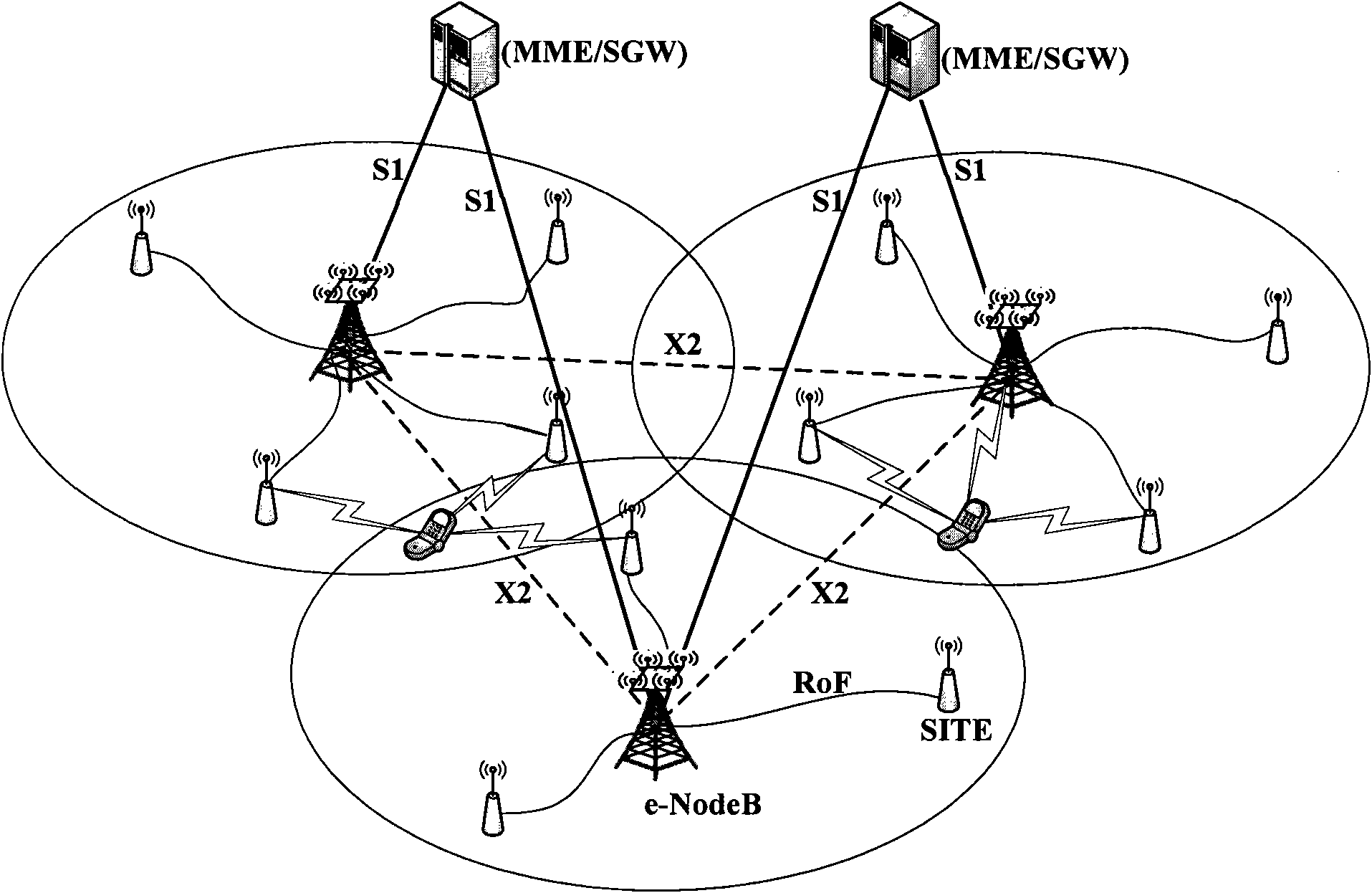
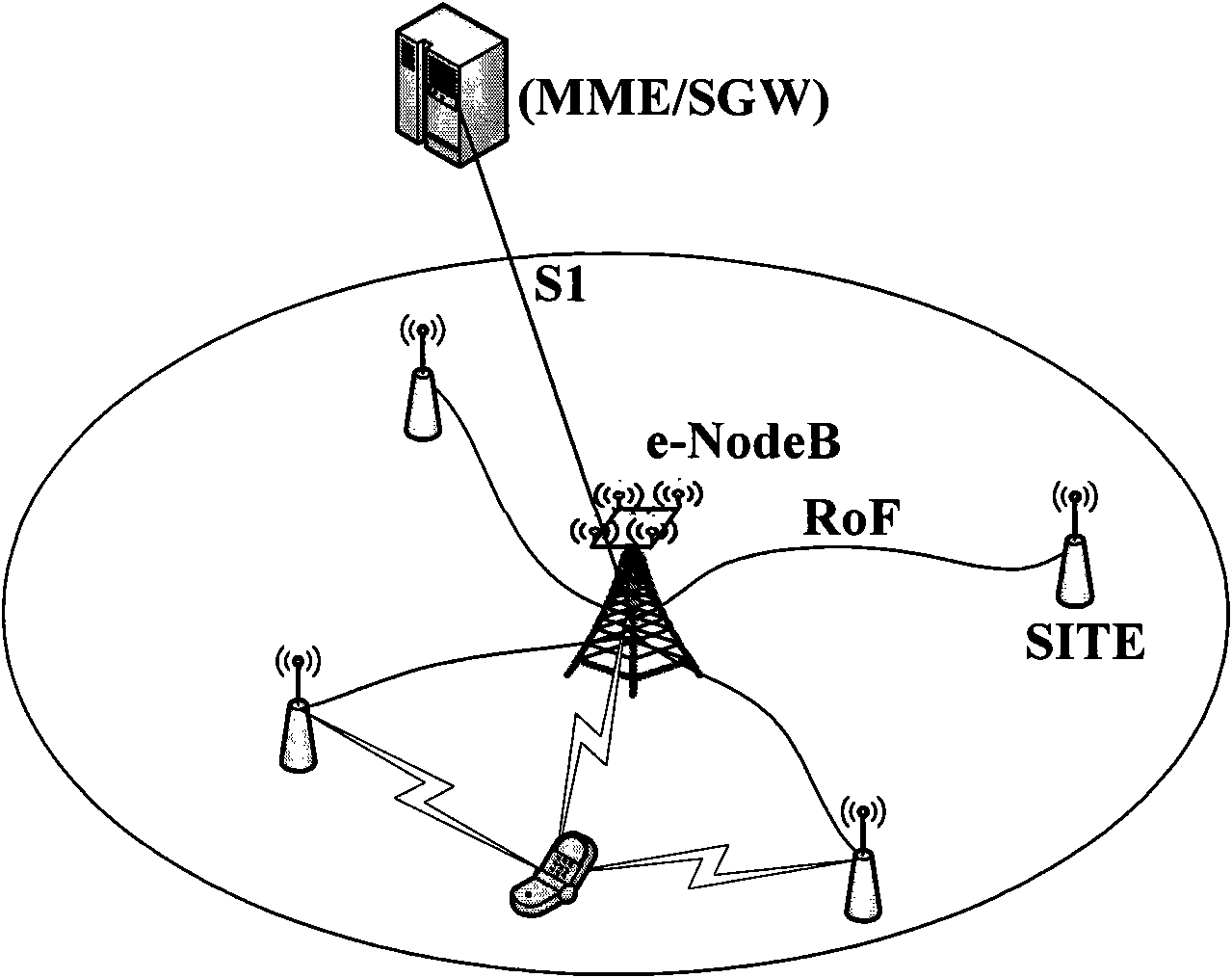
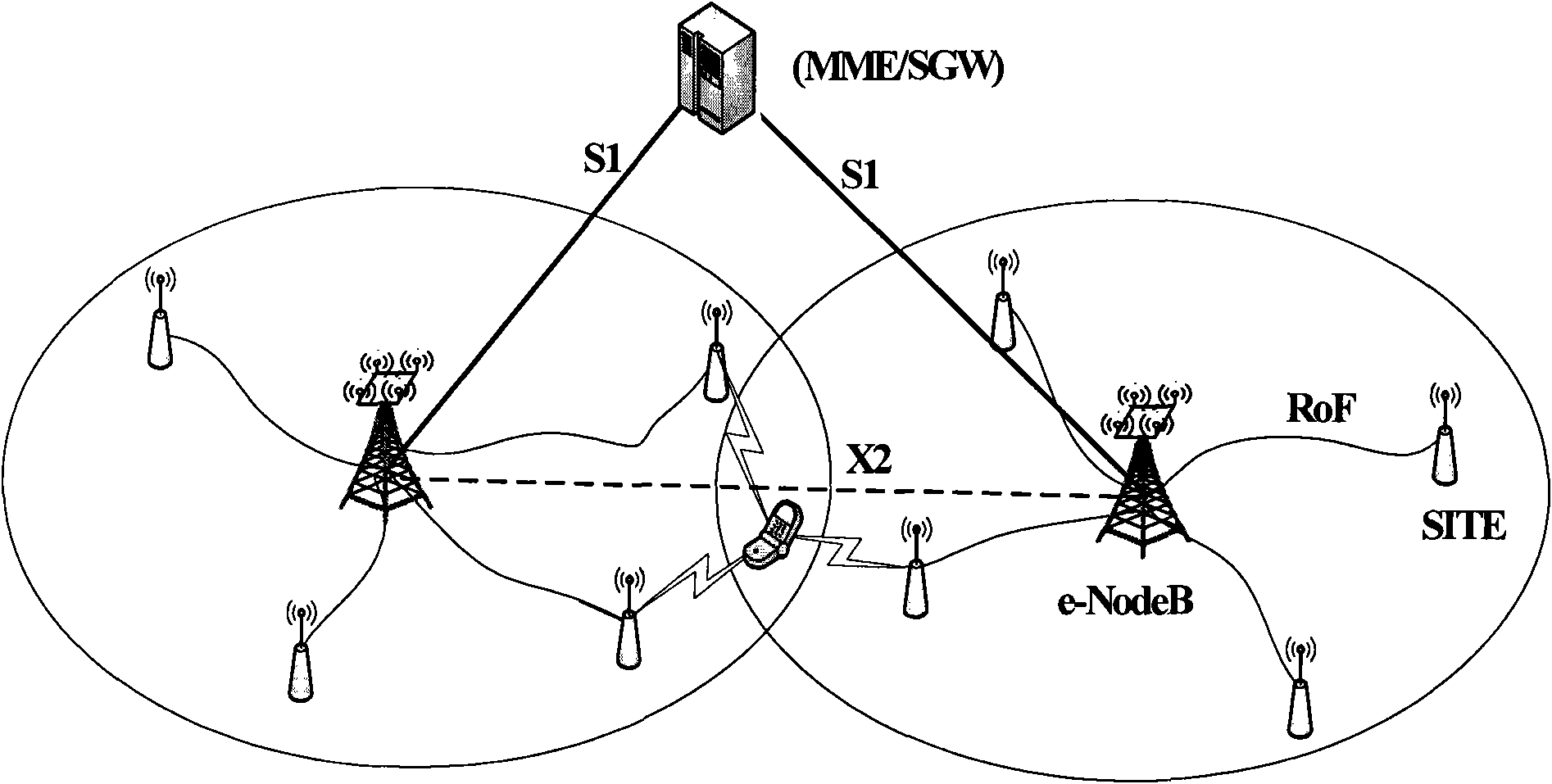
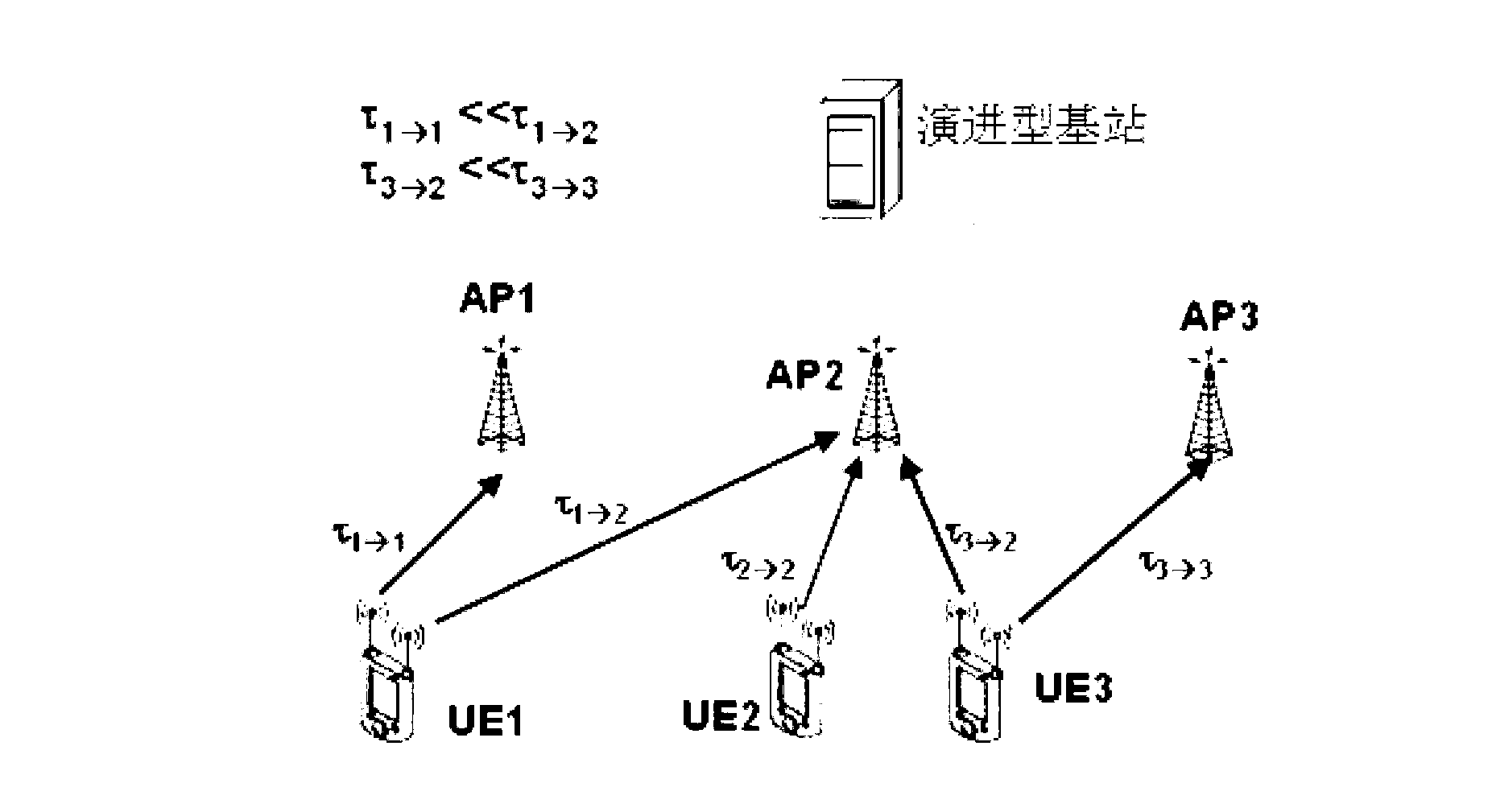
Patents
Literature
89results about How to "Reduce the amount of data interaction" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
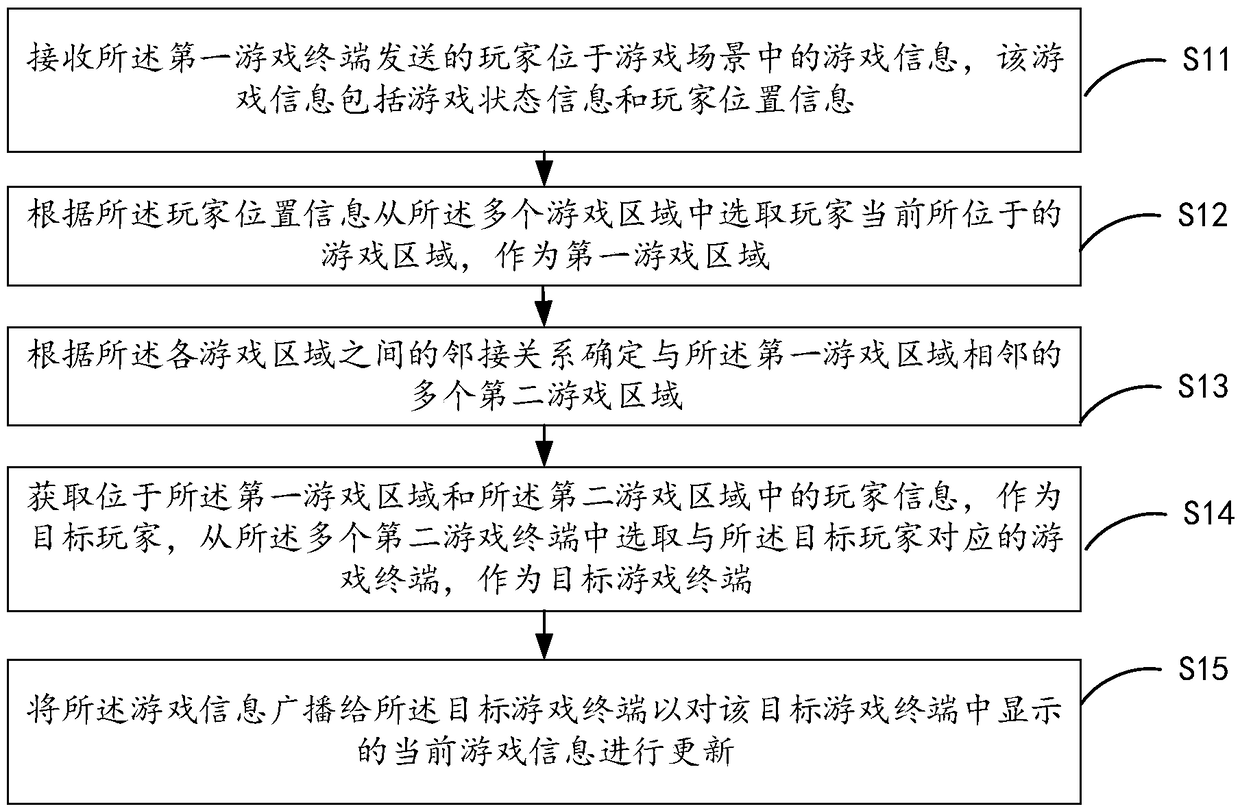
Patent Type
Patent Status
Application Year
Inventor
Distributed cloud storage data integrity protection method
InactiveCN102710757AAchieve positioningSmall amount of local storageTransmissionData integrityLinear coding
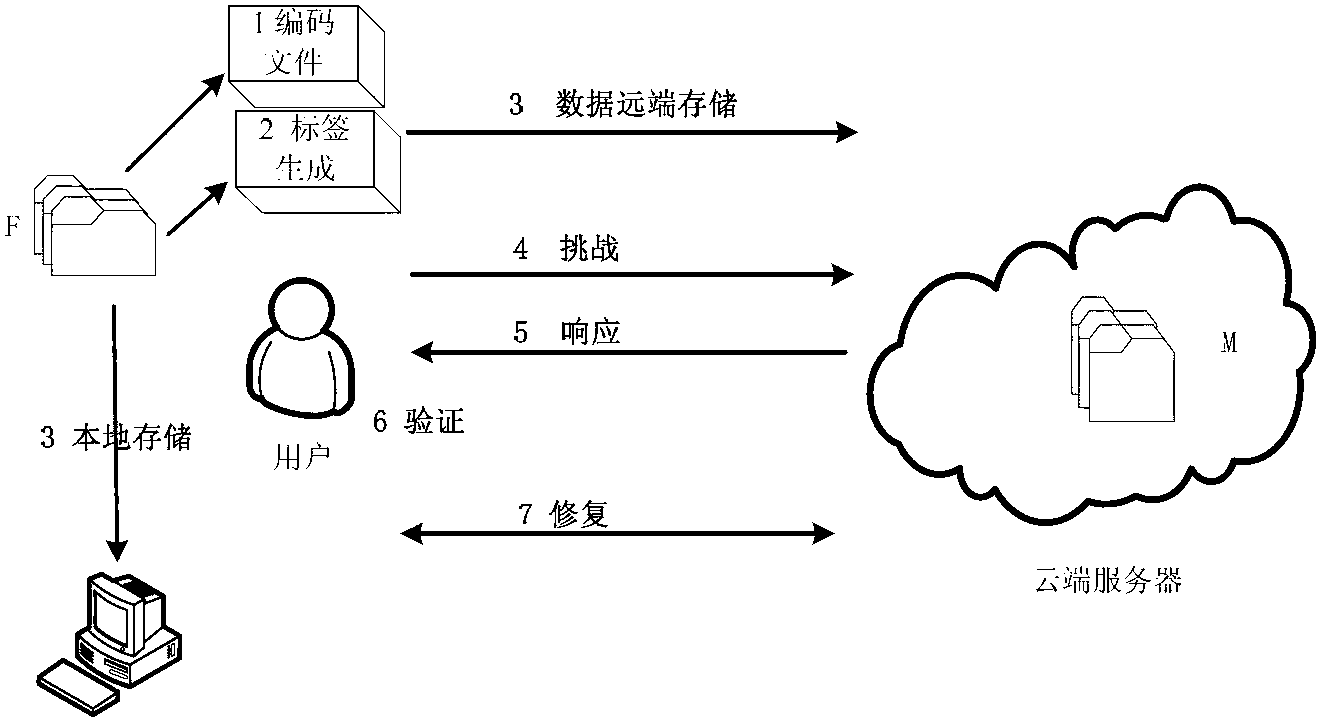
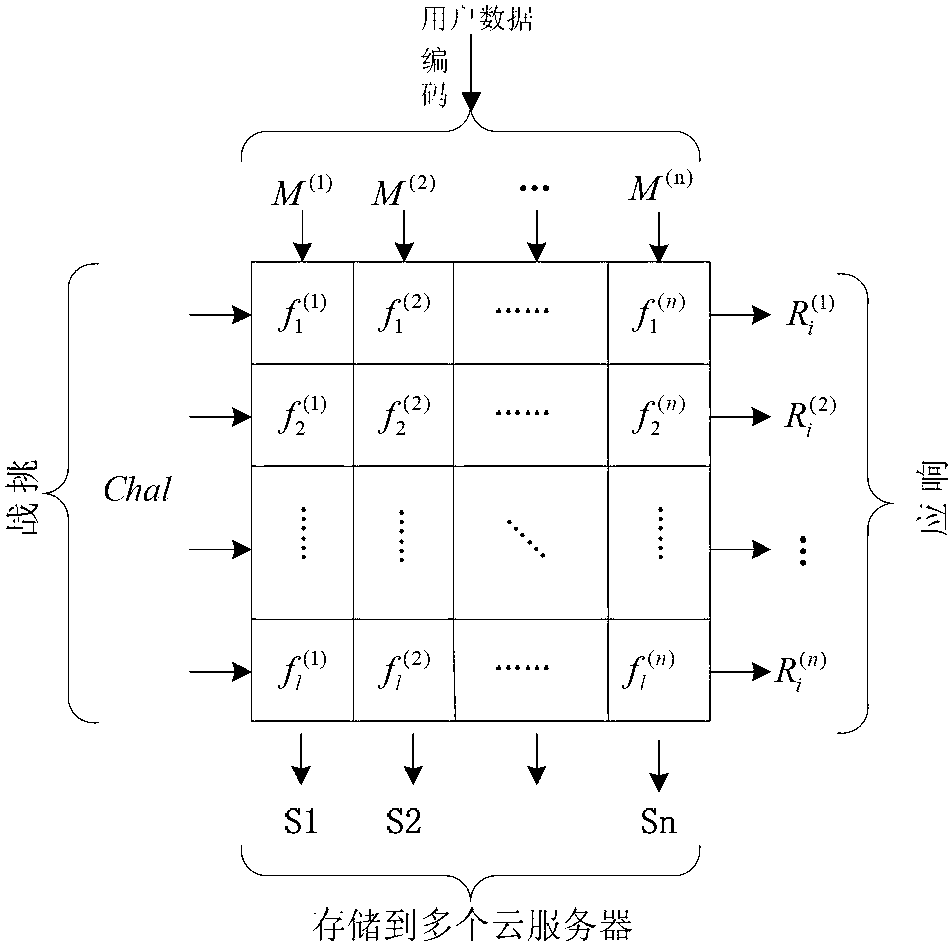
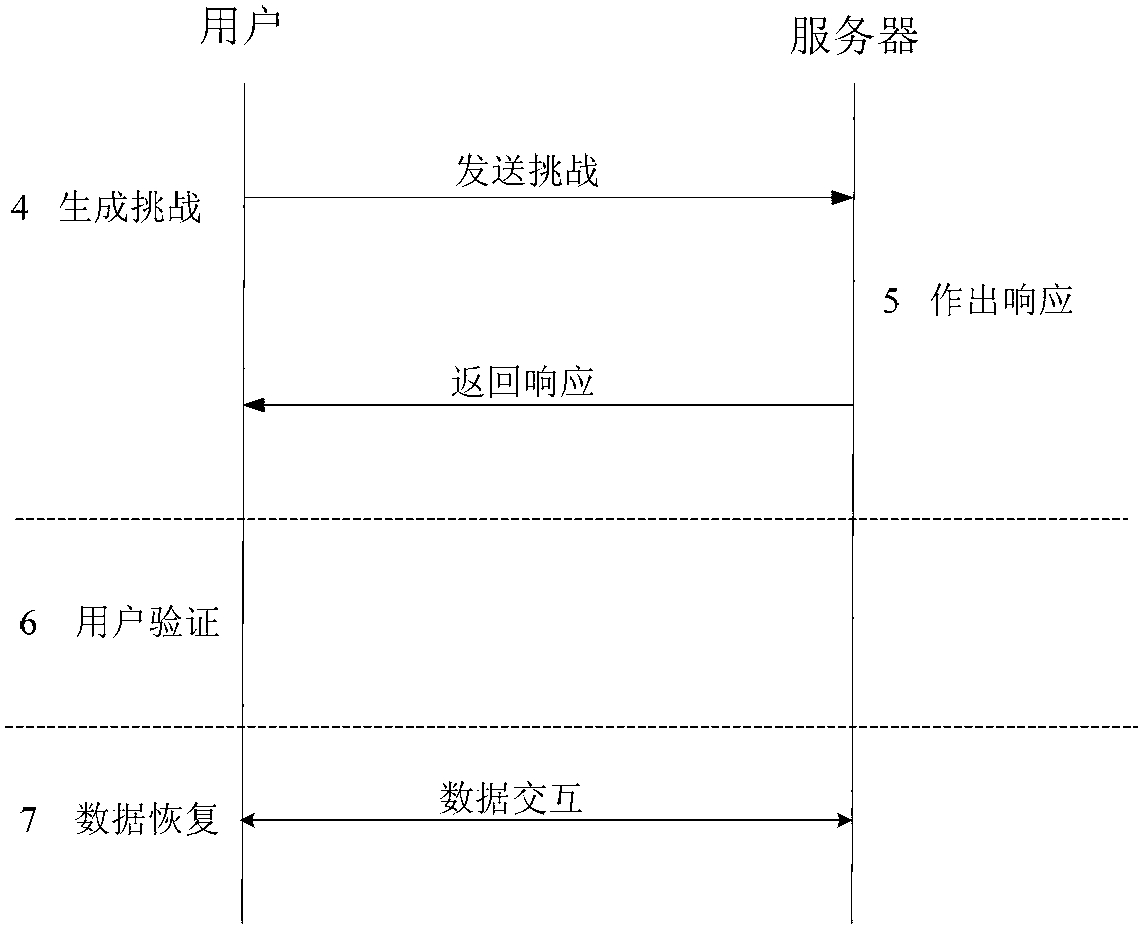
The invention relates to a distributed cloud storage data integrity protection method. The method comprises: (1) data division and coding {F--M}; (2) generation of homomorphic verifiable tags (HVTs) {(sk,F)--HVTs}; (3) remote data storage {(M(j),HVT--Sj)}; (4) a user launching a challenge {chal}; (5) a server making a response {R}; (6) verification{(R,sk)--('success', 'failure')}; and (7) data recovery {(M*,P)--F}. According to the method provided by the invention, the communication cost is reduced by adopting random data block sampling; data error location and error recovery can be realized by using linear coding; and the method has no limits to the number of times for data possession verification, is high in the verification confidence, safe and reliable. Accordingly, the method provided by the invention has good practical value and wide application prospect in the technical field of cloud security.
