Encrypting method base on biology characteristic information
A biometric information and encryption method technology, applied in the field of biometric information-based encryption and single-factor encryption based on biometric information, can solve the problem of improving the system error acceptance rate, failing to provide a strong enough data integrity verification function, and the system Security impact and other issues, to achieve the effect of reducing the system error acceptance rate, realizing high-strength integrity verification, and improving system security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0063] The specific implementation of the two-factor encryption and decryption based on biometric information and key provided by the present invention is as follows:
[0064] 1) Encryption process
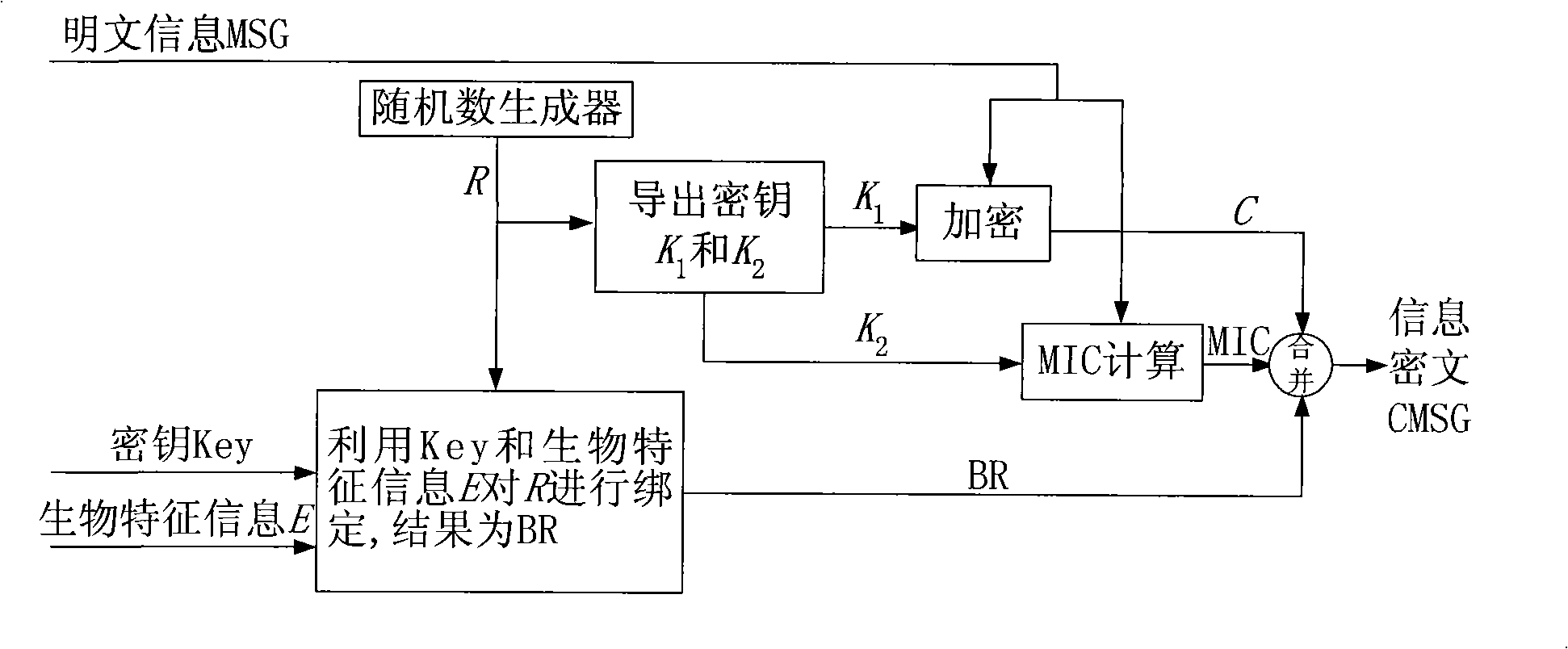
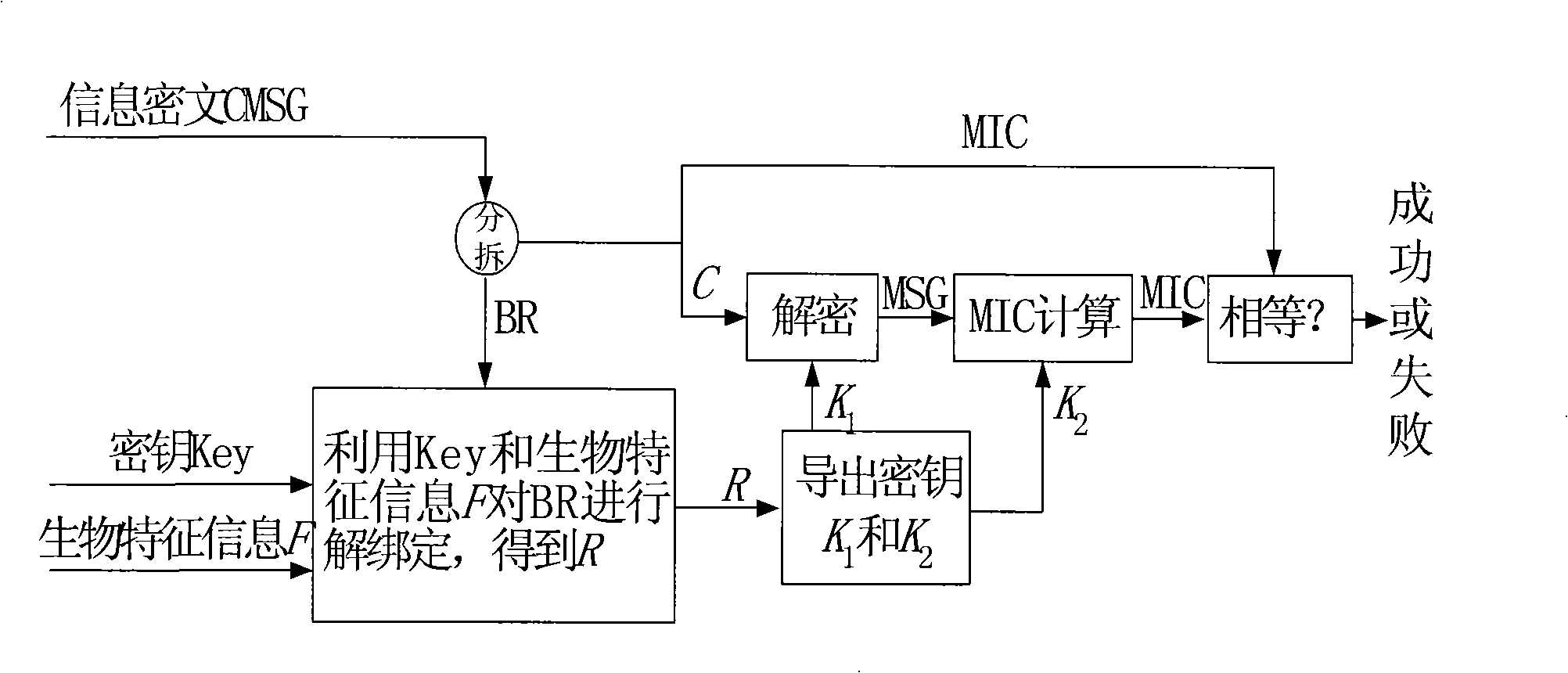
[0065] Such as figure 1 As shown, use the key selected by the user and the user's biometric information E to bind a random number R randomly generated by the system to encrypt the plaintext information MSG to obtain the ciphertext information CMSG, which specifically includes the following implementation steps:
[0066] 1.1) The user randomly selects a key Key and provides the user's biometric information E;
[0067] 1.2) Use a random number generator to generate a random number R, and derive an encryption key K from the random number R 1 and an integrity check key K 2 ;
[0068] 1.3) Using encryption key K 1 Encrypt MSG to obtain information C, and use integrity verification key K 2 Calculate the integrity check code MIC for MSG, that is, perform MIC calculation;
[0069] ...
