Patents
Literature
39results about How to "Reduce interaction steps" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
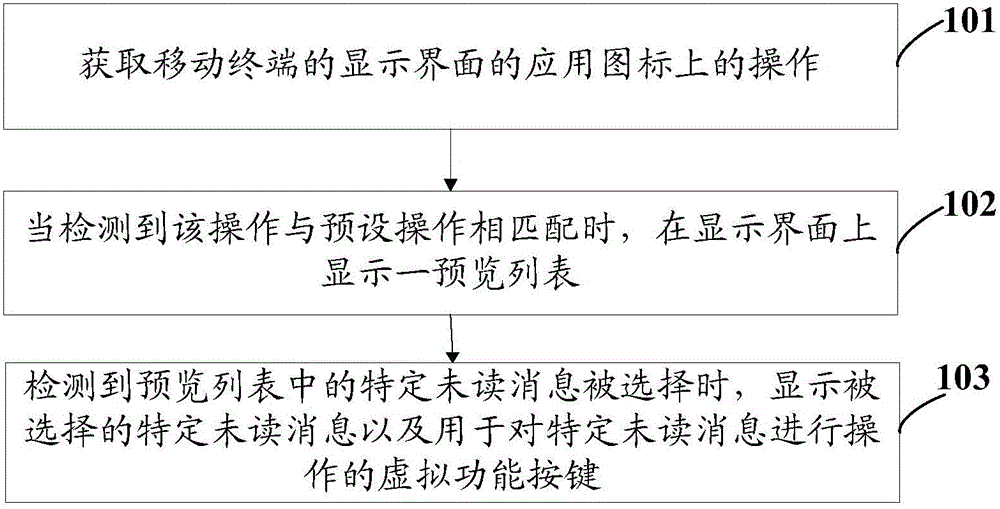
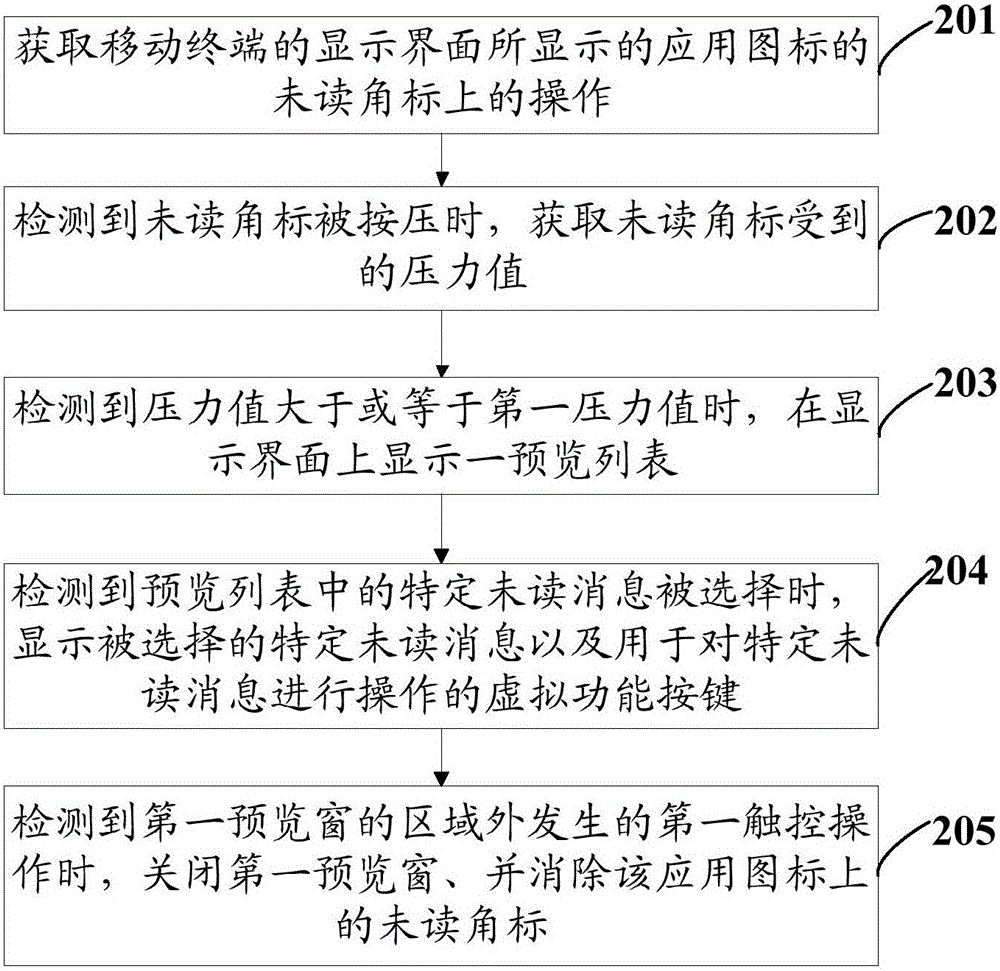
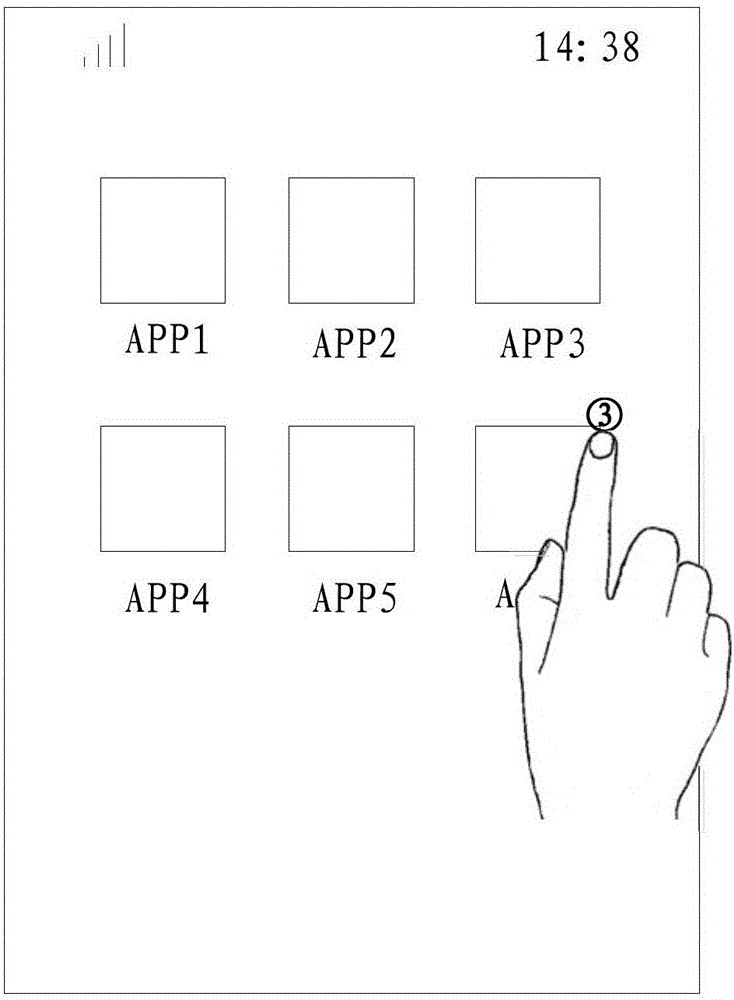
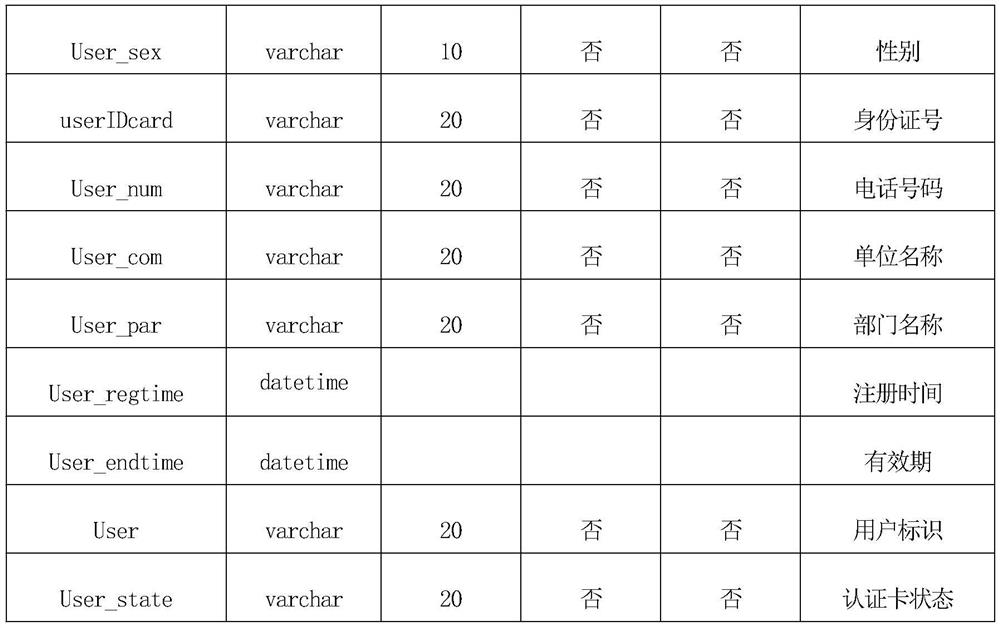
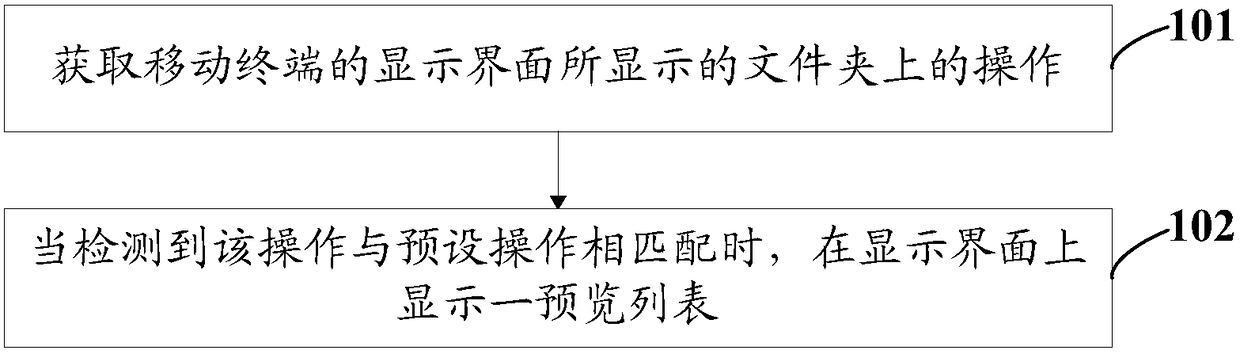
Operation method and mobile terminal for unread messages
ActiveCN106020613AImprove processing efficiencyEasy to operateInput/output processes for data processingComputer hardwareProcess efficiency
The invention discloses an operation method and a mobile terminal for unread messages. The method comprises following steps: obtaining operation on application icons of a display interface of the mobile terminal; display a pre-viewed list on the display interface when detecting operation is matched with pre-set operation, wherein the pre-viewed list comprises a set of unread messages of application programs corresponding to application icons; and displaying selected specific unread messages when detecting that specific unread messages are selected in the pre-viewed list and also displaying virtual function buttons for operation on specific unread messages. The operation method and the mobile terminal for unread messages have following beneficial effects: without entering the application programs, unread messages can be viewed and processed; operation is performed easily; interaction steps are few; and processing efficiency of unread messages is greatly increased.
Owner:VIVO MOBILE COMM CO LTD
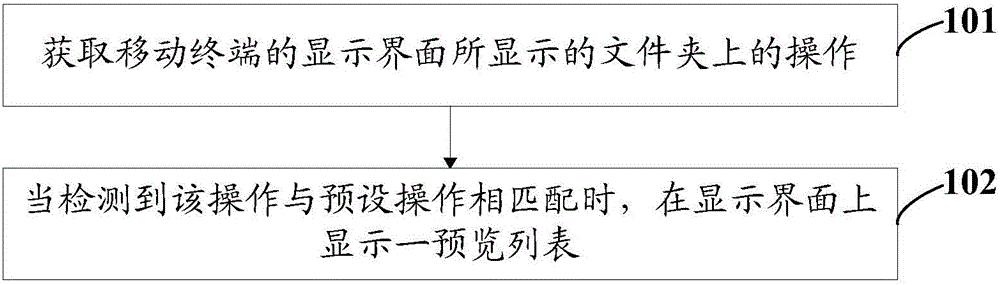
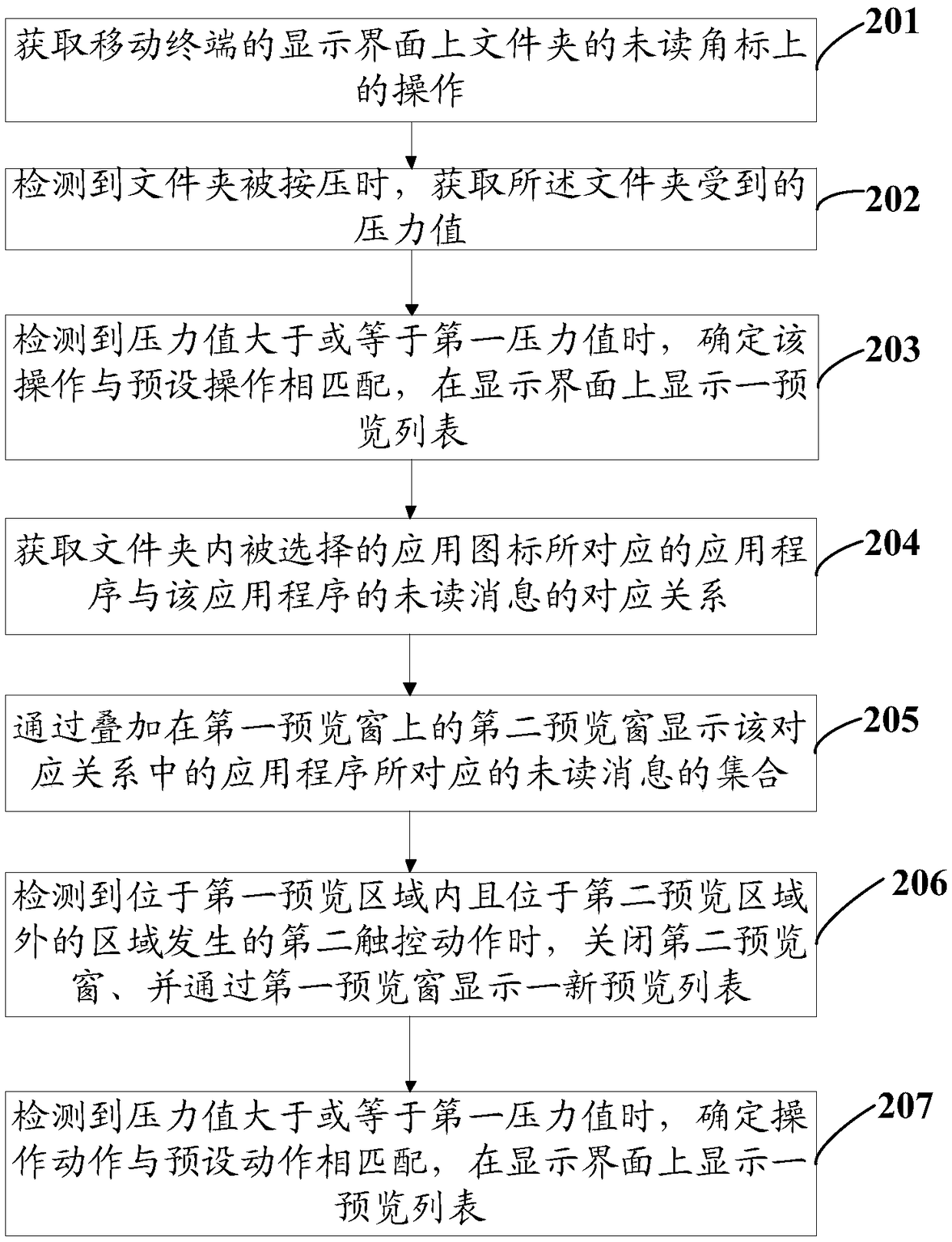
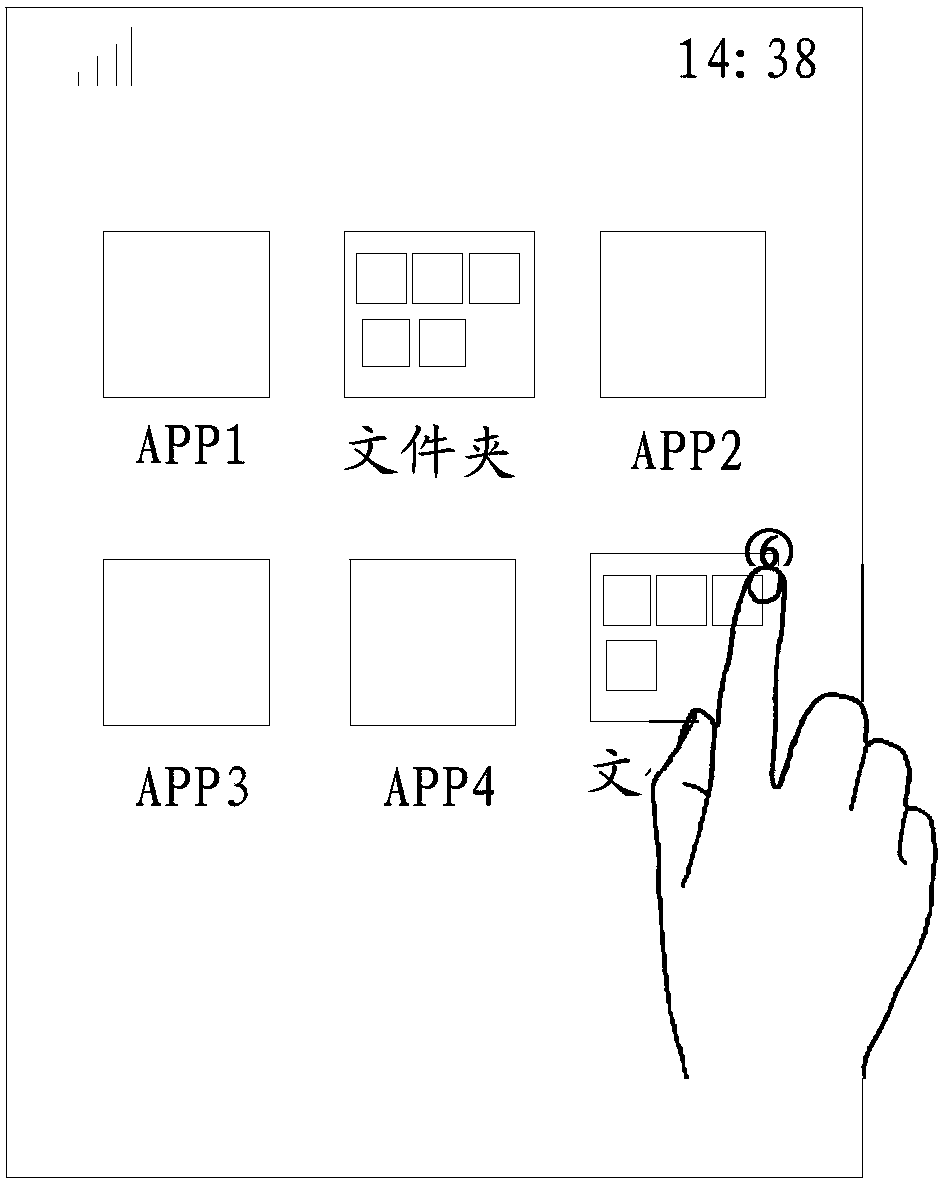
Operating method for folder and mobile terminal
ActiveCN106055195AImprove processing efficiencyEasy to operateFile/folder operationsSpecial data processing applicationsProcess efficiencyComputer terminal
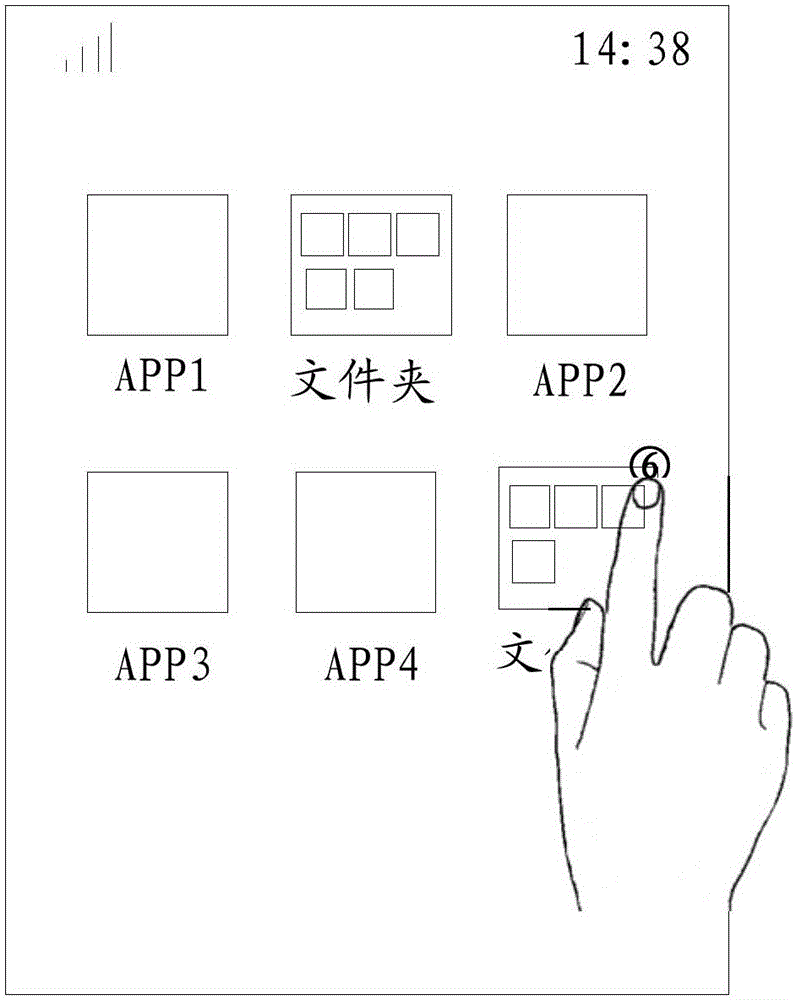
The invention discloses an operating method for a folder and a mobile terminal. The method comprises following steps: obtaining operation of folders displayed on a display interface of the mobile terminal, wherein an application icon of at least one application program is arranged in a folder; and displaying a preview list on the display interface when detecting operation is matched with pre-set operation, wherein the preview list comprises unread prompt message sets of application programs corresponding to all application icons in the folder.The operating method for the folder and the mobile terminal have following beneficial effects: without entering an application program, unread messages of application programs corresponding to application icons in the folder can be searched. After searching unread messages, operation can be performed. The operation steps are simple and interaction processes are few. Processing efficiency of unread messages in the folder is greatly increased.
