Software authorization control method
A control method and software authorization technology, applied in the direction of electrical components, program/content distribution protection, instruments, etc., can solve problems such as misappropriation of company copyrights
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
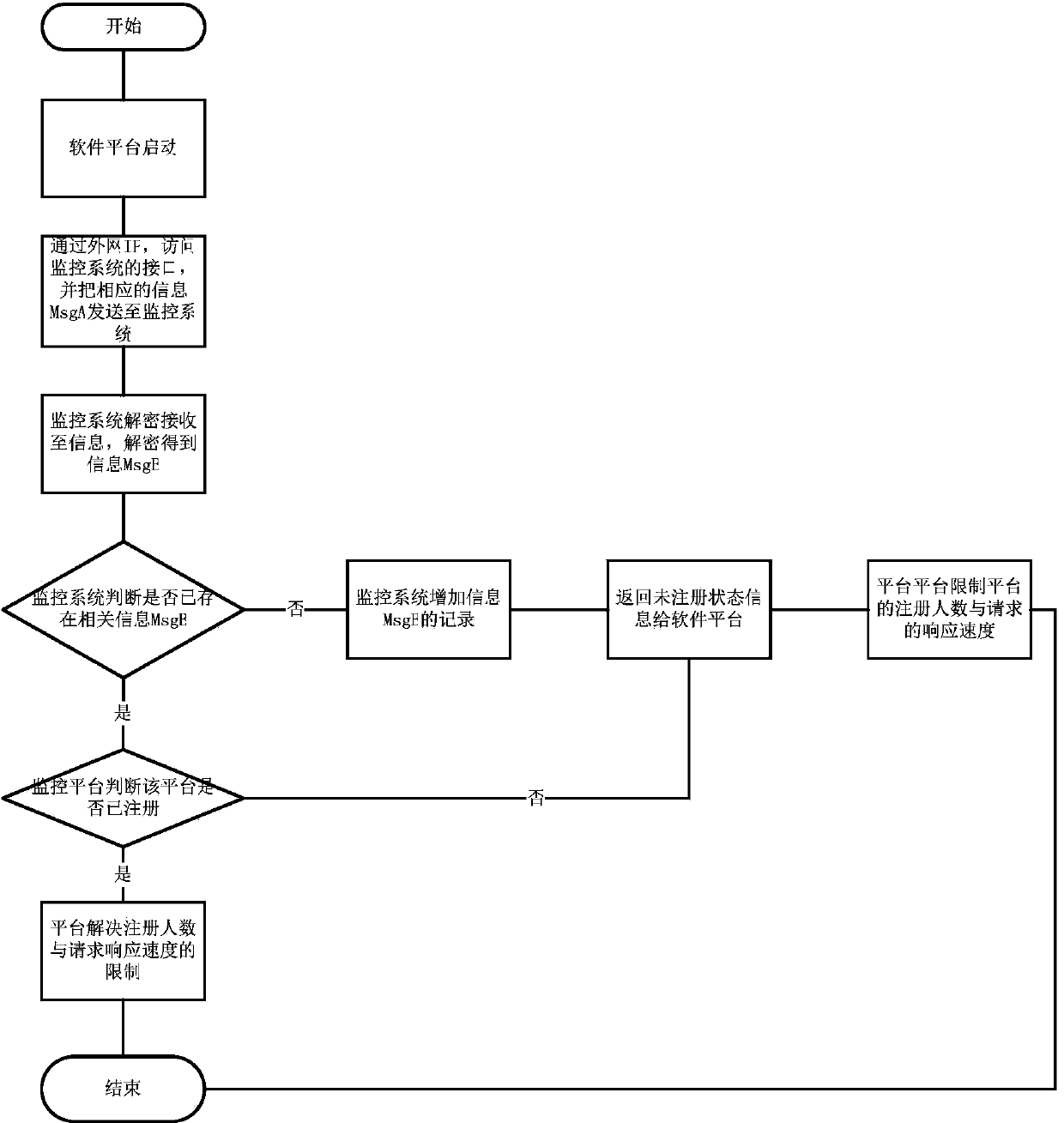
[0020] As shown in the figure, the present invention deploys a monitoring system that can be accessed from the external network; when deploying an application platform, it is necessary to configure the external network access IP for the server of the platform. When the platform is started, it sends the platform server’s MAC address, external network IP address, and internal network IP address to the monitoring platform through the interface; the monitoring platform generates a certain Record made es. The platform can connect with the monitoring system every day through the timer, and send the internal IP, external IP and MAC address of the server to the monitoring platform. The monitoring platform can obtain the es record based on the internal IP and MAC address, and then Access the registration interface of the platform through the external network IP, and send the registration information to the platform. The platform can judge whether the software has been registered by an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com