Patents
Literature
83 results about "Certificate signing request" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
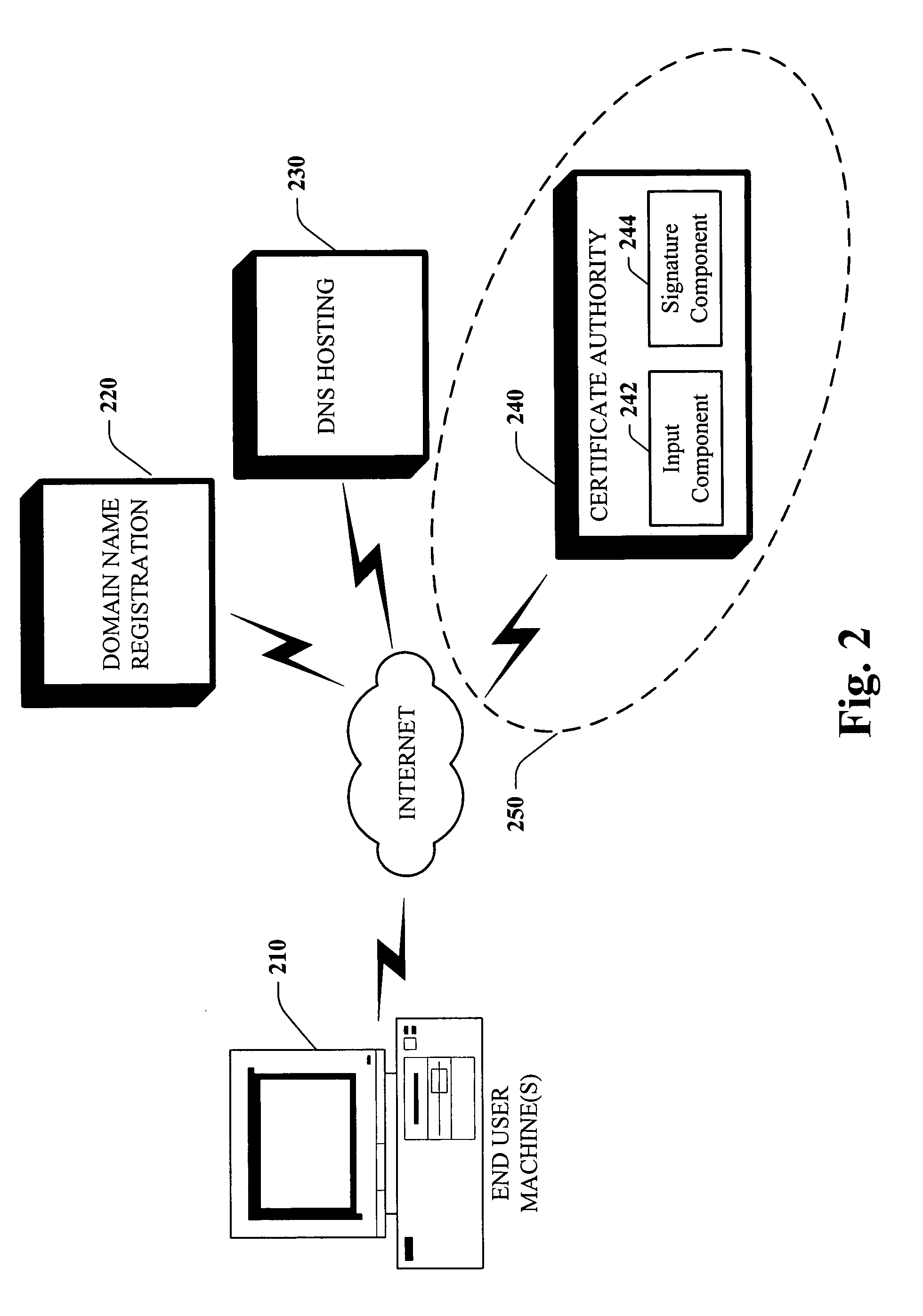
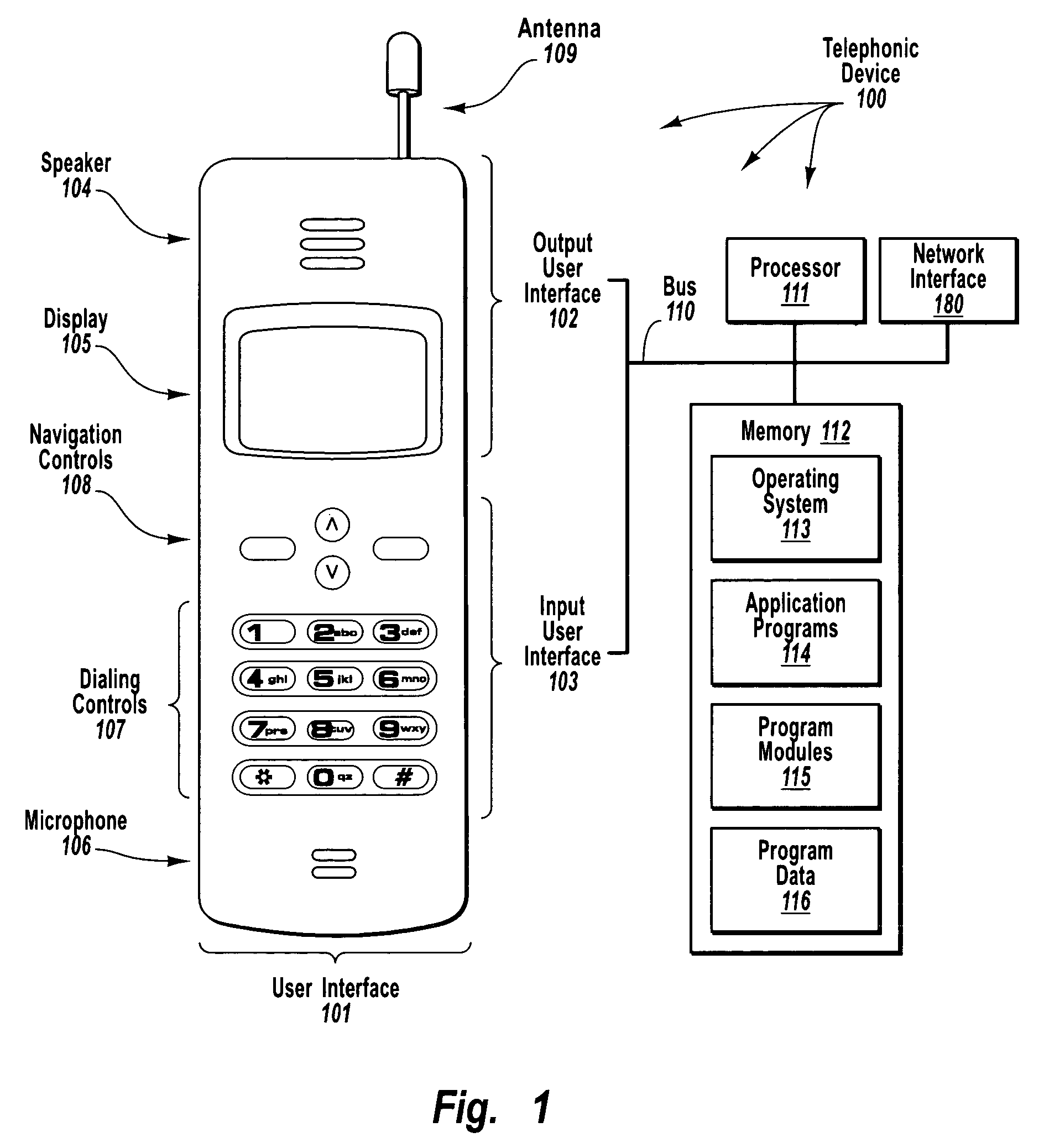
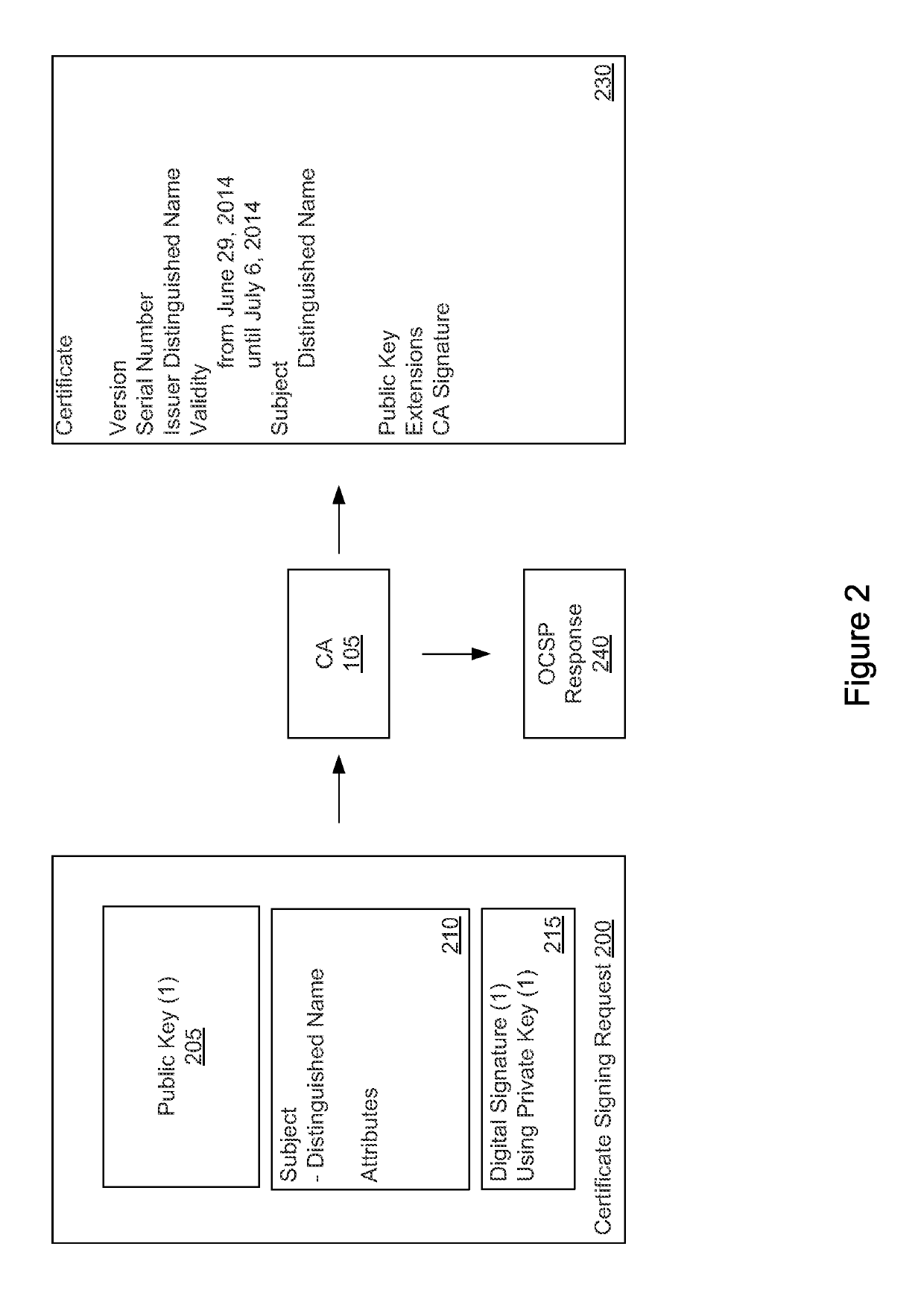
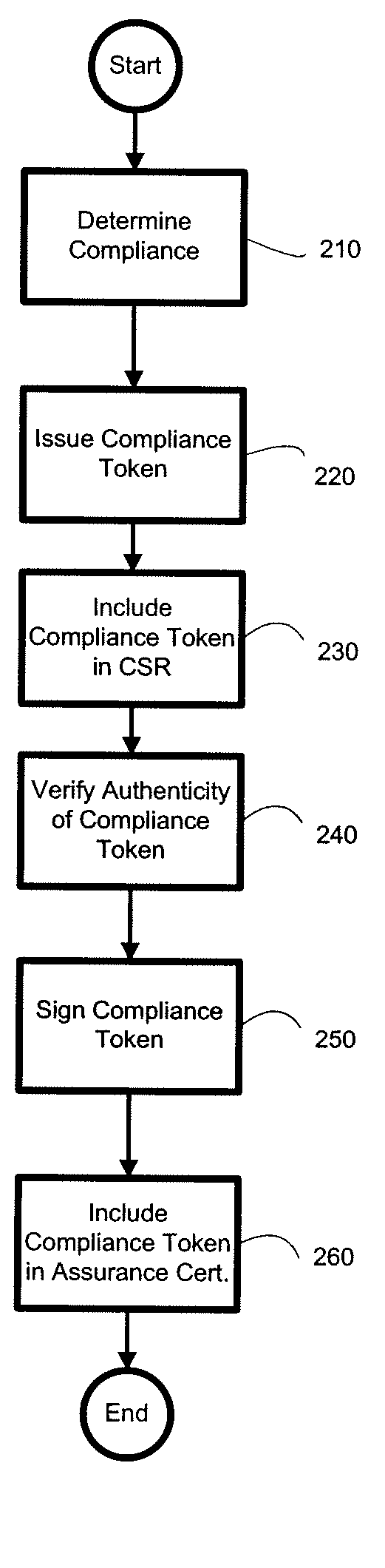
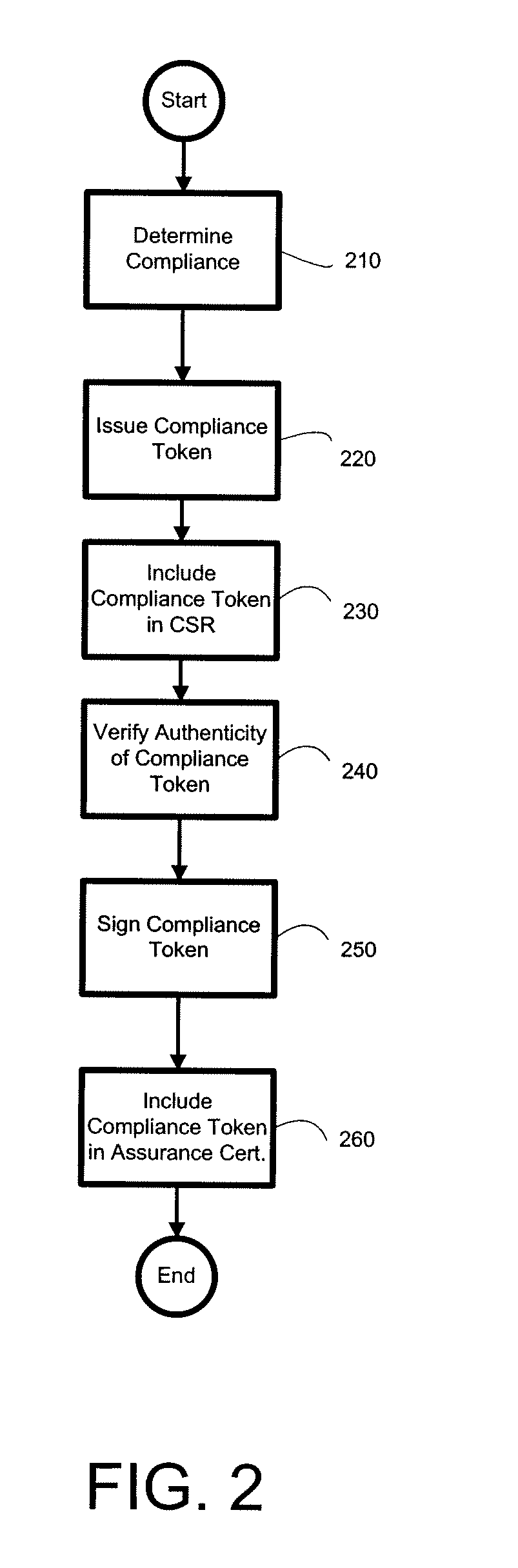
In public key infrastructure (PKI) systems, a certificate signing request (also CSR or certification request) is a message sent from an applicant to a certificate authority in order to apply for a digital identity certificate. It usually contains the public key for which the certificate should be issued, identifying information (such as a domain name) and integrity protection (e.g., a digital signature). The most common format for CSRs is the PKCS #10 specification and another is the Signed Public Key and Challenge SPKAC format generated by some web browsers.
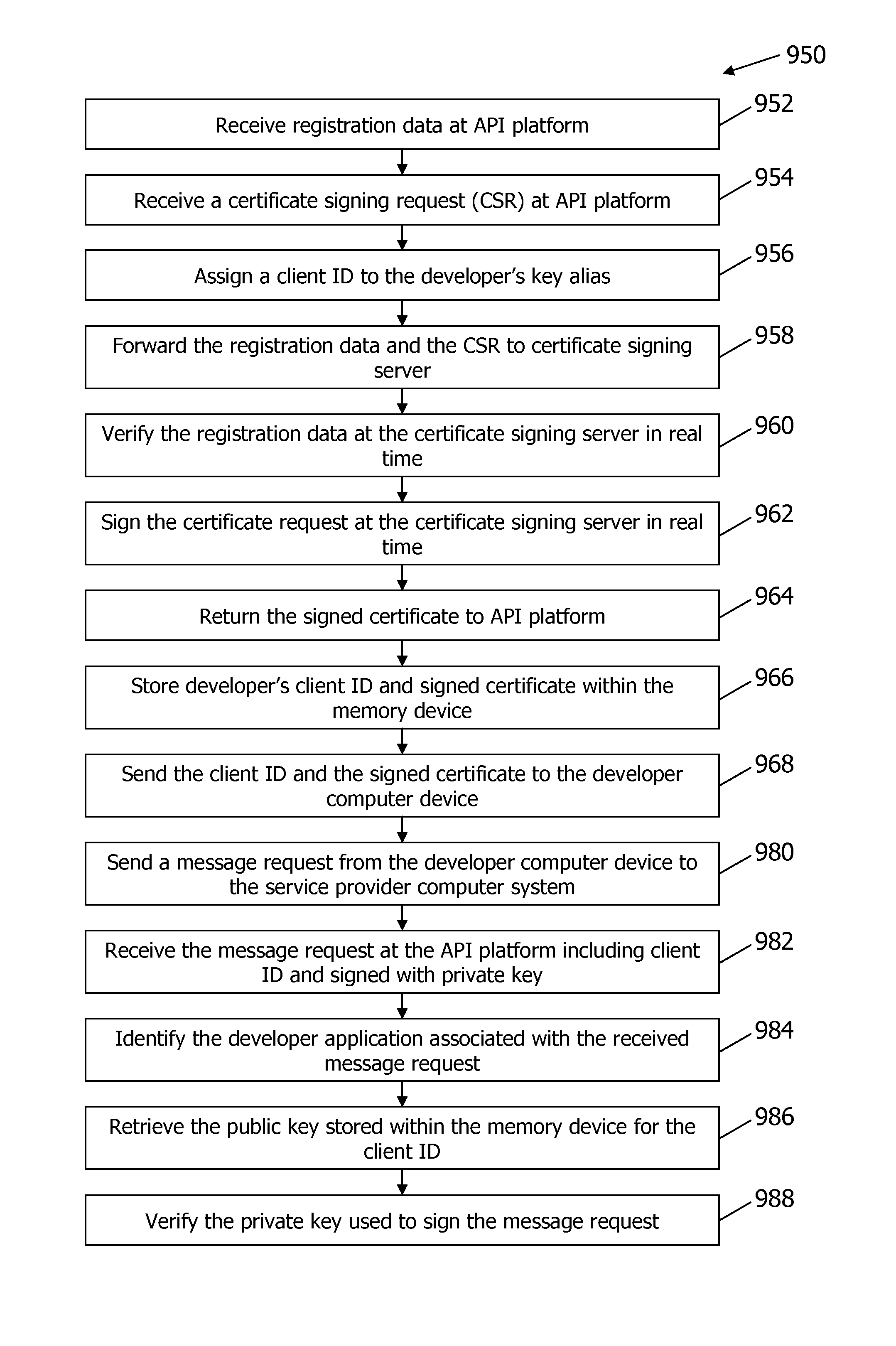
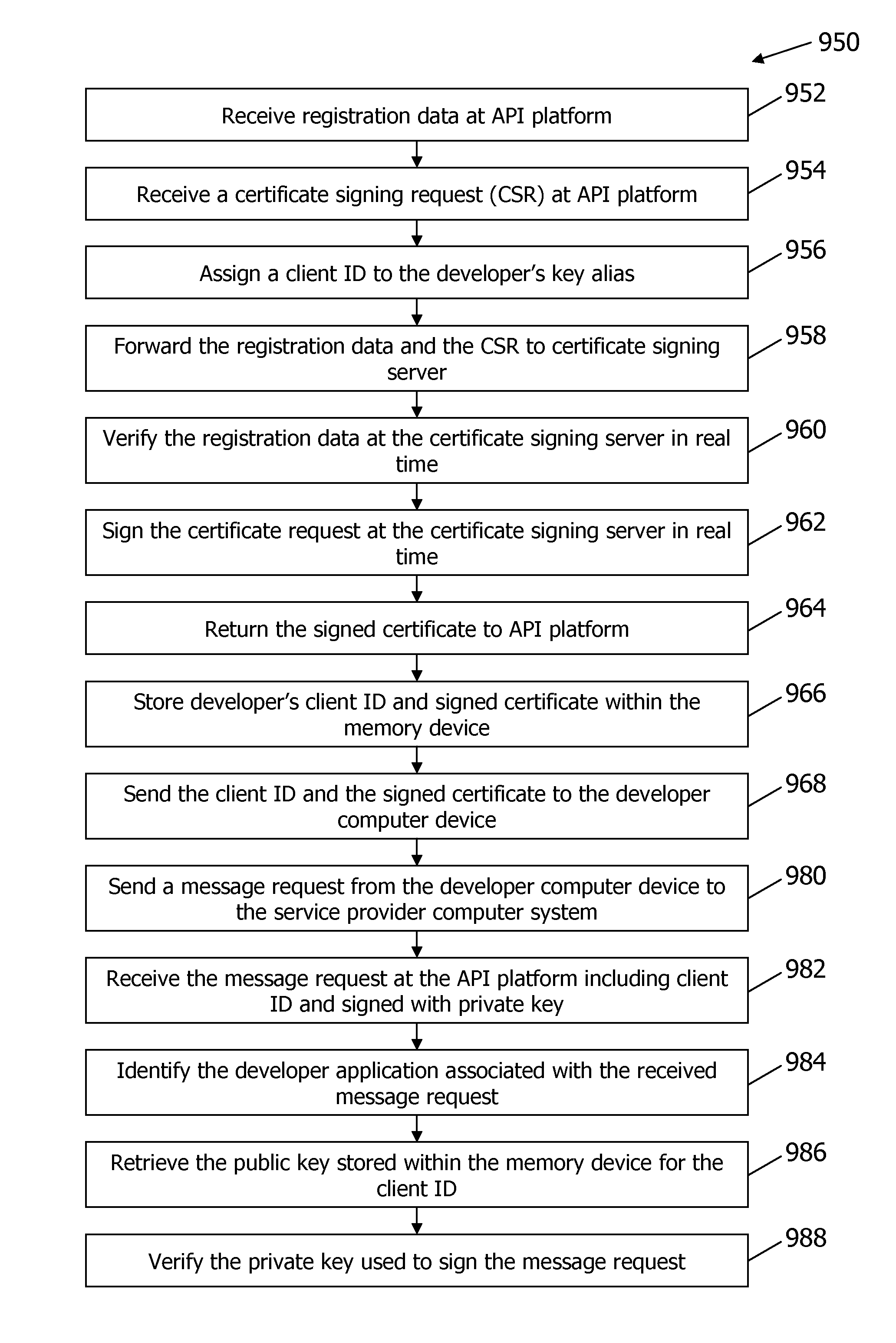
Methods and systems for providing a signed digital certificate in real time
ActiveUS20120179907A1User identity/authority verificationApplication programming interfaceService provision
A method and system for signing a digital certificate in real time for accessing a service application hosted within a service provider (SP) computer system through an open application programming interface (API) platform is provided. The API platform is in communication with a memory device. The method includes receiving registration data from a developer computer device wherein the developer computer device is associated with a developer and configured to store a developer application, receiving a certificate signing request (CSR) from the developer computer device wherein the CSR includes a public key associated with the developer, verifying the registration data as being associated with the developer, signing the CSR to produce a signed certificate after verifying the registration data wherein the verifying and signing steps are performed by the SP computer system in real time, and transmitting the signed certificate and a client ID to the developer computer device.
Owner:MASTERCARD INT INC
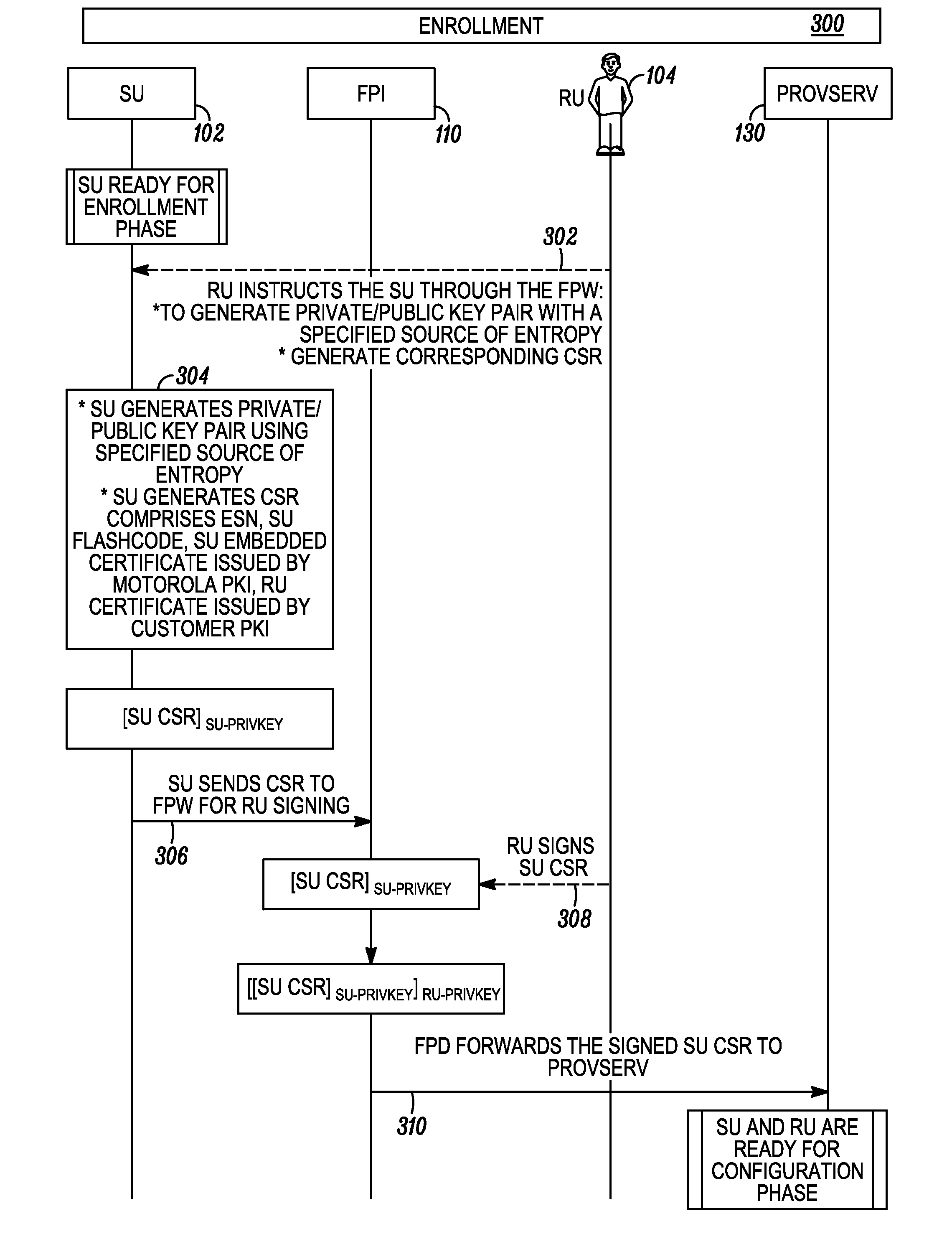
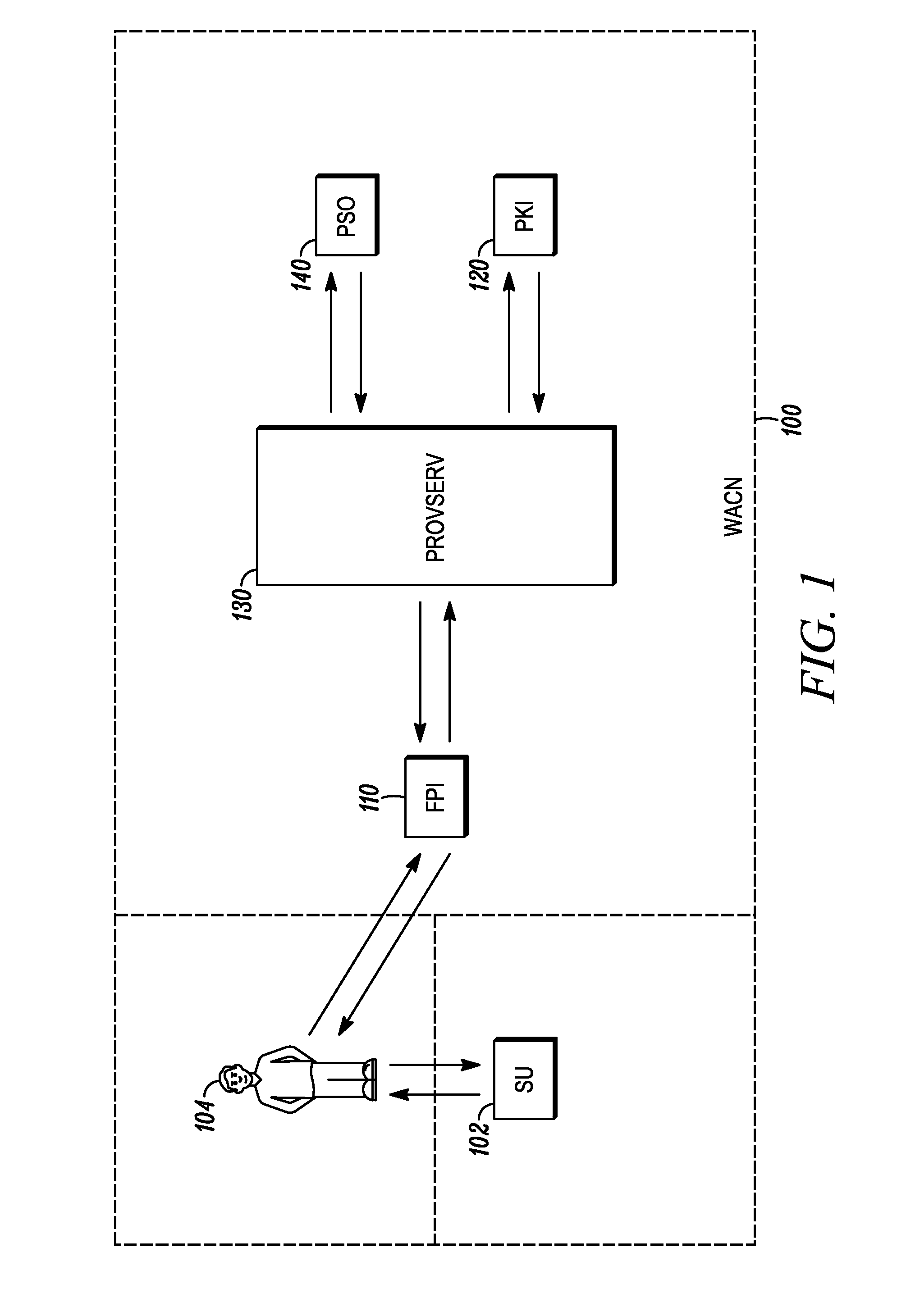
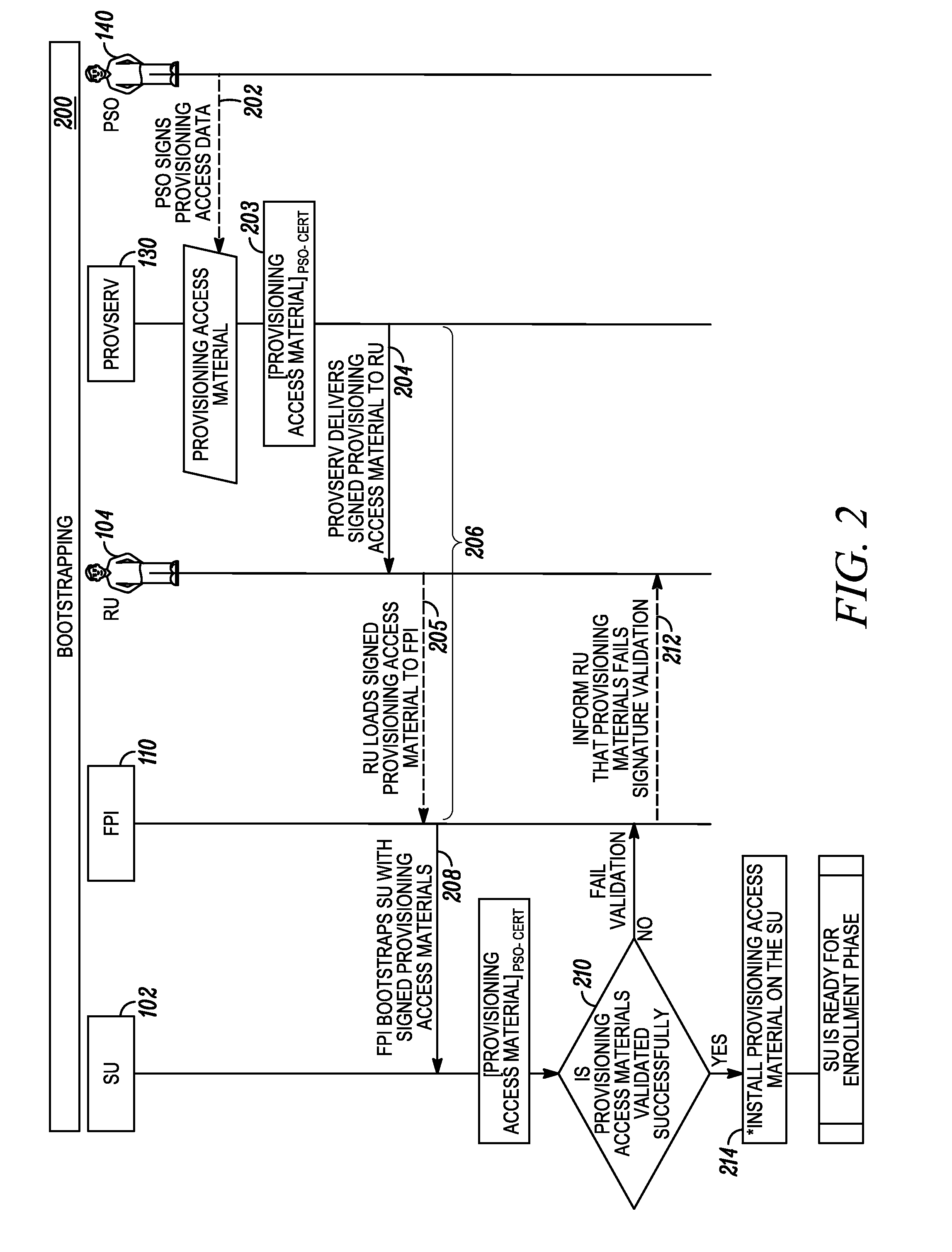
Method to enable secure self-provisioning of subscriber units in a communication system
InactiveUS20110161659A1Service provisioningDigital data authenticationCommunications systemCertificate signing request
A method to enable remote, secure, self-provisioning of a subscriber unit includes, a security provisioning server: receiving, from a subscriber unit, a certificate signing request having subscriber unit configuration trigger data; generating provisioning data for the subscriber unit using the subscriber unit configuration trigger data; and in response to the certificate signing request, providing to the subscriber unit the provisioning data and a subscriber unit certificate having authorization attributes associated with the provisioning data, to enable the self-provisioning of the subscriber unit.