Embodiment 2
[0081] The specific implementation of the single-factor encryption and decryption based on biometric information provided by the present invention is as follows:
[0082] 1) Encryption process
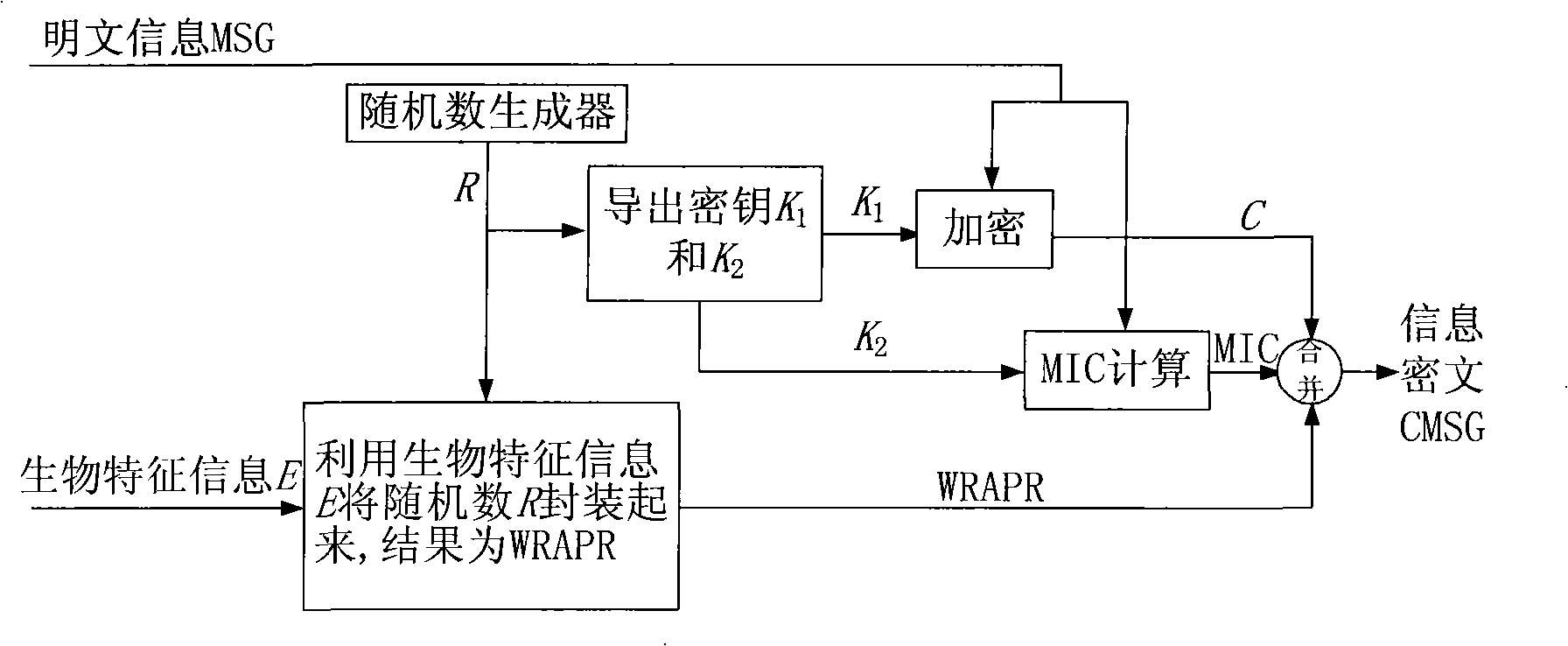
[0083] Such as image 3 As shown, the user encapsulates a random number R randomly generated by the system through the biometric information E to encrypt the plaintext information MSG to obtain the information ciphertext CMSG, which specifically includes the following implementation steps:
[0084] 1.1) The user provides his own biological characteristic information E;
[0085] 1.2) Use a random number generator to generate a random number R, and derive an encryption key K from the random number R 1 and an integrity check key K 2 ;
[0086] 1.3) Using encryption key K 1 Encrypt MSG to obtain information C, and use integrity verification key K 2 Calculate the integrity check code MIC for MSG, that is, perform MIC calculation;
[0087] 1.4) Use the biometric information E to encap...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com