Owner:VIVO MOBILE COMM CO LTD
Method, system and device for switching stream media channel and altering broadcast media
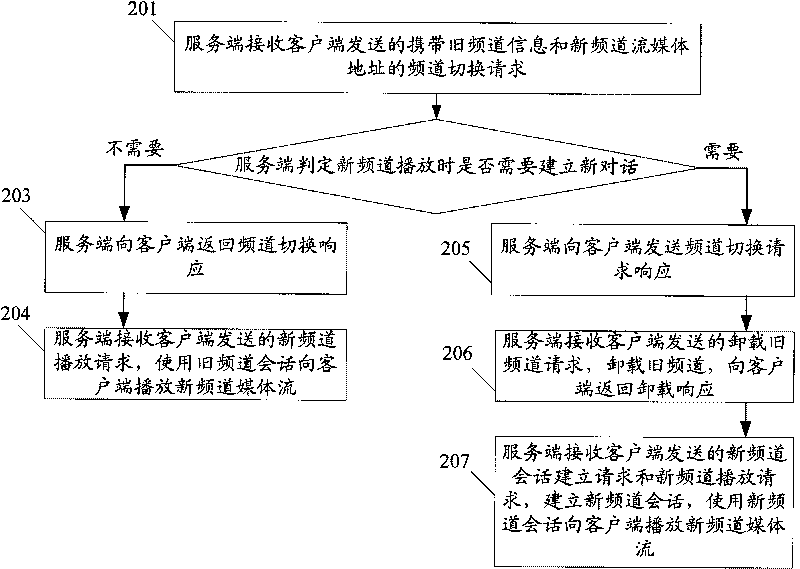
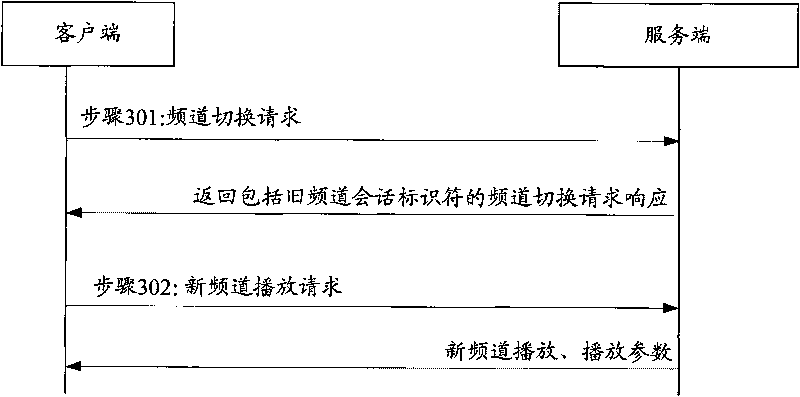
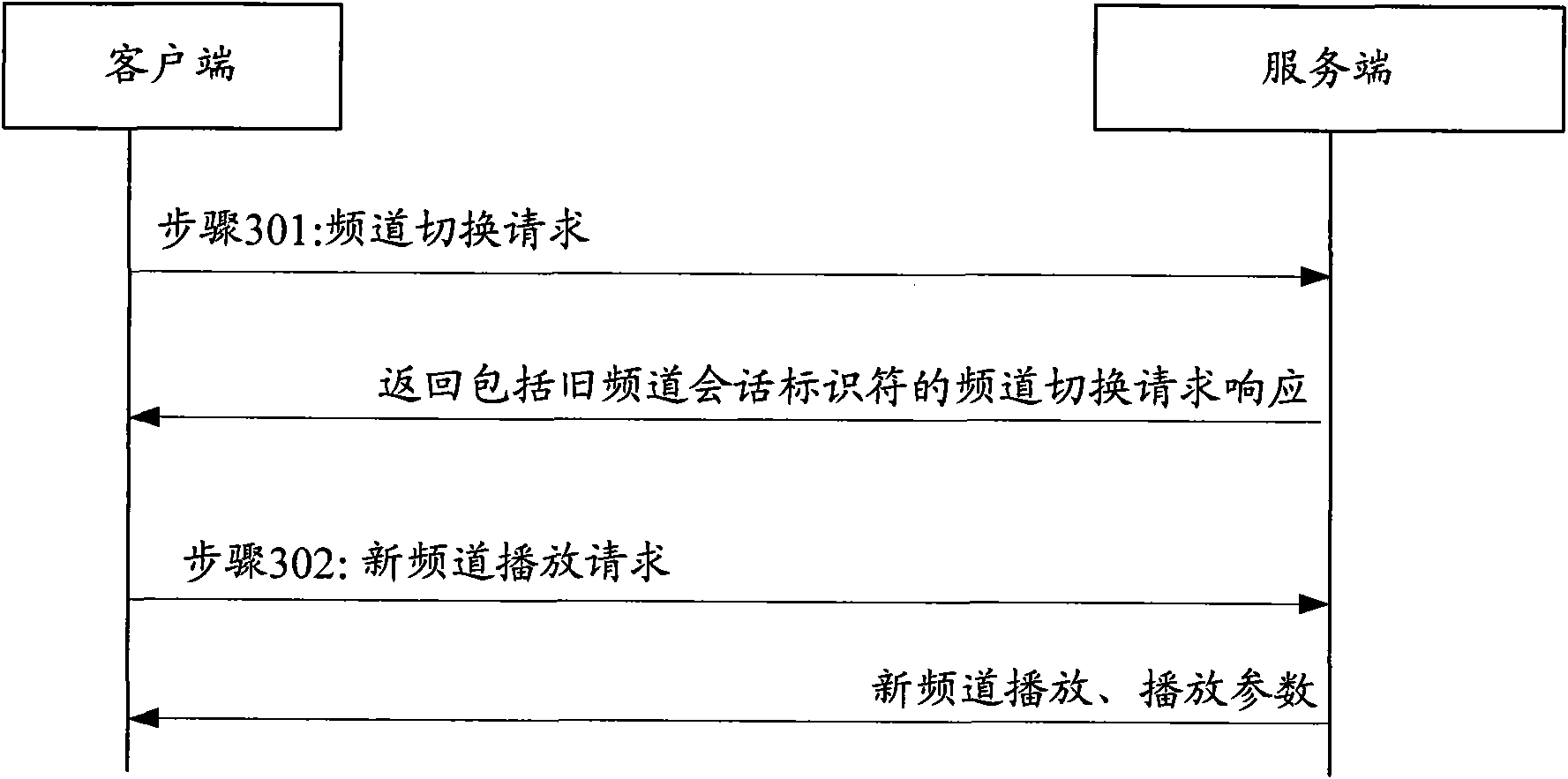
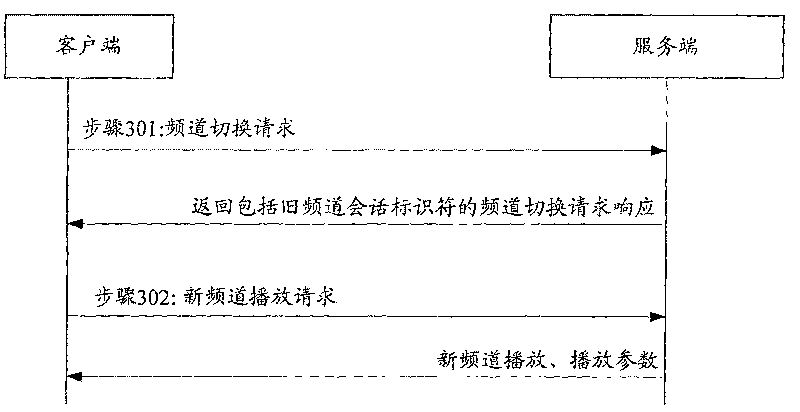
ActiveCN101137043AShorten the timeReduce interaction stepsPulse modulation television signal transmissionTwo-way working systemsDelayed timeComputer science
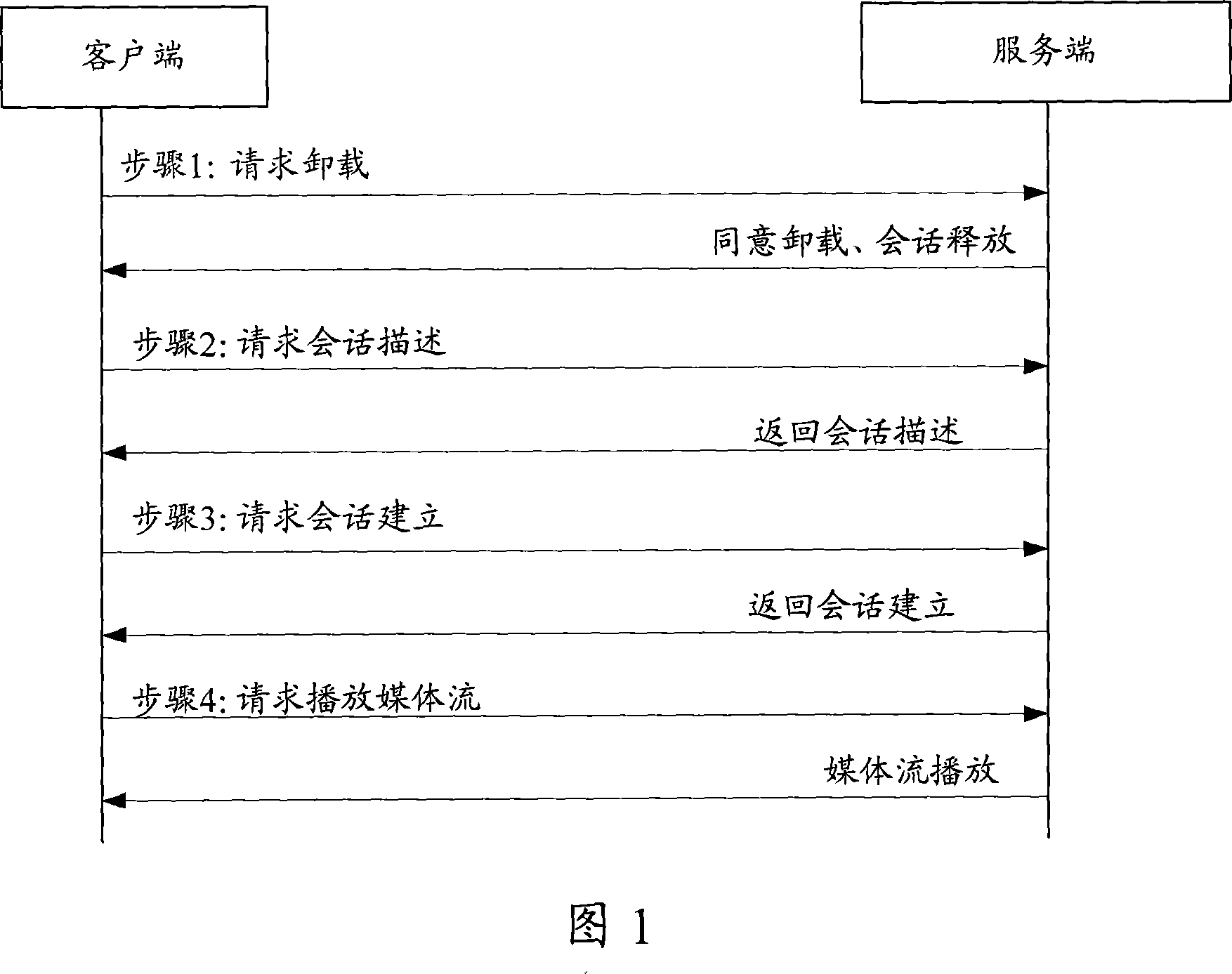
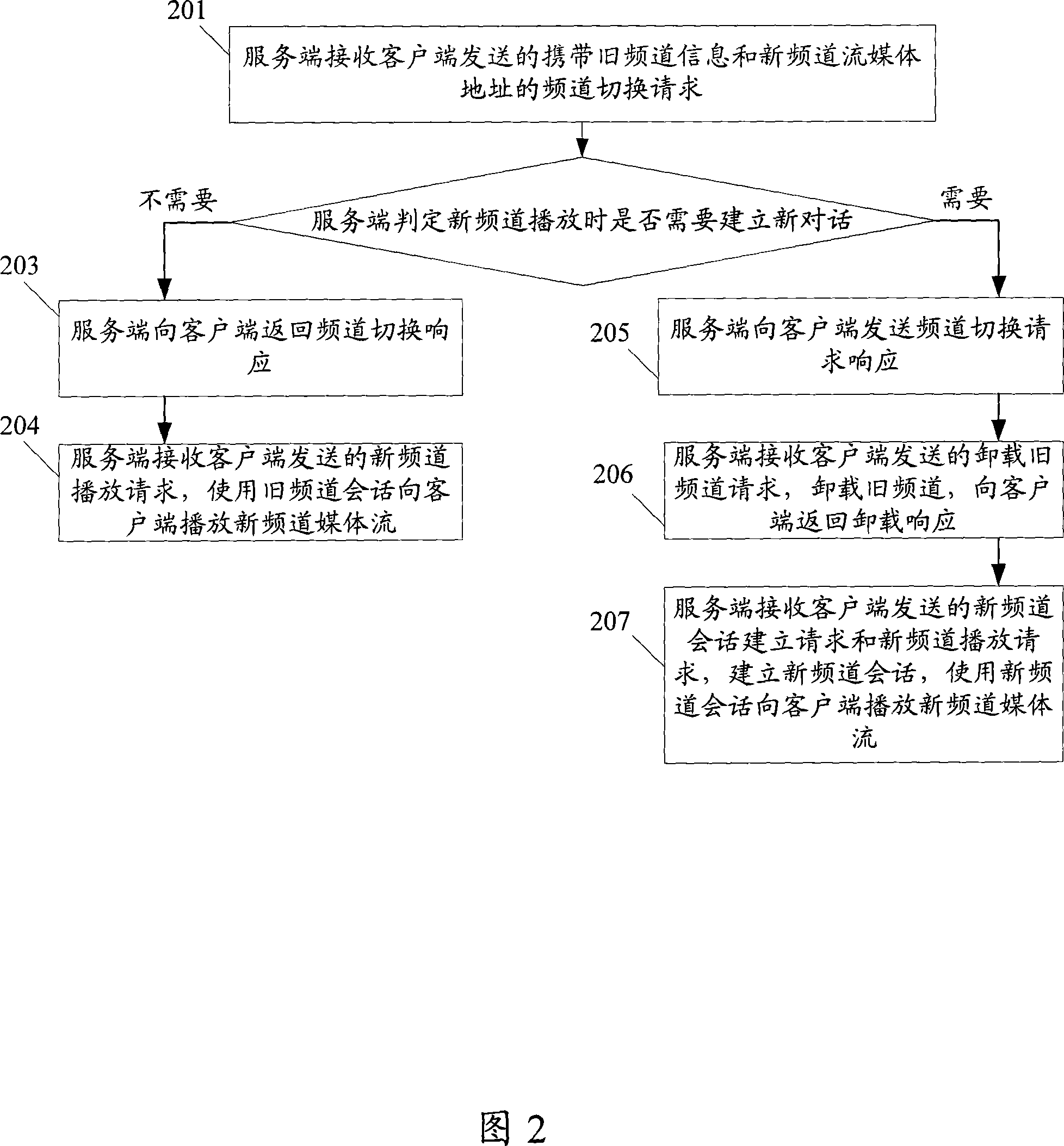
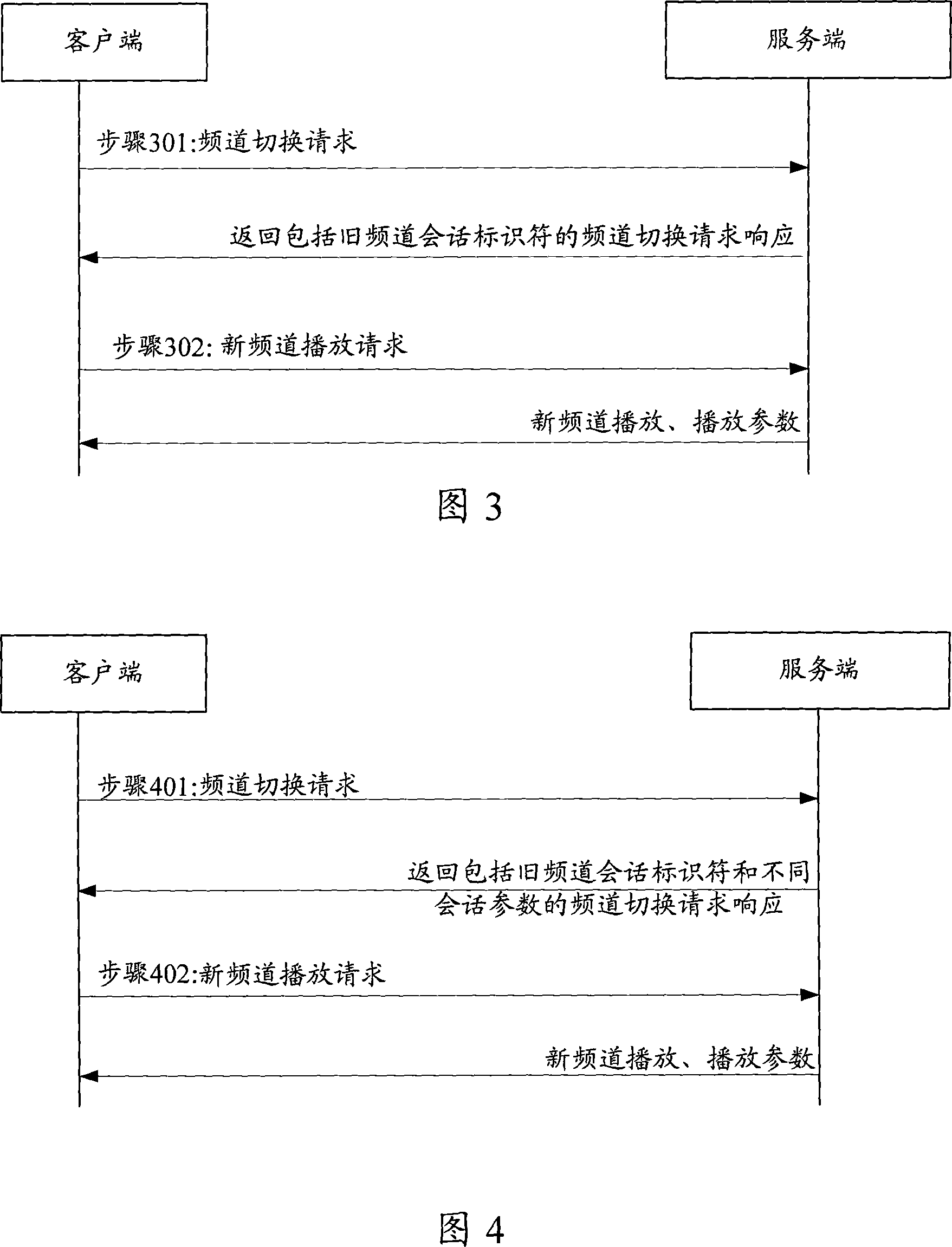
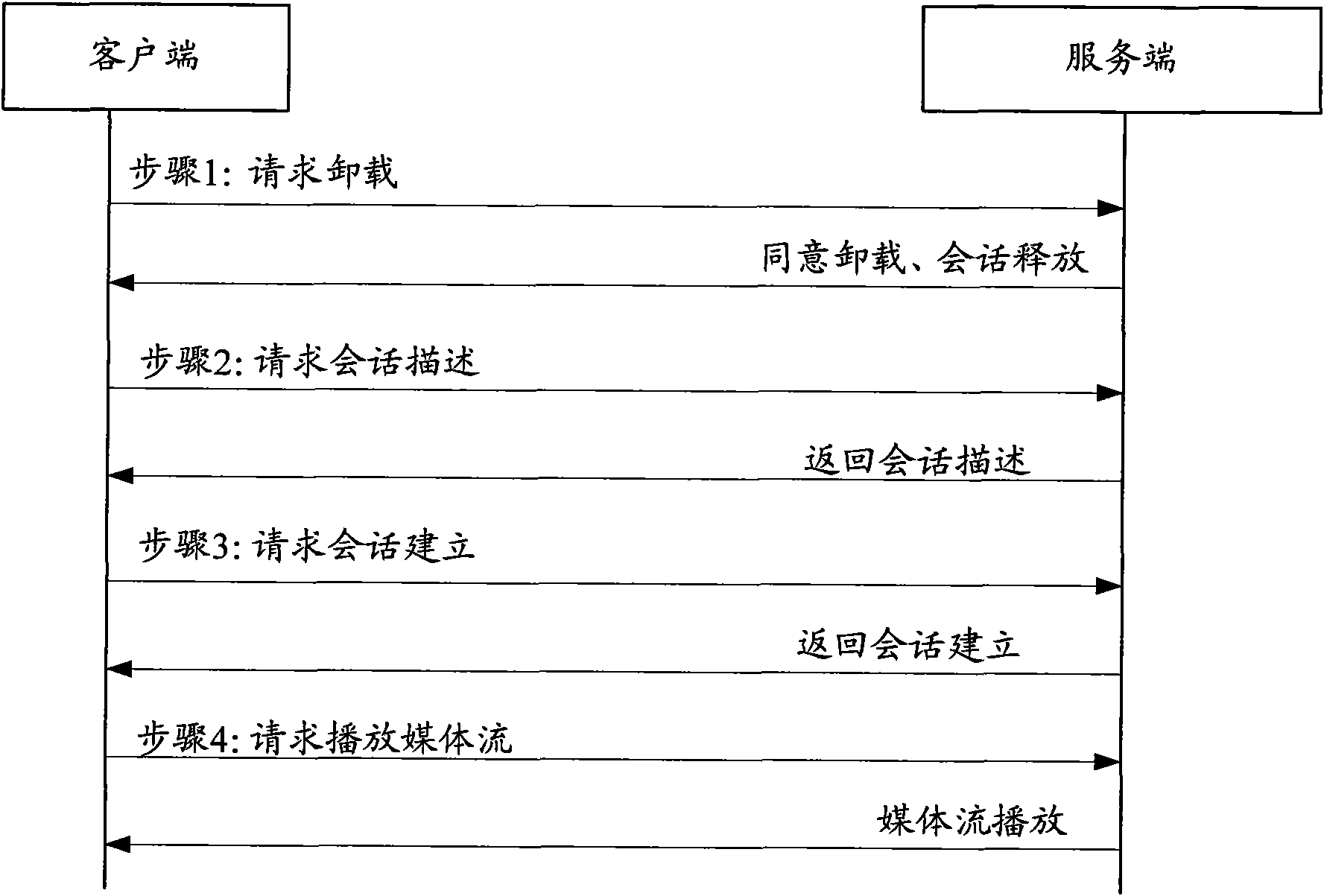
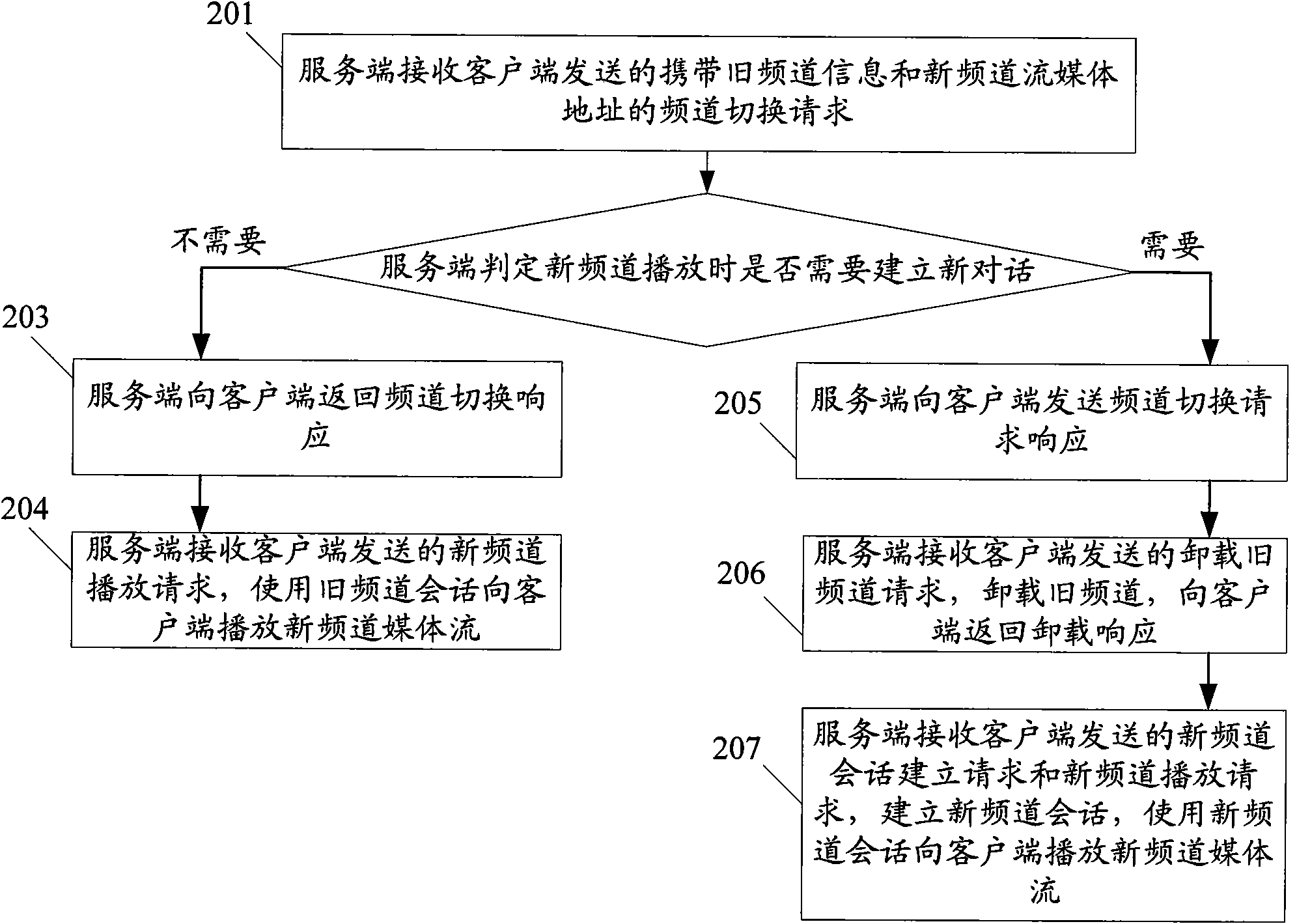
This method includes: (1) the server end (SE) receives frequency channel (FC) switching request with the old FC info (OFI) and the new FC flow-media address (NFFA) sent by user end (UE). (2) according to the result of comparing OFI with the residing server group info corresponding to NFFA, judging that need not to build a new conversation, SE responds UE the FC switching reply. (3) SE receives the new FC playing request sent by UE and uses the old FC conversation to play new FC media flow toward UE. The method of this invention can be realized on the system and device disclosed in this invention. This invention can reduce the delay time during flow-media FC switching and offers a hi-quality flow-media playing service for users.