Owner:MOTOROLA SOLUTIONS INC
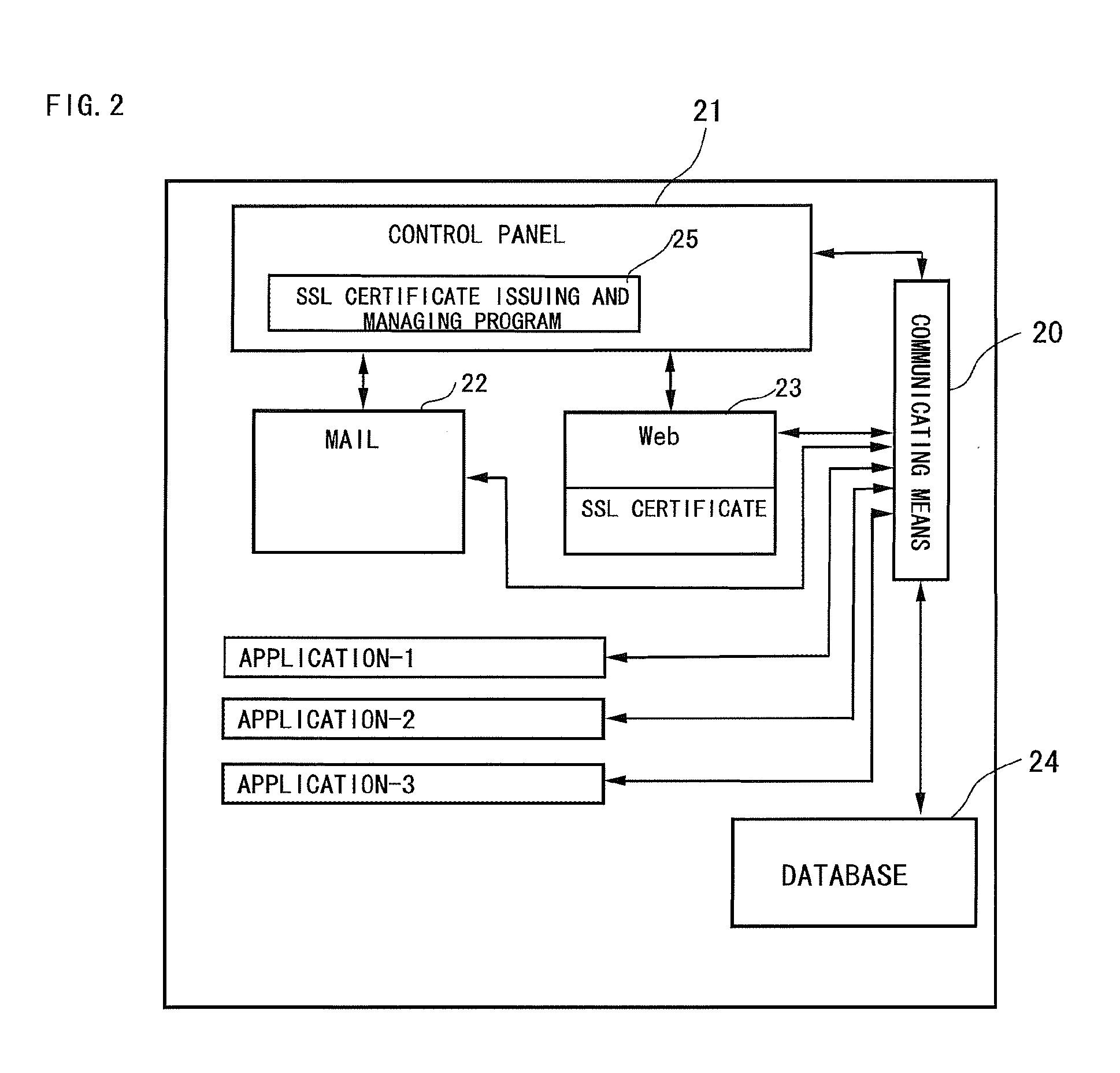
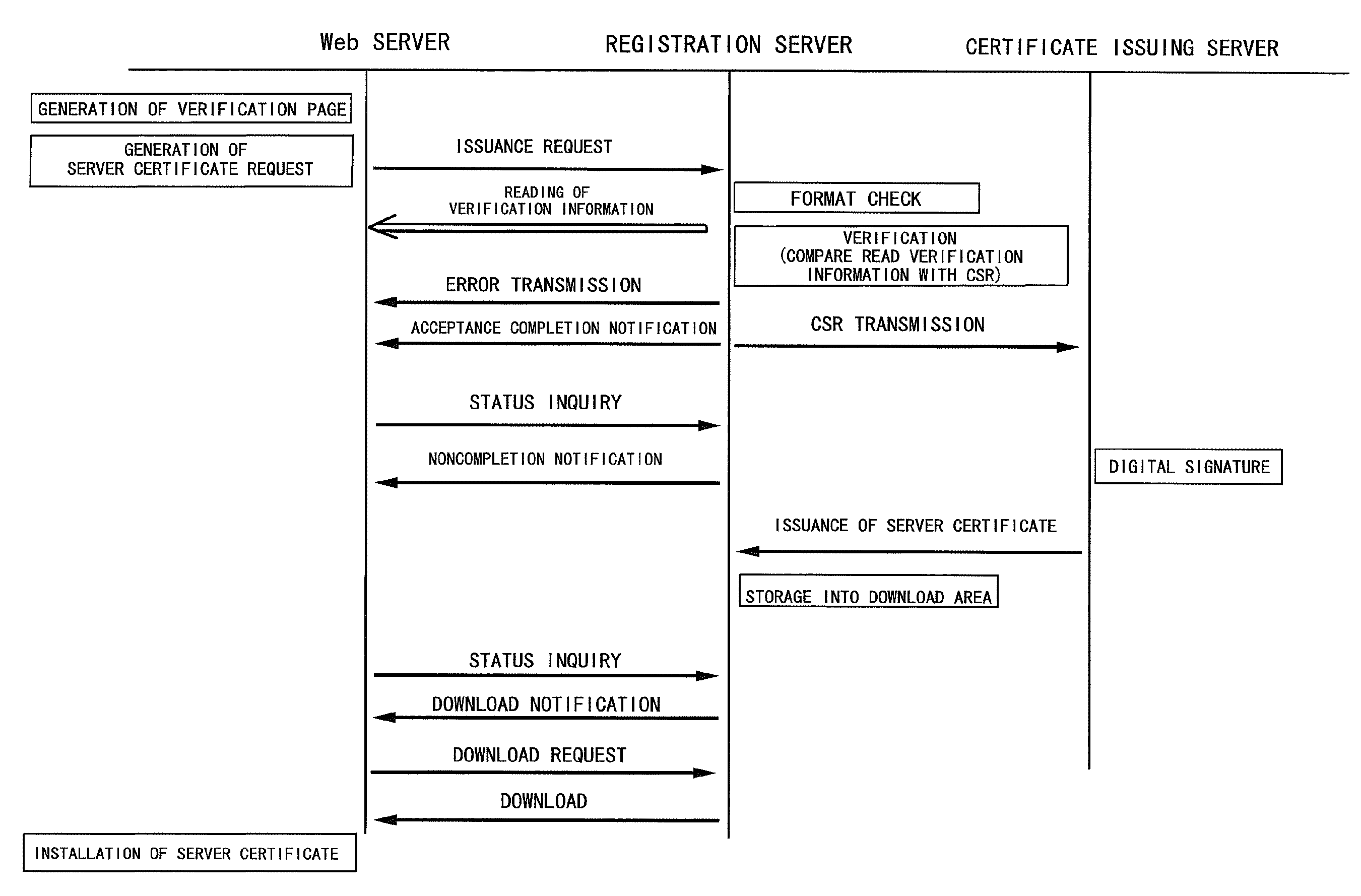
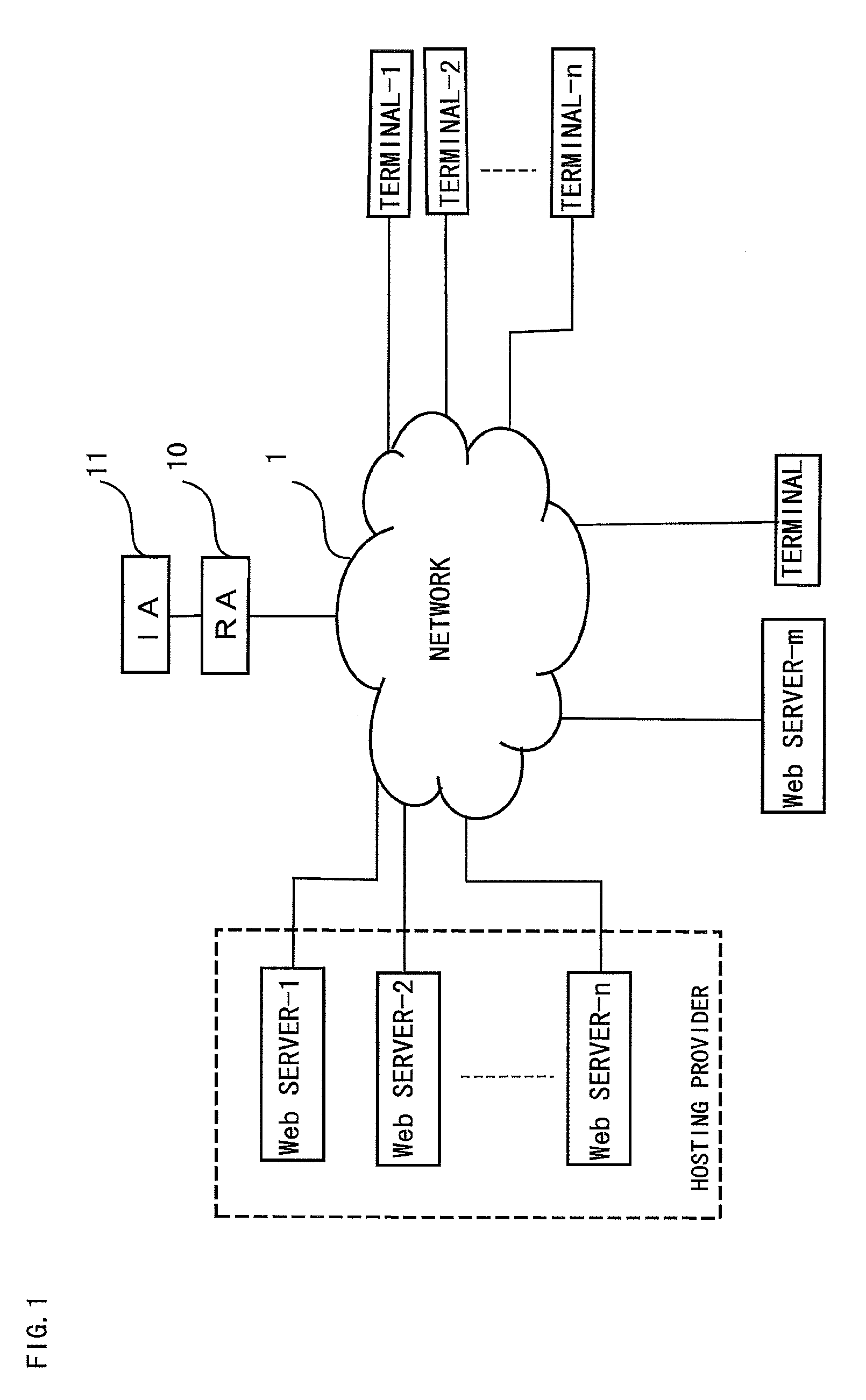
Server Certificate Issuing System
InactiveUS20090092247A1Improve securityReduce the burden onData processing applicationsPublic key for secure communicationWeb serviceCertificate signing request
A server certificate issuing system confirms existence of a Web server for which a certificate is to be issued. The web server includes means for generating an entry screen to input application matters for an issuance of a server certificate, means for generating a key pair of a public key and a private key, means for generating a certificate signing request file (CSR) containing the generated public key, and means for generating a verification page indicating intention of requesting the issuance of the certificate. A registration server retrieves the CSR from a received server certificate request and accesses the Web server to read the verification information, and compares the read verification information with the CSR. If the verification information read from the Web server is identical to the CSR, it is determined that the Web server for which the server certificate is to be issued exists.
Owner:GLOBALSIGN
System and method for secured network access utilizing a client .net software component
InactiveUS20090307486A1Accurate informationUser identity/authority verificationOperational systemWeb browser
A method for self-service authentication of a client and a server. The method includes the server receiving an initialization command from the client. The initialization command may be transmitted to the server via a client web browser over an unsecured data transfer link. The method continues with requesting authentication information from the client. In response to receiving the authentication information from the client, the server transmits a client software component to the client. The client software component utilizes a client-side library installed on the operating system of the client to generate the various client credentials described above. Thereafter, the certificate signing request may be transmitted to a certificate server for signing the certificate signing request. The signed certificate signing request is then received by the client via the client web browser. The client utilizes the information associated with the signed certificate signing request with the client-side library installed on the client to generate a client certificate.
Owner:MULTIFACTOR CORP
Certificate validation method and certificate validation server and storage medium
ActiveUS20110004763A1Effectively and safely performingEfficient executionUser identity/authority verificationDigital data protectionValidation methodsCertificate signing request
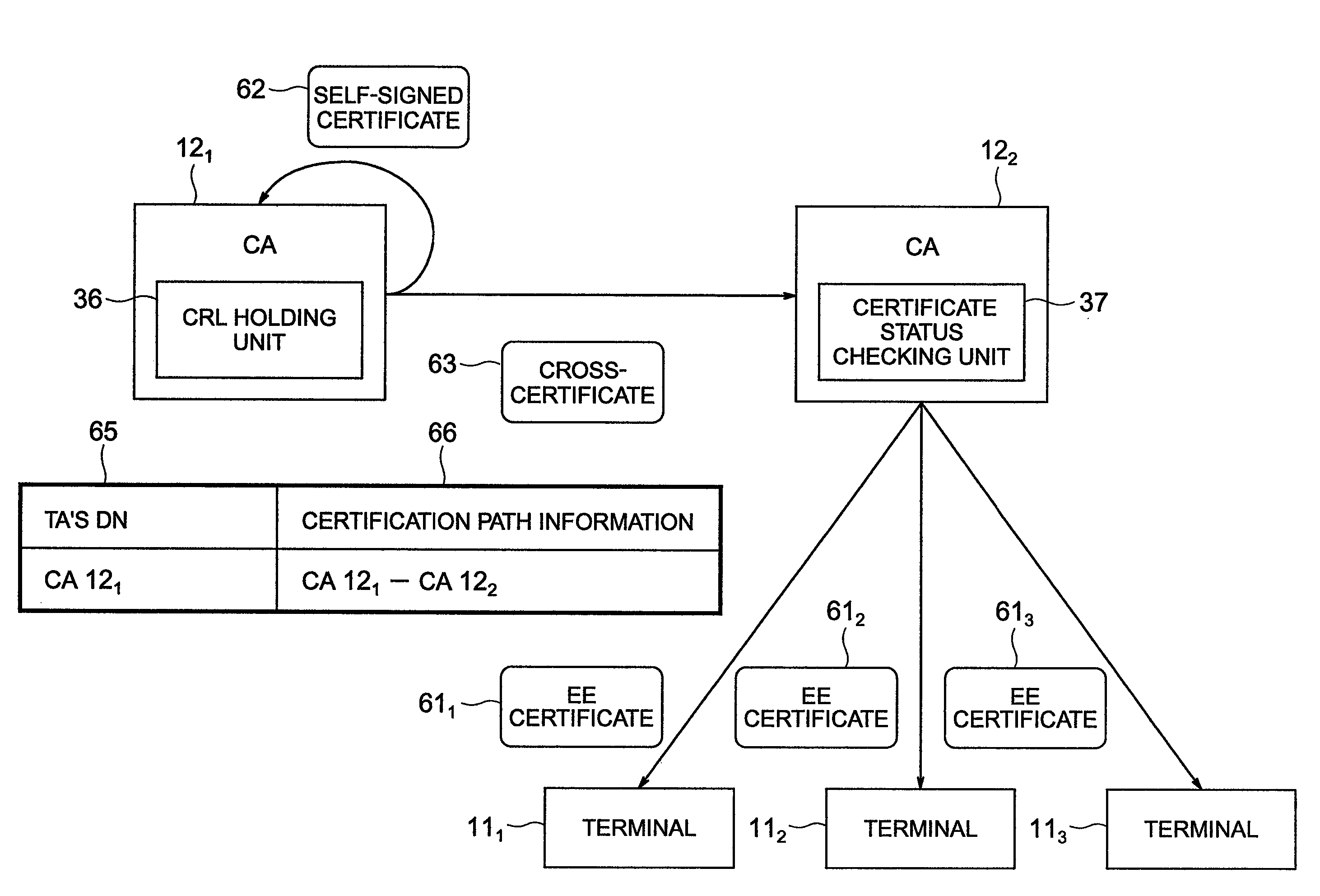
A certificate validation method for causing a certificate validation server to receive a certificate validation request from a given terminal device, build a certification path of from a first certificate authority (CA) to a second CA, perform validation of the certification path, and send a validation result to the terminal which issued the certificate validation request is disclosed. The validation server detects either a key update of any given CA or a compromise of the given CA, acquires a certificate of relevant CA and first certificate status information and second certificate status information, stores the acquired information in a storage unit or, alternatively, updates the information stored in the storage based on the acquired information, and performs the building of a certification path and validation of the certification path by use of the information of the storage unit.
Owner:HITACHI LTD
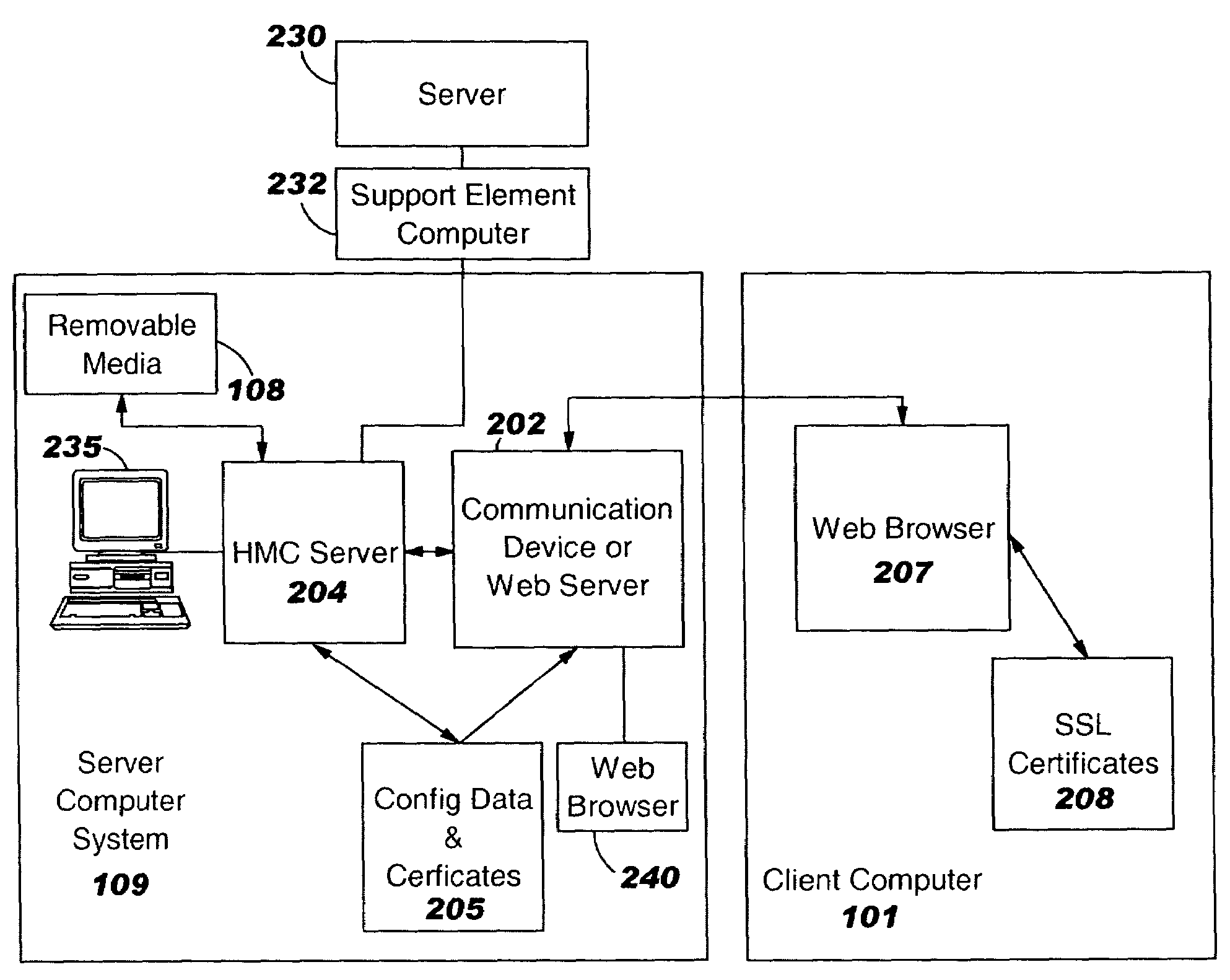
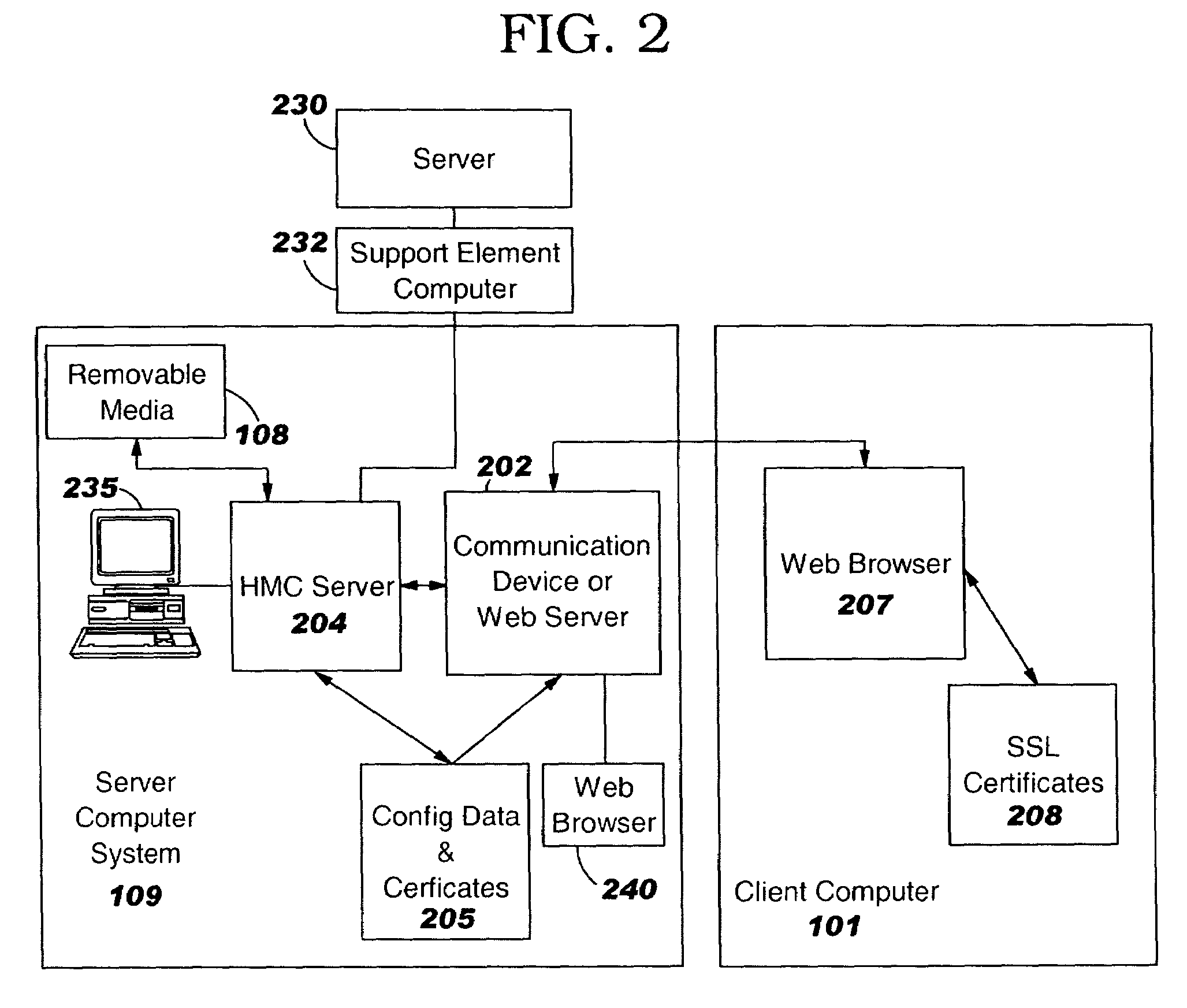
Computer system and program to update SSL certificates
InactiveUS20060075219A1Digital data processing detailsUser identity/authority verificationProgram instructionSelf-signed certificate
System and computer program product for updating an SSL certificate for a server. First program instructions detect when a change has been made to a name, domain or IP address of the server and detect that the server is using an SSL certificate based on a name, domain or IP address applicable before the change. In response, the first program instructions notify an administrator that a change is required to the SSL certificate to reflect the change to the name, domain or IP address. Second program instructions respond to a request by the administrator, to automatically create a new SSL certificate signing request. The new SSL certificate signing request is a form which can be sent to an SSL certificate authority. Third program instructions respond to another request by the administrator, to send the new SSL certificate signing request to the SSL certificate authority. Fourth program instructions respond to receipt of a new SSL certificate from the SSL certificate authority and another request by the administrator, to substitute the new SSL certificate for the existing SSL certificate. Fourth program instructions query the administrator if the administrator wants to use a new self-signed SSL certificate reflecting the change to the name, domain or IP address of the server, until the new SSL certificate signed by the SSL certificate authority is received from the SSL certificate authority, and if so, generate the new SSL self-signed certificate. Other program instructions respond to a request by the administrator, to create a self-signed SSL certificate and substitute the self-signed SSL certificate for the existing SSL certificate.
