Patents
Literature
50results about How to "Solve the theft" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
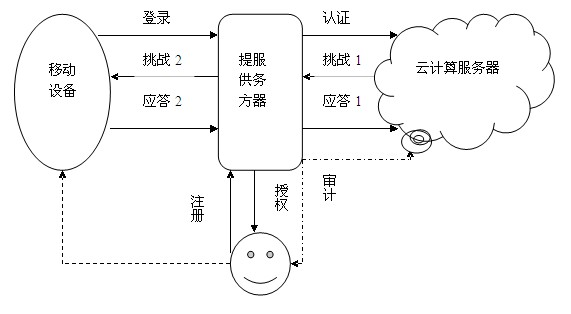
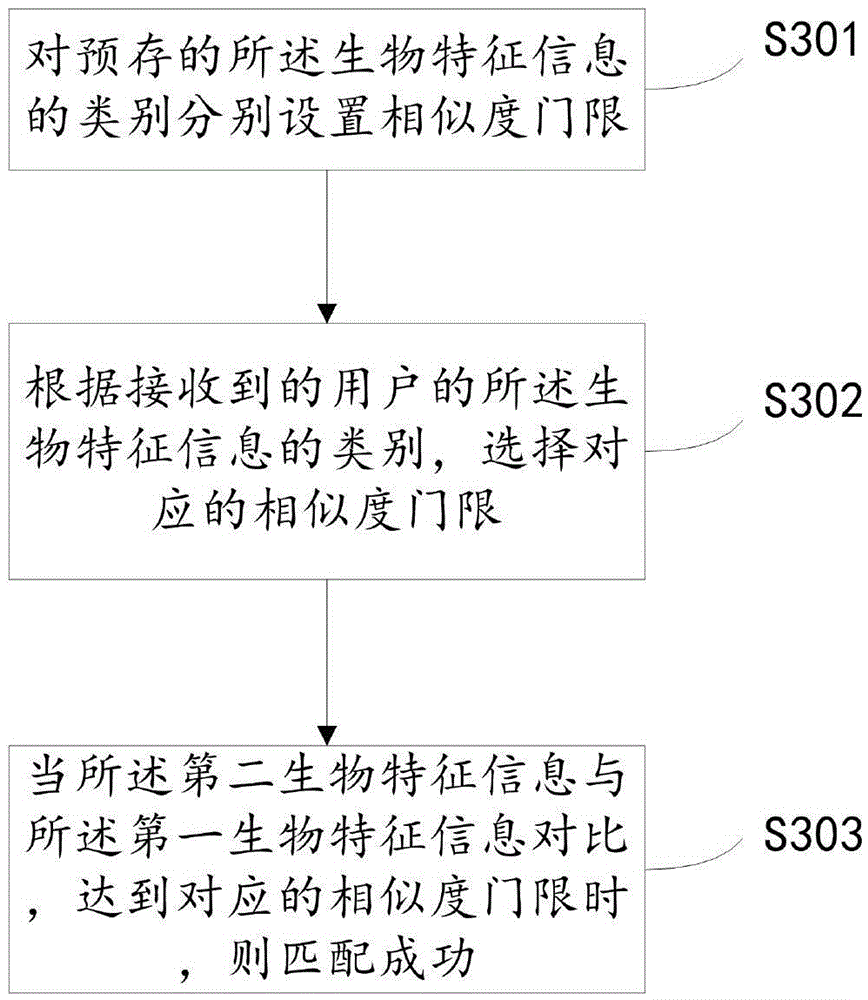
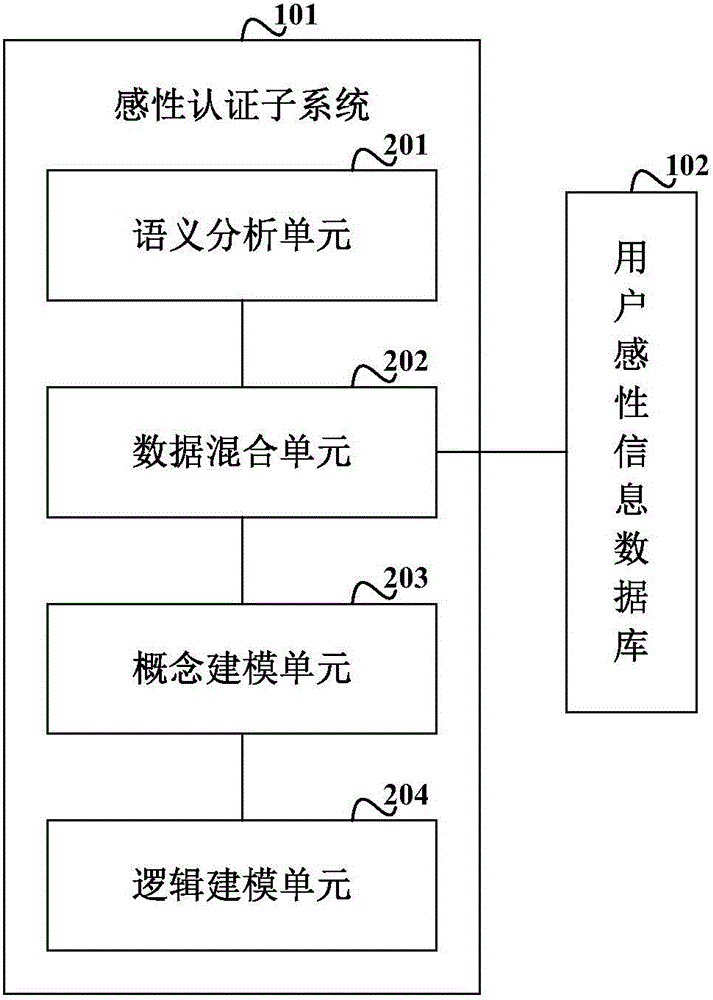
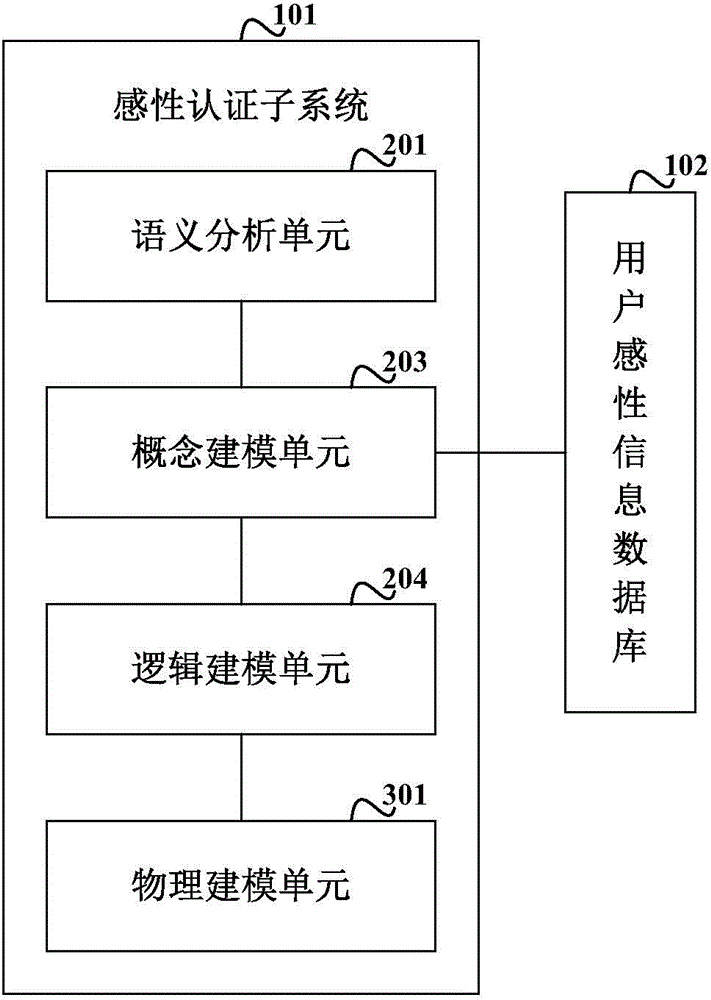
Identity authentication method based on biological feature encryption and homomorphic algorithm
InactiveCN102664885AImprove privacyAvoid crackingUser identity/authority verificationTimestampAlgorithm
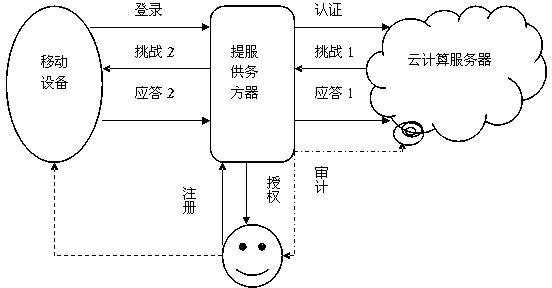
The invention discloses an identity authentication method based on biological feature encryption and a homomorphic algorithm. The method is quicker than a normal password method by using biological features of users as passwords to log in a system through a mobile device, using an encrypted biological template is safer, and privacy of the users can be guaranteed as information is transmitted in a ciphertext form. By adding factors such as timestamps, tri-party authentication among the users, a provider server and a cloud computing server is realized, and reliability among the three parties is enhanced. Legal users can be prevented from using resources in the cloud computing environment illegally to better manage the resources by means of user authentication operation according to attribution predicate encryption and real-time updating of permission information. Operation without encryption can be realized by the aid of the homomorphic algorithm, same effects as decrypting before operation can be achieved, time and space expenses can be saved, system efficiency is greatly improved, and the identity authentication method has high safety and efficiency.
Owner:南京邦普信息科技有限公司
Oil-water separator
ActiveCN103663851ASolve environmental problemsReduce processing linksFatty/oily/floating substances removal devicesMultistage water/sewage treatmentSlagSludge
The invention discloses an oil-water separator comprising a water inlet, a water outlet, a container, a movable filter residue bucket, a fixed filter net, an oil storage area, a vortex shallow filter, a sludge bucket, an electronic integration controller, an oil suction port, a slag suction port and a biological filter disc, wherein the fixed filter net finely filters the wastewater; an oil drop of which the diameter is 10-100 microns is separated and ascended to the oil storage area in the vortex shallow filter; the sludge bucket concentrates the waste residue; the waste residue descends to the bottom of the sludge bucket to be gathered under the effect of gravity after participating on the sludge bucket; the oil suction port is used for absorbing oil; the slag suction port is used for absorbing the slag; the biological filter disc is used for discharging the residual sewage. By adopting the oil-water separator, the environment-friendly problem of emission of restaurant waste water is solved, so that the discharged water achieves the corresponding national emission standards, the congestion problems of drainage pipelines caused by waste oil wall built-up are solved, separated excessive oil impurities are solved, and the processing link of restaurant waste oil in specified use is reduced.
Owner:CLEAR SUZHOU ENVIRONMENTAL TECH CO LTD
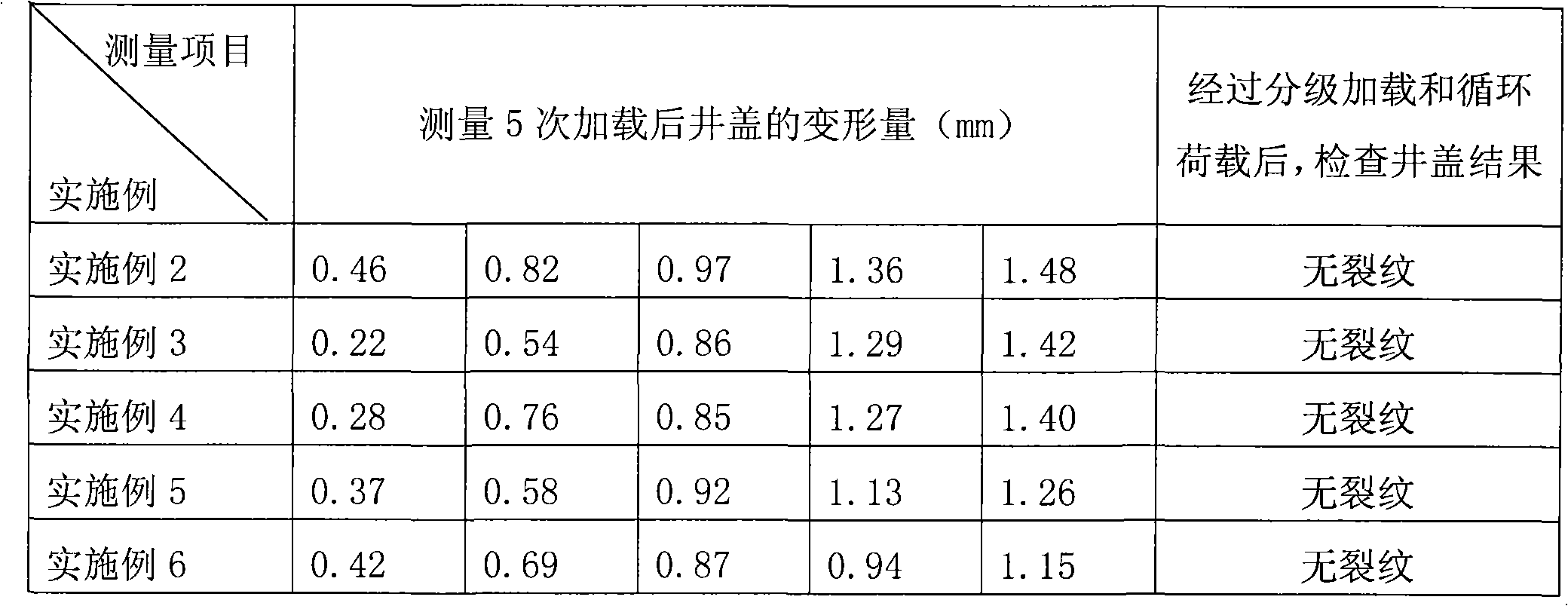
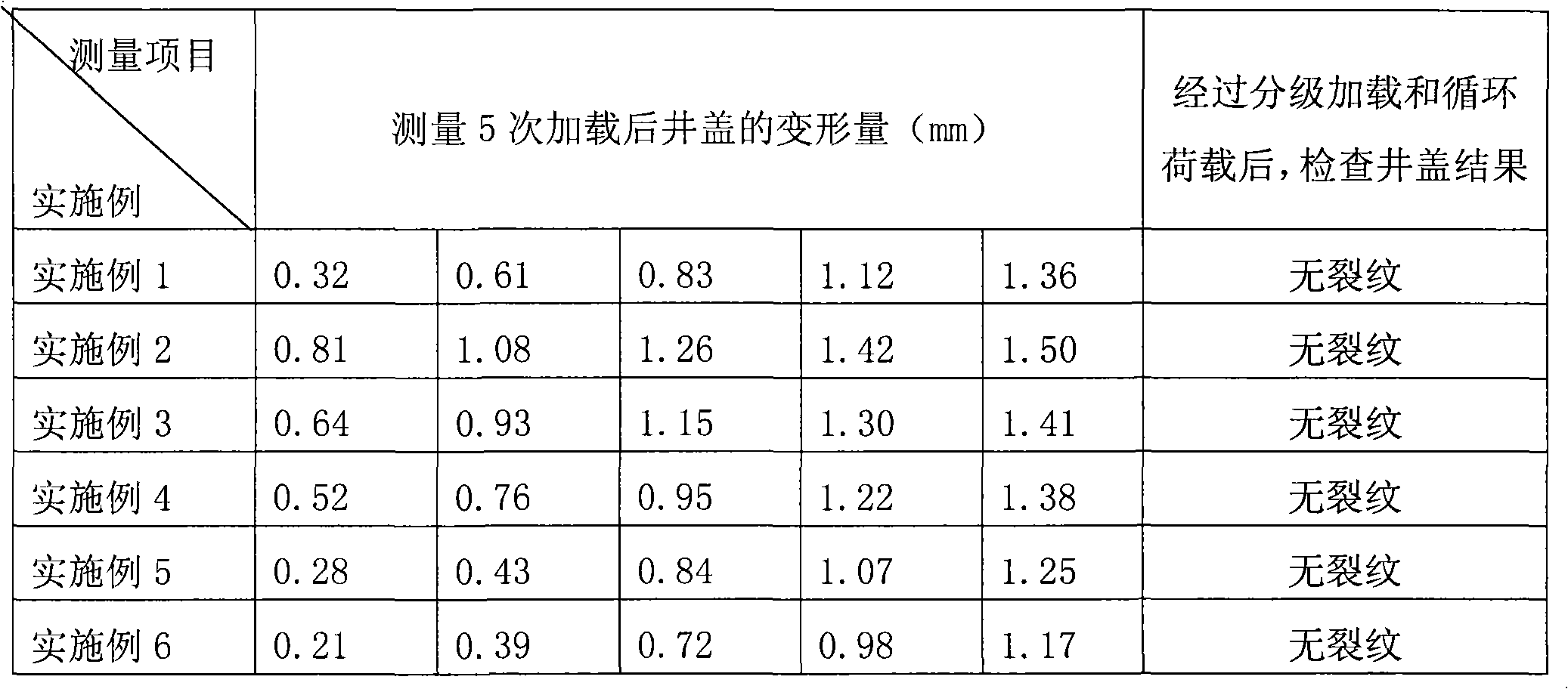
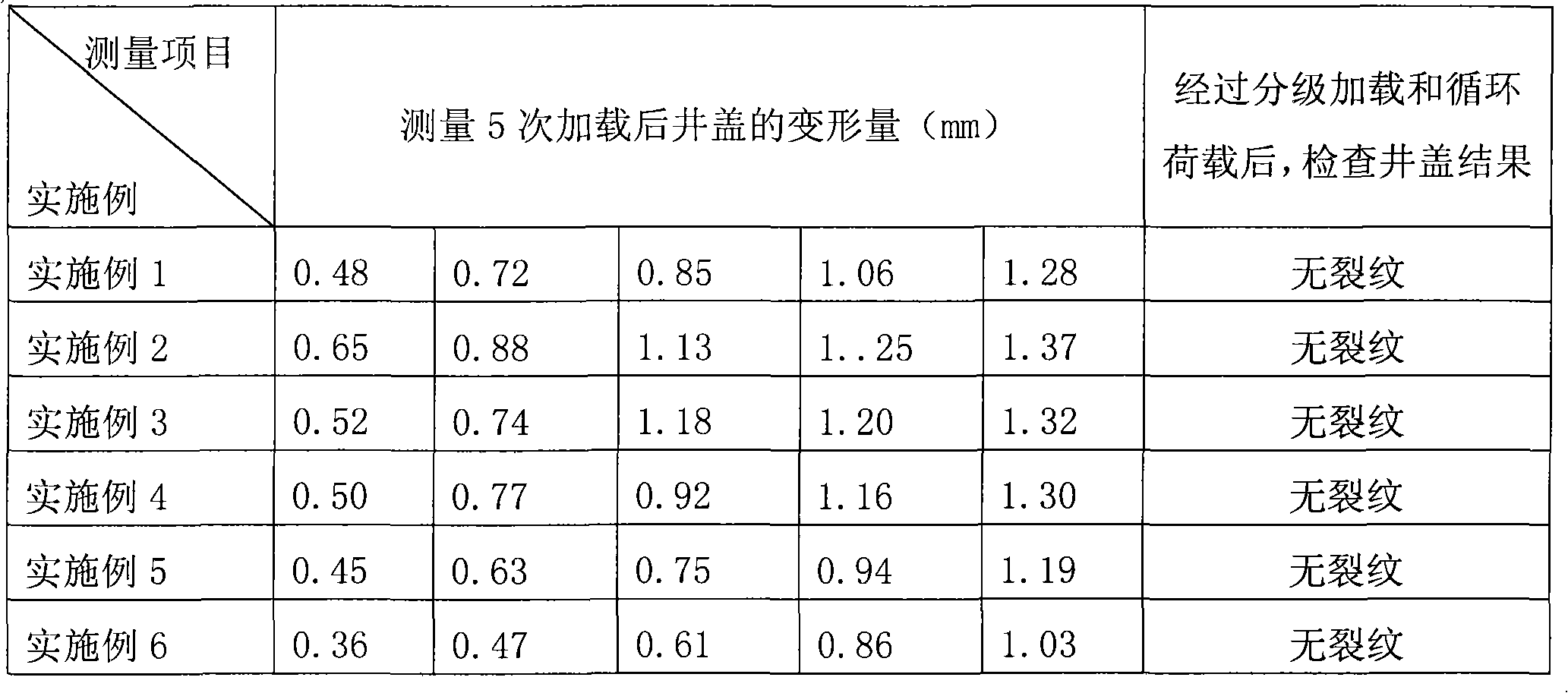
High-strength polyester composite well cover as well as formula and preparation method thereof
InactiveCN101871219AImprove carrying capacityImpact resistantArtificial islandsUnderwater structuresEnvironmental resistanceAlkali free
The invention discloses a formula of a high-strength polyester composite well cover, which comprises the following raw materials in parts by weight: 21-22 parts of unsaturated polyester resin, 8-9 parts of low shrink additive, 40-50 parts of heavy calcium carbonate, 1-1.5 parts of zinc stearate, 0.2-0.8 part of active magnesia, 0.12-0.28 part of curing agent, 0.2-0.8 part of carbon black, 10-20 parts of alkali-free glass fiber roving and 10-20 parts of glass fiber woven roving. A production method of the well cover of the invention comprises the following steps of: firstly preparing resin paste, preparing sheets by utilizing the resin paste, and then, forming the sheets by die pressing. The well cover of the invention has the characteristics of strong carrying capacity, shock resistance, ageing resistance, wear resistance, corrosion resistance, novel and attractive appearance, simple structure, environmental protection and the like, and basically solves the problem of well cover pilfering.