Owner:BEIHANG UNIV
Credible data access control method applied to cloud storage of mobile devices
ActiveCN103763315AReduce the amount of data interactionConfidenceTransmissionCryptographic key generationKey size
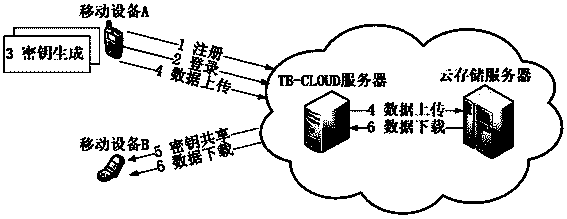
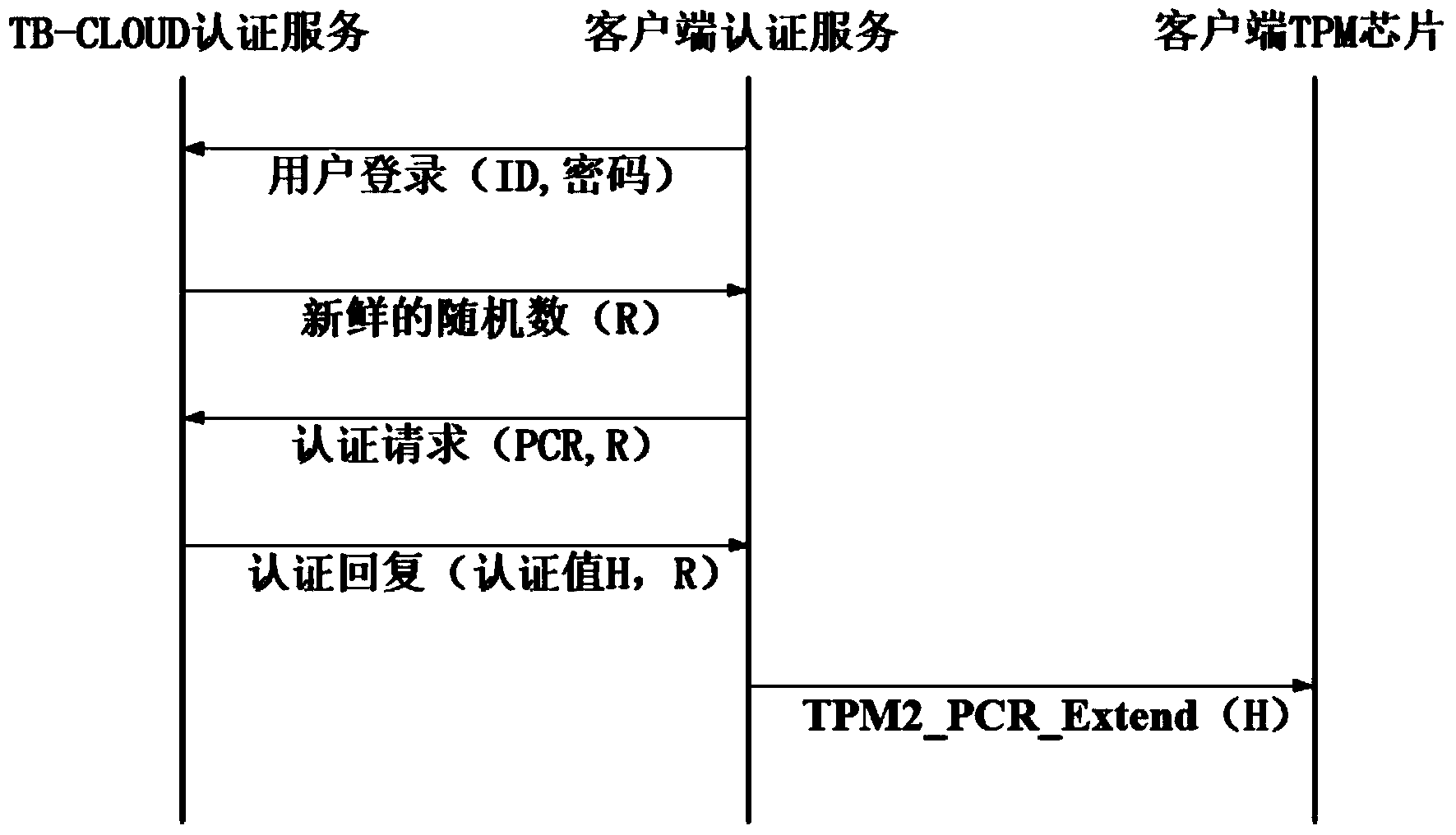
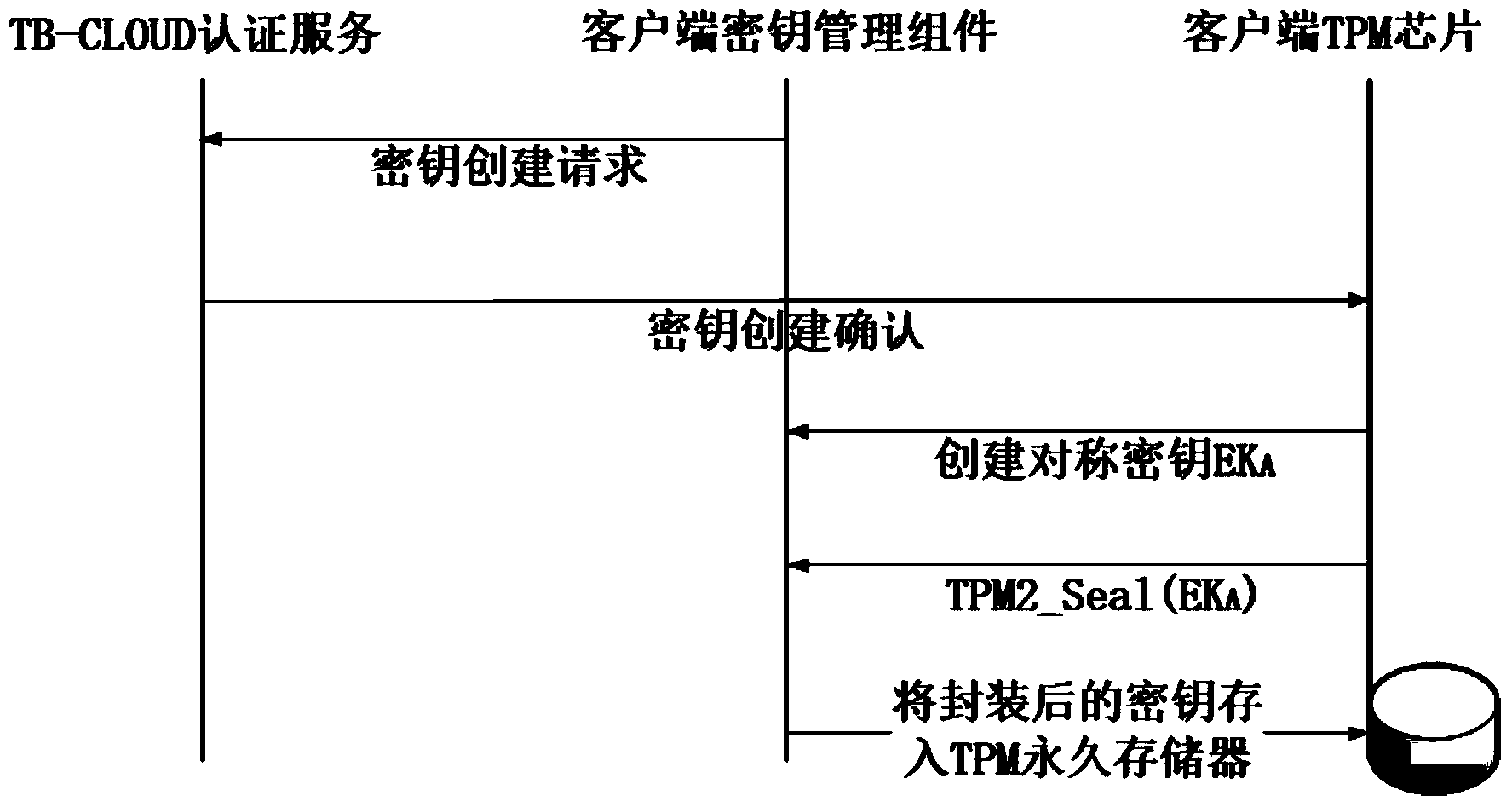
The invention relates to a credible data access control method applied to cloud storage of mobile devices. The credible data access control method includes six steps including user registering, user login, secret key generation, data encryption uploading, data downloading and decryption in three stages. The first step is user registering, the second step is user login with an authentication process, the third step is encryption secret key generation, the fourth step is user data encryption uploading, the fifth step is secret key sharing among the multiple mobile devices, and the sixth step is data downloading and decryption. According to the credible data access control method, transmitting of a credible chain in the secret key exchanging process is guaranteed by a user through a mobile TPM chip, the length of a secret key is reduced through encryption based on a elliptic curve, it is guaranteed that the multiple mobile devices can safely share the secret key, compared with a traditional server terminal or client terminal data encryption method provided by a cloud storage service provider, the credible data access control method is safe, reliable, high in confidence degree and small in interaction data amount, and the good practical value and the wide application prospect are achieved in the technical field of cloud storage safety.
Owner:BEIHANG UNIV
Data integrity verifying method under multi-cloud environment
InactiveCN103605784AIntegrity verification implementationReduce the amount of data interactionComputer security arrangementsTransmissionData labelingCloud service provider
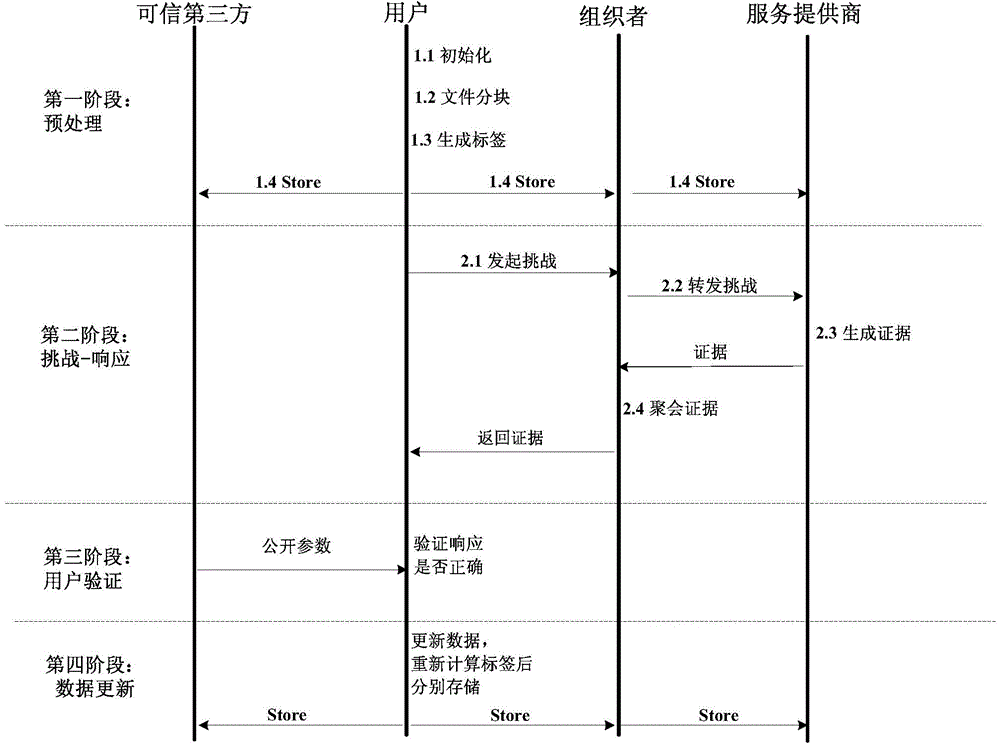
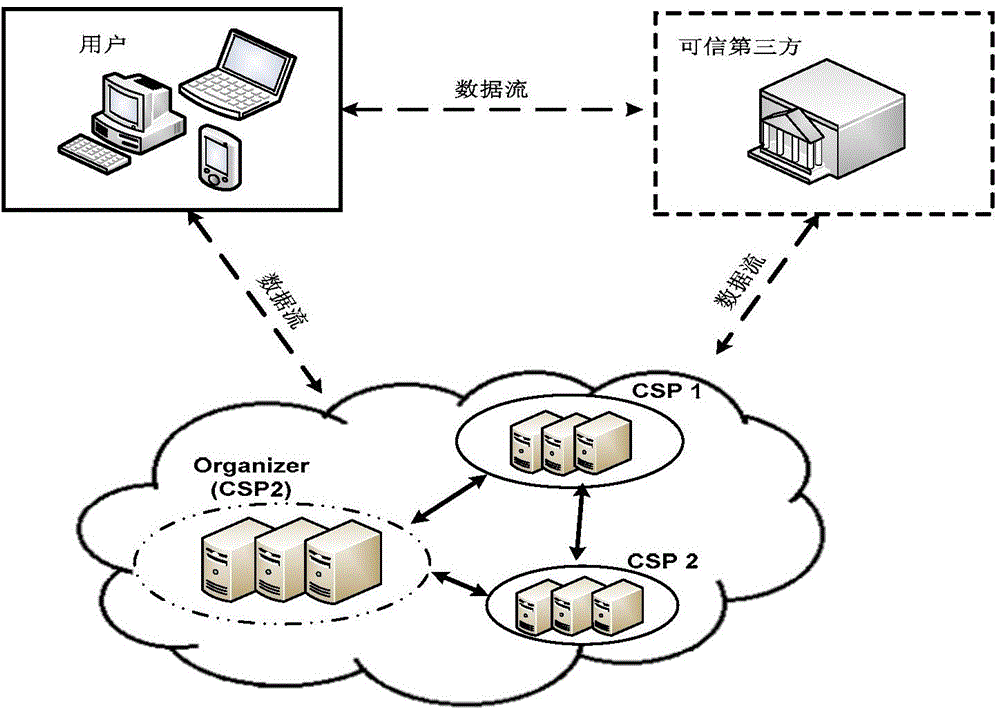
Disclosed is a data integrity verifying method under a multi-cloud environment. The data integrity verifying method comprises the following steps of preprocessing, challenging-responding, user verifying and dynamic upgrading. The first stage (preprocessing) is executed by a client side and comprises the steps of initializing, file partitioning, data label generating and file, label and public parameter storing. The second stage (challenging-responding) is an interaction process between a user and a cloud service provider, the user initiates a challenge to the cloud service provider before data upgrading or after data upgrading, a server makes a corresponding response and the user conducts integrity verifying according to the response made by the server. The third stage (user verifying) is executed by the user, when the user receives data P={P1, P2} returned by an organizer, the user obtains stored public parameters from a reliable third party, the integrity of the data stored in the cloud service provider is verified and if verification successes, accept is output and otherwise reject is output. In the fourth stage (dynamic upgrading), when the user needs to conduct dynamic operation on the data, the user works out new labels and sends the new labels to the organizer and then, the organizer conducts distributed storage.
Owner:BEIHANG UNIV
Method and system for positioning fault of power distribution network
ActiveCN108120900AImprove recognition accuracyReduce the amount of data interactionFault location by conductor typesNetwork modelData combination
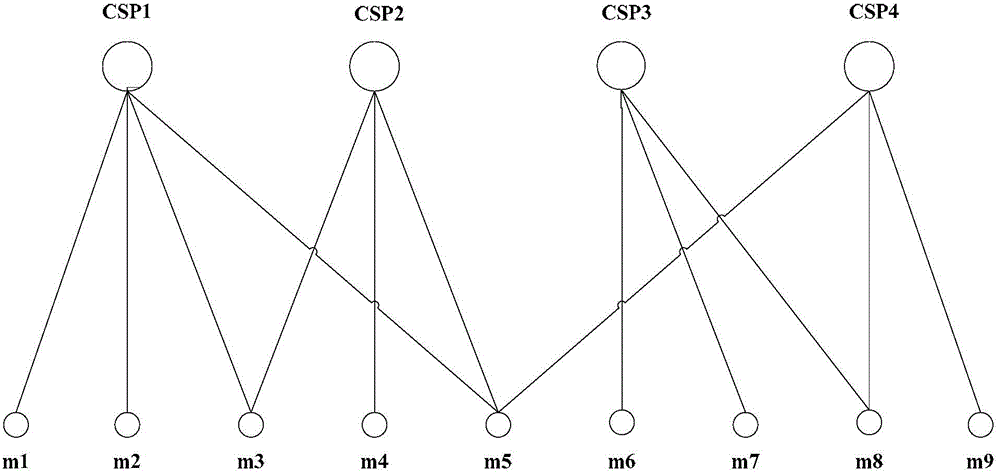
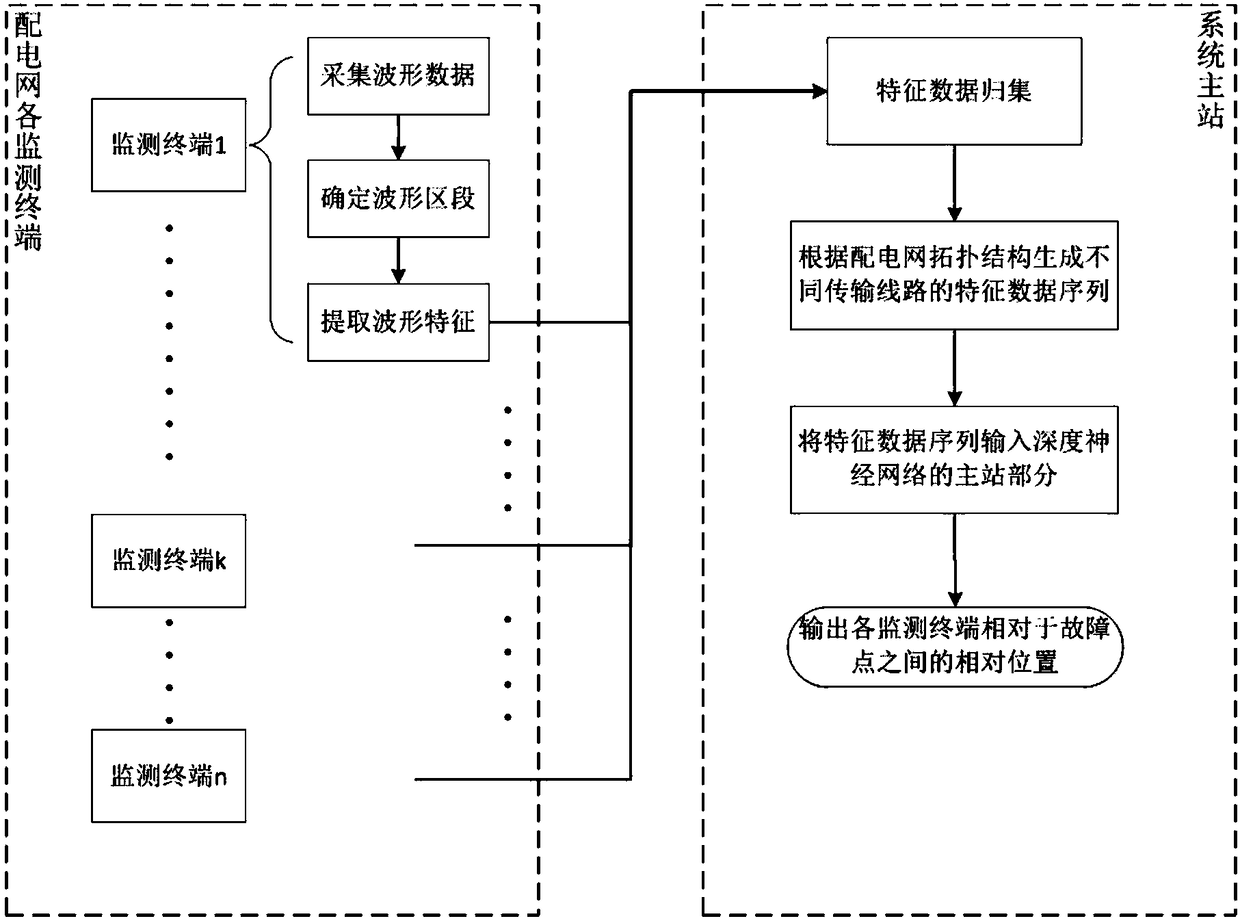
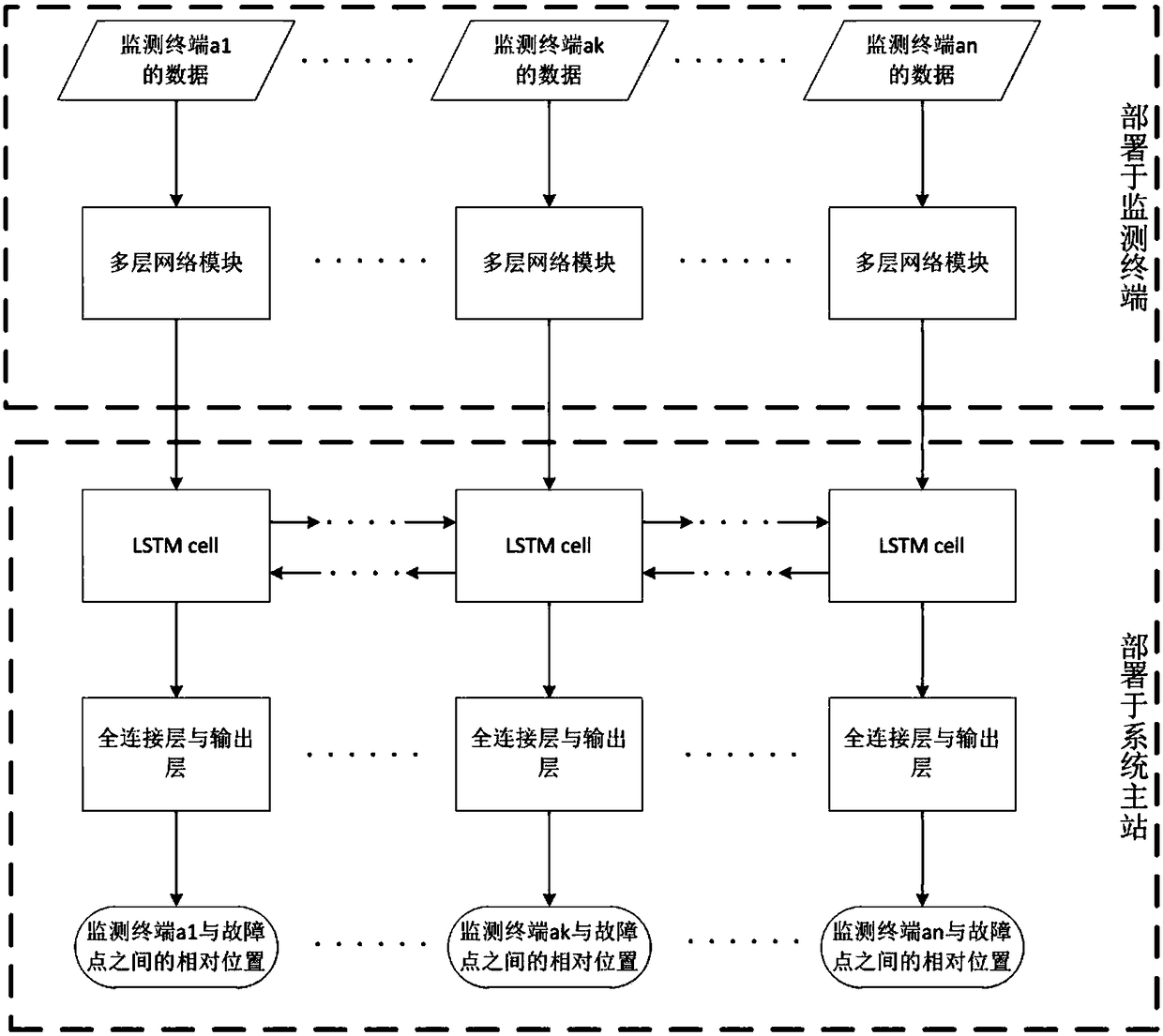
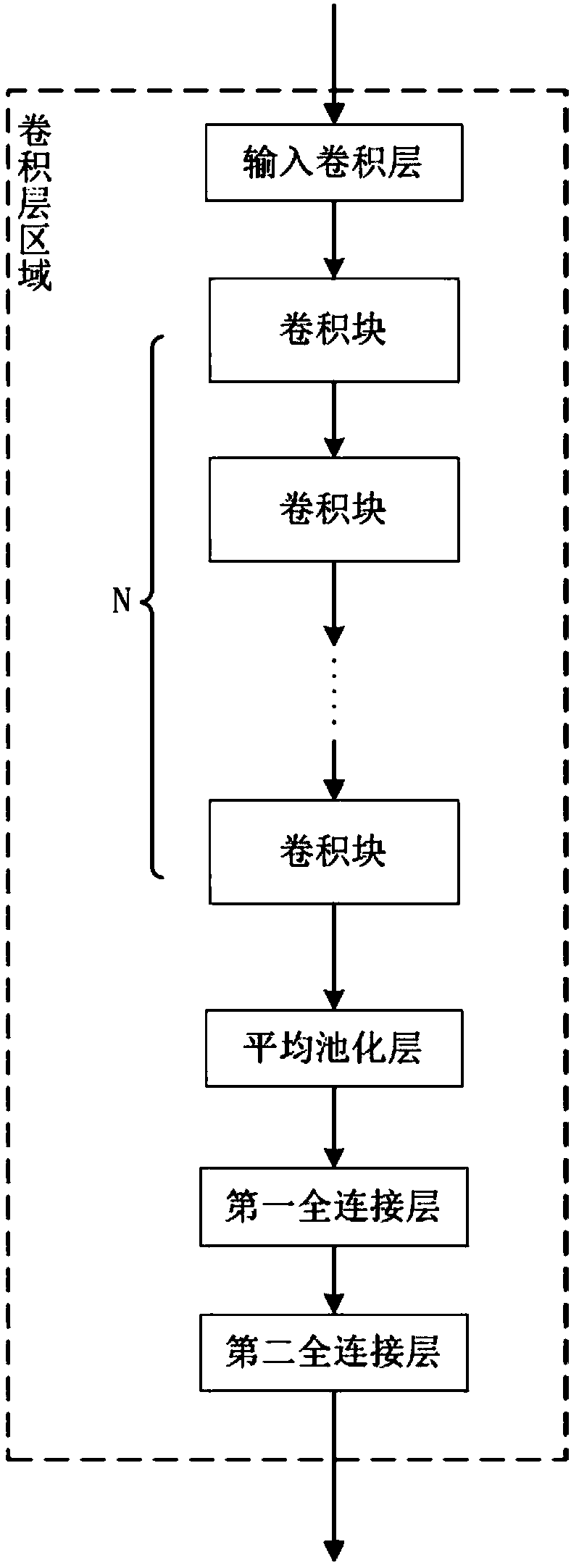
The invention discloses a method for positioning the fault of a power distribution network. The method comprises the following steps: carrying out machine learning training on a deep neural network model frame containing a multilayer network module and a bidirectional long and short time memory network module, and obtaining an optimal deep neural network model; carrying out working condition waverecording on the power distribution network in each monitoring terminal to obtain wave recording data, and intercepting the wave recording data to obtain a fault waveform area; using the multilayer network module in the optimal deep neural network model to carry out feature extraction on the fault waveform area; uploading feature data to a system master station in each monitoring terminal, and carrying out feature data collection on the system master station, and combining the feature data of the monitoring terminals on the same transmission line into a feature data sequence according to a topological structure of the power distribution network; and inputting the feature data sequence into the bidirectional long and short time memory network module so as to obtain relative positions between each monitoring terminal and the fault point.