Owner:IBM CORP
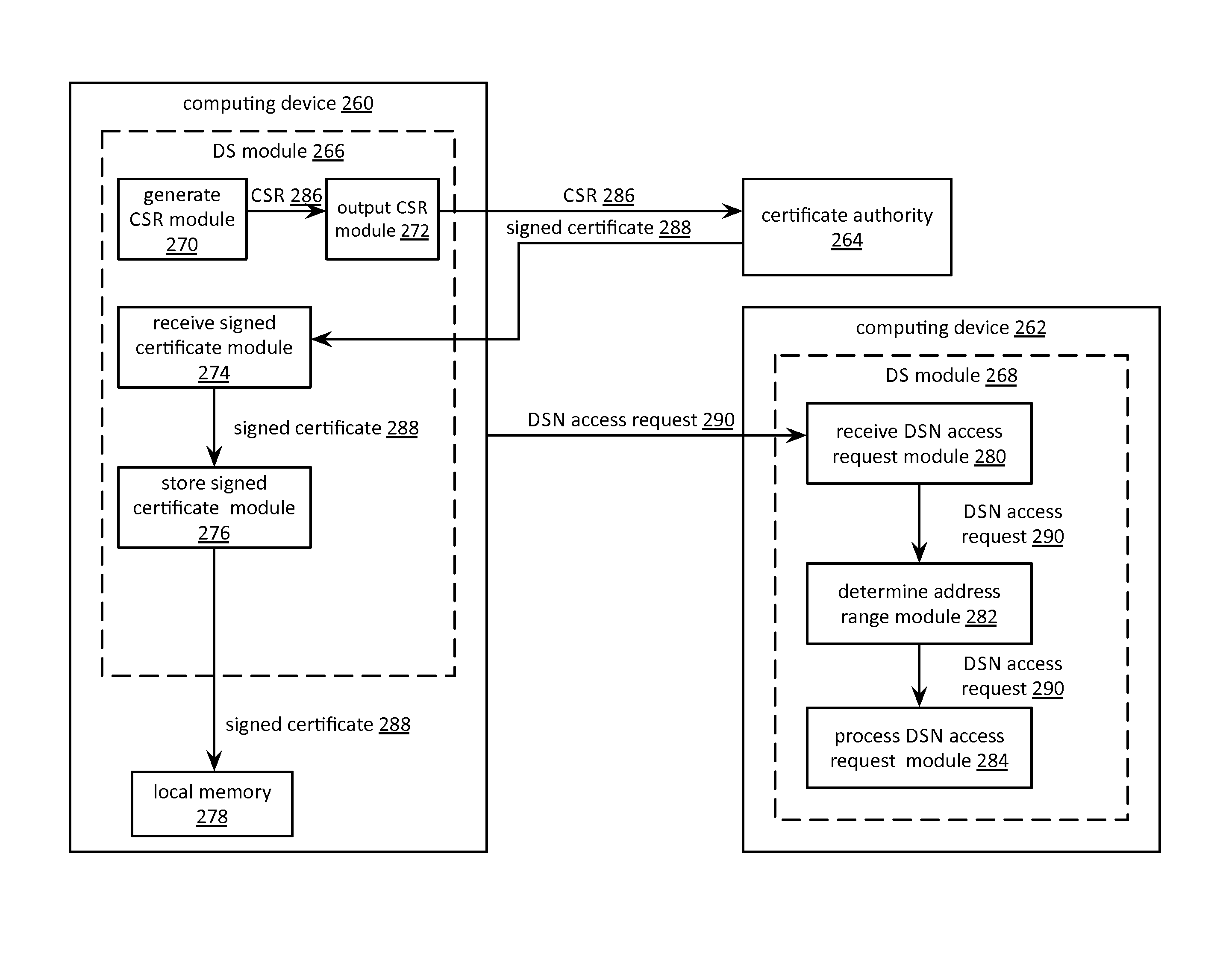
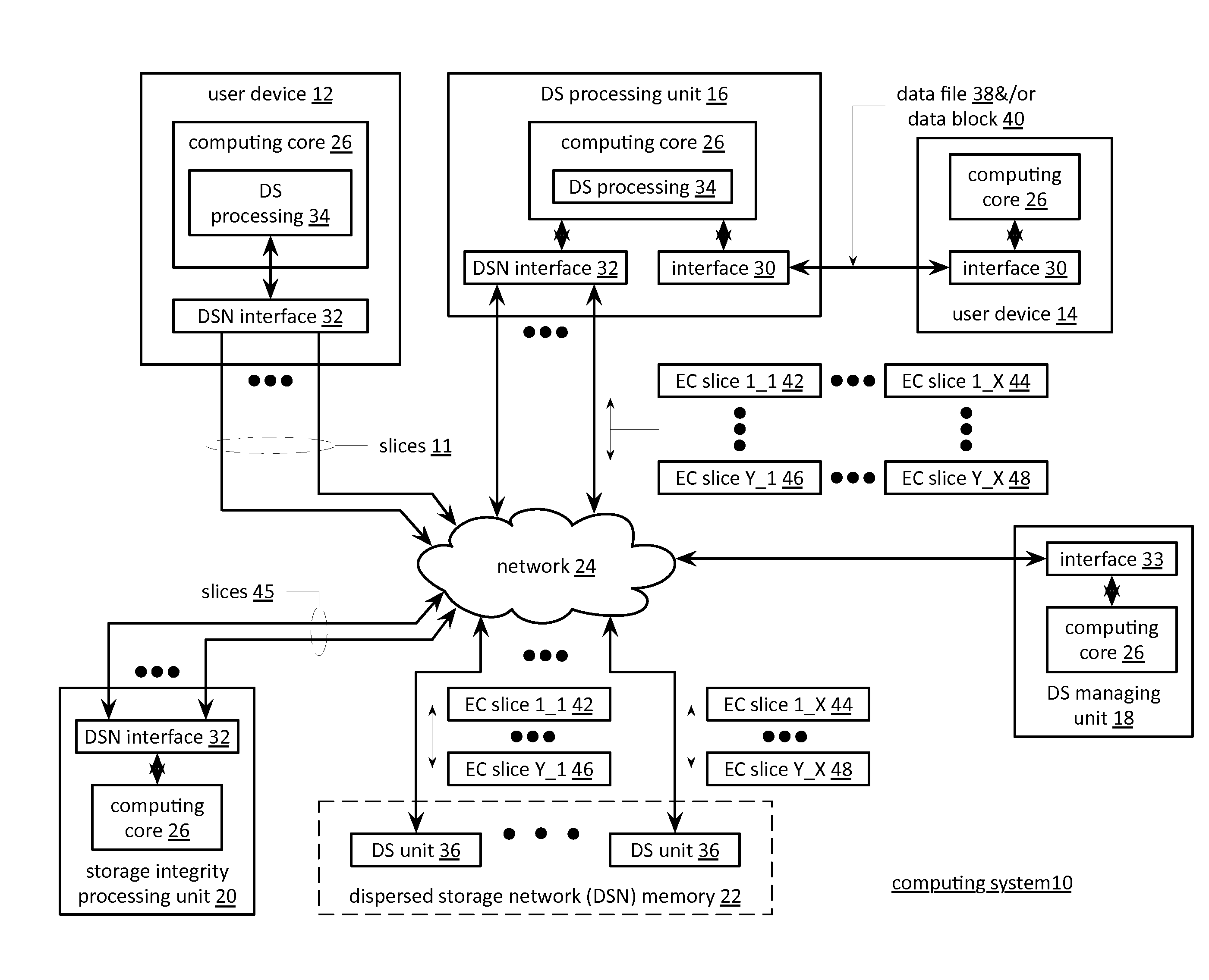
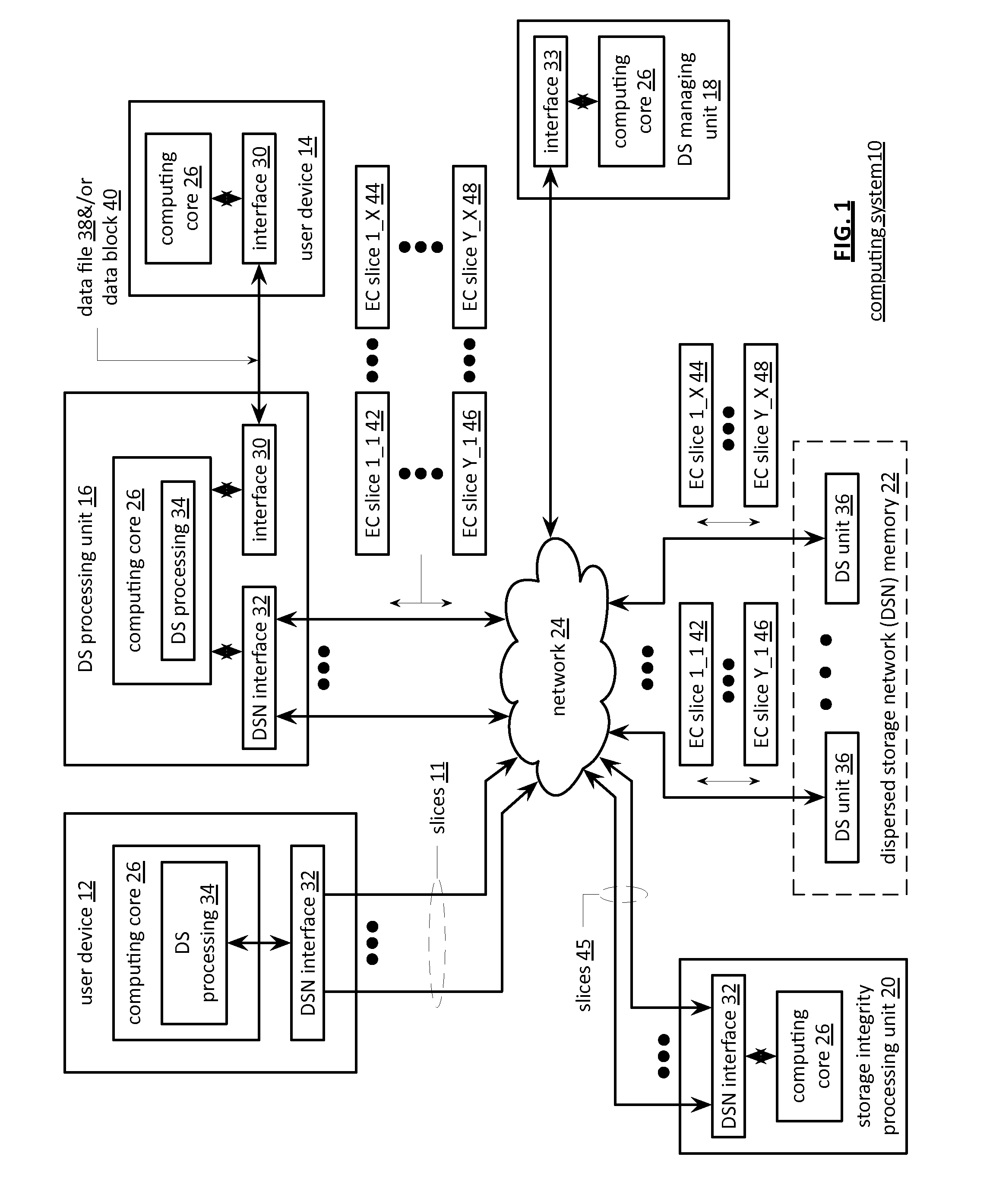
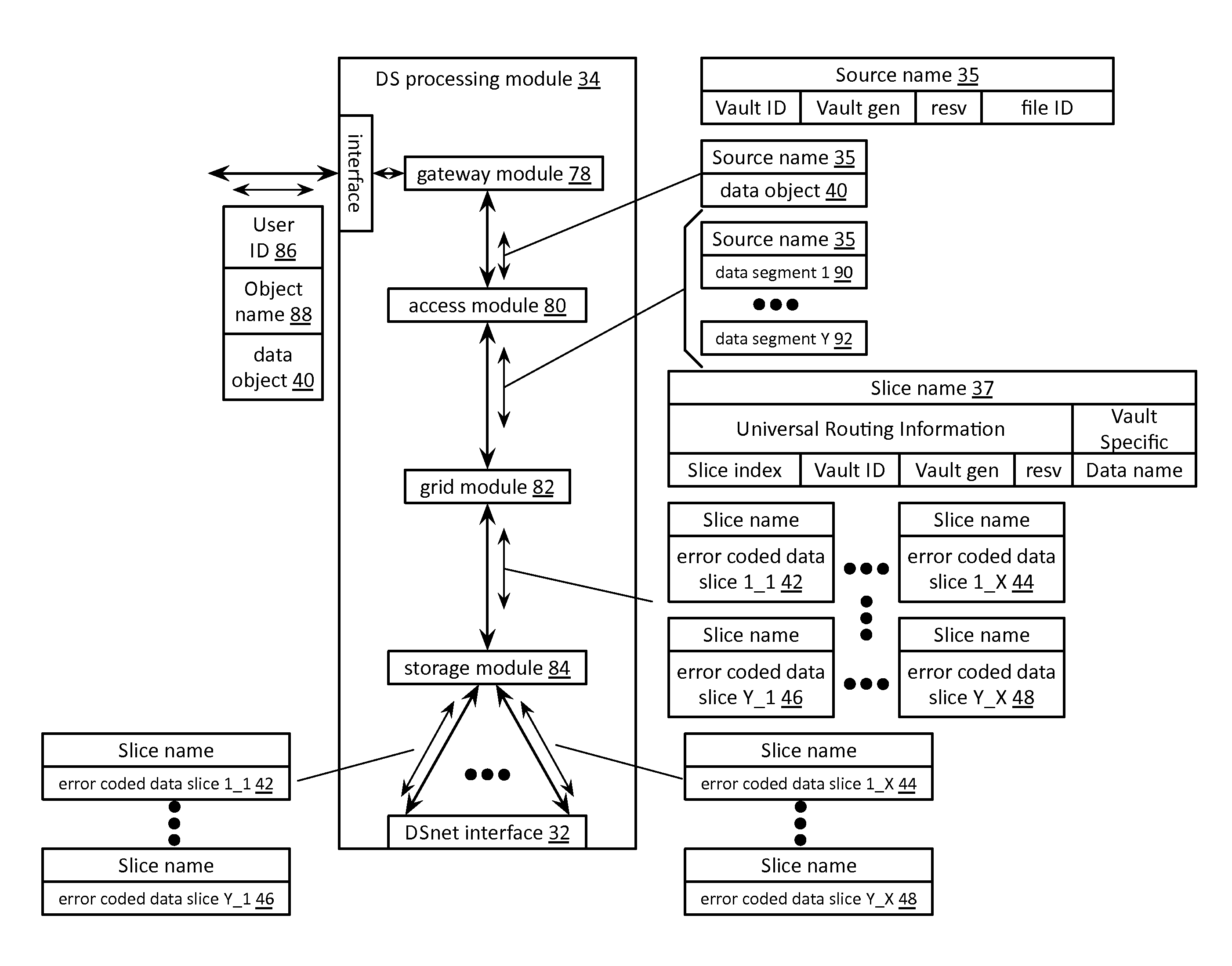
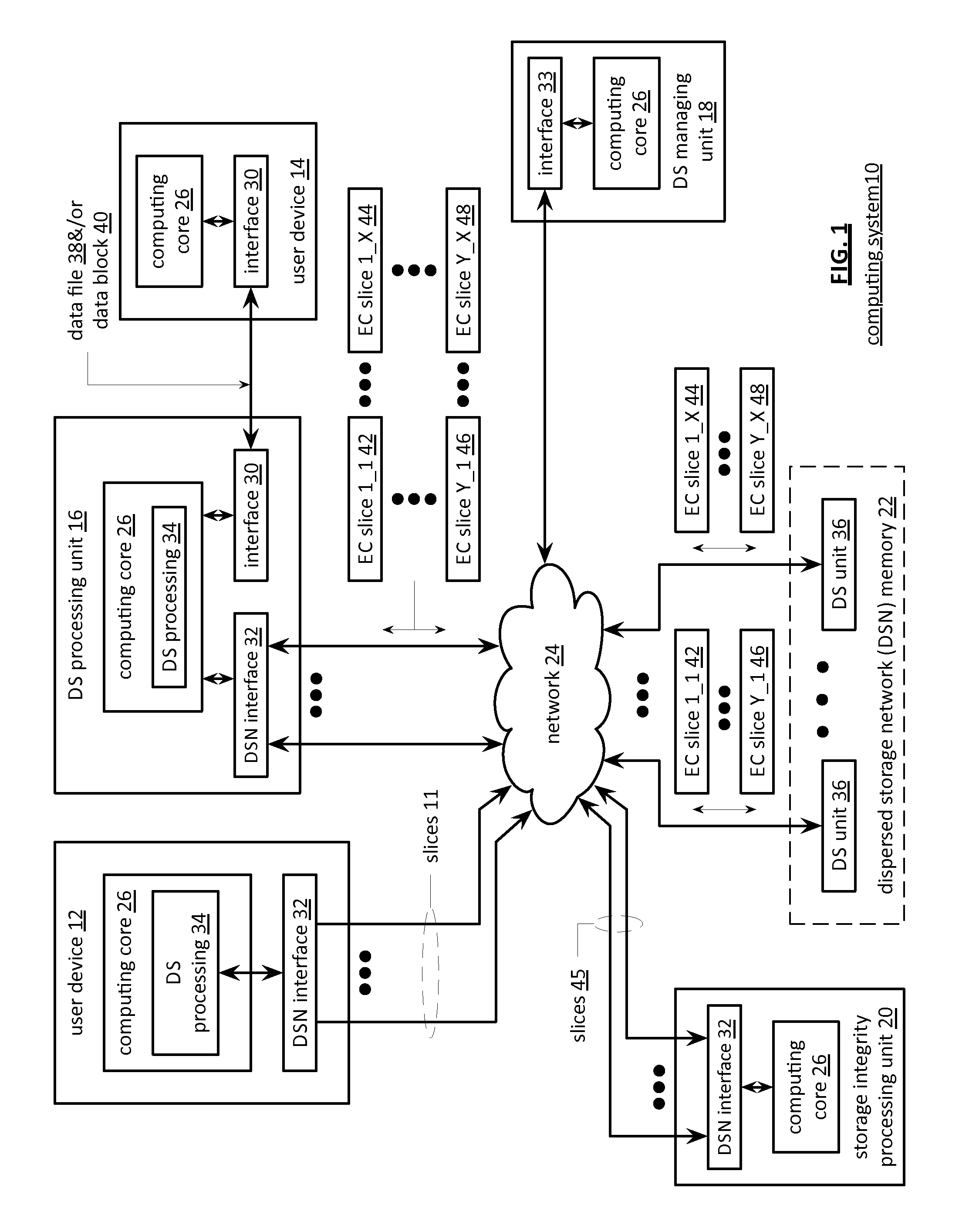
Processing a certificate signing request in a dispersed storage network
ActiveUS20130086377A1Input/output to record carriersError detection/correctionCertificate signing requestDispersed storage
A method begins by a requesting device transmitting a certificate signing request to a managing unit, wherein the certificate signing request includes fixed certificate information and suggested certificate information. The method continues with the managing unit forwarding the certificate signing request to a certificate authority and receiving a signed certificate from the certificate authority, wherein the signed certificate includes a certificate and a certification signature and wherein the certificate includes the fixed certificate information and determined certificate information based on the suggested certificate information. The method continues with the managing unit interpreting the fixed certificate information of the signed certificate to identify the requesting device and forwarding the signed certificate to the identified requesting device.
Owner:PURE STORAGE
Methods and systems for providing a signed digital certificate in real time
ActiveUS9032204B2FinanceDigital data processing detailsApplication programming interfaceService provision
A method and system for signing a digital certificate in real time for accessing a service application hosted within a service provider (SP) computer system through an open application programming interface (API) platform is provided. The API platform is in communication with a memory device. The method includes receiving registration data from a developer computer device wherein the developer computer device is associated with a developer and configured to store a developer application, receiving a certificate signing request (CSR) from the developer computer device wherein the CSR includes a public key associated with the developer, verifying the registration data as being associated with the developer, signing the CSR to produce a signed certificate after verifying the registration data wherein the verifying and signing steps are performed by the SP computer system in real time, and transmitting the signed certificate and a client ID to the developer computer device.
Owner:MASTERCARD INT INC
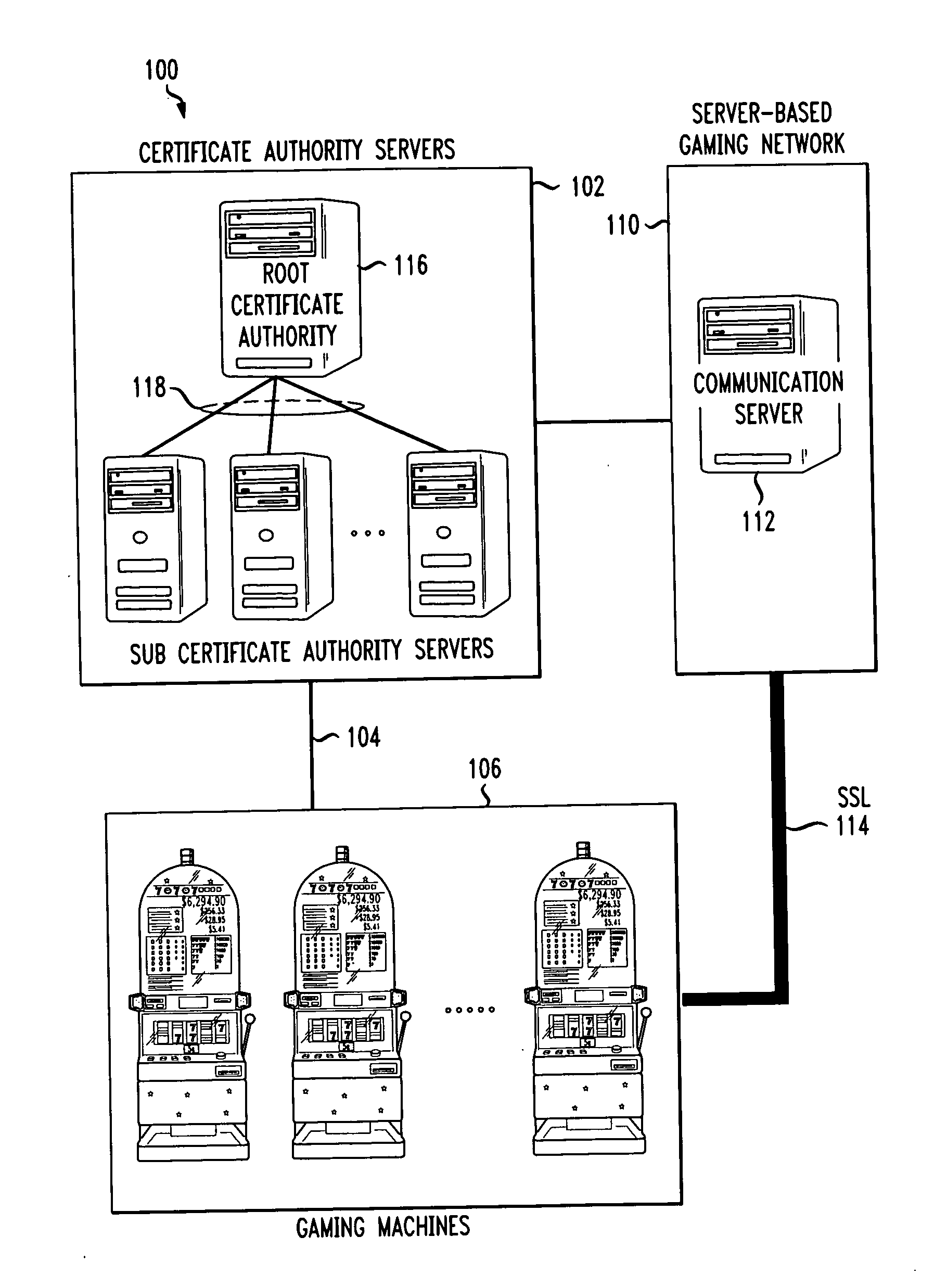
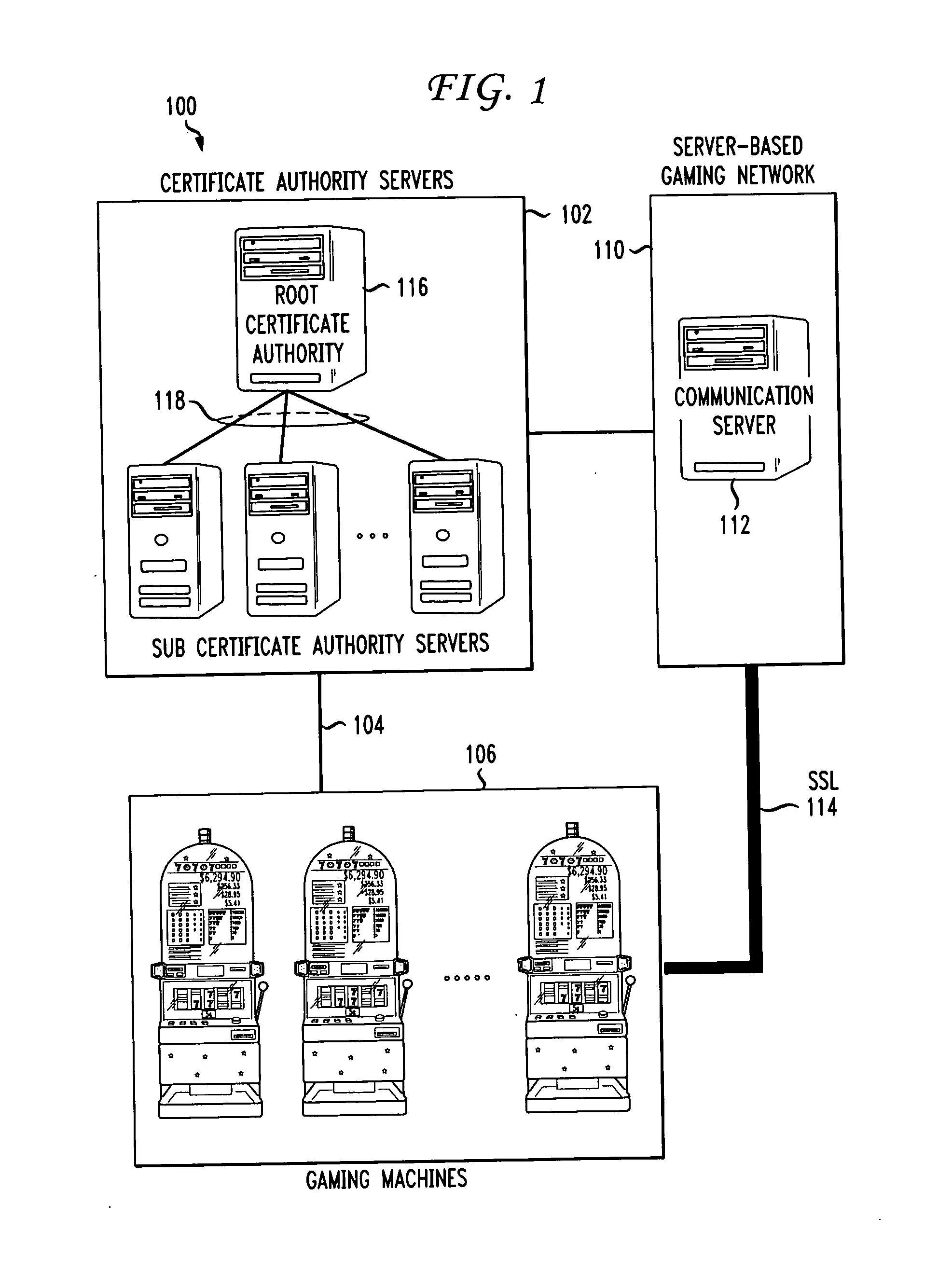
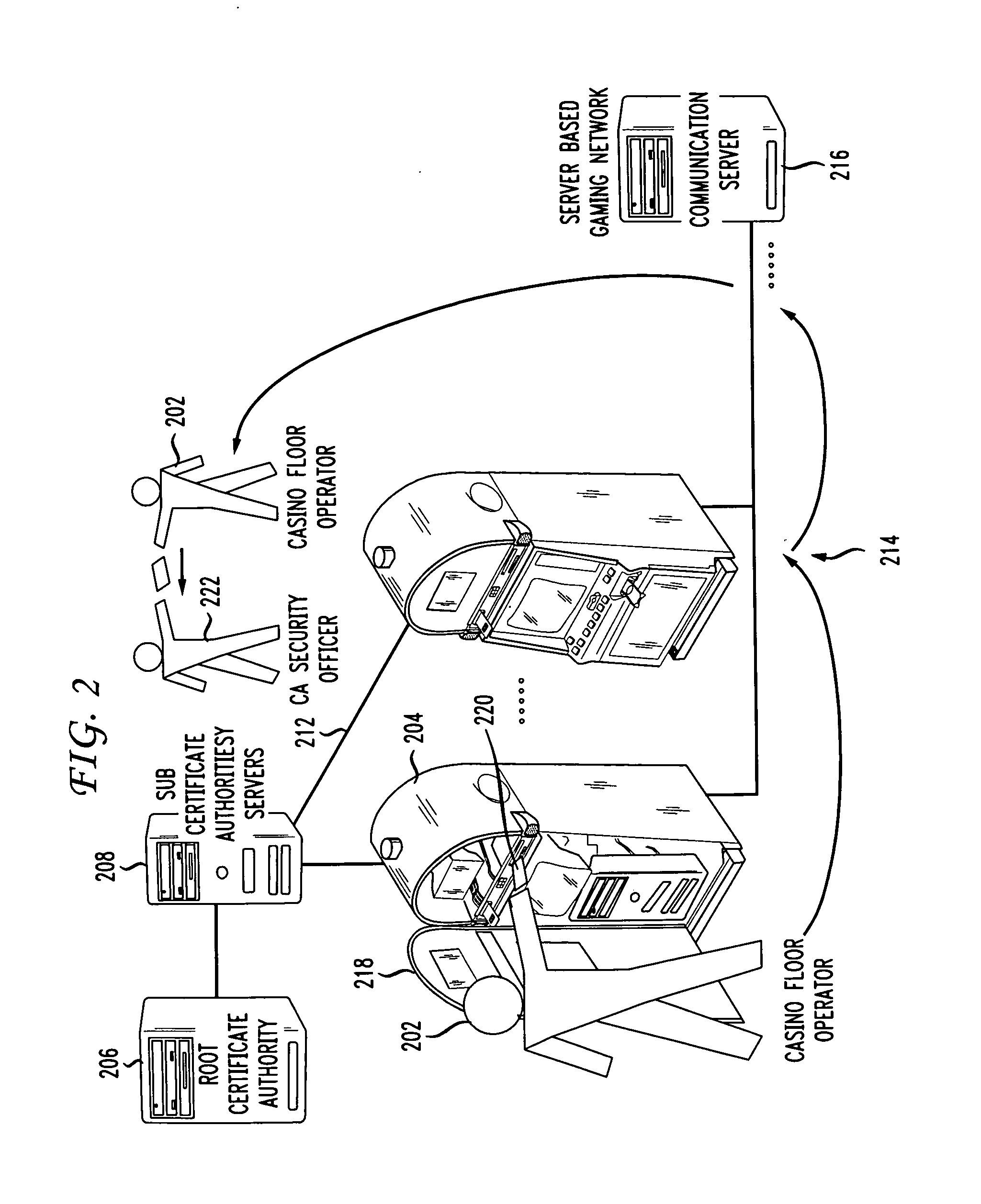
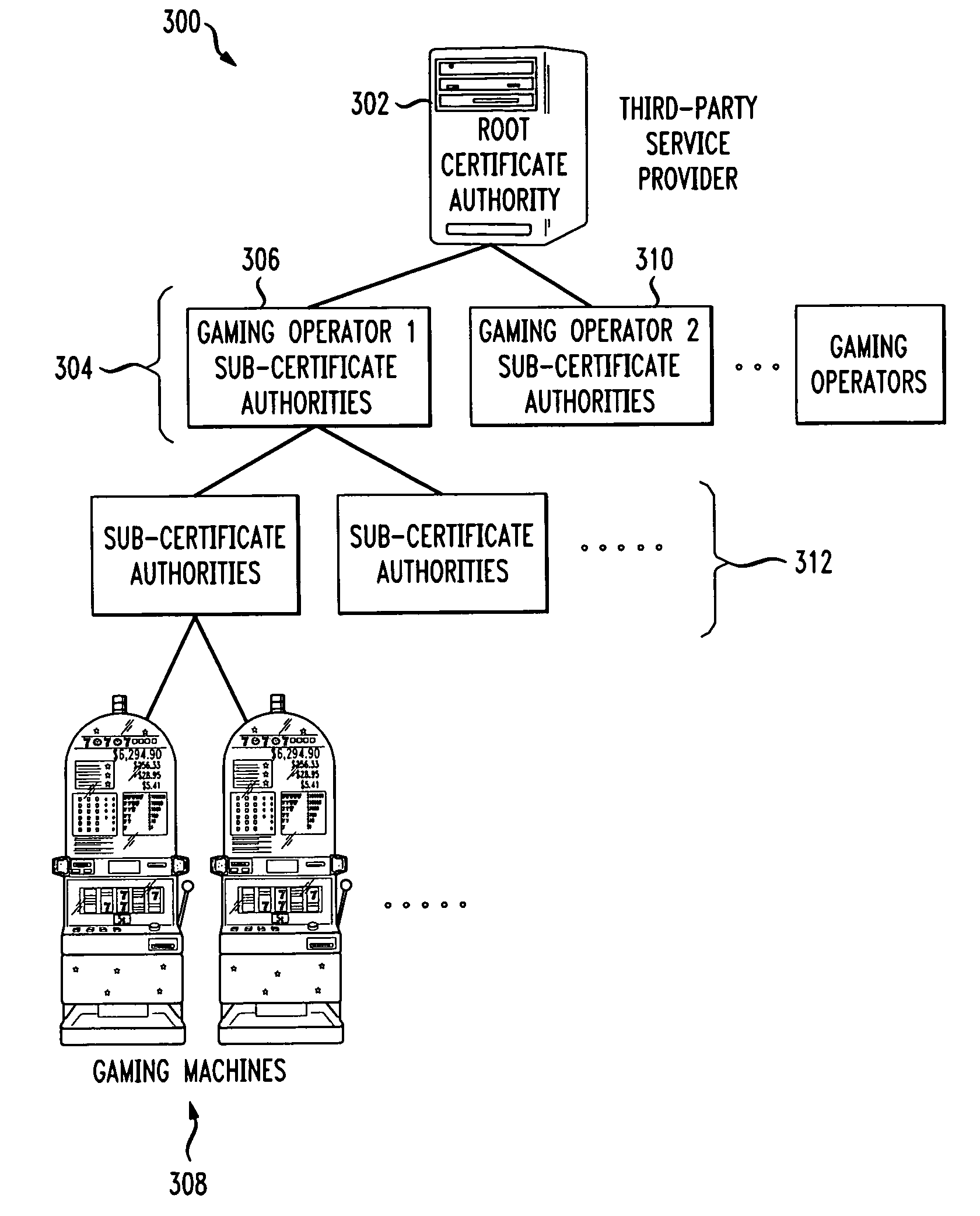
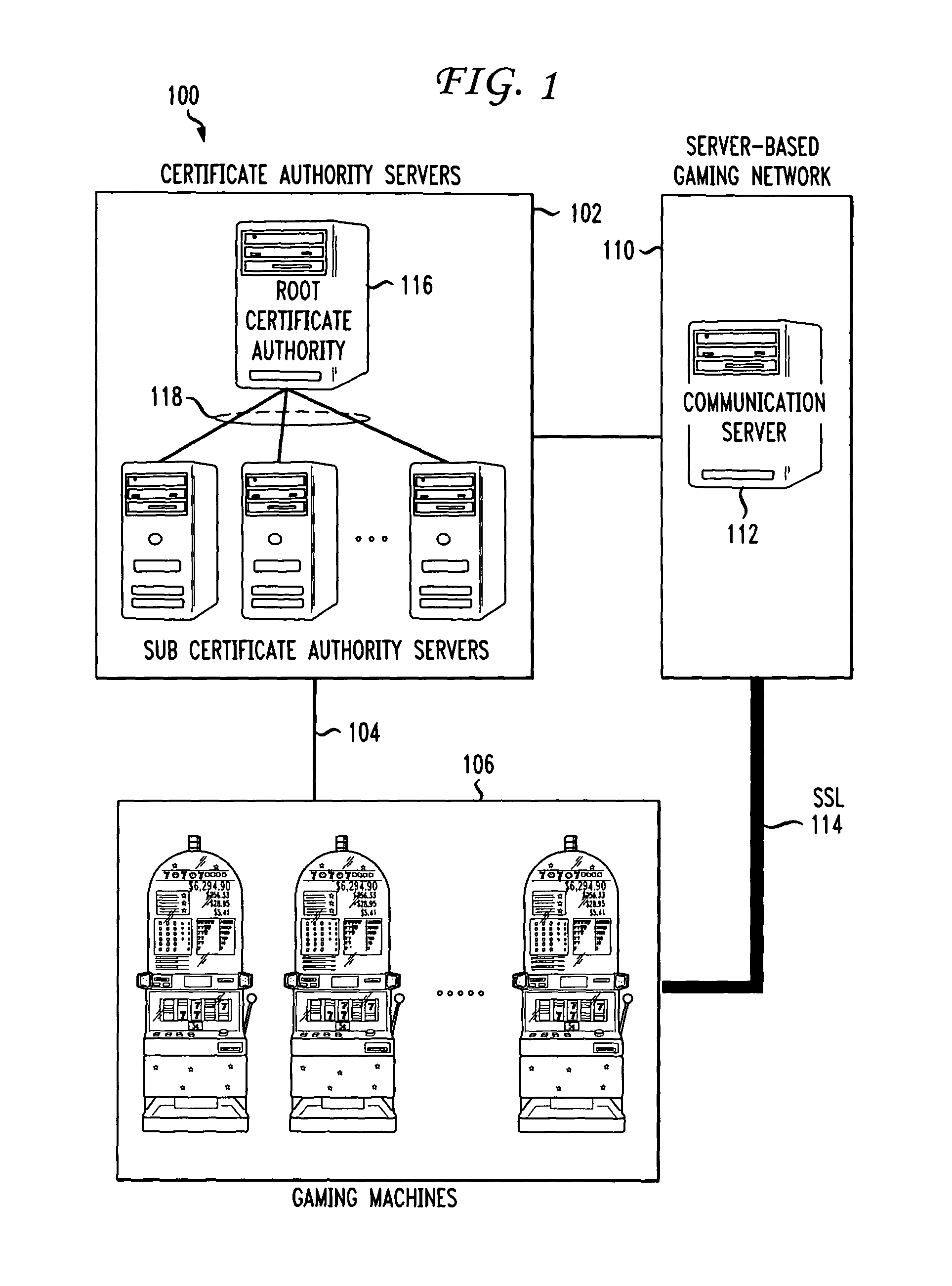
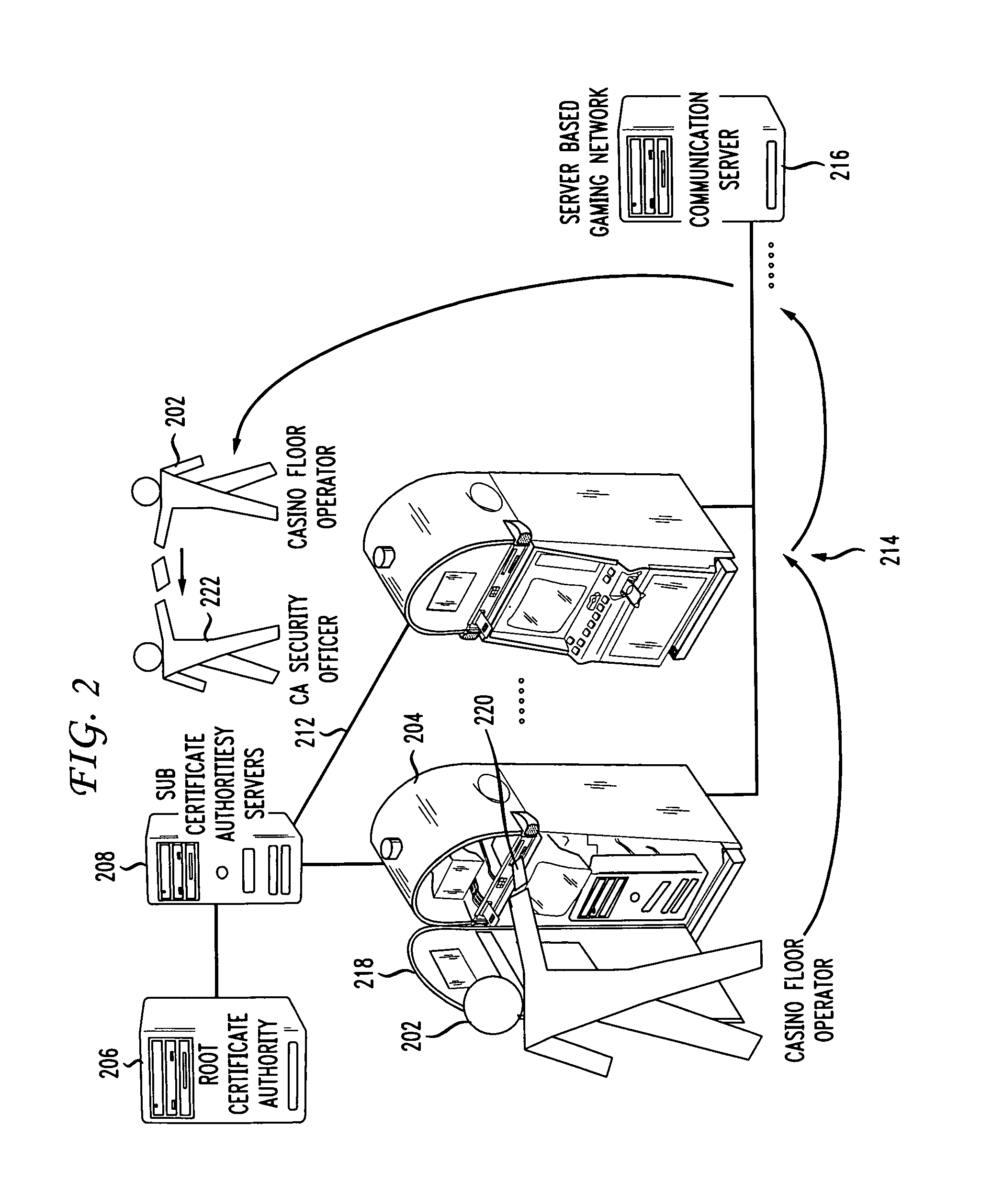
Gaming machine certificate creation and management
ActiveUS20090319796A1Easy to processEasy to issueDigital data processing detailsUser identity/authority verificationCertificate signing requestSoftware
