Patents
Literature
38results about "Program control using record carriers with instructions" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
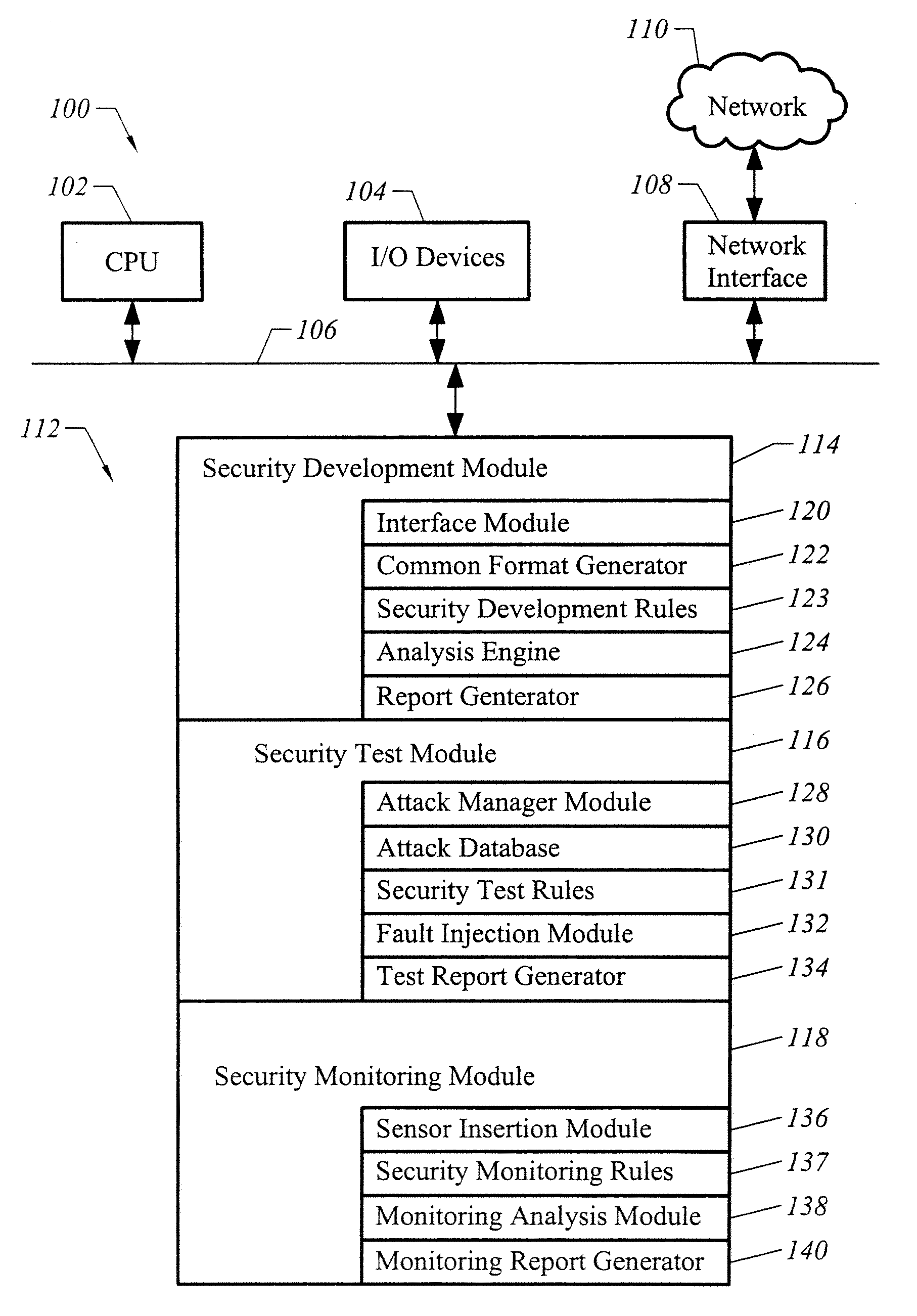
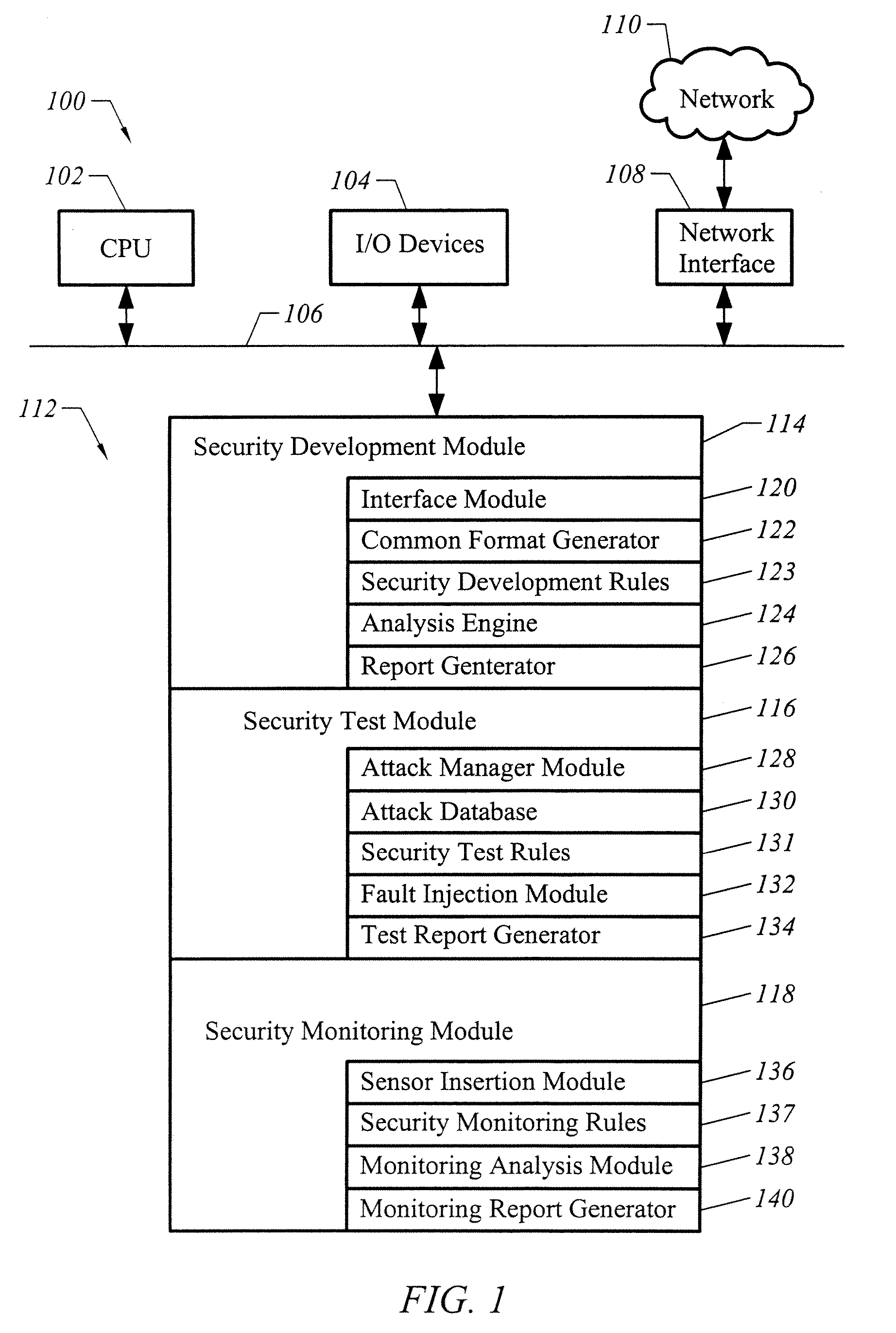
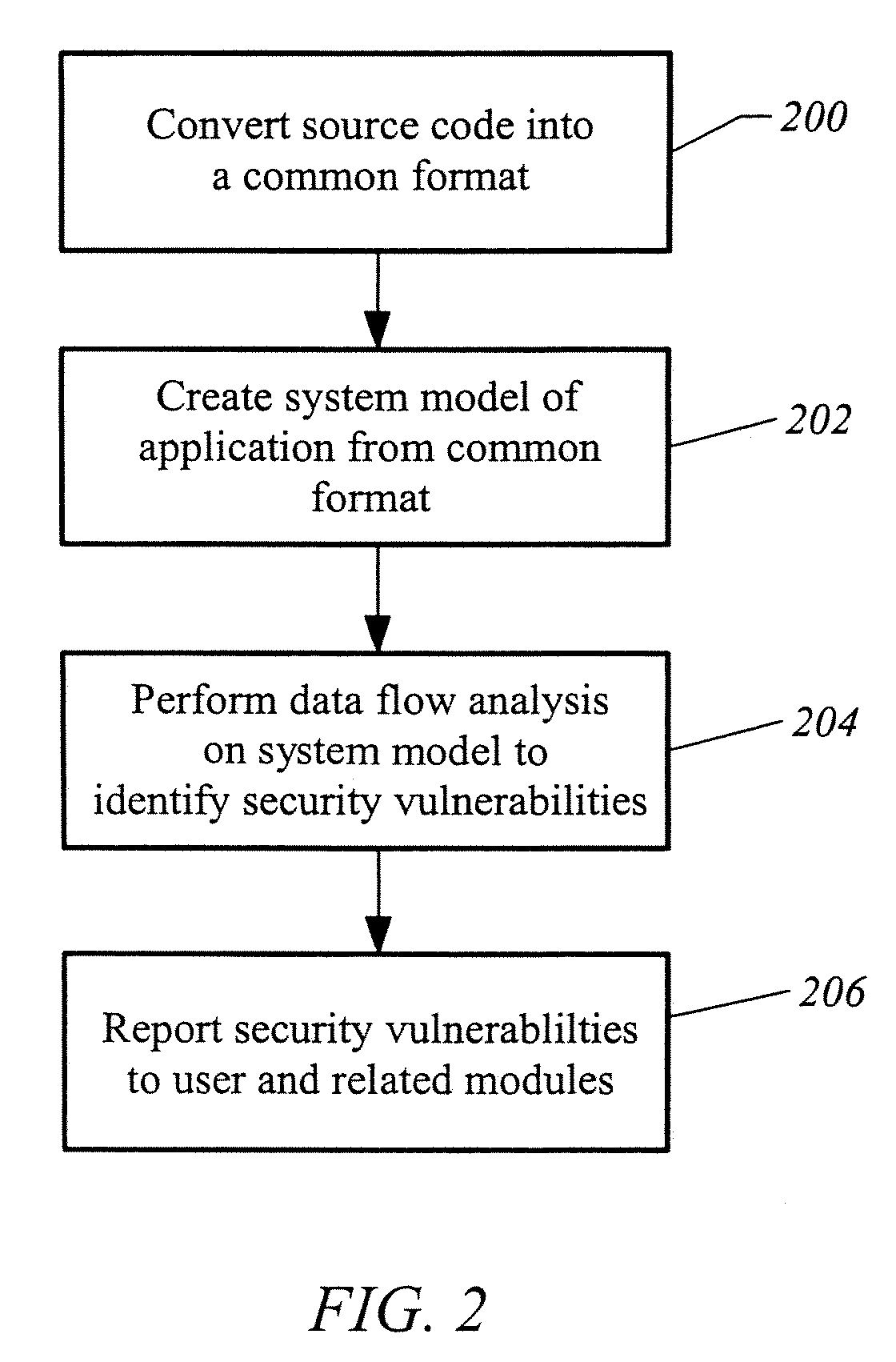
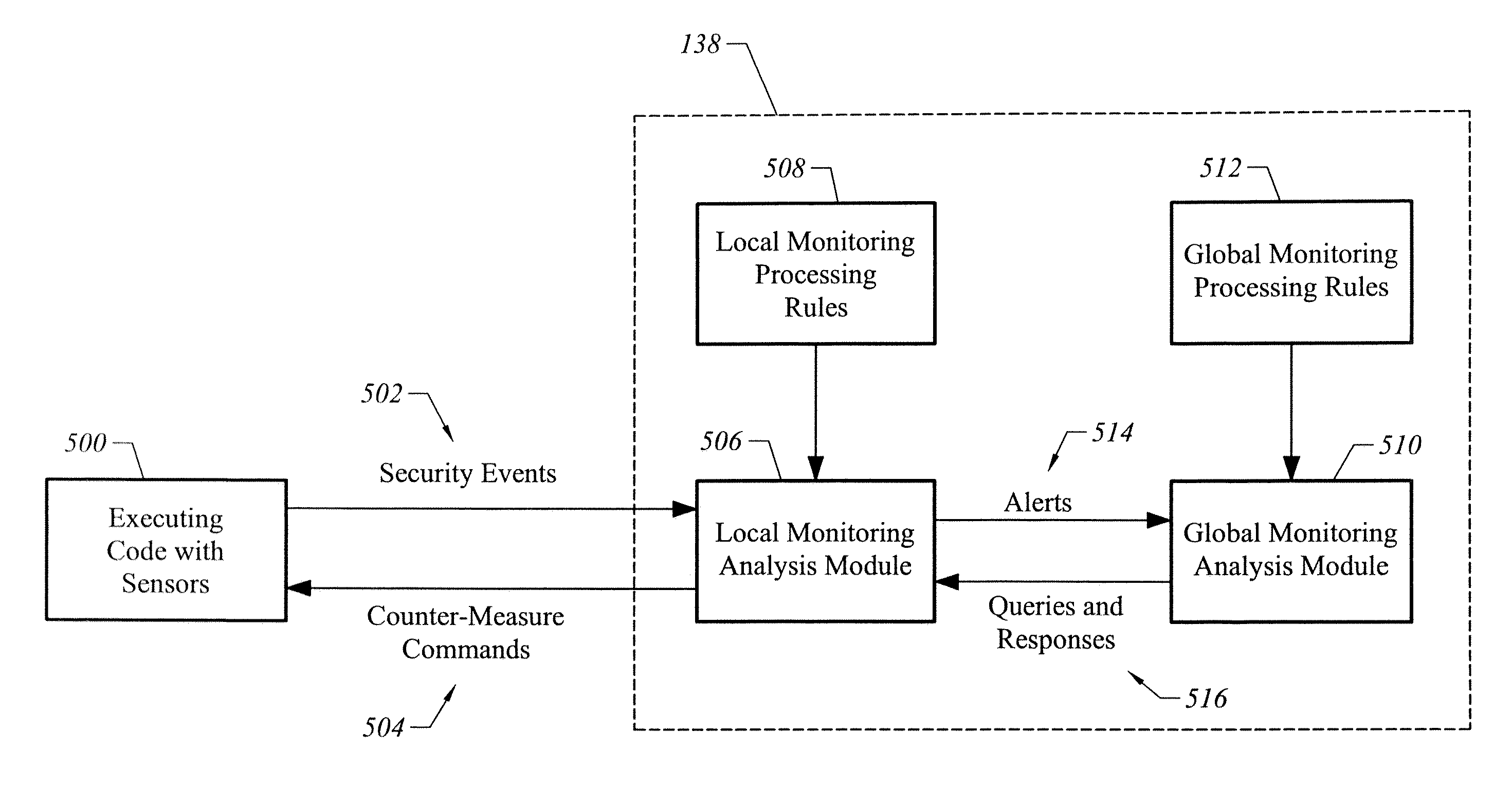
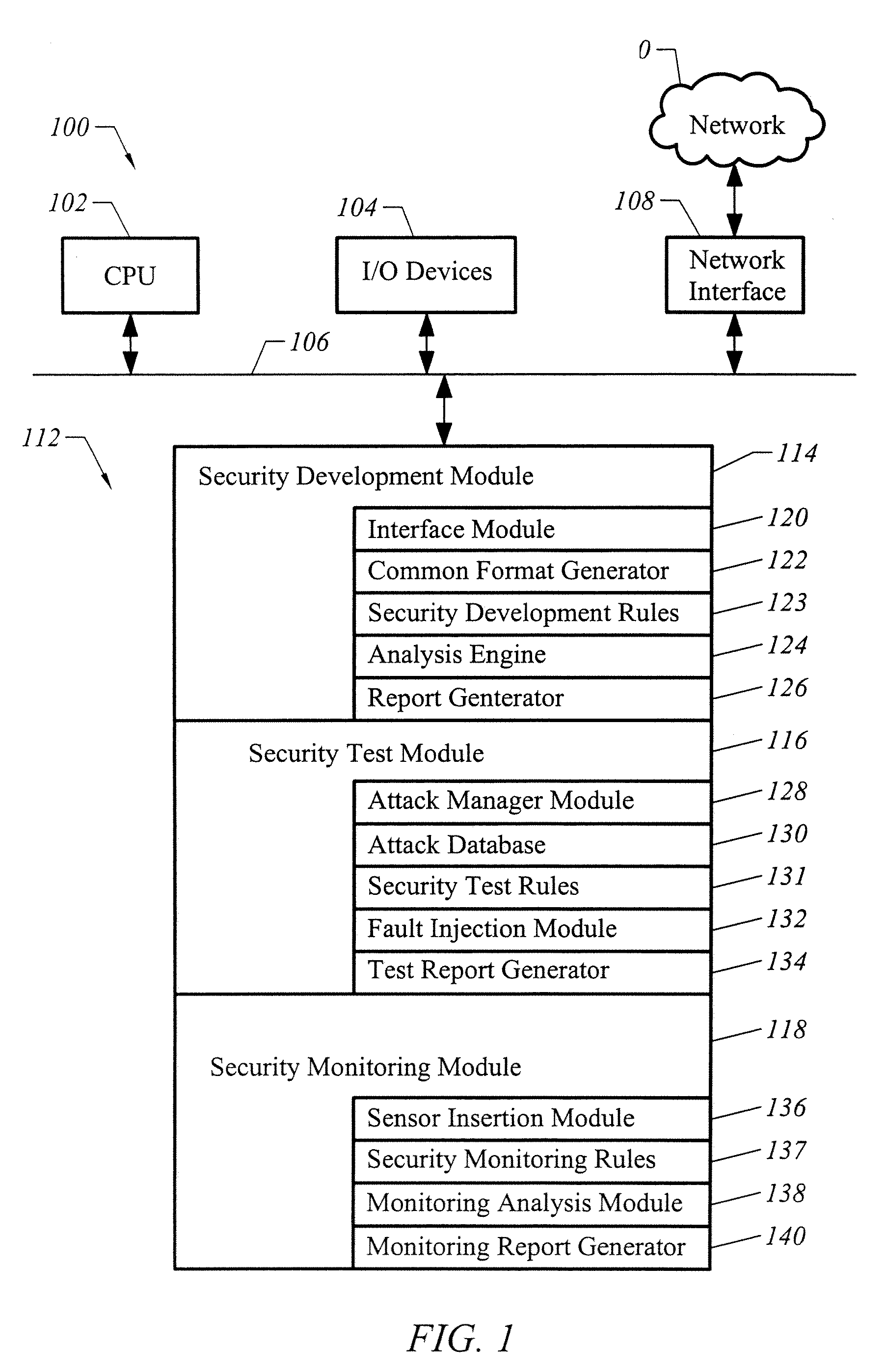
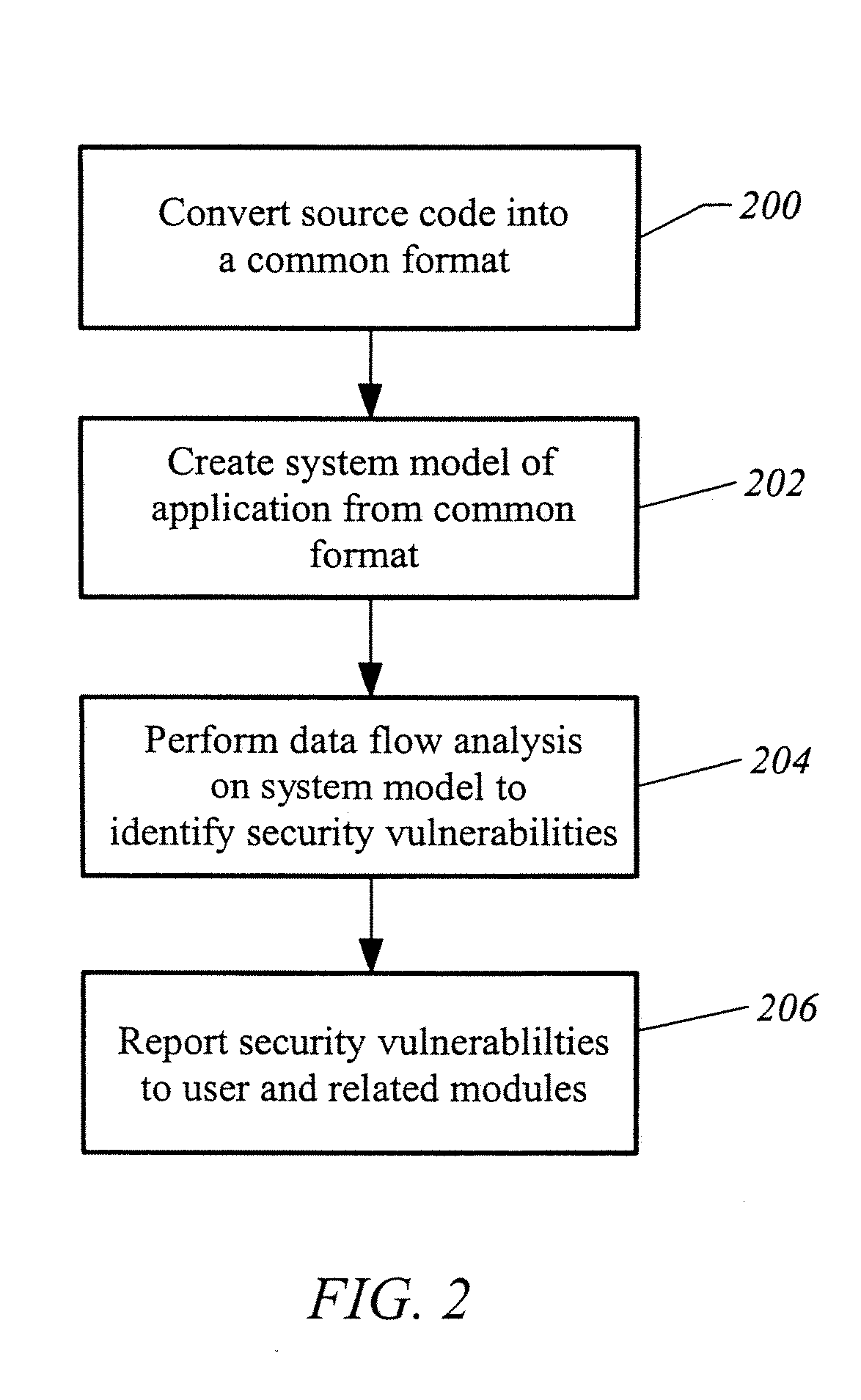
Apparatus and method for developing secure software
ActiveUS20070240138A1Memory loss protectionUser identity/authority verificationProgram instructionVulnerability
A computer readable medium includes executable instructions to analyze program instructions for security vulnerabilities. The executable instructions convert diverse program instruction formats to a common format. A system model is derived from the common format. A static analysis is performed on the system model to identify security vulnerabilities. Security vulnerabilities are then reported.
Owner:MICRO FOCUS LLC
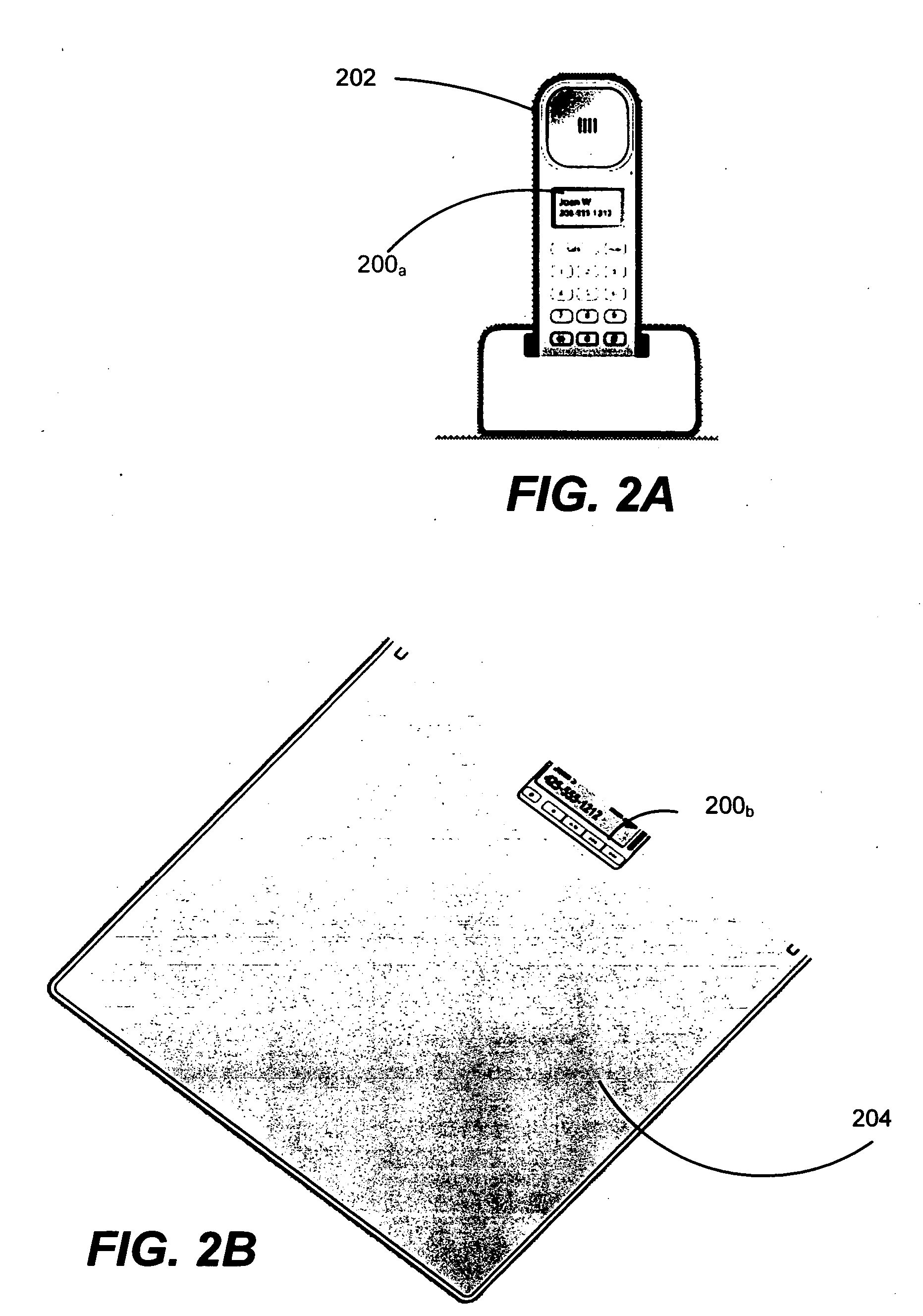
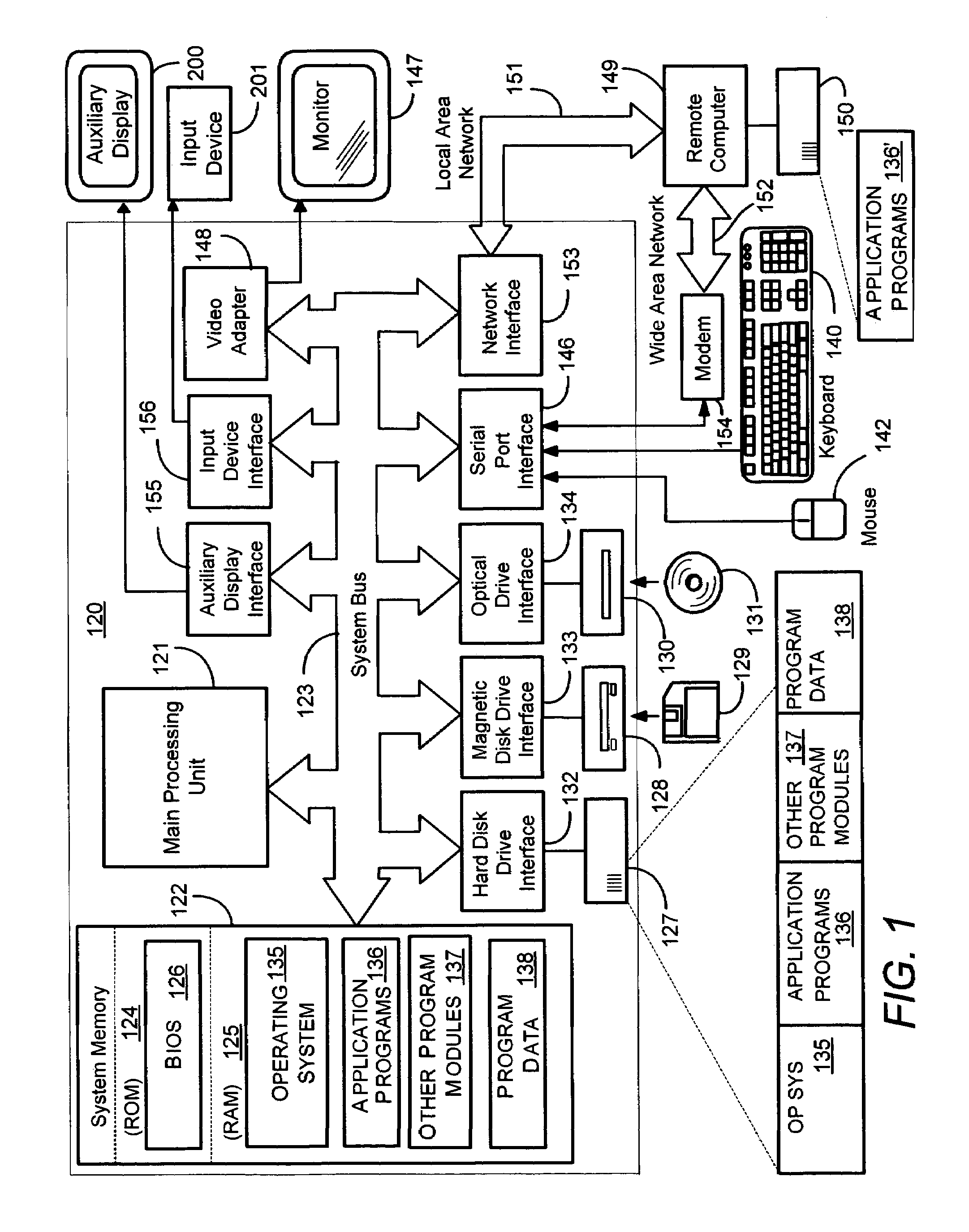
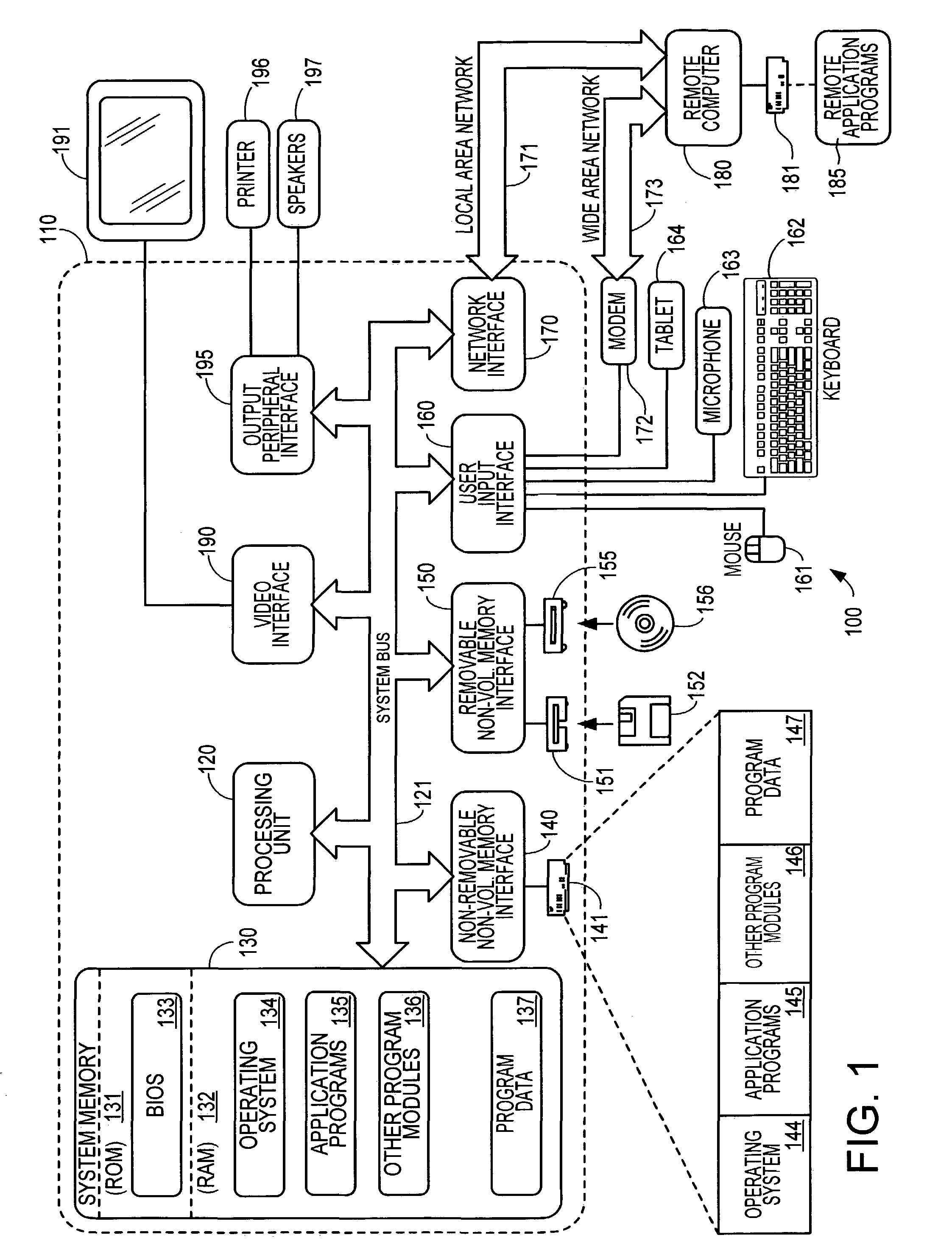
Context-aware auxiliary display platform and applications
InactiveUS20050243019A1Digital data processing detailsProgram control using record carriers with instructionsDisplay deviceContext data
Described is a mechanism by which application programs (or plug-ins) and an auxiliary service adjust the output and / or data available for output on an auxiliary device based on changes detected in the current context of the auxiliary display. Context sensors detect and report changes in context, whereby some action is taken with respect to what information is displayed or can be displayed on the auxiliary display device. Examples of context data that can change include the physical location of the display, detected movement or motion data, presence of a particular user or others, power state, network connectivity status, privacy status and so forth. The auxiliary device can have context as to its position relative to the main display. Information sensitivity levels may be used to specify whether an application program's data can be displayed, based on the perceived sensitivity of the information and the user's current context.
