A password helmet lock and its installation method
A cipher head and cipher technology, applied in the field of lock structures, can solve problems such as helmet theft, achieve a comprehensive article security method, and solve the effect of possible theft of helmets
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
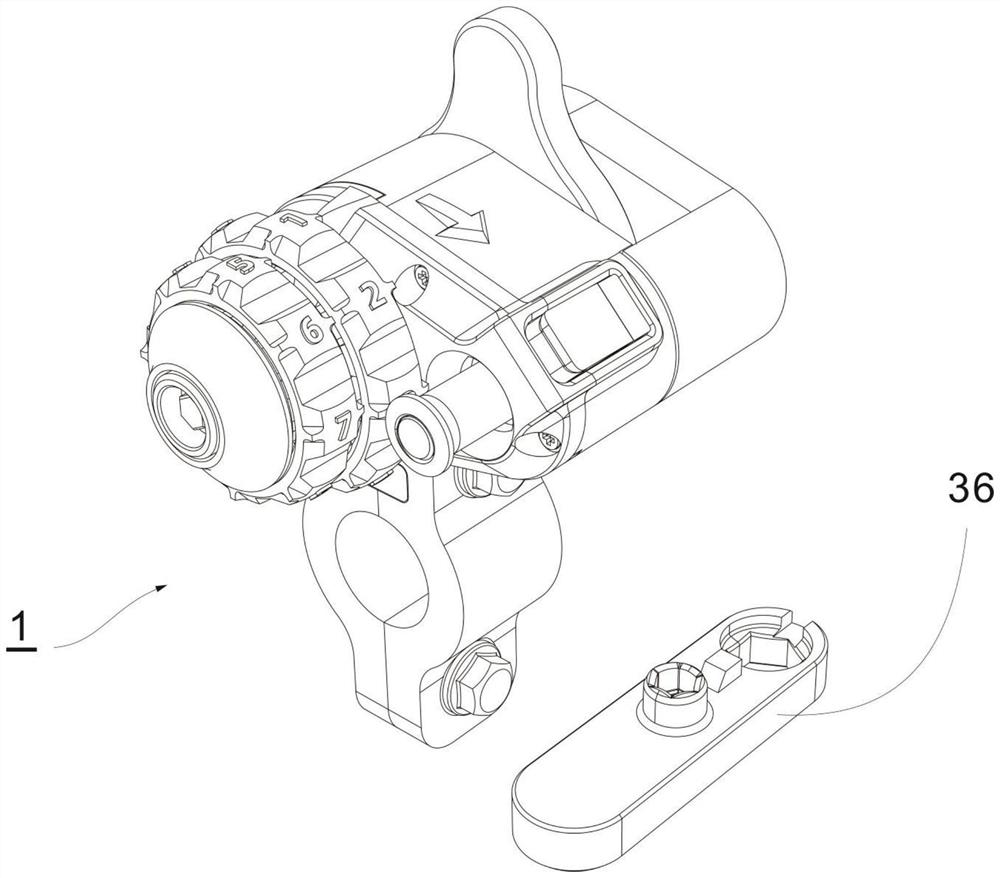
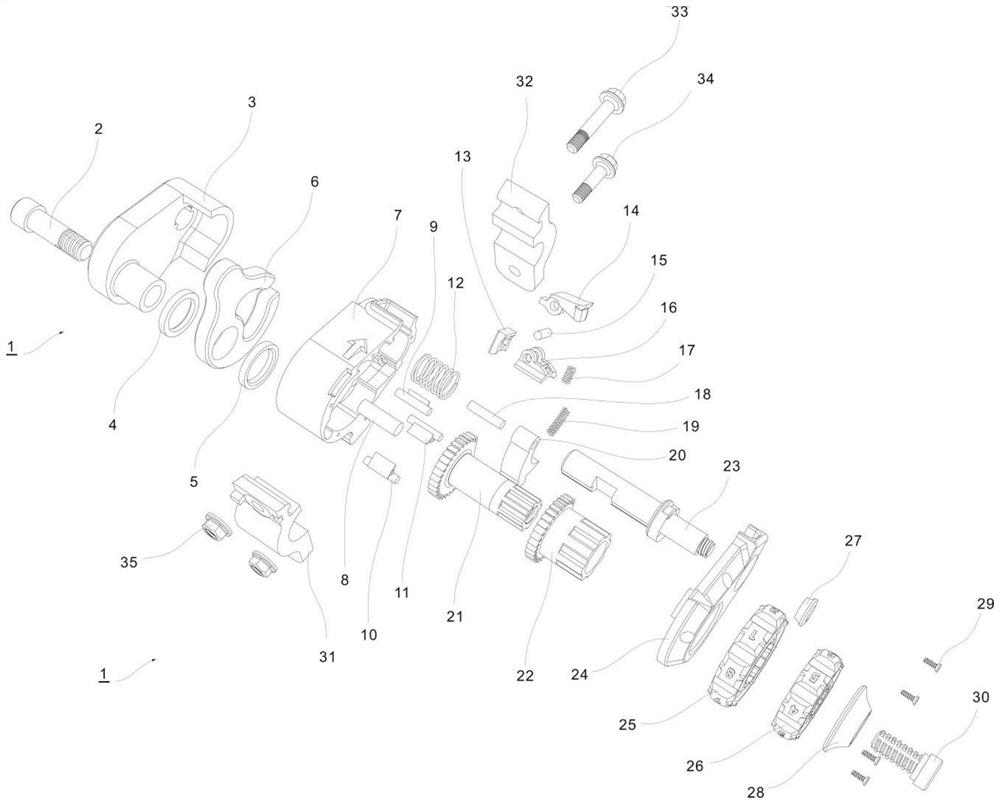
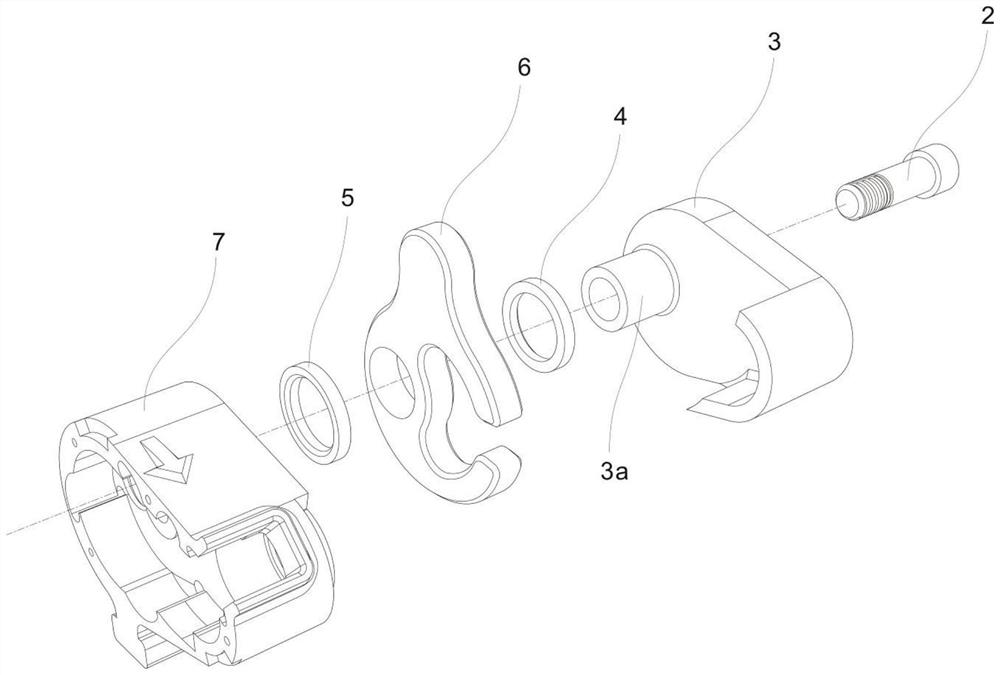
[0051] This embodiment provides a combination helmet lock 1, including a lock 6, a lock machine 7, a release button 14, a half-moon card 20, a small combination gear 21, a large combination gear 22, a lock shaft 23, a lock cover 24, and a large combination wheel 25 , small combination wheel 26, lock shaft cover 27, combination wheel cover 28, handlebar buckle and handlebar buckle bolt. The lock bolt 2 passes through the connection hole of the lock retainer 3, the first lock washer 4, the lock 6, the second lock washer 5 and the lock 7 in turn and fixes it, and uses a special installation wrench 36 to tighten the lock bolt 2 Tighten. The key base 16 is connected with the release key 14 by the key shaft 15, and the key spring 17 is arranged between the key base 16 and the release key 14, and the key base 16 and the release key 14 side cooperate to connect the locking teeth 13, and the locking teeth 13, the releasing key 14. The key shaft 15, the key base 16 and the key spring 1...
Embodiment 2
[0058] The installation method of the password helmet lock comprises the following steps:
[0059] S1. Connect the lock retainer 3, the first lock washer 4, the lock 6, the second lock washer 5 and the lock 7 in sequence through the lock bolt 2, and use the special installation wrench 36 to tighten the lock bolt 2 .
