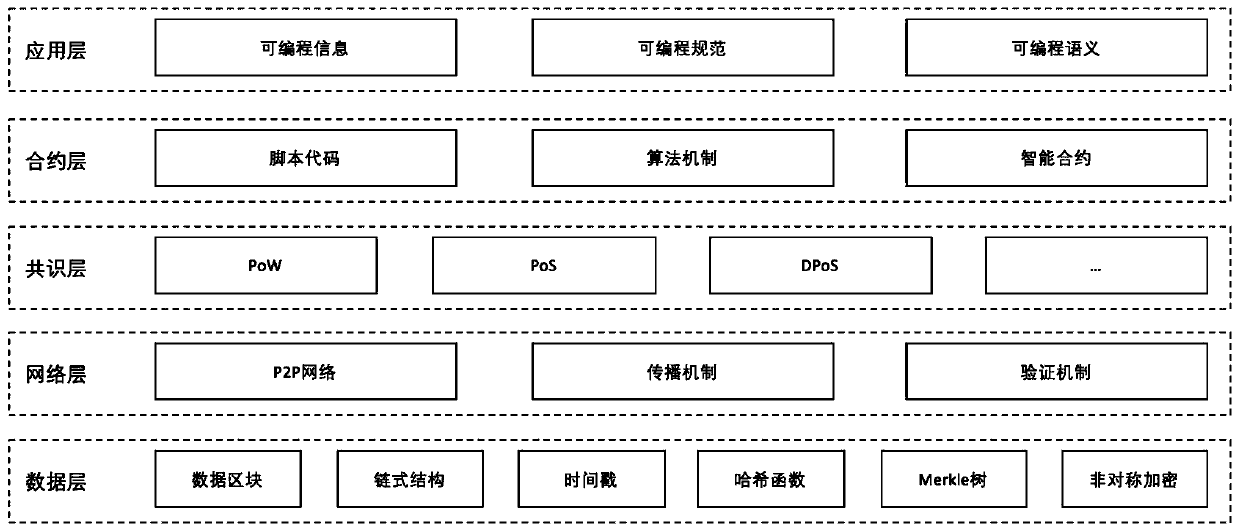
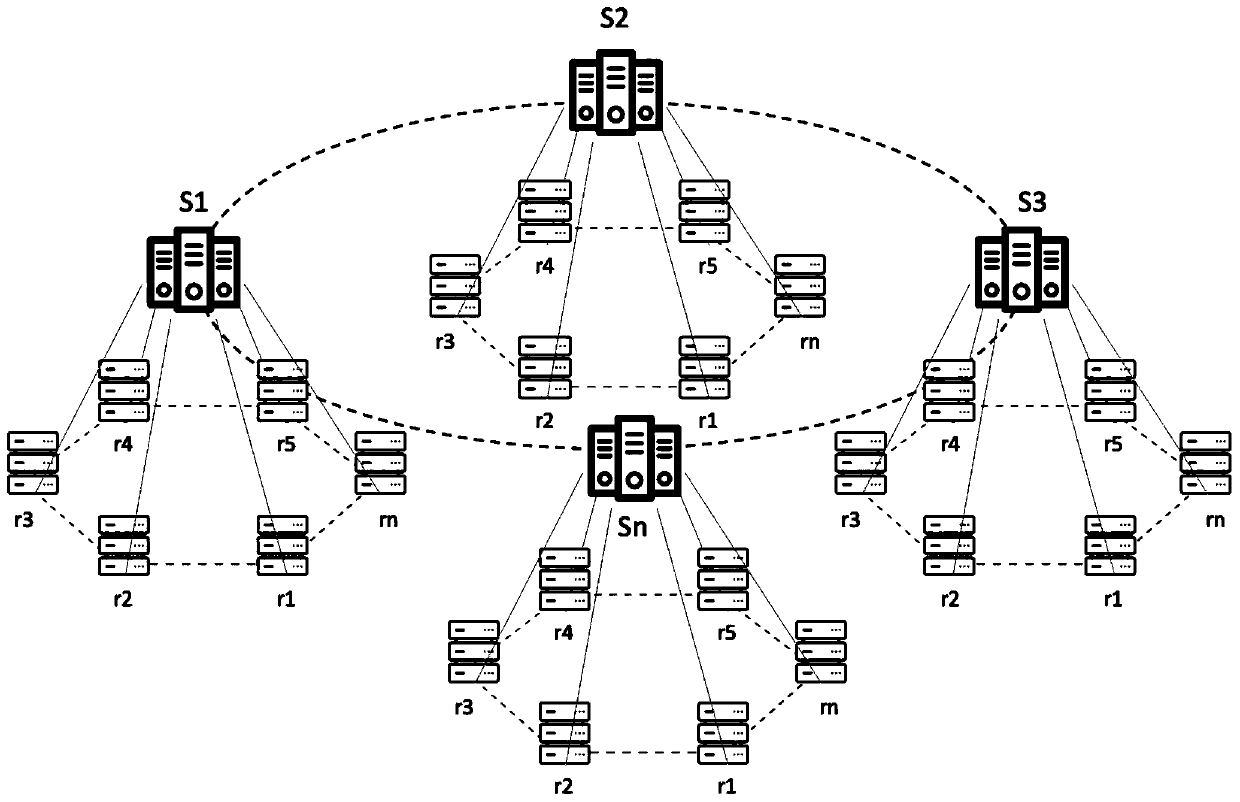
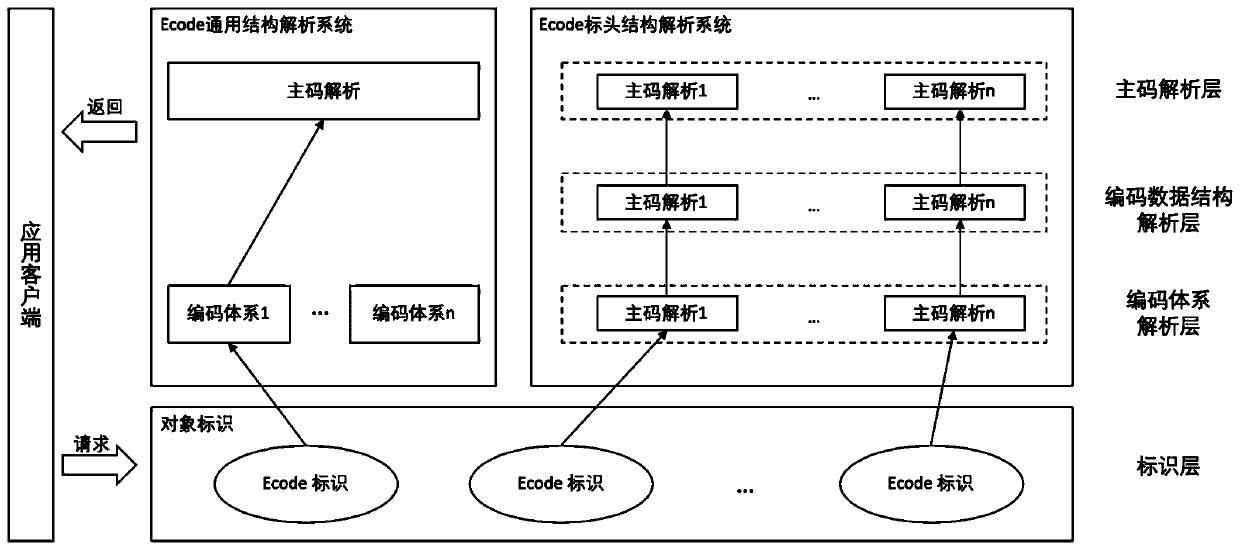
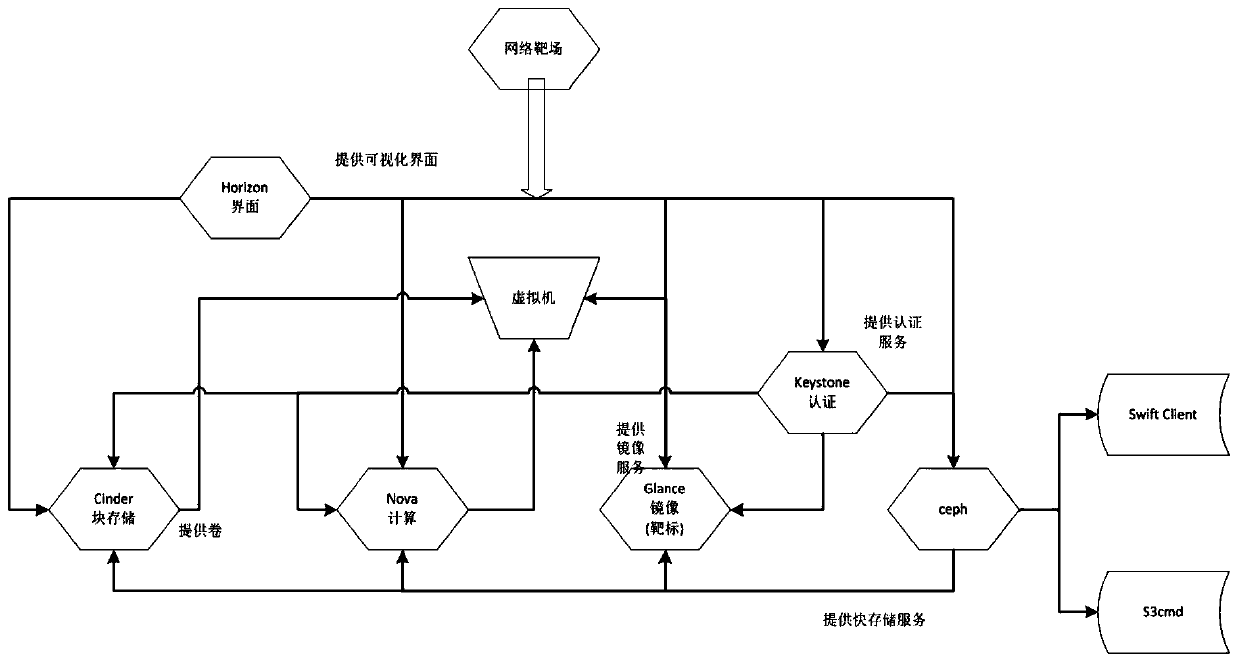
Patents
Literature
250results about How to "Improve storage security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Identification analysis system implementation method based on blockchain technology and identification coding technology
ActiveCN110941611AEnsure safetyGuaranteed reliabilityDatabase distribution/replicationSpecial data processing applicationsThe InternetEngineering
The invention discloses an identification analysis system implementation method based on a blockchain technology and an identification coding technology. The method comprises the following steps: A, establishing a consensus node mechanism; B, carrying out on-chain deployment by utilizing an intelligent contract technology so as to guarantee an identification rule; cC generating a data tree management mode for producing a full link based on a distributed account book technology; D, establishing a component model; E, querying the component model; if a result is inquired, directly entering the step G, otherwise, entering the step F; F, performing intercommunication analysis of the identification system; and G, outputting identification information. According to the method, the management efficiency of the identification data can be effectively enhanced, identification codes are unified, the method is unified with the construction of a national identification analysis system, the identification information management of all elements and all links of an industrial internet identification analysis ecosphere is realized, and an interconnected and intercommunicated data ecological chain isformed between the method and other identification systems.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
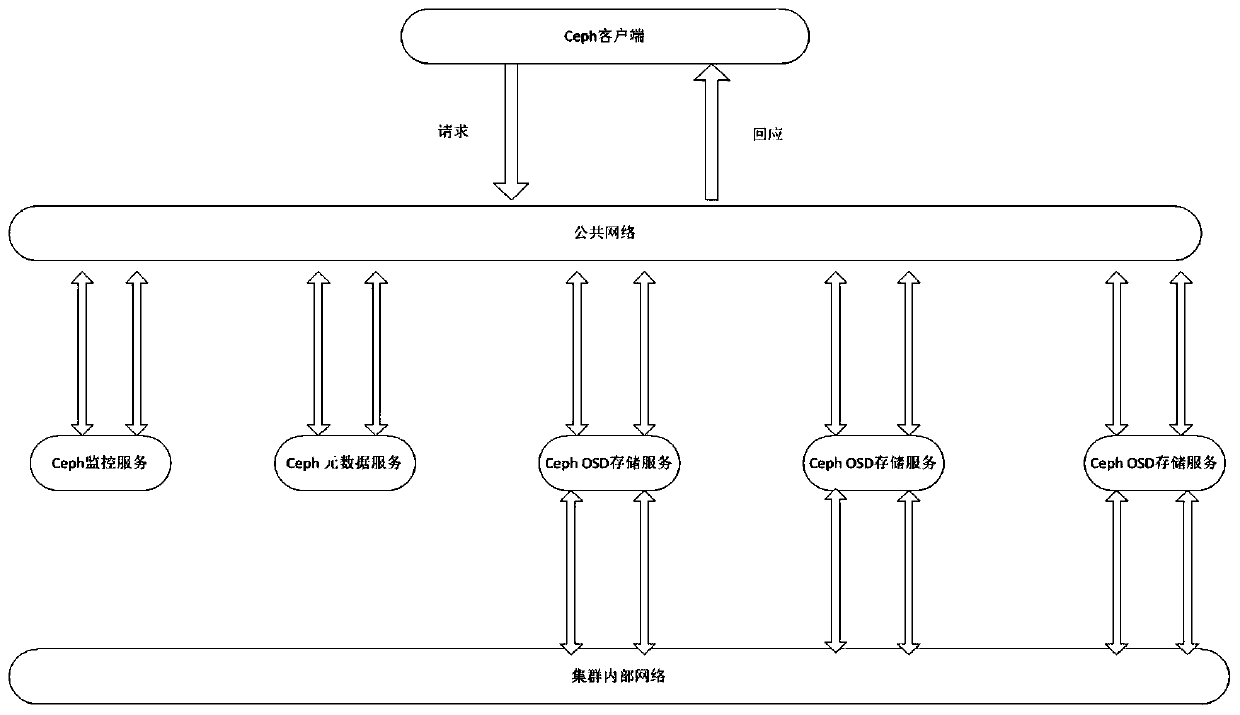
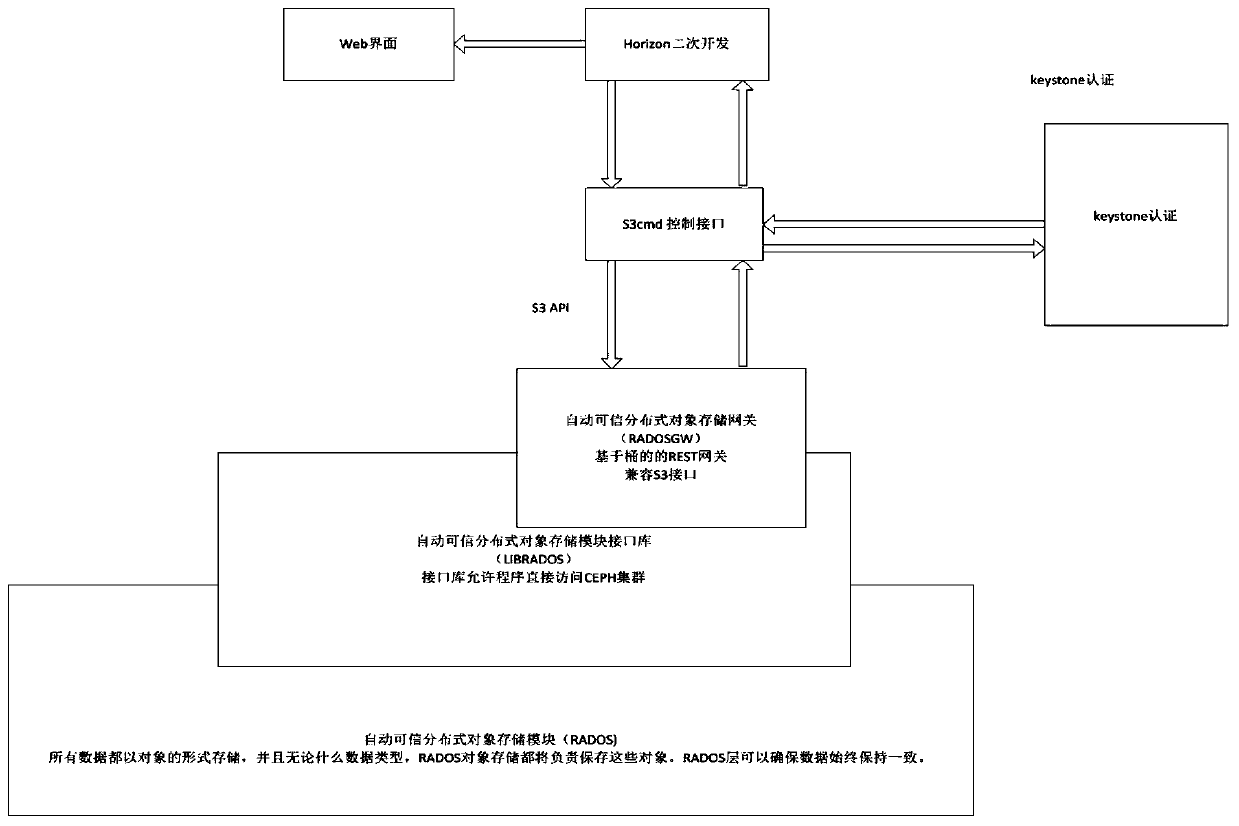
Ceph-based network target range rear-end storage system design method
PendingCN110750334AImprove deployment efficiencyImprove storage securityInput/output to record carriersSoftware simulation/interpretation/emulationStorage securityIncremental backup
The invention relates to a Ceph-based network target range rear-end storage system design method, and relates to the technical field of information security. The invention provides a construction method of a network target range rear-end storage system under a cloud architecture in order to solve the problems existing in an existing network target range rear-end storage system. According to the method, the Ceph is combined with the OpenStack, the Ceph is used as Nova in the OpenStack; an identity authentication service Keystone of the OpenStack is bound with a Ceph object gateway at a storagerear end of a Glance, Cinder native component, and secondary development of management application is carried out based on a Ceph gateway module. The method can effectively improve the deployment efficiency and the storage security of the network target range. Therefore, the functions of second-speed starting of the virtual machine, real-time migration of the virtual machine, data fragmentation storage, data full backup, data incremental backup and the like in the network target range are achieved.
Owner:BEIJING INST OF COMP TECH & APPL
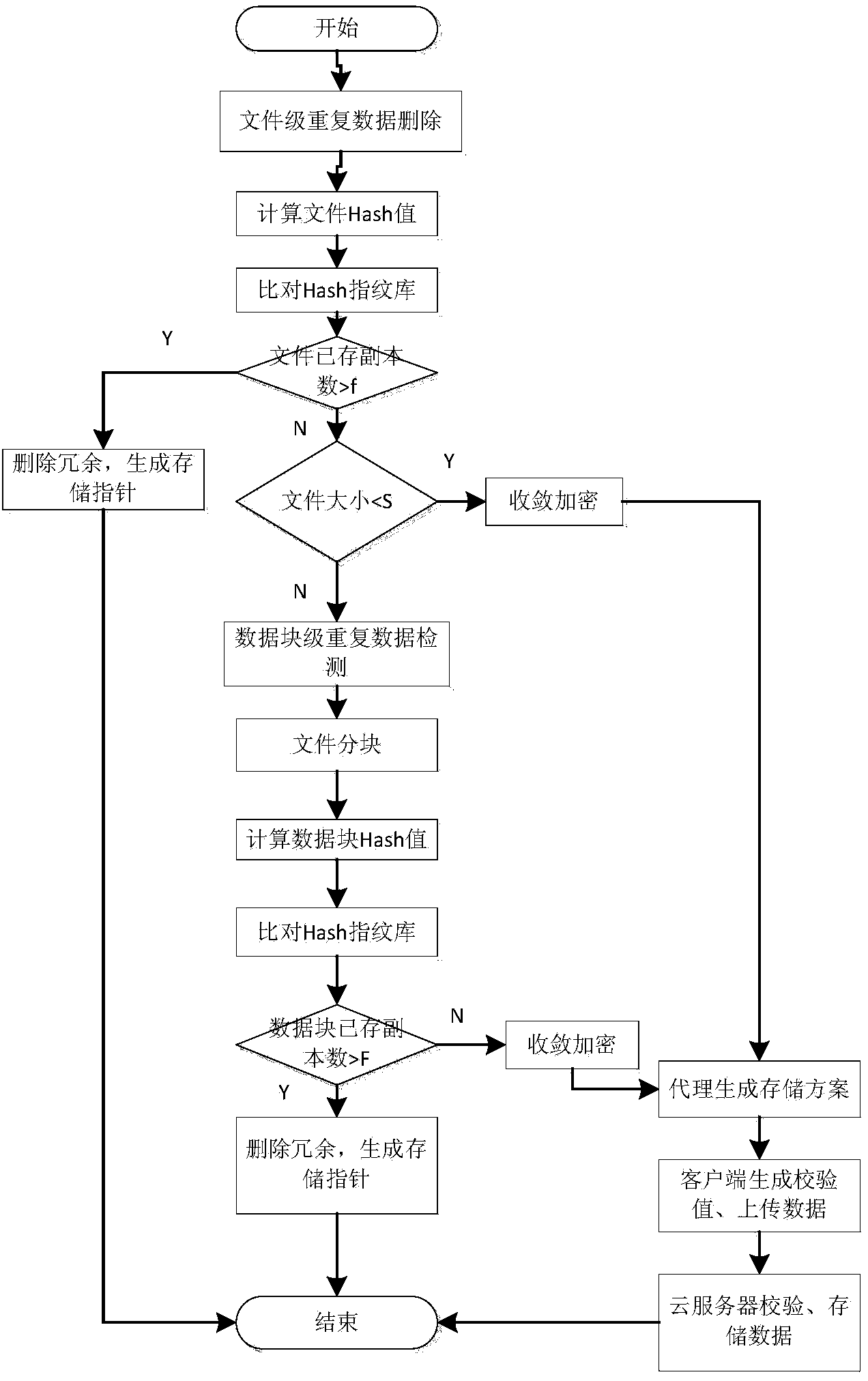
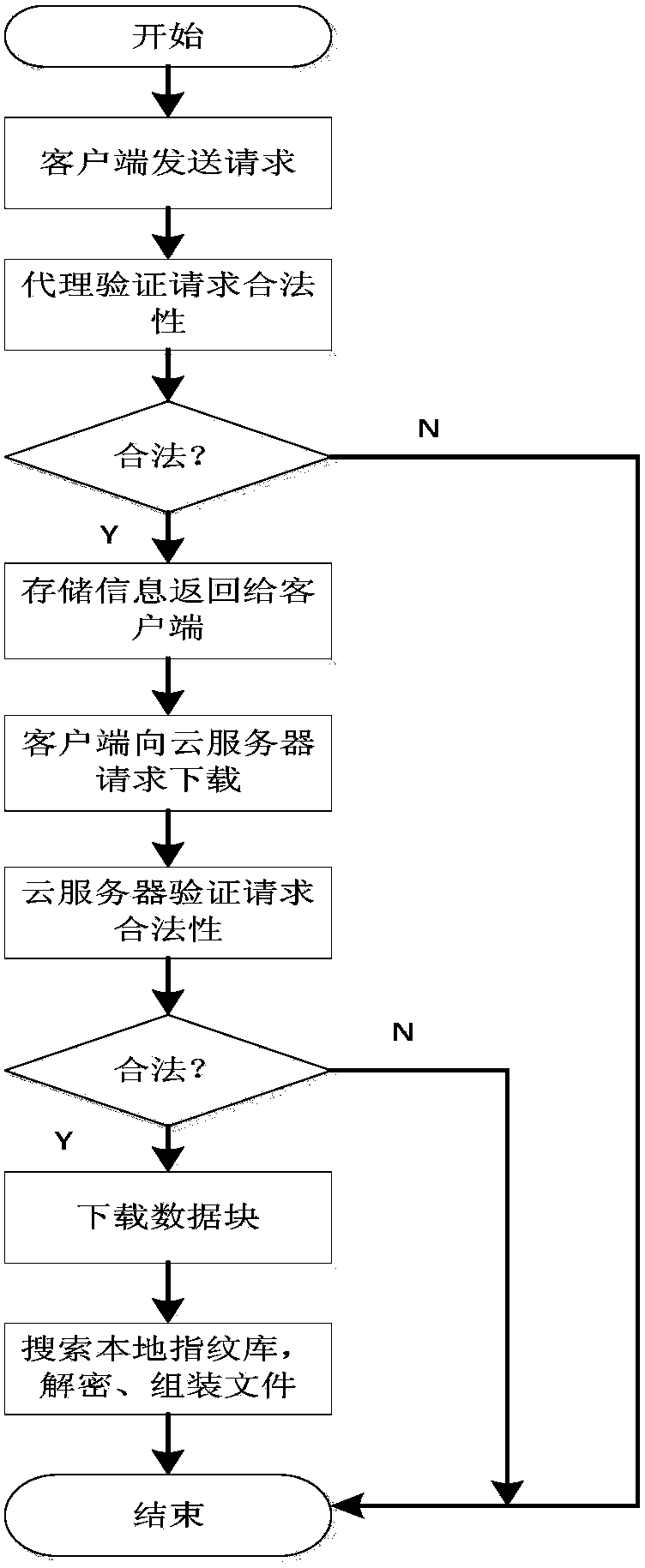
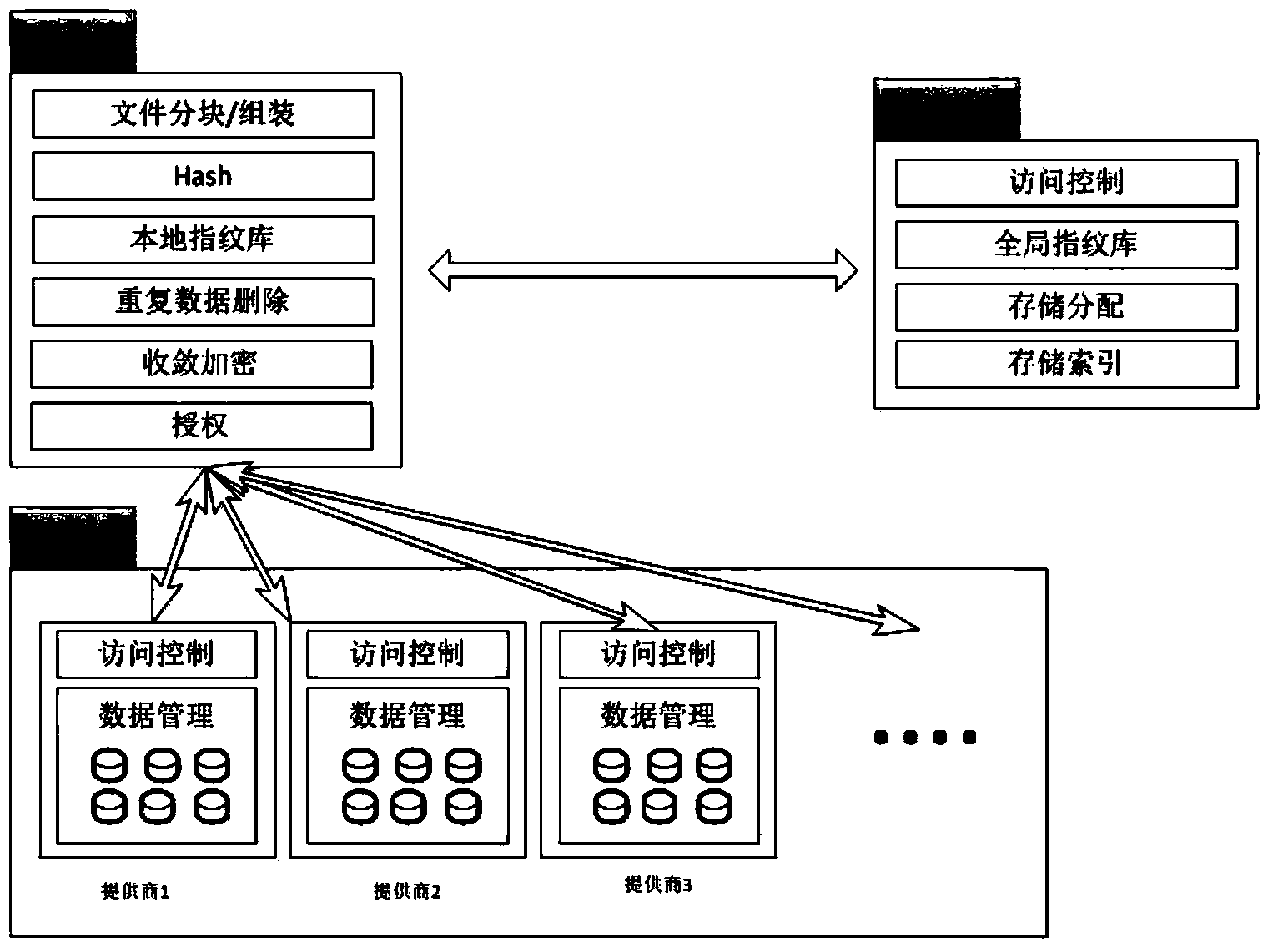
Repeating data deleting system and method applicable to cloud storage
The invention discloses a repeating data deleting system and method applicable to cloud storage. The repeating data deleting system is based on strategies, a security agent and a random storage mechanism are adopted, a storage service is separated from a security service, the space utilization rate of cloud storage is improved, bandwidth occupation of redundant data is reduced, and security of user data and privacies is improved at the same time. The system is mainly composed of a client, the security agent and the cloud storage, wherein the security agent is the most secure core and is mainly used for ensuring the security of the user data and privacies. The repeating data deleting system and method applicable to cloud storage have the advantages of being high in security, system efficiency, bandwidth utilization rate and the like, and can resist replay attack, impersonation attack and security threats brought by partially trusted cloud storage providers.
