Patents
Literature
215results about How to "Valid verification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
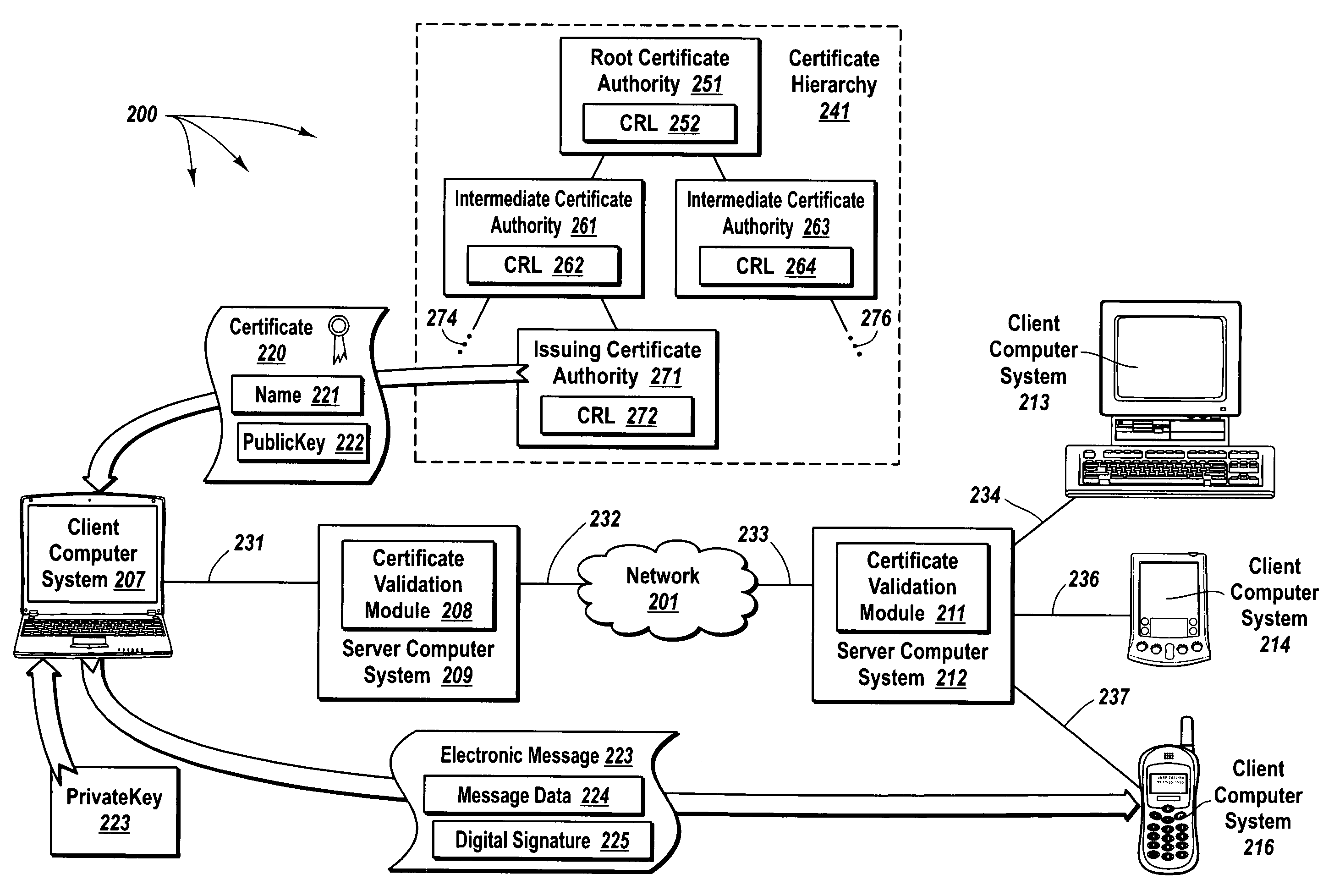
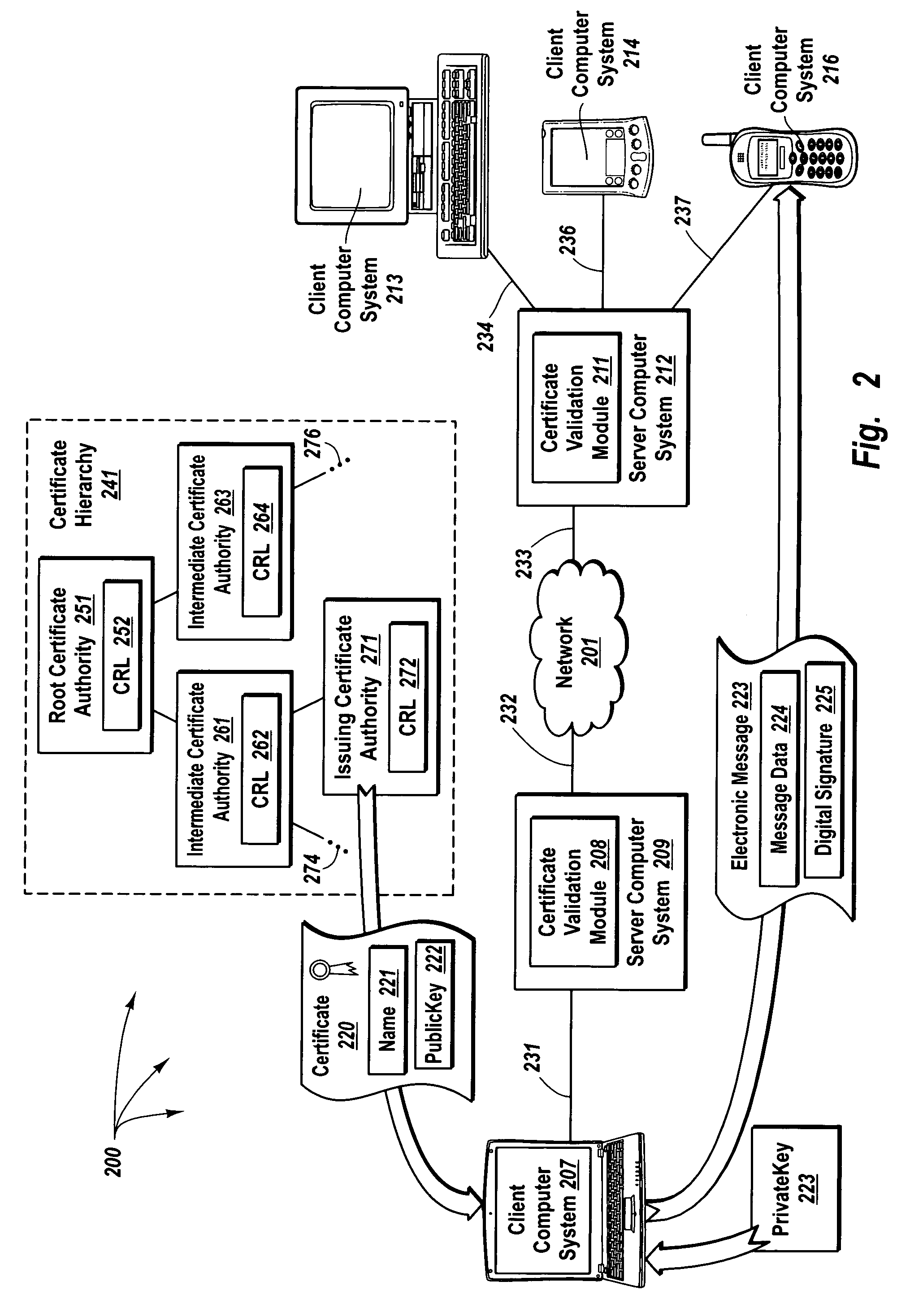
Delegating certificate validation
ActiveUS20050021969A1Efficiently validateValid verificationUser identity/authority verificationClient-sideComputer security