Owner:北京泛亚电通工贸有限责任公司
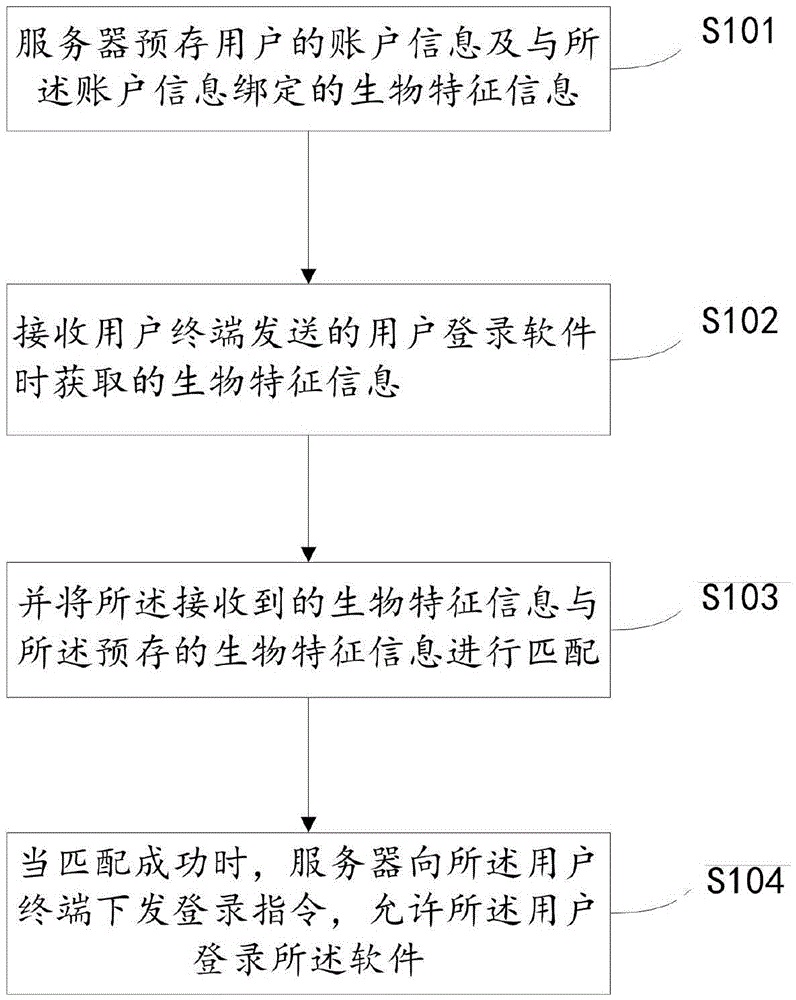
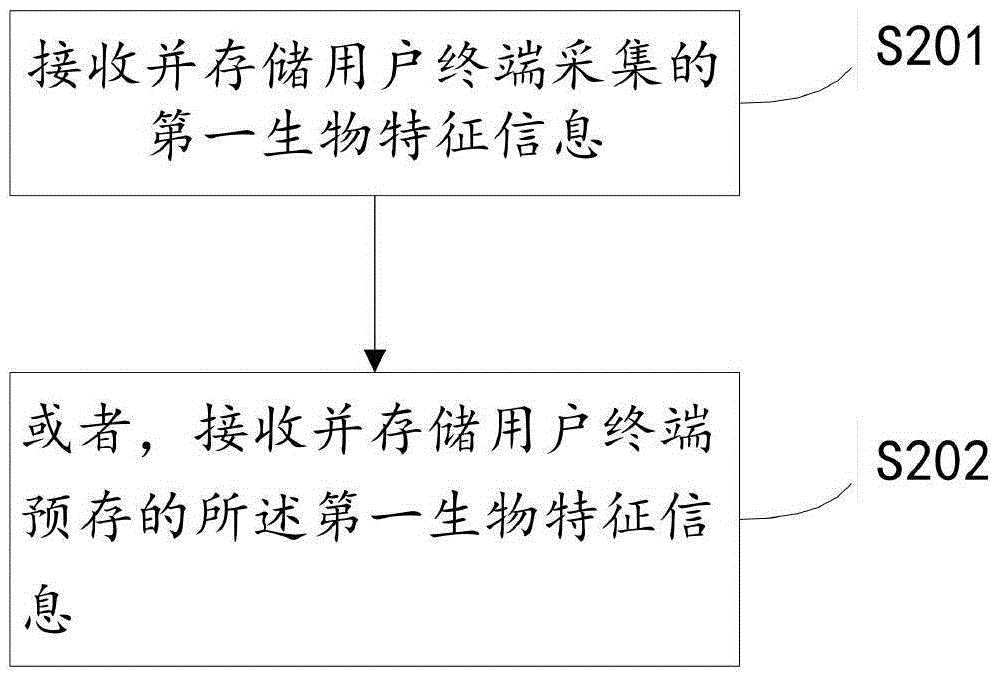
Software login method, terminal, server and system based biological characteristics
InactiveCN105530267ASolve the theftImprove protectionDigital data authenticationTransmissionPasswordPrivacy protection
The invention provides a software login method based on biological characteristics. The software login method comprises the steps that: a server pre-stores account information and biological characteristic information bound to the account information of a user; biological characteristic information which is obtained when the user logs in software and sent by a user terminal is received; the received biological characteristic information is matched with the prestored biological characteristic information; and the server issues a login command to the user terminal when the matching is successful, and the user is allowed to log in the software. That is, the biological characteristic identification is added into software unlocking, the password theft accident is solved, the software is personalized, and other people can do nothing with the password unless the personal biological characteristics are acquired. Therefore, the safety level is significantly promoted, and the personal privacy protection is more powerful.
Owner:PHICOMM (SHANGHAI) CO LTD
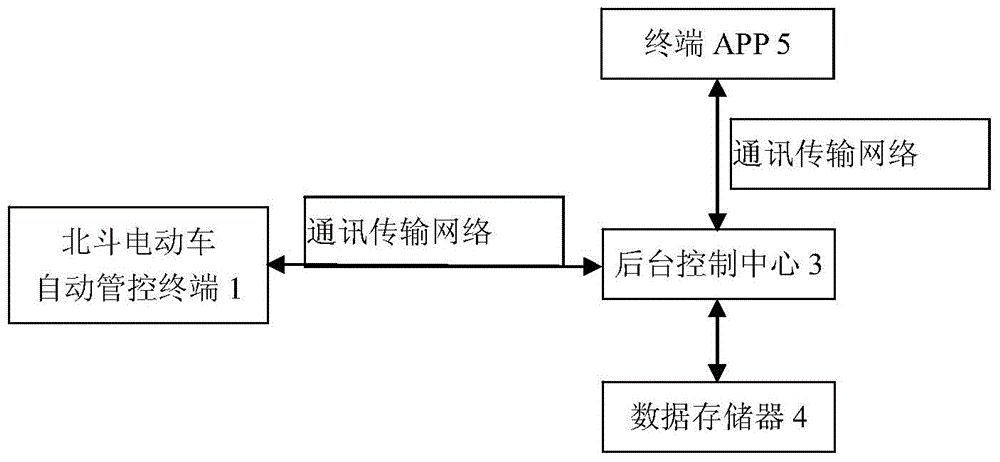
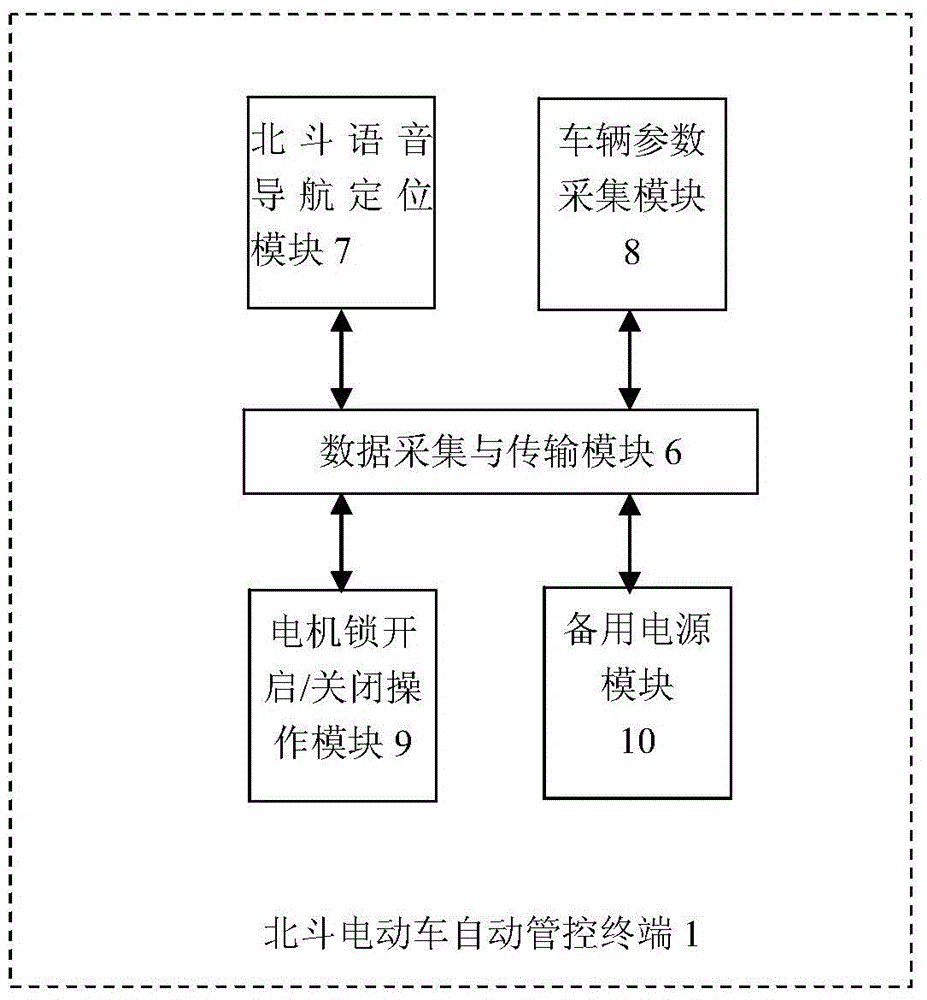
Automatic management and control system of Beidou electric vehicle based on terminal APP
InactiveCN104908881ARealize online monitoringReal-time online monitoringAnti-theft cycle devicesRider propulsionControl systemEngineering
The invention discloses an automatic management and control system of a Beidou electric vehicle based on a terminal APP. The automatic management and control system comprises an automatic management and control terminal of the Beidou electric vehicle, a communication transmission network, a background control center and the terminal APP, wherein the automatic management and control terminal of the Beidou electric vehicle is integrated in the inner part of an electric vehicle controller; the terminal APP is arranged in a mobile equipment terminal such as a cellphone and a PAD; a signal of the electric vehicle is transmitted to the background control center by the automatic management and control terminal of the Beidou electric vehicle through the communication transmission network, and then the signal is transmitted to the terminal APP by the background control center. The terminal APP can transmit an instruction through the background control center, so that daily managements such as navigating and positioning the electric vehicle, managing an electronic anti-theft fence and automatically locking the electric vehicle can be performed; the automatic management and control system of the Beidou electric vehicle based on the terminal APP, which is disclosed by the invention, can allow a vehicle owner to realize the long-distance real-time all-weather full-automatic on-line monitoring of the electric vehicle through the terminal APP.
Owner:QINGDAO ACAD FOR OPTO ELECTRONICS ENG
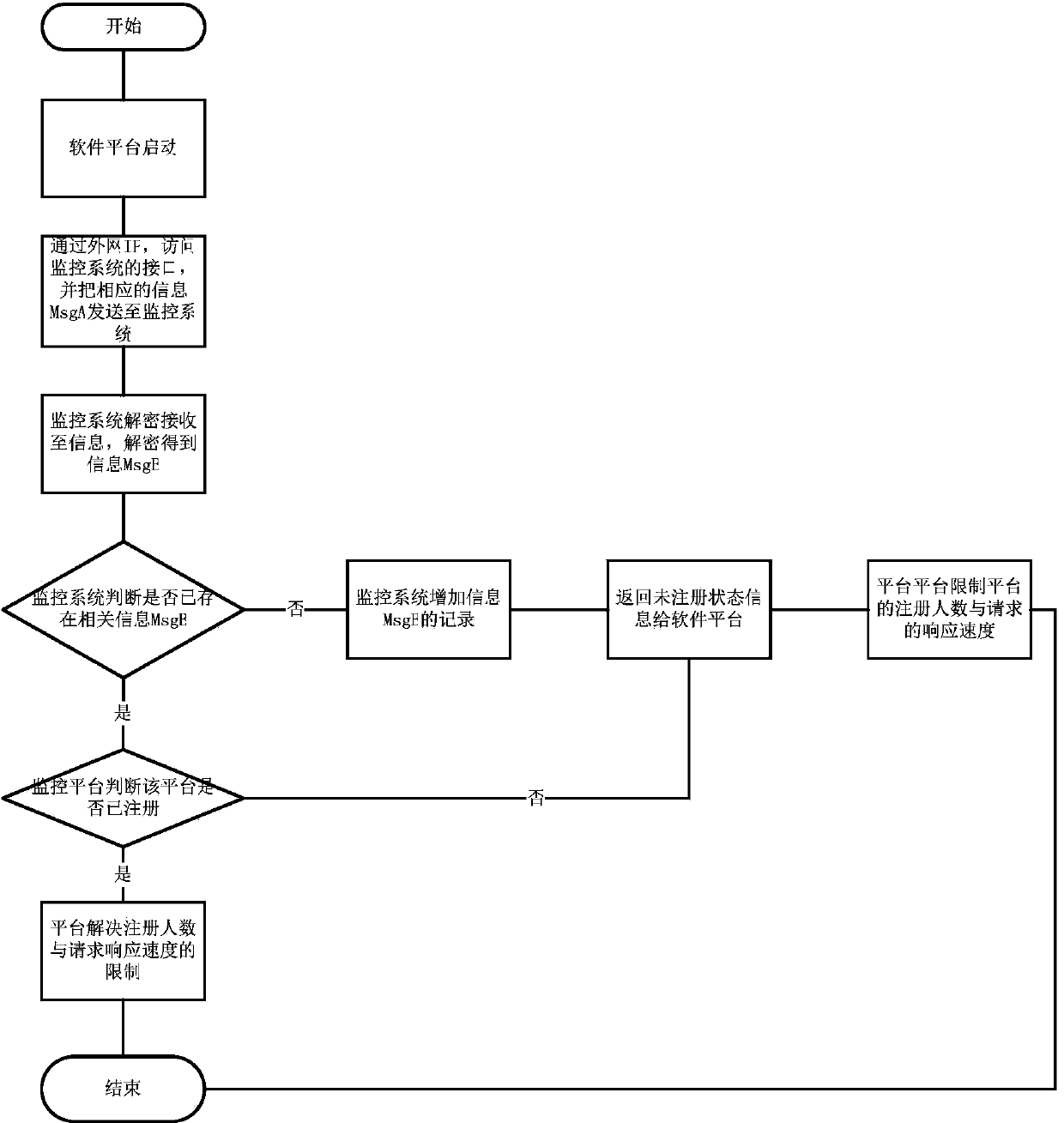
Software authorization control method
ActiveCN103745139ASolve the theftTransmissionProgram/content distribution protectionTimestampSoftware system
The invention relates to the technical field of software development, in particular to a software authorization control method. Operating platforms of other servers are monitored by deploying a monitoring system. When the platforms are firstly started, internal network IP (internet protocol), external network IP and MAC (media access control) addresses of the servers with the platforms are transmitted to a monitoring platform. When the monitoring platform acquires server information of the servers, an authentication code is generated through IP addresses, the external network IP, the MAC addresses and a temporal timestamp and stored in the monitoring system, and the platforms are marked unregistered until the platforms are registered. By the method, registration information is generated according to the internal network IP, the external network IP and the MAC addresses of the servers and the timestamp of the monitoring platform, users can be effectively prevented from obtaining software registration by the aid of fake server information, a software system is prevented from being embezzled, and the method can be used for software authorization control.