Owner:NANJING UNIV OF POSTS & TELECOMM
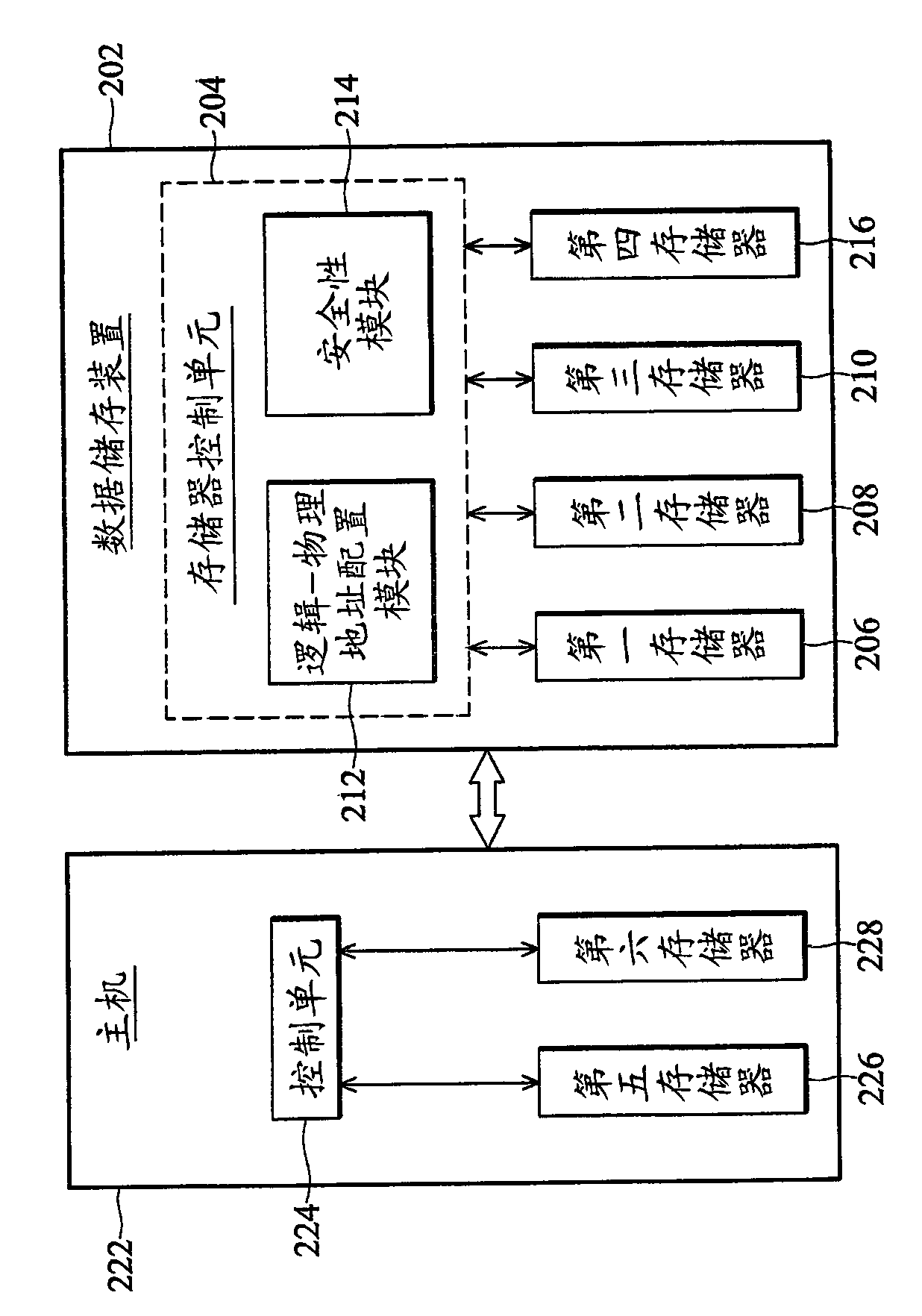
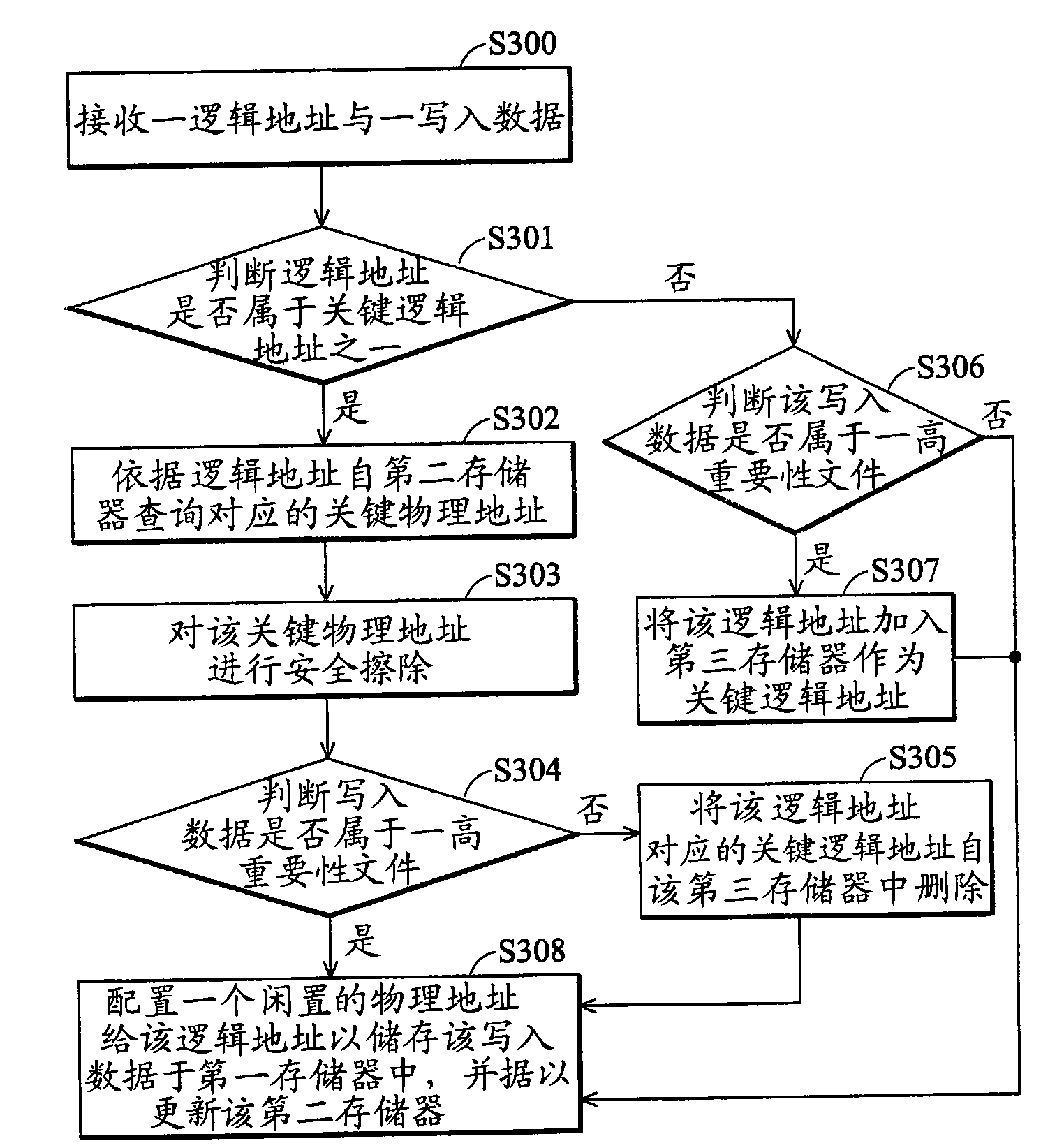
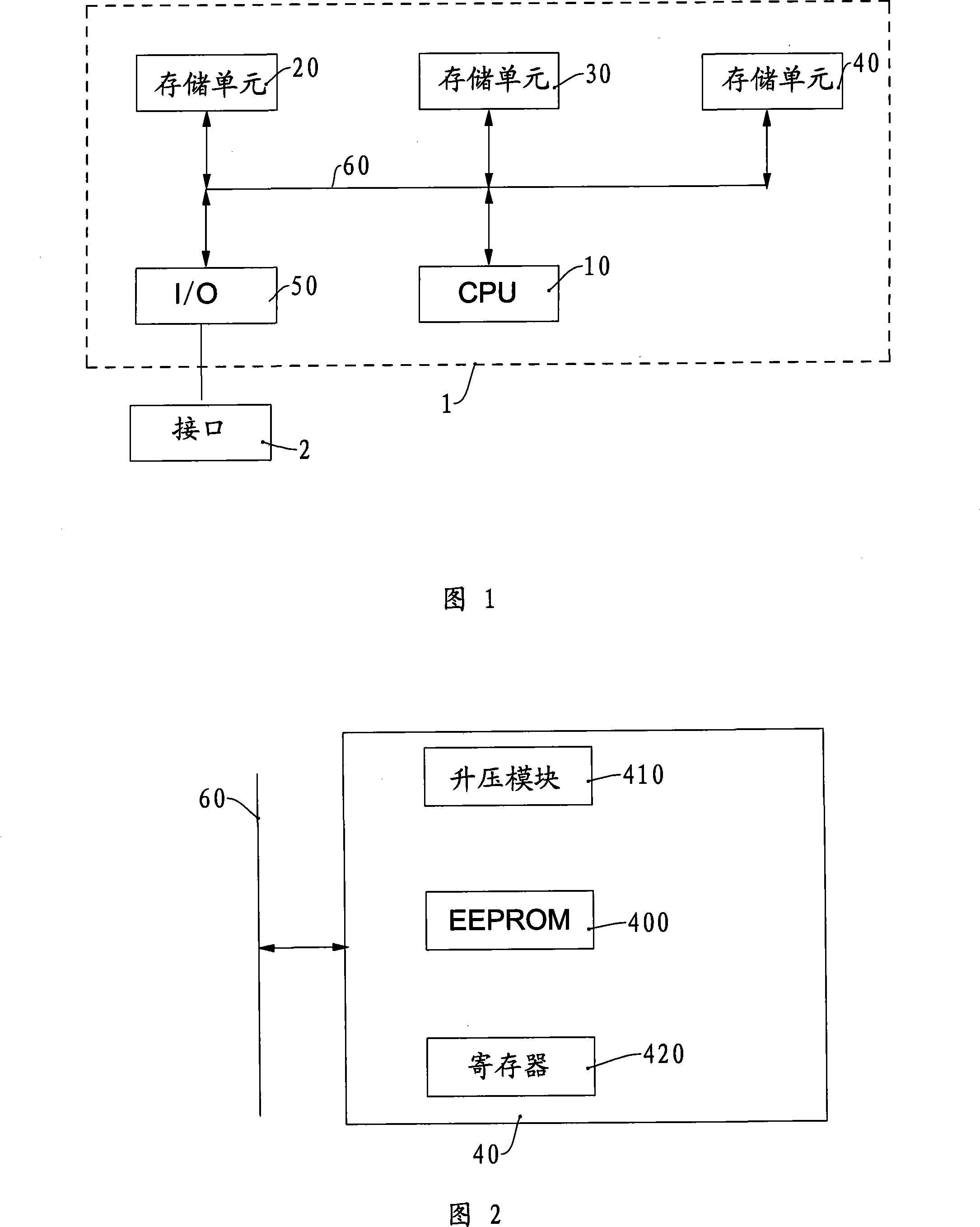
Data storage device and method
ActiveCN101673243AImprove storage securityMemory architecture accessing/allocationMemory adressing/allocation/relocationHost machineTertiary storage
The invention provides a data storage device and a method, wherein, the data storage device comprises a memory control unit and three memories. The memory control unit comprises a security module anda logical-physical address configuration module, and receives a logical address and a writing data from a host under a writing operation; the security module is responsible for judging whether the logical address belongs to one of key physical addresses stored in a third memory, if so, a logical-physical address mapping table in a second memory is searched according to the logical address to obtain a key physical address; and then the logical-physical address configuration module configures a physical address laid aside in a first memory and stores the above writing data to the logical address, and updates the logical-physical address mapping table in the second memory. The invention is conducive to improving the security of data storage.
Owner:VIA TECH INC
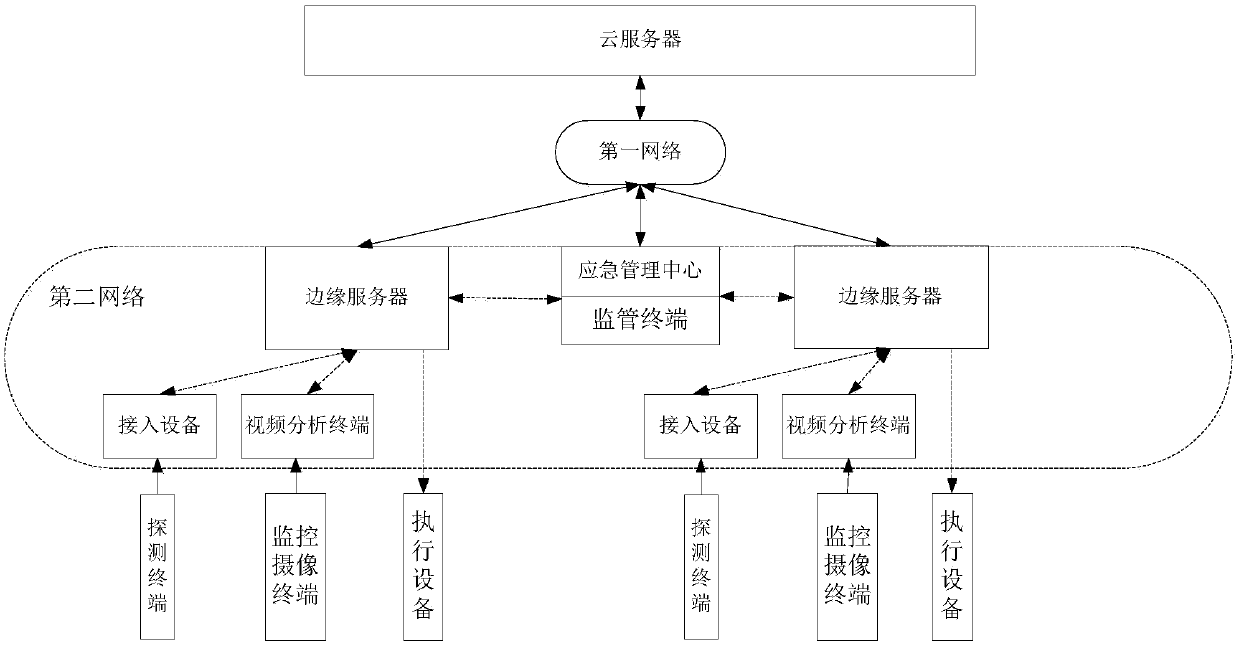
Smart security supervision system
InactiveCN109639797AImprove storage securityImprove robustnessParticular environment based servicesNetwork topologiesMonitoring statusStorage security
The invention is applicable to the technical field of smart security, and provides a smart security supervision system, comprising: a cloud server; a plurality of edge servers that communicate with the cloud server through a first network; a plurality of access devices connected to the edge server; and a plurality of detecting terminals connected to the access devices, wherein the access devices are configured to report the current monitoring data acquired by the detecting terminals to the edge servers by using the second network communication; the edge servers are configured to receive and store the current monitoring data, determine whether the monitoring data exceeds a preset threshold based n the monitoring data, and if so, report the current monitoring data and a first warning messageto the cloud server. The system enhances the storage security of the monitoring data by adding edge servers to analyze and store the monitoring data, so that the data analysis is completed on the local edge server, and the system can still operate normally locally in the case of network delay and network failure with enhanced reliability and good robustness.
Owner:ZDST COMM TECH CO LTD
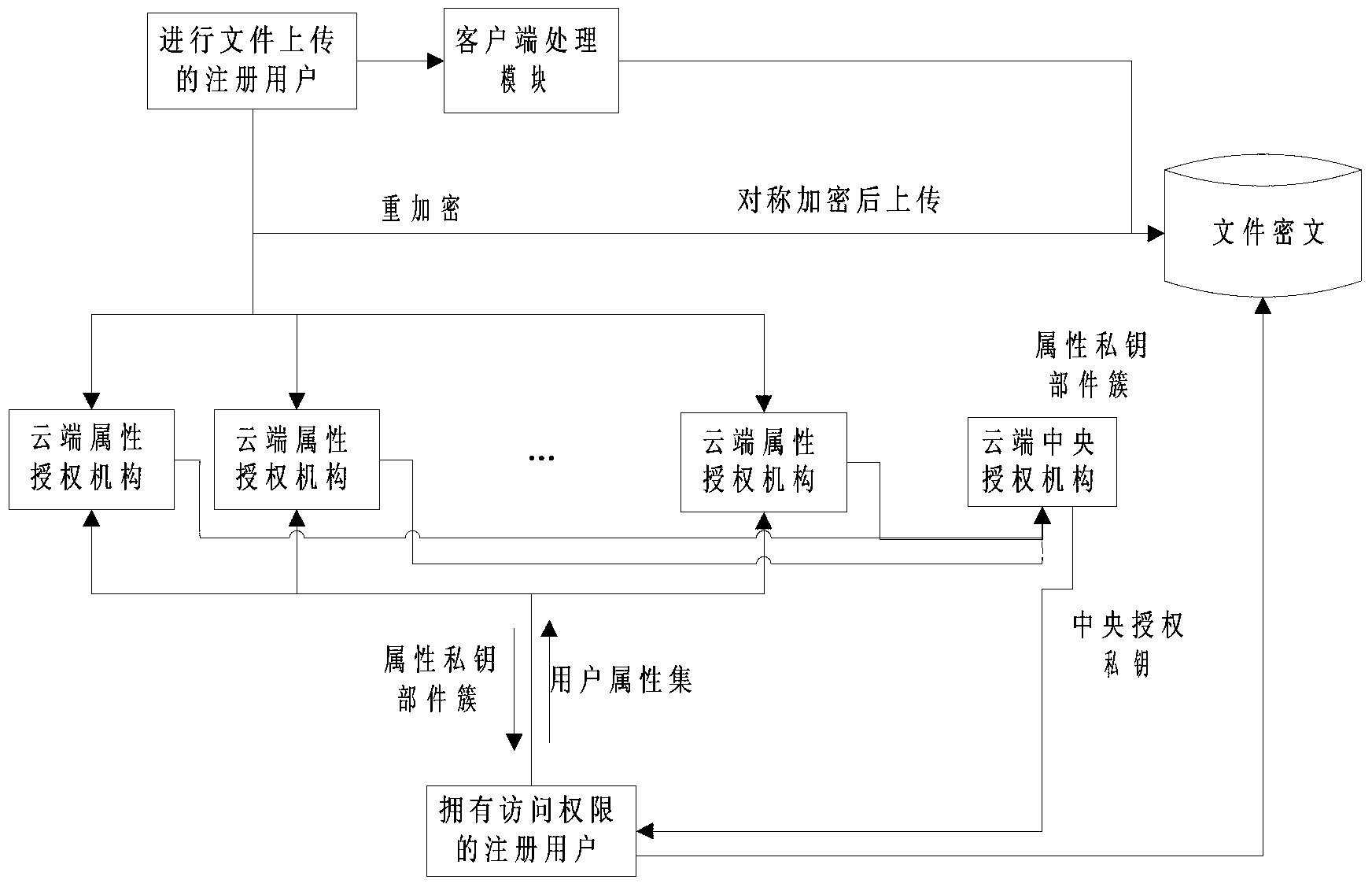
Method for protecting data of cloud storage system
The invention relates to a method for protecting data of a cloud storage system. The cloud storage system comprises a cloud central authorization mechanism, a client processing module, cloud severs and a plurality of cloud attribute authorization mechanisms. The cloud attribute authorization mechanisms manage attribute information of registered users. The method for protecting the data of the cloud storage system has the advantages that the method is based on the various attribute authorization mechanisms specifically for attributes of the registered users, brand new encryption and decryption processes are designed for the user data stored in the cloud storage system, the safety of the user data stored in the cloud storage system is greatly improved, and risks that malicious users breach the attribute authorization mechanisms are spread as compared with an existing cloud storage system with a single authorization mechanism.
Owner:SUZHOU SIJIE MAKEDING SOFTWARE CO LTD
Special water-based ink for printing tipping paper for cigarette and preparation method thereof
The invention provides special water-based ink for printing tipping paper for a cigarette. The special water-based ink comprises pure acrylic resin, pigment, packing, a defoamer, fumed silica, surfactant, wetting dispersant, water and alcohol. A preparation method of the water-based ink is also provided by the invention. Compared with other ink for printing the tipping paper for the cigarette, the special water-based ink for printing the tipping paper for the cigarette disclosed by the invention has the advantages that the ink can be diluted by pure water; the consumption is reduced; and the ink does not burn or blast, does not belong to dangerous chemicals, and increases the printing, transporting and storing safety. The water tolerance, the curling resistance and the printing adaptability of the ink are greatly improved; and the printing effect can be equivalent to those of alcohol-soluble ink and solvent-based ink. In a word, the water-based ink disclosed by the invention is simple in cost, low in price, good in printed adhesive force, strong in water resistance, and fast to dry. Thus, the water-based ink is especially suitable for package printed matters such as foods, beverage and medicaments.
Owner:哈尔滨绿科科技有限公司
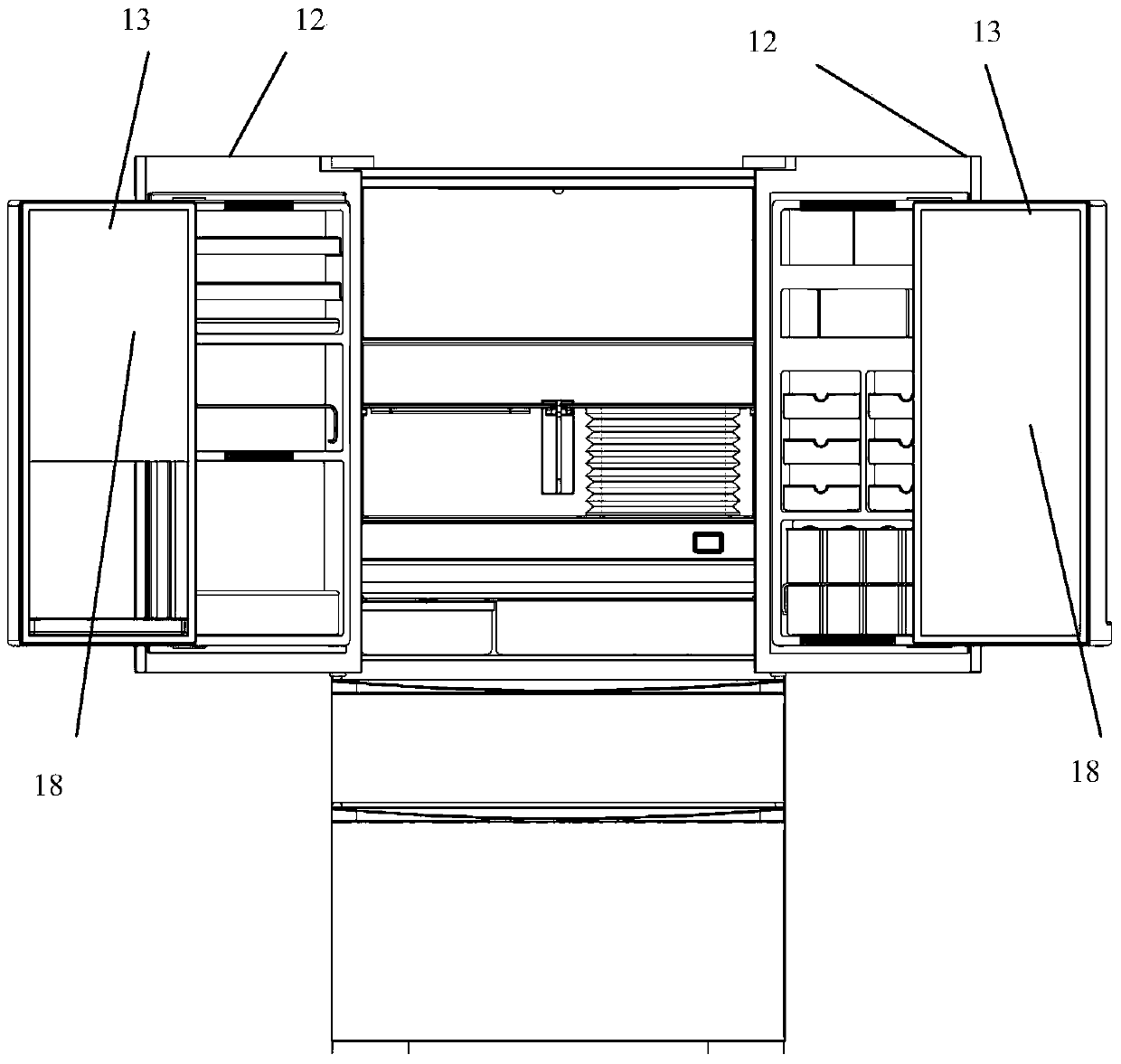
Refrigerator
ActiveCN103471311ASimple structureEasy to useLighting and heating apparatusDomestic refrigeratorsFood materialCold store
The invention relates to a refrigerator which comprises a refrigerator body. A refrigerating chamber is arranged on the upper portion of the refrigerator body, and a freezing chamber is arranged on the lower portion of the refrigerator body. A refrigerator door mounted on the refrigerator body comprises an inner door and an outer door. The inner door and the outer door form the refrigerator door which is of a double-layered door structure. When the refrigerator door is closed, the inner door is positioned in the refrigerator, the outer door facing users enables the users to open the refrigerator body, the inner door and the outer door are in rotating or sliding connection, and the outer door and the refrigerator body are in rotating connection. A plurality of special storage devices and lighting devices are arranged in the refrigerator body, the refrigerating chamber and the freezing chamber according to stored objects. The refrigerator is simple in structure and convenient to use, food can be effectively stored according to different packages or cleanliness, neatness and convenience levels of the food, the problems like scattering and odor tainting of the food or food materials are avoided, safety and convenience in storing of the food or the food materials are improved, and the refrigerator is in conformity with use habits of users.