Owner:HUAWEI TECH CO LTD
Virtual key mutual authentication system and method
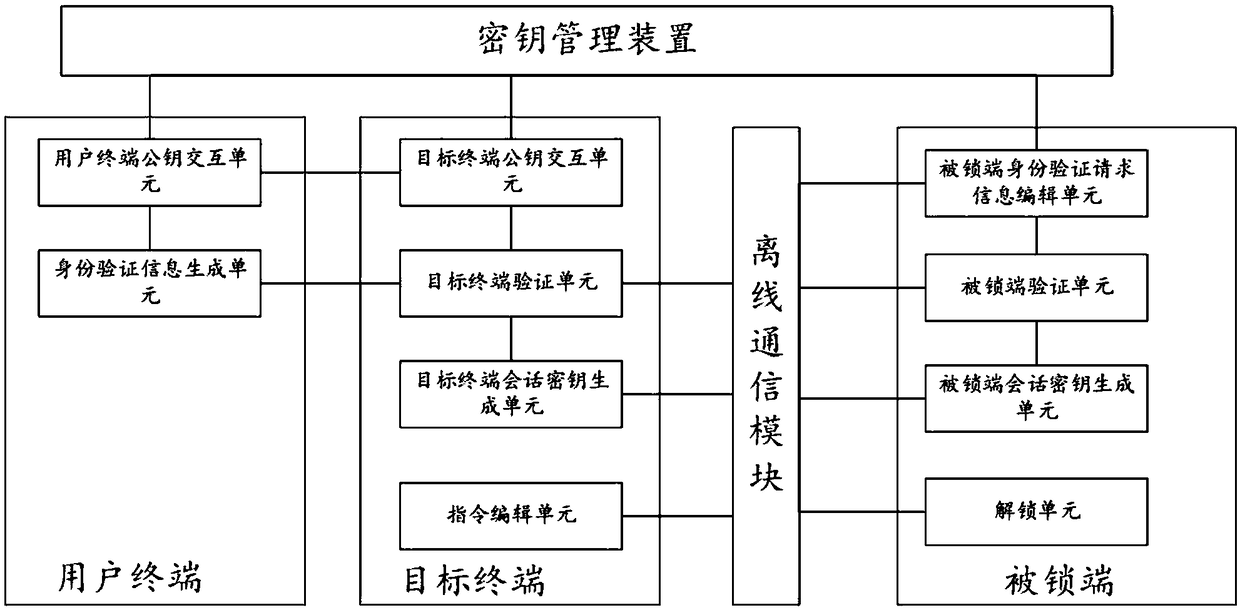
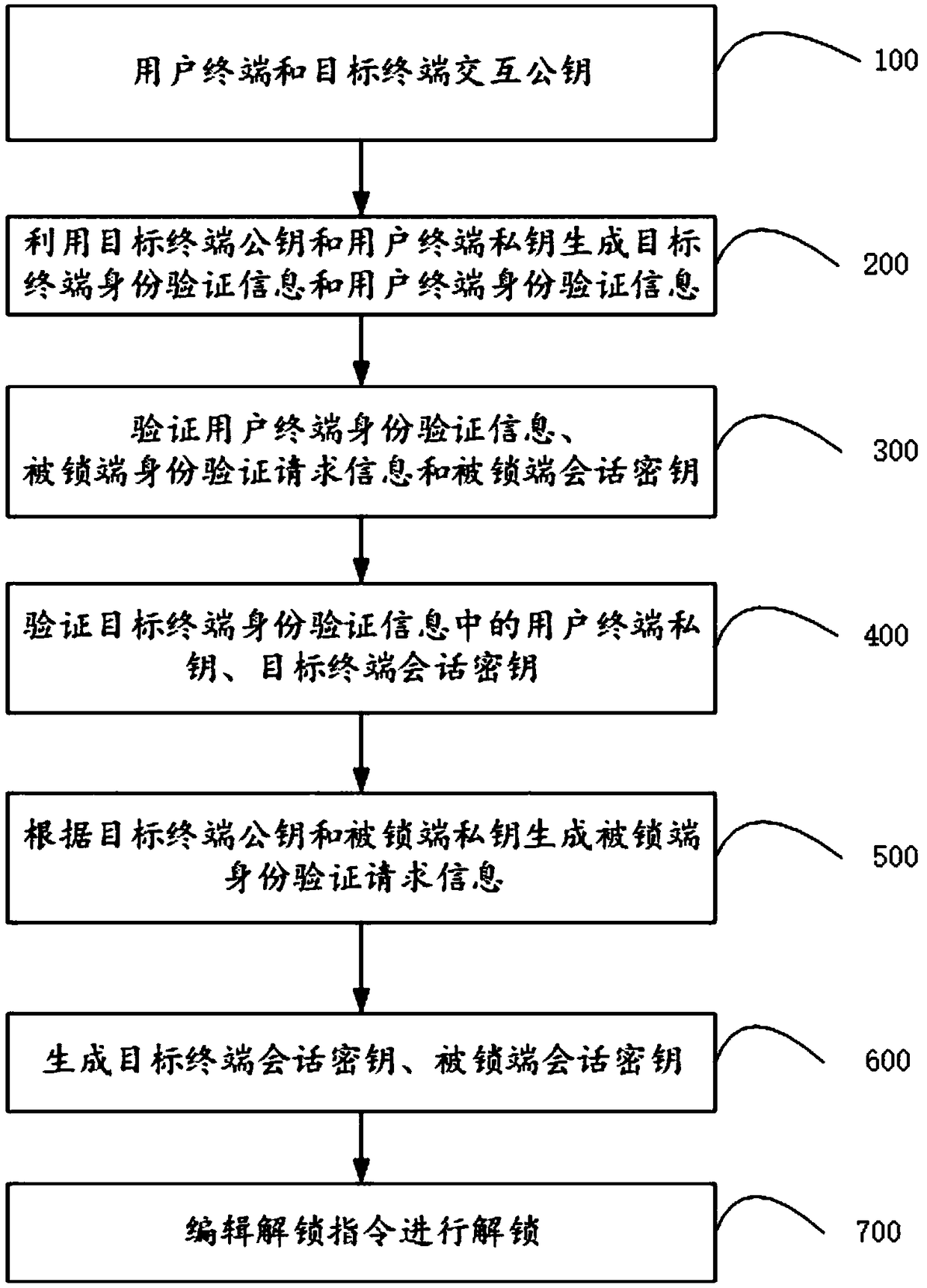
ActiveCN109067549AReduce sensitivityReduce interaction stepsUser identity/authority verificationIndividual entry/exit registersThird partyComputer terminal
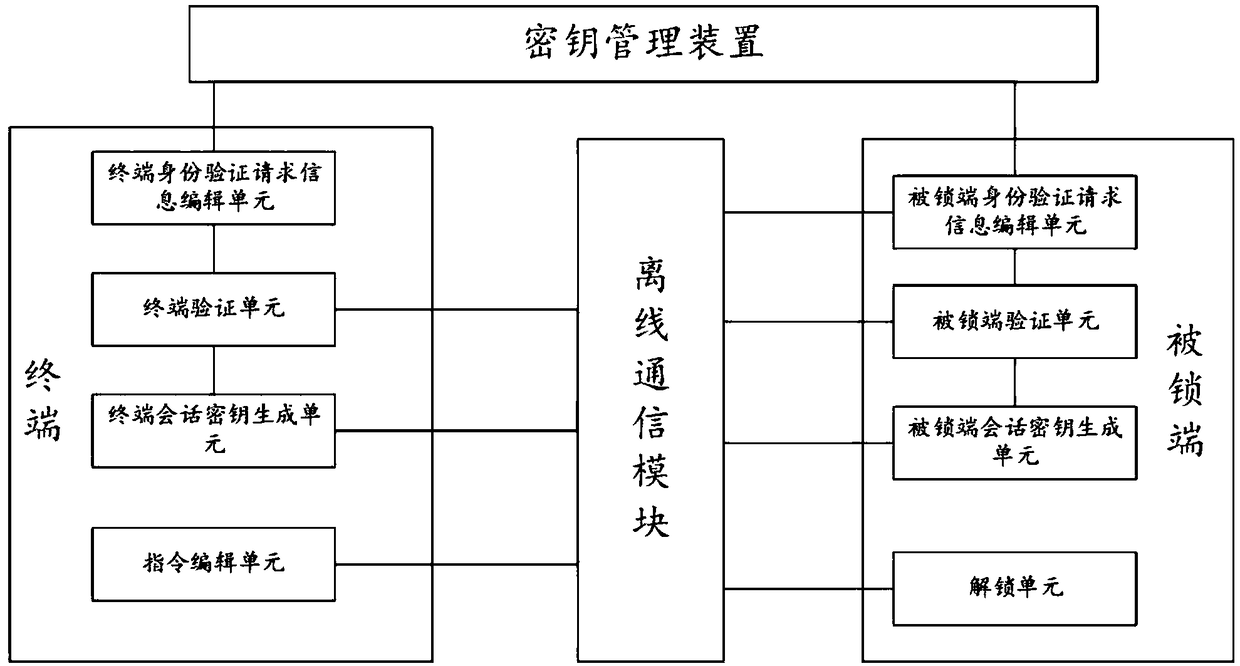
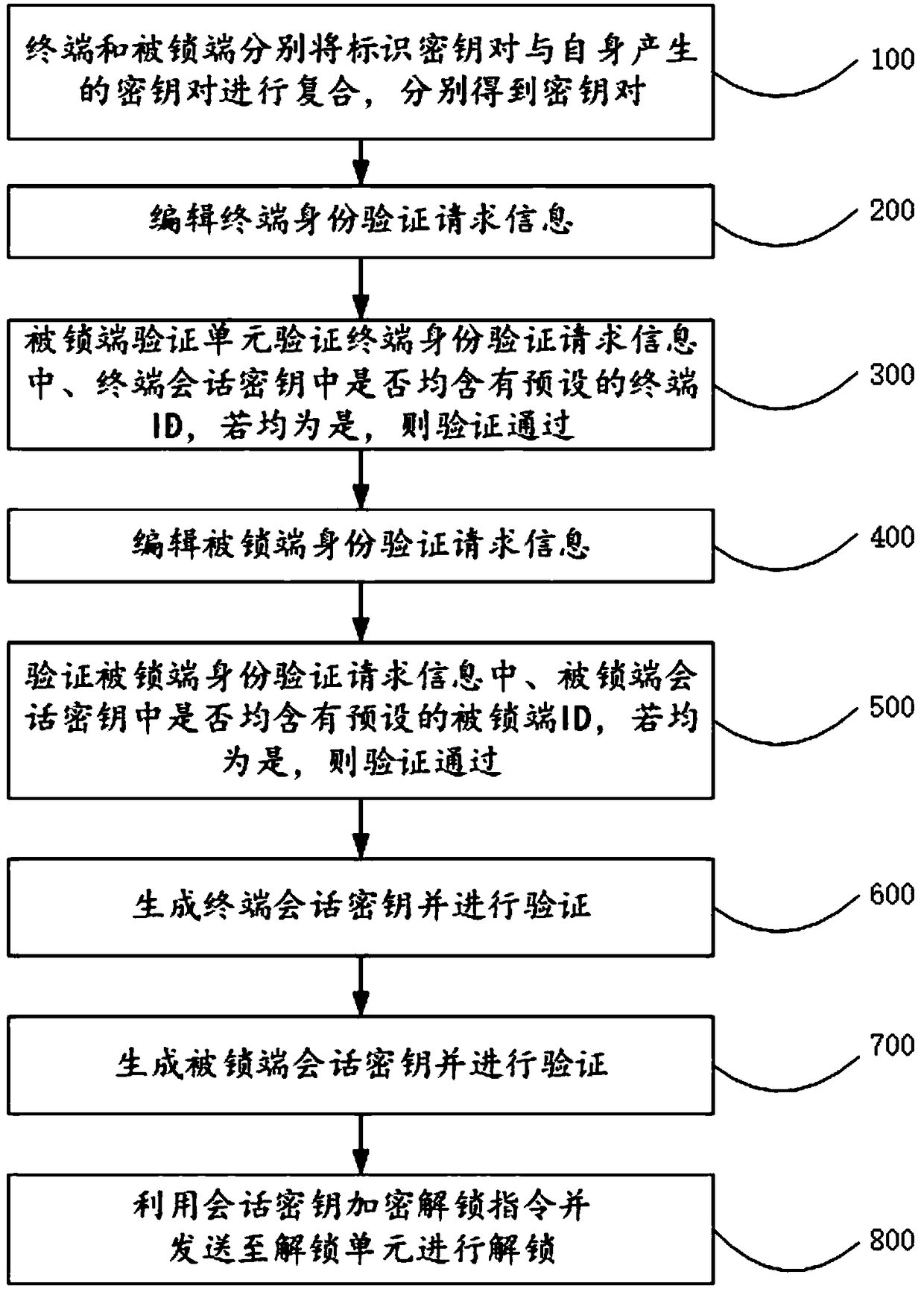
The invention relates to the technical field of communication, in particular to a virtual key two-way authentication system and method. The system comprises a terminal, which is used for generating terminal authentication request information and sending it to the locked end for authentication. If the authentication passes, the generated terminal session key is sent to the locked end for authentication. If the authentication passes, the session key editing and unlocking instruction is sent to the locked end. The locked end is used for generating the authentication request information of the locked end and sending it to the terminal for authentication. If the authentication passes, the locked end session key is generated and sent to the terminal for authentication. If the authentication passes, the locked end session key is unlocked according to the unlocking instruction sent by the terminal. An offline communication module is used for transmitting information between the terminal and the locked end. The invention does not require on-line authentication of a third party when unlocking, but directly carries out information interaction between the terminal and the locked end, reduces the sensitivity of the whole system and the method to the network, and improves the safety and reliability in the use process.
Owner:北京信长城科技发展有限公司
Zero-trust-based power Internet of Things security protection method
PendingCN112507317ASolve management problemsReduce interaction stepsDigital data protectionDigital data authenticationInternet privacyContinuous evaluation
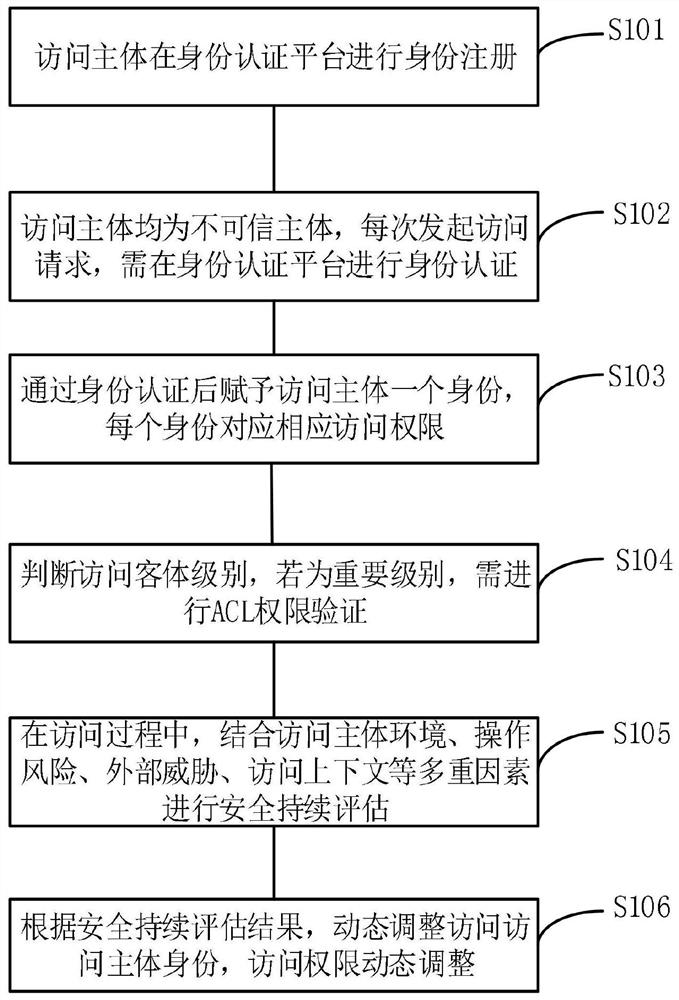
The invention discloses a zero-trust-based power Internet of Things security protection method. The method comprises the steps that an access subject performs identity registration on an identity authentication platform; wherein the access main bodies are incredible main bodies and need to be authenticated through the identity authentication platform every time an access request is initiated; an identity is given to the access subject after passing the identity authentication, wherein each identity corresponds to a corresponding access authority; an access object level is judged, and if the access object level is an important level, ACL permission verification is carried out; in the access process, safety continuous evaluation is carried out in combination with multiple factors such as anaccess subject environment, an operation risk, an external threat and an access context; and the identity of the access subject is dynamically adjusted and the access permission is dynamically adjusted according to the safety continuous evaluation result. According to the invention, the problems of gradual failure of traditional boundary security protection and immature zero-trust security protection are solved.
Owner:STATE GRID HEBEI ELECTRIC POWER RES INST +1
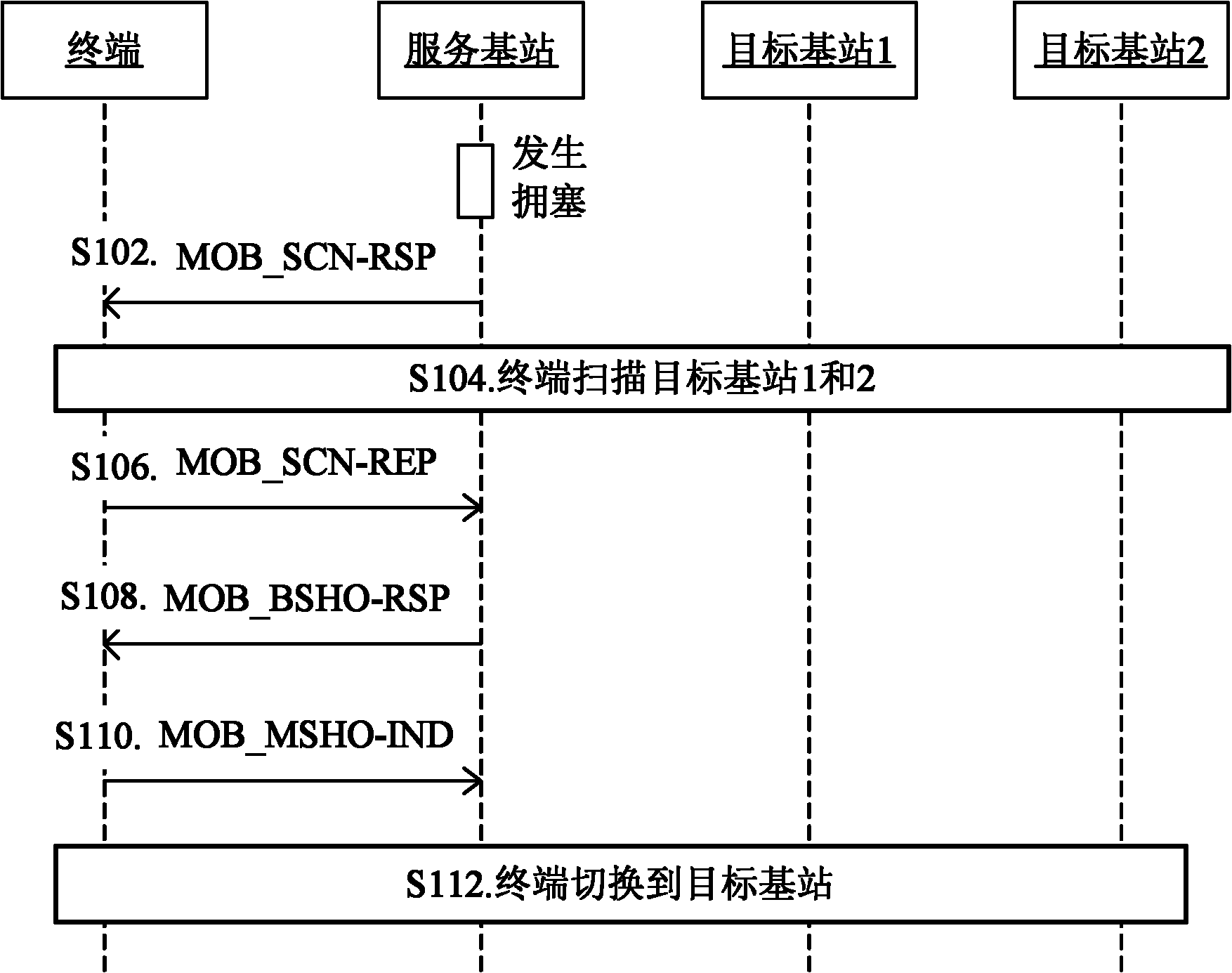
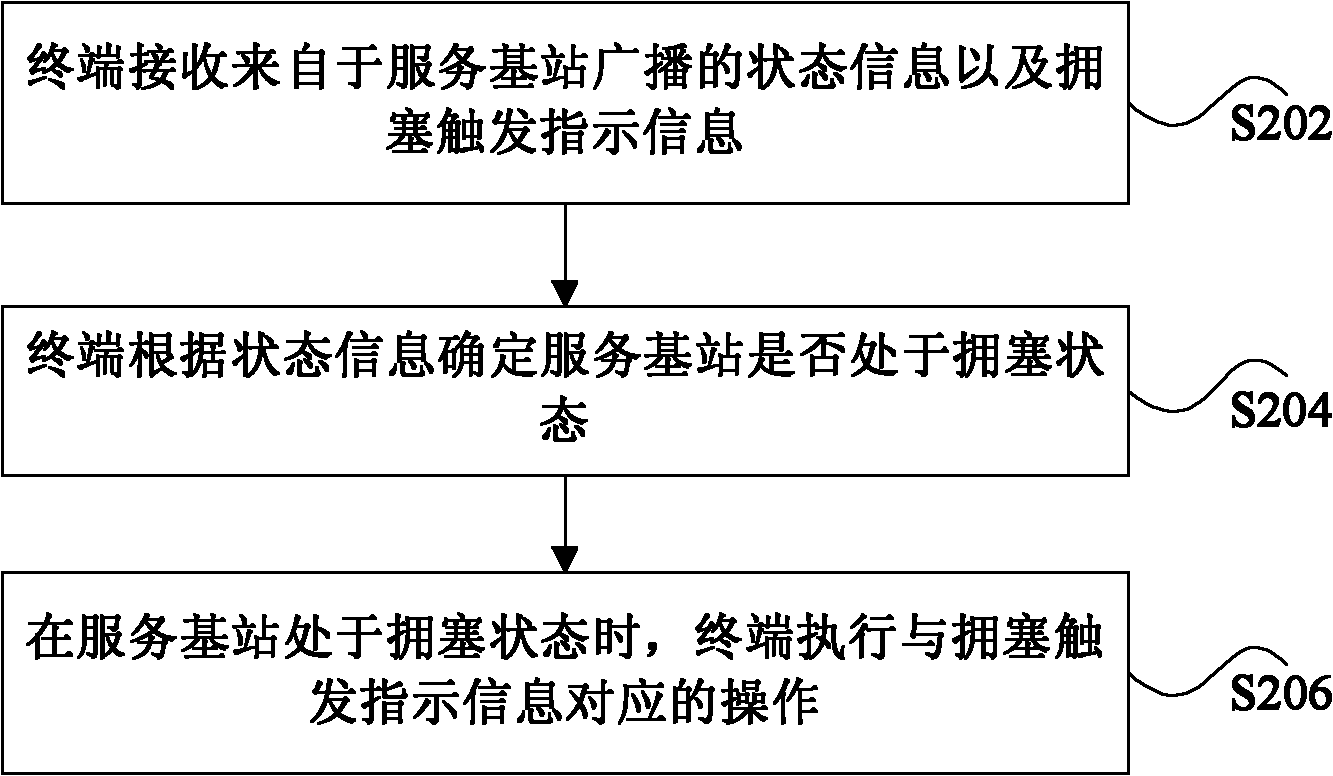
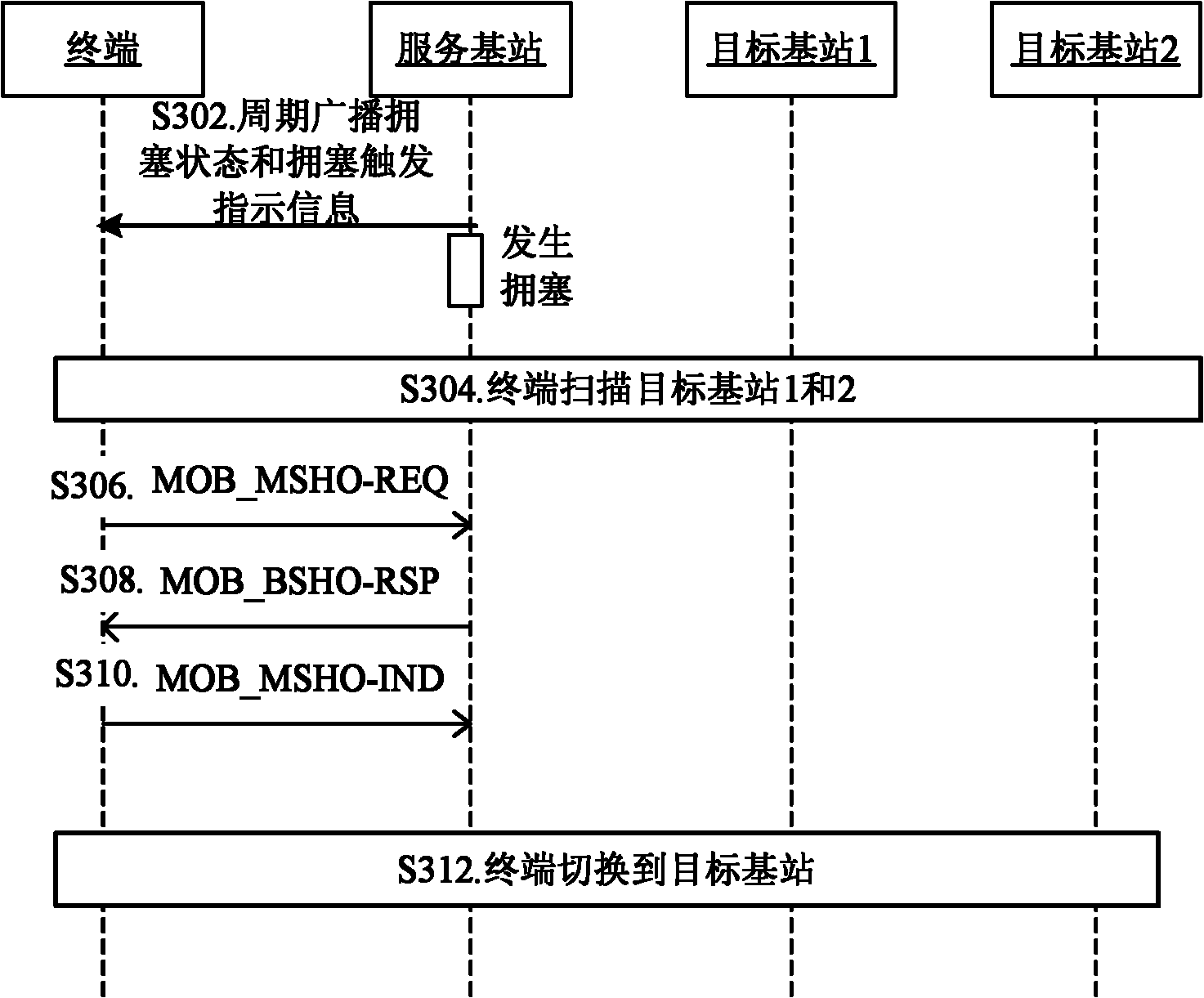
Switching method and system based on congestion control
ActiveCN102006622AReduce interaction stepsReduce workflowNetwork traffic/resource managementNetwork congestionReal-time computing
The invention discloses a switching method and system based on congestion control. The method comprises: the terminal receives the state information broadcast by a service base station and the congestion trigger indicating information; the terminal determines whether the service base station is in a congestion state or not according to the state information; and the terminal executes the operation corresponding to the congestion trigger indicating information when the service base station is in the congestion state. The technical scheme provided by the invention has the advantages that the interactive steps of the terminal and the base station are reduced and the working procedure of the service base station in the congestion state is lightened so as to greatly enhance the timeliness of solving the congestion.
