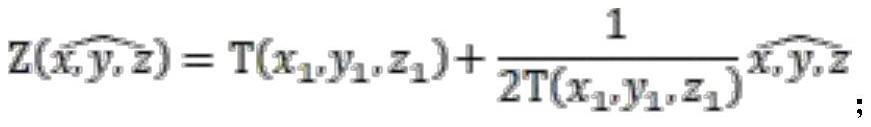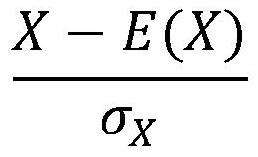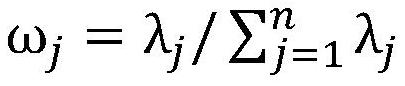Patents
Literature
30 results about "Information sensitivity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Information sensitivity is the control of access to information or knowledge that might result in loss of an advantage or level of security if disclosed to others. Loss, misuse, modification, or unauthorized access to sensitive information can adversely affect the privacy or welfare of an individual, trade secrets of a business or even the security and international relations of a nation depending on the level of sensitivity and nature of the information.
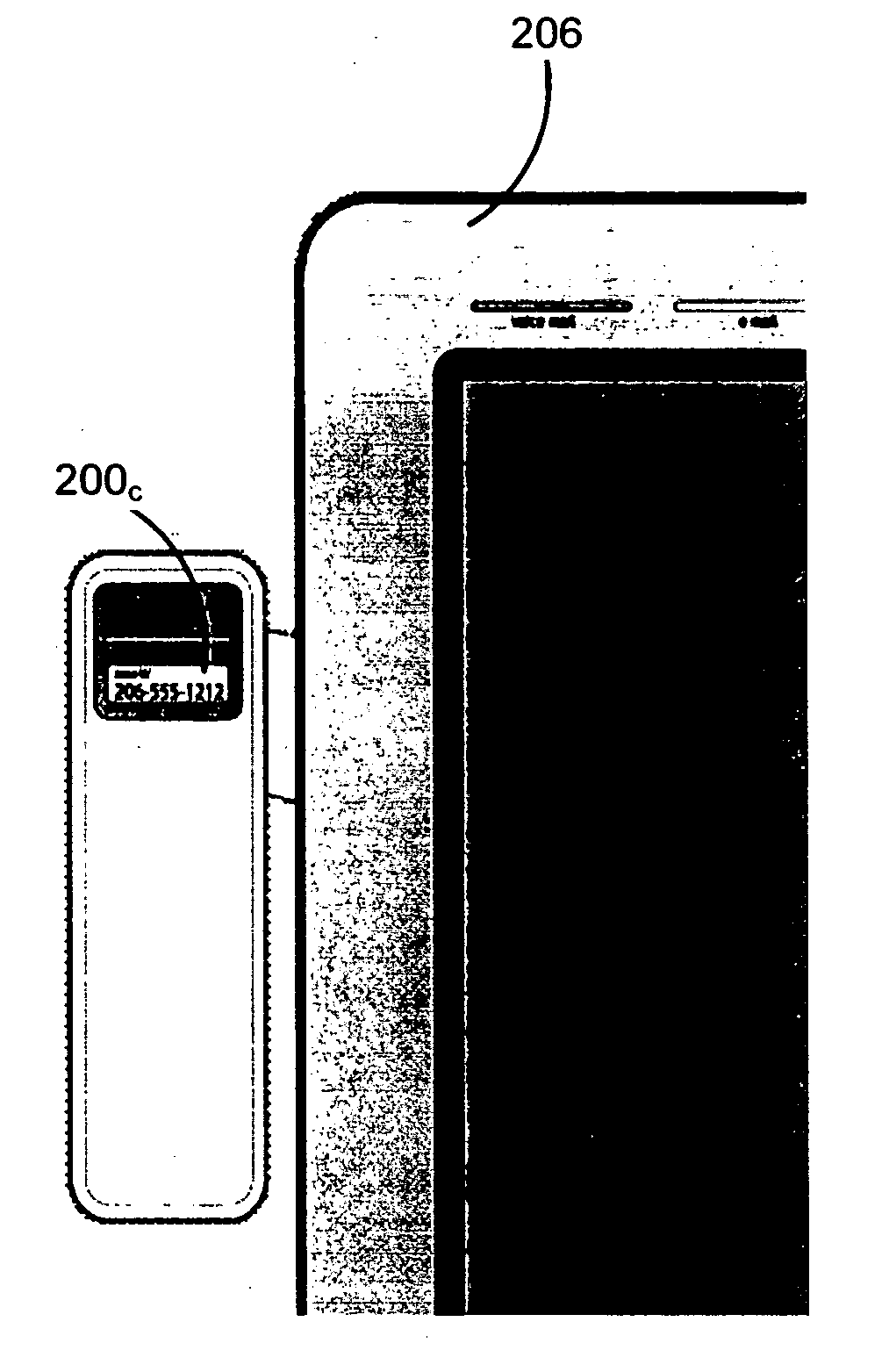
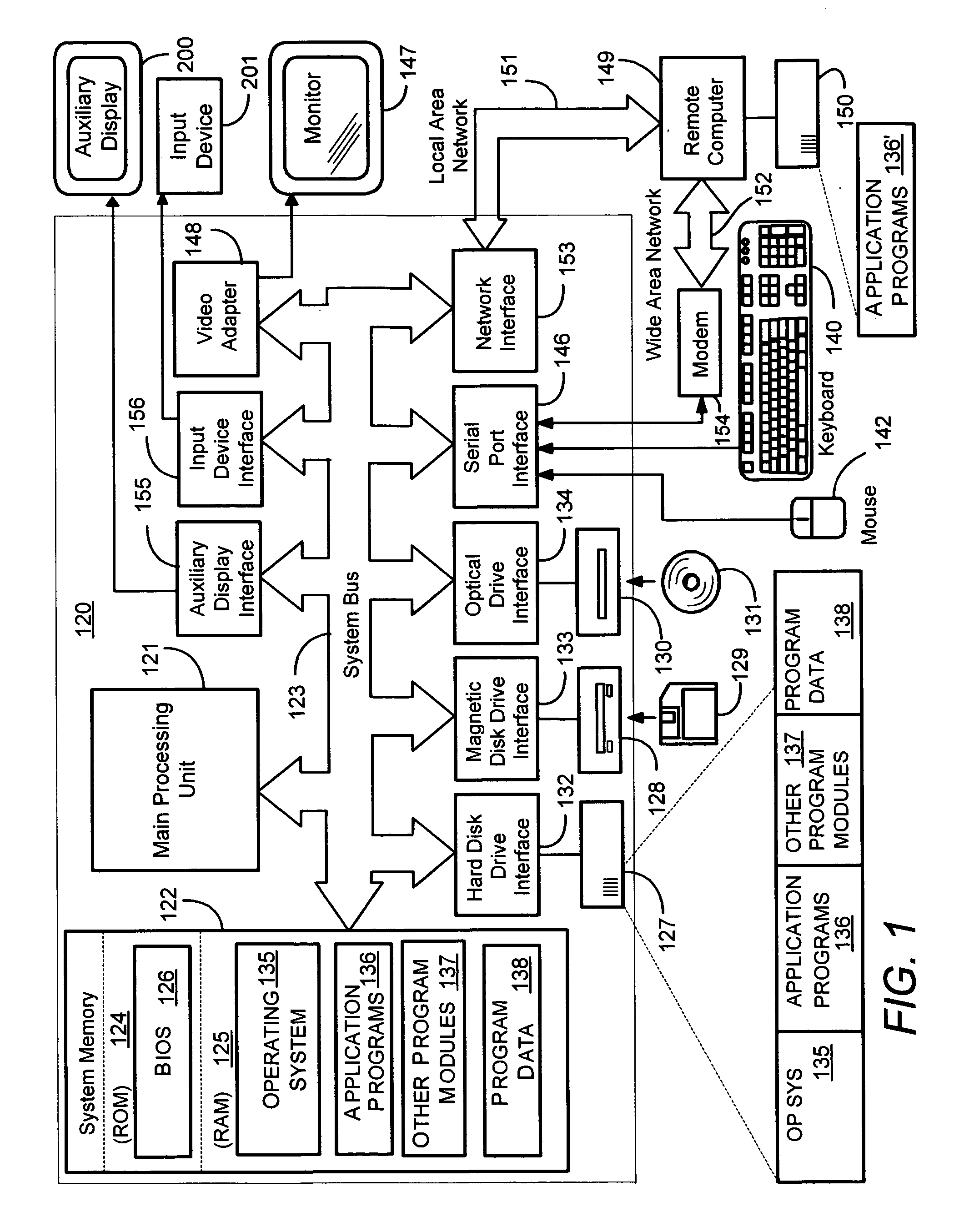
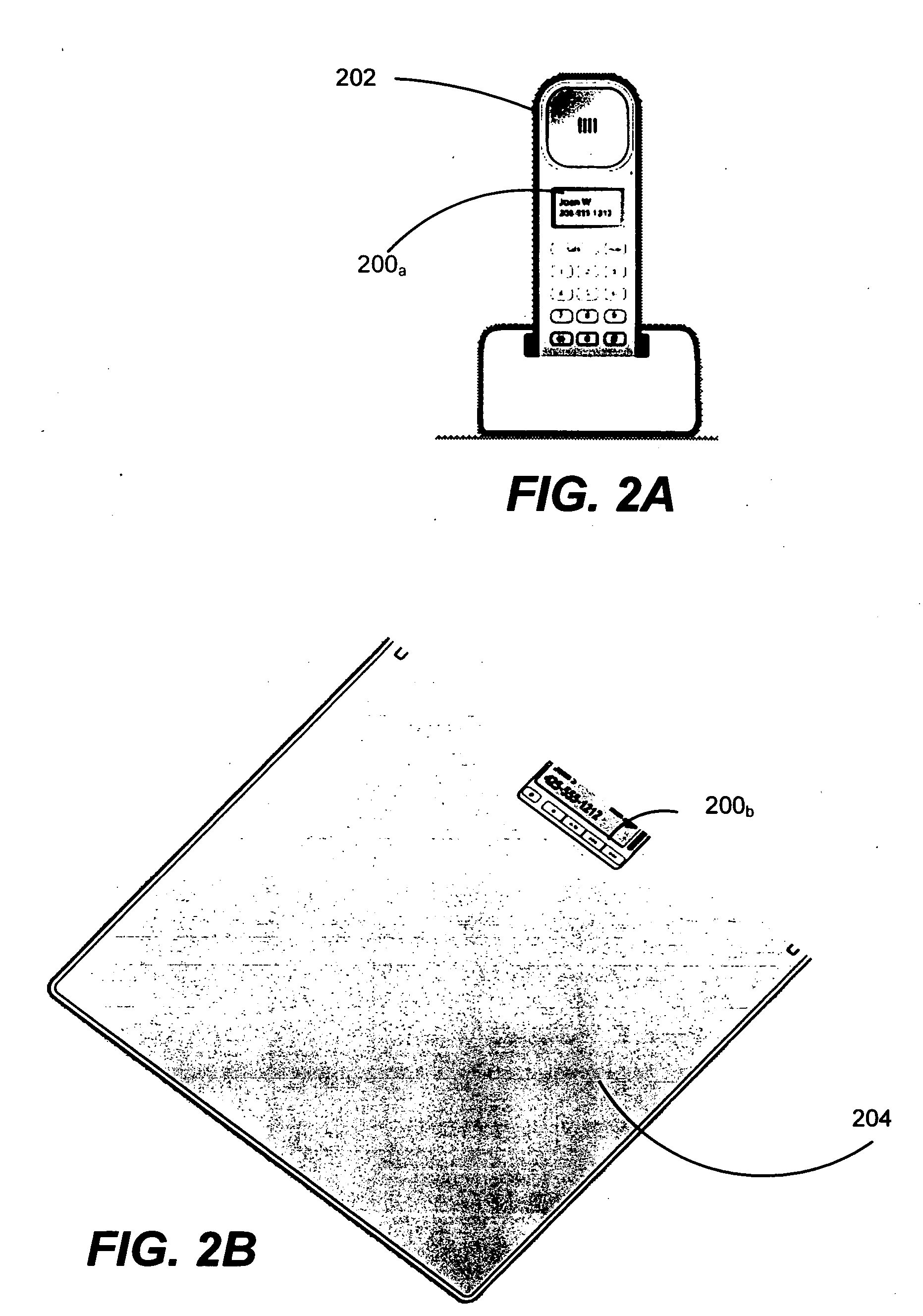
Context-aware auxiliary display platform and applications
InactiveUS20050243019A1Digital data processing detailsProgram control using record carriers with instructionsDisplay deviceContext data
Described is a mechanism by which application programs (or plug-ins) and an auxiliary service adjust the output and / or data available for output on an auxiliary device based on changes detected in the current context of the auxiliary display. Context sensors detect and report changes in context, whereby some action is taken with respect to what information is displayed or can be displayed on the auxiliary display device. Examples of context data that can change include the physical location of the display, detected movement or motion data, presence of a particular user or others, power state, network connectivity status, privacy status and so forth. The auxiliary device can have context as to its position relative to the main display. Information sensitivity levels may be used to specify whether an application program's data can be displayed, based on the perceived sensitivity of the information and the user's current context.
Owner:MICROSOFT TECH LICENSING LLC
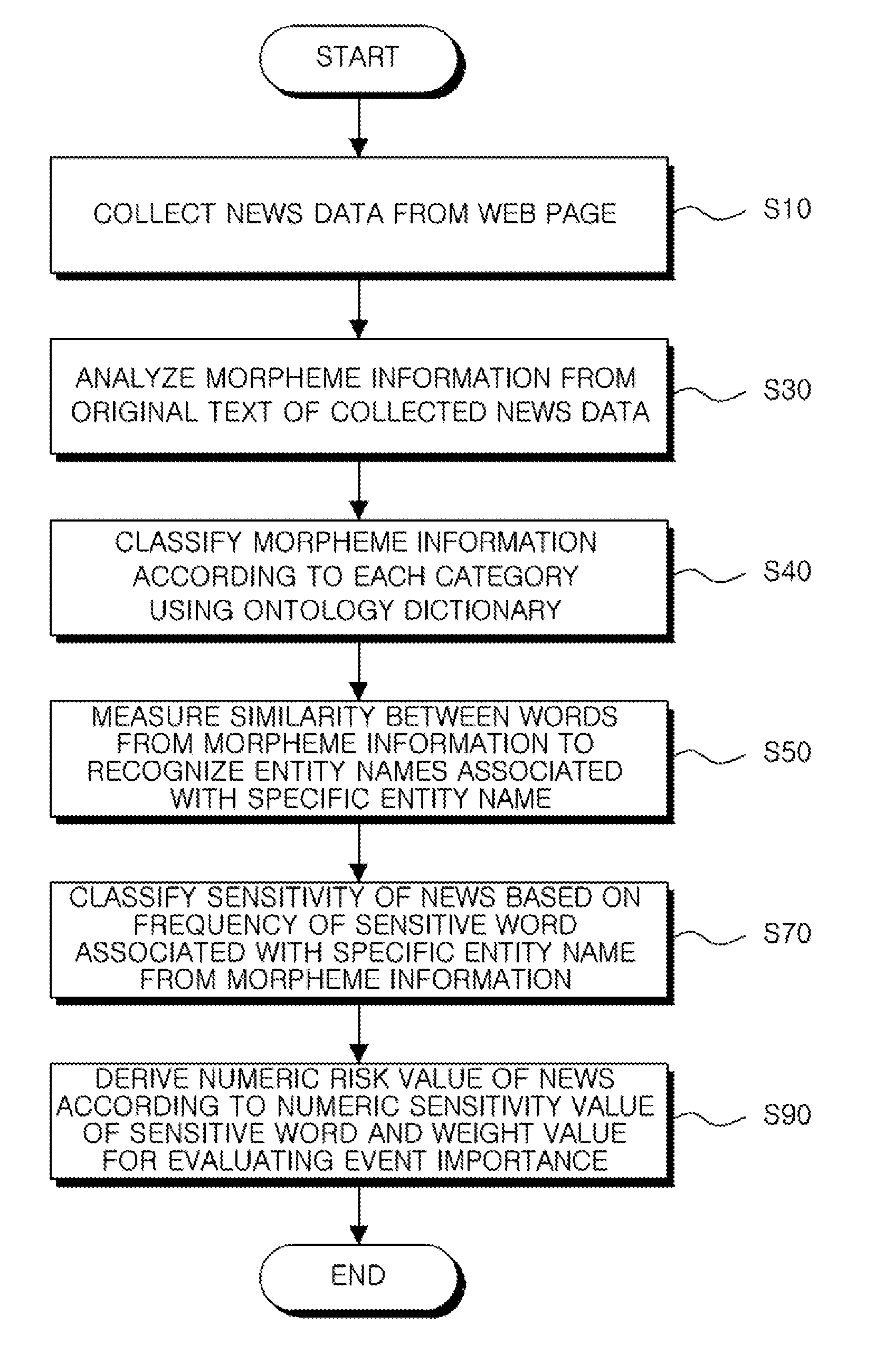
Device and method for analyzing reputation for objects by data mining
ActiveUS20170004128A1Improve reliabilitySemantic analysisUnstructured textual data retrievalMorphemeWeb page
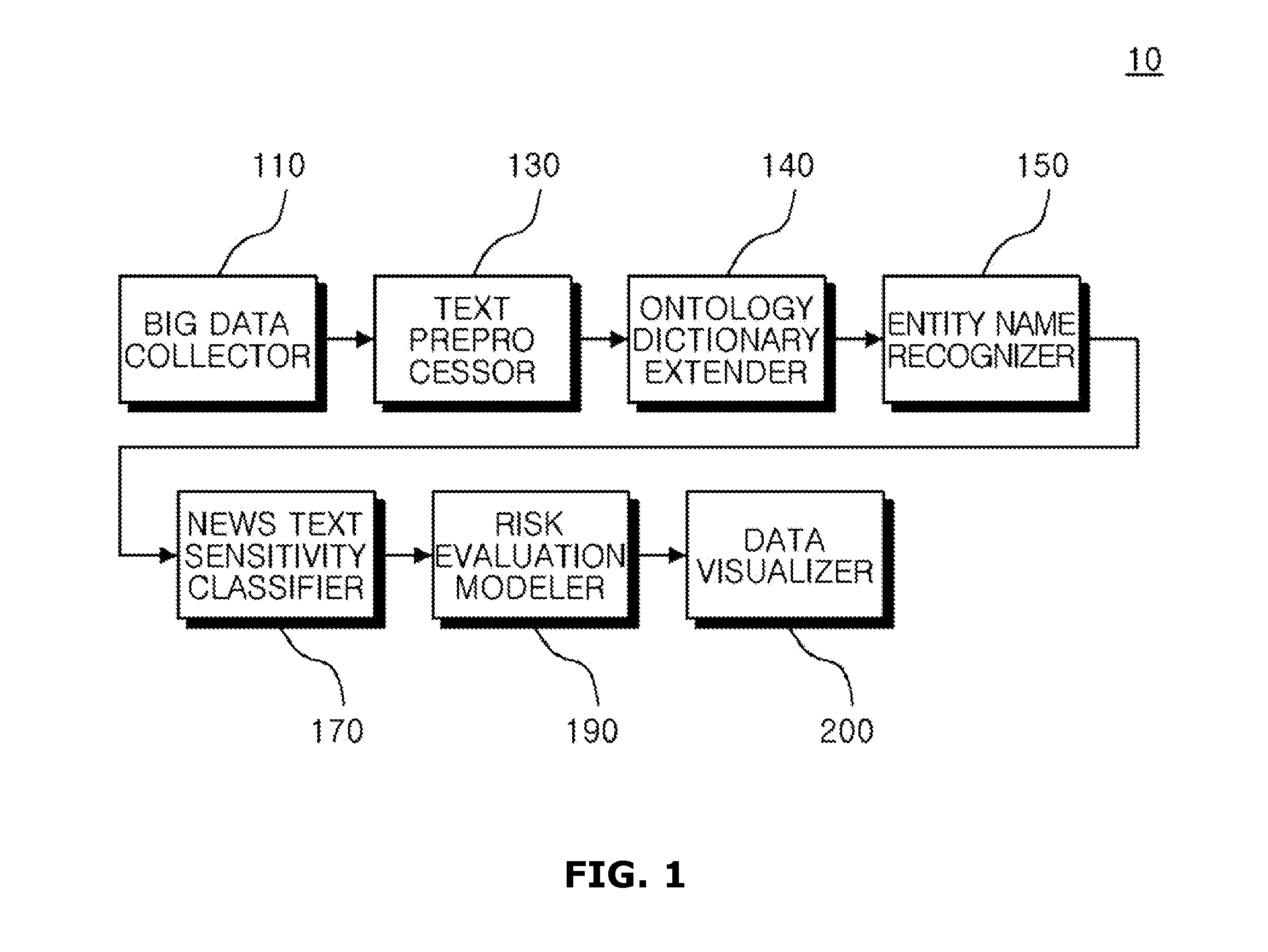
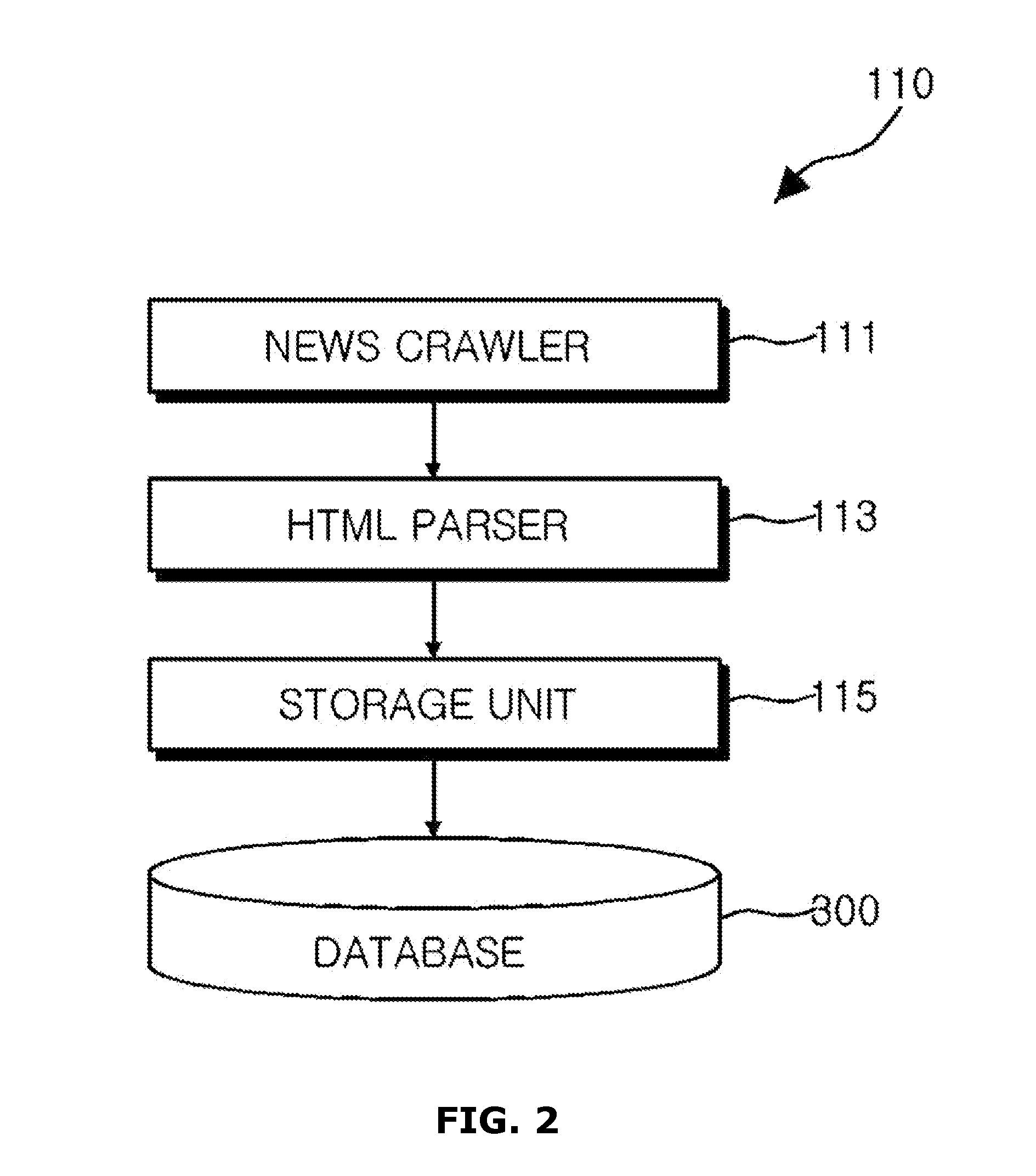
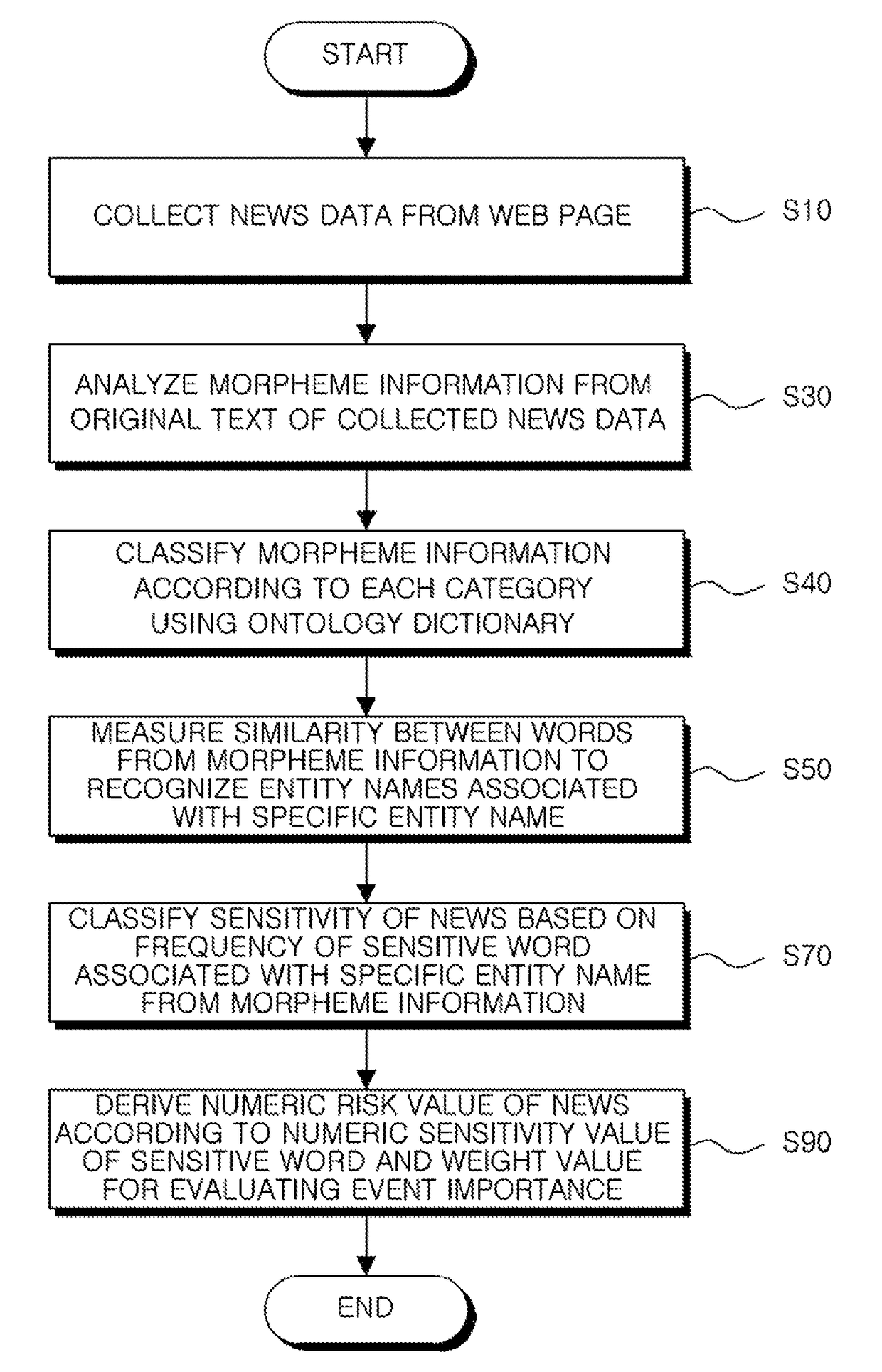
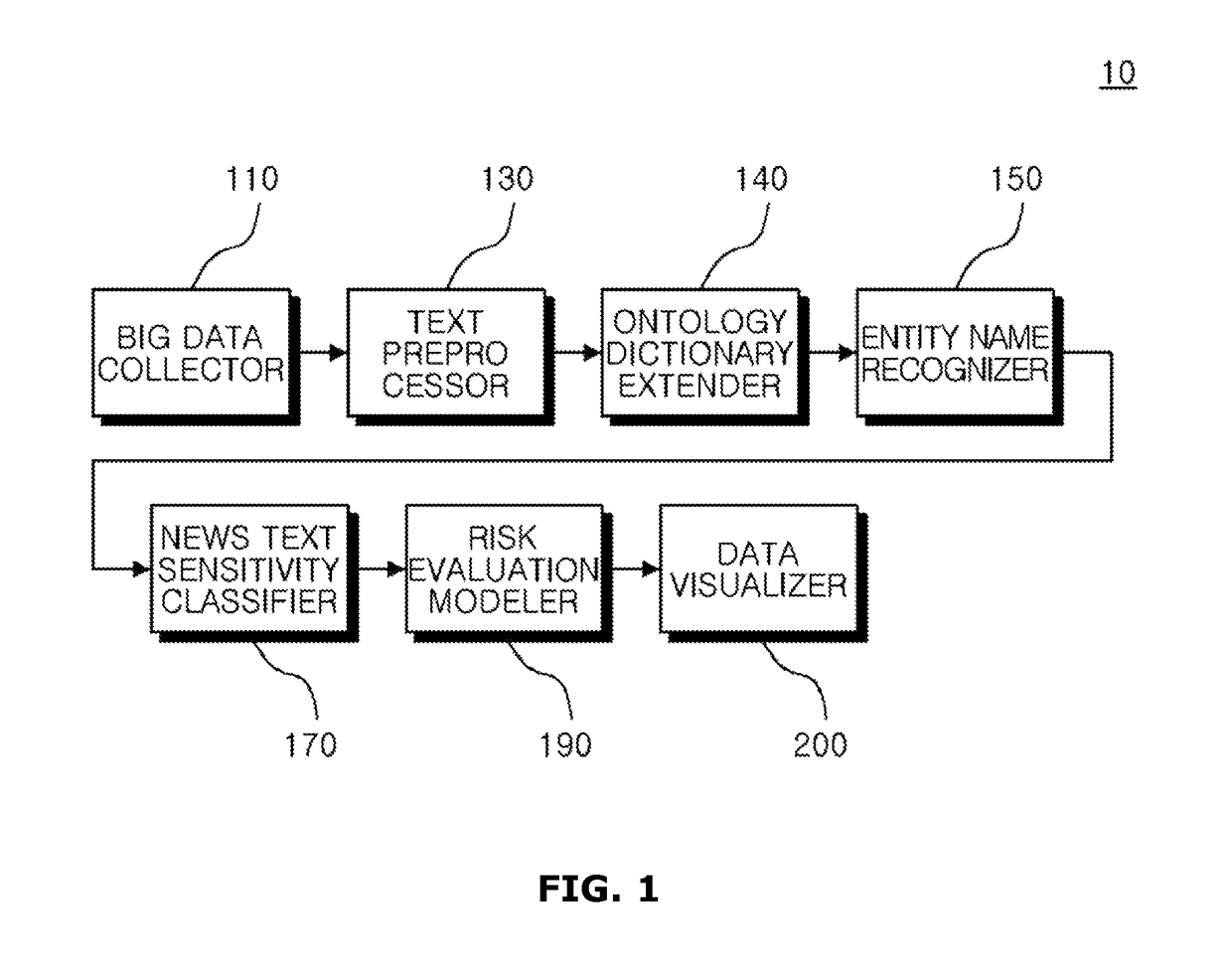
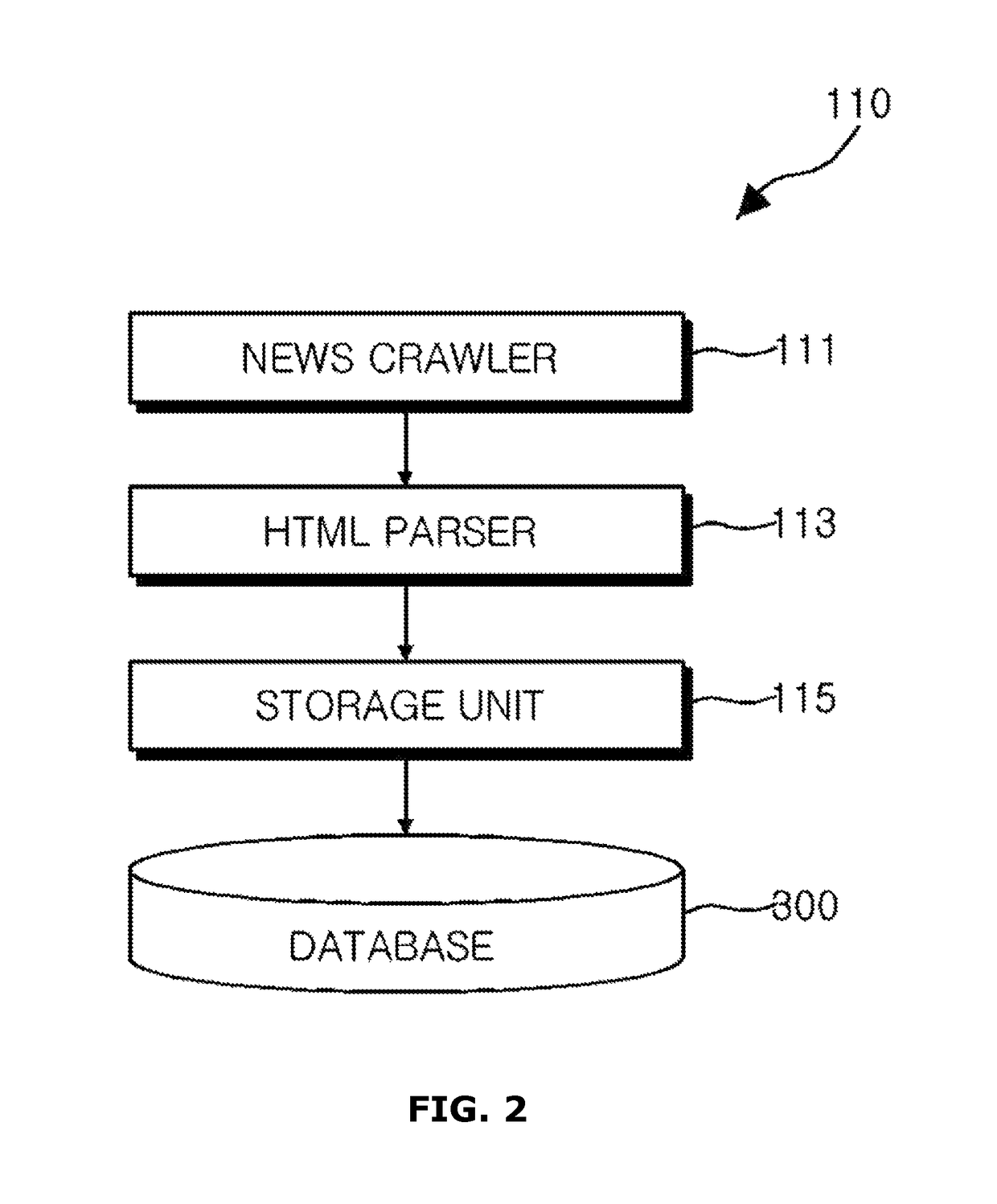
A device for analyzing reputation for objects by data mining is provided. The device includes a big data collector assembly collecting first information from a web page, a text preprocessor assembly analyzing morpheme information from an original text of the first information, an ontology dictionary extender assembly classifying the morpheme information according to each category and extracting an associated word, an object recognizer assembly measuring similarity between the associated word