Owner:G CLOUD TECH
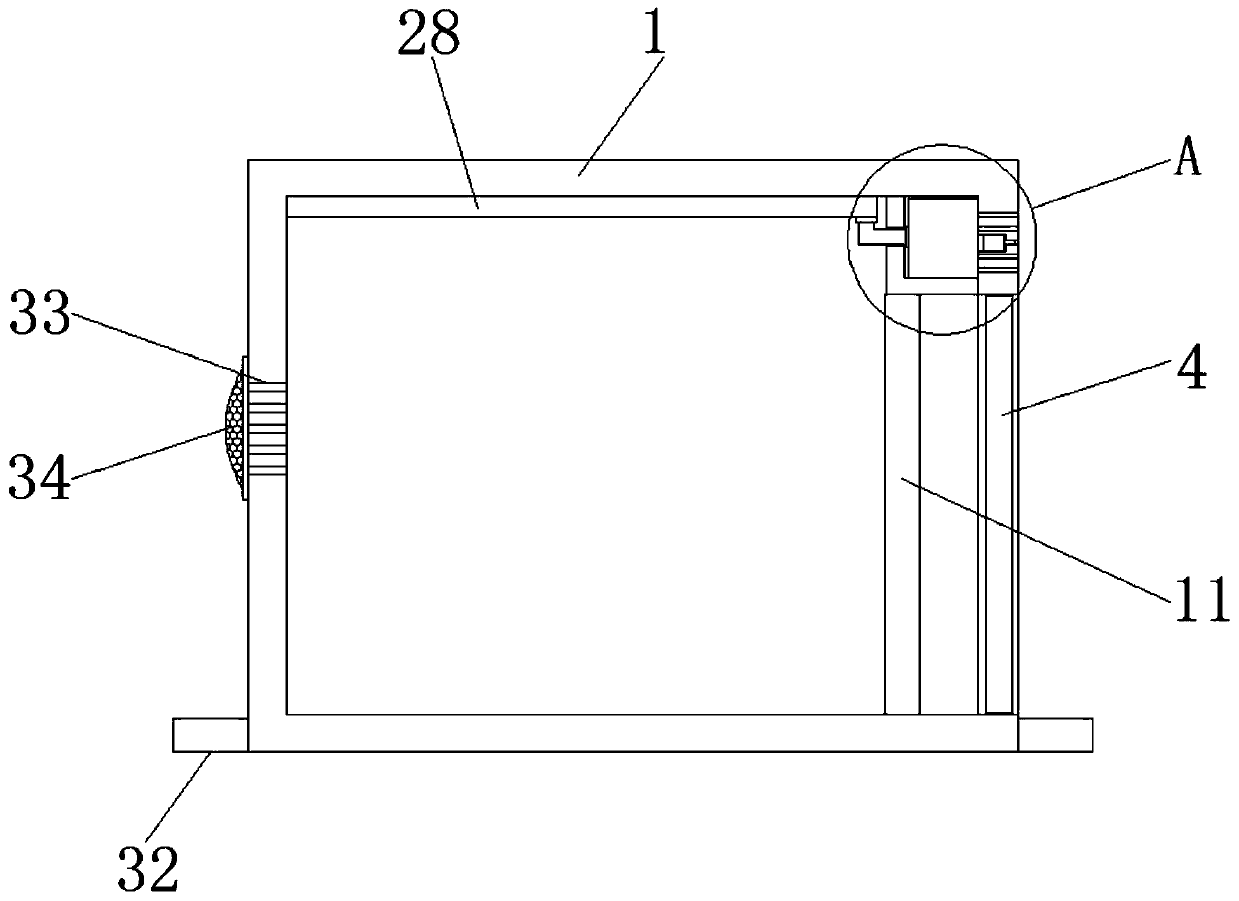
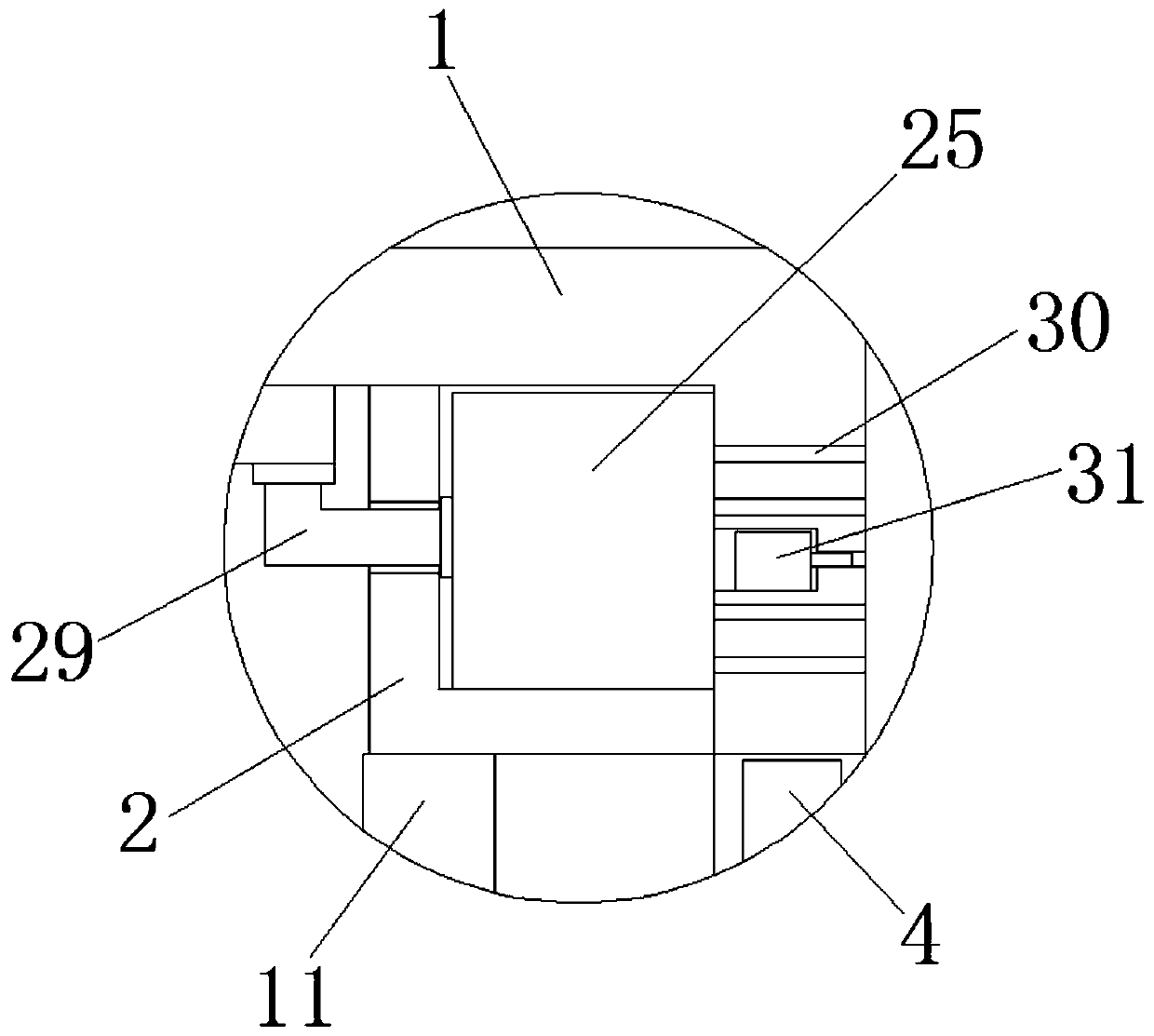
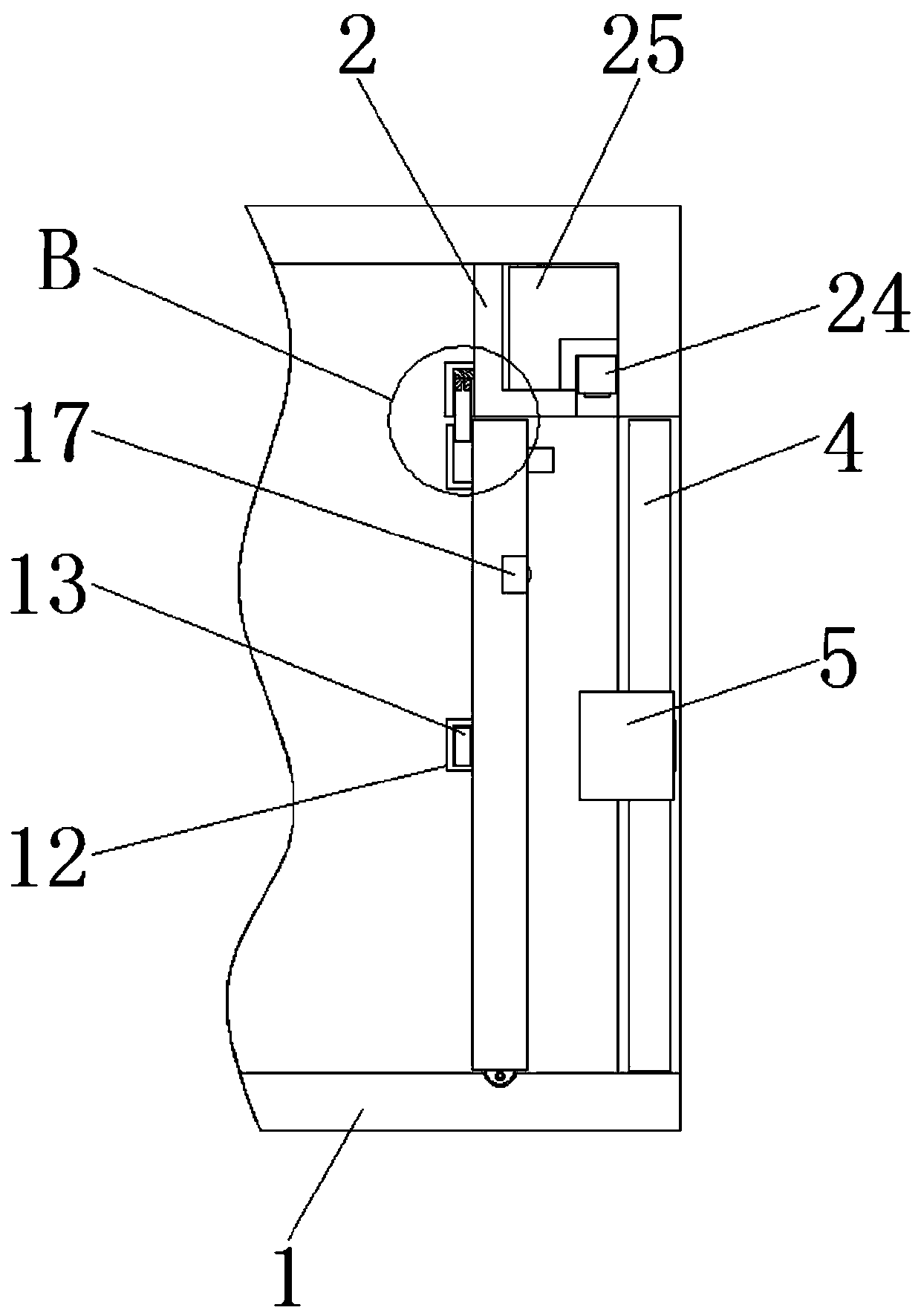
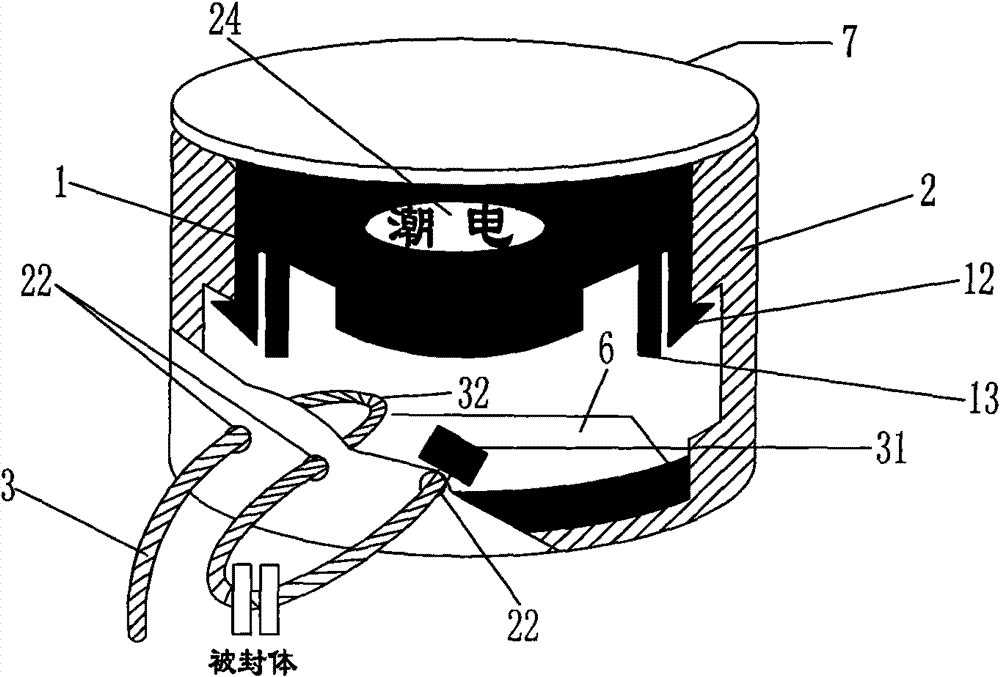
Threading type thief-proof closed device capable of generating identification mark during stealing
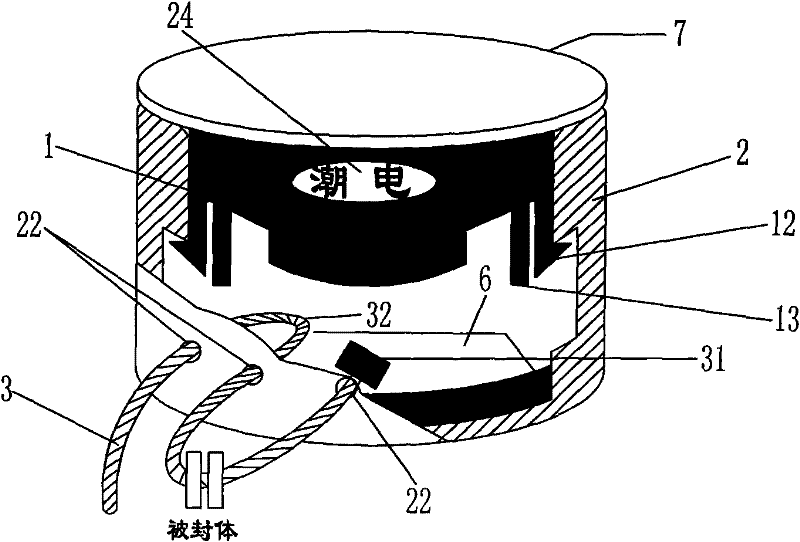
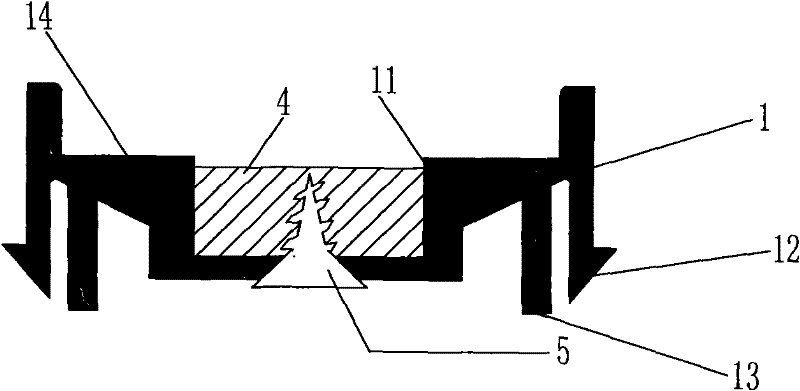
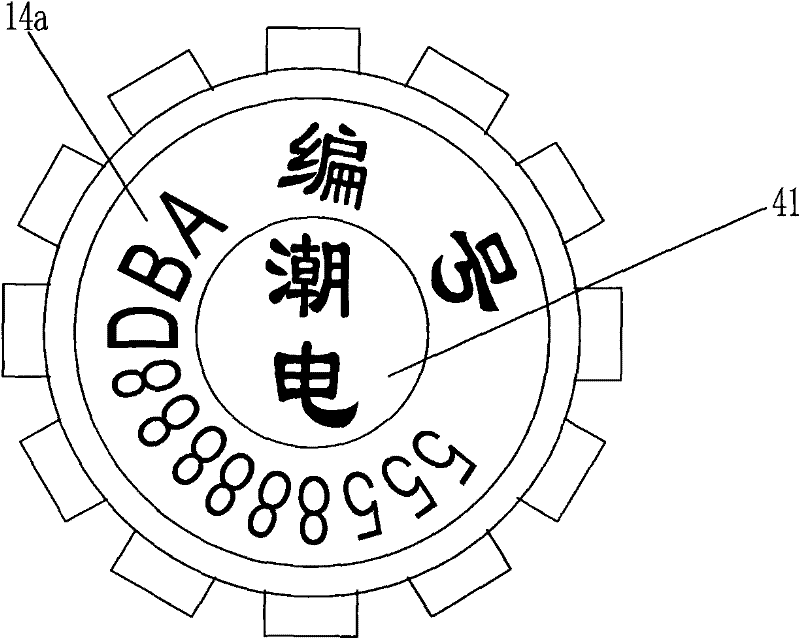
ActiveCN102194372ALeave no traceMeet the distanceStampsIdentification meansClosed loopMechanical engineering
The invention discloses a device which can prevent an unauthorized person from changing a protected object for stealing without leaving traces by counterfeiting or changing a connecting part, and is applied in a device with the need of being closed by a special department. The device is characterized in that a closed loop of a metal connecting rope only extends out of a hole opened on the side wall of a housing of a base, and an end socket of the metal connecting rope and / or the curved connecting part of the metal connecting rope is retained in the housing of the base, so that the end socket of the metal connecting rope and / or the curved connecting part of the metal connecting rope can not move and be used for identifying a stealing mark for stealing from the metal connecting rope; and a closed seat enters from an opening of the housing of the base and is clamped in the position of a clamping ring on the side wall in the housing of the base by a buckle of the closed seat for limiting the separation of the closed seat, the closed seat can not rotate freely in the housing or move up and down freely in the housing, and the closed seat can be used for identifying the stealing mark forstealing from the closed seat. By adopting the device, the role of preventing criminals from damaging the closed seat for stealing from the hole opened at the bottom of the housing of the base is realized.
Owner:余炳顺
Encryption method for mobile phone game software
InactiveCN104166810ASolve the theftProgram/content distribution protectionComputer hardwareMobile phone
The invention discloses an encryption method for mobile phone game software. The mobile phone game software comprises program files and resource files; the encryption process comprises the following steps that (1) the program files and the resource files are merged into at least one large file, a recording file is generated, and the recording file records the starting position and the terminal position of each program file and the starting position and the terminal position of each resource file in the large file; (2) the recording file is merged into the large file; (3) encryption is carried out on the large file to obtain an encrypted file; a decryption process comprises the steps that (4) decryption is carried out on the encrypted file to obtain the large file; (5) the recording file is extracted from the large file; (6) the corresponding program files and the resource files are extracted according to the starting positions and the terminal positions recorded in the recording file. According to the encryption method for the mobile phone game software, simple encryption operations of bit adding or bit subtracting are carried out after the program files and the resource files are merged, and the problem that the program files or the resource files are stolen can be solved effectively.