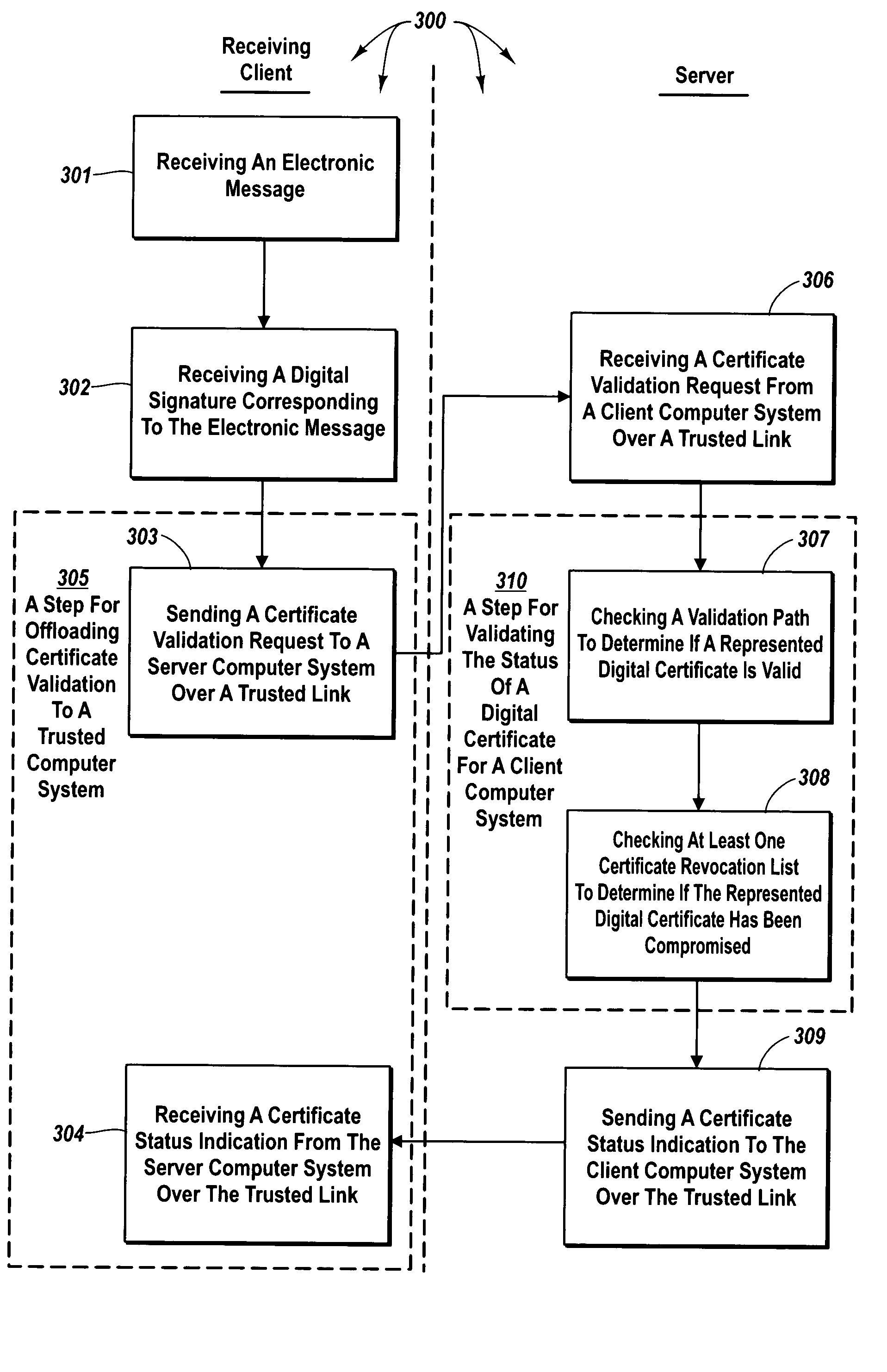
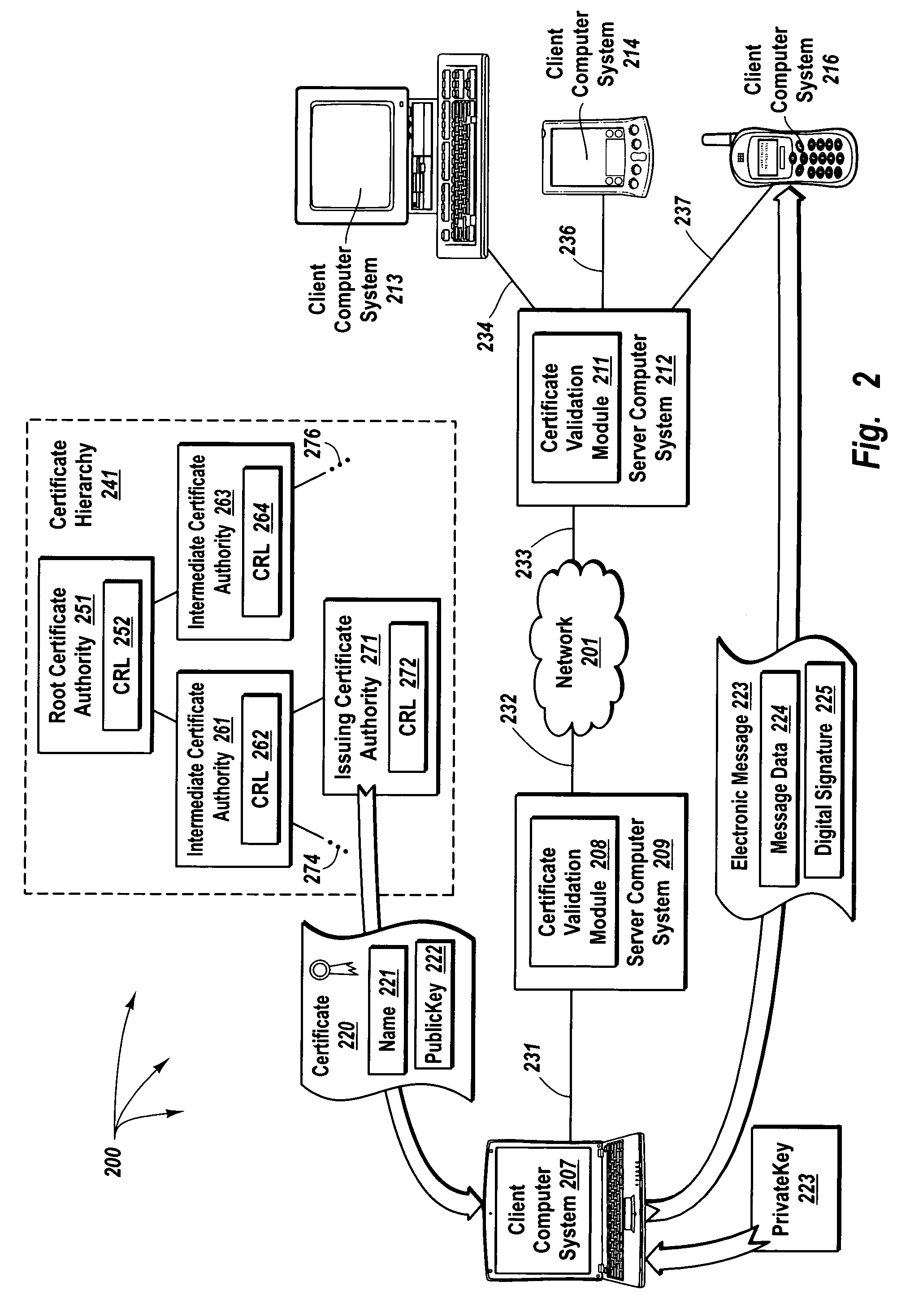
The principles of the present invention provide for delegating certificate validation. A client computer system sends a certificate validation request to a server computer system over a trusted link. The certificate validation request includes at least enough certificate information for a certificate authority to identify a digital certificate that binds a sending entity to a private key. The server computer system checks a validation path to determine if the digital certificate is valid and at least one certificate revocation list to determine if the certificate has been compromised. The server computer system sends a certificate status indication to the client computer system over the trusted link. Accordingly, the resources of the server computer system, instead of the client computer system, are utilized to validate a digital certificate. Further, digital certificate validation can be delegated to a server computer system that attempts to pre-validate a digital certificate.