from the morpheme information to recognize a plurality of entity names associated with a first object, an information sensitivity classifier assembly classifying sensitivity of the first information based on a frequency of a sensitive word associated with the first object from the morpheme information, and a risk evaluation modeler assembly deriving a numeric risk value of the first information according to a numeric sensitivity value of the sensitive word and a weight value level for evaluating event importance.
Owner:INST FOR SUSTAINABLE DEV
Control device for motorized power steering device
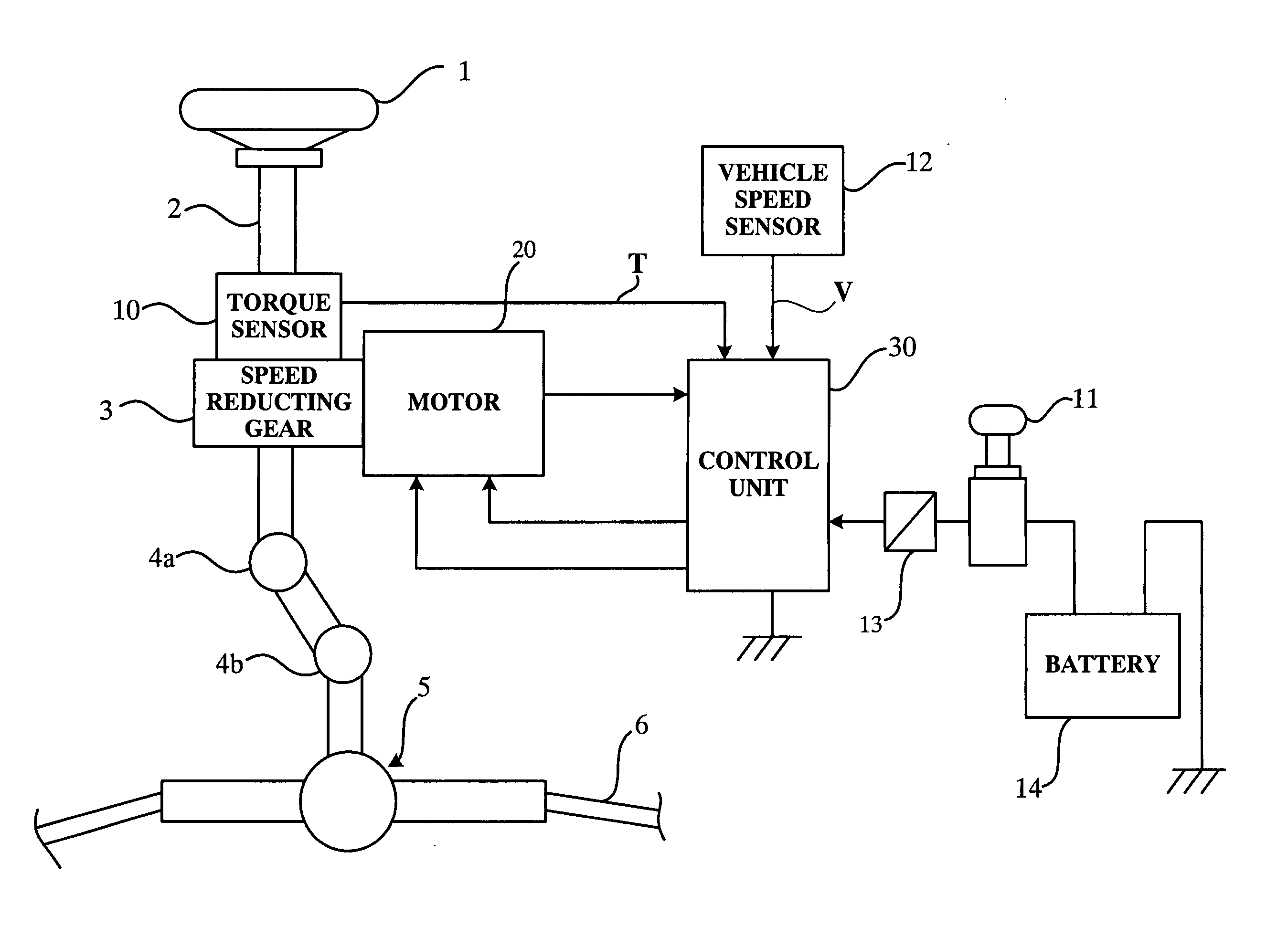
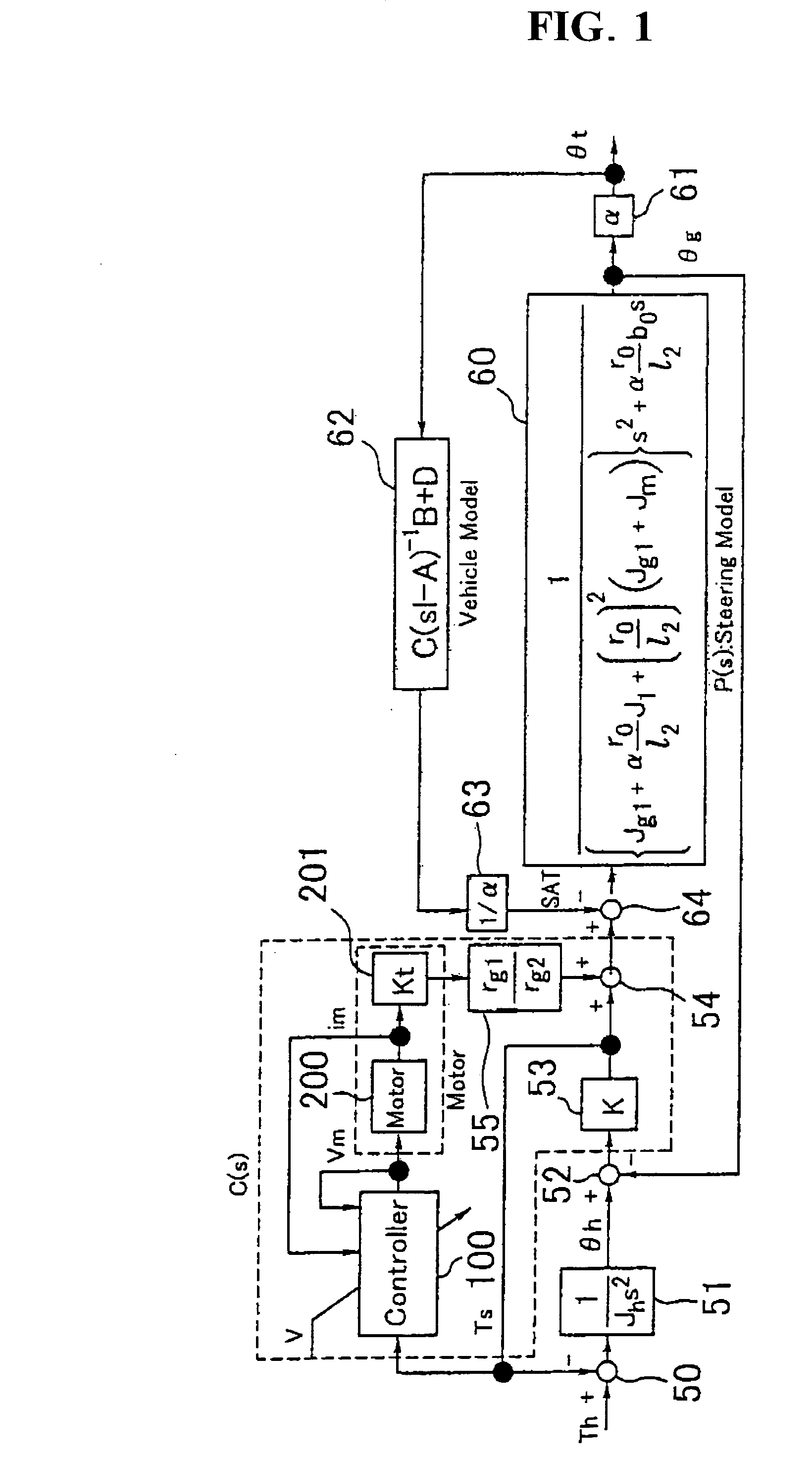
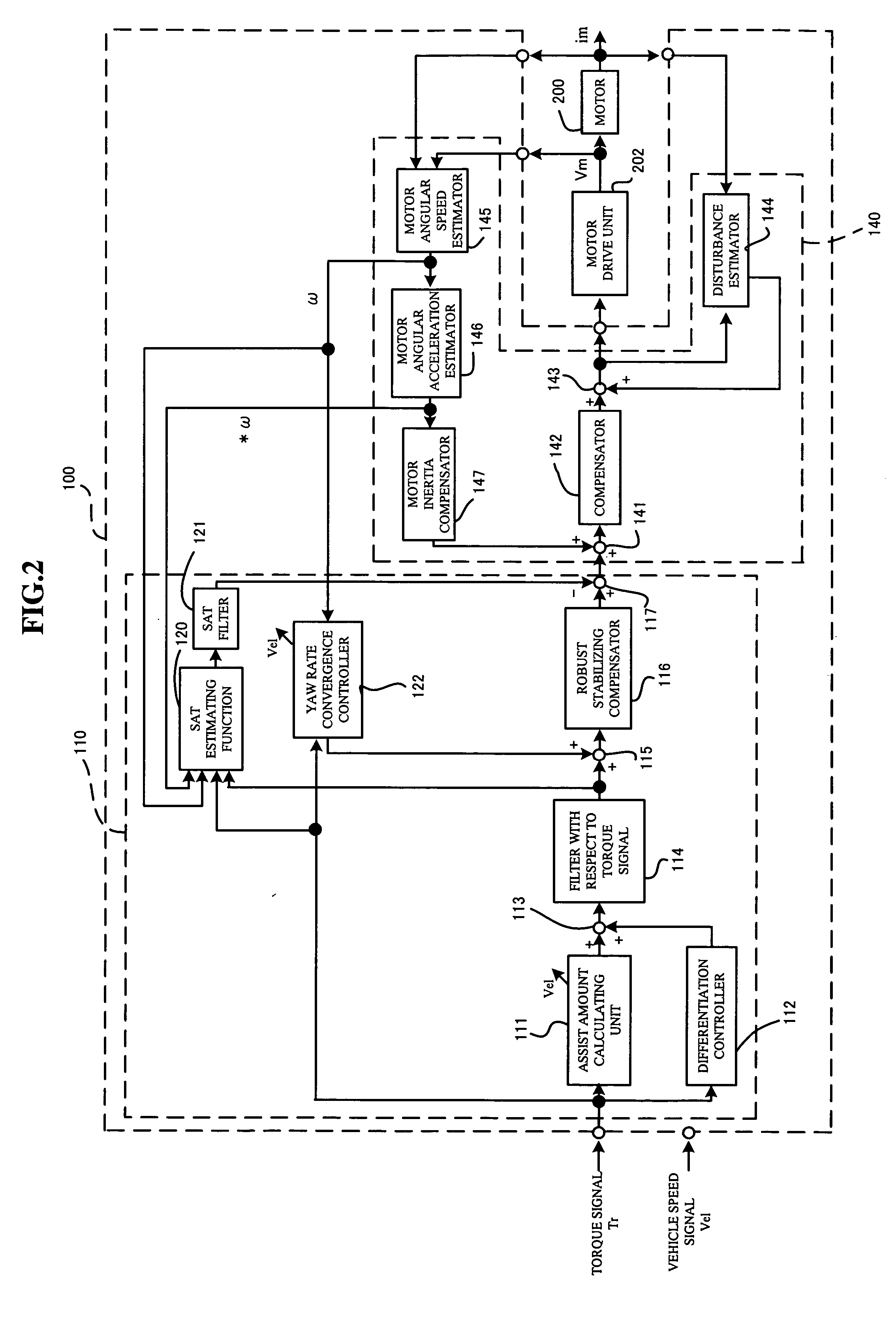
InactiveUS7242161B2Efficient implementationDC motor speed/torque controlSteering initiationsElectric power steeringPower flow
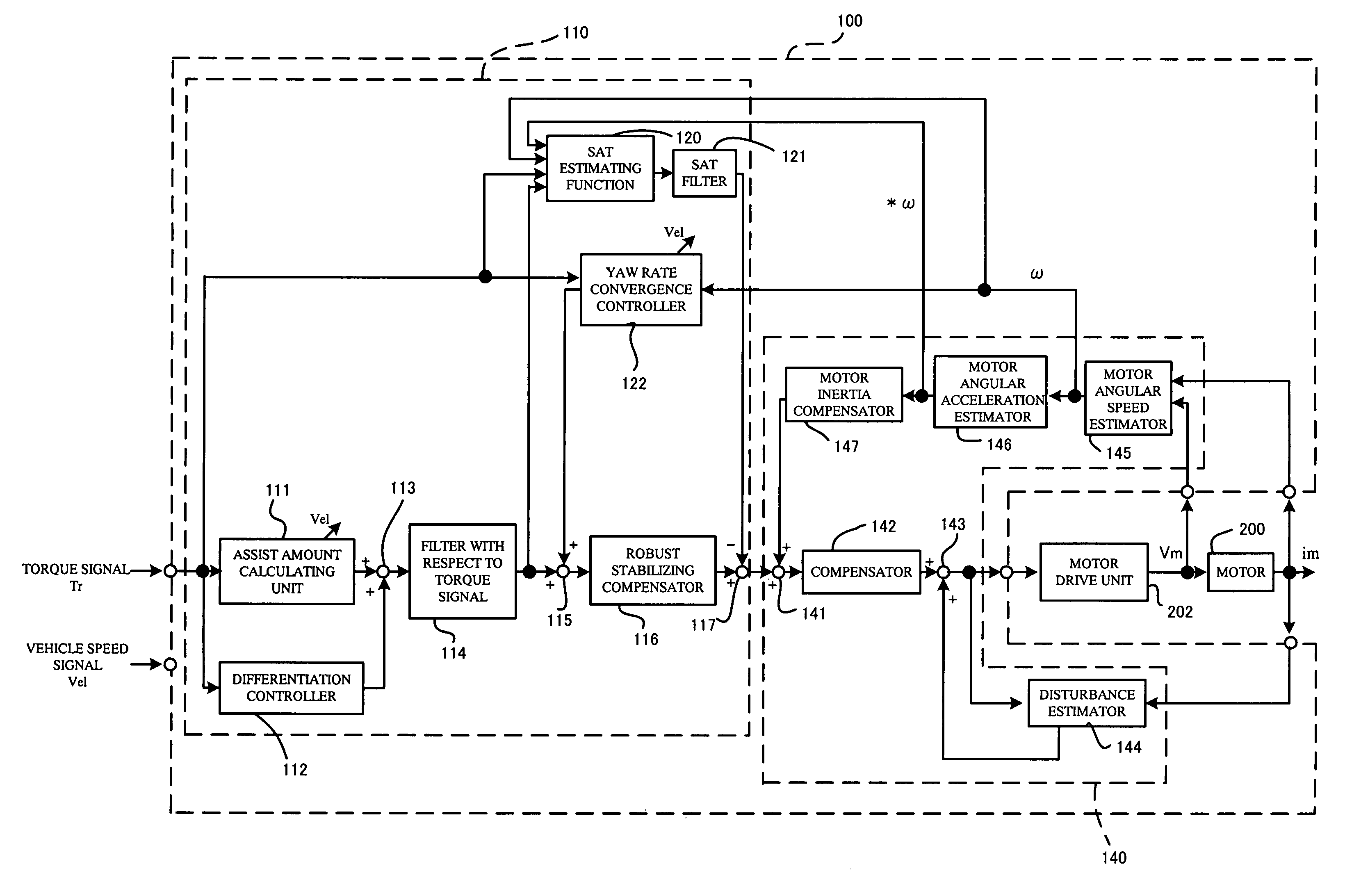
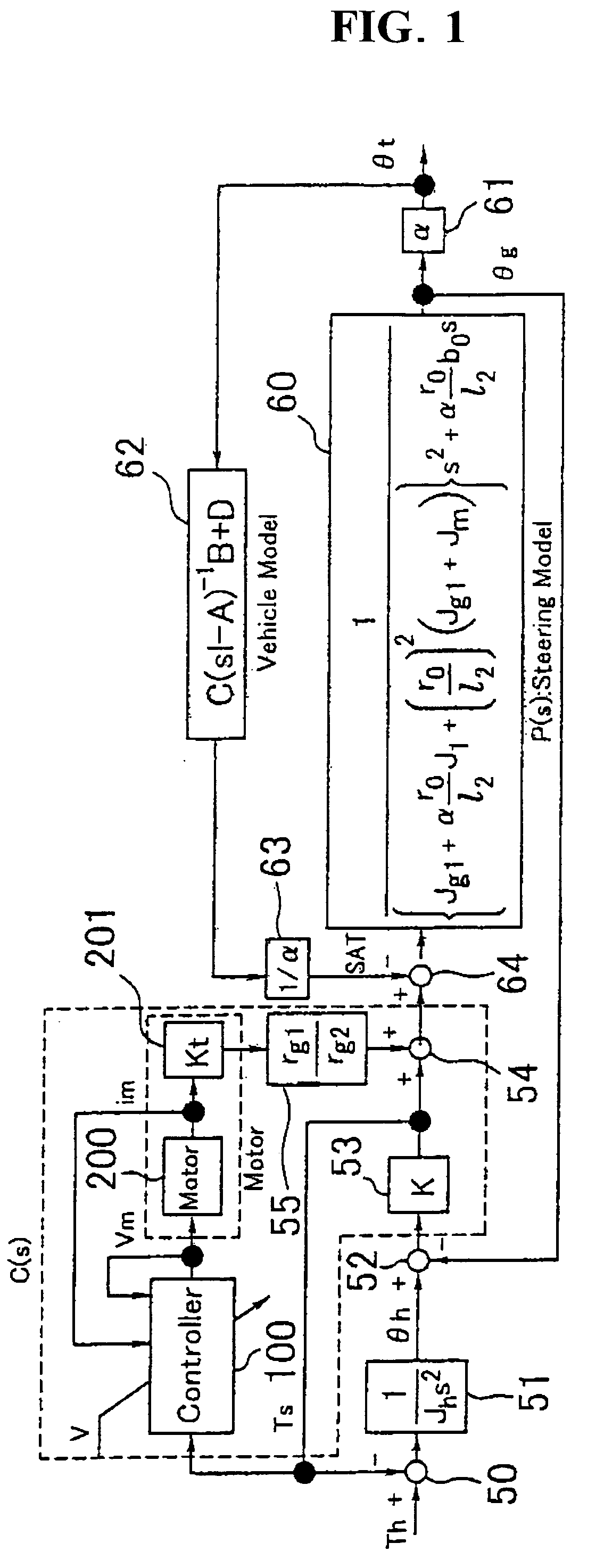
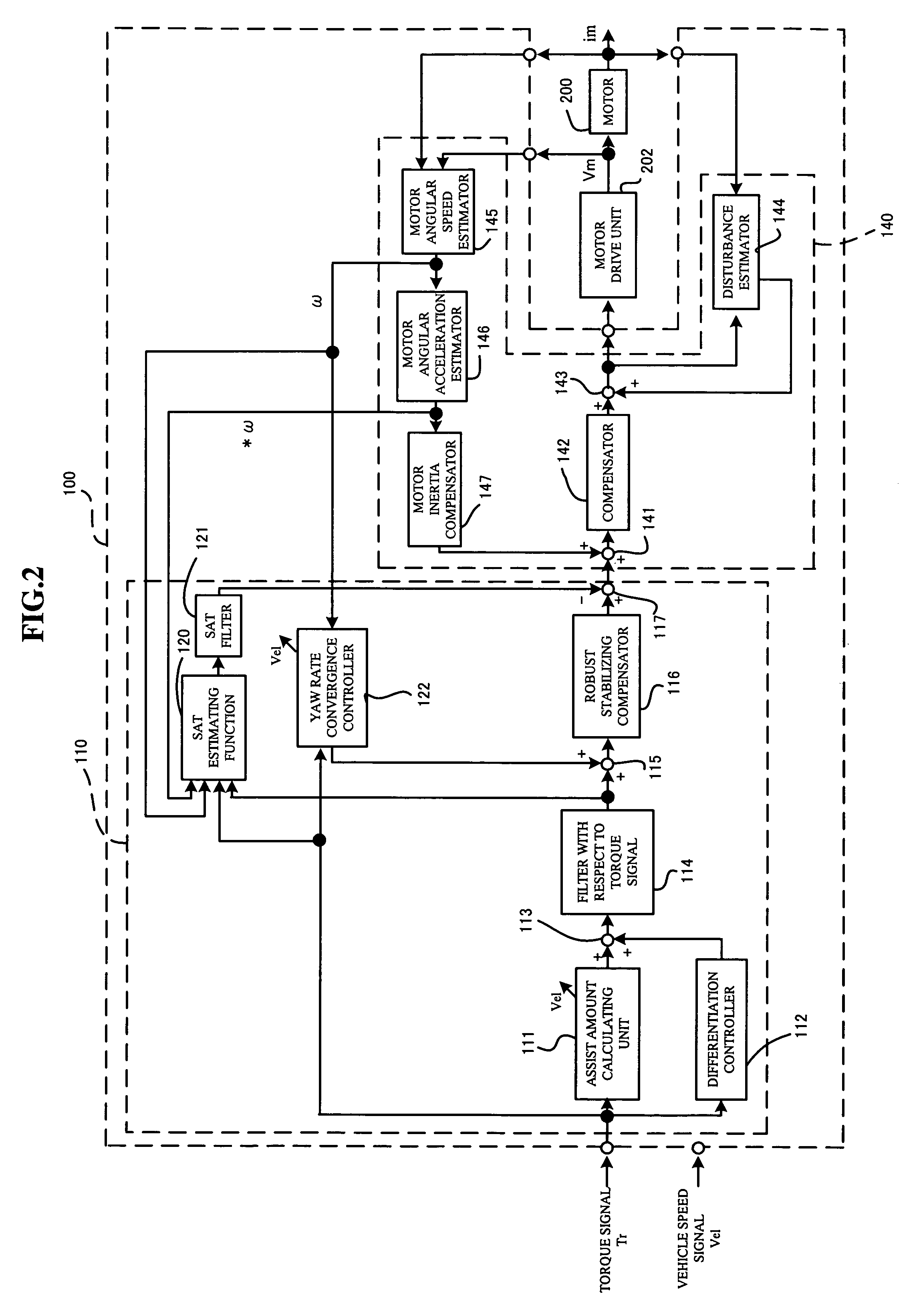
The present invention provides an electric power steering apparatus for controlling a motor based on a current command value calculated from a steering assist command value calculated based on a steering torque generated in a steering shaft and from a current detection value of the motor which gives a steering mechanism a steering assist force. In order to realize ideal road information sensitivity and steering feeling in frequency region at the same time, the electric power steering apparatus comprises a torque filter for processing a torque signal, an SAT estimating function, and an SAT filter for signal-processing SAT information from the SAT estimating function, and the electric power steering apparatus also comprises a control system with two degree of freedom which is capable of independently designing frequency characteristics of steering feeling and road information sensitivity.
Owner:NSK LTD
Context-aware auxiliary display platform and applications
InactiveUS7511682B2Digital data processing detailsProgram control using record carriers with instructionsDisplay deviceContext data
Described is a mechanism by which application programs (or plug-ins) and an auxiliary service adjust the output and / or data available for output on an auxiliary device based on changes detected in the current context of the auxiliary display. Context sensors detect and report changes in context, whereby some action is taken with respect to what information is displayed or can be displayed on the auxiliary display device. Examples of context data that can change include the physical location of the display, detected movement or motion data, presence of a particular user or others, power state, network connectivity status, privacy status and so forth. The auxiliary device can have context as to its position relative to the main display. Information sensitivity levels may be used to specify whether an application program's data can be displayed, based on the perceived sensitivity of the information and the user's current context.