Owner:BEIJING INHAND NETWORKS TECH
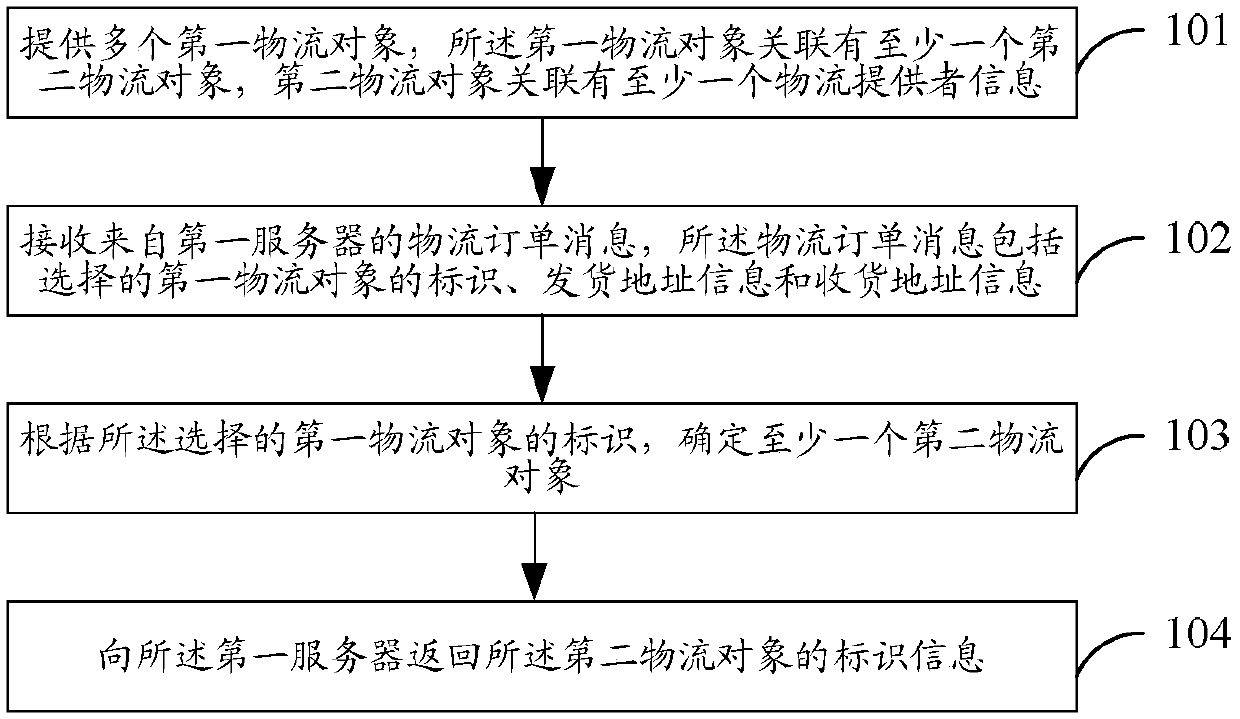
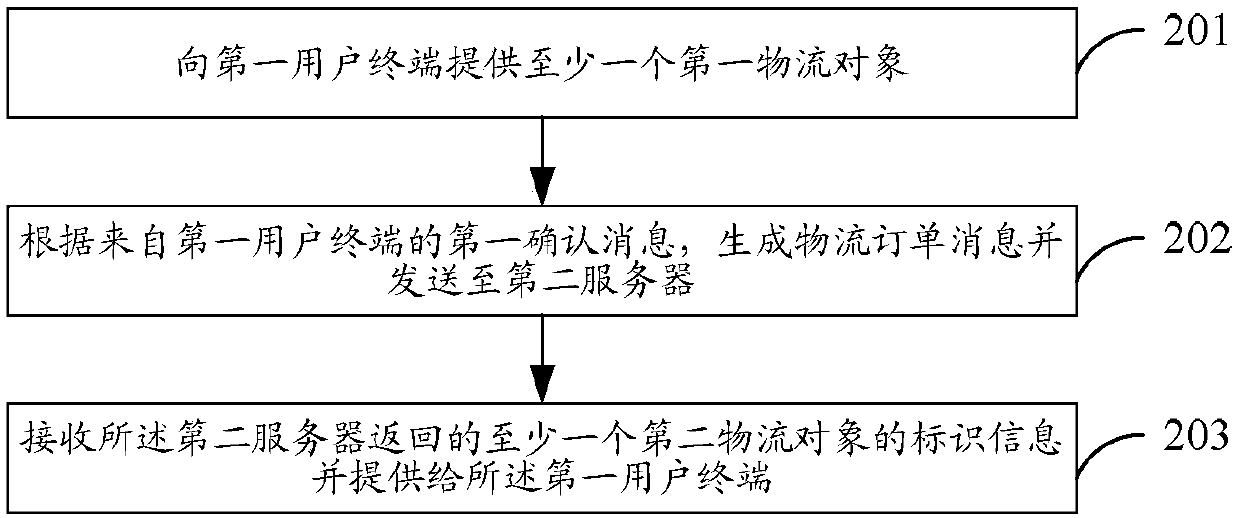
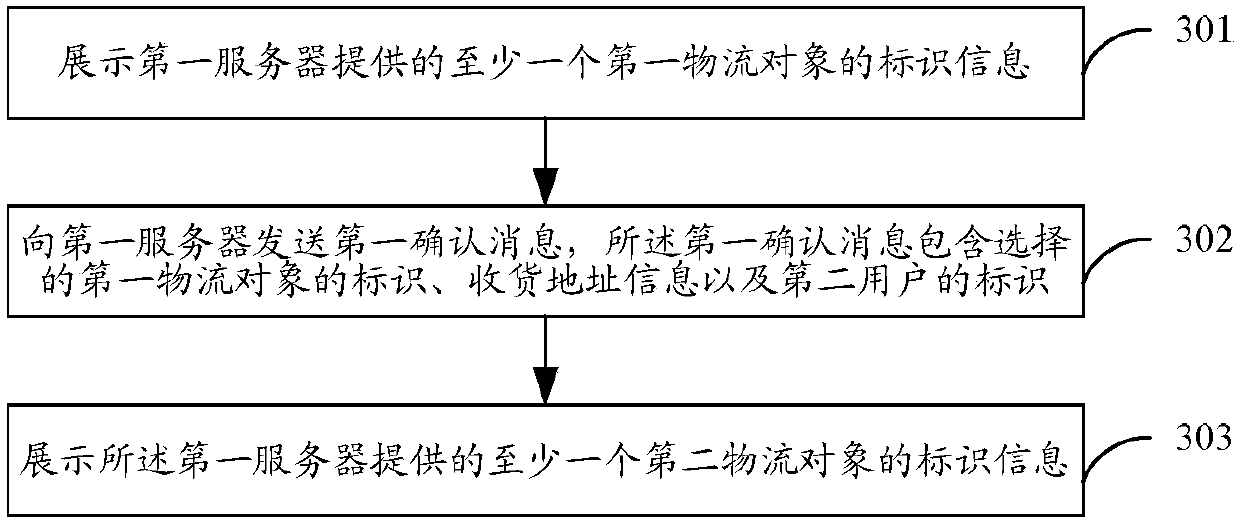
Logistics data processing method, logistics information pushing method and logistics information display method and device
ActiveCN107689025AImprove experienceImprove processing efficiencyLogisticsLogistics managementComputer science
The invention discloses a logistics data processing method, a logistics information pushing method and a logistics information display method and device. The logistics data processing method includesthe steps that a plurality of first logistics objects are provided and associated with at least one second logistics object, and the second logistics objects are associated with information of at least one logistics provider, wherein the first logistics objects include transportation mode information, and the second logistics objects include receiving mode information; a logistics order message from a first server is received, wherein the logistics order message includes the identifier, shipping address information and delivery address information of the first selected logistics object; according to the identifier of the first selected logistics object, at least one second logistics object is determined; the identifier information of the second logistics objects is fed back to the first server. The method and the device improve the user experience, the data interaction amount is also reduced, and the processing efficiency of logistics data is improved.
Owner:CAINIAO SMART LOGISTICS HLDG LTD
Method for configuring up-going detection reference signals and line termination equipment (LTE) heterogeneous network
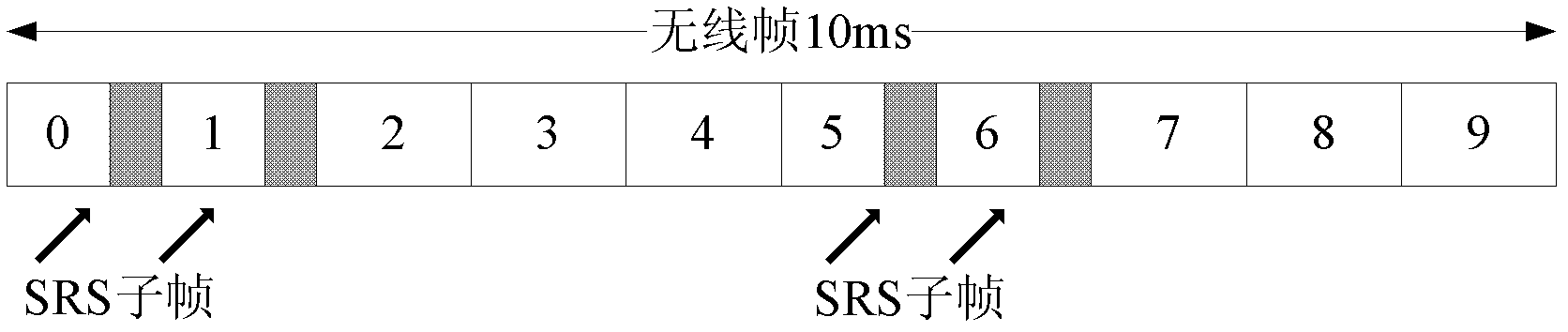
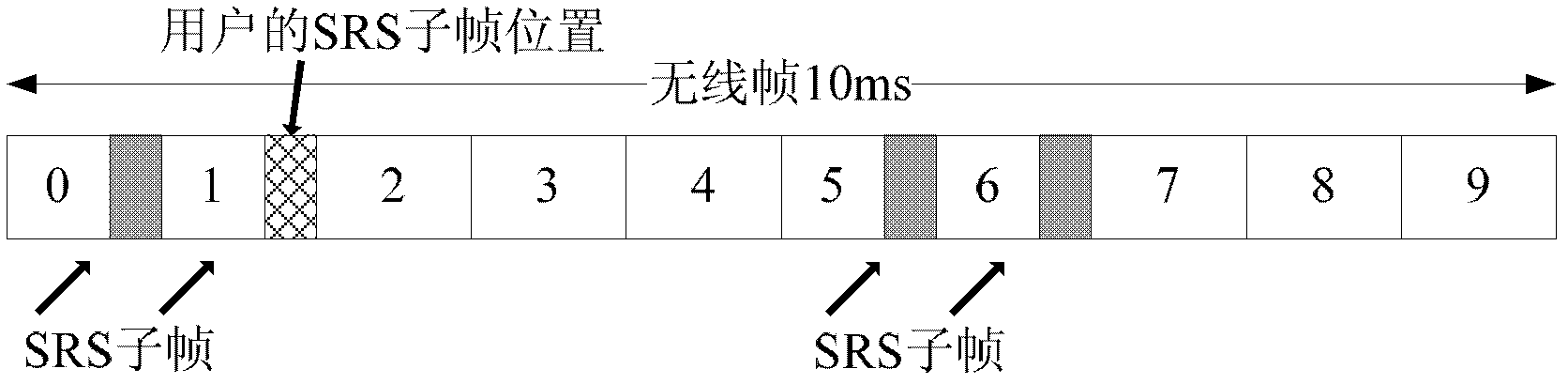
ActiveCN103139913AImprove accuracyReduce distractionsWireless communicationSounding reference signalSignal-to-interference-plus-noise ratio
The invention provides a method for configuring up-going detection reference signals and a line termination equipment (LTE) heterogeneous network. A macro cell site of the LTE heterogeneous network and small power transmission nodes in the covering area of the LTE heterogeneous network form a heterogeneous small area cluster, a plurality of CoMP small areas in the heterogeneous small area cluster forms a CoMP cooperation collection for carrying out coordinated multipoint transmission for a same user terminal, area stage SRS resources of the CoMP area and user stage SRS resources of CoMP user experience design (UE) are uniformly configured by the macro cell site of a cluster, and thus the orthogonality of the CoMP UE and the CoMP, the CoMP UE and non-CoMP UE and the non-CoMP UE and the non-CoMP UE of the small area cooperation collection are achieved. According to the method for configuring the up-going detection reference signals and the LTE heterogeneous network, signal to interference plus noise ratio (SINR) of user SRS is improved, and interactive data quantity brought by coordinated SRS resource configuration of each small area is reduced.
Owner:CHINA TELECOM CORP LTD
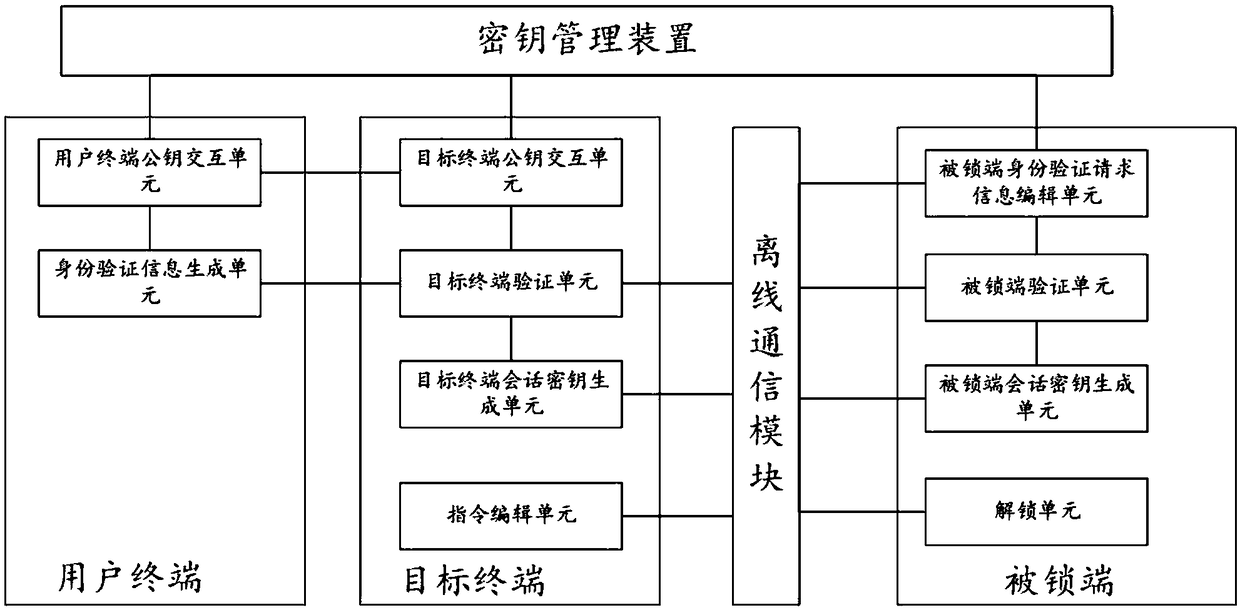
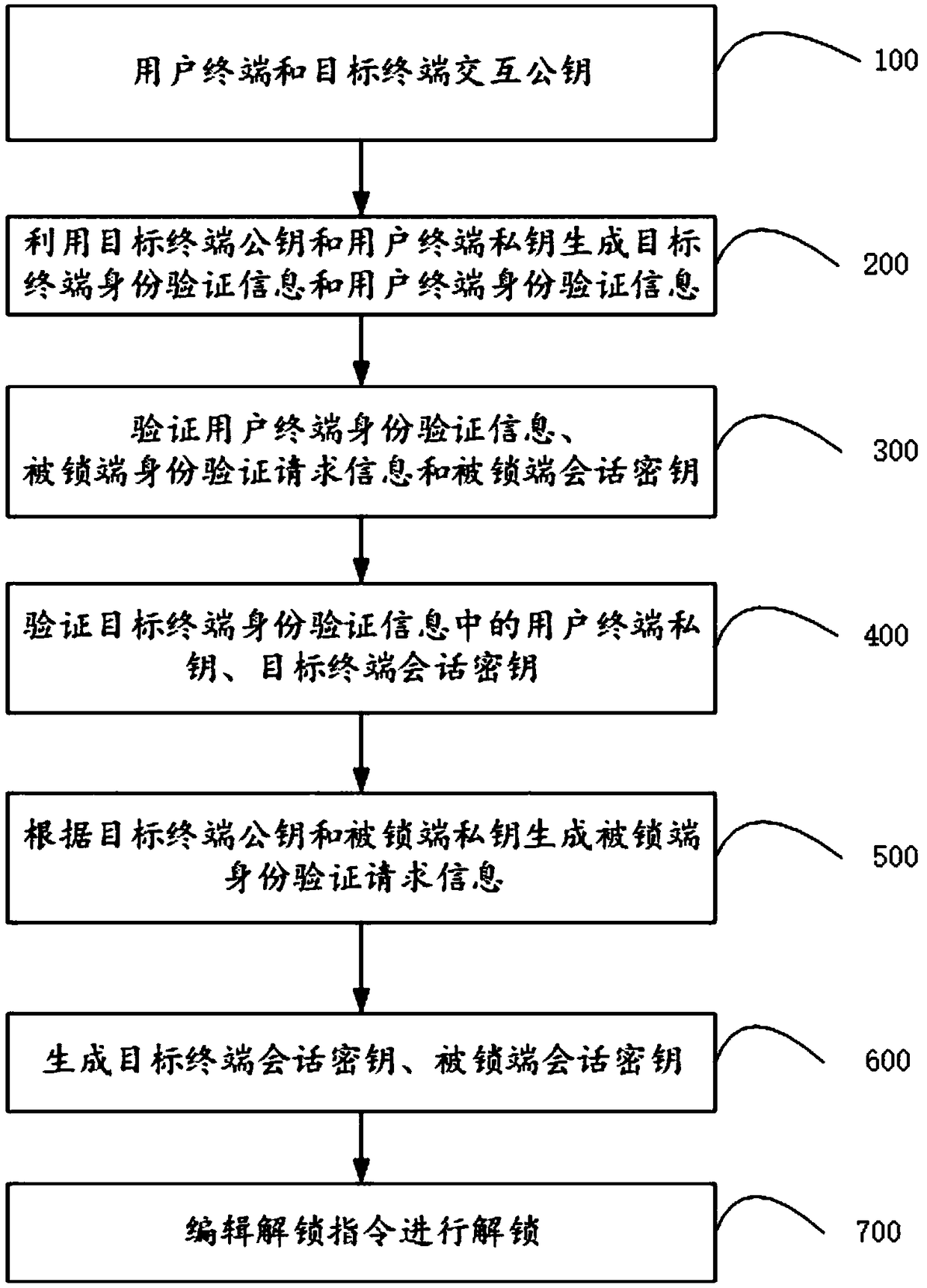
Virtual key mutual authentication system and method
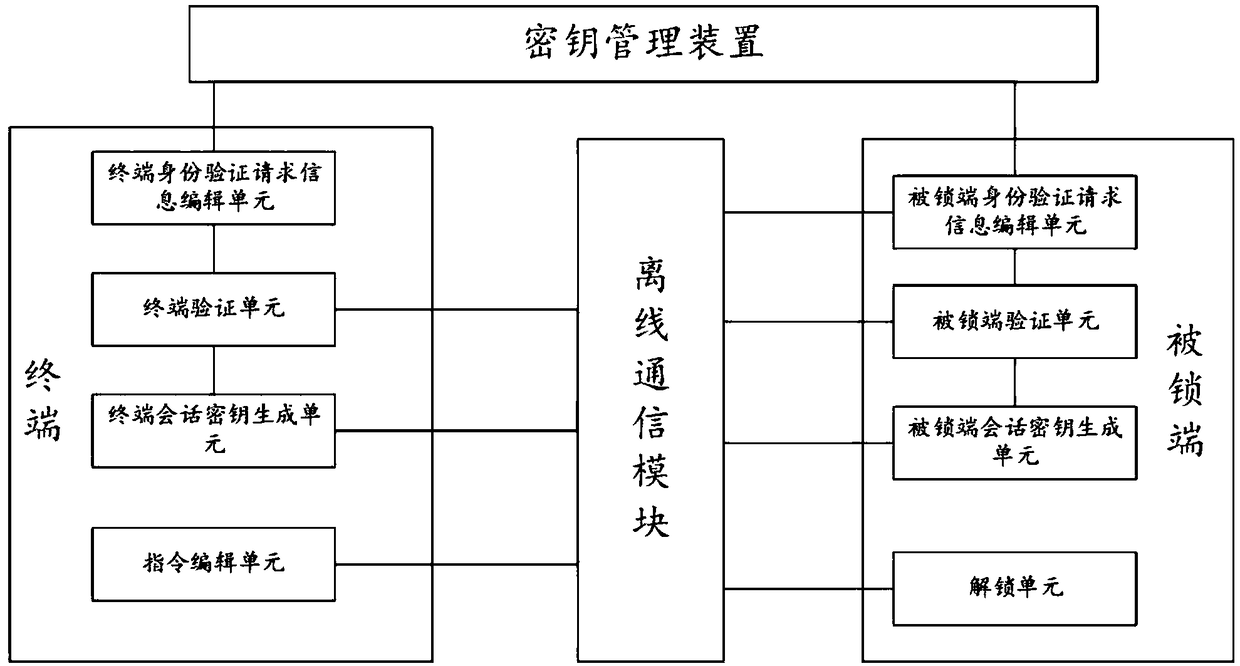
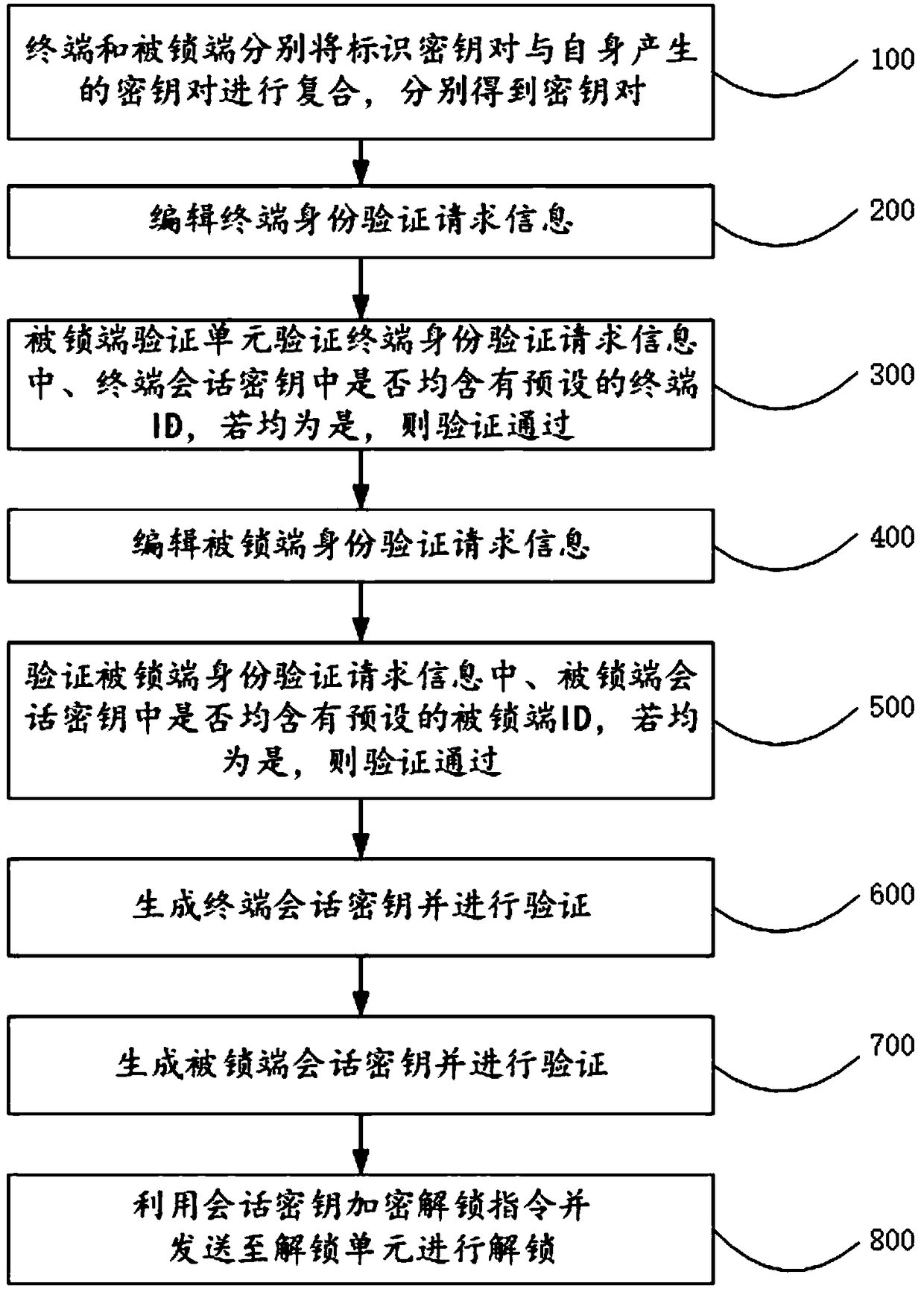
ActiveCN109067549AReduce sensitivityReduce interaction stepsUser identity/authority verificationIndividual entry/exit registersThird partyComputer terminal
The invention relates to the technical field of communication, in particular to a virtual key two-way authentication system and method. The system comprises a terminal, which is used for generating terminal authentication request information and sending it to the locked end for authentication. If the authentication passes, the generated terminal session key is sent to the locked end for authentication. If the authentication passes, the session key editing and unlocking instruction is sent to the locked end. The locked end is used for generating the authentication request information of the locked end and sending it to the terminal for authentication. If the authentication passes, the locked end session key is generated and sent to the terminal for authentication. If the authentication passes, the locked end session key is unlocked according to the unlocking instruction sent by the terminal. An offline communication module is used for transmitting information between the terminal and the locked end. The invention does not require on-line authentication of a third party when unlocking, but directly carries out information interaction between the terminal and the locked end, reduces the sensitivity of the whole system and the method to the network, and improves the safety and reliability in the use process.
Owner:北京信长城科技发展有限公司
Edge computing distributed model training method, terminal and network side equipment
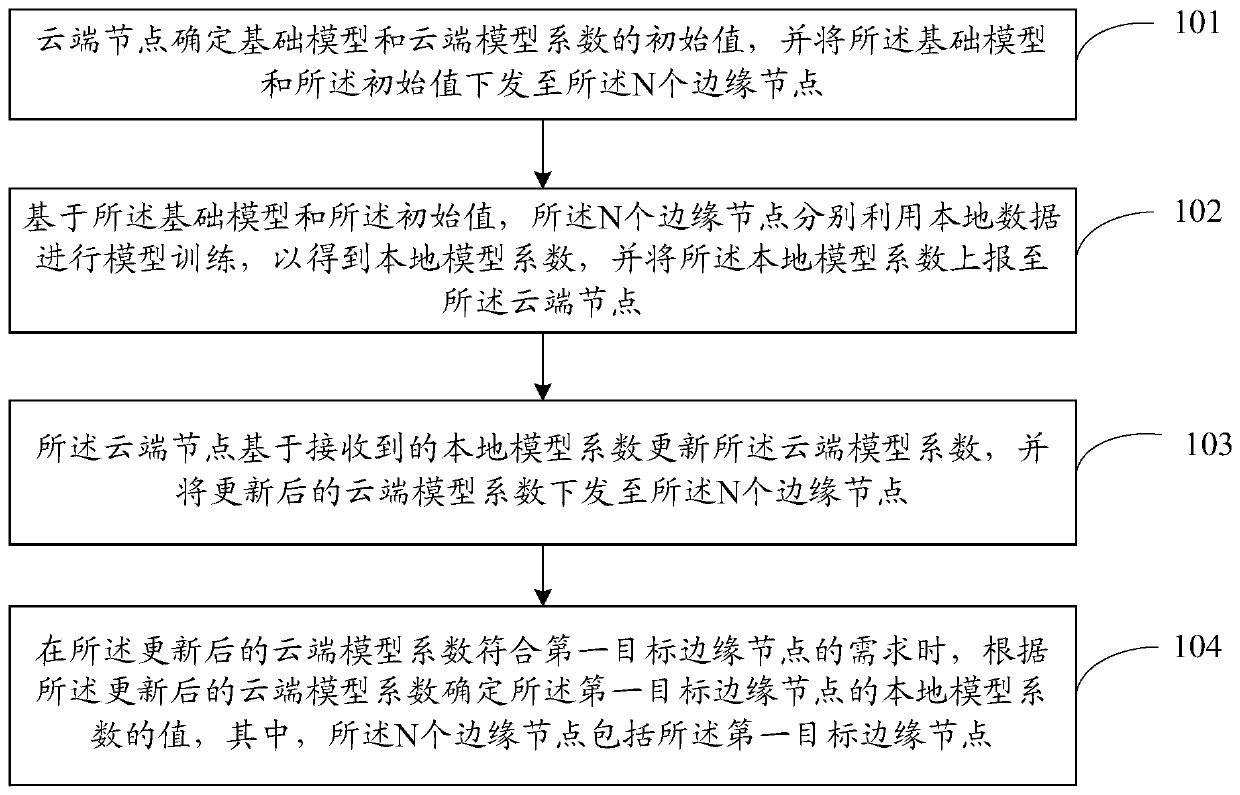
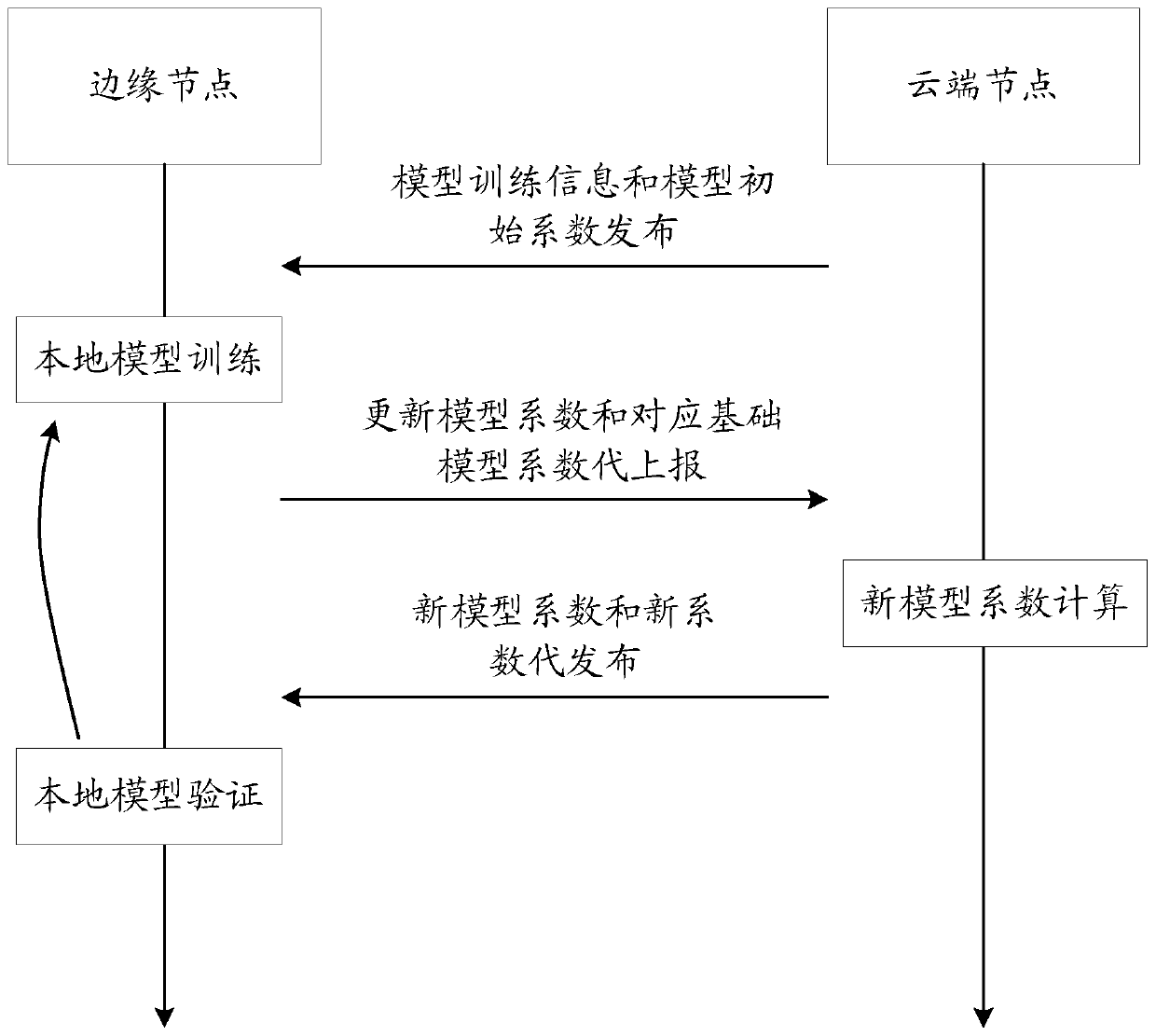
ActiveCN111030861AReduce the amount of data interactionReduce consumptionData switching networksEdge computingEdge node
The embodiment of the invention provides an edge computing distributed model training method, a terminal and network side equipment, and the method comprises the steps: enabling a cloud node to determine a basic model and an initial value of a cloud model coefficient, and transmitting the basic model and the initial value to N edge nodes; performing model training by using local data based on thebasic model and the initial values to obtain a local model coefficient, and reporting the local model coefficient to a cloud node; enabling the cloud node to update the cloud model coefficient based on the received local model coefficient, and issuing the updated cloud model coefficient to the N edge nodes; when the updated cloud model coefficient meets the requirements of the first target edge node, determining that the value of the local model coefficient of the first target edge node is the updated model coefficient. According to the embodiment of the invention, the interactive data volumein the edge computing distributed model training process can be reduced, so the resource consumption is reduced.