Owner:SUZHOU JOYME INFORMATION TECH
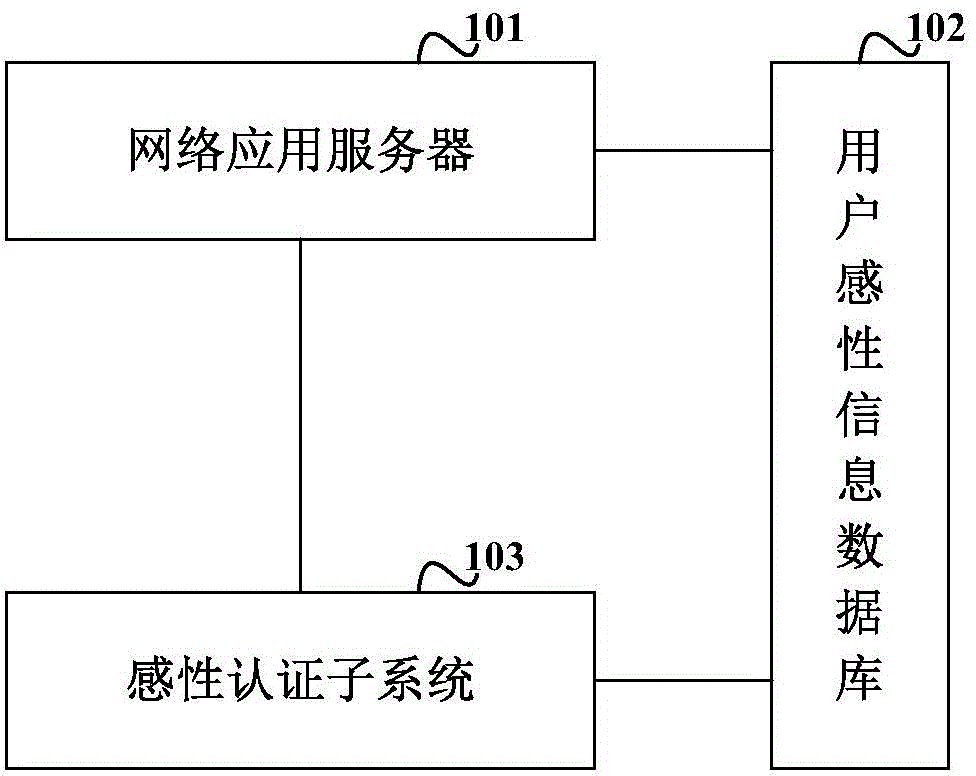
Identity authentication system and method
ActiveCN104980435ASolve lost passwordSolve the theftUser identity/authority verificationPasswordAuthentication system
The invention discloses an identity authentication system and method, and aims at solving problems of user password lost and stealing in the prior art so that security of user identity can be effectively guaranteed. The identity authentication system comprises a network application server, a user perceptual information database and a perceptual authentication subsystem. After an authentication request initiated by a user to be authenticated is received, perceptual authentication questioning-and-answering is performed between the network application server and the user to be authenticated based on a preset perceptual authentication scene, and authentication answer information is transmitted. The user perceptual information database is used for storing user names of all the registered users and corresponding perceptual information including personality characteristic information, emotional activity information and behavior capability information. The perceptual authentication subsystem is used for verifying whether the authentication answer information of the user to be authenticated is simultaneously matched with the perceptual information corresponding to the user name of the user to be authenticated stored in the user perceptual information database. If the verification result is yes, the user to be authenticated passes the identity authentication through judgment, or the user to be authenticated does not pass the identity authentication through judgment.
Owner:MICRO DREAM TECHTRONIC NETWORK TECH CHINACO
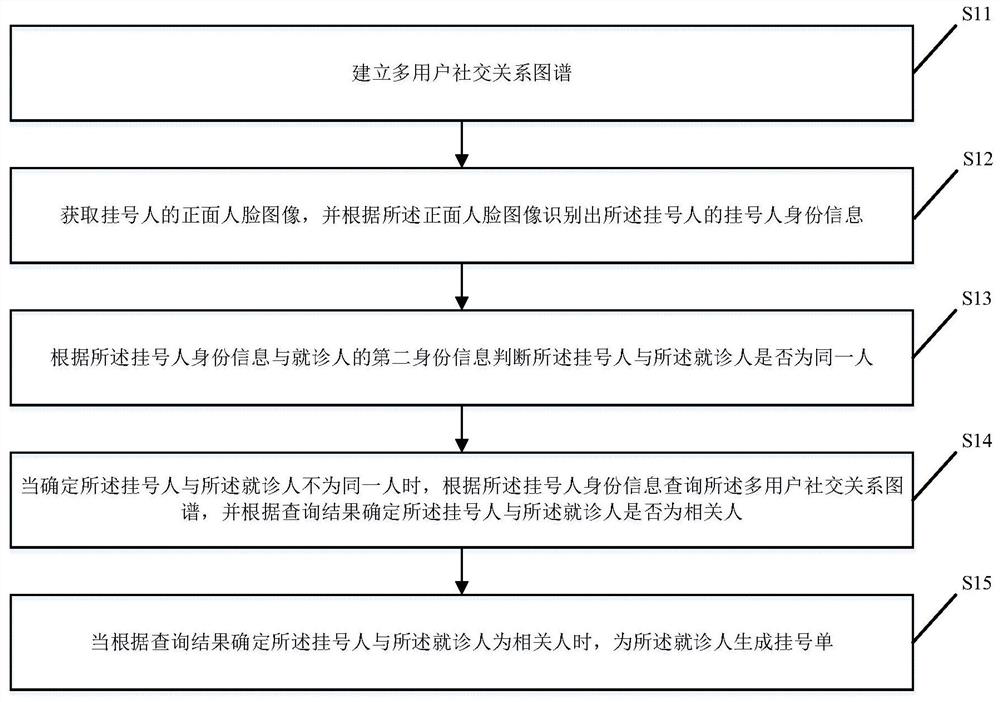
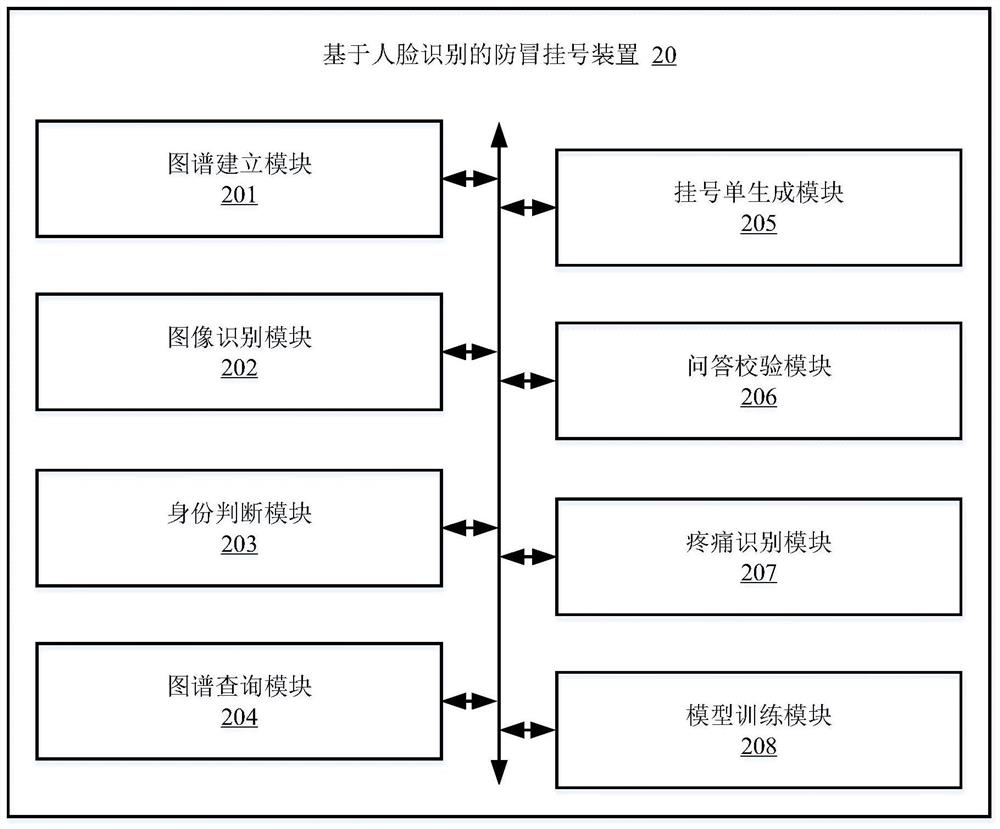
Anti-counterfeiting registration method and device based on face recognition, computer equipment and medium
PendingCN111986794ASolve the theftImprove registration efficiencyData processing applicationsCharacter and pattern recognitionMedical treatmentNursing
The invention relates to the technical field of digital medical treatment, and provides an anti-counterfeiting registration method and device based on face recognition, computer equipment and a medium. The method comprises: establishing a multi-user social relationship graph; acquiring a front face image of a registrar, and identifying the registrar identity information of the registrar accordingto the front face image; according to the identity information of the registrant and the second identity information of a doctor-seeing person, judging whether the registrant and the doctor-seeing person are the same person; when it is determined that the registered person and the doctor-seeing person are not the same person, inquiring the multi-user social relation graph according to the identityinformation of the registrar, and determining whether the registrar and the doctor-seeing person are related persons according to an inquiry result; and when it is determined that the registrar is related to the doctor-seeing person according to the query result, generating a registration list for the doctor-seeing person. According to the invention, the problem that the medical insurance card isstolen can be solved, and the registration efficiency is improved.
Owner:深圳平安智慧医健科技有限公司
Underground waterproof communication device cabin
InactiveCN103414276ALow land useSolve the impact of air pollution on electronic equipmentSupports/enclosures/casingsElectrical apparatus casings/cabinets/drawersDevice breakageEngineering
The invention relates to an underground waterproof communication device cabin which comprises a ground well and a surface cover, wherein the upper end of the surface cover is flush with or higher than the ground. A waterproof cover is arranged in a communication well at the lower end of the surface cover. The communication well is connected with a device installation room. A stair for a person to go up and down, an electronic device of the underground waterproof communication device cabin, an indoor unit of an air conditioner device and space for the person to move are arranged in the device installation room. According to the underground waterproof communication device cabin, the enough space for the person to move is arranged in the ground well, installation and maintenance of the electronic device can be carried out in the ground well, and the problem that the electronic device is damaged due to the fact that the electronic device is lifted to the ground from the underground is solved. According to the underground waterproof communication device cabin, the land use amount of a wireless communication base station is reduced to be the lowest degree, the problem that the electronic device is influenced by air pollution is solved, and meanwhile the problems that the electronic device is stolen and artificially damaged is effectively solved.
Owner:北京国润通达科技有限公司
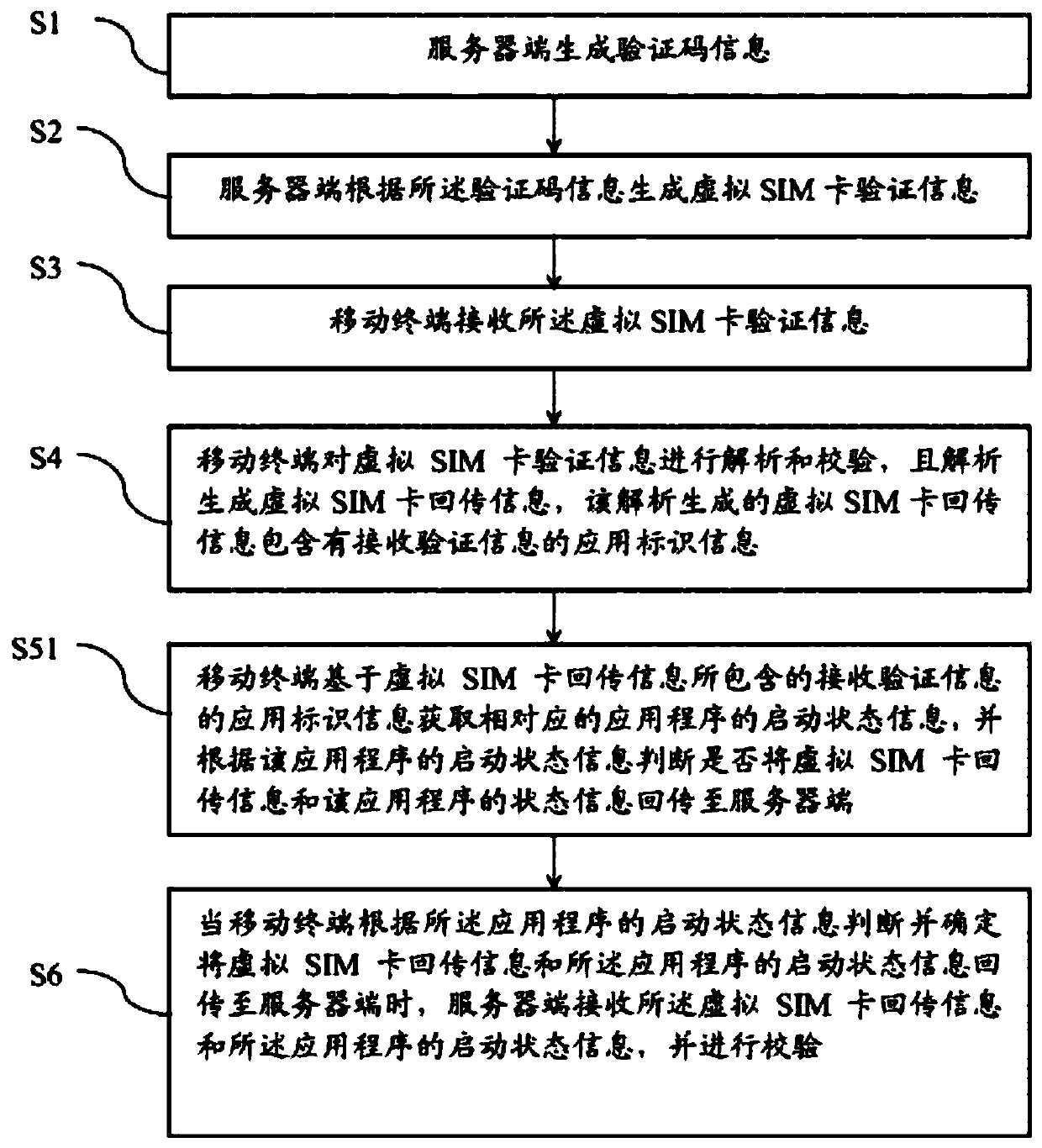
Safety verification method, mobile terminal and server side
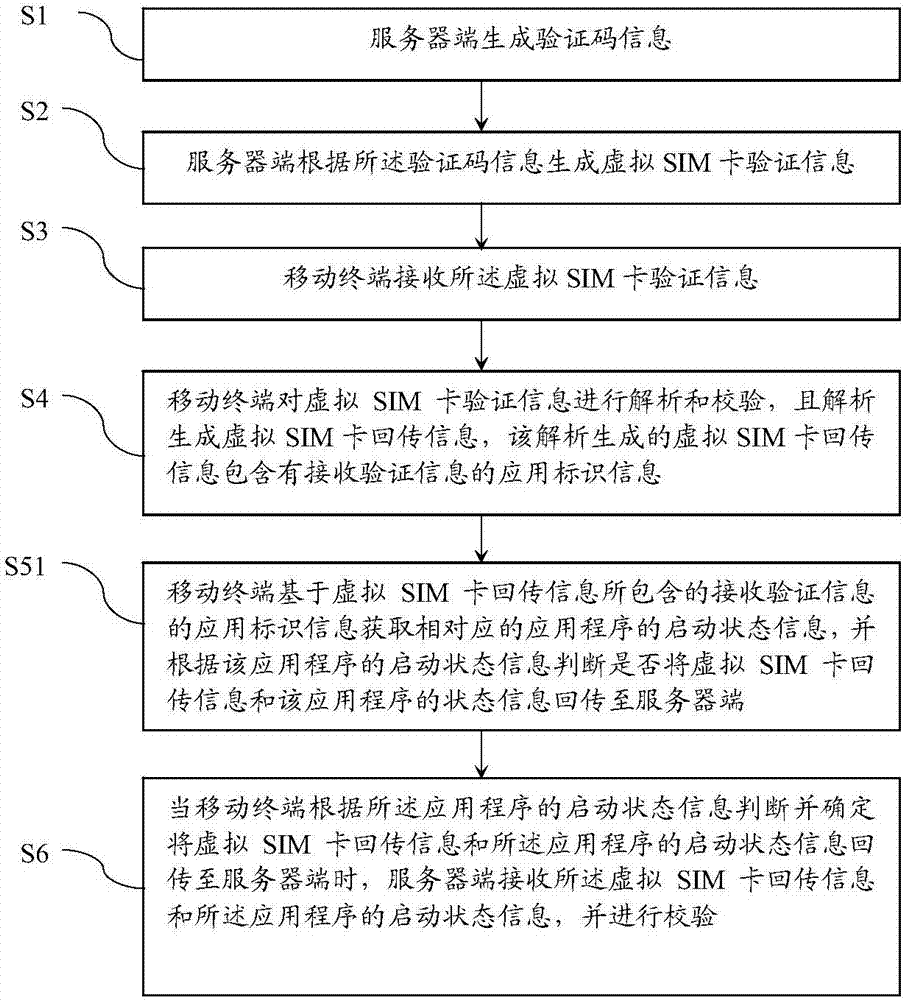
ActiveCN107172076AImprove securitySolve the problem of interception and information theftTransmissionExecution for user interfacesComputer hardwareSecurity validation
The invention discloses a safety verification method, a mobile terminal and a server side. The safety verification method comprises the following steps that the server side generates verification code information; the server side generates virtual SIM card verification information according to the verification code information; the mobile terminal receives the virtual SIM card verification information; the mobile terminal carries out analysis and check on the virtual SIM card verification information and generates virtual SIM card return information through analysis, wherein the virtual SIM card return information which is generated through analysis includes application identification information of receiving verification information; and the mobile terminal obtains status information of a corresponding application based on the application identification information of the receiving verification information, which is included in the virtual SIM card return information, and judges whether to return the virtual SIM card return information and the status information of the application to the server side according to the status information of the application. According to the safety verification method, the problems of information intercept and stealing can be solved and the safety for user check information is guaranteed.
