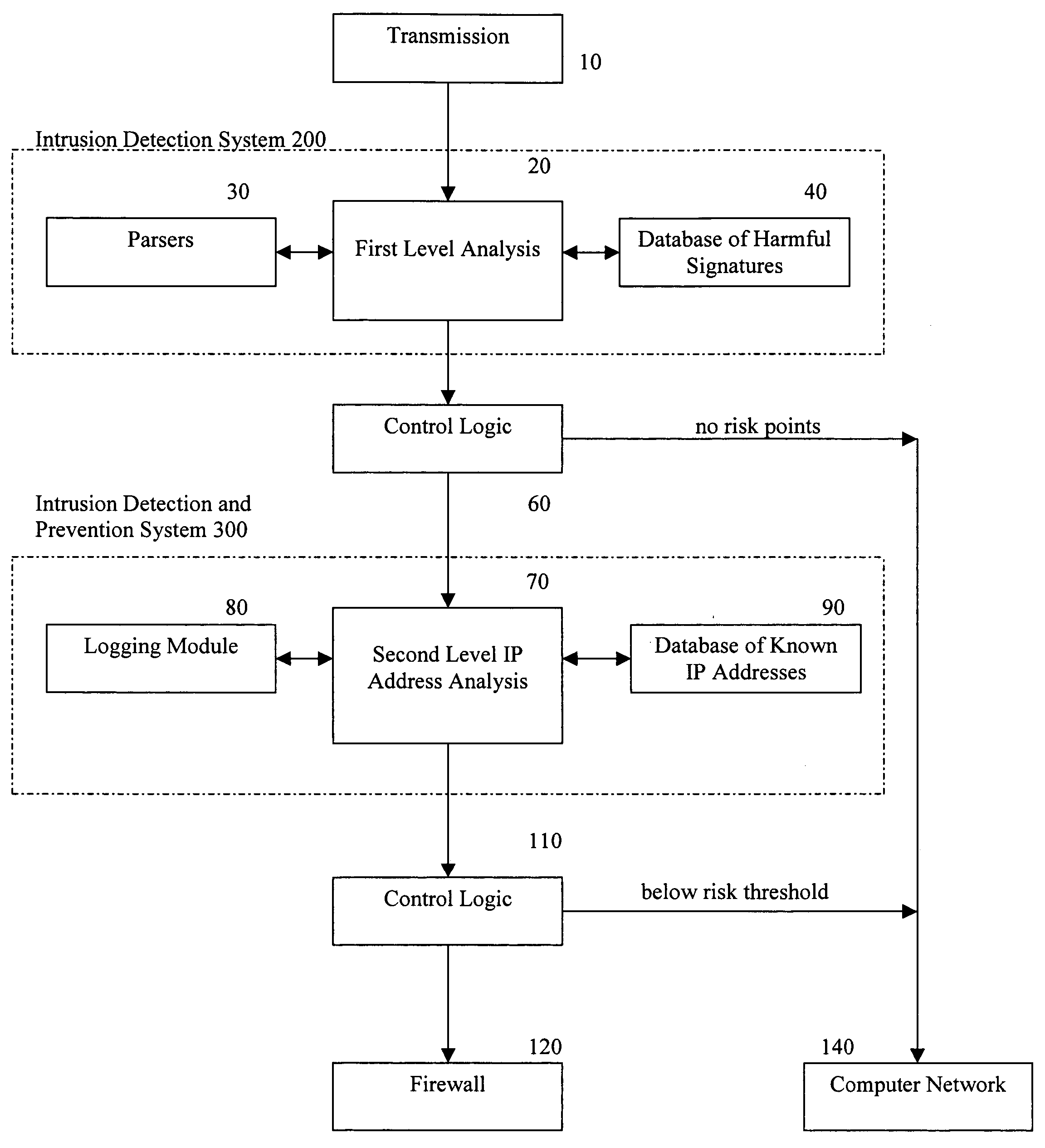
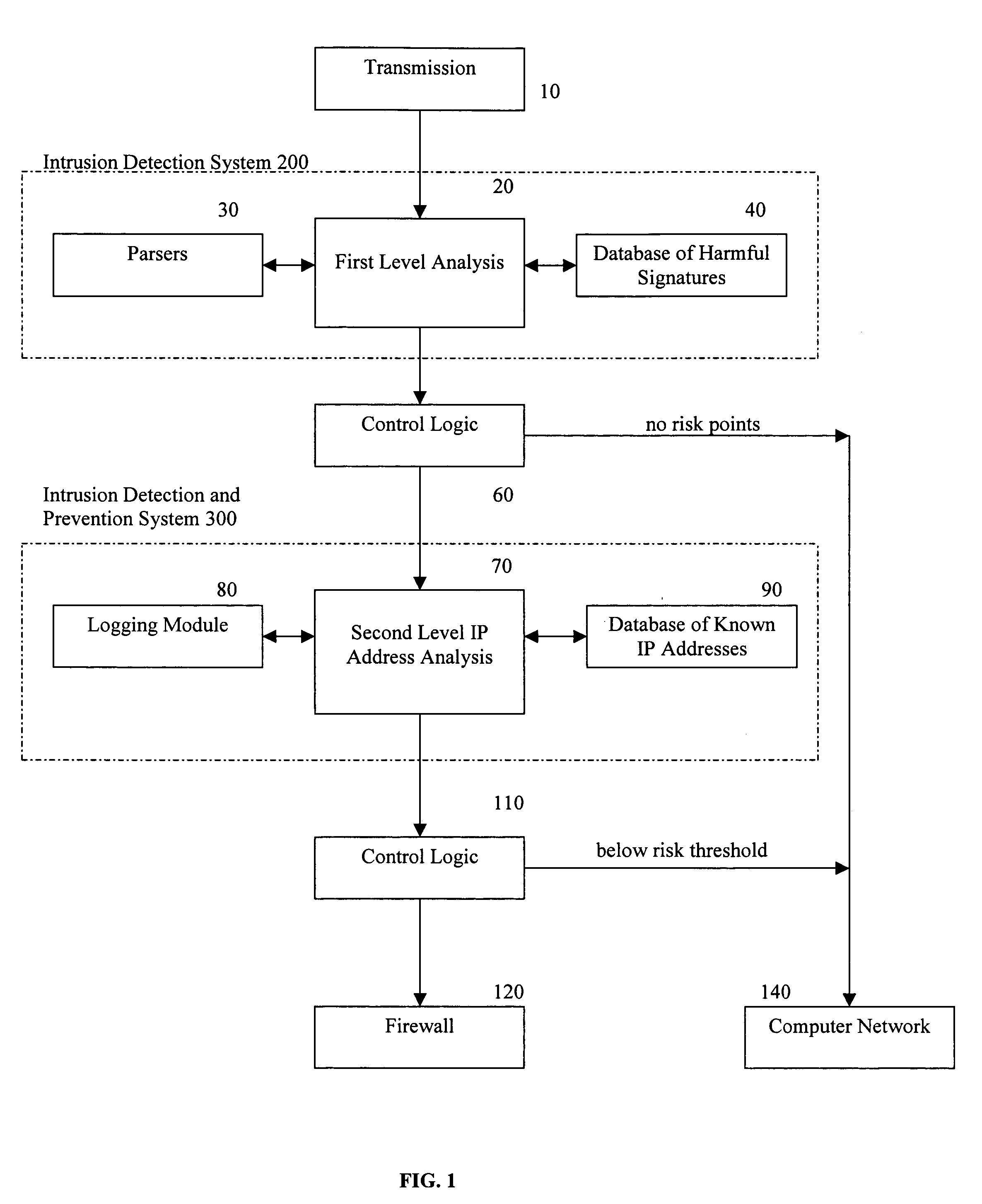
A method for providing security to a computer network by selectively blocking network transmissions from selected IP addresses comprising the steps of: establishing a risk threshold whereby transmissions from IP addresses exceeding said risk threshold are selectively blocked; receiving a network transmission having an originating IP address and payload; analyzing the payload of said transmission and assigning a current risk rating to said IP address on the basis of said analysis; comparing the originating IP address of said transmission to a database of known IP addresses, each of said said previous cumulative assigned risk rating being based on at least one previous transmission from a known IP address; known IP addresses having a previous cumulative assigned risk rating, assigning a new cumulative risk rating to said originating IP address, said new cumulative risk rating being the sum of said current risk rating and said previous cumulative assigned risk rating for said originating IP address, with the proviso that where said originating IP address is not contained in said database of known IP addresses, the new cumulative risk rating will equal the current risk rating; logging the new cumulative risk rating for said originating IP address in said database of known IP addresses, with the proviso that where the originating IP address of said transmission is not contained in said database of known IP addresses, a new record is created for the originating IP address and said new cumulative risk rating in said database of known IP addresses; comparing said new cumulative risk rating to said risk threshold; and automatically blocking said transmission if said new cumulative risk rating exceeds said risk threshold.
Owner:DIGITAL SECURITY NETWORK
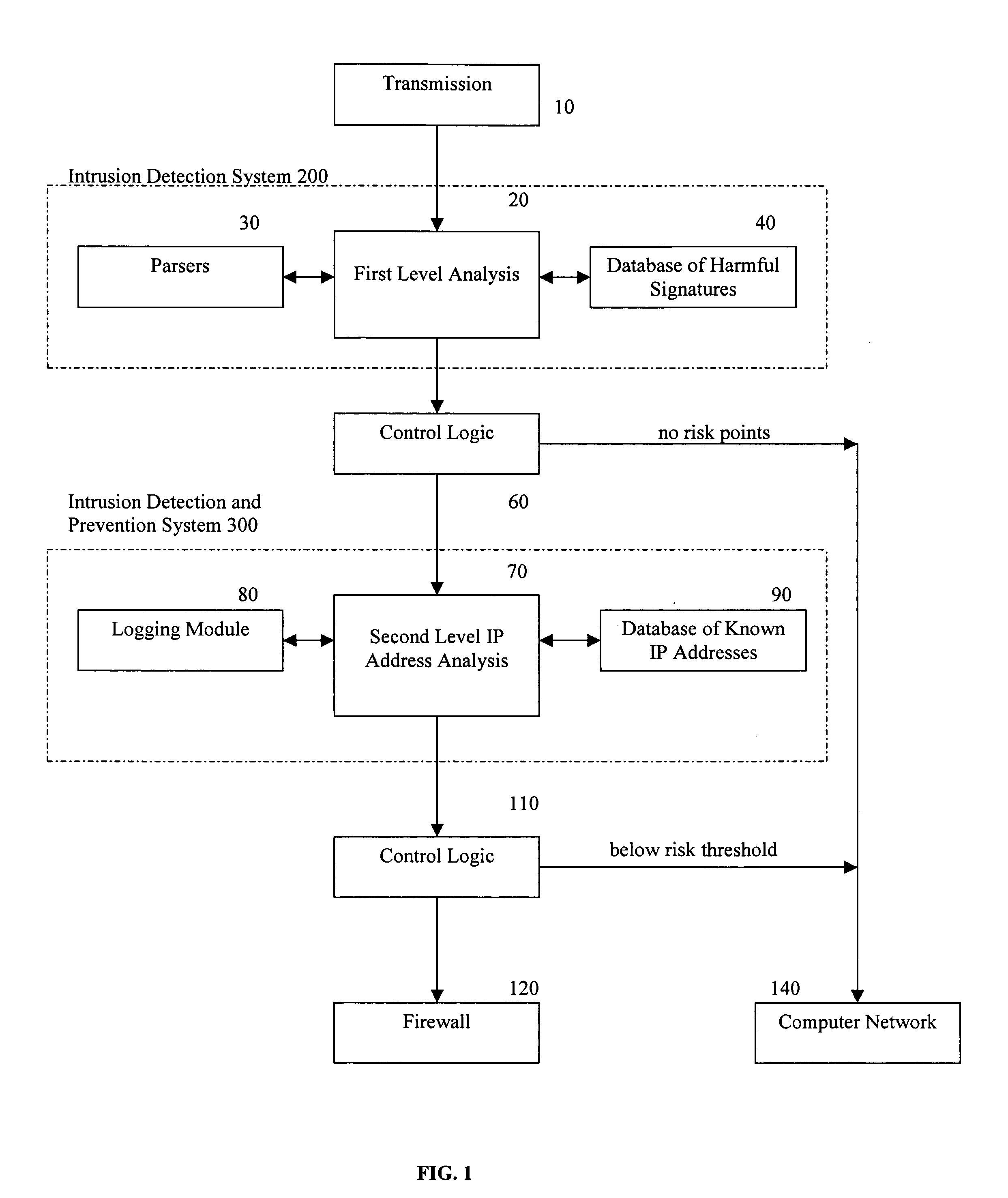
Methods and apparatus for computer network security using intrusion detection and prevention
InactiveUS7225468B2Memory loss protectionDigital data processing detailsIp addressIntrusion detection and prevention
A method provides security to a computer network by selectively blocking network transmissions from selected IP addresses. The method includes the steps of: establishing a risk threshold whereby transmissions from IP addresses exceeding said risk threshold are selectively blocked; receiving a network transmission having an originating IP address and payload; analyzing the payload of said transmission and assigning a current risk rating to said IP address on the basis of said analysis; comparing the originating IP address of said transmission to a database of known IP addresses, each of said known IP addresses having a previous cumulative assigned risk rating, said previous cumulative assigned risk rating being based on at least one previous transmission from a known IP address; assigning a new cumulative risk rating to said originating IP address; logging the new cumulative risk rating for said originating IP address in said database of known IP addresses. The new cumulative risk rating is compared to said risk threshold and the transmission is blocked if said new cumulative risk rating exceeds said risk threshold.
Owner:DIGITAL SECURITY NETWORK
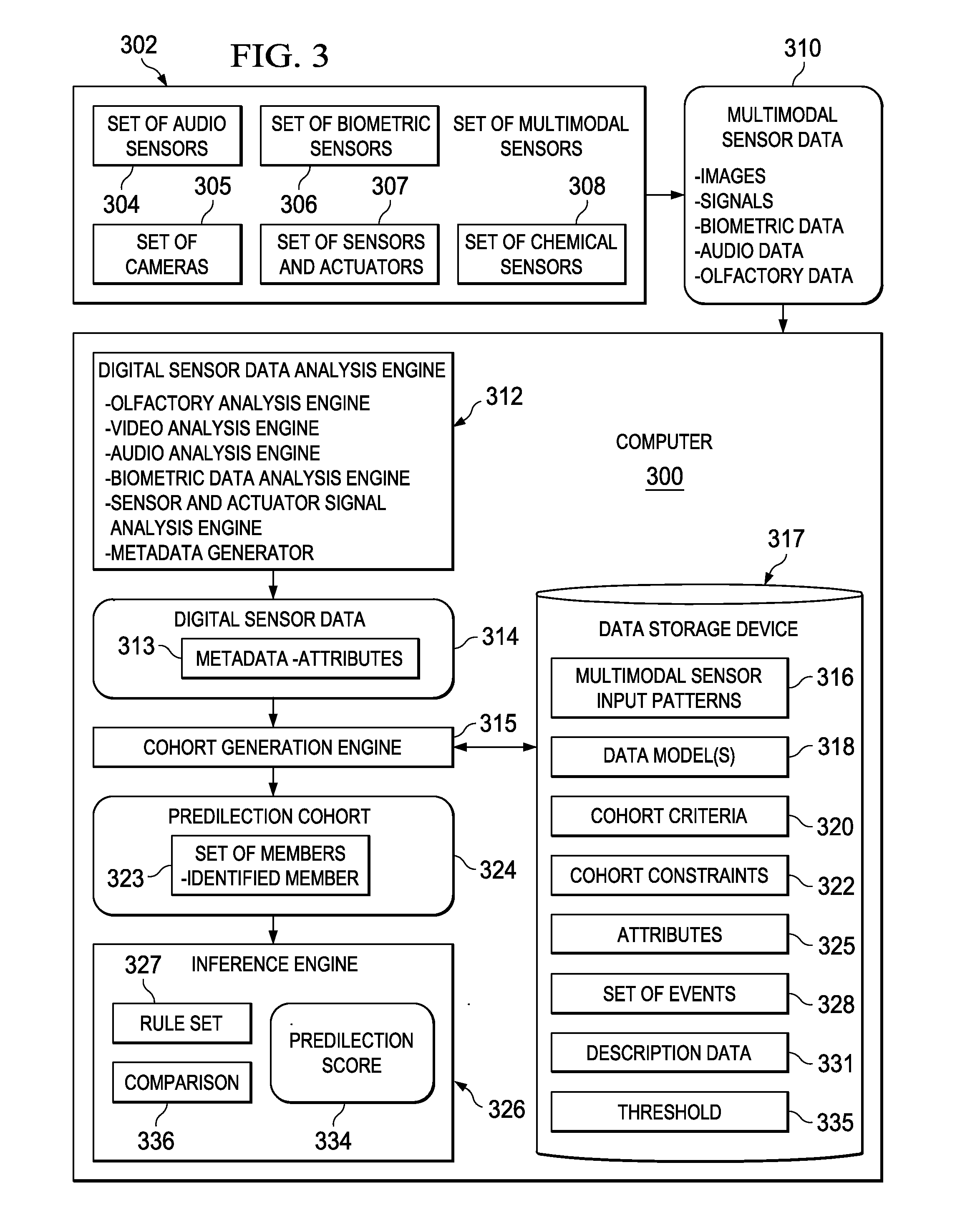
Generating Generalized Risk Cohorts
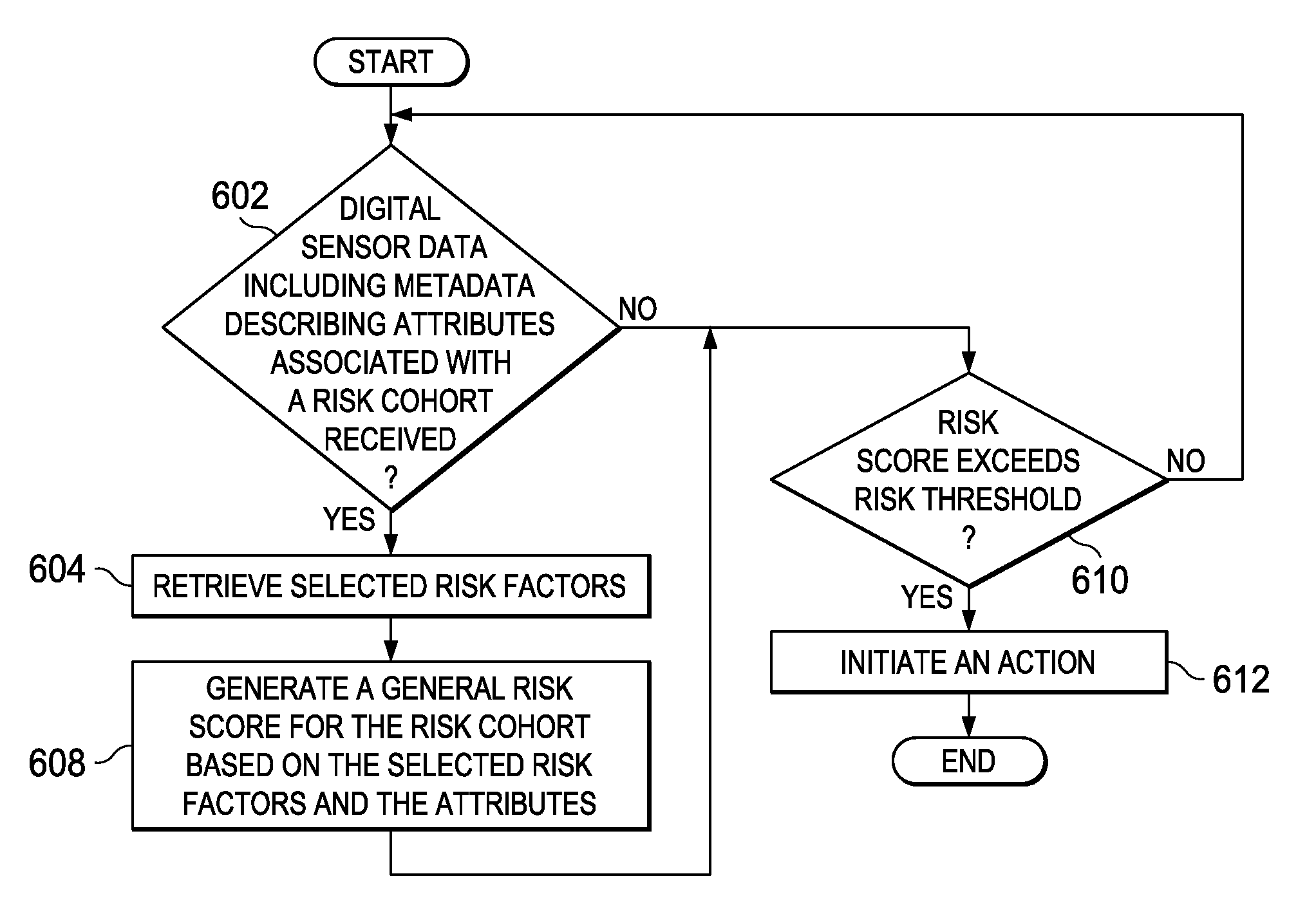
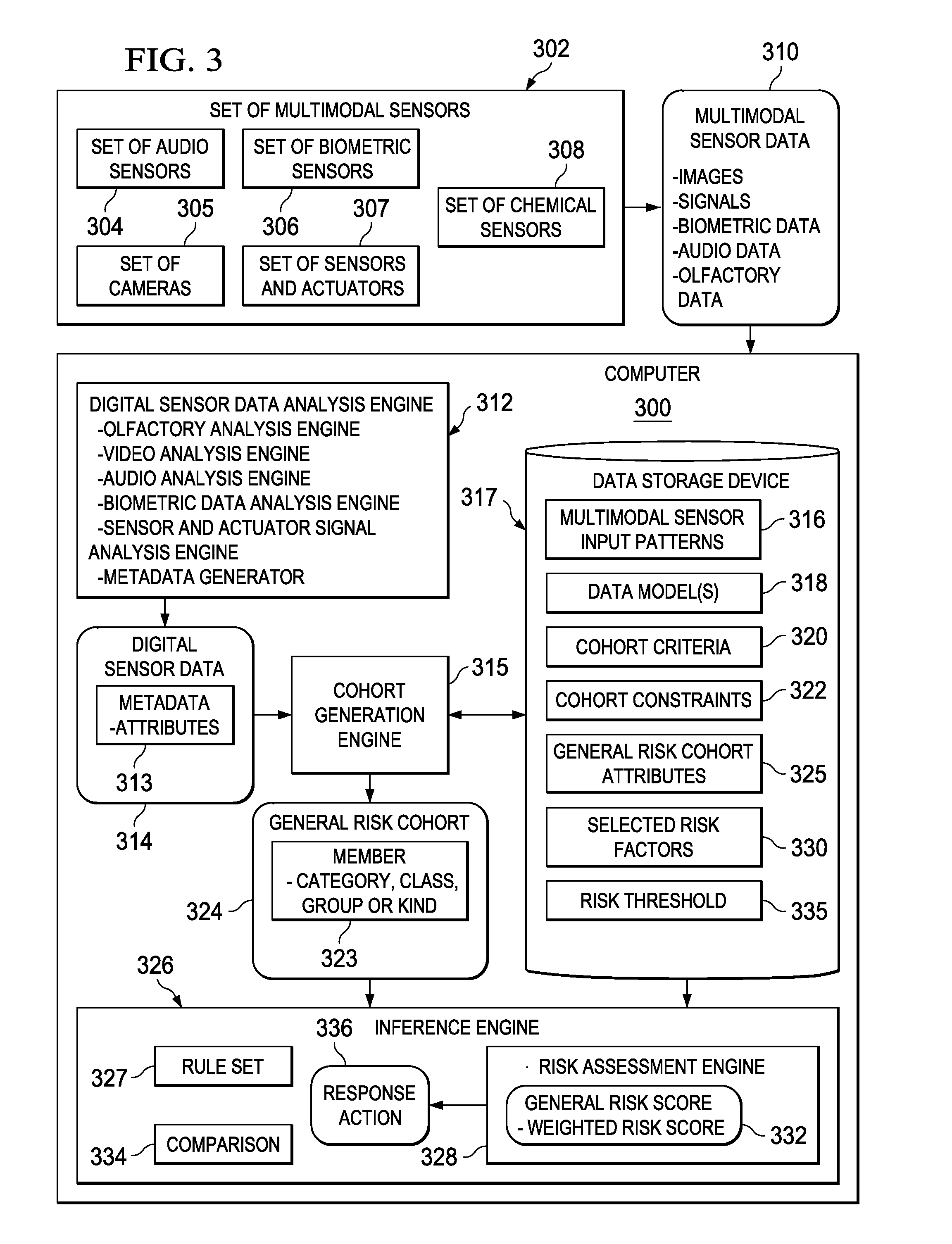
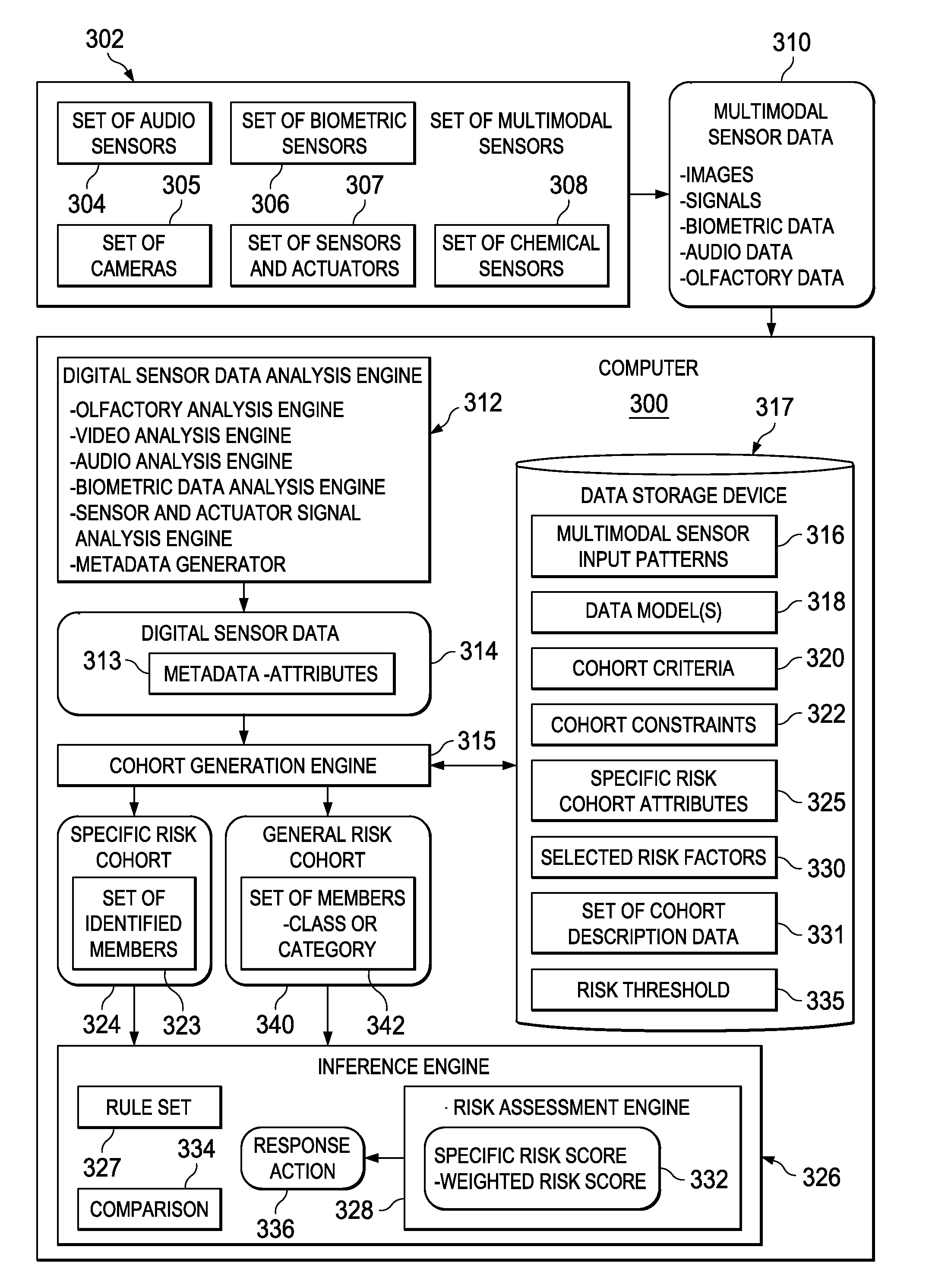
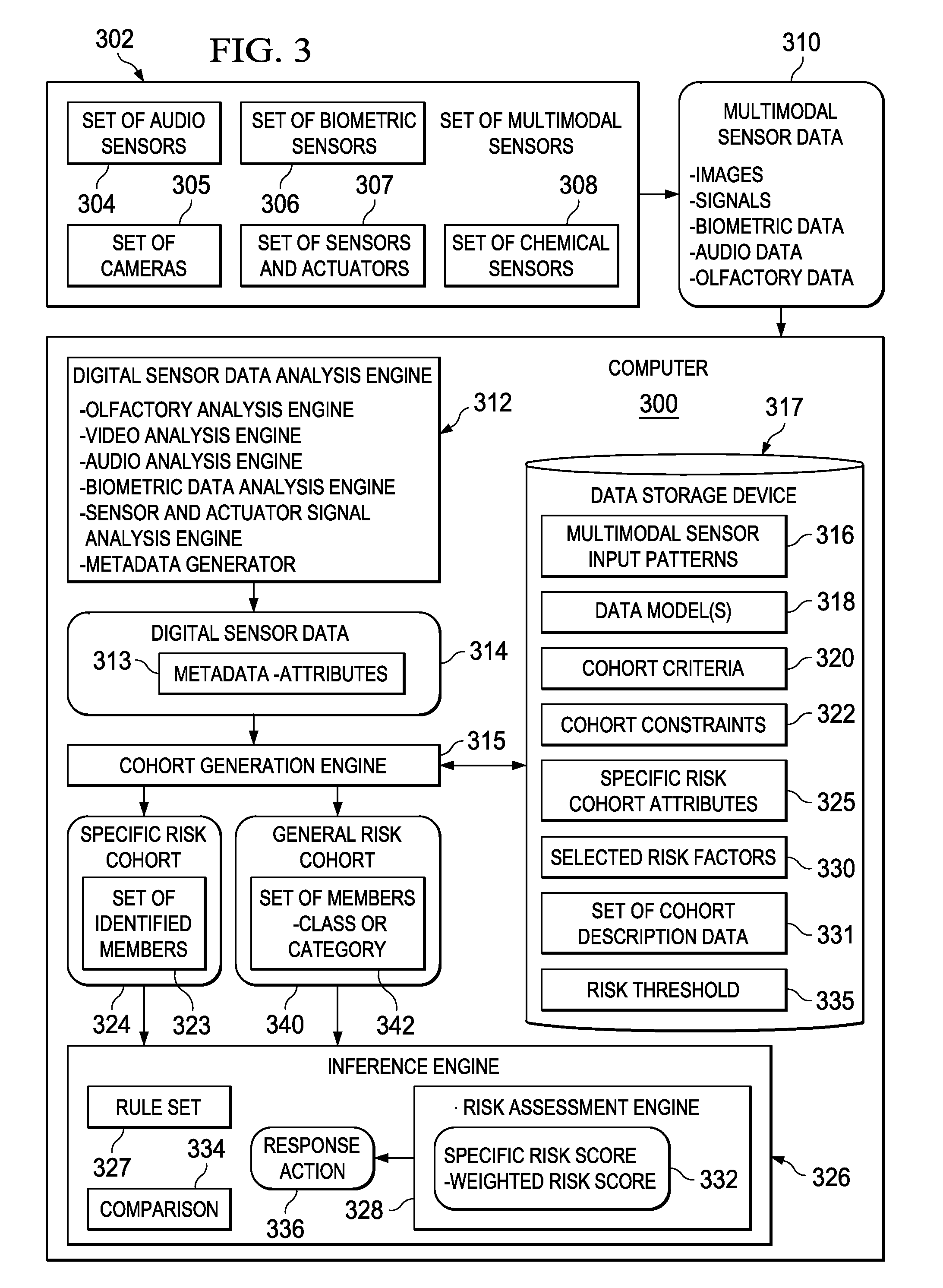
A computer implemented method, apparatus, and computer program product for generating general risk scores for general risk cohorts. Digital sensor data associated with a general risk cohort is received from a set of multimodal sensors. The digital sensor data comprises metadata describing attributes associated with at least one member of the general risk cohort. Each member of the general risk cohort comprises data describing objects belonging to a category. A general risk score for the general risk cohort is generated based on selected risk factors and the attributes associated with the at least one member of the general risk cohort. In response to a determination that the general risk score exceeds a risk threshold, a response action is initiated.