Owner:GUANGDONG CANBO ELECTRICAL
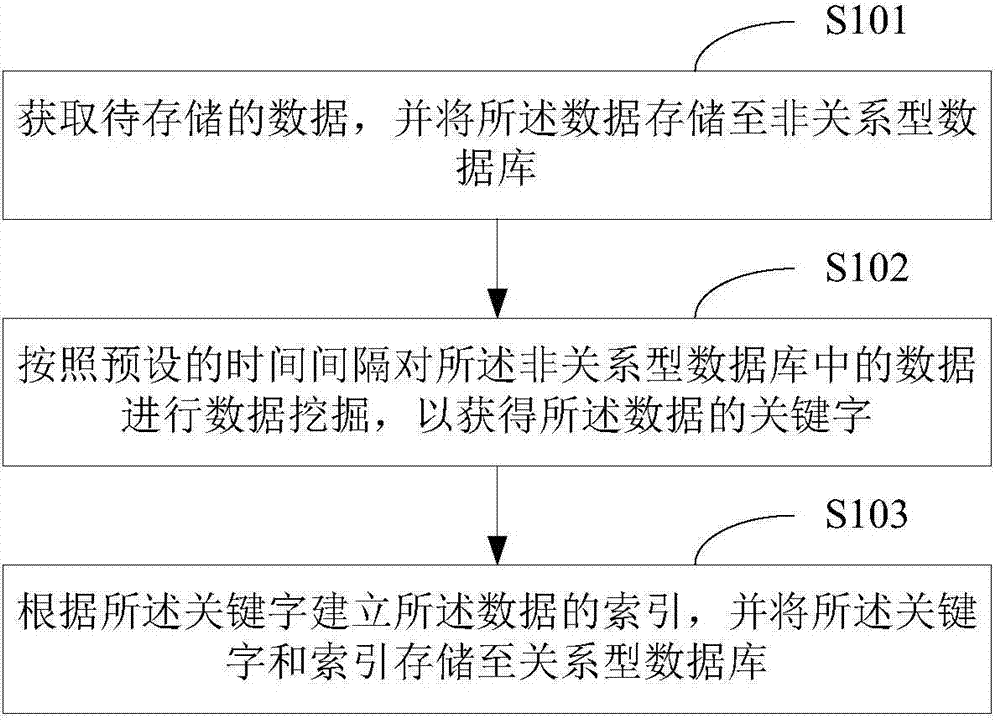
Data storage method and system
InactiveCN104504137ALow costImprove storage securitySpecial data processing applicationsStorage securityData library
The invention is suitable for the technical field of data treatment and discloses a data storage method and system. The data storage method includes that acquiring data to be stored, and storing the data in a non-relational database; carrying out data mining on the data in the non-relational database according to a preset time interval to obtain keywords of the data; building index of the data according to the keywords, and storing the keywords and index in a relational database. The data storage method and system lower the security data storage cost, improve the security data storage safety and improve the security data mining and inquiry efficiency.
Owner:SHENZHEN KEMANDA INTELLIGENT MANAGEMENT SCI &TECH
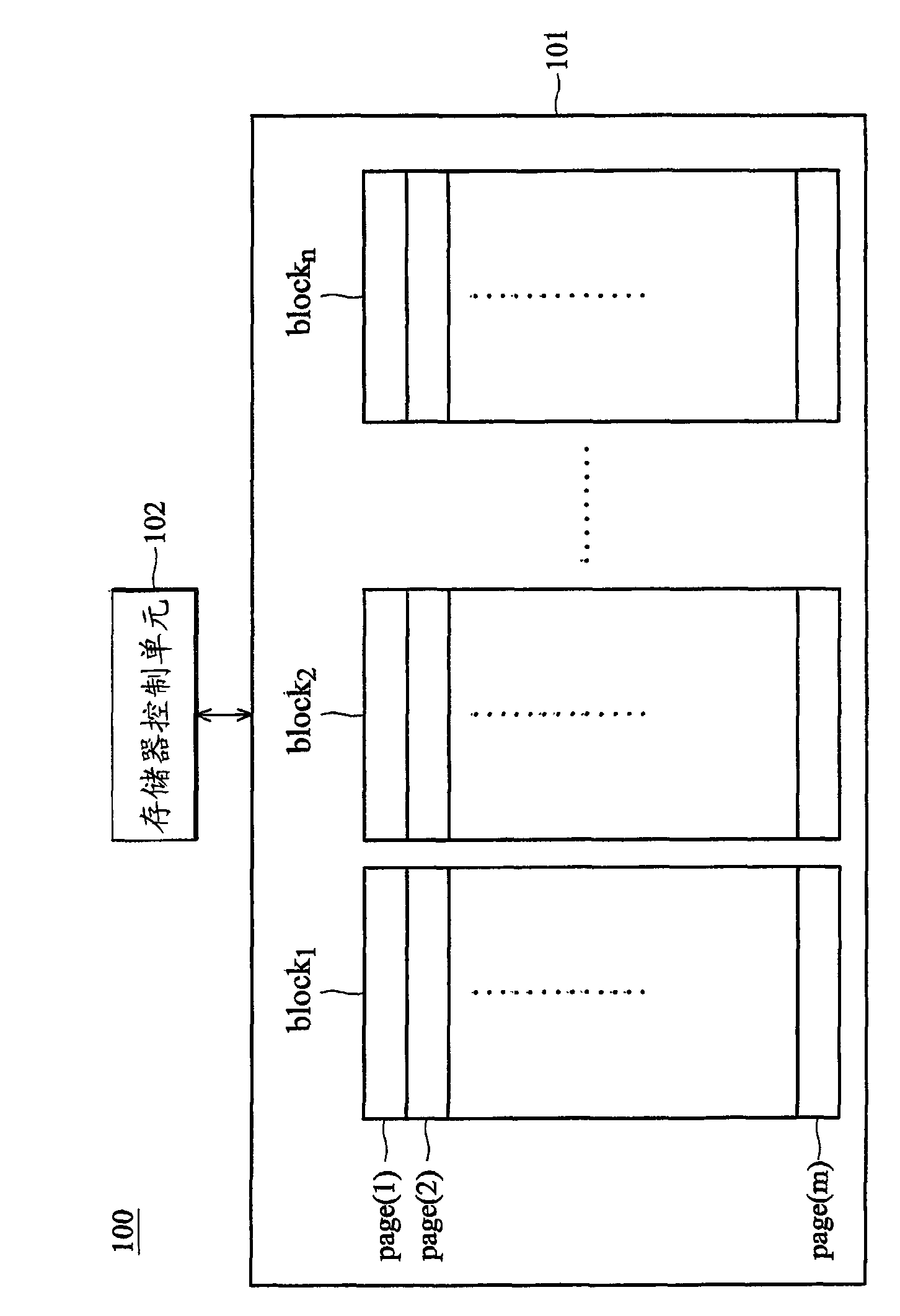
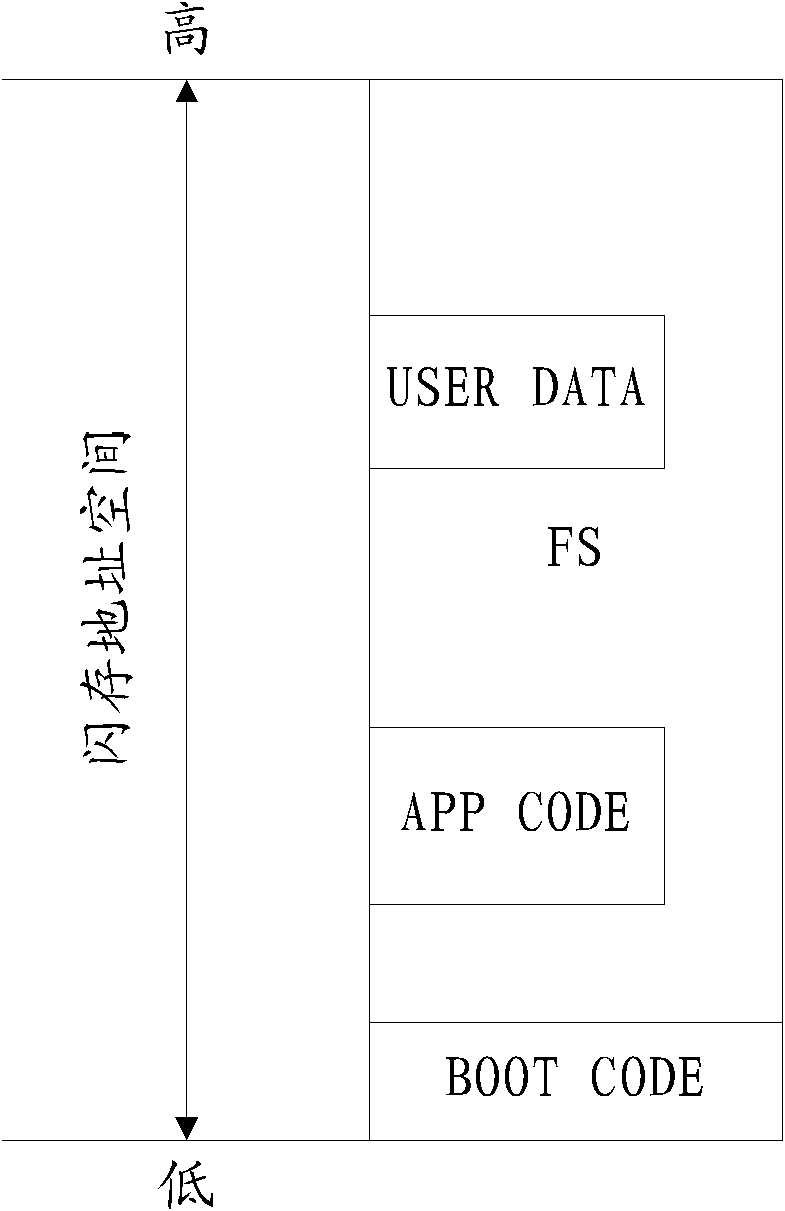
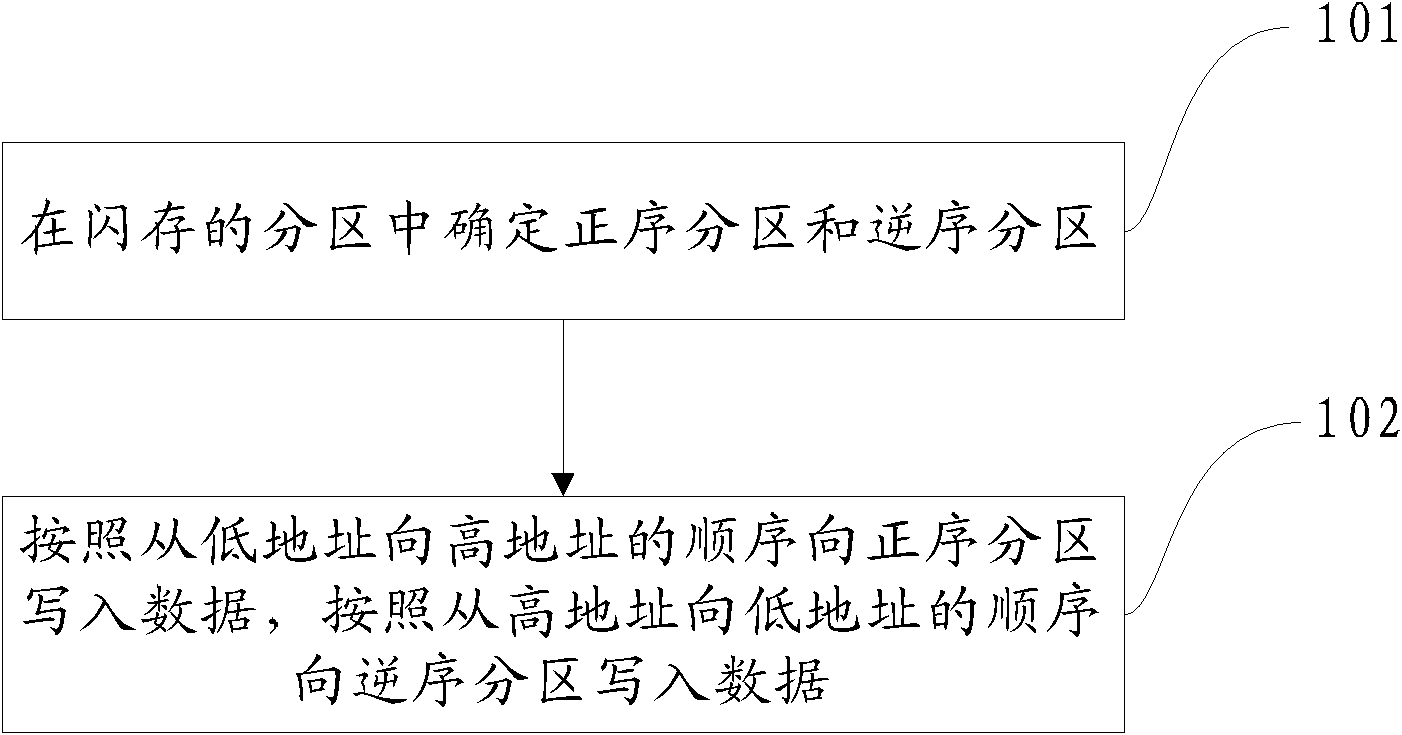
Storing and accessing method of flash memory data and device thereof
ActiveCN102135943AAvoid lossImprove storage securityMemory adressing/allocation/relocationAccess methodComputer science
The embodiment of the invention discloses a storing and access method of flash memory data and a device thereof. In order to improve the safety of data storage and guarantee the high-efficient utilization of Flash resource, the technical scheme provided by the invention comprises the following steps: determining positive sequence partitions and negative sequence partitions in the partitions of the flash memory, wherein the positive sequence partition is a partition including the lowest address or partitions sequentially continuously arranged from the partition including the lowest address, and the negative sequence partitions are other partitions except for the positive sequence partition; and writing data in the positive sequence partition from a low address to a high address, and writing the data in the negative sequence partitions from the high address to the low address. The method and the device are suitable for the operation and the use of the flash memory.
Owner:HUAWEI DEVICE CO LTD
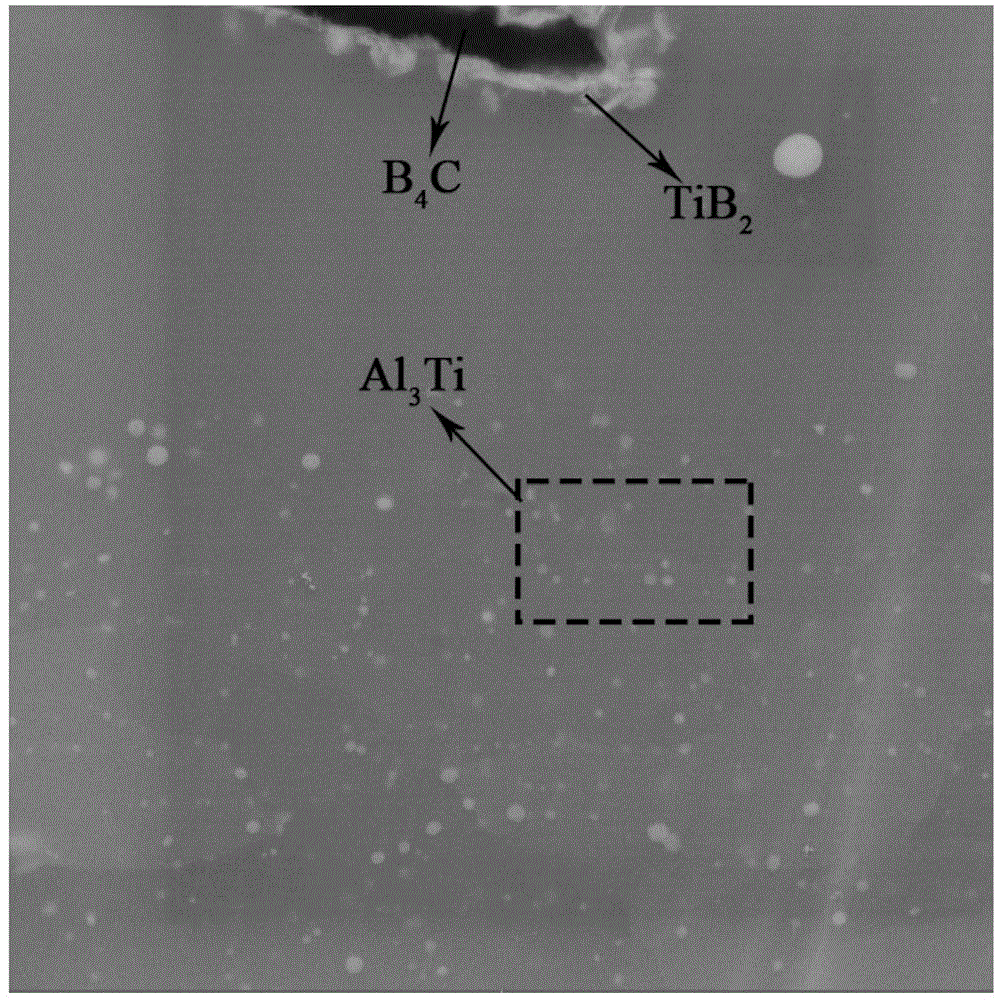
Aluminum-based boron carbide composite material and neutron absorption plate
ActiveCN104313400AImprove mechanical propertiesNot easy to breakNuclear energy generationNuclear reaction controlAl elementBoron carbide
The invention discloses an aluminum-based boron carbide composite material and a neutron absorption plate. The aluminum-based boron carbide composite material comprises the following components in percentage by mass: 15-35 percent of B4C, 0.5-7 percent of a Ti element and 60-84.5 percent of a Al element, wherein in the composite material, the existence form of the Ti element is as follows: the Ti element coats the surface of B4C particles in a TiB2 compound form. The neutron absorption plate is a plate made from the aluminum-based boron carbide composite material. The test proves that the elongation rate of the aluminum-based boron carbide composite material at normal temperature is 6-16 percent and is superior to that of the conventional composite material, and when the prepared neutron absorption plate is used, collision or thermal stress deformation can be resisted, and the plate is difficult to break, so that the storage safety performance is improved. Meanwhile, the tensile strength and neutron absorption performance can meet the application requirements.
Owner:SHENZHEN GRADUATE SCHOOL TSINGHUA UNIV
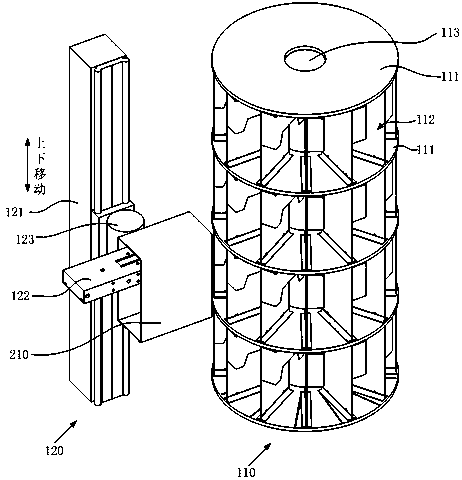
Rotating disc type automatic blood storage device and storage method
PendingCN111498355AImprove storage securityImprove access speedStorage devicesConveyor partsEngineeringRotating disc
The invention discloses a rotating disc type automatic blood storage device and a storage method. The device is characterized in that a central rotating shaft perpendicular to the ground is arranged in a refrigerator, a plurality of partition plates are arranged on the central rotating shaft from top to bottom at intervals, a plurality of storage positions used for placing blood bags are arrangedbetween every two adjacent partition plates, each storage position is provided with a movable storage box, and the blood bags are placed in the storage boxes. According to the device, the blood bags are stored and taken through one set of movable grabbing assembly, the occupied space is small, and the space utilization rate is high; meanwhile, automatic storing and taking of the blood bags are achieved, and the storing and taking speed and accuracy of the blood bags are effectively improved; and the storage environment of the blood bags is constant in humidity, constant in temperature and sterile, and the storage safety of blood is improved.
Owner:QINGDAO HAIER BIOMEDICAL TECH CO LTD +1
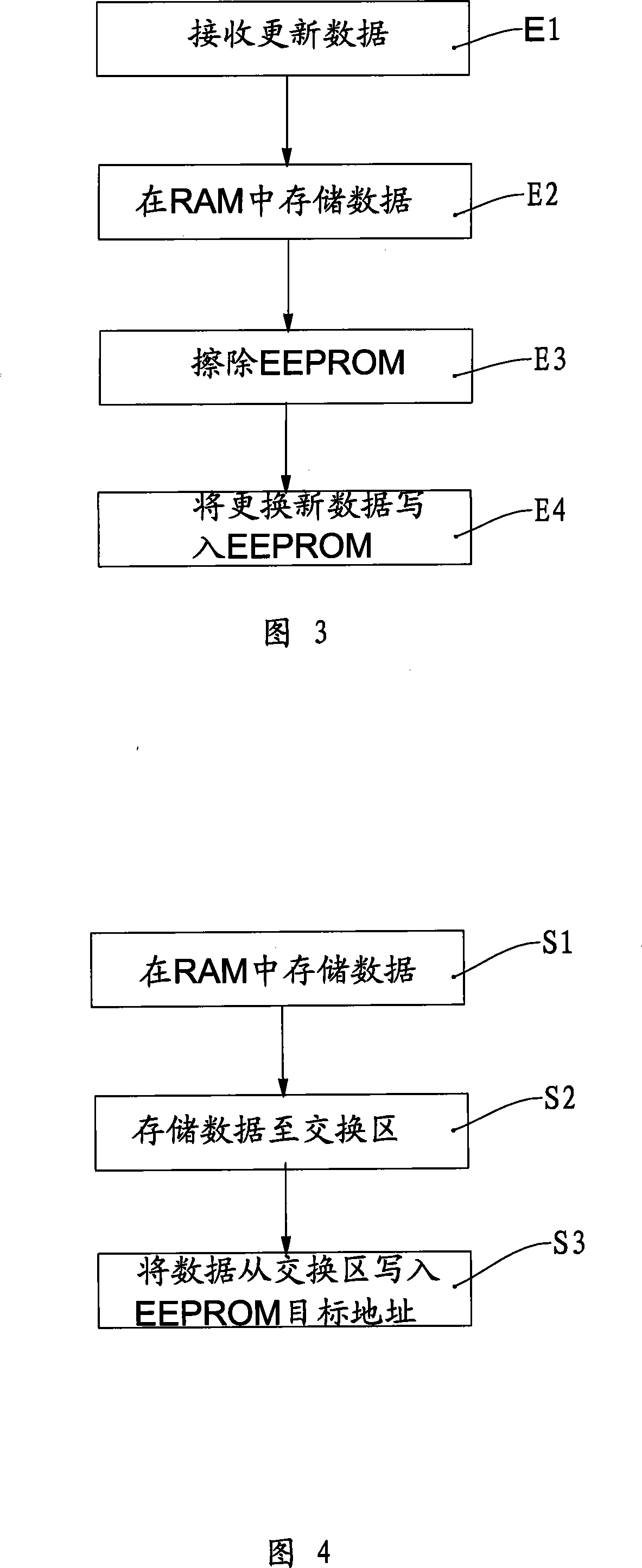
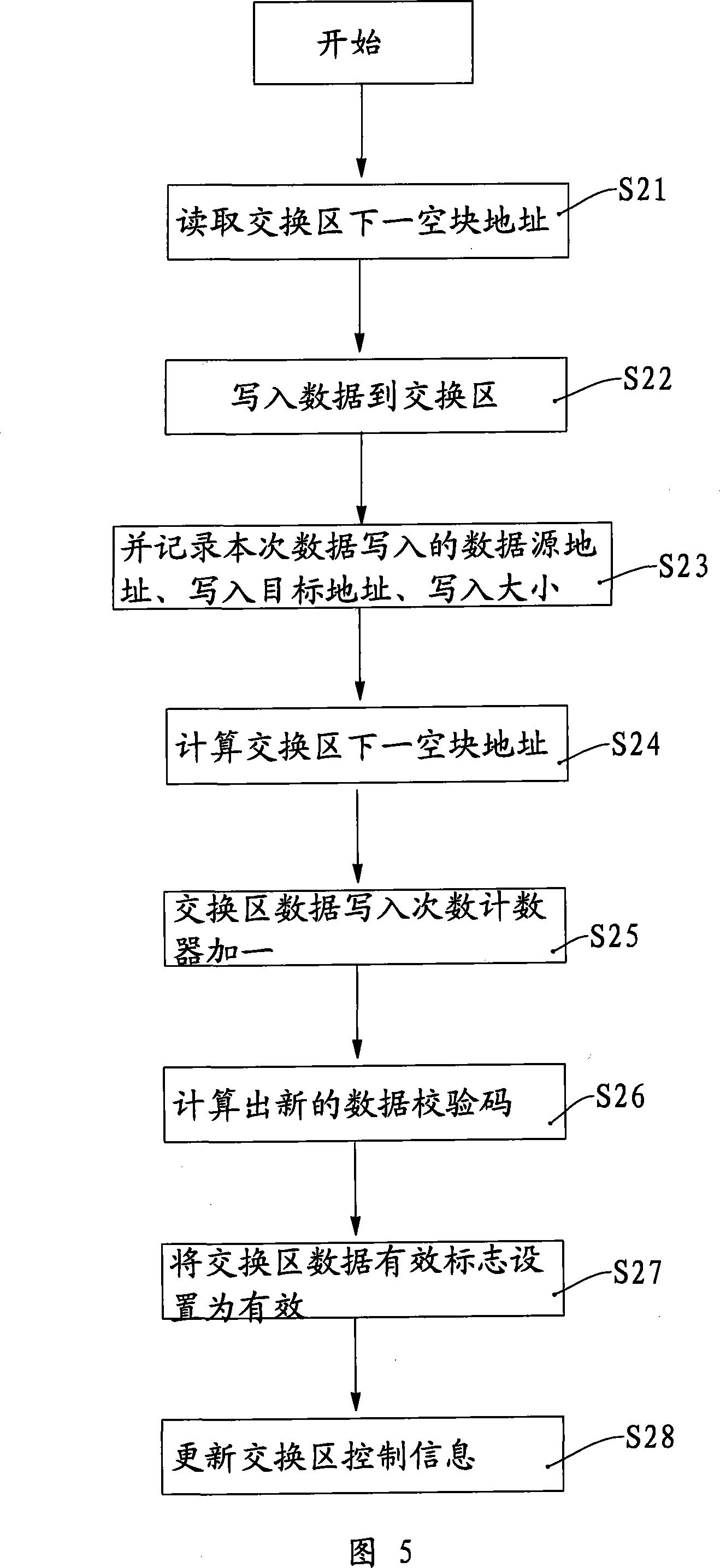
Smart card and data write-in method
ActiveCN101197006AWritten completely and accuratelyImprove storage securityDigitally marking record carriersMemory adressing/allocation/relocationMicrocontrollerStorage security
The present invention relates to various IC cards and a method of writing data into the IC cards. A smart card comprises a microcontroller and an interface ensuring that the smart card can communicate with a reading / writing terminal. The microcontroller comprises a microprocessor, a ROM, a RAM, an EEPROM and an I / O circuit. The ROM, the RAM, the EEPROM and the I / O circuit are connected to the microprocessor through a data bus, wherein, an exchange zone used for writing data each time is arranged inside the EEPROM. The data structure of the exchange zone comprises exchange zone control information and a data exchange zone, wherein, the exchange zone control information comprises an exchange zone data effective mark, an exchange zone data writing times counter, an exchange zone data next empty block address, a data writing target address array, a bad block counter and an exchange zone data check code. A buffer zone which corresponds to and exchanges data with the exchange zone is arranged in the RAM. The smart card of the present invention is high in data storage security, and can guarantee data writing integrity and accuracy each time.