Owner:CHINA MOBILE M2M +1
Updating method and system for game service installation packet
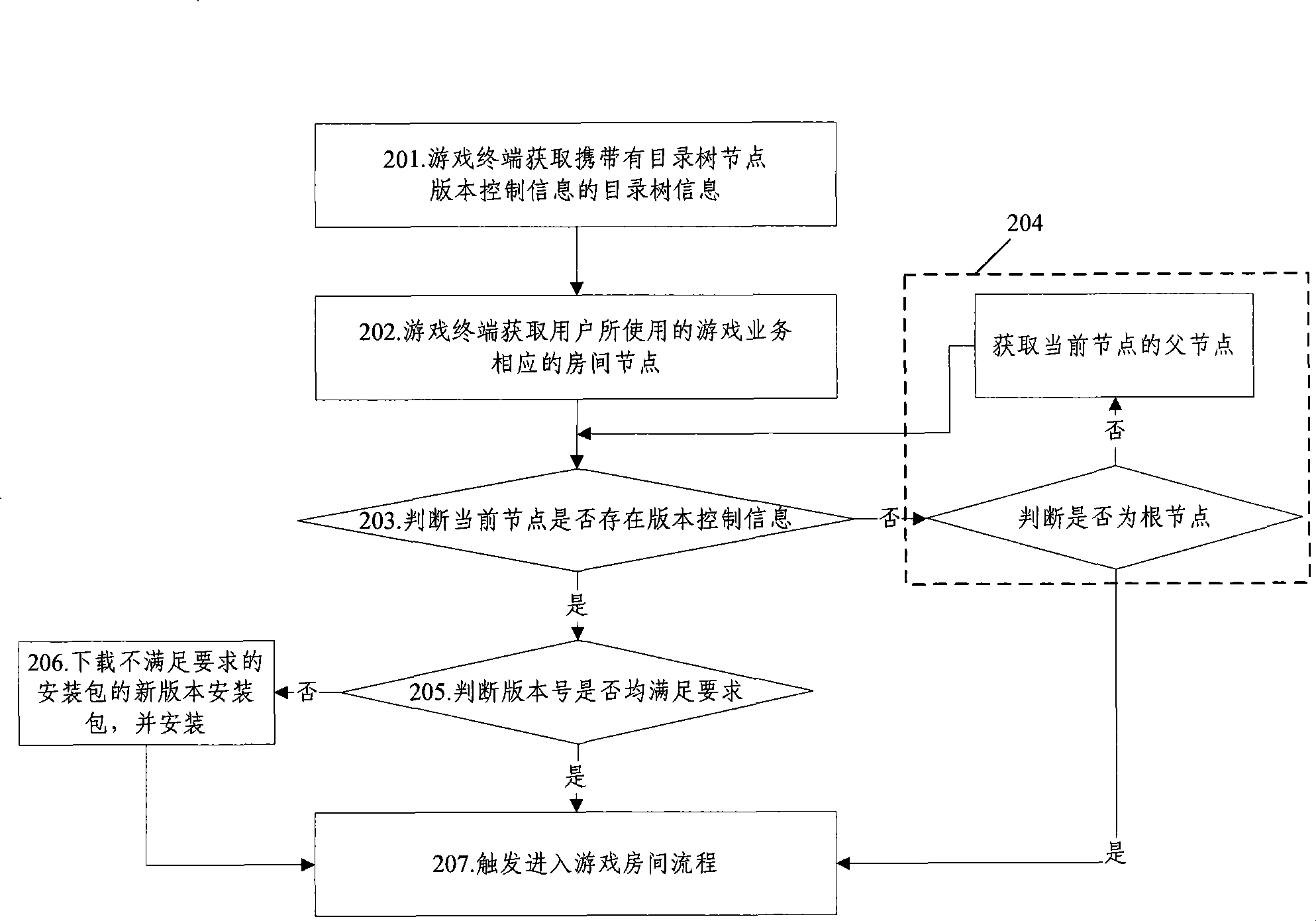
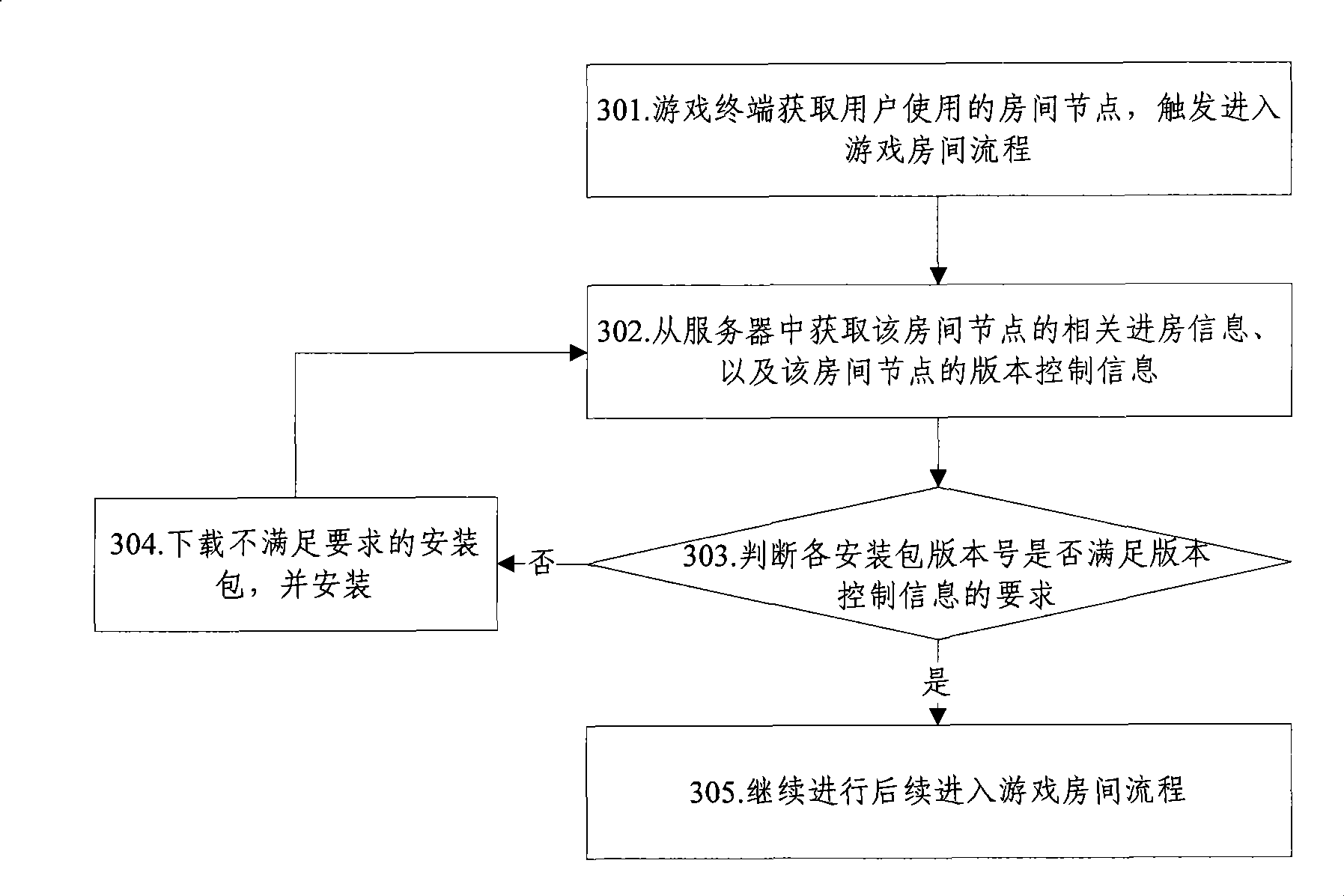
ActiveCN101383821AReduce data volumeSave bandwidth resourcesTransmissionSpecial data processing applicationsQuality of serviceSoftware engineering
The invention provides an updating method of a setup package of a game service. The method comprises the following steps: (A) a game terminal acquires a directory information tree with directory tree node version control information from a game server; (B) room nodes which are corresponding to the game service and are used by users are acquired; and (C) when determining that a current node exists the version information, the game terminal determines whether the version number of the setup package which is set up by the game service satisfies the requirements of the version control information, if so, the game room process is triggered and entered; or, a new setup package of the setup package which does not meet the requirement is downloaded, and after setup, the game room process is triggered and entered. The invention also provides an updating method of the setup package of the game service and a system for realizing the updating of the setup package of the game service; and the method and the system can reduce the maintenance cost of the game server to the room nodes, can avoid the repeated download of the users to the same resources, save the bandwidth and improve the service quality.
Owner:腾讯数码(深圳)有限公司
Network data pushing method, device and system
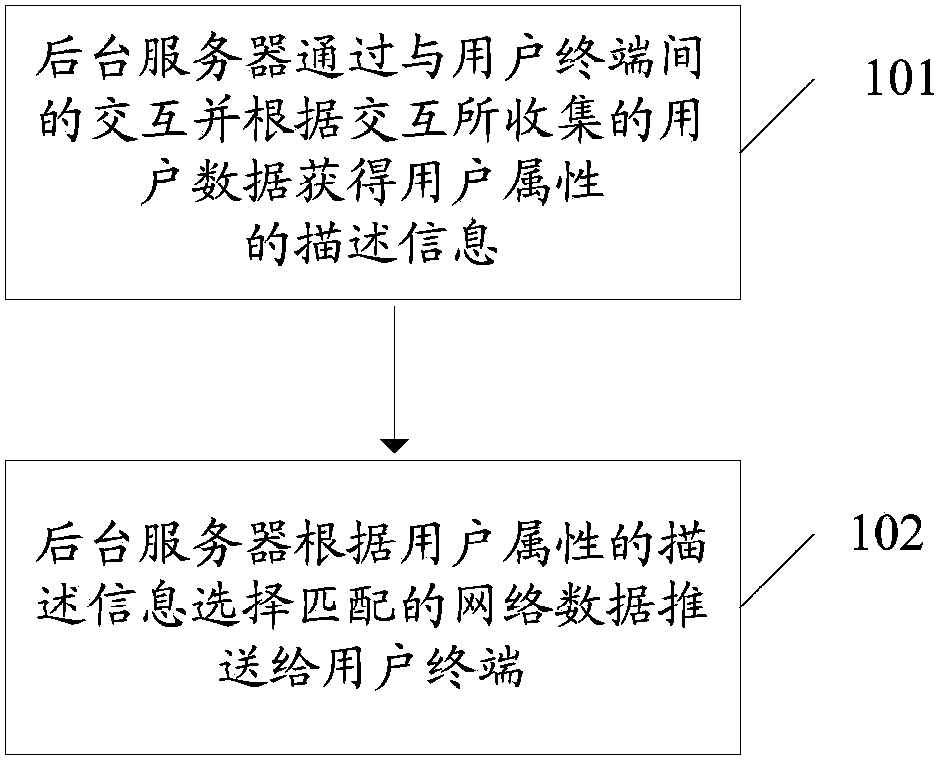
ActiveCN103812880AReduce loadReduce the amount of data interactionTransmissionData contentPersonalization
Owner:TENCENT TECH (SHENZHEN) CO LTD
Parking space reservation method, system and storage medium
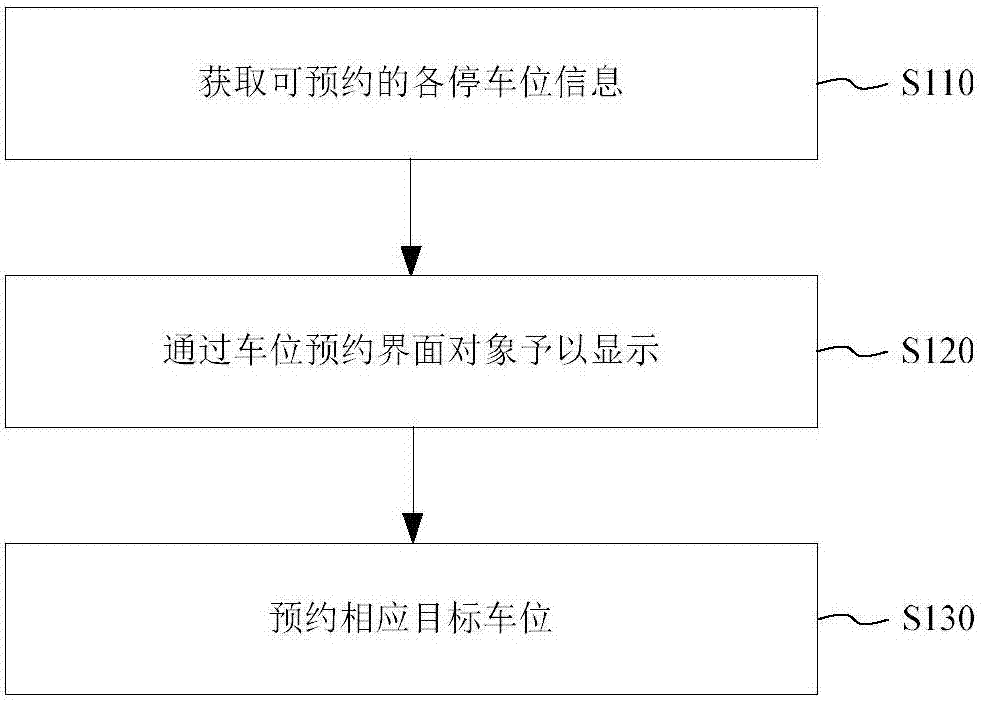
InactiveCN107025804AReduce the amount of data interactionImprove interaction efficiencyReservationsIndication of parksing free spacesParking spaceReal-time computing
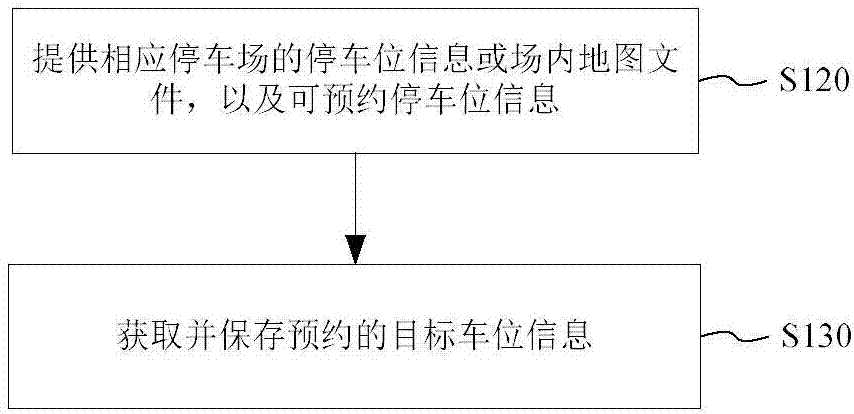
The application provides a parking space reservation method, system and a storage medium. The method includes the following steps: a server terminal, on the basis of a parking lot reservation request from the user terminal, providing available parking space information of a corresponding parking lot, or a lot map file and available parking space information of the corresponding parking lot; a user terminal establishing the correspondence between respective parking space information that is acquired and the pre-stored lot map file of the parking lot to be reserved, and displaying the corresponded lot map file through a parking space reservation interface object; and the user terminal reserving a corresponding target parking space on the basis of reservation operation of the target parking space information from the parking space preservation interface target. The application also provides a self-service method for reserving a specific parking space in a parking lot by using the user terminal.
Owner:上海喜泊客信息技术有限公司
Quick switch method and system under protected mode in passive optical network and optical network unit
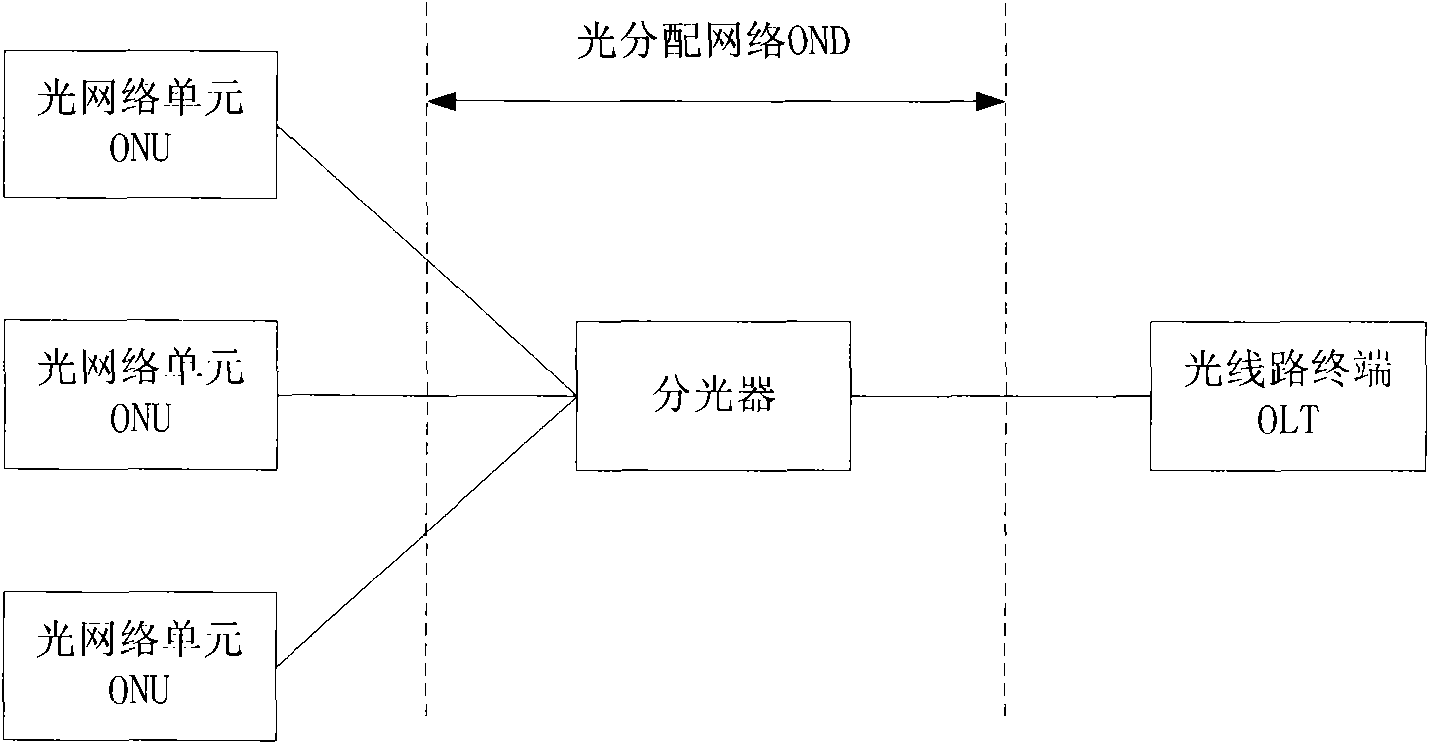
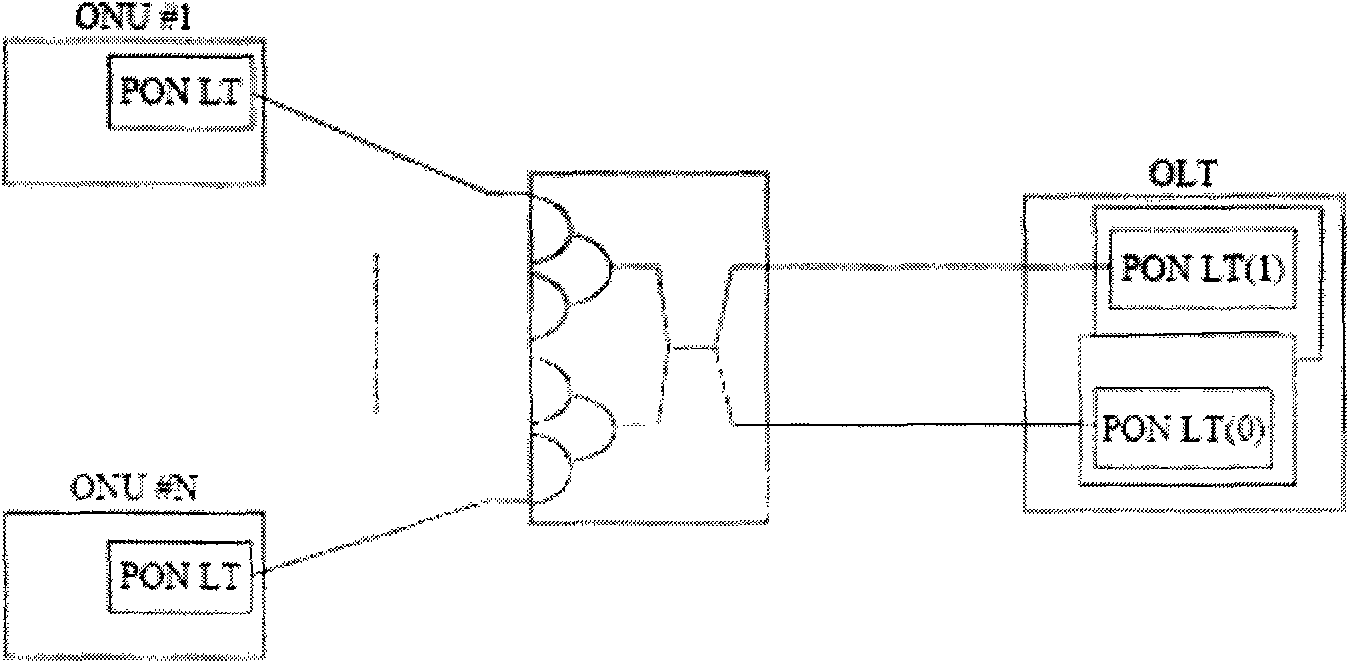
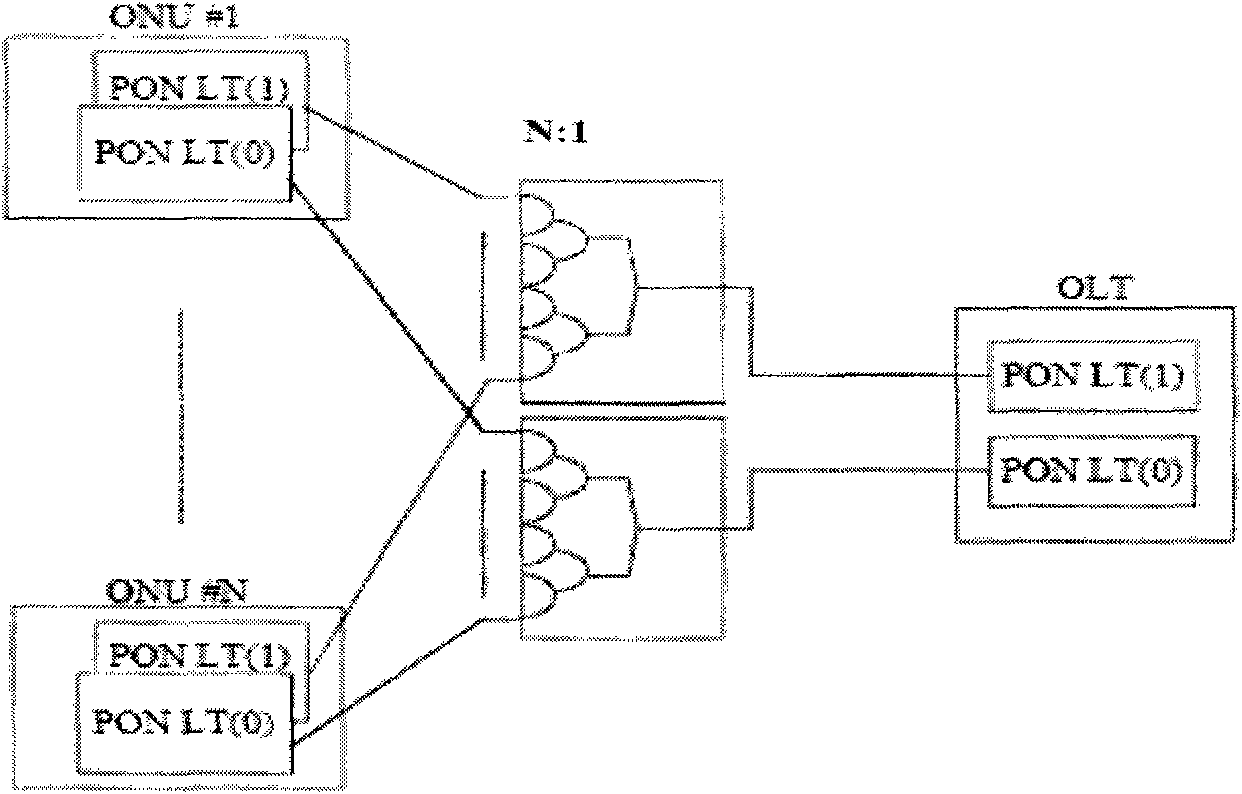
ActiveCN101873514ASimple switching processExtension of timeMultiplex system selection arrangementsElectromagnetic transmissionComputer networkProtected mode
The invention discloses a quick switch method and system under the protected mode in a passive optical network and an optical network unit. The method comprises the following steps: the optical network unit stores the identifier of a protected path corresponding to the optical port of an optical line terminal and a protected path building parameter; after a service path for data communication between the optical network unit and the optical line terminal is invalid, the optical line terminal starts an available optical port and synchronizes with the optical network unit via a path corresponding to the optical port, namely a destination path; the optical line terminal sends a quick switch indication message to the optical network unit and carries the identifier of the destination path, the optical network unit extracts the protected path building parameter of the destination path according to the identifier and completes the subsequent building process with the destination path of the optical line terminal by using the protected path building parameter to enter into the operation state. The invention can reduce the switching time of the optical network unit under the protected mode, reduce the data exchange amount in switching and improve the time for the optical network unit to restore normal work to millisecond level.