Owner:ZTE CORP
Rapid reconnecting method based on XMPP (extensible messaging and presence protocol) client side, terminal and server
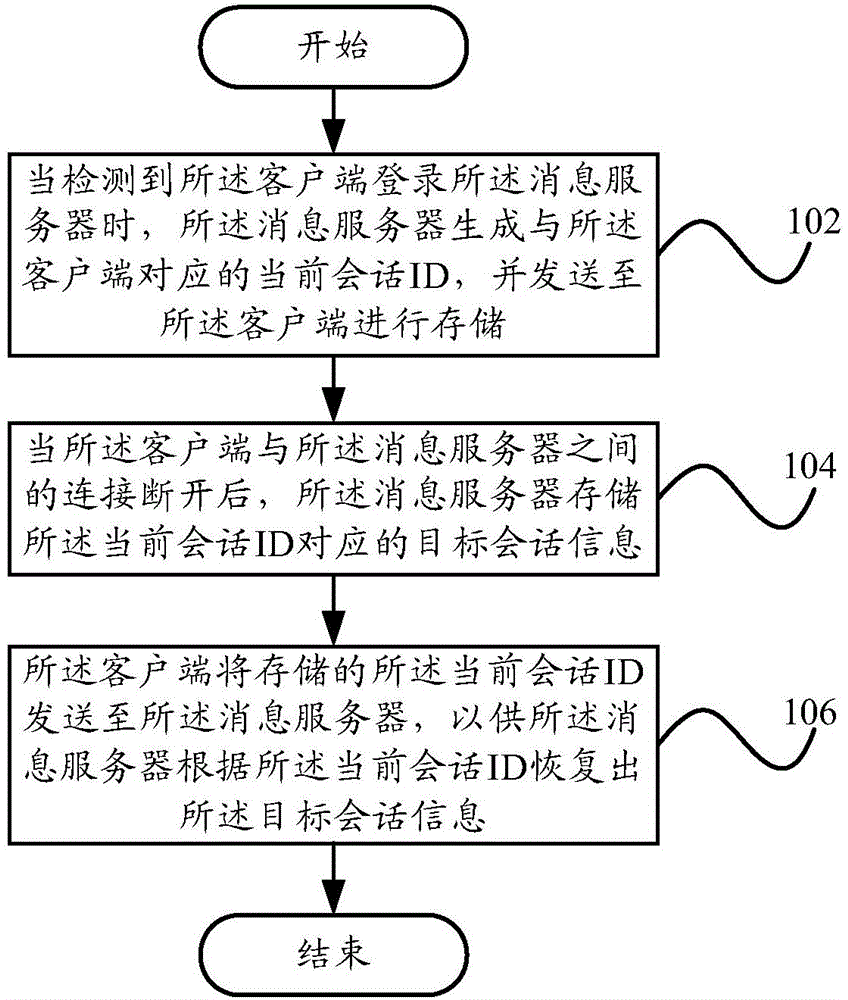
InactiveCN104580537AReduce interaction stepsImprove user experienceTransmissionClient-sideSession ID
The invention provides a rapid reconnecting method based on an XMPP (extensible messaging and presence protocol) client side, a terminal and a message server, wherein the rapid reconnecting method comprises the following steps that: the message server generates a current session ID corresponding to the client side when the client side is detected to login the message server, and sends the current session ID to the client side to store; when the connection between the client side and the message server is disconnected, the message server stores a target session message corresponding to the current session ID; the client side sends the stored current session ID to the message server, so that the message server recovers the target session message according to the current session ID. According to the technical scheme adopted by the invention, after the client side and the message server are disconnected, the client side only needs to send a repaid re-connecting message to the message server to recover the last reconnecting session, and does not need to re-login, so that an interaction step, time and resources are omitted, and the user experience is improved.
Owner:ZICT TECH CO LTD
Method, system and device for modifying playing streaming media
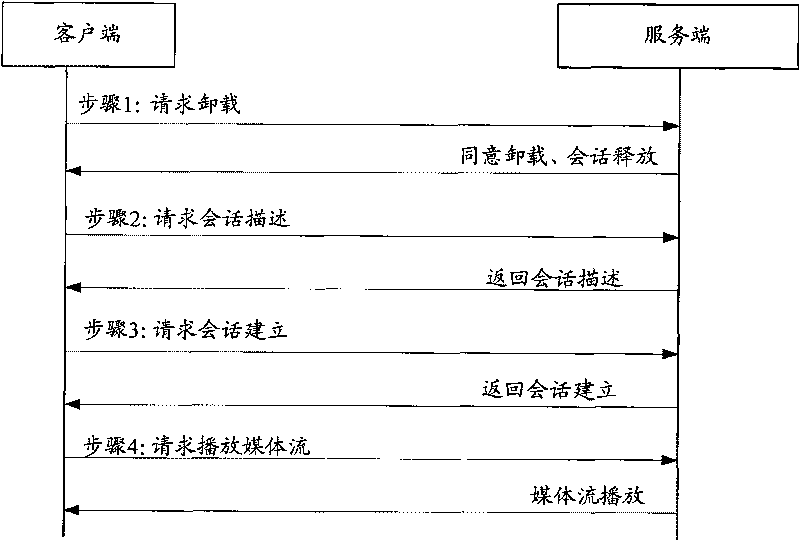
ActiveCN101714977AShorten the timeReduce interaction stepsSpecial service provision for substationTwo-way working systemsComputer network
The invention discloses a method, a system and a device for modifying playing streaming media. In the method for modifying playing streaming media, a service end receives a playing media modifying request which is sent by a client end and carries the information of playing media needed to be modified by the current play channel, and the service end modifies the playing media according to the request. The method disclosed by the invention can be realized on the system and the device disclosed by the invention which can provide high-quality streaming media playing service for users.
Owner:HUAWEI TECH CO LTD
Virtual key sharing system and method
ActiveCN109067548ASimple structureSimple methodUser identity/authority verificationIndividual entry/exit registersComputer terminalKey sharing
The invention relates to the technical field of communications, in particular to a virtual key sharing system and method. The system comprises a user terminal, which is used for interacting with a target terminal and generating authentication information of the target terminal and authentication information of the user terminal. The target terminal is used for verifying the received authenticationinformation of the user terminal, generating a session key of the target terminal, and sending an unlocking instruction edited by the session key to the locked terminal. The locked end is used for verifying the received authentication information of the target terminal with the private key of the user terminal, generating a session key of the locked end, and unlocking according to an unlocking instruction sent by the target terminal. An offline communication module is used for transmitting information between the terminal and the locked end. The user terminal and the target terminal of the invention carry out authentication of the identity information through the interactive public key, and only if the authentication is successful, the target terminal can use the identity information of the user terminal to unlock the locked end, which has the advantages of simple structure, simple method and safe and convenient use.
Owner:北京信长城科技发展有限公司
Control method and device
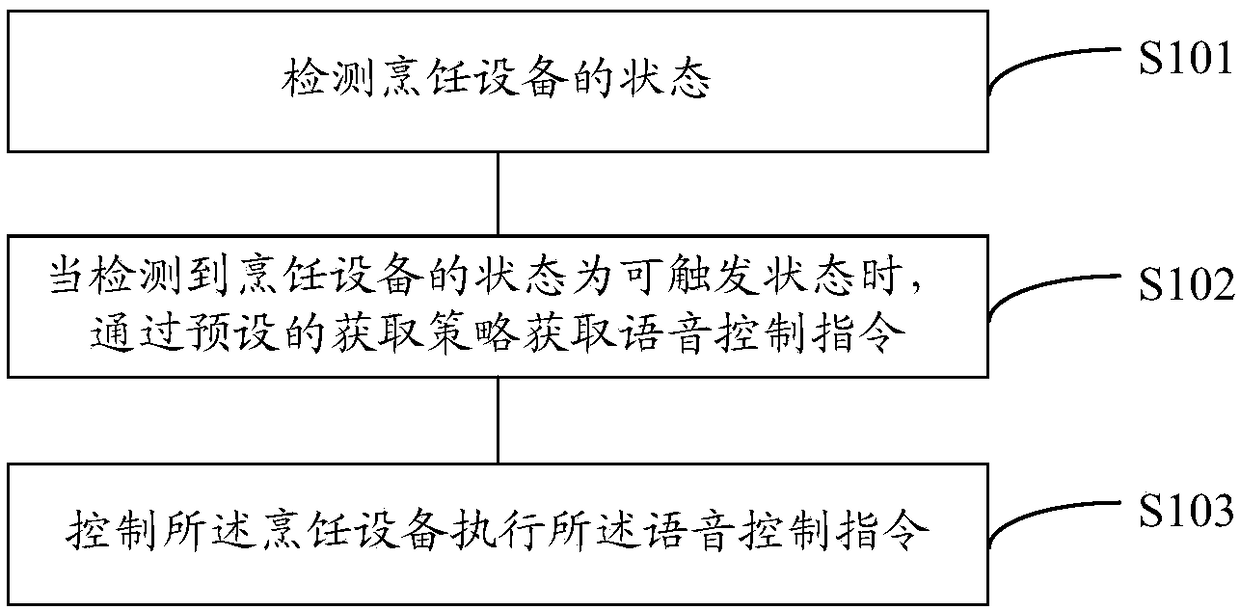
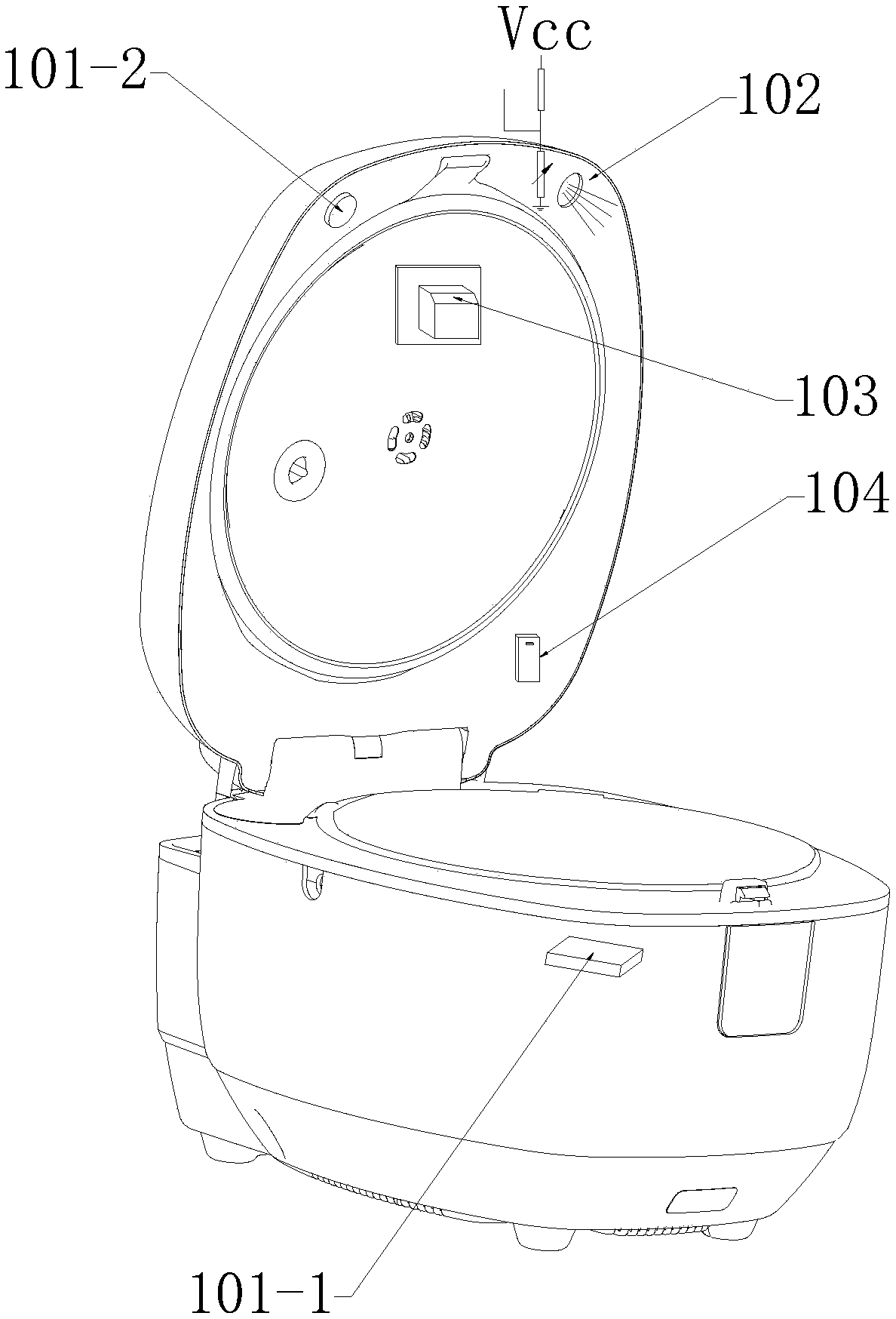
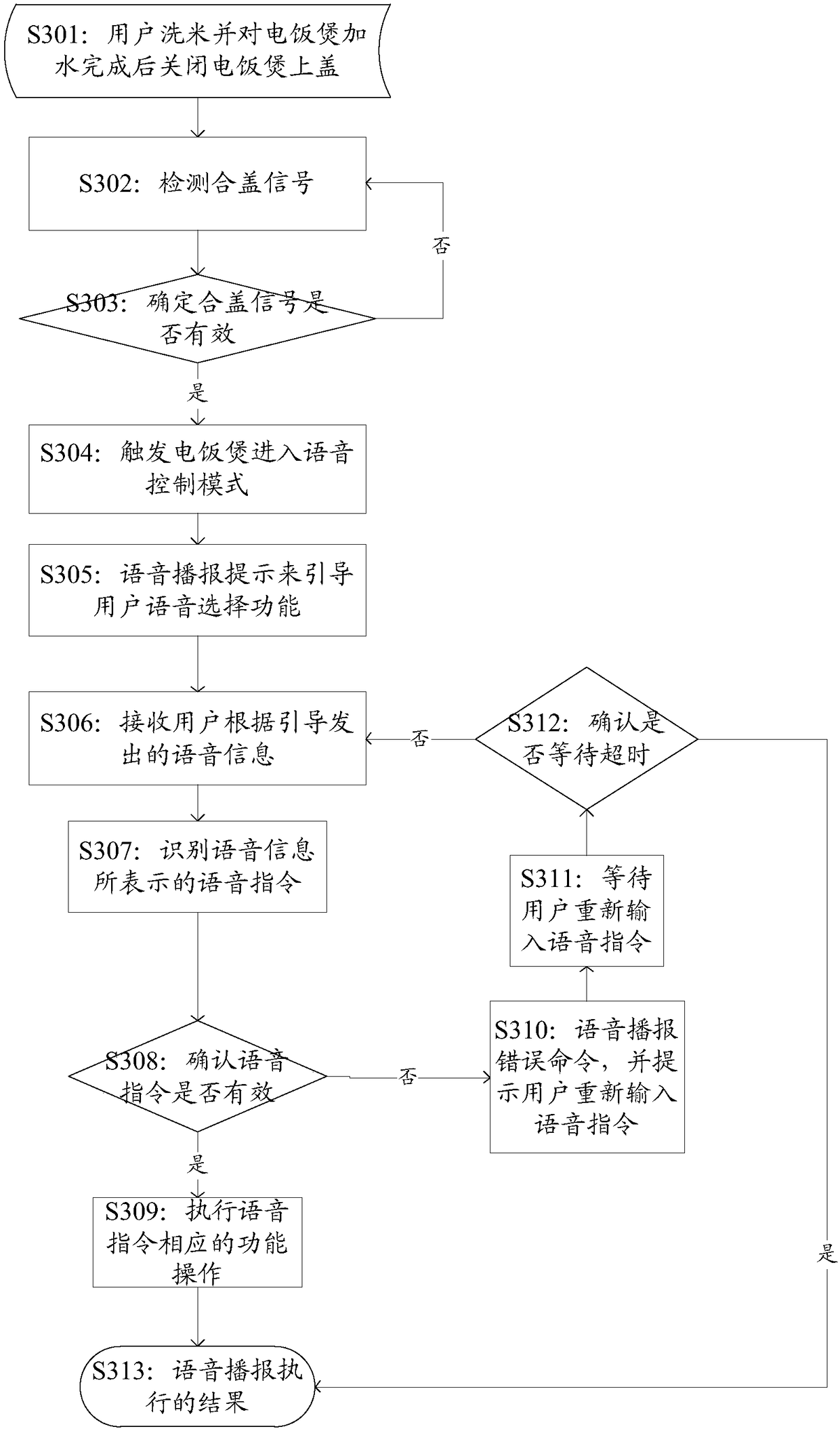
ActiveCN109215644AConvenient voice controlReduce interaction stepsSpeech recognitionTime-controlled ignitorsSpeech soundControl mode
The embodiment of the invention discloses a control method and a device. The method may include: a state of the cooking apparatus is detected; when the state of the cooking apparatus is detected to betriggerable, the voice control instruction is obtained through a preset acquisition strategy; and the cooking apparatus is controlled to execute the voice control instruction. The state detection ofthe cooking apparatus replaces the wake-up of the voice control mode artificially in the traditional voice control scheme so as to reduce the interactive steps between the user and the cooking apparatus, thereby facilitating the user to carry out voice control on the cooking apparatus and improving the control efficiency.
Owner:FOSHAN SHUNDE MIDEA ELECTRICAL HEATING APPLIANCES MFG CO LTD
Method and device for interaction between VR/AR system and user
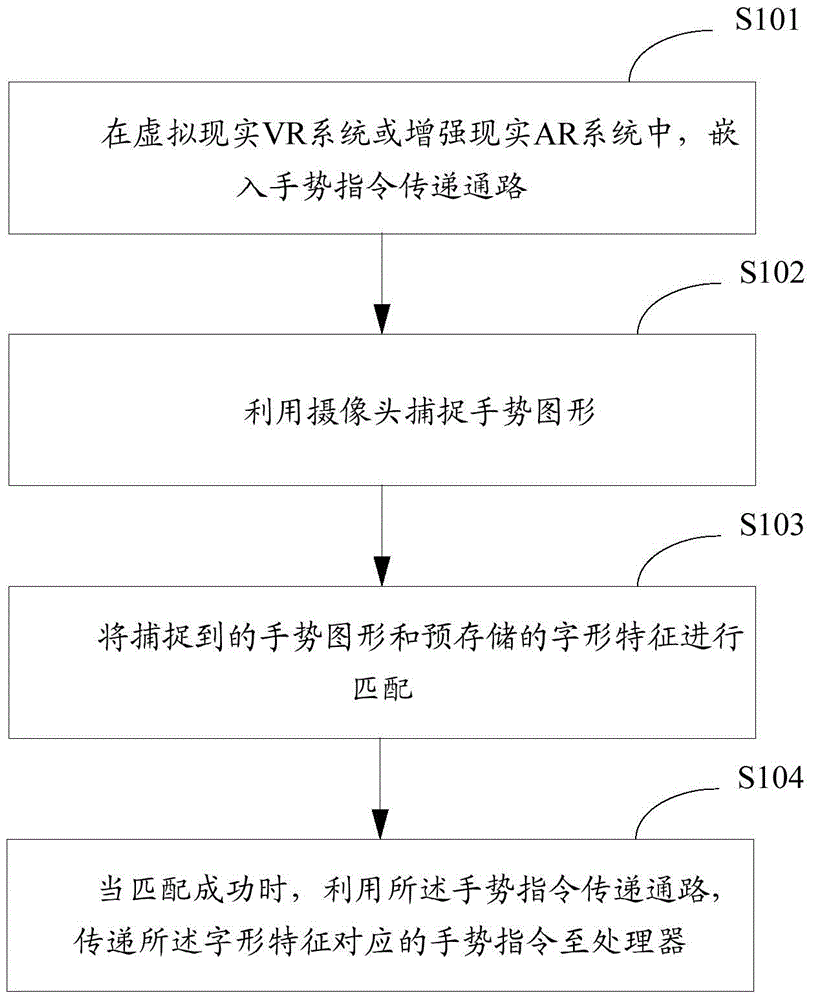
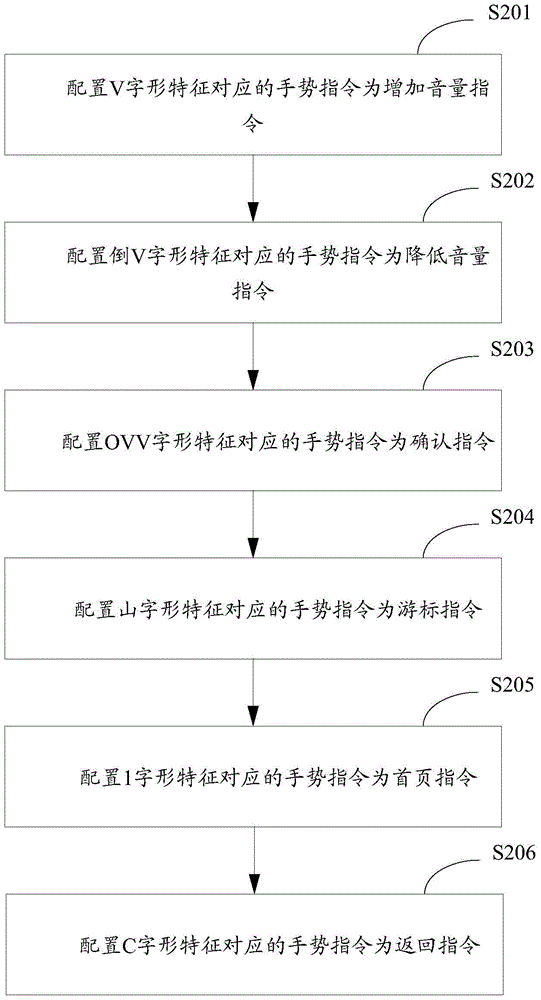
InactiveCN106527677AImprove interaction efficiencyInteraction efficiency is shortenedInput/output for user-computer interactionGraph readingGraphicsVirtual reality
The invention is applicable to the field of VR or AR and provides a method and device for interaction between a VR / AR system and a user. The method for the interaction between the VR / AR system and the user comprises the steps that a gesture instruction transmission path is inlaid in a VR system or an AR system; a camera is used to capture a gesture graph; the captured gesture graph is matched with a pre-stored font characteristic; and when matching is successful, the gesture instruction transmission path can transmit a gesture instruction corresponding to the font characteristic to a processor. According to the invention, the gesture can be used to satisfy a demand for the interaction between the VR / AR system and the user. The method and device have the beneficial effects that on one side, interaction duration is reduced and interaction efficiency is increased through decrease of interaction steps and data; and on the other side, the cost for adding external input equipment is reduced.