Owner:新格云信科技有限公司
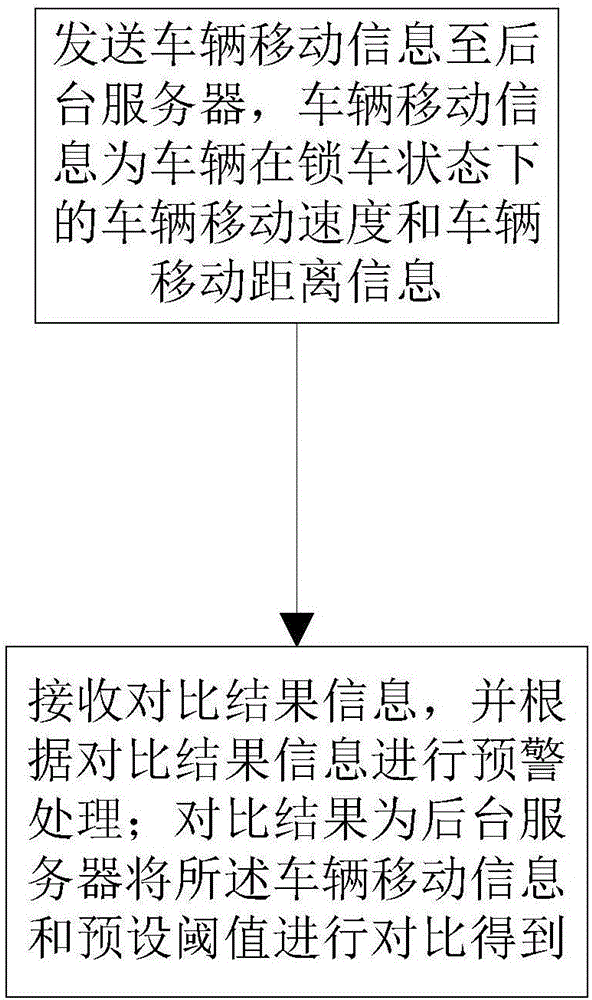
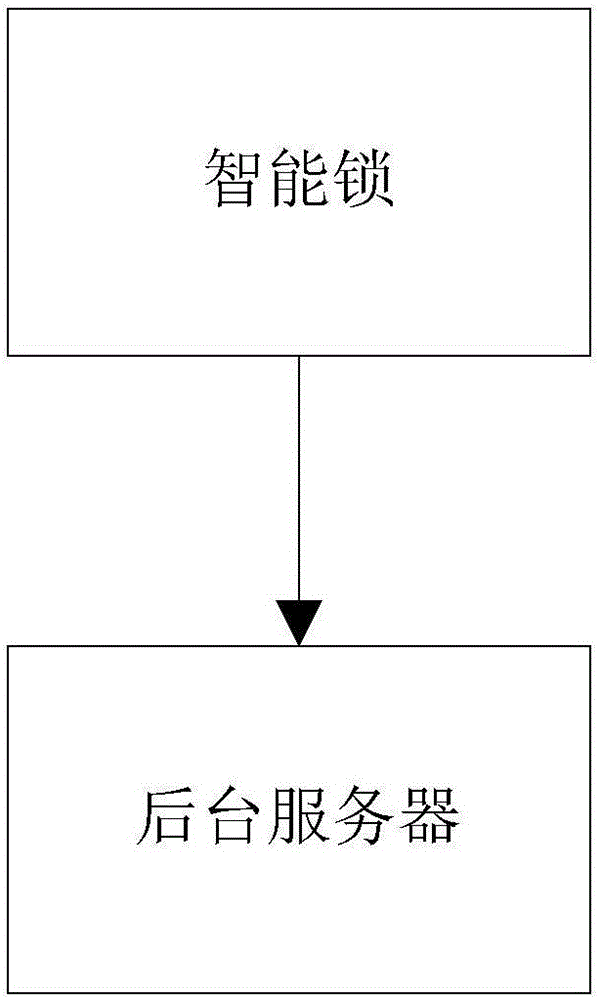
Illegal-moving-based positioning method, electronic equipment, and storage medium
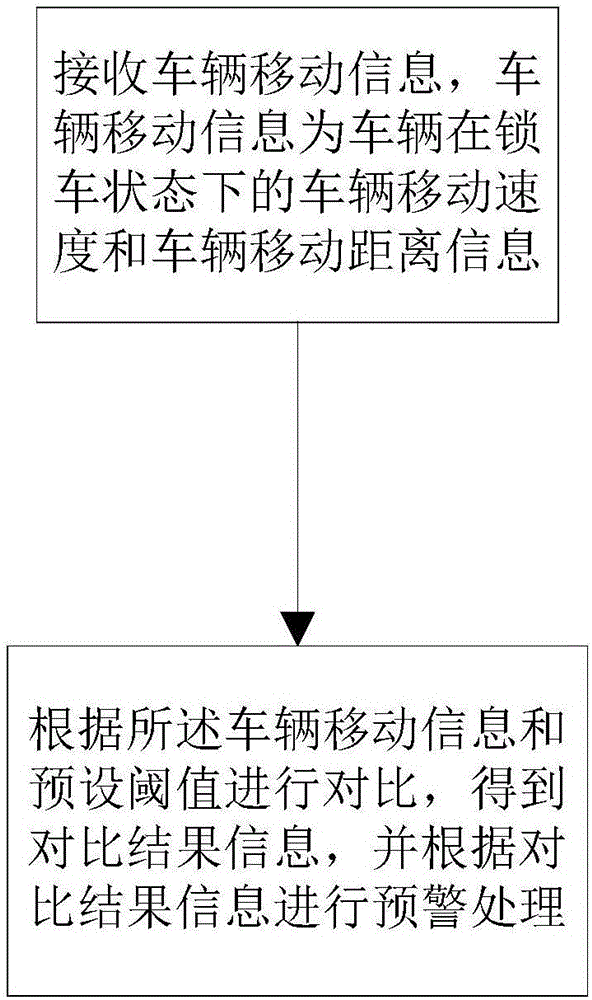
InactiveCN107527498ASolve the theftRoad vehicles traffic controlIndividual entry/exit registersMoving speedReal-time computing
The invention discloses an illegal-moving-based positioning method. The method comprises a receiving step and a comparison and early warning step. At the receiving step, vehicle movement information is received, wherein the vehicle movement information is vehicle movement speed and vehicle movement distance information of a vehicle in a locked state. At the comparison and early warning step, comparison with a preset threshold is carried out based on the vehicle movement information to obtain comparison result information; and early warning processing is carried out based on the comparison result information. Or the method includes a sending step and a comparison and early warning step. At the sending step, vehicle movement information is sent to a backend server, wherein the vehicle movement information is vehicle movement speed and vehicle movement distance information of a vehicle in a locked state. And at the comparison and early warning step, comparison result information is received and early warning processing is carried out based on the comparison result information, wherein the comparison result is obtained by comparing the vehicle movement information with a preset threshold by the backend server. In addition, the invention also discloses electronic equipment and a storage medium. Therefore, a problem that vehicles are stolen by some users by means of illegal movement is solved.
Owner:广州捷泰通贸易有限公司
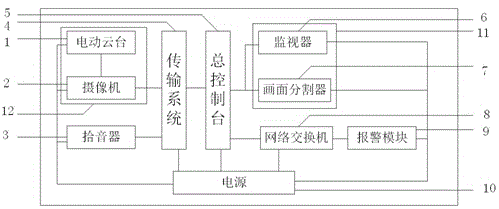
Novel video security monitoring alarm system
InactiveCN106888362ASolve the theftFix security issuesClosed circuit television systemsBurglar alarm mechanical actuationVideo monitoringCredit union
A new type of video security monitoring and alarm system, the invention belongs to the field of security technology, and specifically provides a new type of video security monitoring system with digital monitoring and remote monitoring functions to effectively improve the security and technical level of credit unions at all levels, so that video Monitoring technology is developing in the direction of digitization, intelligence, automation and networking. It consists of electric pan / tilt, camera, pickup, transmission system, main console, monitor, screen divider, network switch, alarm module, power supply, display system, and camera system. It solves the problem of unsafe incidents such as theft and robbery in various financial business outlets and the surrounding environment due to the defects of the traditional video surveillance system. It has the characteristics of safety, accuracy and real-time performance.
Owner:西安正通电子科技有限公司
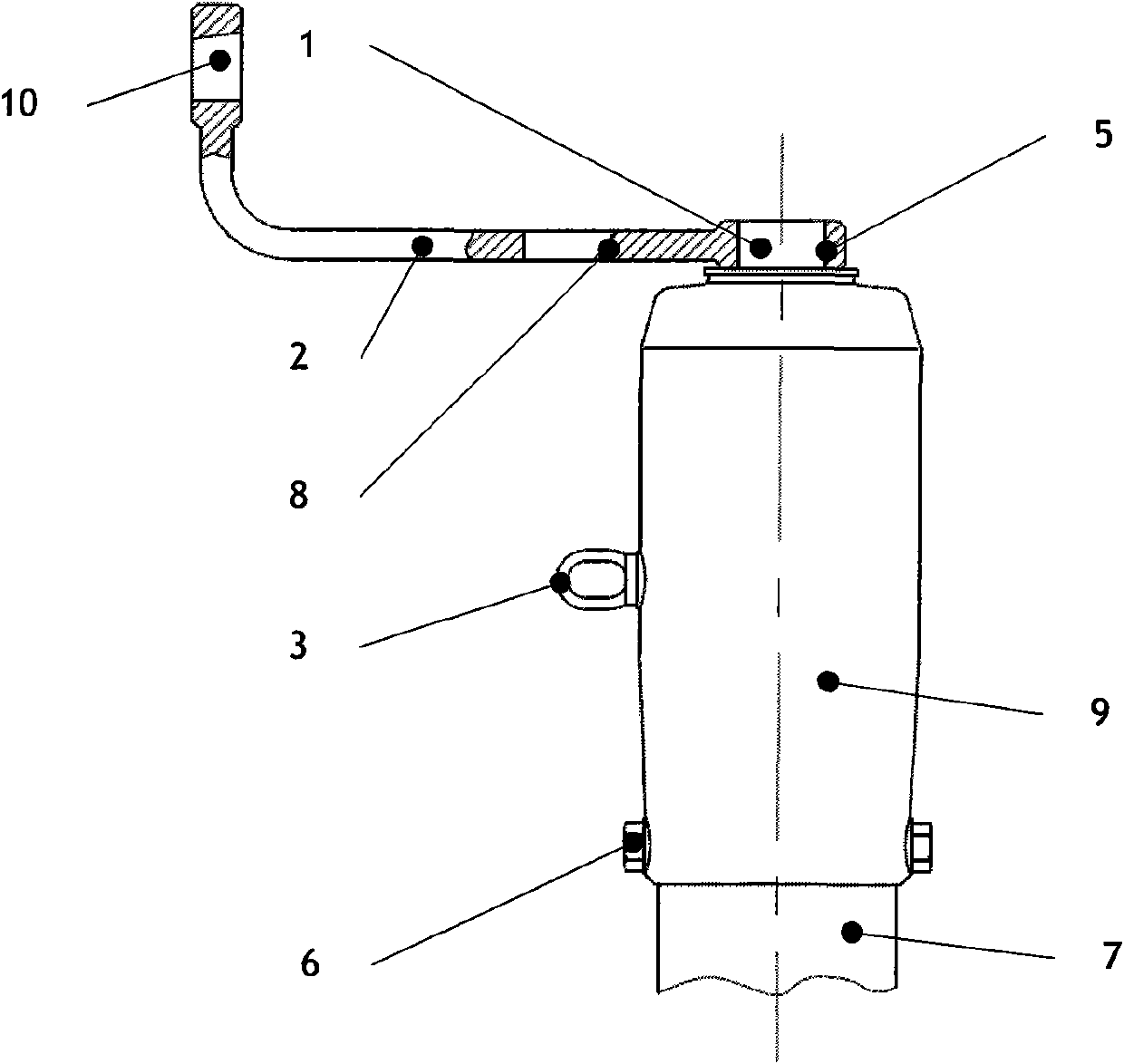
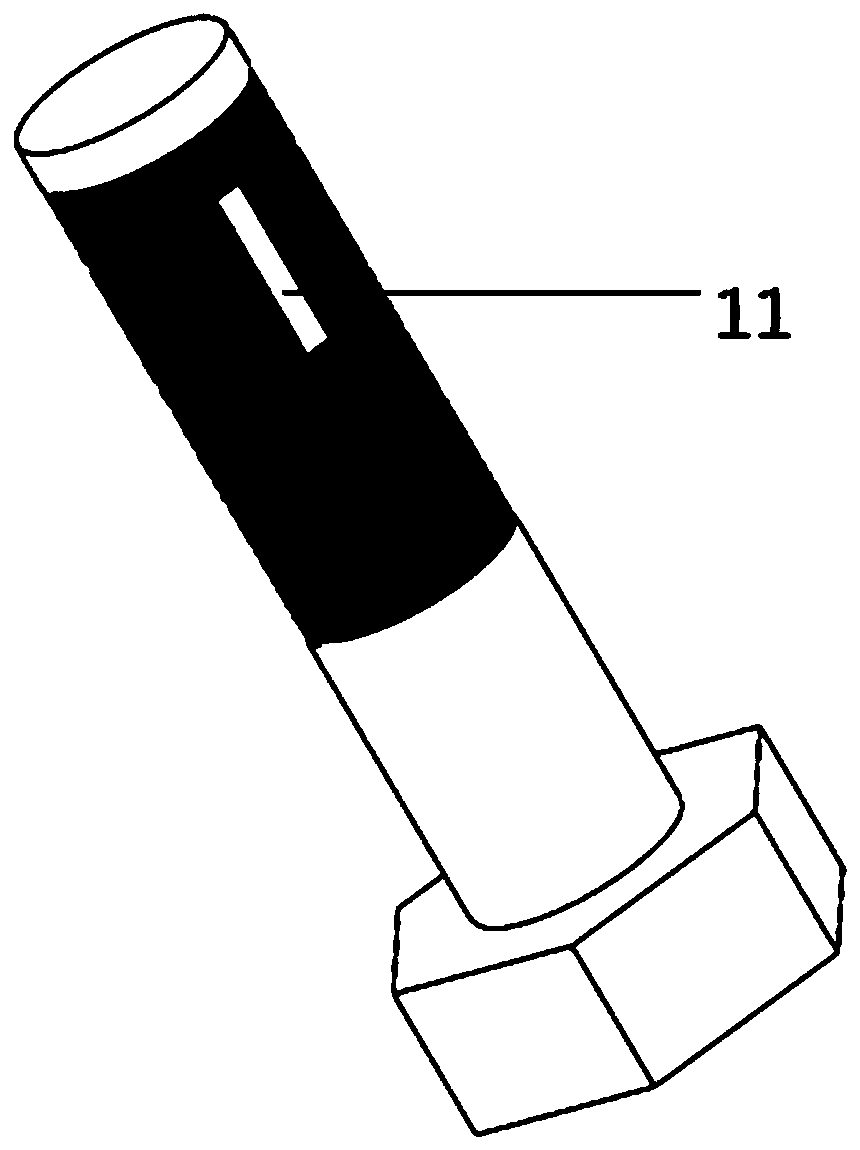
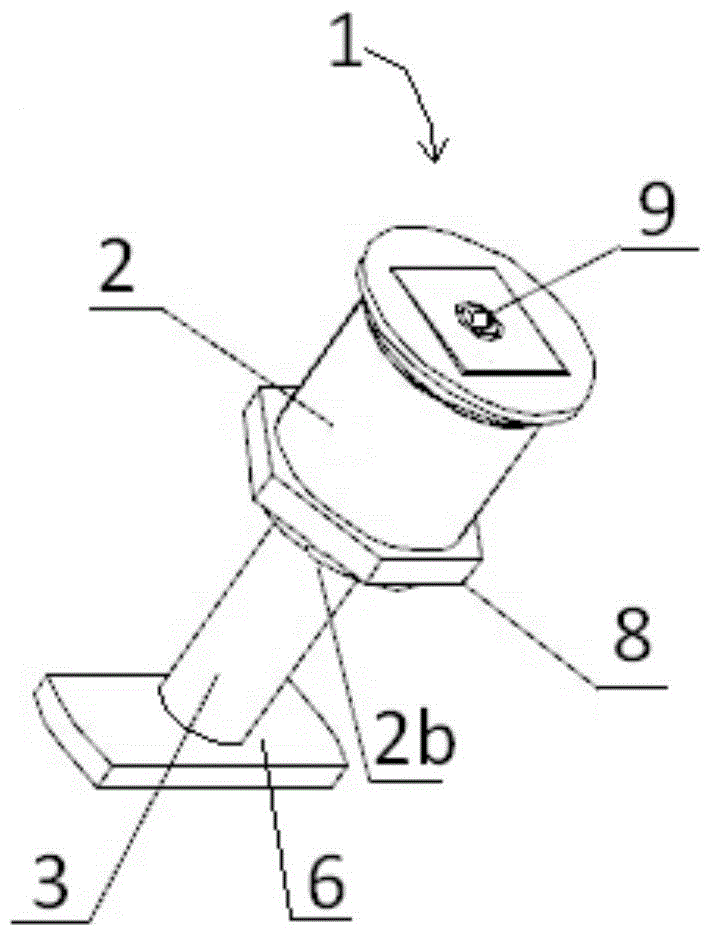
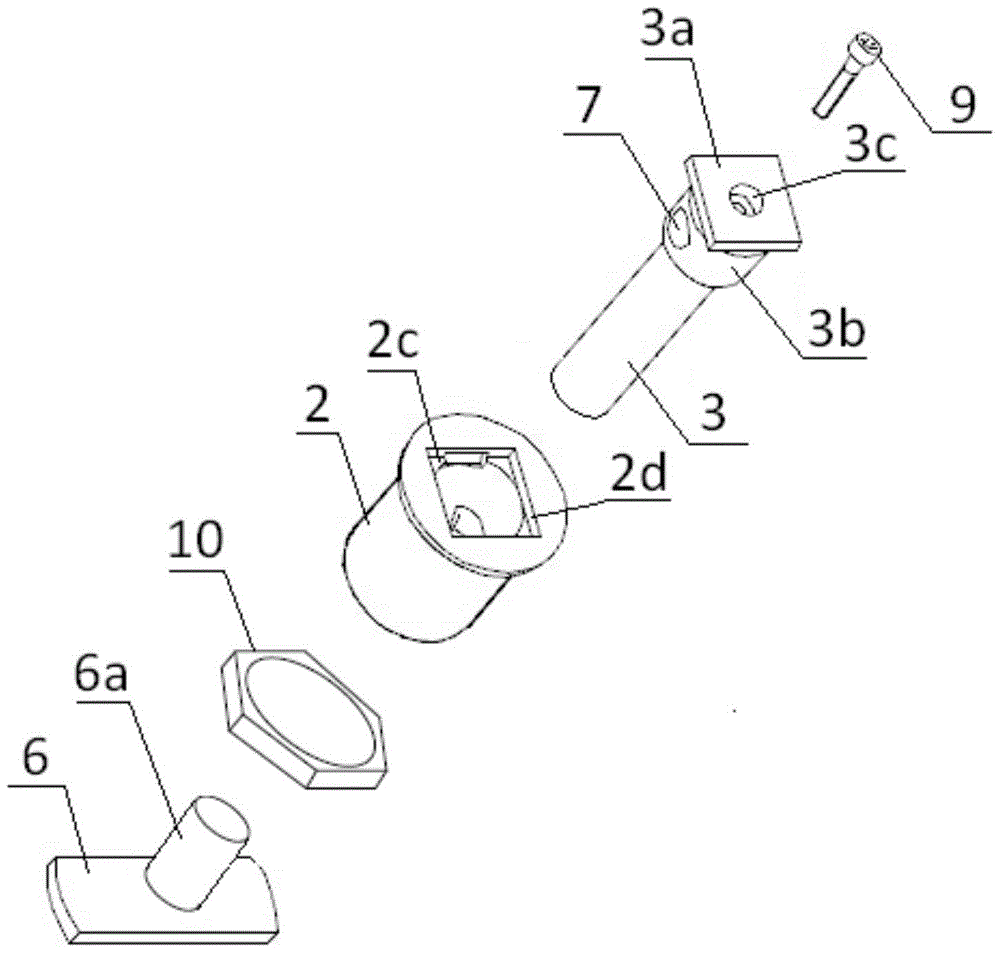
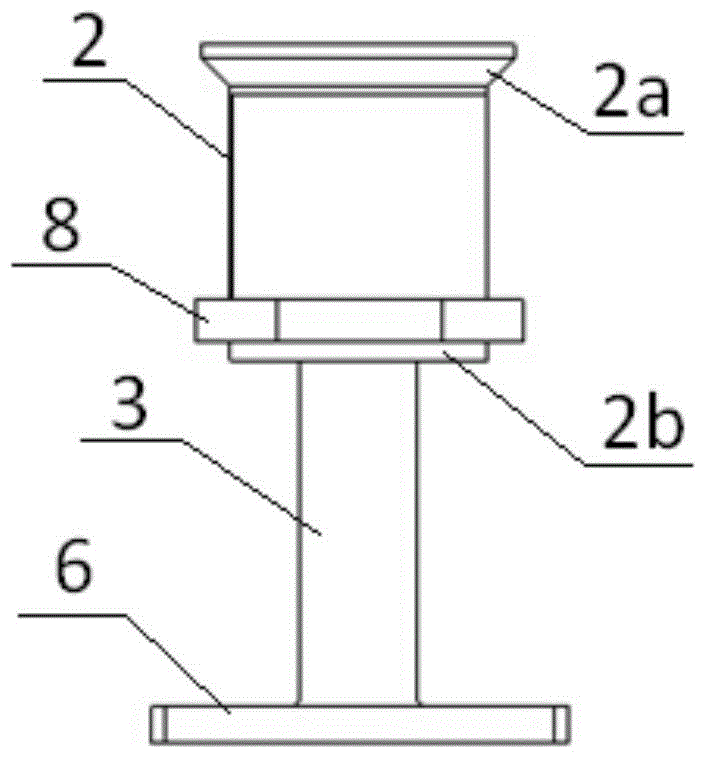
Liquid-sealed integration bolt
The invention discloses a liquid-sealed integration bolt. The liquid-sealed integration bolt comprises a cylindrical bolt body, the bolt body is provided with a nut and a thread structure, the bolt body is also provided with a pressure push groove structure which penetrates through the whole bolt body, two sealing membranes are arranged inside the pressure push groove, liquid curable adhesive is arranged between the sealing membranes, and the upper end of the thread structure of the bolt body is provided with two liquid outlet hole structures. According to the liquid-sealed integration bolt, the liquid curable adhesive is arranged inside the pressure push groove inside the bolt body to complete the tight connection between the bolt and a screw hole, so that the structure is simple, the connection effect is good, thread slipping, loosening and the like can be avoided during long-time usage, the service life is long, and the problem of theft of bolts of power equipment can be solved.
