Method for detecting database risk, server and storage medium
A database and risk technology, applied in electrical components, transmission systems, etc., can solve problems such as inability to deal with data leakage, inability to deal with mutated attack methods, inability to deal with failure of database update and protection failure, etc., to improve security and improve efficiency and accuracy, the effect of avoiding data leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
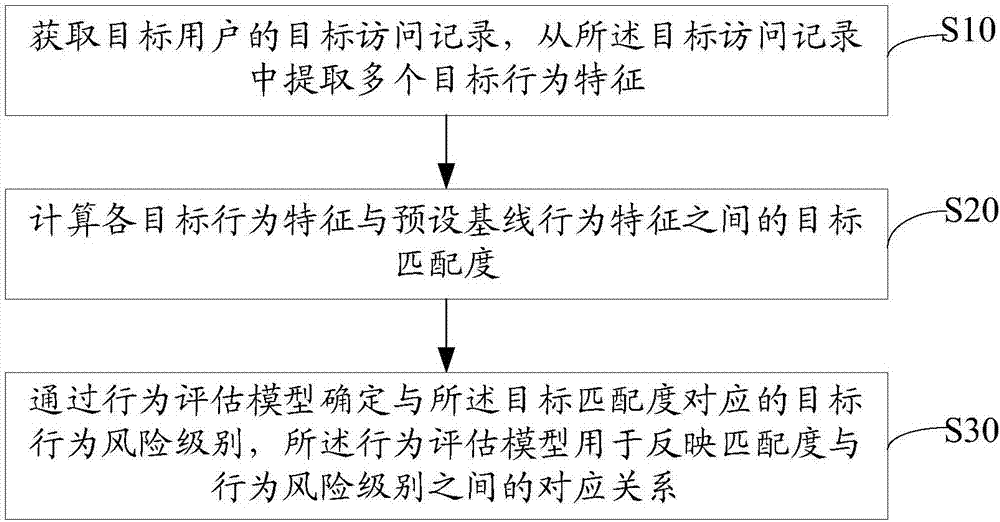
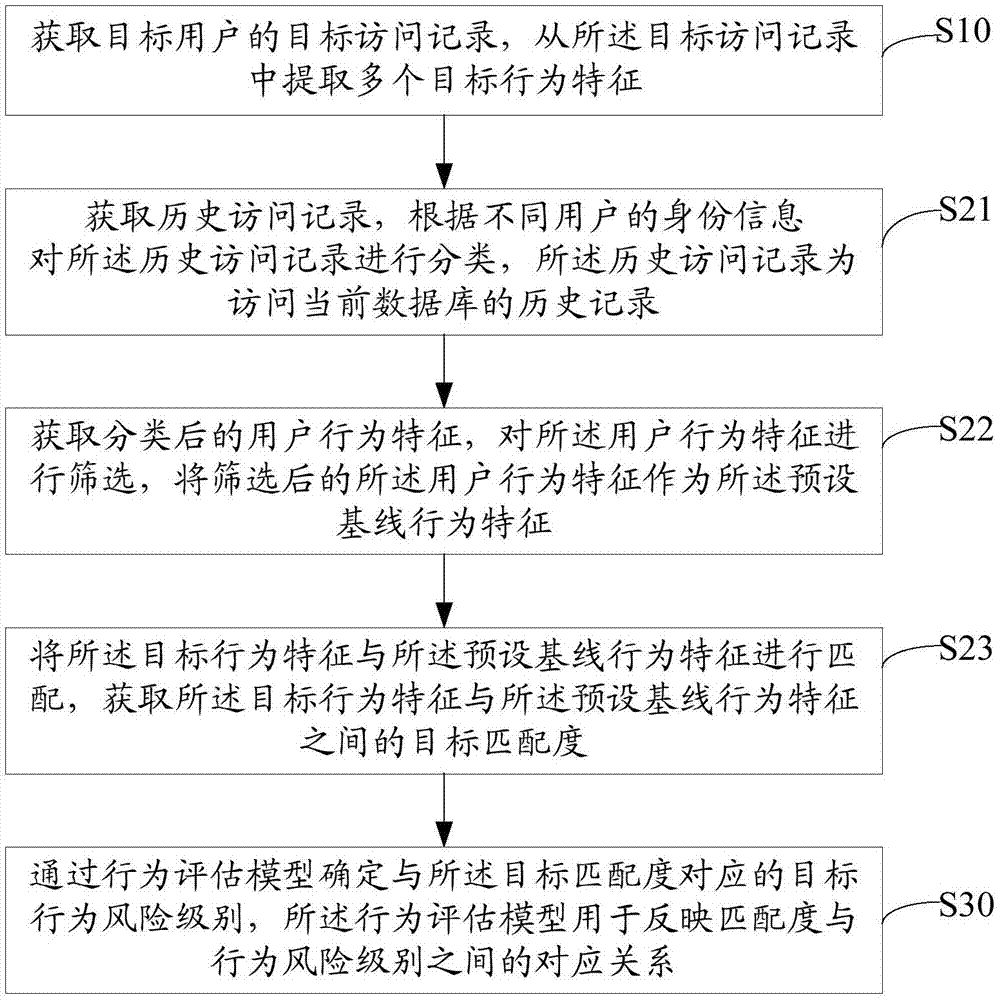
[0047] The solution of the embodiment of the present invention is mainly: by acquiring the target user’s target access records, extracting multiple target behavior features from the target access records, and calculating the target matching degree between each target behavior feature and the preset baseline behavior feature , using a behavior assessment model to determine the target behavior risk level corresponding to the target matching degree, the behavior assessment model is used to reflect the correspondence between the matching degree and the behavior risk level, and based on the preset baseline behavior characteristics, external attacks and Internal threats can also be effectively detected in response to mutation attacks, without the need to repeatedly update the database in real time, avoiding the occurrence of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com