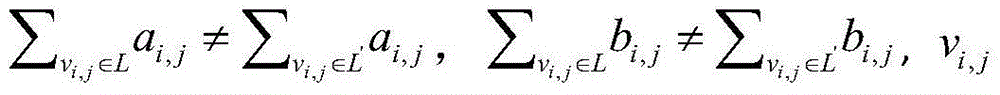Encryption method and system based on attributes
An encryption method and attribute technology, applied in the field of information security, can solve the problem of leaking user privacy and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
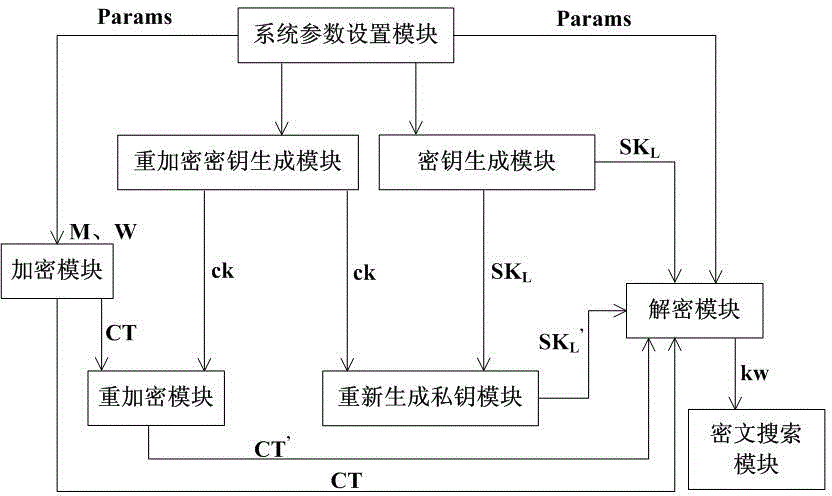
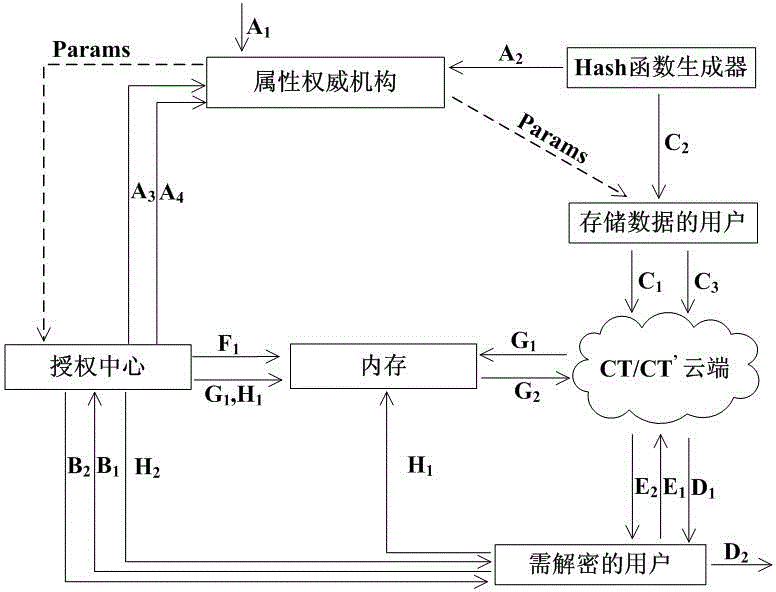
[0080] The technical solution of the present invention will be further described in detail below in conjunction with the accompanying drawings:
[0081] 1. Description of mathematical knowledge used in the present invention:
[0082] 1. Bilinear Pairing
[0083] Here is a brief introduction to the basic definition of bilinear mapping and the properties it needs to satisfy.
[0084] Let G, G T Are two multiplicative cyclic groups of order p, where p is a prime number and g is the generator of G. Define the bilinear mapping on the two groups as: e:G×G→G T , And satisfy the following properties:
[0085] (1) Bilinearity: e(g a ,g b )=e(g,g) ab , For all g∈G,a,b∈Z p Are all established.
[0086] (2) Non-degeneration: e(g,g)≠1.
[0087] (3) Computability: There is an effective algorithm to calculate e(g,g), which is true for all g∈G.
[0088] 2. Access Structure
[0089] Let {P 1 ,P 2 ,...,P n } Is the set of n participants. Assume Represents a set composed of a subset of the participant set...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com