Methods and systems for creating and managing certificates for gaming machines in a gaming network using a portable memory device are described. A gaming machine creates a certificate signing request which is stored on a portable memory device at the machine by an operator. The memory device is handed over to a certificate authority (CA) security officer at the casino and is coupled with an appropriate CA server. A certificate batch utility program on the server downloads and processes the CSRs. A certificate services program on the server issues gaming machine certificates according to the CSRs. In one embodiment, the certificates are uploaded onto the memory device, along with copies of certificate authority server certificates, including a root CA certificate. The CA security officer hands the memory device to the casino floor operator. At the machine, the operator inserts or couples the device and software on the machine identifies and downloads its certificate based on the certificate file name. The machine also downloads copies of the CA server certificates which it may use in a certificate chain validation procedure. In another embodiment, the certificates are placed in a shared file on the CA server and retrieved by the gaming machines over a gaming network.
Owner:IGT
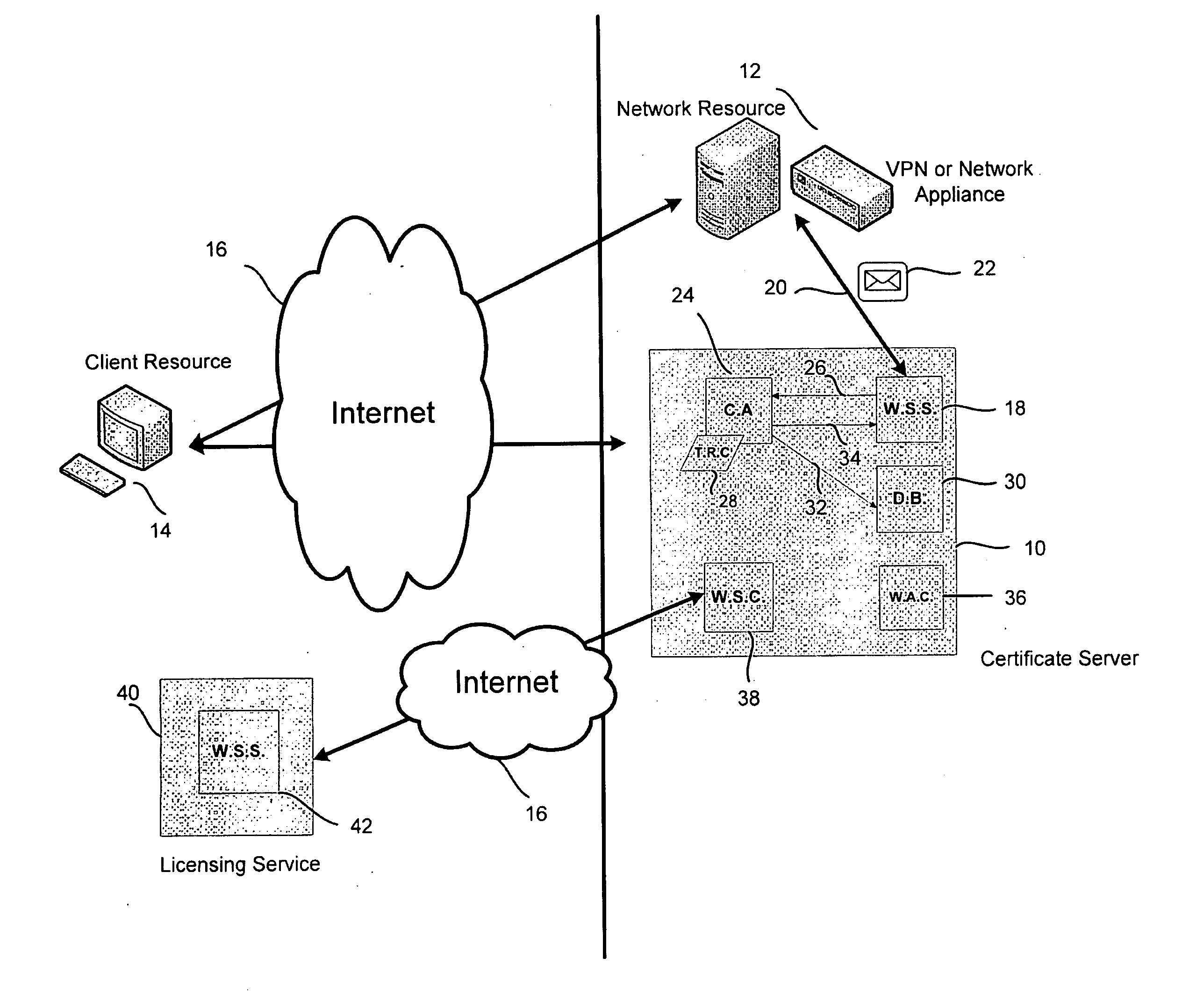
Method and system for generating digital certificates and certificate signing requests
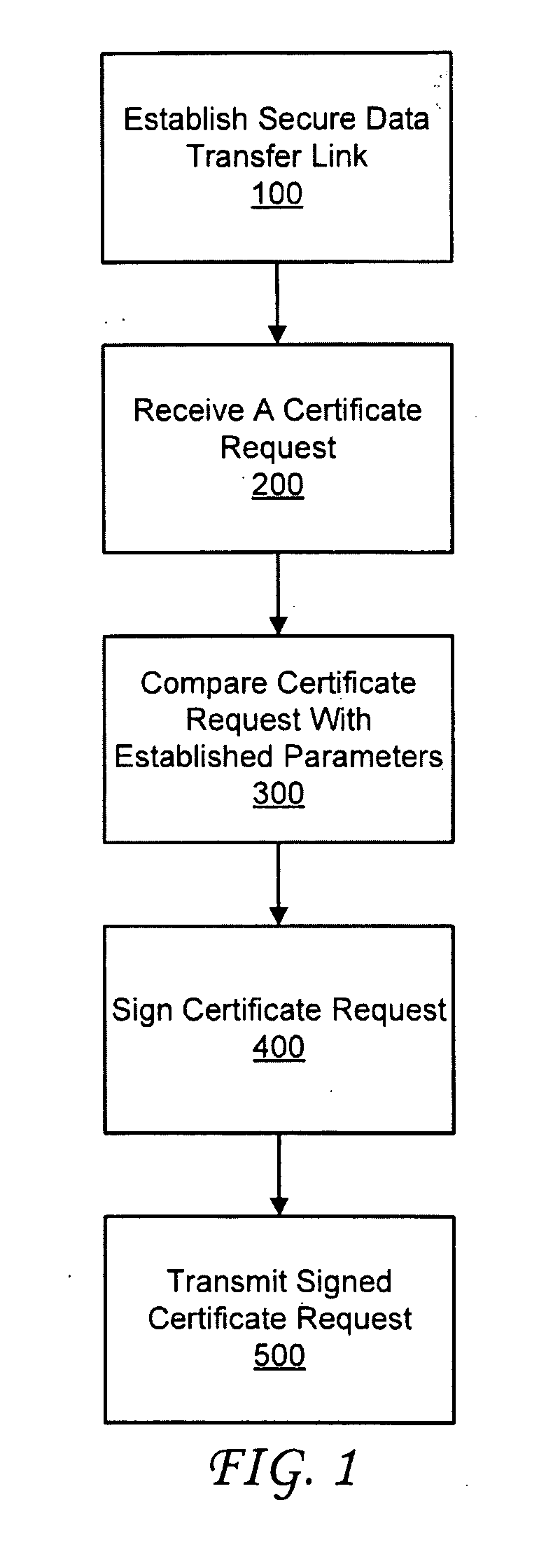
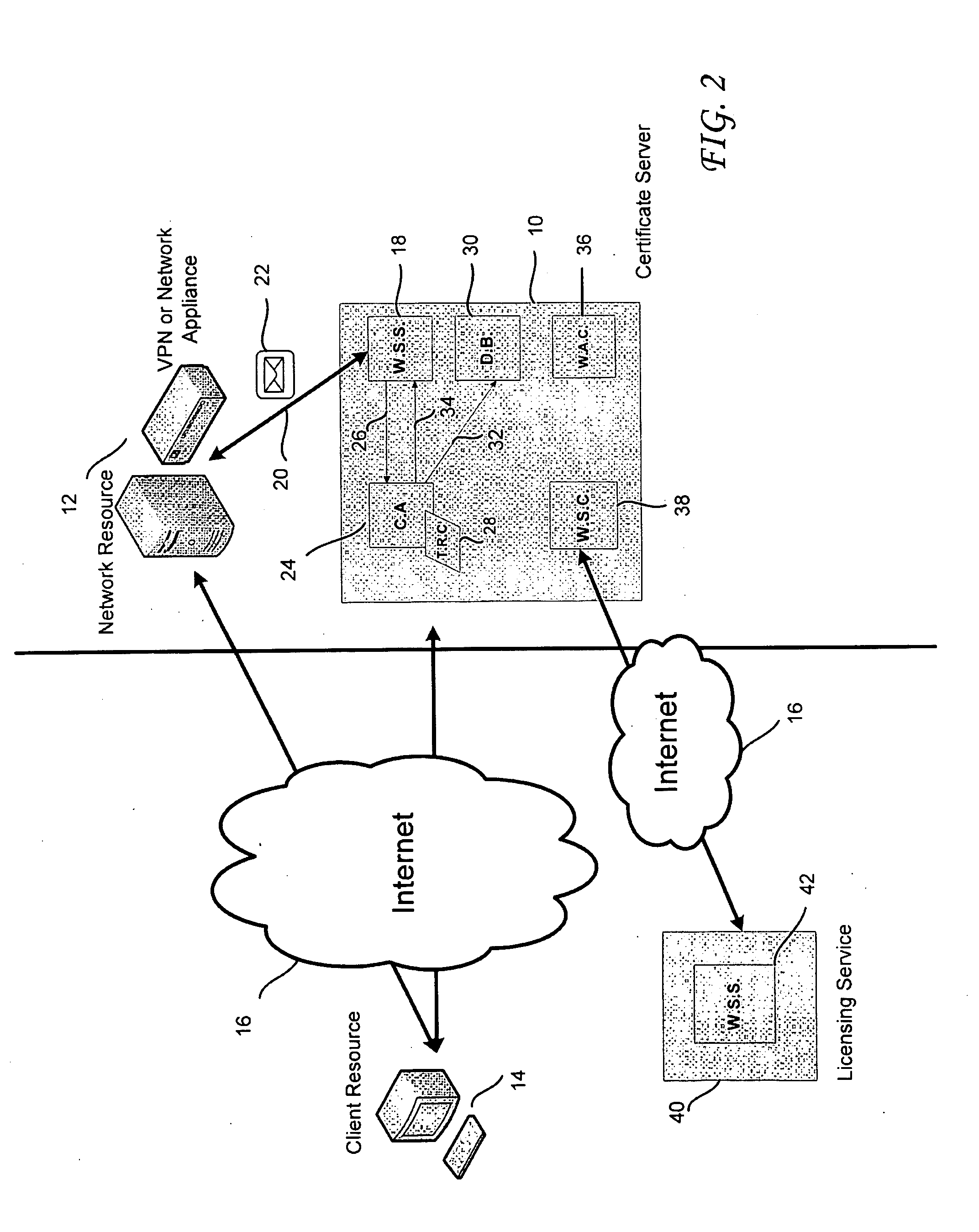
InactiveUS20100138907A1Easy to trackDigital data processing detailsUser identity/authority verificationDigital signatureWeb service
A certificate server is provided for issuing digital certificates to be used by a network resource and / or a client resource. The certificate server is configured to communicate with the network resource or the client resource to receive a certificate request. Upon receiving the certificate request, the certificate server may automate the process for authenticating the certificate request, validating the terms of the certificate request and digitally signing the certificate request. An authentication appliance may communicate with or be integrated within the certificate server. The certificate server includes a web service server, a certificate authority component, and a database that enable communication with either the network resource, client resource, or the authentication appliance to automate the administration process typically involved in receiving and signing a certificate request. The certificate authority component may sign the certificate request with a trusted root chain associated with the network resource.
Owner:SECUREAUTH CORP
Secure circuit for encryption key generation
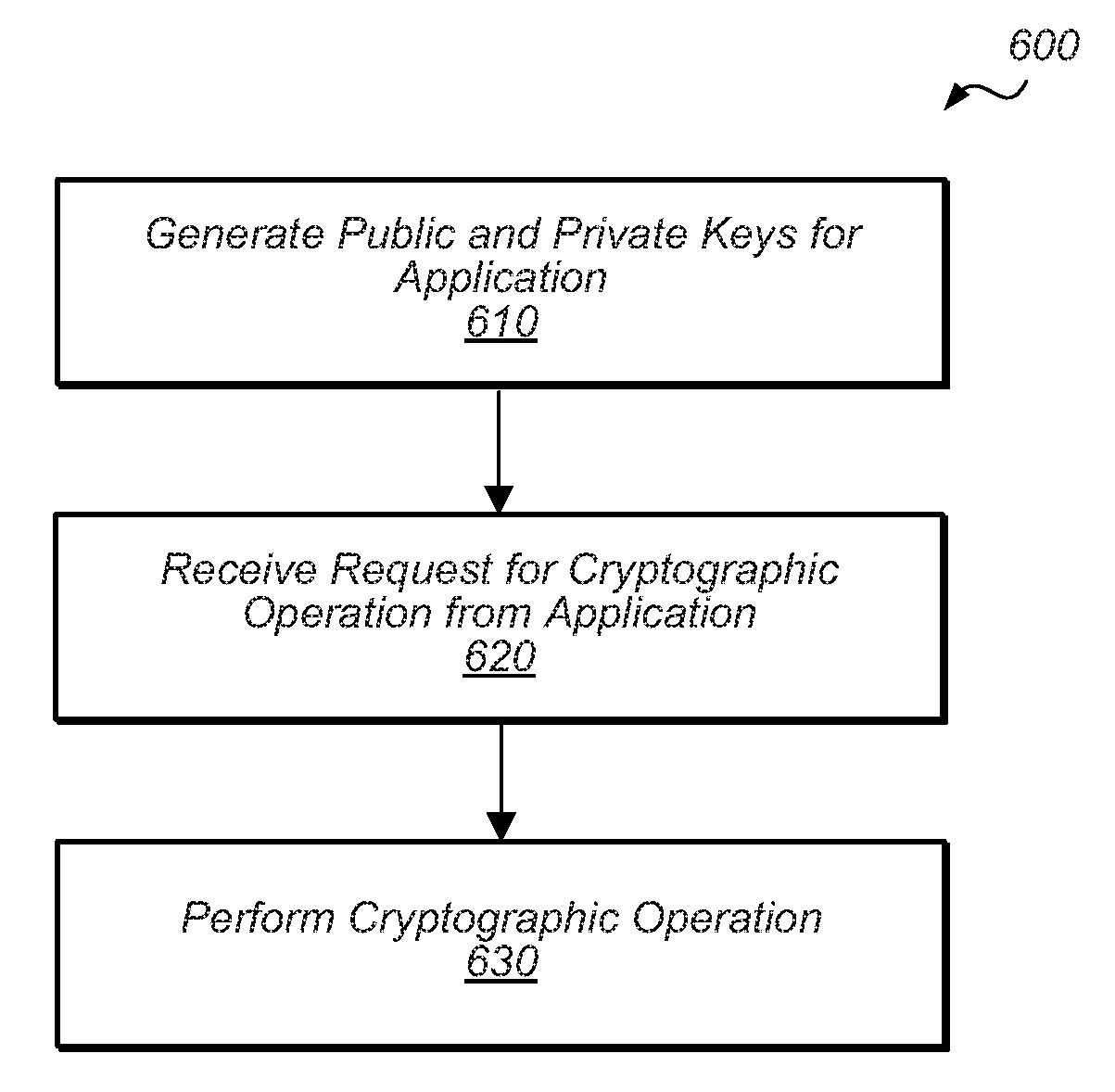
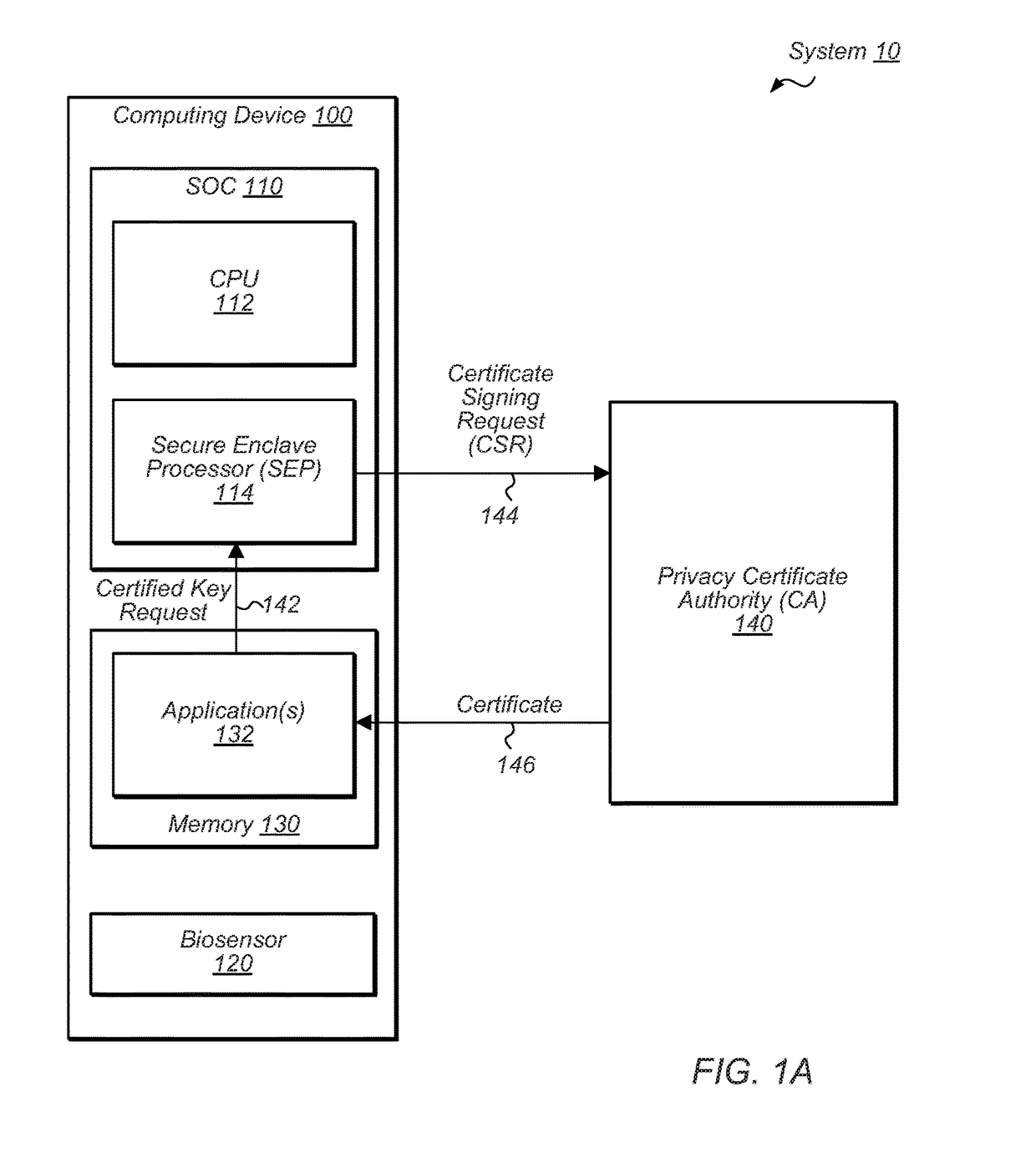
ActiveUS20170373843A1Easy to useKey distribution for secure communicationMultiple keys/algorithms usageCryptographic key generationCertificate signing request
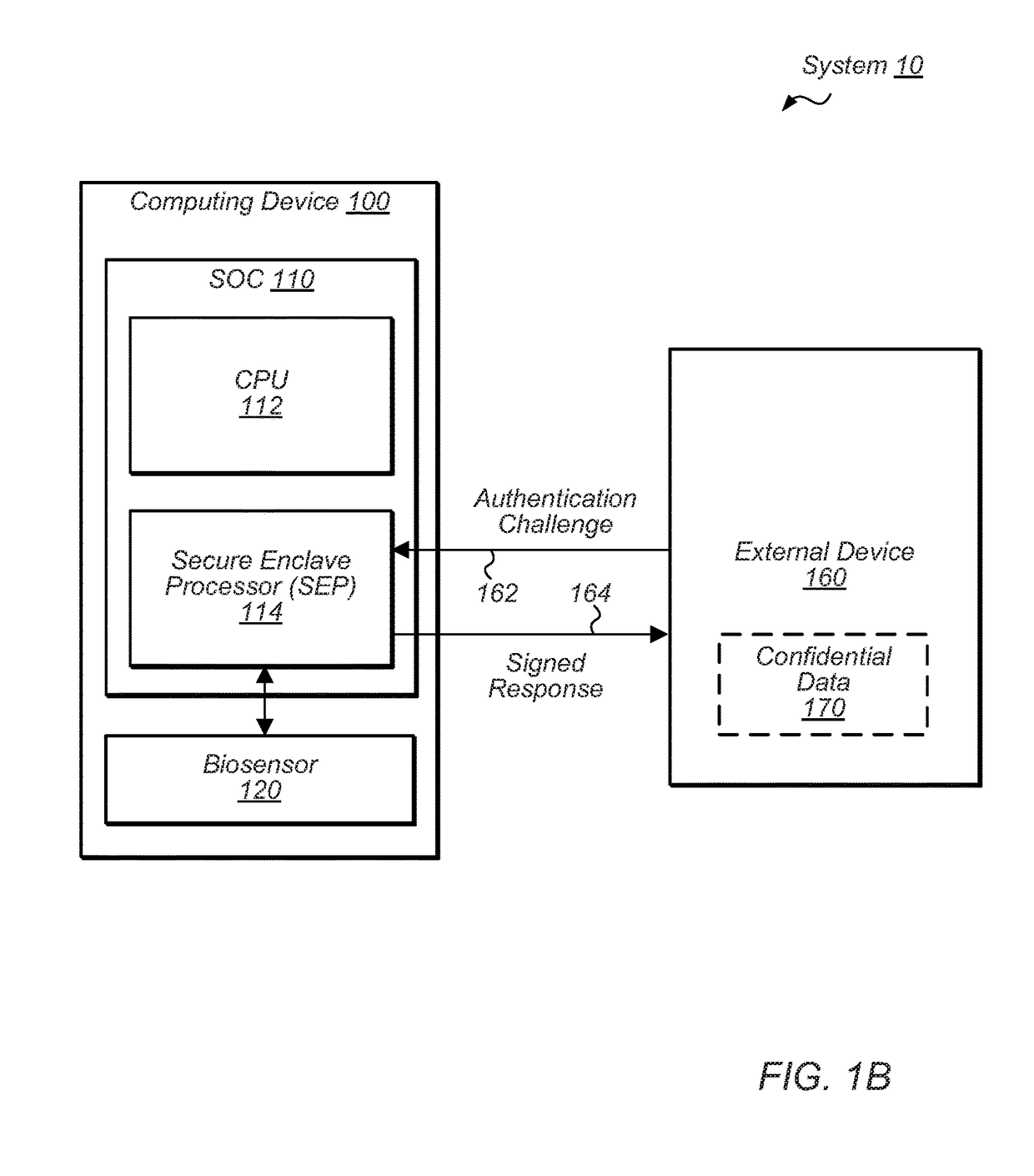
Techniques are disclosed relating to relating to a public key infrastructure (PKI). In one embodiment, an integrated circuit is disclosed that includes at least one processor and a secure circuit isolated from access by the processor except through a mailbox mechanism. The secure circuit is configured to generate a key pair having a public key and a private key, and to issue, to a certificate authority (CA), a certificate signing request (CSR) for a certificate corresponding to the key pair. In some embodiments, the secure circuit may be configured to receive, via the mailbox mechanism, a first request from an application executing on the processor to issue a certificate to the application. The secure circuit may also be configured to perform, in response to a second request, a cryptographic operation using a public key circuit included in the secure circuit.