Owner:EASTCOMPEACE TECH
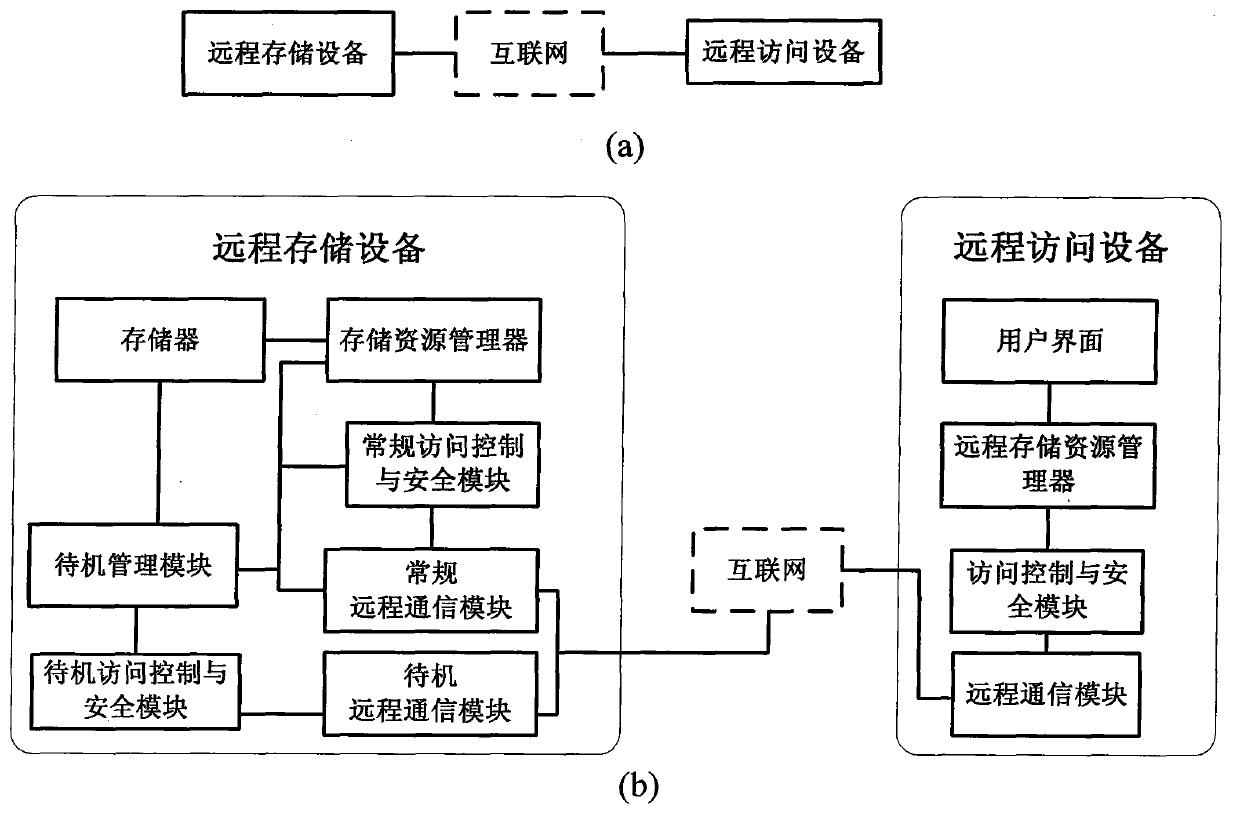
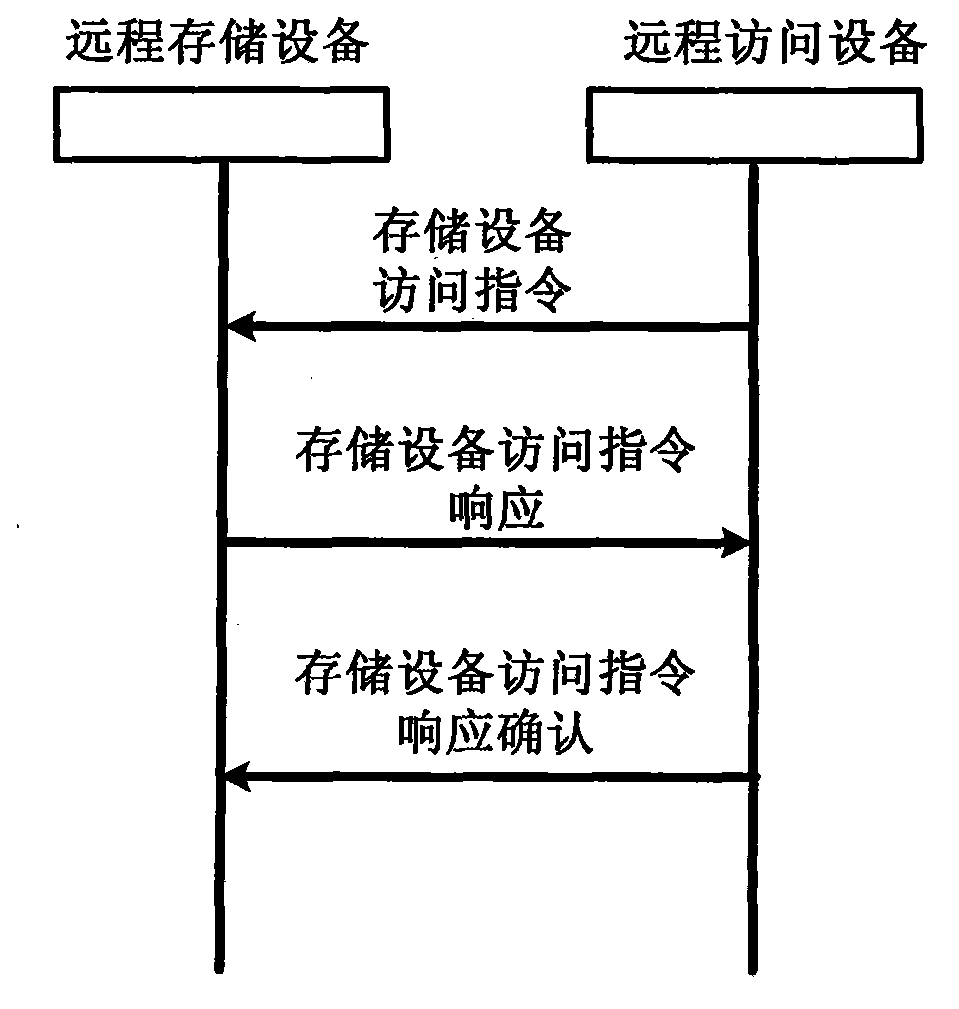
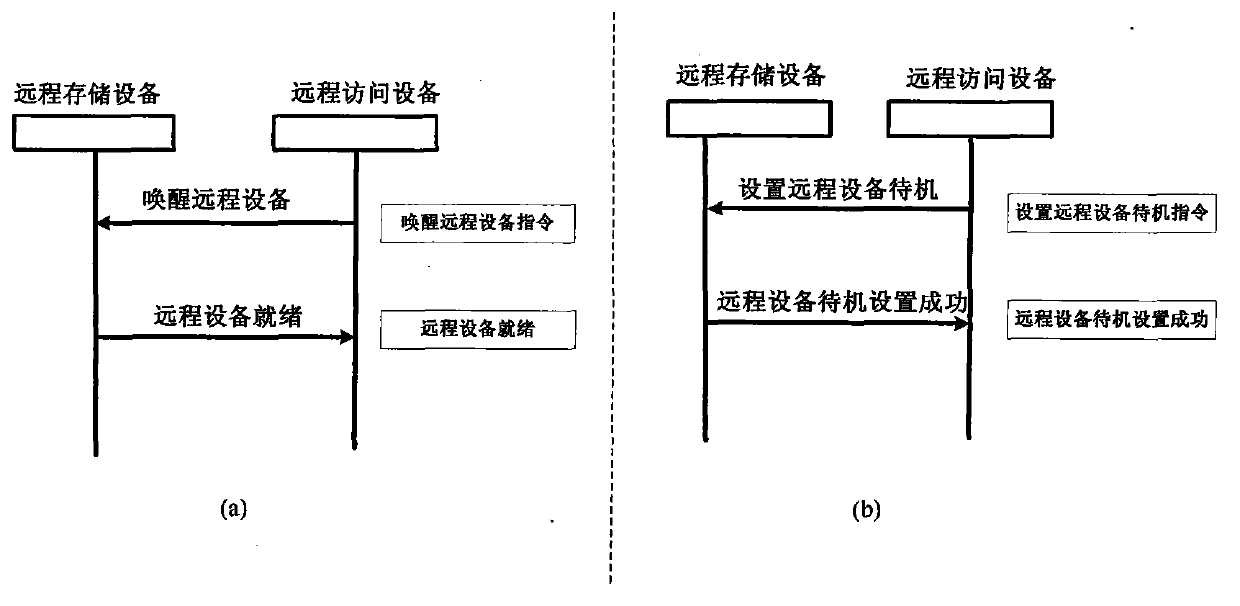
Low-energy-consumption remote storage system and design method thereof
InactiveCN103873540AIncrease capacityReduce lossUnauthorized memory use protectionPower supply for data processingEnd-to-end encryptionNetwork communication
The invention relates to a low-energy-consumption remote storage system and a design method thereof, in particular to a method of remote data storage by utilizing network communication, and a storage system, and belongs to the technical field of network communication and data storage. The remote storage system comprises a remote storage device and a remote access device, and has normal and standby work modes. The remote storage device comprises a storer, a storage resource manager, a normal access control and security management module, a standby access control and security management module, a normal remote communication module, a standby remote communication module and a standby management module, and the remote access device comprises a user interface, a remote storage resource manager, an access control and security module, and a remote communication module. In the period that the storer does not carry out an access operation, the storage device is in a low-power-consumption or power-off state, the energy consumption is effectively reduced; the end-to-end encryption can be performed, and the basic guarantee of the security of data resources of the user is provided.
Owner:李祥明 +2
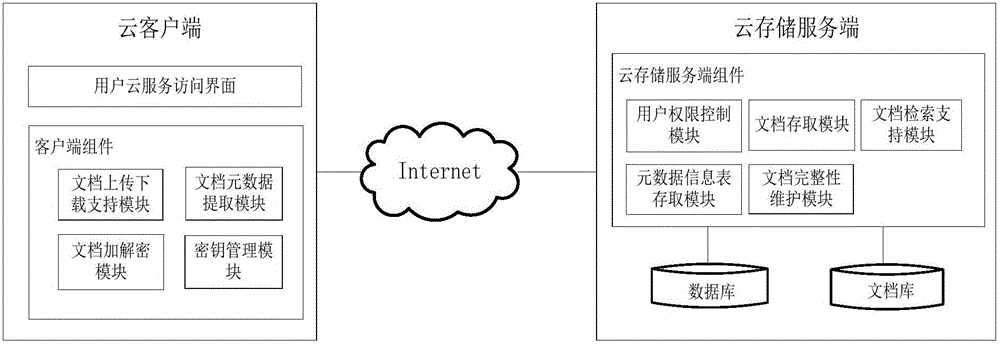
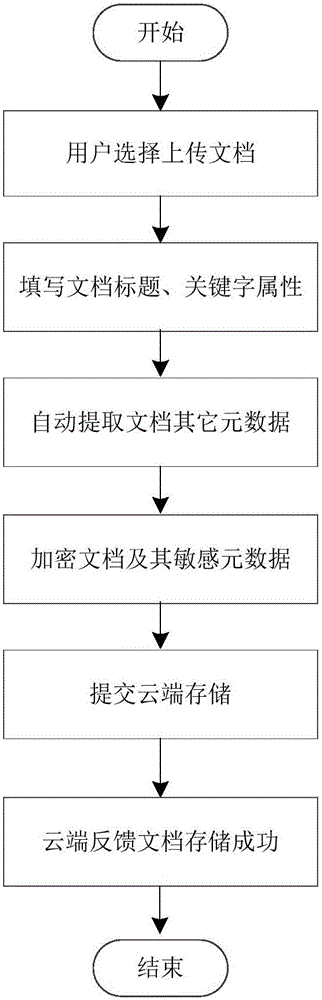
Document safety access method for cloud storage environment
InactiveCN104992124AImprove securityImprove storage securityDigital data protectionAccess methodDigital signature
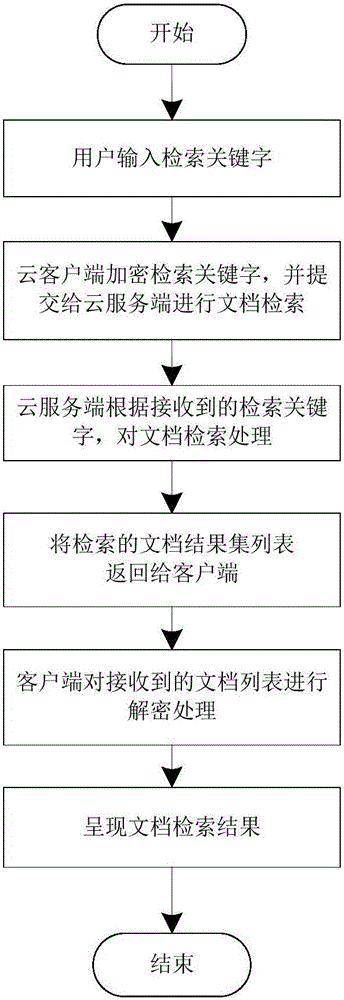
The invention belongs to the cloud technical field, and relates to a document safety access method for a cloud storage environment; the method uses client document encryption / decryption process and cloud cryptograph storage technology to ensure document safety access, and realizes cloud retrieval process through document meta-data information. The method can encrypt data content of uploaded documents, and can encrypt sensitive meta-data of the uploaded documents; a user can retrieval the documents through document keyword meta-data, and can determine document integrity according to a digital signature. The beneficial effects are that the cloud client can encrypt the document data, so the documents can be transmitted and stored in the cloud environment in an encryption mode, thus enhancing data safety level of the documents in the cloud environment. In addition, the document condition retrieval process can enable the user to realize fast retrieval access of the cloud documents; the method is especially suitable for user document safety storage application under a public cloud environment.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
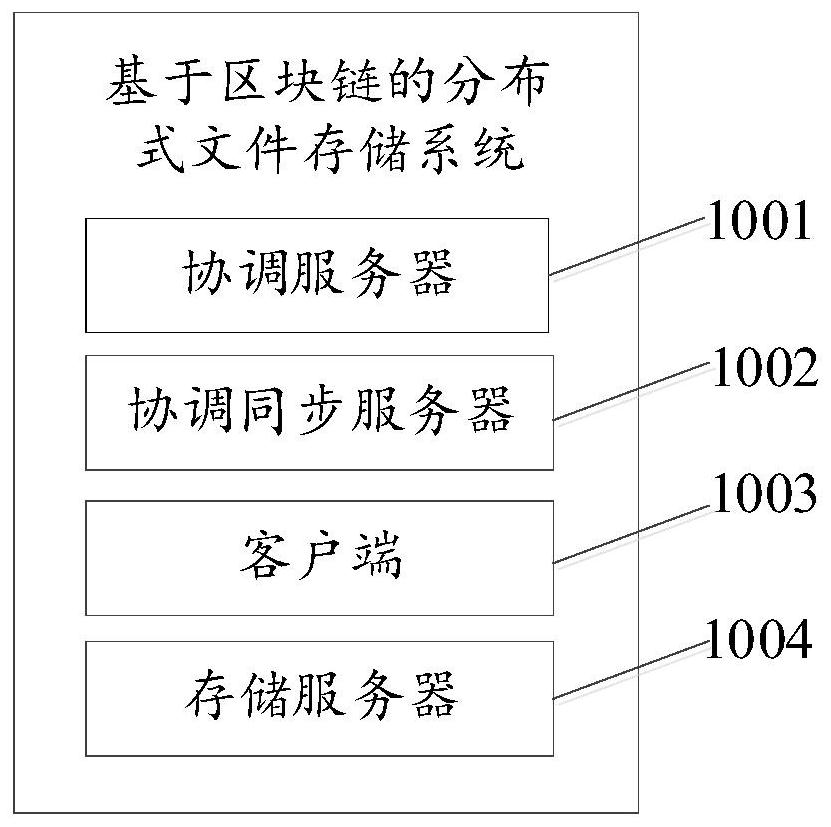
Distributed file storage method and system based on block chain
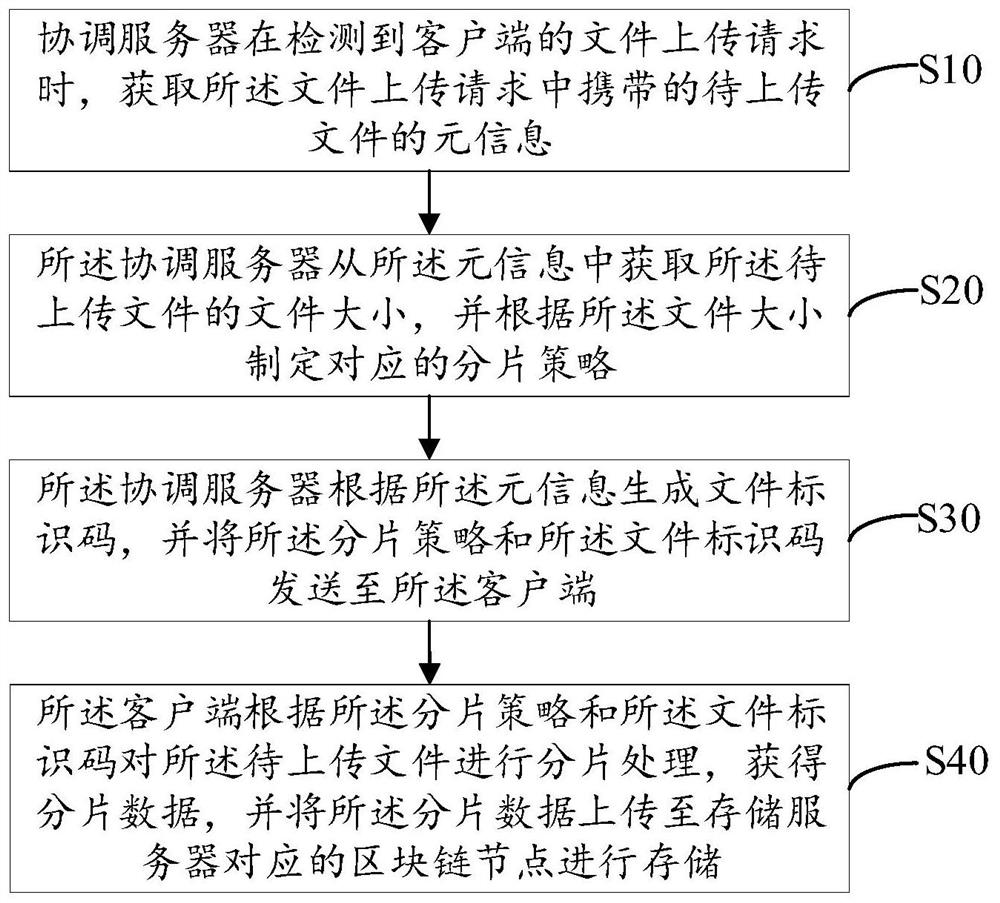
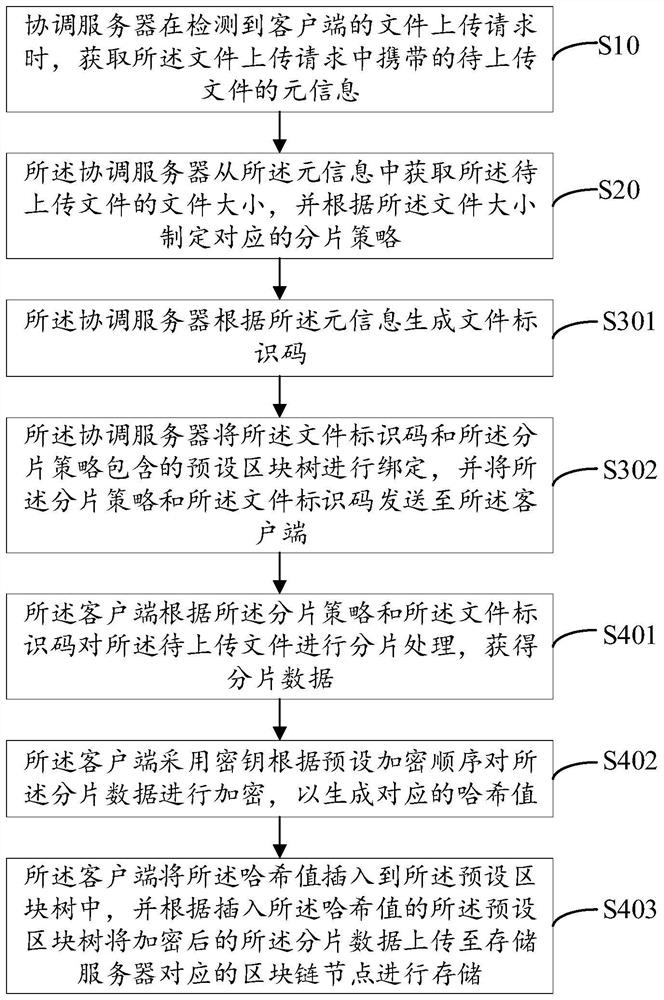
PendingCN112256663AImprove storage efficiencyImprove storage securityDigital data protectionFile access structuresThird partyStorage security
The invention relates to the technical field of block chains, and discloses a distributed file storage method and system based on a block chain, and the method comprises the steps: meta-information ofa to-be-uploaded file carried in a file uploading request is acquired when a coordination server detects the file uploading request of a client, a coordination server obtains the file size of the to-be-uploaded file from the meta-information, formulates a corresponding fragmentation strategy according to the file size, generates a file identification code according to the meta-information, and sends the fragmentation strategy and the file identification code to a client; and the client performs fragmentation processing on the to-be-uploaded file according to the fragmentation strategy and thefile identification code to obtain fragmentation data, and uploads the fragmentation data to a block chain node corresponding to the storage server for storage so as to realize distributed storage ofthe file. Potential safety hazards caused by the fact that the to-be-uploaded file is stored in the third-party server in the prior art are avoided, the storage pressure of the storage server is reduced, and the file storage efficiency and the storage safety are improved.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
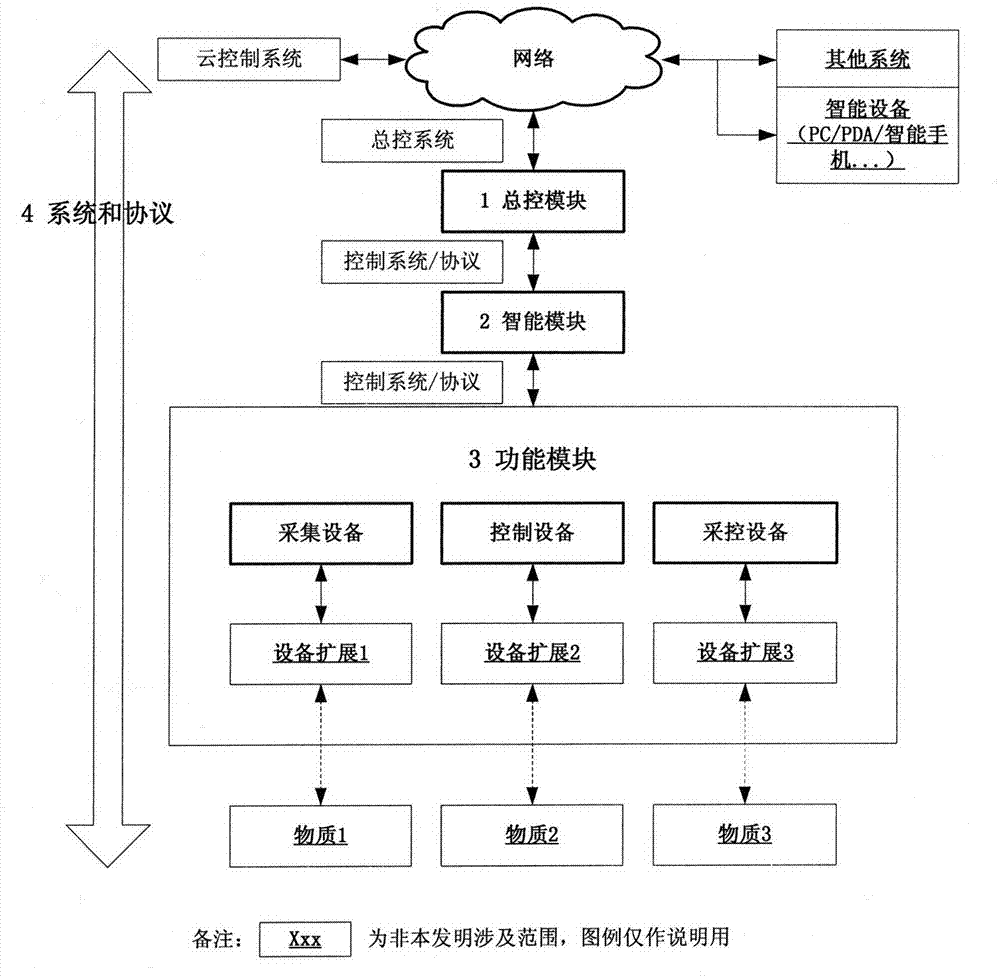
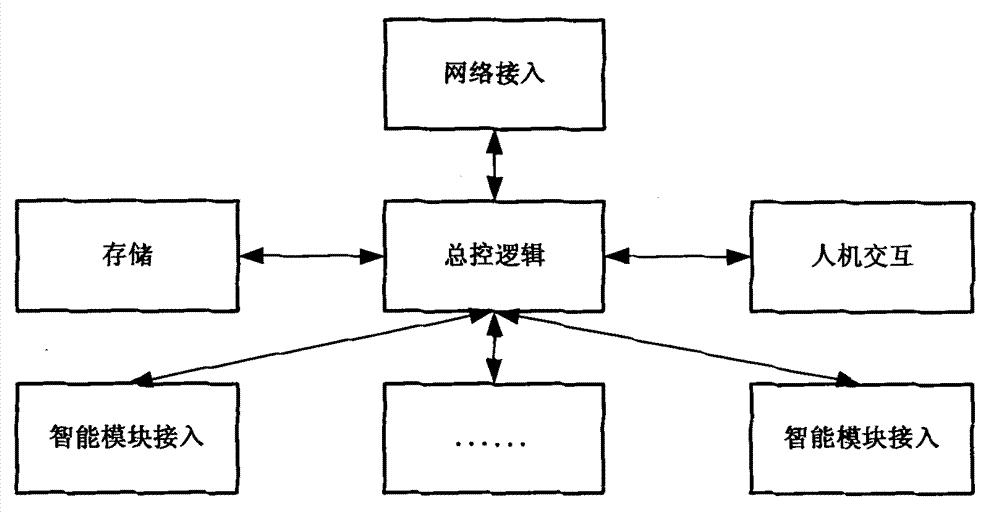
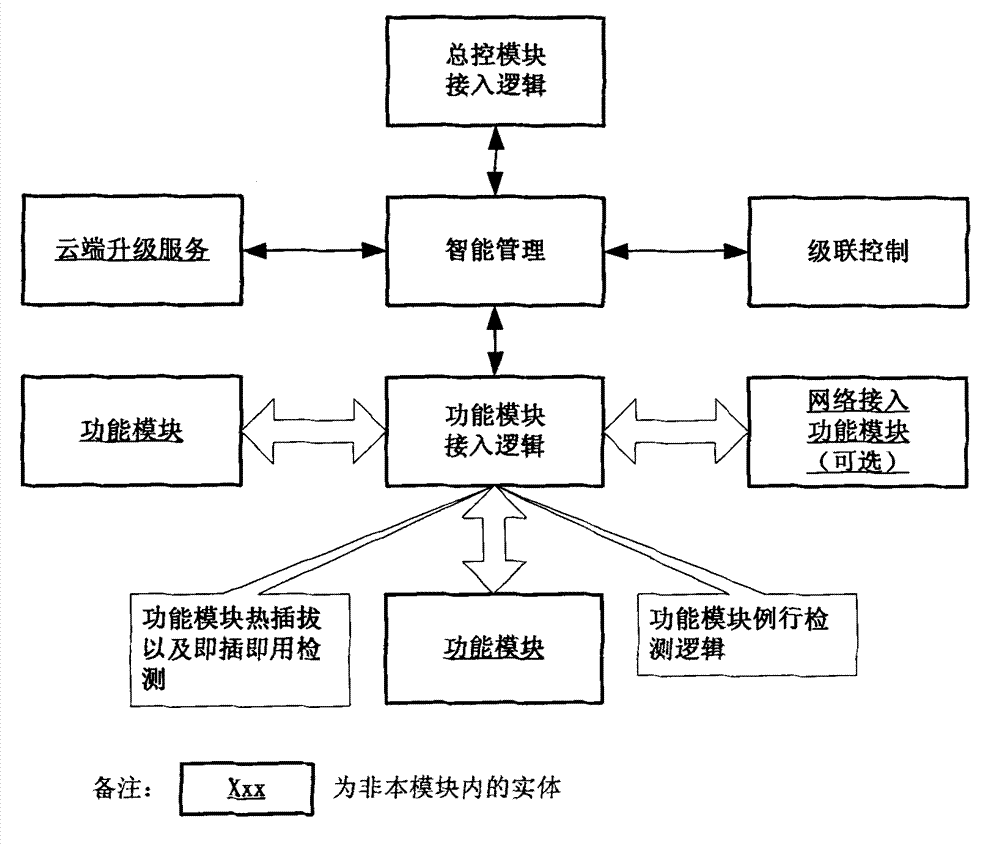
Modularized intelligent terminal implementation method
InactiveCN103945012AImprove real-time responseImprove storage securityData switching networksDistributed intelligenceEngineering
The invention discloses a distributed intelligent Internet of Things with high flexibility. The distributed intelligent Internet of Things comprises a public and private cloud service, a general control module, an intelligent module, an intelligent module expansion module, a function module and a function module peripheral, which are networked and connected in a flexible manner, so that owning and maintenance costs are reduced, the rapid deployment of the service is achieved, more application requirements are met by convenient combination. According to the distributed intelligent Internet of Things with high flexibility, through the definition of an standard interface, the flexible networking is achieved, the cost for primarily owning by a user is reduced, and the cost for subsequently required expansion is also reduced; through the convenient cloud service, each module is convenient to upgrade and maintain, and the maintenance cost is lowered; through the convenient, safe and economical cloud storage, the safe historic recording of key data can be achieved; through the developed network, convenient use is achieved at any time and any place; through the expansion of the function module, the deployment with the requirement of low cost is achieved; through the expansion of the intelligent module, the cost ratio of the intelligent module is reduced.