Owner:IBM CORP
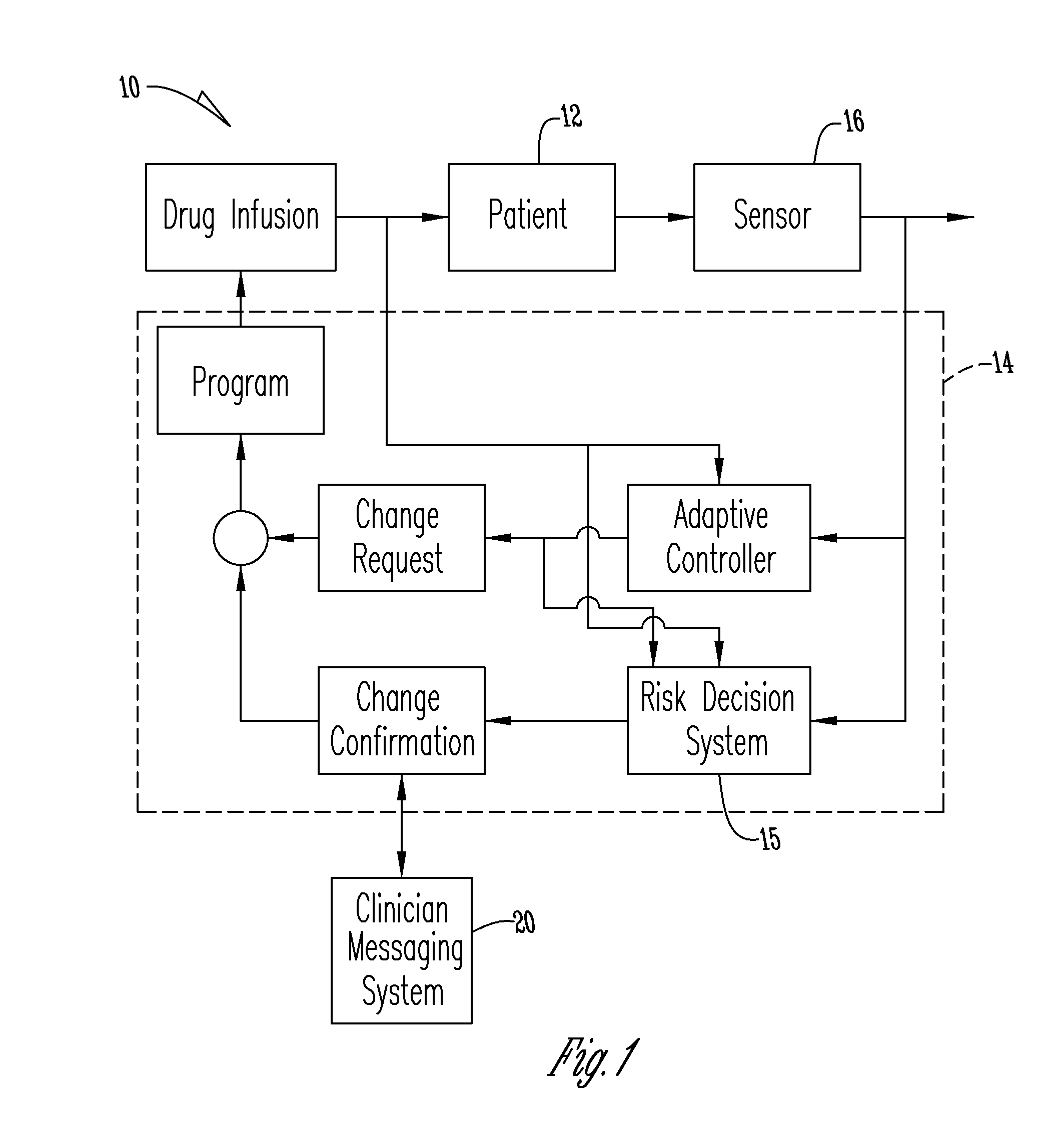
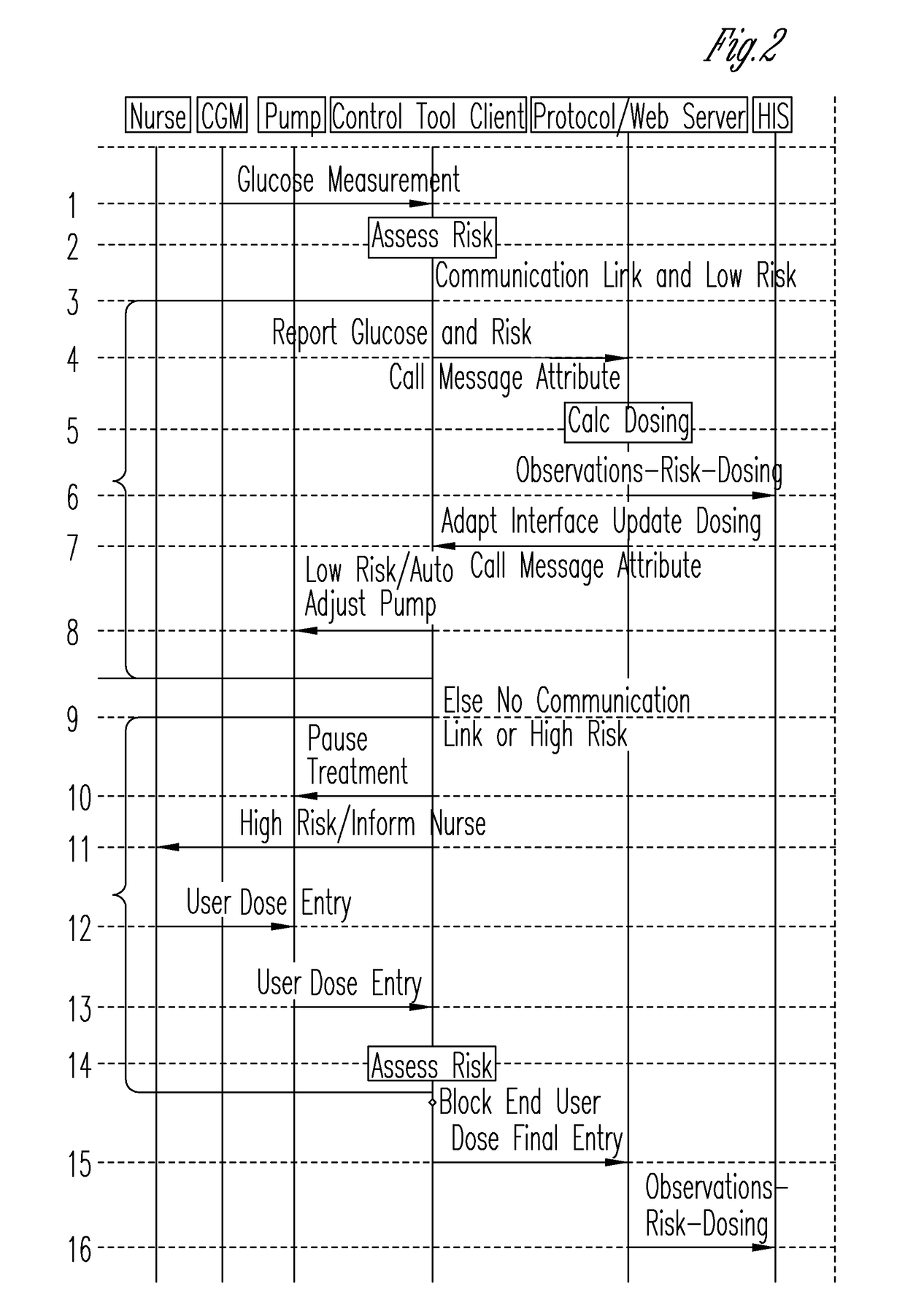
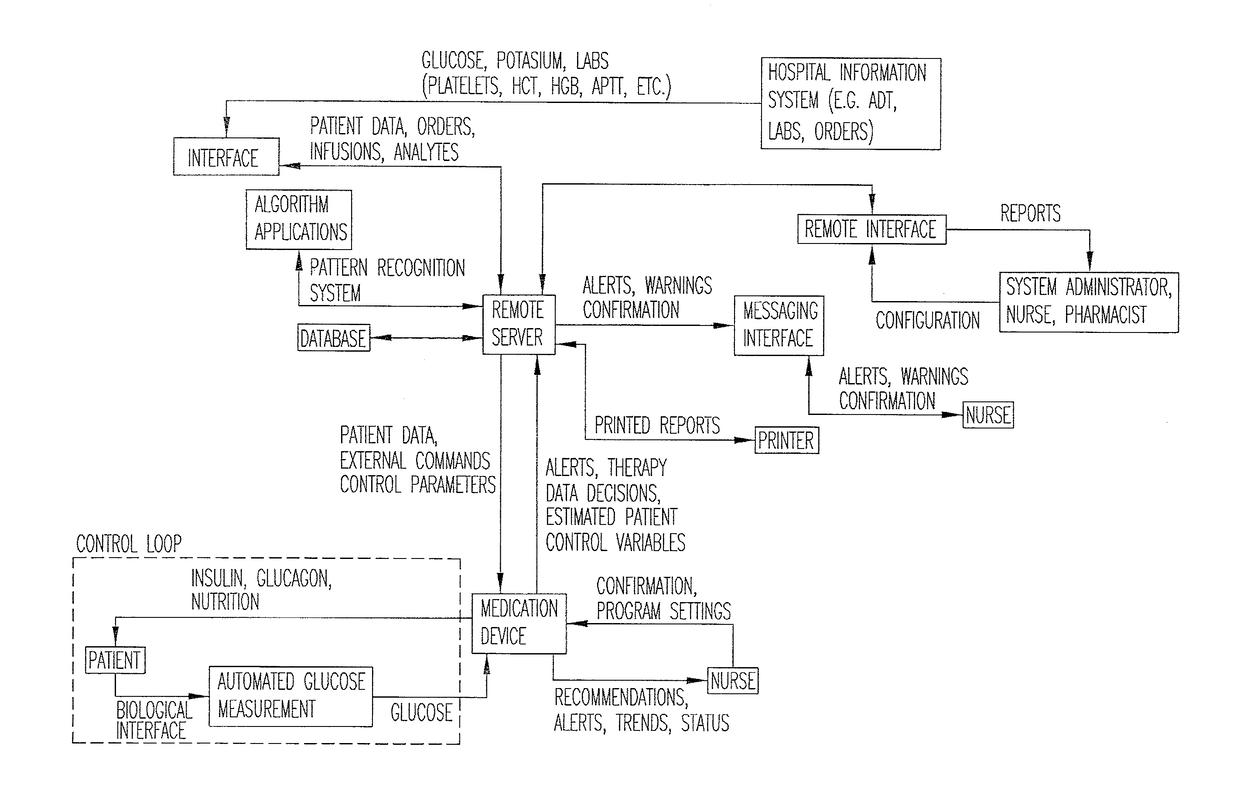
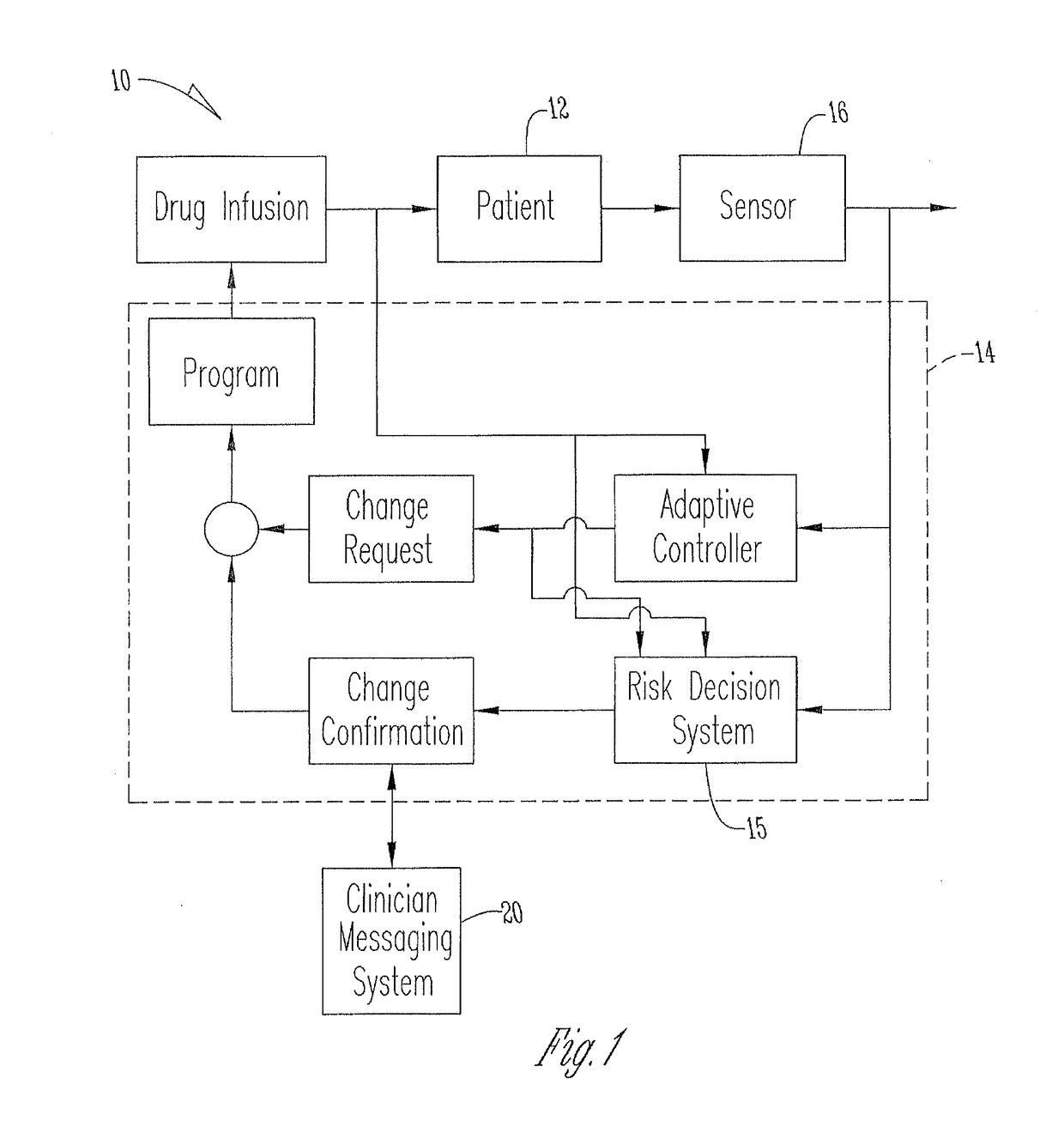
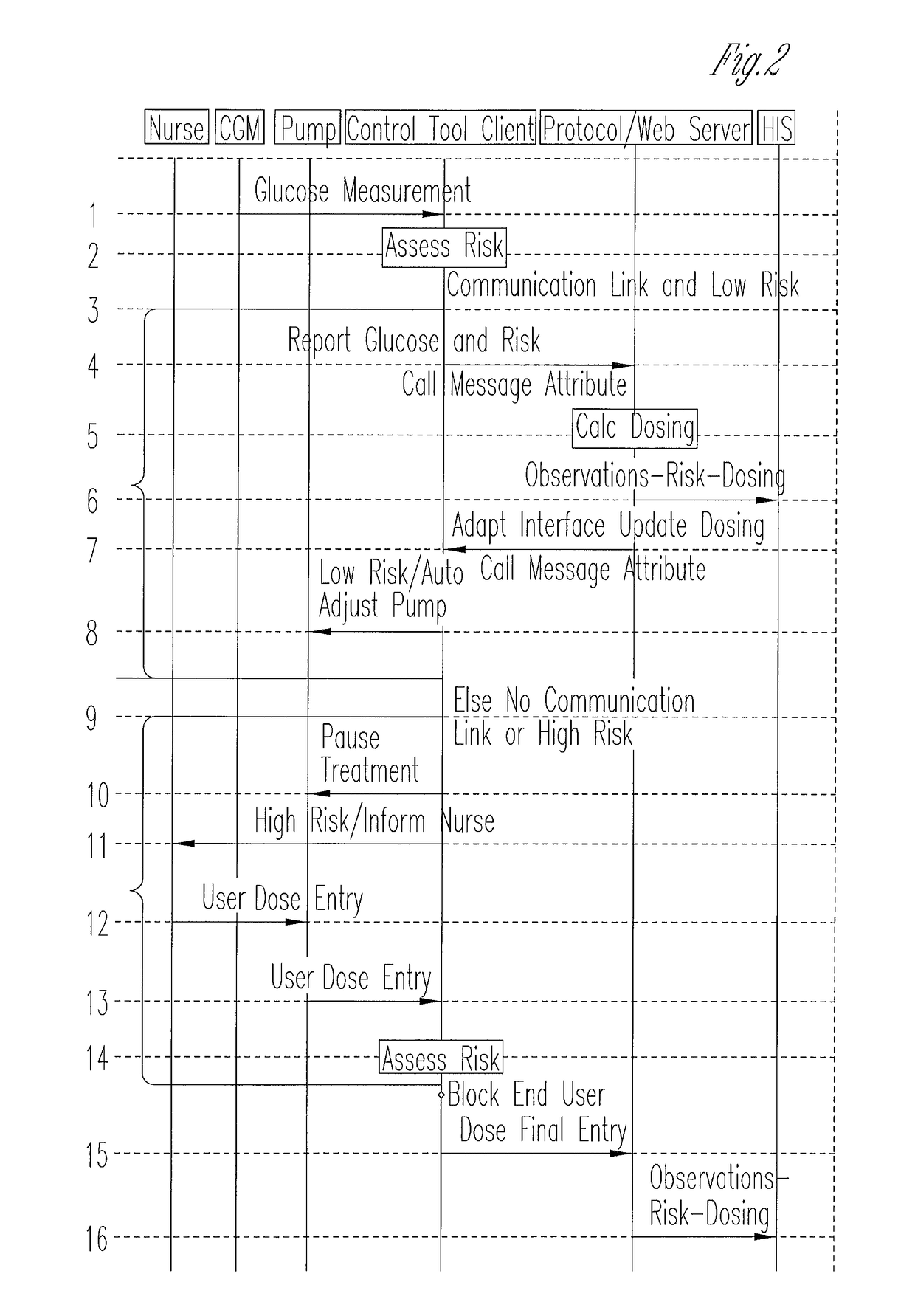
System for monitoring and delivering medication to a patient and method of using the same to minimize the risks associated with automated therapy
ActiveUS20130158504A1Potential riskRisk minimizationMedical simulationHealth-index calculationClosed loopMedical treatment
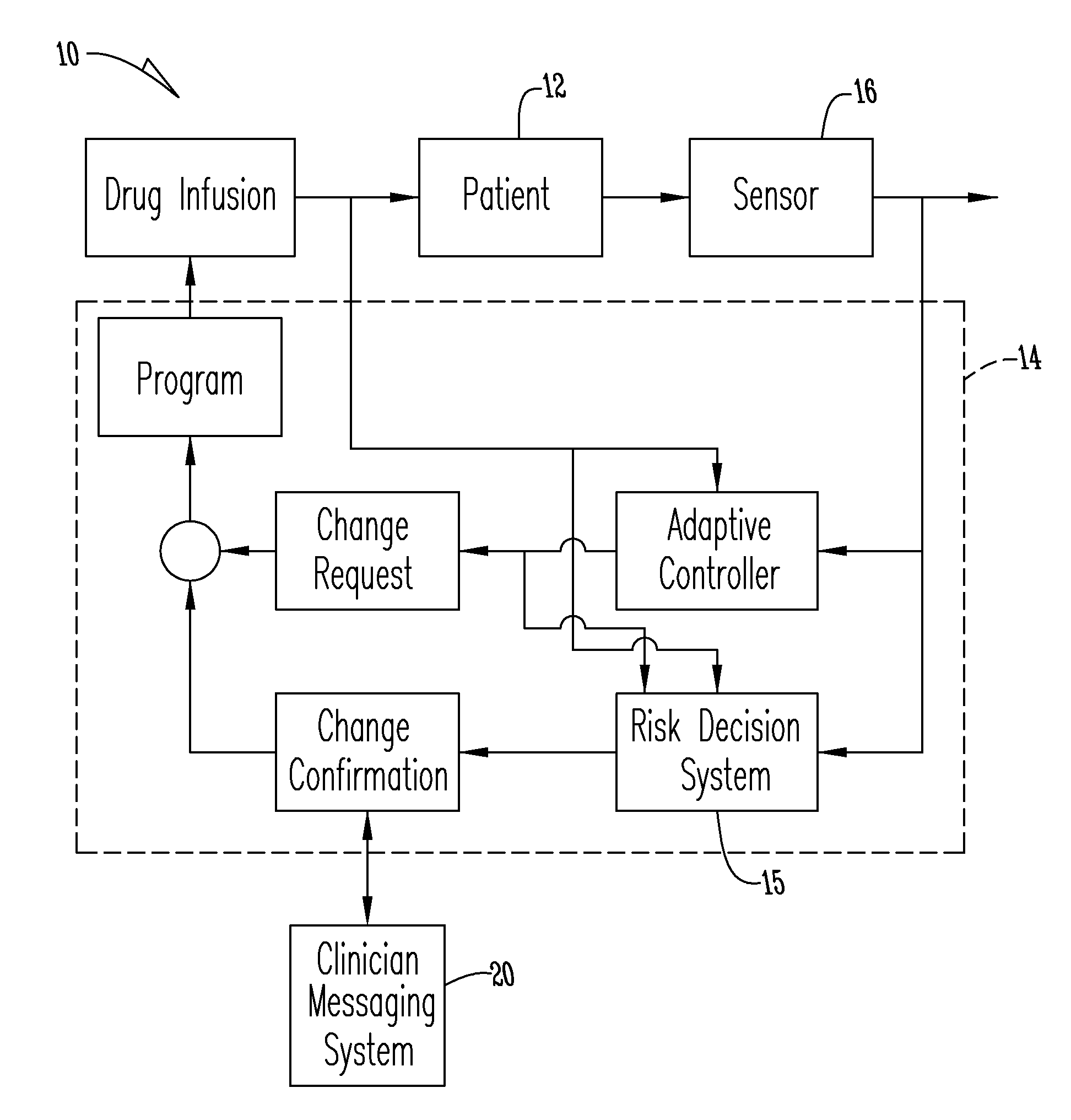
A system and method for monitoring and delivering medication to a patient includes a controller that has a control algorithm and a closed loop control that monitors the control algorithm. A sensor is in communication with the controller and monitors a medical condition. A rule base application in the controller receives data from the sensor and the closed loop control and compares the data to predetermined medical information to determine the risk of automation of therapy to the patient. The controller then provides a predetermined risk threshold where below the predetermined risk threshold automated closed loop medication therapy is provided. If the predetermined risk threshold is met or exceeded, automated therapy adjustments may not occur and user / clinician intervention is requested.