Owner:JIANGSU YONGHAO HIGH STRENGTH BOLT
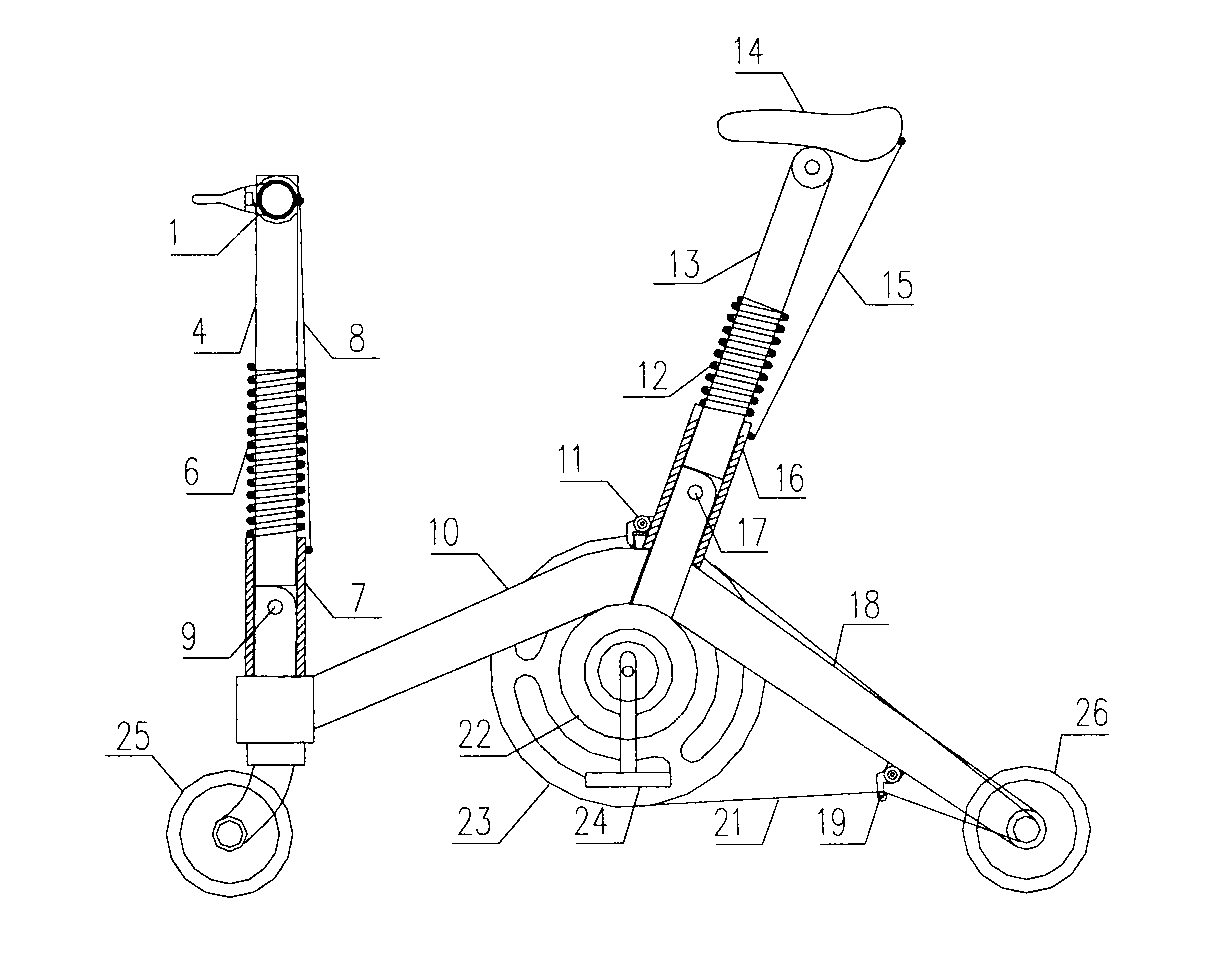
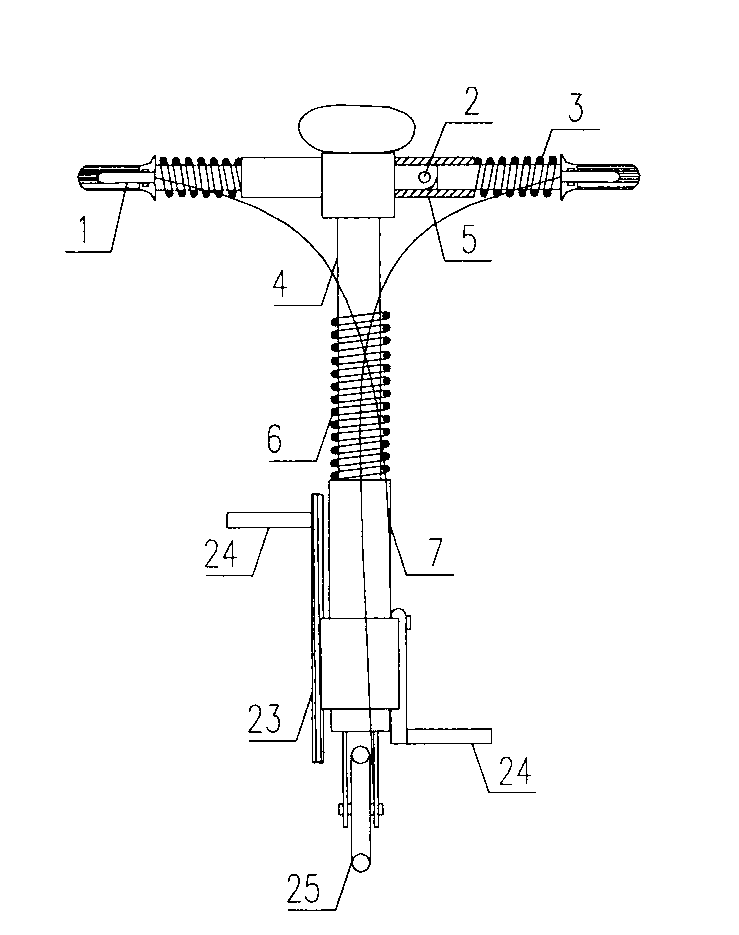
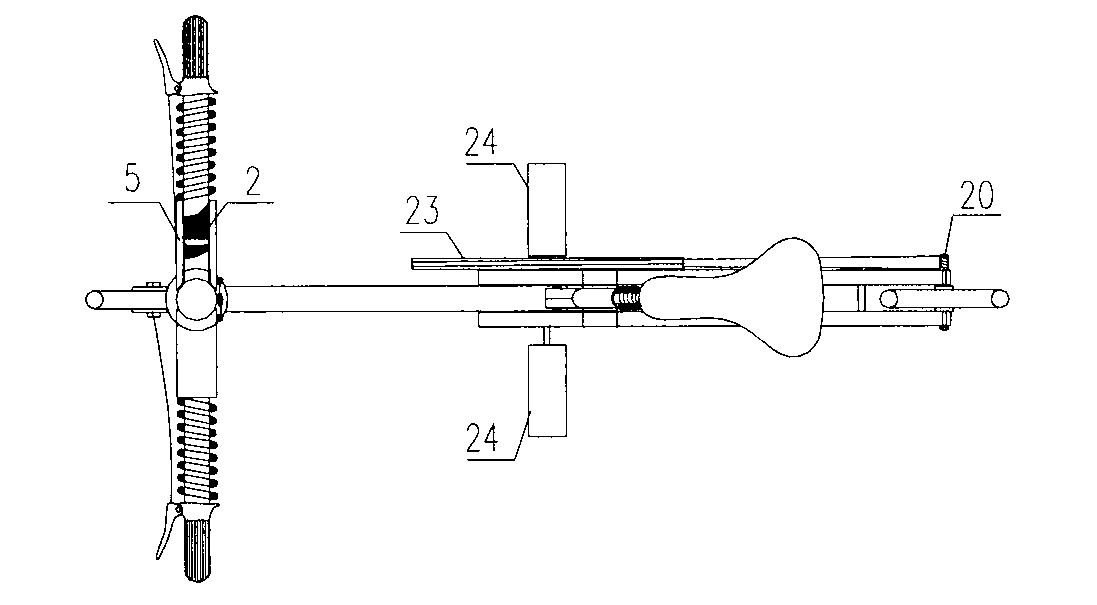
Folding bicycle
The invention provides a portable folding bicycle. The folding bicycle adopts light materials totally to produce various systems; a front frame and a rear frame adopt the lever principle, according to folding and spreading of each system, the stability of an internal frame plane is maintained through a front and rear frame coupling mechanism, and the problem about power transmission is solved through steel wire stranded wire or belt transmission. The systems include a handlebar folding system, a handlebar upright rod folding system, a sitting stool folding system, a front and rear frame folding system, a transmission system and a plane internal-stabilizing system. The folding bicycle is light, small in size, fast in folding, portable, and convenient to ride before getting on or after getting off when people take a bus, subway, train and private car and when people in a travel destination; public transportation green travel is promoted; and the problem that the riding vehicle is stolen is solved completely.
Owner:肖蜀明
A Secure Payment System
ActiveCN109242679AAvoid double paymentSolve the theftFinancePayment protocolsCommunications securityPublic account
The invention relates to a secure payment system, comprising a client, a checking module, a storage module, a public account and a block chain. By charging a packing fee, the height of the block waiting for a transaction is set to prevent users from paying the same transaction repeatedly in a short period of time. Block chain, cryptography, communication security and other axiomatic technologies are used to protect the payment instructions of various digital assets, and the problems of the instruction theft, tampering and other problems are solved from the principle.
Owner:HANGZHOU FUZAMEI TECH CO LTD
Mobile phone without SIM card
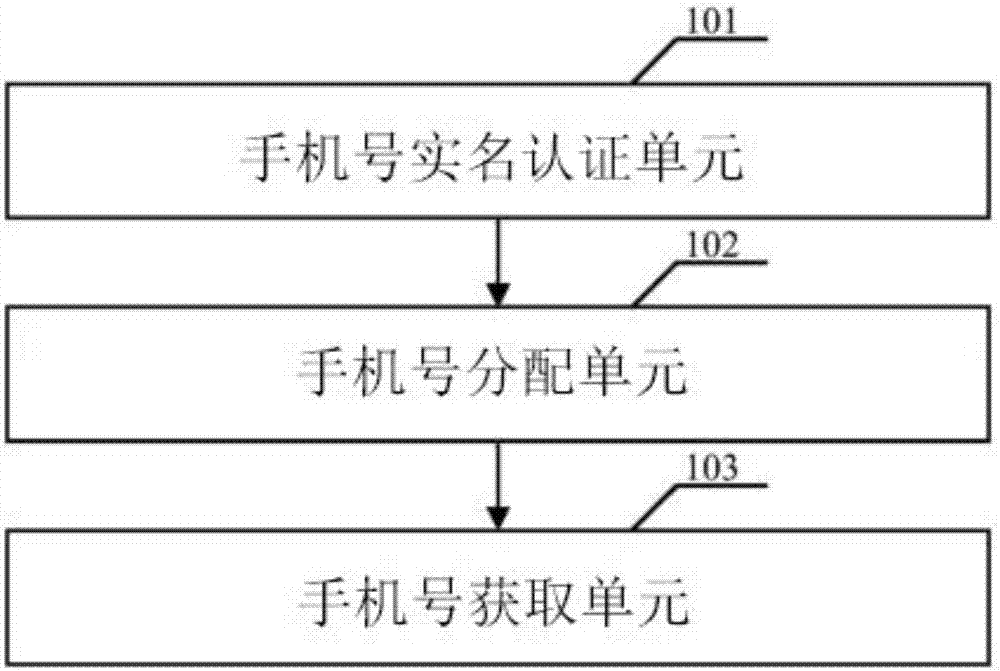
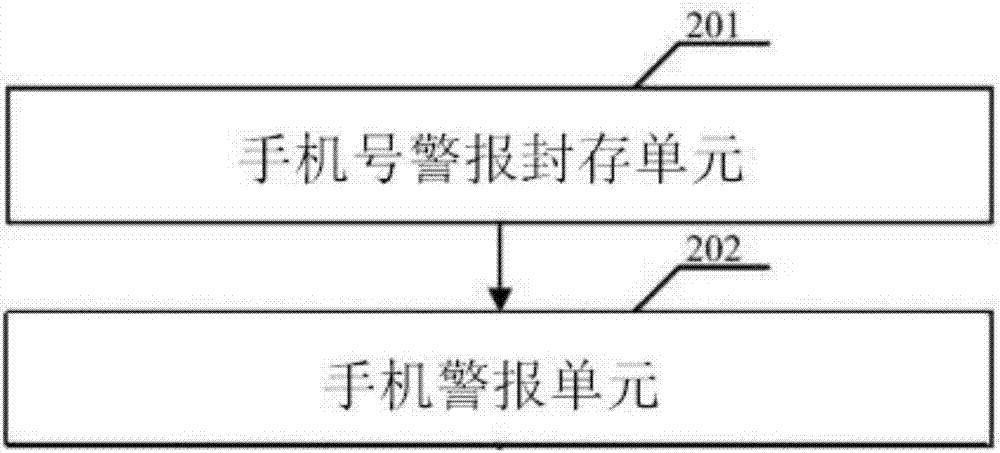
InactiveCN107071761ASave external spaceAvoid exposure to problems that adversely affect useNetwork data managementWork memoryData memory
The invention relates to the technical field of mobile phones, and particularly to a mobile phone without an SIM card. The mobile phone without the SIM card is internally integrated with a microprocessor, a program memory, a work memory, a data memory and a serial communication unit which realizes functions of a real SIM card and is in an integrated structure with the phone body; the mobile phone without the SIM card is provided with a mobile phone number obtaining unit which is connected with an operator server, and the corresponding operator server is provided with a mobile phone number allocation unit; the mobile phone without the SIM card is provided with a mobile phone alarming unit which is connected with the operator server, and the corresponding operator server is provided with a mobile phone number saving unit. The mobile phone without the SIM card not only solves the problem that the existing SIM card slot occupies the external space of the mobile phone, but also solves the problem of information leakage of the stolen mobile phone, and further avoids the theft problem of the mobile phone efficiently.