Owner:APPLE INC
Automatic certificate enrollment in a special-purpose appliance
ActiveUS20150295892A1Multiple digital computer combinationsProgram controlUser authenticationCertificate signing request
A digital certificate is created transparently on a mobile device. A VPN appliance receives user credentials from an app, the credentials familiar to the user and associated with an enterprise authentication service. The credentials are validated, comprising the first user authentication in a two-factor authentication method. The user is then presented with a display in the app asking for a PIN. The appliance generates a PIN and sends it to the user via the user enterprise email. The user enters the PIN in the app display. This is the second factor in the two-factor authentication. Once the user is authenticated, the appliance sends data for generating a Certificate Signing Request (CSR) to the app. The app generates a CSR and the appliance sends the CSR to an enterprise CA. A certificate is signed and enrolled. The signed digital certificate is then sent to the wrapped app.
Owner:BLUE CEDAR NETWORKS INC
Gaming machine certificate creation and management
ActiveUS8386785B2Facilitates processing and issuingDigital data processing detailsUser identity/authority verificationCertificate signing requestComputer science
Owner:IGT
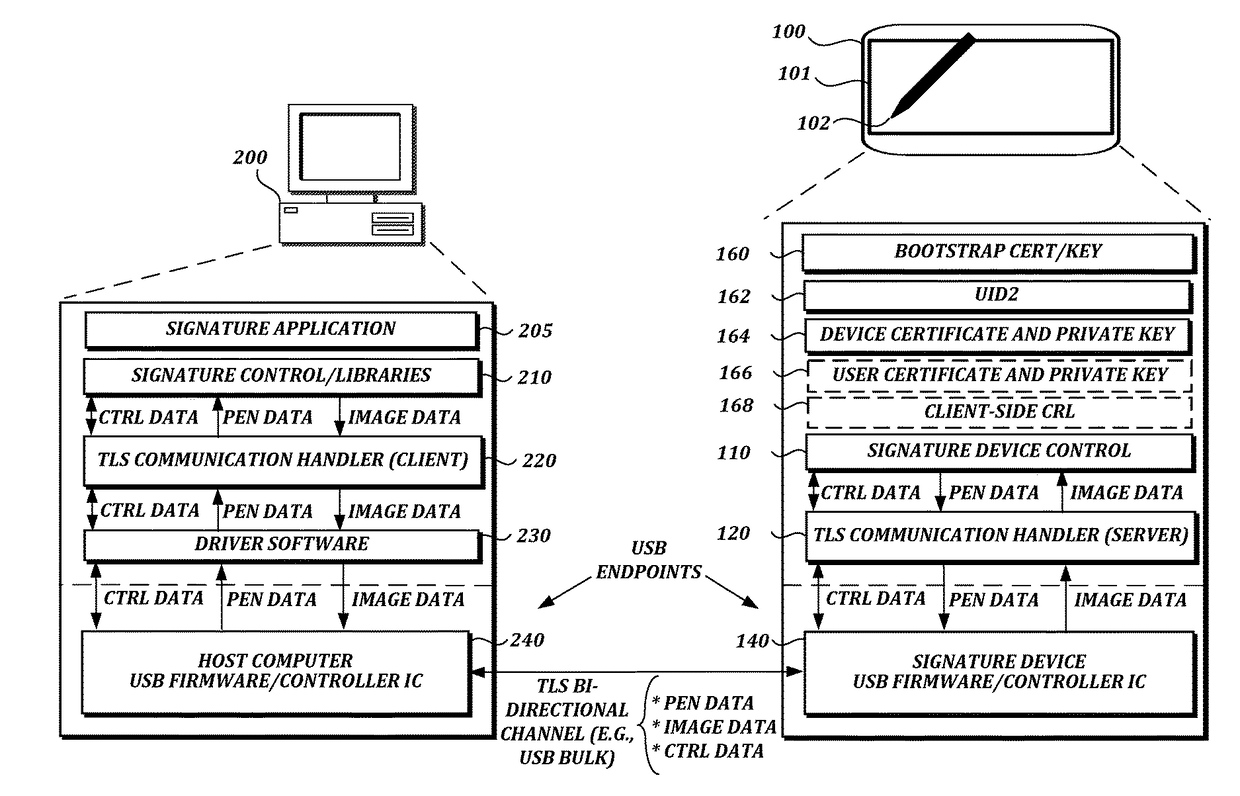
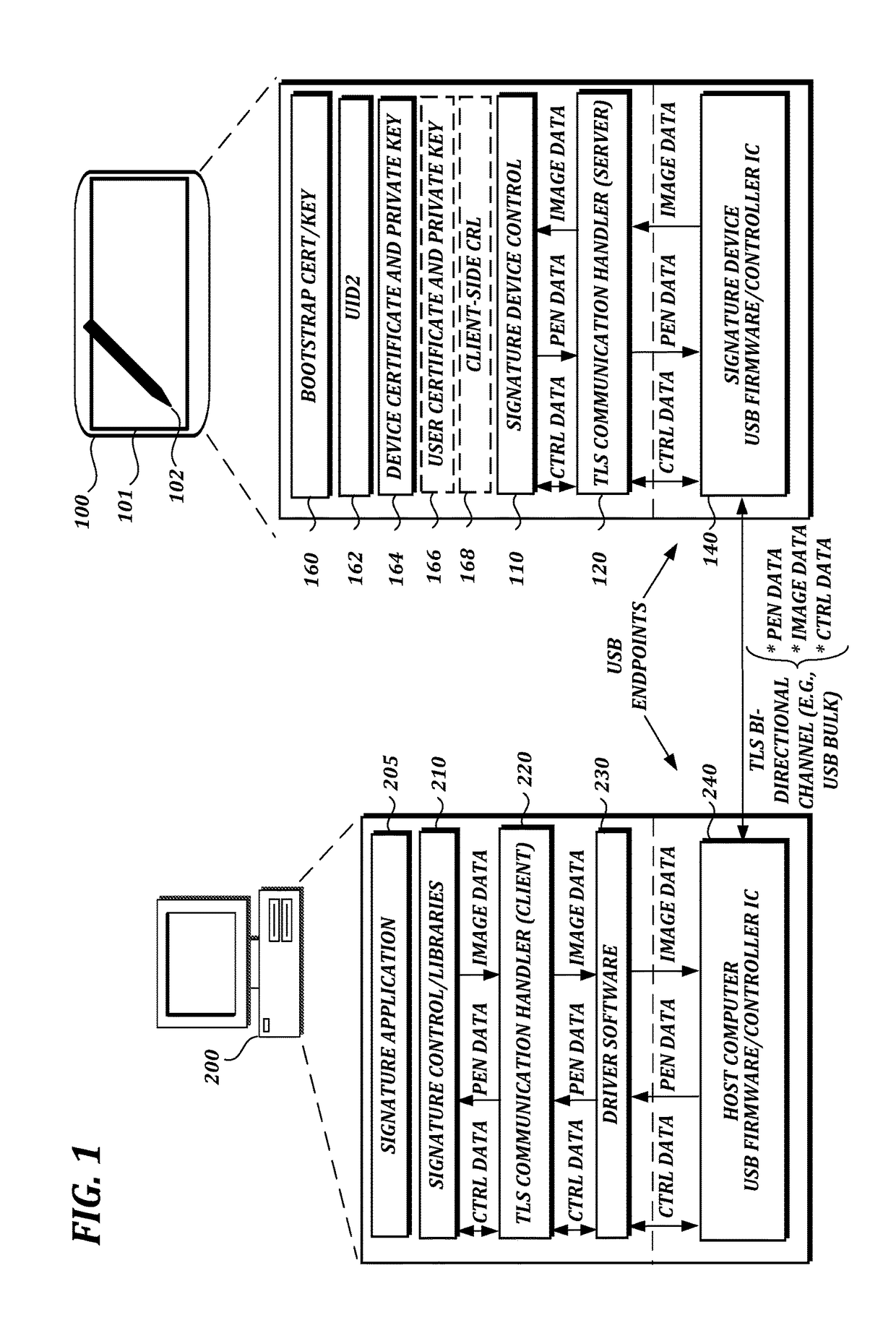
Authentication and secure transmission of data between signature devices and host computers using transport layer security
ActiveUS20180060608A1Well formedAcutation objectsKey distribution for secure communicationSecure transmissionCertificate signing request
A transport layer security (TLS) connection is established between a signature device and the host computer via an interface (e.g., a universal serial bus (USB) interface). The signature device acts as a TLS server, and the host computer acts as a TLS client. Data such as pen data, control data, or image data may be received or transmitted via a USB bulk transfer mechanism. In one aspect, the host computer sends a command via the interface to the signature device to generate a new key pair, receives a certificate signing request (CSR) from the signature device via the interface, sends the CSR to a user certificate authority, receives a public key certificate from the user certificate authority, and sends the public key certificate to the signature device via the interface.
Owner:WACOM CO LTD
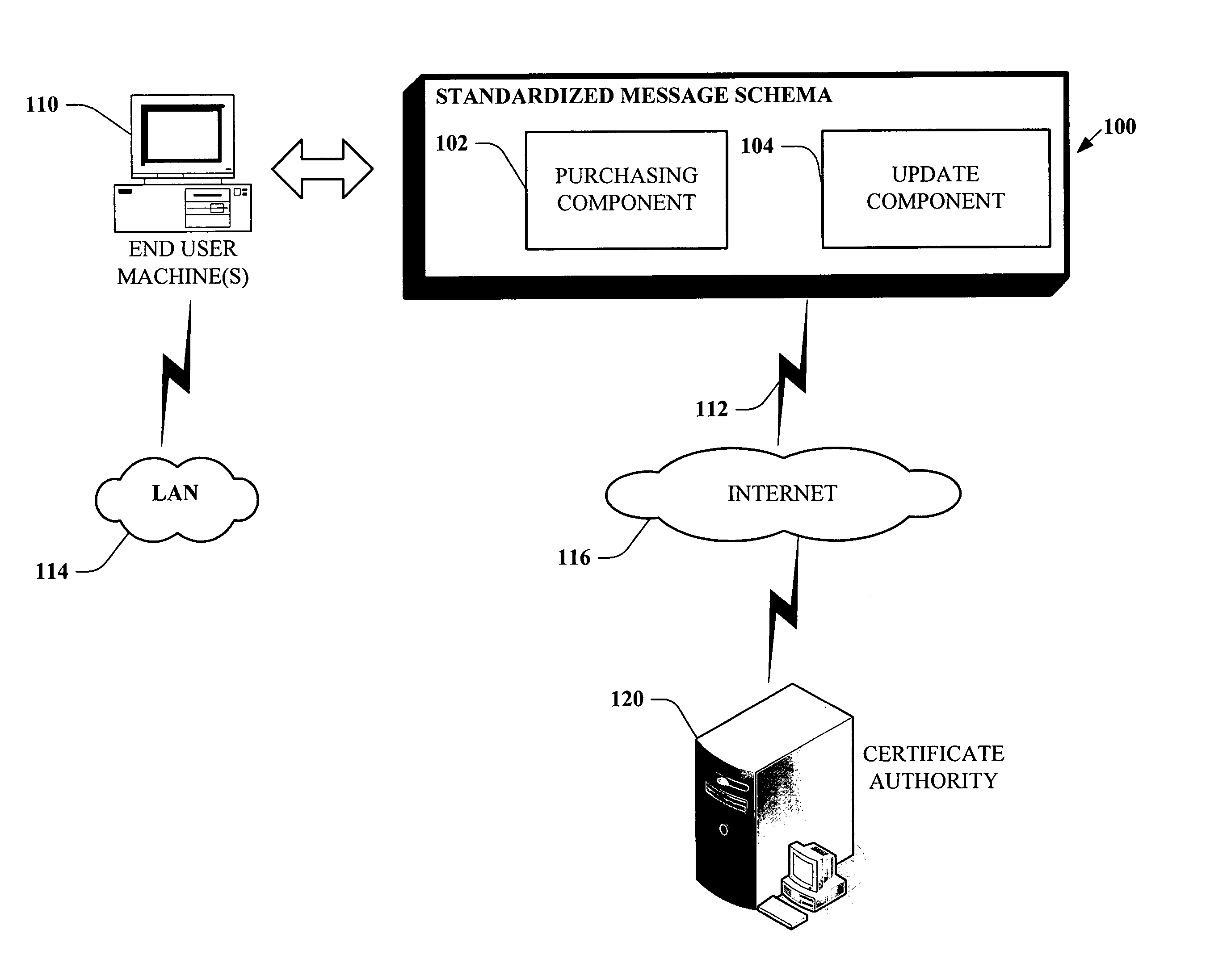
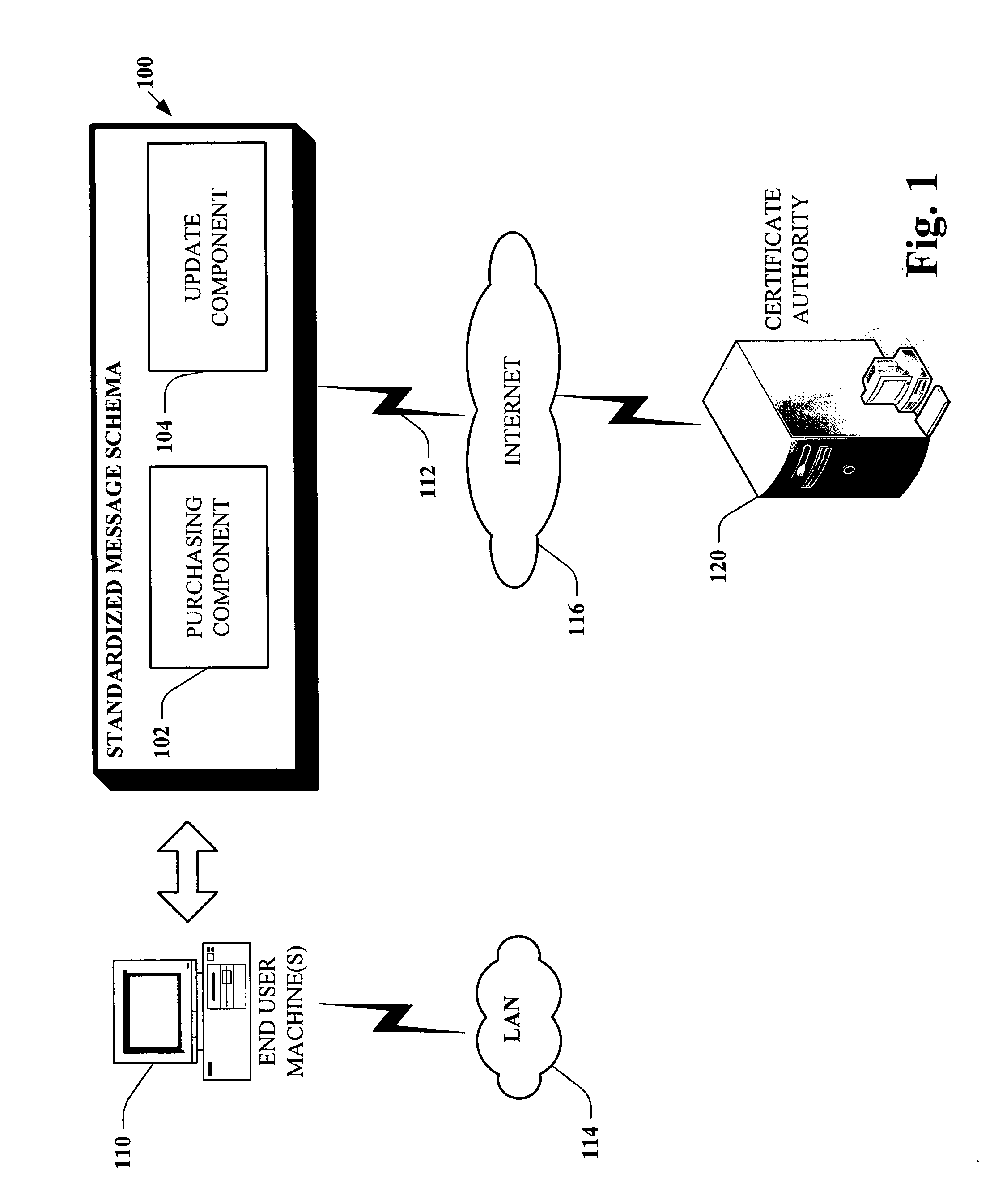
Message based network configuration of server certificate purchase
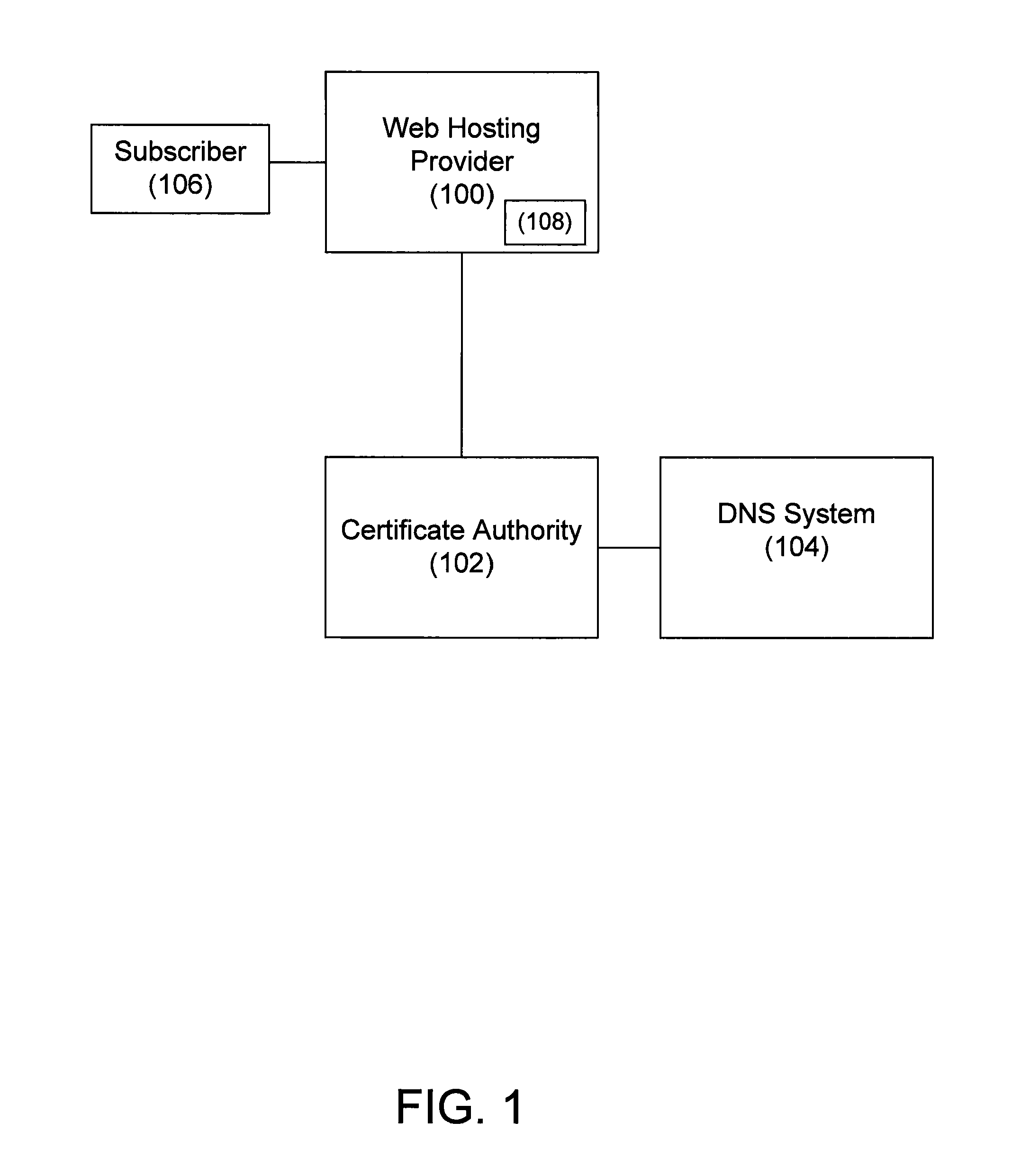
InactiveUS20060129804A1Facilitates initial server configurationSimple componentsUser identity/authority verificationDigital data authenticationDomain nameService planning
Systems and methodologies that facilitate obtaining a digital certificate from a Certificate Authority, by using a well defined protocol exchanged between a user machine and the Certificate Authority. The well defined protocol employs; a purchasing component and an update component. Once a user has obtained a domain name, the purchasing component can be used to query the Certificate Authority for terms of the service plans to issue the digital certificate and to programmatically create and transmit a certificate signing request. The purchase component will also allow the signed certificate to be configured on the requesting cluster of machines. The update component can provide a revised and / or updated list of contact information to the Certificate Authority in addition to revoking an existing certificate.