Owner:ICU MEDICAL INC
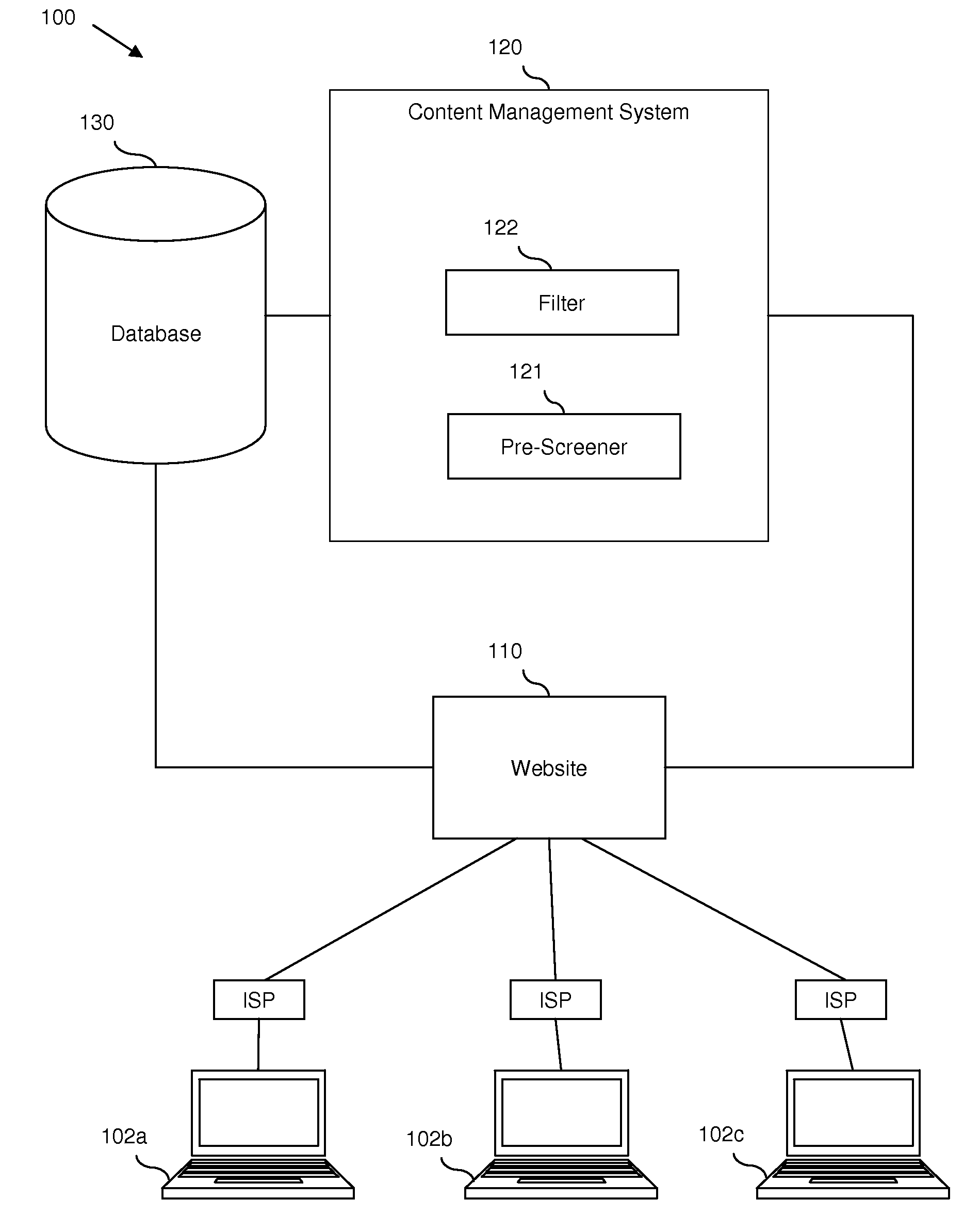
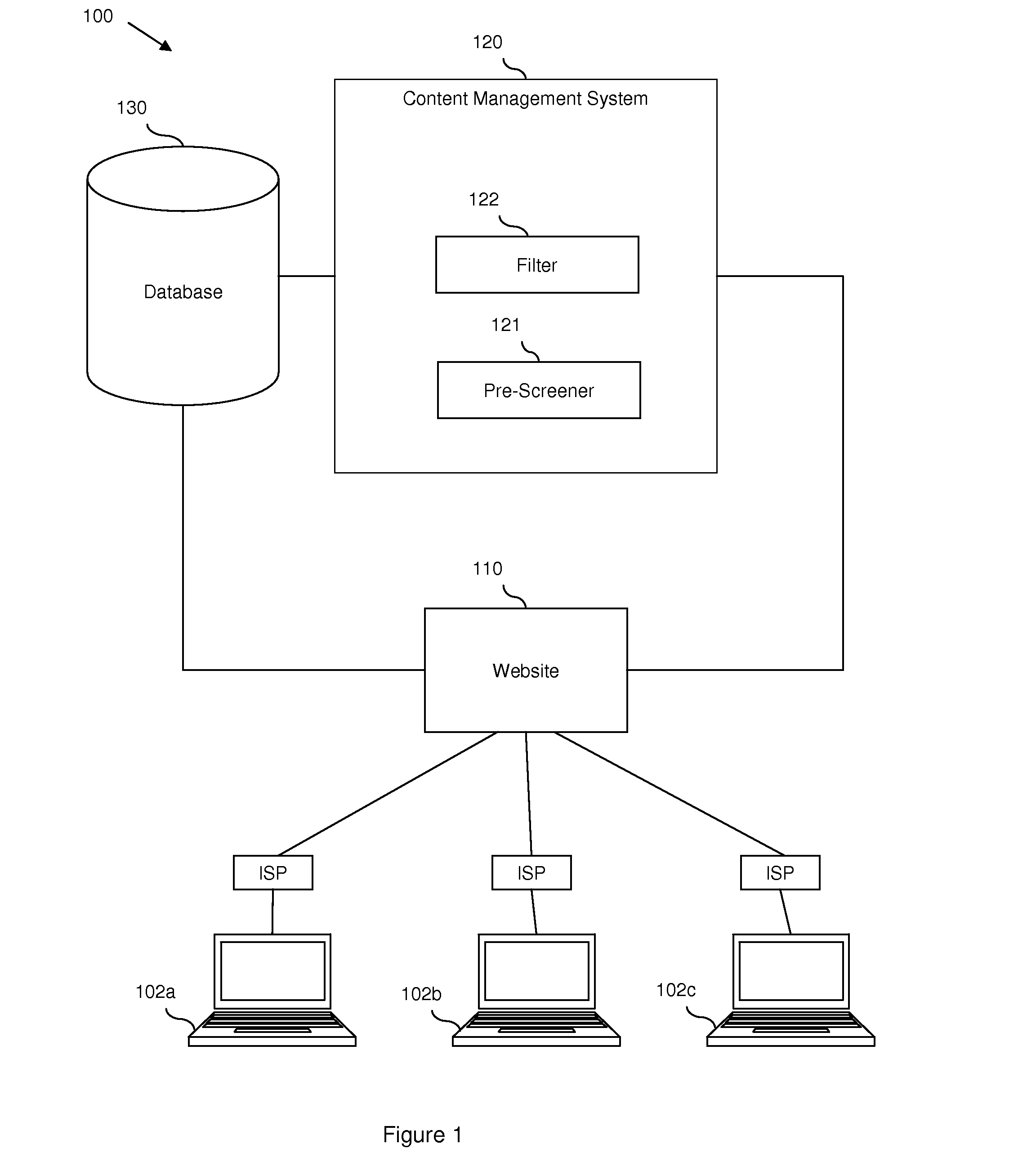
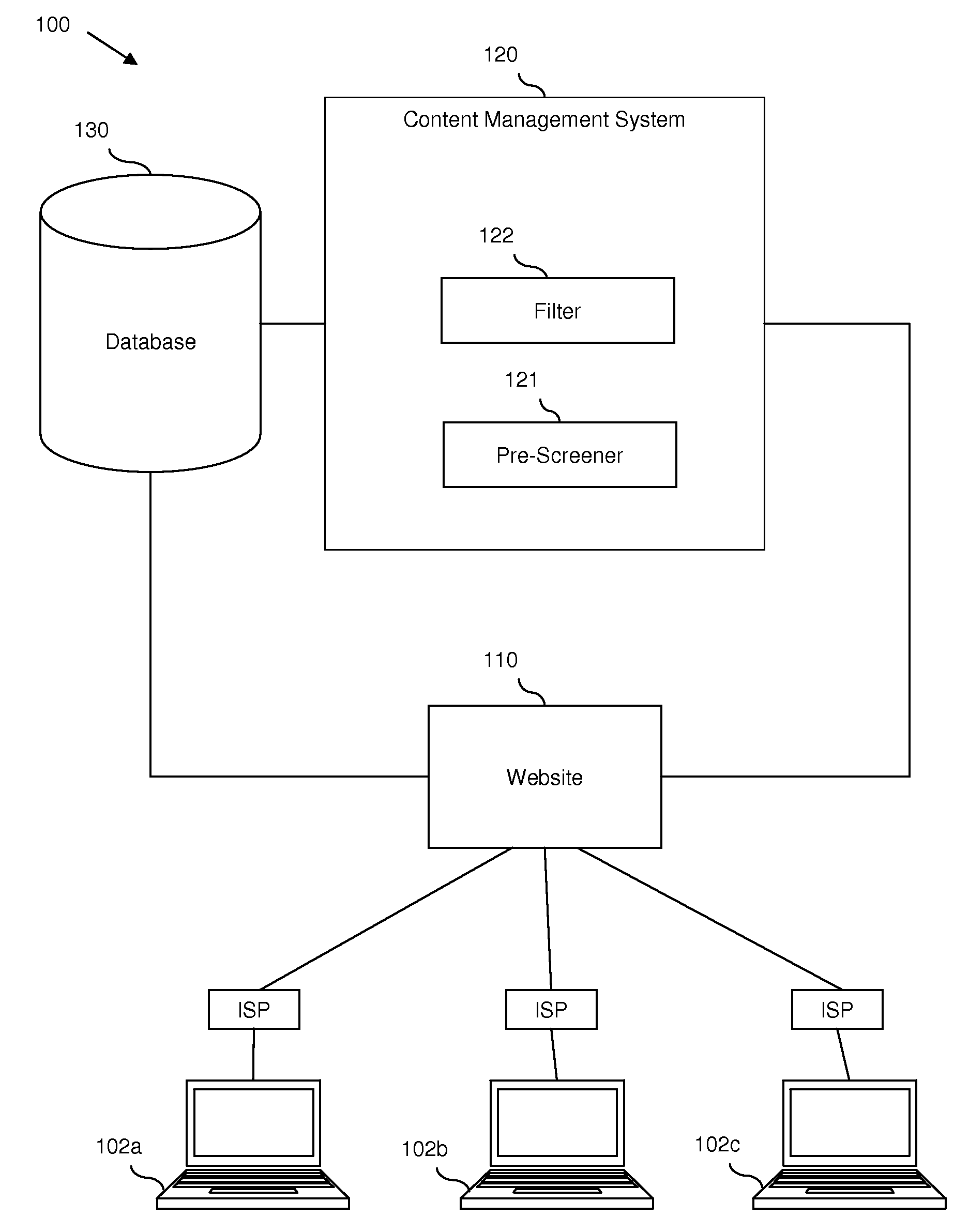
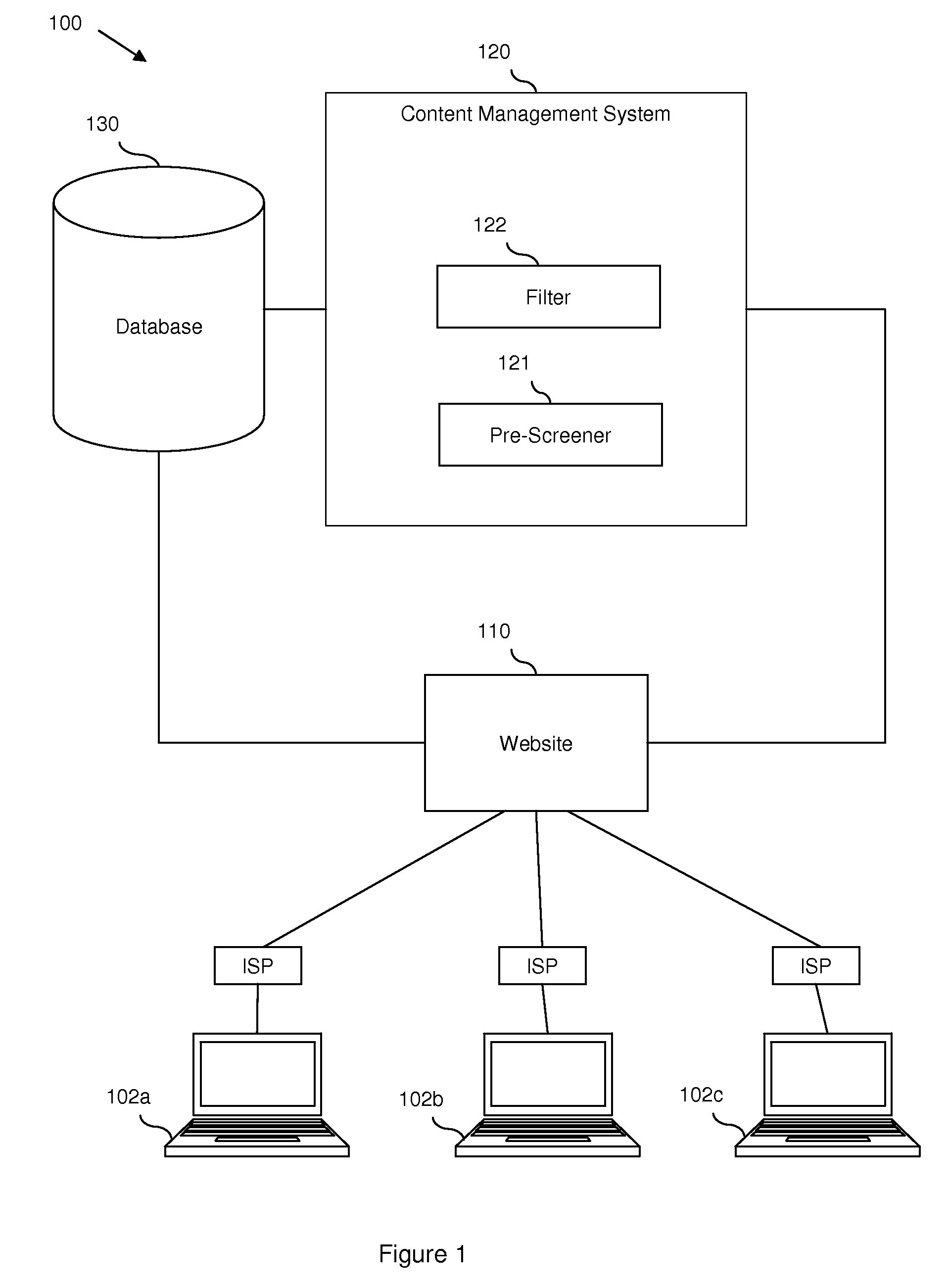
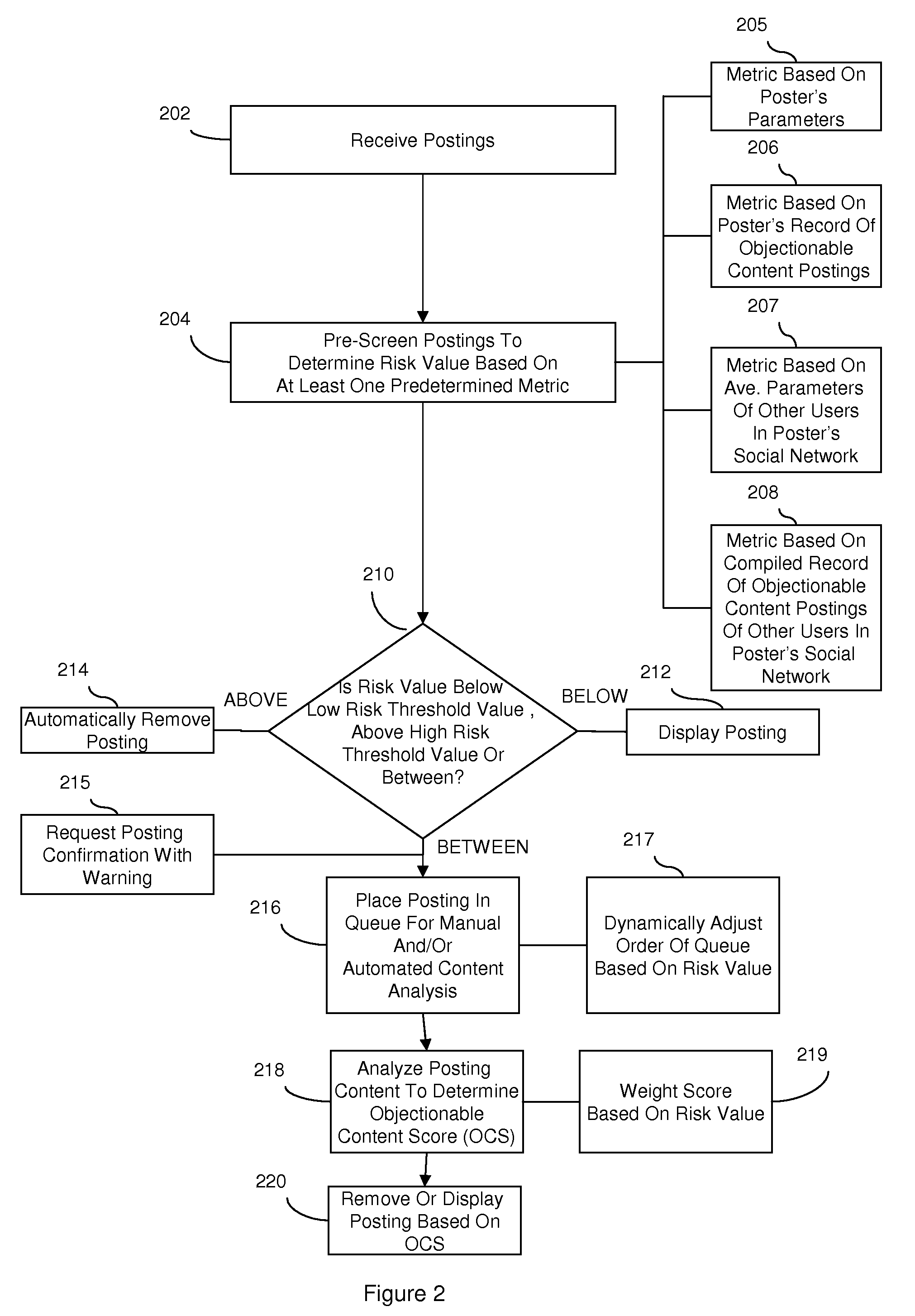
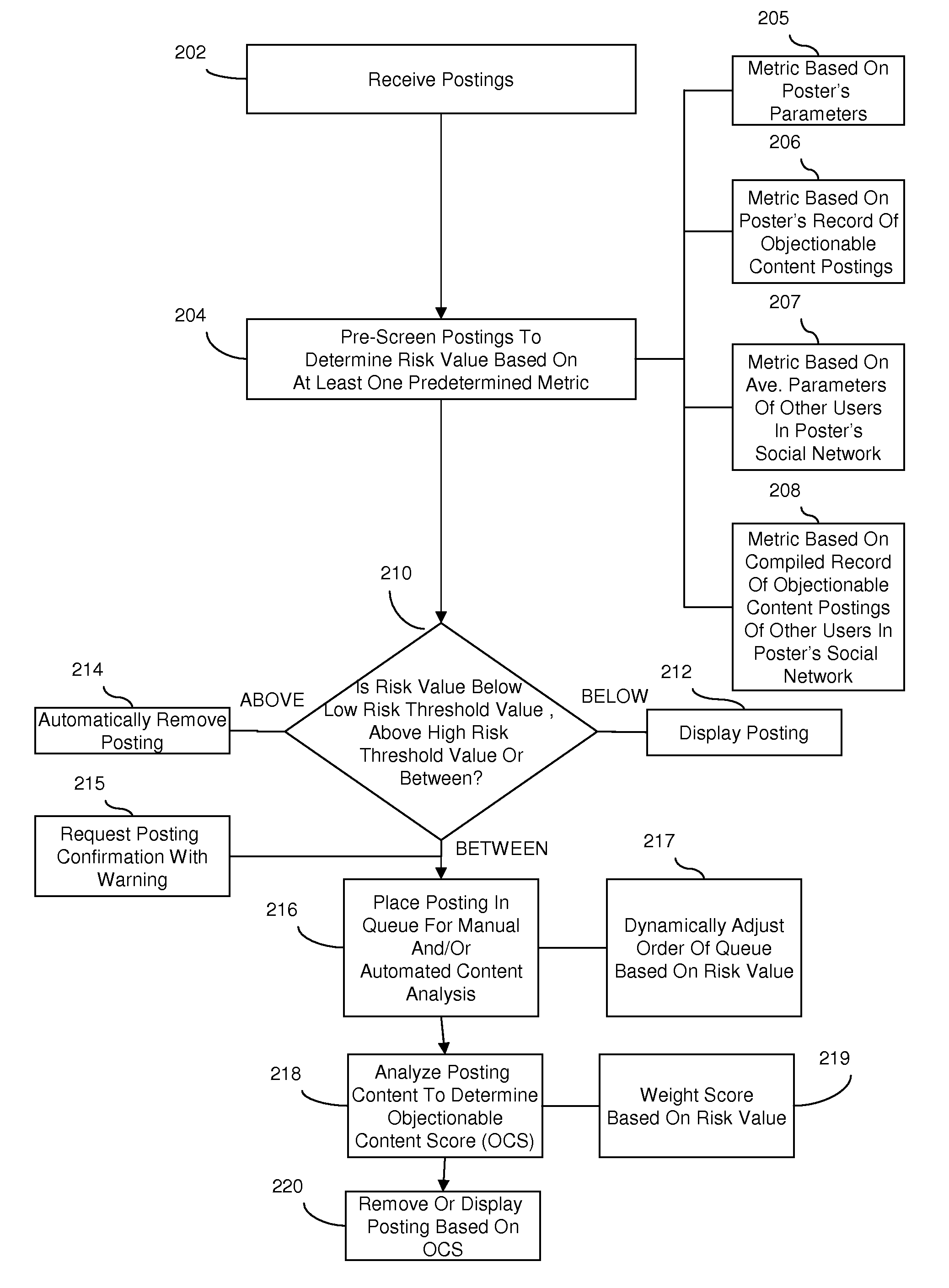
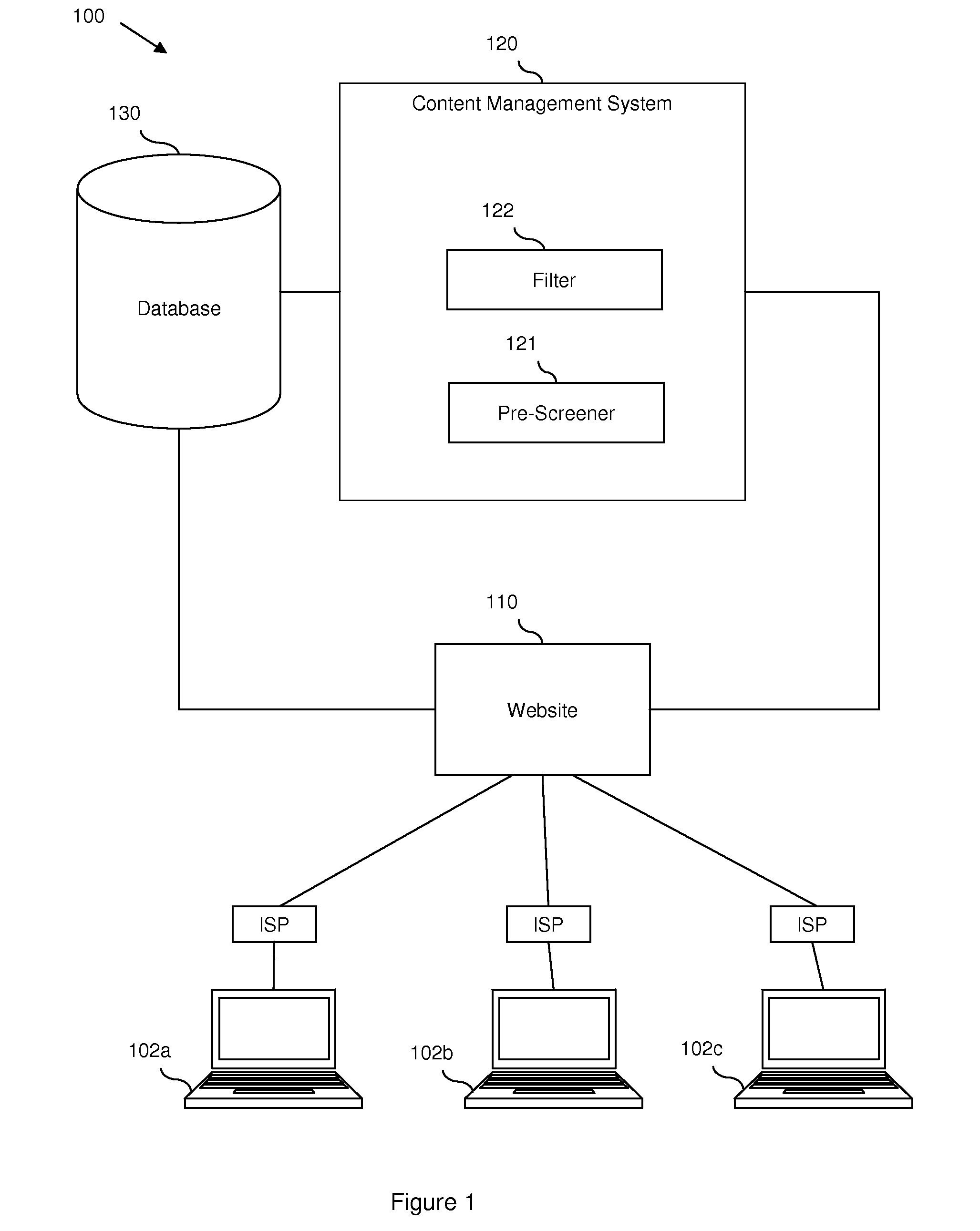
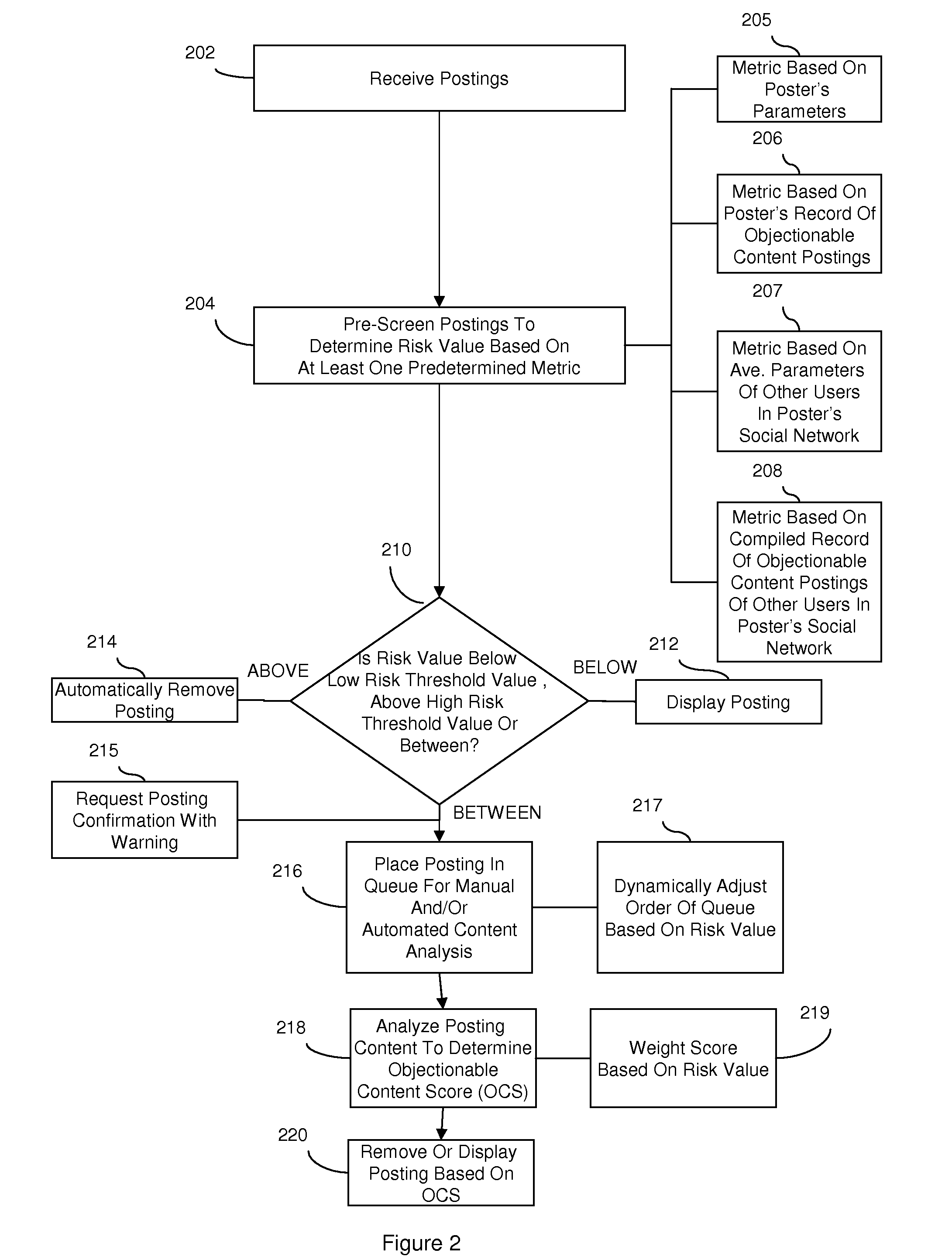
Content monitoring in a high volume on-line community application
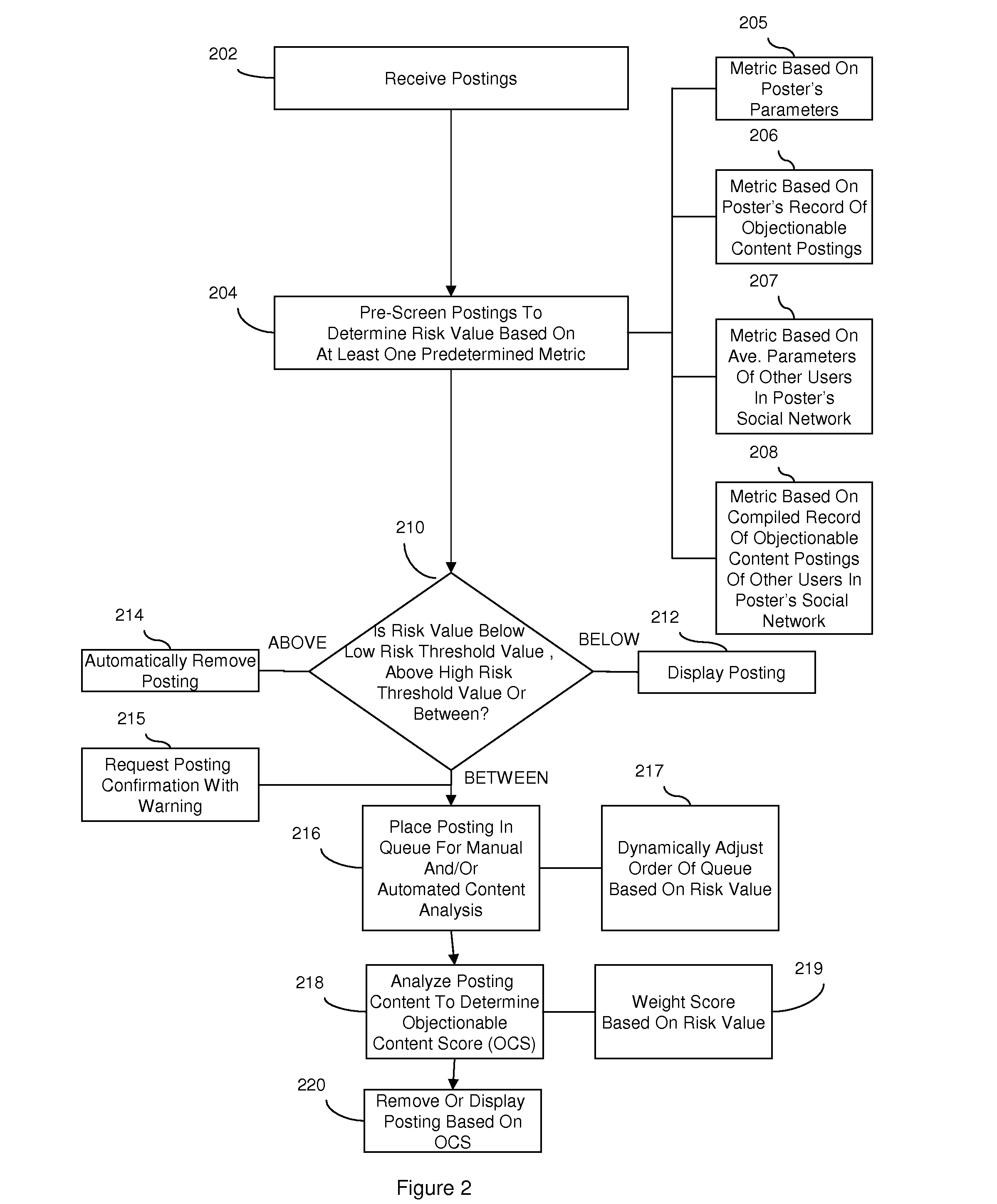
InactiveUS20080172412A1Delay minimizationMinimizing substantially exposure to riskDigital data processing detailsInput/output processes for data processingContent analyticsApplication software
Disclosed are embodiments a system and method for managing an on-line community. Electronic postings are pre-screened based on one or more metrics to determine a risk value indicative of the likelihood that an individual posting contains objectionable content. These metrics are based on the profile of a poster, including various parameters of the poster and / or the poster's record of objectionable content postings. These metrics can also be based on the social network profile of a poster, including the average of various parameters of other users in the poster's social network and / or a compiled record of objectionable content postings of other users in the poster's social network. If the risk value is relatively low, the posting can be displayed to the on-line community immediately. If the risk value is relatively high, display of the posting can be delayed until further content analysis is completed. Finally, if the risk value is above a predetermined high risk threshold value, the posting can be removed automatically.
Owner:IBM CORP
Adaptive, multi-modal fraud detection system
ActiveUS20190037081A1Facilitate communicationEfficient and accurate detectionInterconnection arrangementsSpecial service for subscribersSelf adaptiveManagement system
A system and method for fraud detection and management are provided. The system includes a first communication device that receives a phone call from a second communication device, wherein a call flow of the phone call comprises one or more distinct phases. The system also includes a fraud detection and management system (FDMS) platform that determines whether the phone call exceeds a predetermined risk threshold at each distinct phase of the call flow.
Owner:VAIL SYST
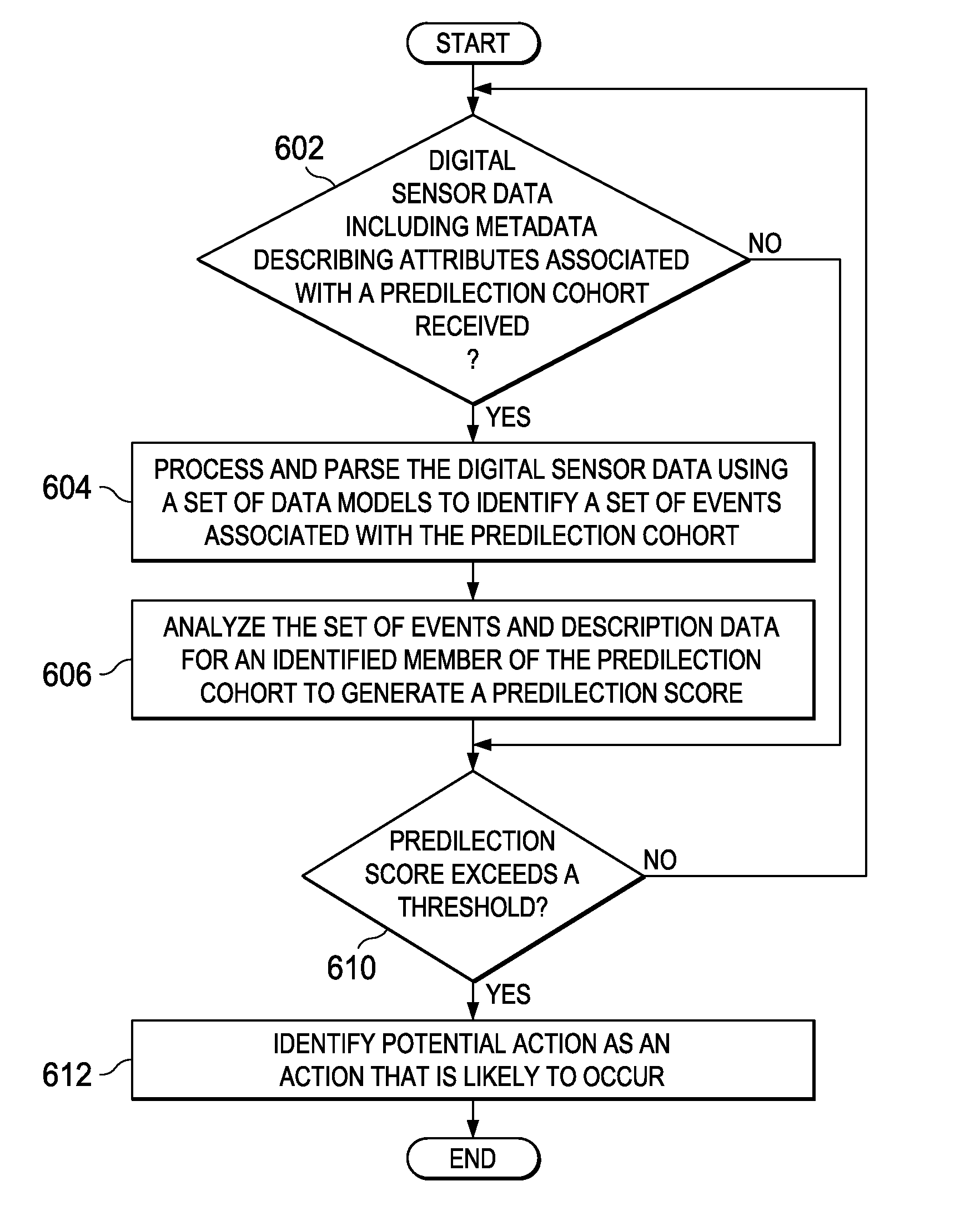
Generating Specific Risk Cohorts
A computer implemented method, apparatus, and computer program product for generating risk scores for specific risk cohorts. Digital sensor data associated with a specific risk cohort is received from a set of multimodal sensors. The specific risk cohort includes a set of identified cohort members. The digital sensor data includes metadata describing attributes associated with at least one cohort member in the set of identified cohort members. Description data for each cohort member in the set of identified cohort members is retrieved to form a set of cohort description data. The description data for each cohort member comprises data describing a previous history of the cohort member or a current status of the cohort member. The cohort member is a person, animal, plant, thing, or location. A specific risk score is generated for the specific risk cohort based on selected risk factors, the attributes associated with the at least one identified member, and the set of cohort description data. A response action is initiated in response to a determination that the specific risk score exceeds a risk threshold.
Owner:IBM CORP
Generating Predilection Cohorts
