Intelligent terminal App permission privacy risk monitoring and evaluation system and method
A smart terminal and evaluation system technology, applied in the field of computer security, can solve problems such as difficulty in implementation, low calculation efficiency, difficulty in data acquisition, and complicated calculation methods for authority privacy risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
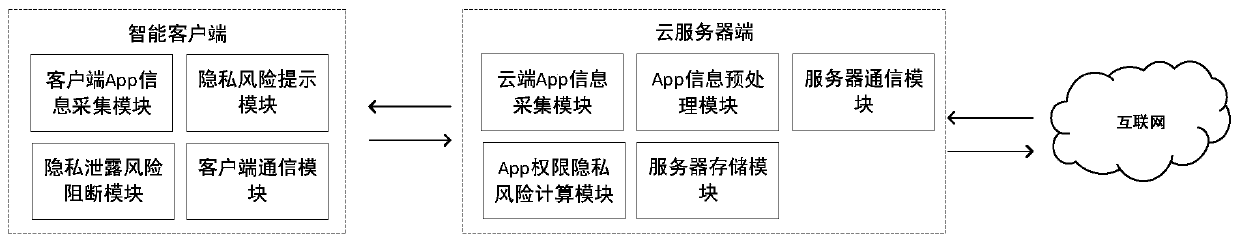
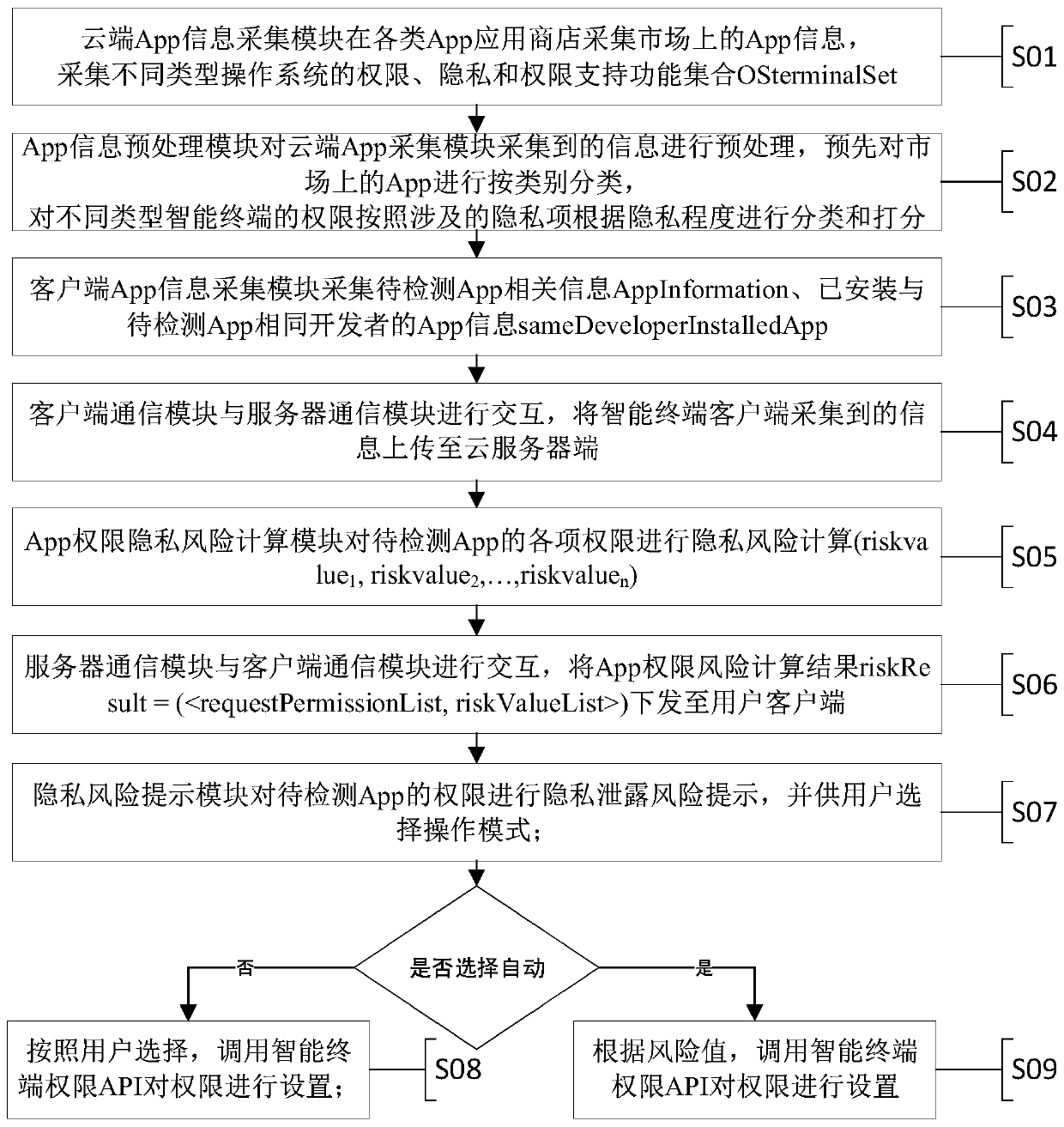
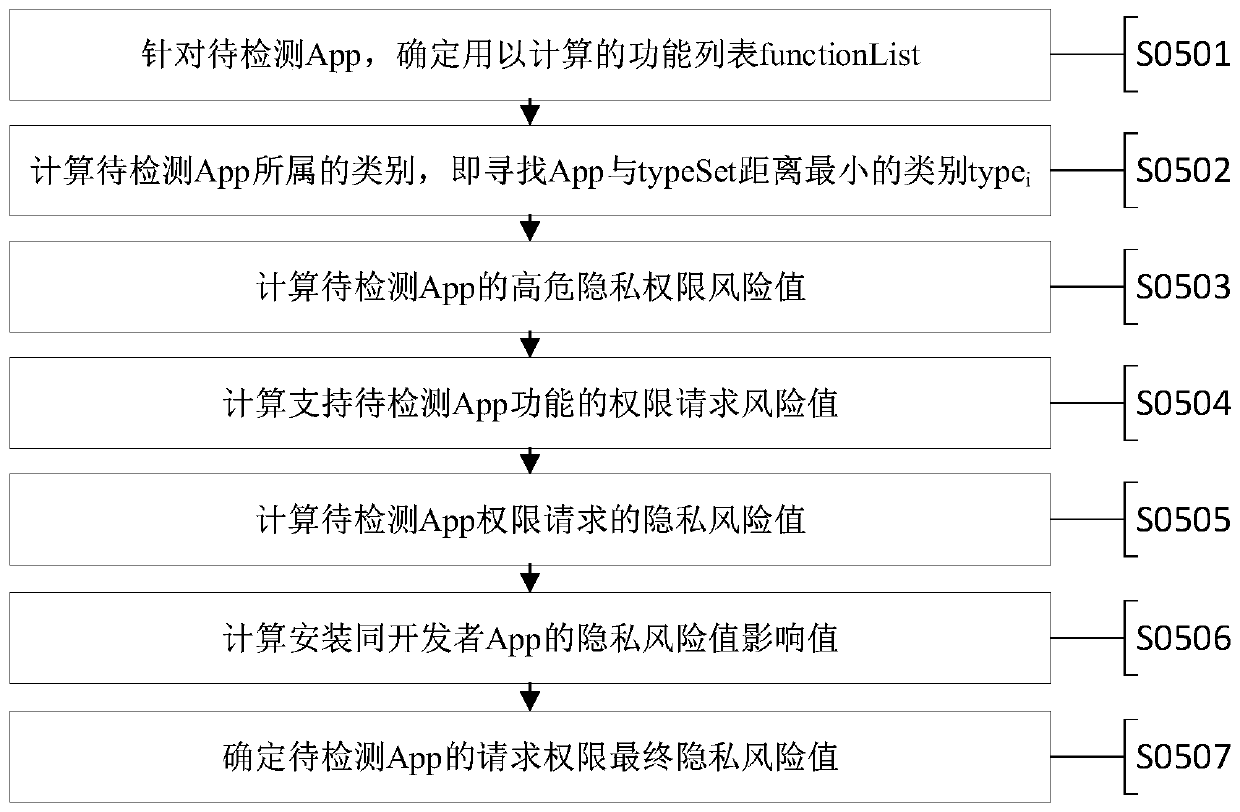
Image
Examples
Embodiment 2
[0065] Embodiment 2 of the present invention: Android mobile phone upgrades and installs App authority privacy risk monitoring and evaluation and privacy leakage blocking
[0066] This embodiment is designed in order to further illustrate the principle of the present invention and facilitate the skilled person to better understand the process of the present invention. Assume that on the Android 7.X mobile phone produced by manufacturer A, an instant messaging app released by a certain developer is upgraded on the mobile phone, and no other apps of the developer have been installed on the mobile phone. During the upgrade process, the app already has 5 Permissions, 2 new permissions are requested. This embodiment process is as follows:
[0067] Steps 1) to 2) are the same as Steps 1) to 2) in Example 1.
[0068] 3) The client App information collection module collects relevant information of the App to be detected AppInformation = (name, version, developer, permittedList, requ...
Embodiment 3
[0072] Embodiment 3 of the present invention: Monitoring and evaluation of privacy risks of Android mobile phones and blocking of privacy leakage of newly installed App permissions with multiple APPs installed by the same developer
[0073] In this embodiment, it is assumed that the user has already installed two different apps from the same developer (such as a map app and a picture sharing app) on his Android 7.x mobile phone from manufacturer A, and now installs the instant messaging app. The example is as follows:
[0074] Steps 1) to 2) are the same as Steps 1) to 2) in Example 1.
[0075] 3) The client-side App information collection module collects relevant information about the App to be detected AppInformation=(name, version, developer, permittedList, requestPermissionList, functionList, OS), where the permittedList is an empty set, the OS is Android 7.x, and the collected ones are installed Developer App information sameDeveloperInstalledApp=(1 ,version 1 ,permitte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com