Log ciphertext retrieval method based on alarm association
A log file and log technology, which is applied in the field of alarm log retrieval, can solve the problems of alarm log attacks, difficulty in guaranteeing log integrity and security, and low analysis efficiency, so as to ensure safe storage, improve analysis efficiency, and improve storage efficiency. safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0014] The present invention will be described in detail below in conjunction with the specific embodiment of accompanying drawing:
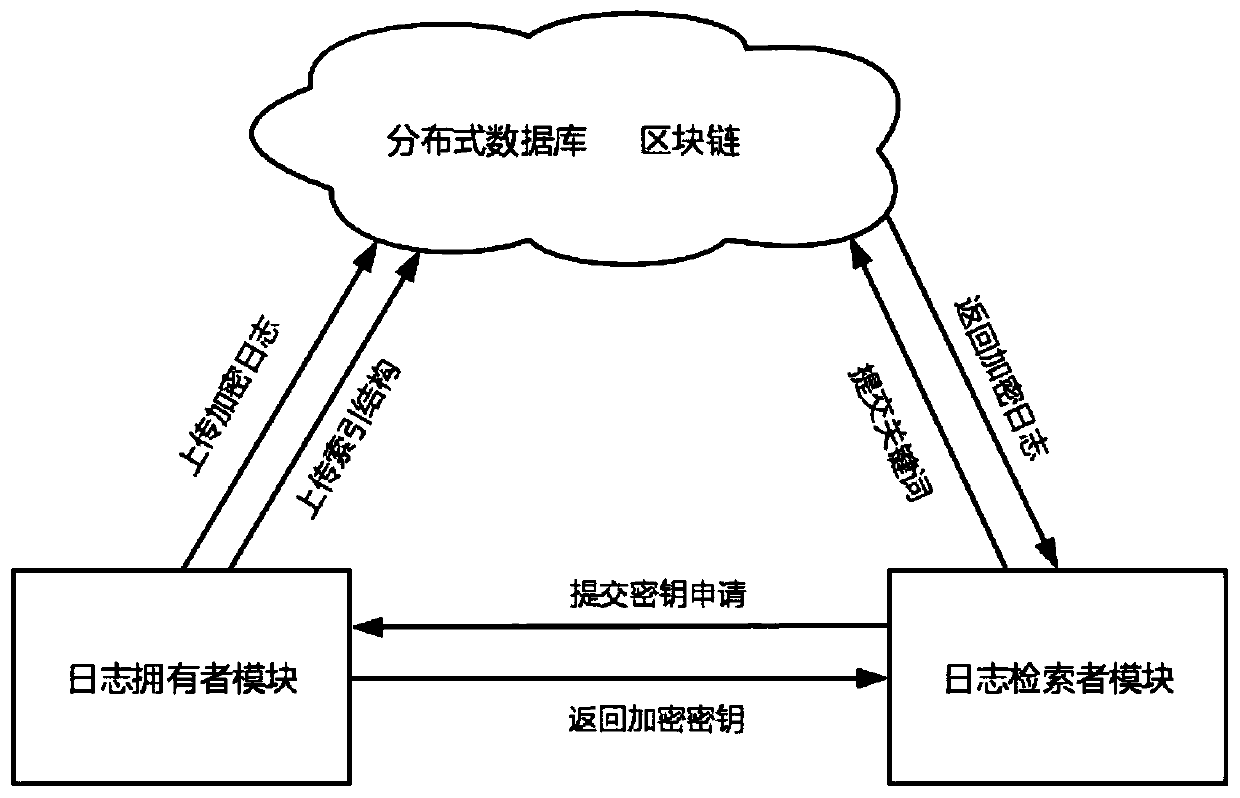
[0015] figure 1 It is a log ciphertext retrieval model diagram based on alarm correlation, including:
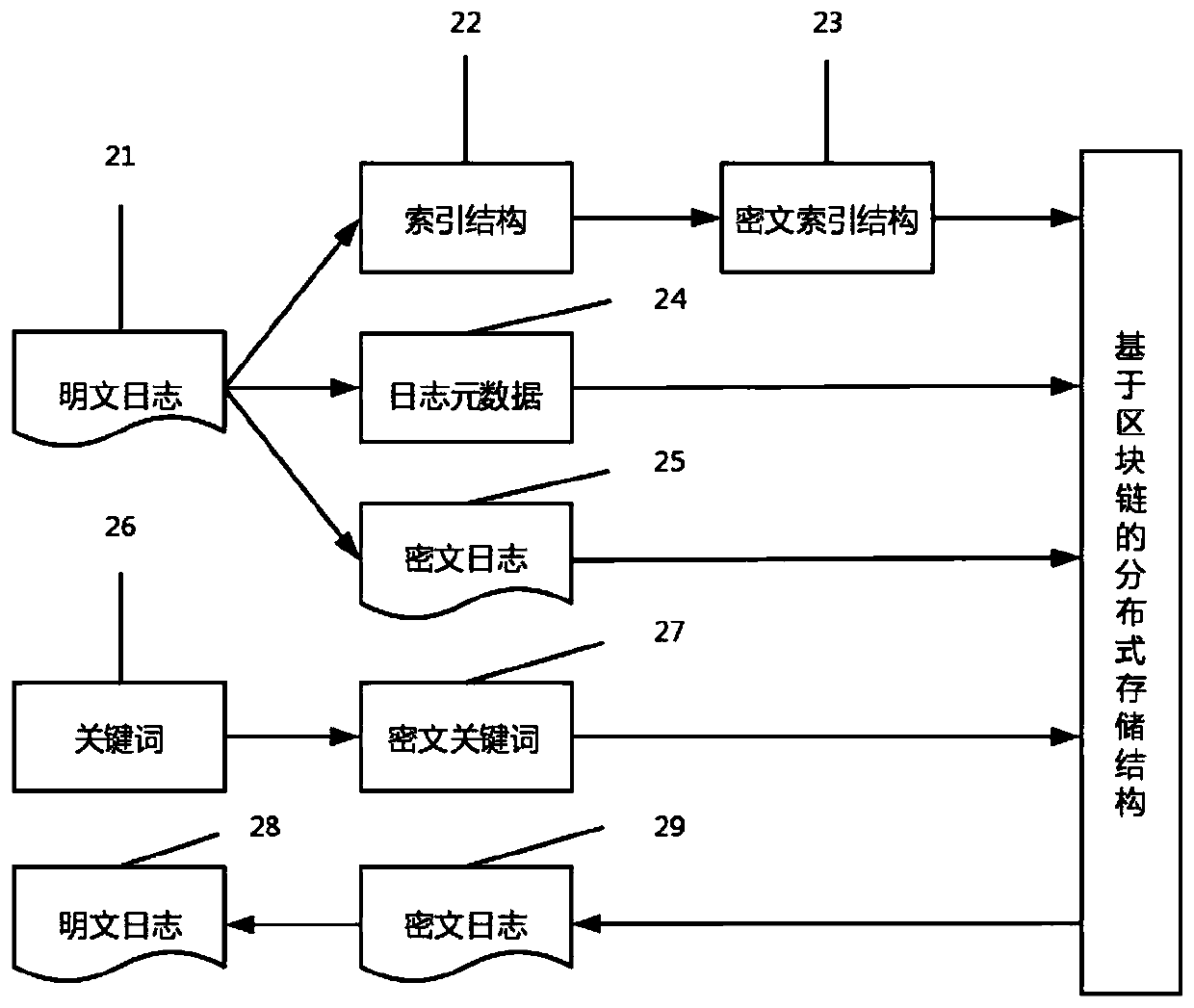
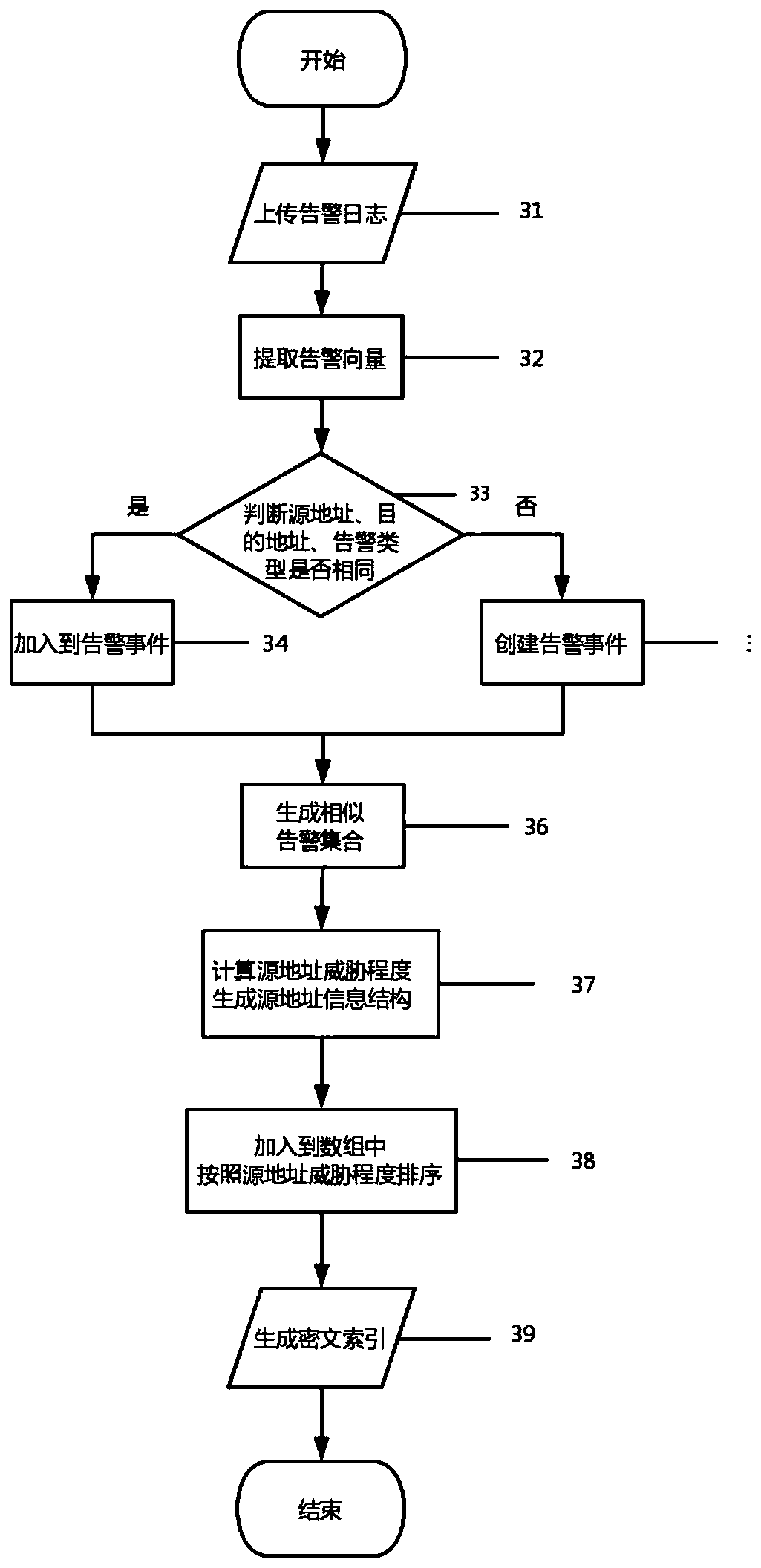
[0016] The log owner module is the owner of the alarm log. The log owner extracts the alarm vector from the alarm log through the client, extracts the ciphertext index structure according to the alarm vector and index construction algorithm, and extracts the log Hash from the alarm log. The value and the log storage address form the log metadata. After all the log collections are processed, they are packaged with the ciphertext index structure and uploaded to the blockchain node. It is necessary to keep the key of the encrypted log. When receiving the key application, the searcher’s identity information To verify, only after the verification is completed can the key be sent to the log retriever who has completed the authentication.
[0017] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com