A computer implemented method, apparatus, and computer program product for generating risk scores for specific risk cohorts. Digital sensor data associated with a specific risk cohort is received from a set of multimodal sensors. The specific risk cohort includes a set of identified cohort members. The digital sensor data includes metadata describing attributes associated with at least one cohort member in the set of identified cohort members. Description data for each cohort member in the set of identified cohort members is retrieved to form a set of cohort description data. The description data for each cohort member comprises data describing a previous history of the cohort member or a current status of the cohort member. The cohort member is a person, animal, plant, thing, or location. A specific risk score is generated for the specific risk cohort based on selected risk factors, the attributes associated with the at least one identified member, and the set of cohort description data. A response action is initiated in response to a determination that the specific risk score exceeds a risk threshold.
Owner:NUANCE COMM INC
System for monitoring and delivering medication to a patient and method of using the same to minimize the risks associated with automated therapy
ActiveUS10022498B2Potential riskRisk minimizationMedical simulationHealth-index calculationClosed loopCvd risk
A system and method for monitoring and delivering medication to a patient includes a controller that has a control algorithm and a closed loop control that monitors the control algorithm. A sensor is in communication with the controller and monitors a medical condition. A rule base application in the controller receives data from the sensor and the closed loop control and compares the data to predetermined medical information to determine the risk of automation of therapy to the patient. The controller then provides a predetermined risk threshold where below the predetermined risk threshold automated closed loop medication therapy is provided. If the predetermined risk threshold is met or exceeded, automated therapy adjustments may not occur and user / clinician intervention is requested.
Owner:ICU MEDICAL INC
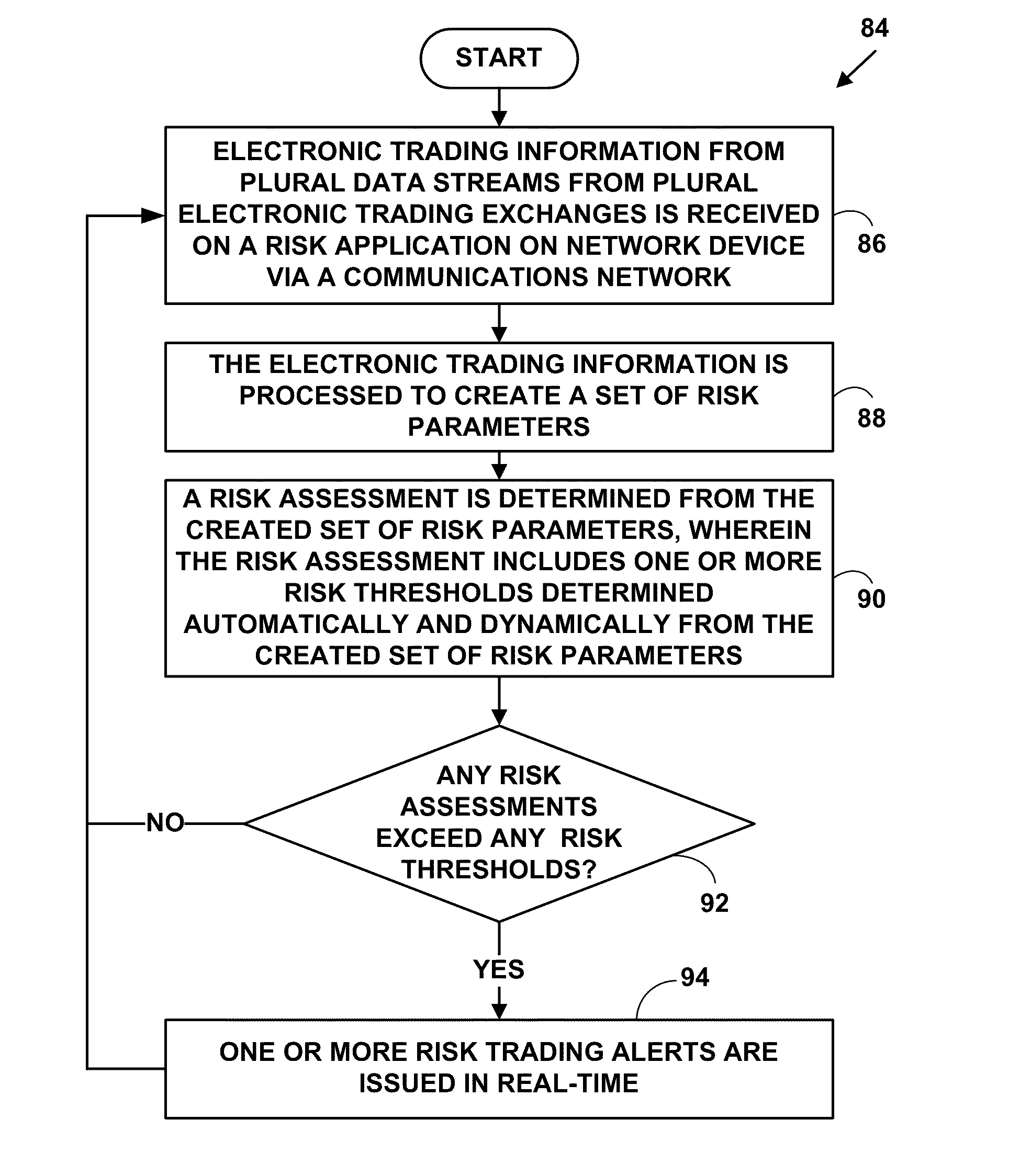
Method and system for providing electronic information for risk assesement and management via net worth for multi-market electronic trading
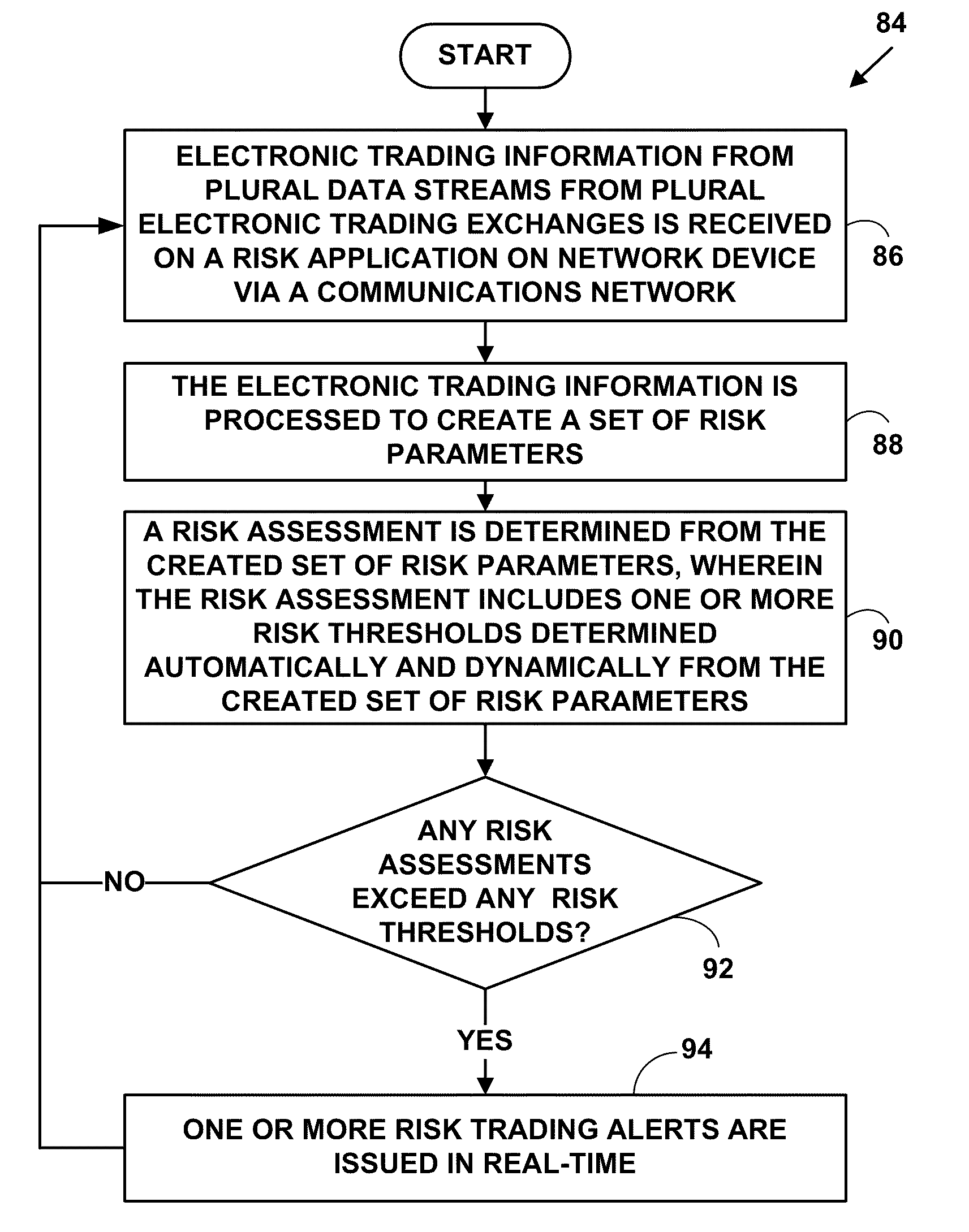
A method and system for providing risk management, reporting and assessment for multi-market electronic trading. The method and system allow risk assessment management and reporting to be determined using current and historical trading losses over a pre-determined trading period compared against a pre-determined percentage of current and historical net worth values for electronic trading at a trading firm, a trading firm office and a trading account. Risk thresholds are selectively and dynamically configurable for automatically displaying risk information for and automatically disabling electronic trading when risk thresholds are exceeded.
Owner:ROSENTHAL COLLINS GROUP
Content monitoring in a high volume on-line community application
InactiveUS20080177834A1Minimize exposureDelay minimizationMultiple digital computer combinationsContent analyticsApplication software
Disclosed are embodiments a system and method for managing an on-line community. Electronic postings are pre-screened based on one or more metrics to determine a risk value indicative of the likelihood that an individual posting contains objectionable content. These metrics are based on the profile of a poster, including various parameters of the poster and / or the poster's record of objectionable content postings. These metrics can also be based on the social network profile of a poster, including the average of various parameters of other users in the poster's social network and / or a compiled record of objectionable content postings of other users in the poster's social network. If the risk value is relatively low, the posting can be displayed to the on-line community immediately. If the risk value is relatively high, display of the posting can be delayed until further content analysis is completed. Finally, if the risk value is above a predetermined high risk threshold value, the posting can be removed automatically.