Owner:深圳市原点创新有限公司
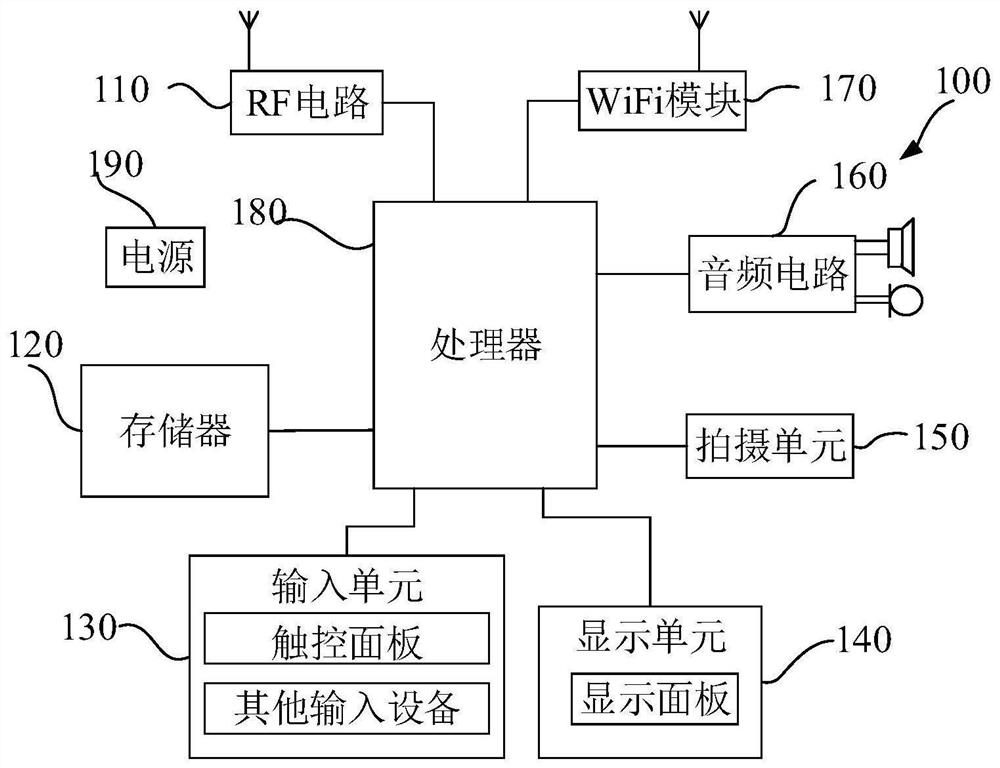
Information display method of mobile terminal, mobile terminal and readable storage medium
PendingCN109753210AGood visual presentationImprove user experienceInput/output processes for data processingComputer scienceCommunication Contact
The invention provides an information display method of a mobile terminal. The method comprises the following steps: detecting a gesture operation acting on a display interface of the mobile terminal;wherein the display interface comprises a first area and a second area, the first area is used for displaying a communication record list, and the second area is used for displaying a contact information list; wherein the first area and the second area are displayed according to a first preset display proportion; and when a sliding operation is detected on the first area and the duration of the sliding operation exceeds a preset duration threshold value, expanding the first area according to a second preset display proportion, and reducing the second area. The invention also provides a mobileterminal and a readable storage medium. The technical problems that user operation is increased and related function module resources cannot be fully utilized due to the fact that communication contact person information and communication records are displayed separately by an existing mobile terminal are solved.
Owner:上海豹云网络信息服务有限公司
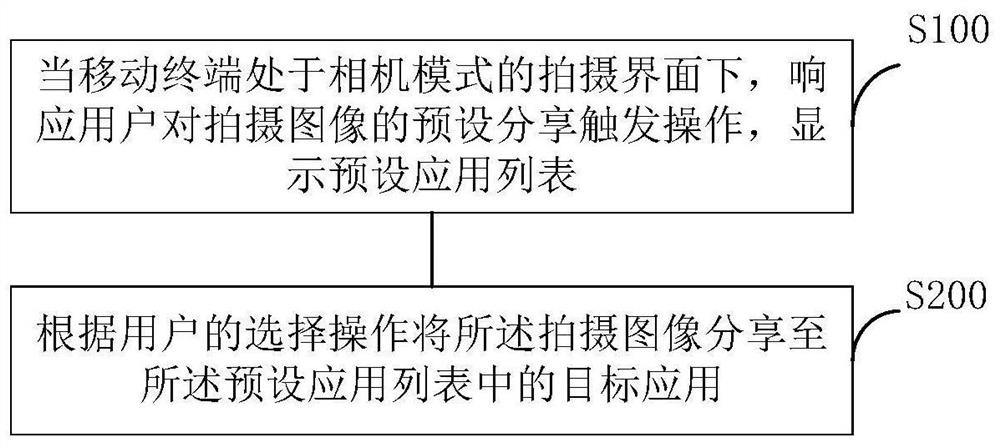
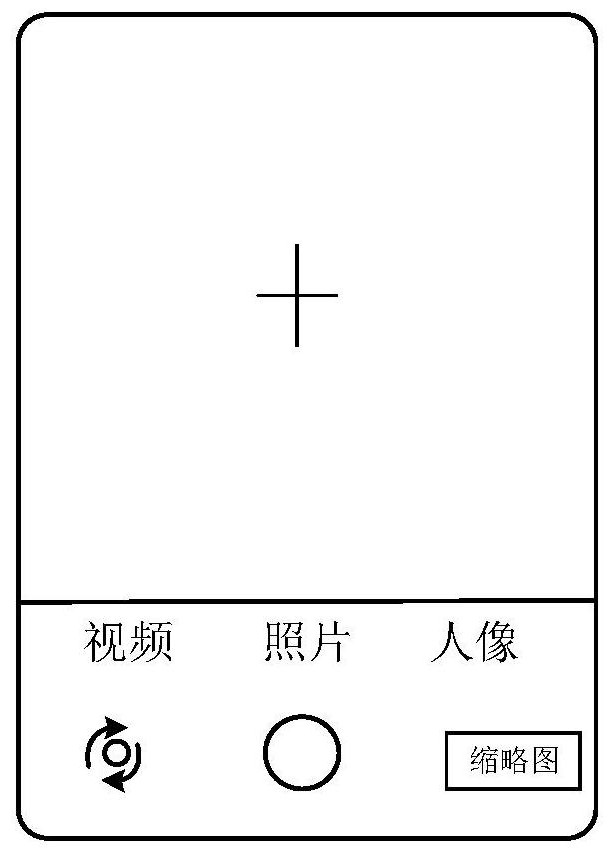
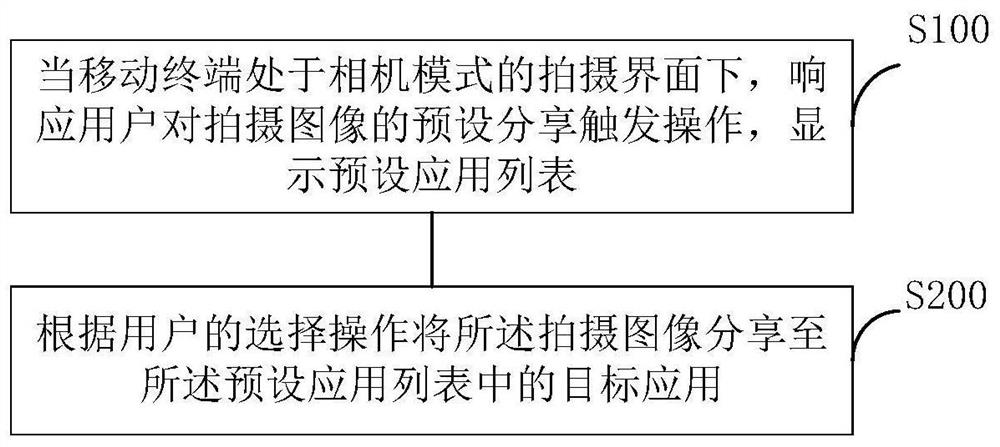
Shot image sharing method and device, mobile terminal and readable storage medium
ActiveCN112839163AReduce interaction stepsImprove experienceTelevision system detailsColor television detailsComputer hardwareEngineering
The invention discloses a shot image sharing method and device, a mobile terminal and a readable storage medium, and the method comprises the steps: responding to a preset sharing triggering operation of a user on a shot image when the mobile terminal is in a shooting interface of a camera mode, and displaying a preset application list; and sharing the shot image to a target application in the preset application list according to a selection operation of a user. According to the technical scheme provided by the invention, the latest shot image can be quickly shared in the camera mode, compared with the existing sharing operation, the steps of interaction with the user and skipping with other applications are reduced, the method is convenient and quick, and the user experience is improved.
Owner:ONEPLUS TECH SHENZHEN
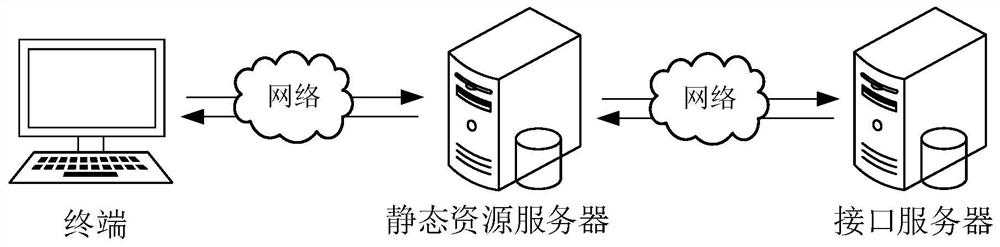
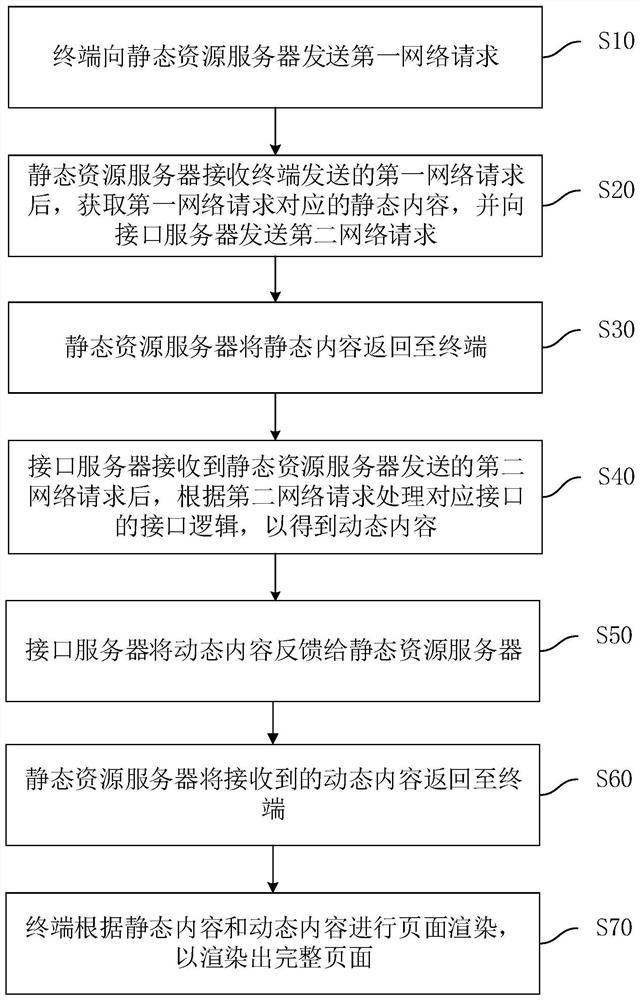
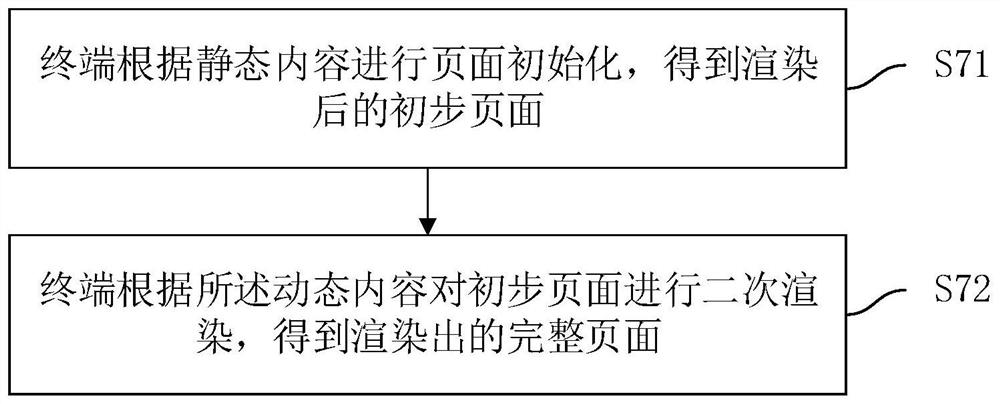
Page rendering method and system
PendingCN112685669AShorten the timeReduce interaction stepsWeb data browsing optimisationTerminal equipmentIndustrial engineering
The invention relates to the technical field of artificial intelligence, and provides a page rendering method and system. The method comprises the steps that a static resource server receives a first network request sent by a terminal, and locally obtains static content corresponding to the first network request from the static resource server; the static resource server returns the static content to the terminal; the static resource server sends a second network request to the interface server and receives dynamic content fed back by the interface server according to the second network request; and the static resource server returns the dynamic content to the terminal, so that the terminal performs page rendering according to the static content and the dynamic content to render a complete page. After the static resource server receives the first network request sent by the terminal device, the static resource server sends the second network request to the interface server, the terminal does not need to request the interface server again after page initialization, the steps of interaction between the interface server and the terminal are reduced, and the page request rendering time is shortened.
Owner:PINGAN PUHUI ENTERPRISE MANAGEMENT CO LTD
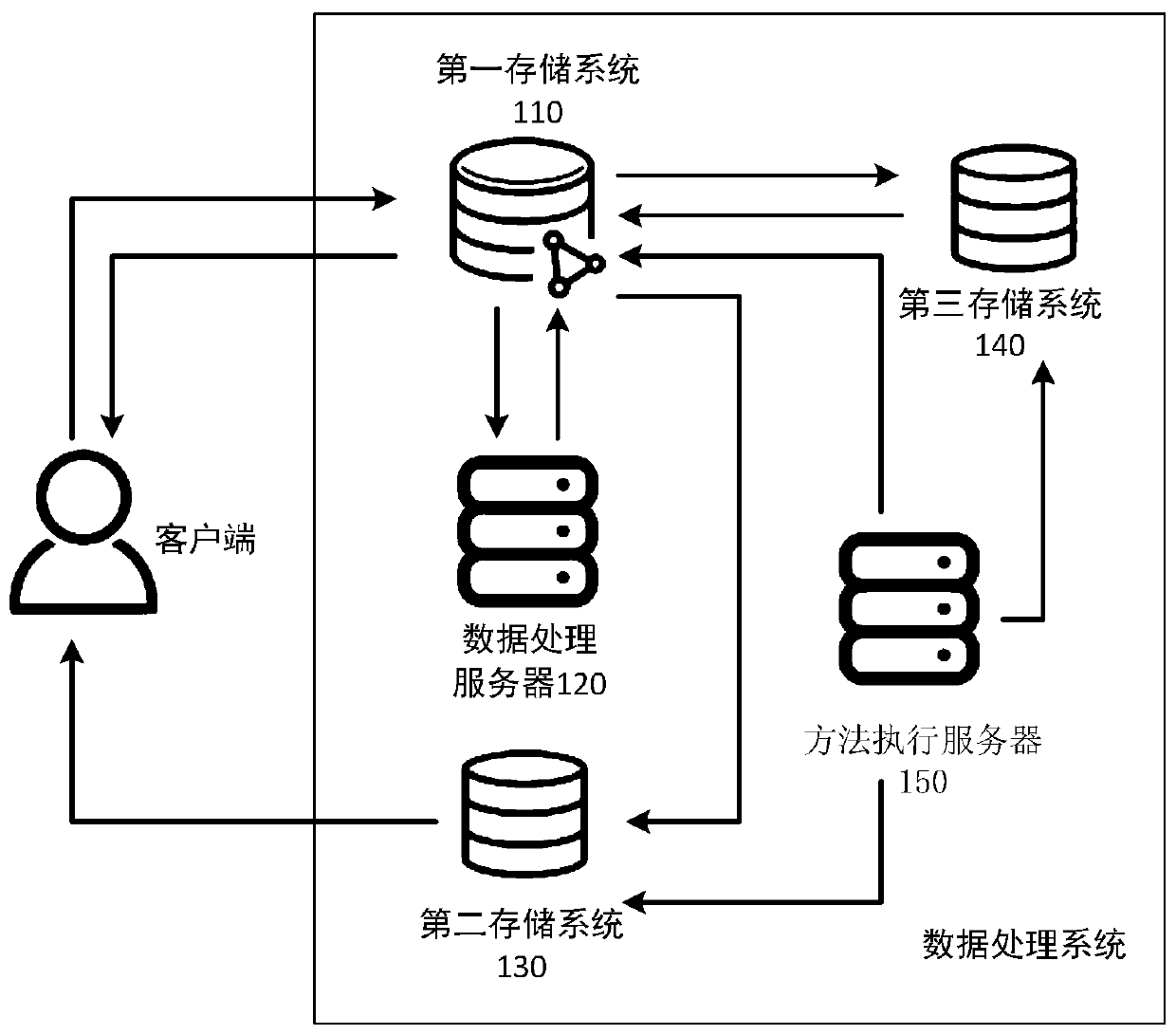
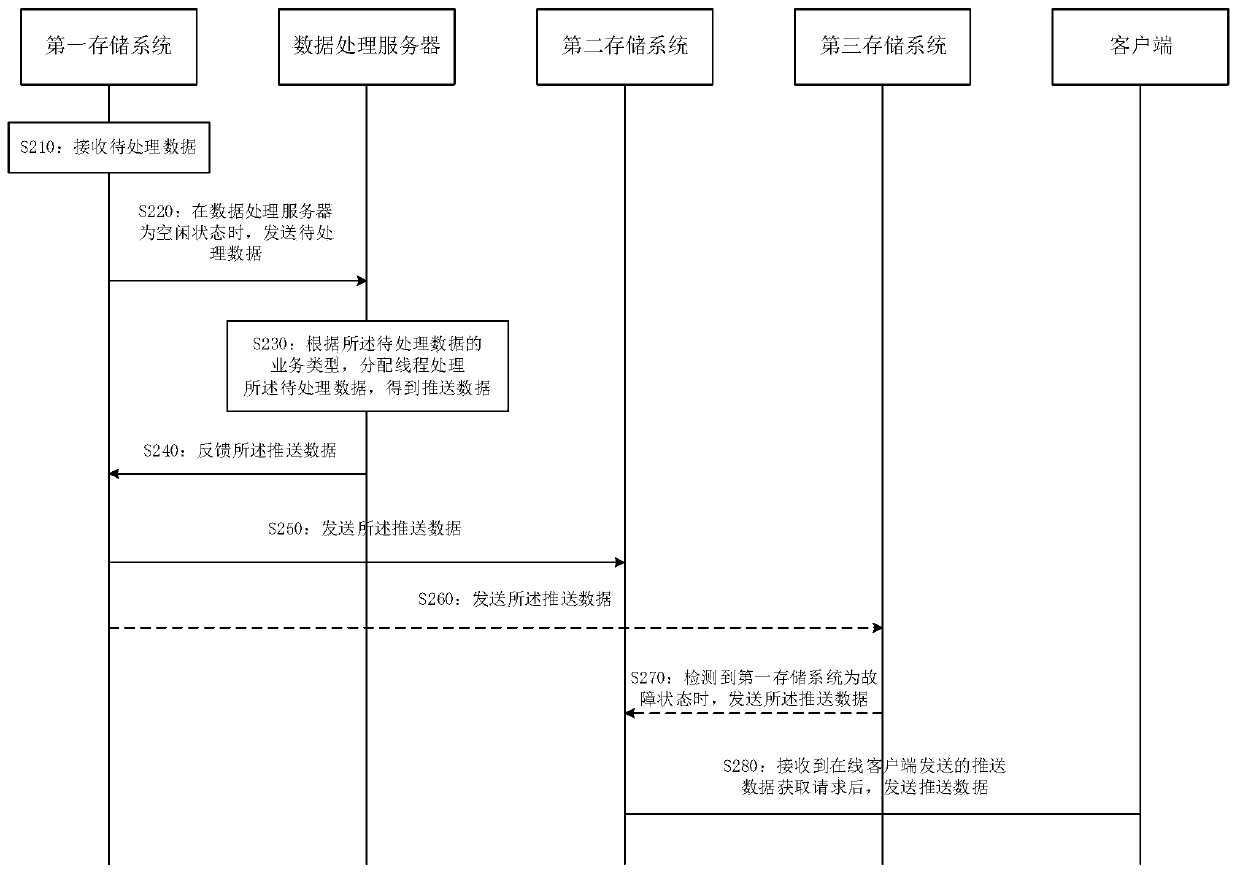
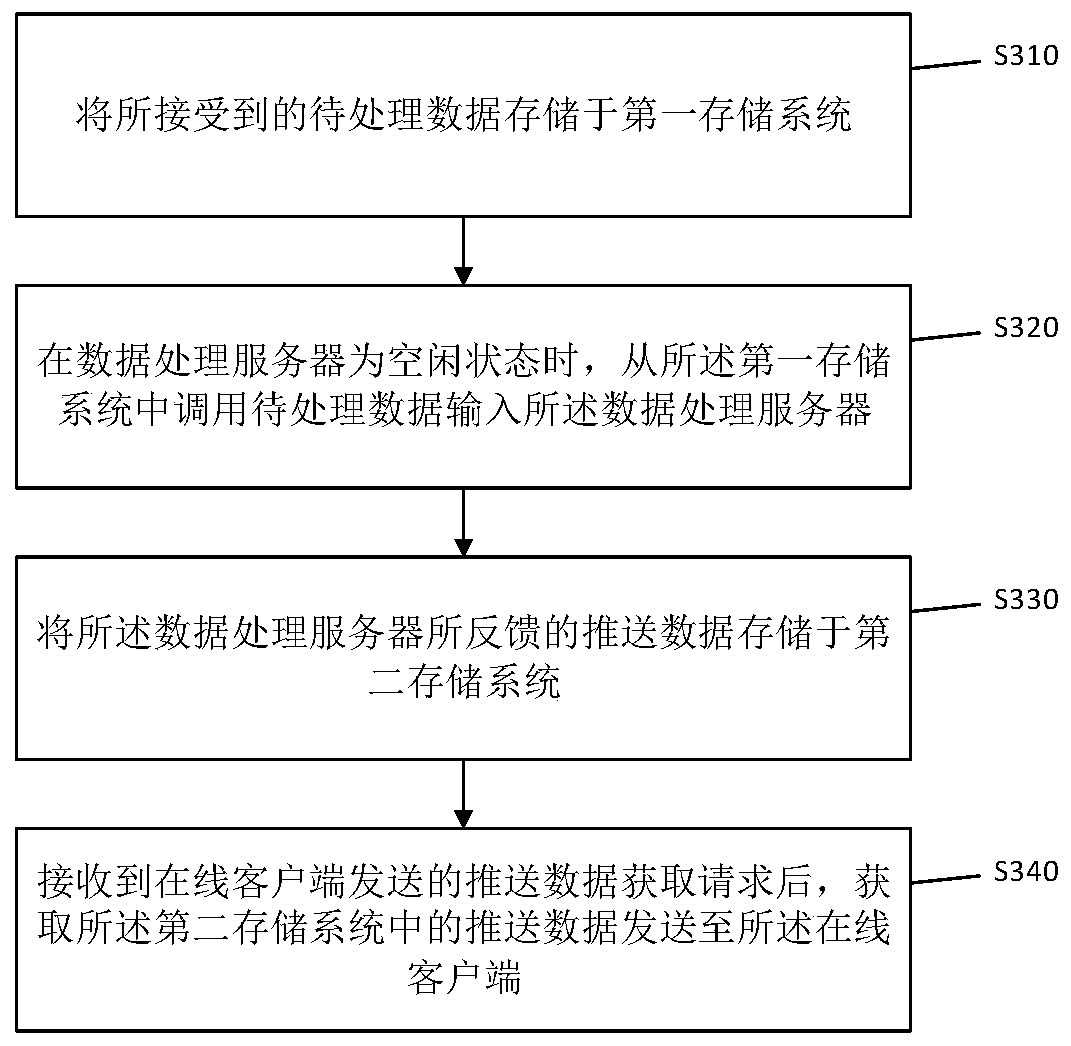
Data processing method and device
InactiveCN110413696AReduce pressure on resourcesNormal executionDatabase distribution/replicationSpecial data processing applicationsData acquisitionClient-side
The embodiment of the invention provides a data processing method and a data processing device. The method comprises the following steps: storing received to-be-processed data in a first storage system; when the data processing server is in an idle state, calling to-be-processed data from the first storage system and inputting the to-be-processed data into the data processing server; storing the push data fed back by the data processing server in a second storage system; and after receiving a push data acquisition request sent by an online client, acquiring push data in the second storage system and sending the push data to the online client. According to the method, the first storage system is used for interacting with the to-be-processed data. The additional second storage system is usedfor storing the pushed data, so that the architecture form of large database interaction amount and high resource pressure in the prior art is changed. The data processing speed is increased.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Method and device for controlling virtual character, equipment and storage medium
