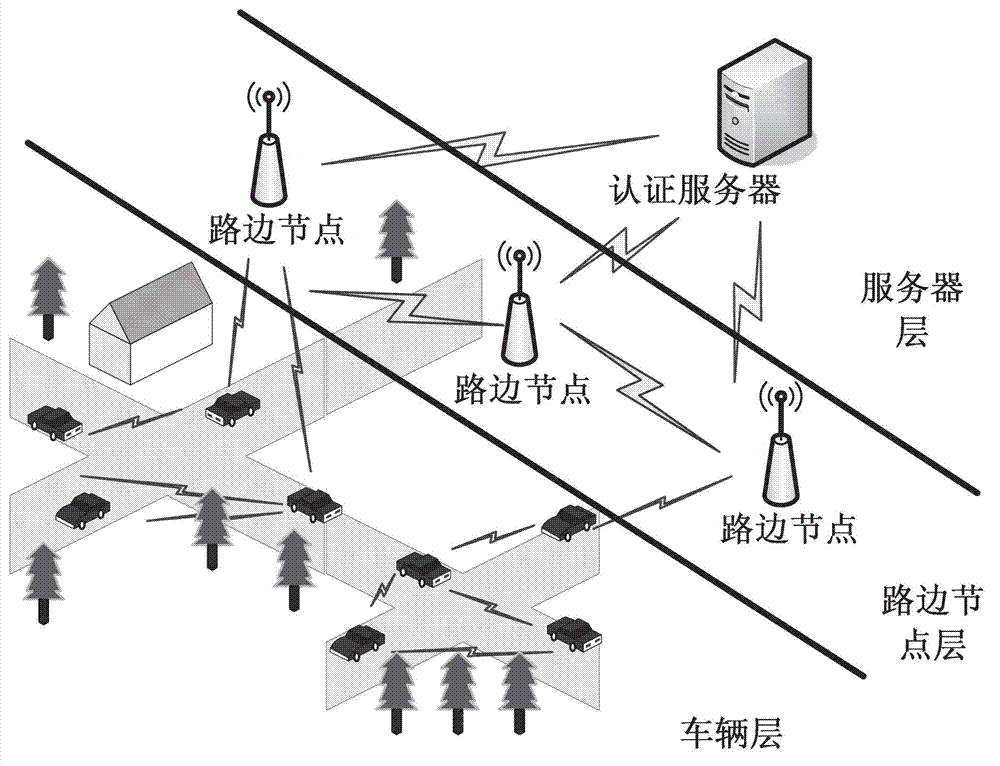
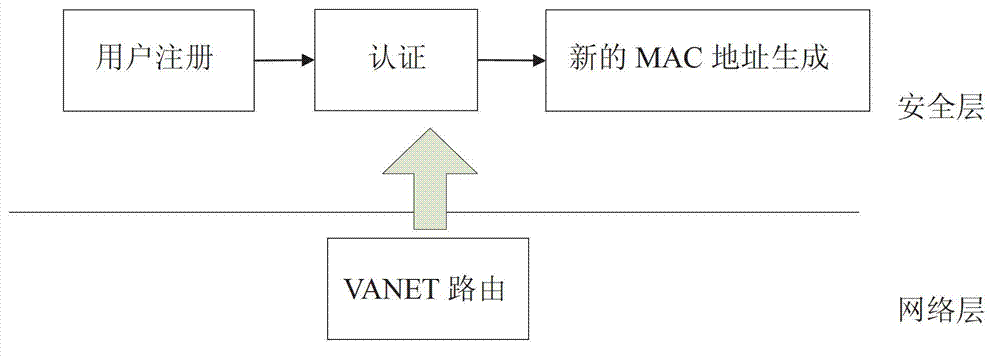
Anonymous authentication scheme under vehicular ad hoc network based on biometric encryption technology
A vehicle-mounted self-organizing and anonymous authentication technology, applied in the field of information security, can solve the problem of difficult to find a balance between information exchange and privacy protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0069] Example 1: Research on the Average Anonymity of Users
[0070] The purpose of the experiment: To study the average number of anonymous users in the system. The larger the average number of anonymous users, the stronger the system's anonymous security protection for users.
[0071] Experiment introduction: In this experiment, the average number of anonymous users refers to how many other users can be found by any user in the network as their own anonymous users at a certain point in time. That is, from the attacker's point of view, if two users negotiate the MAC address with the server at the same time when the distance is relatively close, then after the negotiation, since both of them have changed the MAC address, the attacker cannot obtain the MAC address from the data frame. The MAC address infers which user the current data packet is sent to.
[0072] The calculation method of the average anonymous number of users is as follows: the inventor assumes that the set of...
example 2
[0075] Example 2: Research on the probability of users being attacked
[0076] Purpose of the experiment: Although the method of hiding the MAC address can ensure that the attacker cannot infer the identity of the user from the content of the data packet. But the attacker can still analyze the source of the data packets based on the location of the user, and then deduce the real identity of the user. Therefore, the inventor studies the probability of success of an assailant performing a correlation attack in the system.
[0077] Experiment introduction: This experiment focuses on studying the attacker's attack success rate. In the previous analysis, the inventor learned that using the method of MAC hiding can make it impossible for an external attacker to correlate the user's MAC address before and after, thereby protecting the user's real identity. In this experiment, the inventor focuses on studying the situation that the attacker simply correlates the user identity from t...
example 3
[0080] Example 3: Research on the entropy of the system
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com