Owner:INT BUSINESS MASCH CORP
Content monitoring in a high volume on-line community application
InactiveUS7523138B2Minimize exposureDelay minimizationSpecial data processing applicationsInput/output processes for data processingContent analyticsApplication software
Disclosed are embodiments a system and method for managing an on-line community. Electronic postings are pre-screened based on one or more metrics to determine a risk value indicative of the likelihood that an individual posting contains objectionable content. These metrics are based on the profile of a poster, including various parameters of the poster and / or the poster's record of objectionable content postings. These metrics can also be based on the social network profile of a poster, including the average of various parameters of other users in the poster's social network and / or a compiled record of objectionable content postings of other users in the poster's social network. If the risk value is relatively low, the posting can be displayed to the on-line community immediately. If the risk value is relatively high, display of the posting can be delayed until further content analysis is completed. Finally, if the risk value is above a predetermined high risk threshold value, the posting can be removed automatically.
Owner:INT BUSINESS MASCH CORP
System for monitoring and delivering medication to a patient and method of using the same to minimize the risks associated with automated therapy
ActiveUS9724470B2Potential riskRisk minimizationDrug and medicationsMedical devicesRemote systemClosed loop
A system and method for monitoring and delivering medication to a patient. The system includes a controller that has a control algorithm and a closed loop control that monitors the control algorithm. A sensor is in communication with the controller and monitors a medical condition. A rule based application in the controller receives data from the sensor and the closed loop control and compares the data to predetermined medical information to determine the risk of automation of therapy to the patient. A system monitor is also in communication with the controller to monitor system, remote system, and network activity and conditions. The controller then provides a predetermined risk threshold where below the predetermined risk threshold automated closed loop medication therapy is provided. If the predetermined risk threshold is met or exceeded, automated therapy adjustments may not occur and user / clinician intervention is requested.
Owner:ICU MEDICAL INC
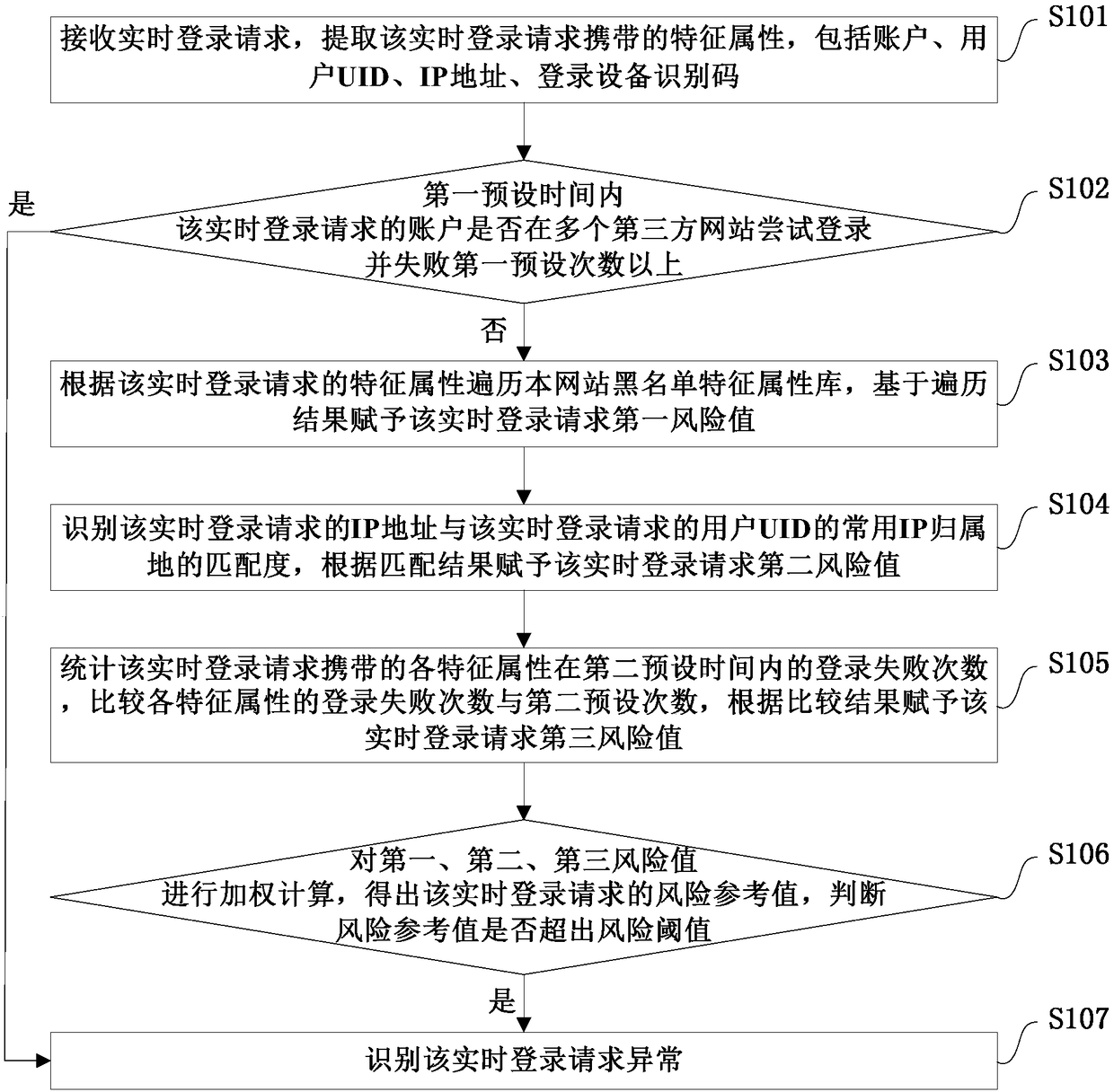
Abnormal login identification method and system, storage medium and electronic equipment
ActiveCN108092975AEnsure safetyAccurate and effective identification and defenseTransmissionThird partyIp address
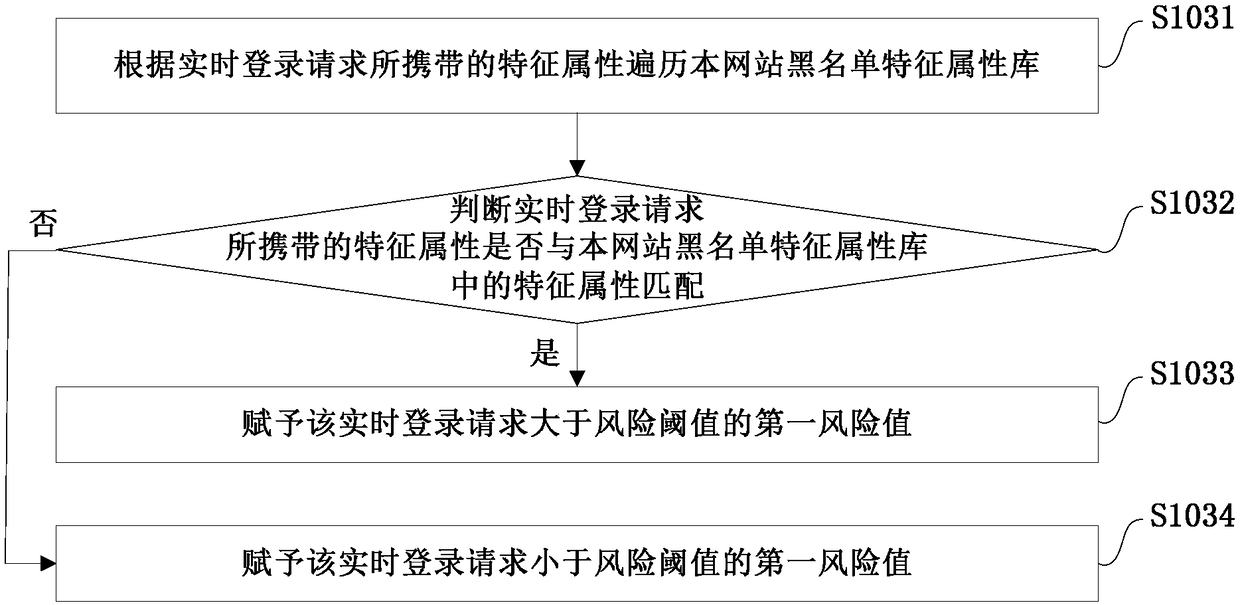
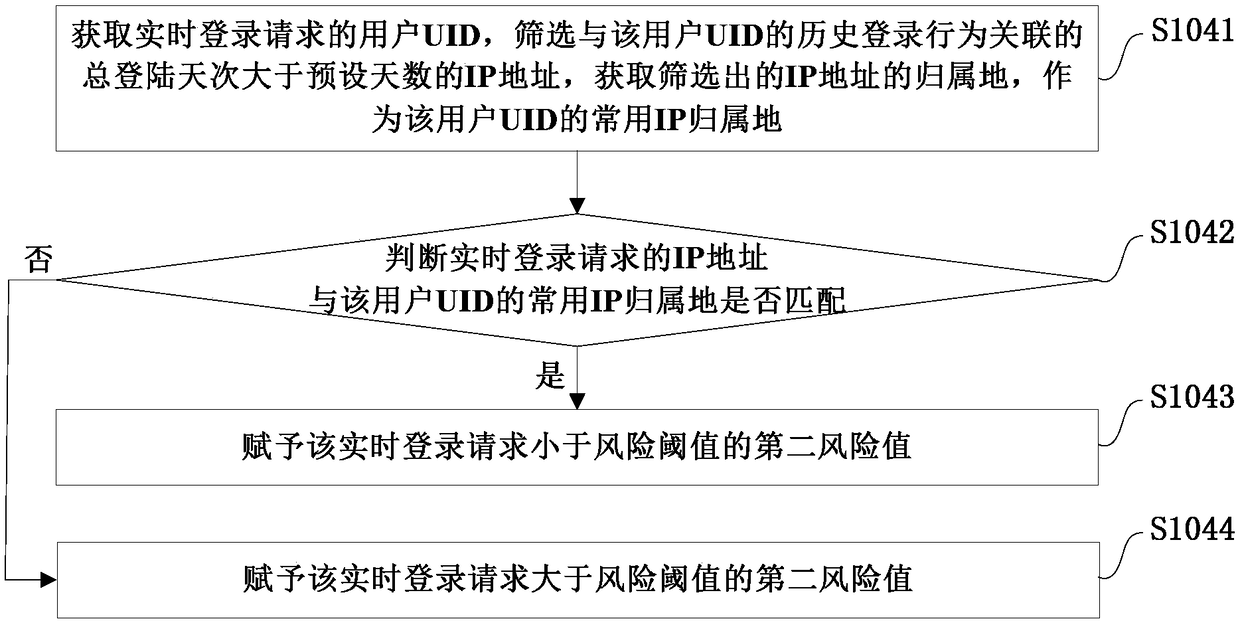
The invention provides an abnormal login identification method and system, a storage medium and electronic equipment. The method includes the following steps: receiving and extracting characteristic attributes carried in a real-time login request; judging whether an account of the real-time login request tries to log in to multiple third-party websites within a preset time and fails more than a preset number of times, and if yes, identifying the login as an abnormal login; traversing a blacklist library according to the extracted characteristic attributes, and assigning a first risk value based on a traversal result; assigning a second risk value according to the matching degree between an IP address of the real-time login request and a common IP attribution of a UID of the real-time loginrequest; comparing the number of login failures and the number of preset times of each characteristic attribute within the preset time, and assigning a third risk value according to a comparison result; and performing weighted calculation on the first, second and third risk values to obtain a risk reference value of the real-time login request, and identifying the login as the abnormal login whenthe risk reference value exceeds a risk threshold. According to the scheme of the invention, by combining the external anti-scanning identification and the internal multidimensional identification, abnormal login behaviors can be intercepted to a maximum extent.
Owner:SHANGHAI CTRIP COMMERCE CO LTD
Cloud-based analytics to mitigate abuse from internet trolls
An approach is provided in which an information handling system creates a first language profile corresponding to a first user account in response to determining that the first user account generated a first offensive message. The information handling system computes an accumulated risk score of the first user account based on correlating the first language profile to a second language profile corresponding to a second user account that generated a second offensive post. The accumulated risk score is based on a first risk score of the first user account and a second risk score of the second user account. In turn, the information handling system generates a notification in response to determining that the accumulated risk score reaches a risk threshold.
Owner:IBM CORP
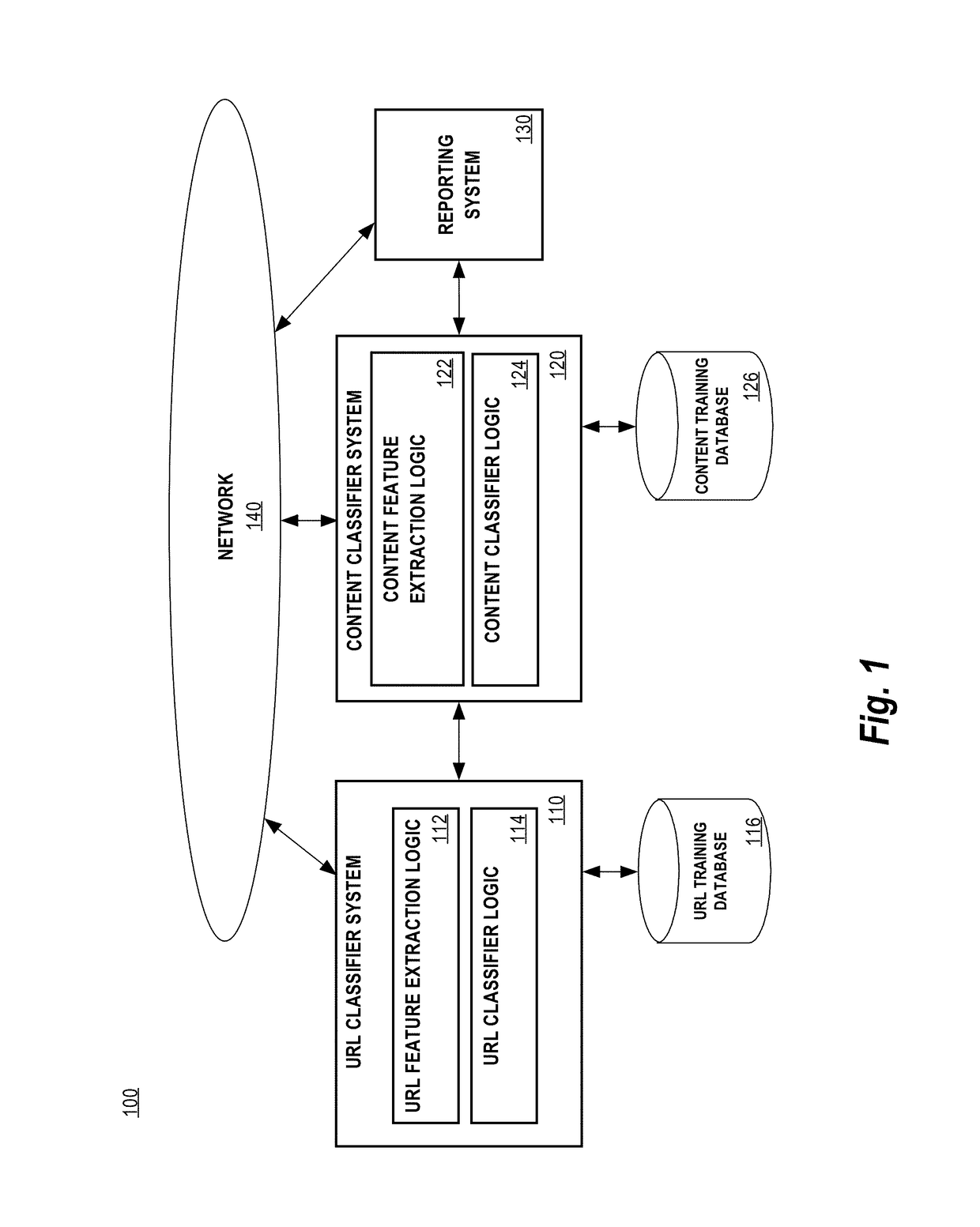
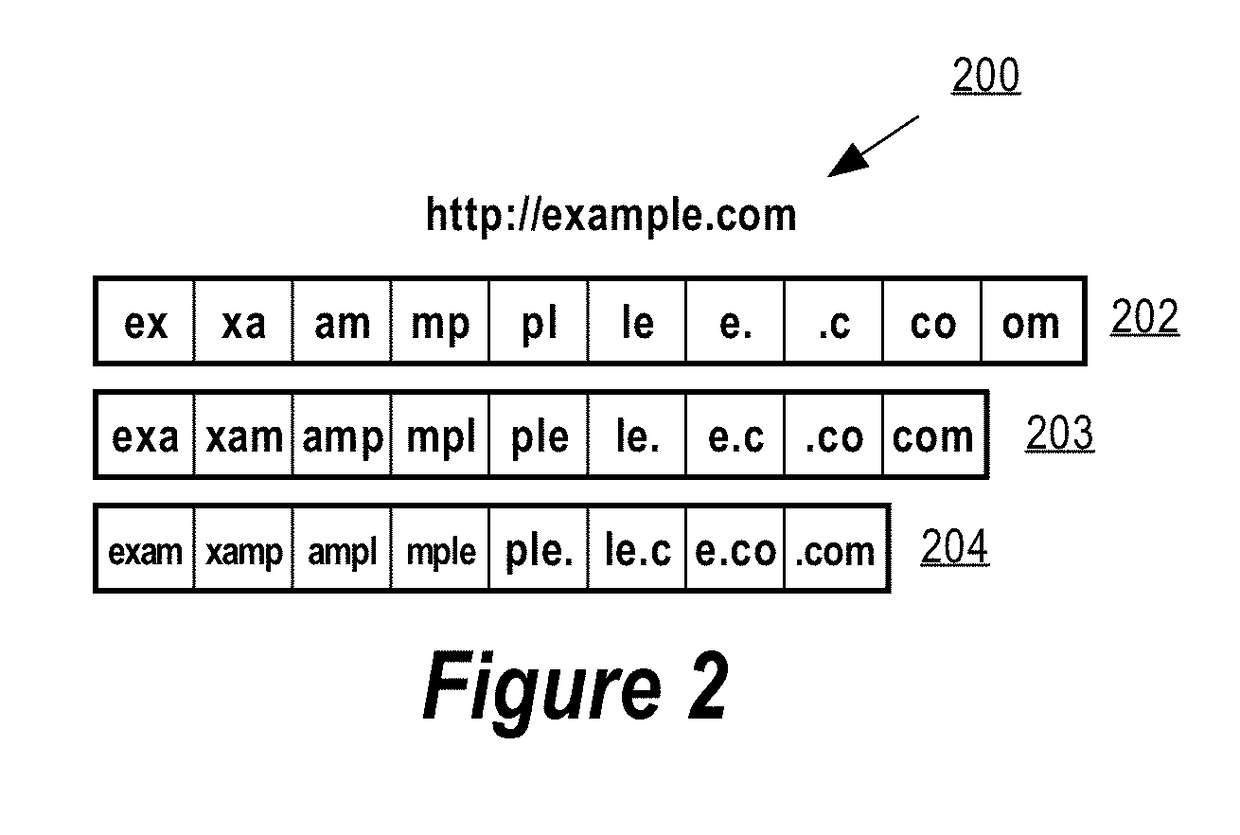
Using machine learning for classification of benign and malicious webpages
In an embodiment, a data processing method providing an improvement in computer security, comprises selecting a uniform resource location (URL) for classification wherein the selected URL is associated with a webpage; determining a URL risk score for the selected URL; comparing the URL risk score to a URL risk threshold; in response to determining that the URL risk score exceeds the URL risk threshold, determining a maliciousness risk score for the webpage content associated with the selected URL; comparing the maliciousness risk score to a maliciousness risk threshold; and classifying the URL based on the comparison between the maliciousness risk score and the maliciousness risk threshold; in response to determining that the maliciousness risk score exceeds the maliciousness risk threshold, classifying the URL as malicious; in response to determining that the maliciousness risk score does not exceed the maliciousness risk threshold, classifying the URL as benign.
Owner:CLOUDFLARE
Method and system for monitoring electronic bank risks
InactiveCN101706937AReduce transaction riskImprove securityFinancePlatform integrity maintainanceRisk identificationData needs
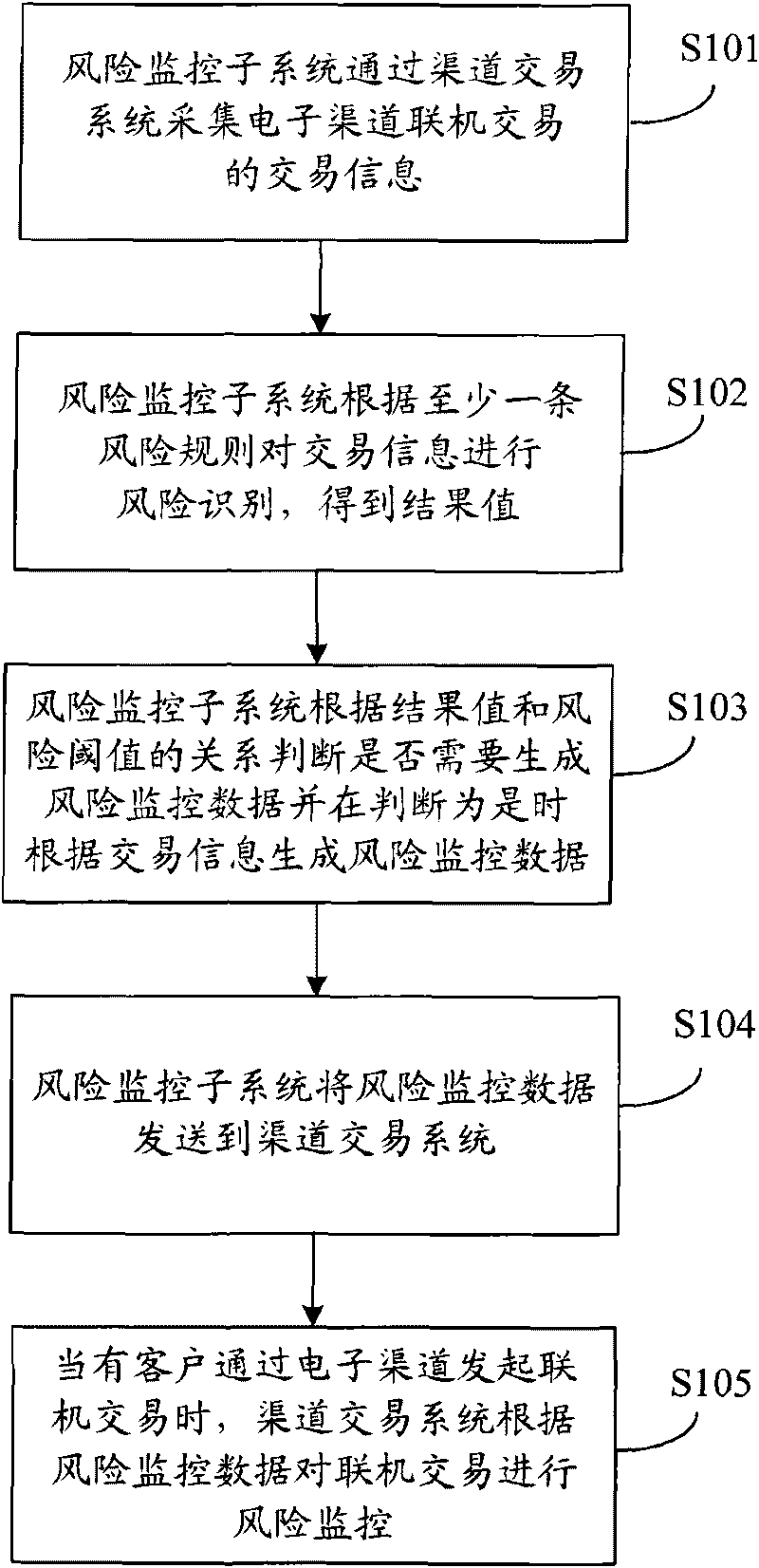
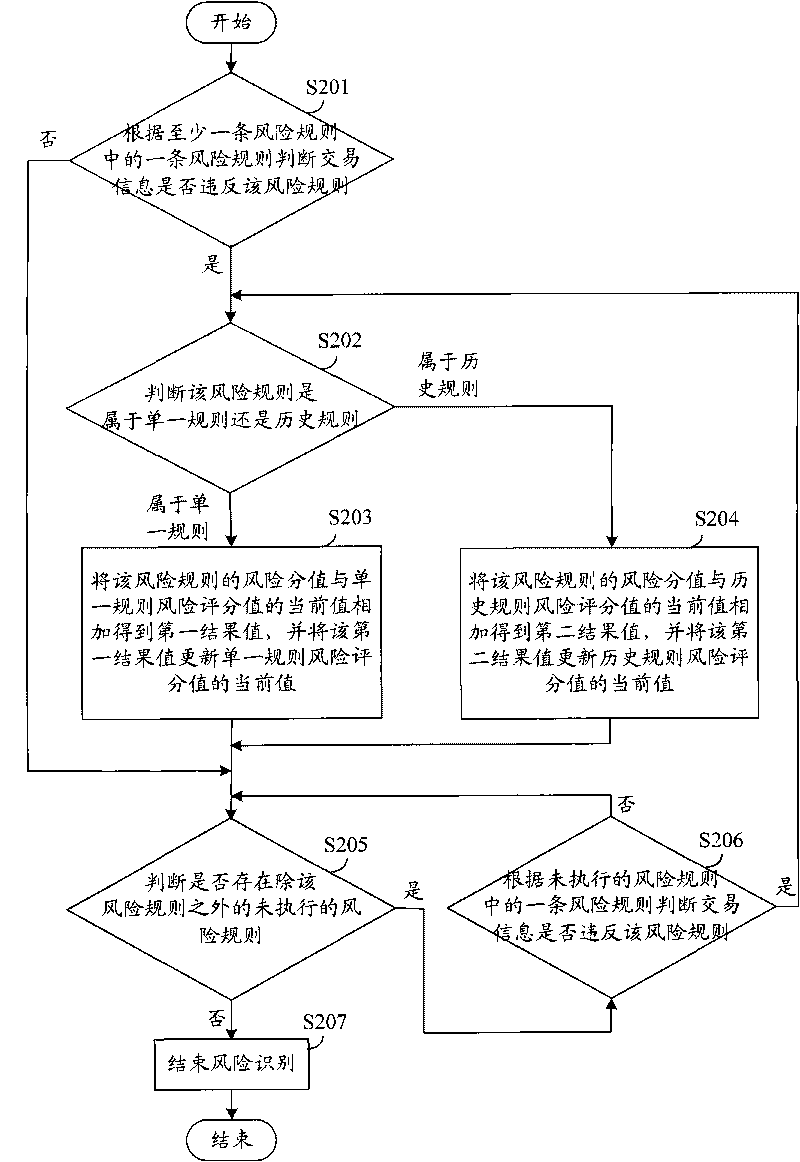
The invention discloses a method and a system for monitoring electronic bank risks, wherein the method comprises the following steps of: collecting trading information on-line traded by an electronic channel through a channel trading system by a risk monitoring subsystem, identifying risks for the trading information according to at least a risk rule, obtaining a result value, judging whether risk monitoring data need to be generated according to the relation between the result value and a risk threshold value, and if so, generating the risk monitoring data according to the trading information and sending the risk monitoring data to the channel trading system; and when a customer initiates on-line trading through the electronic channel, the channel trading system monitors the risks of the on-line trading according to the risk monitoring data. The risk identification of the trading information for electronic banks is carried out through the risk monitoring subsystem, and real-time risk monitoring for the on-line trading is carried out through the channel trading system according to the result of risk identification, thereby reducing the trading risks of each channel of the electronic banks and enhancing the security of customer trading.