Owner:MICROSOFT TECH LICENSING LLC
Control device for motorized power steering device
ActiveUS20060017413A1Efficient implementationDC motor speed/torque controlDigital data processing detailsElectric power steeringPower flow
The present invention provides an electric power steering apparatus for controlling a motor based on a current command value calculated from a steering assist command value calculated based on a steering torque generated in a steering shaft and from a current detection value of the motor which gives a steering mechanism a steering assist force. In order to realize ideal road information sensitivity and steering feeling in frequency region at the same time, the electric power steering apparatus comprises a torque filter for processing a torque signal, an SAT estimating function, and an SAT filter for signal-processing SAT information from the SAT estimating function, and the electric power steering apparatus also comprises a control system with two degree of freedom which is capable of independently designing frequency characteristics of steering feeling and road information sensitivity.
Owner:NSK LTD
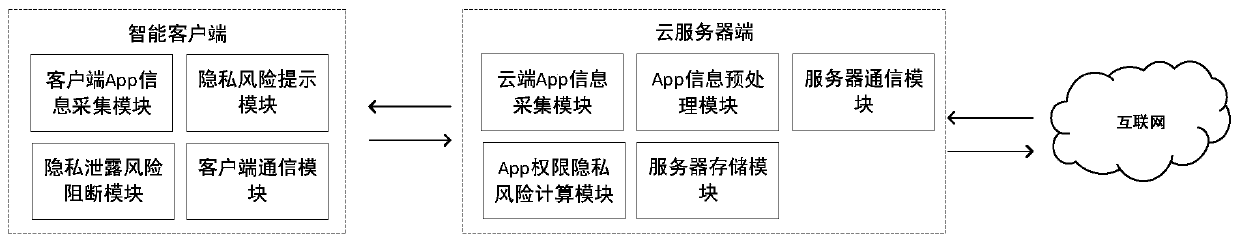
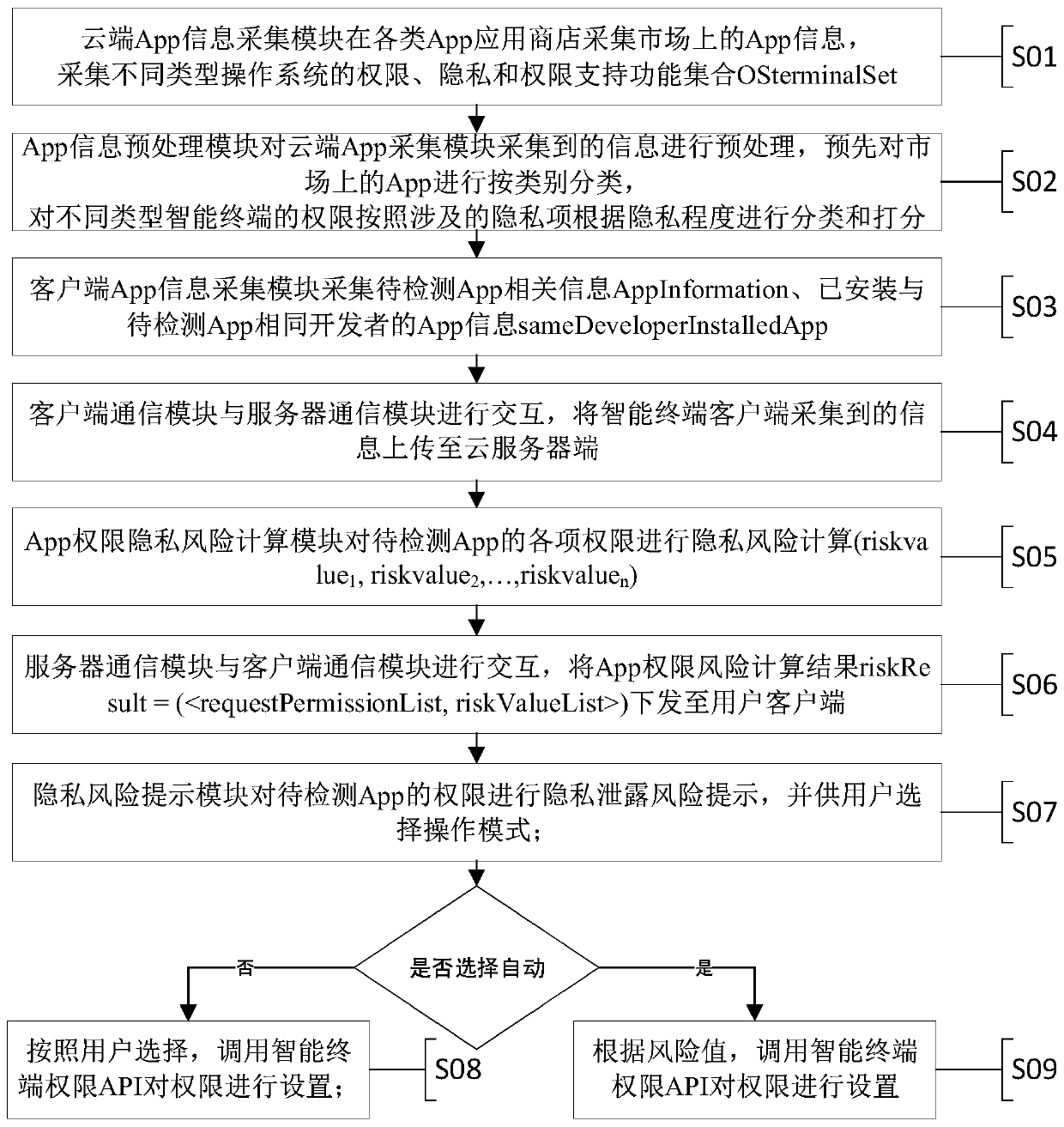
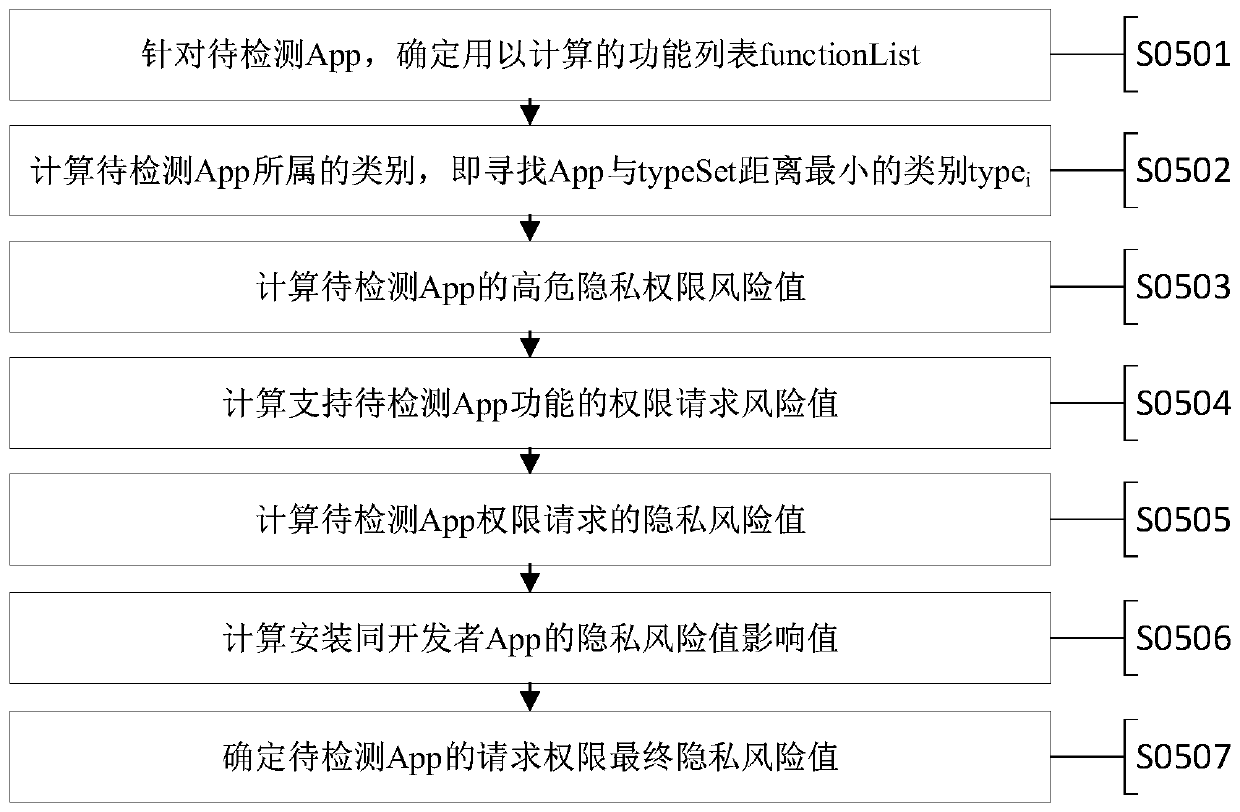
Intelligent terminal App permission privacy risk monitoring and evaluation system and method
ActiveCN110298176APrivacy protectionDigital data protectionPlatform integrity maintainanceComputation complexityRelevant information
The invention discloses an intelligent terminal App permission privacy risk monitoring and evaluation system and method. Aiming to solve the problem of privacy disclosure of a user caused by user permission abuse in the application process of an existing intelligent terminal App and solve the technical problems of large data acquisition amount, high calculation complexity, high implementation difficulty, easy misjudgment and the like in the prior art, the invention provides an intelligent terminal App permission privacy risk detection and evaluation method and a privacy disclosure blocking system, being characterized by collecting an App permission list and related information; calculating permission analysis of an App to be detected, an App of the same kind, an App of the same function and an App of the same developer and privacy information sensitivity of related permissions, so as to provide the privacy disclosure risk evaluation method for the intelligent terminal App permission, and providing an unloading prompt for blocking high-risk App permission or App according to permission privacy disclosure risk grading, so that efficient, convenient and accurate intelligent terminal App permission privacy disclosure risk evaluation and blocking are realized, and the privacy of a user is protected.