[0060] S2. Assemble the locking tooth 13, release button 14, button shaft 15, button seat 16 and button spring 17 into a release button assembly, and then put it into the key groove 7a of the lock machine 7, and the two sides of the button seat 16 protrude 16a Closely cooperate with the button groove 7a of the lock machine 7; reassemble the half-moon card shaft 18, the half-moon card spring 19 and the half-moon card 20, and put them into the lock machine 7 after assembling; the password gear shaft 8 is internally connected with the small password gear 21, Small coded gear 21 is externally connected with large coded gear 22. Small coded gear 21 and large coded ge...
Embodiment 3
[0064] The locking step of the password helmet lock: the top view projection position of the lock 6 of the password helmet lock 1 is located in the gap 23a of the lock shaft, and the lock 6 can be opened by rotating upward through the lock shaft 3a of the lock retainer 3 , insert the helmet strap into the arc-shaped gap of the buckle 6, rotate the buckle 6 downward through the buckle shaft 3a of the buckle retainer 3 to close, push the lock shaft cover 27 and the lock shaft 23 inward with your fingers, Make the end face 23b of the lock shaft contact the end face 13a of the locking tooth under the elastic force of the locking shaft spring 12. At this time, the button spring 17 is in a compressed state, and its elastic force is applied to the locking tooth 13 by releasing the button 14, preventing the lock shaft from 23 to move outward; then, turn the large password wheel 25 or the small password wheel 26 clockwise, or rotate both clockwise simultaneously, so that the notch end f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com