Method for loading user security seal in visited page and device thereof
A user and stamp technology, applied in the Internet field, can solve the problem that phishing sites are difficult for users to see through, and achieve the effect of improving user experience, avoiding counterfeiting, and ensuring normal access
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The present invention will be described in further detail below in conjunction with the accompanying drawings.
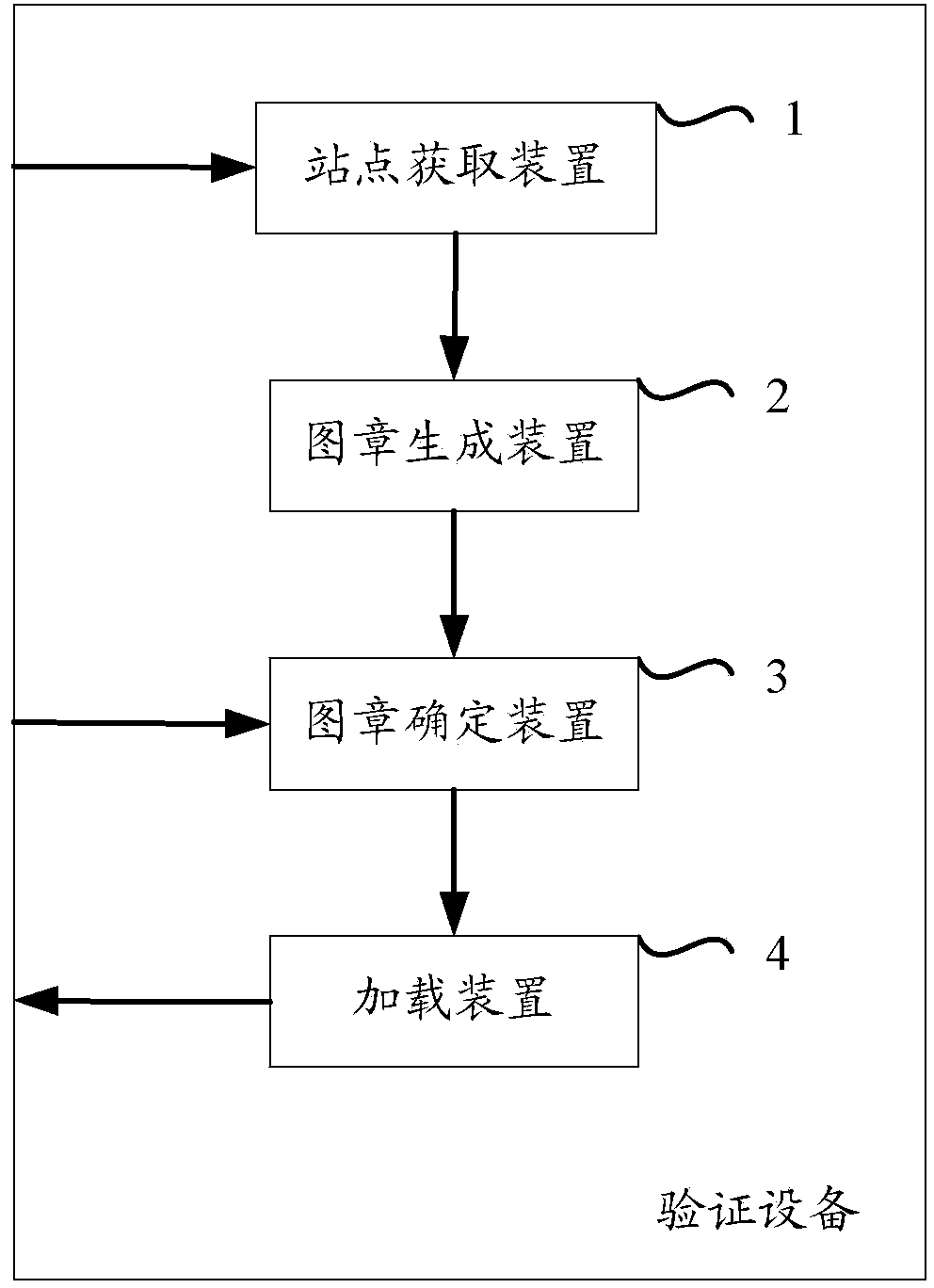