Owner:GUIZHOU UNIVERSITY OF FINANCE AND ECONOMICS
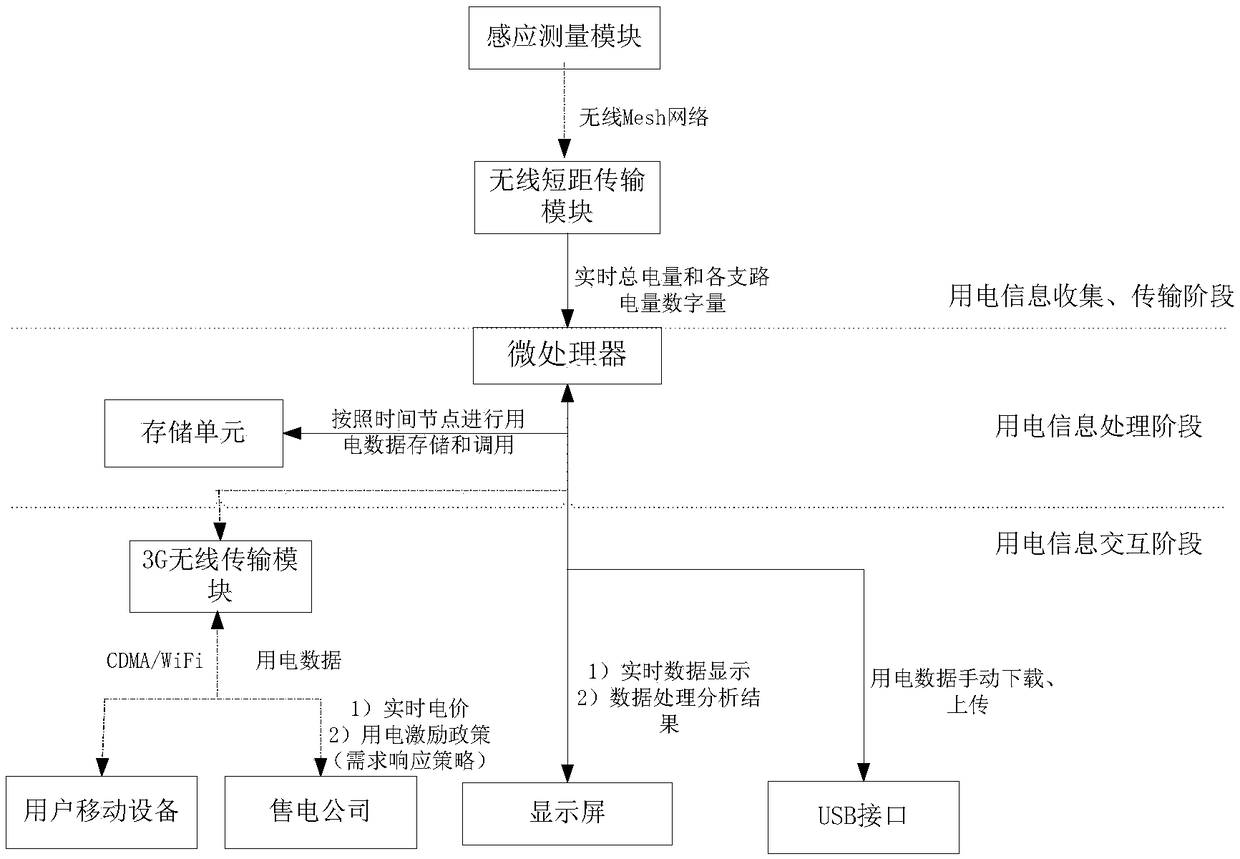
Intelligent power utilization terminal and Intelligent power utilization method based on real-time electricity price
InactiveCN108596358AEasy to moveEasy to chargeTransmission systemsForecastingElectricity priceProgram planning
The present application relates to the technical field of intelligent power utilization terminals, in particular to an intelligent power utilization terminal and an intelligent power utilization method based on real-time electricity price. Metering, storage, processing, analysis and information interaction functions of power utilization information of a user are integrated in a light, simple and plug-and-play smart terminal, so current electricity price and power consumption incentive policies of an electricity sales company are displayed to the user in real time, electricity charges of the user in the future are predicated on the basis of stored power utilization habits of the user, and a power utilization plan targeting the lowest electricity charges or the lowest power consumption is formulated for the client. In this way, the participation degree and information sensitivity of a terminal user in an electricity sales market and in an electricity price mechanism are improved and technical support is provided for future terminal users to participate in the demand response. Meanwhile, power utilization information of the user can be provided as feedback to the electricity sales company, and data support is provided for the electricity sales company to carry out research on user types and power utilization habits to formulate demand response plans and different electricity pricemechanisms.
Owner:YUNNAN POWER GRID CO LTD ELECTRIC POWER RES INST
Device and method for analyzing reputation for objects by data mining
ActiveUS9990356B2Improve reliabilitySemantic analysisUnstructured textual data retrievalMorphemeWeb page
A device for analyzing reputation for objects by data mining is provided. The device includes a big data collector assembly collecting first information from a web page, a text preprocessor assembly analyzing morpheme information from an original text of the first information, an ontology dictionary extender assembly classifying the morpheme information according to each category and extracting an associated word, an object recognizer assembly measuring similarity between the associated word from the morpheme information to recognize a plurality of entity names associated with a first object, an information sensitivity classifier assembly classifying sensitivity of the first information based on a frequency of a sensitive word associated with the first object from the morpheme information, and a risk evaluation modeler assembly deriving a numeric risk value of the first information according to a numeric sensitivity value of the sensitive word and a weight value level for evaluating event importance.
Owner:INST FOR SUSTAINABLE DEV
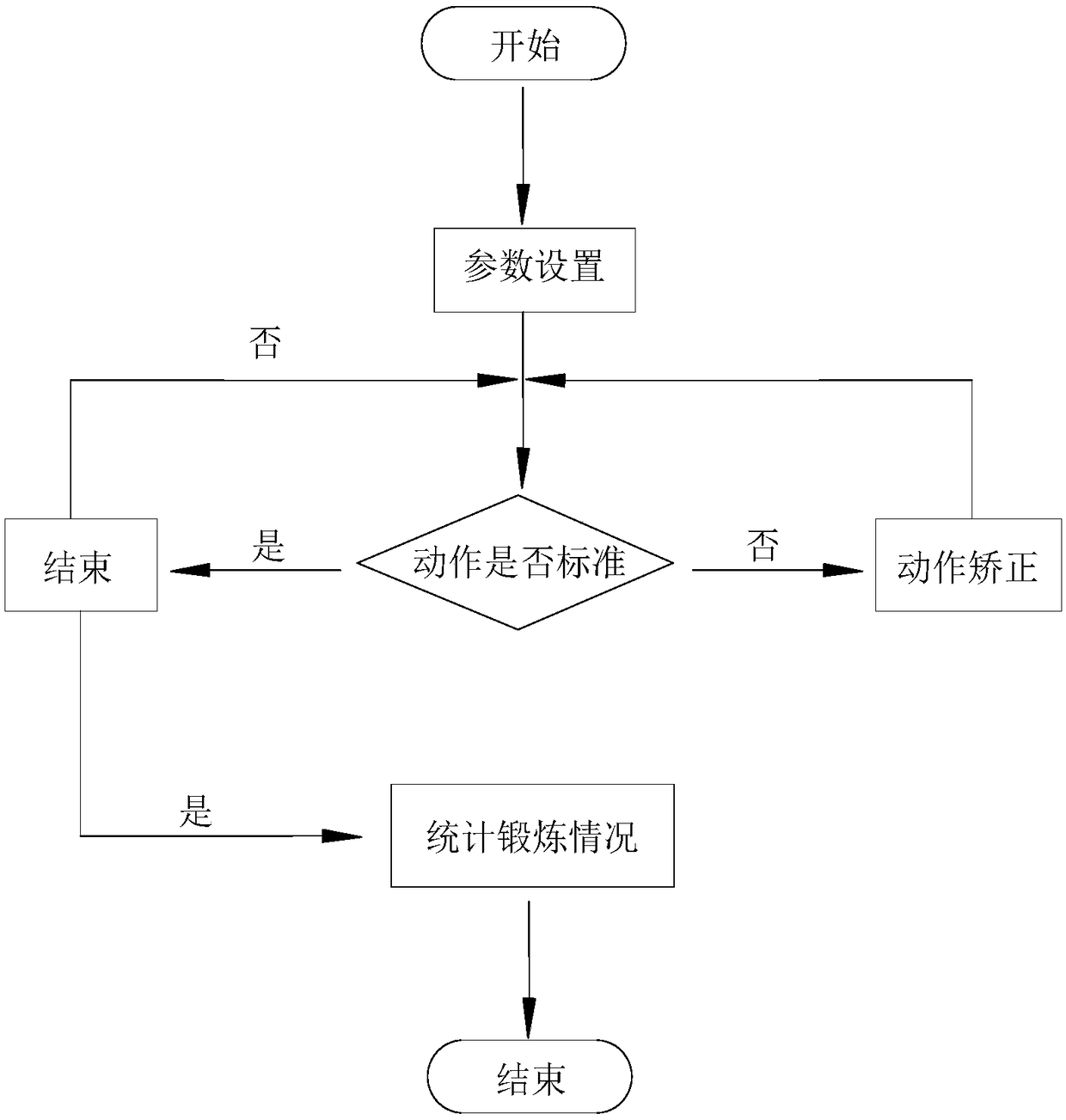
Intelligent fitness equipment
The invention provides intelligent fitness equipment which comprises a body and an intelligent system. The intelligent system is arranged on the body and comprises a control chip, a sensor module andan output module, and the sensor module and the output module are both connected with the control chip; in the intelligent system, the sensor module detects user's fitness action parameters, and the control chip controls the output module to give feedback on whether the fitness action is standard or not to the user and output standard fitness action guidance information. The intelligent fitness equipment has a complete human-machine interaction function system, by combining the advantages of information collection and guided fitness, the fitness process can be more scientifically detected andguided, and the user's fitness condition is automatically checked to provide a scientific reference for the next fitness process and make a personal scientific fitness plan. Besides, the intelligent fitness equipment is guided fitness equipment which does not need to be connected to a mobile phone, and is high in information sensitivity and higher in user-friendliness, convenience and intelligentization.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
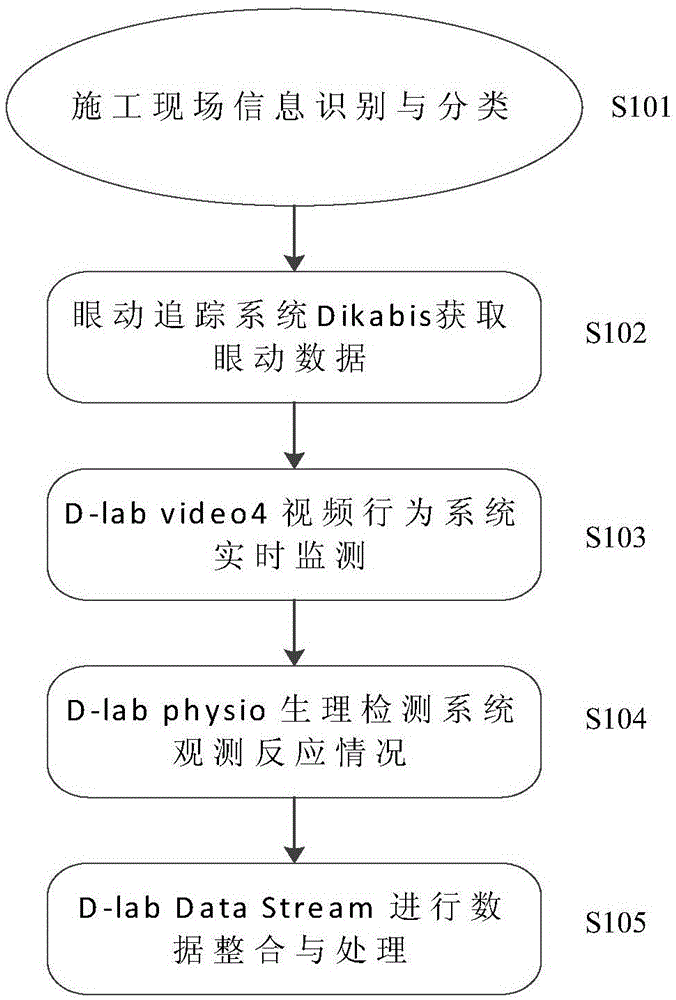
Method for measuring insecurity psychology under interaction effect of construction site multiple information factors by means of behavior data platform
InactiveCN105054950AAccurately reflectInstant responsePsychotechnic devicesHuman behaviorUtilization behavior
The invention discloses a method for measuring insecurity psychology under the interaction effect of construction site multiple information factors by means of a behavior data platform, and relates to the field of human behavior safety science. Firstly, the data statistical material of psychological changes of construction site operating personnel under the interaction effect of multiple information factors is acquired, by means of the interaction of four systems comprising an eye movement tracking system, a video behavior system, a physiology detection and analysis system and an external data acquisition and analysis system, multiple information sensitive factors in the construction site are measured, after many kinds of information is processed and analyzed, a psychological change rule curve is drafted, the threshold of the generation of insecurity psychology of the operating personnel under the interaction effect of construction site multiple information factors is worked out, an early warning boundary region is found out, and finally a computer simulation technology is employed to demonstrate and verify the scientificity and accuracy of the above method. The method for measuring insecurity psychology under the interaction effect of construction site multiple information factors by means of the behavior data platform is characterized by being high in detection efficiency and authenticity.
Owner:TIANJIN UNIVERSITY OF TECHNOLOGY
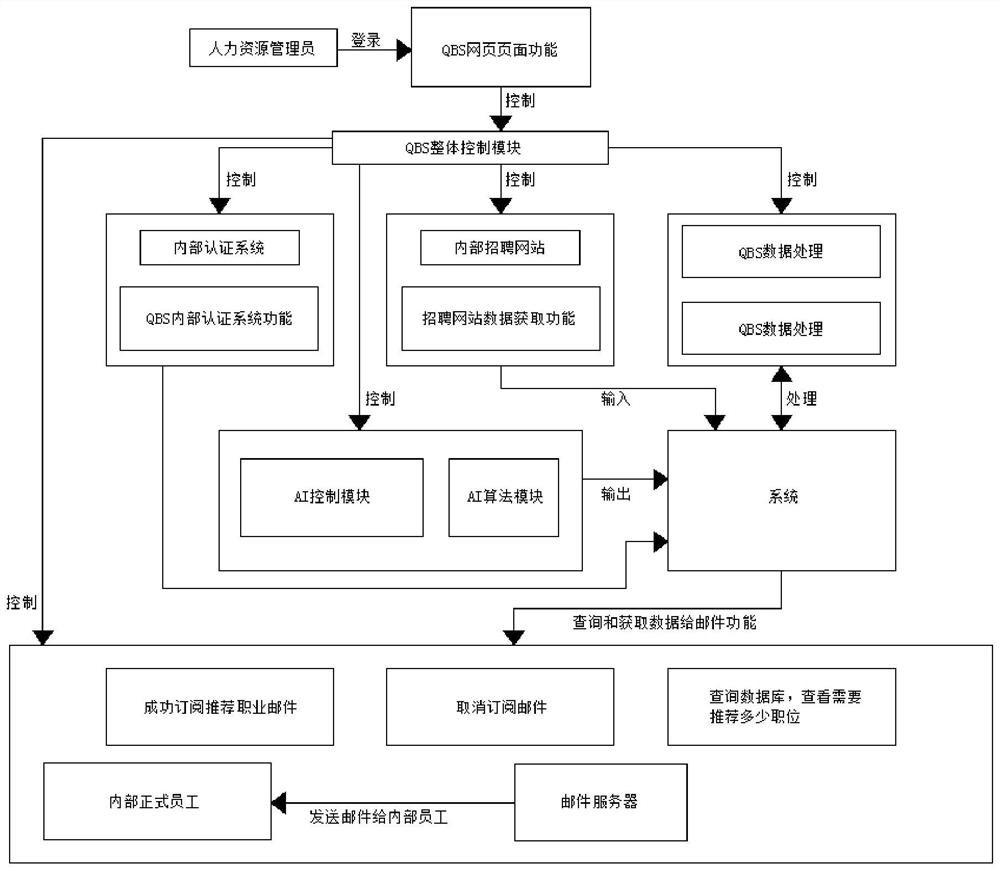
Efficient and accurate internal post recommendation process system
PendingCN114764474AMake up for lack of experienceHighly consistent taxonomySemantic analysisOffice automationFeature extractionData modeling
The invention provides an efficient and accurate internal post recommendation process system. The efficient and accurate internal post recommendation process system comprises the following steps: S1, creating a customized QBSAI model, and constructing artificial intelligence data modeling suitable for a company by inputting two parameters of typical post description and post hierarchy list of each post type of the company; and S2, recommending positions through the constructed QBSAI model. According to the efficient and accurate internal post recommendation process system provided by the invention, the QBS system analyzes post information feature extraction by performing semantic analysis and understanding on each post description, so that effective classification of post information is realized, the accuracy is higher and more reliable, the QBS uses a function information division list of internal human resources of a company and current post information of employees, and the post recommendation efficiency is improved. The problem that the resume cannot be used due to unwilling to upload, unwilling to update, personal information sensitivity and the like is effectively solved.