Owner:ZTE CORP
Virtual key sharing system and method
ActiveCN109067548ASimple structureSimple methodUser identity/authority verificationIndividual entry/exit registersComputer terminalKey sharing
The invention relates to the technical field of communications, in particular to a virtual key sharing system and method. The system comprises a user terminal, which is used for interacting with a target terminal and generating authentication information of the target terminal and authentication information of the user terminal. The target terminal is used for verifying the received authenticationinformation of the user terminal, generating a session key of the target terminal, and sending an unlocking instruction edited by the session key to the locked terminal. The locked end is used for verifying the received authentication information of the target terminal with the private key of the user terminal, generating a session key of the locked end, and unlocking according to an unlocking instruction sent by the target terminal. An offline communication module is used for transmitting information between the terminal and the locked end. The user terminal and the target terminal of the invention carry out authentication of the identity information through the interactive public key, and only if the authentication is successful, the target terminal can use the identity information of the user terminal to unlock the locked end, which has the advantages of simple structure, simple method and safe and convenient use.
Owner:北京信长城科技发展有限公司
Power information physical system joint simulation platform and synchronization method thereof
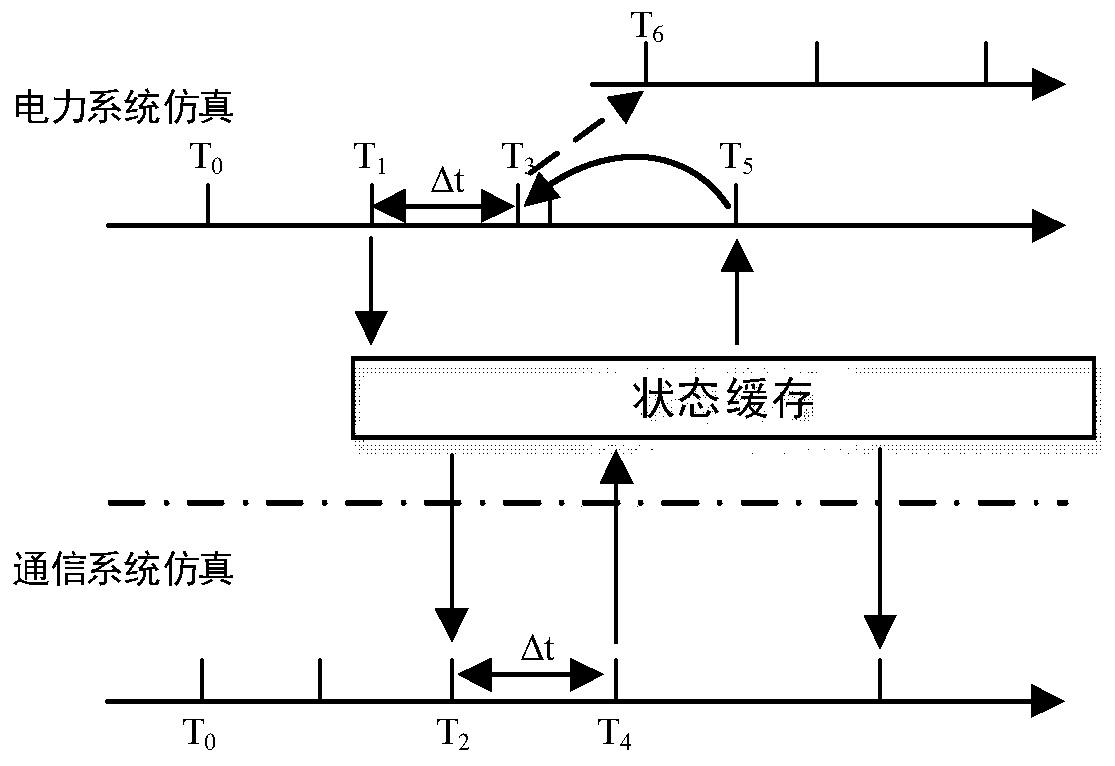
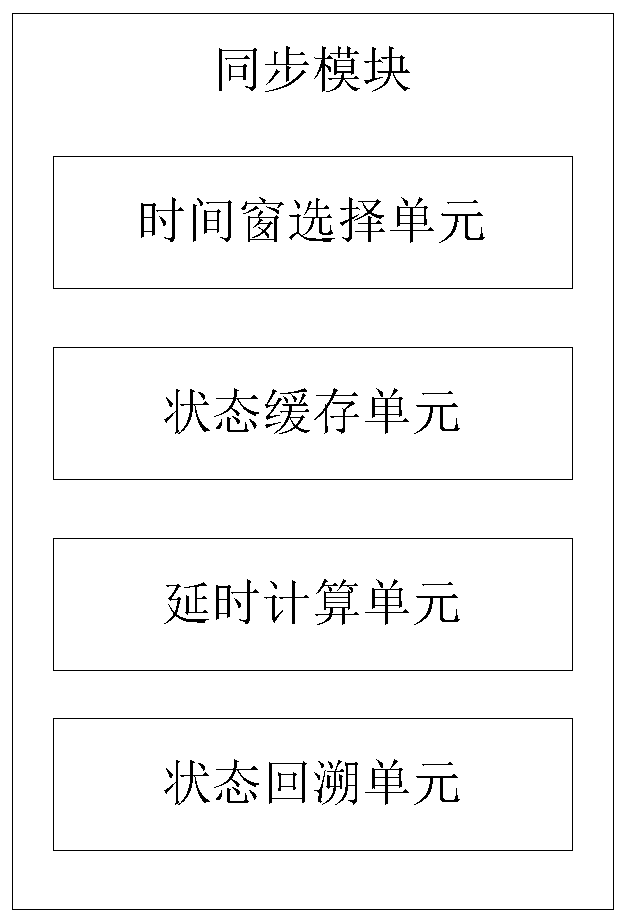
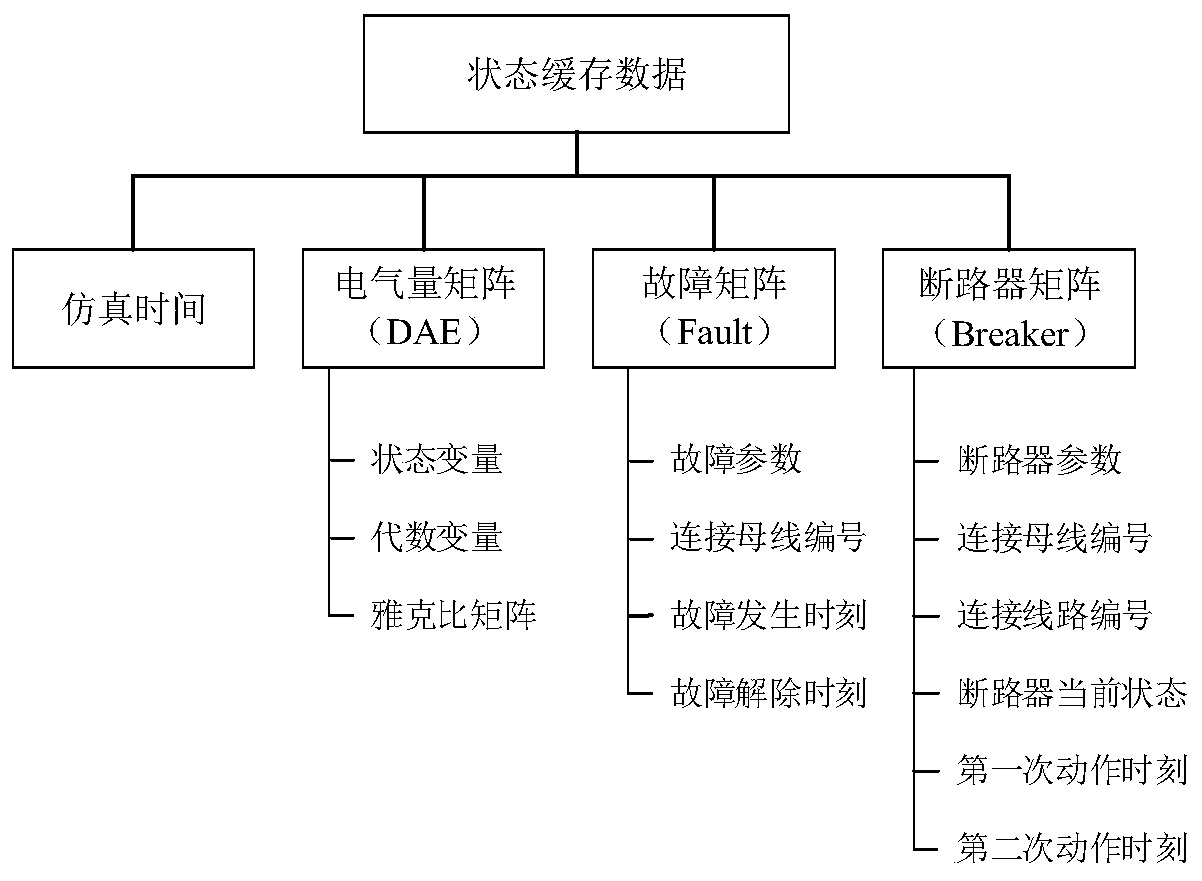
ActiveCN109977541AReduce the amount of data interactionImprove Co-Simulation EfficiencyData processing applicationsDesign optimisation/simulationElectric power systemSimulation
The invention discloses an electric power information physical system joint simulation platform and a synchronization method thereof, which can be used for simulating a large-scale electric power information physical system and improving the simulation efficiency while ensuring the simulation precision. According to the simulation platform and the synchronization method thereof, by storing the simulation result of each step length of the electric power simulation software into a state cache in a certain time window; acquiring a key event of a power system, sending data to communication simulation software only when the key event occurs, judging whether the state of the power system is changed or not by a simulation platform according to a simulation result of the communication simulation software, and recalling power simulation only when the state is changed and the action time is before the current simulation time, the unnecessary data interaction amount and the simulation start-stopfrequency between the electric power simulation software and the communication simulation software are reduced, the simulation precision and speed are considered, and the efficiency of joint simulation of the electric power information physical system is improved.
Owner:SOUTHEAST UNIV +1
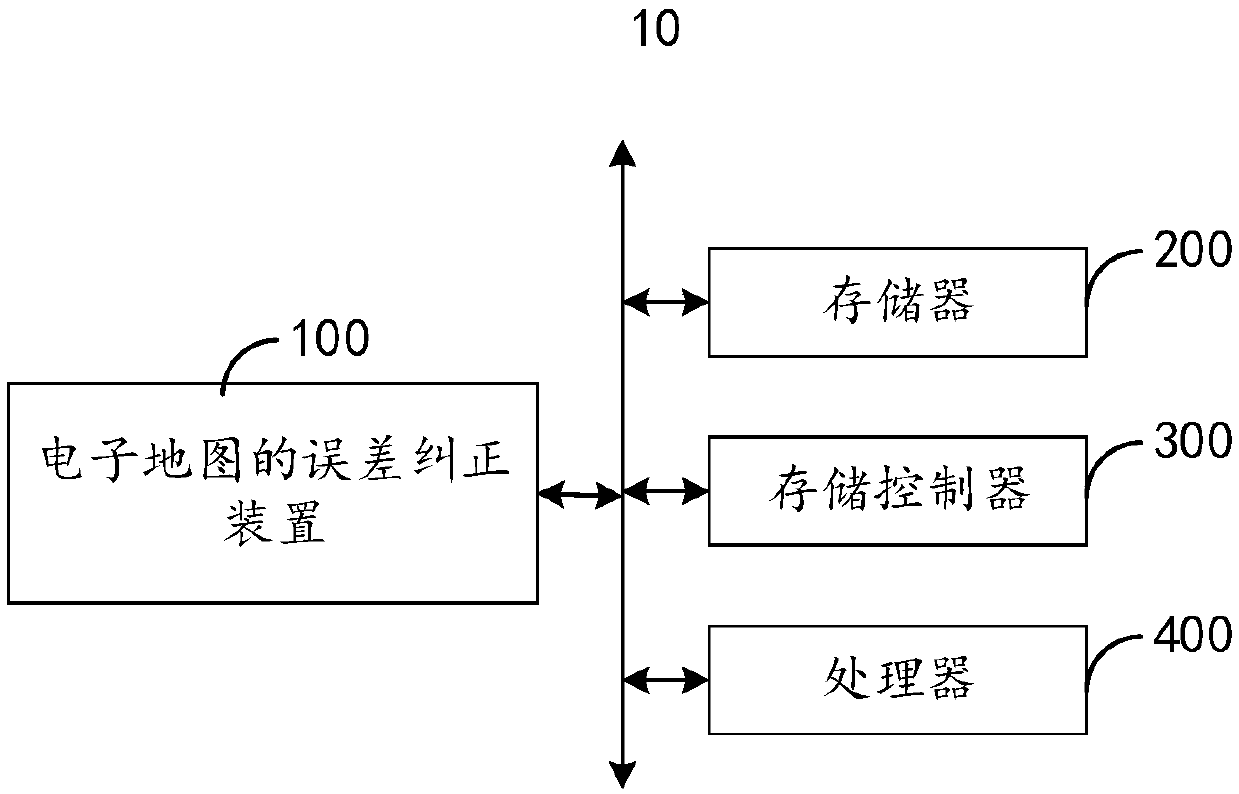
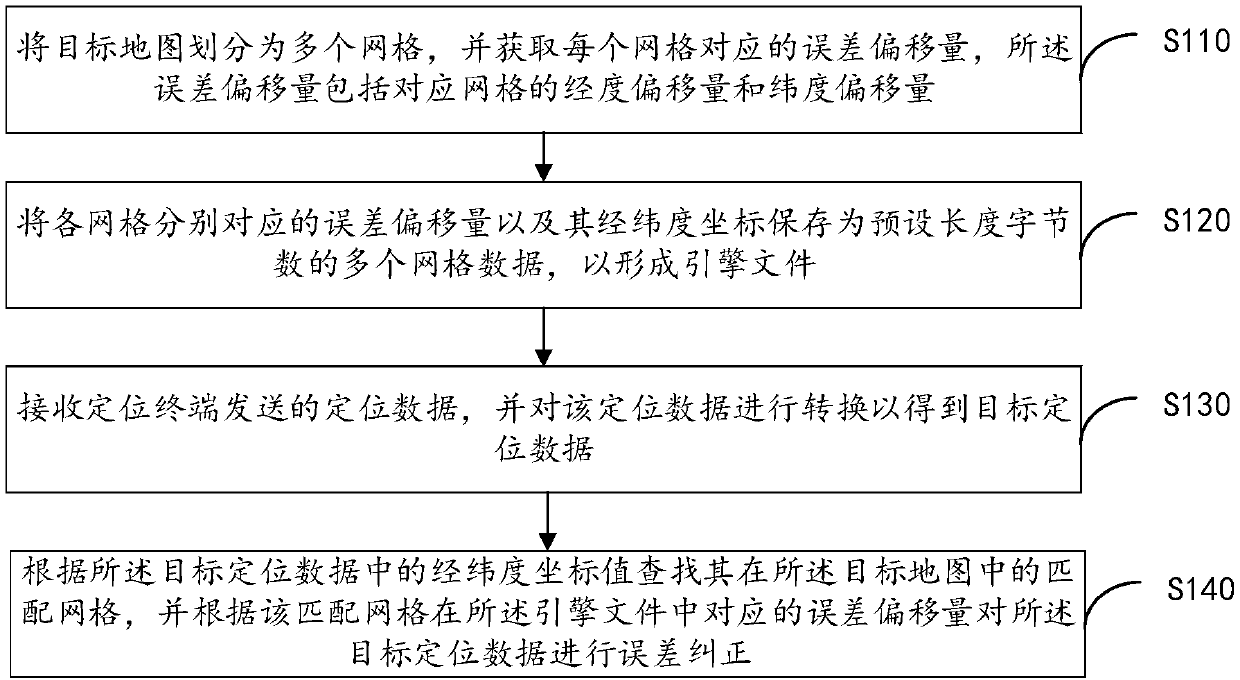
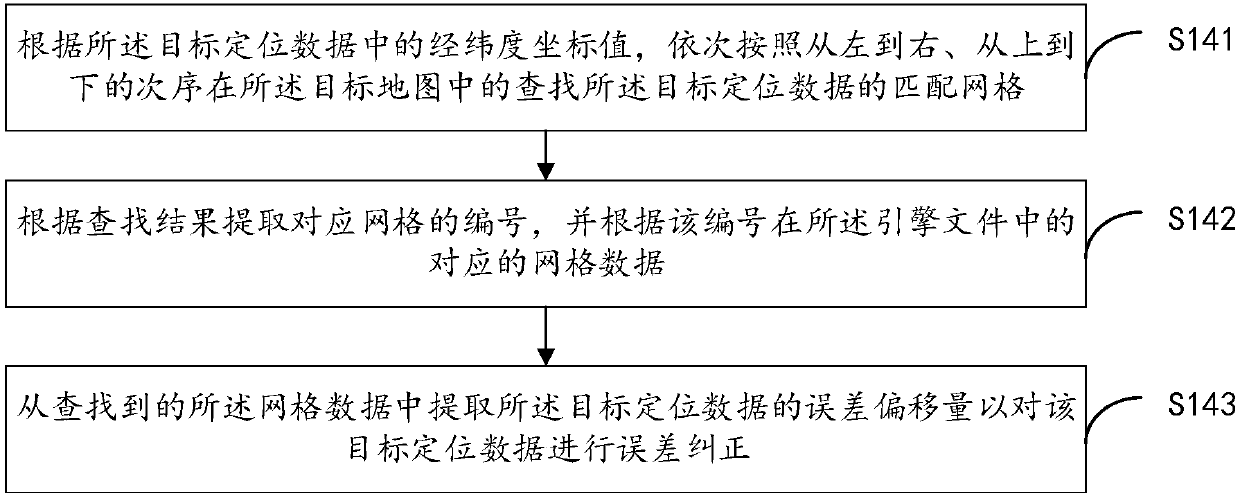
Error correction method and device of electronic map
InactiveCN107832386AReduce the amount of data interactionReduce error correction timeGeographical information databasesSpecial data processing applicationsElectronic mapCorrection method
The invention provides an error correction method and device of an electronic map. The method comprises the steps that a target map is divided into multiple grids, and the error offset amount corresponding to each grid is obtained; the error offset amounts respectively corresponding to the grids and their longitude and latitude coordinates are stored as multiple piece of grid data having preset length byte numbers to form an engine file; positioning data sent by a positioning terminal is received and is converted to obtain target positioning data; according to the longitude and latitude coordinate values in the target positioning data, matched grids in the target map are looked up, and error correction is conducted on the target positioning data according to the corresponding error offsetamounts of the matched grids in the engine file. The data interaction amount during error correction is effectively decreased by pre-generating the engine file for error correction, the error correction efficiency is improved, and error correction accuracy is high.
Owner:AERIAL PHOTOGRAMMETRY & REMOTE SENSING CO LTD
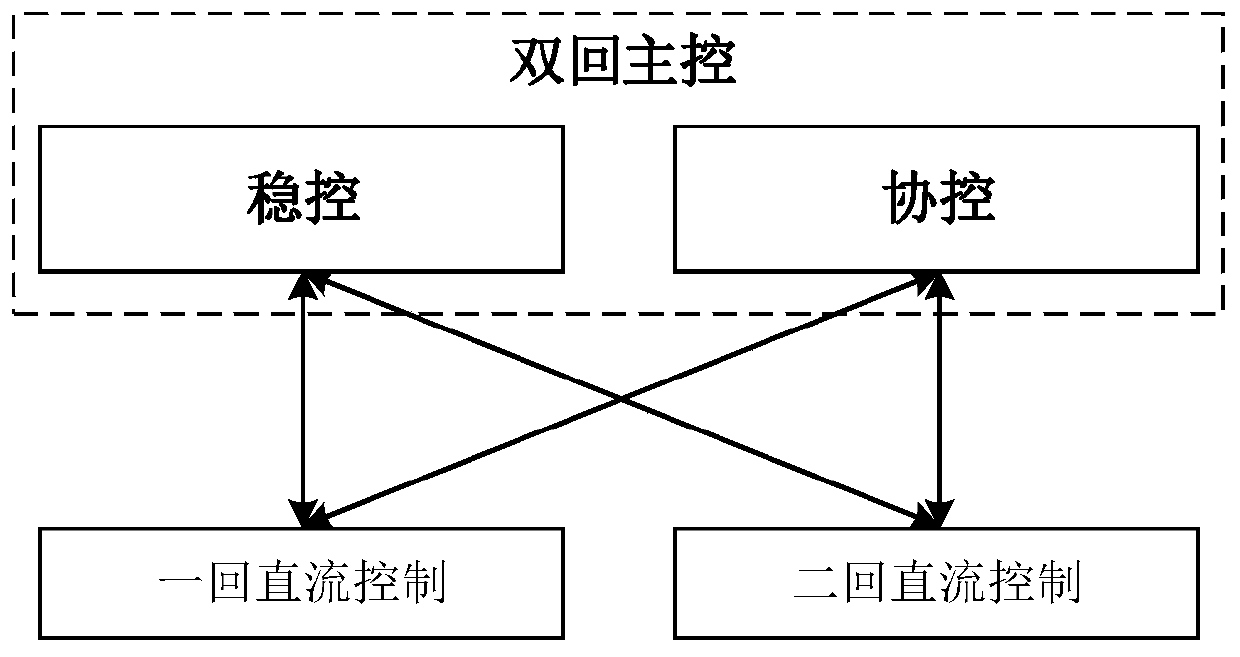
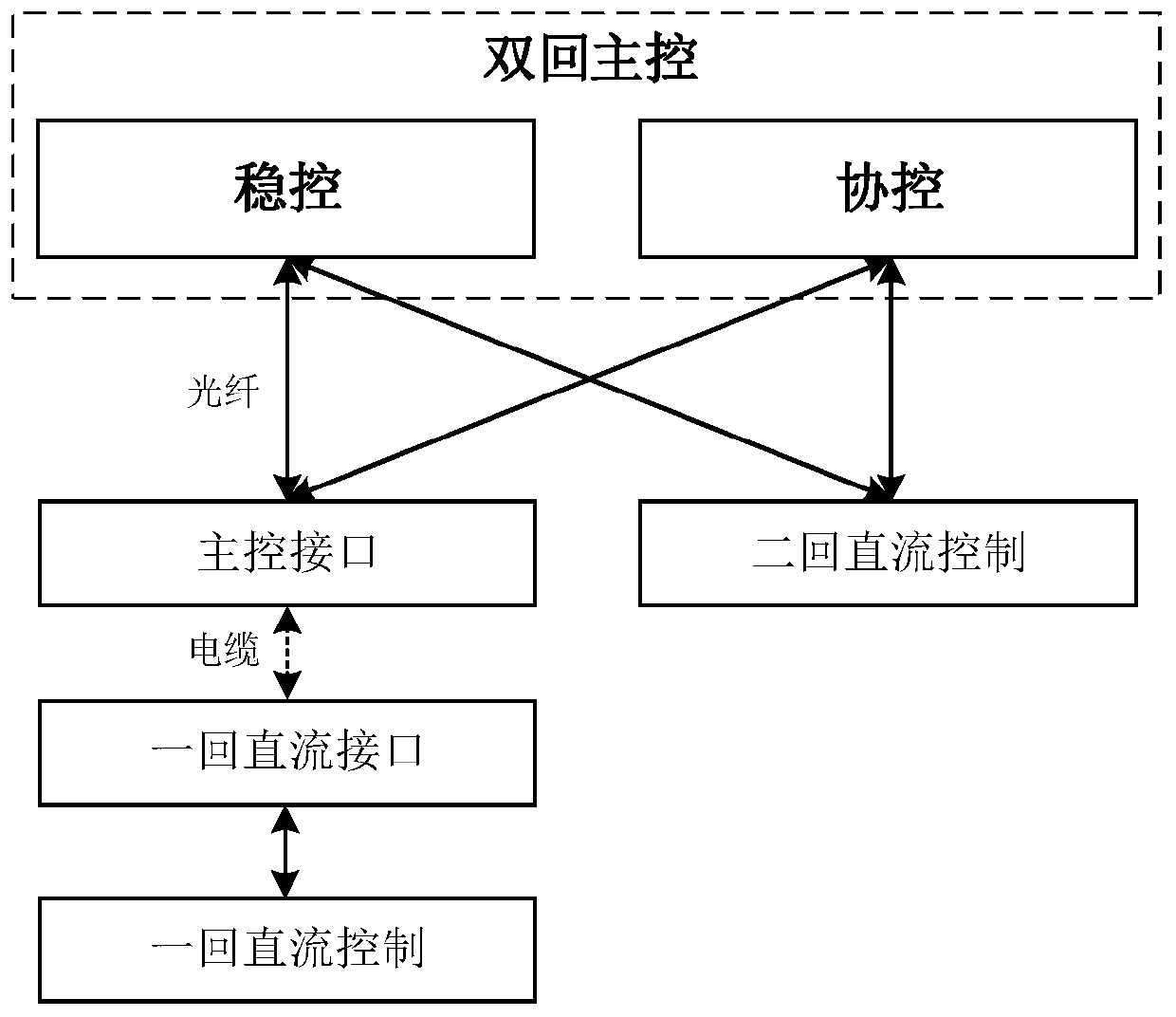
Master control system of two-loop DC power transmission system and configuration method
ActiveCN109873444AReduce the amount of data interactionElectric power transfer ac networkAc networks with different sources same frequencyControl systemComputer module
The invention discloses a master control system of a two-loop DC power transmission system and a configuration method. A sending end or a receiving end of a two-loop direct current are arranged at thesame converter station, and the two-loop direct current is designed and runs independently due to factors such as stage construction and attachment to different industries; and since the two-loop direct current shares the same AC bus, and synergic control is needed on aspects of active power and reactive power. The invention proposes a two-loop DC master control system. The master control systemcomprises two parts of a stable control host and a synergic control host, wherein the stable control host and the synergic control host are independent to each other, signal interaction with a two-loop DC control system is performed, a two-loop DC active power synergic control module and a system safe and stable control module are arranged in the stable control host, and a two-loop DC reactive power synergic control module and an additive control synergic control module are arranged in the synergic control host. By reasonable host arrangement and functional allocation, and the two-loop DC synergic control can be achieved when the two-loop DC sending end or the receiving end are arranged at the same converter station.
Owner:NR ELECTRIC CO LTD +2
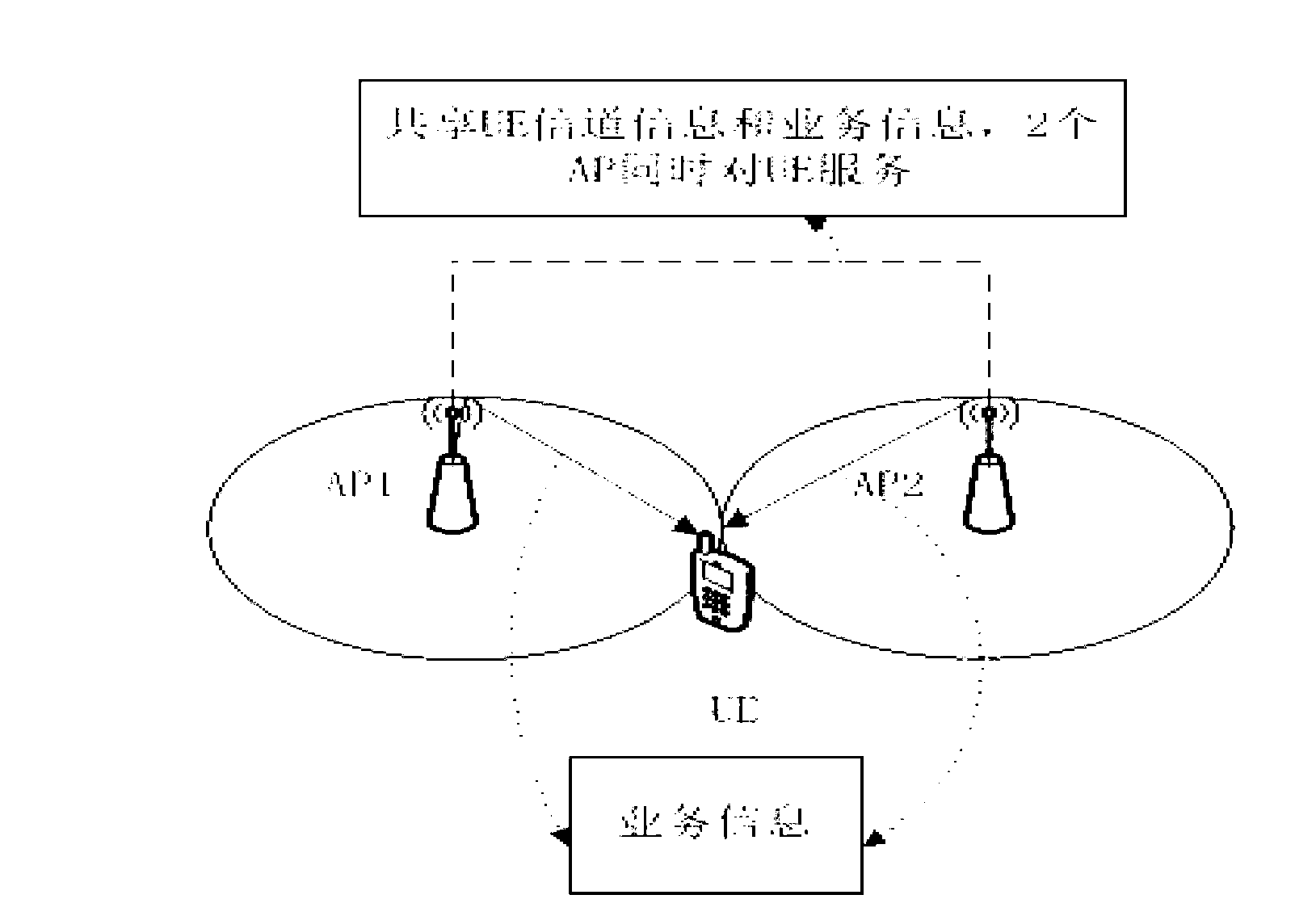
Multi-point coordination-based data transmission method and device
InactiveCN101938300AReduce the amount of data interactionEasy to detectSite diversitySpatial transmit diversityData transmissionComputer science
The invention discloses a multi-point coordination-based data transmission method and a multi-point coordination-based data transmission device. The method comprises the followings steps of: receiving user data in coordinated resources and detecting coordinated user data from the user data by using a serving cell; and if the coordinated user data is detected to be false, informing coordinated cells of transmitting detected coordinated resource data to the serving cell and processing according to received feedback information from all of the coordinated cells. The method and the device reduce data interaction amount between base stations and improve system detection performance.