Owner:MICROSOFT TECH LICENSING LLC
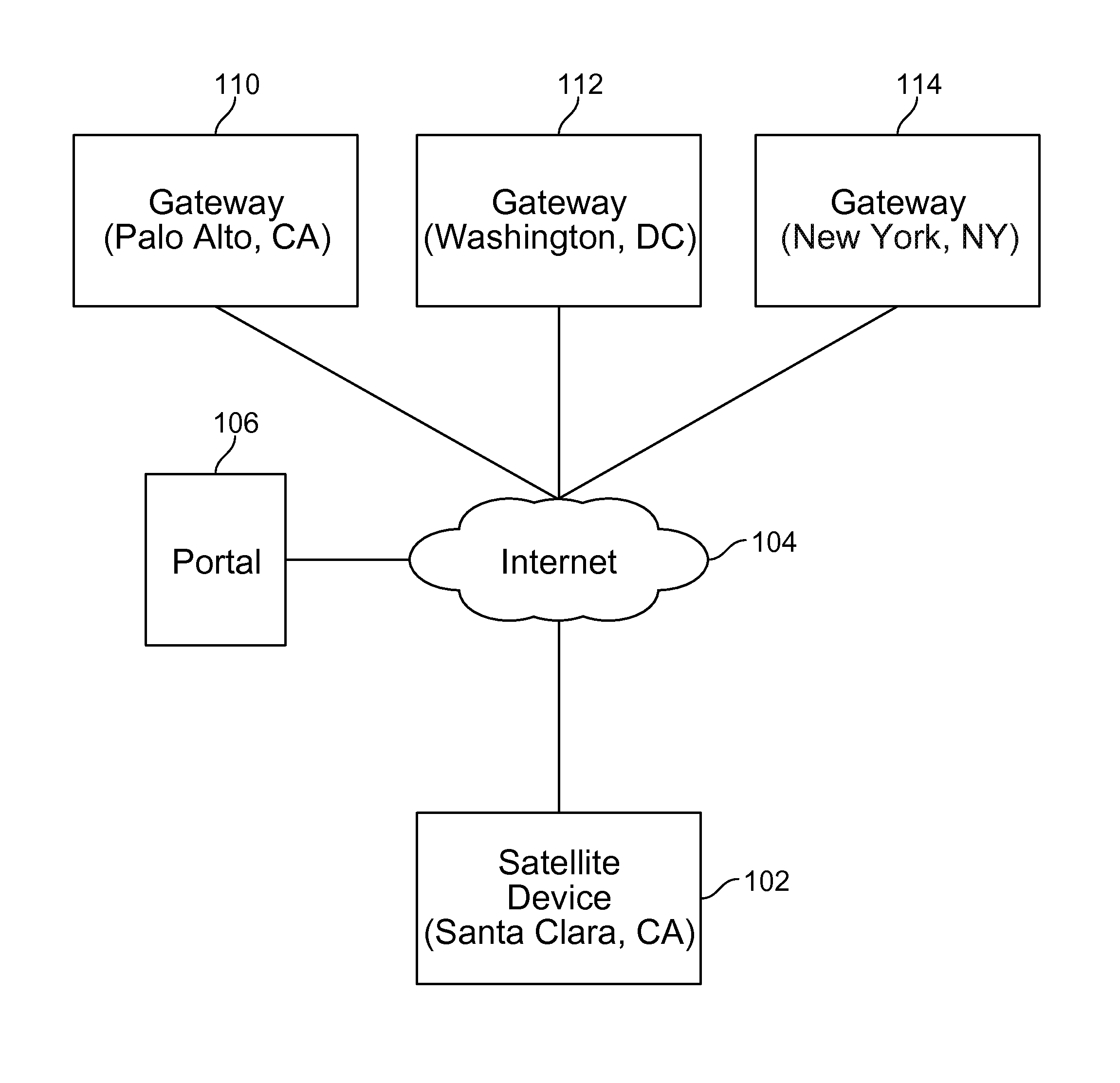
Credentials management in large scale virtual private network deployment
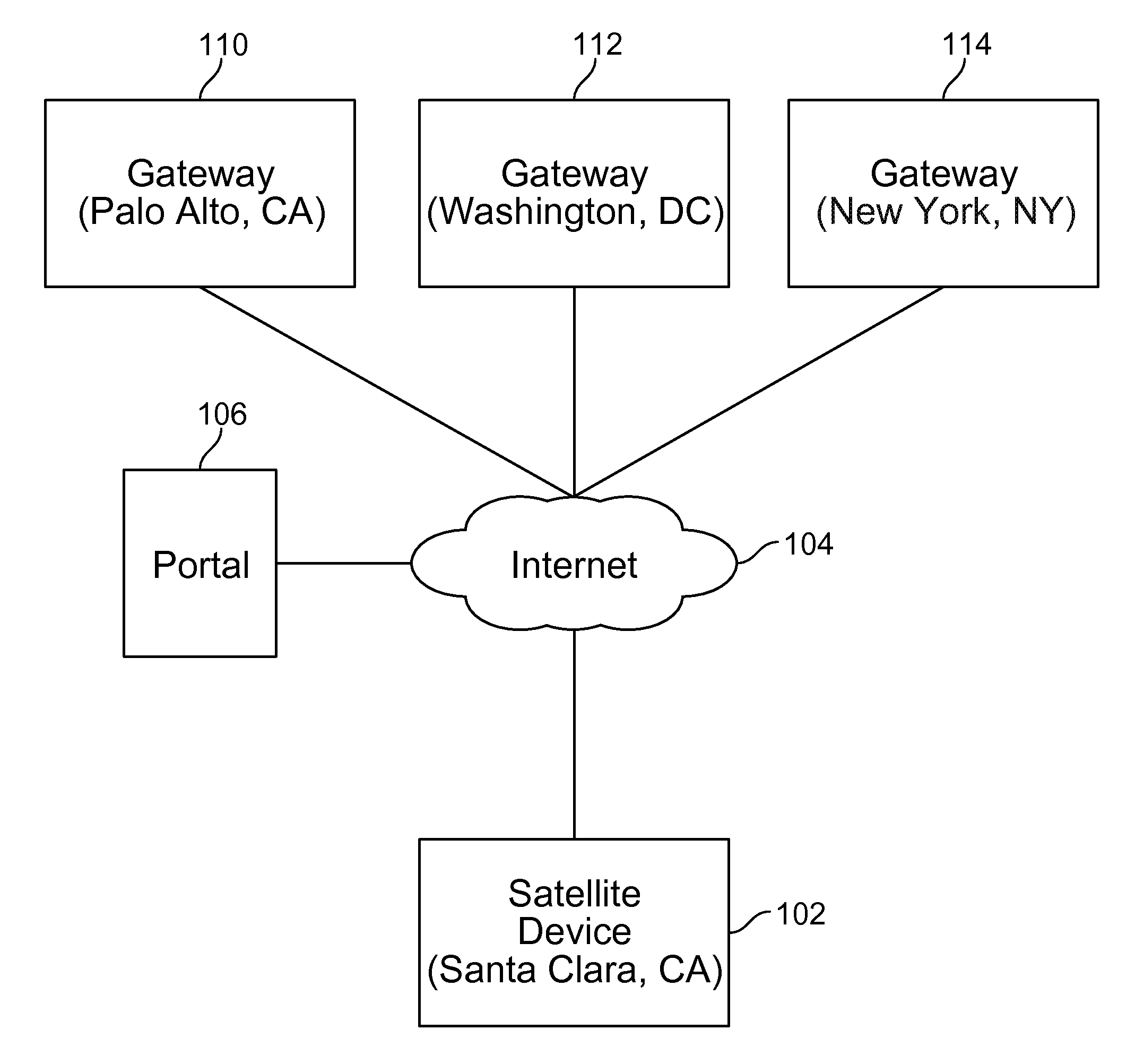
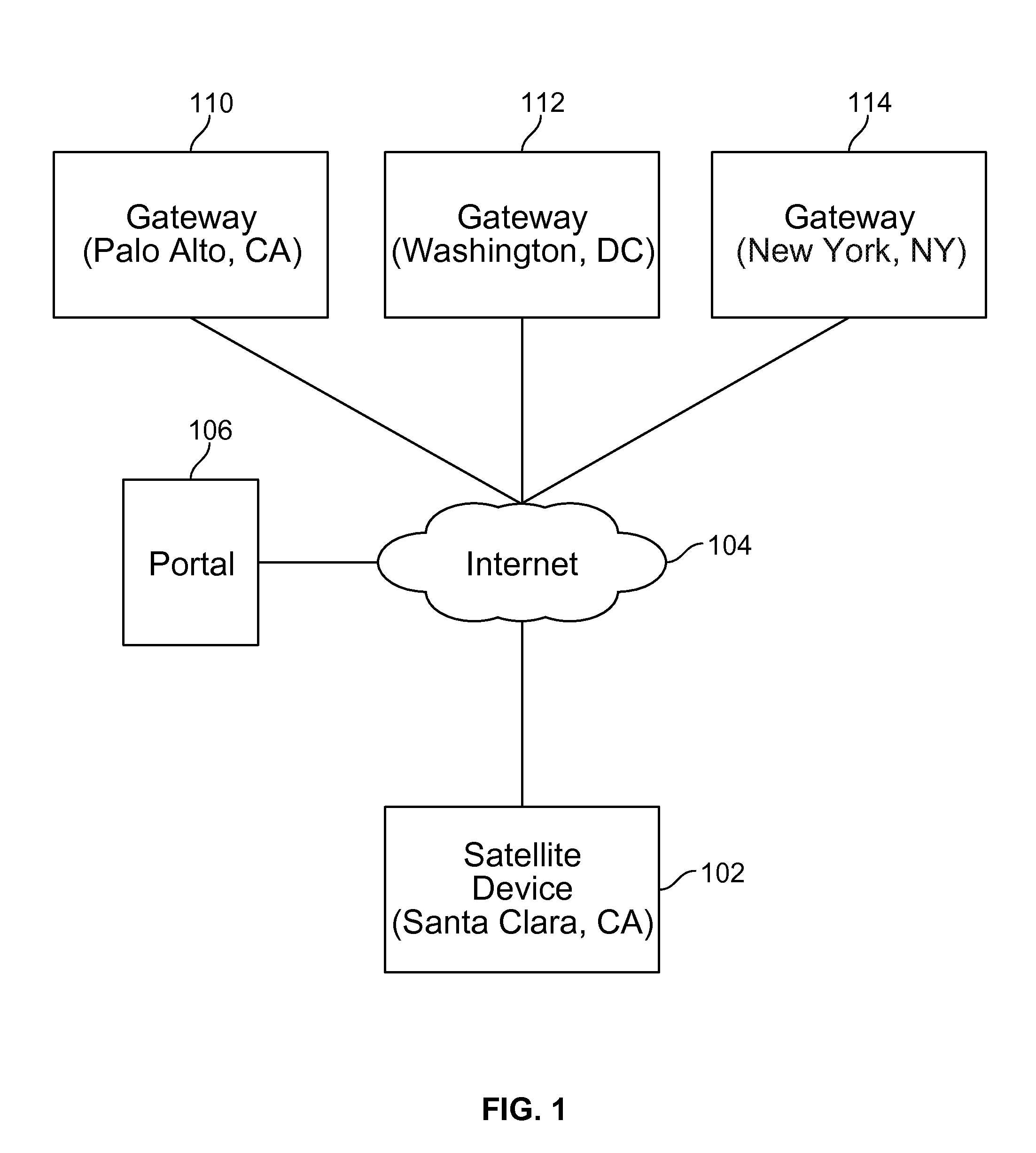
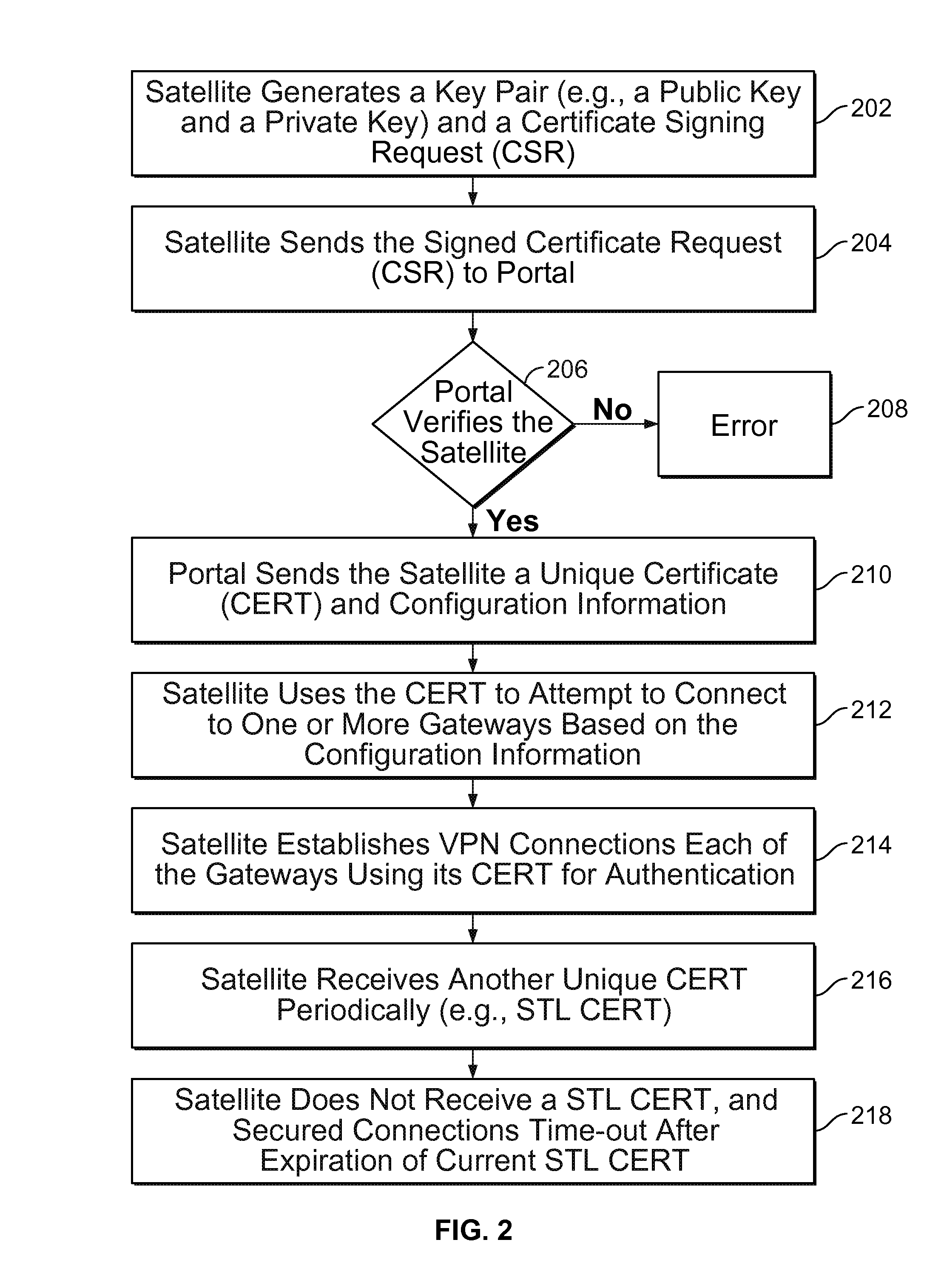
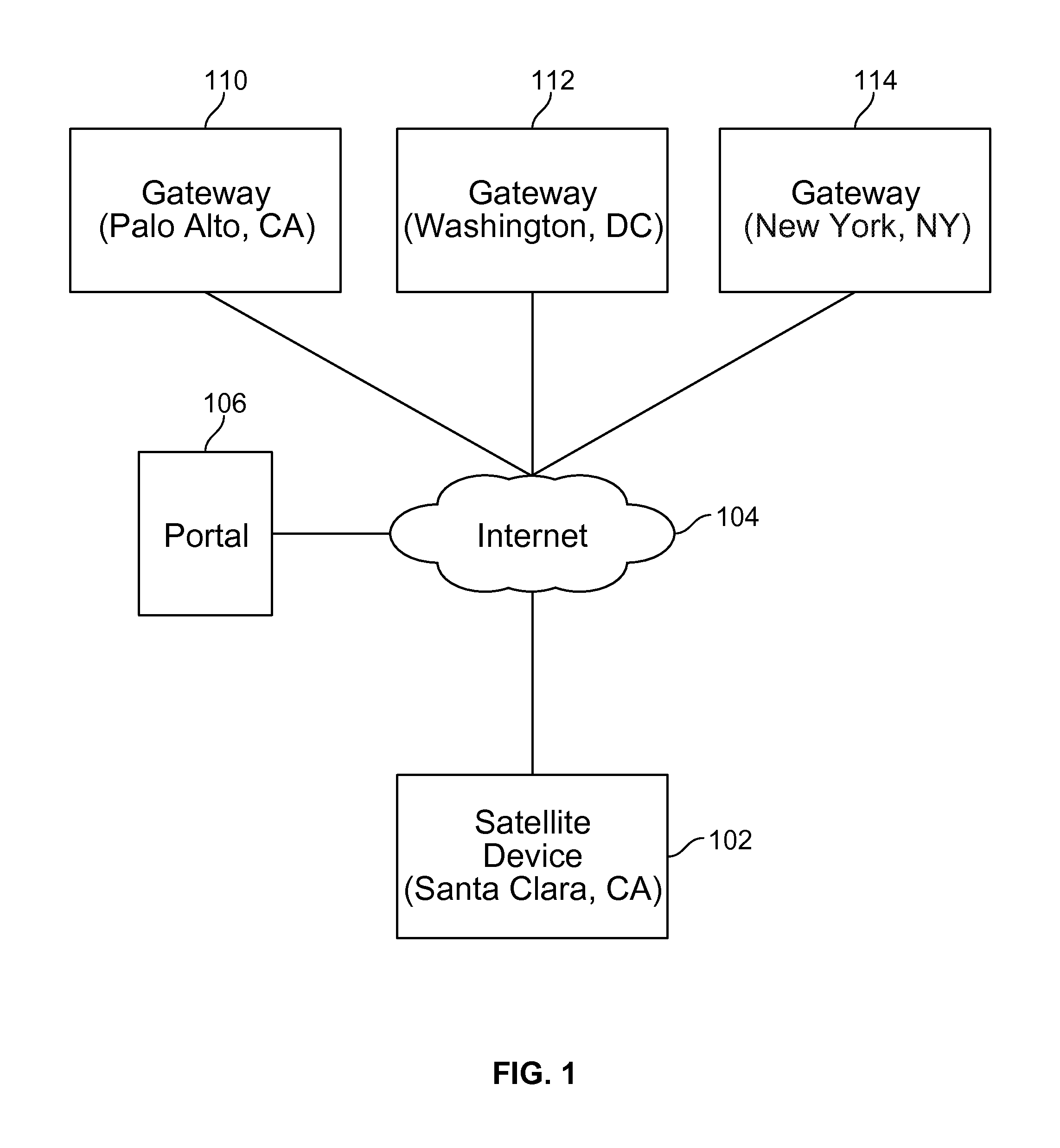
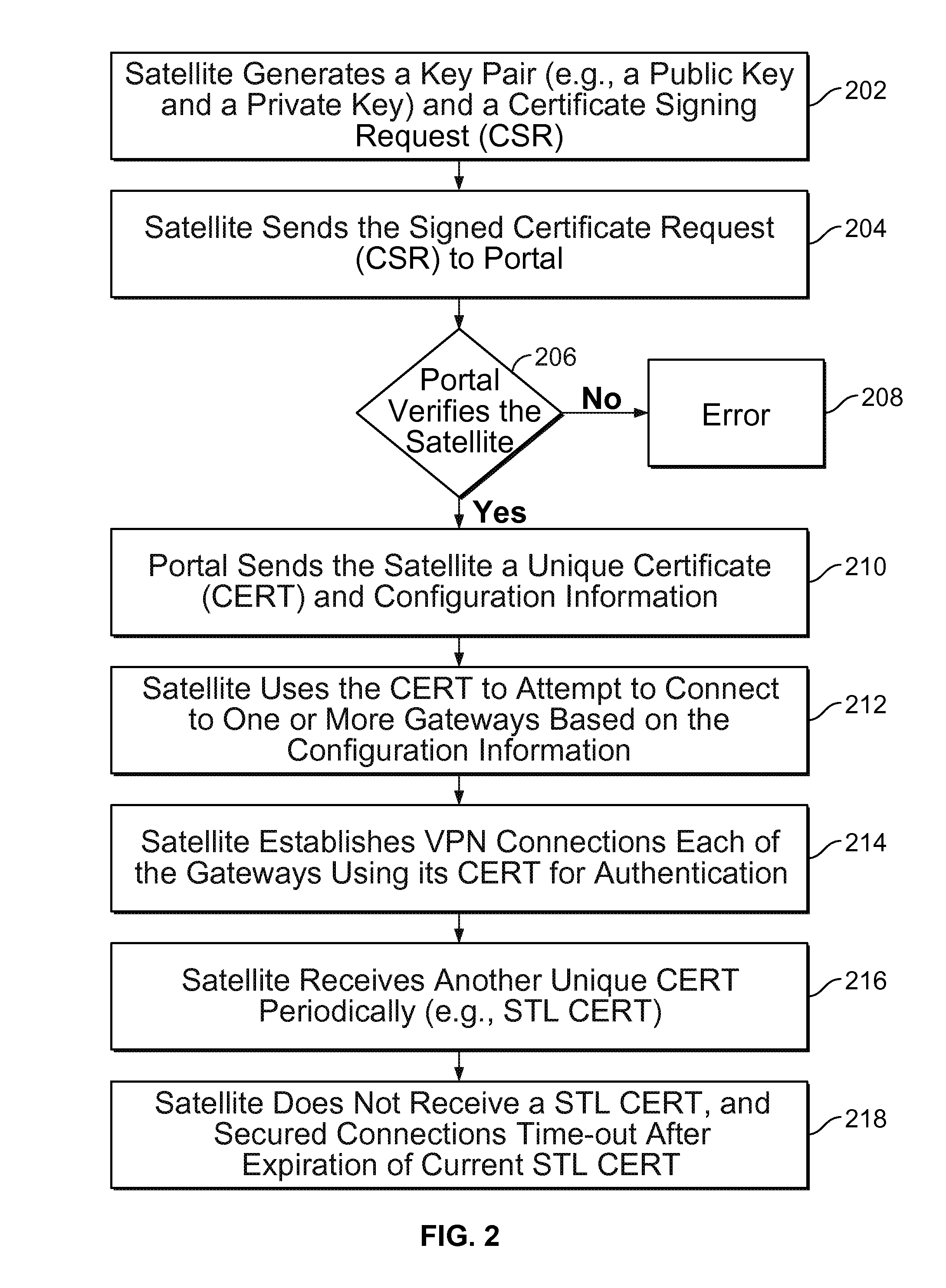
Techniques for credentials management in large scale virtual private network (VPN) deployment are disclosed. In some embodiments, credentials management in large scale VPN deployment includes generating a public / private key pair and a certificate signing request at a satellite device; automatically communicating the certificate signing request to a portal over a public, untrusted network to authenticate the satellite device using a serial number associated with the satellite device, in which the certificate signing request and the serial number are verified by the portal; and receiving a certificate from the portal for using to establish VPN connections and configuration information for the satellite device, in which the certificate includes a credential signed by a trusted certificate authority, and the configuration information includes gateway configuration information identifying a plurality of gateways to which the satellite device is configured to connect using VPN connections.
Owner:PALO ALTO NETWORKS INC
Computer system and program to update SSL certificates
InactiveUS7512974B2Digital data processing detailsUser identity/authority verificationProgram instructionSelf-signed certificate
System and computer program product for updating an SSL certificate for a server. First program instructions detect when a change has been made to a name, domain or IP address of the server and detect that the server is using an SSL certificate based on a name, domain or IP address applicable before the change. In response, the first program instructions notify an administrator that a change is required to the SSL certificate to reflect the change to the name, domain or IP address. Second program instructions respond to a request by the administrator, to automatically create a new SSL certificate signing request. The new SSL certificate signing request is a form which can be sent to an SSL certificate authority. Third program instructions respond to another request by the administrator, to send the new SSL certificate signing request to the SSL certificate authority. Fourth program instructions respond to receipt of a new SSL certificate from the SSL certificate authority and another request by the administrator, to substitute the new SSL certificate for the existing SSL certificate. Fourth program instructions query the administrator if the administrator wants to use a new self-signed SSL certificate reflecting the change to the name, domain or IP address of the server, until the new SSL certificate signed by the SSL certificate authority is received from the SSL certificate authority, and if so, generate the new SSL self-signed certificate. Other program instructions respond to a request by the administrator, to create a self-signed SSL certificate and substitute the self-signed SSL certificate for the existing SSL certificate.
Owner:IBM CORP
Credentials management in large scale virtual private network deployment
ActiveUS20150195252A1Digital data processing detailsMultiple digital computer combinationsPrivate networkCertificate signing request
Techniques for credentials management in large scale virtual private network (VPN) deployment are disclosed. In some embodiments, credentials management in large scale VPN deployment includes generating a public / private key pair and a certificate signing request at a satellite device; automatically communicating the certificate signing request to a portal over a public, untrusted network to authenticate the satellite device using a serial number associated with the satellite device, in which the certificate signing request and the serial number are verified by the portal; and receiving a certificate from the portal for using to establish VPN connections and configuration information for the satellite device, in which the certificate includes a credential signed by a trusted certificate authority, and the configuration information includes gateway configuration information identifying a plurality of gateways to which the satellite device is configured to connect using VPN connections.
Owner:PALO ALTO NETWORKS INC
Entity registration in multiple dispersed storage networks
InactiveUS20110289566A1Error detection/correctionDigital data processing detailsStorage area networkCertificate signing request
A method begins by a processing module outputting a registration request message that includes requesting access to a local dispersed storage network (DSN) and requesting access to a global DSN. The method continues with the processing module receiving a registration response message that includes a global universal unique identifier (UUID) and a local UUID. The method continues with the processing module generating a global public-private key pair and a local public-private key pair and generating a global certificate signing request (CSR) based on the global UUID and a private key of the global public-private key pair. The method continues with the processing module generating a local CSR based on the local UUID and a private key of the local public-private key pair, sending the global and local CSRs to a certificate authority (CA), and receiving a signed global certificate and a signed local certificate.
Owner:PURE STORAGE
Security certificate updating method, client and server
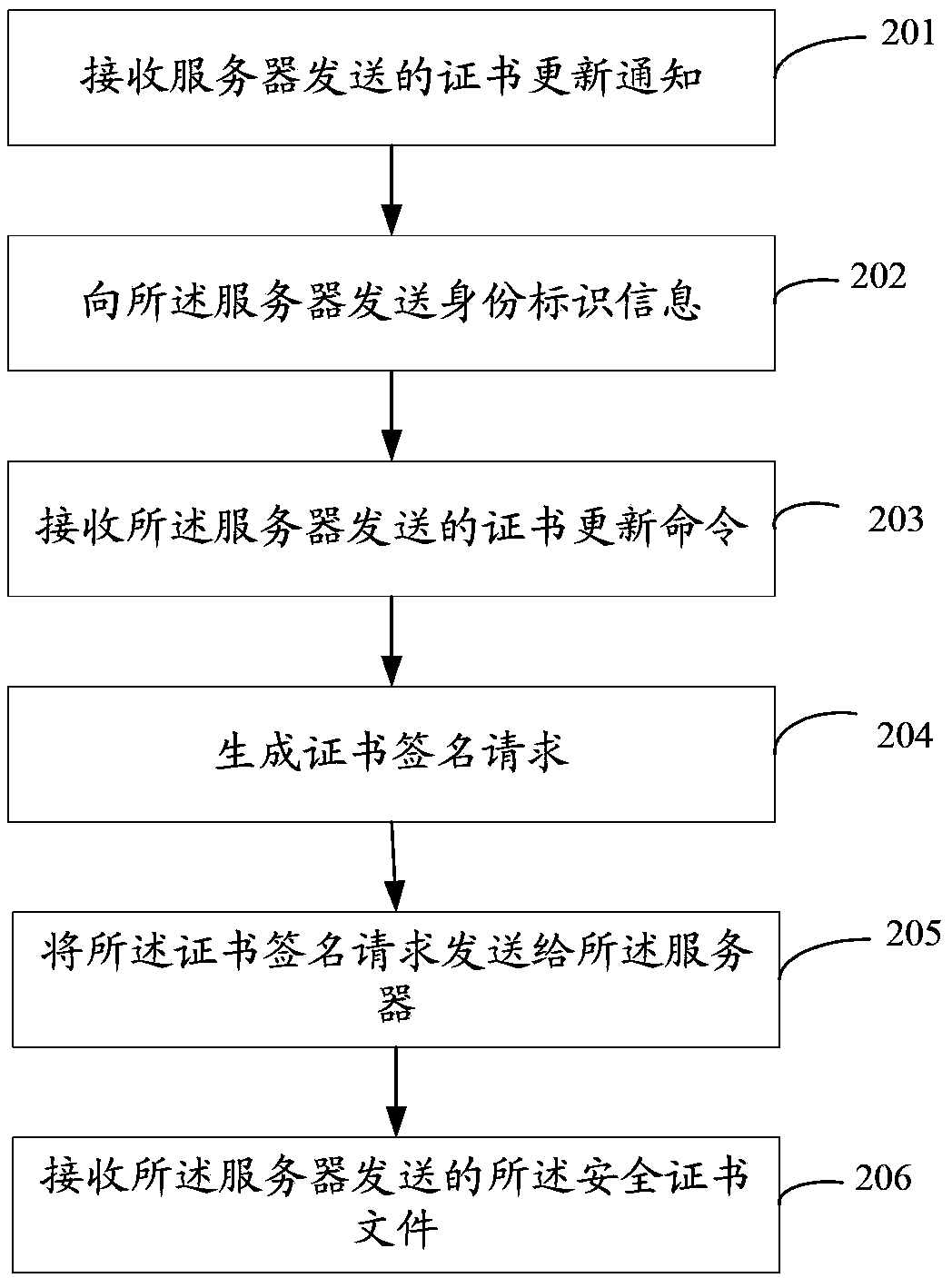
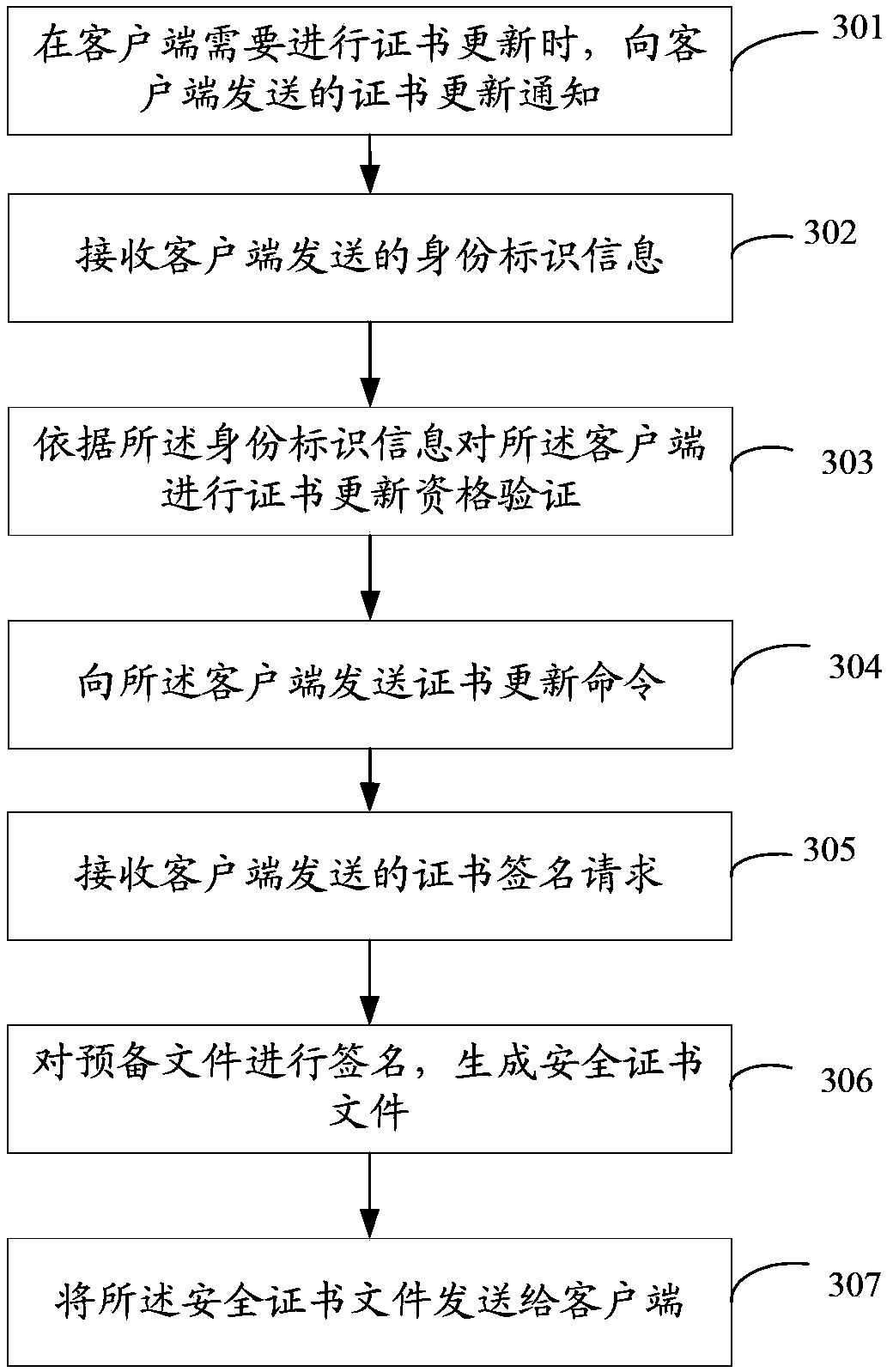
ActiveCN103888422ACause costImprove maintenance efficiencyTransmissionCertificate signing requestClient-side
The invention relates to a security certificate updating method. The method comprises the following steps: after a client establishes a connection with a server, the client receives a certificate updating notification sent by the server when a certificate needs updating; after receiving the certificate updating notification, the client sends identity identification information to the server; the client receives a certificate updating command which is sent when the server determines the client is qualified for carrying out certificate updating, and generates a certificate signature request comprising a security certificate preparation file after receiving the certificate updating command; the client sends the certificate signature request to the server; and the client receives the security certificate file sent by the server. According to the security certificate updating method provided in the embodiment of the invention, cost on manual maintenance which is performed by workers on the client can be avoided, and the maintenance efficiency of the remote client is improved.
Owner:杭州平治信息技术股份有限公司
Storage and retrieval of dispersed storage network access information
A method begins by a dispersed storage (DS) processing module receiving a certificate signing request (CSR) from a user device. The method continues with the DS processing module generating a set of hidden passwords based on the CSR and accessing a set of authenticating units to obtain a set of passkeys. The method continues with the DS processing module retrieving a set of encrypted shares and decrypting the set of encrypted shares to produce a set of encoded shares. The method continues with the DS processing module decoding the set of encoded shares to recapture a private key and generating a user signed certificate based on the private key. The method continues with the DS processing module discarding the private key to substantially protect the private key from the user device and outputting the user signed certificate to the user device.