Owner:MICROSOFT TECH LICENSING LLC
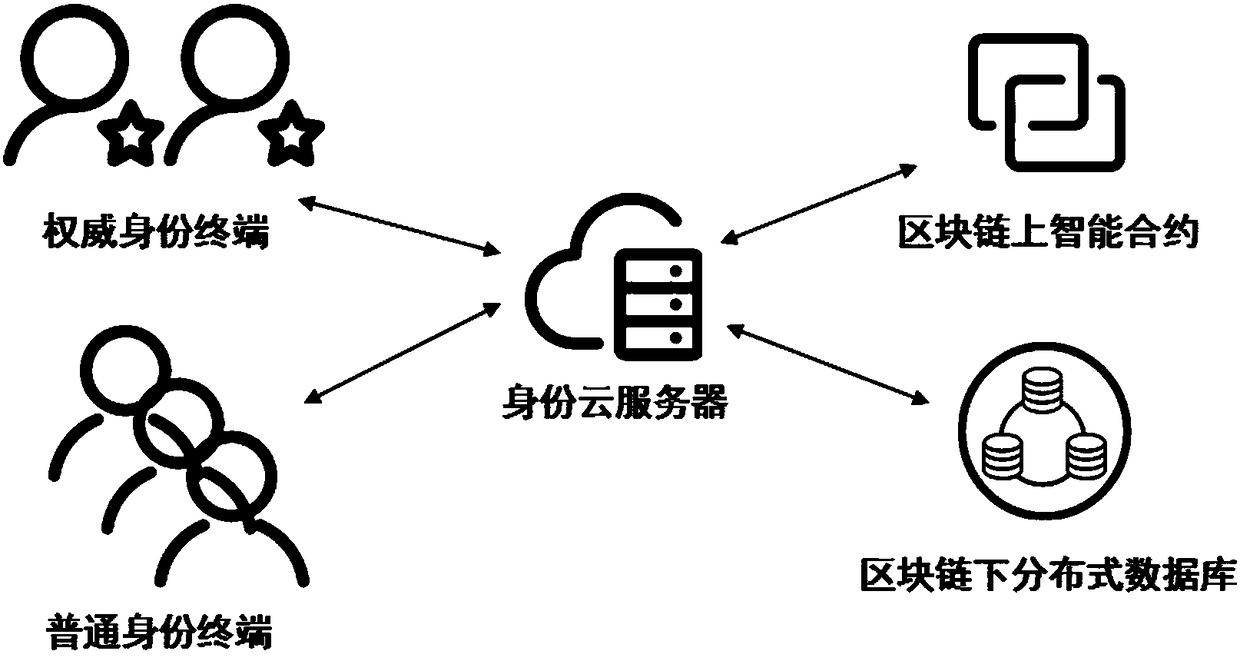
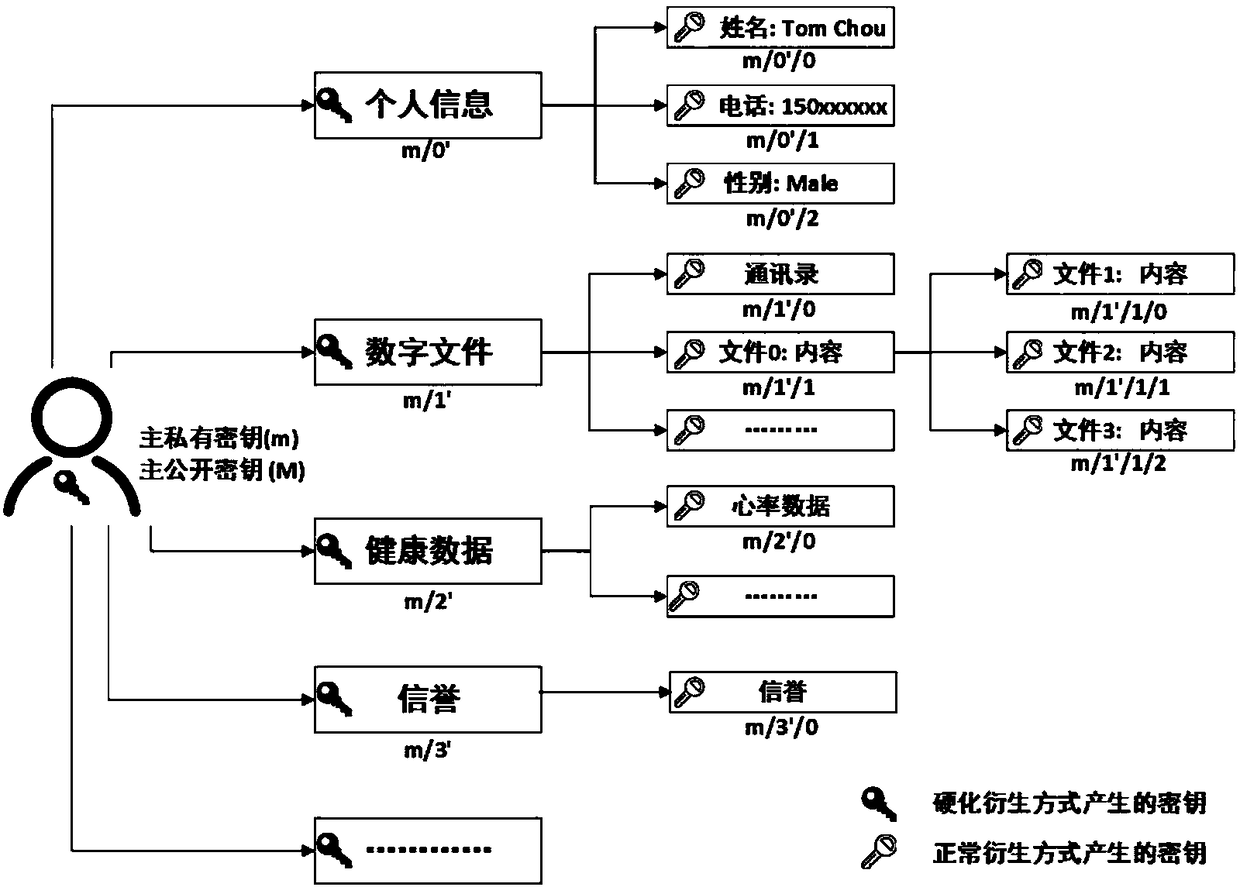
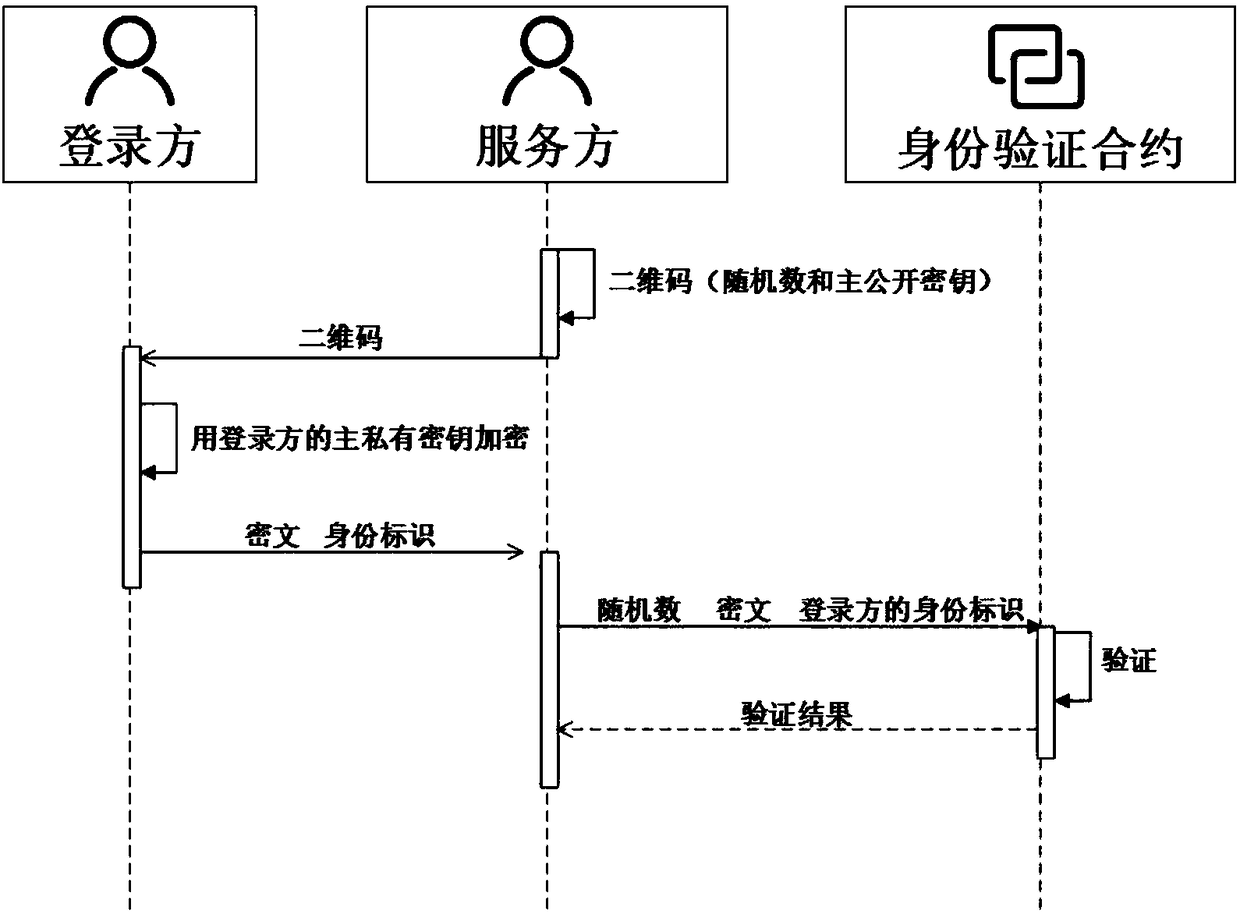
Self-certified digital identity management system and method based on smart contract
ActiveCN108234515AImplement passwordless loginMaster self-managementUser identity/authority verificationDigital identitySelf certified
The invention discloses a self-certified digital identity management system and method based