Owner:CHINA CONSTRUCTION BANK
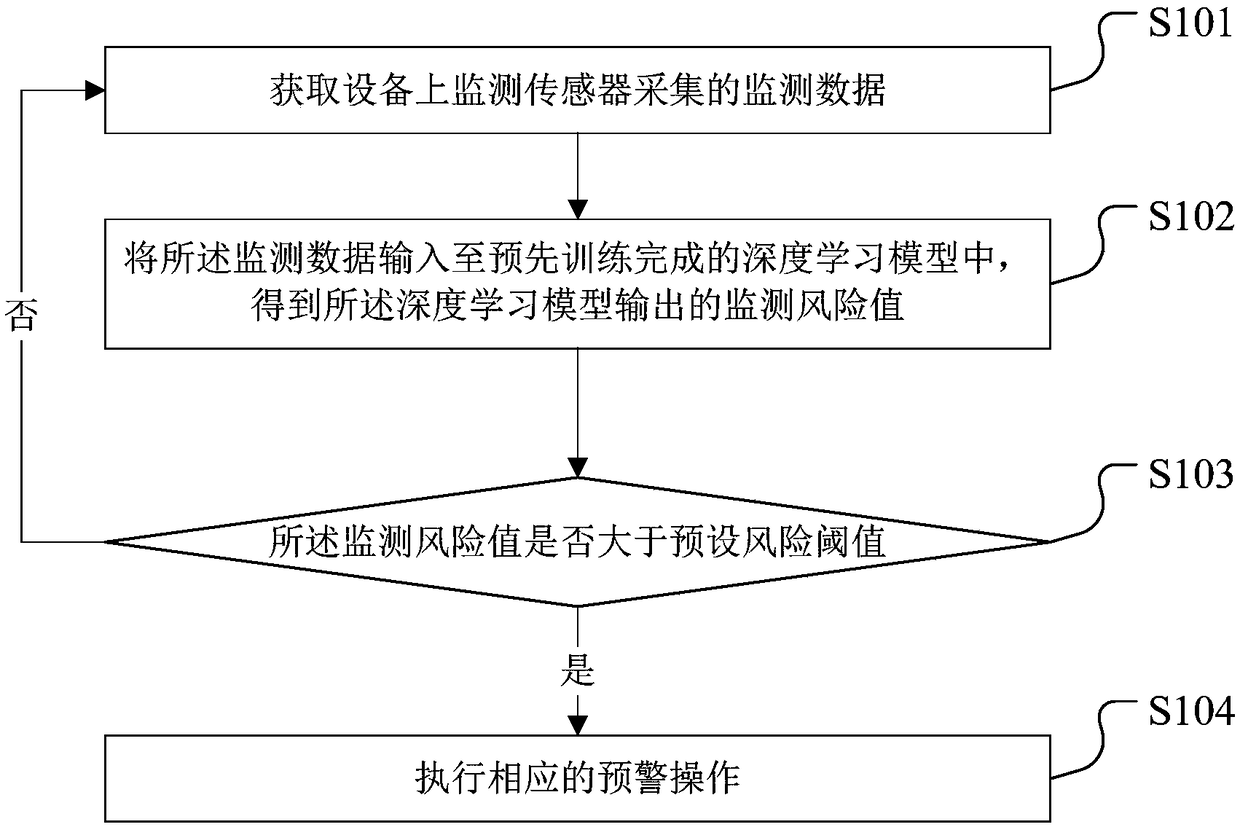
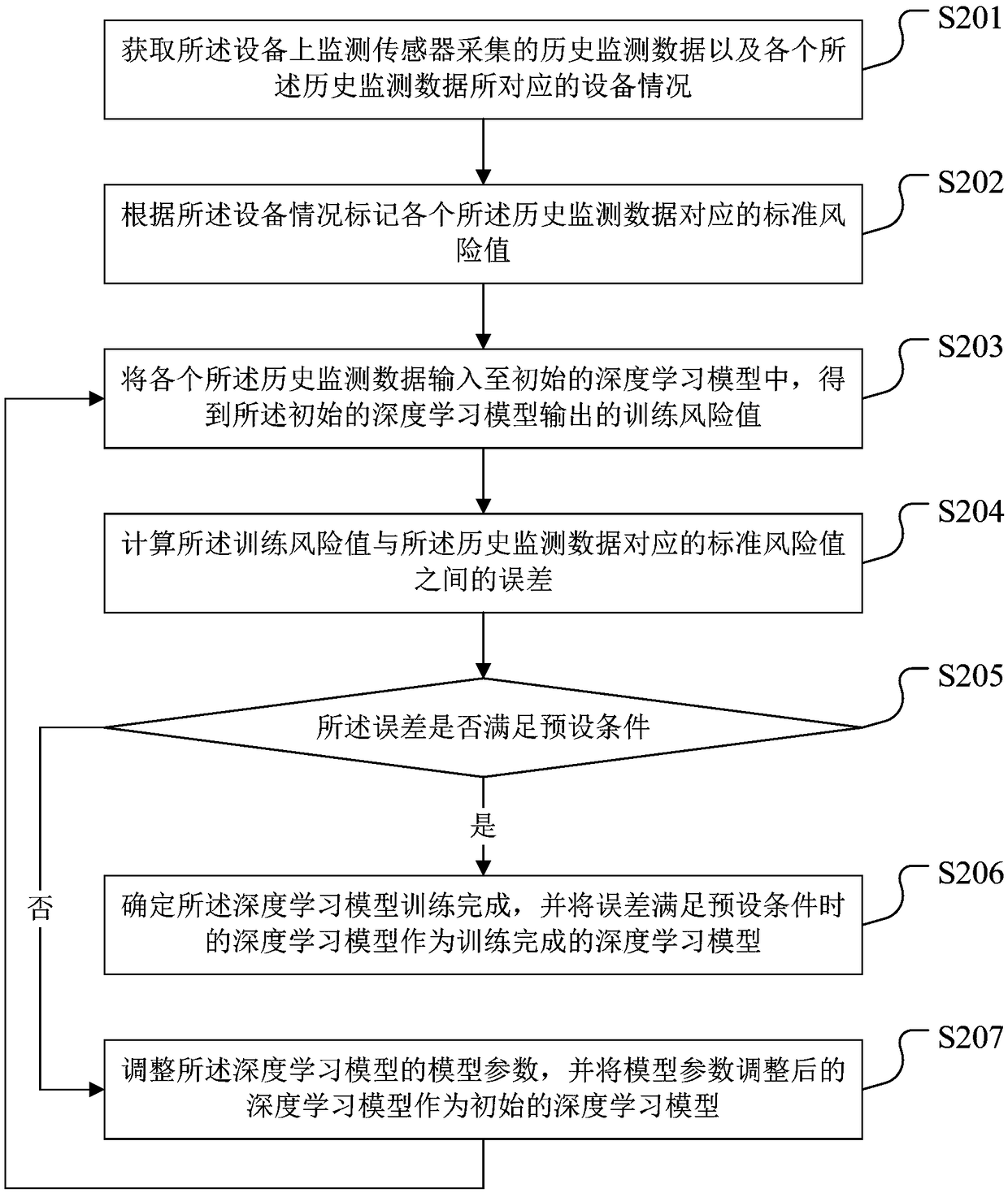
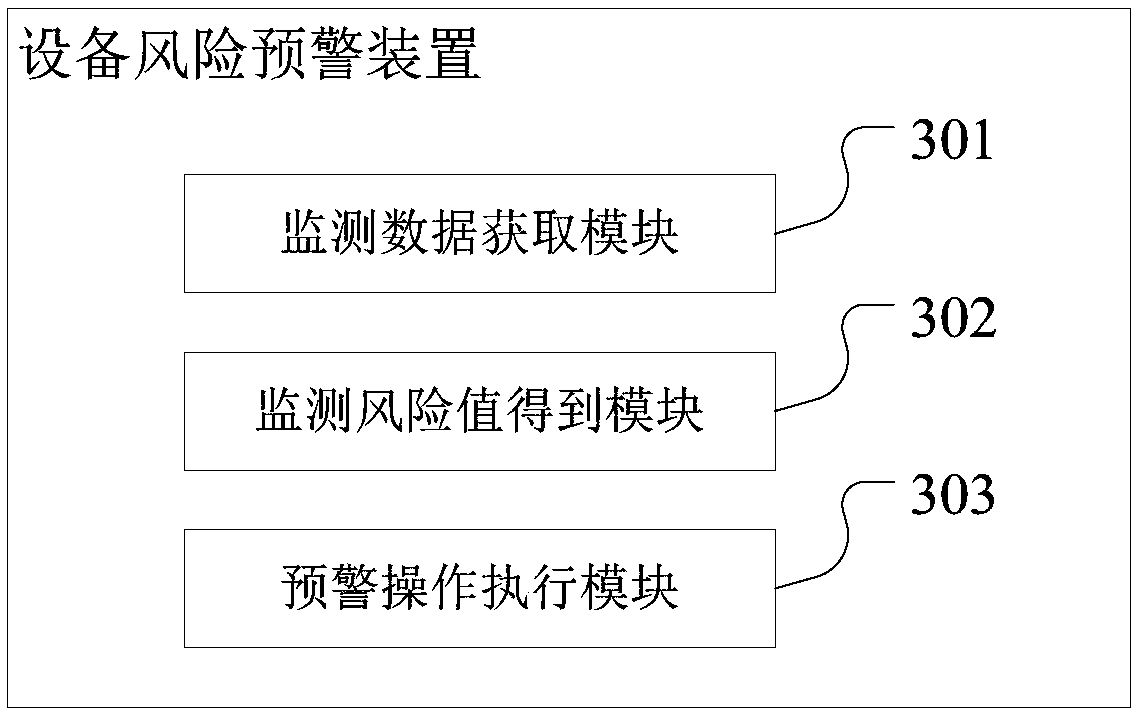
Equipment risk early-warning method and device, terminal equipment and storage medium
InactiveCN109269556AAchieve automationReal-timeMeasurement devicesTerminal equipmentComputer terminal
The invention discloses an equipment risk early-warning method and device, terminal equipment and a storage medium. The method includes: acquiring monitoring data collected by a monitoring sensor on equipment; inputting the monitoring data into a pre-trained deep learning model to obtain a monitoring risk value output by the deep learning model; and carrying out a corresponding early-warning operation when the monitoring risk value is greater than a preset risk threshold. In the method, the monitoring data on the equipment are collected in real time through the monitoring sensor, the monitoring risk value corresponding to the monitoring data is automatically and accurately acquired through the deep learning model, thus whether an equipment risk exists can be accurately determined accordingto the monitoring risk value, the corresponding early-warning operation can be carried out, automaticity and real-time performance of equipment risk monitoring are realized, monitoring efficiency ofequipment risk monitoring is improved, and then timeliness of equipment risk early-warning is realized.
Owner:ZDST COMM TECH CO LTD
Method for fast early warning against water body water bloom risk
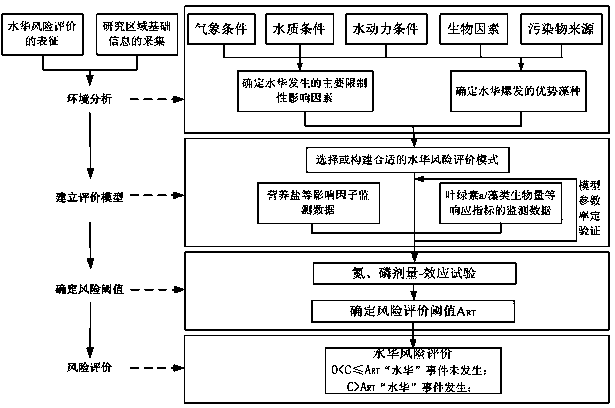
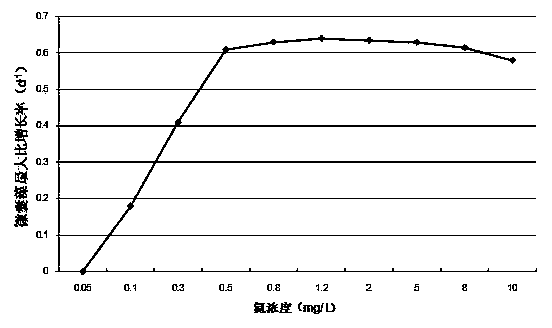
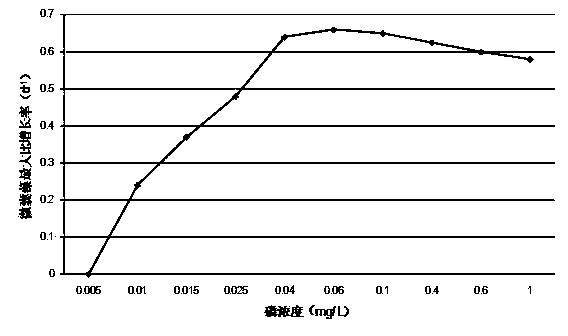
ActiveCN104112080ASimple structureFew parametersSpecial data processing applicationsEnvironmental qualityCvd risk
The invention discloses a method for fast early warning against a water body water bloom risk. The method comprises a first step of constructing an alga biomass prediction model based on environment analysis results; a second step of adopting the alga biomass prediction model to obtain an alga biomass prediction value; a third step of determining an alga biomass water bloom risk threshold of advantageous algae; and a fourth step of comparing the alga biomass prediction value with the alga biomass water bloom risk threshold and judging whether water bloom early warning is sent out. The method is suitable for water environmental quality monitoring, is simple, convenient and rapid, can achieve fast early warning of the water bloom risk and can provide timely and effective technical support for water environment emergency management.
Owner:珞珈浩景数字科技(湖北)有限公司
Method and system for providing electronic information for risk assesement and management via dynamic total net worth for multi-market electronic trading
Owner:ROSENTHAL COLLINS GROUP
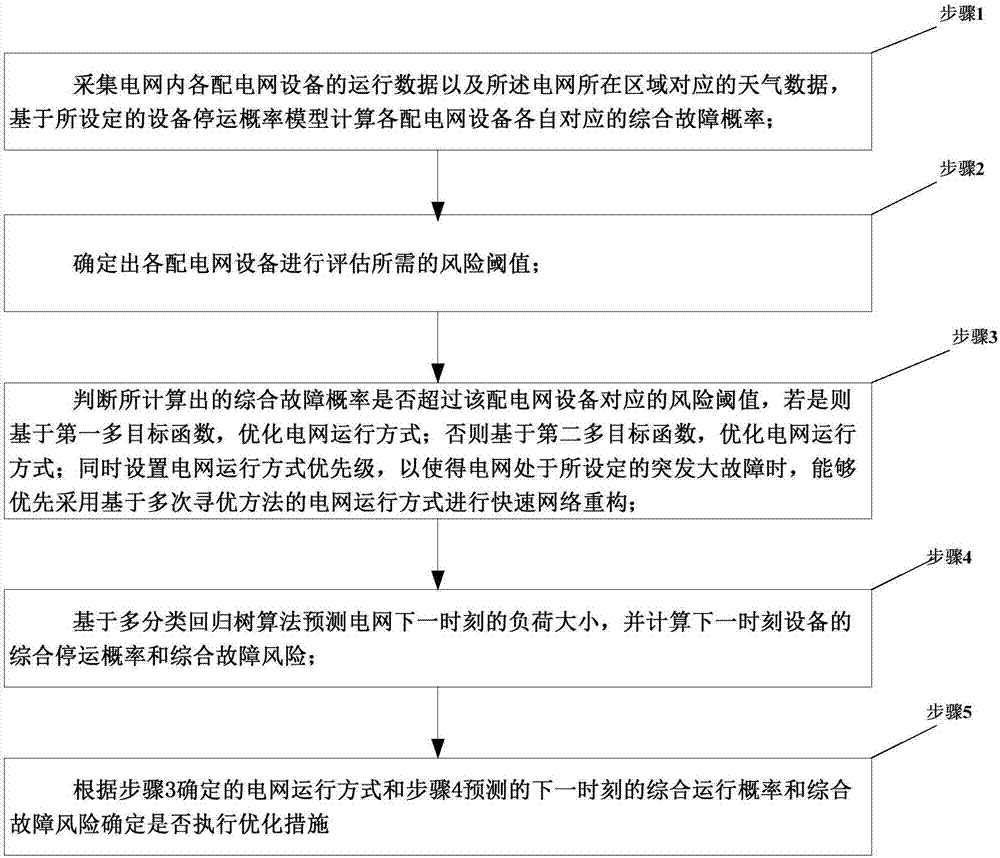
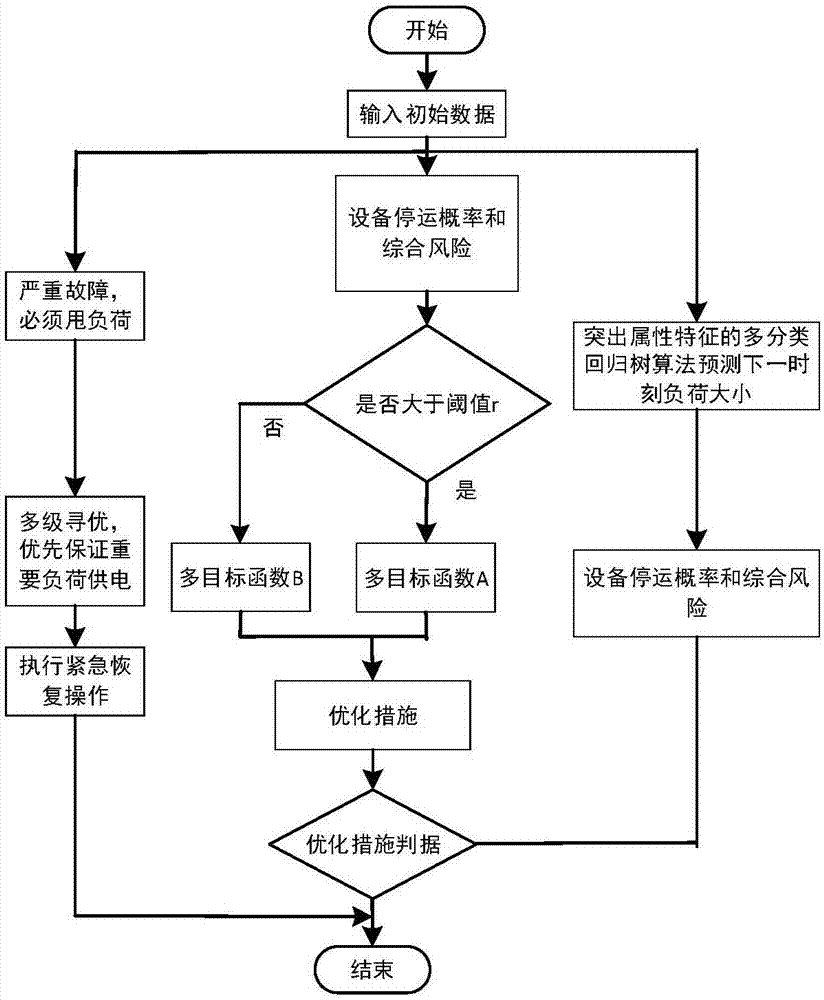
Difference self-healing control method based on device failure probability and power grid operation risks
The invention discloses a difference self-healing control method based on device failure probability and power grid operation risks. The difference self-healing control method includes the steps: 1 acquiring operation data and weather data, and calculating comprehensive failure probability corresponding to power distribution network devices; 2 determining risk threshold values; 3 judging whether the comprehensive failure probability exceeds the risk threshold values corresponding to the power distribution network devices or not, optimizing power grid operation modes based on first multi-objective functions if the comprehensive failure probability exceeds the risk threshold values corresponding to the power distribution network devices, optimizing the power grid operation modes based on second multi-objective functions if not, and setting priorities of the power grid operation modes; 4 forecasting loads of power grids next moment based on a multi-classification regression tree algorithm, and calculating comprehensive stoppage probability and comprehensive risk probability of devices in the next moment; 5 determining whether optimization measures are executed or not. According to the method, the device failure probability and the power grid operation risks are fully considered, economical and reliable operation of the power grids is achieved by difference self-healing control without rejecting loads as far as possible.