Owner:MICROSOFT TECH LICENSING LLC
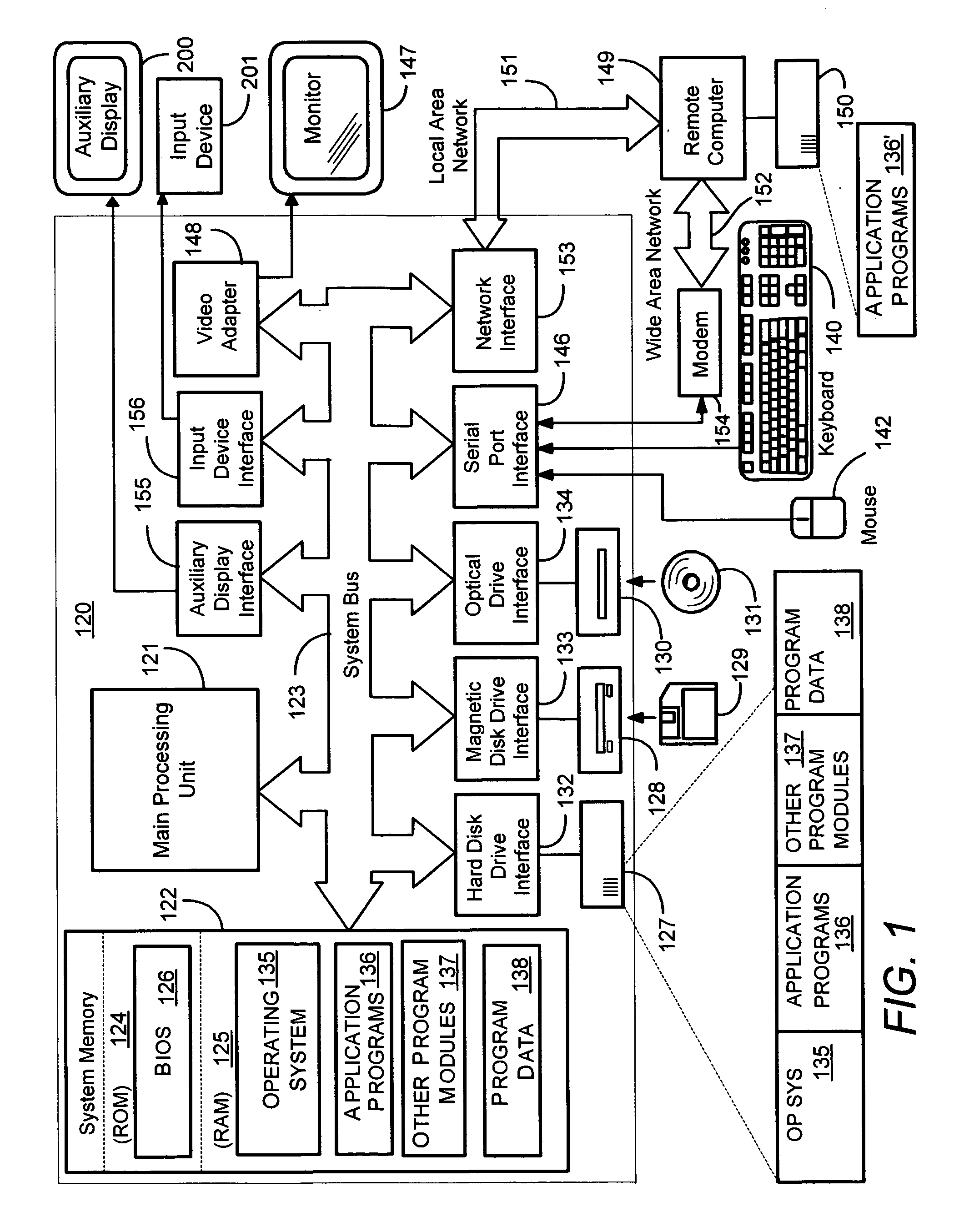
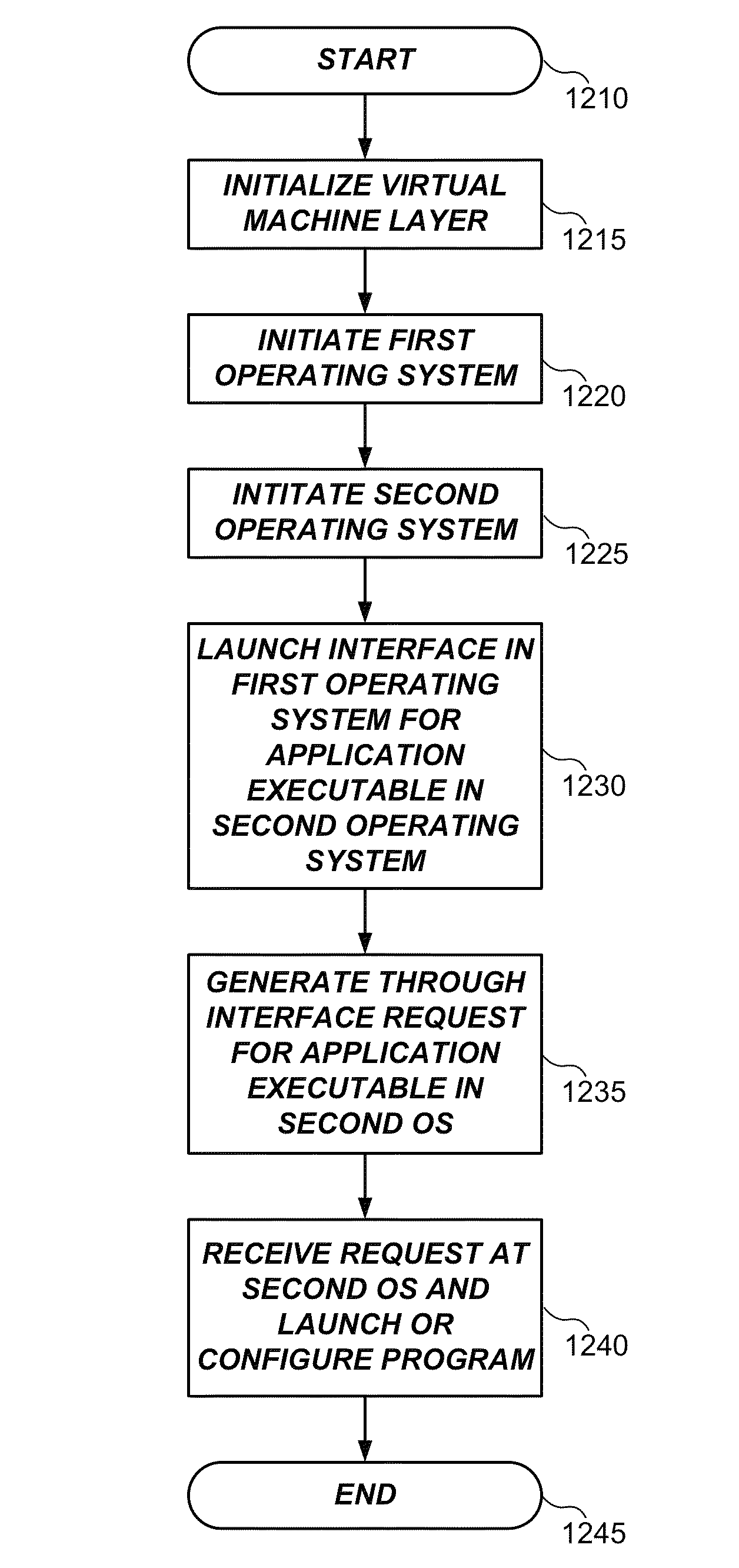
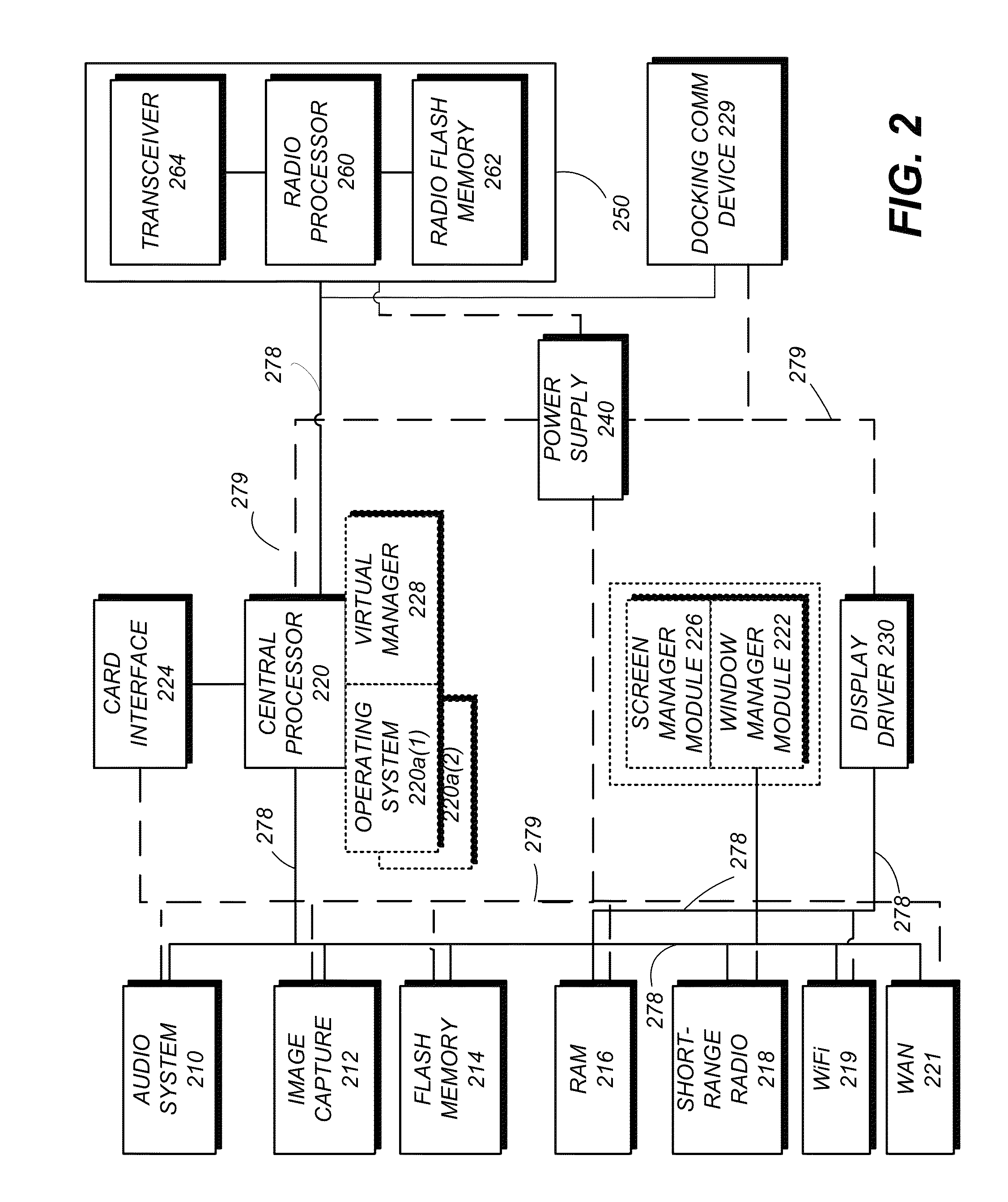
Dual operating system operation and configuration
ActiveUS8589952B2Program control using record carriers with instructionsSoftware simulation/interpretation/emulationDocking stationData management
Owner:QUALCOMM INC
Apparatus and method for developing secure software
ActiveUS9400889B2Memory loss protectionUser identity/authority verificationProgram instructionVulnerability
A computer readable medium includes executable instructions to analyze program instructions for security vulnerabilities. The executable instructions convert diverse program instruction formats to a common format. A system model is derived from the common format. A static analysis is performed on the system model to identify security vulnerabilities. Security vulnerabilities are then reported.
Owner:MICRO FOCUS LLC
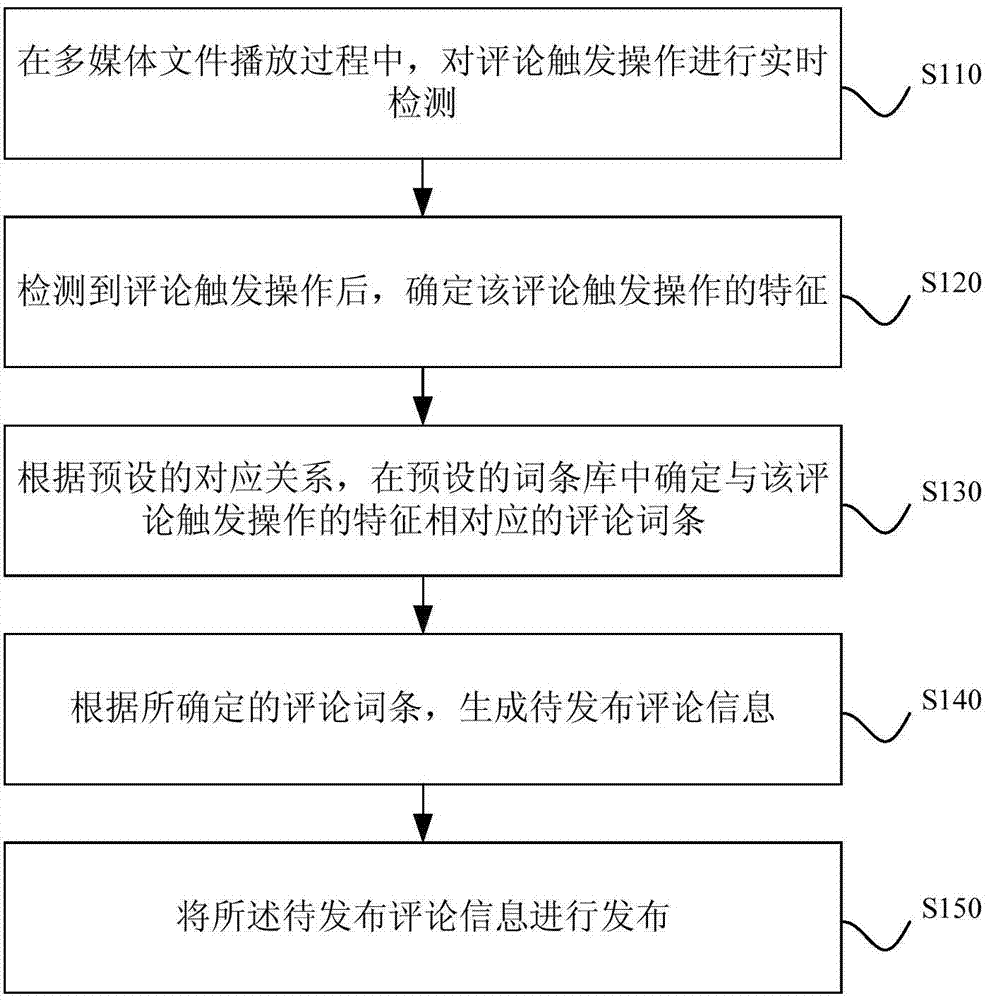
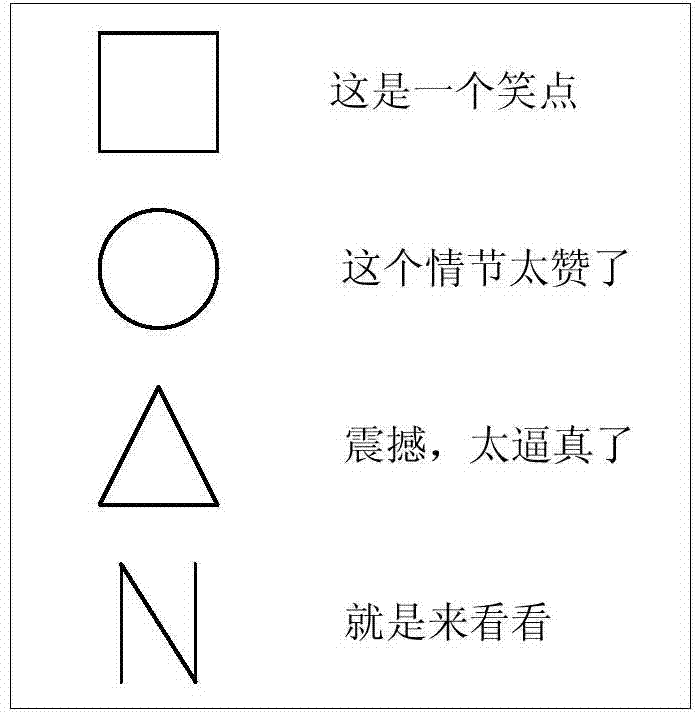
Comment information issuing method and device
ActiveCN104731554AImprove interactive experienceImprove viewing experienceProgram control using record carriers with instructionsInput/output processes for data processingComputer terminalMultimedia
The embodiment of the invention discloses a comment information issuing method and device. The comment information issuing method is applied to a multimedia file playing terminal. The comment information issuing method comprises the following steps that the comment triggering operation is detected in real time in the multimedia file playing process; after the comment triggering operation is detected, the feature of the comment triggering operation is determined; a comment entry corresponding to the feature of the comment triggering operation is determined in a preset entry library according to a preset corresponding relation; comment information to be issued is generated according to the determined comment entry; the comment information to be issued is issued. By means of the technical scheme, better interaction experience and watching experience can be brought to a user.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
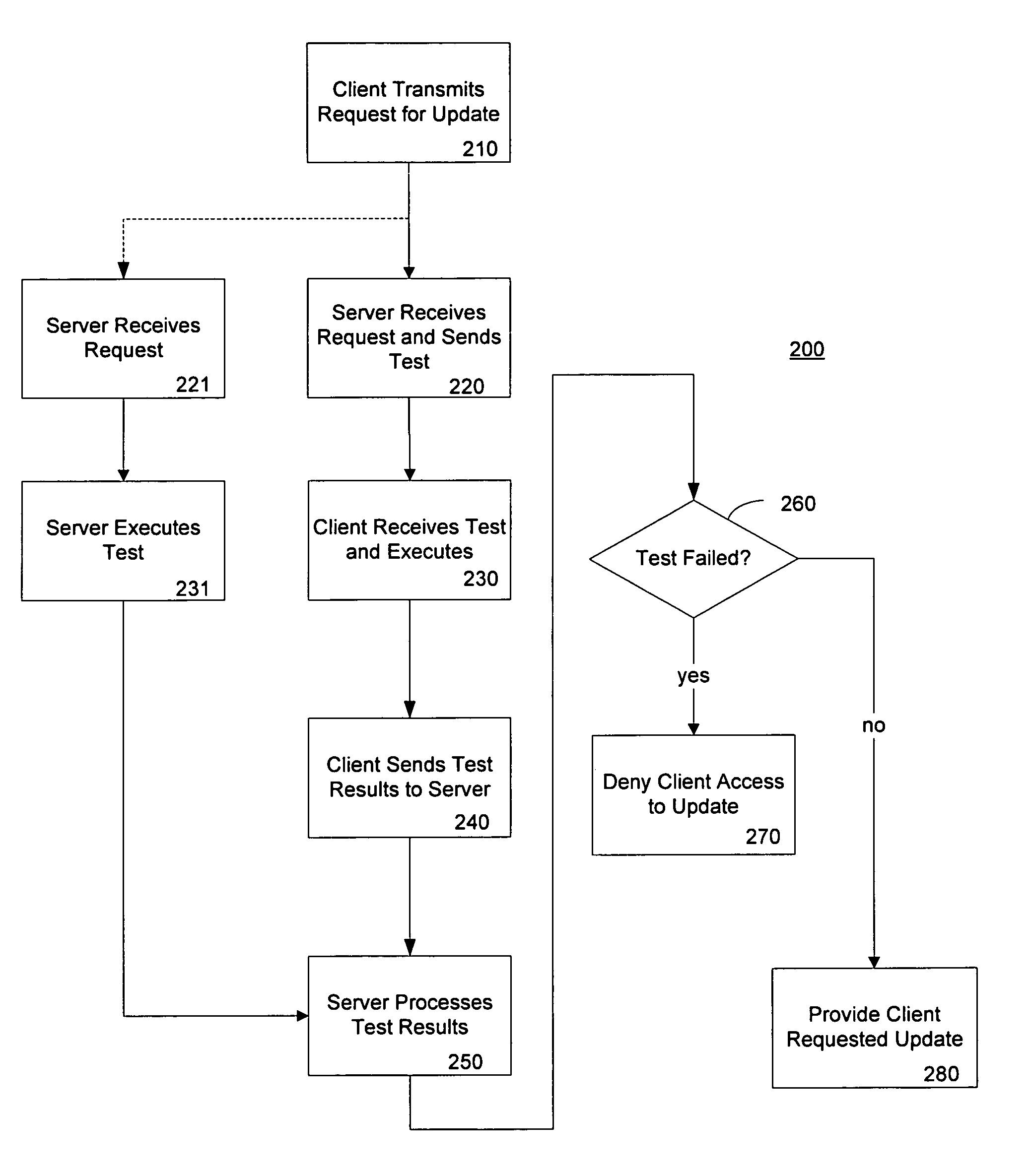
Method and system for limiting software updates
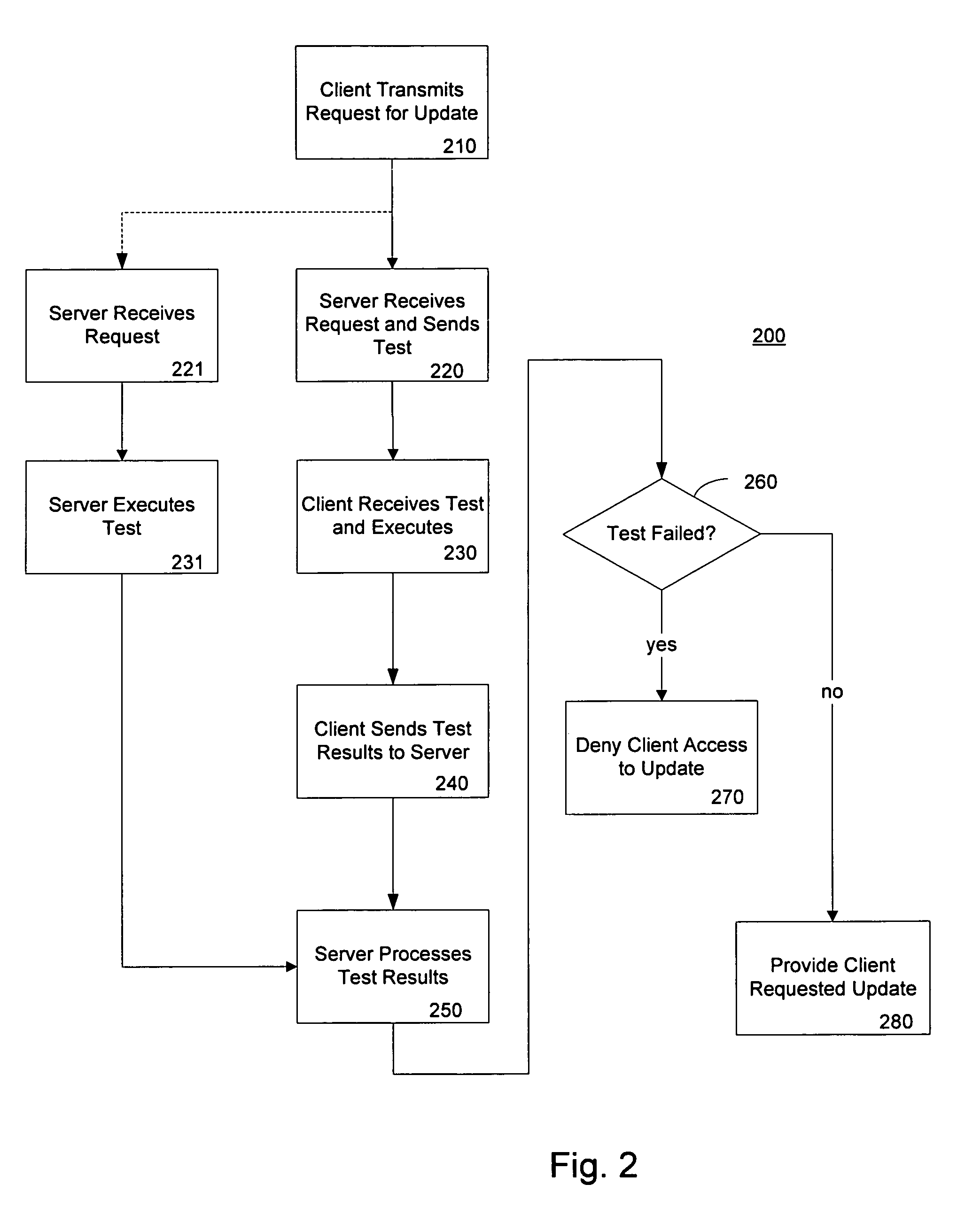
InactiveUS7331063B2Stopping propagationDigital data processing detailsUser identity/authority verificationSoftware updateClient-side
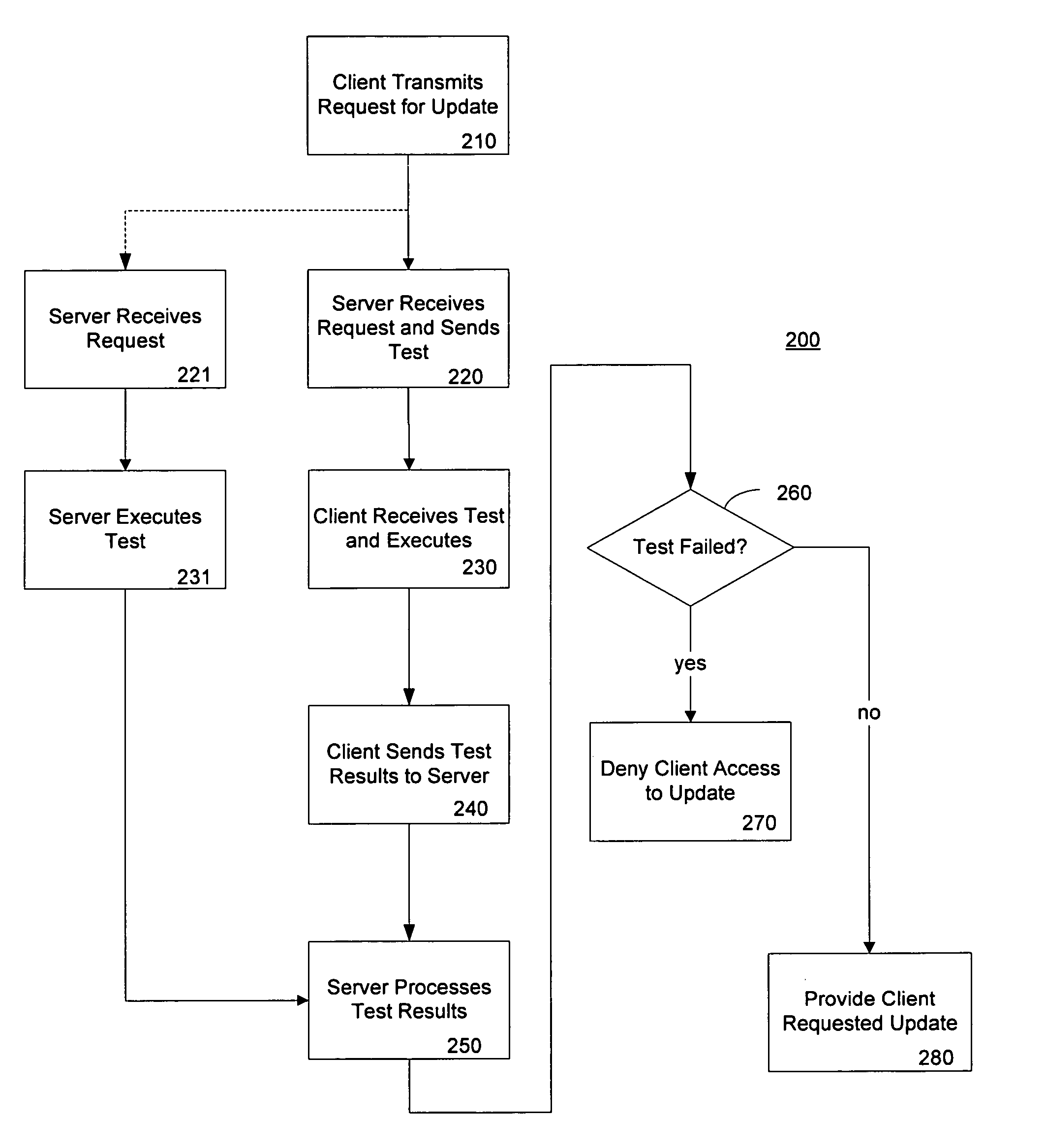
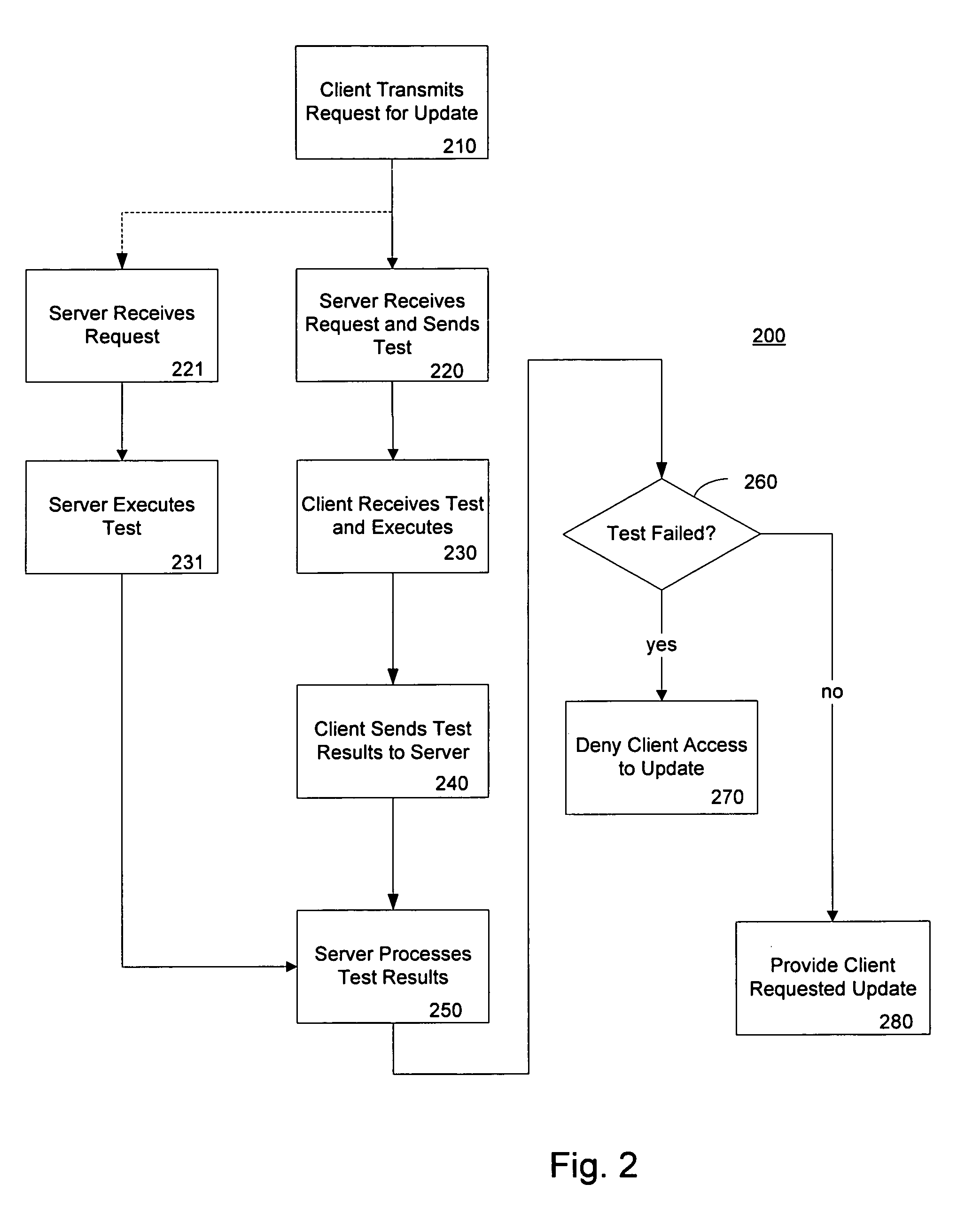
