Identity authentication method based on biological feature encryption and homomorphic algorithm
A biometric and identity authentication technology, applied in user identity/authority verification, electrical components, transmission systems, etc., can solve the problems of different users and illegal access to system resources by legitimate users, so as to facilitate login and prevent illegal use of resources , the effect of high security strength
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
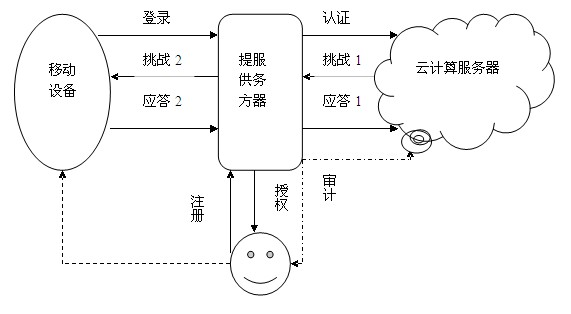
[0037] The use process of the identity authentication scheme based on biometric encryption and homomorphic algorithm designed by the present invention includes the following five stages:
[0038] (1) Registration stage. The user first logs in to the registration page of the provider server of the cloud computing environment, applies for registration of an account, enters some necessary personal information PI, signs it with its own private key Pr and sends it to the provider server. The provider server uses the user’s public key Pu Verify the sent signature. If it is determined that the information sent by the user is true and valid, then feedback to the user for biometric (voice or fingerprint, etc.) collection I. After collecting the user’s biometric BC, extract a secret from the user’s registration information Key, after the result of the exclusive OR between the encryption key of the provider server and the biological feature, it is stored in the cloud computing server as an ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com