Owner:汇丰软件开发(广东)有限公司
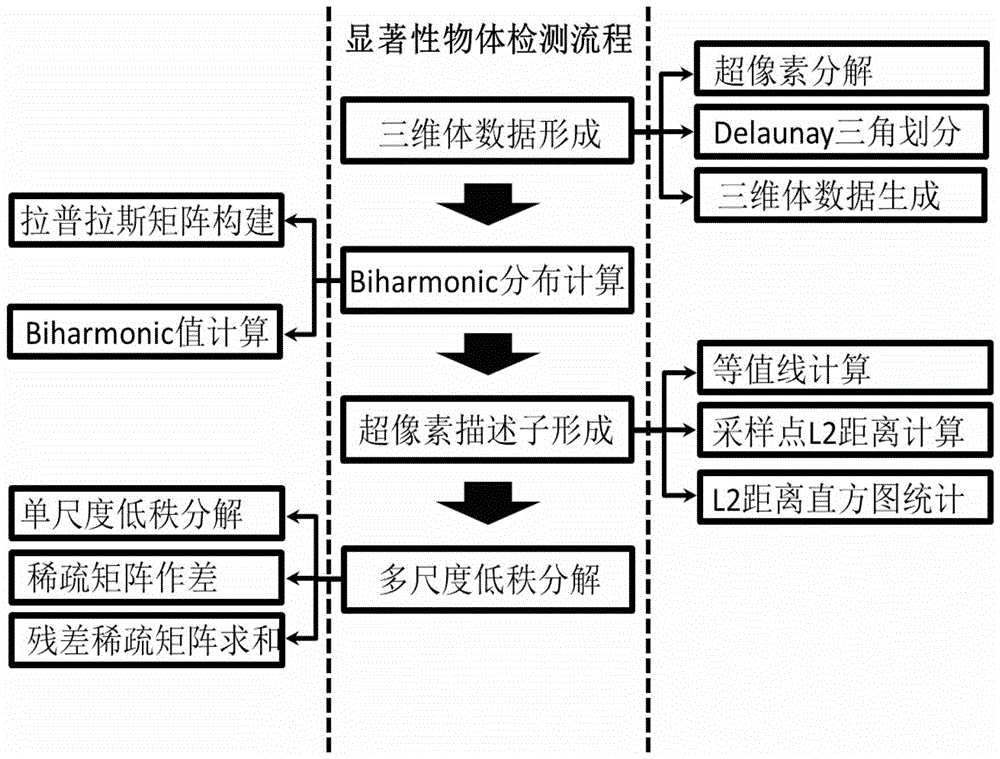
Image salient object detection method based on multi-scale low-rank decomposition and sensitive to structural information
InactiveCN103700091BImprove separabilityComplete detectionImage enhancementImage analysisGraphicsDiffusion
Owner:BEIHANG UNIV
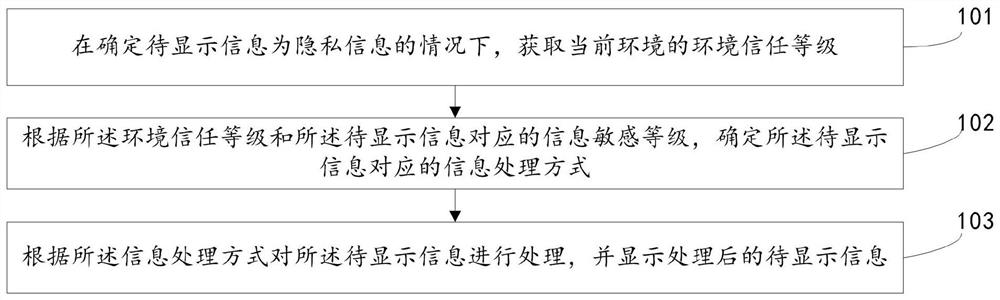
Information display method and device
ActiveCN112104785APrevent leakageCutting costsDigital data protectionSubstation equipmentInformation processingTrust level
The invention discloses an information display method and device, and belongs to the technical field of communication. The method comprises the steps of obtaining an environment trust level of a current environment under the condition that to-be-displayed information is determined to be private information; determining an information processing mode corresponding to the to-be-displayed informationaccording to the environment trust level and the information sensitivity level corresponding to the to-be-displayed information; and processing the to-be-displayed information according to the information processing mode, and displaying the processed to-be-displayed information. The information processing mode is determined by combining the environment trust level and the information sensitivitylevel of the environment where the user is located to process the to-be-displayed information, a screen protection film does not need to be additionally installed, privacy information of the user canbe prevented from being leaked on the basis of reducing expenditure of the user, and user experience is improved.
Owner:VIVO MOBILE COMM CO LTD
Track data acquisition system and method based on privacy perception
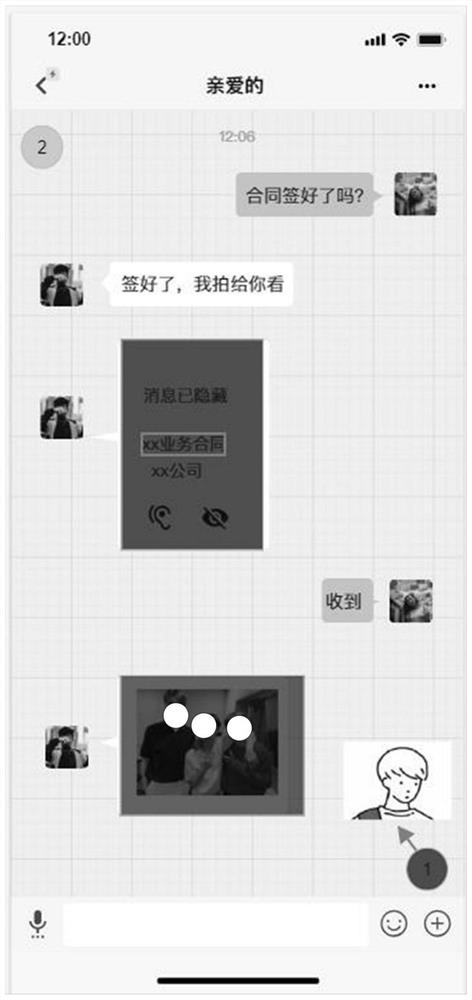
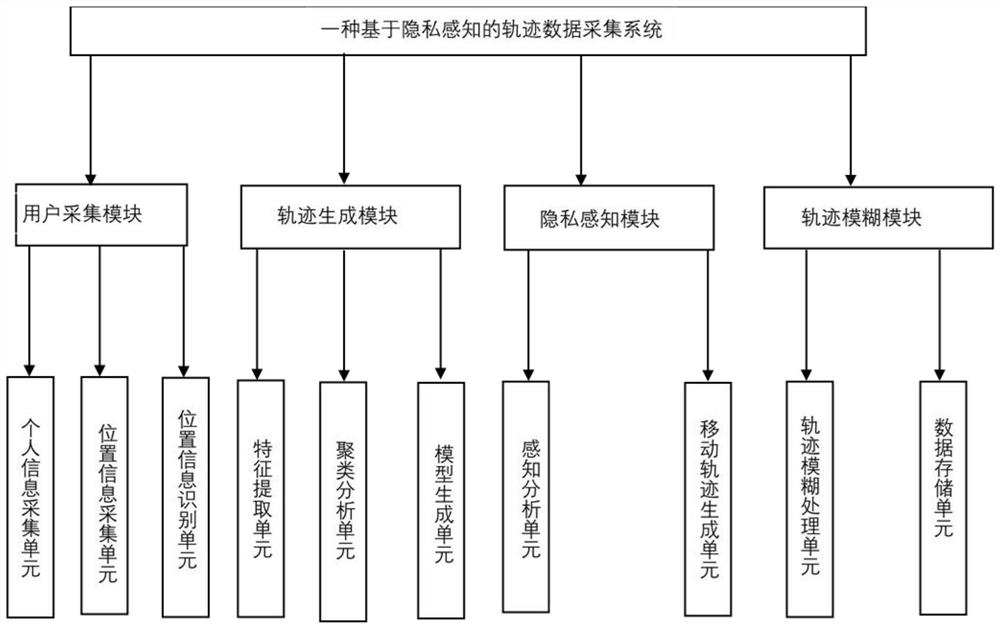
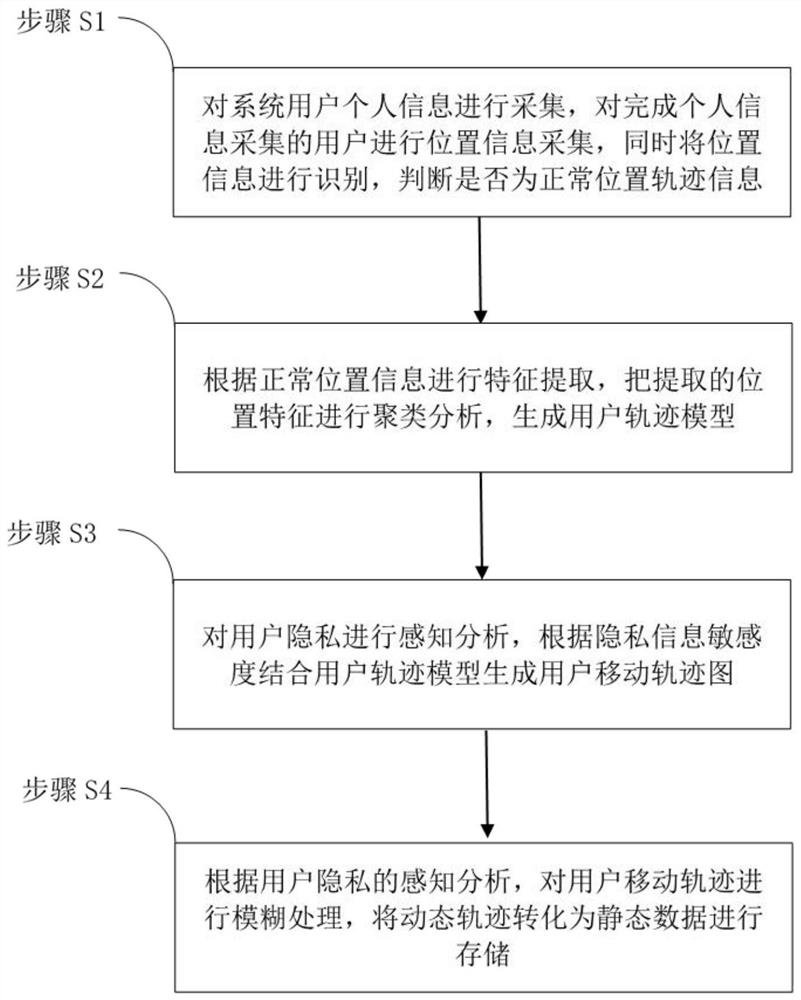
ActiveCN112182658AImprove accuracyImprove certaintyCharacter and pattern recognitionDigital data protectionTracking modelData acquisition
The invention discloses a track data acquisition system based on privacy perception, which comprises a user acquisition module, a track generation module, a privacy perception module and a track fuzzyprotection module. The invention also discloses a track data acquisition method based on privacy perception. Through acquiring system user personal information, position information of the user completing personal information acquisition is acquired, the position information is identified, whether the position information is normal position track information or not is judged, features are extracted according to the normal position information, clustering analysis is conducted on the extracted position features, a user track model is generated, perception analysis on user privacy is carried out, a user movement track diagram is generated according to privacy information sensitivity in combination with a user track model, fuzzy processing on a user movement track is carried out according toprivacy perception analysis, and a dynamic track is converted into static data for storage, thereby providing a data acquisition method with high safety and high operability, and providing a good reference basis.
Owner:钱才英
Non-contact conversation confidence rate test system and method
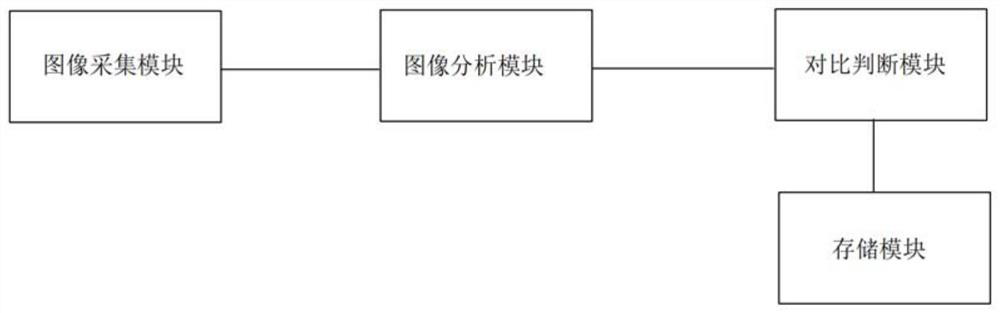
PendingCN112932485AImprove reliabilityImprove securityTelevision system detailsCharacter and pattern recognitionVideo imageInformation sensitivity
The embodiment of the invention discloses a non-contact conversation confidence rate test system and method. The system comprises an image collection module which is used for continuously collecting the vibration of tiny muscles of the face, neck and other parts of the body of a to-be-tested person and the overall change of the body, and then obtaining video image information; an image analysis module is used for obtaining vibration parameters of the to-be-tested person according to the pixel point vibration frequencies and amplitudes of the multiple frames of images continuously collected by the image collection module; a storage module is used for storing standard parameters reflecting psychological and physiological states and emotion changes; a comparison and judgment module is used for comparing the vibration parameters of the to-be-tested person with standard parameters to obtain a physiological reaction change index of the to-be-tested person and further obtain a lie index reflecting the credibility of the statement content of the to-be-tested person. The embodiment of the invention provides the non-contact conversation confidence rate test system and the non-contact conversation confidence rate test method, which are used for solving the problem of poor sensitivity and reliability of non-contact equipment or psychophysiological information lack in the prior art.
Owner:金纪高科智能科技(北京)有限公司
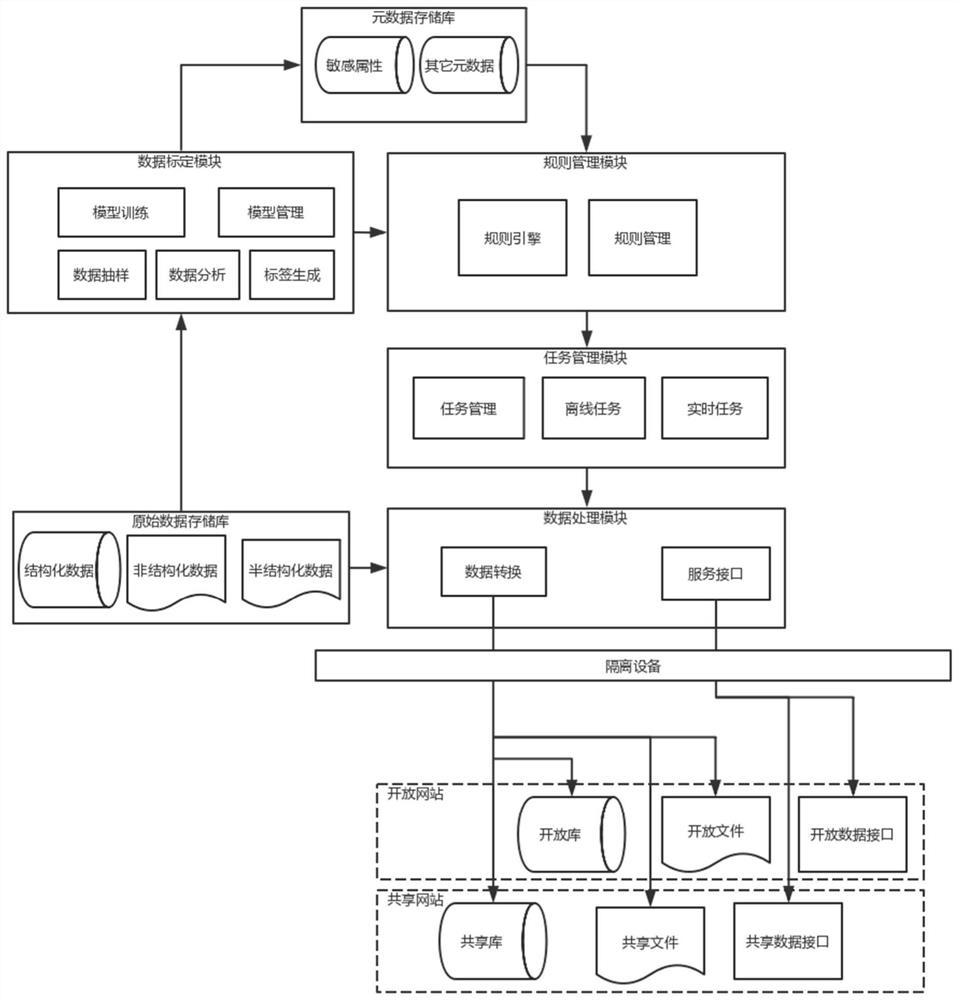
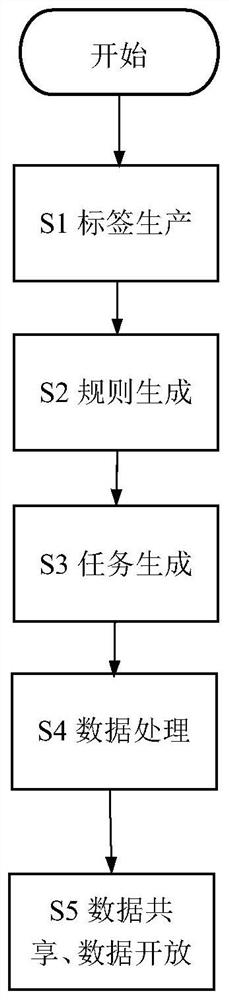
Data sharing and opening method and system for preventing sensitive information from being leaked
The invention discloses a data sharing and opening method and system for preventing sensitive information from being leaked. The system comprises an original data storage library, a metadata storage library, a data calibration module, a task management module, a data processing module, a data sharing website and a data opening website. The method comprises the following steps: identifying and calibrating information sensitivity contained in original data; generating a data processing rule according to the calibration result; generating a data processing task according to the data processing rule; executing a processing task to process sensitive information contained in the original data; and providing data sharing and open services to the outside based on the processed data. According to the method and the system, the sensitive information in the data can be effectively identified, and the converted data can be automatically extracted to the physically isolated shared library and open library to provide data service externally or provide data sharing open service externally in the form of a data service interface, so that the sensitive information can be effectively prevented from being leaked, and the treatment efficiency is extremely high.