A method of detecting pirated software includes receiving a request for a software update by a client computer and providing to the client computer a test to be performed. The test is performed on the client computer against the client software application. The client computer may be denied a software update as a result of the test finding an illegitimate copy of the client software. The invention may be practiced in a network environment where a server transfers a test program for a client to execute upon request of a software update. The test performs an integrity check and denies the request for a software update if the client software is found to be illegitimate.
Owner:MICROSOFT TECH LICENSING LLC
Controlling an Electronic Device
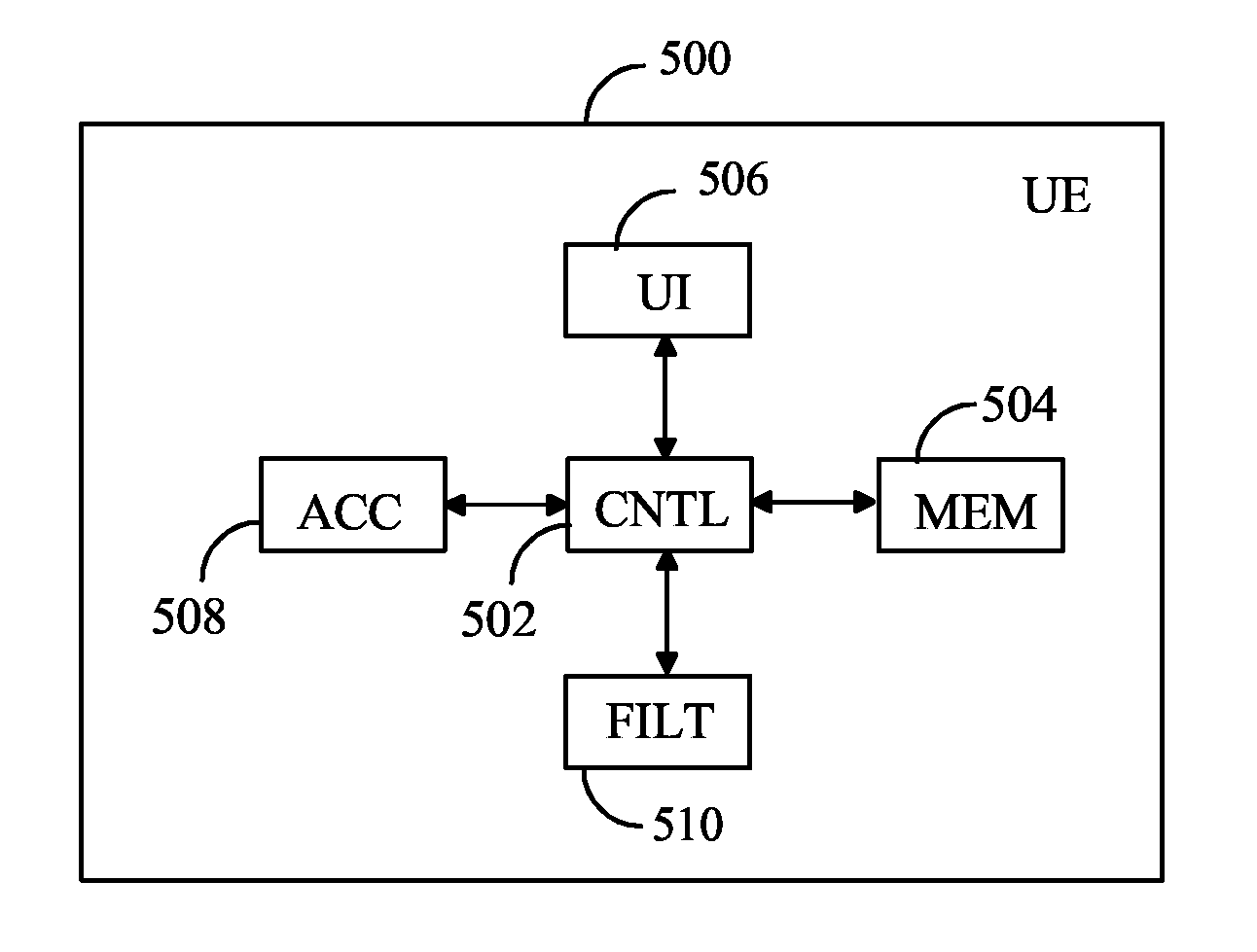
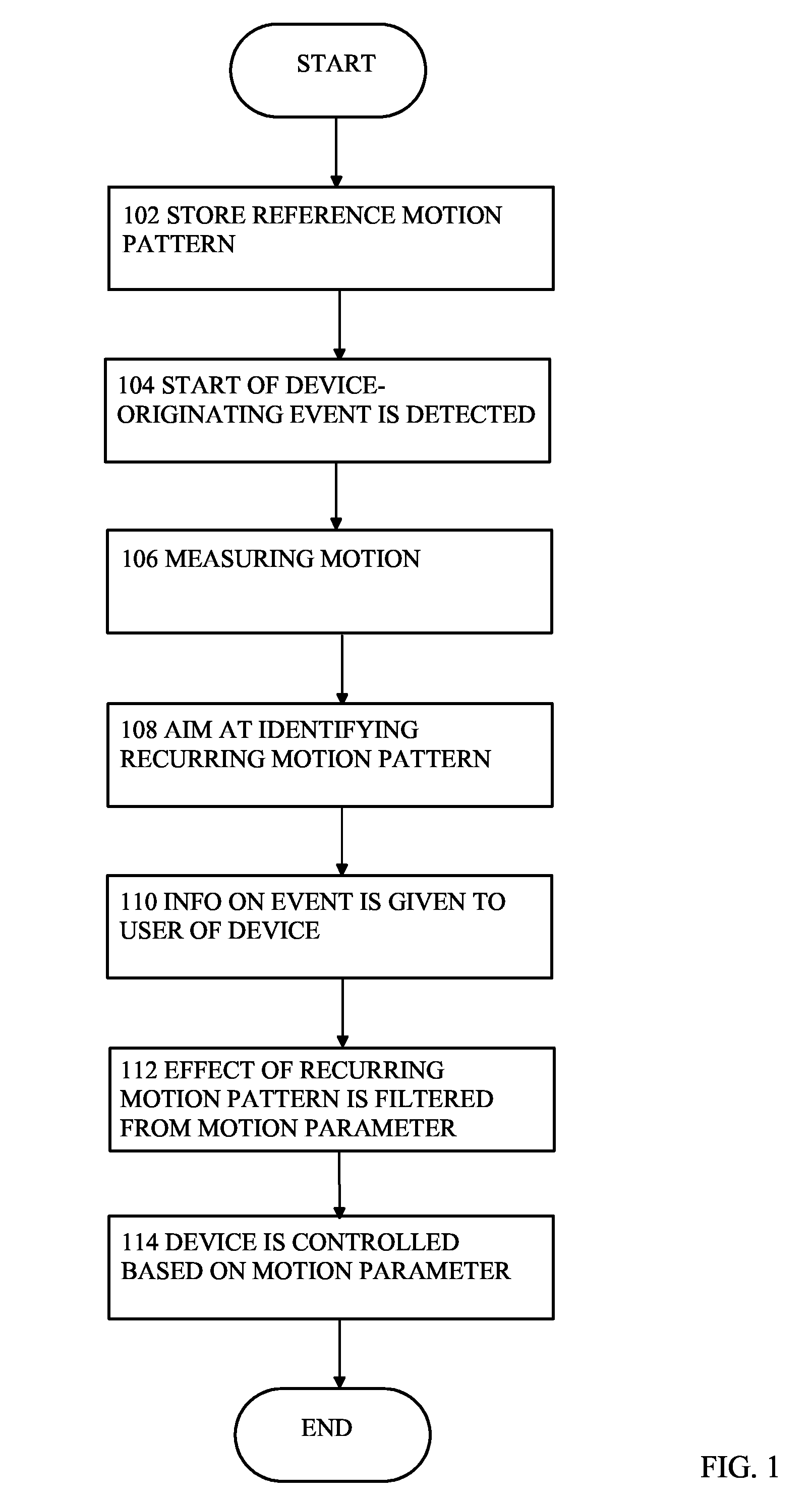
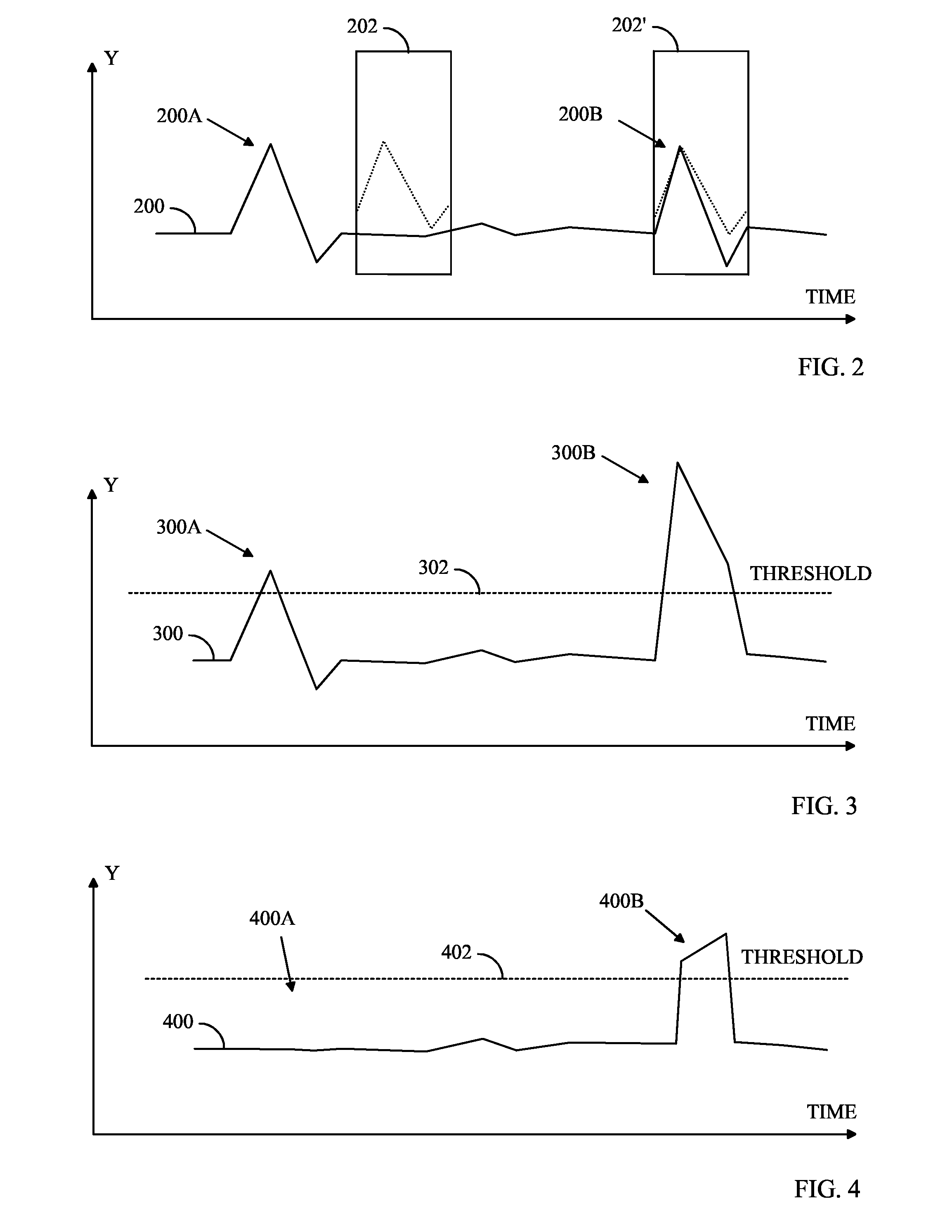
InactiveUS20070225935A1Few erroneous identificationEasy to identifyInput/output for user-computer interactionDigital computer detailsControl electronicsIdentification device
Owner:NOKIA CORP
Method and system for limiting software updates
InactiveUS20050246537A1Stopping propagationDigital data processing detailsUser identity/authority verificationSoftware updateClient-side
A method of detecting pirated software includes receiving a request for a software update by a client computer and providing to the client computer a test to be performed. The test is performed on the client computer against the client software application. The client computer may be denied a software update as a result of the test finding an illegitimate copy of the client software. The invention may be practiced in a network environment where a server transfers a test program for a client to execute upon request of a software update. The test performs an integrity check and denies the request for a software update if the client software is found to be illegitimate.
Owner:MICROSOFT TECH LICENSING LLC
Context-aware auxiliary display platform and applications
InactiveUS7511682B2Digital data processing detailsProgram control using record carriers with instructionsDisplay deviceContext data
Described is a mechanism by which application programs (or plug-ins) and an auxiliary service adjust the output and / or data available for output on an auxiliary device based on changes detected in the current context of the auxiliary display. Context sensors detect and report changes in context, whereby some action is taken with respect to what information is displayed or can be displayed on the auxiliary display device. Examples of context data that can change include the physical location of the display, detected movement or motion data, presence of a particular user or others, power state, network connectivity status, privacy status and so forth. The auxiliary device can have context as to its position relative to the main display. Information sensitivity levels may be used to specify whether an application program's data can be displayed, based on the perceived sensitivity of the information and the user's current context.