Owner:ZTE CORP
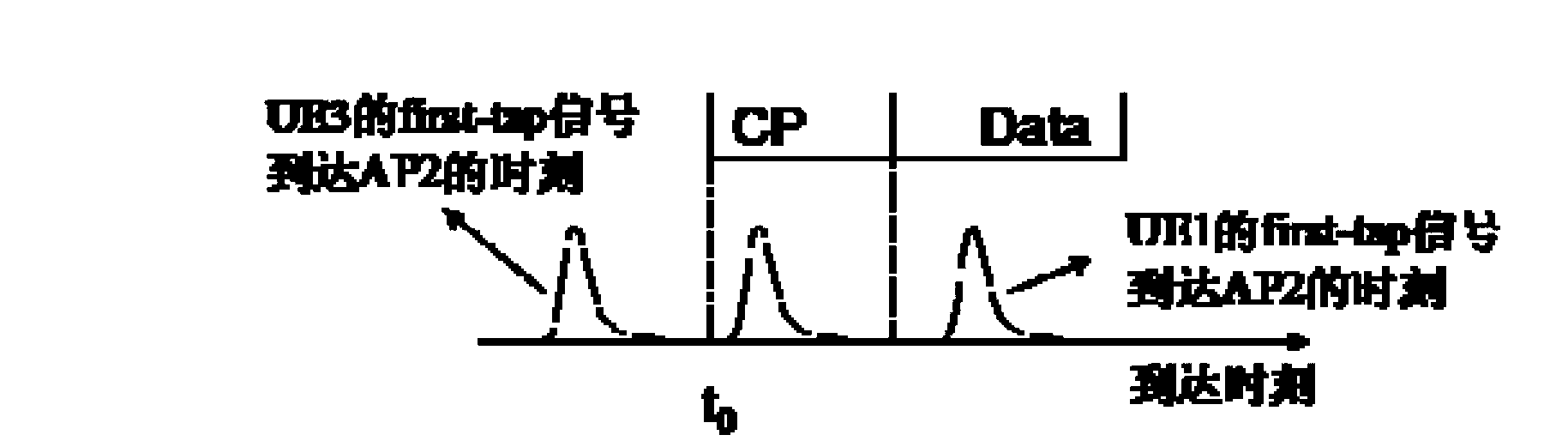
Method and device for selecting time advanced-adjustment reference nodes in CoMP (coordinated multi-point) uplinks
ActiveCN102711186AReduce the amount of data interactionSimple methodNetwork traffic/resource managementAssess restrictionTransfer modeComputer science
The invention provides a method and a device for selecting time advanced-adjustment reference nodes in CoMP (coordinated multi-point) uplinks. The method includes firstly determining a current transmission model of a downlink CoMP; selecting an access point nearest to a user as a time advanced-adjustment reference node if the transmission mode is determined as a jointly processing mode; or selecting a main service access point of a user equipment as the time advanced-adjustment reference node if the transmission mode is determined as a coordinate dispatch / shaping mode. By utilizing different methods to select time advanced-adjustment reference nodes according to different transmission modes, data interaction quantity among base stations is greatly reduced. Further, the method is simple and easy, and no modification is carried on hardware of existing communication mechanisms.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
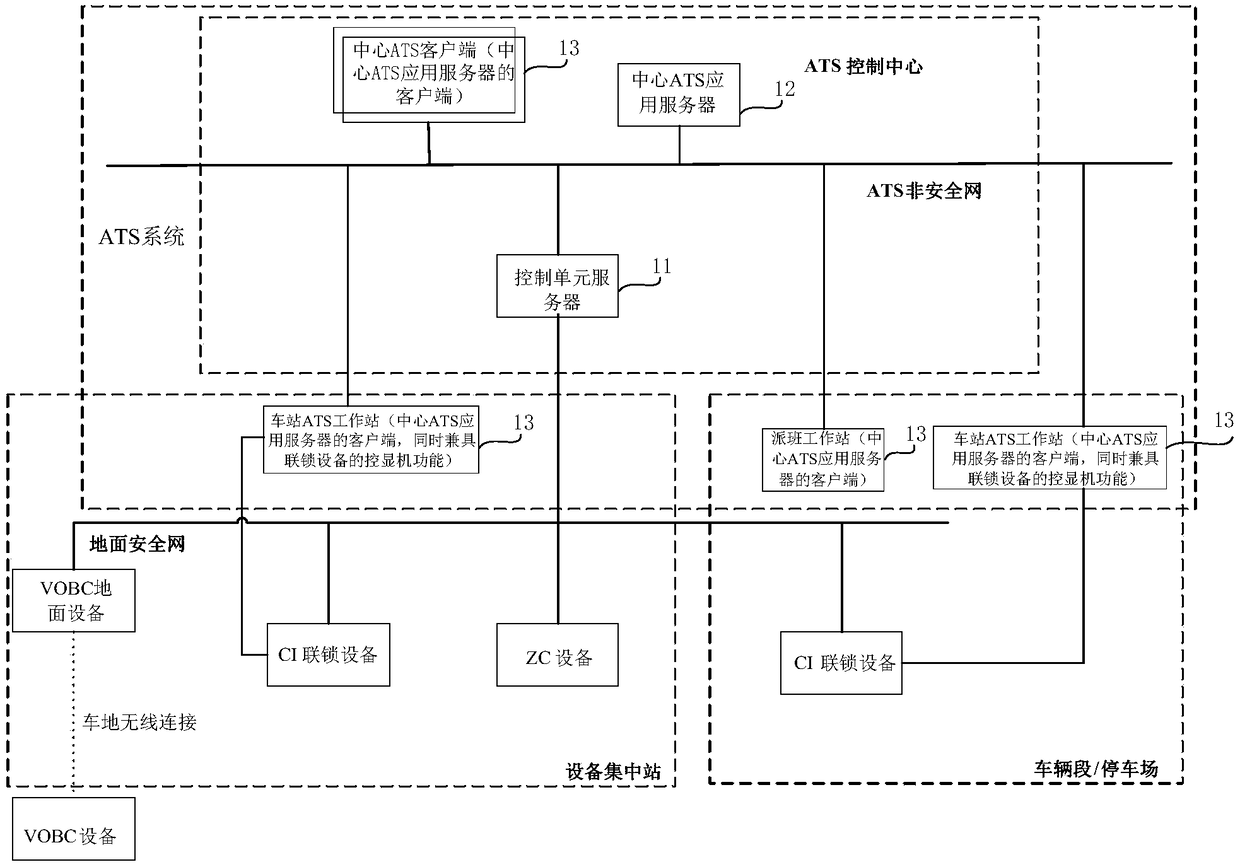
Automatic monitoring system for train
The present invention provides an automatic monitoring system for a train and a control unit server. The ATS system includes a control unit server, a central ATS application server, and an ATS client.The control unit server is configured to send the monitoring data to the central ATS application server, and the central ATS application server is configured to generate an operation command and sendthe operation command to the control unit server. The control unit server is further configured to perform protocol conversion of the operation command, and transmit the converted operation command to a destination plane device. In the ATS system, there is no need of an independent station or vehicle segment ATS application server, and an interlocking display control machine of the station is notseparately set, thereby reducing the hardware cost. The monitoring data is centrally processed by the central ATS application server, thereby reducing the data interaction quantity between the central ATS application server and the station or vehicle segment ATS client, and reducing the complexity of software development.
Owner:BYD CO LTD
Method and device for re-authenticating terminal
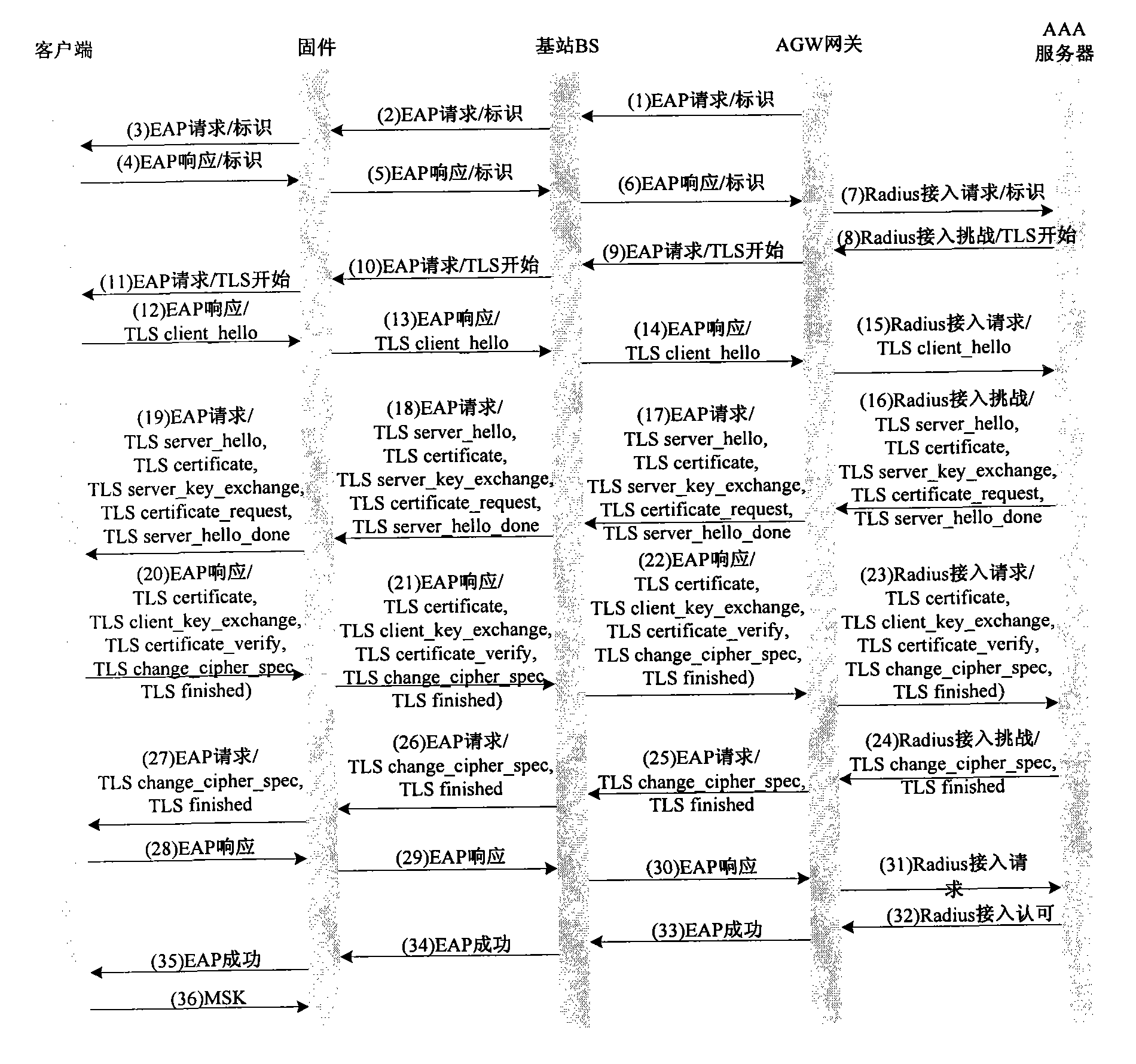
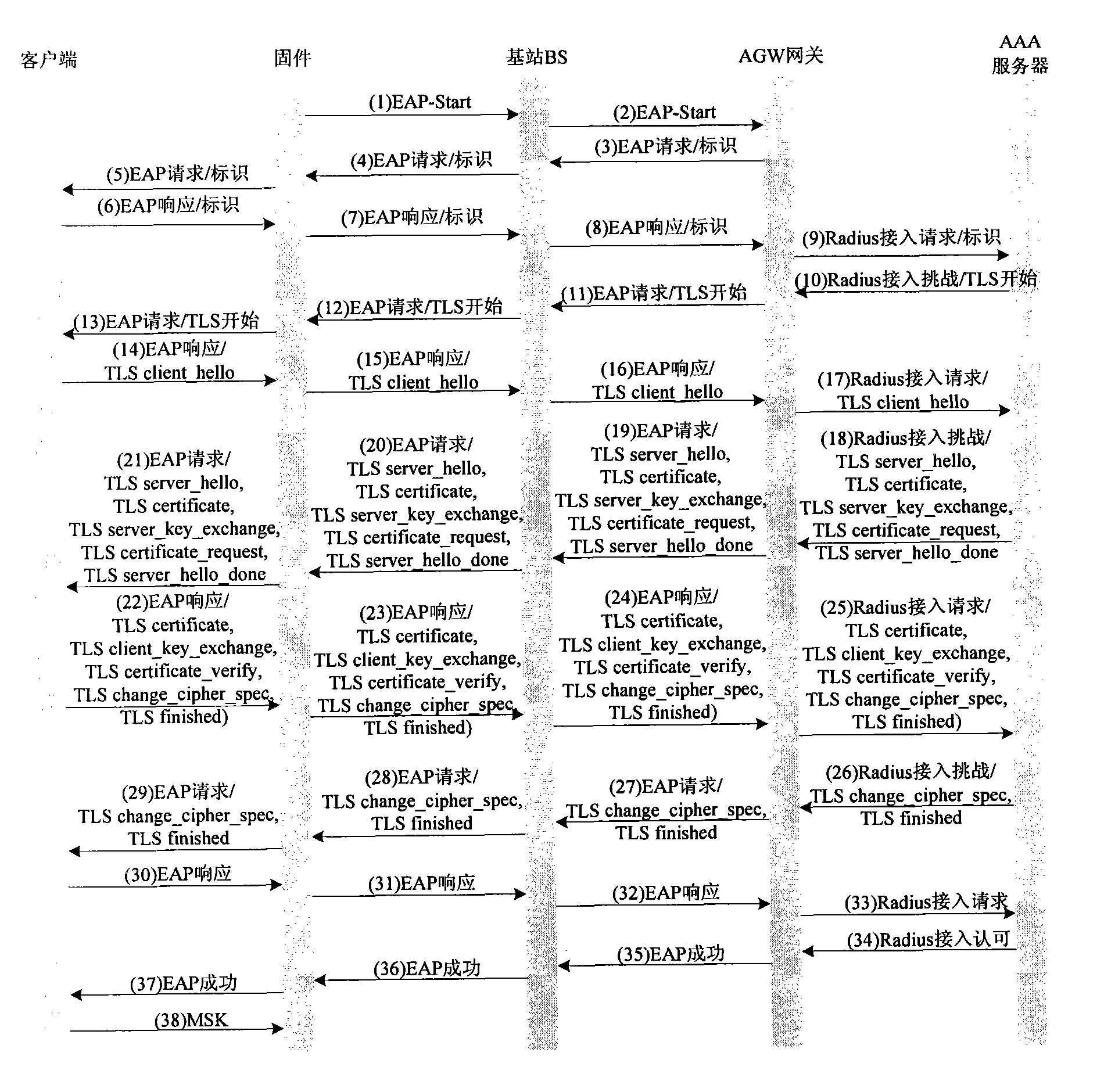
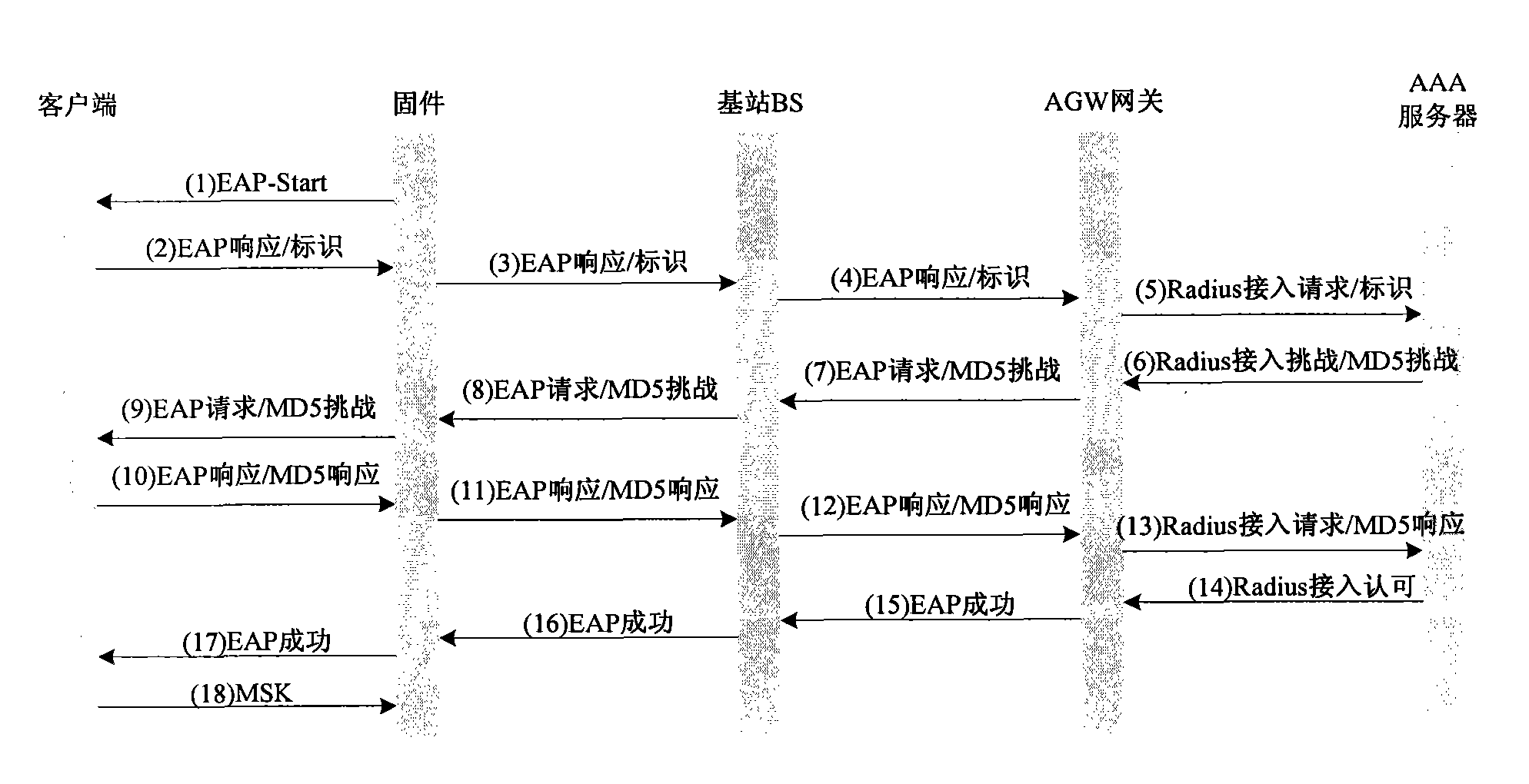
InactiveCN101626569AImprove access speedQuick interactionTransmissionSecurity arrangementHigh pressureClient-side
The invention provides a method for re-authenticating a terminal, which aims to optimize an access process of the re-authentication of the existing WiMAX terminal and solve the problems of relatively slower re-authentication of the existing WiMAX terminal and higher pressure of an AAA server. The method comprises the following steps: sending an authentication start message (namely an EAP-Start message) to an authentication client (such as Supplicant) by firmware (which can be a chip embedded in the terminal such as WiMAX chip); generating an authentication response message and sending the authentication response message to the AAA server by the authentication client; sending a challenge message of a preset algorithm to the authentication client by the AAA server; sending a response message of the preset algorithm corresponding the challenge message of the preset algorithm to the AAA server by the authentication client; and sending a successful authentication message to the authentication client by the AAA server, wherein the authentication response message carries the identification information of the terminal. In addition, the invention also provides a device for re-authenticating the terminal.
Owner:ZTE CORP
Internet-of-Things dynamic NTRU access authentication method based on time information
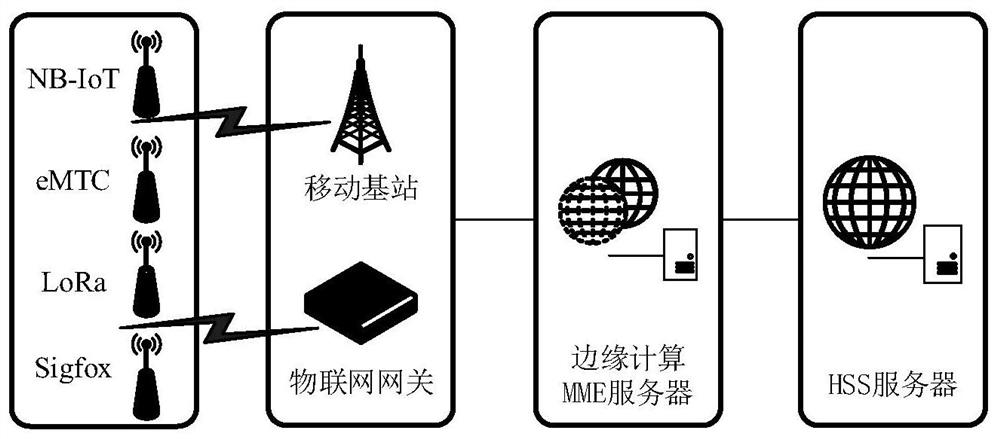
ActiveCN112601221AImprove securityReduce the amount of data interactionEncryption apparatus with shift registers/memoriesPublic key for secure communicationNetwork terminationTime information
The invention relates to the field of communication, in particular to an Internet-of-Things dynamic NTRU access authentication method based on time information, which comprises the following steps: asystem user HSS server sends initialization information, and power Internet-of-Things terminal equipment encrypts the initialization information by using an NTRU security encryption algorithm with anMD5 function to form authentication information containing the time information, and sends the authentication information to an edge computing MME server; after the edge computing MME server receivesthe authentication information, MD5 functions of three adjacent time points are calculated to achieve system synchronization, the edge computing MME server uses the MD5 functions for calculation to obtain returned authentication information, and the electric power Internet-of-Things terminal device compares and verifies the returned authentication information of the edge computing MME server and local information; and if verification succeeds, an encrypted secure channel is established.