Owner:范伟飞
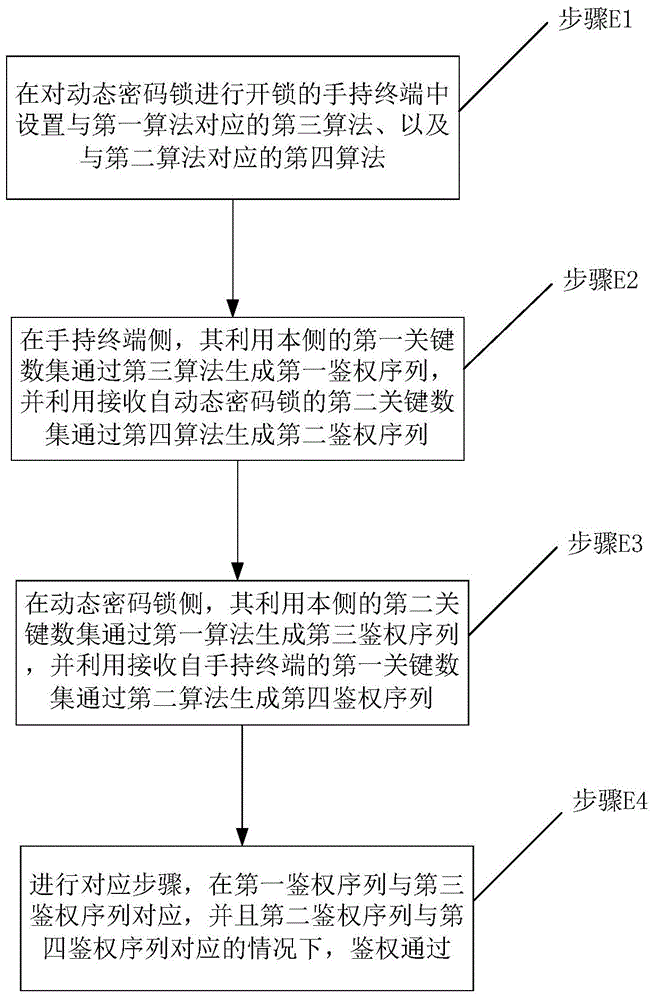
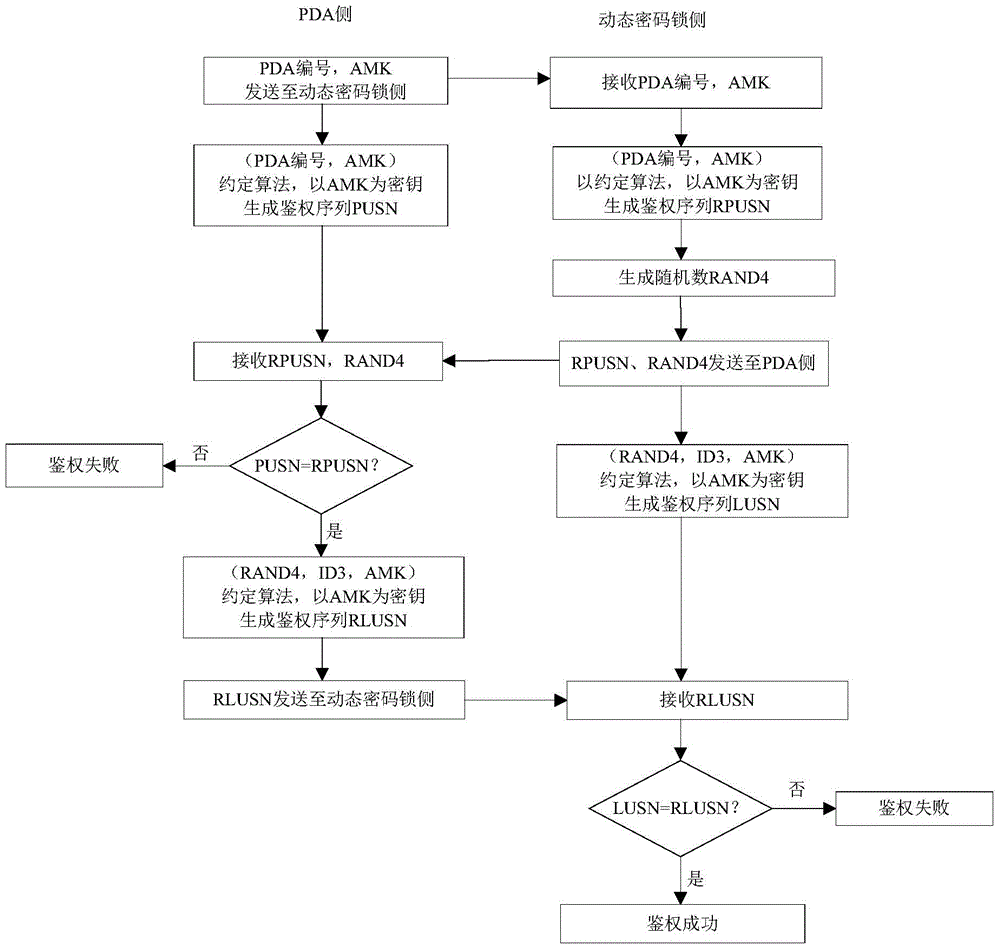
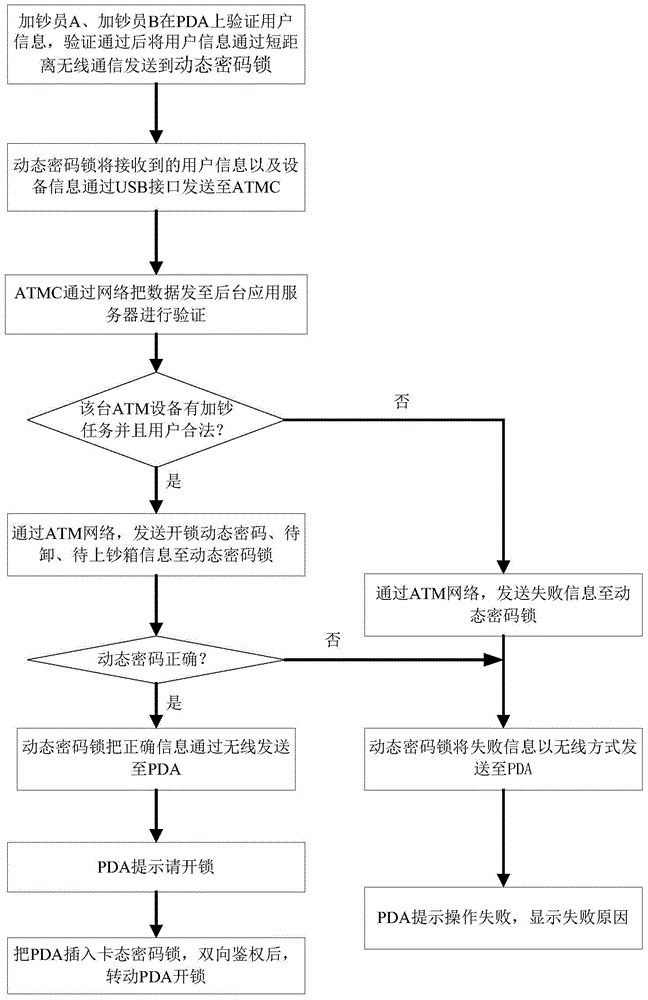
Authentication method, unlocking method and unlocking system for dynamic password lock
ActiveCN105635089AImprove securityImprove security levelUser identity/authority verificationPasswordHand held
The invention provides an authentication method, an unlocking method and an unlocking system for a dynamic password lock. The authentication method comprises the following steps: setting a third algorithm corresponding to a first algorithm and a fourth algorithm according to a second algorithm in a hand-held terminal for unlocking the dynamic password lock; generating a first authentication sequence on the hand-held terminal side by use of a first key number set through the third algorithm, and generating a second authentication sequence through a second key number set received from the dynamic password lock through the fourth algorithm; generating a fourth authentication sequence on the dynamic password lock side through the second key number set of the current side through the second algorithm, and generating a third authentication sequence through a first key number set received from the dynamic password lock through the first algorithm; and carrying out corresponding steps, and determining that the authentication is passed in the case that the first and the third authentication sequences are correspondent and the second and the fourth authentication sequences are correspondent. By adopting the authentication method provided by the invention, the security performance of the dynamic password lock can be improved.
Owner:SGSG SCI & TECH CO LTD
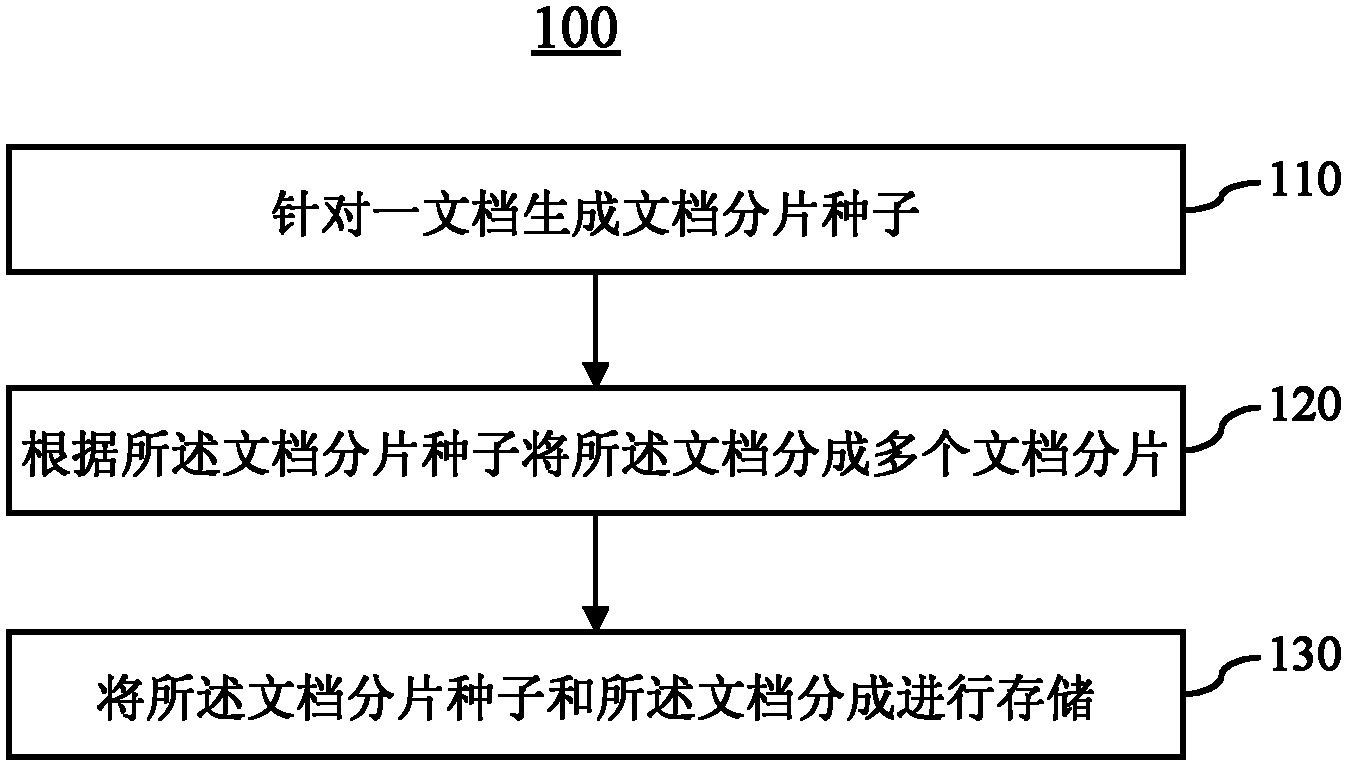
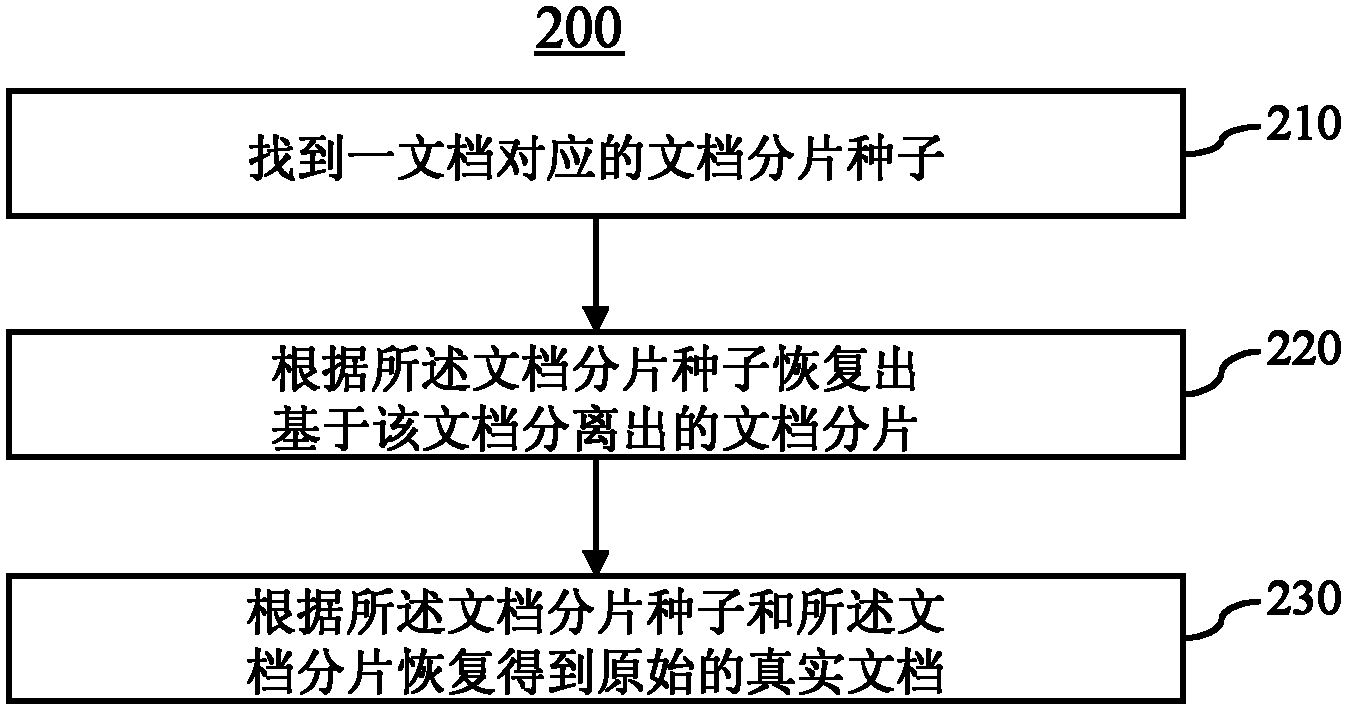
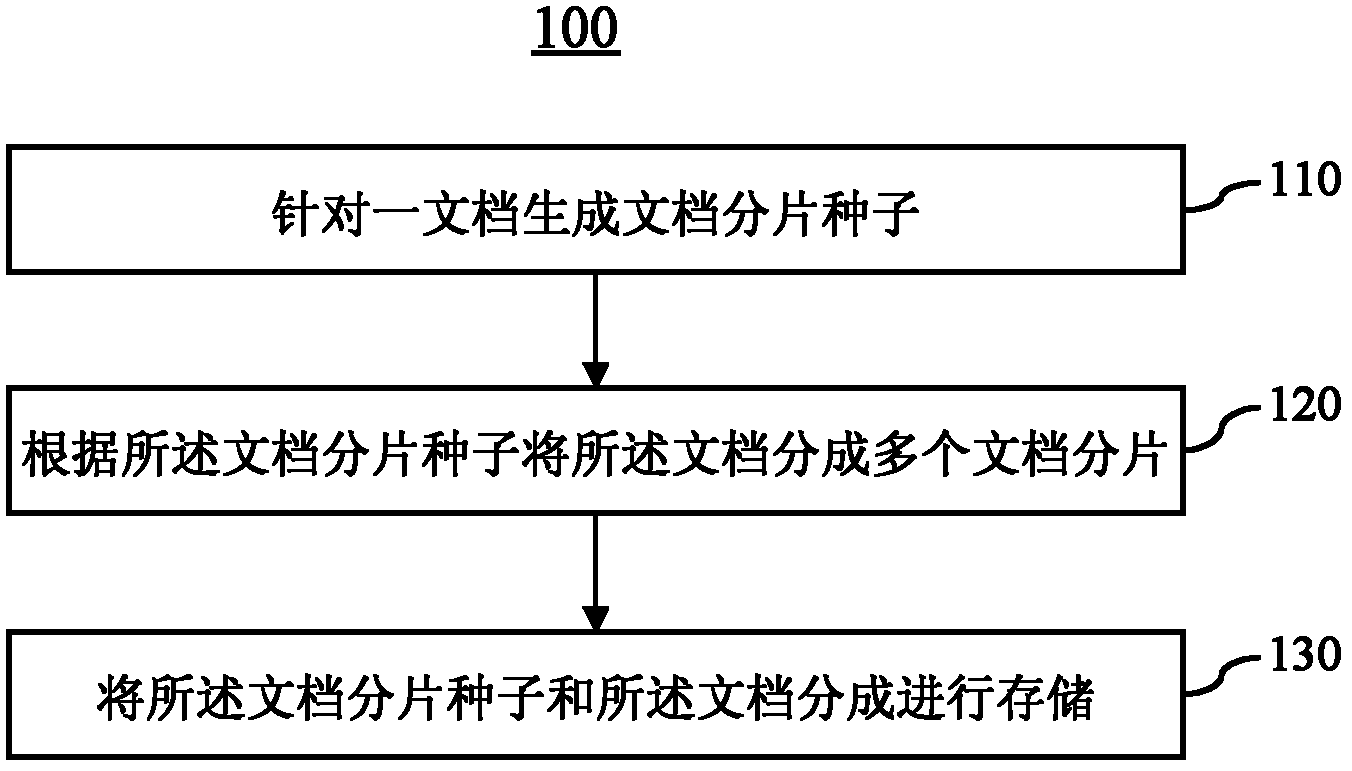
Document storage method and document recovery method
InactiveCN102194014AImprove storage securityEasy to implementDigital data protectionSpecial data processing applicationsDocument preparationRecovery method
The invention provides a document storage method which comprises the following steps: generating document fragmentation seeds against a document; dividing the document into a plurality of document fragments according to the document fragmentation seeds; and storing the document fragmentation seeds and the document fragments. By adopting the method, the document can be fragmented or re-combined to the result document which has the complete fragments and contents incapable of being read directly, and the storage safety is higher.