Owner:PURE STORAGE
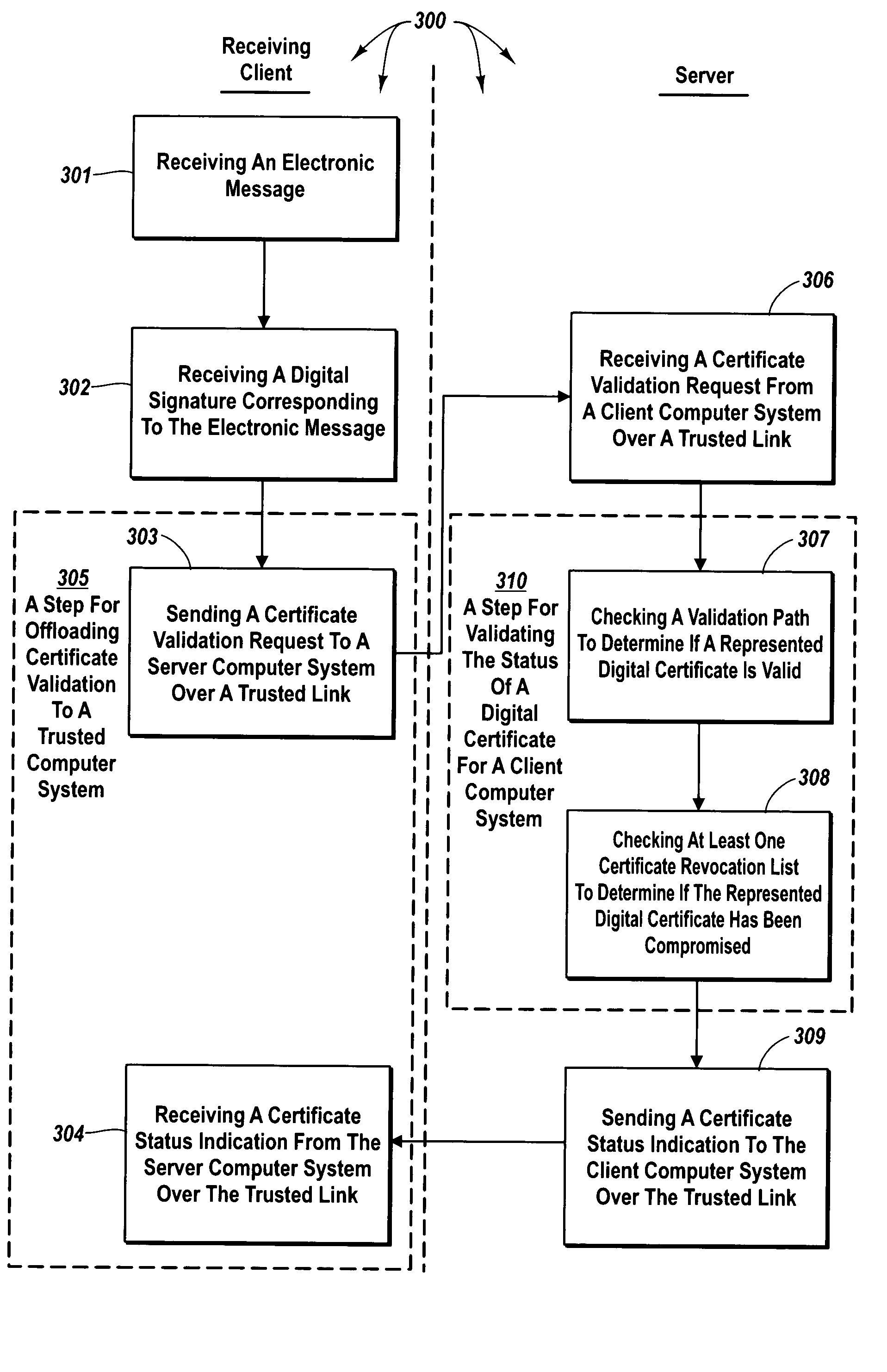
Delegating certificate validation
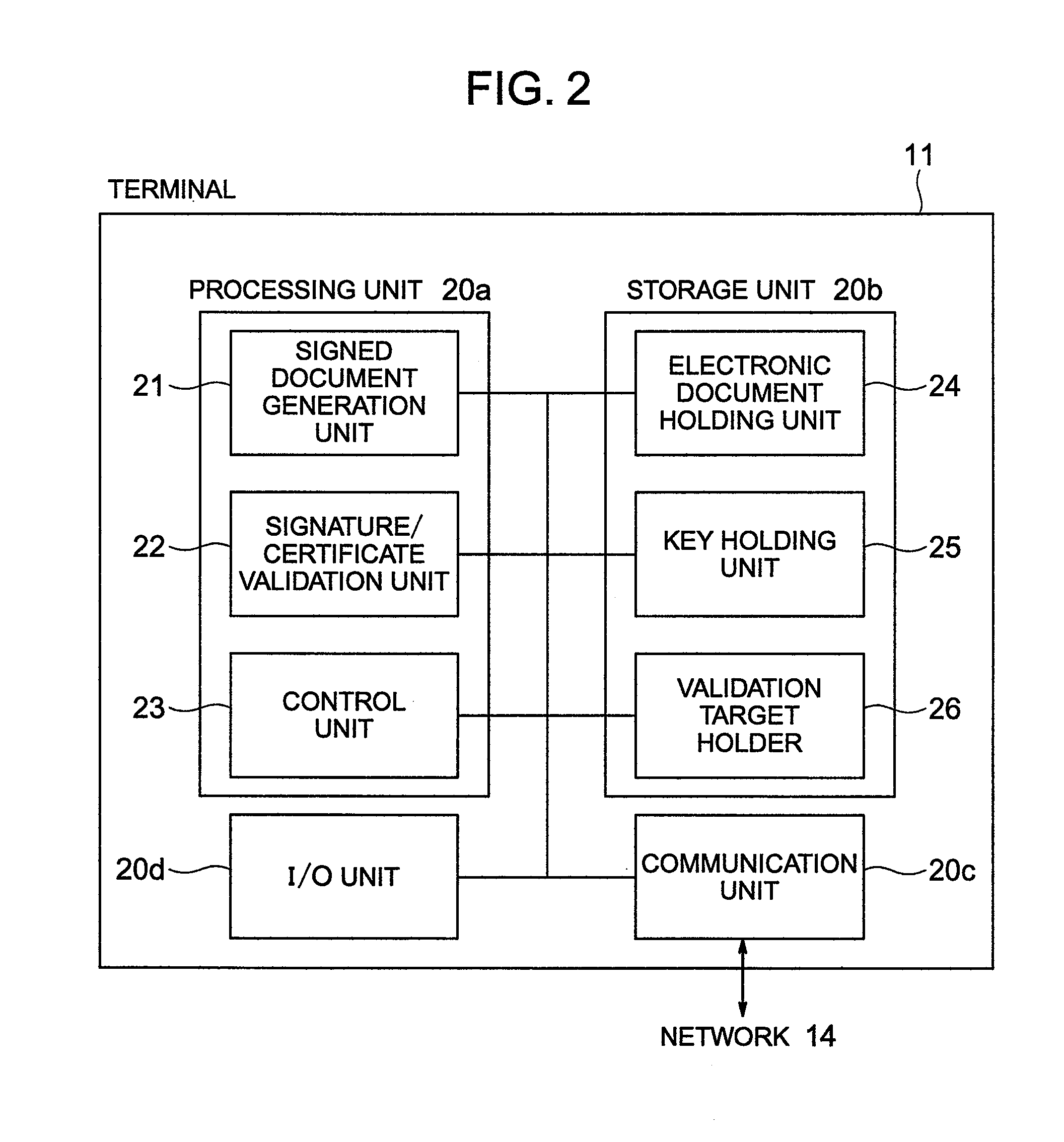
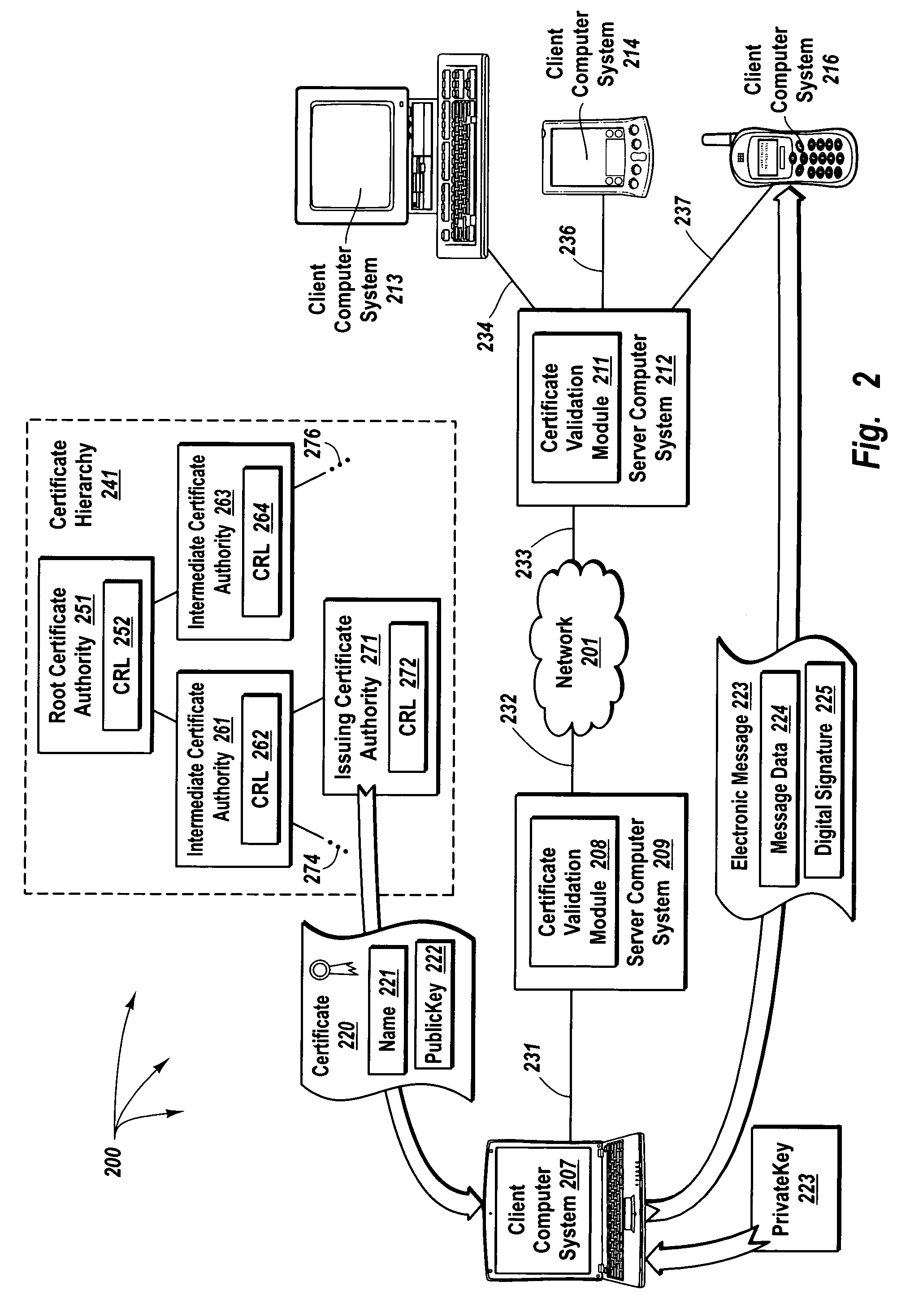
ActiveUS7395428B2Valid verificationSufficient informationUser identity/authority verificationCertificate signing requestComputerized system
The principles of the present invention provide for delegating certificate validation. A client computer system sends a certificate validation request to a server computer system over a trusted link. The certificate validation request includes at least enough certificate information for a certificate authority to identify a digital certificate that binds a sending entity to a private key. The server computer system checks a validation path to determine if the digital certificate is valid and at least one certificate revocation list to determine if the certificate has been compromised. The server computer system sends a certificate status indication to the client computer system over the trusted link. Accordingly, the resources of the server computer system, instead of the client computer system, are utilized to validate a digital certificate. Further, digital certificate validation can be delegated to a server computer system that attempts to pre-validate a digital certificate.
Owner:MICROSOFT TECH LICENSING LLC
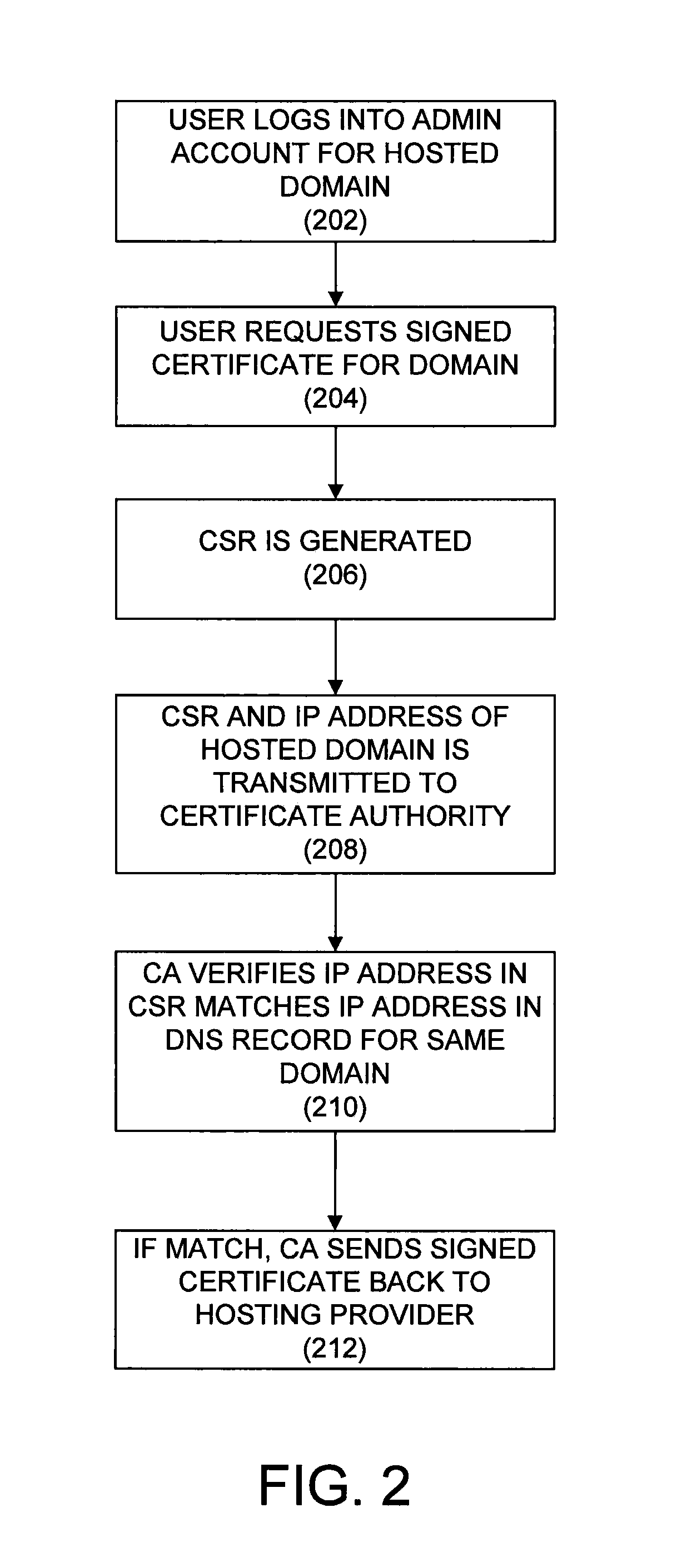
System for domain control validation
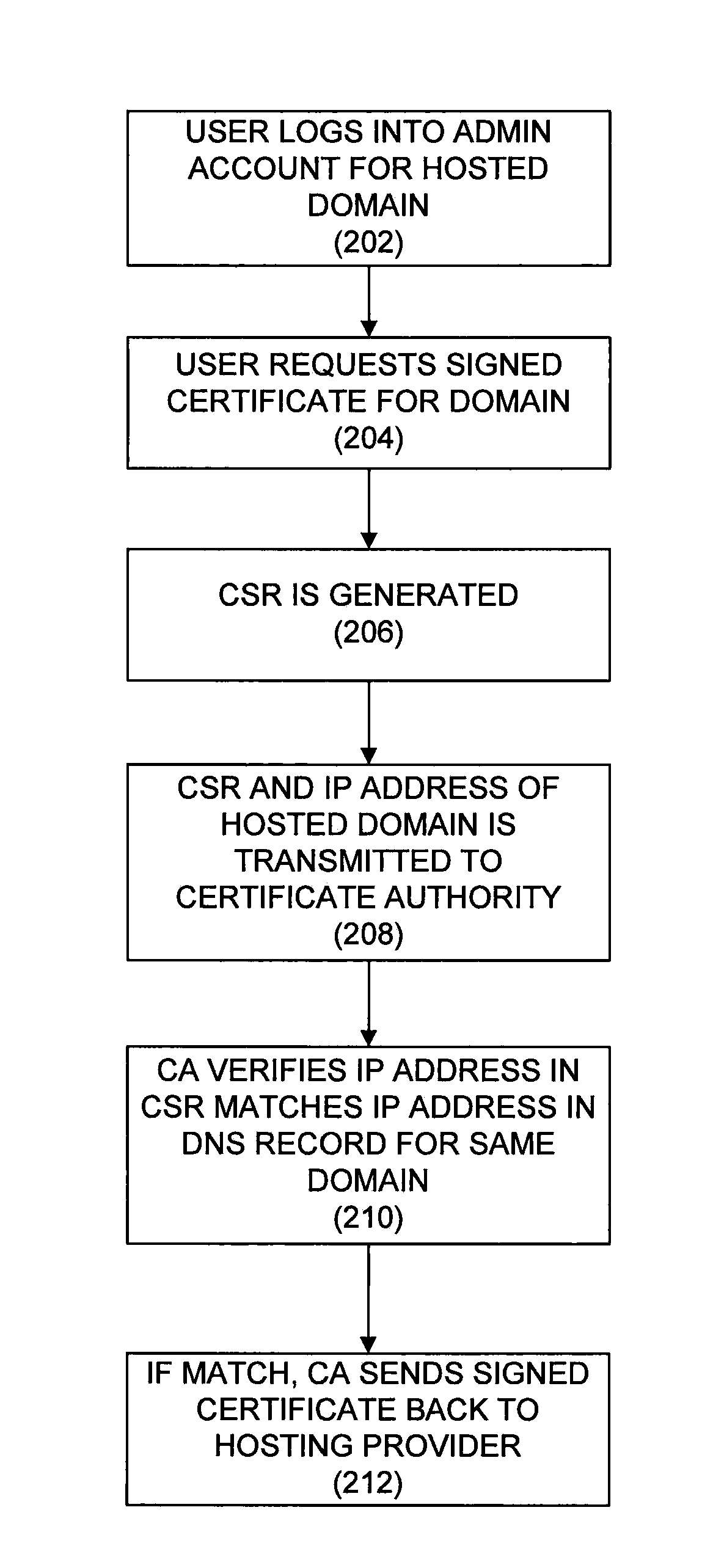
ActiveUS20140373097A1Digital data processing detailsMultiple digital computer combinationsComputer networkCertificate signing request
A system and method for domain control validation is presented. At a certificate authority a request is received. The request includes a certificate signing request and a first Internet protocol address. The certificate signing request identifies a domain and a certificate. A second Internet protocol address for the domain is retrieved from a domain name system. When the first Internet protocol address is the same as the second Internet protocol address, the certificate is signed, and the signed certificate is transmitted to a requester of the request. When the first Internet protocol address is not the same as the second Internet protocol address, the certificate signing request is rejected.
Owner:GO DADDY OPERATING
Server certificate issuing system
InactiveUS7673331B2Improve securityReduce the burden onData processing applicationsDigital data processing detailsWeb serviceCertificate signing request
A server certificate issuing system confirms existence of a Web server for which a certificate is to be issued. The web server includes means for generating an entry screen to input application matters for an issuance of a server certificate, means for generating a key pair a public key and a private key, means for generating a certificate signing request file (CSR) containing the generated public key, and means for generating a verification page indicating intention of requesting the issuance of the certificate. A registration server retrieves the CSR from a received server certificate request and accesses the Web server to read the verification information, and compares the read verification information with the CSR. If the verification information read from the Web server is identical to the CSR, it is determined that the Web server for which the server certificate is to be issued exists.
Owner:GLOBALSIGN
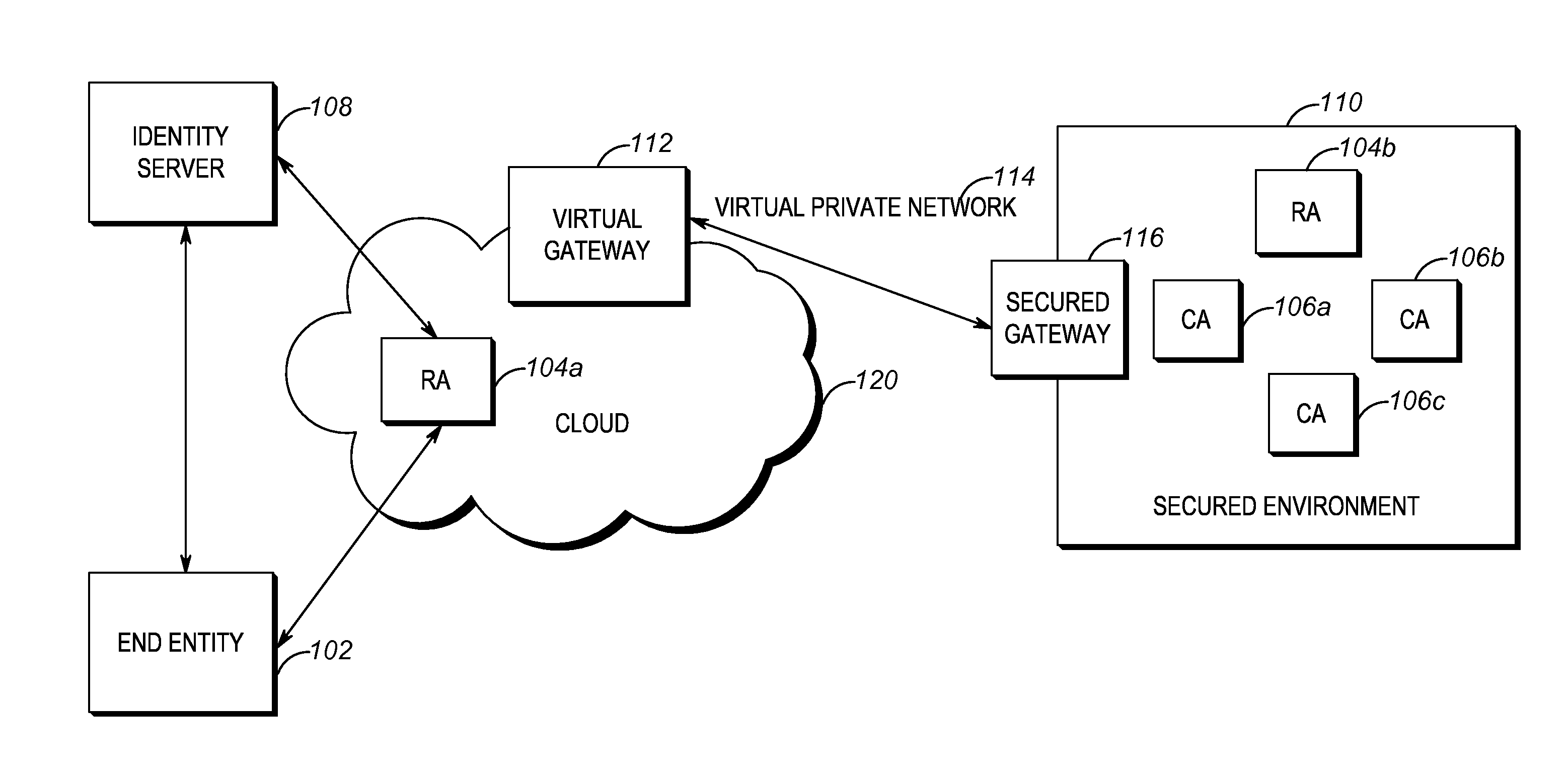
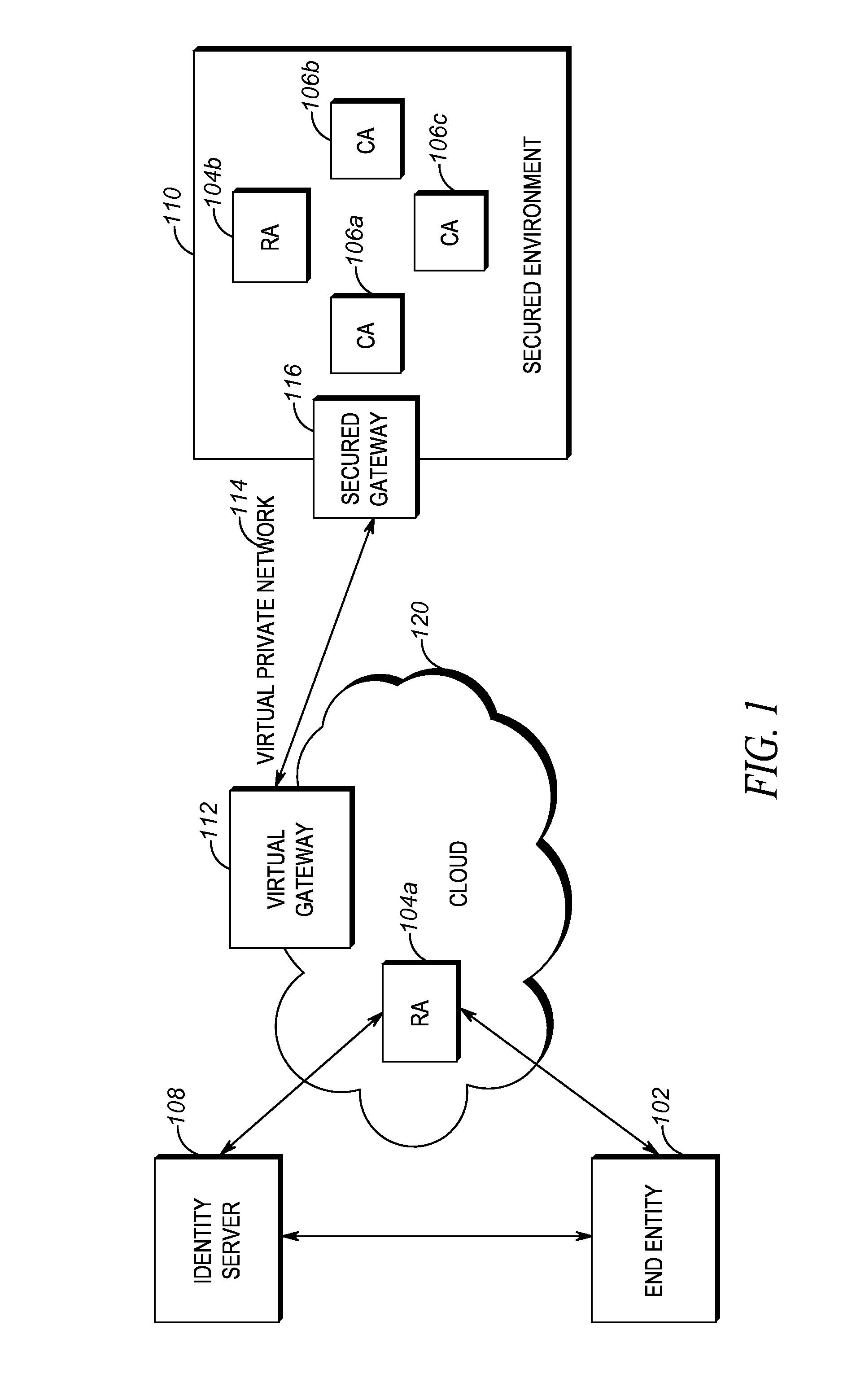
Method and apparatus for enabling secured certificate enrollment in a hybrid cloud public key infrastructure
InactiveUS20160127353A1Public key infrastructure trust modelsCertificate signing requestStatus changed
In a method a public key infrastructure (PKI) device receives a certificate signing request (CSR) and an identity assertion cryptographically bound to an end entity issuing the CSR. The PKI device validates the authenticity and integrity of the CSR using the identity assertion. In response to validating the authenticity and integrity of the CSR, the PKI device issues a certificate based on at least one of the CSR and fields in the identity assertion.
Owner:MOTOROLA SOLUTIONS INC
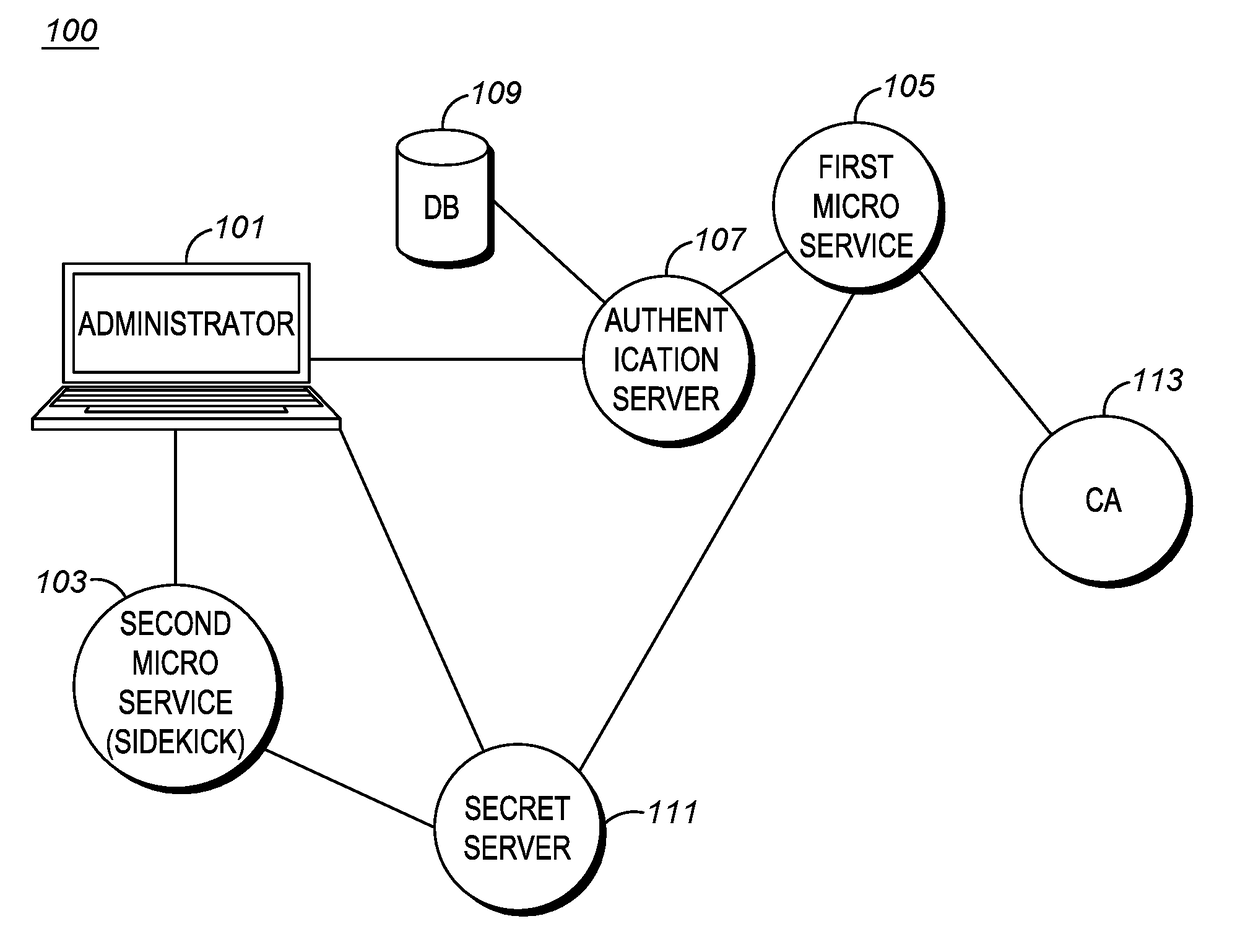
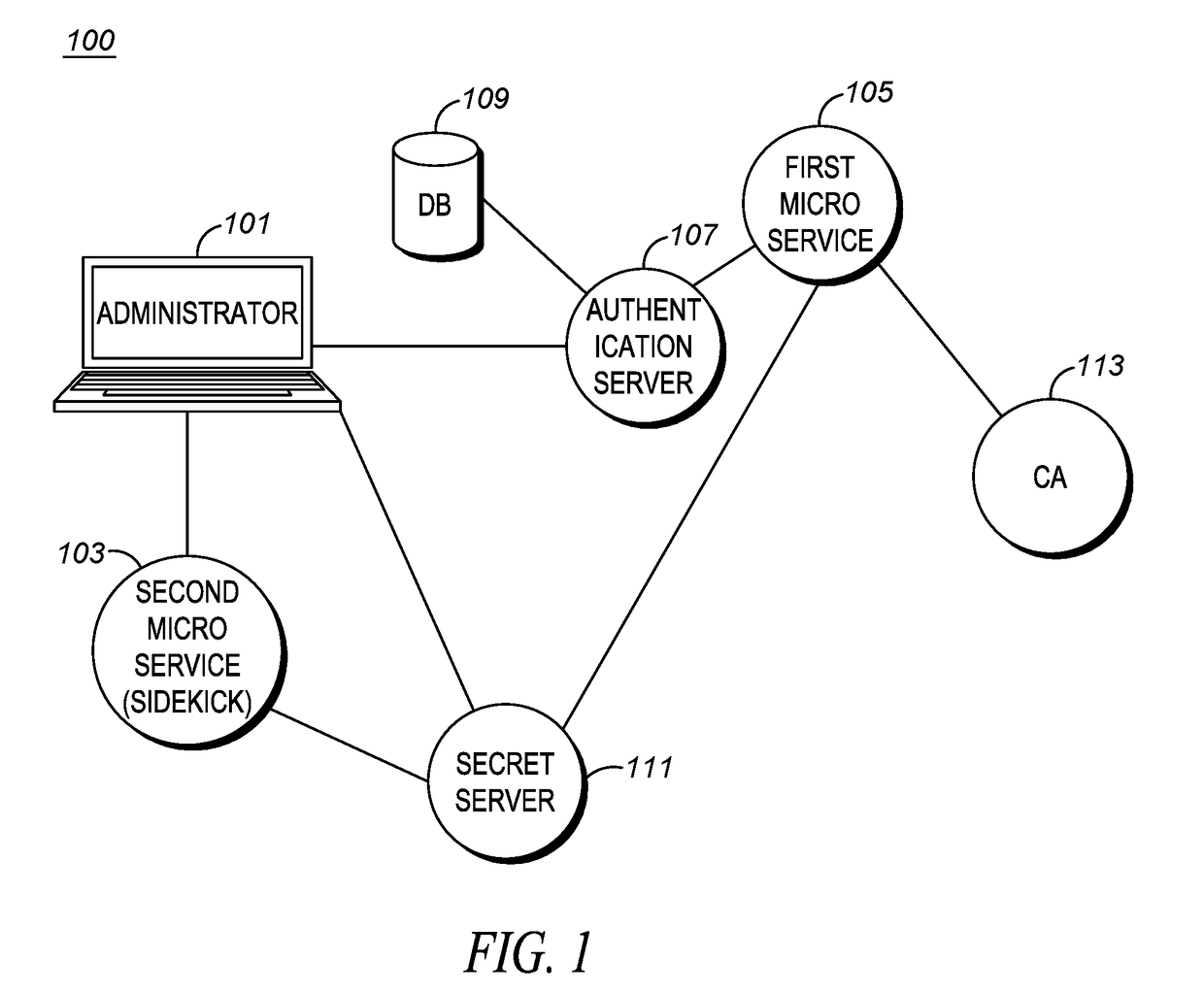
Method for obtaining vetted certificates by microservices in elastic cloud environments
ActiveUS20180048638A1Multiprogramming arrangementsPlatform integrity maintainanceElastic cloudCertificate signing request
A method and is provided for obtaining a vetted certificate for a microservice in an elastic cloud environment. The microservice receives a one-time authentication credential. The microservice utilizes the one-time authentication credential to obtain a client secret. The microservice obtains an access token and CSR (Certificate Signing Request) attributes using the client secret and constructs a CSR utilizing the CSR attributes. The microservice requests a vetted certificate from a Certificate Authority (CA) and includes the access token and the CSR in the request. If the access token and the CSR pass vetting at the CA, the CA sends a vetted certificate to the microservice.