Owner:ELECTRIC POWER RESEARCH INSTITUTE OF STATE GRID NINGXIA ELECTRIC POWER COMPANY
Screening module and screening method based on FPGA (Field Programmable Gate Array)
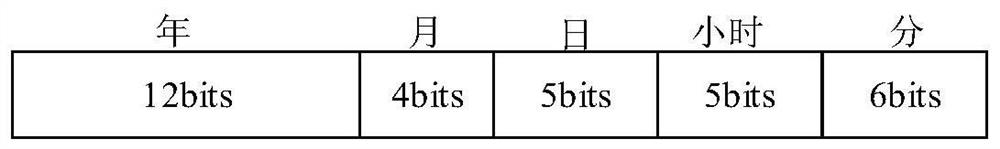
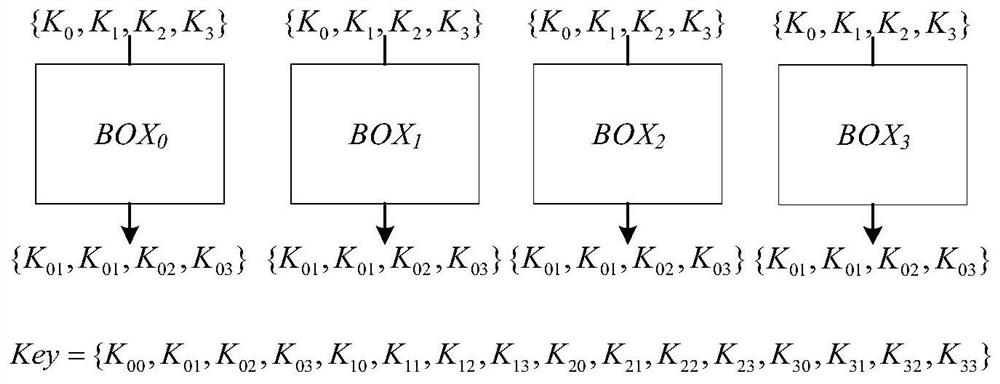
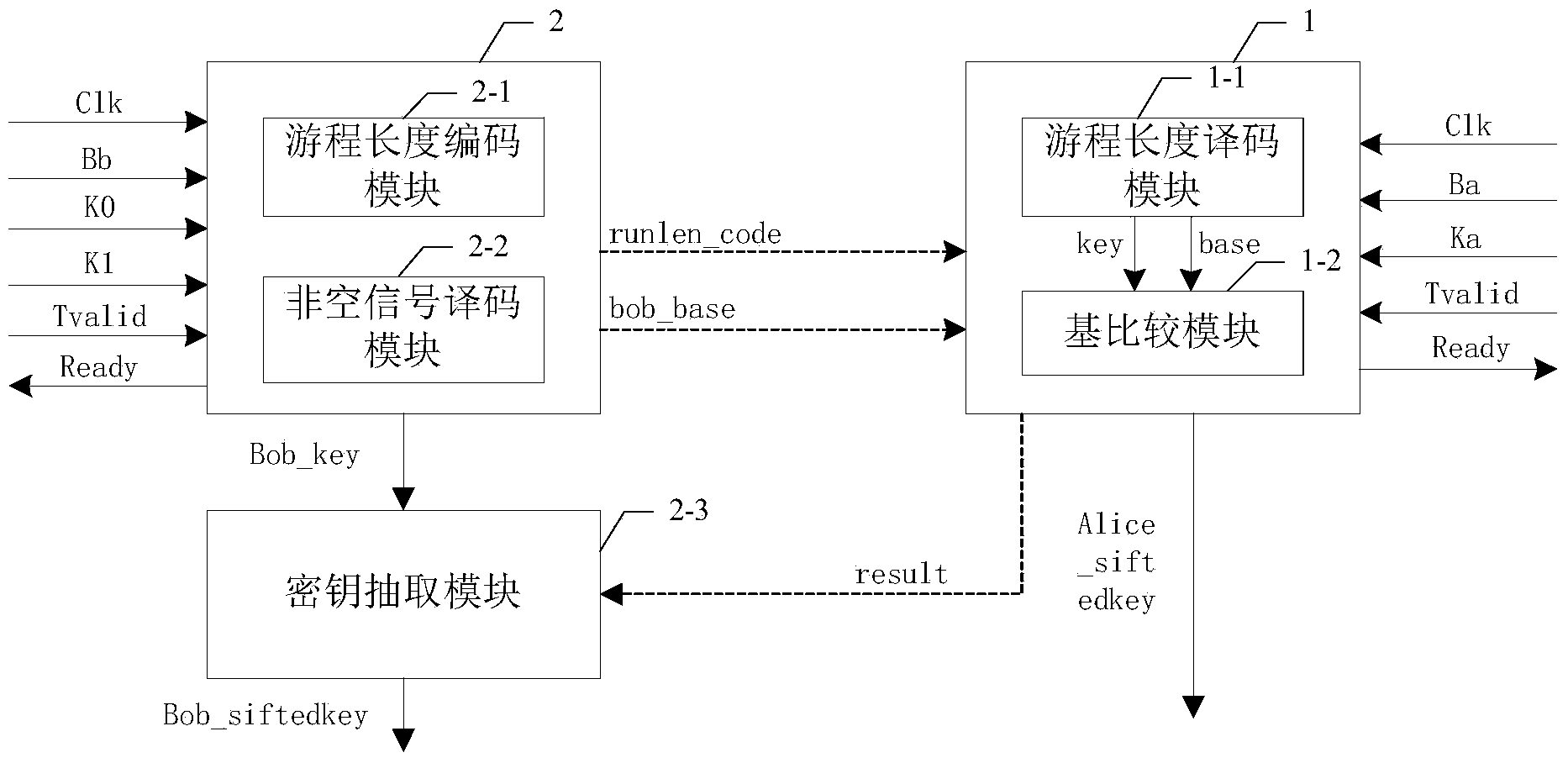
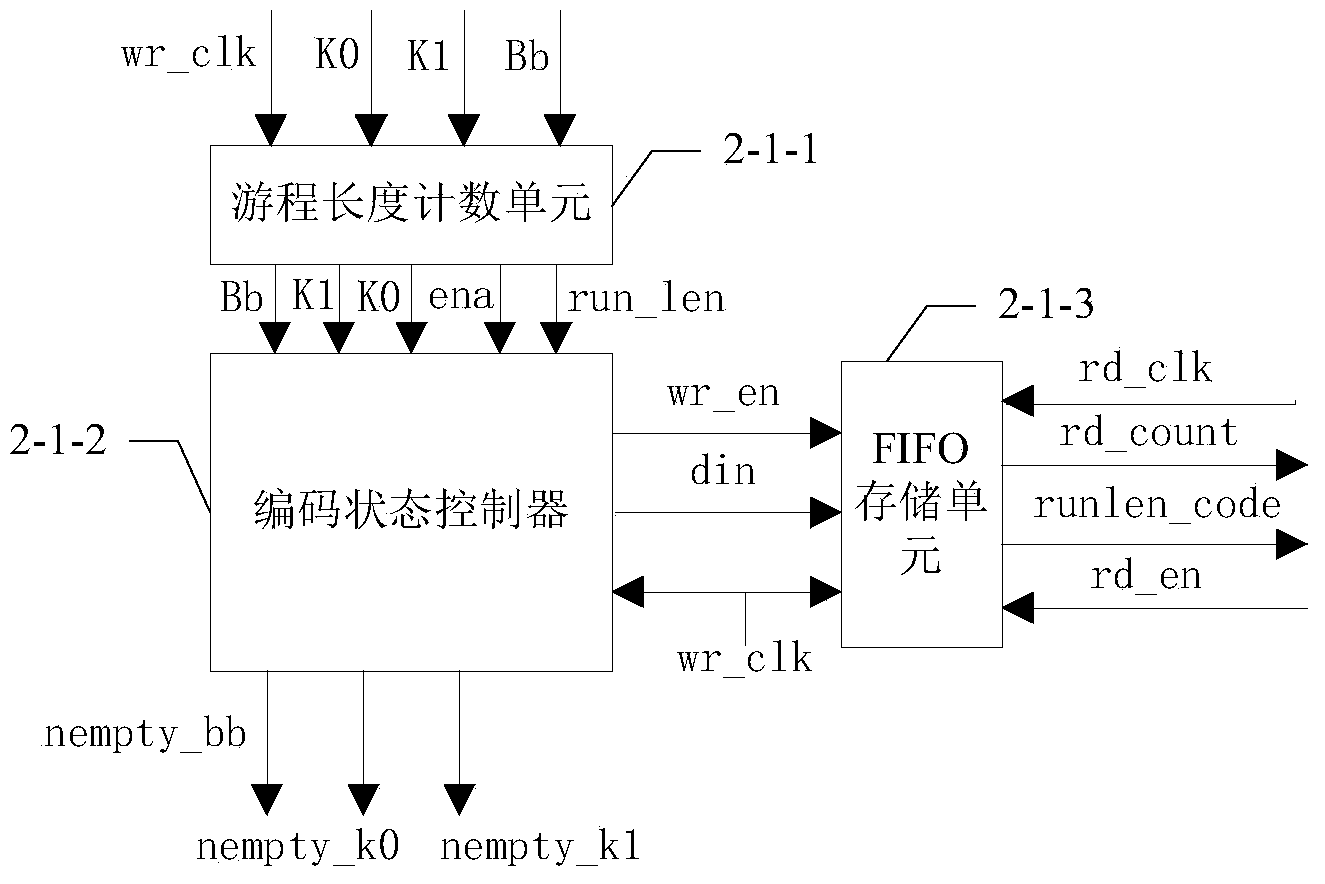
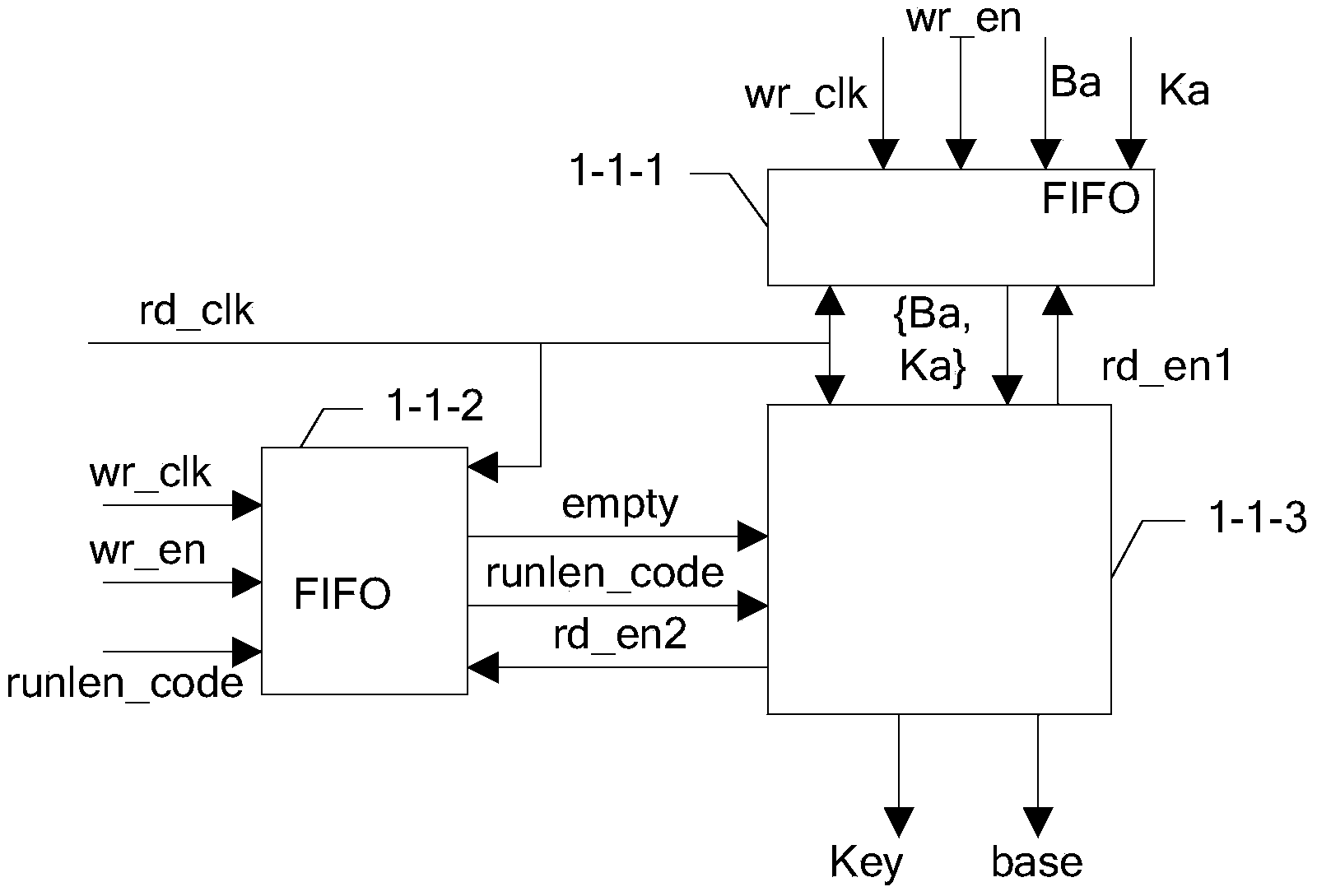
ActiveCN103825726AReduce the amount of interactive dataReduce storage pressureKey distribution for secure communicationRun-length encodingKey generation
The invention discloses a screening module and a screening method based on an FPGA (Field Programmable Gate Array), belonging to the field of quantum secret communication, for solving the problem that great storage burden is caused as the conventional screening module and the screening method are poor in real-time property of key generation velocity and large in data interaction. The screening method comprises the following steps: calculating the times that one of two adjacent events, which meets the condition that K is either 0 or 1 through a run length encoding module, wherein the two adjacent events both meet the condition that K is neither 0 nor 1, obtaining counting result run_1en, adding an identification bit to the counting result run_1en, subsequently conveying the counting result run_1en as a run length code run1en_code to an Alice module for processing to obtain a screening code Alice_siftedkey of the Alice module, further resulting the position information of the screening code Alice_siftedkey output from the Alice module to a key extract module in a Bob module, further extracting and outputting a screening code Bob_siftedkey from a valid naked code Bob_key according to the position information result of the screening code Alice_siftedkey, and outputting the screening code to the Bob module through the screening code Bob-siftedkey. The screening module and the screening method are applicable to the field of key screening in quantum secret communication.
Owner:深圳数安智行科技有限公司
Safety management and control system and method for capital construction site
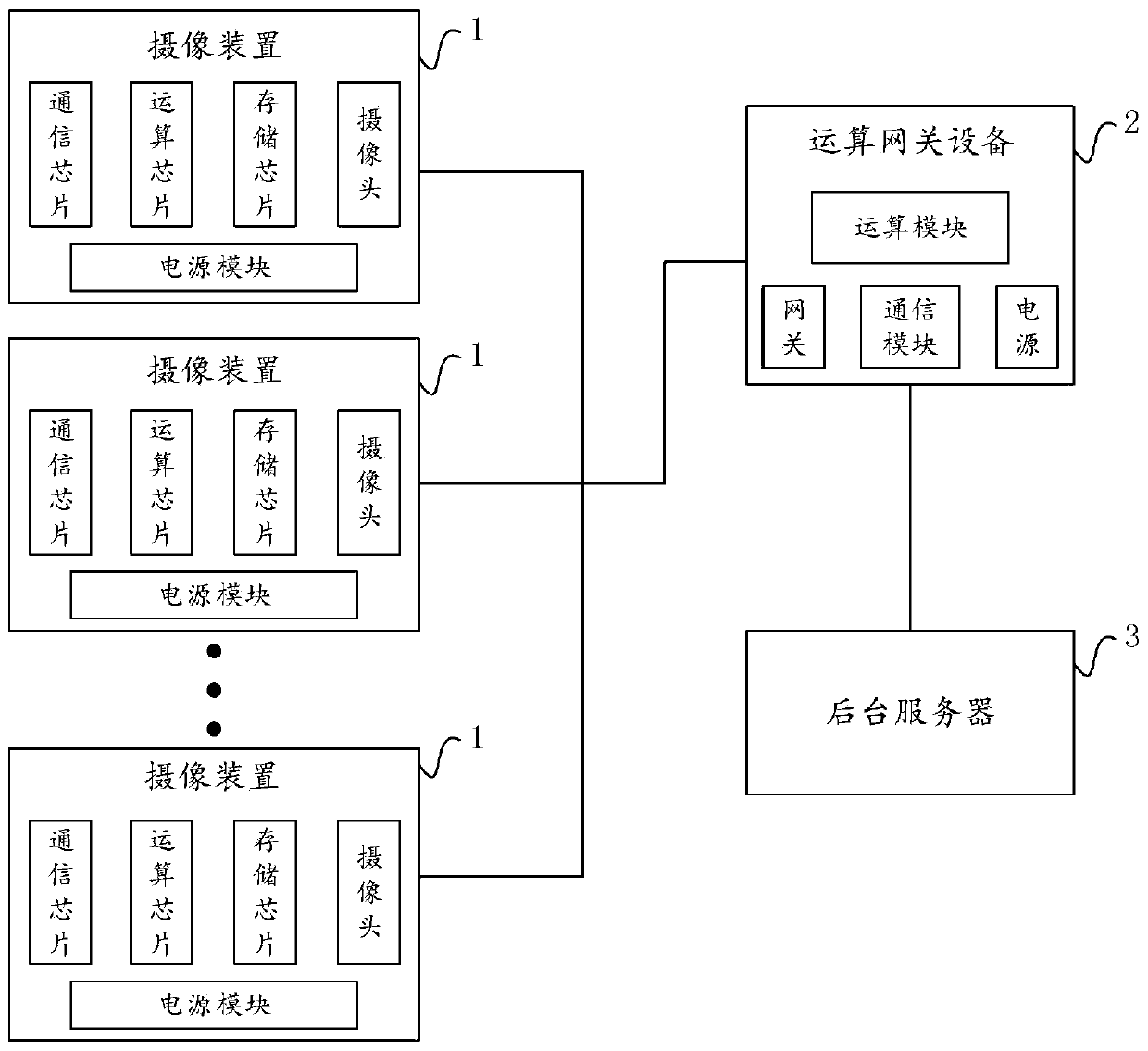
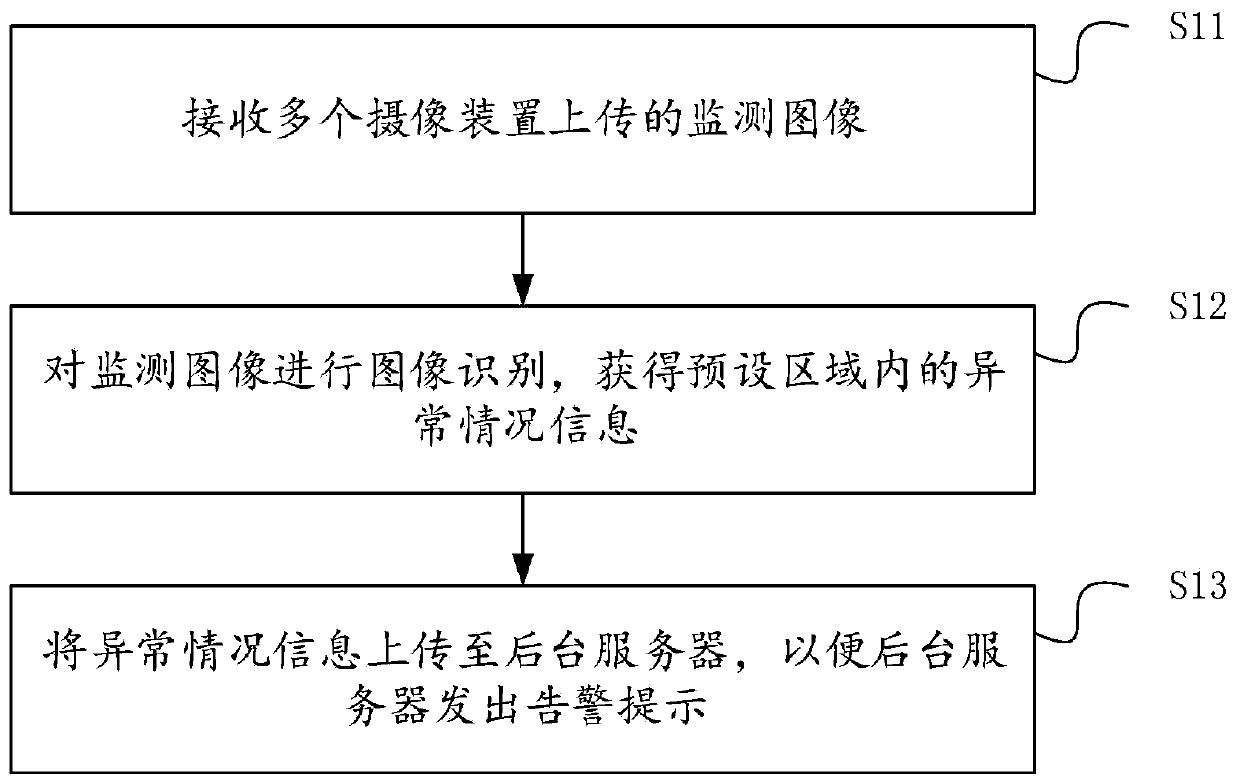
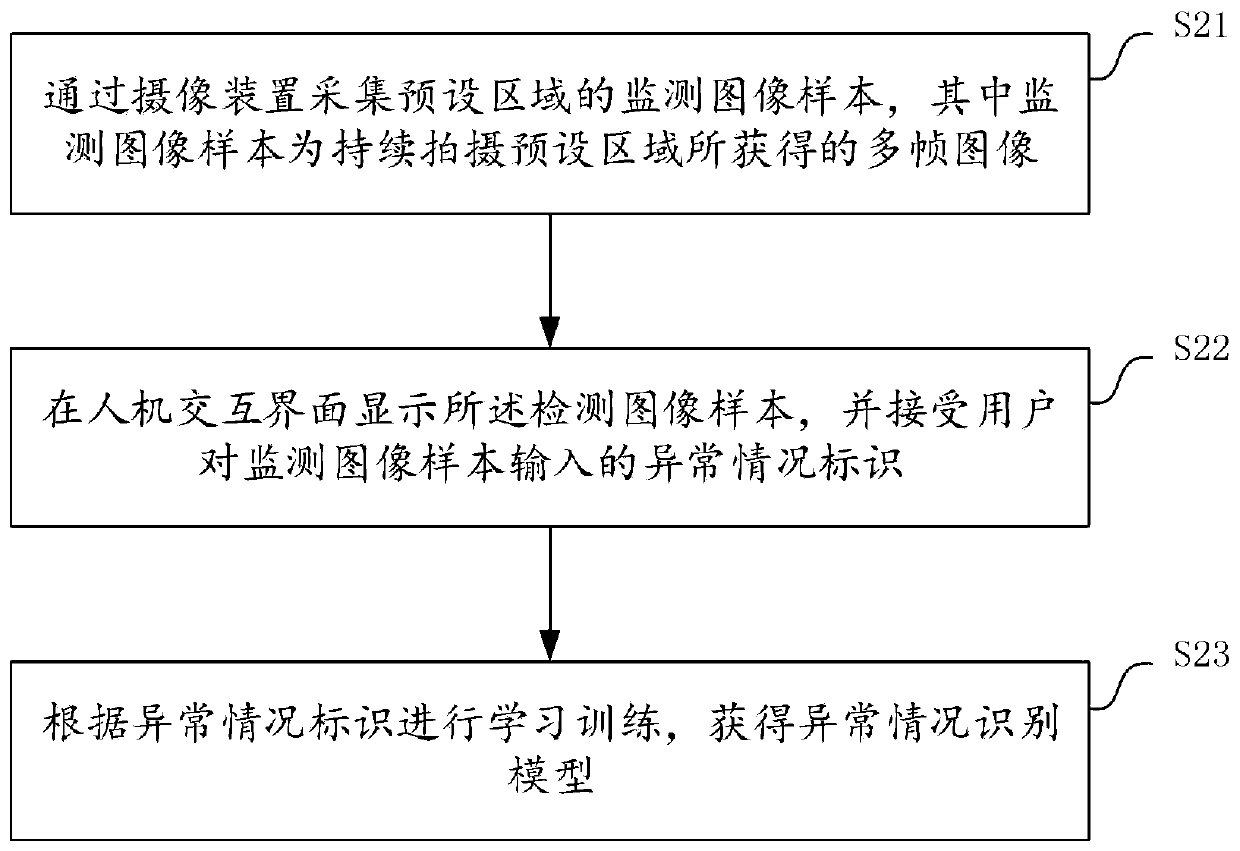
PendingCN110287917ALower requirementReduce processingData processing applicationsCharacter and pattern recognitionControl systemSafety control
The invention discloses a safety management and control system for a capital construction site, and the system comprises a camera device which is used for shooting a monitoring image of a preset area of the capital construction site in real time, and uploading a monitoring image which is shot subsequently to operation gateway equipment if the monitoring image of the current frame is different from a pre-stored image; the operation gateway equipment is used for carrying out image recognition on the received monitoring image, obtaining abnormal condition information in a preset area and uploading the abnormal condition information to the background server; and the background server sends an alarm prompt according to the abnormal condition information. The safety management and control system is simple in equipment structure, easy to configure and install, low in operation and use cost and capable of being repeatedly used on a plurality of capital construction sites, the safety maintenance cost of the capital construction sites is reduced to a great extent, and urbanization is facilitated. The invention further provides a safety control method for the capital construction site, and the safety control method has the above beneficial effects.
Owner:GUANGDONG POWER GRID CO LTD +1
Method and system for processing multi-user parallel signalling tracking at client
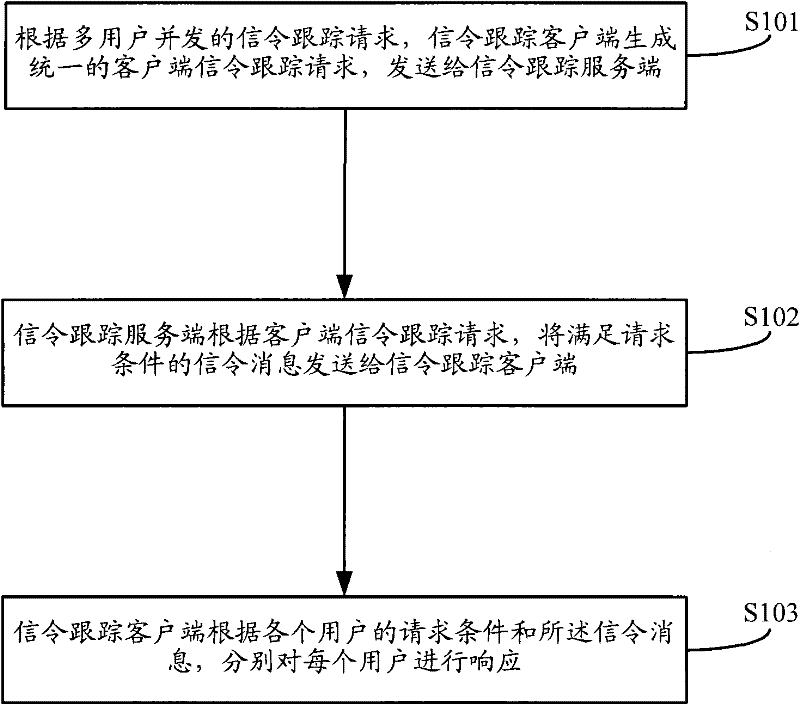
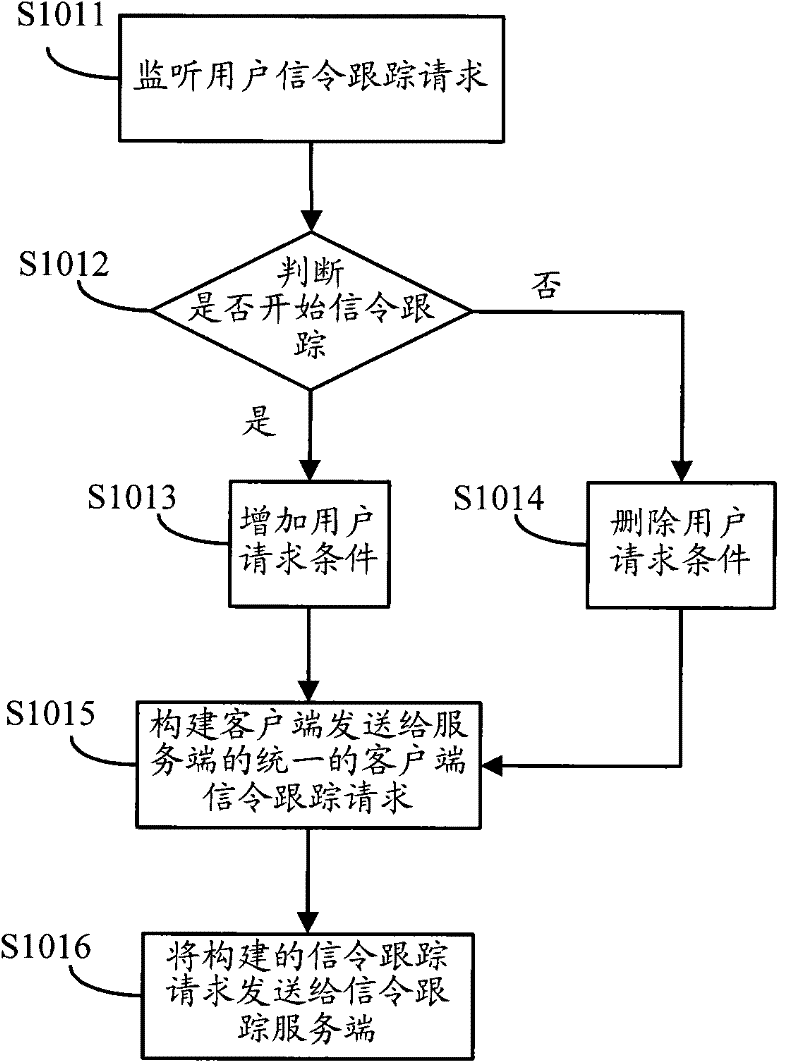
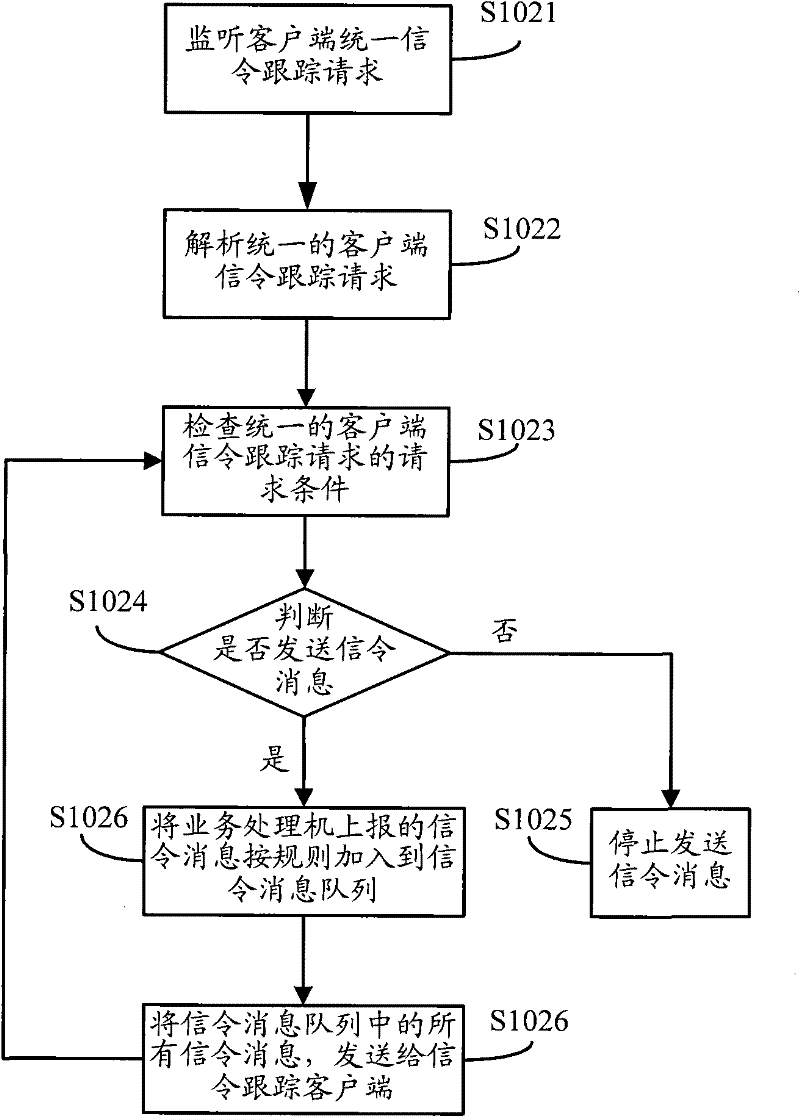
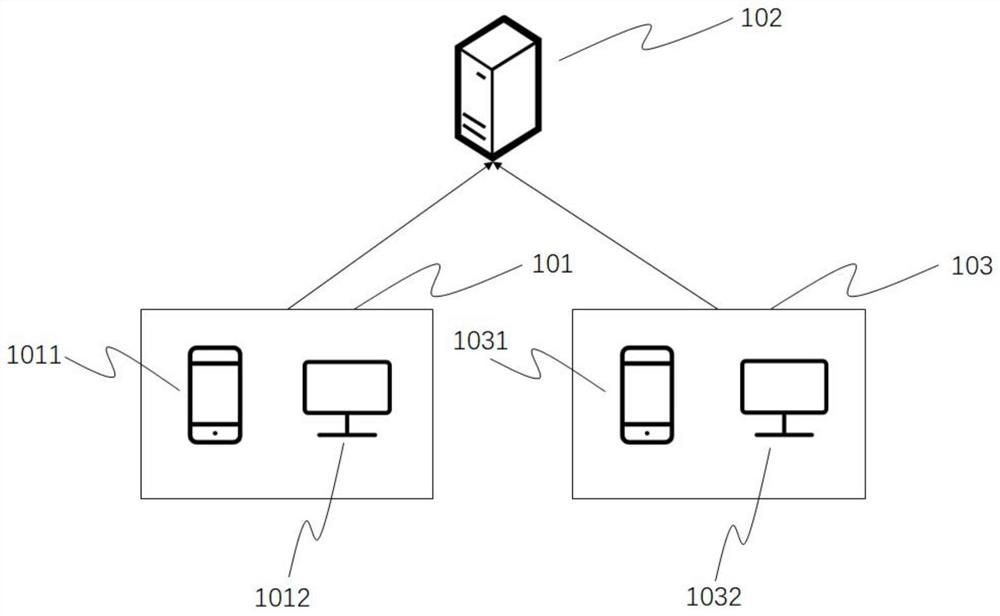
ActiveCN102238505AEasy to handleReduce the amount of data interactionServices signallingCommunication linkClient-side
The invention discloses a method and a system for processing multi-user parallel signalling tracking at a client. The method comprises the following steps that: a signalling tracking client generates a uniform signalling tracking request of the client according to signalling tracking requests initiated in parallel by multiple users and sends the uniform signalling tracking request of the client to a signalling tracking serving end; the signalling tracking serving end sends a signalling message, which is matched with the request condition, to the signalling tracking client according to the signalling tracking request of the client; and the signalling tracking client responds to each user respectively according to the request condition of each user. When multiple users initiate parallel signalling tracking requests to the signalling tracking client, the method disclosed by the invention reduces interactive data traffic of a communication link between the signalling tracking client and the serving end by sending the uniform signalling tracking request of the client intensively; the signalling tracking serving end only responds to the uniform signalling tracking request of the client; and the processing performance of the serving end is improved.