Owner:SHANDONG RONGAN ELECTRONICS SCI & TECH CO LTD
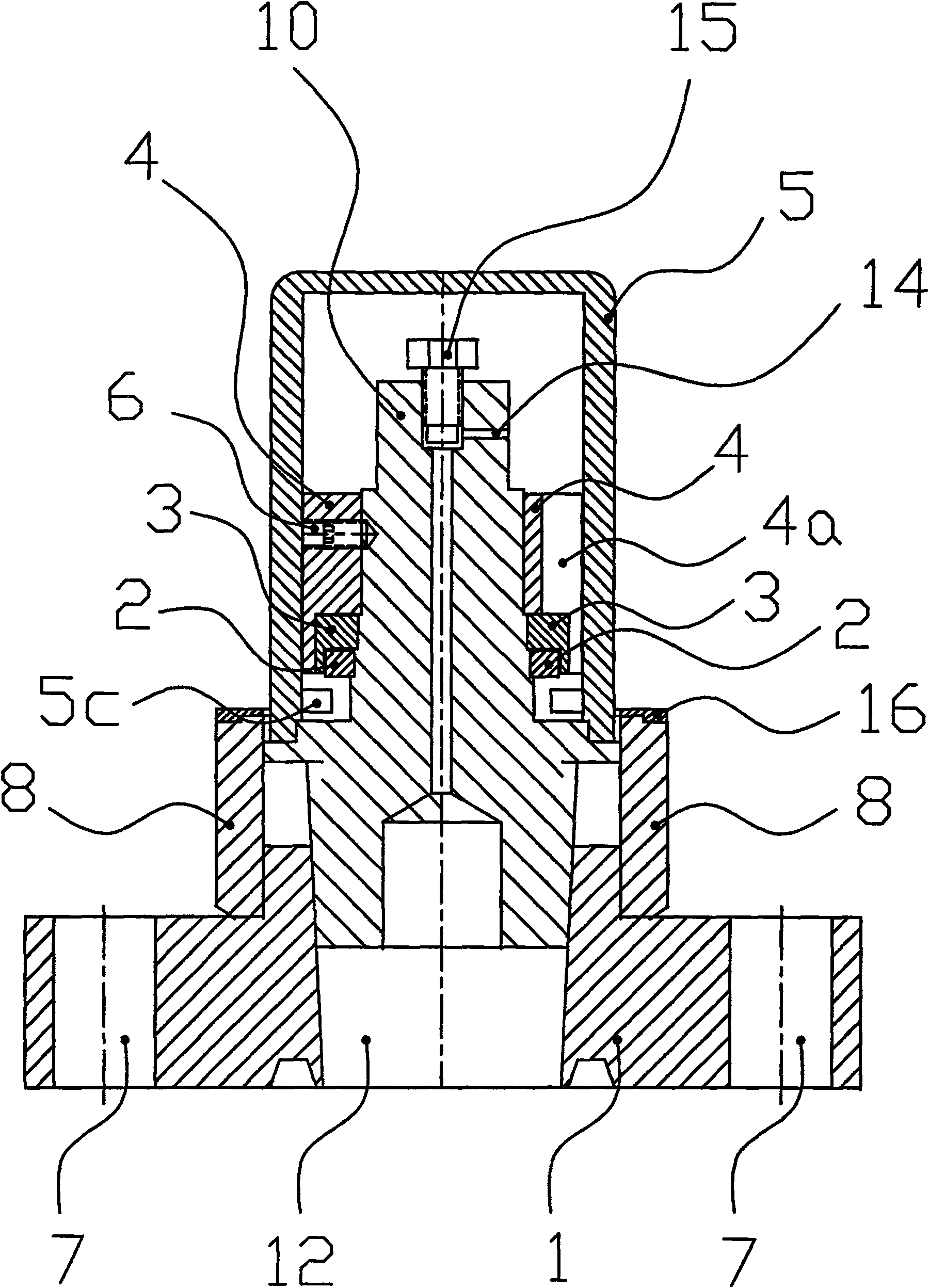
A safety lock control drive device
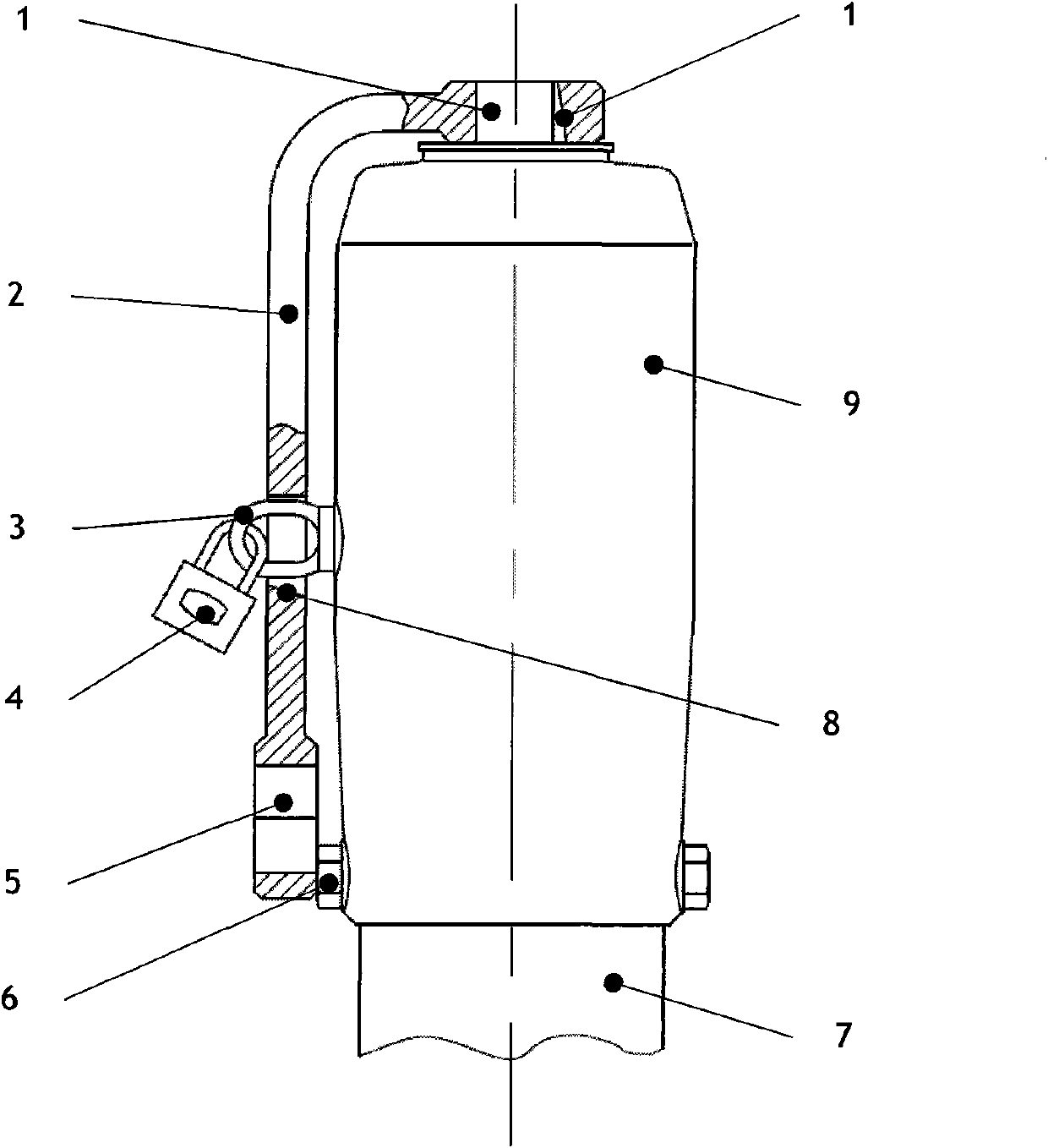
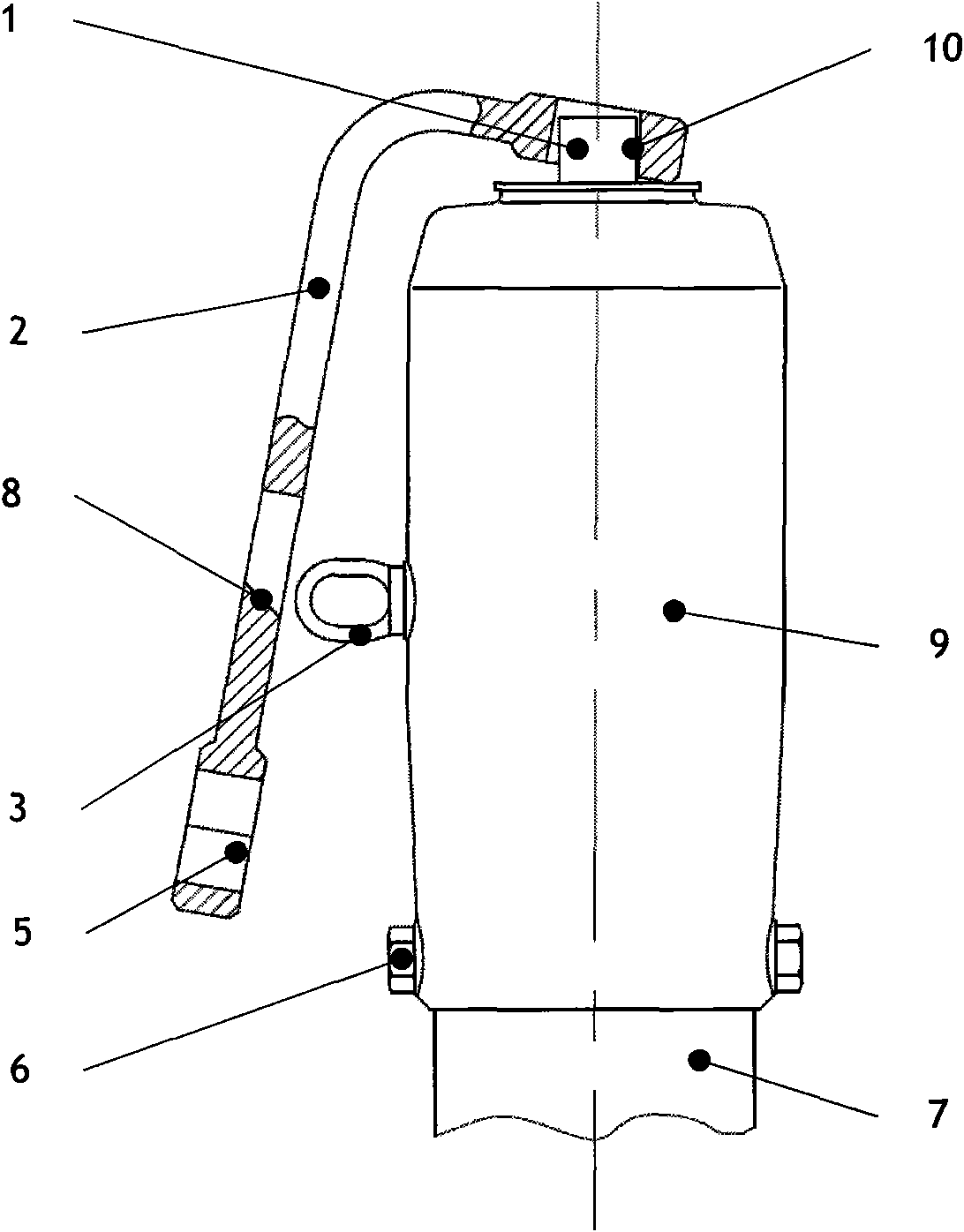
ActiveCN102022581ASolve the theftPrevent random switchingOperating means/releasing devices for valvesPreventing unauthorised/accidental actuationEngineeringWrench
The invention relates to a safety lock control drive device, comprising a driving rod, a wrench, a lock ring, a padlock, a bolt, a protection cylinder and a shield. The protection cylinder and the shield are successively provided outside the driving rod; the driving rod is protected in the protection cylinder and the shield with the upper exposed end connected with the wrench; the bolt is arranged on the shield to fix the shield onto the protection cylinder; the lock ring and the bolt are arranged at same side of the shield, and the lockpad is disposed on the lock ring. Compared with the prior arts, the invention solves the problems of valve random switch and parts stolen just utilizing a wrench, and has the advantage of a simple and compact structure.
Owner:SHANGHAI KARON VALVES MACHINERY +1
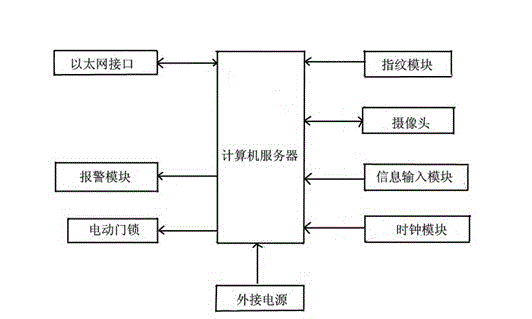
Remote control system for rural supermarket
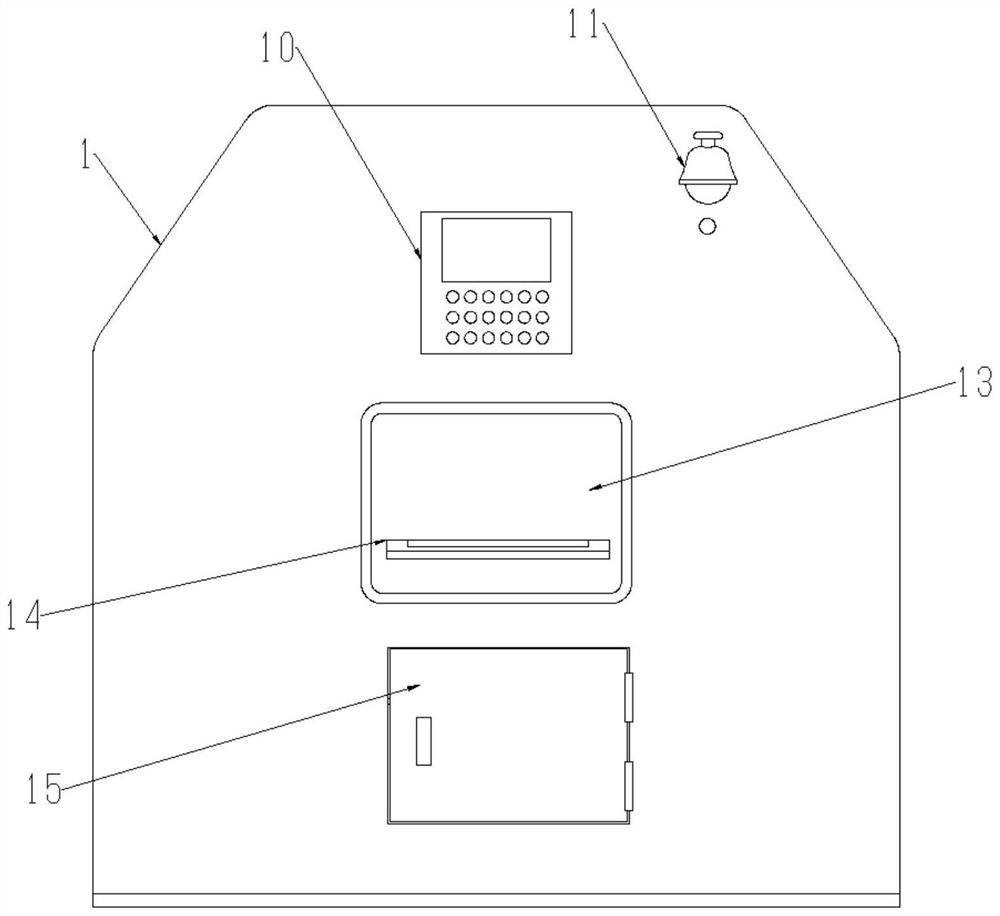
InactiveCN103605334ASolve the theftReduce power consumptionProgramme total factory controlRemote controlControl system
The invention discloses a remote control system for a rural supermarket. The control system includes a computer server, a biological radio-frequency fingerprint module, a camera module, a voice alarm module, a computer network interface, an information input module, a power-supply module, an electrical door lock, a display module and a clock module. The beneficial effects of the remote control system for the rural supermarket are that the system is low in power consumption, flexible to use and man-power saving and enables the rural supermarket to be more competitive with large-scaled supermarkets and to be capable of maintaining the competitive ability.
Owner:KUNSHAN HONGLING ELECTRONICS
Self-tightening bolt and nut tightening assembly
PendingCN110296139ALoose protection problemDoes not affect fatigue strengthNutsBoltsAxial pressureMechanical engineering
The invention provides a self-tightening bolt and nut tightening assembly. The assembly comprises a bolt, and an upper nut, a self-tightening nut, a lower nut, a self-locking gasket and an end nut which are in connecting fit in sequence. Long screw portions which are symmetrically arranged in the diameter direction are arranged on a screw stem. The upper nut and the lower nut are each provided with a circular truncated cone shaped hole. The self-tightening nut comprises two circular truncated cone shaped columns matched with the circular truncated cone shaped holes of the upper nut and the lower nut correspondingly, and further comprises a radial staggered through gap. The self-locking gasket comprises elastic narrow curved surface clamping spine portions symmetrically arranged in the diameter direction and end surface radial wedge-shaped oblique toothed convex grooves matched with the end nut. When under axial pressure, the clamping spine portions deform and stretch and can block thelong groove portions of the screw stem portion of the bolt; and the end nut end surface is provided with wedge-shaped oblique toothed concave grooves in the radial direction, the wedge-shaped obliquetoothed concave grooves can be engaged with the wedge-shaped oblique toothed convex grooves of the self-locking gasket mutually, the screwing-out direction of the end nut is the same as the directionof engaging between the wedge-shaped oblique toothed concave grooves of the end nut and the wedge-shaped oblique toothed convex grooves of the self-locking gasket, and damping and locking effects areachieved.
Owner:高明
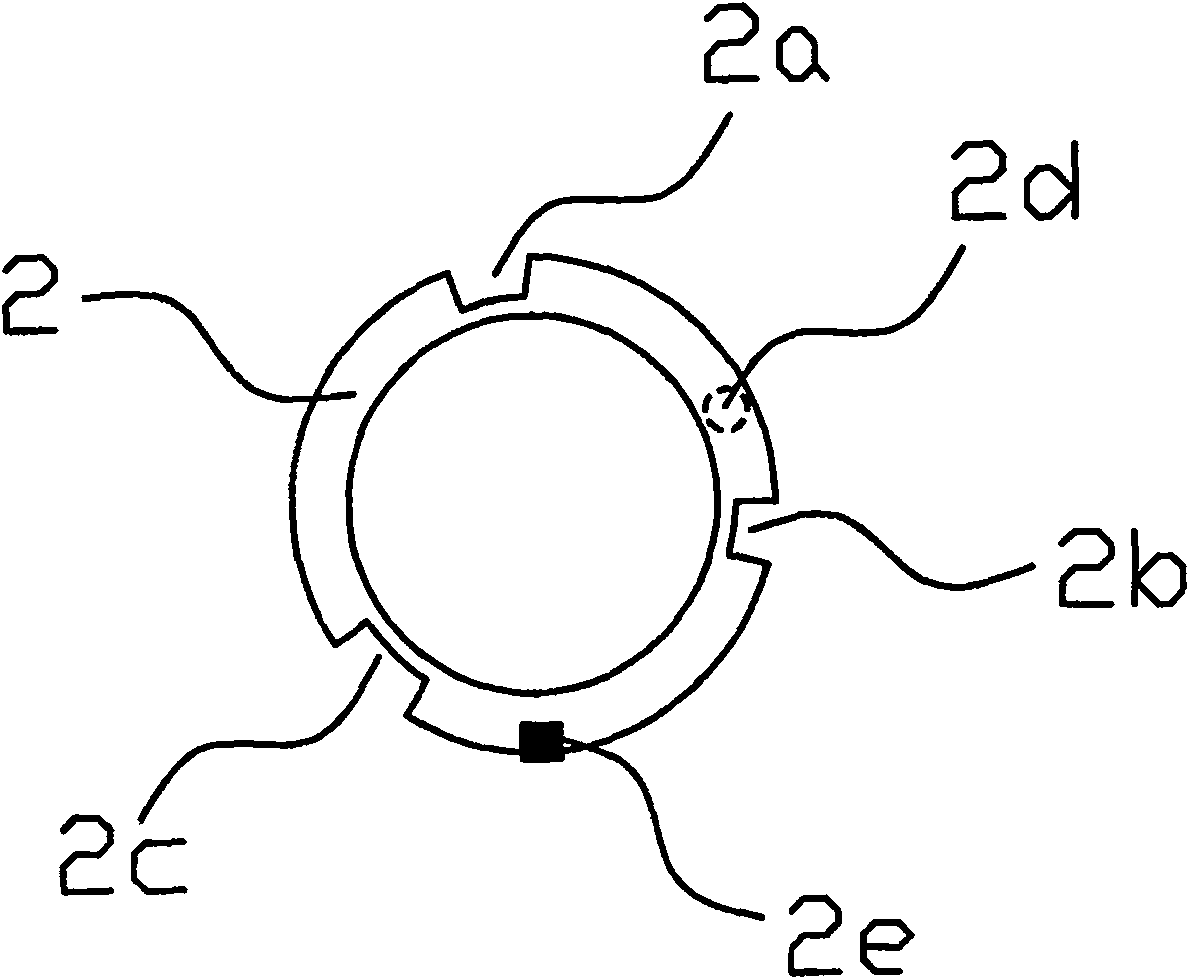
A password helmet lock and its installation method
ActiveCN113404392BConvenient and reliable locking deviceSolve the theftLocks for portable objectsPuzzle locksComputer hardwareKey pressing
The invention relates to a coded helmet lock, including a lock, a lock machine, a release button, a half-moon card, a small coded gear, a large coded gear, a lock shaft, a lock cover, a large coded wheel, a small coded wheel, a lock shaft cover, a coded wheel cover, The handlebar buckle and the handlebar buckle bolt; the lock bolt passes through the lock retainer, the first lock washer, the lock buckle, the second lock washer and the connection hole of the lock in turn and fixes it; the button seat and the release button pass through the button Shaft connection, a key spring is set between the key base and the release key, and the key base and the side of the release key are connected to the locking teeth. The locking teeth, the release key, the key shaft, the key base and the key spring form the release key assembly and are loaded into the In the button groove of the lock machine; the half-moon card shaft is connected with the shaft hole of the half-moon card, and the half-moon card is connected to the half-moon card spring. The beneficial effects of the present invention are: the present invention can provide a convenient and reliable helmet locking device for electric bicycle users, and solve the problem that the helmet may be stolen when going out.
Owner:ZHEJIANG UNIV CITY COLLEGE
A front panel with a locking device
The invention discloses a front edge board provided with a locking device. The front edge board is provided with an installing hole, and the locking device comprises a sleeve fixedly arranged at the installing hole position in a penetrating mode, a locking rod movably arranged inside the sleeve in a penetrating mode, a locking tongue fixed on the locking rod and fixed on a truss or the front edge board with the rotation of the locking rod, an axial limit piece located on the sleeve and used for limiting the movement limit position of the locking rod and a suspension piece located on the locking rod and exposed or hidden on the top surface of the front edge board with the lifting of the locking rod. The front edge board provided with the locking device effectively and simply solves the theft problem of the front edge board, only a professional worker can unlock, the locking rod plays the role of lifting the front edge board, the locking rod and the suspending device of the front edge board are integrated into a whole, the number of openings of the front edge board is reduced, and the attractiveness and the whole strength of the front edge board are guaranteed.