Owner:MICROSOFT TECH LICENSING LLC
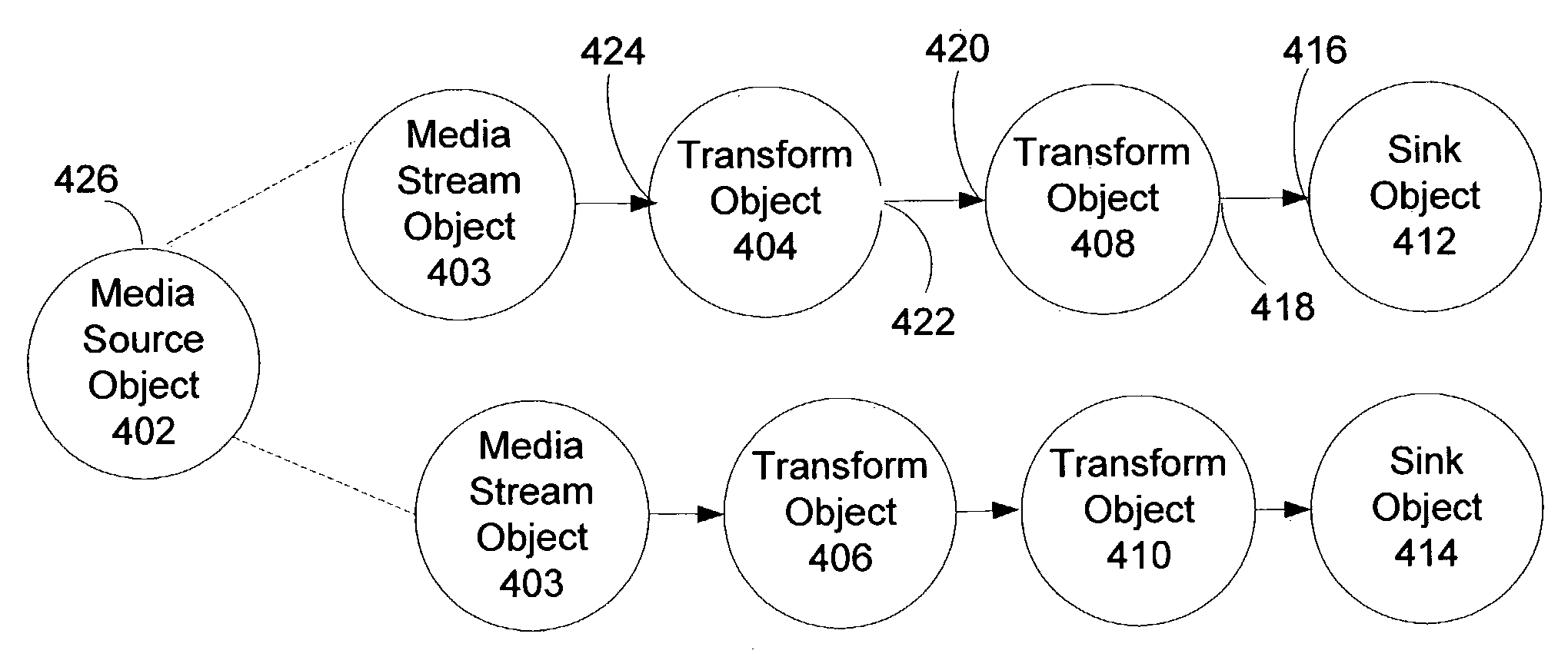
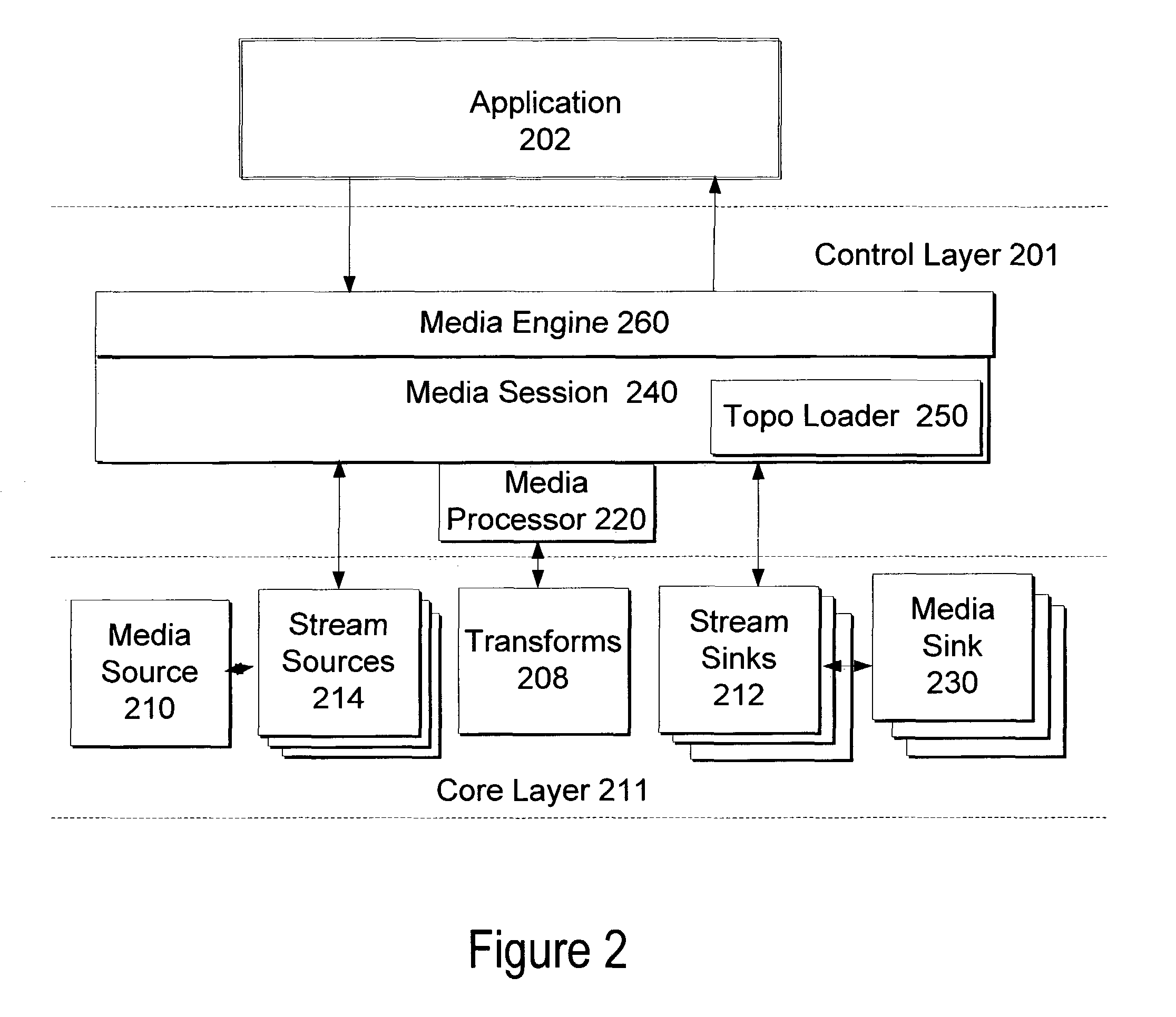
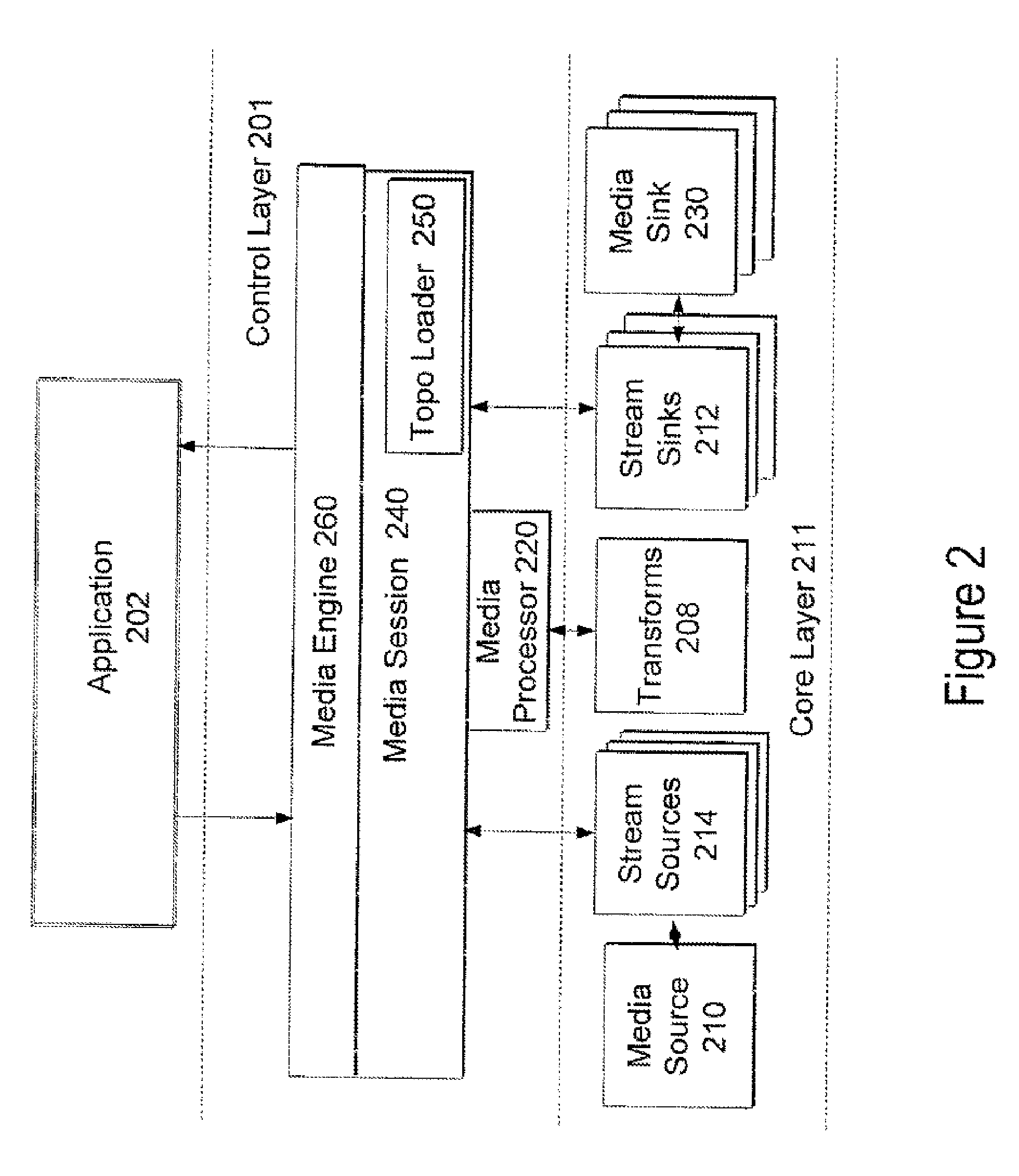
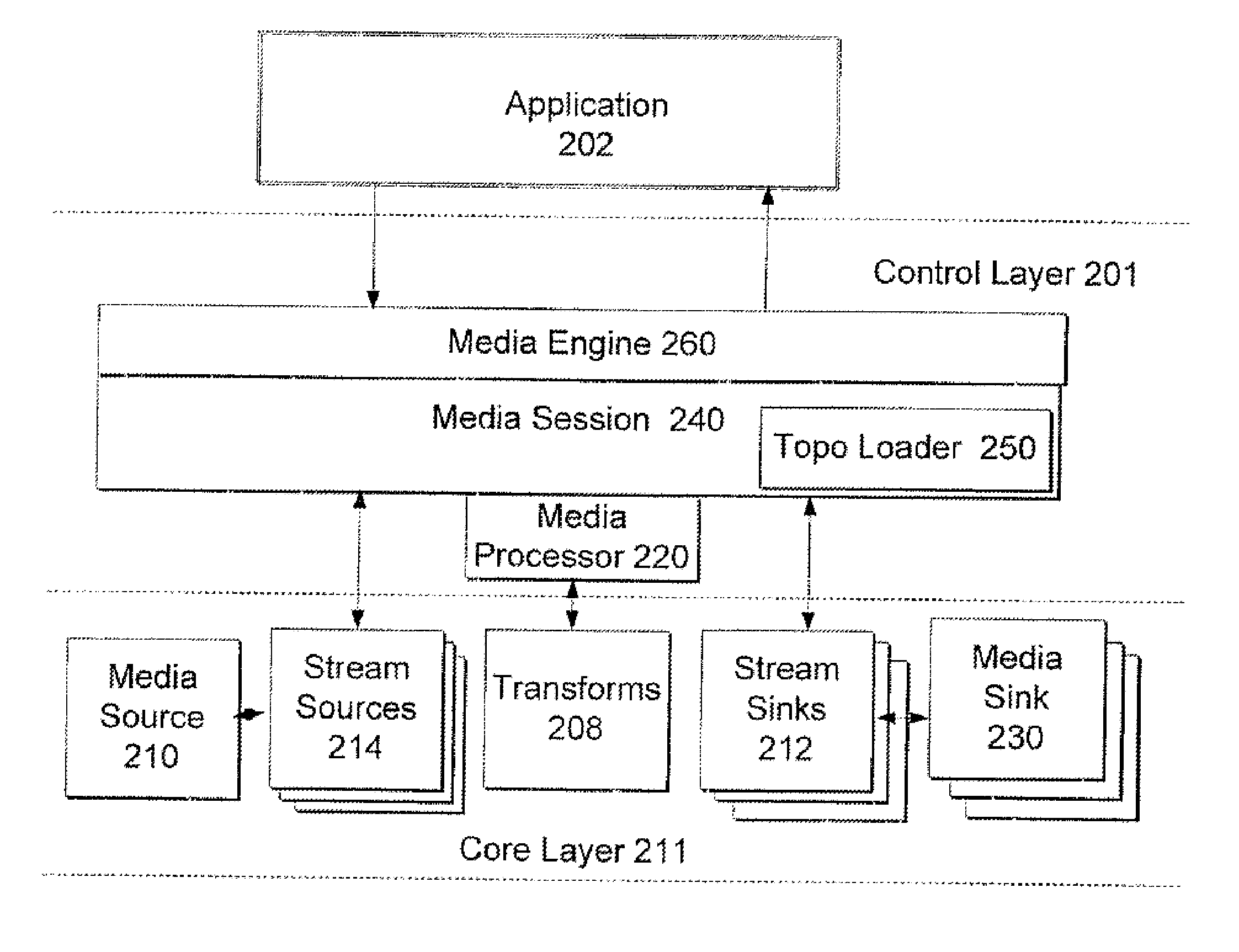
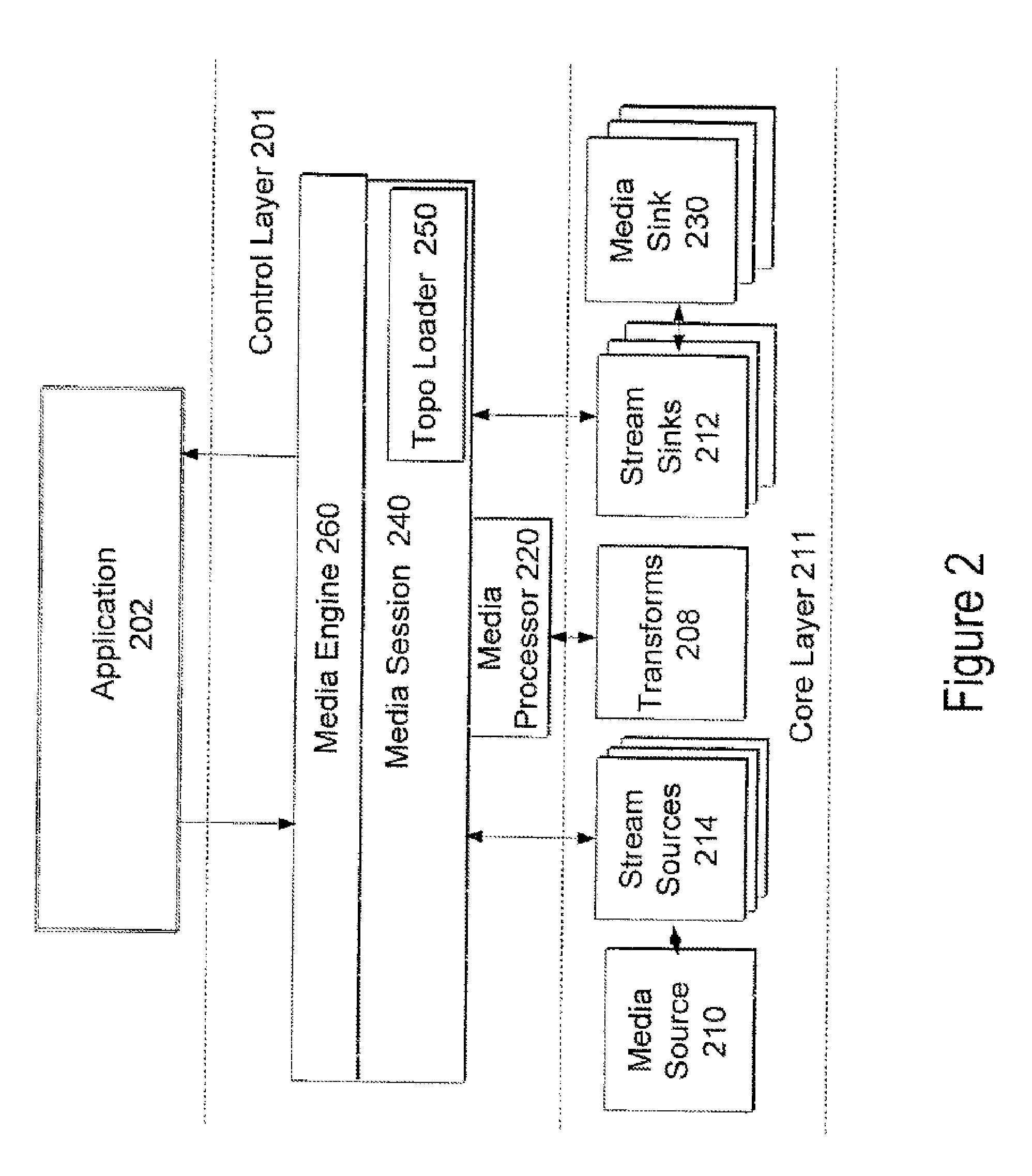
Media foundation media processor
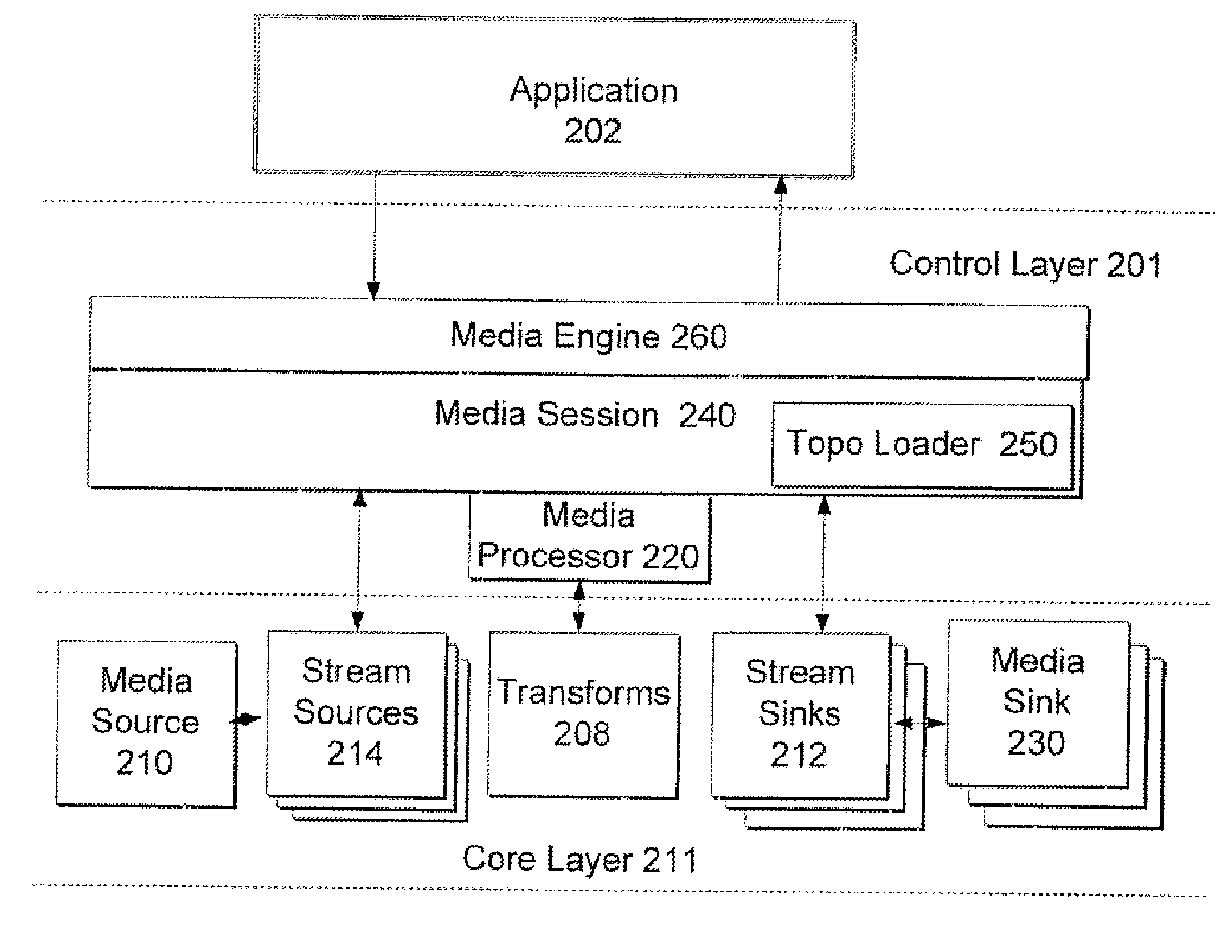
ActiveUS7555540B2Digital data processing detailsElectronic editing digitised analogue information signalsComputer hardwareMultimedia streams
A system and method for a media processor separates the functions of topology creation and maintenance from the functions of processing data through a topology. The system includes a control layer including a topology generating element to generate a topology describing a set of input multimedia streams, one or more sources for the input multimedia streams, a sequence of operations to perform on the multimedia data, and a set of output multimedia streams, and a media processor to govern the passing of the multimedia data as described in the topology and govern the performance of the sequence of multimedia operations on the multimedia data to create the set of output multimedia streams. The core layer includes the input media streams, the sources for the input multimedia streams, one or more transforms to operate on the multimedia data, stream sinks, and media sinks to provide the set of output multimedia streams.
Owner:MICROSOFT TECH LICENSING LLC
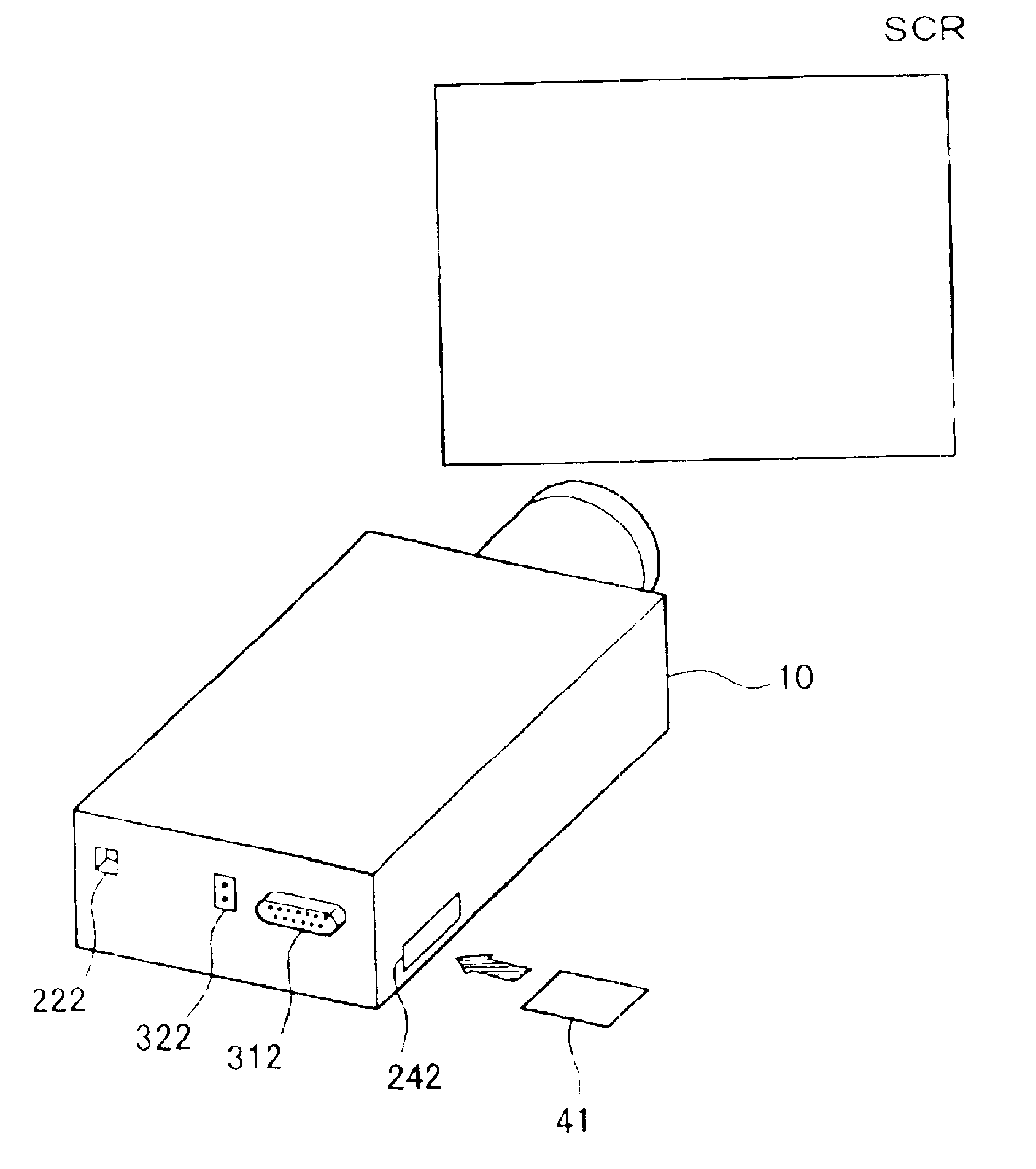
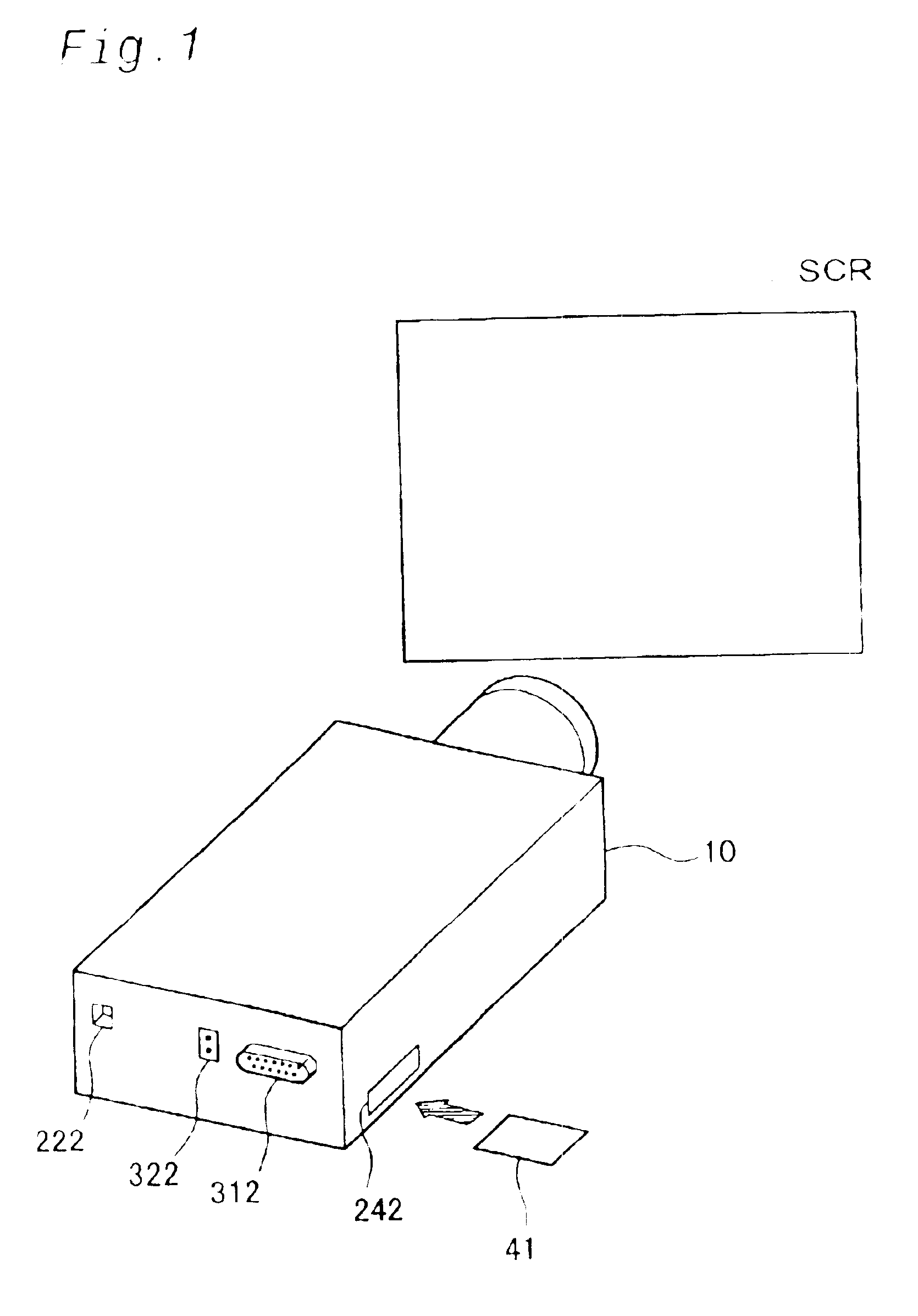
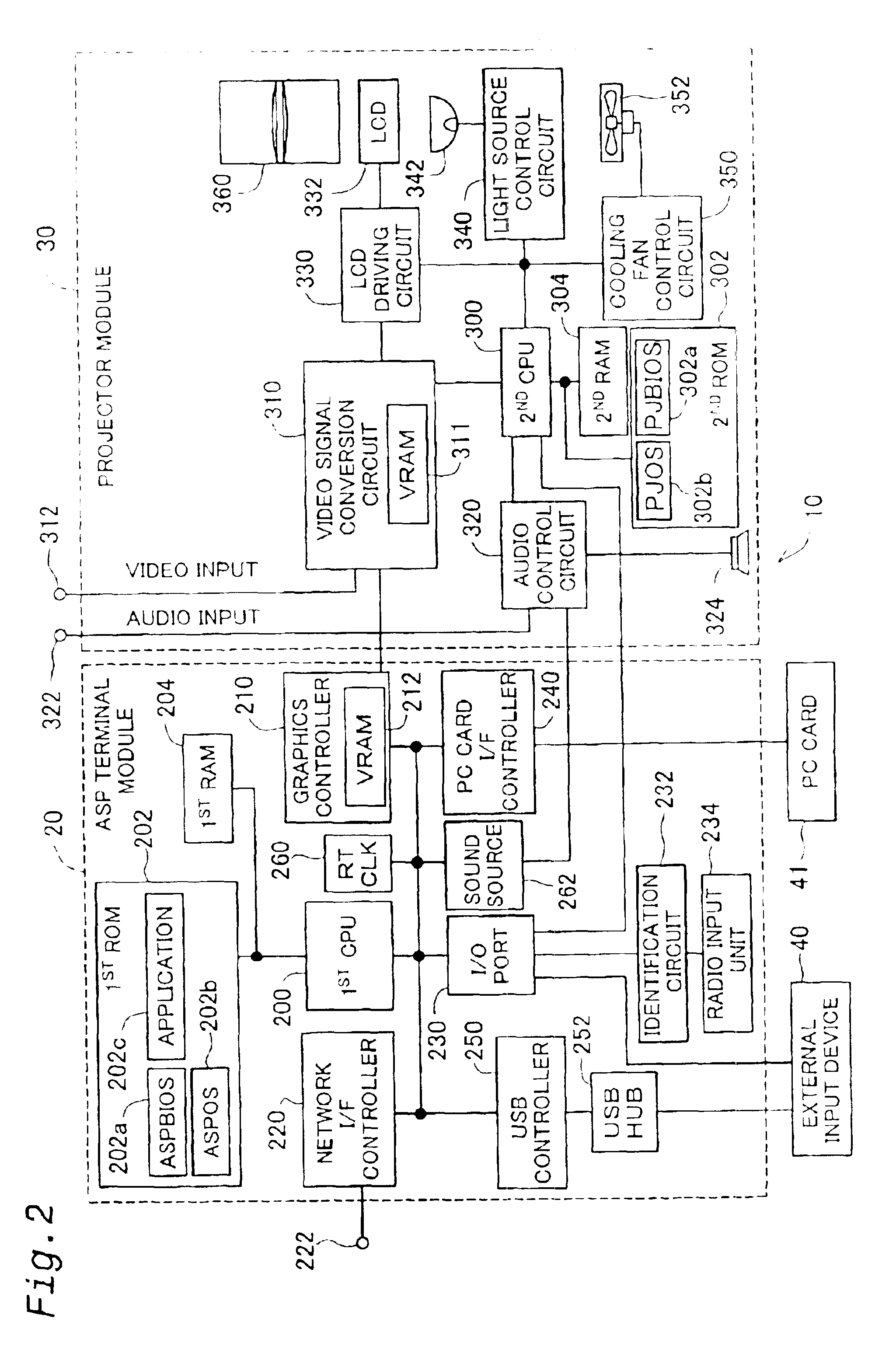
Actuation of projector by system stored in mobile memory
InactiveUS6877091B2Easy to updateTelevision system detailsDigital data processing detailsOperational systemControl system
A projector including a computer has: an internal storage device that stores therein a basic system, which is executed first by the computer on actuation of the projector, and a first control system that is activated through processing of the basic system to control operations of the projector; and a memory controller that reads information stored in a mobile memory. On actuation of the projector, the basic system reads information stored in a specific area of the mobile memory attached to the memory controller prior to activation of the first control system, identifies whether or not the information in the specific area is a specific piece of information, and, when the information in the specific area is identified as the specific piece of information, activates a second control system stored in the mobile memory, in place of the first control system. This arrangement enables the projector to utilize a new operating system.