Owner:MOTOROLA SOLUTIONS INC
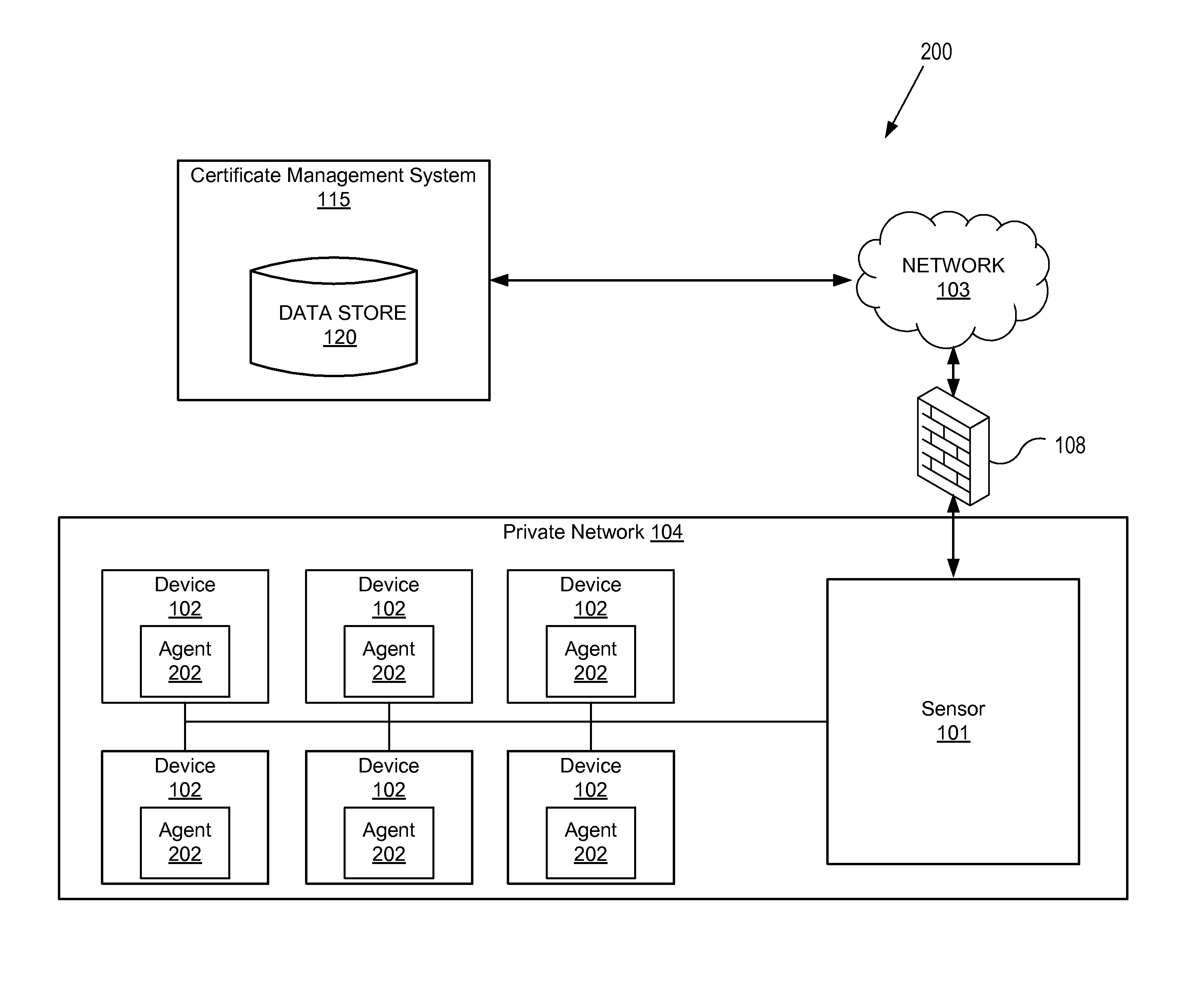
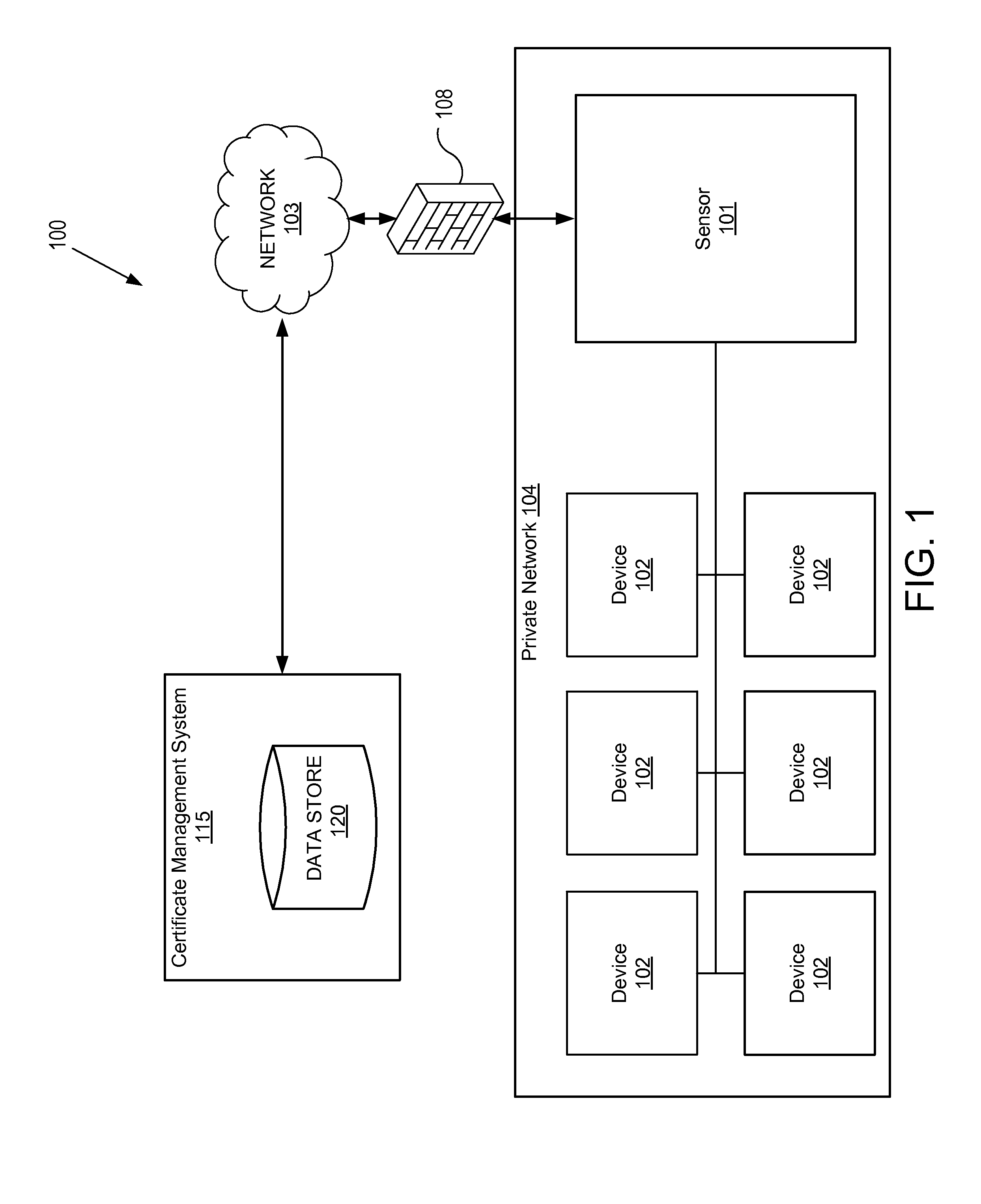
Automatic configuration and provisioning of SSL server certificates
ActiveUS8707027B1User identity/authority verificationSecret communicationCertificate signing requestManagement system
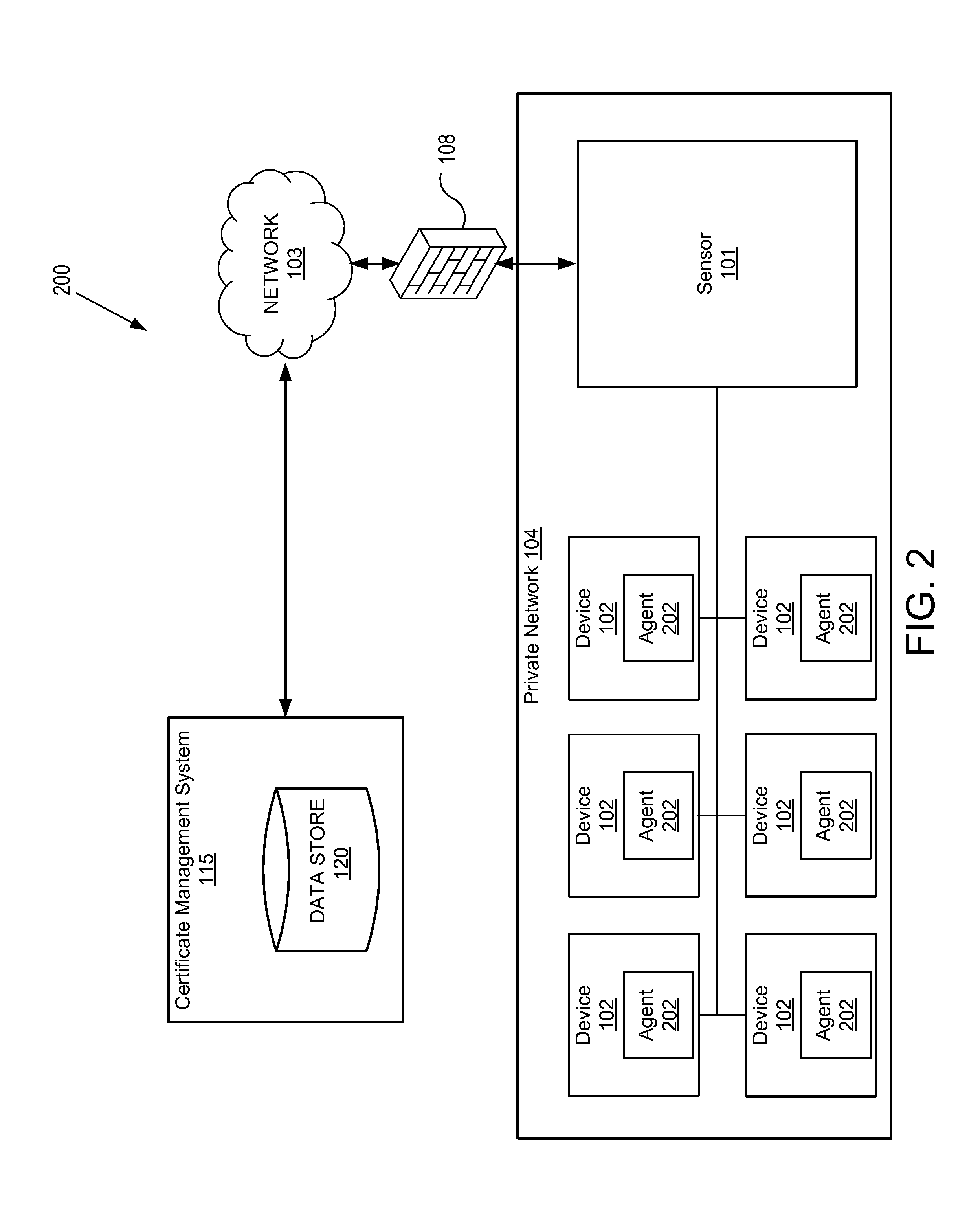
A method and apparatus for automatically configuring and provisioning cryptographic certificates is described. A certificate management sensor receives instructions from a first computing device to analyze a second computing device to identify an application on the second computing device associated with cryptographic network traffic on the second computing device, generates an application fingerprint based on application characteristics of the application, transmits the application fingerprint and a certificate signing request (CSR) to a certificate management system (CMS), and receives second instructions from the CMS to automatically install a cryptographic certificate on the second computing device based on the application fingerprint and CSR.
Owner:DIGICERT
Authentication process for issuing sequence of short-lived digital certificates
ActiveUS10277406B1Key distribution for secure communicationPublic key for secure communicationCertificate signing requestAuthentication protocol
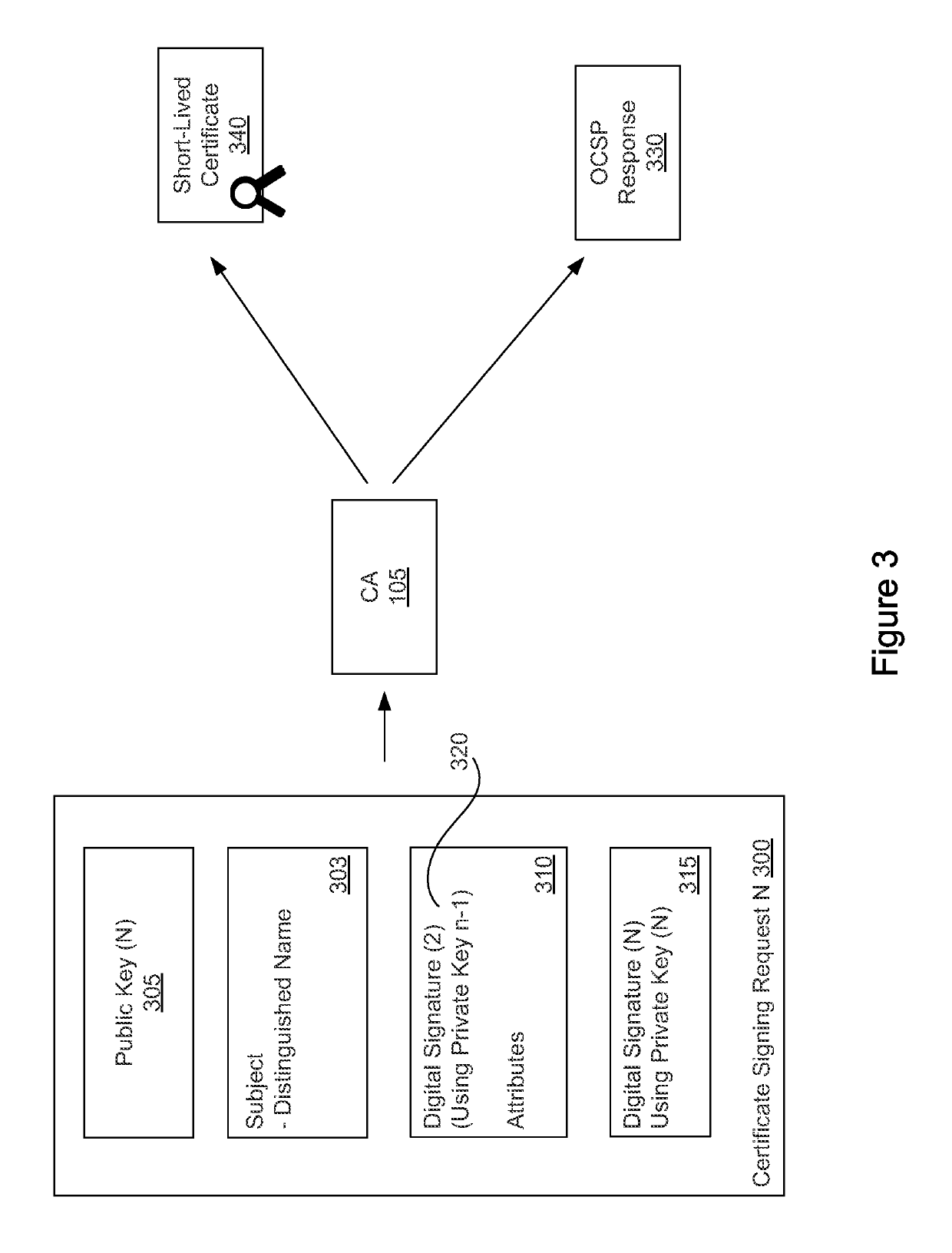
Embodiments presented herein provide techniques for managing a digital certificate enrollment process. In particular, embodiments presented herein provide techniques for a certificate authority to issue short-lived SSL certificates and an authentication method for validating certificate signing requests (CSR) for short-lived certificates.
Owner:DIGICERT
Compliance assessment reporting service
Disclosed herein is a method for providing assurance information regarding a business entity to a customer for an electronic transaction. The method comprises submitting a compliance token to a certificate authority as part of a certificate signing request wherein the compliance token comprises an assessment result describing the business entity's level of compliance with an assurance policy, as determined by an assessor, receiving an assurance certificate from the certificate authority, wherein the certificate includes the compliance token, and providing the assurance certificate to a customer in order to provide security information to the customer as part of an electronic transaction.
Owner:VISA USA INC (US)
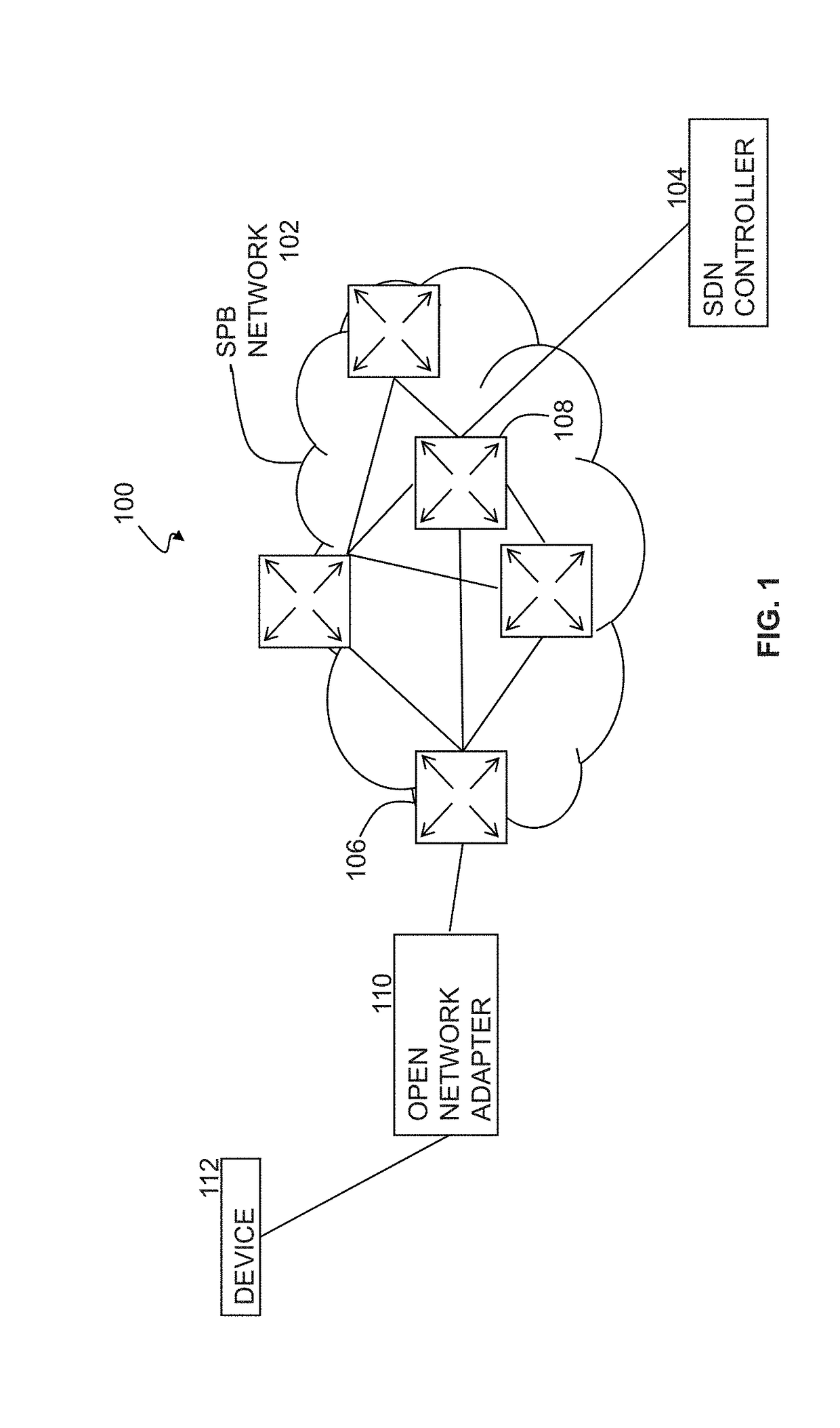
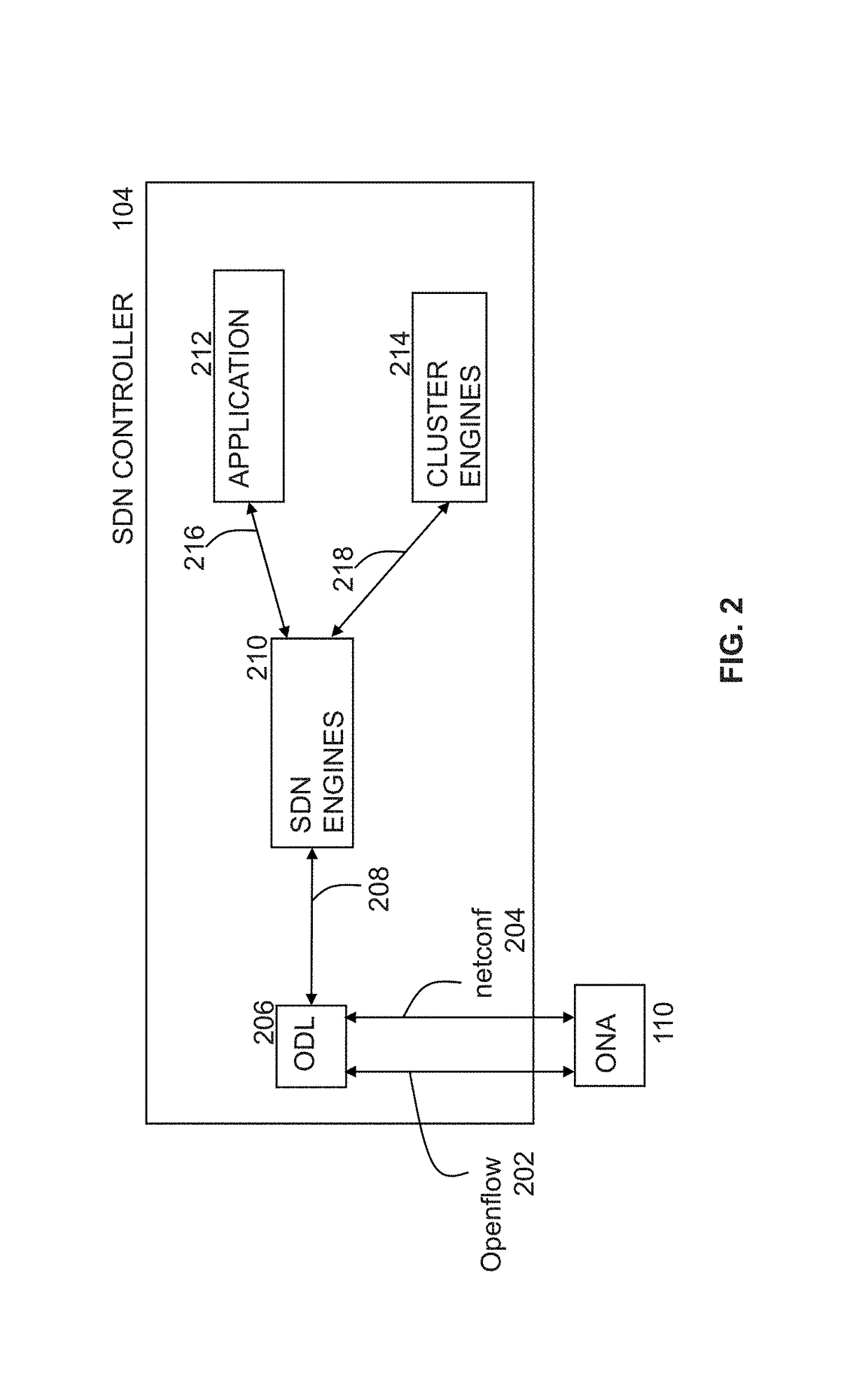
Customer-centric Workflow for Initial On-boarding of an Openflow Enabled Switch
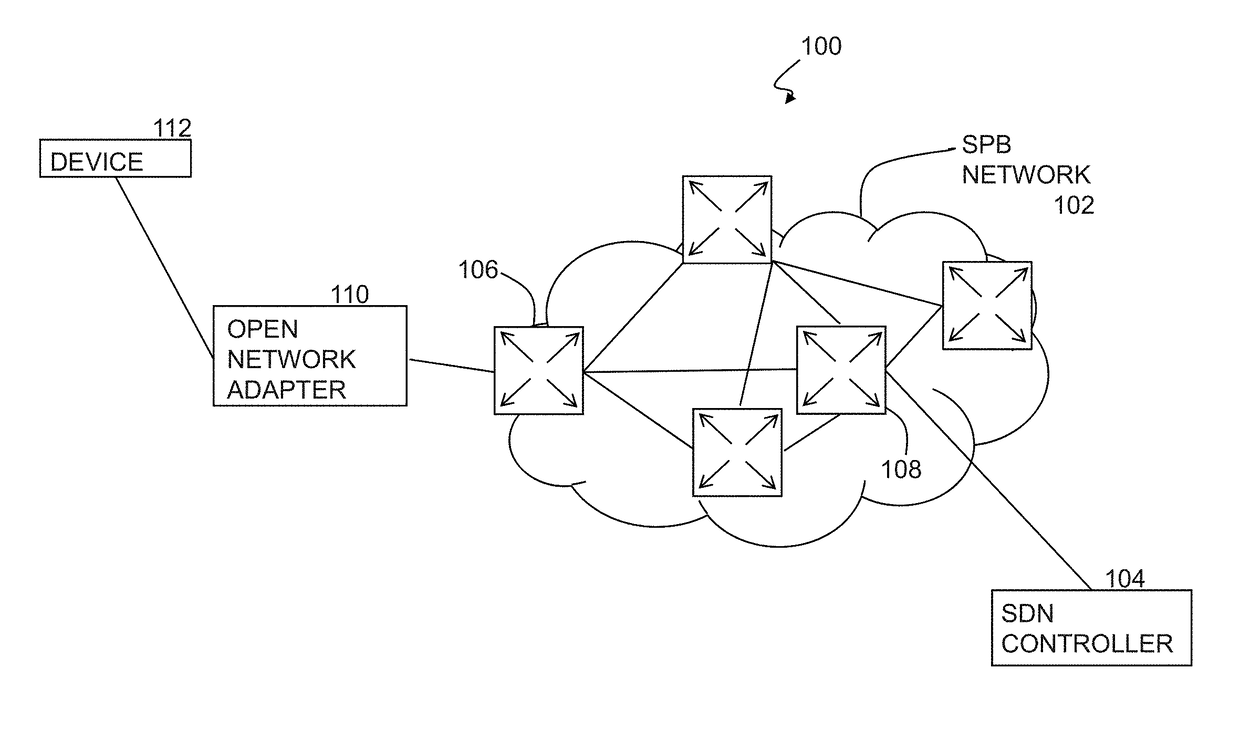
ActiveUS20170339144A1Coding/ciphering apparatusPublic key infrastructure trust modelsCertificate signing requestOpenFlow
Authenticating a networking appliance attempting to attach to a network includes receiving at least one value associated with an identity of the networking appliance; receiving a certificate signing request (CSR) from the networking appliance, wherein the CSR comprises credential data associated with the identity of the networking appliance; and generating an appliance certificate based on the credential data and a certificate authority (CA) certificate associated with the computer. The method also includes returning the appliance certificate to the networking appliance; receiving a request from the networking appliance to attach to the network; and authenticating the identity of the networking appliance based on both a) the at least one value associated with the identity of the networking appliance; and b) the appliance certificate.
Owner:AVAYA INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com