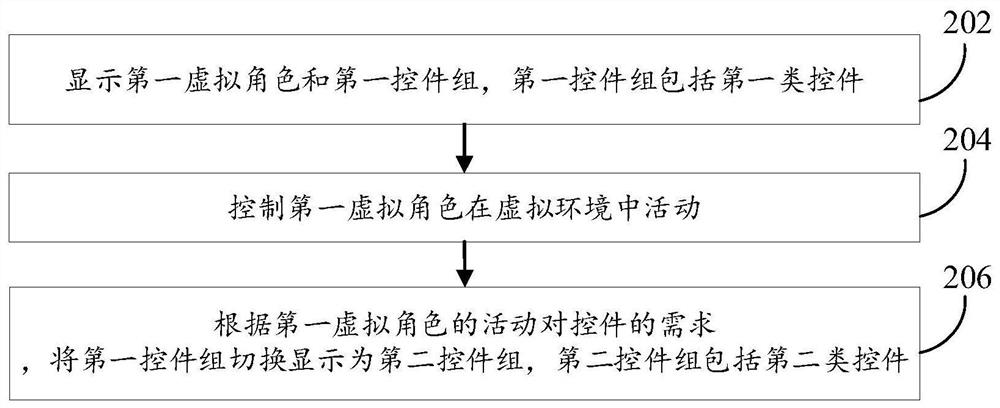
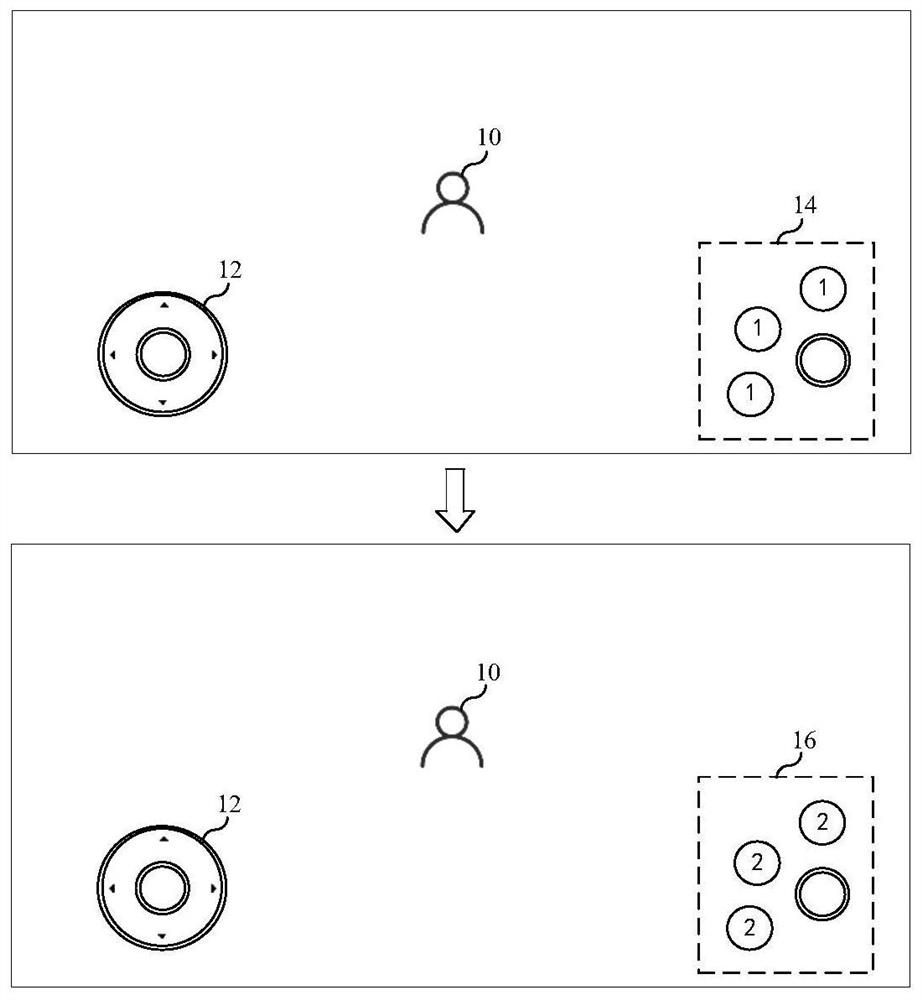
PendingCN113521724AReduce interaction stepsImprove interaction efficiencyVideo gamesInput/output processes for data processingInteraction layerControl engineering
The invention discloses a method and a device for controlling a virtual character, equipment and a storage medium, and belongs to the field of human-computer interaction. The method comprises the following steps: displaying a first virtual character and a first control group, wherein the first control group comprises first type of controls, and the first type of controls are used for triggering the first virtual character to release skills; controlling the first virtual character to move in a virtual environment; and based on the demand of the activity of the first virtual character for the controls, switching the first control group to a second control group, and displaying the second control group, wherein the second control group comprises second type of controls. According to the invention, the second type of controls can be intelligently and directly displayed on the foremost interaction level, and a user does not need to rummage the second type of controls on a deeper interaction level, so that the man-machine interaction efficiency is improved.
Owner:TENCENT TECH SHANGHAI
Display equipment, server and voice interaction method
PendingCN113079400AReduce interaction stepsImprove interactive experienceSpeech recognitionSelective content distributionData packDisplay device
The embodiment of the invention provides display equipment, a server and a voice interaction method. The display equipment comprises a display; and a controller connected with the display, wherein the controller is configured to receive a voice instruction input by a user; in responding to the voice instruction, obtain response data corresponding to the voice instruction; when the response data comprises audio data and display data, if the display data comprises answer data of the voice instruction and recommendation data of the voice instruction, generate a response interface comprising an image-text object corresponding to the answer data and a recommendation control corresponding to the recommendation data, wherein the recommendation control is configured to jump to a user interface corresponding to the recommendation control in response to triggering; and control the display to display the response interface, and control an audio output device connected with the display to play audio corresponding to the audio data. The technical problem of poor voice interaction experience is solved.
Owner:HISENSE VISUAL TECH CO LTD
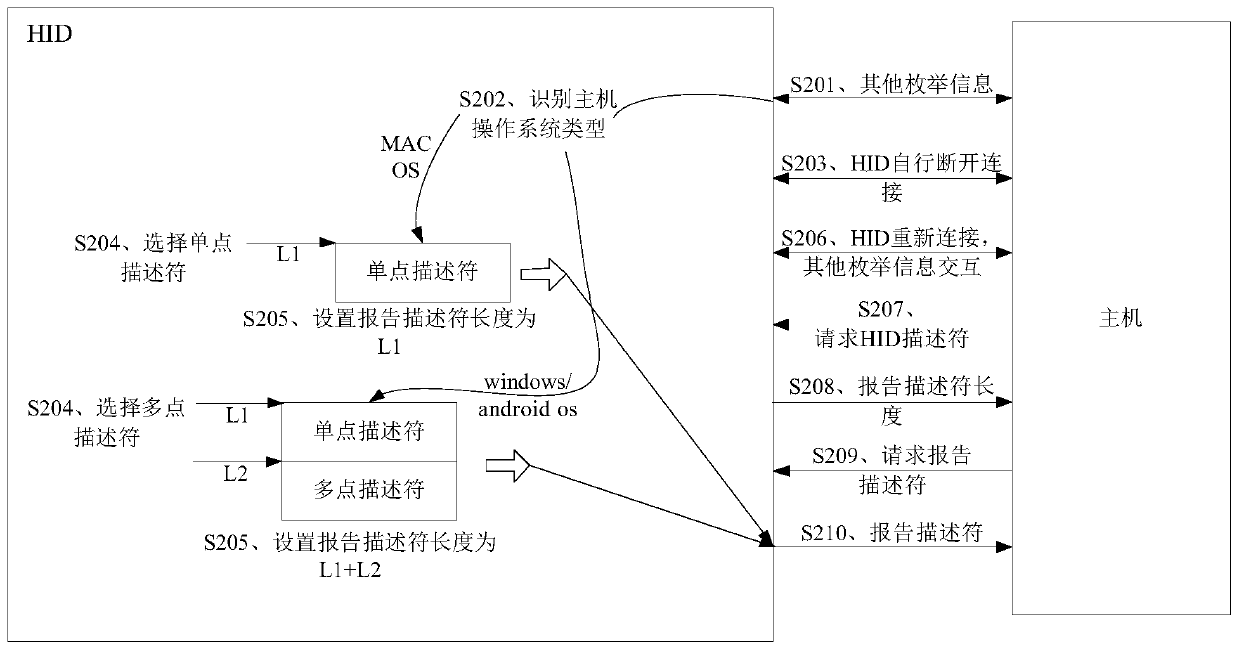
Human-computer interaction equipment enumeration processing method and device and human-computer interaction equipment
ActiveCN110688052AShorten the durationReduce interaction stepsInput/output processes for data processingInteraction deviceEngineering
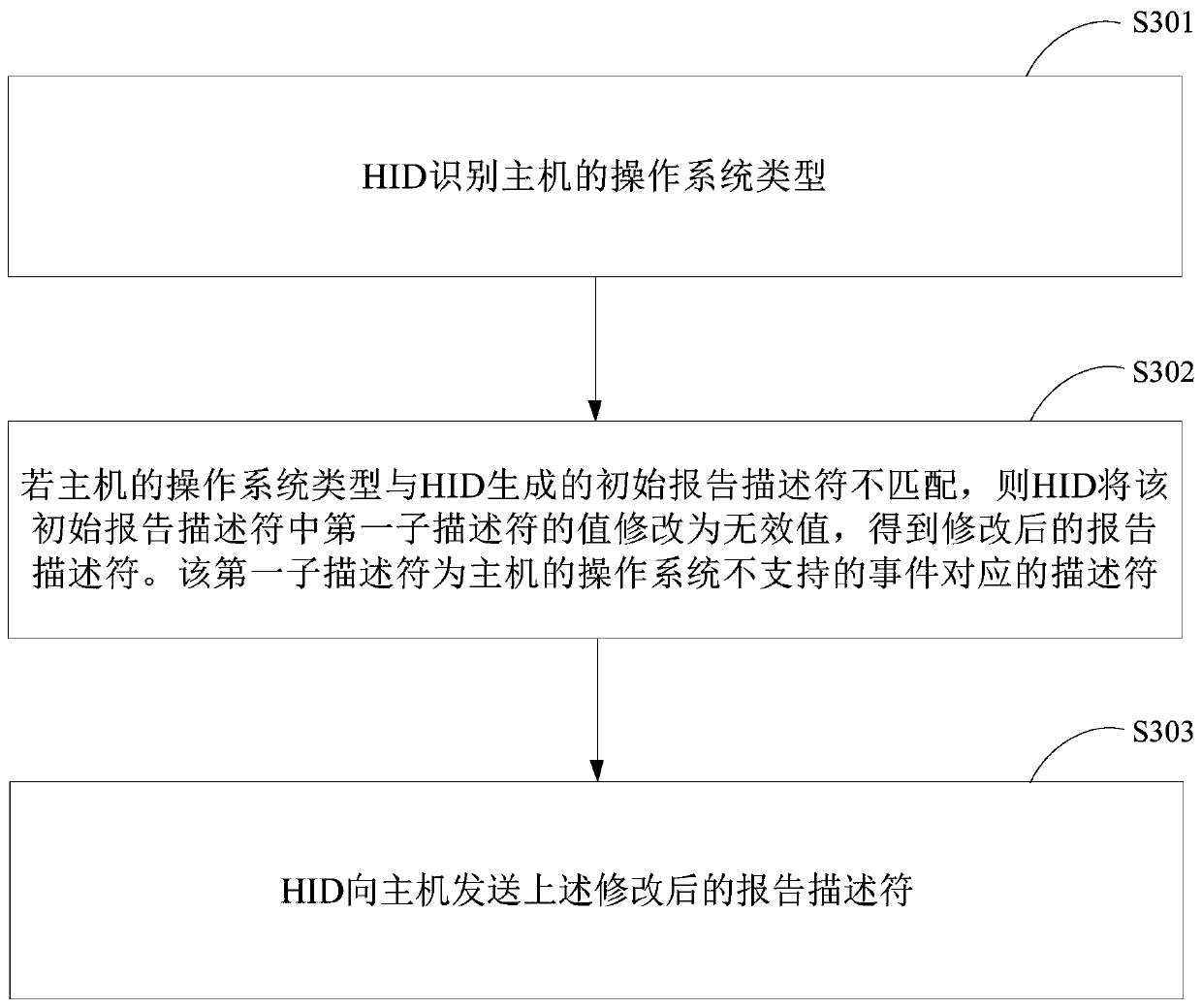
The embodiment of the invention provides a human-computer interaction device enumeration processing method and device and a human-computer interaction device. The method comprises the steps that the human-computer interaction device HID identifies the operating system type of a host; if the operating system type of the host is not matched with the initial report descriptor generated by the HID, determining that the HID is not matched with the initial report descriptor; if yes, the HID modifies the value of a first sub-descriptor in the initial report descriptor into an invalid value to obtaina modified report descriptor, and the first sub-descriptor is a descriptor corresponding to an event which is not supported by an operating system of the host; and the HID sends the modified report descriptor to the host. According to the method, the HID recognition duration can be greatly saved, and the use experience of the user is greatly improved.
Owner:GUANGZHOU SHIYUAN ELECTRONICS CO LTD +1
Human-computer interaction method for computer auxiliary design and fabrication
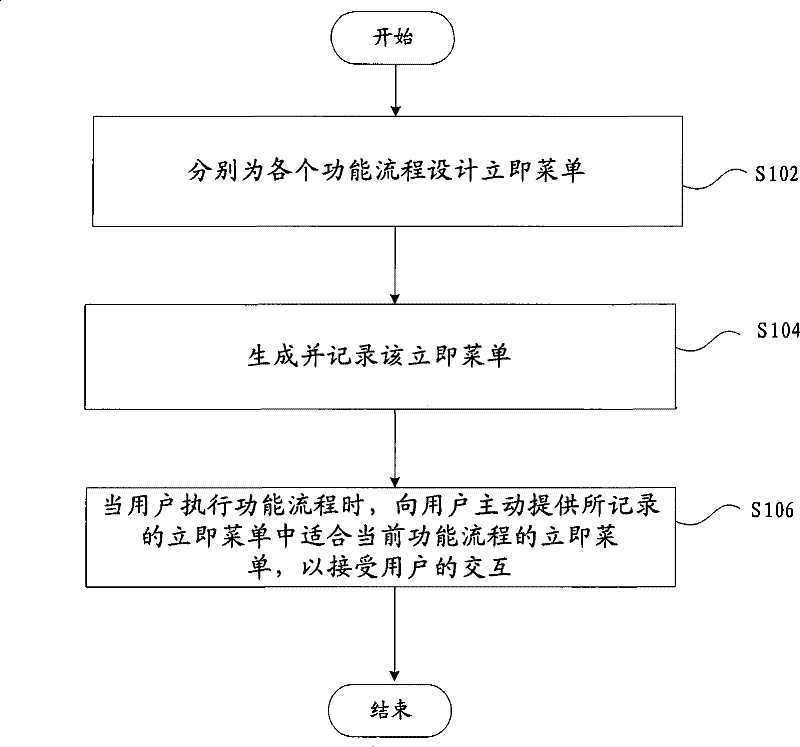
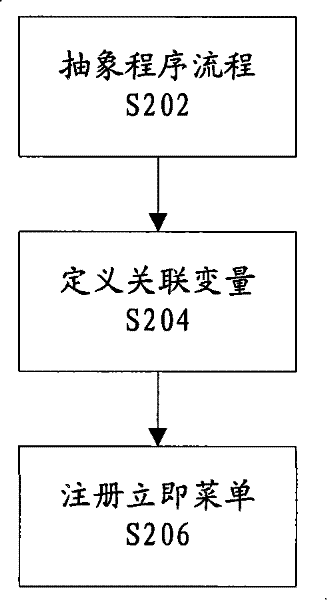
ActiveCN101599092AOvercoming the problem of many interactive stepsReduce interaction stepsSpecial data processing applicationsComputer Aided DesignHuman system interaction
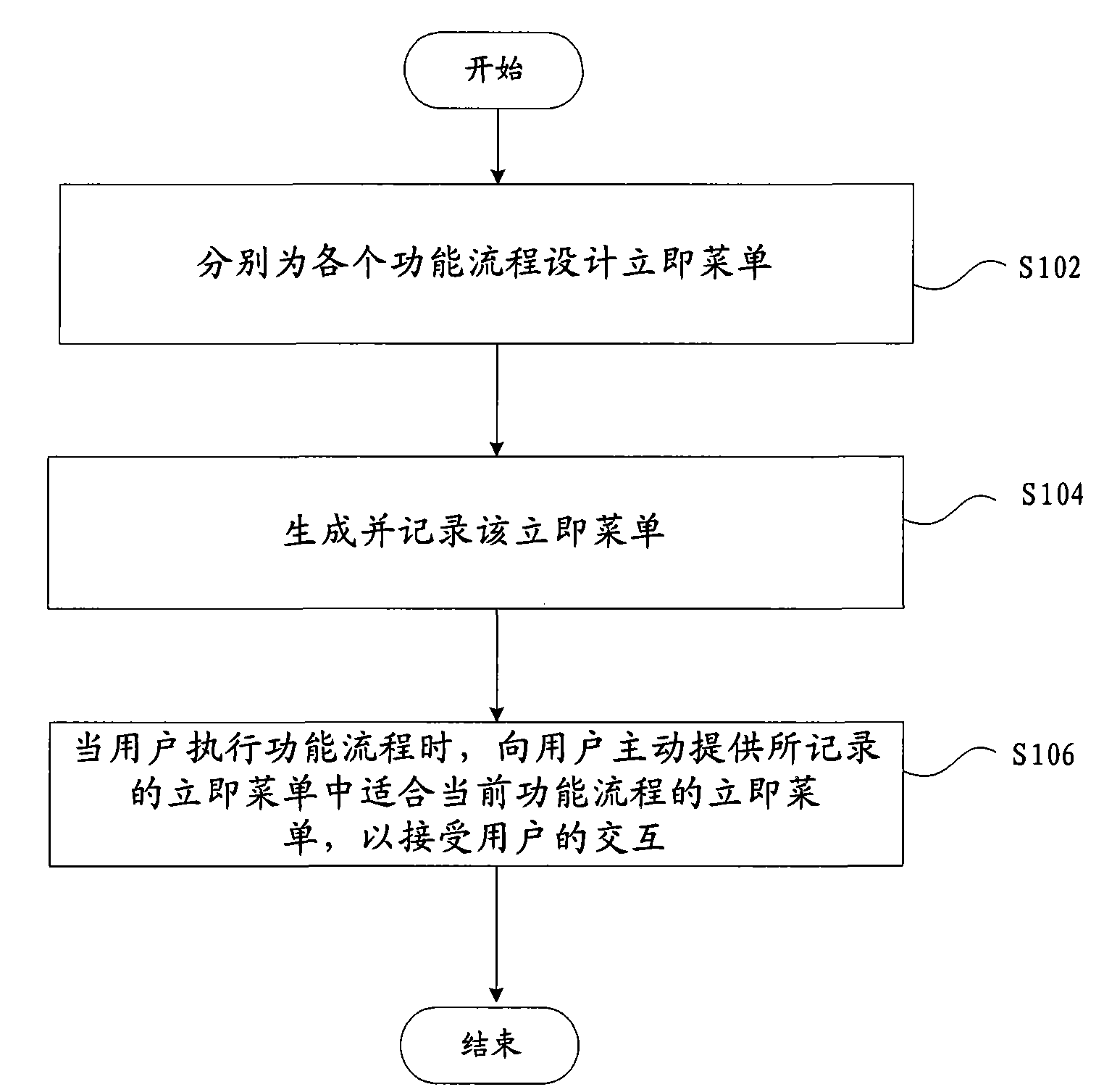
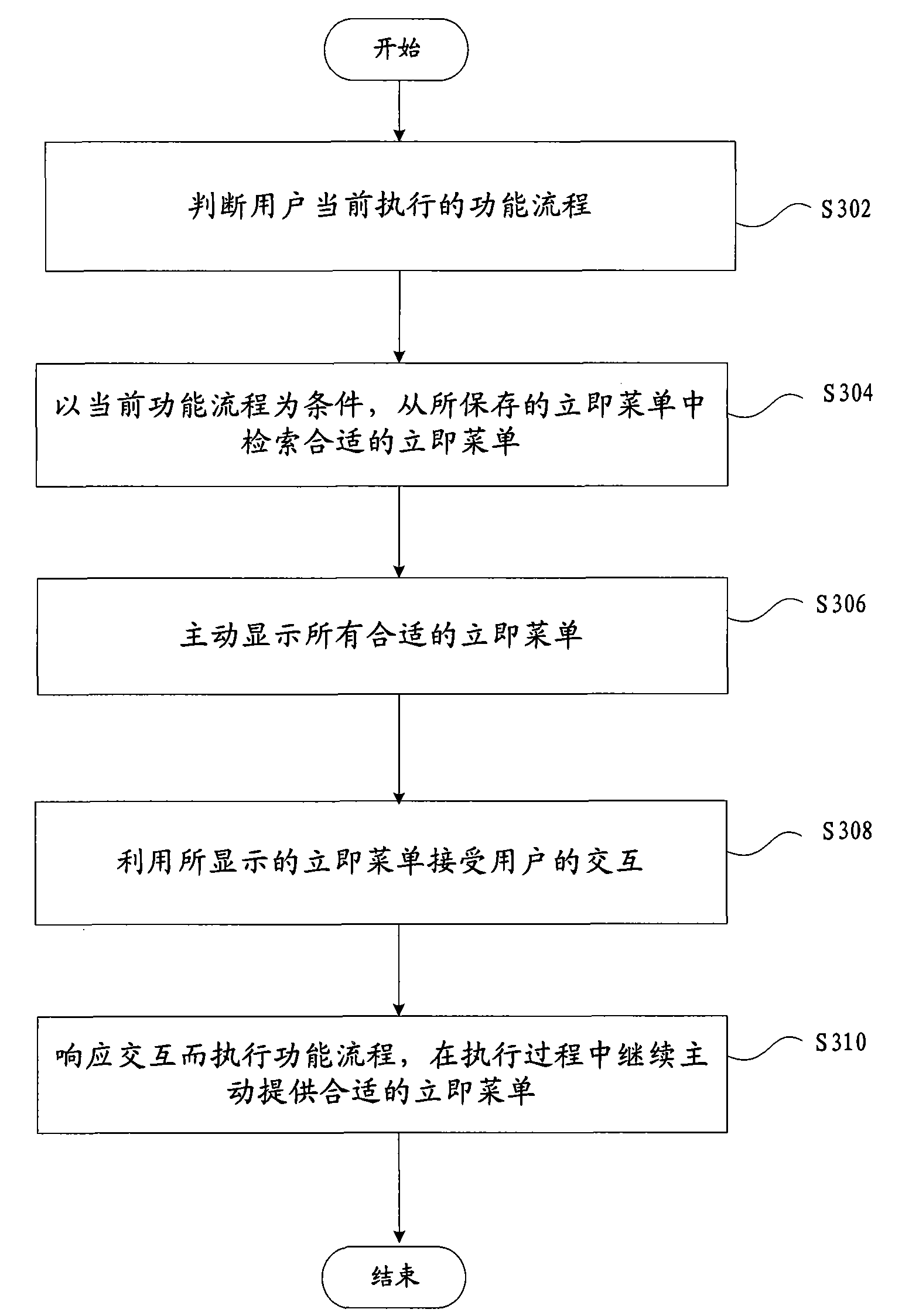
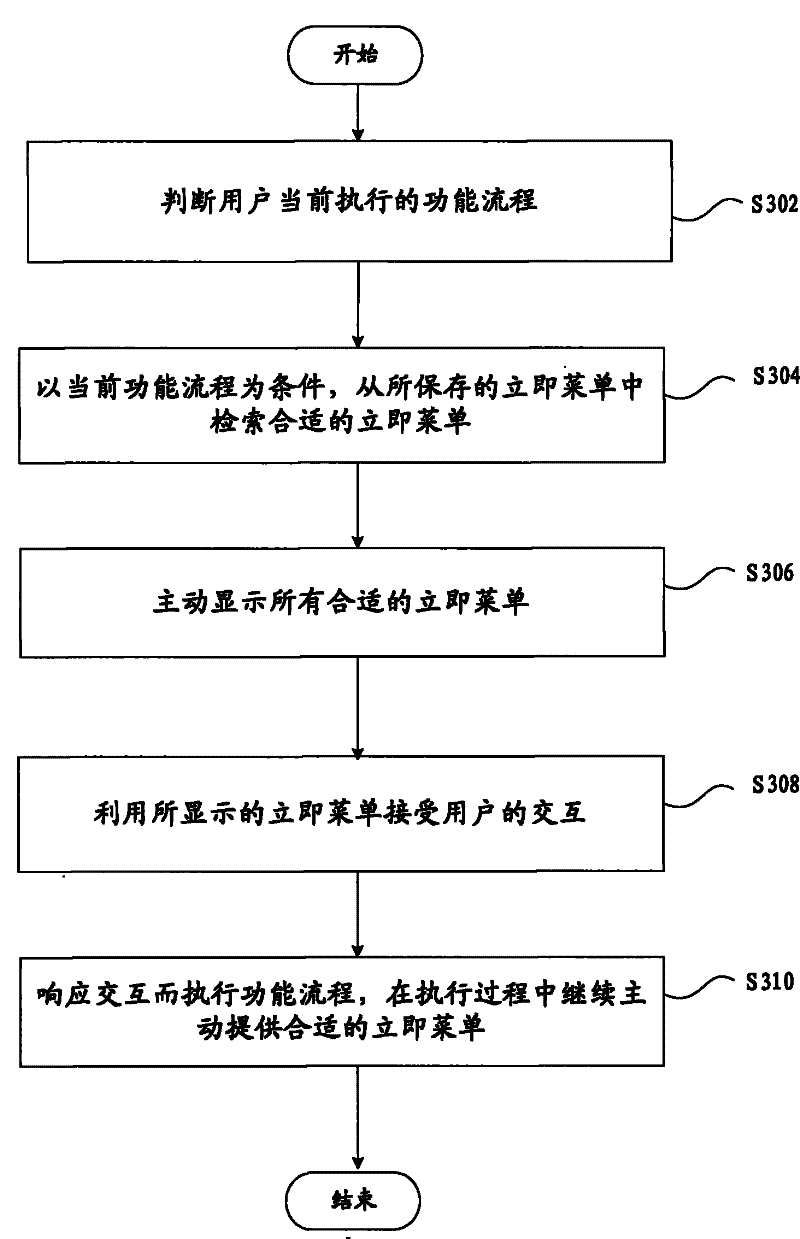
The invention provides a human-computer interaction method for computer auxiliary design and fabrication, which comprises the following steps: respectively designing an immediate menu for each functional process, wherein each immediate menu comprises possible process control selections and required parameters of each functional process and logic relation among the process control selections and the required parameters; generating and recording the immediate menus; and actively providing the immediate menu suitable to the current functional process in recorded immediate menus for a user so as to receive the interaction of the user. The invention reduces the interaction step, improves the interaction flexibility and increases the drawing efficiency.