Owner:SEIKO EPSON CORP
System and method for generating embedded resource updates for output device
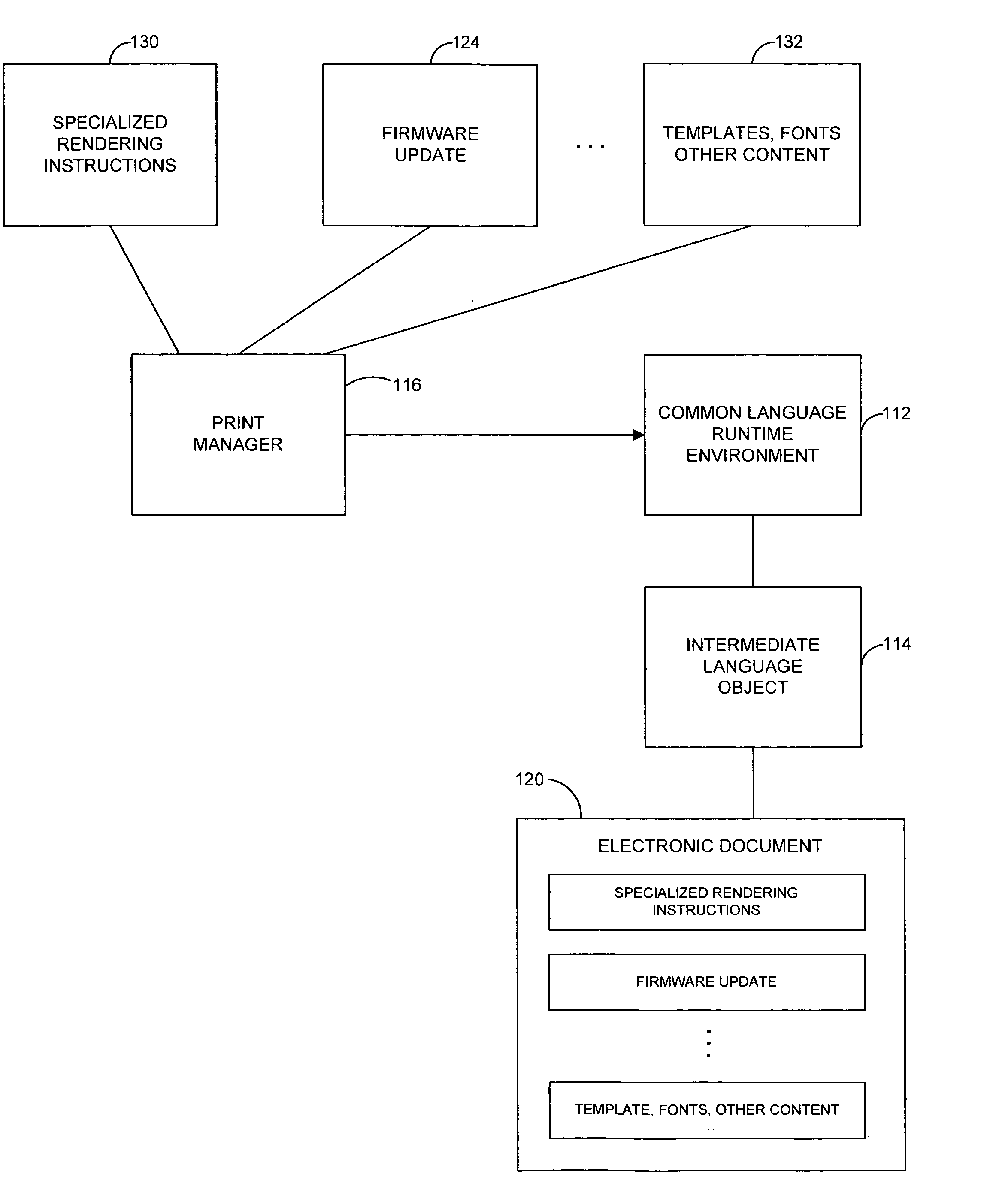
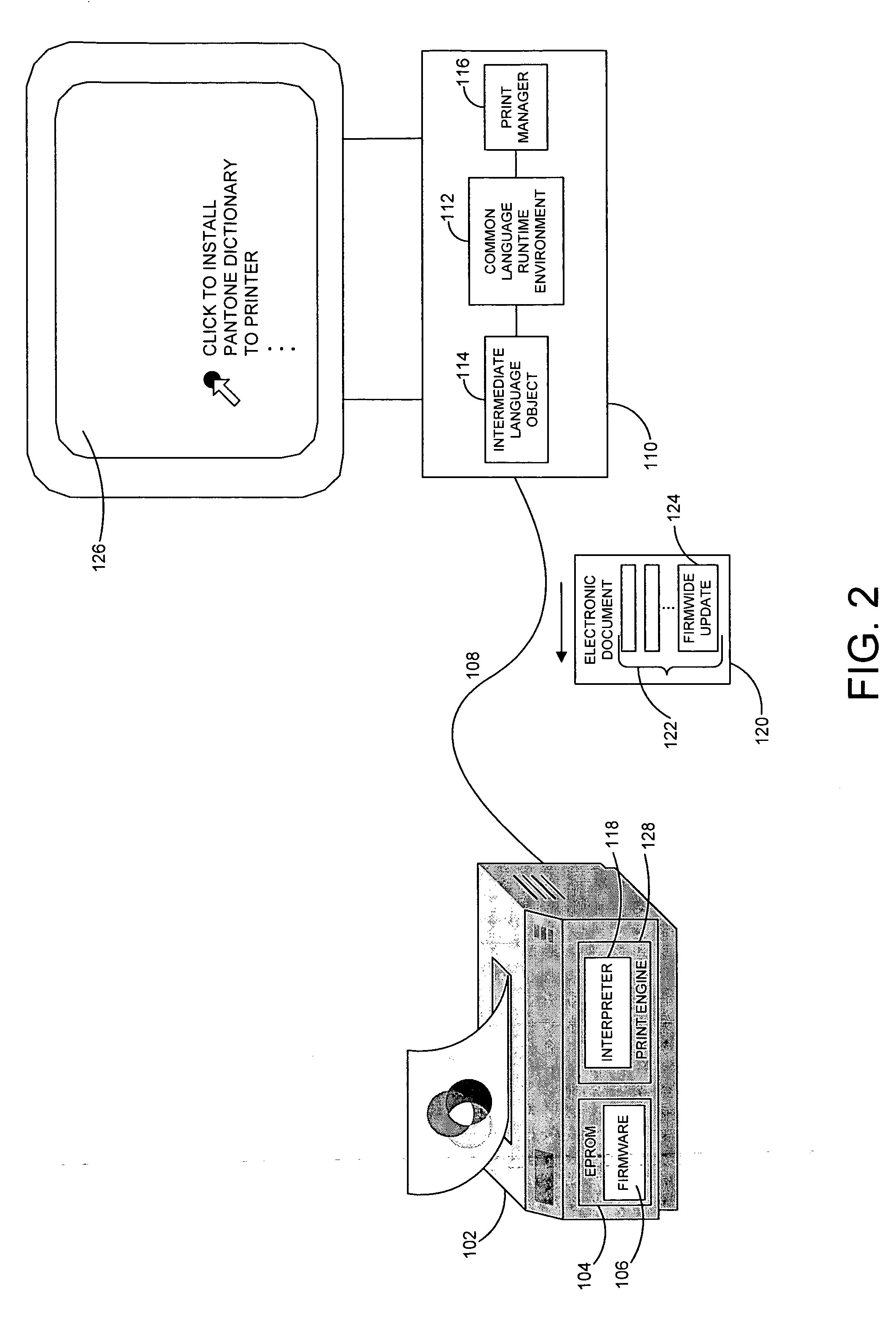
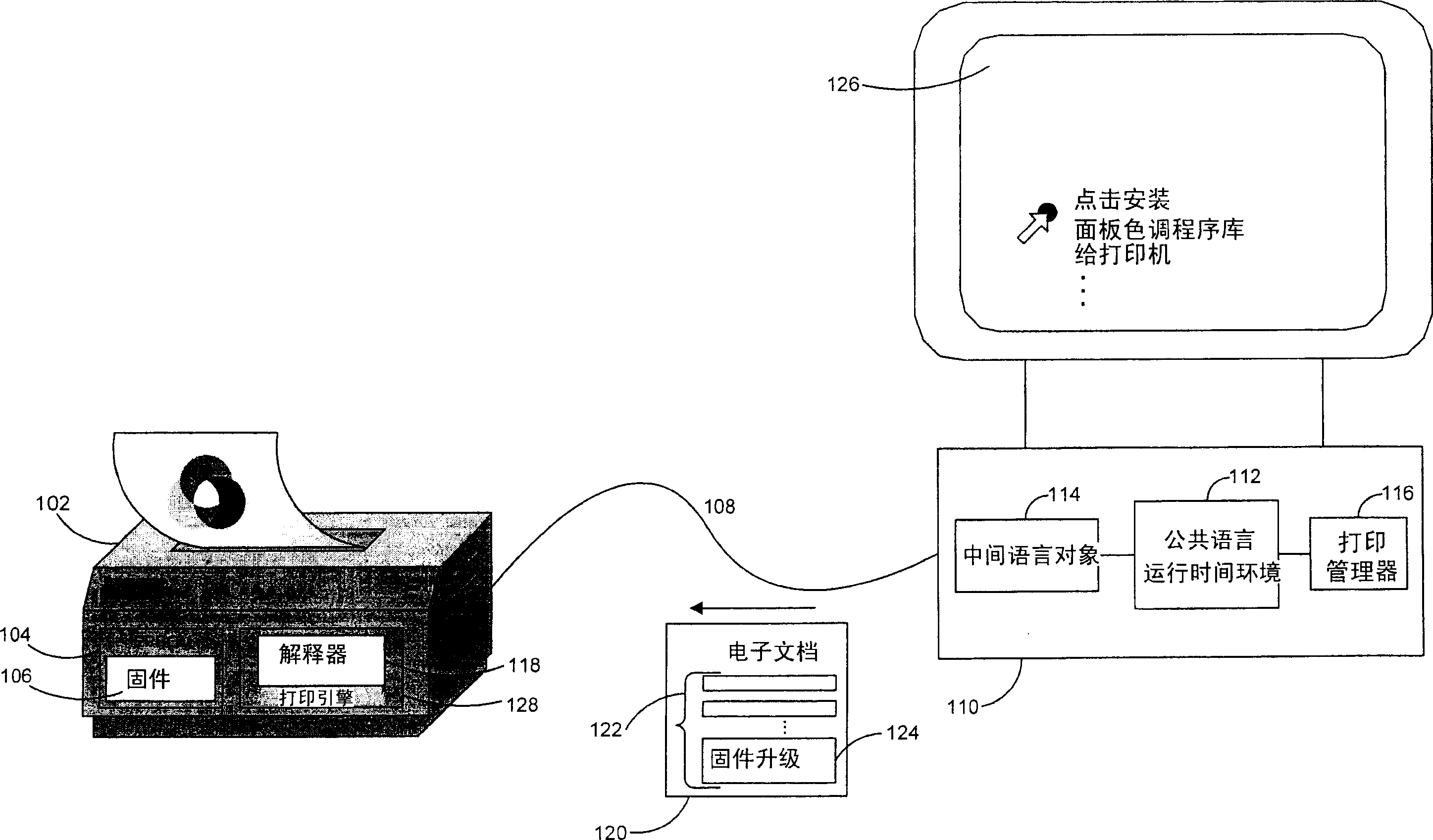
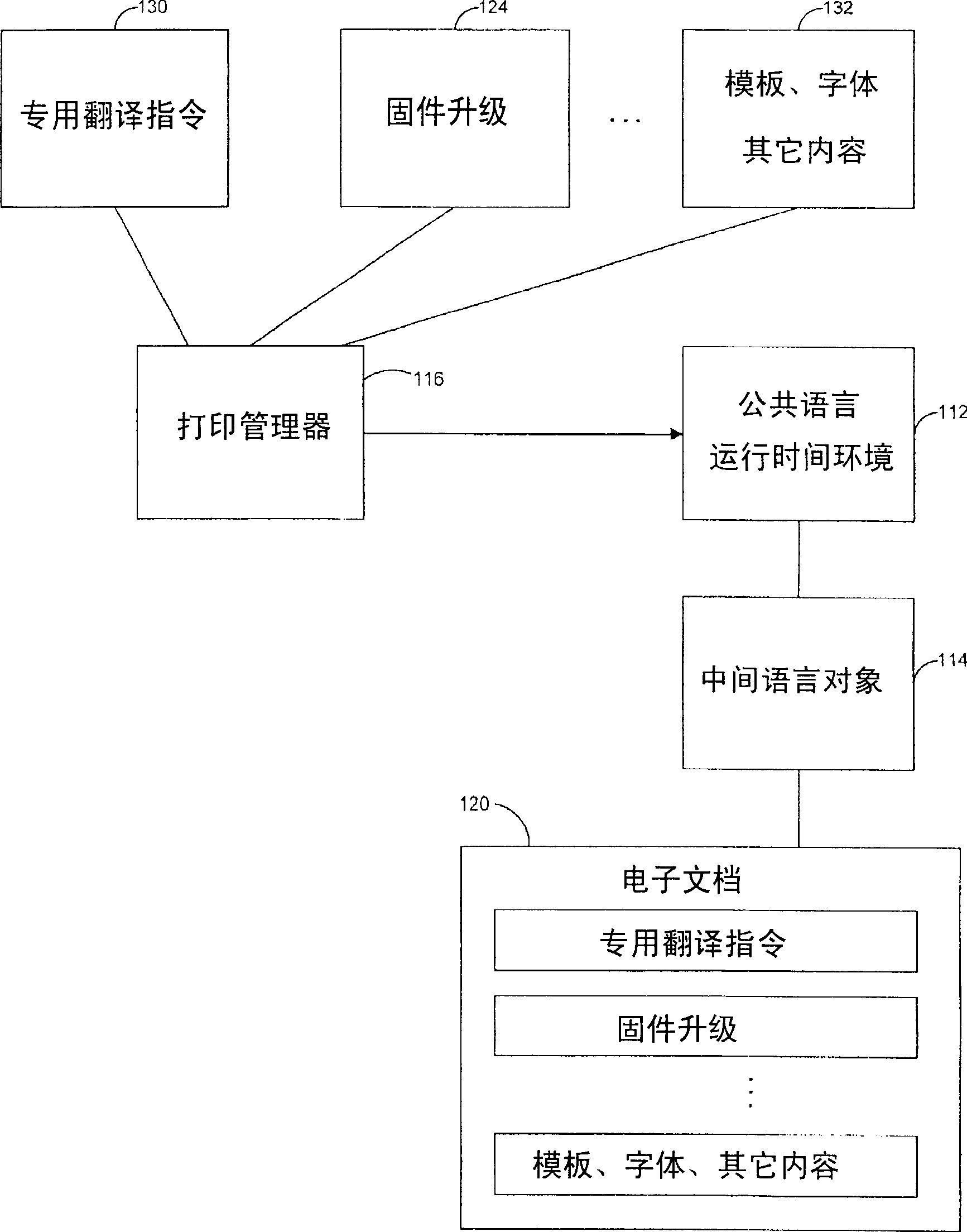
InactiveUS20050262497A1Reliable and powerful and flexibleProgram control using record carriers with instructionsDigital computer detailsElectronic documentComputer printing
A system and related techniques generate an update to control programming, such as firmware, to embed in an electronic document and transmit to a printer, facsimile or other output device. Compatible printers or other output devices according to embodiments of the invention may contain an intermediate language interpreter which receives, interprets and executes the embedded update in the electronic document. That update may include for example an update to the printer's firmware, downloaded forms, fonts or other updates or enhancements which may for instance stored into EPROM or other memory in the output device. Because the resource update is encapsulated in an intermediate language object which may be universally interpreted by compatible printers, facsimile machines and other devices, updates may be delivered with a need to generate specialized code or follow specialized procedures for specific manufacturer's products.
Owner:MICROSOFT TECH LICENSING LLC
Media foundation media processor
InactiveUS20080168100A1Efficient processingDigital data processing detailsElectronic editing digitised analogue information signalsMultimedia streamsComputer hardware
A system and method for a media processor separates the functions of topology creation and maintenance from the functions of processing data through a topology. The system includes a control layer including a topology generating element to generate a topology describing a set of input multimedia streams, one or more sources for the input multimedia streams, a sequence of operations to perform on the multimedia data, and a set of output multimedia streams, and a media processor to govern the passing of the multimedia data as described in the topology and govern the performance of the sequence of multimedia operations on the multimedia data to create the set of output multimedia streams. The core layer includes the input media streams, the sources for the input multimedia streams, one or more transforms to operate on the multimedia data, stream sinks, and media sinks to provide the set of output multimedia streams.
Owner:MICROSOFT TECH LICENSING LLC
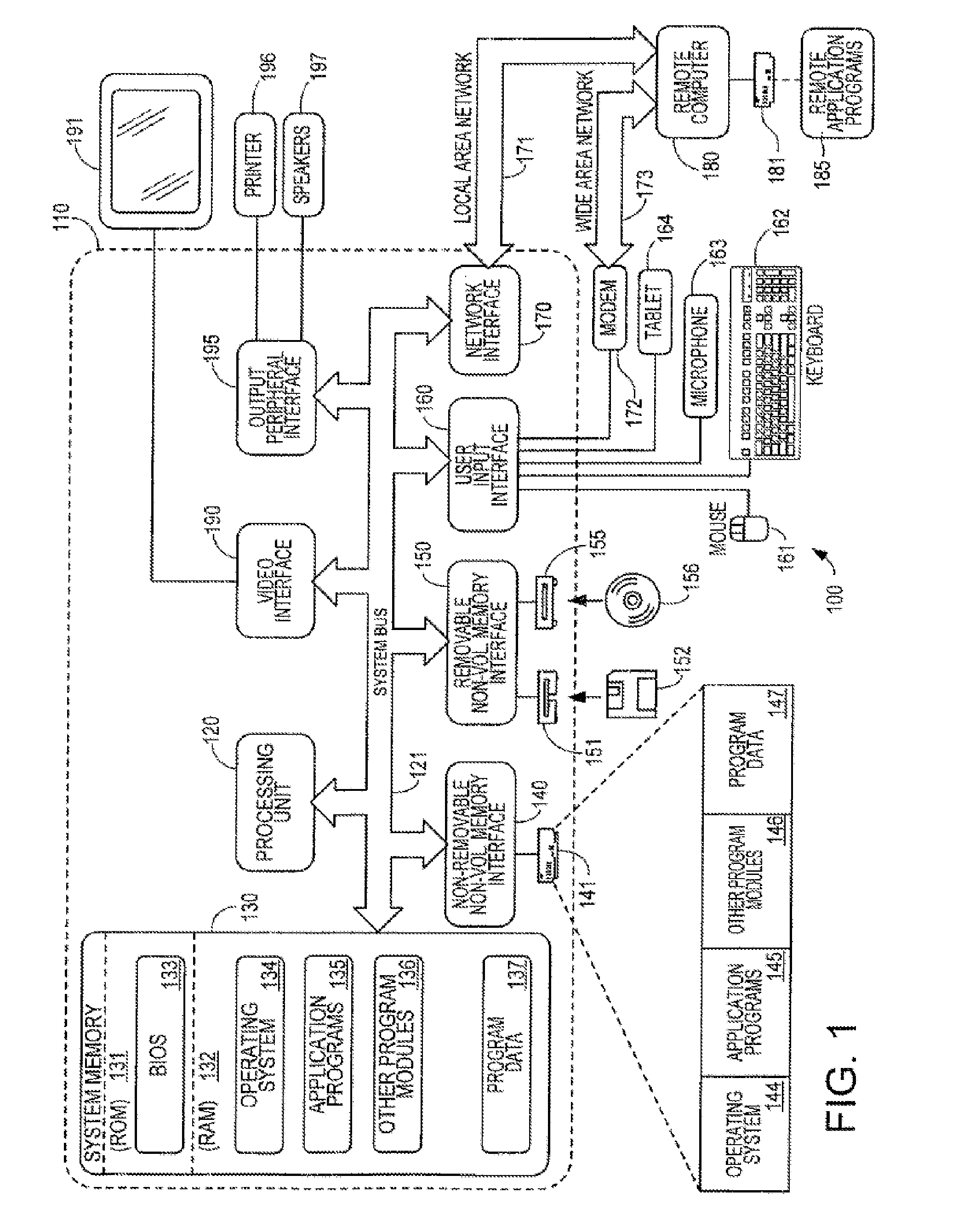
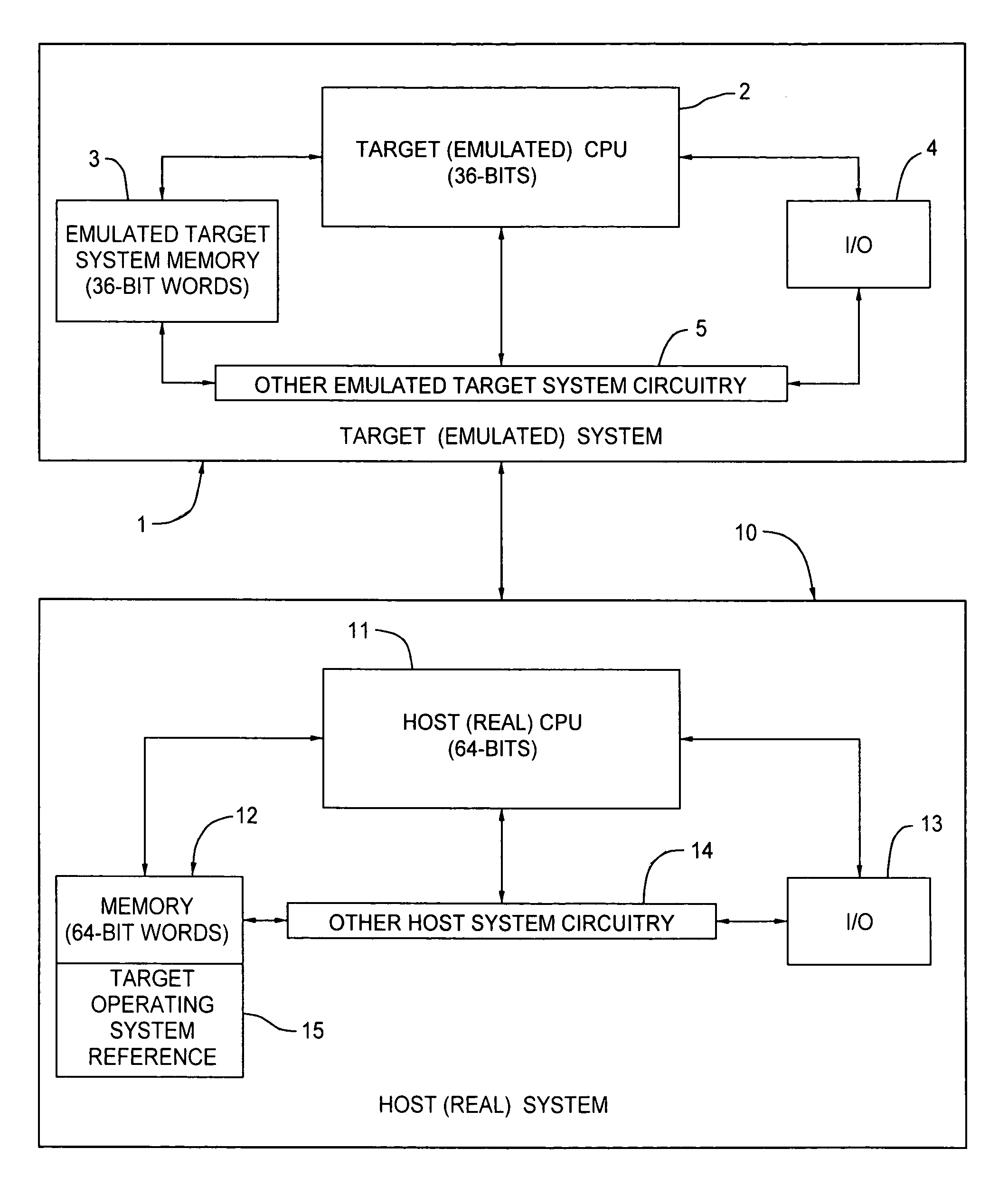
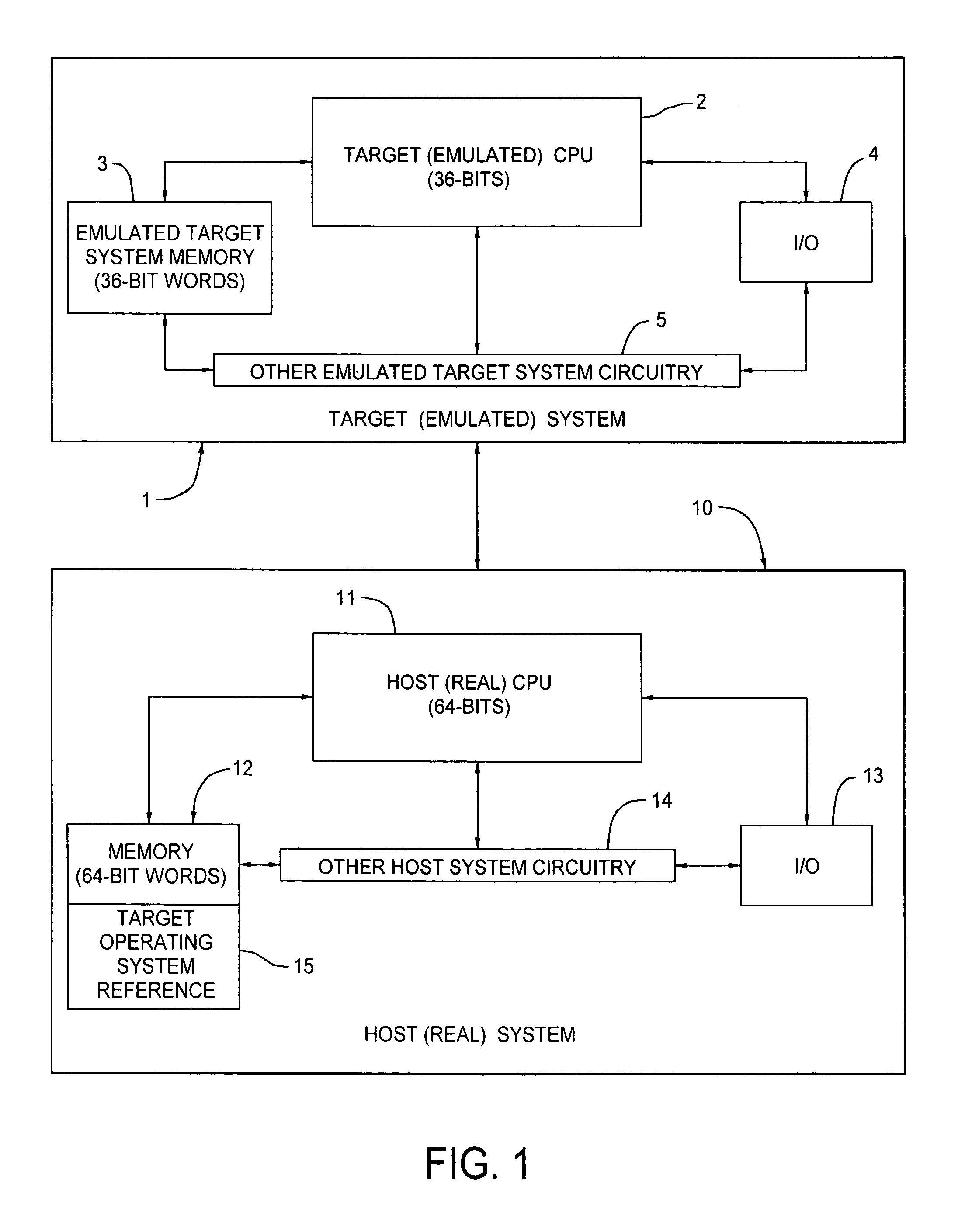
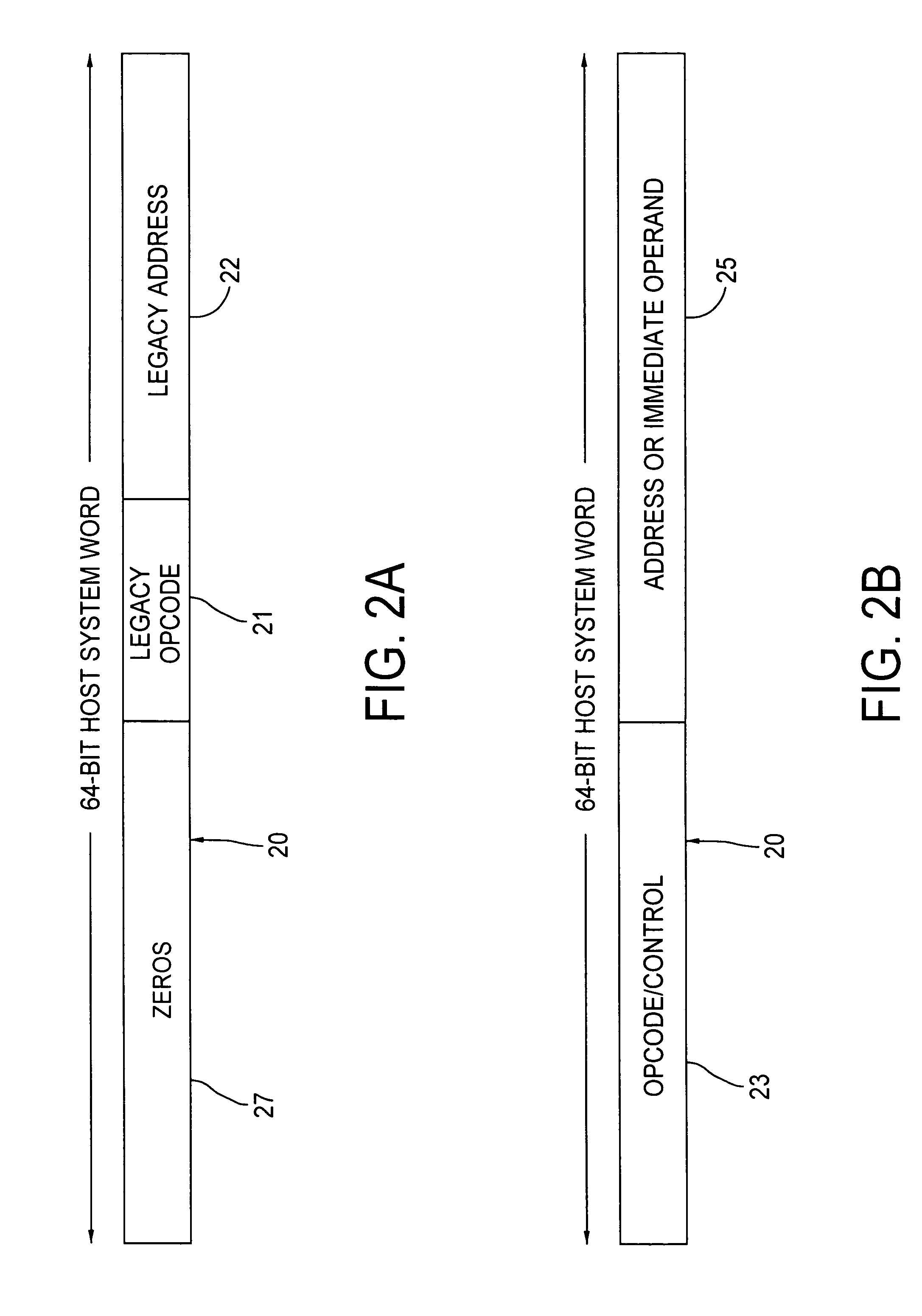
Host computer system emulating target system legacy software and providing for incorporating more powerful application program elements into the flow of the legacy software
ActiveUS7809547B2Adding to and improving performanceImprove abilitiesProgram control using record carriers with instructionsDigital computer detailsProprietary hardwareOperational system
As manufacturers of very fast and powerful commodity processors continue to improve the capabilities of their products, it has become practical to emulate the proprietary hardware and operating systems of powerful older computers on platforms built using commodity processors such that the manufacturers of the older computers can provide new systems which allow their customers to continue to use their highly-regarded proprietary legacy software on state-of-the-art new computer systems by emulating the older computer in software that runs on the new systems. In an example of the subject invention, a 64-bit Cobol Virtual Machine instruction provides the capability of adding to or improving the performance of legacy 36-bit Cobol code. Legacy Cobol instructions can be selectively diverted, in the host CPU, to a 64 bit Virtual Machine Implementation. The output legacy and new Cobol code is compiled in a dedicated implementation of the Cobol compiler, and the output of the special purpose compiler is emulated in a special purpose software emulator, separate from the main software emulator that handles the normal 36-bit stream of legacy code.
