Data sharing and opening method and system for preventing sensitive information from being leaked
A sensitive information and data sharing technology, applied in digital data protection, electronic digital data processing, instruments, etc., can solve the problems of sensitive data leakage, lax audit, low labor efficiency, etc. The effect of leaked, efficient automation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] Embodiments of the present invention will be described below with reference to the accompanying drawings.
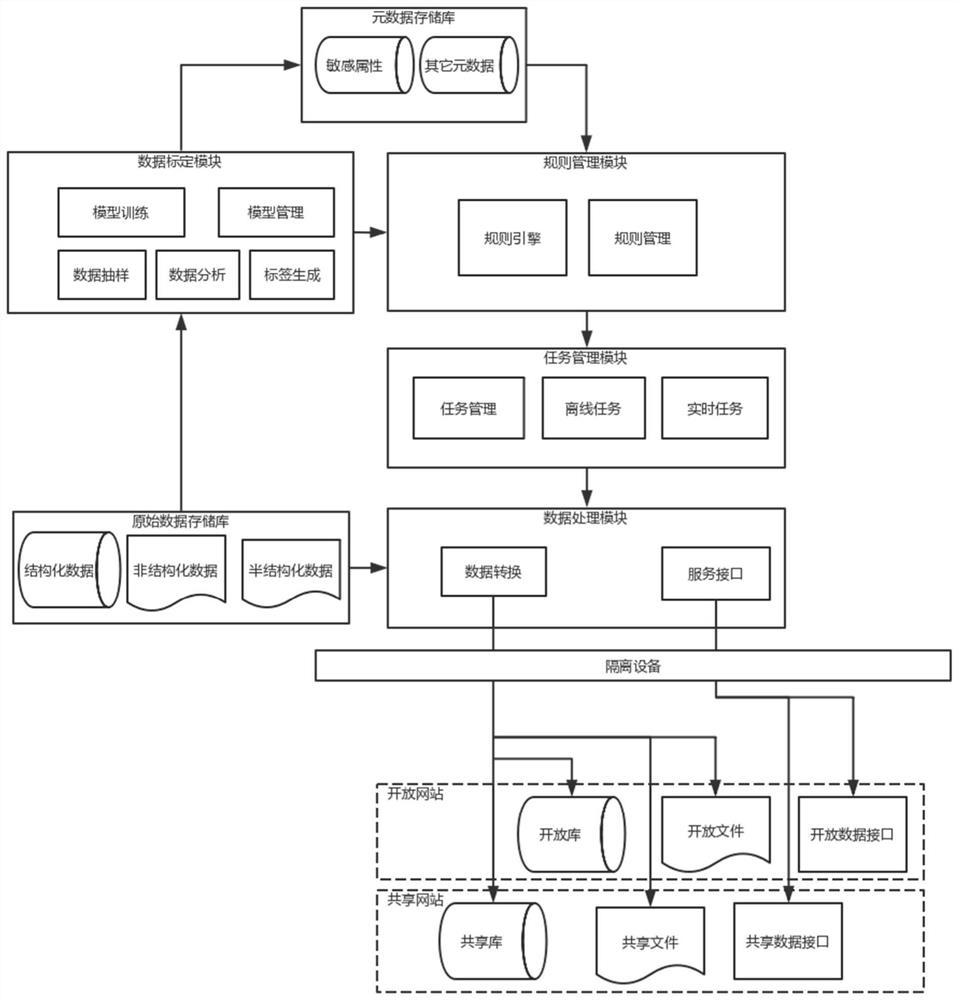
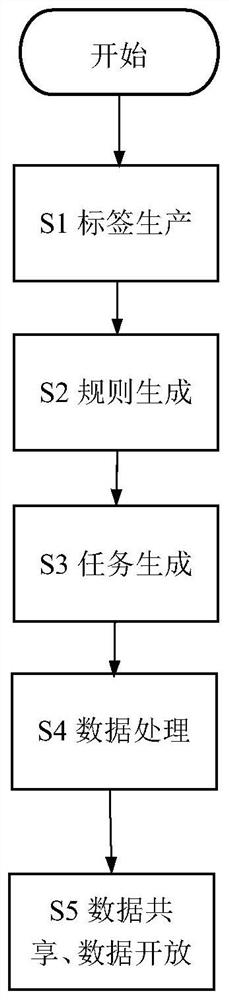
[0045] The first embodiment of the present invention discloses an open data sharing method that prevents leakage of sensitive information, such as figure 2 shown, including:
[0046] S1. Identify and calibrate the sensitive information contained in the original data;
[0047]S2. Generate a data processing rule base according to the calibration result;
[0048] S3. Generate data processing procedures and tasks according to the data processing rule base;
[0049] S4. Execute data processing tasks and process sensitive information contained in the original data;
[0050] S5. Provide data sharing and opening services based on the processed data and the data sharing and opening rules. The data sharing and opening rules are set according to business needs, including unconditional sharing and opening, only some fields can be shared and opened, and fields need to be d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com