Owner:YOZOSOFT
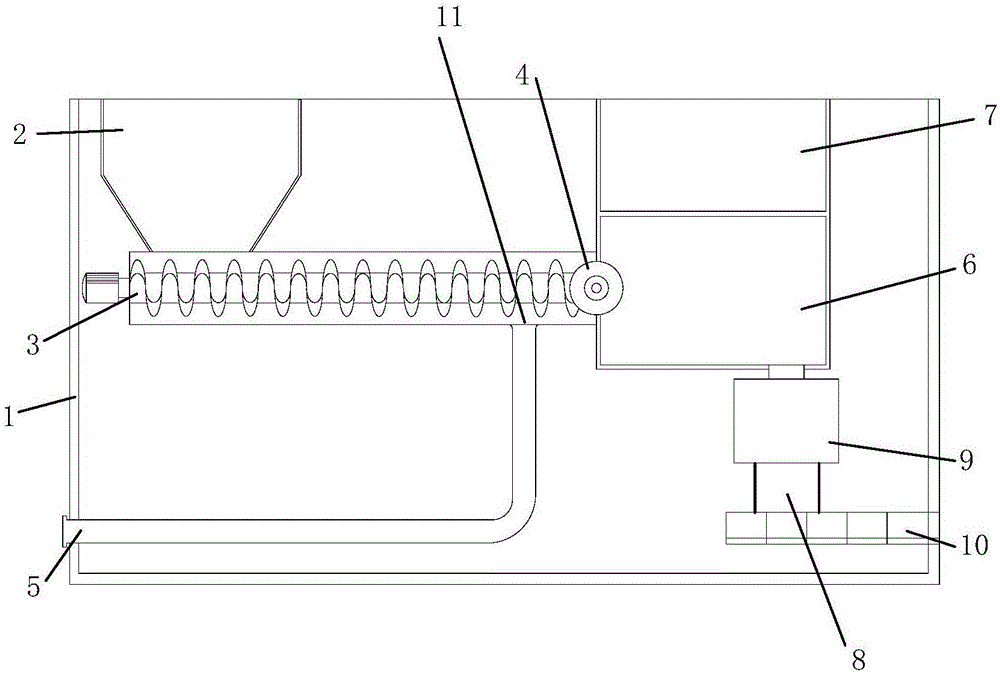
Kitchen waste treatment device and kitchen waste treatment method
InactiveCN105689368AAchieve the purpose of breakingTimely processingSolid waste disposalSewageWaste treatment
The invention discloses a kitchen waste treatment device and a kitchen waste treatment method. The kitchen waste treatment device comprises a feeding hopper, a screw conveyor, a stirring and mixing chamber, an EM storage box and a filling and sealing machine. The feeding hopper, the screw conveyor, the stirring and mixing chamber and the filling and sealing machine are sequentially connected. A valve is arranged on a discharging opening of the screw conveyor. A drain outlet is formed in the pipe wall, below the feeding opening side of the valve, of the screw conveyor. The drain outlet is connected with a sewage draining pipeline. A screen is mounted on the drain outlet. The EM storage box communicating with the stirring and mixing chamber is arranged on the stirring and mixing chamber. By the adoption of the kitchen waste treatment method, kitchen waste can be treated in time, the storage life of the kitchen waste is greatly prolonged, and the storage safety of the kitchen waste is greatly improved; and the treated kitchen waste can be stored and transported conveniently, meanwhile anaerobic fermentation can continue in the storage and transportation processes, and the subsequent treatment time of the kitchen waste is shortened greatly.
Owner:GUANGDONG INST OF APPLIED BIOLOGICAL RESOURCES
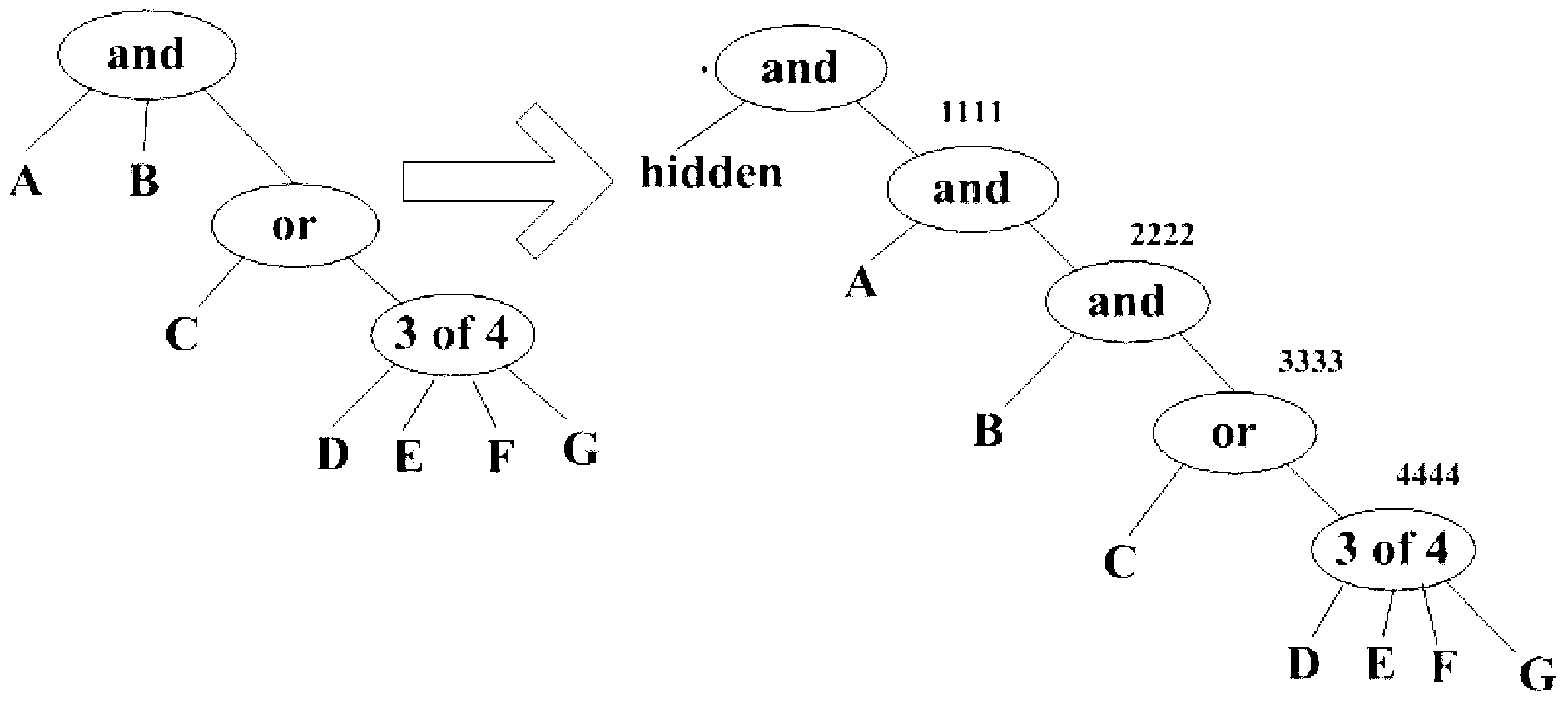
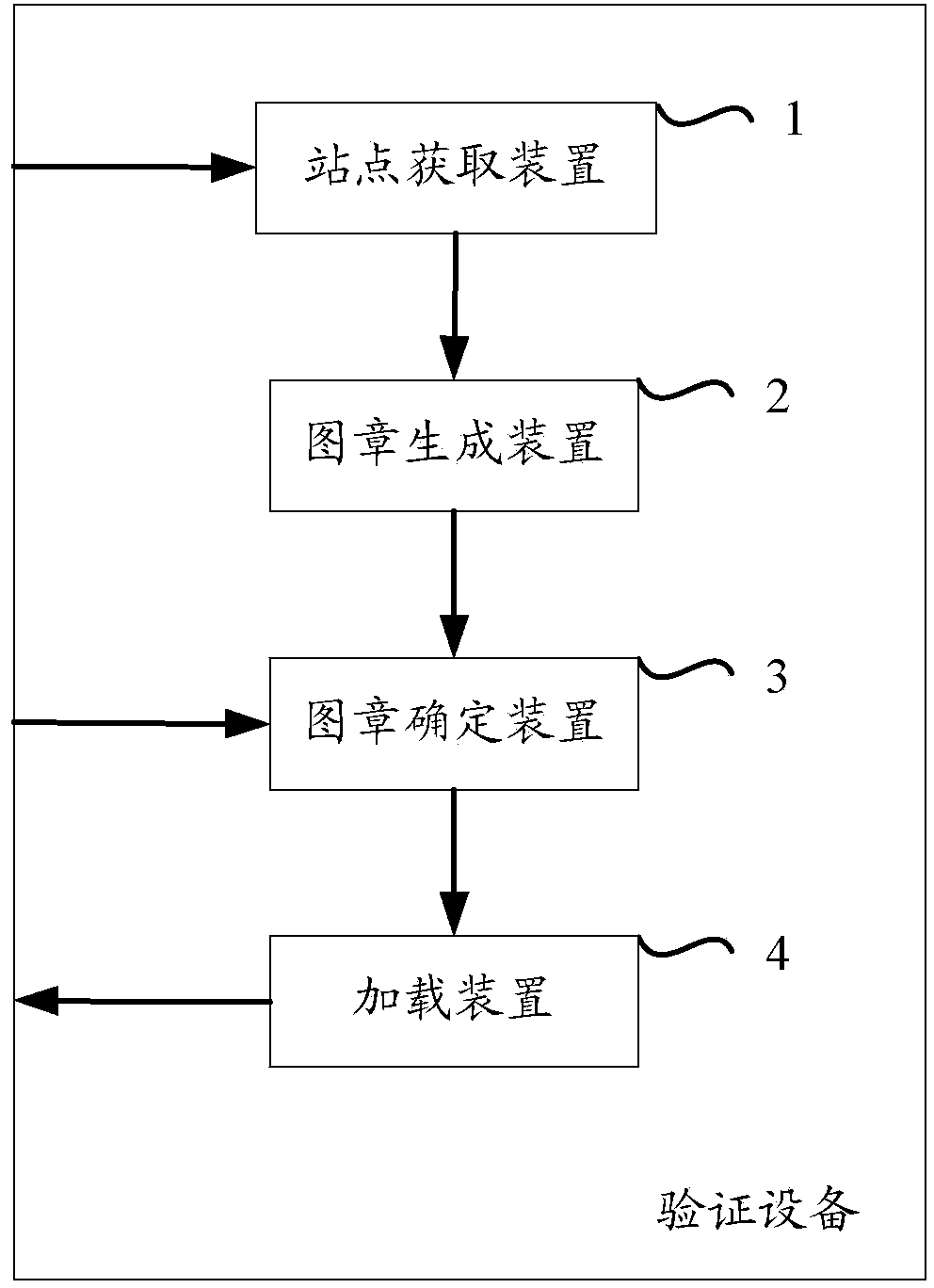
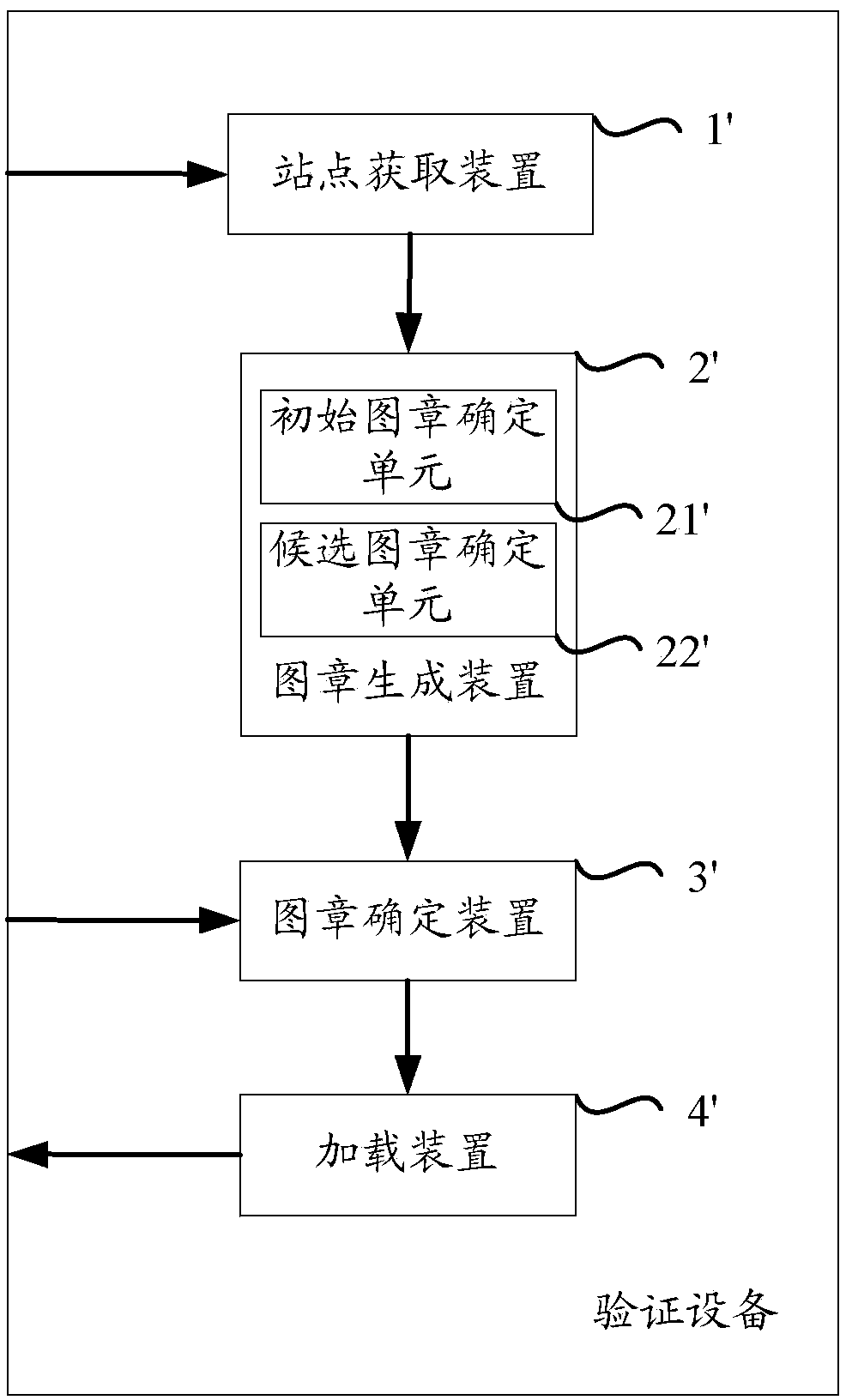
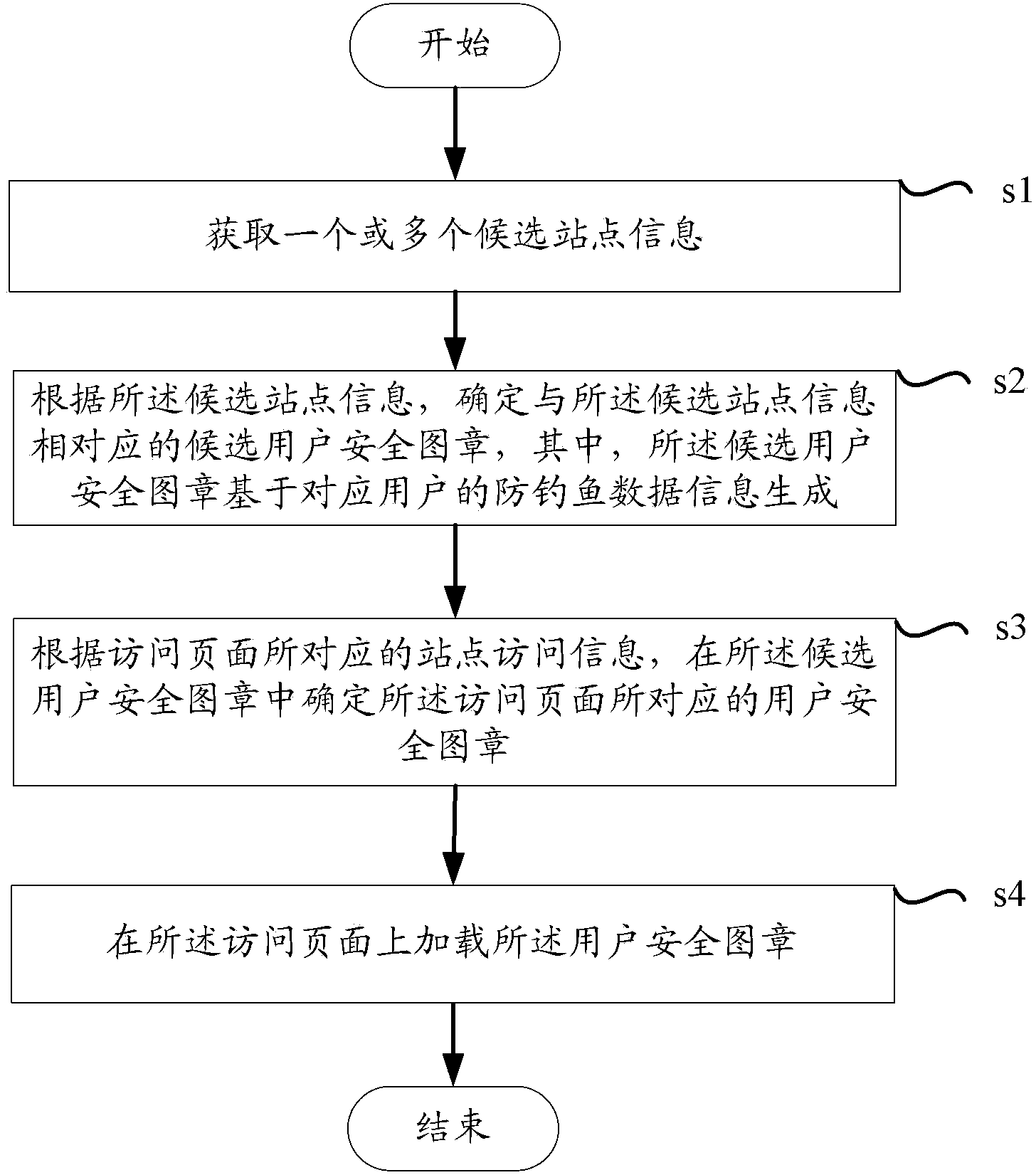
Method for loading user security seal in visited page and device thereof
The aim of the invention is to provide a method for loading a user security seal in a visited page and a device thereof. Through one or more candidate site information and anti phishing data information corresponding to a user, a candidate user security seal corresponding to the candidate site information is generated, according to site visit information corresponding to a visited page, a user security seal corresponding to the visited page is determined in the candidate user security seal, and then the user security seal is loaded to the visited page. Compared with the prior art, personalized user security seals are arranged for a plurality of sites, the cost of making and using the user security seal is reduced, the counterfeiting of a real website by a phishing website is avoided, the normal access of the user is ensured, the security of the access is raised, and the user experience of the user is improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Log ciphertext retrieval method based on alarm association
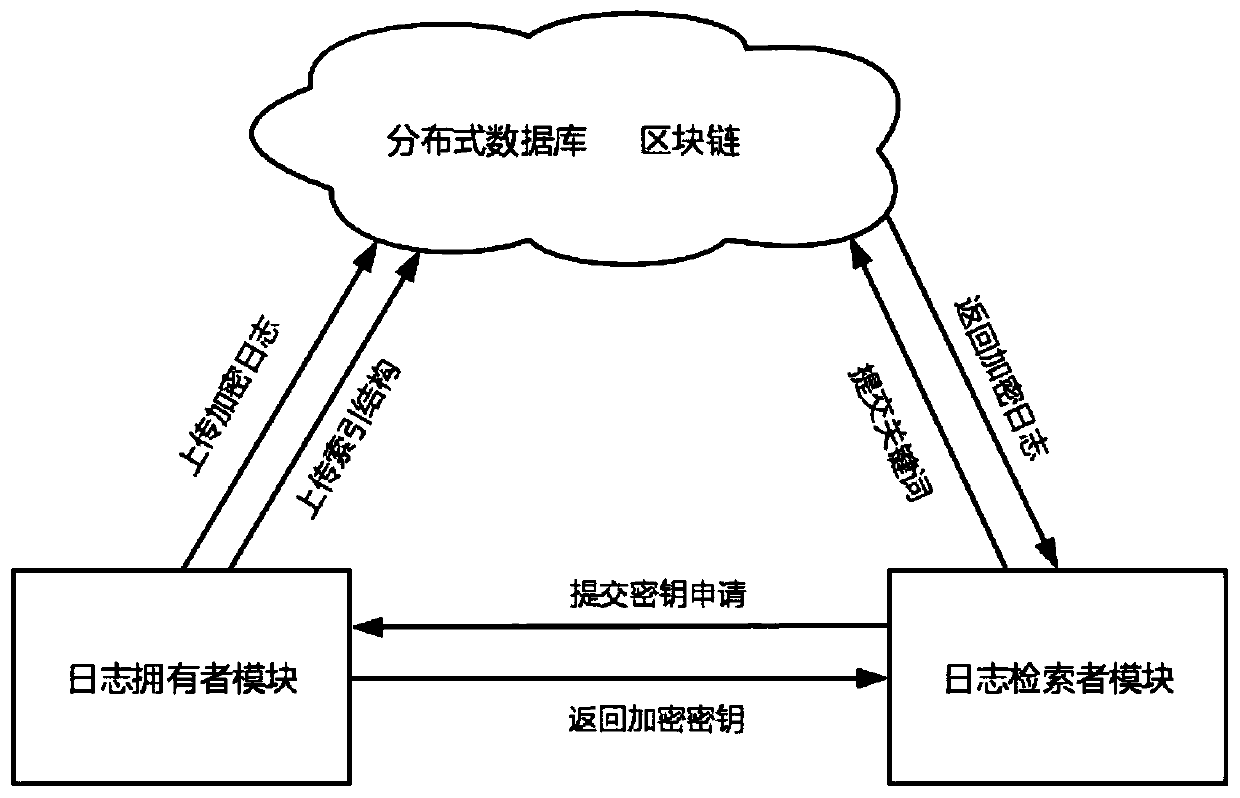
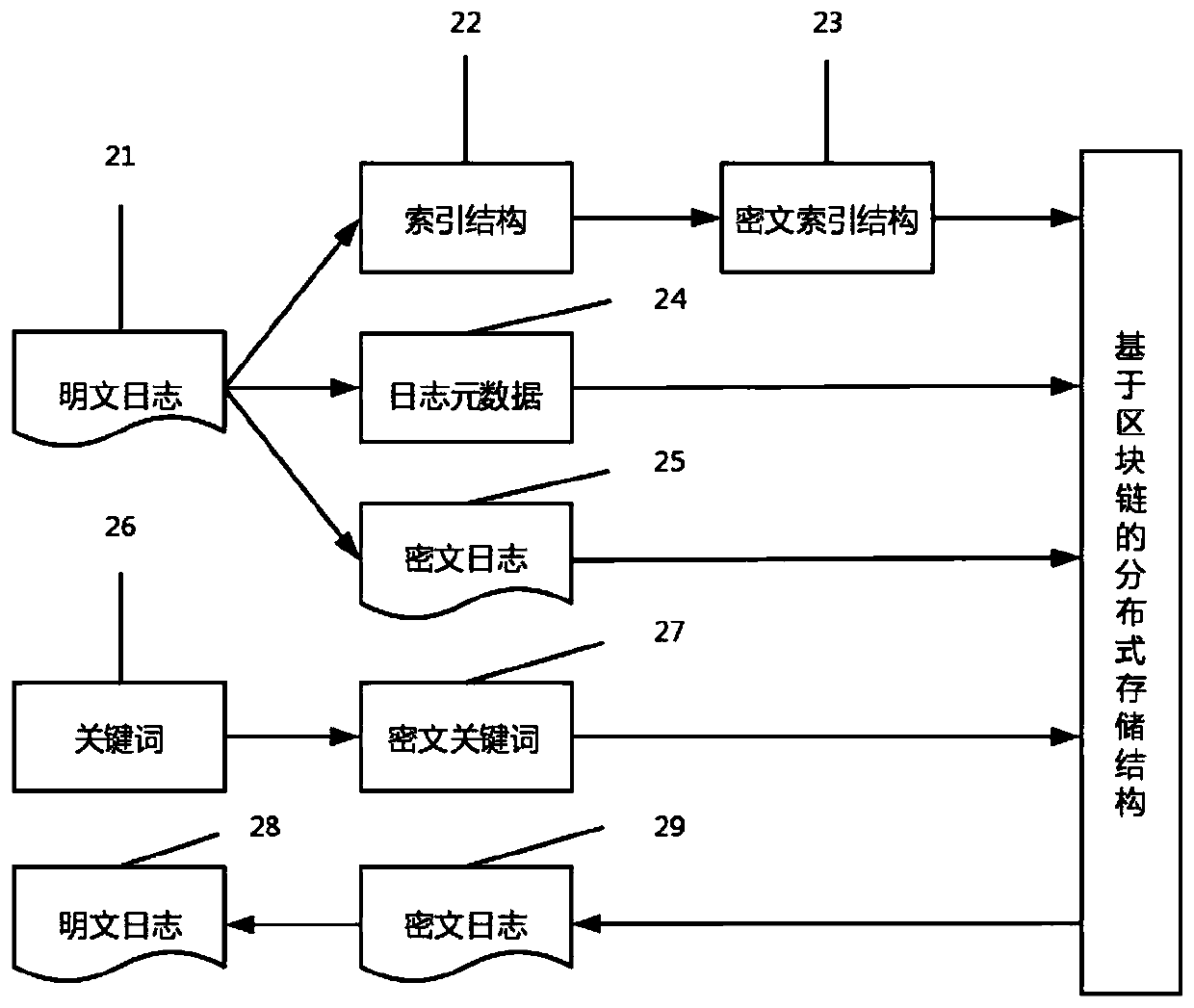
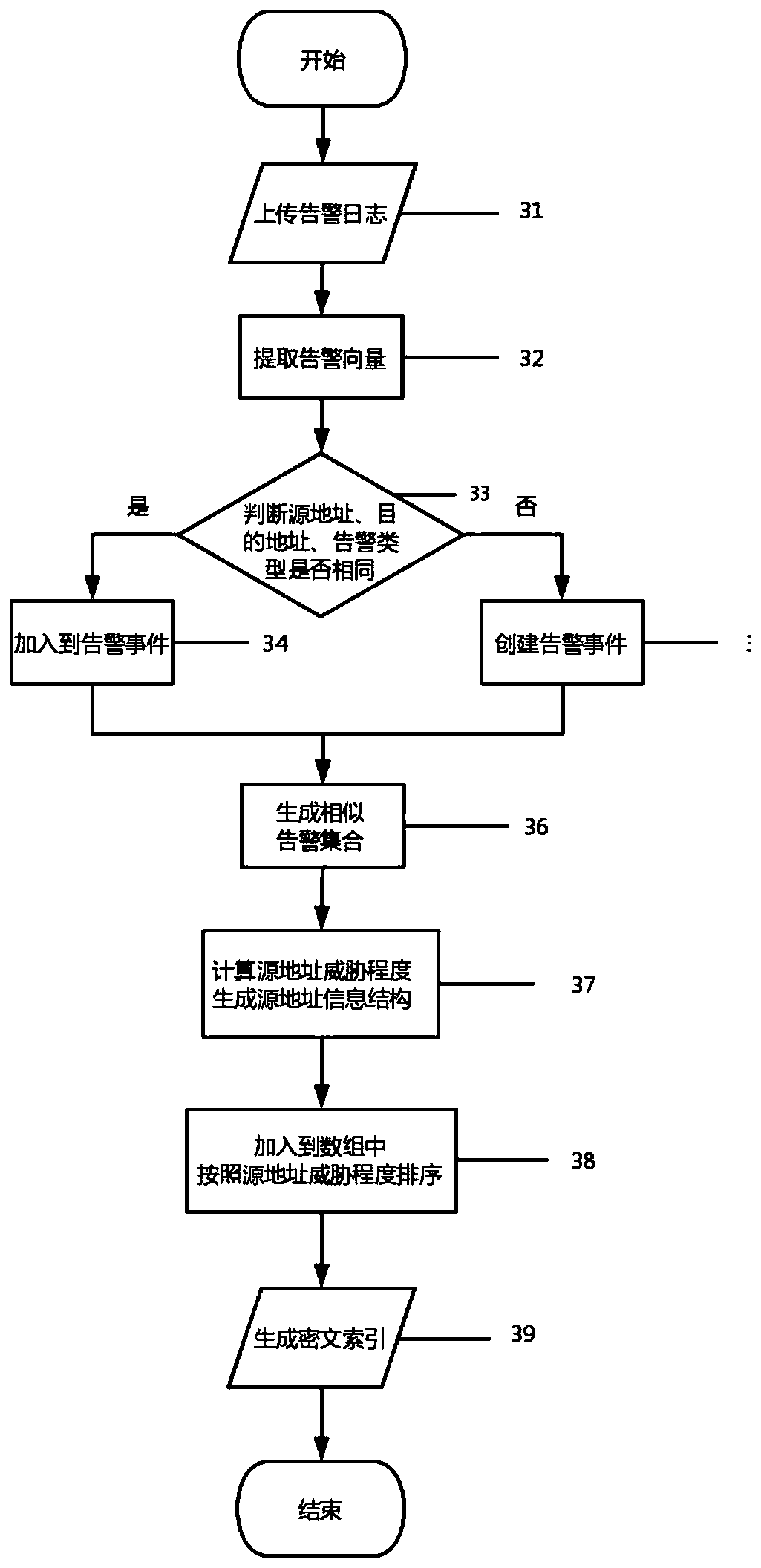
PendingCN110362536AImprove storage securityImprove analysis efficiencyDigital data protectionFile access structuresStorage securityCiphertext
The invention discloses a log ciphertext retrieval method based on alarm association. A distributed storage structure based on a block chain is constructed, so that the security of the alarm log is ensured; a function for calculating the threat degree of the source address is defined; clustering and index construction are carried out on the alarm logs according to the calculated threat degree; theindex construction method based on alarm association is designed, the alarm logs belonging to the same attack process are extracted by performing correlation analysis on the alarm logs, the securityindex is constructed, effective retrieval is performed, the alarm logs with attack intention are acquired, and the analysis efficiency of the alarm logs can be improved. The designed method comprisesa log owner module, a distributed log storage module and a log searcher module, and has the advantages of being high in storage safety, high in log search efficiency and the like.