Owner:BULL HN INFORMATION SYST INC
Media foundation media processor
InactiveUS20080168101A1Efficient processingDigital data processing detailsElectronic editing digitised analogue information signalsComputer hardwareMultimedia streams
A system and method for a media processor separates the functions of topology creation and maintenance from the functions of processing data through a topology. The system includes a control layer including a topology generating element to generate a topology describing a set of input multimedia streams, one or more sources for the input multimedia streams, a sequence of operations to perform on the multimedia data, and a set of output multimedia streams, and a media processor to govern the passing of the multimedia data as described in the topology and govern the performance of the sequence of multimedia operations on the multimedia data to create the set of output multimedia streams. The core layer includes the input media streams, the sources for the input multimedia streams, one or more transforms to operate on the multimedia data, stream sinks, and media sinks to provide the set of output multimedia streams.
Owner:MICROSOFT TECH LICENSING LLC
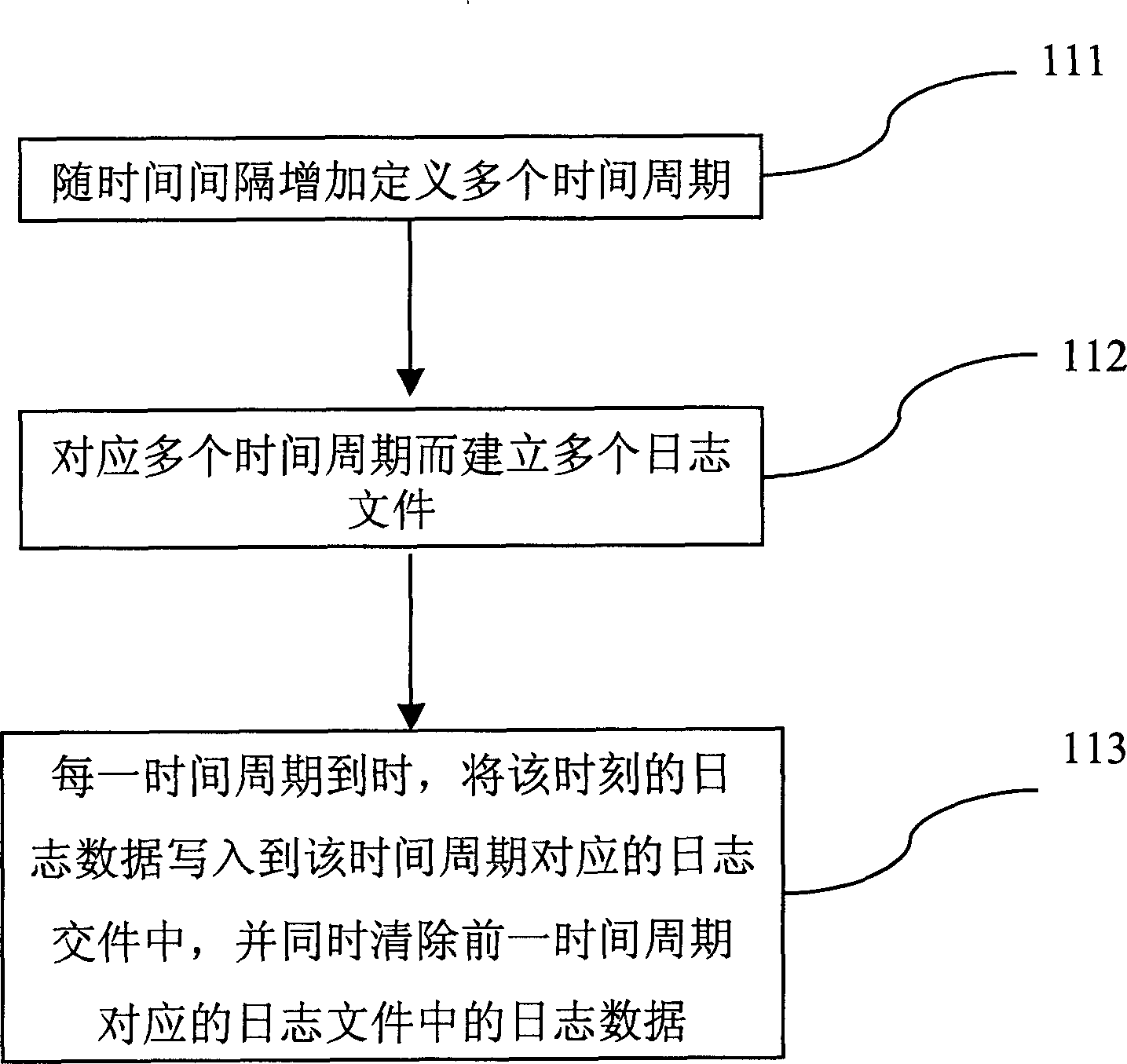
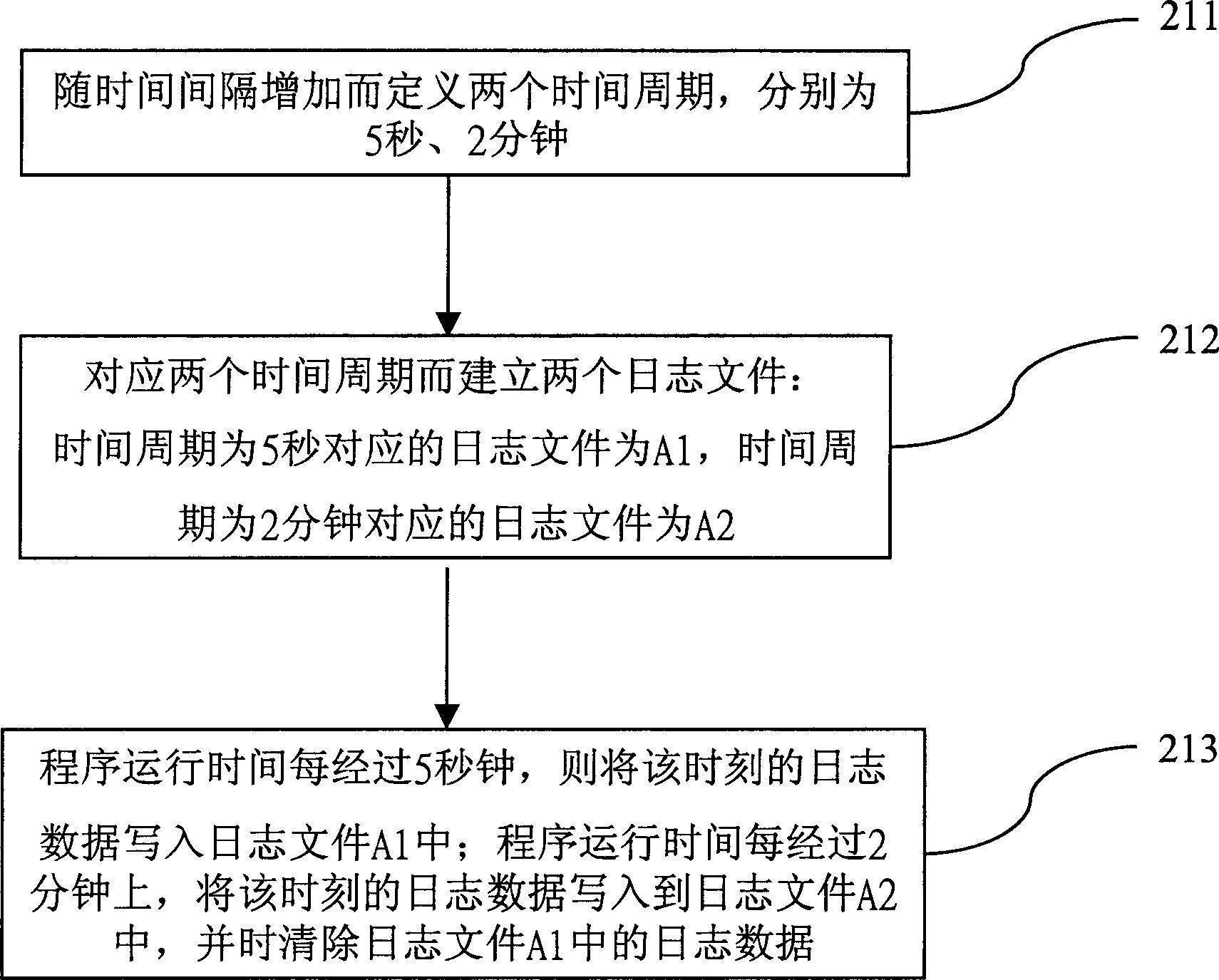
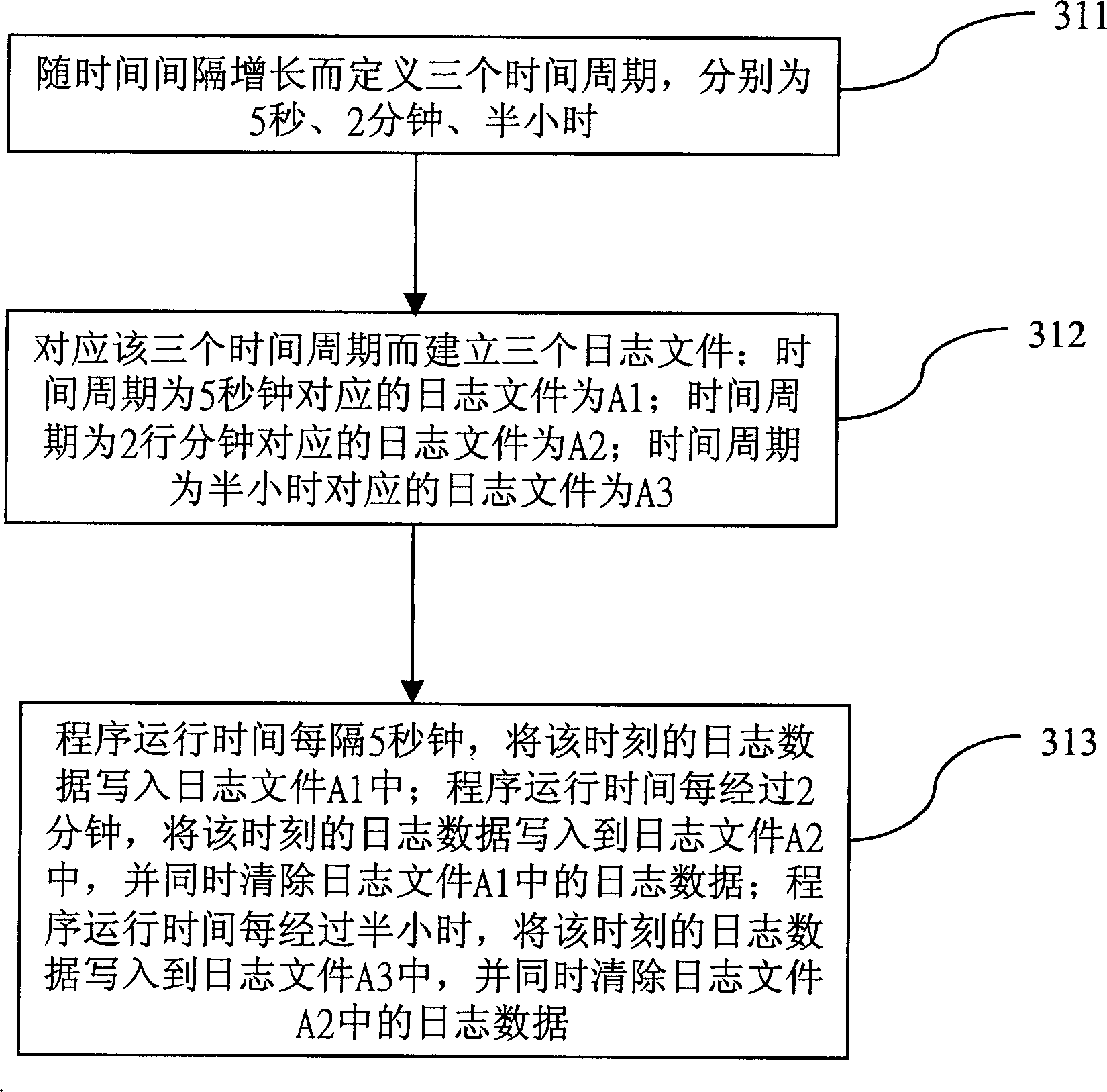
Dynamic journal recording method
InactiveCN1506805AProgram control using record carriers with instructionsMemory systemsProfile analysisData mining
The present invention provides one kind of dynamic journal recording method, and journal data may be recorded dynamically in different journal documents according to program operating period. First, several time periods in different time interval are defined; then several corresponding journal documents are established; and in any time, and the journal data are written into journal document corresponding to the time period while the journal data of the foregoing time period in the journal document are eliminated. The said dynamic journal recording method can limit the volume of the total journal document, and this saves magnetic disc space and raises data analyzing efficiency.
Owner:INVENTEC CORP
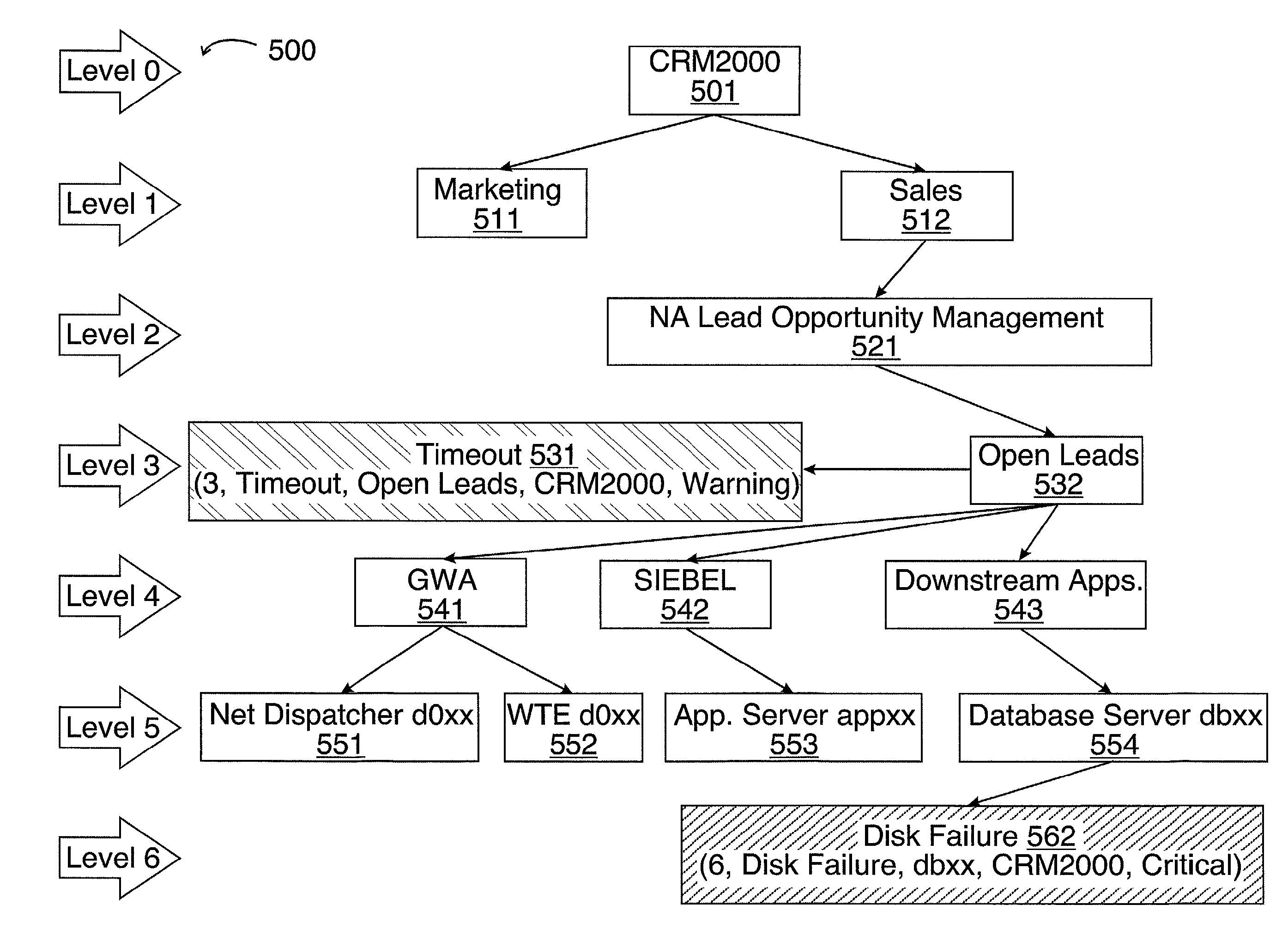
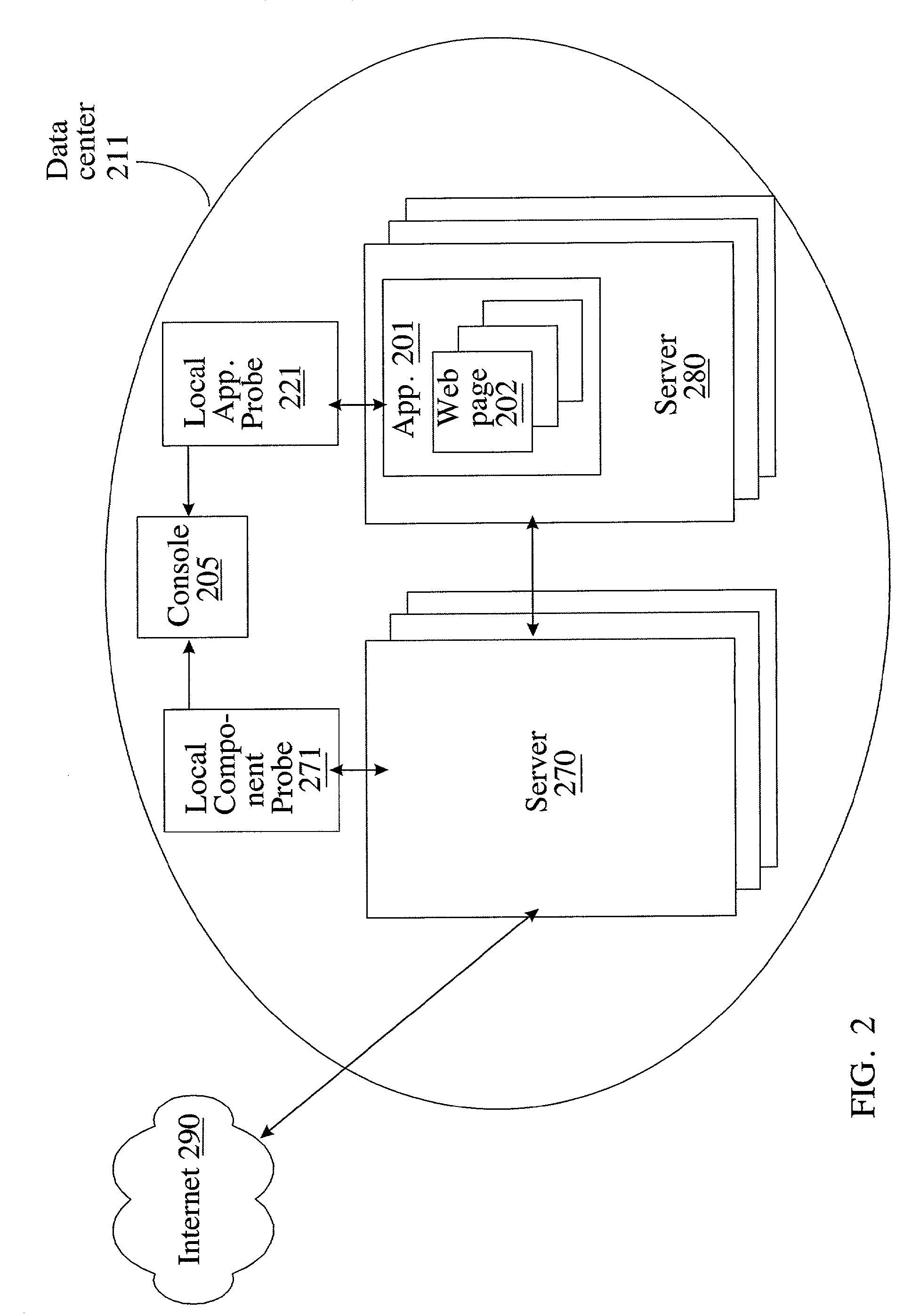
Graphics for end to end component mapping and problem-solving in a network environment
InactiveUS8316381B2Program control using record carriers with instructionsDigital computer detailsGraphicsProblem solve
An example of a solution provided here comprises receiving as input at least one event (chosen from an event generated by an application probe, and an event generated by a component probe), and providing graphical output based on the inputs, whereby a user correlates a component problem with a performance problem affecting an application. Methods connected with graphics for end to end component mapping and problem-solving in a network environment, systems for executing such methods, and instructions on a computer-usable medium, for executing such methods, are provided.
