Distributed cloud storage data integrity protection method
A data integrity and cloud storage technology, applied in the field of cloud computing security, can solve problems such as difficulties, achieve high confidence, reduce computing overhead, and reduce storage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
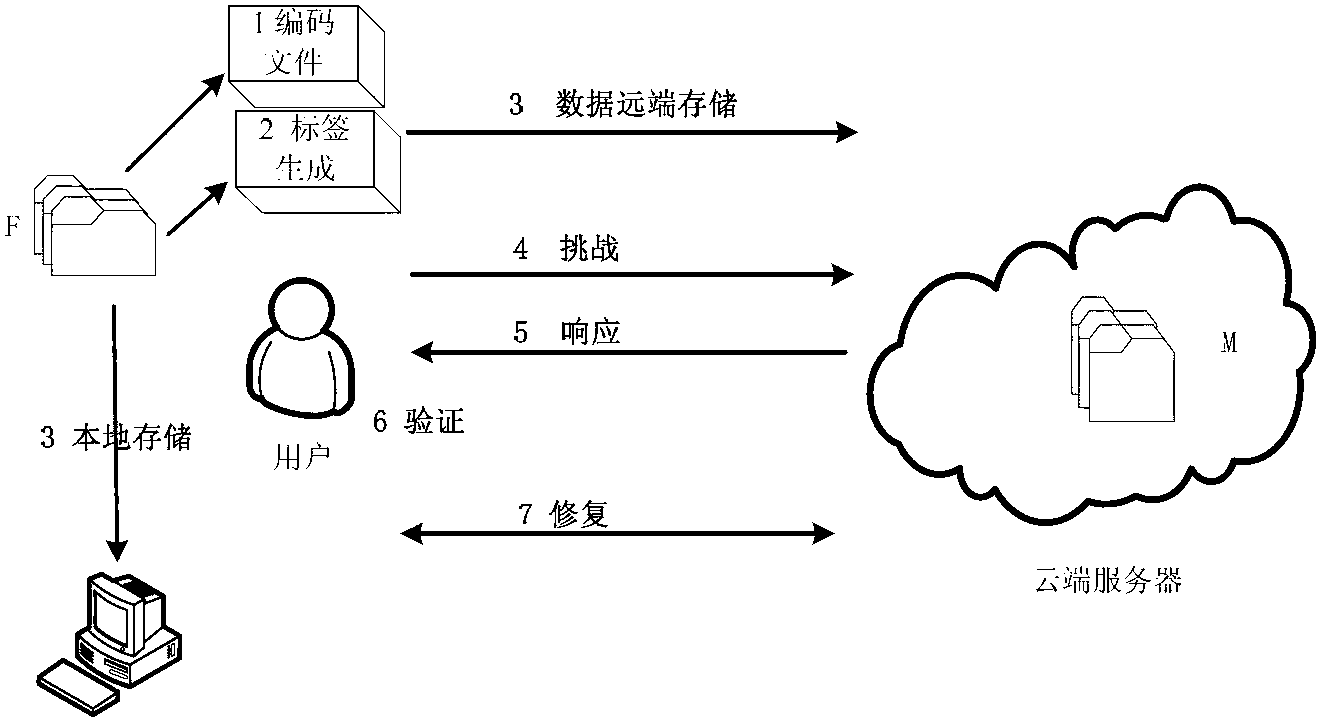
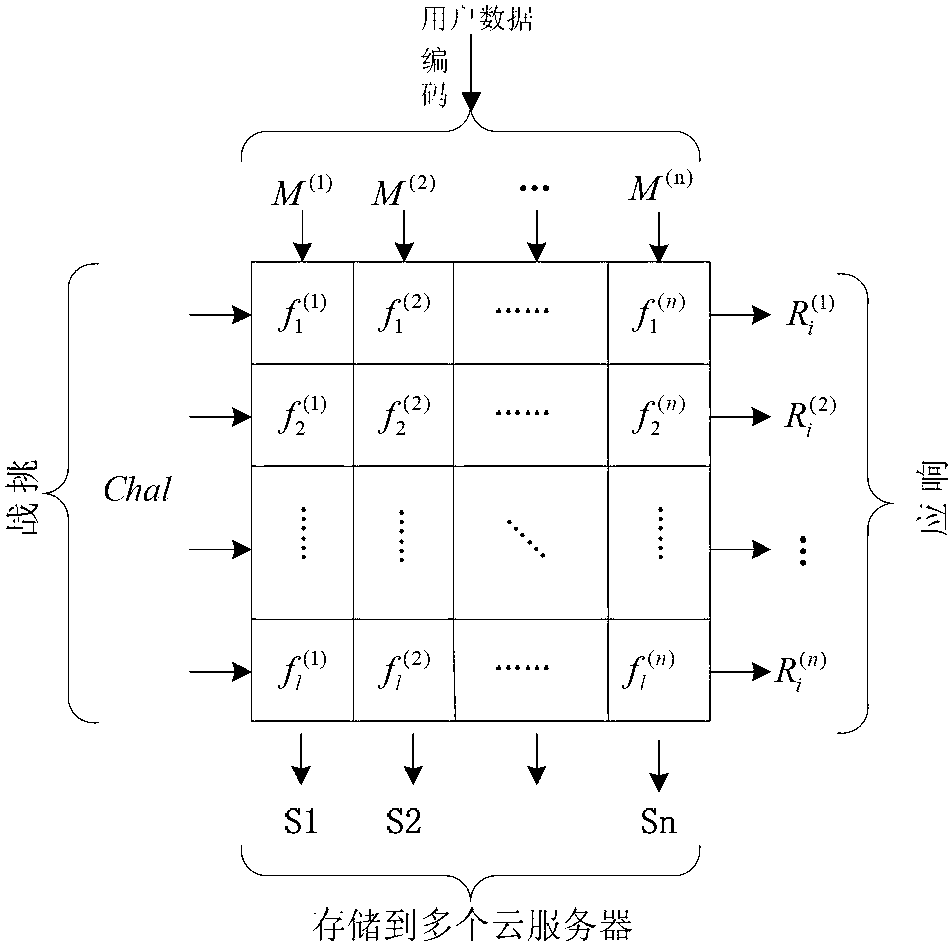
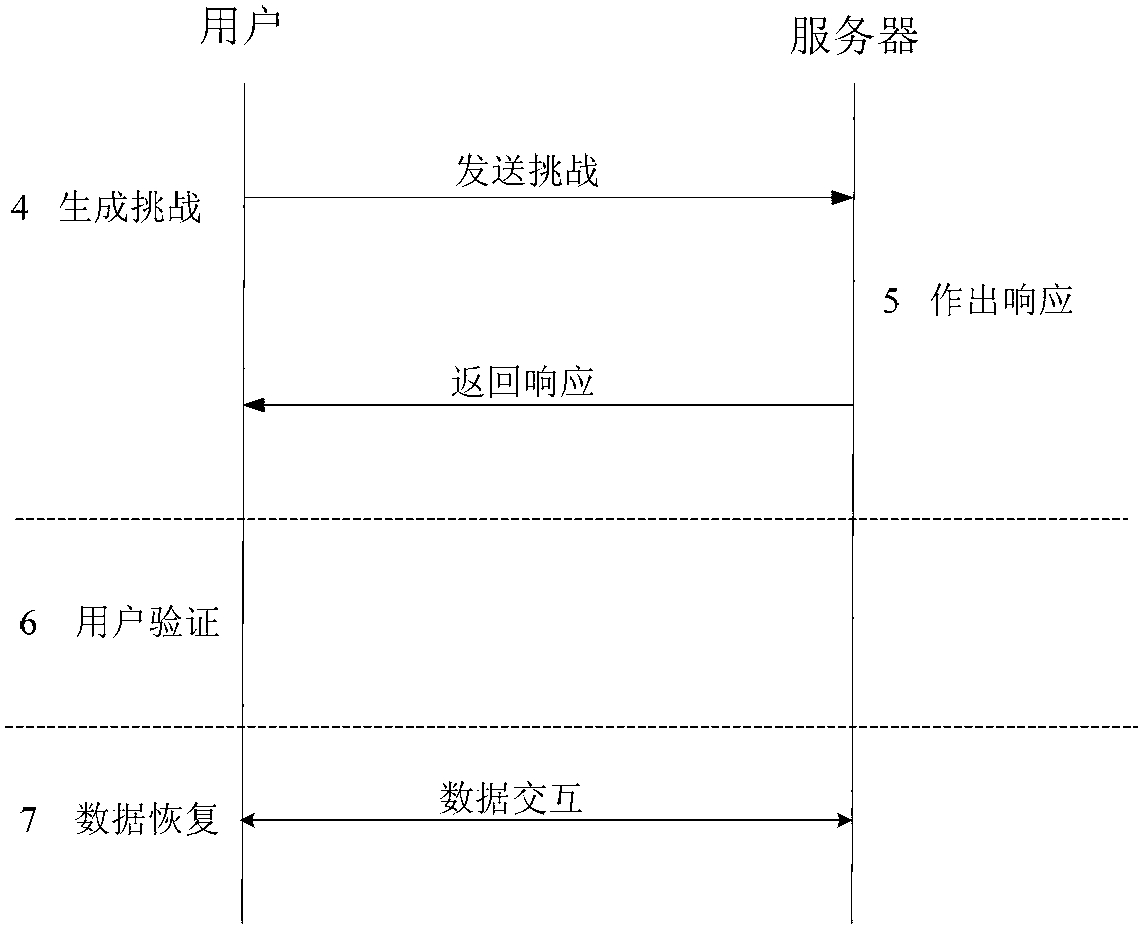
[0034] The integrity protection method described will be described in detail below in conjunction with the accompanying drawings, figure 1 It is a flow chart of the present invention; figure 2 It is a schematic diagram of distributed storage after data preprocessing in the present invention; image 3 It is an interaction diagram of the challenge-response mechanism of the present invention.
[0035] Main symbols and algorithm explanations:
[0036] (1) F represents the user's original data, and M represents the encoded data, including n×l data blocks. is the i-th block of the j-th data vector, which will be stored in the server S j ·G * =(I (n-r)×(n-r) |P T ) represents the generation matrix of the Goppa code, where P is the generation matrix of the redundancy check block; M * Represents the data blocks stored in error in the server.
[0037] (2) E() and D() are the encryption algorithm and decryption algorithm of the Paillier cipher algorithm respectively, k 1 is it...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com