Owner:HANGZHOU XO ELEVATOR
Encrypted sealing joint for oil gas well
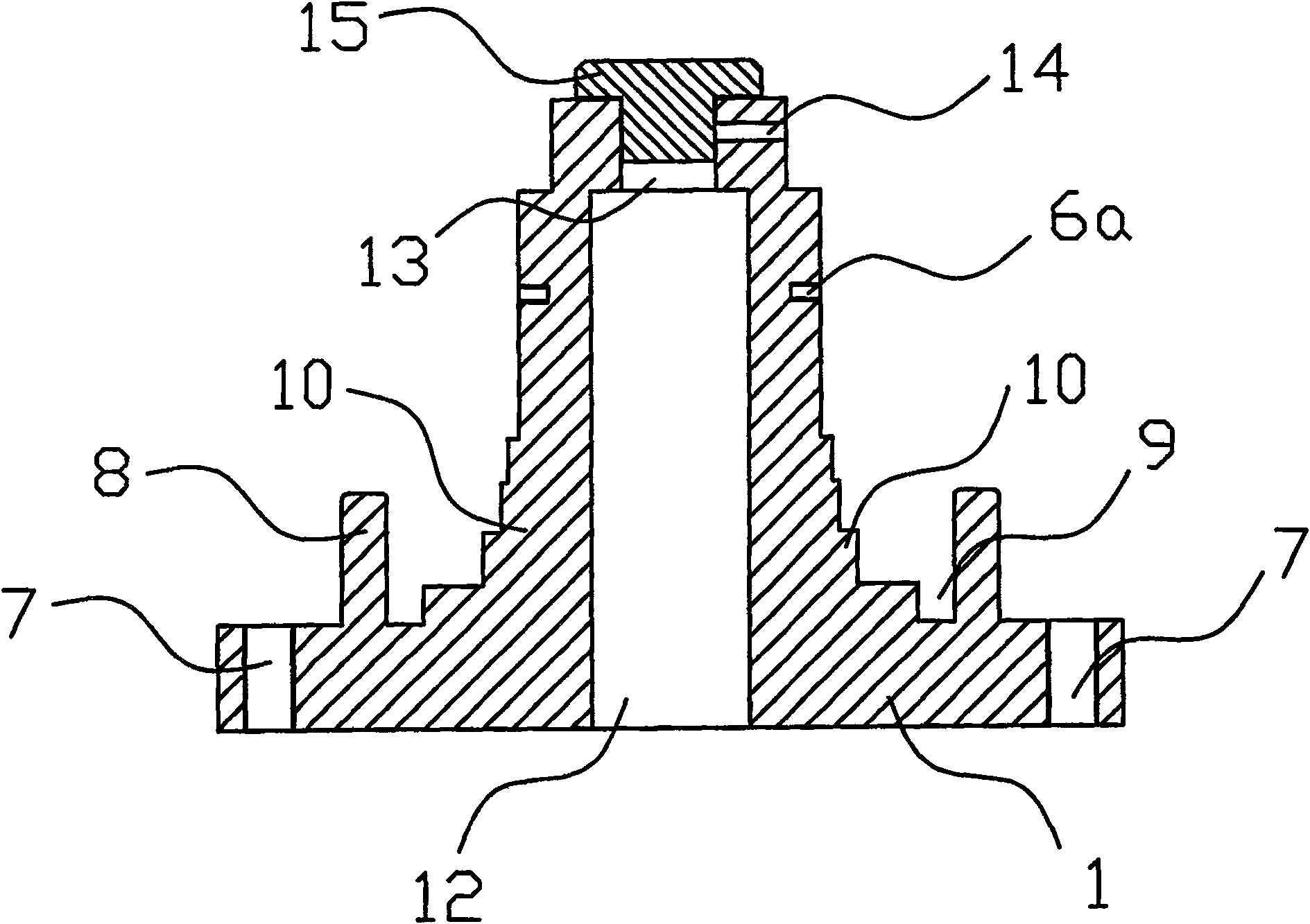
The present invention provides one kind of sealed oil gas well joint, which includes one joint body, one coded lock core set on the joint body, one protecting sleeve in the lower part of the coded lock core, and one anti-theft protecting cover set inside the ring slot between the protecting sleeve and the coded lock core. The sealed oil gas well joint has one coded lock structure, capacity of preventing gas theft and intended damage, high operation efficiency and other advantages.
Owner:许现西
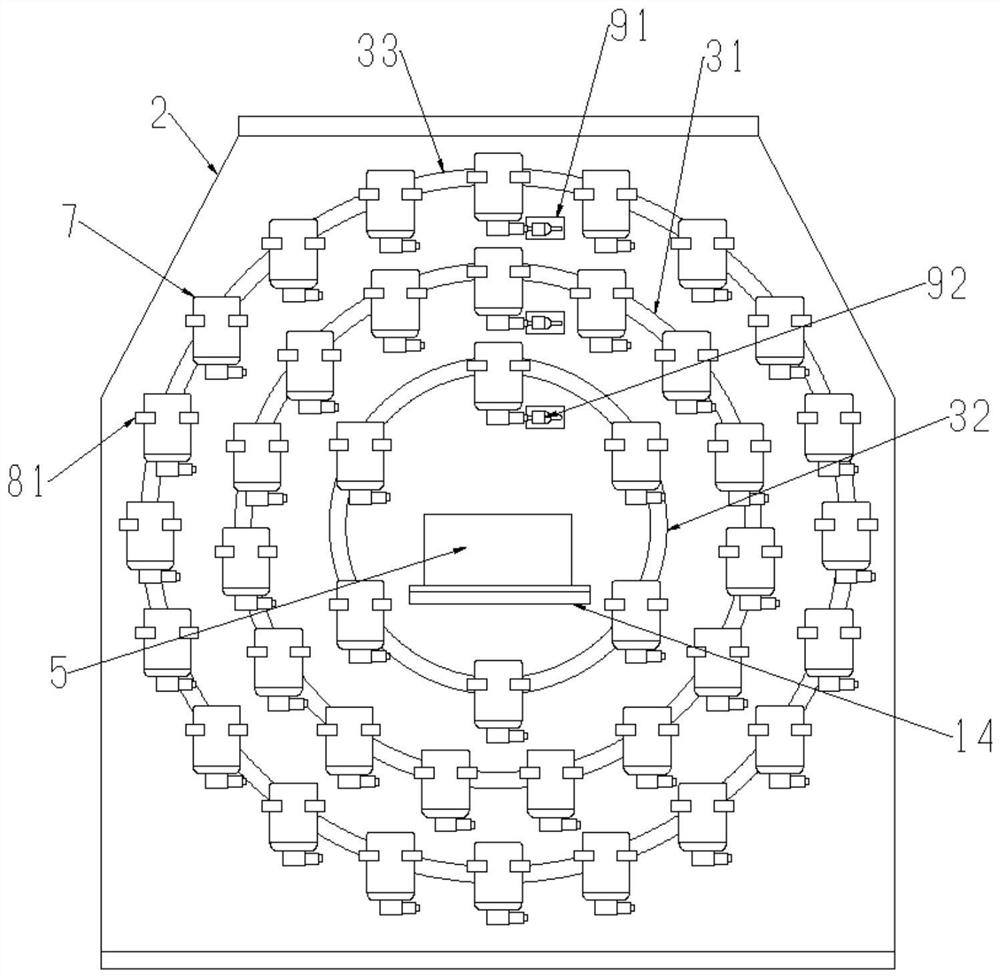
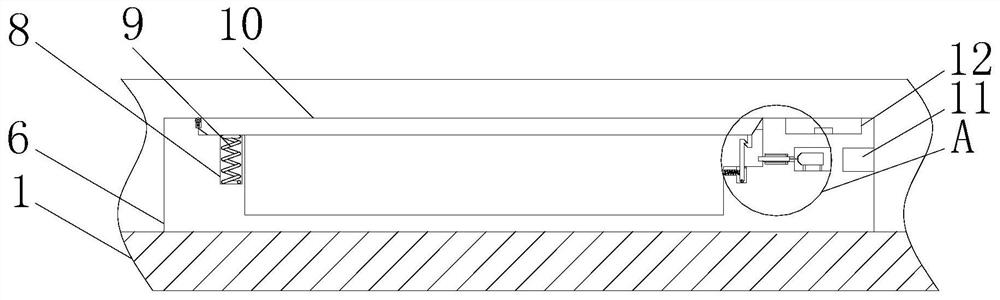
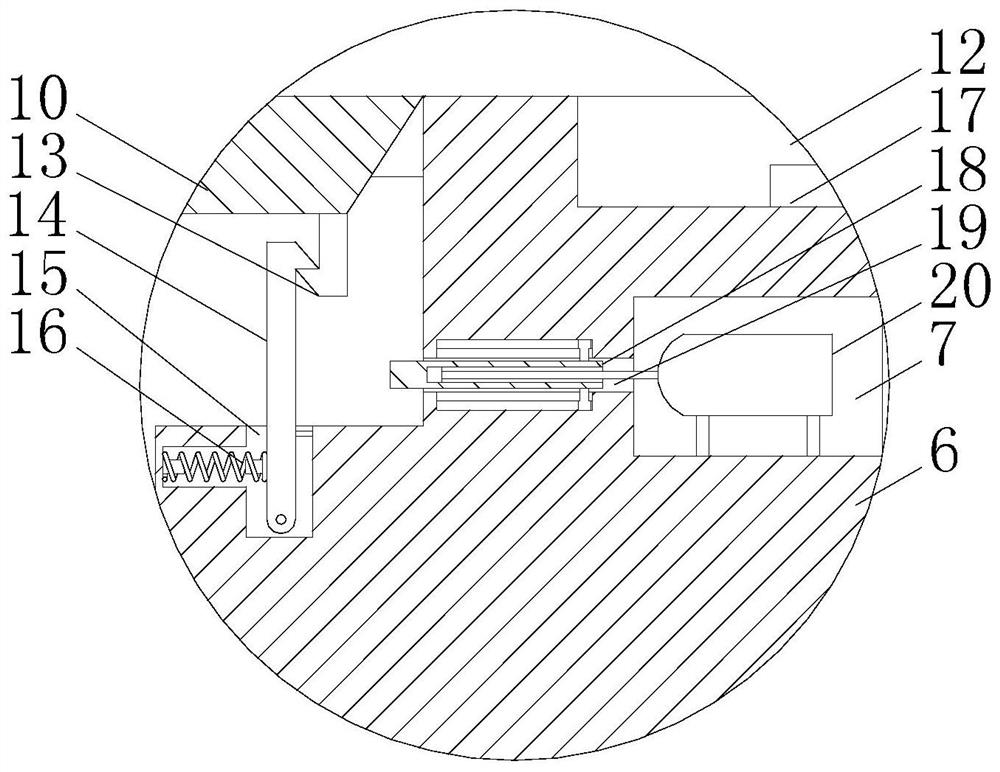
Intelligent paint storage rack based on Internet of Things
ActiveCN114394337ASolve the theftAccurate calculationTelevision system detailsDispensing apparatusThe InternetGas supply
The invention relates to the technical field of paint storage racks, and discloses an intelligent paint storage rack based on the Internet of Things, which comprises a cabinet body, a storage cavity is formed in the cabinet body, a door is arranged on the cabinet body, a paint taking position is arranged on the cabinet body, and an annular conveying rail arranged around the paint taking position is arranged in the storage cavity; a plurality of mounting parts are rotatably mounted on the annular conveying rail, the paint bucket assembly is mounted on the mounting parts, the paint bucket assembly comprises a bucket body and a bucket cover, the bucket cover is detachably mounted on the bucket body in a sealed mode, a valve, a pressure detection sensor and an inflation nozzle are arranged on the bucket cover, and the inflation nozzle is used for being connected with an air supply mechanism; through the arrangement of the pressure detection sensor and the air supply mechanism, the pressure in the barrel is the same under the condition of different paint amounts, the constant discharge amount of the paint per unit time is achieved, the paint amount can be accurately controlled by controlling the opening time of the valve, and the problem that the paint is stolen is solved.
Owner:杭州以诺行汽车科技股份有限公司
Anti-theft luggage
InactiveCN111700356AEasy to moveImplement dragLuggageOther accessoriesEngineeringStructural engineering
Owner:南京市浦口区浦城资产经营有限公司
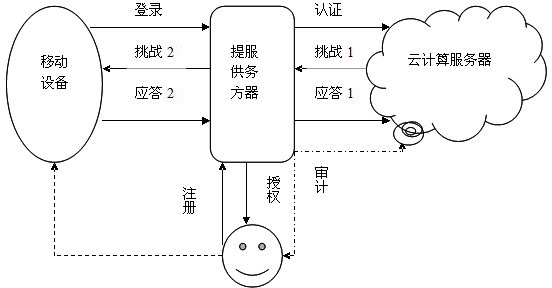
Identity authentication method based on biological feature encryption and homomorphic algorithm
InactiveCN102664885BImprove privacyAvoid crackingUser identity/authority verificationAlgorithmCiphertext
An identity authentication method based on biometric encryption and homomorphic algorithm, which uses the user's biometrics as a password to log in to the system through a mobile device, which is faster than the usual password method, and the use of encrypted biometric templates is more secure, while information is transmitted The process is transmitted in the form of ciphertext, which ensures the privacy of the user; factors such as time stamps are added to enable three-party authentication between the user and the provider server and cloud computing server, which enhances the credibility of the three parties; The user performs the authorization operation based on the predicate encryption of the attribute and updates the permission information in real time, which can prevent legitimate users from illegally using resources in the cloud computing environment and better manage resources. The homomorphic algorithm can be used to operate without decryption, just as the effect of decryption first and then operation is the same, which saves time and space overhead, greatly improves the efficiency of the system, and has high security and efficiency.
Owner:南京邦普信息科技有限公司
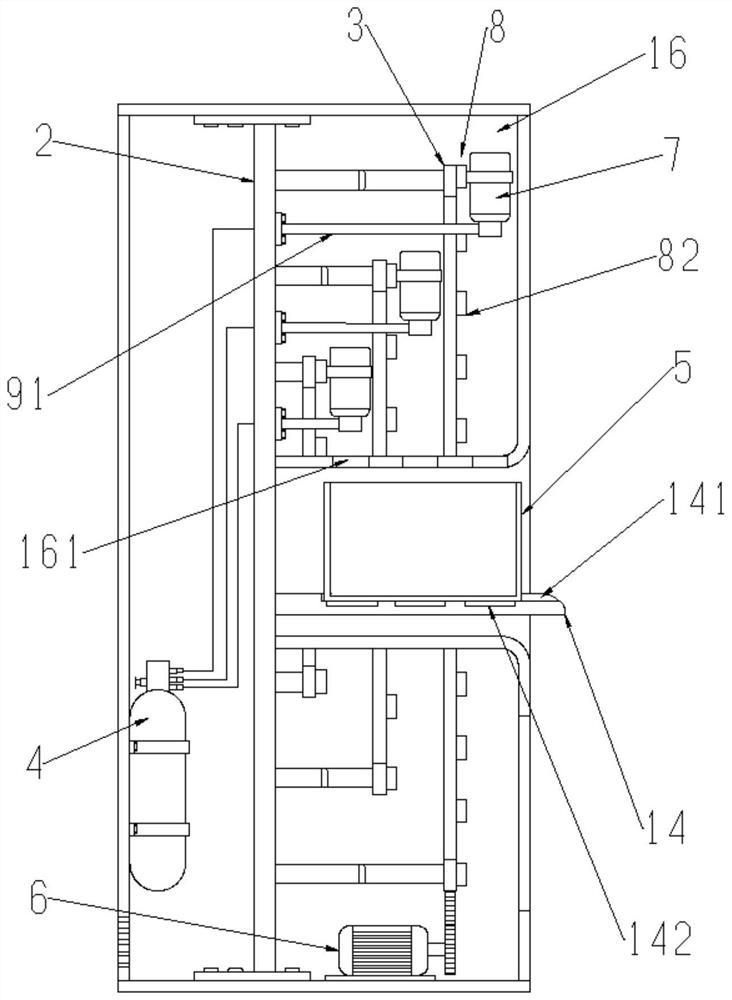
An anti-theft and alarm computer network equipment box
ActiveCN108541160BSolve the theftImprove securityBurglar alarm with fastening tamperingBurglar alarm by openingStructural engineeringMechanical engineering
The invention discloses an anti-theft and alarm computer network equipment box, which includes a box body, an isolation plate is fixedly connected to the upper right corner of the inner cavity of the box, and the front and rear sides of the inner wall of the box are located below the isolation plate. The hinge is hinged with a first box door, the inside of the first box door is fixedly connected with a lock body, the inside of the lock body is rotatably connected with a lock cylinder, and the left side of the inner surface of the lock body is fixedly connected with a first conductive sheet, and is located at A sliding plate is slidably connected to the inside of the lock body and between the first conductive sheet and the lock cylinder, and the second conductive sheet is fixedly connected to the left side of the sliding plate, which relates to the technical field of anti-theft equipment boxes. In the anti-theft and alarm computer network equipment box, the lock cylinder of the device is shorter than that of an ordinary lock, so when a general lock picking tool is inserted into the lock cylinder, it will pass through the lock cylinder and push the slide plate to slide to the left, thereby making the The second conductive sheet is in contact with the first conductive sheet to make the alarm alarm, which solves the problem of stealing internal components due to picking the lock.
Owner:台州市奥金电器股份有限公司
Threading type thief-proof closed device capable of generating identification mark during stealing
ActiveCN102194372BImprove the protective effectTo achieve the perfect effectStampsIdentification meansClosed loopEngineering
The invention discloses a device which can prevent an unauthorized person from changing a protected object for stealing without leaving traces by counterfeiting or changing a connecting part, and is applied in a device with the need of being closed by a special department. The device is characterized in that a closed loop of a metal connecting rope only extends out of a hole opened on the side wall of a housing of a base, and an end socket of the metal connecting rope and / or the curved connecting part of the metal connecting rope is retained in the housing of the base, so that the end socket of the metal connecting rope and / or the curved connecting part of the metal connecting rope can not move and be used for identifying a stealing mark for stealing from the metal connecting rope; and a closed seat enters from an opening of the housing of the base and is clamped in the position of a clamping ring on the side wall in the housing of the base by a buckle of the closed seat for limiting the separation of the closed seat, the closed seat can not rotate freely in the housing or move up and down freely in the housing, and the closed seat can be used for identifying the stealing mark forstealing from the closed seat. By adopting the device, the role of preventing criminals from damaging the closed seat for stealing from the hole opened at the bottom of the housing of the base is realized.
Owner:余炳顺
And mobile terminal and server side are used for safety verification
InactiveCN111447612AImprove securitySolve the theftUser identity/authority verificationExecution for user interfacesUser verificationSoftware engineering
The invention discloses a mobile terminal for safety verification and a server side. The safety verification method comprises the steps that the server side generates verification code information; the server generates virtual SIM card verification information according to the verification code information; the mobile terminal receives the virtual SIM card verification information; the mobile terminal analyzes and verifies the virtual SIM card verification information, virtual SIM card return information is generated through analysis, and the virtual SIM card return information generated through analysis comprises application recognition information for receiving the verification information; and the mobile terminal acquires state information of the corresponding application program basedon the application recognition information for receiving the verification information contained in the virtual SIM card return information, and judges whether to return the virtual SIM card return information and the state information of the application program to the server according to the state information of the application program. According to the safety verification method, the problems ofinformation interception and stealing can be solved, and the safety of user verification information is guaranteed.
Owner:吴彬
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com