Owner:NORTHEASTERN UNIV
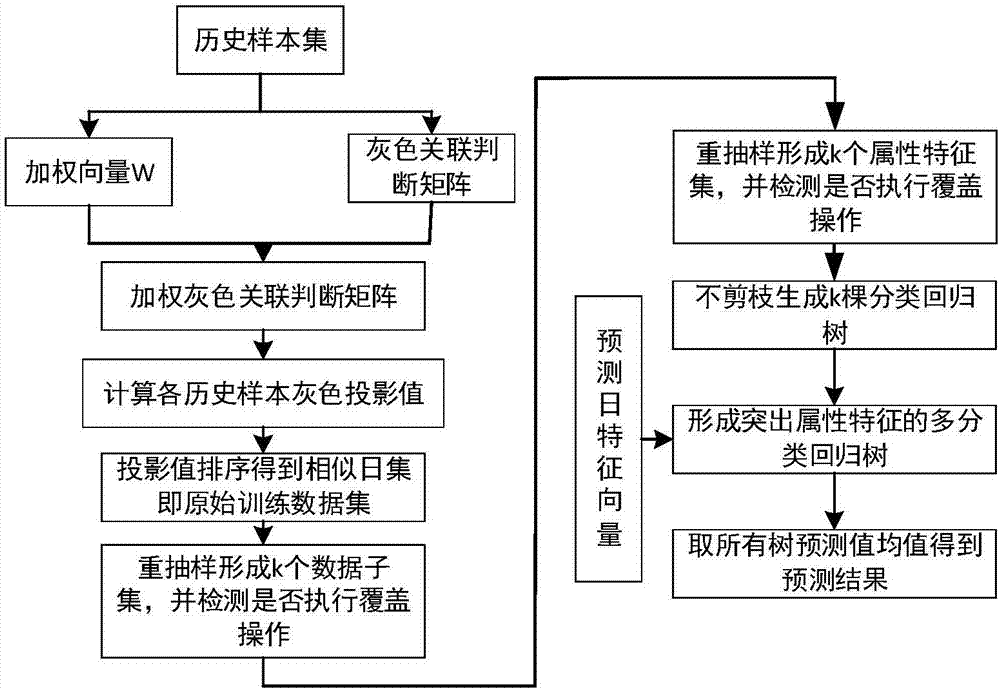
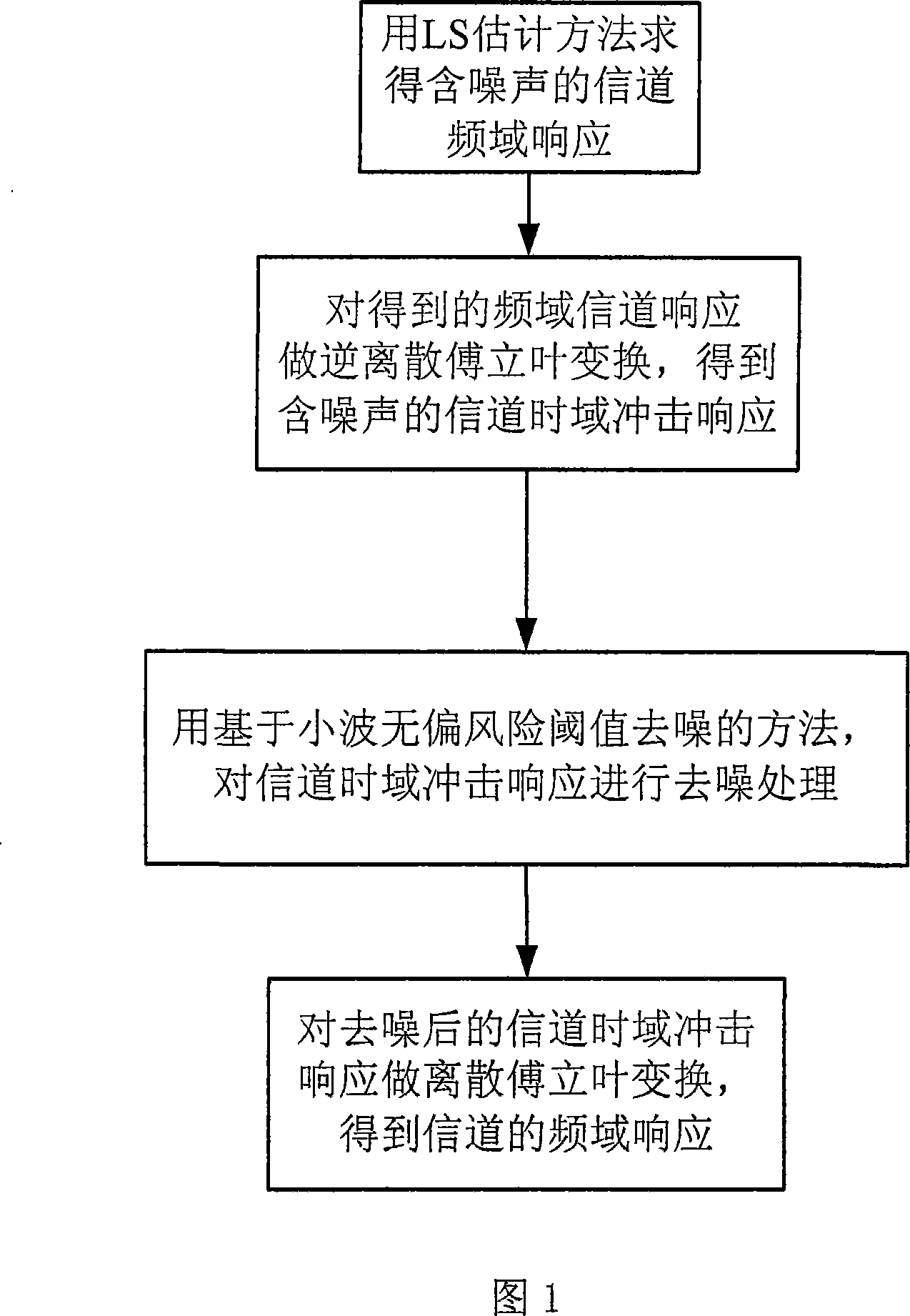
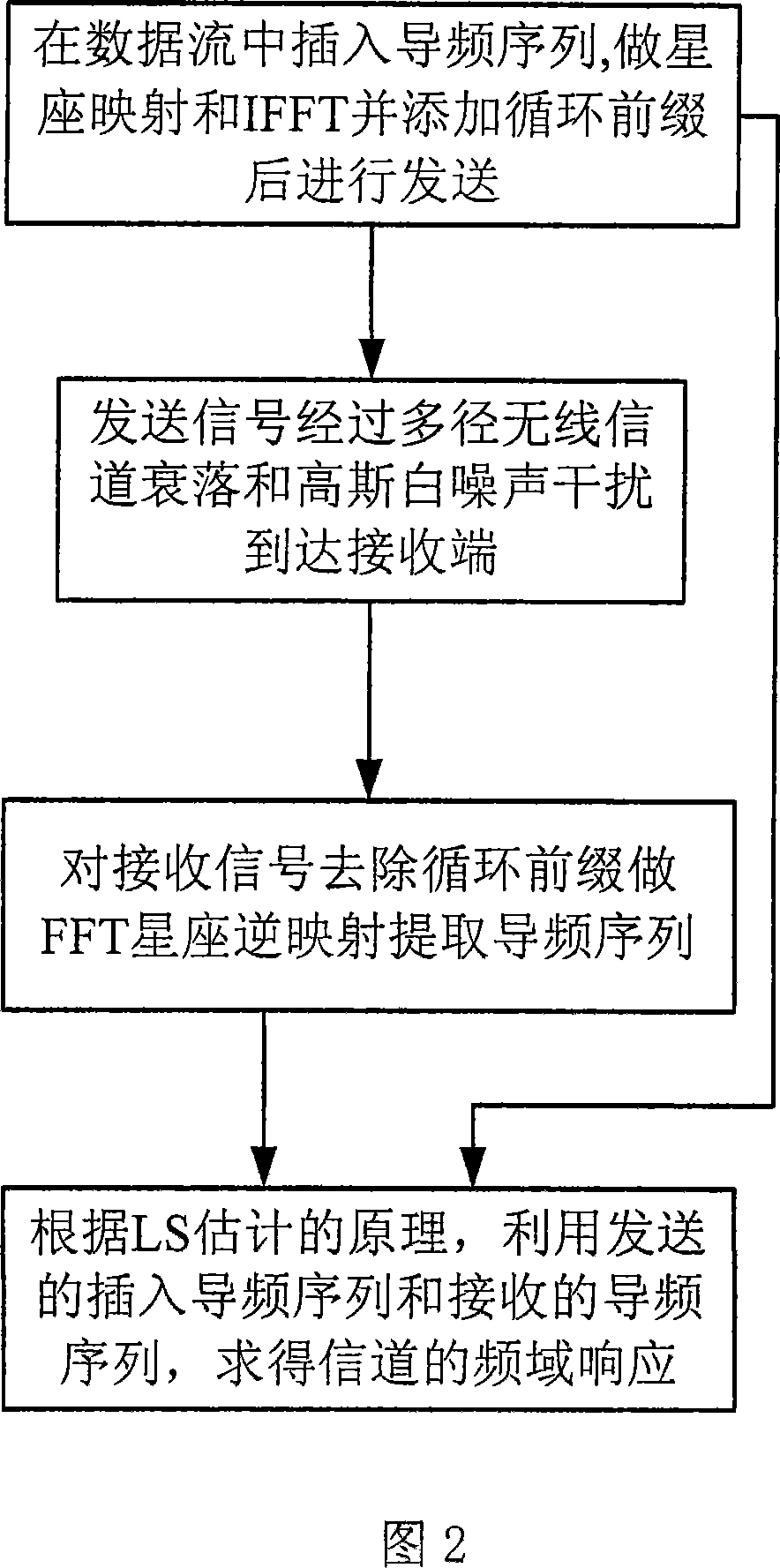
OFDM channel estimating method based on wavelet unbiased risk threshold value noise elimination
InactiveCN101227438AImprove estimation performanceImprove performanceBaseband system detailsMulti-frequency code systemsValue noiseFourier transform on finite groups
The invention discloses an OFDM channel estimation method for de-noising which is based on wavelet unbiased risk threshold value, which relates to the technical field of communication, the purpose of the invention is that the problem that an LS method is easy to be influenced by noise under the condition without channel information is effectively solved. The realizing process of the method comprises first, obtaining channel frequency response which contains noise according to the LS channel estimation method which is on the basis of an OFDM system which is based on pilot frequency, second, doing inverse discrete Fourier transform for the channel frequency response which is obtained and to get channel time-domain impulse response which contains noise, third, de-noising the channel time-domain impulse response the method for de-noising which is based on wavelet unbiased risk threshold value, and getting channel time-domain impulse response after de-noising, fourth, doing inverse discrete Fourier transform for the channel time-domain impulse response after de-noising, and getting frequency domain response of channel, and compensating the received signals by the channel time-domain impulse response after de-noising. The method can be used in OFDM channel estimation techniques under various multi-path channels.
Owner:XIDIAN UNIV
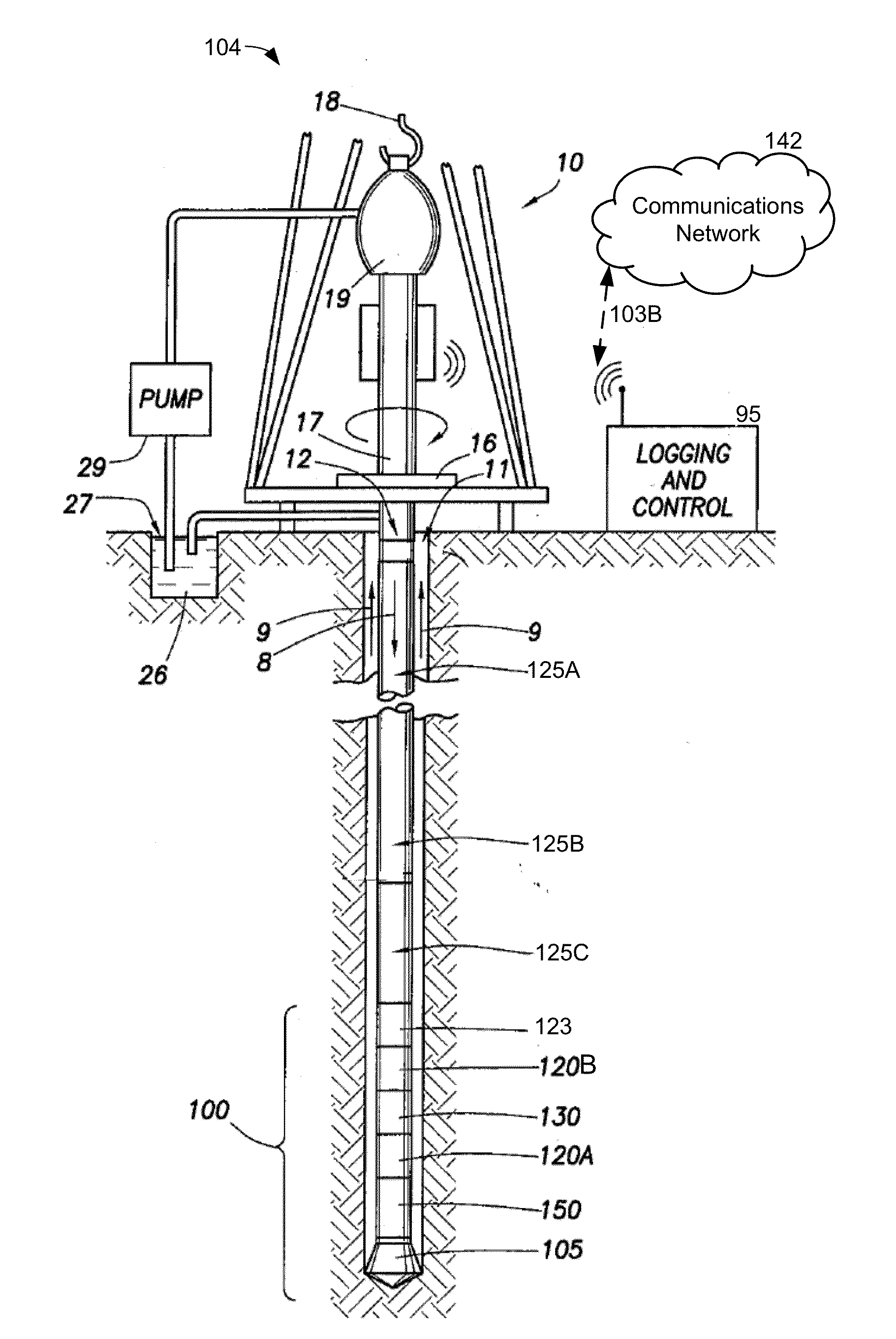
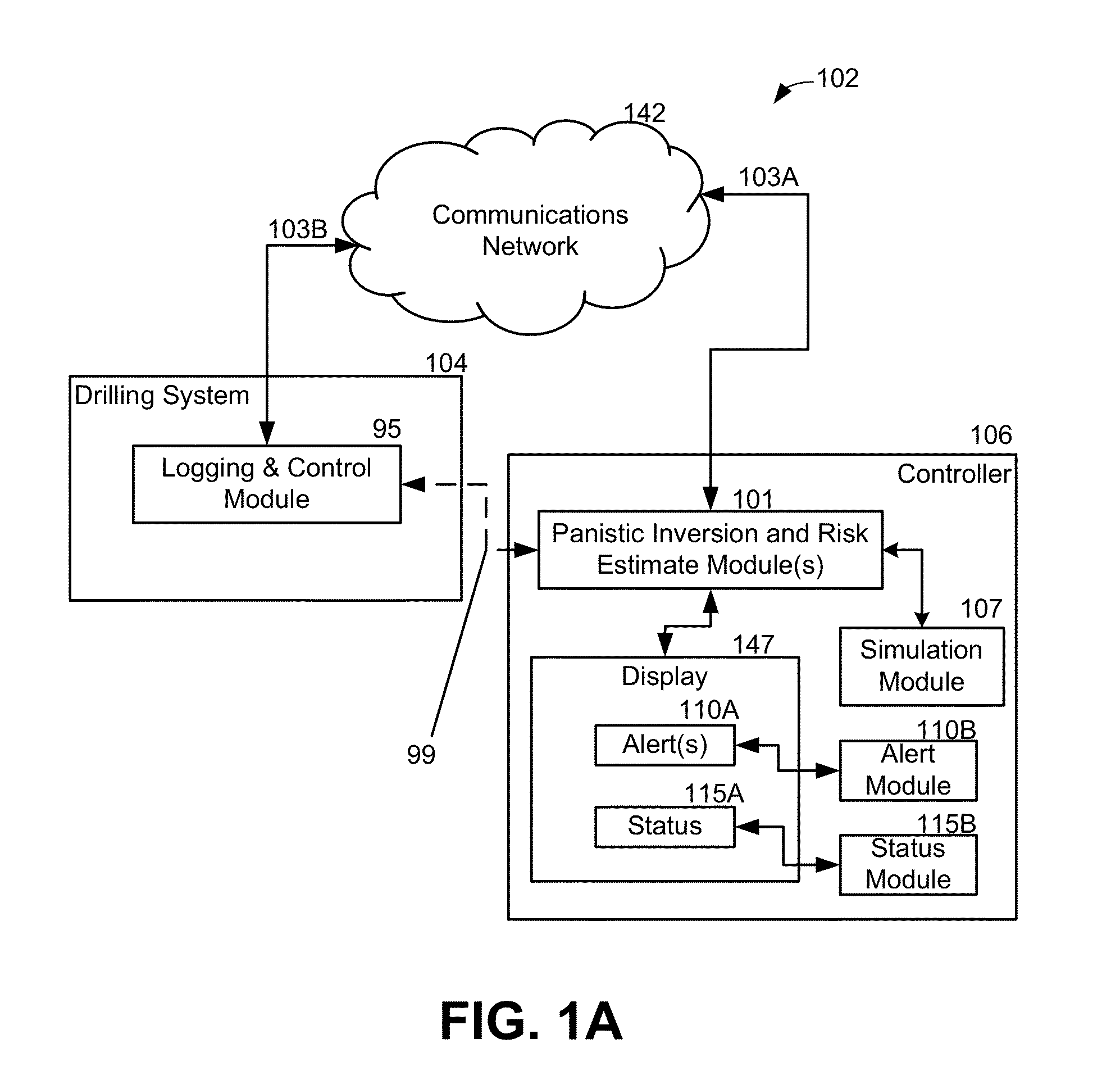
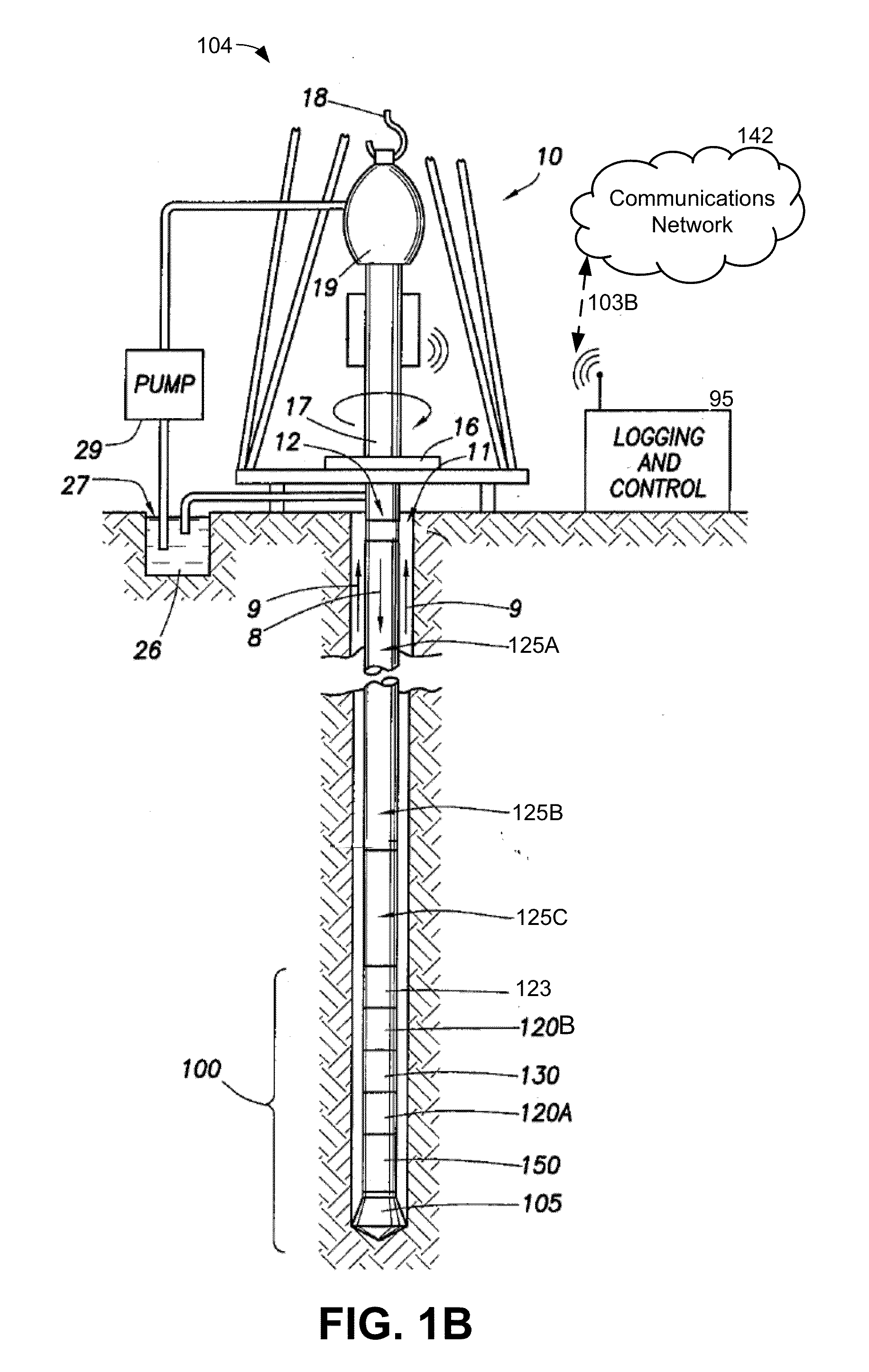
System and method for controlling and monitoring a drilling operation using refined solutions from a panistic inversion
During a drilling operation, measured data from the drilling operation may be received with a panistic inversion and risk estimate module. The panistic inversion and risk estimate module may generate a plurality of mathematical solutions from a panistic inversion that uses the measured data and one or more earth models. The one or more earth models having various parameters may be selected prior to drilling and / or while the drilling operation occurs. For each solution of the plurality of mathematical solutions generated from the panistic inversion, the panistic inversion and risk estimate module may determine if the measured data exceeds one or more probability risk thresholds associated with the drilling operation. If the measured data exceeds the probability risk threshold associated with the drilling operation, then the panistic inversion and risk estimate module may generate an alert.
Owner:SCHLUMBERGER TECH CORP
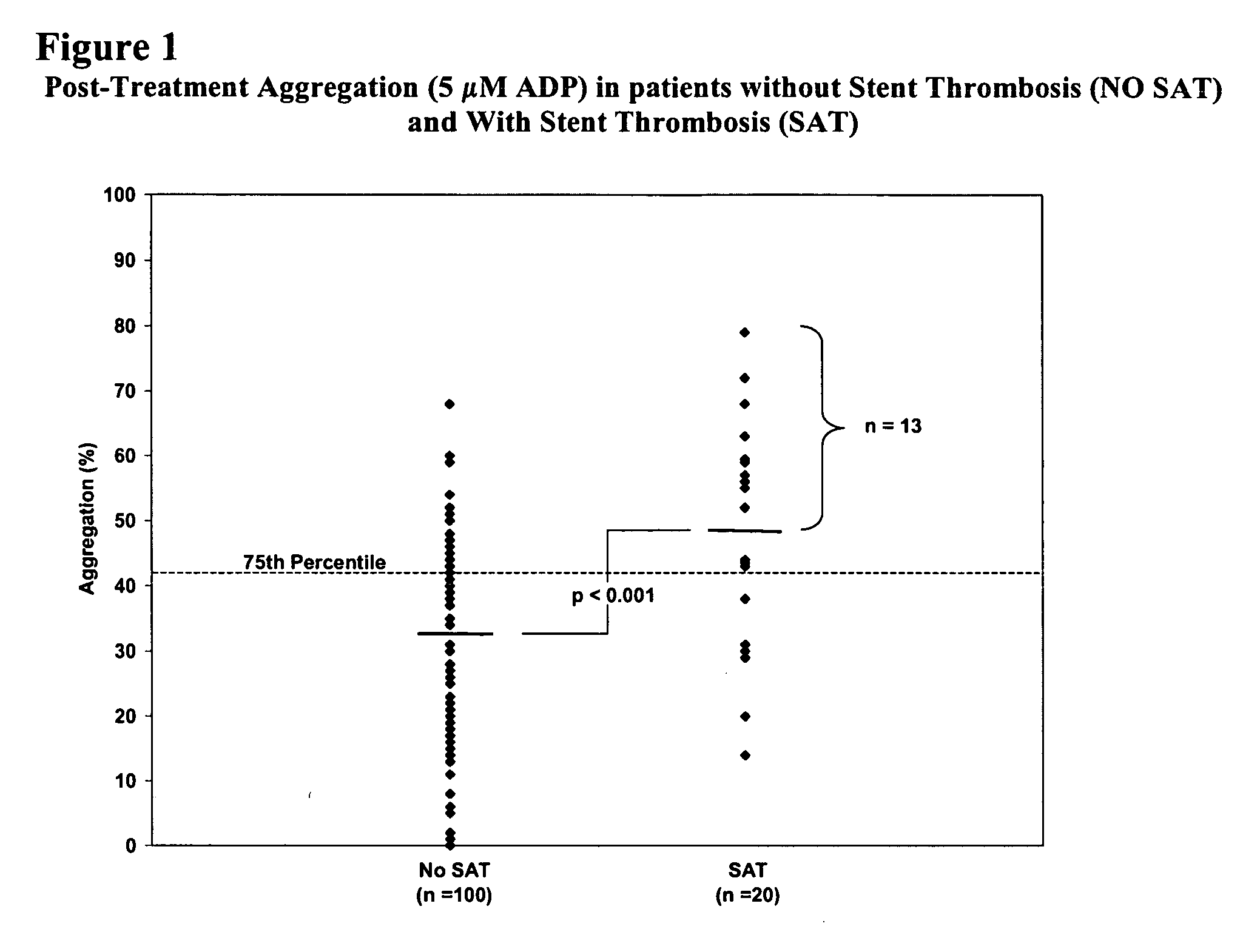
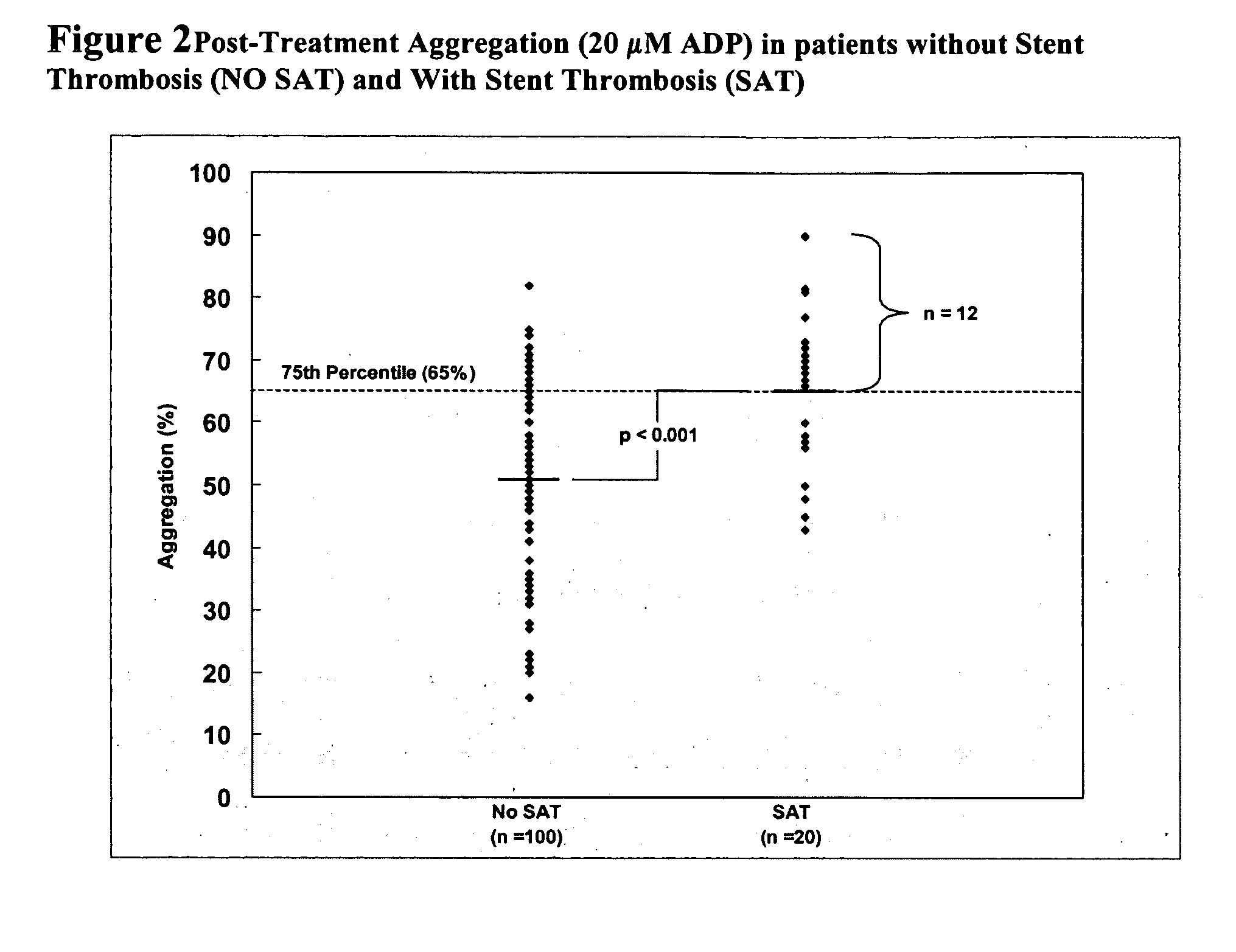
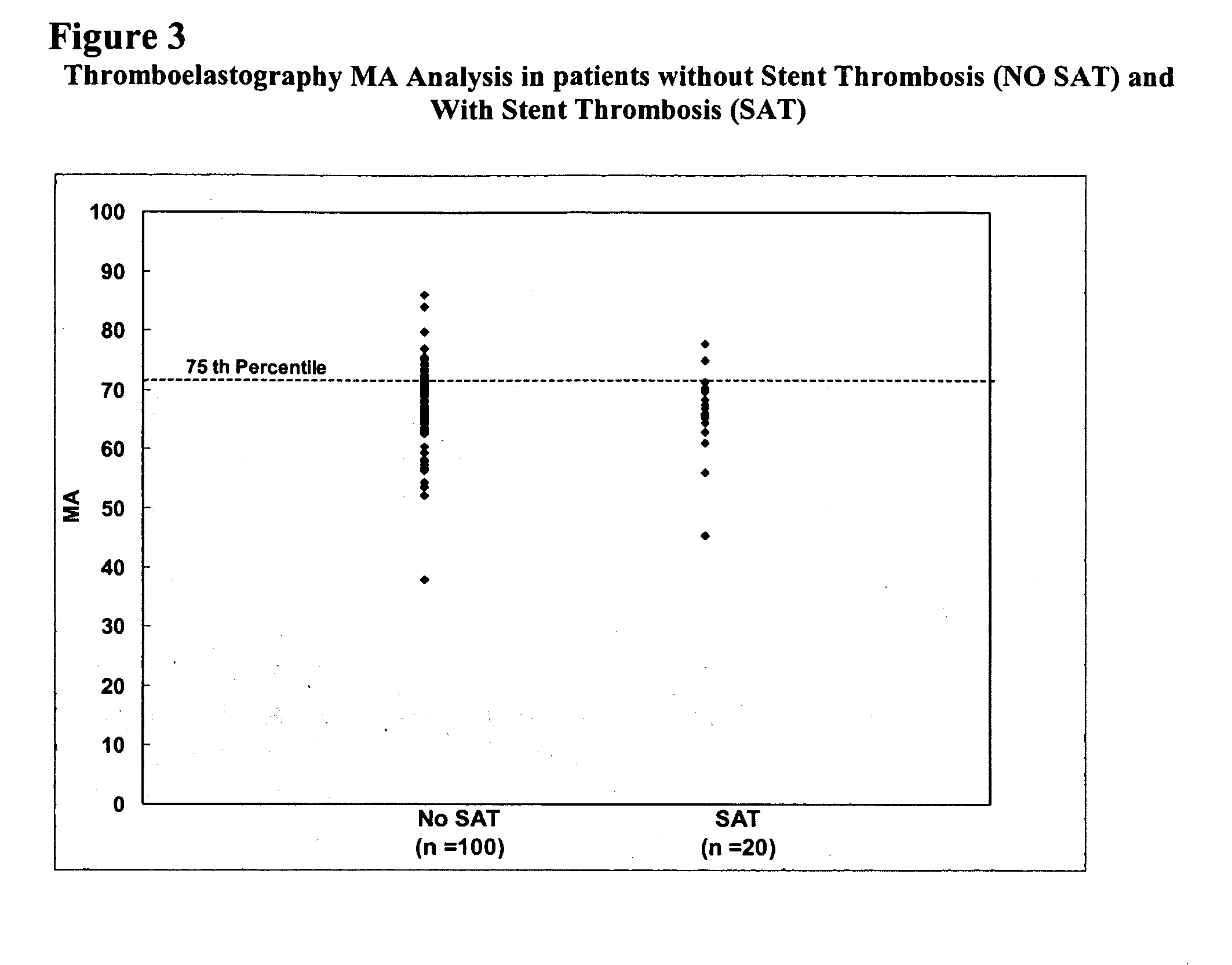
Assessment of cardiac health and thrombotic risk in a patient
ActiveUS20060199239A1Reduce riskRisk of the thrombotic event is assessedOrganic active ingredientsPeptide/protein ingredientsDiseasePercent Diameter Stenosis
The invention features methods and compositions for assessing risk, particularly immediate risk, of thrombotic events in patients with suspected or known vascular disease, and more particularly to assessing risk of thrombotic events in patients with coronary artery disease, particularly acute myocardial infarction, stroke, unstable angina, stable angina, or restenosis. Risk of thrombosis can be assessed by analysis of platelet reactivity and / or velocity of thrombin or fibrin formation, and determining whether the patient has a score associated above a risk threshold value. In other embodiments, risk of thrombosis in a patient is evaluated in the context of a profile generated from values obtained from one or more assays that evaluate various factors associated with thrombosis and / or atherosclerosis.