Owner:NANJING LES CYBERSECURITY & INFORMATION TECH RES INST CO LTD
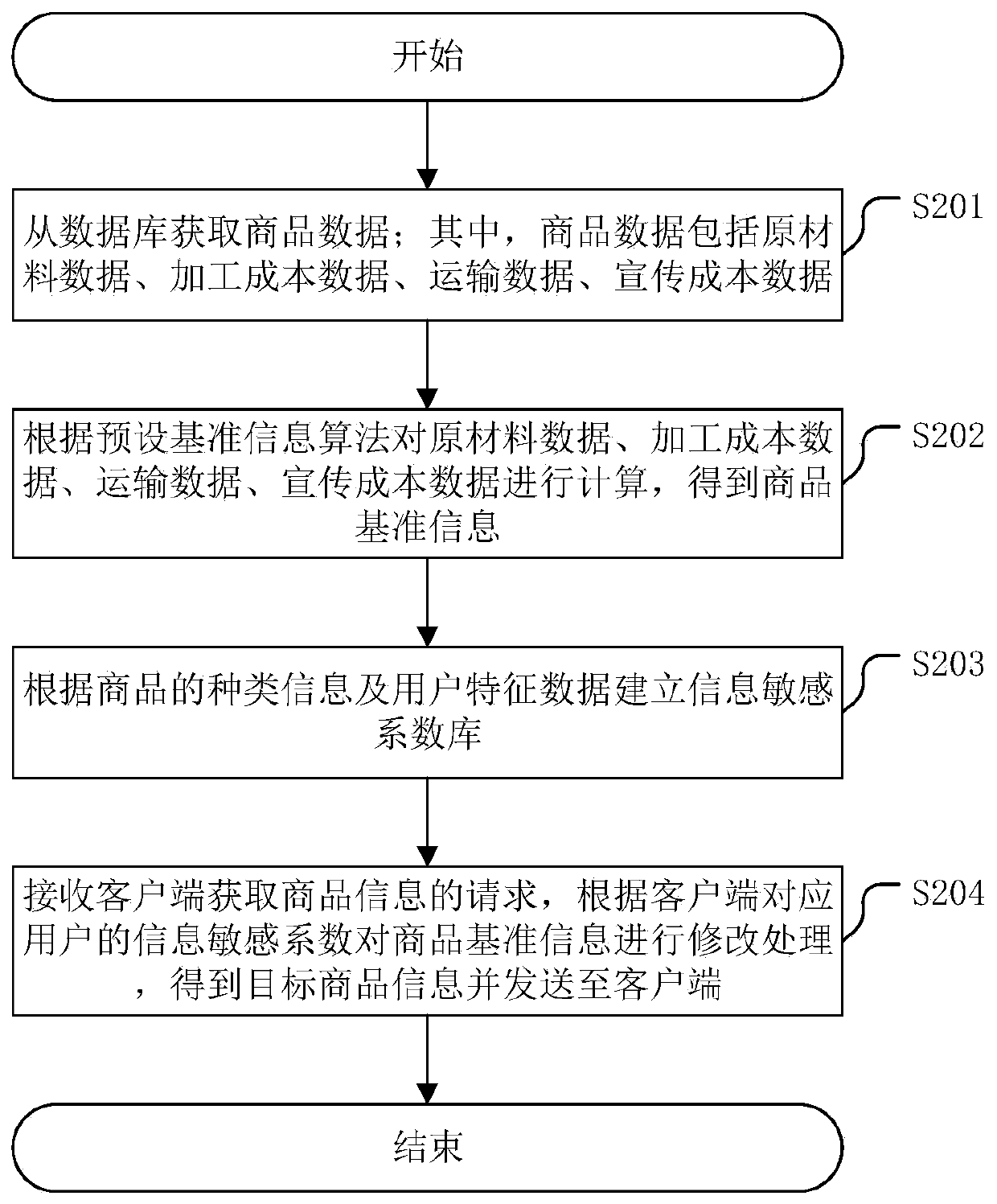
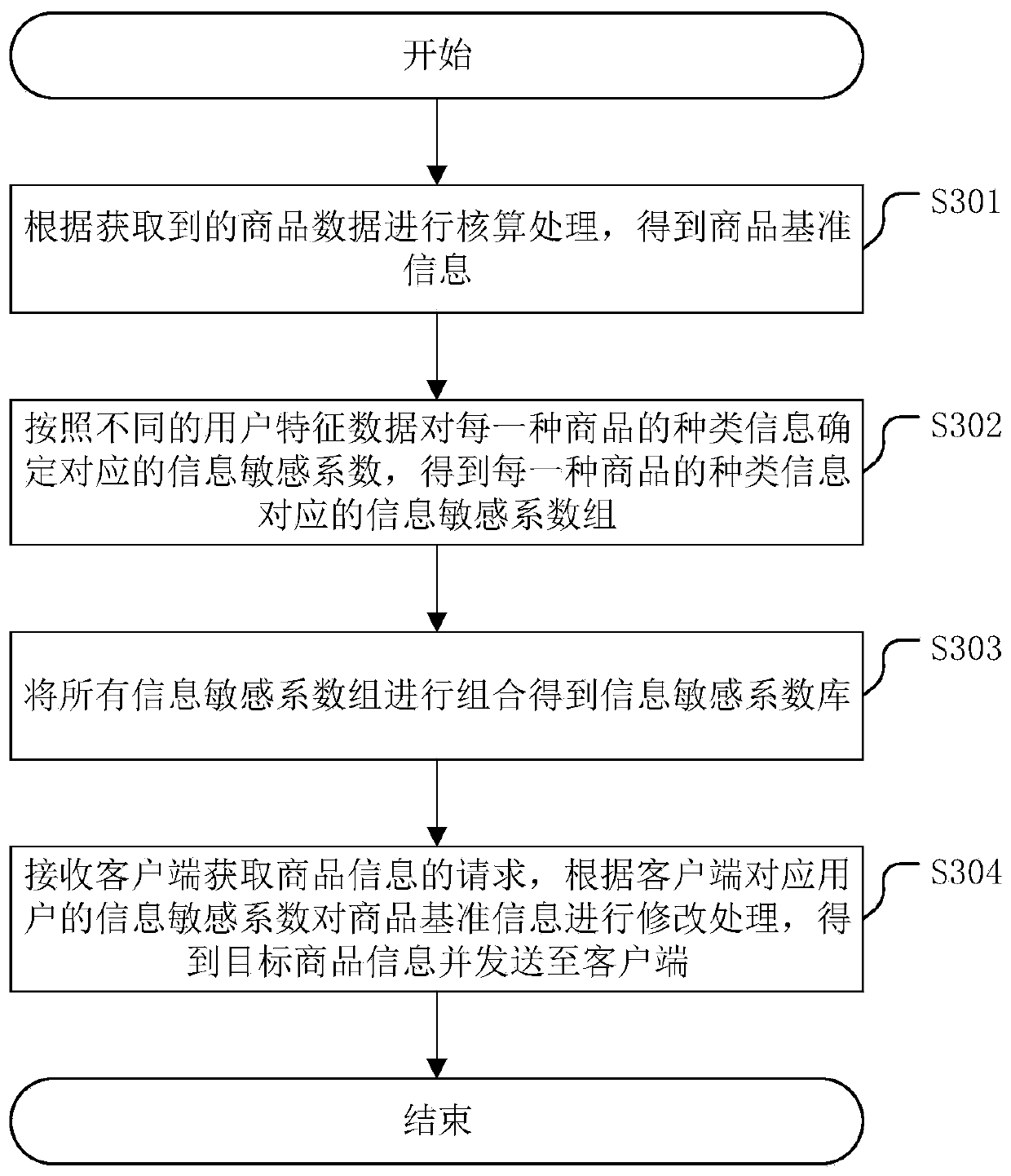
Commodity information adjusting method and device, server and medium
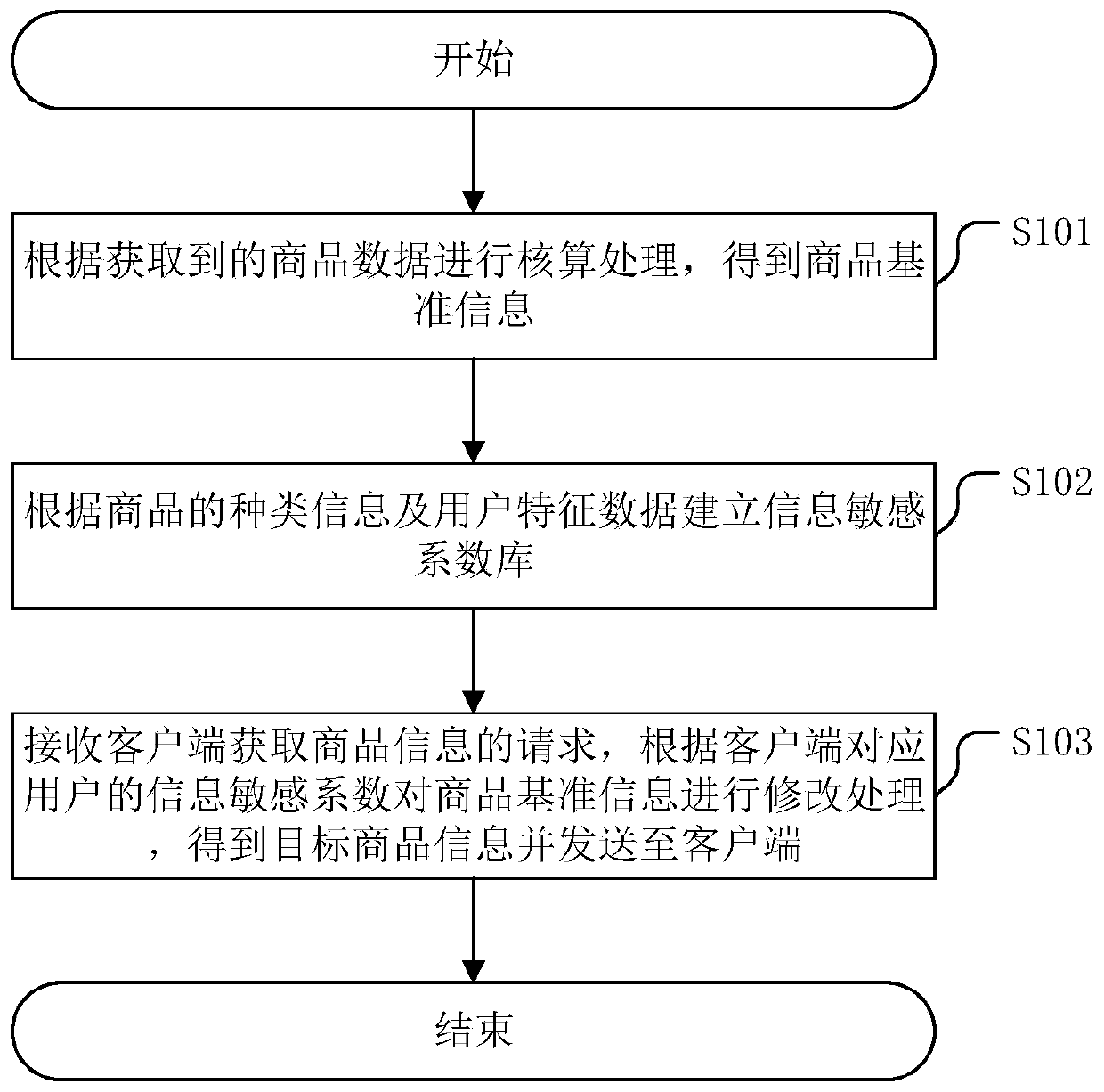
PendingCN111563780AGood modification effectImprove modification efficiencyMarket predictionsBuying/selling/leasing transactionsE-commerceData mining
The invention discloses a commodity information adjustment method, which comprises the steps of performing accounting processing according to acquired commodity data to obtain commodity reference information; establishing an information sensitivity coefficient library according to the type information of the commodity and the user characteristic data; and receiving a request of the client for obtaining the commodity information, modifying the commodity reference information according to the information sensitivity coefficient of the user corresponding to the client to obtain target commodity information, and sending the target commodity information to the client. The commodity reference information is modified through the established information sensitivity coefficient library, so that anautomatic modification mode is realized, the commodity information modification efficiency is improved, and the transmission efficiency and real-time performance of the commodity information in the e-commerce network are kept. The invention further discloses a commodity information adjusting device, a server and a computer readable storage medium, which have the above beneficial effects.
Owner:LAUNCH TECH CO LTD
A method of measuring unsafe psychology under the interaction of multiple information factors at the construction site using a behavioral data platform
The invention discloses a method for measuring unsafe psychology under the interaction of multiple information factors at a construction site by using a behavioral data platform, which relates to the field of human behavior safety science, and first collects the psychological changes of relevant construction site workers under the interaction of multiple information factors The statistical data of the data, using the interaction between the four systems of eye movement tracking system, video behavior system, physiological detection and analysis system, and external data collection and analysis system, is used to measure the multi-information sensitive factors in the construction site, and the multi-category After the information is processed and analyzed, the psychological change curve is drawn, the threshold value of unsafe psychology produced by the operators under the interaction of multiple information on the construction site is calculated, and the warning boundary area is found, and finally the scientificity of the method is verified by computer simulation technology drills. sex and accuracy. The method has the characteristics of high detection efficiency and strong authenticity.
Owner:TIANJIN UNIVERSITY OF TECHNOLOGY
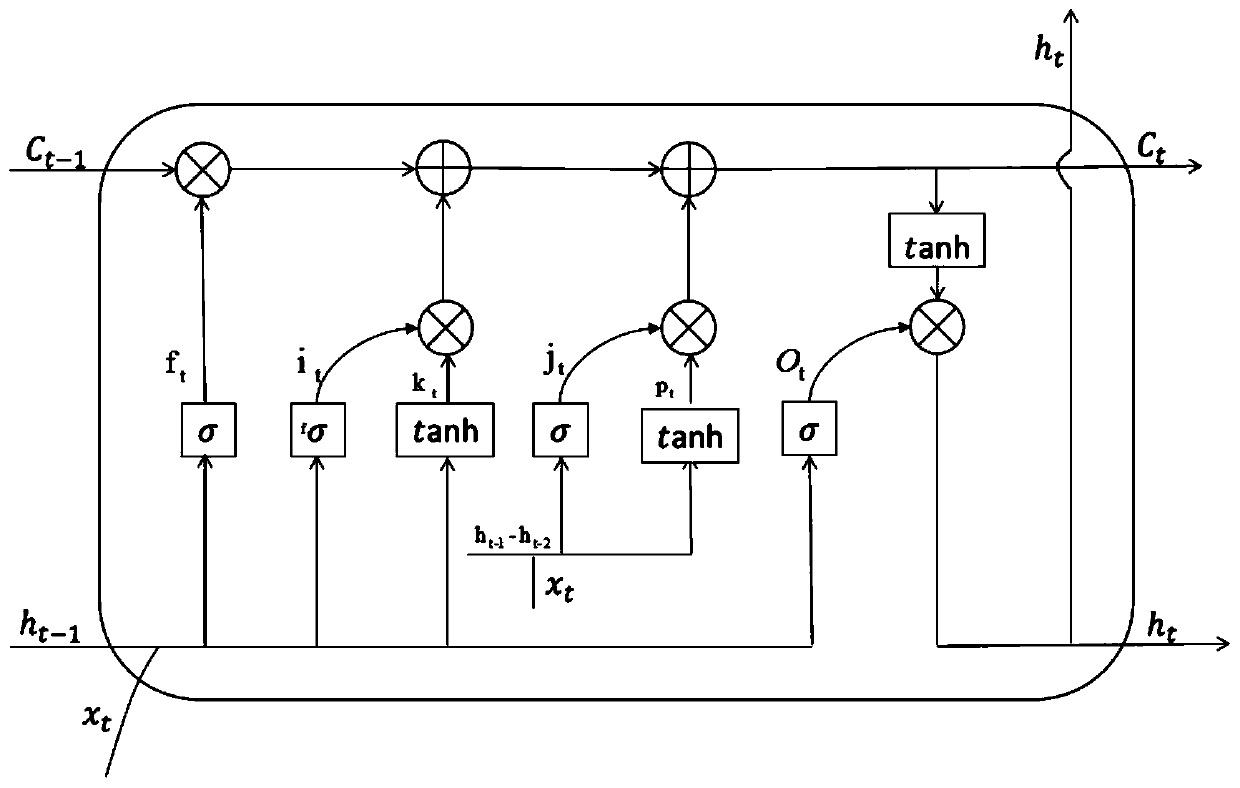
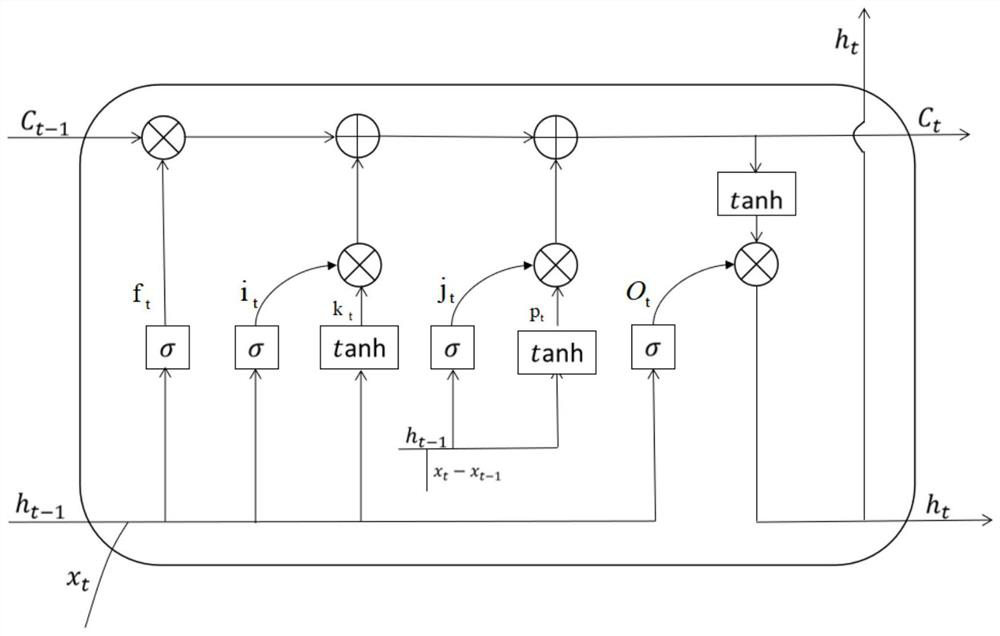
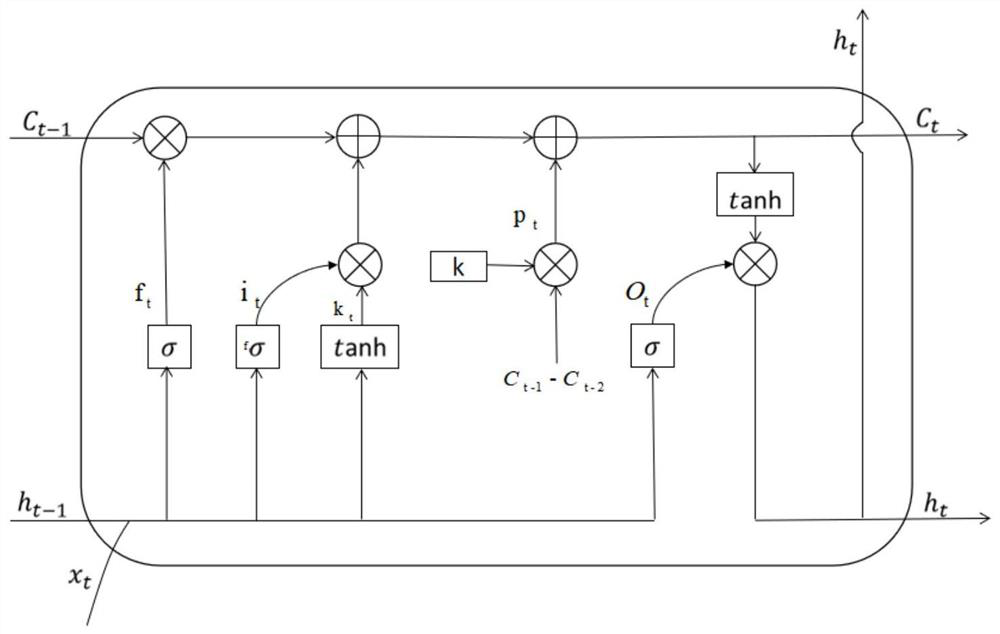
Sensitive long-term and short-term memory method based on output variation differentiation
ActiveCN110472726AIncreased sensitivityImprove responseNeural architecturesNeural learning methodsTemporal informationShort-term memory
The invention discloses a sensitive long-term and short-term memory method based on output variation differentiation. The objective of the invention is to improve the response capability of a traditional LSTM neural network to short-time information. According to the method, the neural unit of the long-term and short-term memory network with increased information sensitivity is added, so that theresponse capability of the network to short-term information can be well improved. The application real-time performance of the network is improved. More perfect real-time analysis can be carried out.Micro-actions and other contents can be further analyzed. The application value is improved.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
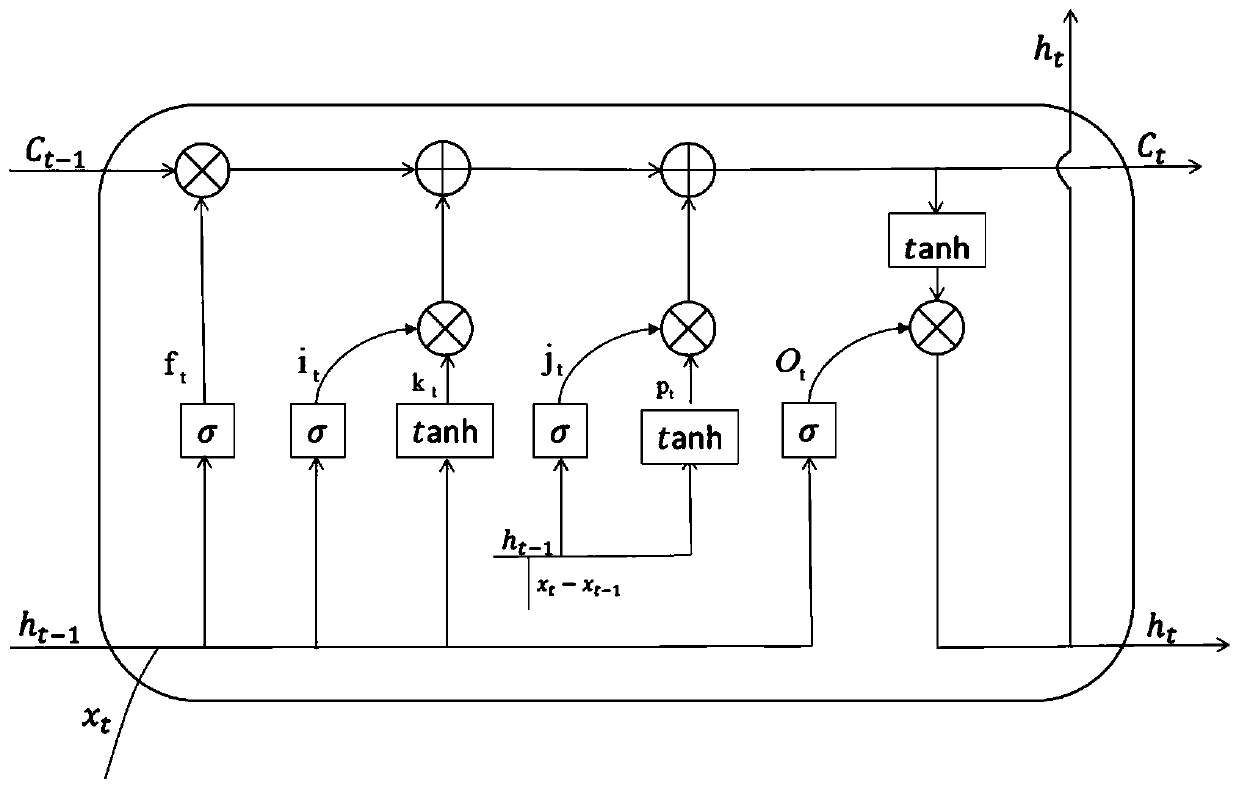
Sensitive long-term and short-term memory method based on input variation differentiation