Owner:CAXA TECH
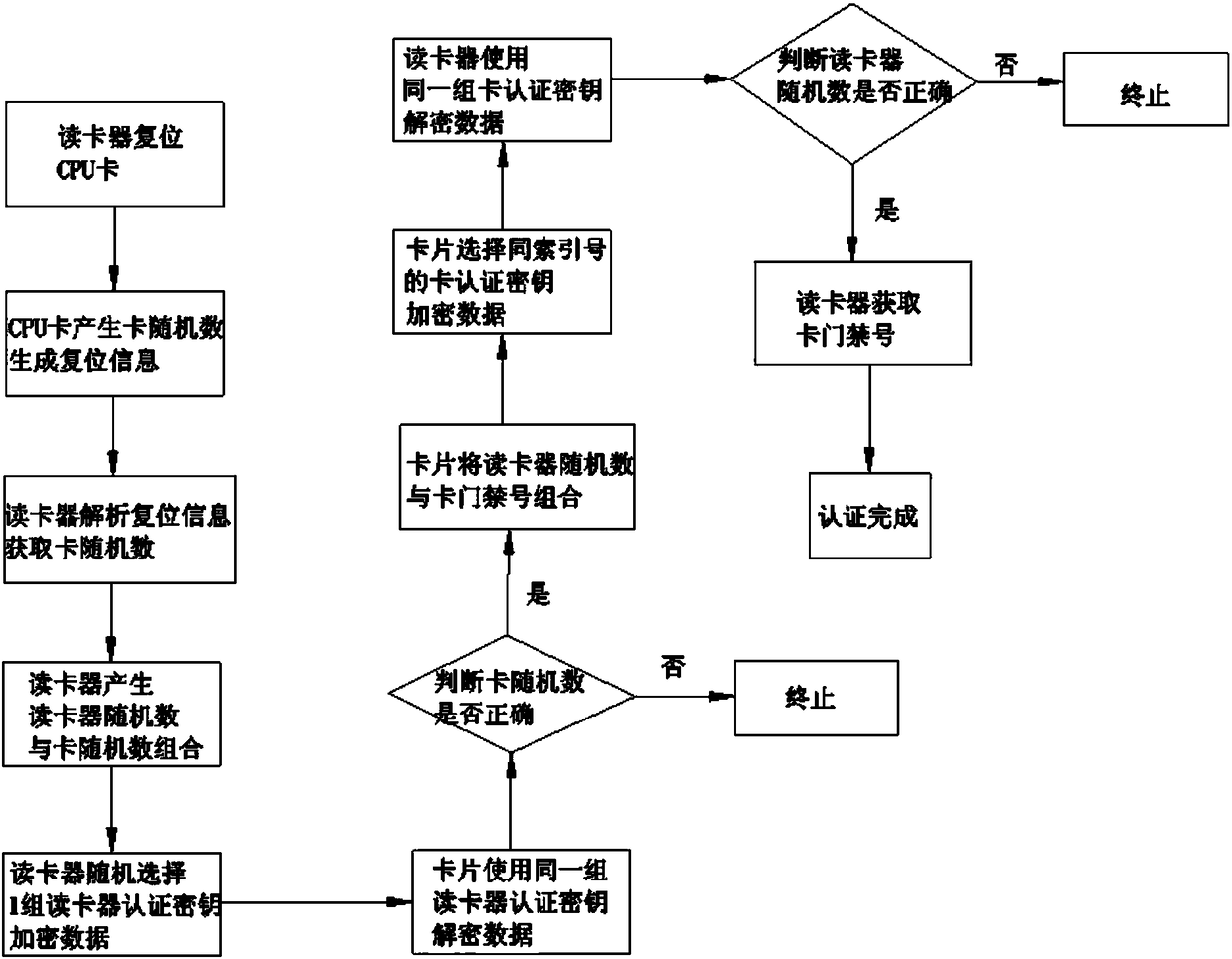
A security authentication method for a two-way authentication CPU card access control card reader
ActiveCN106056726BHigh strengthReduce interaction stepsIndividual entry/exit registersProtected modeReading card
The invention discloses a safe authentication method of a CPU card entrance guard reader capable of implementing bidirectional authentication. The authentication method is specially designed for requirement characteristics of application of an entrance guard system, an authentication step between the card reader and a CPU card is simplified, meanwhile, a bidirectional authentication mode between the CPU card and the card reader is realized, safety is greatly improved, the technical difficulty of card copying is greatly increased, a plurality of groups of keys are used, encipherment protection modes are selected randomly, and risks of violent breaking of the keys are greatly reduced; and meanwhile, steps of authenticating and reading card entrance guard numbers are simplified, and an authentication process is simplified into a group of interaction commands by card reset information.
Owner:BEIJING DINGHE SIRUI SOFTWARE TECH CO LTD
Human-computer interaction method for computer auxiliary design and fabrication
ActiveCN101599092BOvercoming the problem of many interactive stepsReduce interaction stepsSpecial data processing applicationsComputer Aided DesignHuman–robot interaction
The invention provides a human-computer interaction method for computer auxiliary design and fabrication, which comprises the following steps: respectively designing an immediate menu for each functional process, wherein each immediate menu comprises possible process control selections and required parameters of each functional process and logic relation among the process control selections and the required parameters; generating and recording the immediate menus; and actively providing the immediate menu suitable to the current functional process in recorded immediate menus for a user so as to receive the interaction of the user. The invention reduces the interaction step, improves the interaction flexibility and increases the drawing efficiency.
Owner:CAXA TECH
Method, system and device for modifying playing streaming media
ActiveCN101714977BShorten the timeReduce interaction stepsSpecial service provision for substationTwo-way working systemsComputer networkComputer science
The invention discloses a method, a system and a device for modifying playing streaming media. In the method for modifying playing streaming media, a service end receives a playing media modifying request which is sent by a client end and carries the information of playing media needed to be modified by the current play channel, and the service end modifies the playing media according to the request. The method disclosed by the invention can be realized on the system and the device disclosed by the invention which can provide high-quality streaming media playing service for users.
Owner:HUAWEI TECH CO LTD
Method, system and device for switching stream media channel and altering broadcast media
ActiveCN101137043BShorten the timeReduce interaction stepsPulse modulation television signal transmissionTwo-way working systemsDelayed timeComputer science
This method includes: (1) the server end (SE) receives frequency channel (FC) switching request with the old FC info (OFI) and the new FC flow-media address (NFFA) sent by user end (UE). (2) accordingto the result of comparing OFI with the residing server group info corresponding to NFFA, judging that need not to build a new conversation, SE responds UE the FC switching reply. (3) SE receives thenew FC playing request sent by UE and uses the old FC conversation to play new FC media flow toward UE. The method of this invention can be realized on the system and device disclosed in this invention. This invention can reduce the delay time during flow-media FC switching and offers a hi-quality flow-media playing service for users.
Owner:HUAWEI TECH CO LTD
A method for operating a folder and a mobile terminal
ActiveCN106055195BImprove processing efficiencyEasy to operateFile/folder operationsSpecial data processing applicationsProcess efficiencyApplication software
The invention discloses an operating method for a folder and a mobile terminal. The method comprises following steps: obtaining operation of folders displayed on a display interface of the mobile terminal, wherein an application icon of at least one application program is arranged in a folder; and displaying a preview list on the display interface when detecting operation is matched with pre-set operation, wherein the preview list comprises unread prompt message sets of application programs corresponding to all application icons in the folder.The operating method for the folder and the mobile terminal have following beneficial effects: without entering an application program, unread messages of application programs corresponding to application icons in the folder can be searched. After searching unread messages, operation can be performed. The operation steps are simple and interaction processes are few. Processing efficiency of unread messages in the folder is greatly increased.
Owner:VIVO MOBILE COMM CO LTD
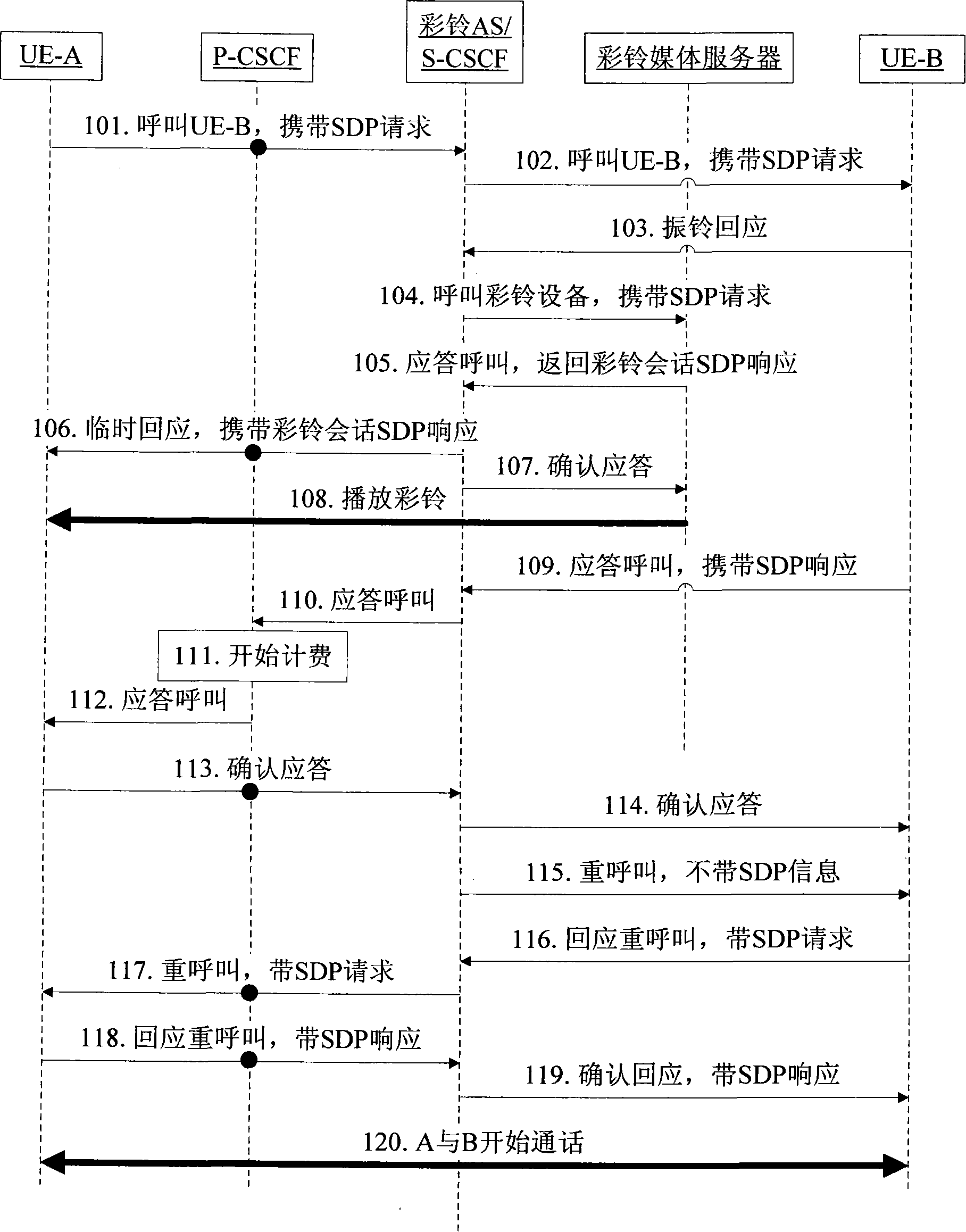
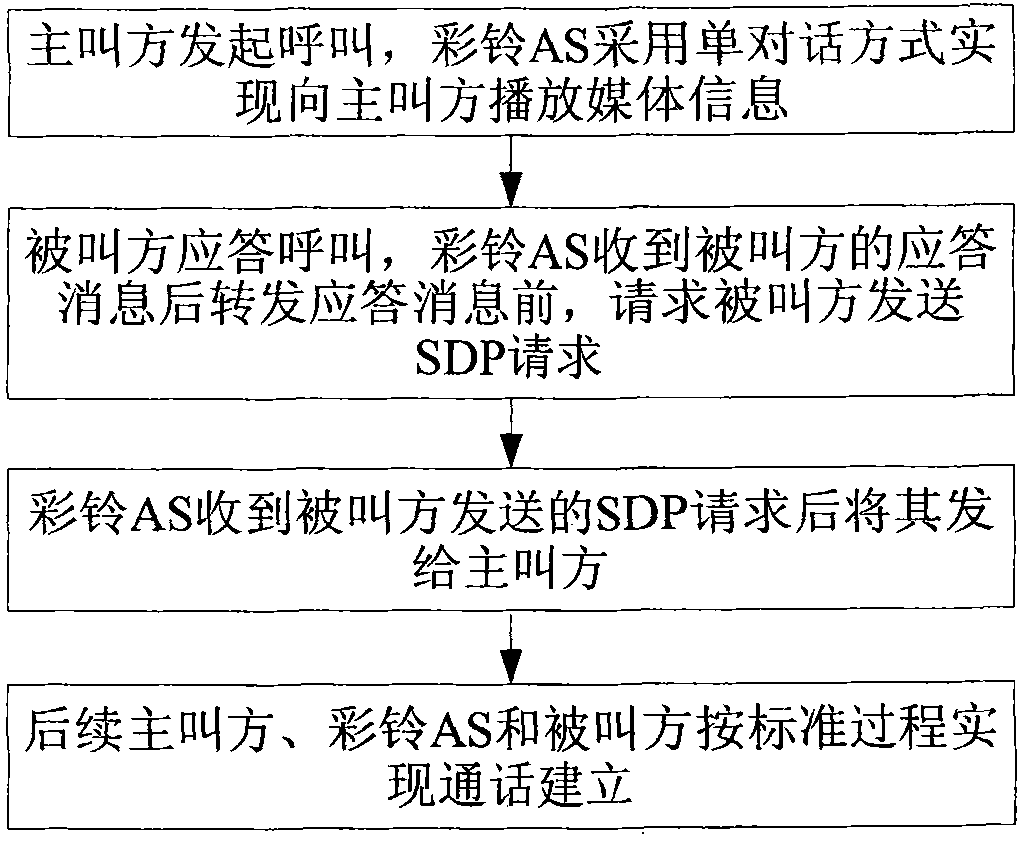
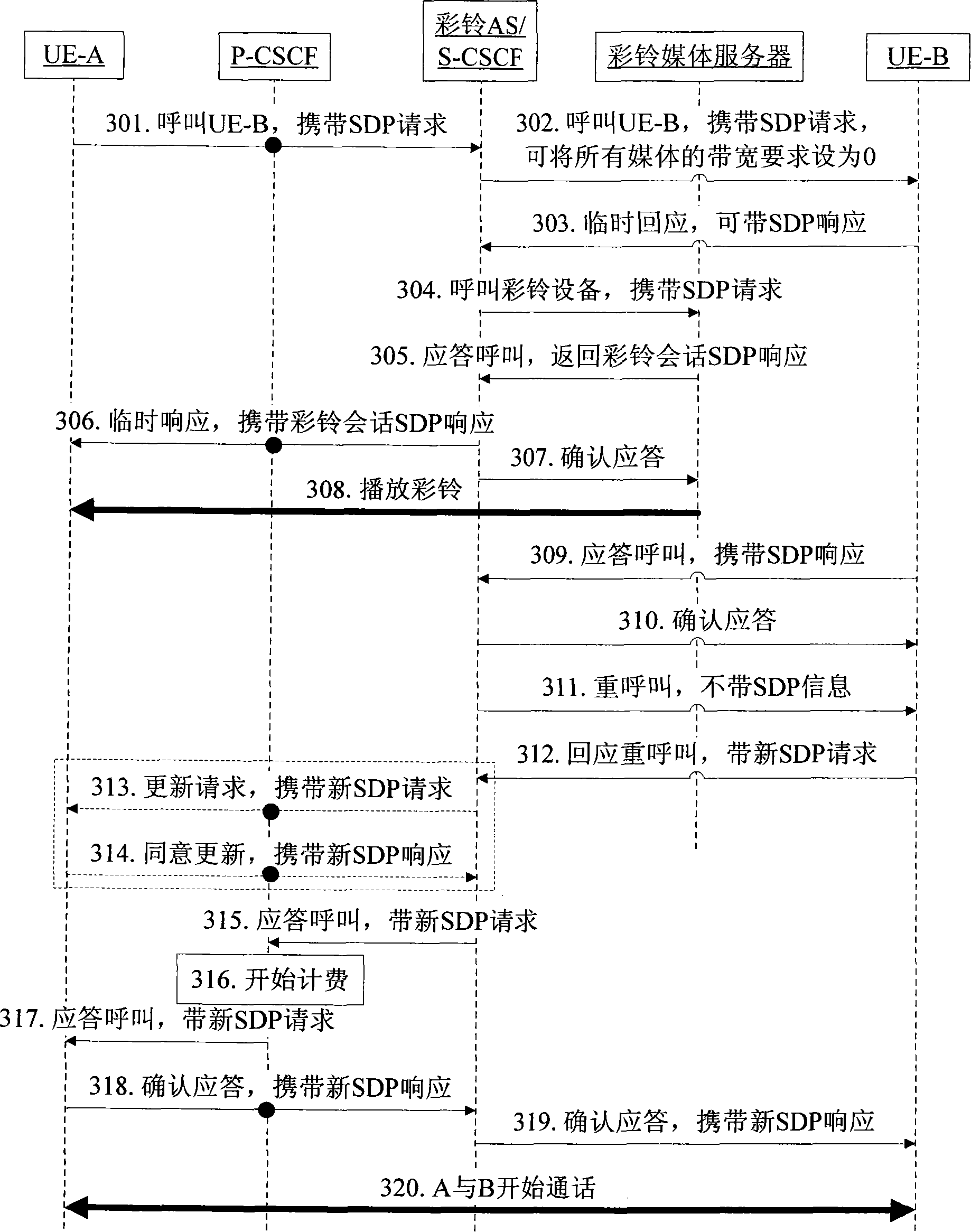
Call-establishing method for realizing single-conversation color ring back tone service
InactiveCN101448046BImprove experiencePrevent data delivery errorsInterconnection arrangementsSpecial service for subscribersTelecommunicationsApplication server
The invention discloses a call-establishing method for realizing single-conversation coloring ring back tone service. The method comprises the steps as follows: a calling party initiates a call, and a coloring ring back tone application server (AS) plays media information to the calling party in a single-conversation way; a called party answers the call, and after receiving the response information of the called party and before transmitting the response information, the coloring ring back tone AS requests the called party to send an SDP request; the coloring ring back tone AS sends the SDP request to the calling party after receiving the SDP request sent by the called party; and the calling party, the coloring ring back tone AS and the called party realize the call establishment by a standard process. The technical proposal improves the processing after the called party responds, reduces the interactive steps after the response and adjusts the time for starting charging, thereby simplifying the process between responding and starting the call greatly, improving the experience of a user and avoiding charging by mistake.