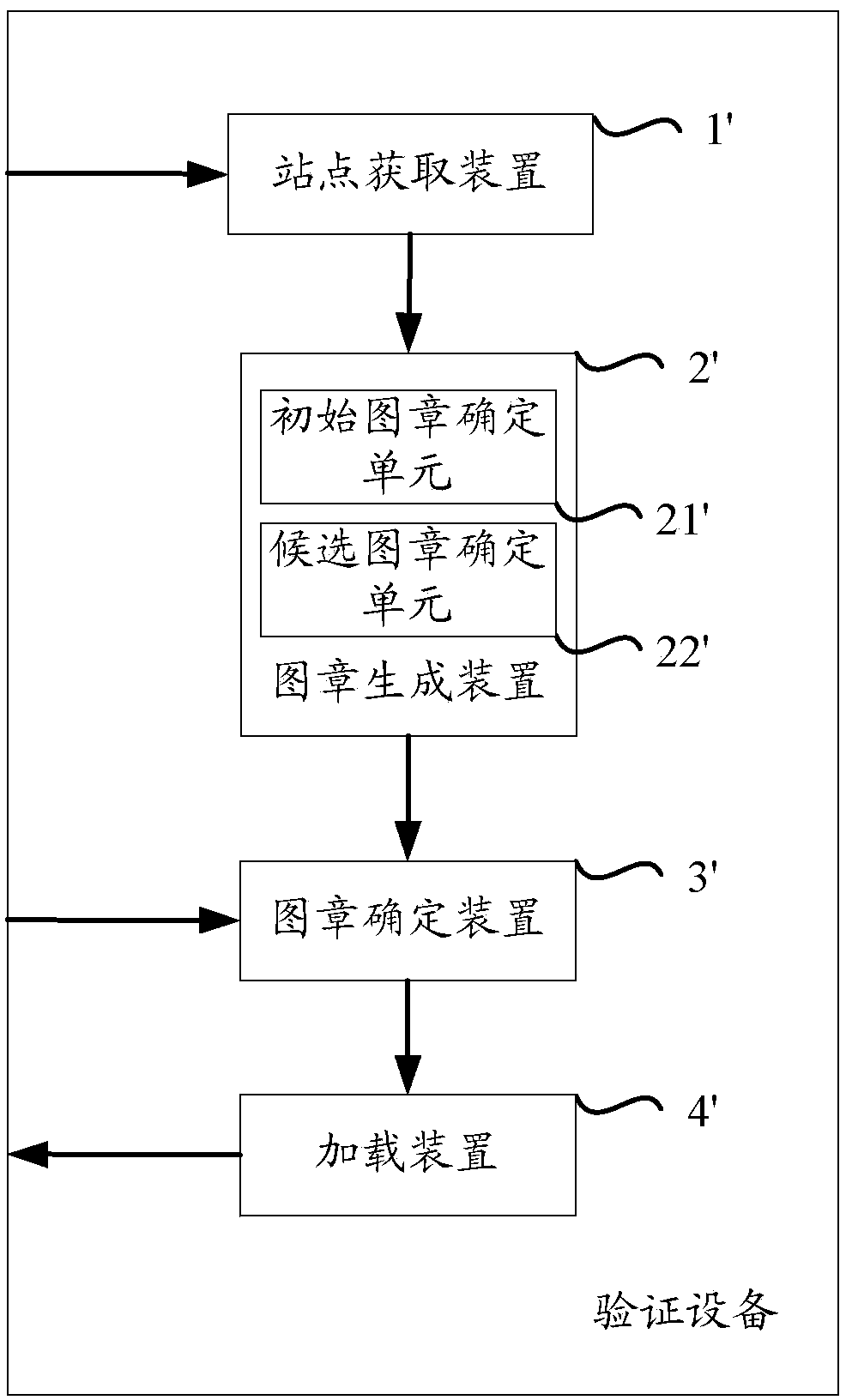
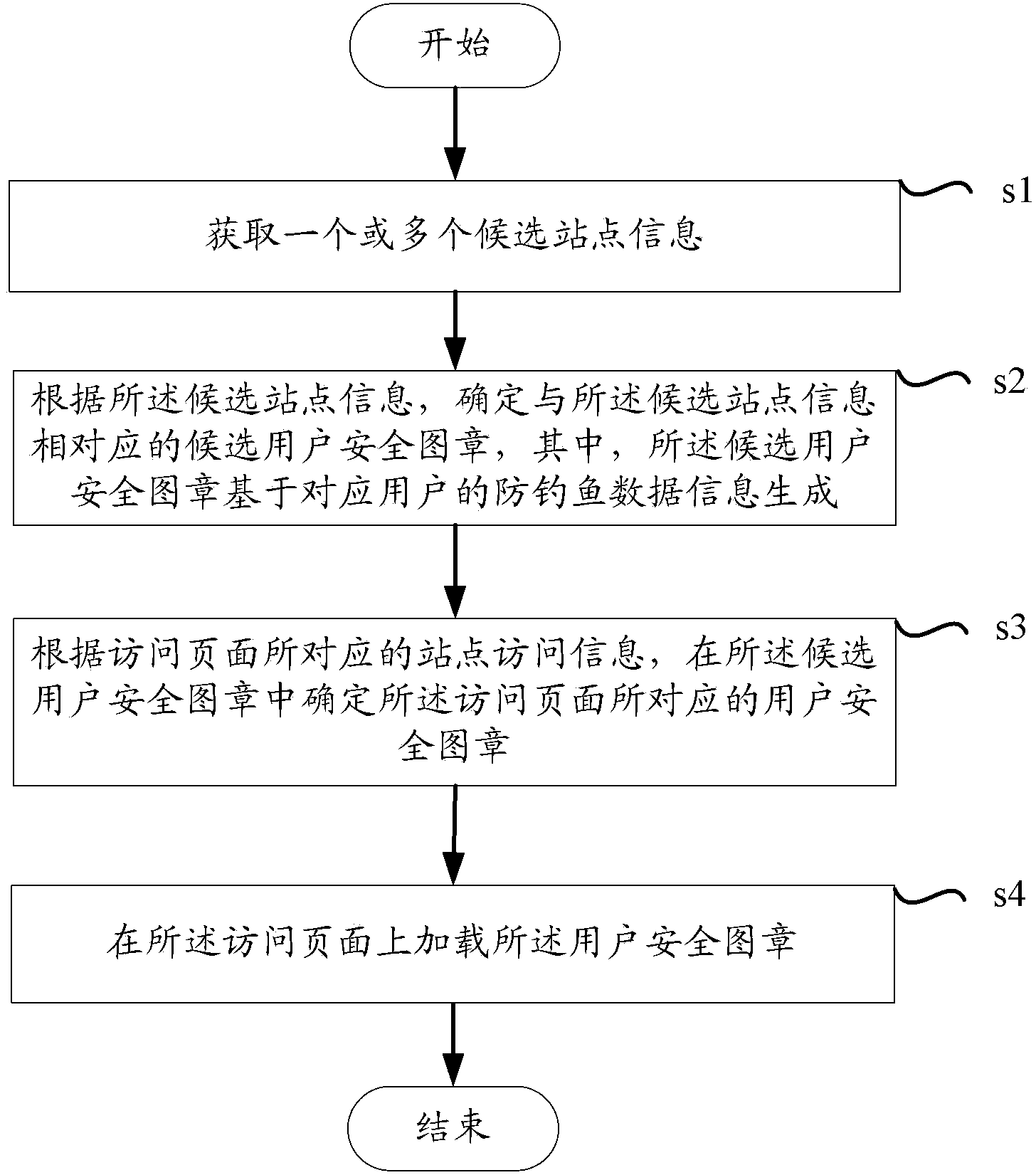
[0037] figure 1It shows a schematic diagram of a verification device for loading a user security seal on an access page according to one aspect of the present invention; wherein, the verification device includes a site acquisition device 1, a seal generation device 2, a seal determination device 3, and a loading device 4 . Specifically, the site acquiring means 1 acquires information on one or more candidate sites; the seal generating means 2 determines a candidate user security seal corresponding to the candidate site information according to the candidate site information, wherein the The candidate user security stamp is generated based on the anti-phishing data information of the corresponding user; the stamp determination device 3 determines the user security stamp corresponding to the visited page in the candidate user security stamp according to the si...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com