Owner:ZTE CORP
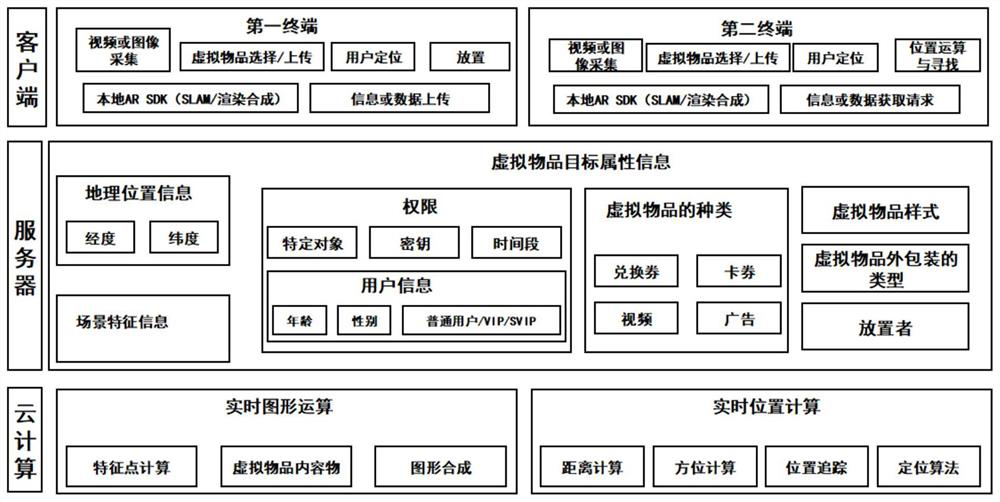
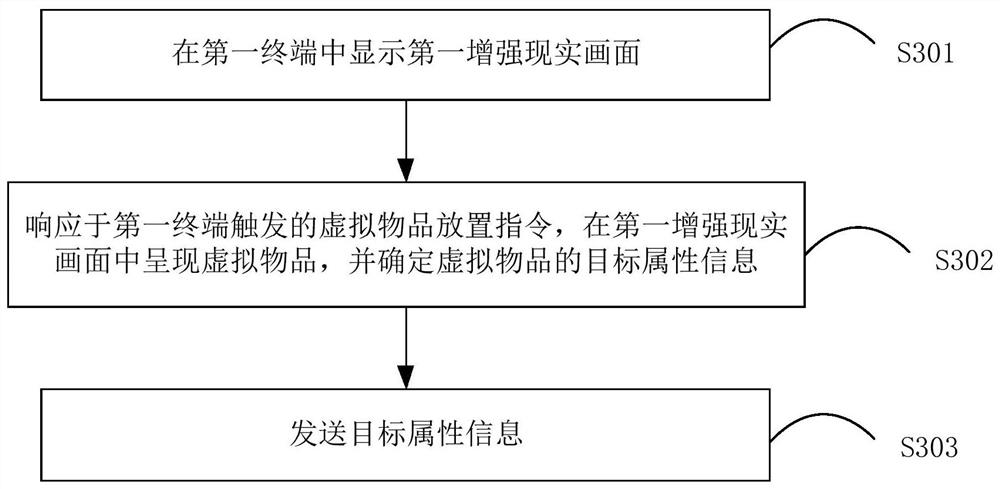
Interaction method and device based on virtual article and storage medium
PendingCN112330819AReduce the amount of data interactionReduce computing burdenImage data processingInput/output processes for data processingHuman–computer interactionServer
The invention discloses an interaction method and device based on a virtual article and a storage medium. The method comprises the steps of: displaying a first augmented reality picture in a first terminal; in response to a virtual article placement instruction triggered by the first terminal, presenting a virtual article in the first augmented reality picture, and determining target attribute information of the virtual article, wherein the target attribute information comprises first geographic position information of a placement place of the virtual article and first scene feature information when the virtual article is placed; and sending the target attribute information. According to the embodiment of the invention, the placement of the virtual article is realized through the first terminal, the searching and receiving of the virtual article are realized through the target attribute matching of the second terminal, and the server, the remote monitoring terminal and the like store the target attribute information and forward the data, so that the operation burden and pressure of the server, the remote monitoring terminal and the like are reduced, and richer user interaction experience is provided, and the method can be widely applied to the technical field of computers.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Information synchronization method and device
InactiveCN109364480AReduce the amount of data interactionSave bandwidthVideo gamesHuman–computer interactionComputer terminal
Owner:HANGZHOU ELECTRONICS SOUL NETWORK TECH
Smart card and working method of smart card
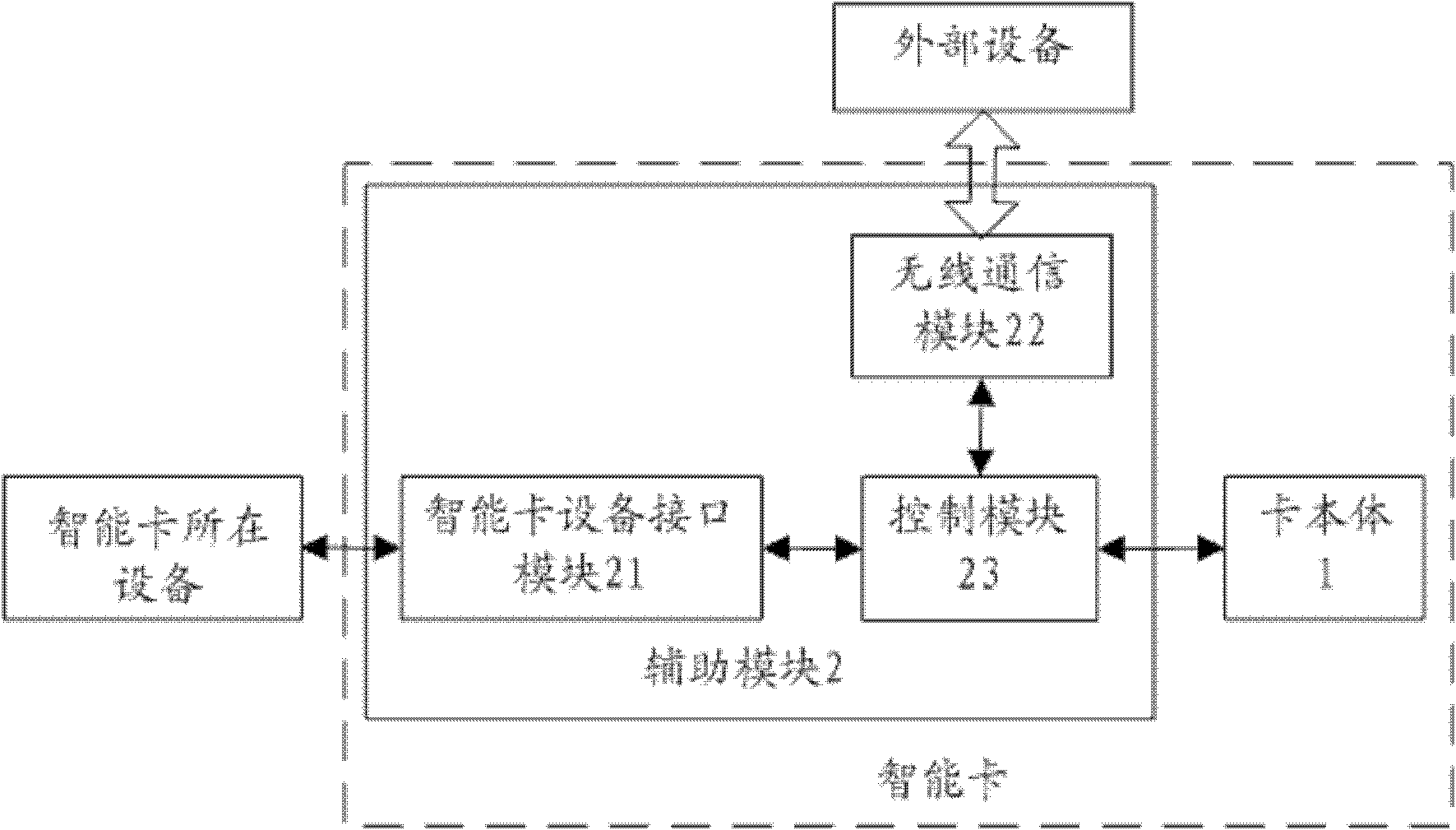
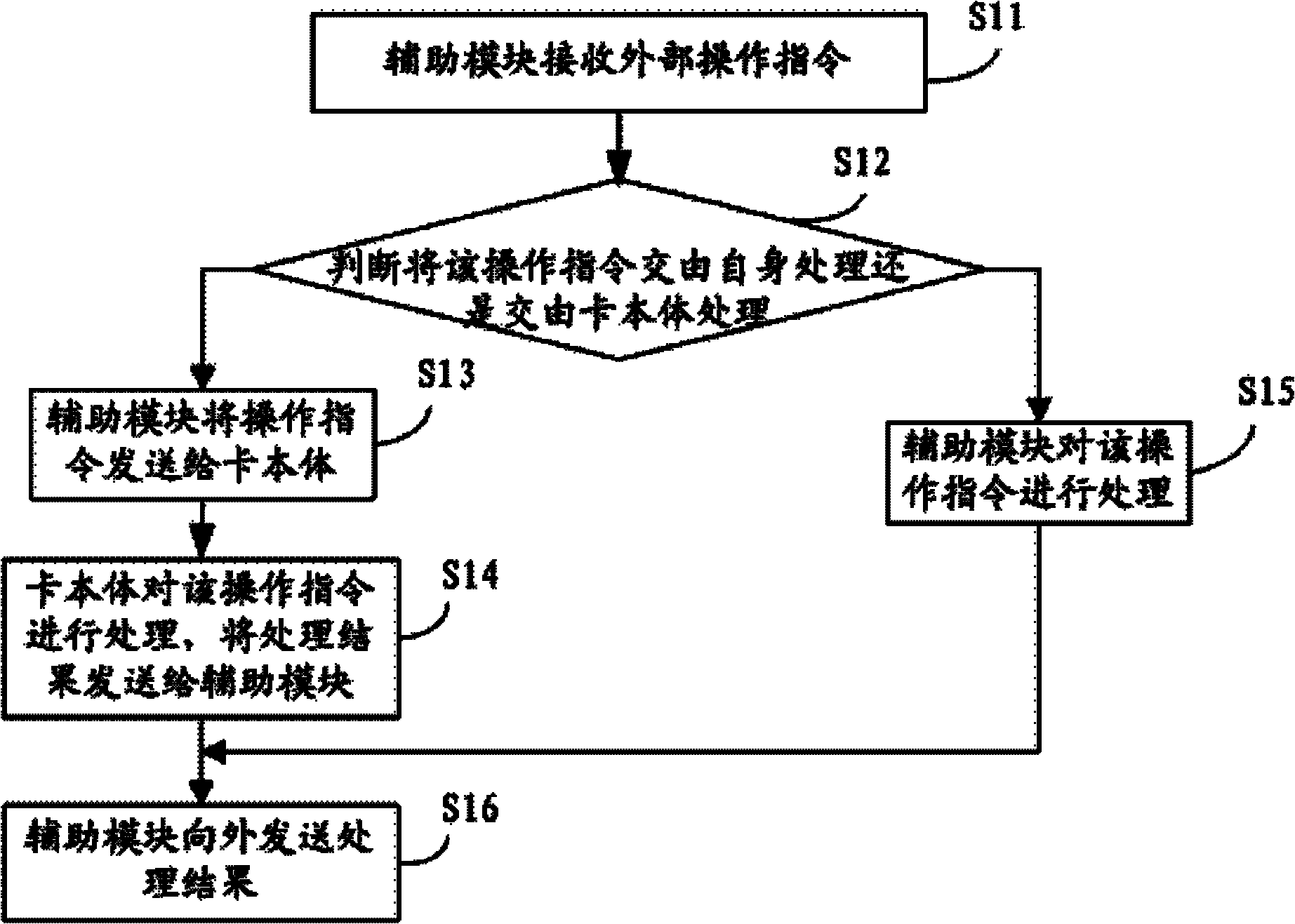
InactiveCN103186804AExpand mobile payment application functionalityReduce the amount of data interactionRecord carriers used with machinesComputer moduleSmart card
The invention discloses a smart card and a working method of the smart card. The smart card comprises a card body and an auxiliary module connected with the card body, wherein the auxiliary module is used for receiving an operational order and judges whether the operational order is given to the auxiliary module or the card body for processing; if the operational order is given to the card body for processing, the auxiliary module sends the operational order to the card body; if the operational order is given to the auxiliary module for processing, the auxiliary module processes the operational order; the auxiliary module sends a processed result outside after the processing by the auxiliary module or the card body is completed, and the card body is used for receiving the operational order transmitted by the auxiliary module, processes the operational order, and transmits the processed result to the auxiliary module.
Owner:NATIONZ TECH INC
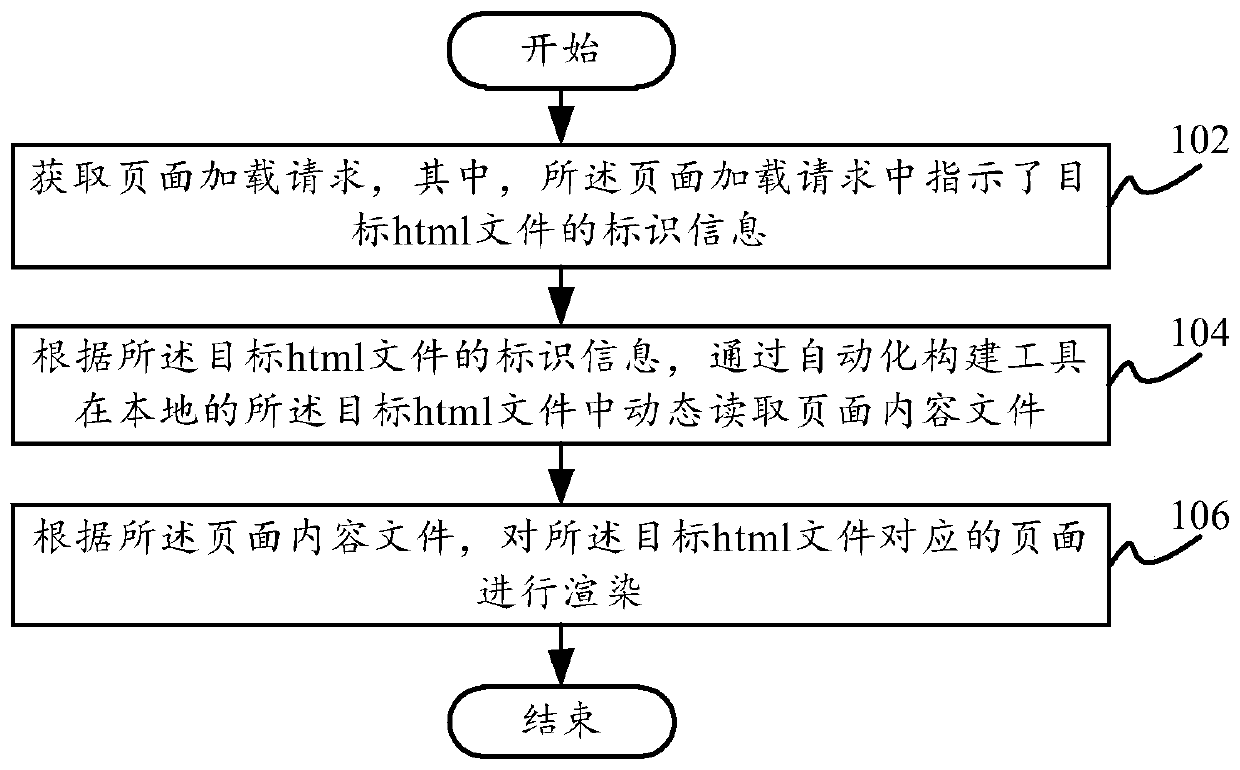
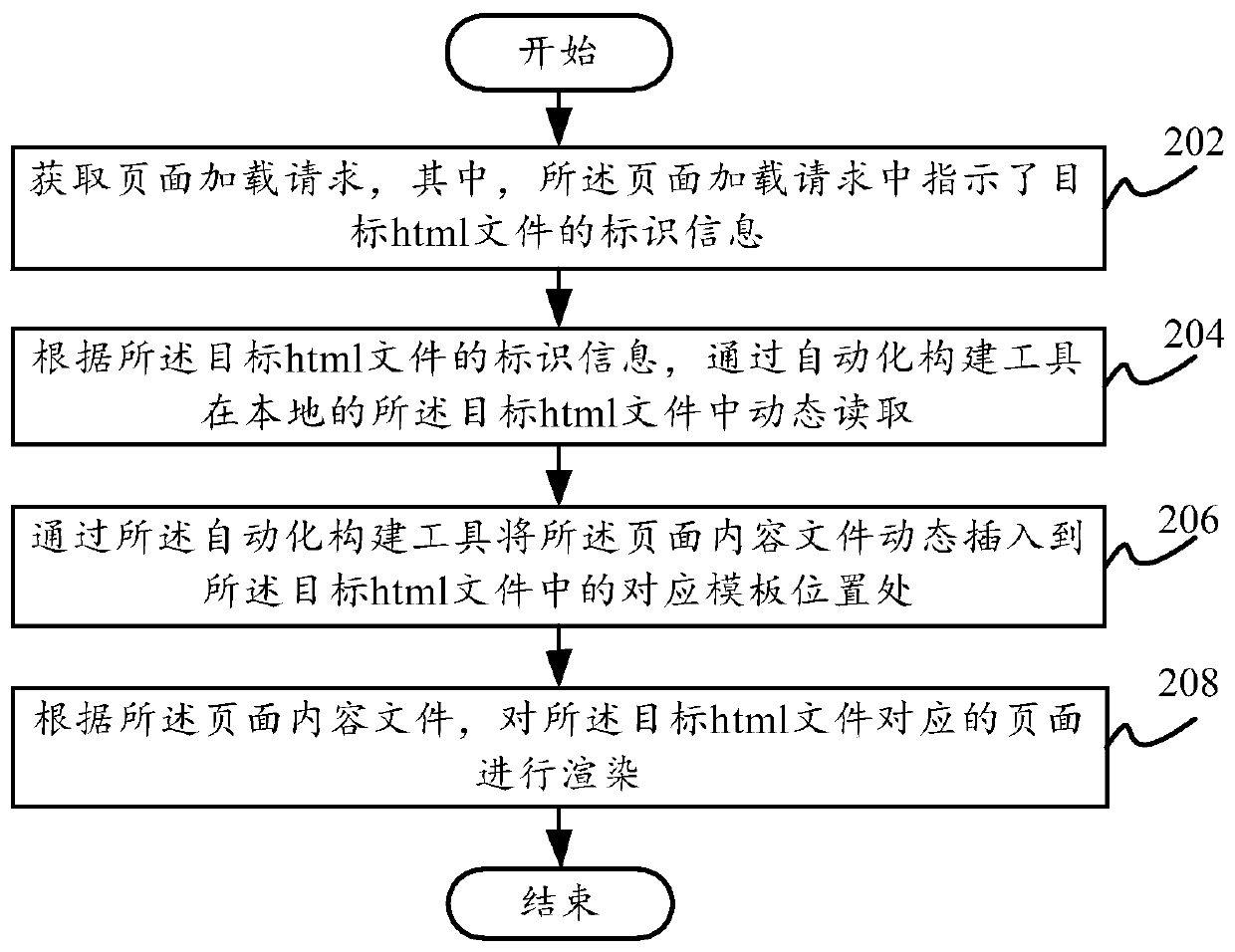
Page loading method and device, electronic equipment and computer readable storage medium
PendingCN109783752AHigh speedReduce the amount of data interactionWebsite content managementComputer scienceDatabase
The invention provides a page loading method and device, electronic equipment and a computer readable storage medium, and relates to the technical field of research and development management, the method comprises the following steps: obtaining a page loading request, the page loading request indicating identification information of a target html file; Dynamically reading a page content file fromthe local target html file through an automatic construction tool according to the identification information of the target html file; And according to the page content file, rendering a page corresponding to the target html file. According to the technical scheme provided by the invention, the technical scheme that the webpage reads the data in the local html file repalces the technical scheme that the webpage requests data from the outside in the related technology. data interaction between the webpage and the outside is reduced, the webpage can obtain the webpage content file more quickly,the webpage rendering and loading process is simplified, the overall time of webpage loading can be saved, the burden of the webpage is reduced, and the user experience is improved.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
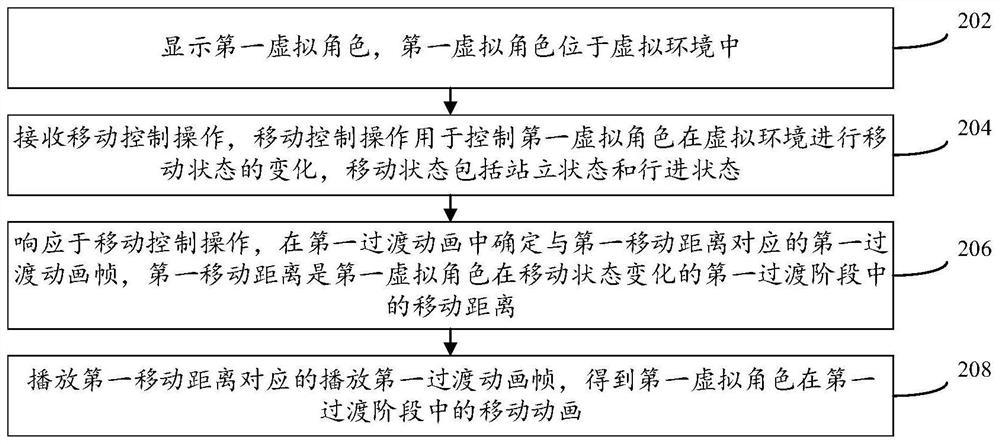
Virtual character control method and device, equipment and medium
ActiveCN113209618AReduce computing pressureReduce the amount of data interactionVideo gamesAnimationEngineering
The invention discloses a virtual character control method and device, equipment and a medium, and is applied to the field of virtual world. The method comprises the following steps: displaying a first virtual character in a virtual environment; receiving a movement control operation used for controlling the first virtual character to change the movement state in the virtual environment, wherein the movement state comprises a standing state and an advancing state; in response to the movement control operation, determining a first transition animation frame corresponding to a first movement distance in a transition animation, the first movement distance being a movement distance of the first virtual character in a first transition stage of the movement state change; and playing the first transition animation frame corresponding to the first moving distance to obtain a moving animation of the first virtual character in the first transition stage. According to the method, on the premise that the calculation pressure of the server is small, the change of the moving state of the virtual character is natural.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Processing unit and information processing method
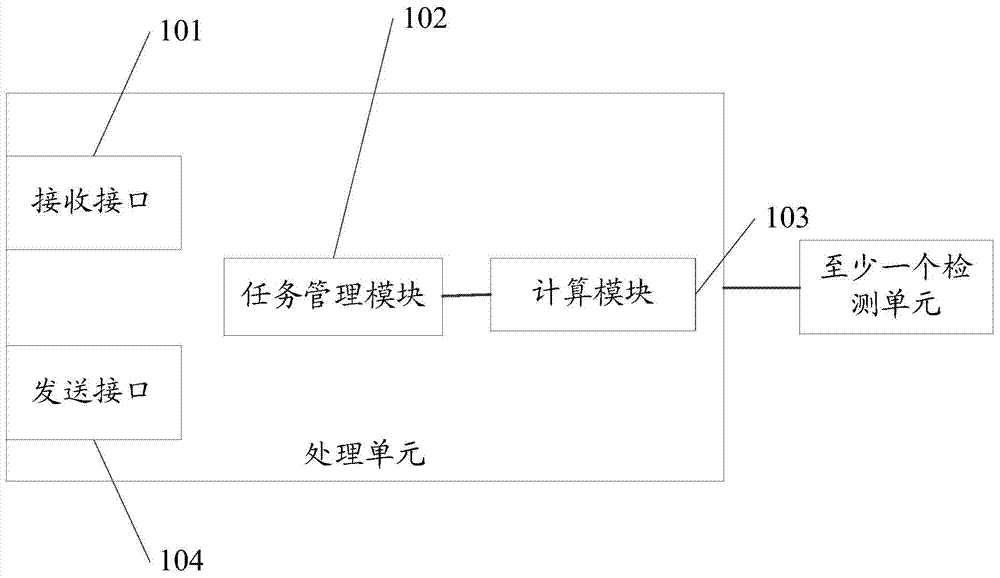
ActiveCN104750474AImprove unitySolve technical problems with a large amount of data interactionInput/output for user-computer interactionGraph readingInformation processingTask management
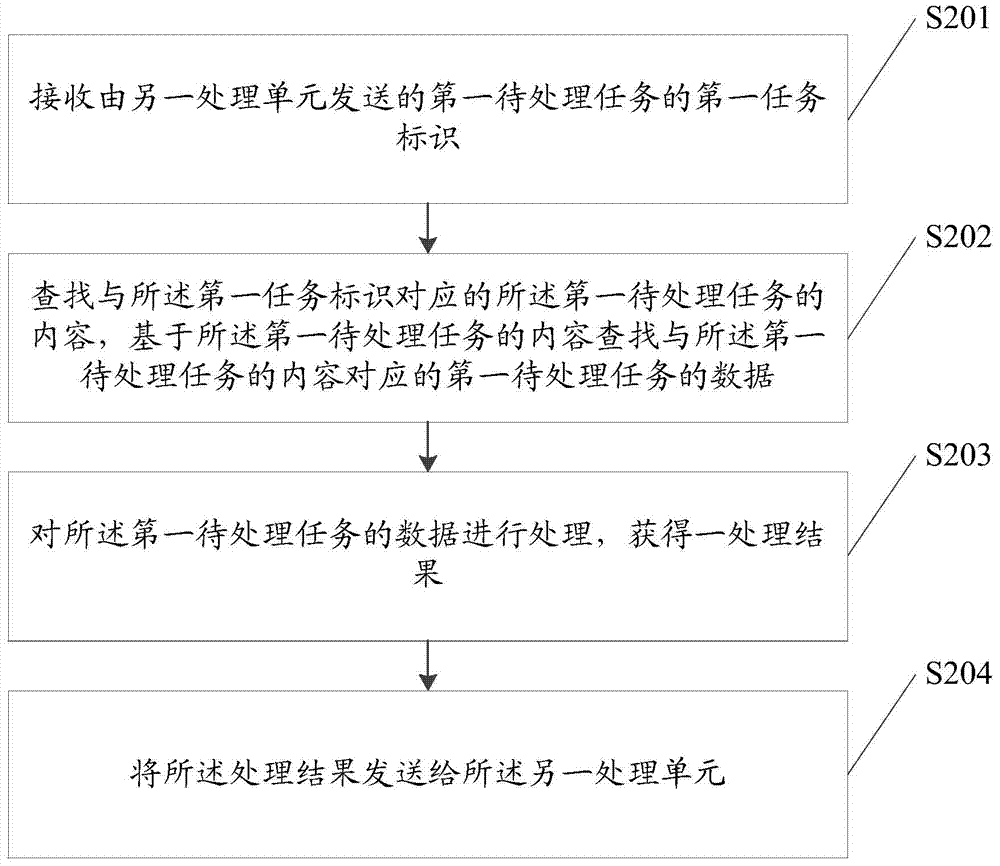
The invention discloses a processing unit. The processing unit is connected with at least one detecting unit and is characterized by comprising a receiving interface, a task management module, a computation module and a sending interface, wherein the receiving interface is used for receiving a first task identifier of a first to-be-processed task sent by another processing unit, the task management module is used for searching content of the first to-be-processed task corresponding to the first task identifier and searching data, corresponding to the content of the first to-be-processed task, of the first to-be-processed task on the basis of the content of the first to-be-processed task, the computation module is connected with the task management module and used for processing the data of the first to-be-processed task to acquire a processing result, and the sending interface is used for sending the processing result to another processing unit.
Owner:LENOVO (BEIJING) LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com