Owner:BEIJING UNIV OF TECH
Intensive solar parking pavilion for electrocars
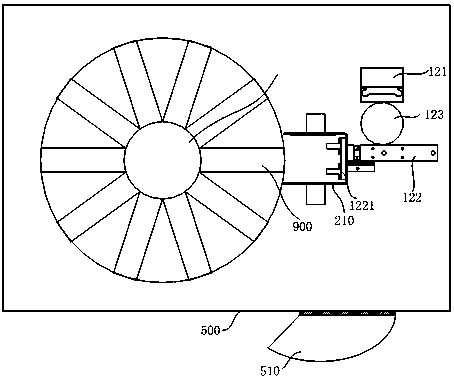
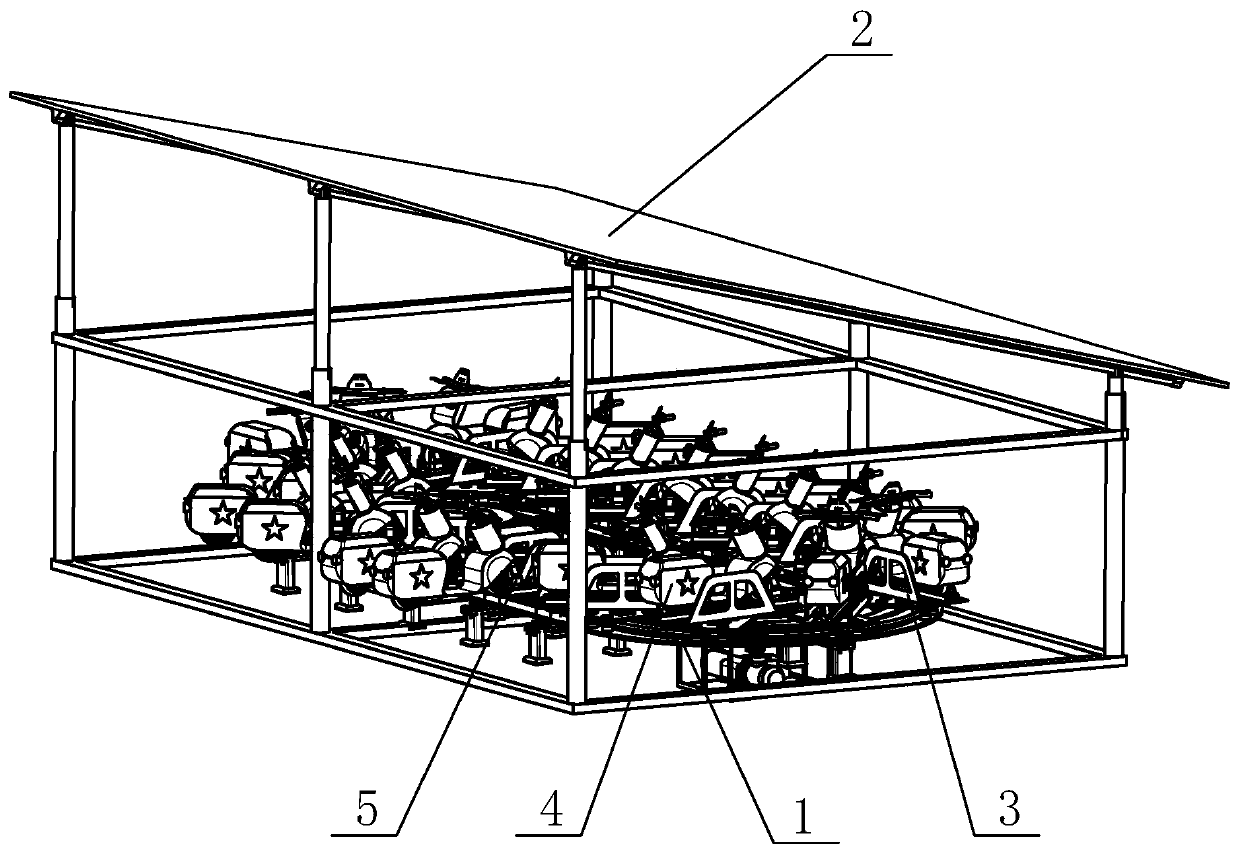
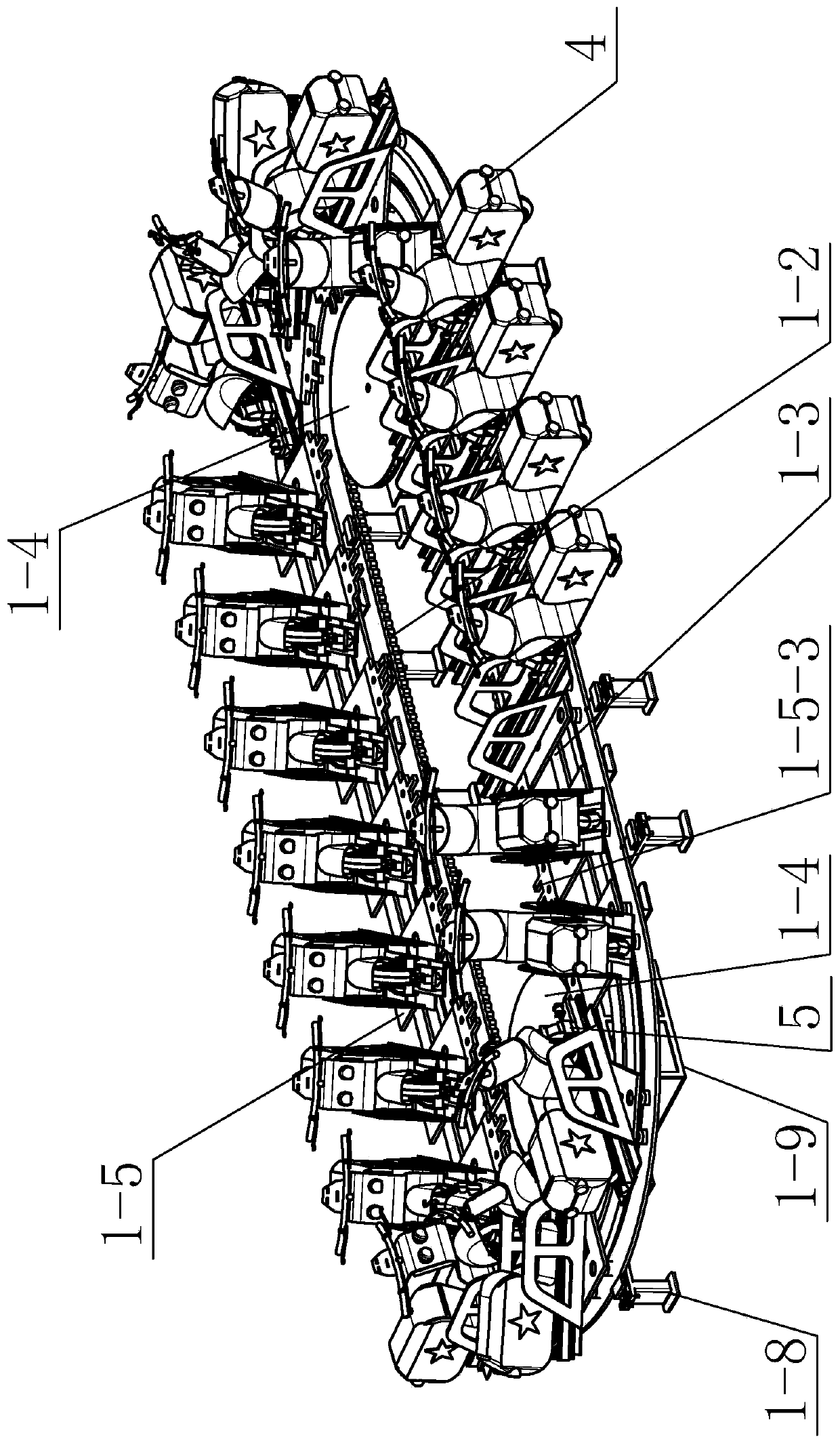
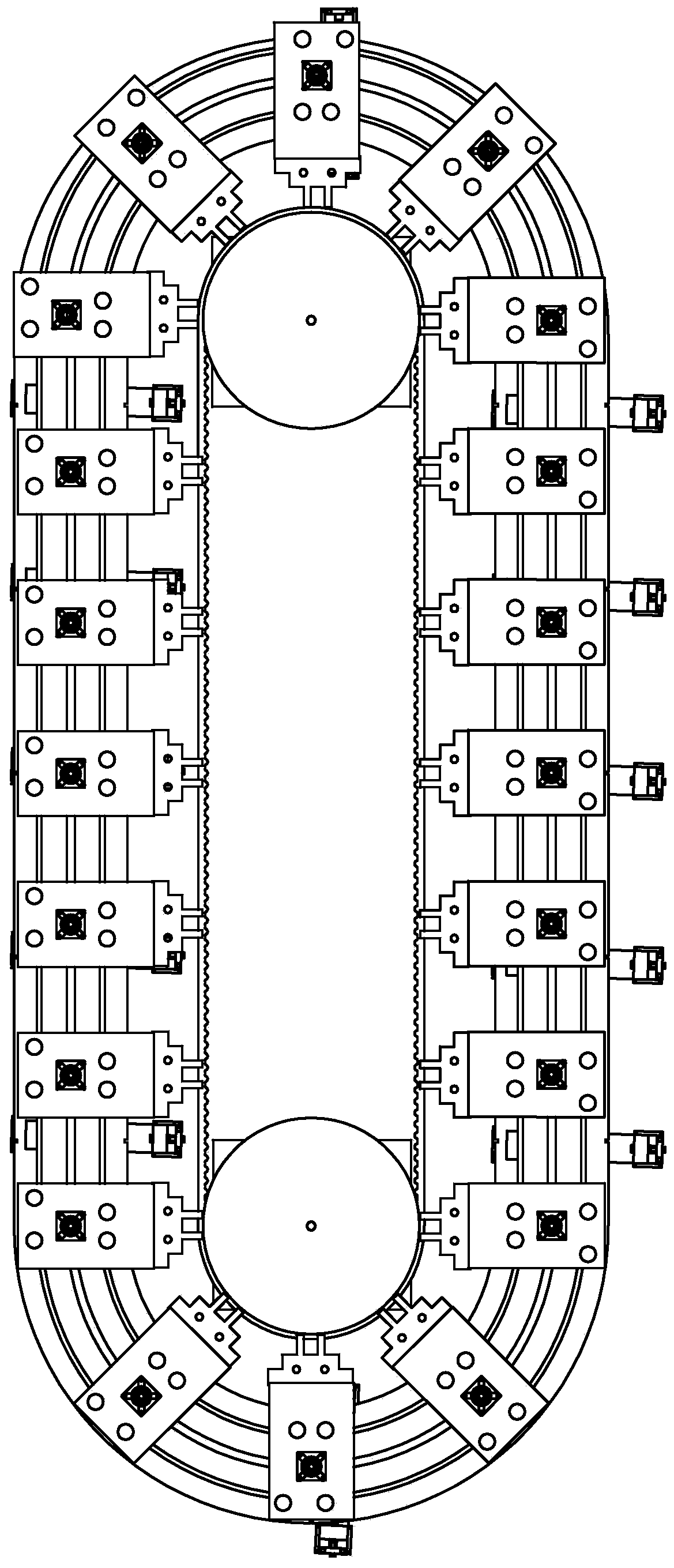
PendingCN110259211ARealize rational utilizationRealize security and anti-theftPhotovoltaic supportsRoof covering using slabs/sheetsPavilionAutomotive engineering
The invention provides an intensive solar parking pavilion for electrocars. The electrocars need to occupy large space when the electrocars are used in large quantities and stored centrally, the process of storing and taking the electocars take up a lot of space, orderly storing-taking and centralized charging processes are difficult to achieve. The intensive solar parking pavilion comprises a rotary chassis, a solar roof and a plurality of storing-taking car single bodies, the solar roof is arranged on upper part of the rotary chassis the storing-taking car single bodies are arranged on the rotary chassis in the circumferential direction of the rotary chassis in a distribution mode, the bottom of each storing-taking car single body is hinged to the rotary chassis, the power supply end of the solar roof is connected with each storing-taking car single body, each storing-taking car single body is provided with a clamping mechanism, each clamping mechanism is correspondingly provided with one electrocar. The intensive solar parking pavilion is used outdoors.
Owner:GUILIN UNIV OF ELECTRONIC TECH
Sample storage library and sample storage method
PendingCN111332768ARealize fully automatic storageNo human intervention requiredConveyor partsProcess engineeringManipulator
The invention discloses a sample storage library and a sample storage method. The sample storage library comprises a sorting library and a storage library, wherein the sorting library is internally provided with a temporary storage rack, a scanning device, a test tube capping device, a test tube recycling device, a second manipulator and a third manipulator; and the storage library is internally provided with a storage rack and a fourth manipulator, and the storage library communicates with the sorting library. When test tubes are put in storage, the second manipulator conveys the test tubes to be put in storage to the scanning device for scanning, the test tube capping device caps the test tubes which are correctly scanned, the third manipulator conveys the capped test tubes to the temporary storage rack, and after the test tubes are placed on the temporary storage rack for a period of time, the test tubes are conveyed to the storage rack under the action of the third manipulator andthe fourth manipulator; and after the test tubes are placed on the storage rack for a period of time, the test tubes to be recycled are conveyed to the test tube recycling device under the action of the third manipulator and the fourth manipulator. Manual intervention is not needed in the warehousing, ex-warehousing, capping and recycling processes of the samples, full-automatic storage of the samples is achieved, and the test tube storage efficiency is improved.
Owner:QINGDAO HAIER BIOMEDICAL TECH CO LTD +1
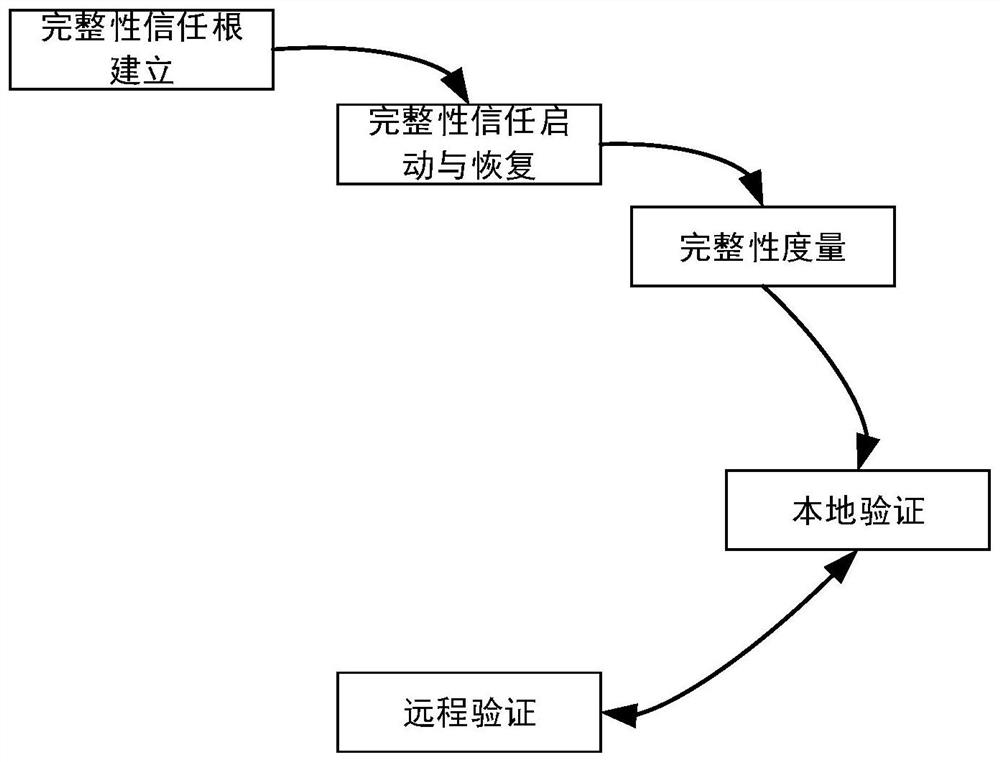
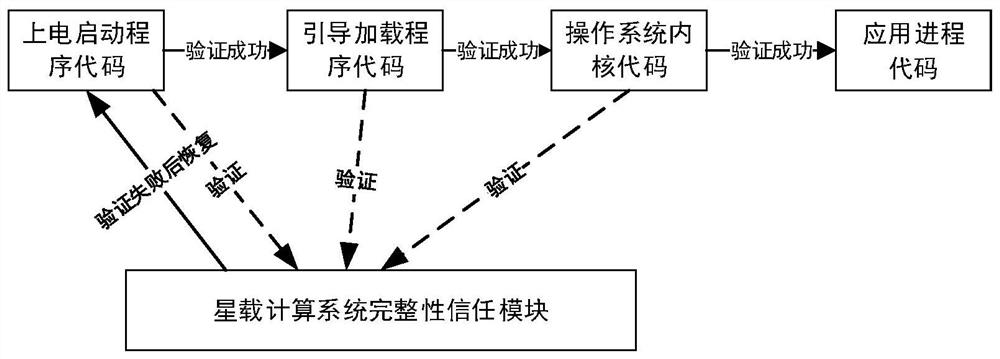
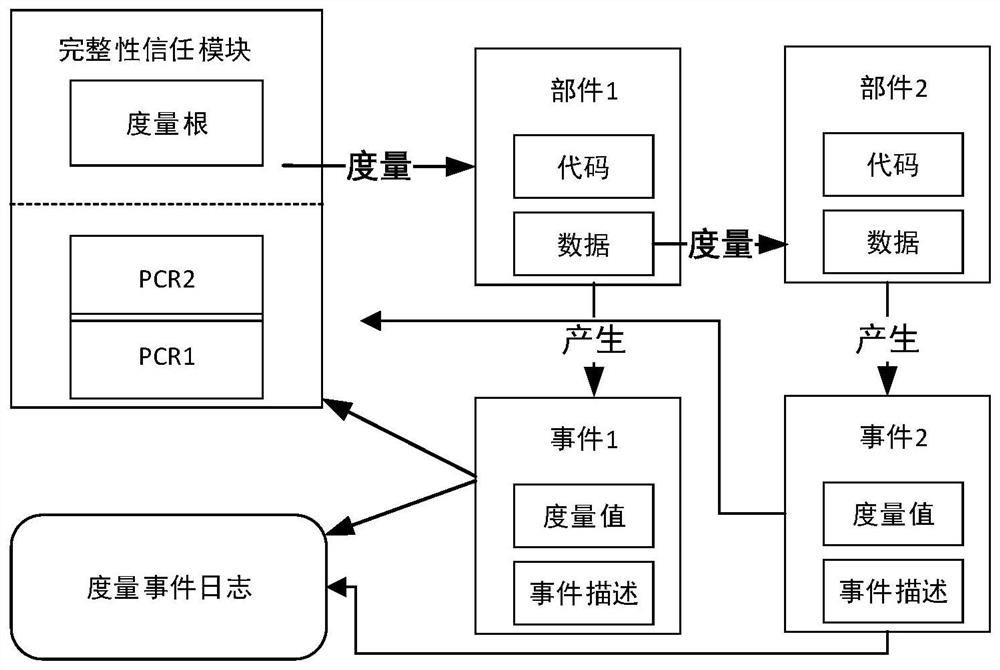
Information integrity measurement verification method and system for satellite-borne computing system
PendingCN111783097AImprove storage securitySave storage spaceDigital data protectionDigital data authenticationAttackData transport
The invention discloses an information integrity measurement verification method and system for a satellite-borne computing system. The method comprises the following steps: S1, establishing a trust chain in a whole starting sequence; taking the integrity trust module as a starting point, carrying out integrity measurement and local verification on the next object in the starting sequence on the premise of trusting the current object, considering that the next object is credible after the local verification is passed, transferring the control right to the next object, and sequentially pushingbackwards until the object in the whole starting sequence completes the local verification; S2, in the running process of the system, conducting integrity measurement and local verification on the data in the memory; and when the ground system sends a task to the satellite-borne computing system, carrying out data transmission after remote verification is passed. Safety measures are taken from thebottom layers of hardware and software of the satellite-borne computing system, measurement and verification of the system and key applications are increased, tampering attacks and the like can be better resisted, and the integrity and authenticity of platform codes and data can be verified.
Owner:中国星网网络应用有限公司
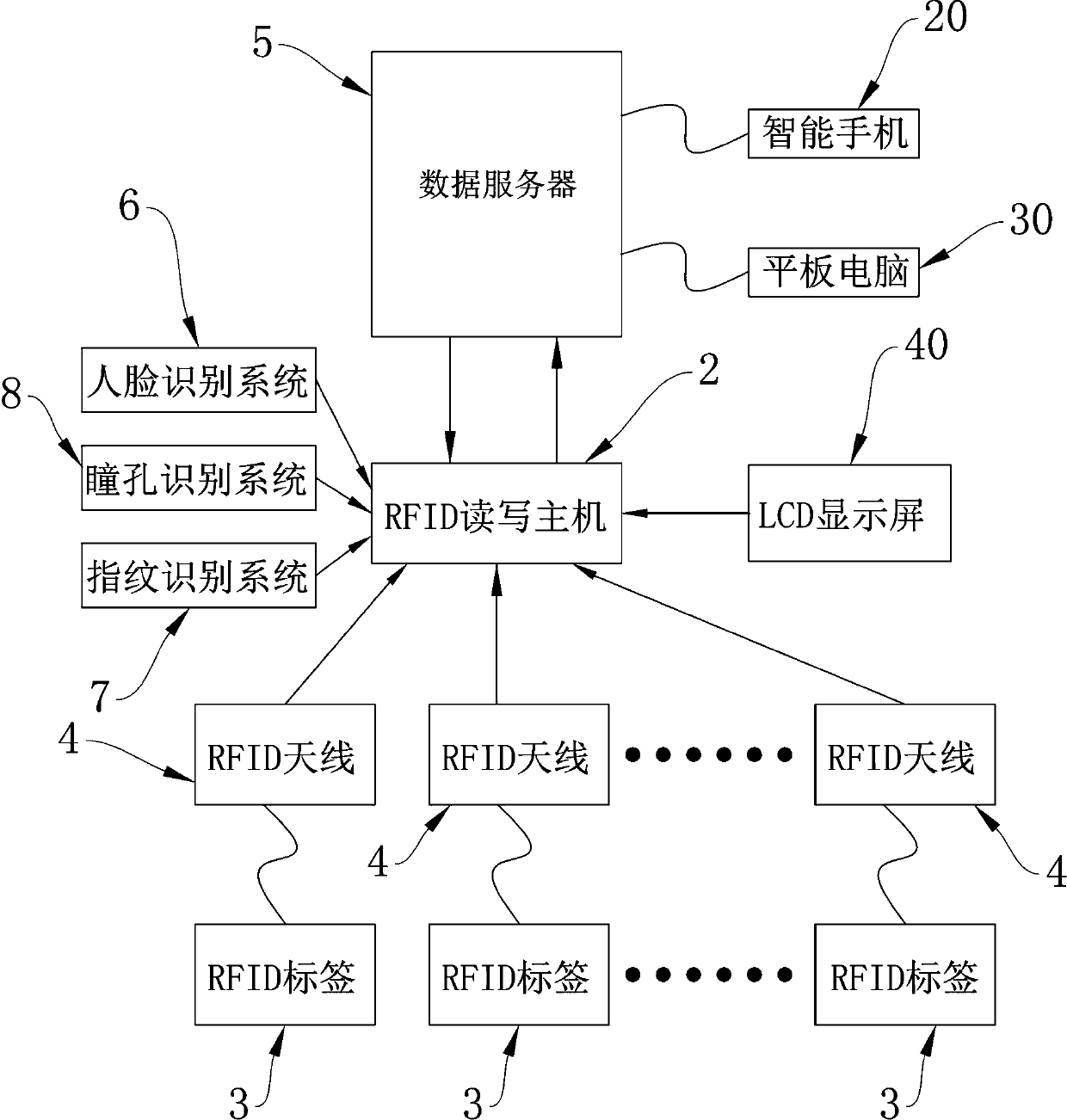
Achievement method of custody, storage and intelligent management of important objects
InactiveCN107481433AImprove securityAddress security flawsCo-operative working arrangementsApparatus for meter-controlled dispensingUltrahigh frequencyOperating system
The invention relates to an achievement method of custody, storage and intelligent management of important objects. According to the achievement method, by means of all-weather seamless real-time connection between ultrahigh-frequency RFID tags, RFID antennas, an RFID read-write mainframe and a data server, the objects in storage cabinets are monitored, the objects in each storage unit in the cabinets are under all-weather real-time monitoring, and monitoring signals of each storage unit are fed back to a computer system in time; meanwhile, when an abnormal situation happens, an alarm signal or prompt signal is sent out in time to inform the management staff; moreover, according to a storage cabinet system, object monitoring is not conducted through judging of whether or not a cabinet door is open, or times of open or close, so that a cabinet body scheme with or without the cabinet doors is implemented. By means of the storage cabinet system, the safety of custody and storage of the objects is greatly improved, and the problem of safety defects of existing storage cabinet systems is effectively solved.
