Microcontroller object code protection method and system
A technology of object code and micro-controller, which is applied in the field of micro-controller encryption, can solve the problems of increasing manufacturing cost and not being suitable for widespread promotion and use, and achieve the effects of reducing manufacturing and using costs, ensuring storage security, and a high degree of confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
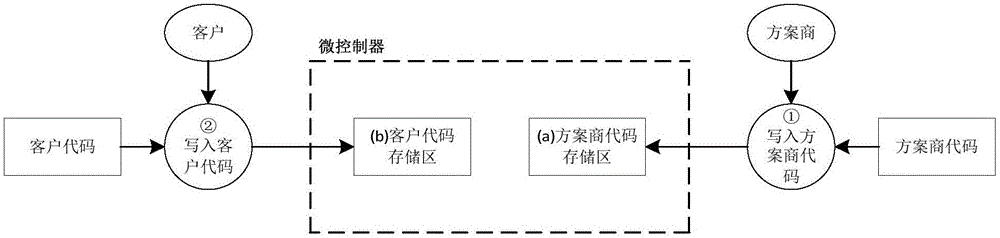
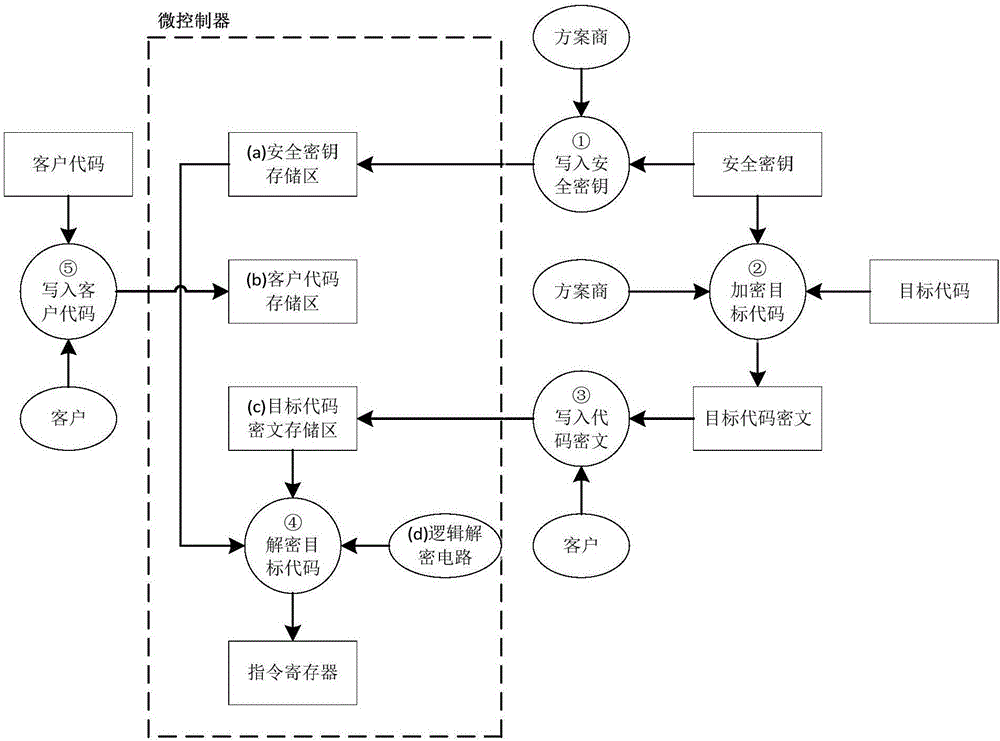
[0059] This embodiment describes in detail the microcontroller object code protection method of the present invention, and its flow chart can be found in image 3 , the storage space in the microcontroller is divided into a security key storage area, an object code ciphertext storage area, and a customer code storage area. The object code protection method is mainly divided into the following major steps:
[0060] (1) Write the security key: the IP supplier (that is, the solution provider in the figure) writes the security key into the security key storage area inside the microcontroller;
[0061] The security key is used to encrypt and decrypt the target code. In order to ensure the confidentiality of the security key, the security key must be written by the IP supplier, and can only be written by the program and read by the internal logic. Read by programs or various debugging methods (such as JTAG).
[0062] (2) Encrypted object code: the IP supplier encrypts the object co...
Embodiment 2
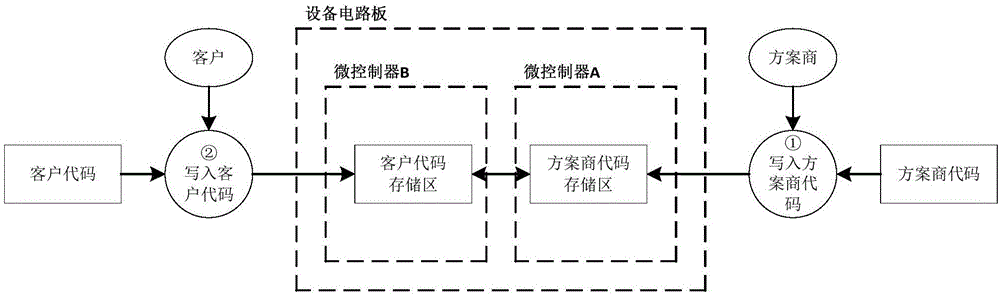
[0085] This embodiment describes in detail the microcontroller object code protection system of the present invention, which can be referred to Figure 5 , Figure 5 It is a schematic diagram of the internal structure of the microcontroller. As shown in the figure, the microcontroller includes a storage module, an instruction register, a program counter and a decryption module. In order to illustrate the principle of the target code protection system, only the required The memory module, instruction register, program counter and decryption module of the microcontroller, other modules in the microcontroller are in Image 6 is not drawn in detail.
[0086] The system divides the storage space in the storage module into a security key storage area (a), an object code cipher text storage area (c), and a customer code storage area (b). The text and customer code can be respectively stored in the security key storage area, the target code cipher text storage area, and the customer...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com