Safe online fingerprint matching method
A matching method and fingerprint technology, applied in the fields of information security and privacy protection, can solve the problems of high computational complexity, high implementation cost, and few homomorphic encryption algorithms.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0059] This application proposes a new secure privacy protection scheme—Security e-finger scheme, which introduces the idea of LWE problem to protect the privacy of the user's temporary fingerprint feature information. The Security e-finger solution proposed by this application can solve the privacy protection security problem of fingerprint data in the online fingerprint authentication system, and at the same time take into account the system's requirements for efficiency, and provide a new privacy protection technical solution for the biometric authentication system , providing a theoretical basis and technical support for the popularization of the secure fingerprint authentication system.
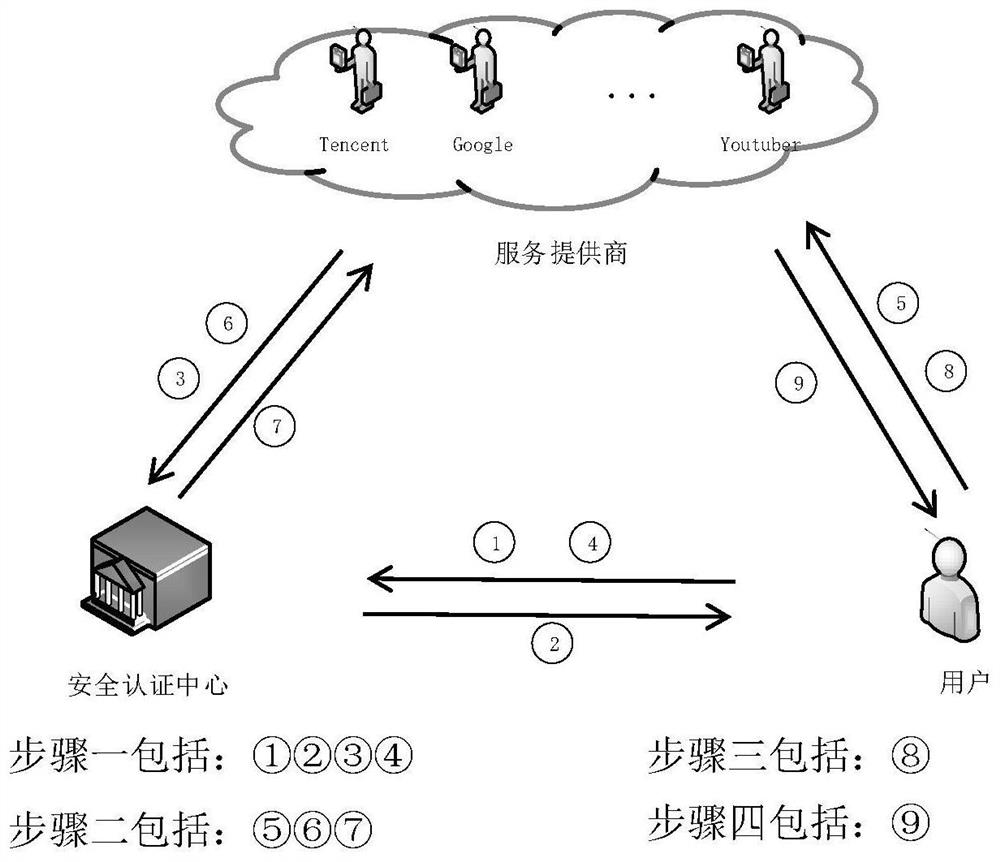
[0060] combine figure 1 Introduce the specific implementation process of this application:
[0061] Security certification center initialization phase
[0062] The specific operation is: the security certification center initializes and selects a security parameter Run the function...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com