Key generation device, key utilization device, and key generation method
A key generation device and key technology, applied to key distribution, can solve problems such as inapplicable methods, and achieve the effect of high-precision authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
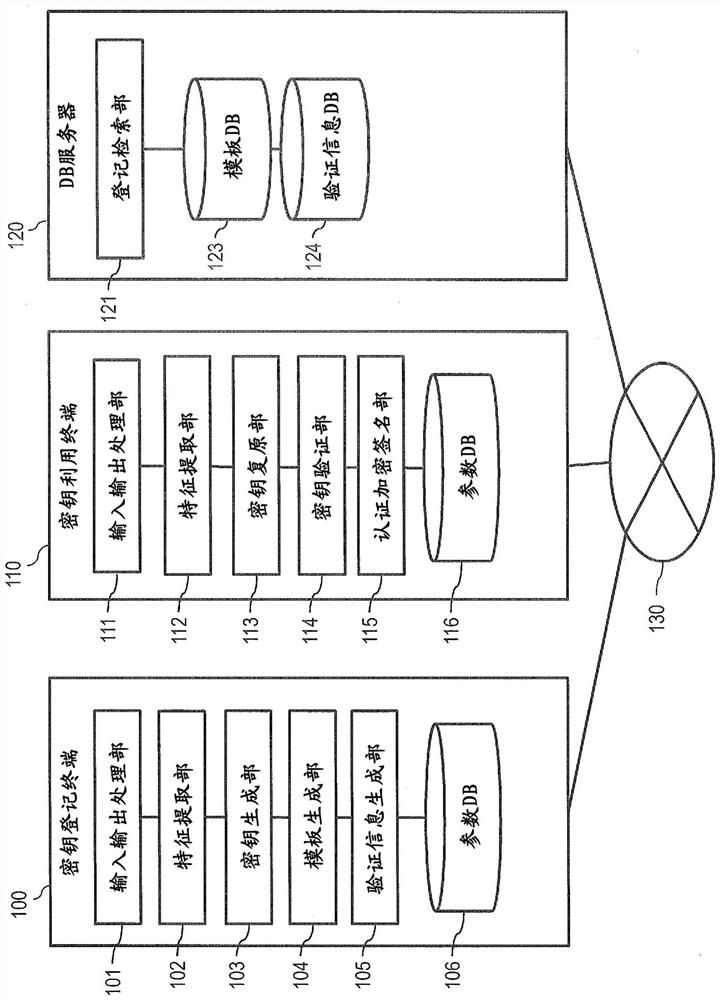
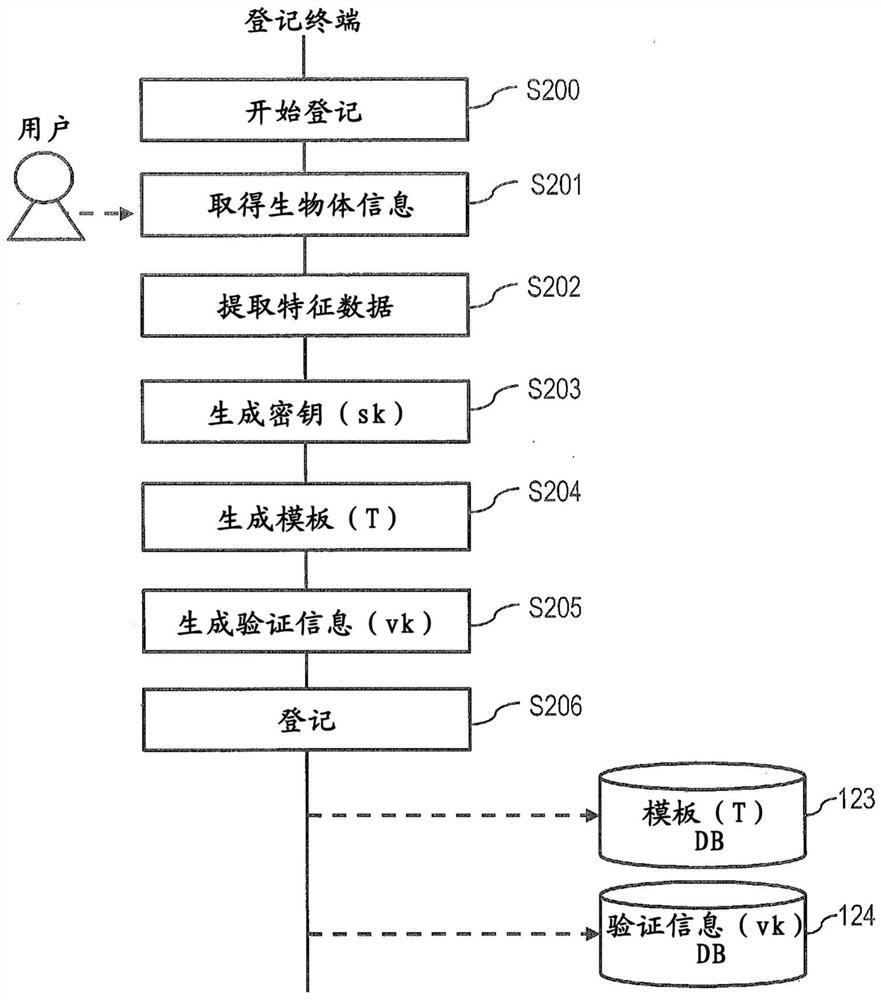
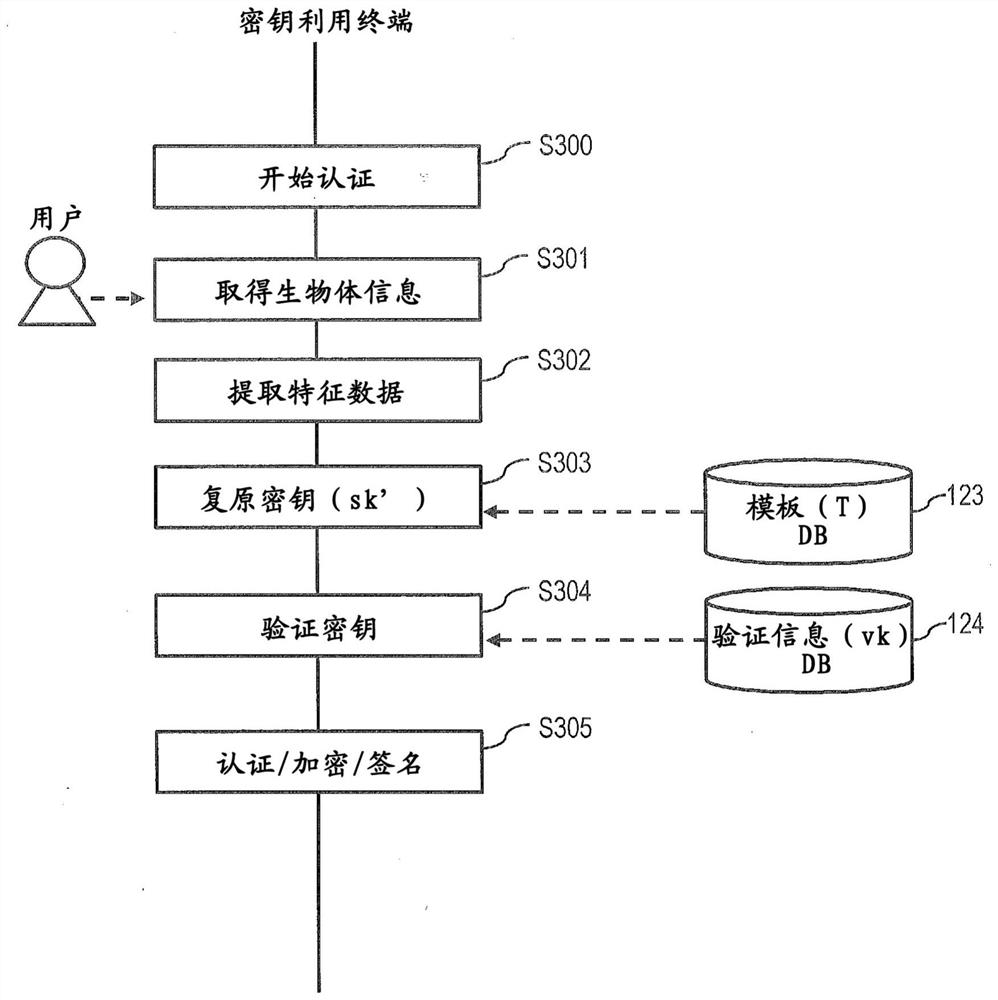
[0030] The biometric authentication system of this embodiment creates and registers a template and verification information for a verification key based on the biometric information of the user, restores the key using the template and the biometric information of the user newly acquired, and uses the key User authentication, data encryption and decryption, and electronic signature creation are performed.
[0031] figure 1 It is a block diagram showing a configuration example of a biometric authentication system. The biometric authentication system includes, for example, one or more key registration terminals 100 , one or more key use terminals 110 , and a DB (Data Base) server 120 connected to each other via a network 130 such as the Internet.
[0032] In addition, any two or three of the key registration terminal 100 , the key use terminal 110 , and the DB server 120 may all be installed in the same apparatus. In addition, in the case where all these three are installed in ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com