Owner:广东亿锋物联网科技有限公司
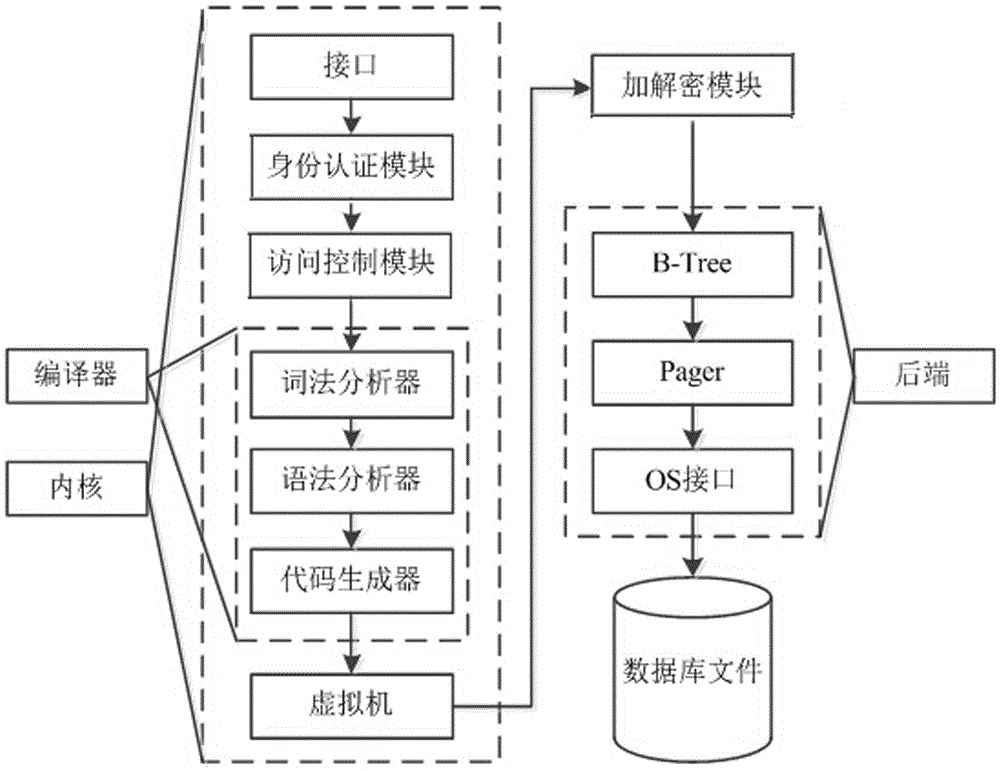
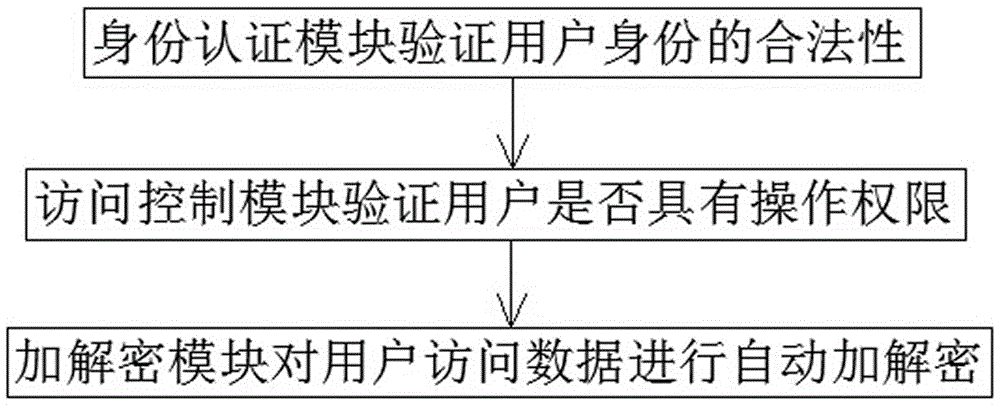
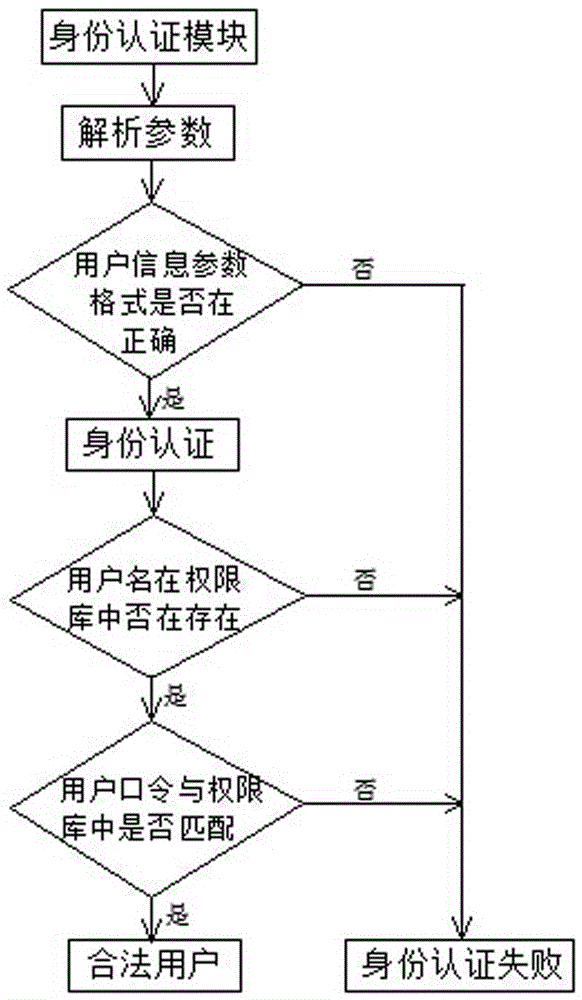
Hybrid SQLite3 safety access method
InactiveCN105528556AImprove storage securityEasy accessDigital data protectionDigital data authenticationPlaintextAccess method
The present invention discloses a hybrid SQLite3 safety access method. The method comprises establishing an identity authentication module and an access control module at an application layer, and establishing an encryption and decryption module at a physical storage stage. At the application layer, validity of user identity is verified through the identity authentication module; when the user identity is valid, authority level and extent of the roles that a user is in are verified through the access control module, so that whether operation required by the user on an SQLite3 database is satisfied is determined; and before the user accesses data in the SQLite3 database, the data are decrypted through the encryption and decryption module from a ciphertext form to a plaintext form. Unauthorized use of valid users and authority embezzlement of invalid users are effectively avoided, and a multi-level, multi-stage and configurable safety access method is provided for access of the embedded database SQLite3.
Owner:THE PLA INFORMATION ENG UNIV
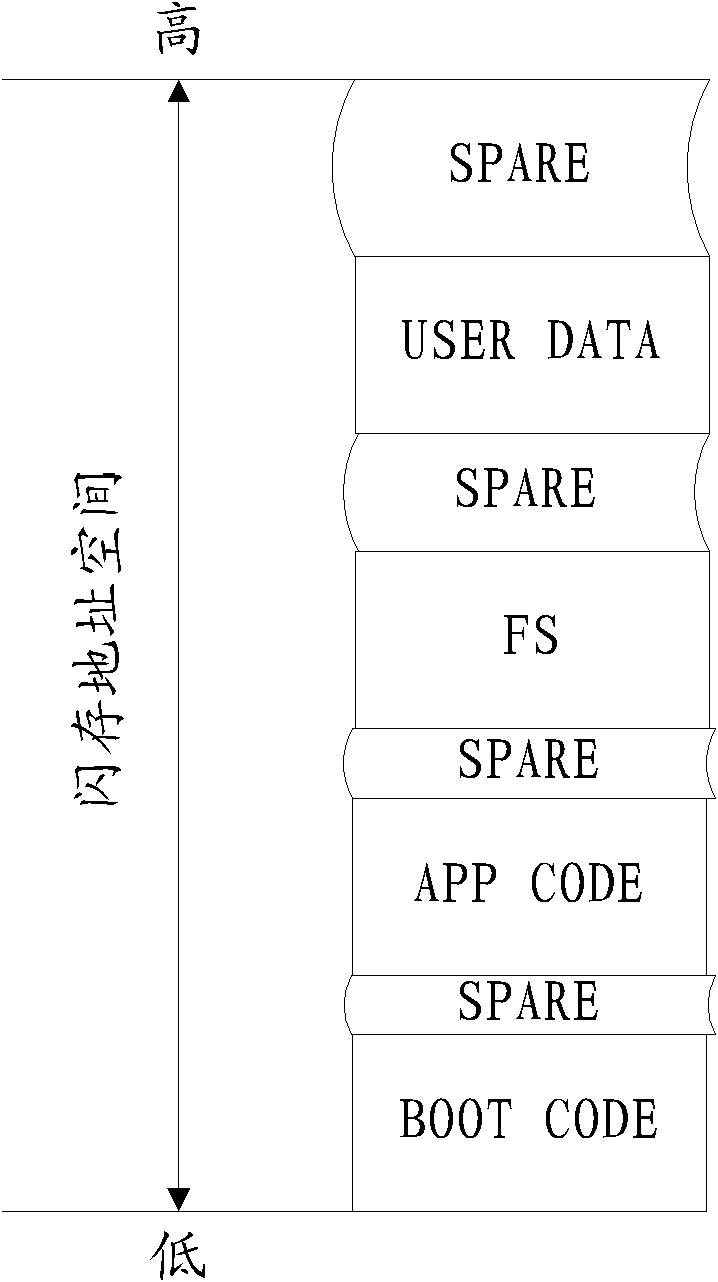
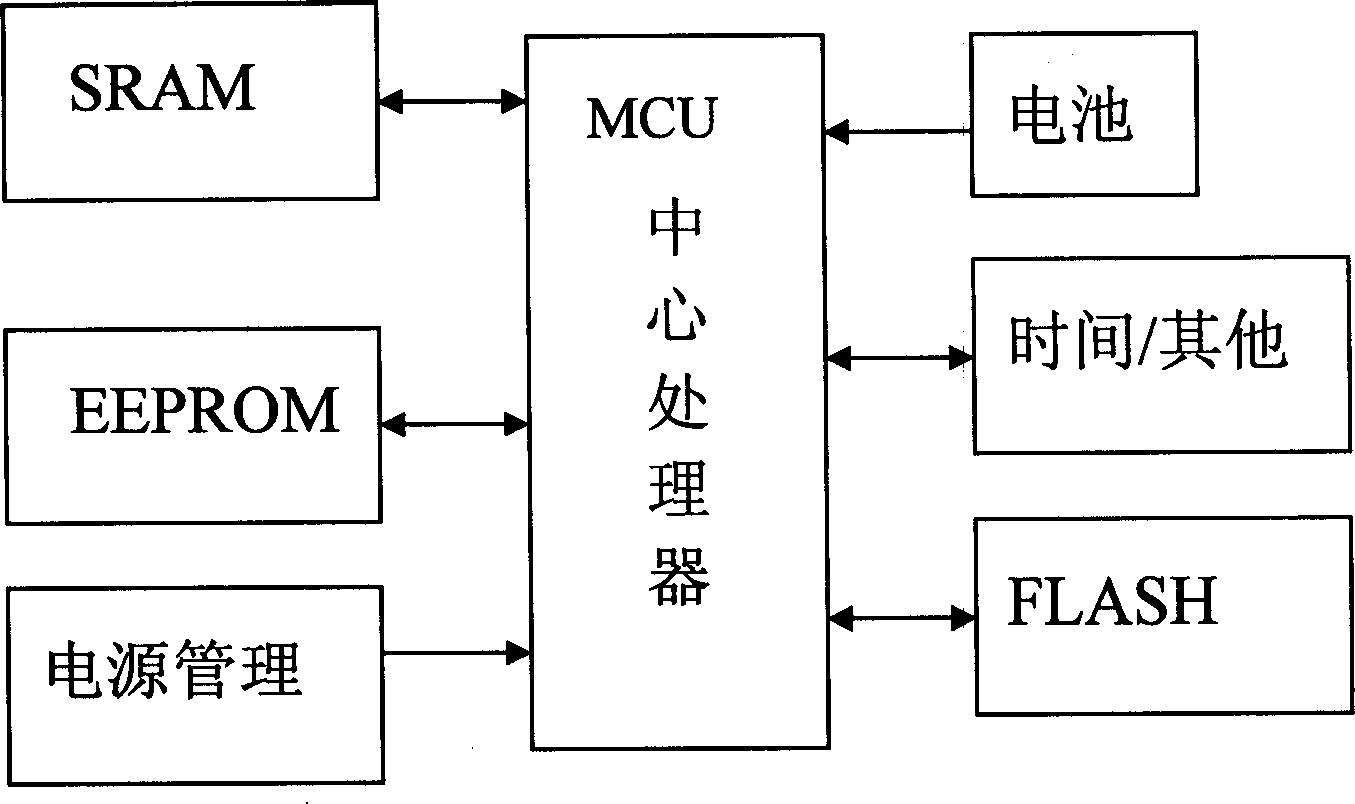
Data storage system for tax controlled cash register
InactiveCN1804908AReduce the number of operationsImprove reliabilityCash registersData informationData storing
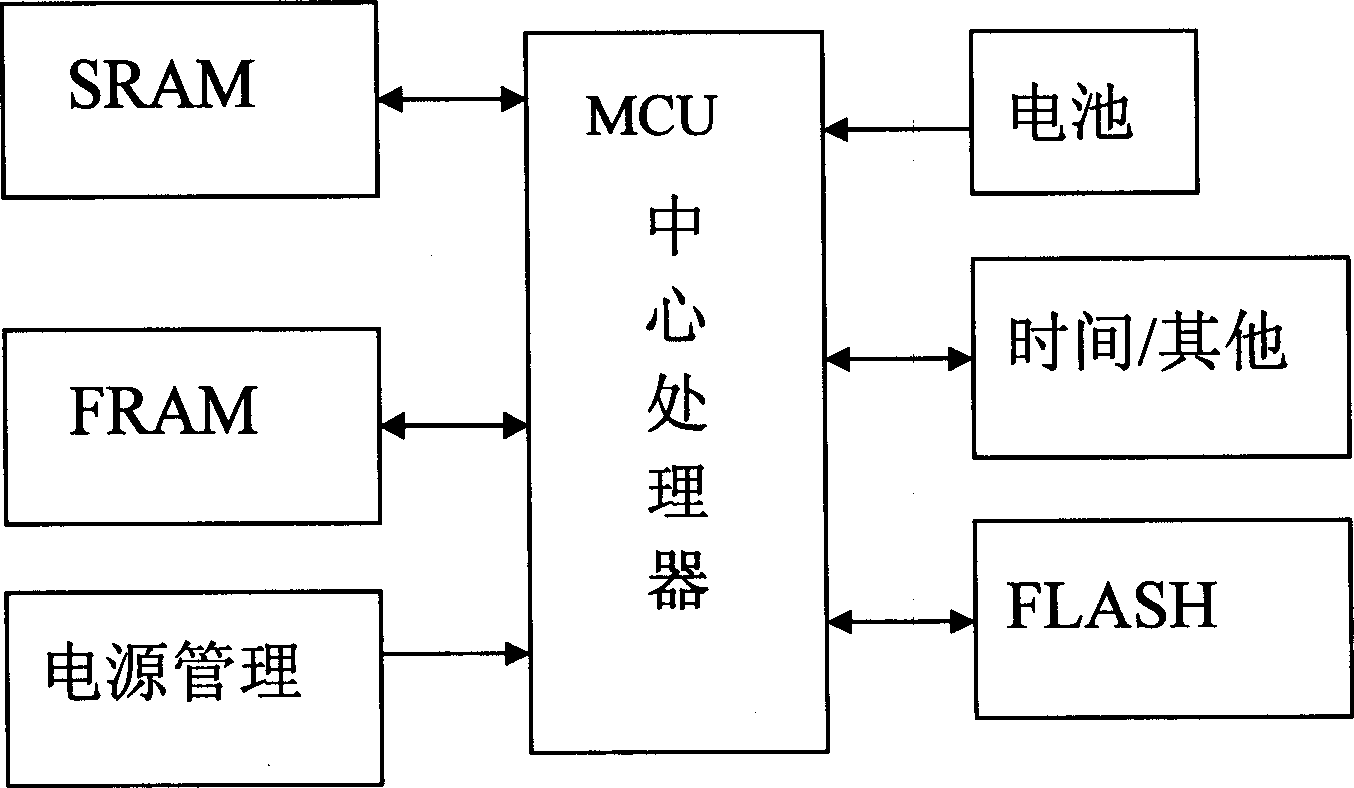
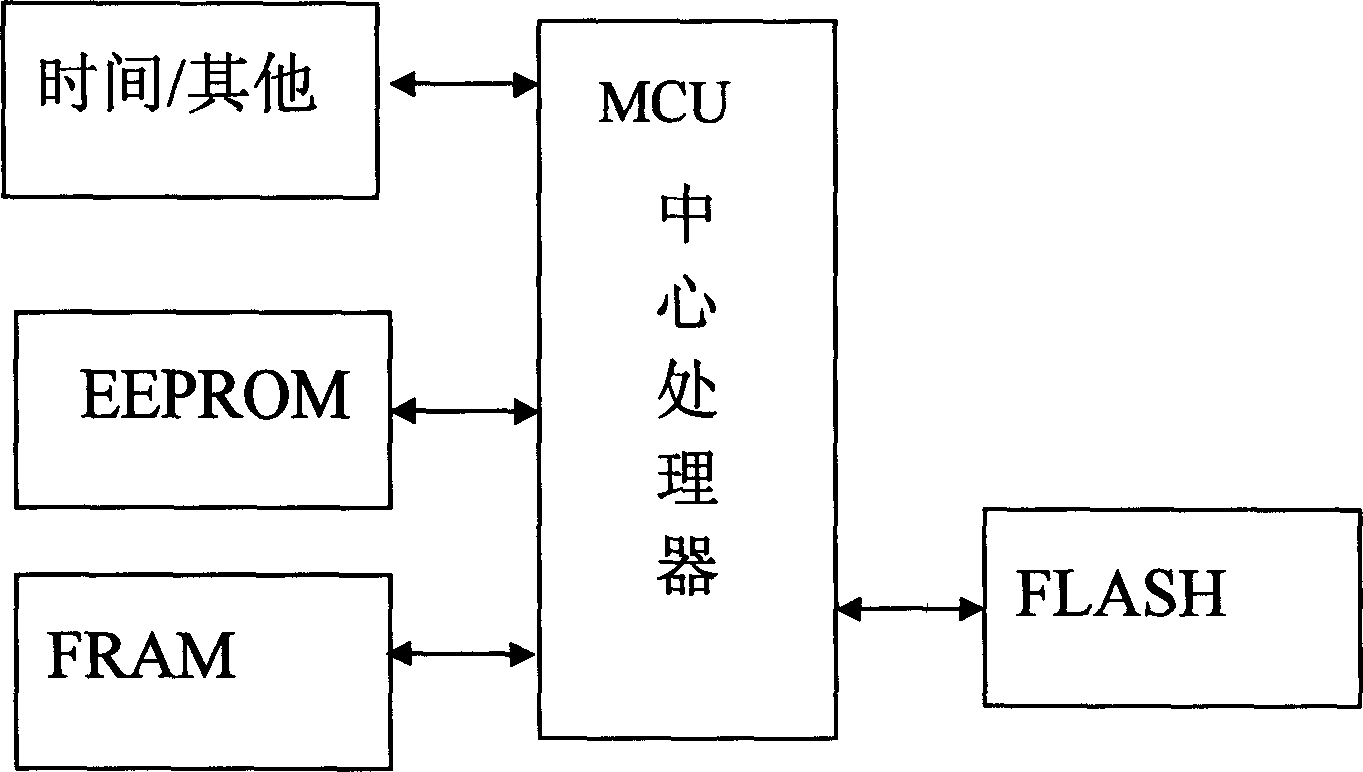
The invention discloses a tax control cashier's machine data storing system which comprises: a Flash storage used to store a plurality of data, wherein the rub-write operation is distributed on each rub-write block of the Flash storage during the storing course; a EEPROM storage used to store the buffer data, when the data in EEPROM storage accumulates to a block data amount of the Flash storage, it concentrates to write it to another rub-write block of the Flash storage; a FRAM iron electric storage used to store the data which is normal used or the preserved data without power; wherein the Flash storage, the EEPROM storage and the FRAM iron electric storage are separately change the data information with the MCU center processor.
Owner:CHENGDU QIANFENG ELECTRONICS APPLIANCES GROUP
Cotton warehouse safety monitoring system based on 3G network
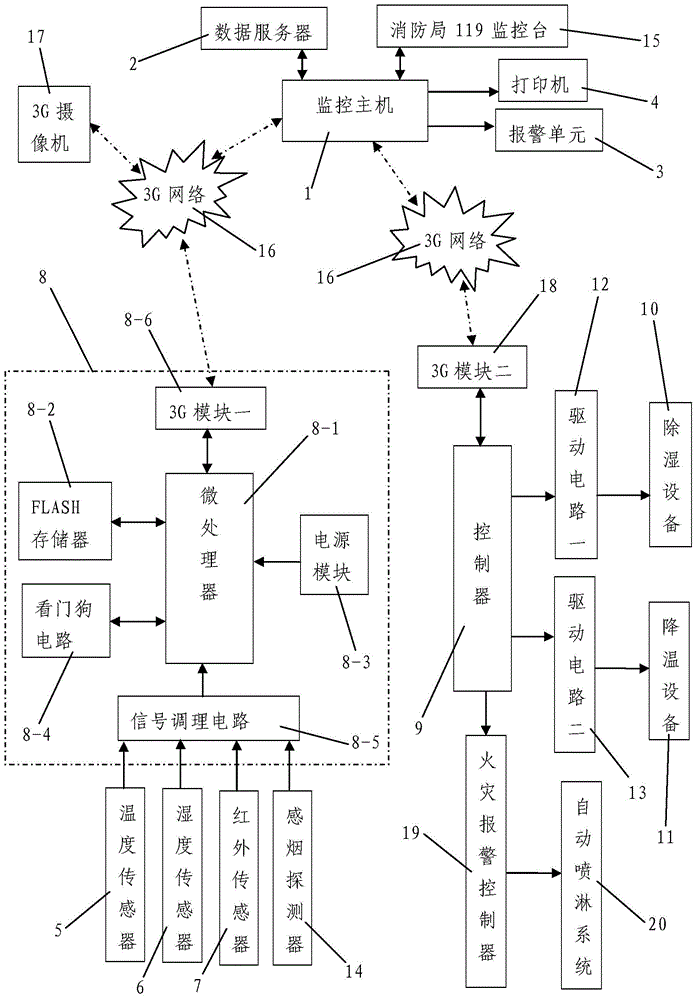
InactiveCN104656601AThe system is safe and reliableImprove storage quality and securitySimultaneous control of multiple variablesProgramme total factory controlFirefightingData collector
The invention discloses a cotton warehouse safety monitoring system based on a 3G network. The cotton warehouse safety monitoring system comprises a monitoring center upper computer, a data acquisition unit, a safety control unit and a 3G network, wherein the monitoring center upper computer comprises a monitoring host, a data server, an alarm unit, a printer and a Fire Department 119 monitoring station; the data acquisition unit comprises a temperature sensor, a humidity sensor, an infrared sensor, a smoke detector, a 3G video camera and a data collector; the safety control unit comprises a main controller, dehumidifying equipment, cooling equipment, a fire alarm controller and an automatic sprinkling system. The cotton warehouse safety monitoring system realizes wireless detection and control on the temperature and the humidity of a cotton warehouse through the 3G network in real time, and has automatic safe protection and firefighting functions. On one hand, the cotton storage quality and safety are greatly improved, and on the other hand, the problems of a wired communication system, such as complicated wiring, high investment cost and poor system expandability are solved.
Owner:XIAN ZHONGZHI HUIZE PHOTOELECTRIC TECH
Large file storage method
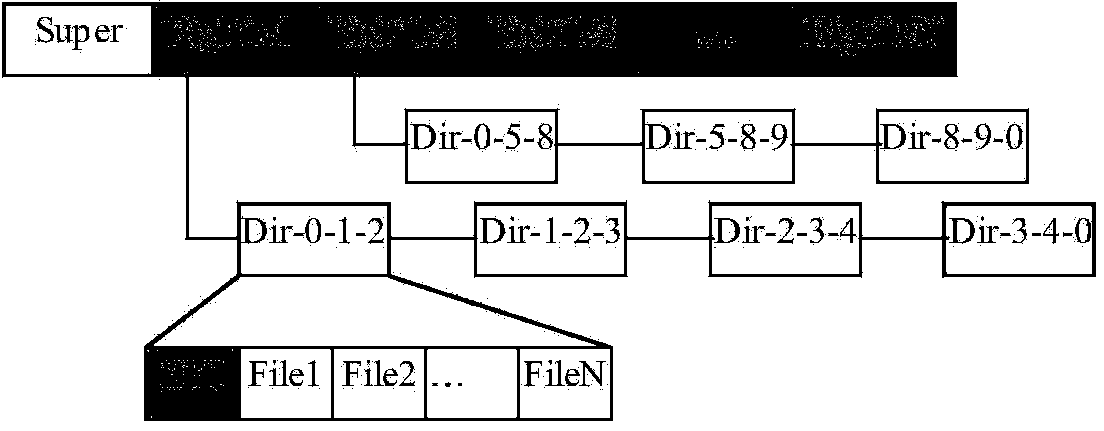
InactiveCN103970869AImprove storage securityFile access structuresFile/folder operationsData fileStorage security
The invention provides a large file storage method. The large file storage method comprises the steps that a large file is mapped into at least one catalog of at least one file system; an index of the large file records an initial address of a first catalog after mapping, the address of a storage region where the index of the large file is located and basic information of the large file; a plurality of data files are included in each catalog after mapping of the large file. According to the scheme of the large file storage method, the storage safety of the large file is higher.
Owner:ZHEJIANG UNIVIEW TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com