Owner:GURBEL PAUL A
Generating predilection cohorts
A computer implemented method, apparatus, and computer program product for generating risk scores for specific risk cohorts. Digital sensor data associated with a specific risk cohort is received from a set of multimodal sensors. The specific risk cohort includes a set of identified cohort members. The digital sensor data includes metadata describing attributes associated with at least one cohort member in the set of identified cohort members. Description data for each cohort member in the set of identified cohort members is retrieved to form a set of cohort description data. The description data for each cohort member comprises data describing a previous history of the cohort member or a current status of the cohort member. The cohort member is a person, animal, plant, thing, or location. A specific risk score is generated for the specific risk cohort based on selected risk factors, the attributes associated with the at least one identified member, and the set of cohort description data. A response action is initiated in response to a determination that the specific risk score exceeds a risk threshold.
Owner:NUANCE COMM INC
Washing machine control method and device, washing machine
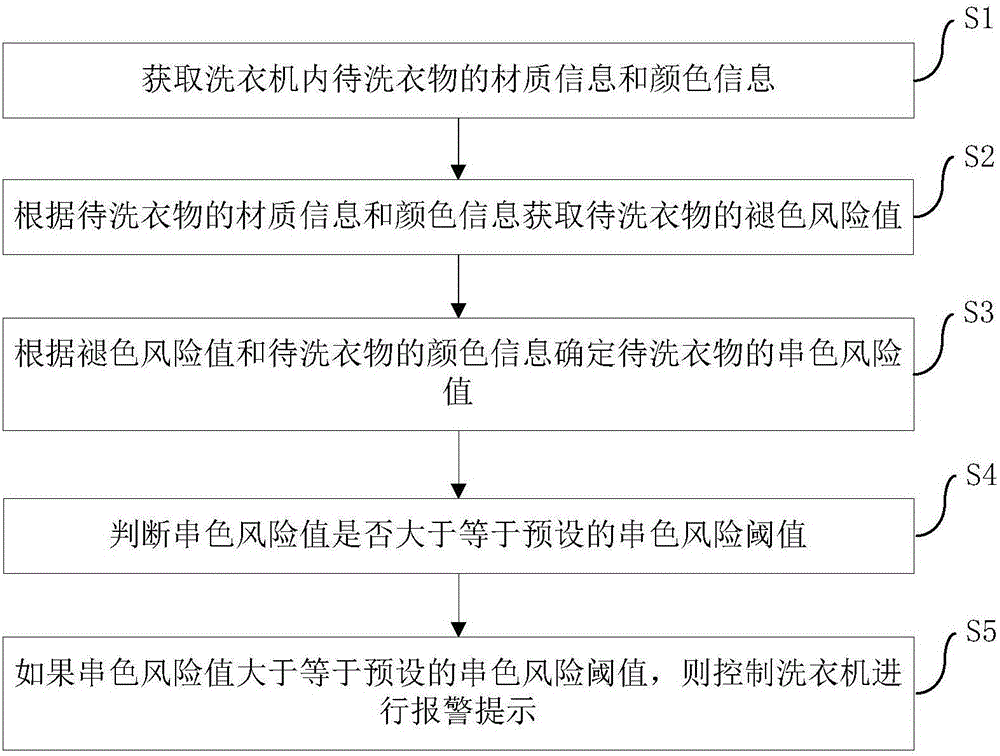
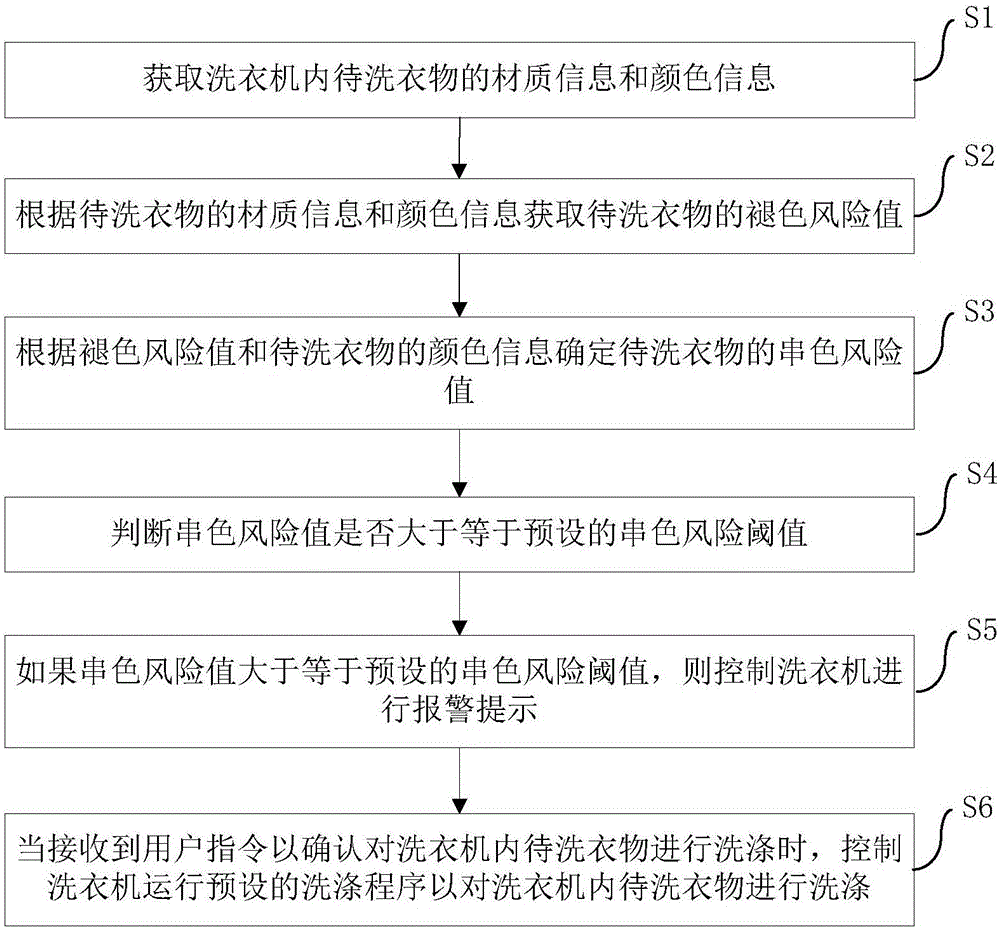
ActiveCN106637812AImprove experienceReduced risk of color crossoverControl devices for washing apparatusTextiles and paperMachine controlProcess engineering
The invention discloses a washing machine control method and device, and a washing machine. The control method includes the following steps: acquiring texture information and color information of clothes to be washed; acquiring a fading risk value of the clothes to be washed according to the texture information and the color information of the clothes to be washed; determining a color-crossing risk value of the clothes to be washed according to the fading color risk value and the color information of the clothes to be washed; determining if the color-crossing risk value is greater than or equal to a preset color-crossing risk threshold or not; and controlling the washing machine to send an alarm prompt if the color-crossing risk value is greater than the preset color-crossing risk threshold. The control method can determine the color-crossing risk value of the clothes to be washed by processing the texture information and the color information of clothes to be washed, can determine if the clothes to be washed in the washing machine has a dyeing risk or not according to the color-crossing risk value of the clothes to be washed, can greatly lower the dyeing risk of the clothes to be washed, and can improve the user experience.
Owner:WUXI LITTLE SWAN ELECTRIC CO LTD
Major hazard recognition method, major hazard recognition system, storage medium and computer device
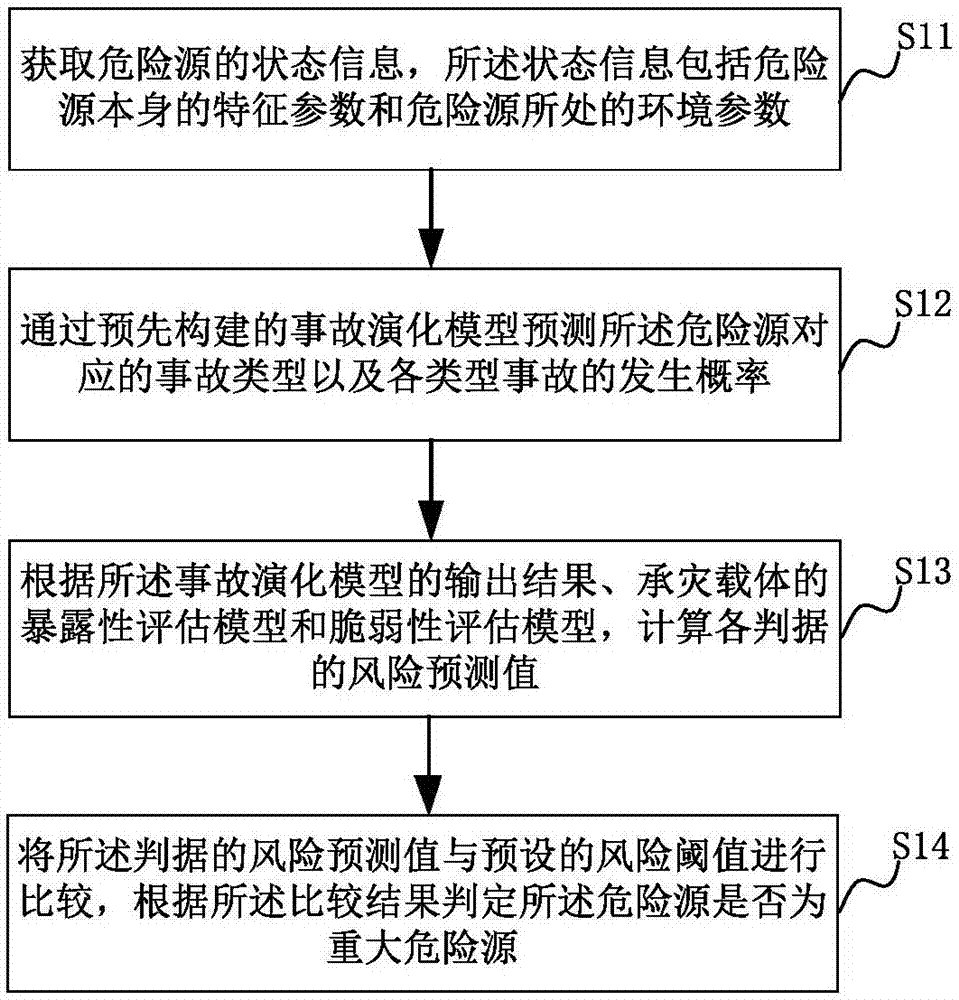
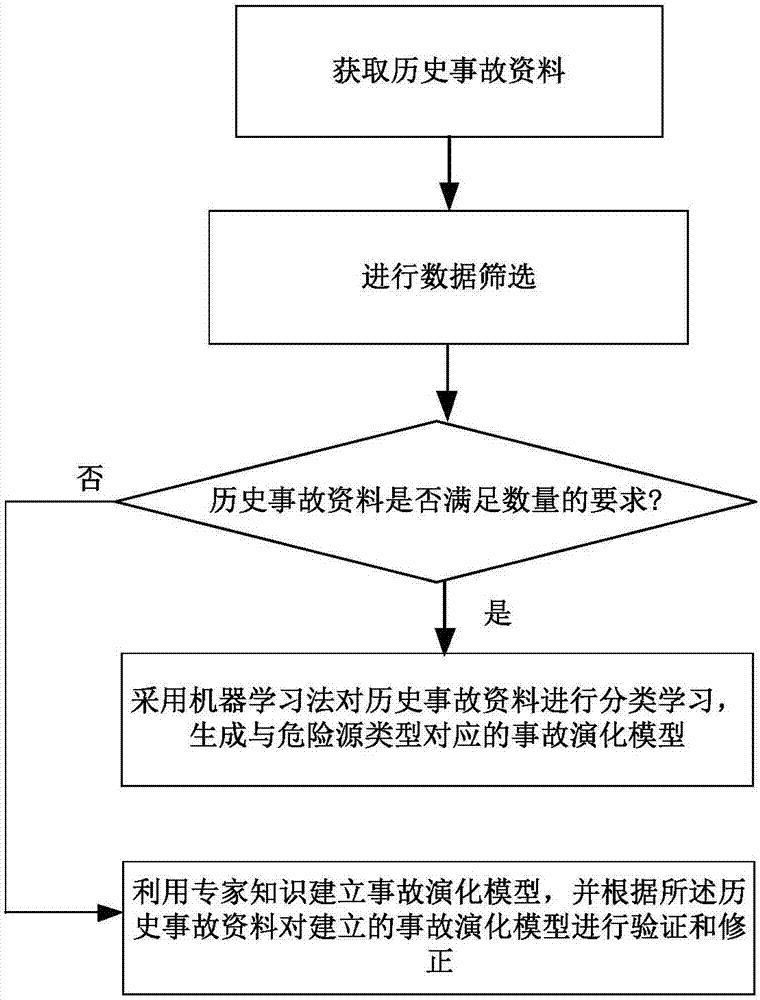
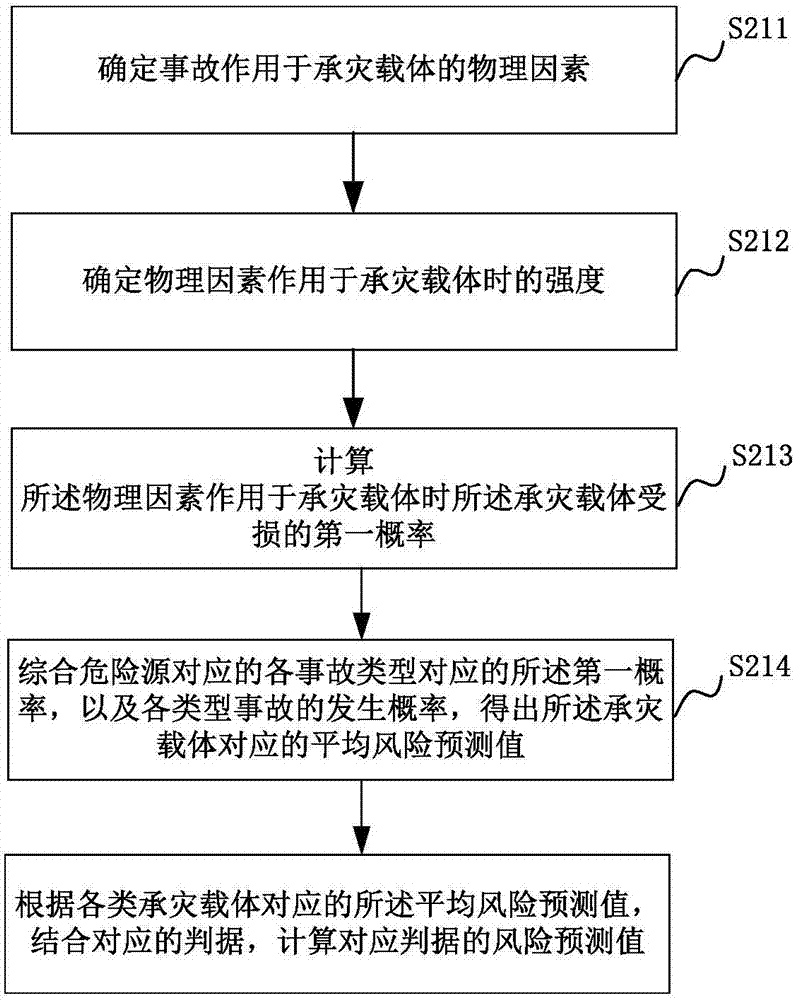
ActiveCN107169600APrevent major dangerous accidentsForecastingVulnerability evaluationComputer science
The invention relates to a major hazard recognition method, a major hazard recognition system, a storage medium and a computer device. The method comprises steps: the state information of a hazard is acquired; the state information is inputted to a pre-built accident evolution model, and an accident type evolved by the hazard and the happening possibility of each accident type are obtained; according to the preset criterions, a disaster bearing carrier corresponding to the hazard is determined, and an exposure assessment model and a vulnerability assessment model of the disaster bearing carrier are acquired, wherein the number of preset criterions is at least two; the output result of the accident evolution model is read, and according to the output result, the exposure assessment model and the vulnerability assessment model, a risk prediction value corresponding to each criterion is calculated; and the risk prediction value of each preset criterion is compared with a corresponding risk threshold, and according to the comparison result, whether the hazard is a major hazard is judged. Thus, the major hazard can be effectively recognized, and happening of a major accident is prevented.
Owner:INST OF IND TECH GUANGZHOU & CHINESE ACADEMY OF SCI
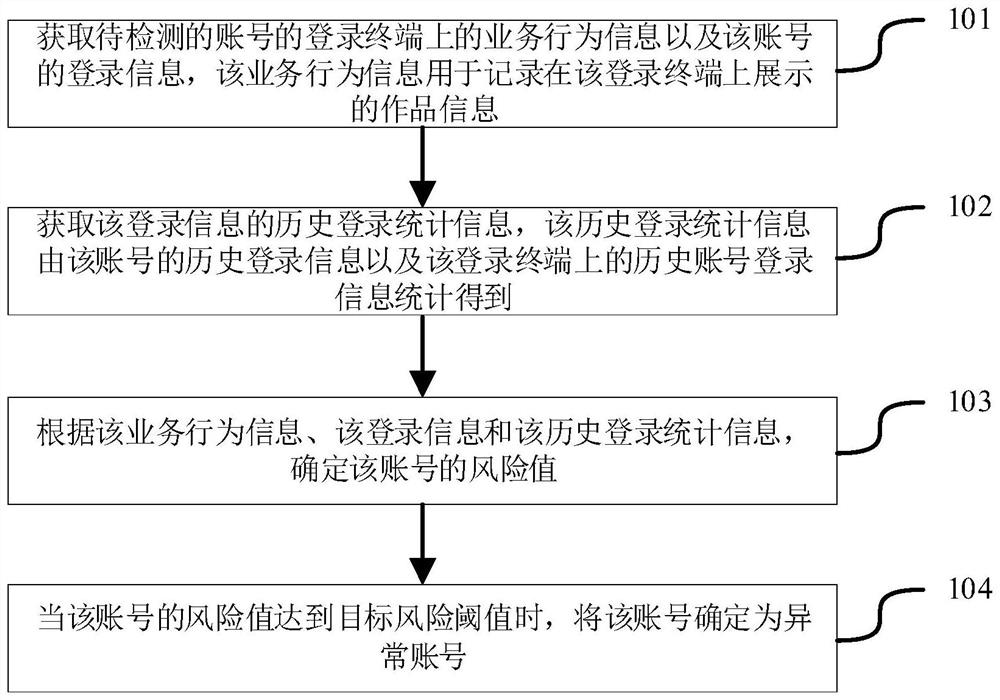
Account detection method and device, server and storage medium
PendingCN112417439AImprove accuracyCharacter and pattern recognitionPlatform integrity maintainanceEngineeringData mining
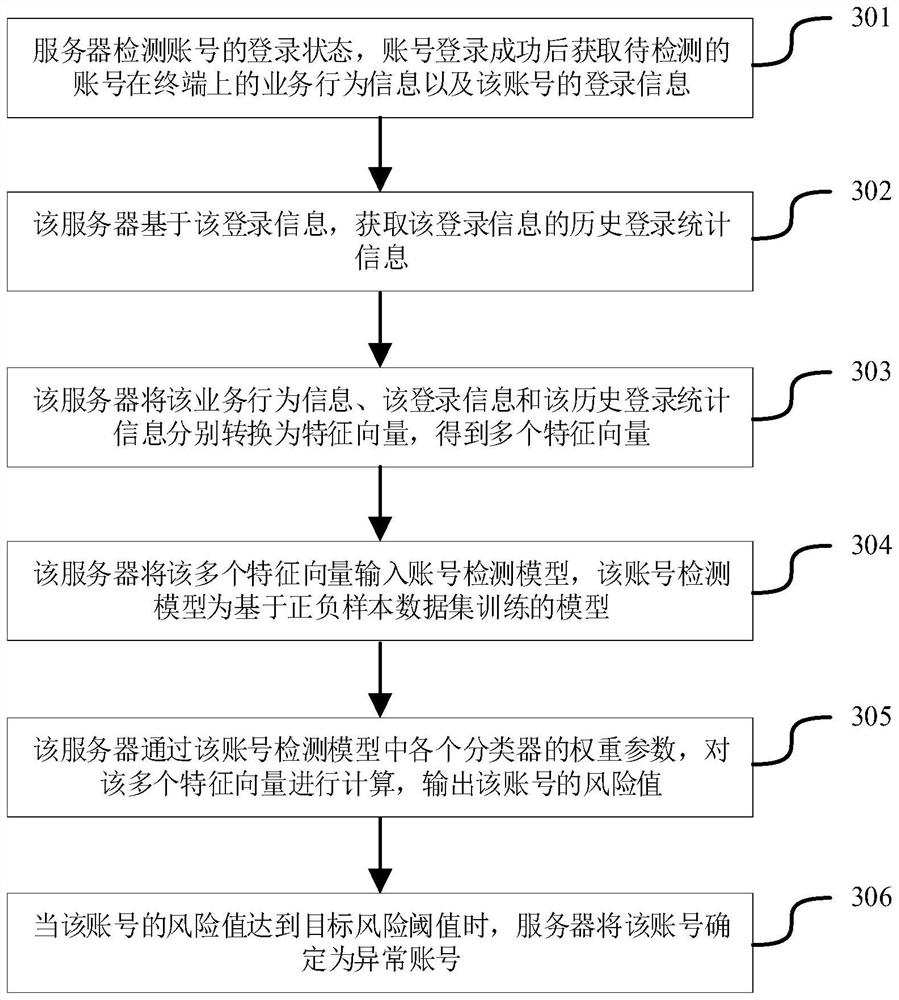
The invention relates to an account detection method and device, a server and a storage medium. The method comprises the following steps: acquiring current login information and historical login statistical information of a to-be-detected account, analyzing whether a login place, login equipment and the like of the to-be-detected account are normal or not, performing information acquisition on thecurrent login equipment, acquiring service behavior information of the to-be-detected account on a terminal, analyzing whether the business behavior of the account to be detected after login is normal user operation or not, detecting the account security from multiple dimensions, determining the risk value of the account, and taking the account with the risk value greater than a target risk threshold as an abnormal account. In the account detection mode, the risk value of the account is determined according to the login information, the historical login statistical information, the service behavior information and other data, the security of the account can be comprehensively analyzed from the dimensions of service behaviors, login equipment and the like, and the accuracy of account detection is improved.
Owner:BEIJING DAJIA INTERNET INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com