Owner:ZTE CORP
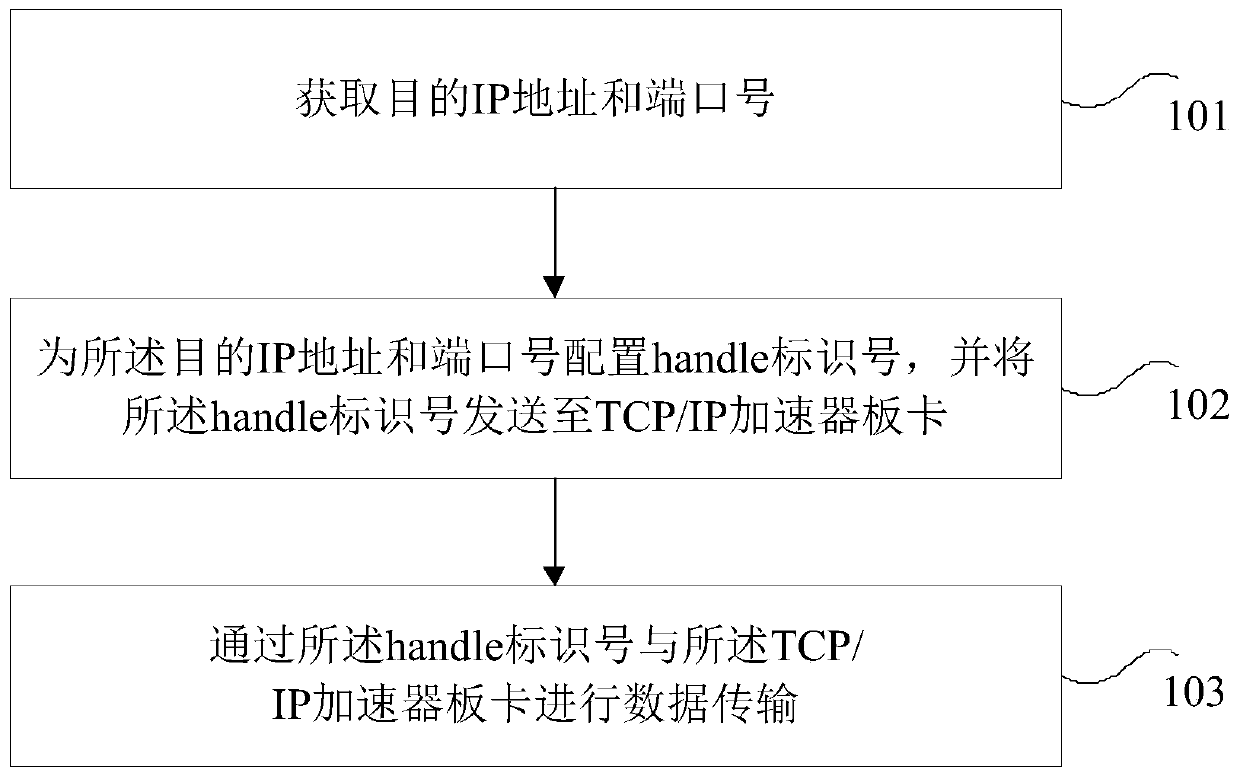
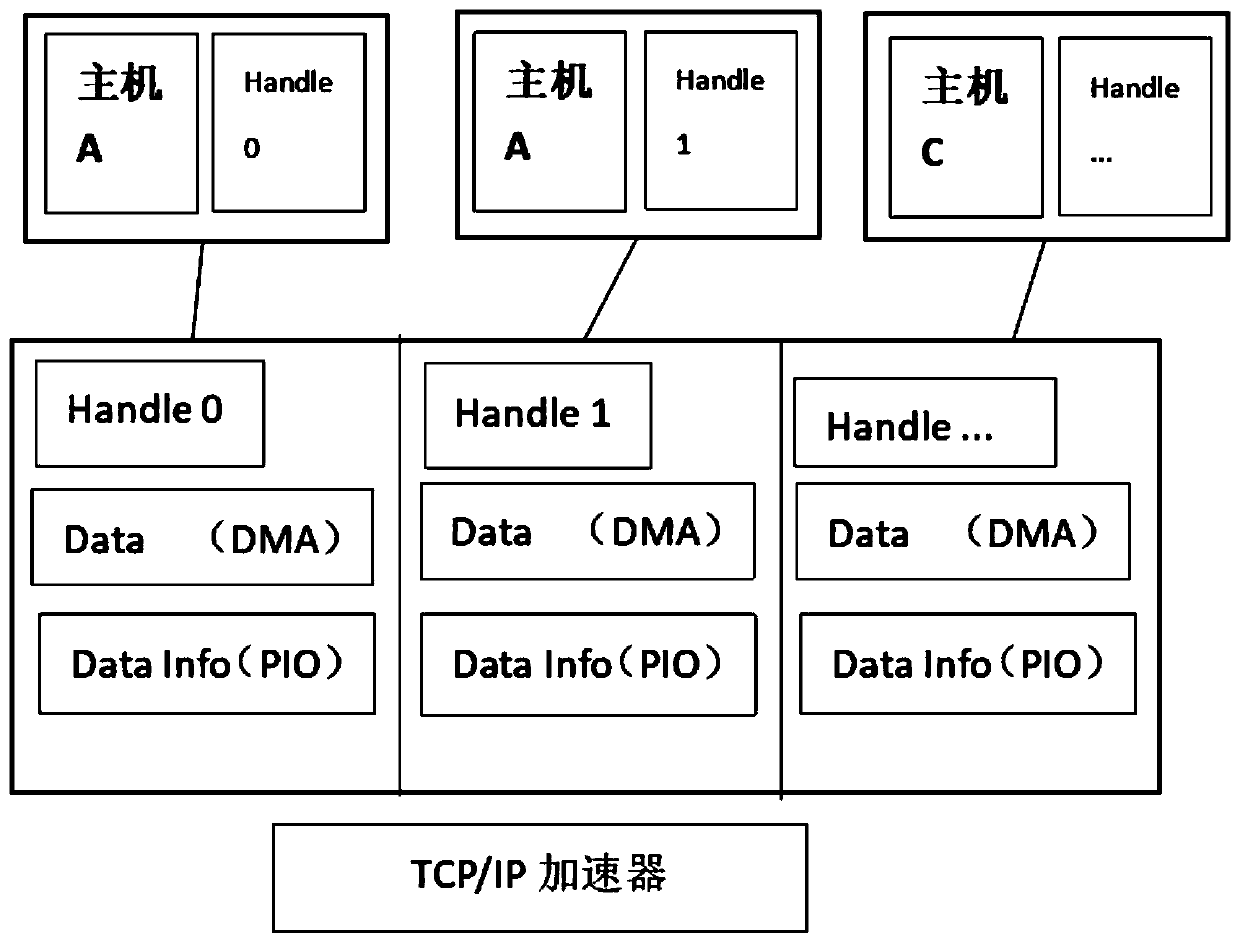
Data transmission method and device
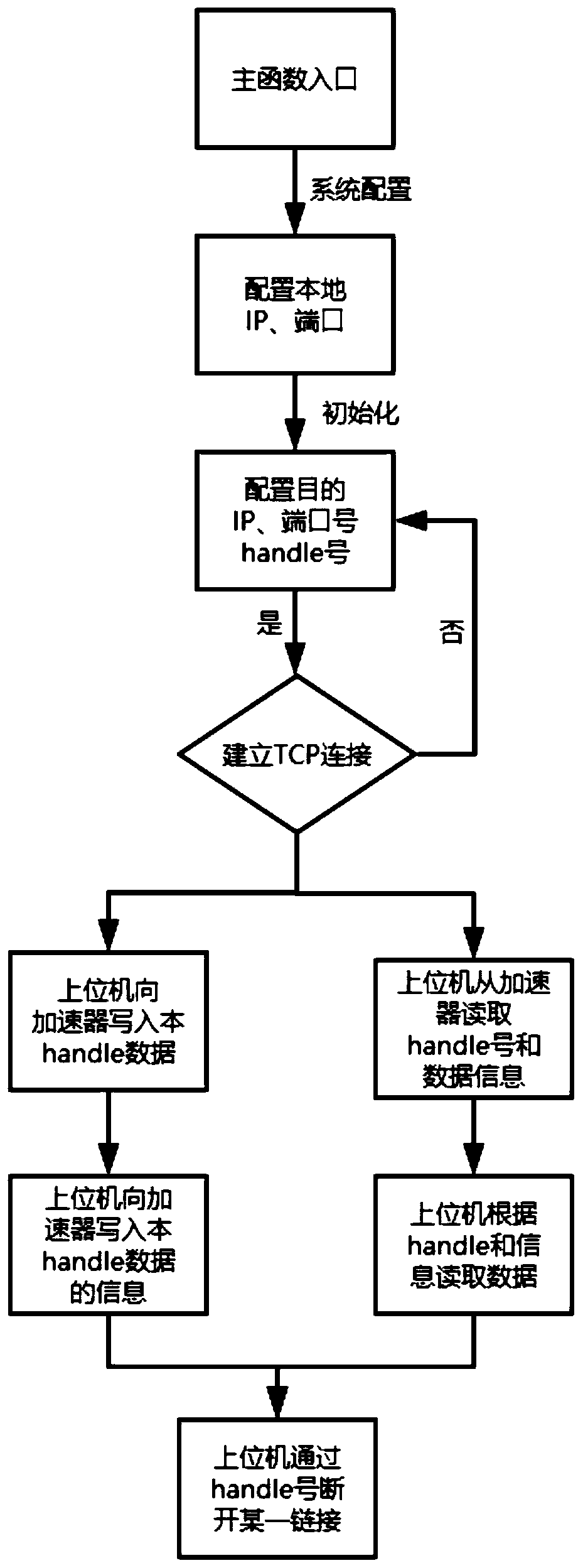
ActiveCN111245794AEasy to handleReduce interaction stepsTransmissionEmbedded systemData transmission
The invention provides a data transmission method and device, and the method comprises the steps: obtaining a destination IP address and a port number; configuring a handle identification number for the destination IP address and the port number, and sending the handle identification number to a TCP / IP accelerator board card; and performing data transmission with the TCP / IP accelerator board cardthrough the handle identification number. By means of the mode, the possibility of congestion in the data transmission process is avoided, hardware resources are saved, and therefore the processing performance of the TCP / IP accelerator is improved.
Owner:YUSUR TECH CO LTD
Shooting image sharing method, device, mobile terminal and readable storage medium
ActiveCN112839163BReduce interaction stepsImprove experienceTelevision system detailsColor television detailsComputer hardwareImage sharing
The invention discloses a shooting image sharing method, device, mobile terminal and readable storage medium. The method includes: when the mobile terminal is in the shooting interface of the camera mode, responding to the preset sharing trigger operation of the shooting image by the user, displaying the preset An application list is set, and the captured image is shared to target applications in the preset application list according to the user's selection operation. The technical solution of the present invention can realize fast sharing of the latest captured images in the camera mode, and compared with the existing sharing operation, it reduces the interaction steps with the user and the jumps with other applications, It is convenient and fast, and improves the user experience.
Owner:ONEPLUS TECH SHENZHEN
Intelligent touch system, operation method and vehicle
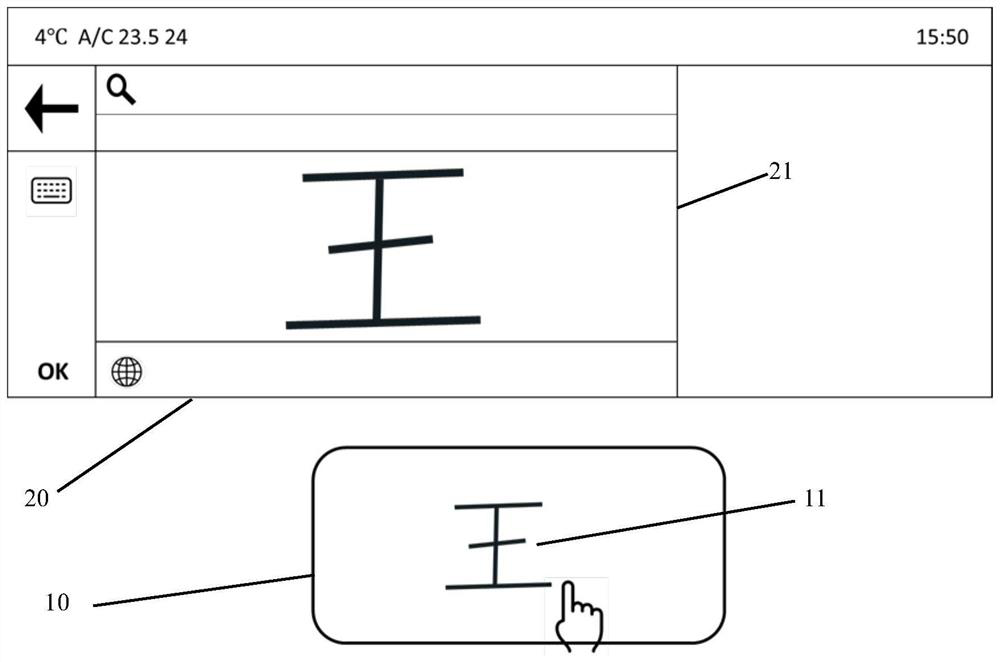
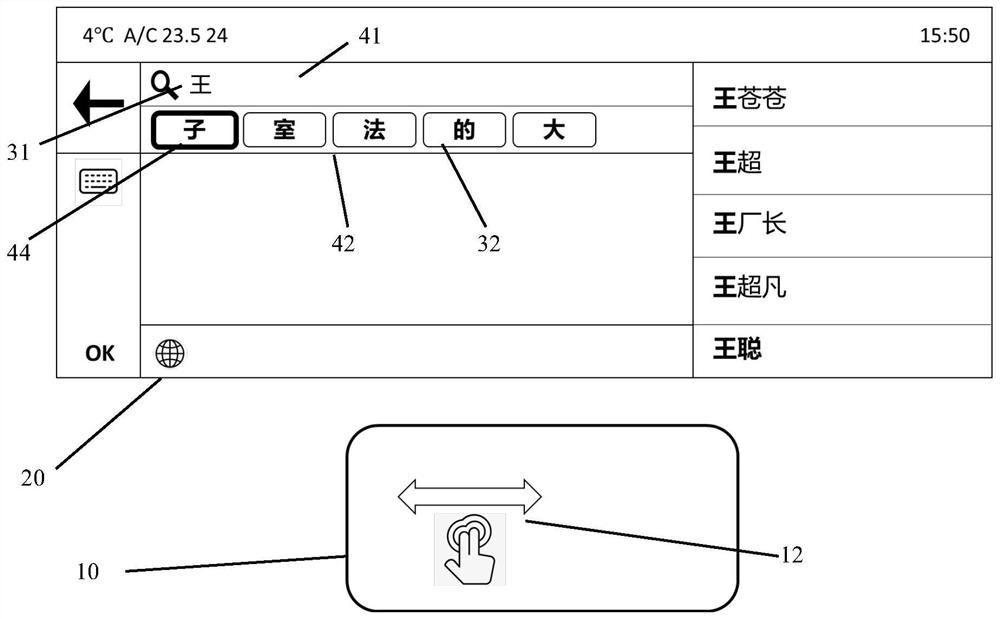
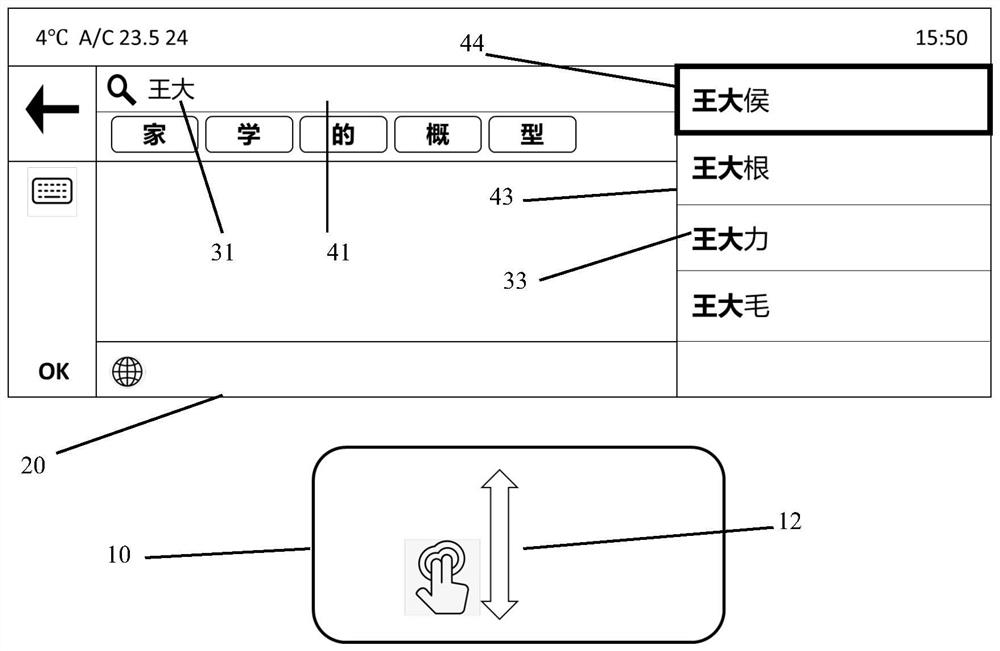
PendingCN114764302AImprove experienceReduce interaction stepsVehicle componentsInput/output processes for data processingComputer hardwareHandwriting
The invention provides an operation method of an intelligent touch control system, which comprises the following steps: inputting a handwritten signal on an intelligent touch control pad, identifying the handwritten signal as a first word by the intelligent touch control system, and generating a plurality of second words and a plurality of third words according to the first word; and selecting the required second word or third word by inputting a gesture signal on the intelligent touch pad. According to the operation method of the intelligent touch control system, a user does not need to switch to a vehicle-mounted touch screen in the handwriting process, the whole handwriting process can be completed only through the intelligent touch pad, and therefore interaction steps can be reduced, and user experience is improved.
Owner:PEZHO SITROEN AUTOMOBILS SA
Application switching method, device, electronic device and storage medium
ActiveCN110602321BImprove efficiencyReduce interaction stepsDevices with sensorSubstation equipmentComputer hardwareComputer graphics (images)
Owner:TENCENT TECH (SHENZHEN) CO LTD
Authentication method and system based on application login and computer readable storage medium
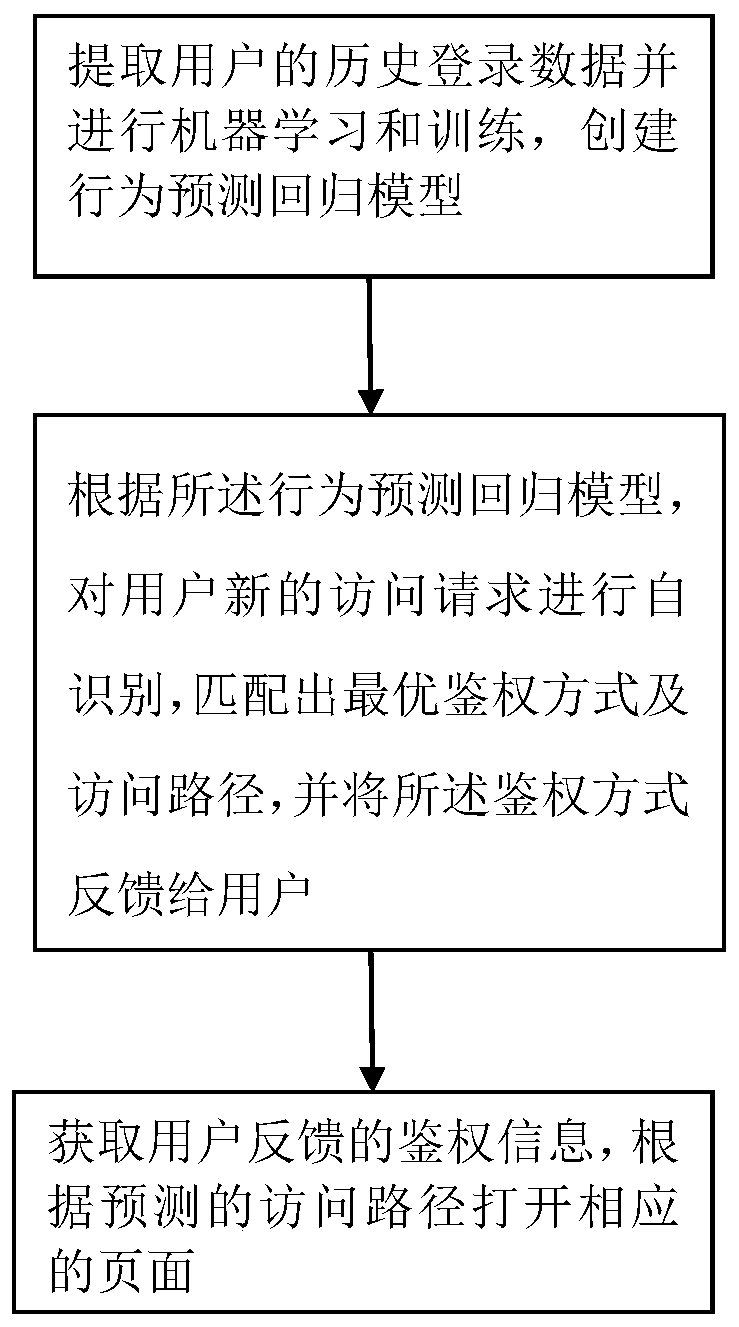
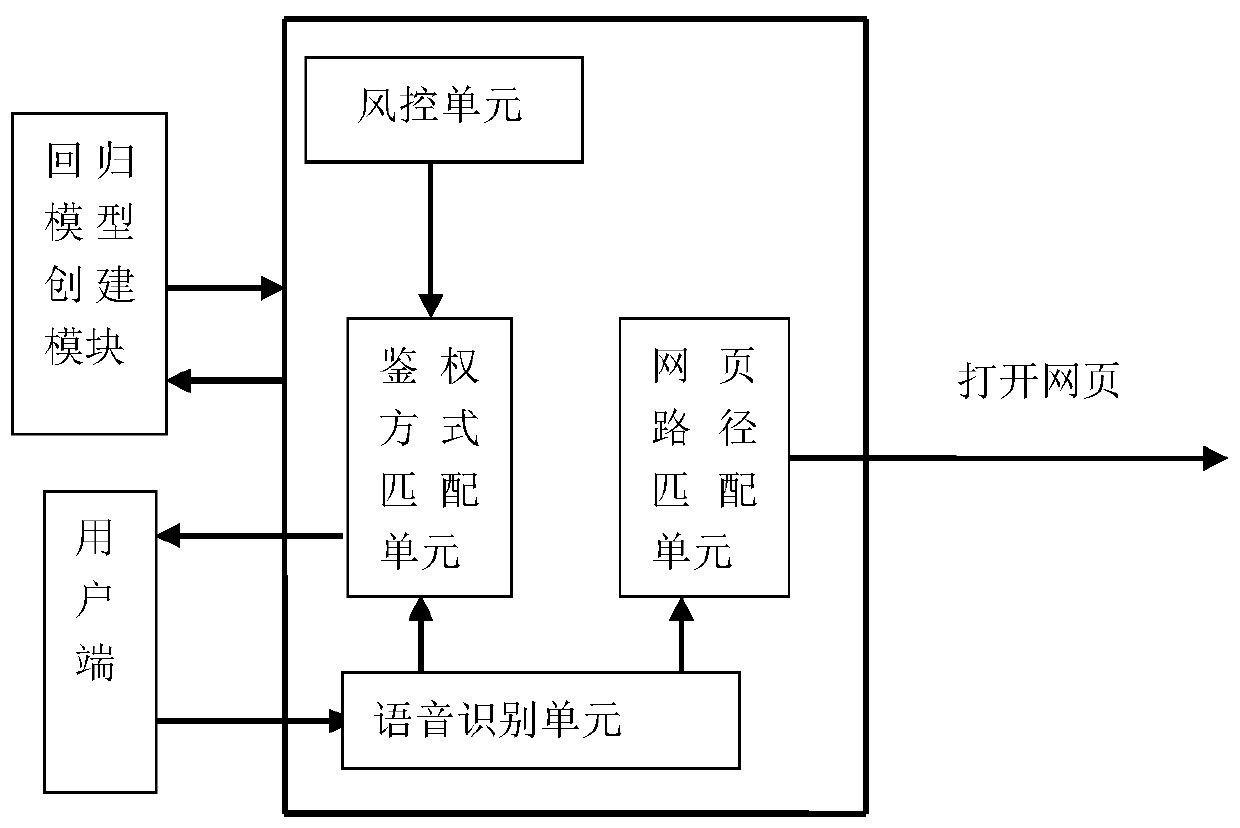
PendingCN111581608AImprove operational efficiencyReduce interaction stepsDigital data information retrievalDigital data authenticationTheoretical computer scienceEngineering
The invention discloses an authentication method based on application login, and the method comprises the steps: extracting the historical login data of a user, and creating a behavior prediction regression model; according to the behavior prediction regression model, identifying a new access request of the user, performing matching to obtain an optimal authentication mode and an access path, andfeeding back the authentication mode to the user; and obtaining authentication information fed back by the user, and opening a corresponding page according to the predicted access path. According to the invention, the login data of the user is extracted; big data storage is utilized, the data is analyzed and trained through machine learning to obtain the customized regression model, and the most common and most convenient login authentication mode of the user is intelligently predicted according to the login history and habit of the user, so that the interaction steps between the user and theapplication system are reduced, the operation efficiency of the user is improved, and the user experience is improved.
Owner:SUNING CLOUD COMPUTING CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com