ActiveCN110390386AIncreased sensitivityImprove responseCharacter and pattern recognitionNeural architecturesTemporal informationShort-term memory
The invention discloses a sensitive long-term and short-term memory method based on input variation differentiation. In order to improve the response capability of a traditional LSTM neural network toshort-time information, the neural unit of the long-term and short-term memory network with information sensitivity is added, so that the response capability of the network to short-term informationcan be well improved, the application real-time performance of the network is improved, more perfect real-time analysis can be carried out, micro-actions and other contents can be further analyzed, and the application value is improved.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
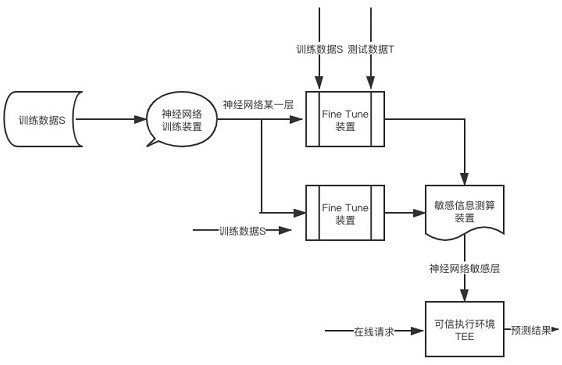
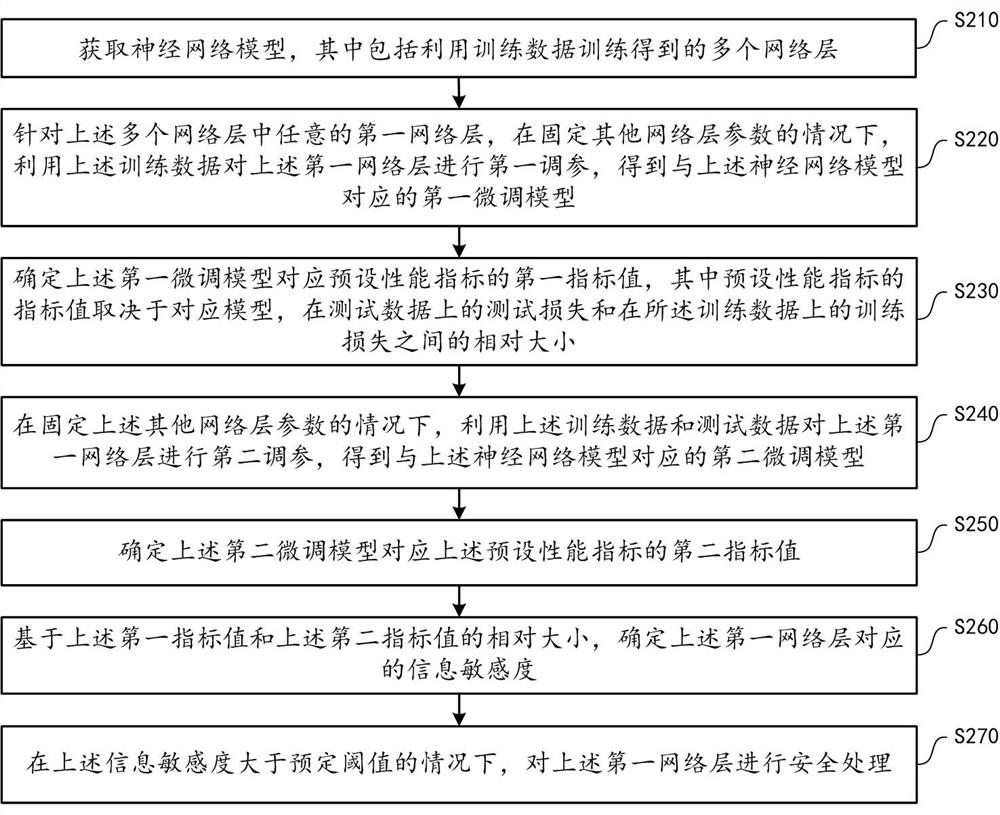
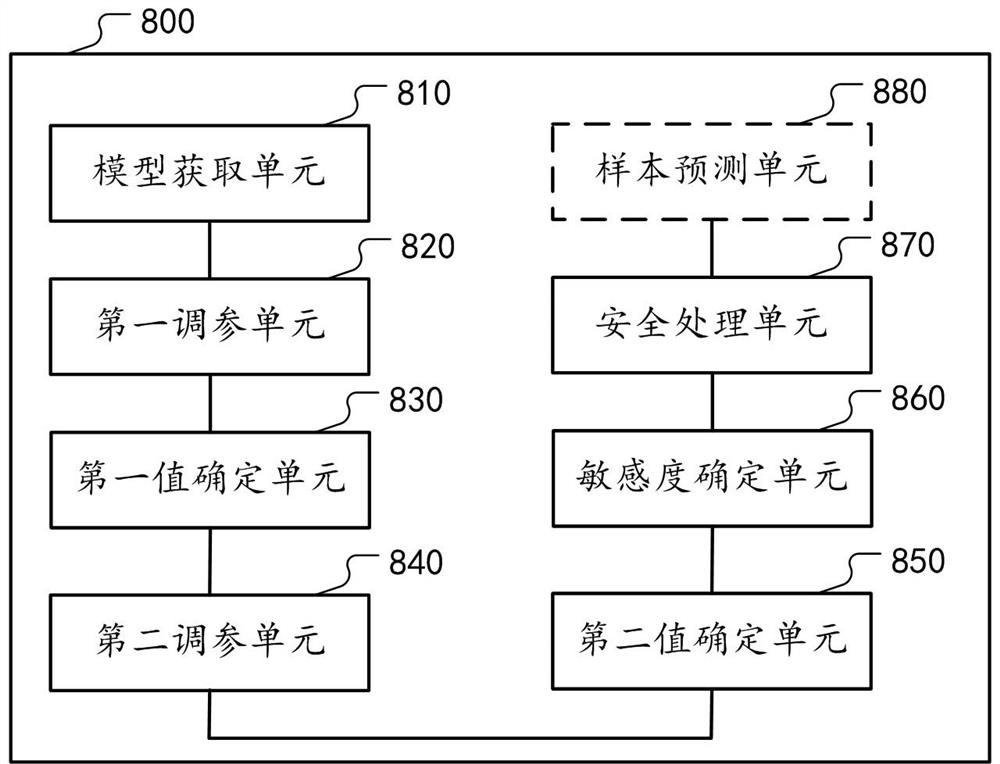
Method and device for protecting safety of neural network model
ActiveCN112948836AGuaranteed uptime performance and efficiencyReduce resource consumptionPlatform integrity maintainanceResourcesEngineeringNetwork model
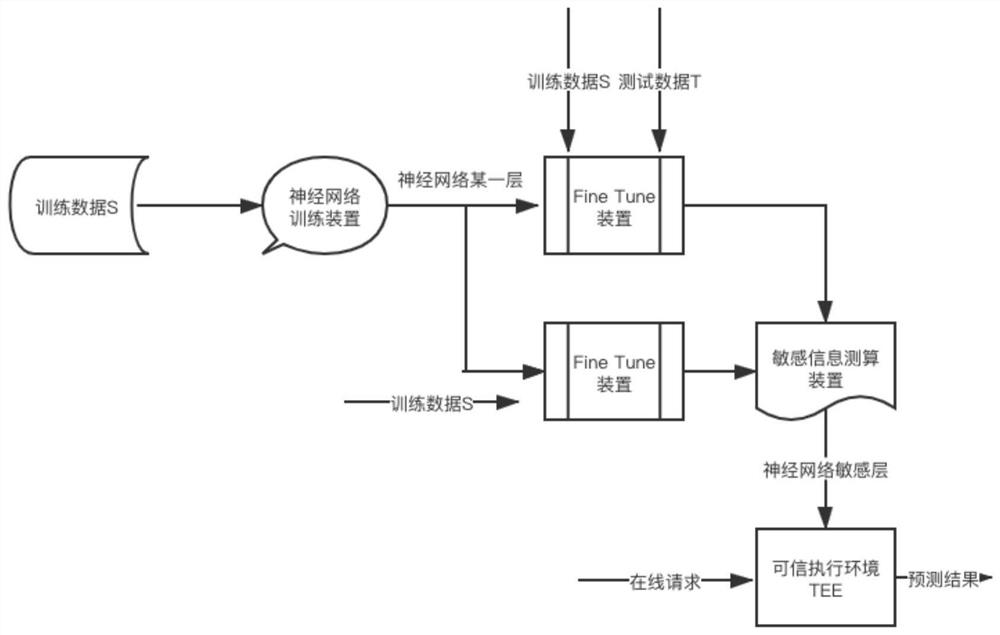
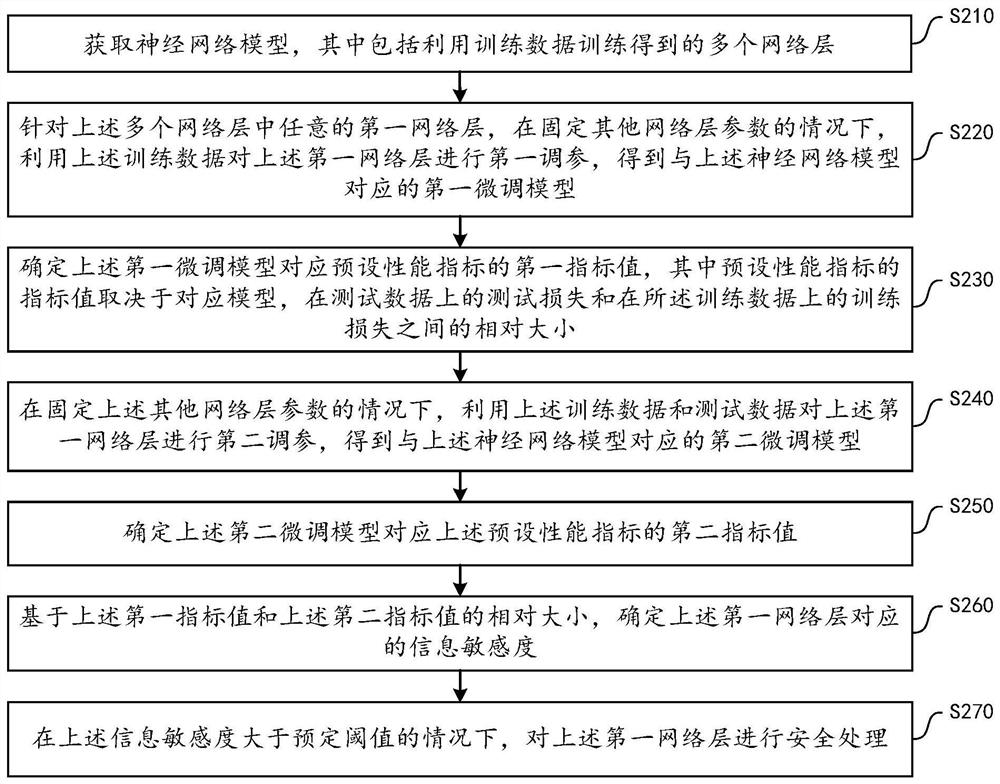
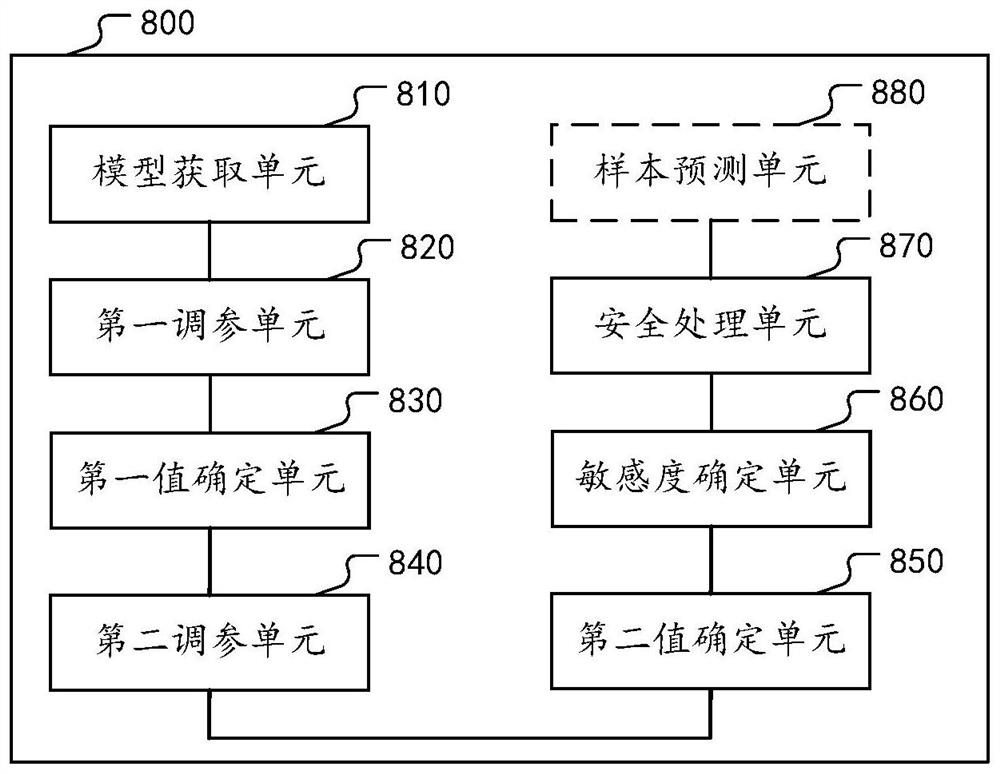
The embodiment of the invention provides a method for protecting the safety of a neural network model, and the method comprises the steps: obtaining a neural network model which comprises a plurality of network layers obtained through training of training data; for any first network layer, under the condition that parameters of other network layers are fixed, performing first parameter adjustment on the first network layer by using the training data to obtain a first fine adjustment model; determining a first index value of a preset performance index corresponding to the first fine tuning model, wherein the index value of the preset performance index depends on the relative size of the corresponding model, the test loss on the test data and the training loss on the training data; similarly, performing second parameter adjustment on the first network layer by using the training data and the test data to obtain a second fine adjustment model, and determining a second index value; and based on the relative size of the first index value and the second index value, determining the information sensitivity corresponding to the first network layer, and when the information sensitivity is greater than a predetermined threshold, performing security processing on the first network layer.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
Power sensitive information adaptive security routing method for information sensitivity perception
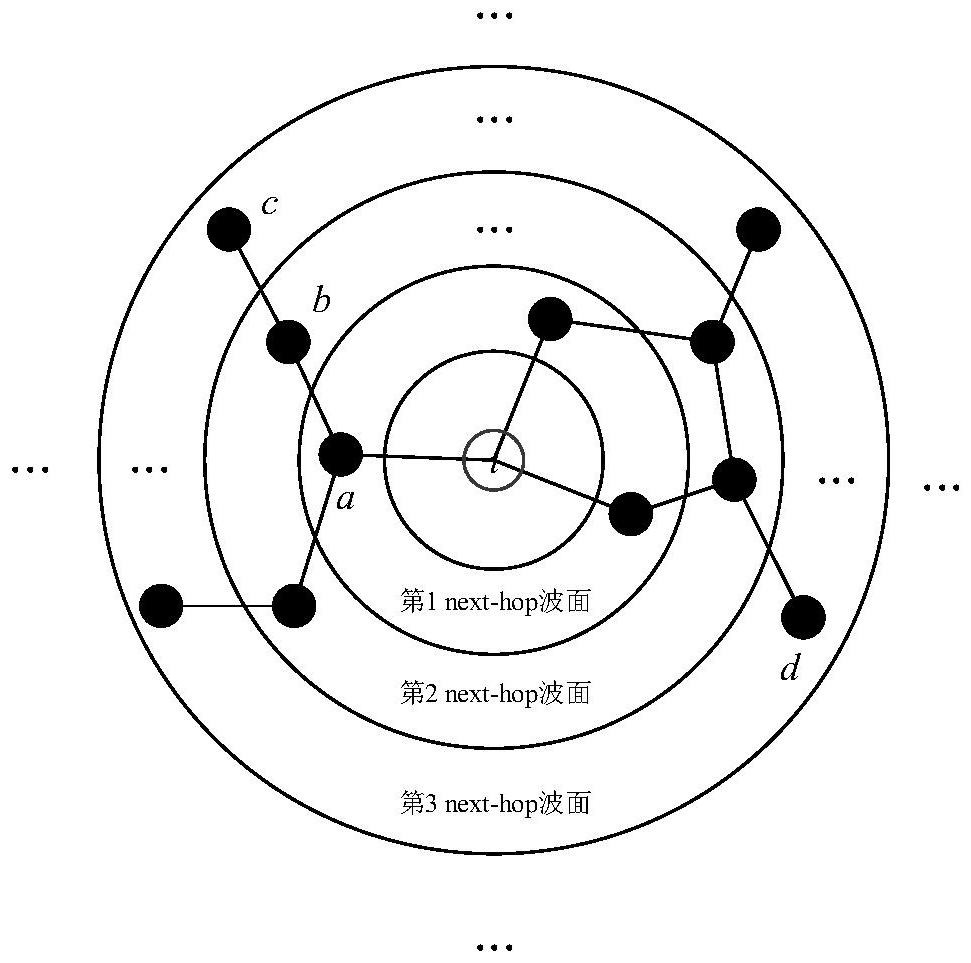
ActiveCN114024892AReduce security risksSecure transmissionTransmissionHigh level techniquesPathPingSecure by design
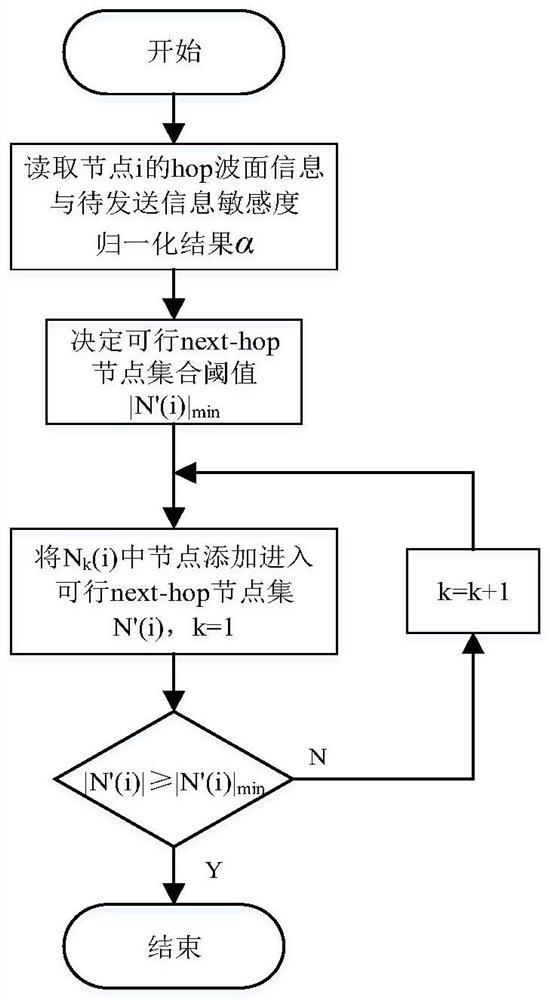
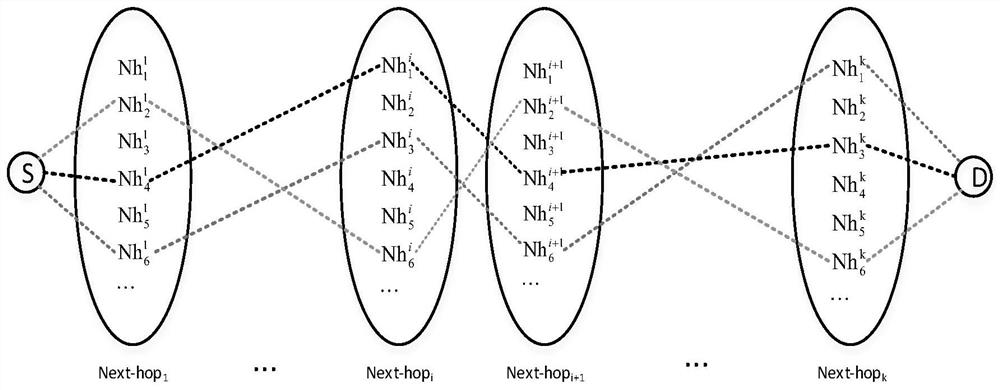
The invention discloses a power sensitive information adaptive security routing method for information sensitivity perception, relates to the field of power communication network security routing, and aims to reduce security risks existing in a transmission process of sensitive data of smart grid service application. According to the technical scheme, the method is characterized by comprising the following steps of: constructing a node next-hop wave surface according to the shortest path hop count from each node to a current node; according to the node next-hop wave surface, generating a feasible next-hop node set; calculating a node priority selection probability in the feasible next-hop node set; constructing a sensitive information virtual transmission path; and constructing a physical transmission path corresponding to the virtual transmission path according to a shortest path method. According to the method, a secure transmission guarantee scheme can be specifically designed for sensitive data in different service scenes, and the security risk of the sensitive information of the intelligent power grid service in the transmission process is reduced.