Owner:INT BUSINESS MASCH CORP
Controlling an electronic device
InactiveCN1969250AEliminate distractionsReduce misidentificationInput/output for user-computer interactionDigital data processing detailsElectric equipmentComputer science
Owner:NOKIA CORP
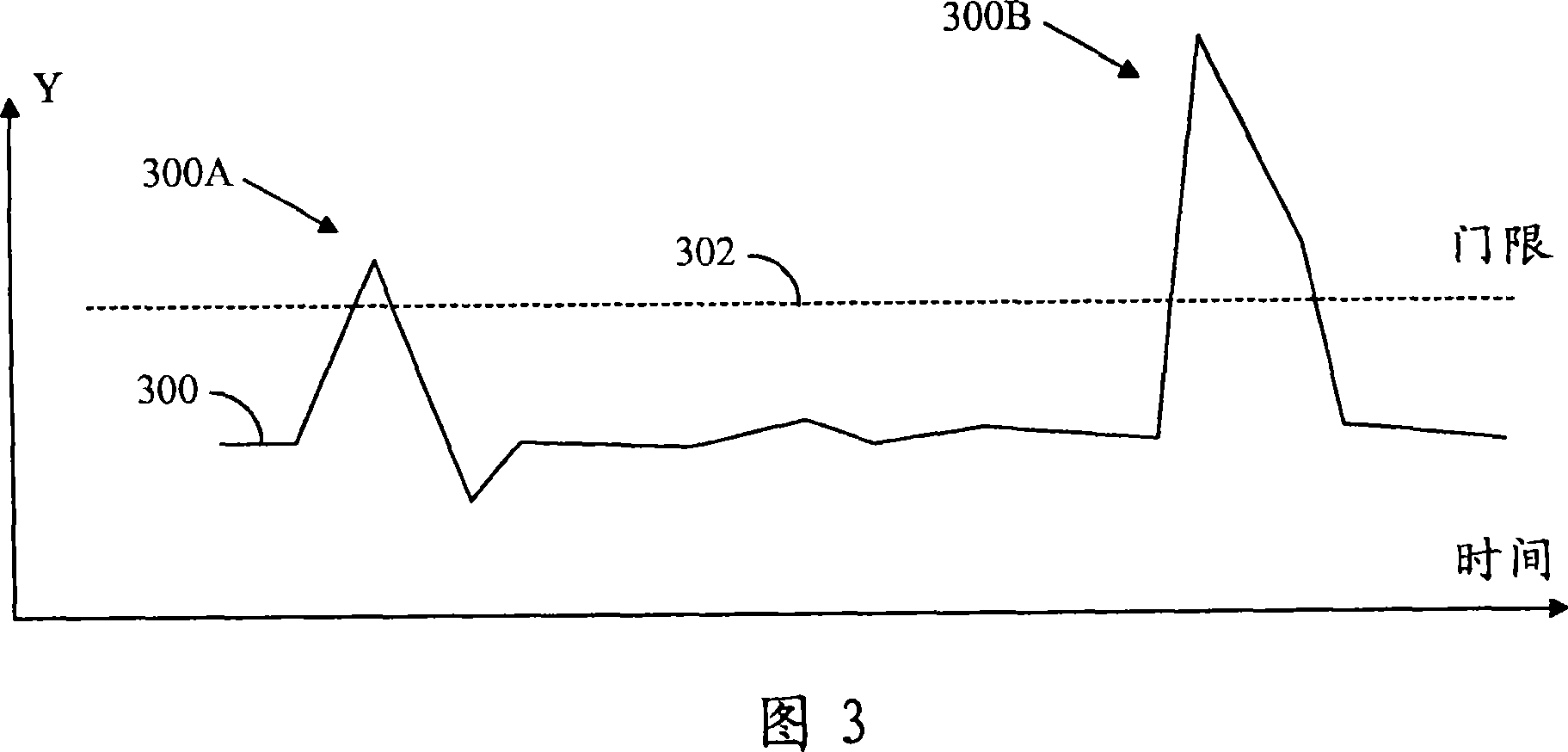
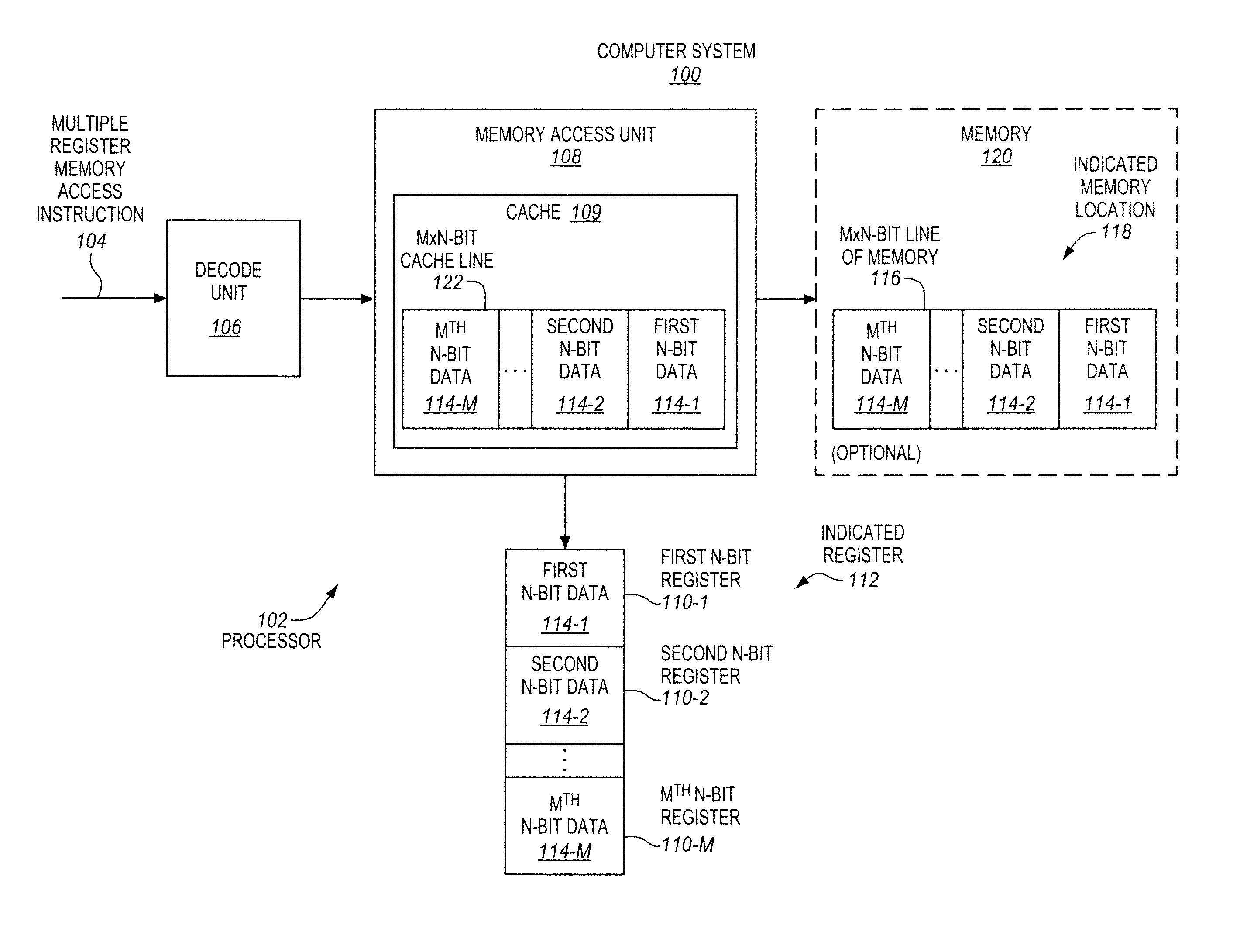
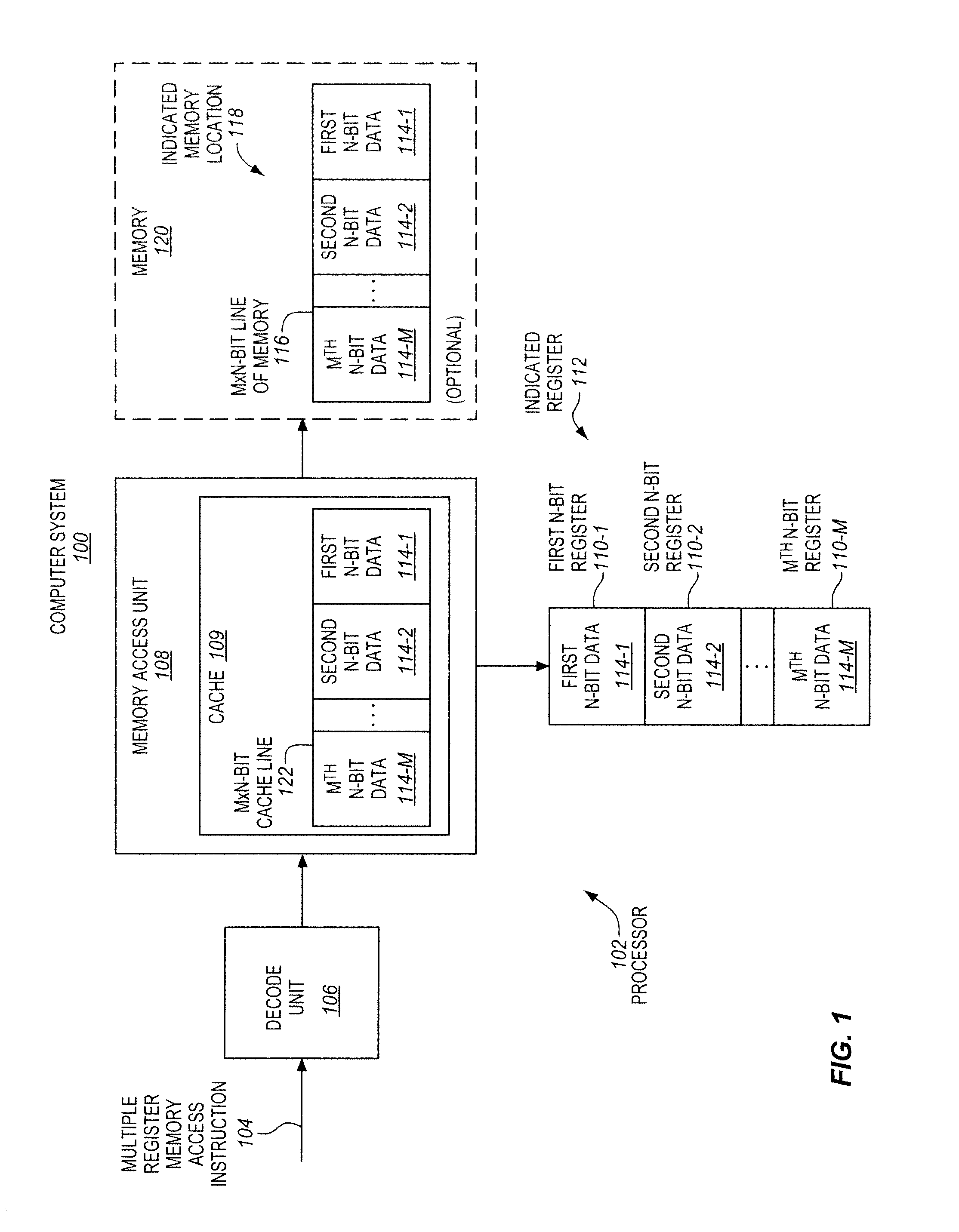
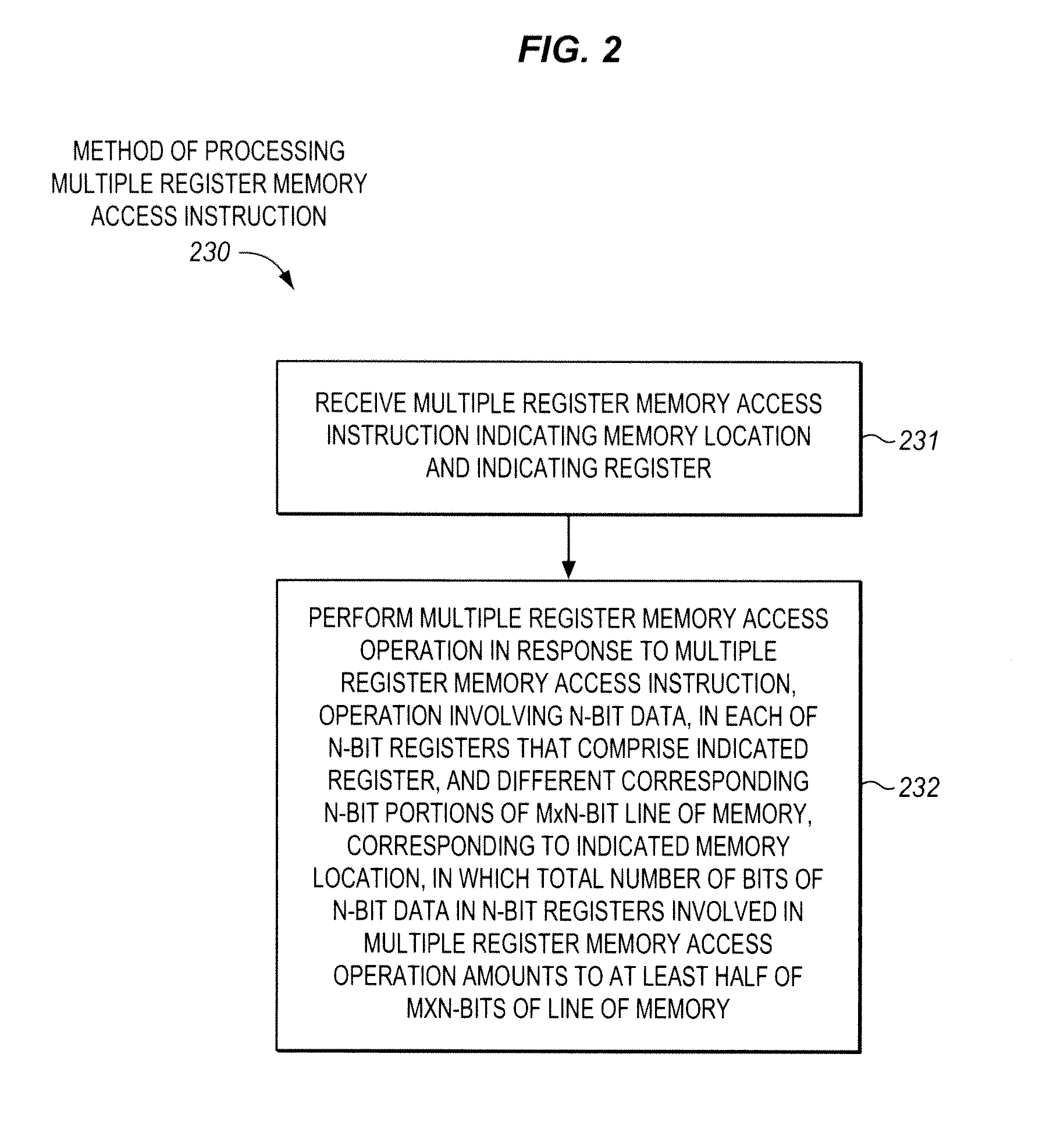
Multiple register memory access instructions, processors, methods, and systems
ActiveUS9424034B2Program control using record carriers with instructionsDigital storageBit lineProcessor register
Owner:INTEL CORP
Programmable logic controller (PLC) with an additional memory
InactiveCN1567181AProgram control using record carriers with instructionsInternal memoryProgrammable logic controller
It is a programmable logic controller with append memory which is to use data bus to connect a append memory and to store a direction order in the memory of the programmable logic controller body. When it reads this section direction order, it will self direct to the address of the append memory and execute its inner stored append program codes. In the situation without changing its inner memory, it can effectively provide a order expansion of the programmable logic controller.
Owner:DELTA ELECTRONICS INC
System and method for generating embedded resource updates for output device
InactiveCN1728092AProgram control using record carriers with instructionsDigital computer detailsElectronic documentOutput device
The present invention provides a system and related techniques generate an update to control programming, such as firmware, to embed in an electronic document and transmit to a printer, facsimile or other output device. Compatible printers or other output devices according to embodiments of the invention may contain an intermediate language interpreter which receives, interprets and executes the embedded update in the electronic document. That update may include for example an update to the printer's firmware, downloaded forms, fonts or other updates or enhancements which may for instance stored into EPROM or other memory in the output device. Because the resource update is encapsulated in an intermediate language object which may be universally interpreted by compatible printers, facsimile machines and other devices, updates may be delivered with a need to generate specialized code or follow specialized procedures for specific manufacturer's products.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for controlling encoded image production using image signatures
InactiveCN1898895AUser identity/authority verificationProgram control using record carriers with instructionsAuthorizationAutomated method
An automated method for authorizing and controlling the production of optically encoded images is provided. The method comprises receiving from a user data processor a request for authorization to produce an encoded image. The authorization request includes user-supplied data comprising at least one authentication image file. The method further comprises determining whether the user is authorized to produce an encoded image using the user-supplied data. Responsive to a determination that the user is authorized to produce an encoded image using the user-supplied data, an authentication image signature is generated from the at least one authentication image file using an image signature algorithm and a positive authorization response is returned to the user data processor. The positive authorization response includes the authentication image signature.
Owner:GROPHIC SECURITY SYST CORP
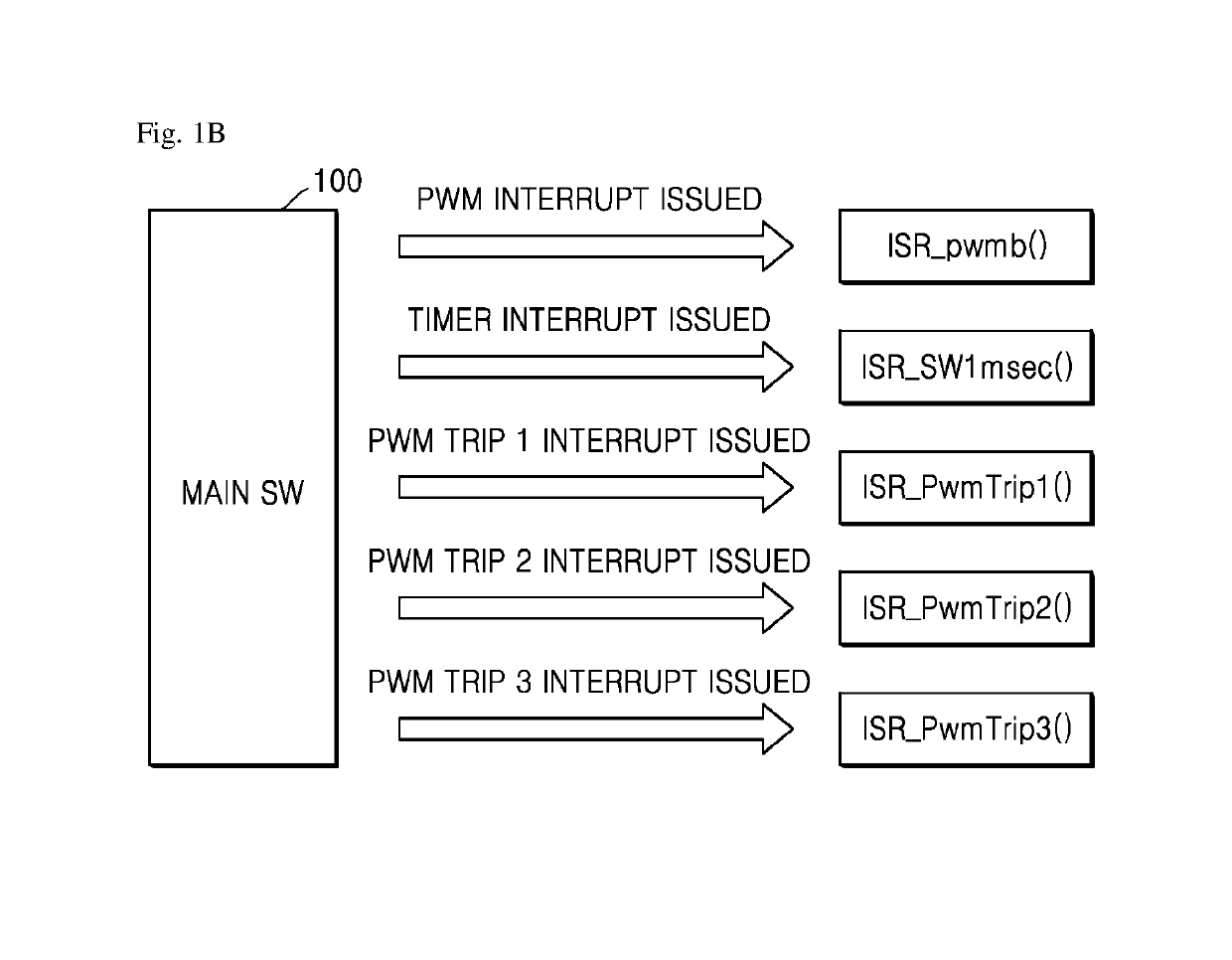
Method for controlling interrupt in inverter
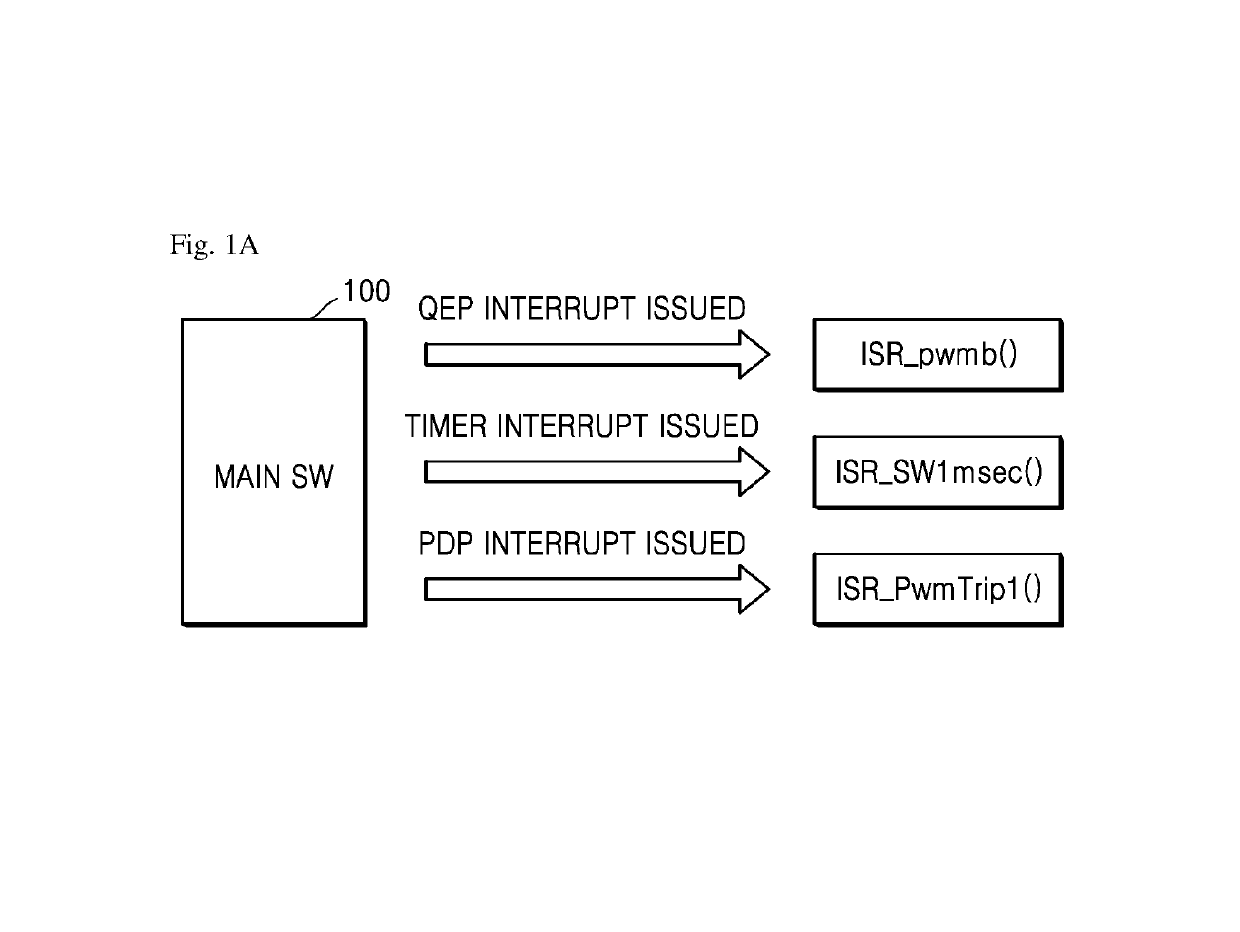
InactiveUS10275374B2Improve reusabilityShorten development timeProgramme controlProgram control using record carriers with instructionsFrequency changerEmbedded system
Owner:LSIS CO LTD
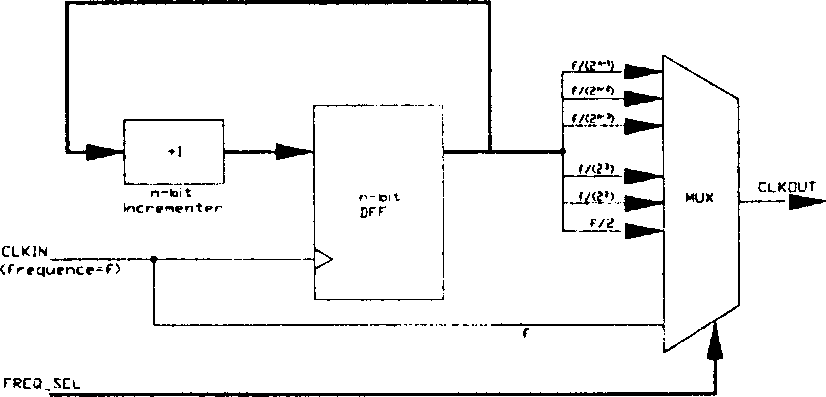
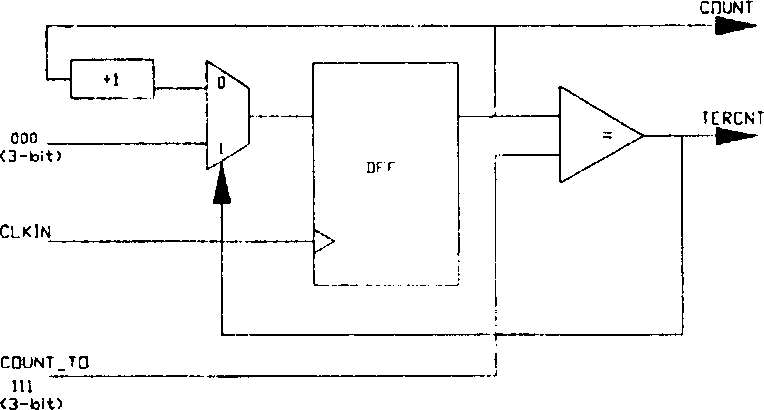
Sequencing frequency divider
InactiveCN1521593ANo clock jitter (glitch) problemProgram control using record carriers with instructionsPower supply for data processingProgram instructionEngineering
The invention provides a programmed frequency division apparatus comprising an n digit adder and an n digit type D trigger for switching an input clock into a target clock, and the input clock frequency is the m to the power of 2 times of the destination clock frequency, the adder produces a first output signal based on an adjustment parameter and a feedback signal. The type D trigger is connected with the adder to form a ring form loop for receiving a first output signal and the input clock and producing a second output signal.
Owner:ELAN MICROELECTRONICS CORPORATION
Seeding product information
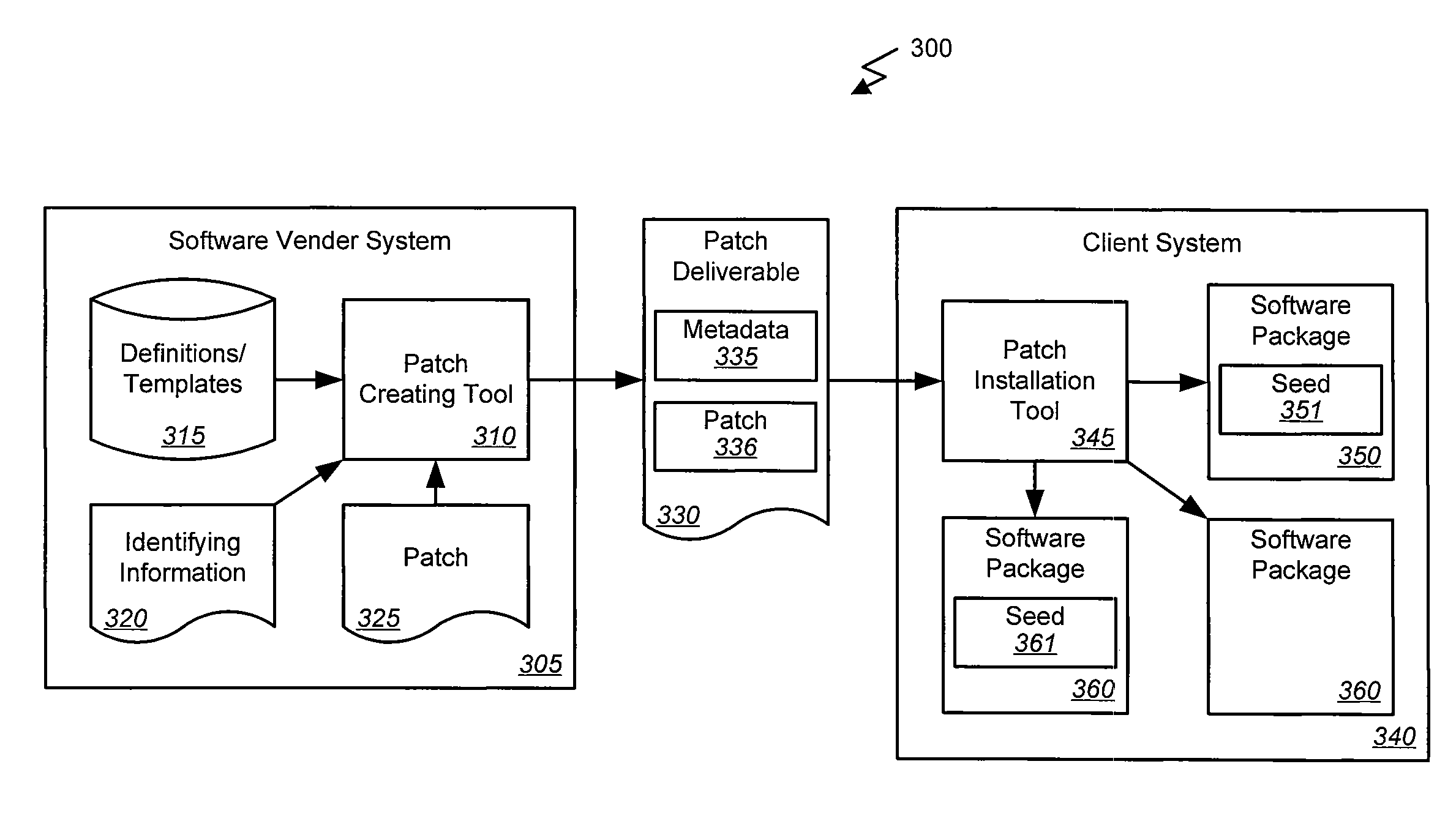
ActiveUS8615751B2Program control using record carriers with instructionsProgram loading/initiatingSoftware engineeringSoftware product line
Systems, methods, and machine-readable media are disclosed for patching software based on seeded product information. In one embodiment, patching software can comprise receiving a patch deliverable that can include a software patch and information identifying a target software package. The information identifying the target software package can be read and a determination can be made as to whether the information indicates a known software package. In response to determining the information indicates a known software package, the patch can be installed. In response to determining the information does not indicate a known software package options identifying software packages for which the patch may be used can be presented to a user and a selection of one of the packages can be received. The selected software package can be seeded with the information identifying the target software package and the patch can be installed for the selected software product.
Owner:ORACLE INT CORP
Computer implementing method for providing an electronic intermediate platform
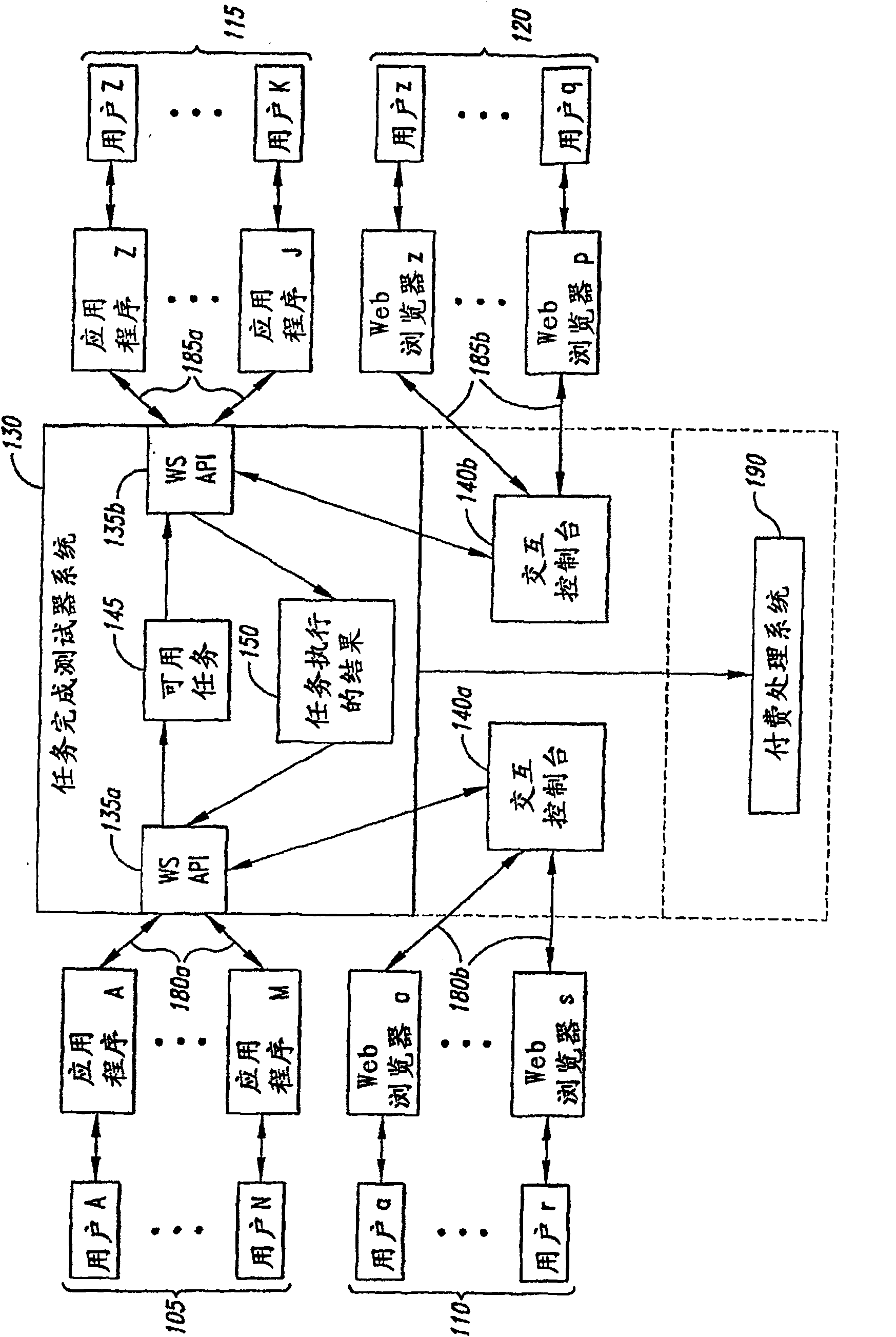
ActiveCN100565448CFinanceProgram control using record carriers with instructionsInteraction controlWeb browser
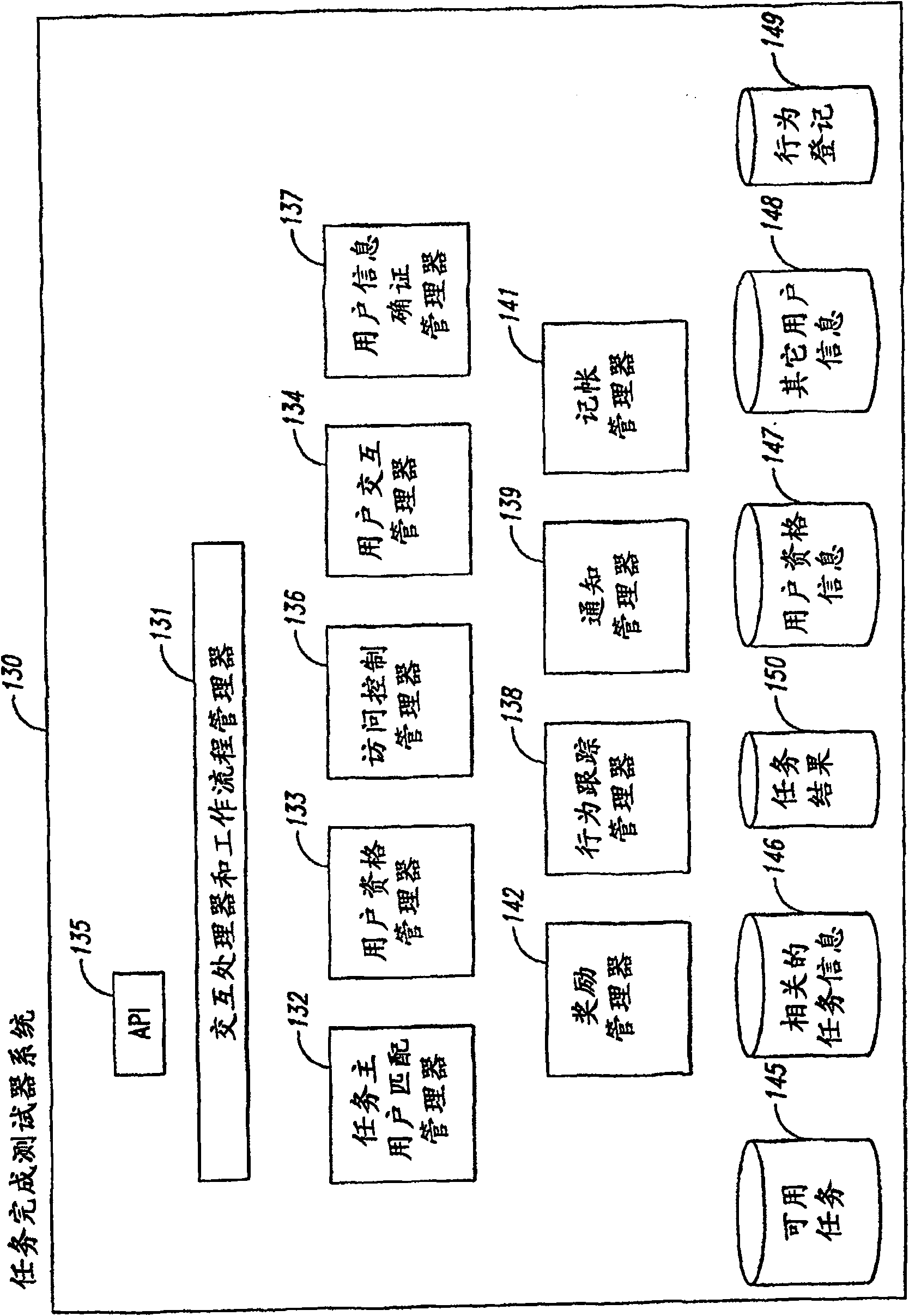
The invention describes task-performer users (120) of various types who interact with the electronic marketplace to perform available tasks. The various task performer users (120) interact with a web browser program executing on the task performer client computing system that communicates (185b) with the interactive console (140b) of the TFF system ).