Owner:STATE GRID SICHUAN ECONOMIC RES INST
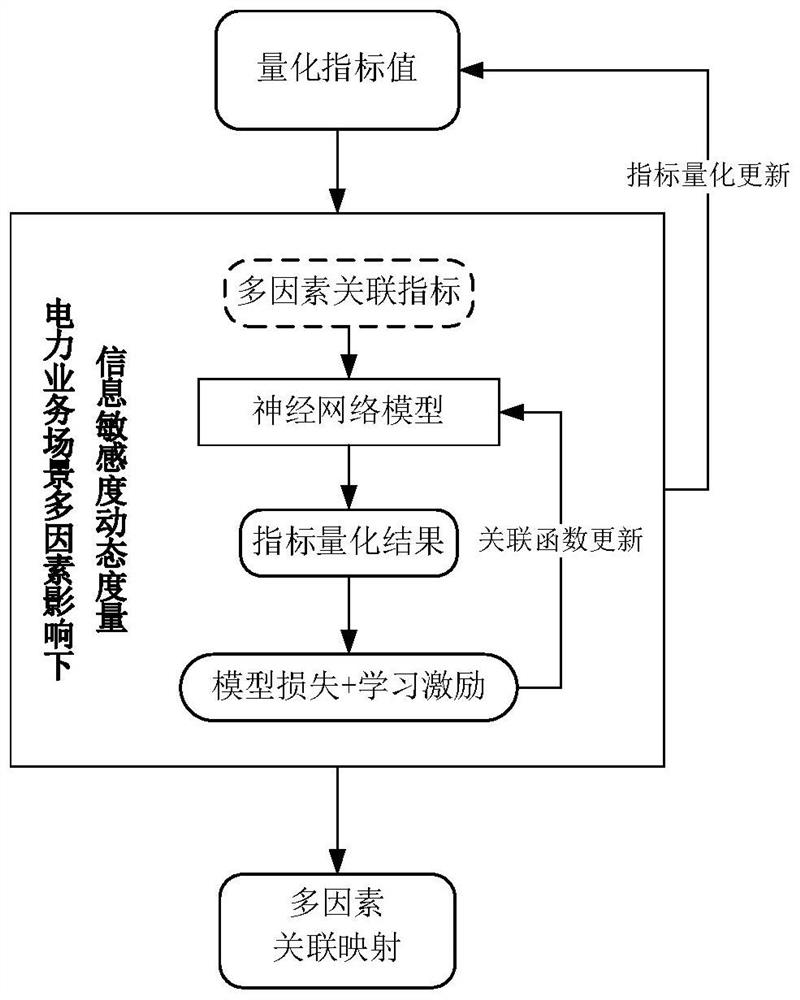
Dynamic evaluation method and system for information sensitivity of smart power grid
PendingCN114036570ADescribe the actual privacy and security needsImprove accuracyData processing applicationsDigital data protectionDynamical optimizationSimulation
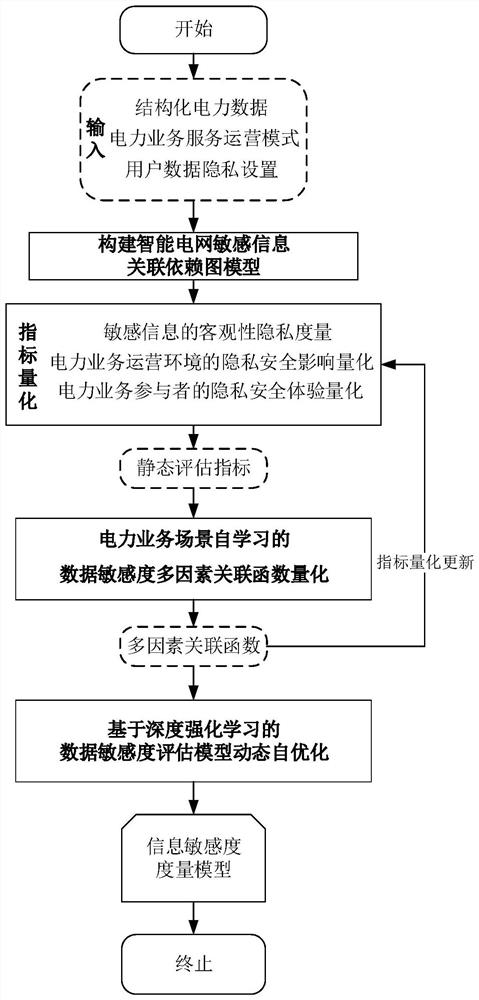
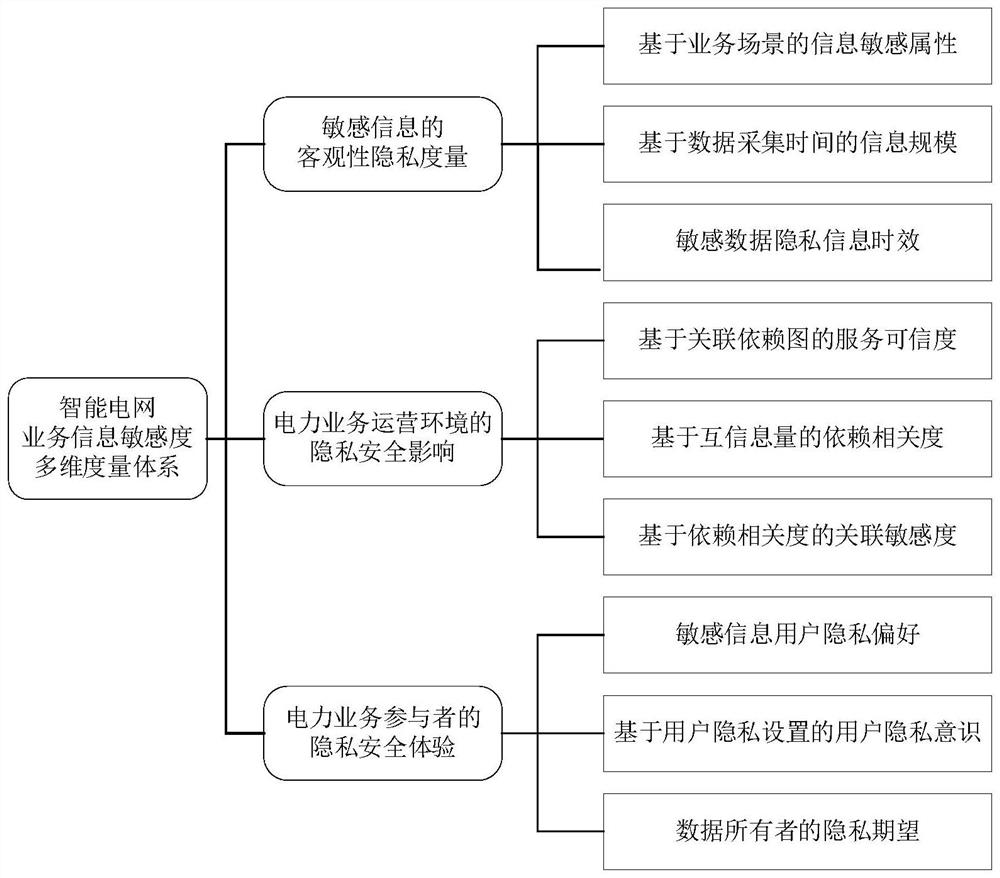
The invention discloses a dynamic evaluation method and system for the information sensitivity of a smart power grid, and the method mainly comprises the following steps: firstly, considering the influence of a data objective information factor I, a power business operation environment C and business participant experience P on the information sensitivity of the smart power grid, and constructing a multi-dimensional measurement system for the business information sensitivity of the smart power grid; secondly, analyzing a multi-factor association mapping relationship among I, C and P, and proposing an information sensitivity dynamic measurement system under the influence of multiple factors of a power business scene; and finally, proposing a power business scene self-learning data sensitivity dynamic evaluation method, and adopting a dynamic feedback mechanism based on deep reinforcement learning to realize dynamic optimization of an information sensitivity evaluation model based on scene self-adaption. The invention has the beneficial effects that the evaluation of the information sensitivity is more universal and targeted, and the dynamic evaluation of the information sensitivity based on scene self-adaption is realized, so that the accuracy of the calculation of the information sensitivity of the intelligent power grid is improved.
Owner:STATE GRID SICHUAN ECONOMIC RES INST
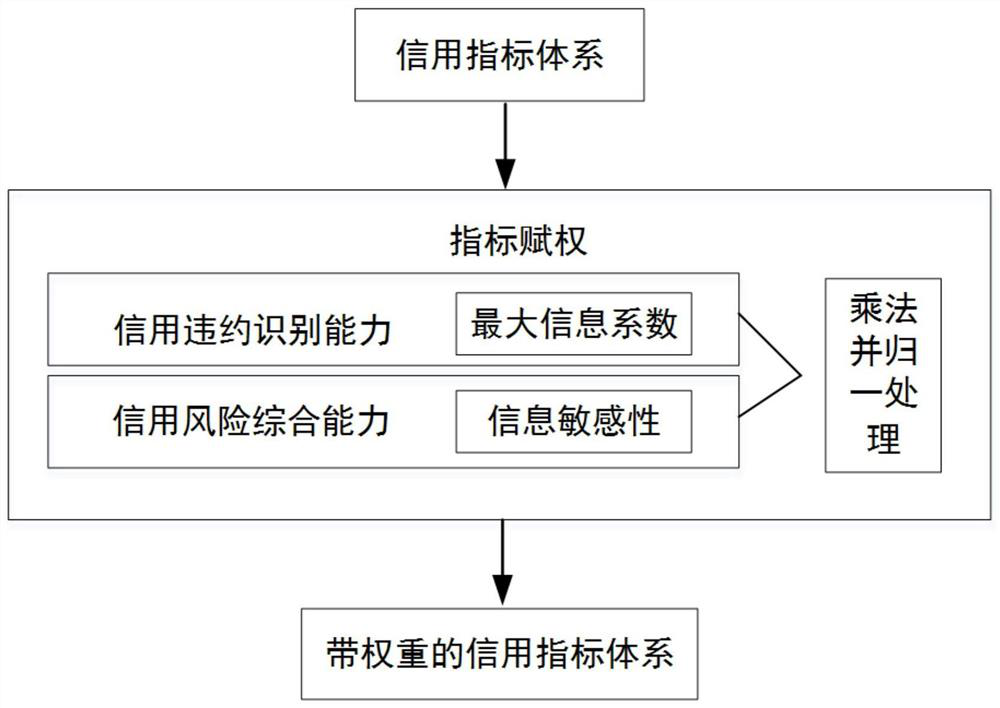
Comprehensive and efficient credit rating index weighting method
The invention discloses a comprehensive and efficient credit rating index weighting method, and relates to the technical field of multivariate statistical analysis; the method is used for weighting acredit rating index based on a maximum information coefficient and information sensitivity. the ratio of the maximum information coefficient of one credit rating index to the sum of the maximum information coefficients of all the credit rating indexes is calculated as a first-layer weight; the information sensitivity of each index is calculated, wherein the ratio of the information sensitivity ofeach index to the sum of the information sensitivities of all the indexes is used as a second-layer weight; the weights of the two layers are multiplied, and normalization processing is carried out toserve as the weighting of the credit index. The final weight of the credit rating index weighting method can reflect the recognition capability of the index for violation or not, can reflect the comprehensive risk capability of the index credit violation, and overcomes the defects of the existing research weighting.
Owner:天元大数据信用管理有限公司
A Sensitive Long Short-Term Memory Method Based on Differentiation of Input Changes
ActiveCN110390386BIncreased sensitivityImprove responseCharacter and pattern recognitionNeural architecturesTime informationReal time analysis
The invention discloses a sensitive long-term and short-term memory method based on input variation differentiation. In order to improve the traditional LSTM neural network's ability to respond to short-term information, a neural unit of the long-term and short-term memory network with increased information sensitivity is added, which can It greatly increases its ability to respond to short-term information, improves the real-time performance of its application, and enables more complete real-time analysis, further analysis of micro-actions and other contents, and improves the application value.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
Health archive system design method based on BS framework
InactiveCN107919952AThe need for ease of diggingImprove good performanceKey distribution for secure communicationEncryption apparatus with shift registers/memoriesSystems designInformation diversity
The invention discloses a health archive system design method based on a BS framework. The method comprises the following steps that step one, archive template information and user archive informationare saved by the system by using the XML format for aiming at the problem of the information format diversity of the health archive, the problem of adapting to the information diversity of the healtharchive is solved by the great expansibility and flexibility of XML, and formatted query is supported by XML so that the requirement for deep mining of the data in the future is facilitated; step two, the 3DES encryption and decryption technology is used for aiming at the requirements of the members for the information sensitivity and security and the concept of the shared lock is put forward; and step three, interface designing and template designing are performed. According to the health archive system design method based on the BS framework, the practical significance of the health archivesystem based on the BS framework for enhancing the medical information level is clear, and the system uses the Microsoft NET Framework technology and uses the BS framework and XML with combination ofthe database method so that the basic function of the health archive management system of the internet platform can be realized.
Owner:HARBIN GUANGKAI TECH DEV
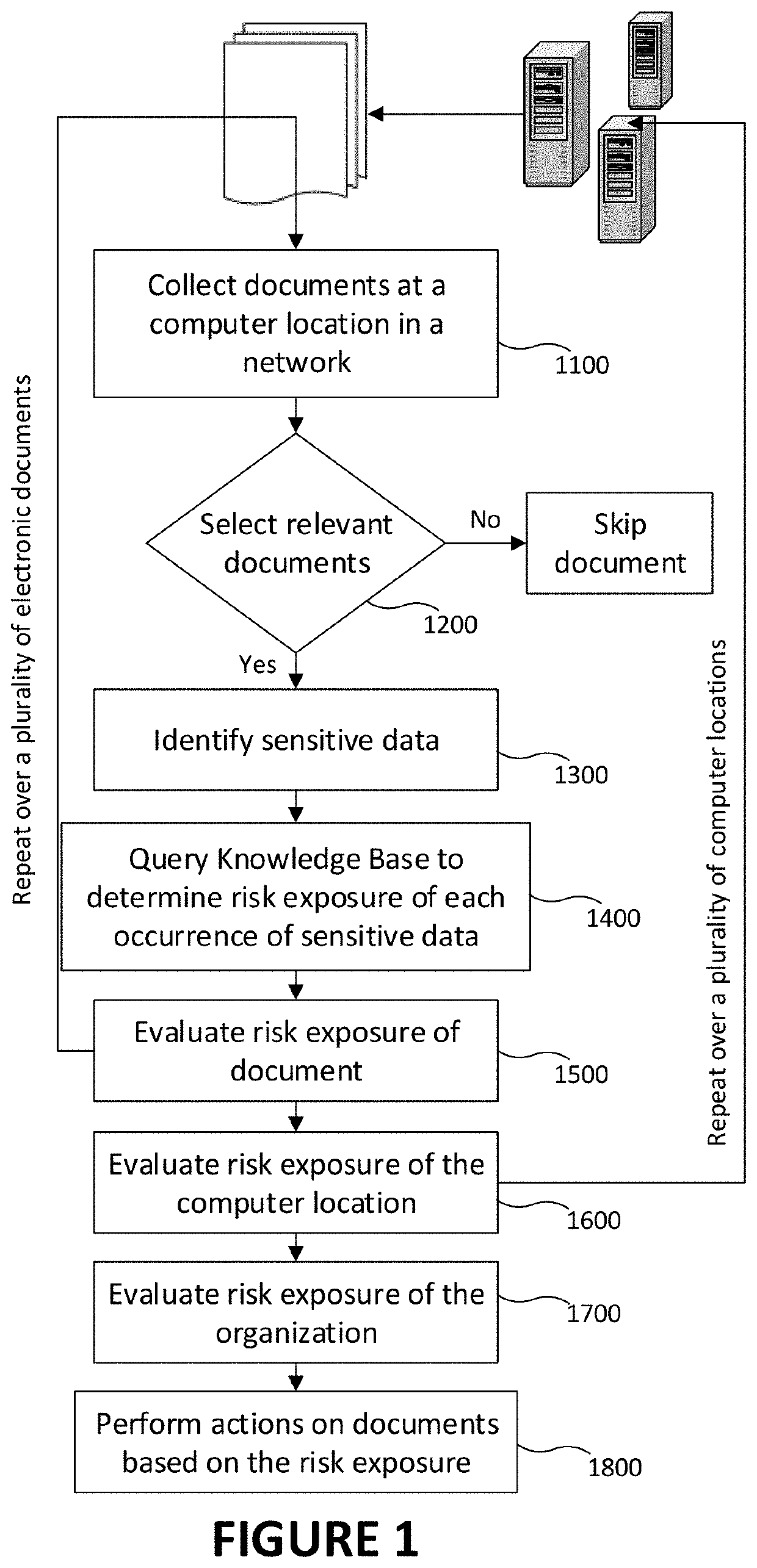
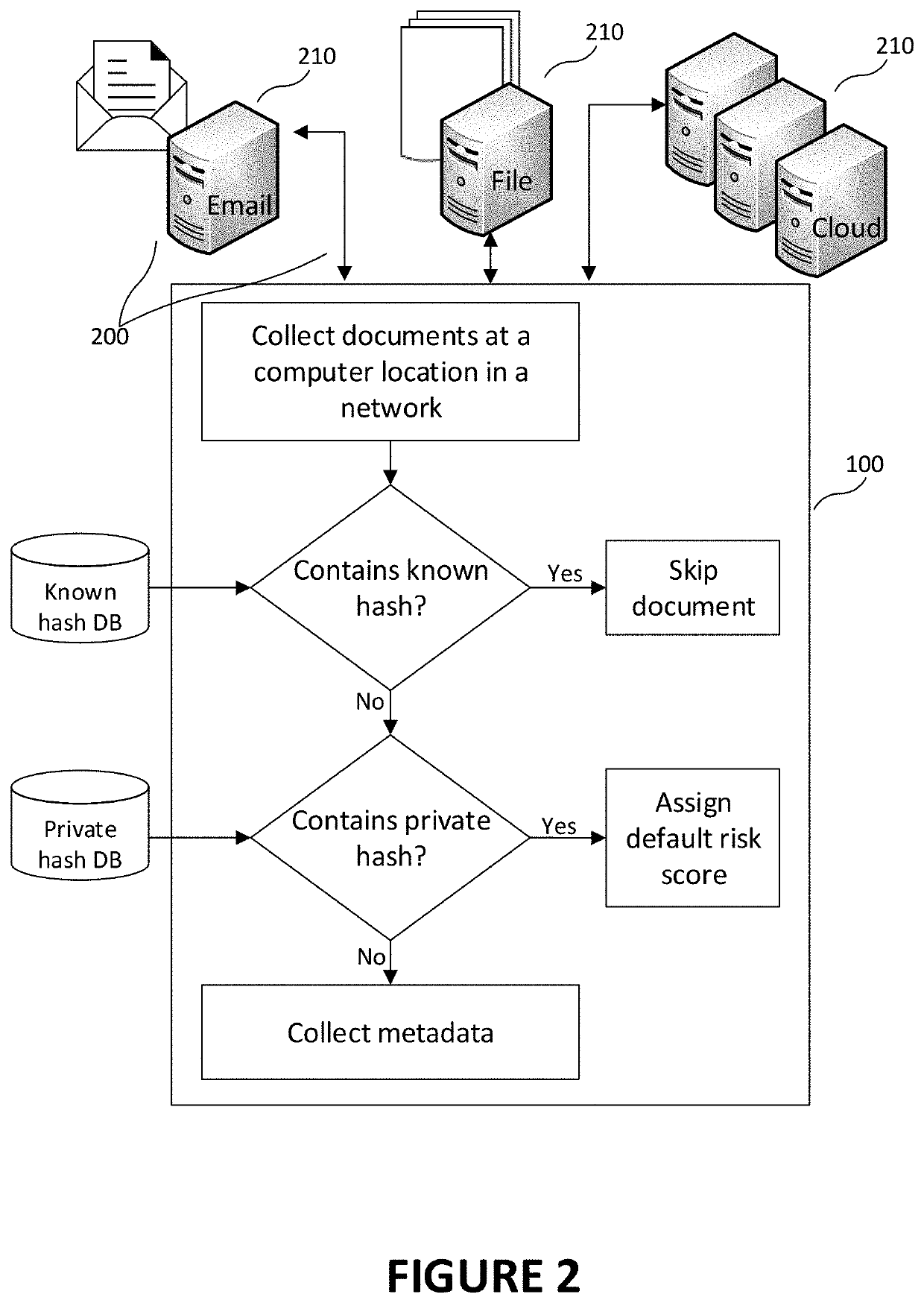
Method and system for managing electronic documents based on sensitivity of information
There is described a method for determining a level of sensitivity of information in an electronic document. The method comprises scanning a computer location to select the electronic document, such as an unstructured document in which the sensitive nature of a given portion of the contents is not trivial. In the electronic document, contents and metadata of the electronic document are scanned, and each occurrence of sensitive data is identified by classifying each portion of the contents forming the electronic document as sensitive, or not sensitive, per se. For each occurrence of the sensitive data, there are determined a type of the sensitive data and a risk score associated to the type of the sensitive data, for example from a knowledge base. Using the risk score of each occurrence of the sensitive data, one can determine an exposure risk score of the electronic document.
Owner:NETGOVERN INC
Method and device for protecting neural network model security
ActiveCN112100628BProtect privacy and securityGuaranteed uptimePlatform integrity maintainanceNeural architecturesEngineeringNetwork model
The embodiment of this specification provides a method for protecting the safety of a neural network model, including: obtaining a neural network model, including multiple network layers obtained by training with training data; for any first network layer among them, fixing other network layer parameters In the case of , the above-mentioned training data is used to perform the first parameter adjustment on the first network layer to obtain the first fine-tuning model; determine the first index value corresponding to the preset performance index of the first fine-tuning model, and the index of the preset performance index The value depends on the corresponding model, the relative size between the test loss on the test data and the training loss on the above training data; similarly, using the training data and test data to perform the second parameter adjustment on the first network layer, we get The second fine-tuning model, and determine the second index value; based on the relative size of the first index value and the second index value, determine the information sensitivity corresponding to the first network layer, and if it is greater than a predetermined threshold, the first network layer for security processing.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
A Sensitive Long Short-Term Memory Method Based on State Change Differentiation
ActiveCN110490299BIncreased sensitivityImprove responseNeural architecturesNeural learning methodsTime informationReal time analysis
The invention discloses a sensitive long-term and short-term memory method based on state change differentiation. In order to improve the traditional LSTM neural network's ability to respond to short-term information, a neural unit of the long-term and short-term memory network with increased information sensitivity is added, which can It greatly increases its ability to respond to short-term information, improves the real-time performance of its application, and enables more complete real-time analysis, further analysis of micro-actions and other contents, and improves the application value.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
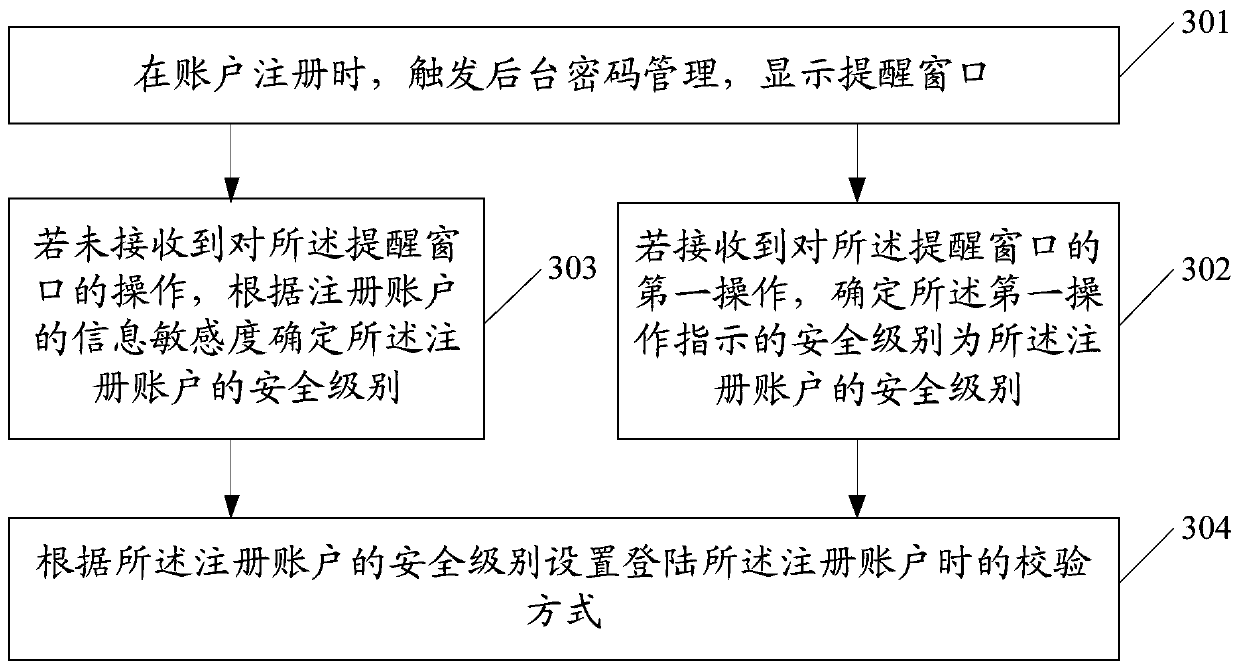
An information processing method, terminal and computer-readable storage medium
The embodiment of the invention discloses an information processing method and terminal and a computer readable storage medium. The information processing method includes the steps that during accountregistration, background password management is triggered, and a reminding window is displayed and used for reminding a user to hierarchically select passwords of a registered account; if first operation on the reminding window is received, it is determined that the safety level indicated by the first operation is the safety level of the registered account; if the operation on the reminding window is not received, the safety level of the registered account is determined according to the information sensitivity of the registered account; the verification mode when the user logs in the registered account is set according to the safety level of the registered account, in this way, different verification modes are adopted for login according to account passwords different in risk degree by hierarchically managing the account passwords used by the user in life, the process of remembering and inputting the account password information is omitted, and time is saved.
Owner:江苏方洋智能科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com