Owner:AMAZON TECH INC
Fusion mapping method of common information model and IEC61850 model
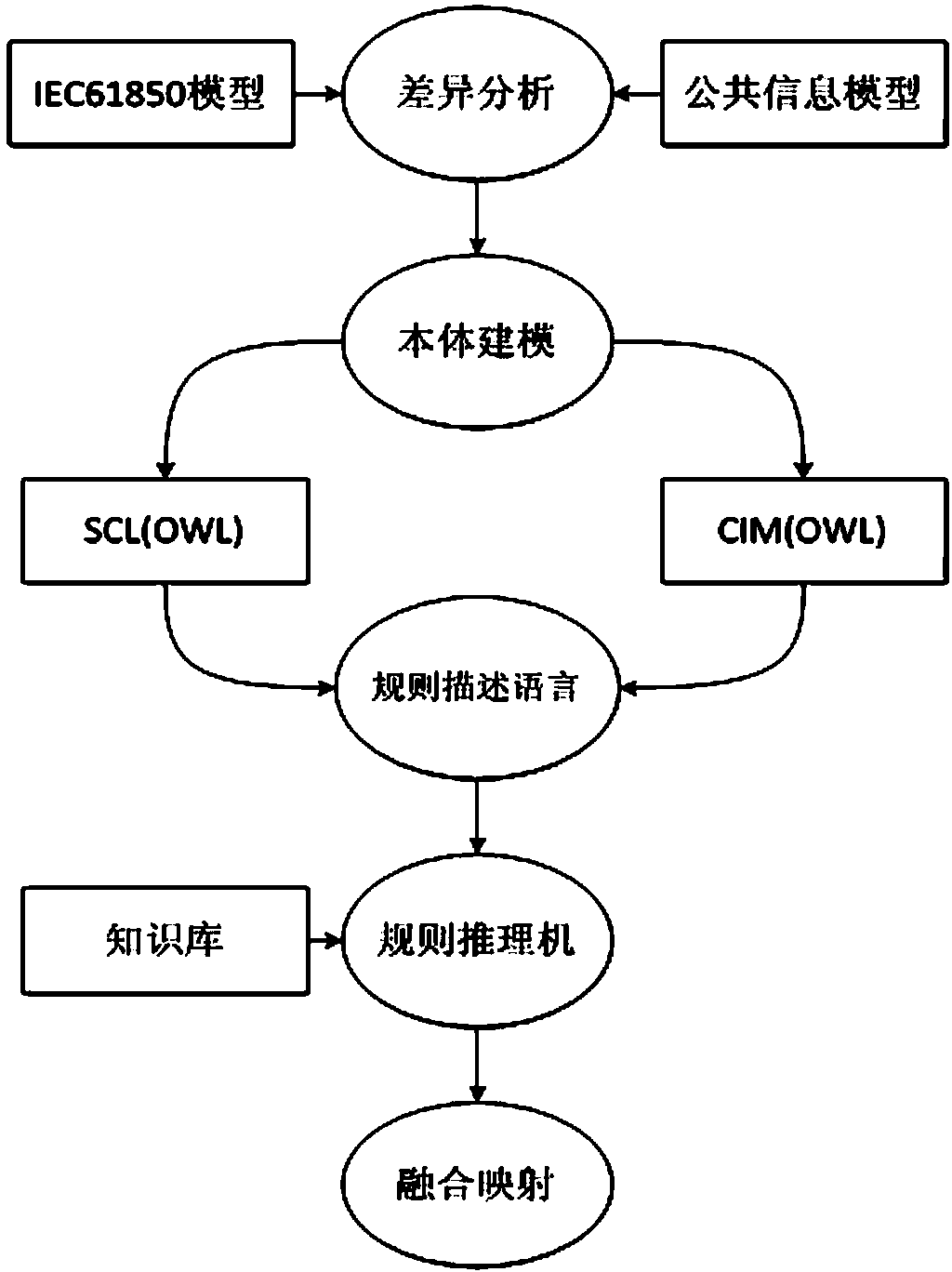
InactiveCN104346130AImprove interoperabilityAchieve integrationProgram control using record carriers with instructionsTransformerMaster station
The invention discloses a fusion mapping method of a common information model and an IEC61850 model, and fusion mapping of the common information model and the IEC61850 model is realized by using a rule reasoning method and combining rule description language. According to the fusion mapping method, model mapping is performed on the common information model and the IEC61850 model by using the rule reasoning technique, so that interoperation of the common information model and the IEC61850 model is realized, model fusion of a distribution master station and a transformer substation is realized, the workload of interaction of the common information model and the IEC61850 model is reduced and the work management efficiency of the distribution master station and the transformer substation is improved.
Owner:STATE GRID CORP OF CHINA +2
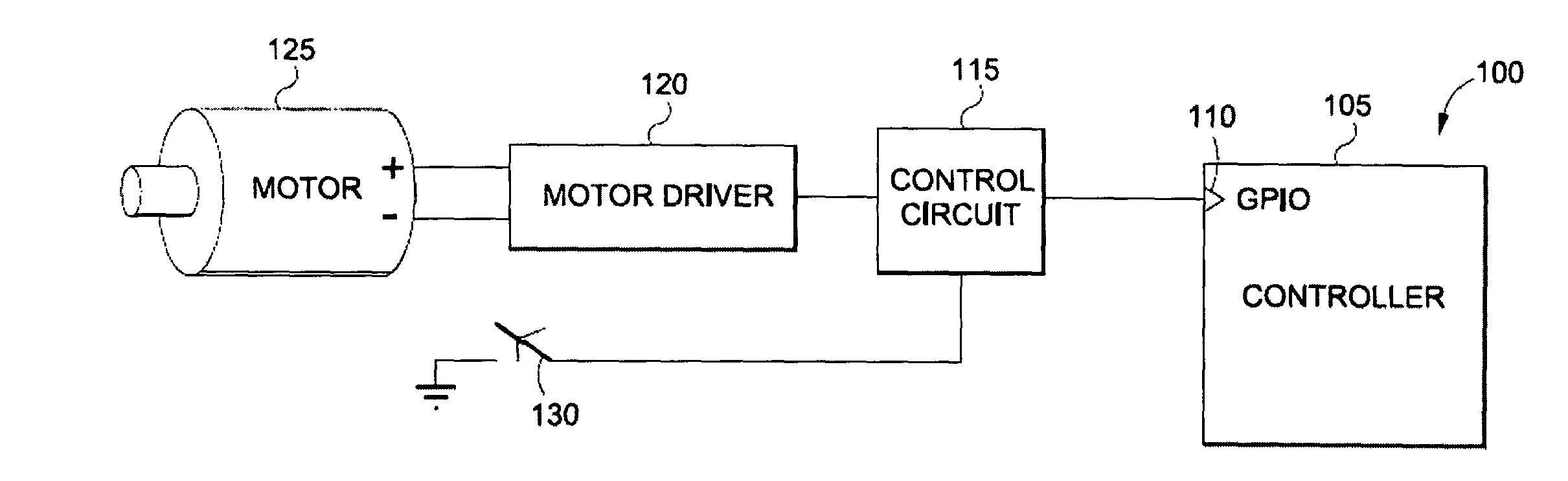
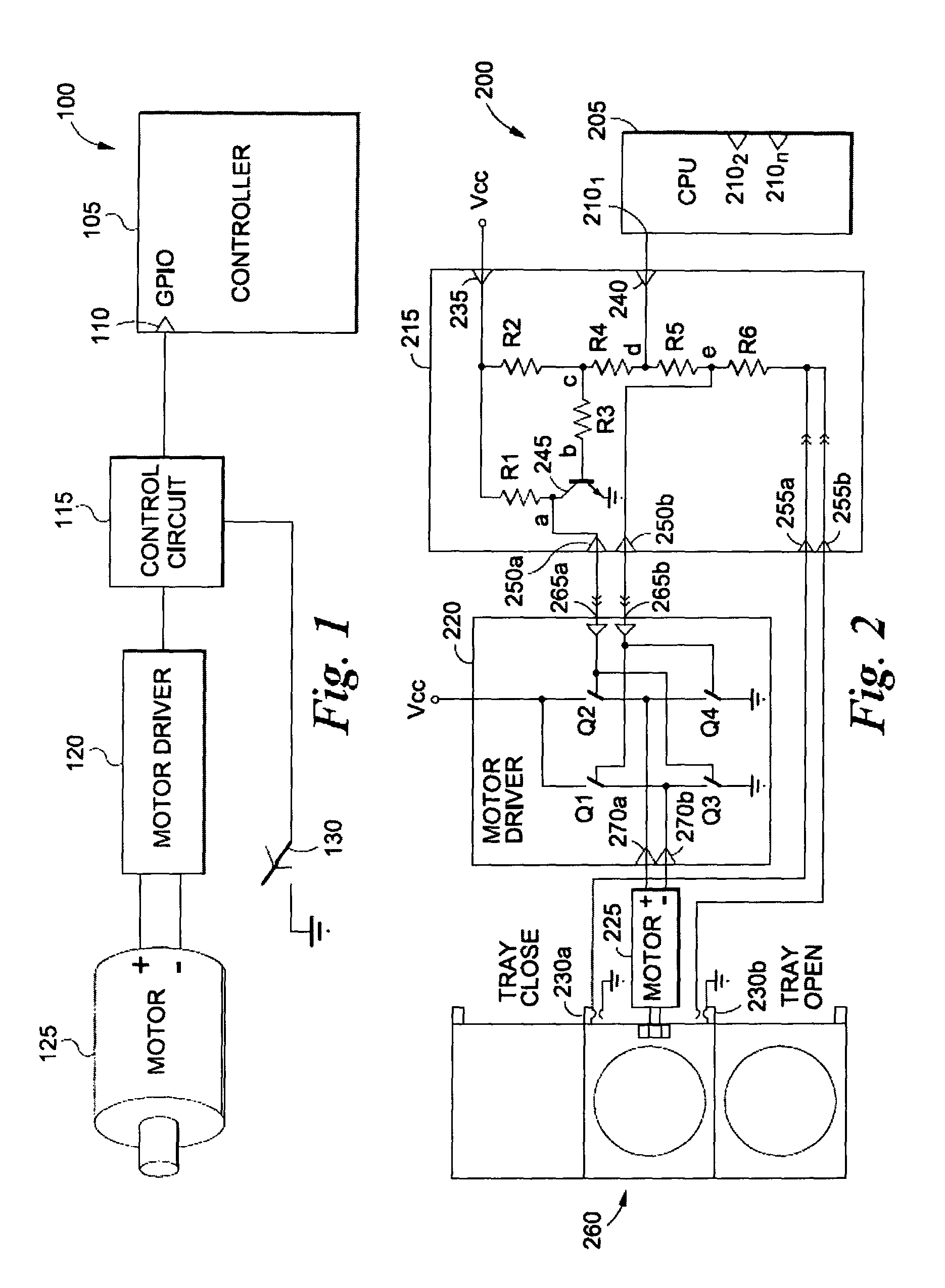
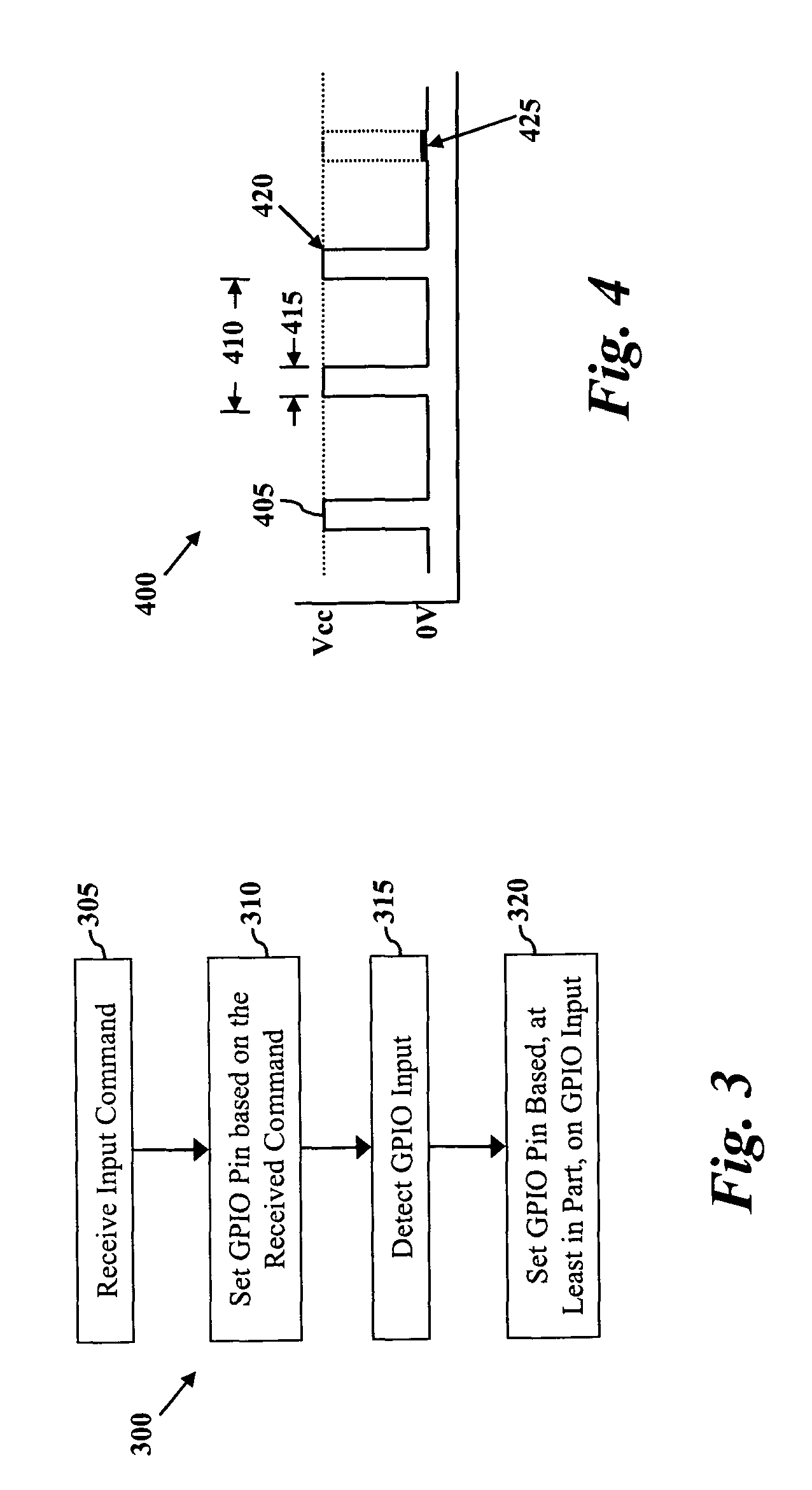
Single general purpose input/output (GPIO) pin motor control circuit
System and method for operating a motor using a single general purpose input / output (GPIO) pin of a controller. In one embodiment, a control circuit may include a first terminal coupled to a GPIO pin of a controller. The first terminal can be configured to receive, and output, at least one or more signals. The control circuit may include a plurality of elements coupled to the first terminal, and motor driver circuit output terminal, such that the control circuit may be configured to output one more control signals to the motor driver circuit output terminal for control the motor driver circuit. Motor driver control signals may be based, at least in part, on one or more signals received from the first terminal.
Owner:CSR TECH INC
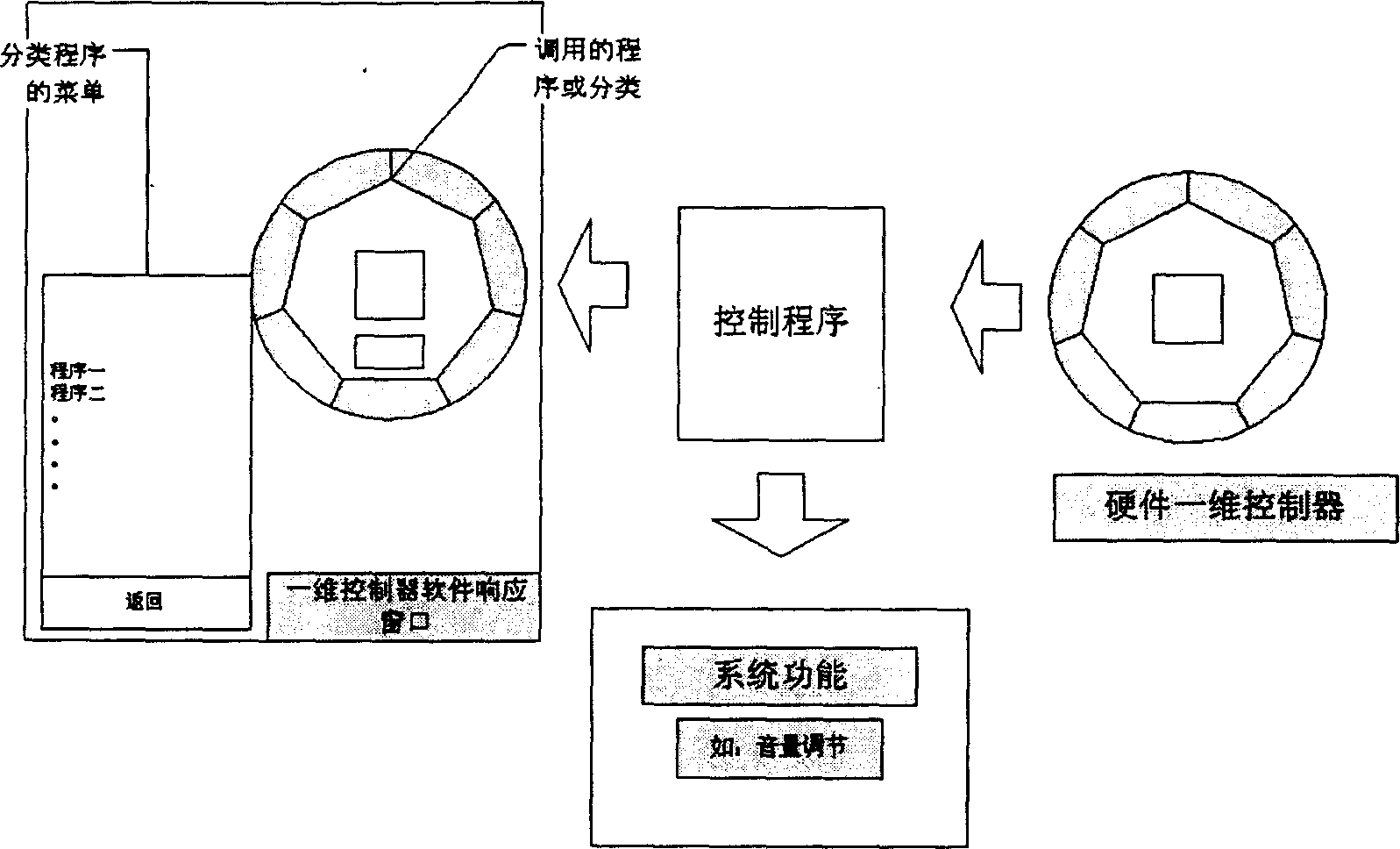
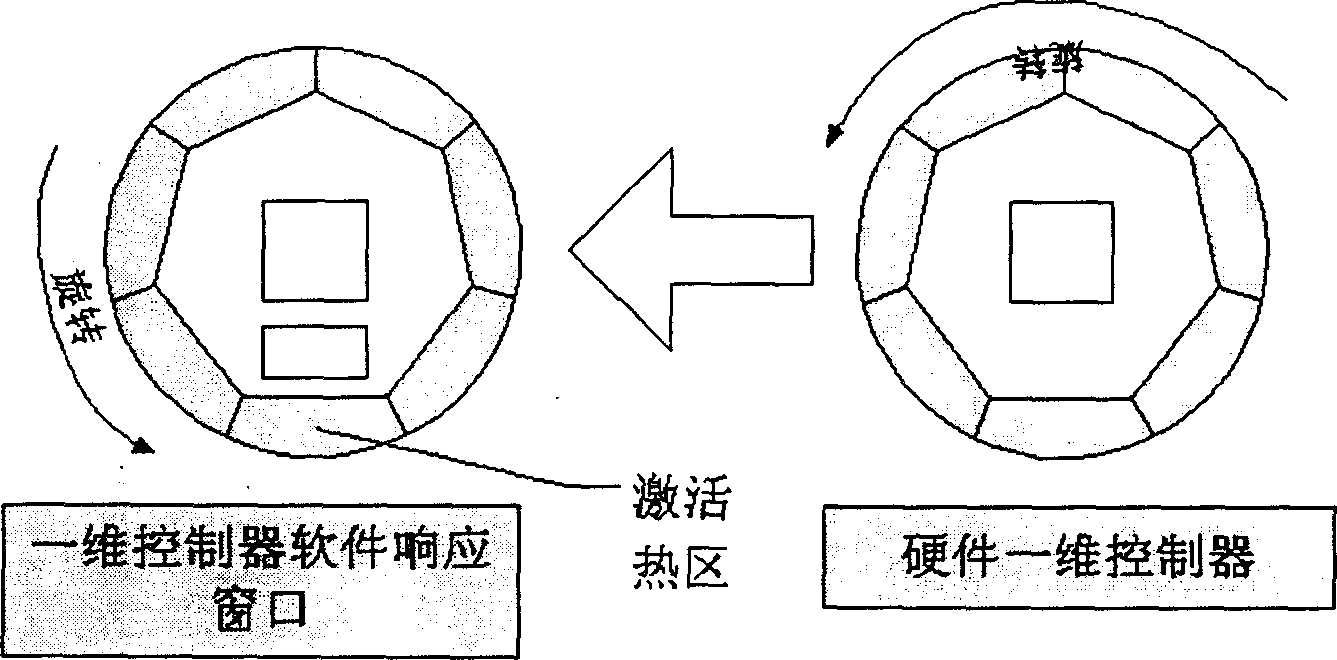
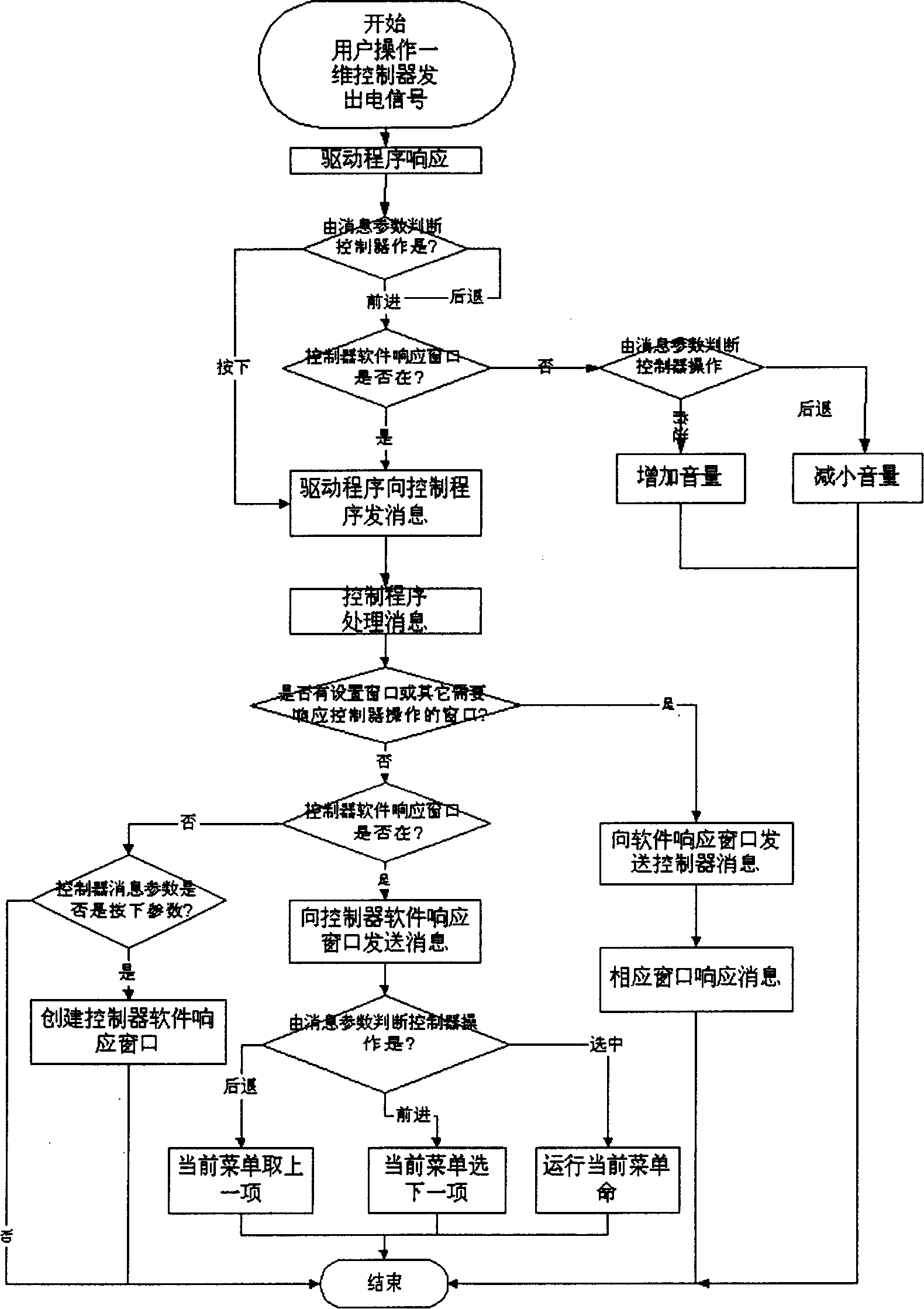
Control system for calling applications by one-dimensional operation and method for realizing same
InactiveCN1508669AOperation will not affectEasy to callProgram control using record carriers with instructionsOperational systemControl system
The invention refers to a method and the system for calling the application procedure through one dimension operation. The system comprises a hardware one dimension controller one keyboard and the circuit for connecting the controller and the keyboard, the action signal of the controller is transmitted to keyboard driving procedure through I / O circuit. The driving procedure converts the received signal into correspondent window procedure, the keyboard driving procedure judges if the response window of the controller software has message type, when it exists, all the messages are sent to the control procedure which can identify the message and transmit then them to the window procedure, when it doesn't exist, the selected message is sent to the control procedure, the control procedure starts the software response window, the forwards and backwards message are transmitted to the operation system function, the function changes the system state.
Owner:LENOVO (BEIJING) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com