on a smart contract. An identity terminal sends a public key and associated digital information to a cloudserver via the Internet, and accomplishes registration and login of digital identity, and the authorization, operation and verification of digital information depending on the smart contract on a block chain and a distributed database under the block chain. A unique identity of the whole network can be provided, passwordless login is achieved by scanning a two-dimensional code, the login mode of the traditional username and password is broken through, and a user entirety can securely and effectively manage the digital identity and the associated digital information, on-demand authorization, operation and verification of information are achieved, thus realizing a decentralized, self-certified digital identity management system.
Owner:安徽中科晶格技术有限公司
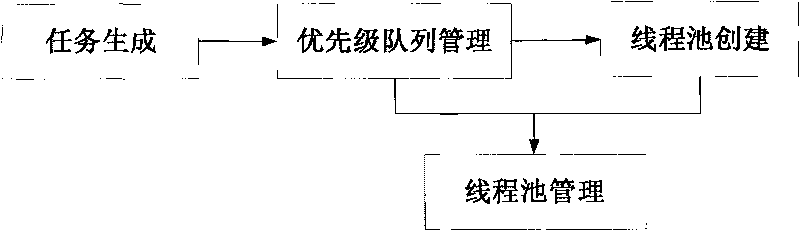
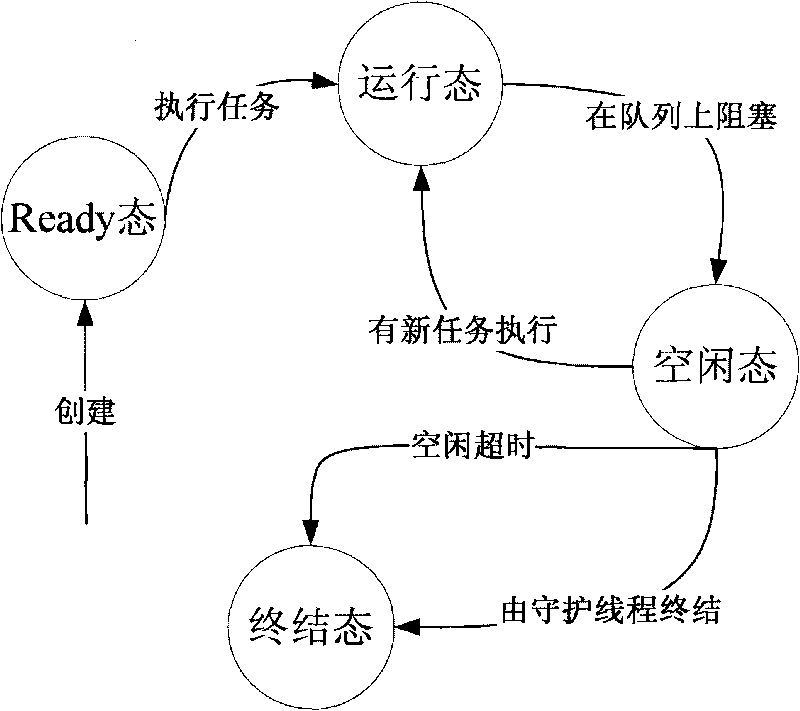
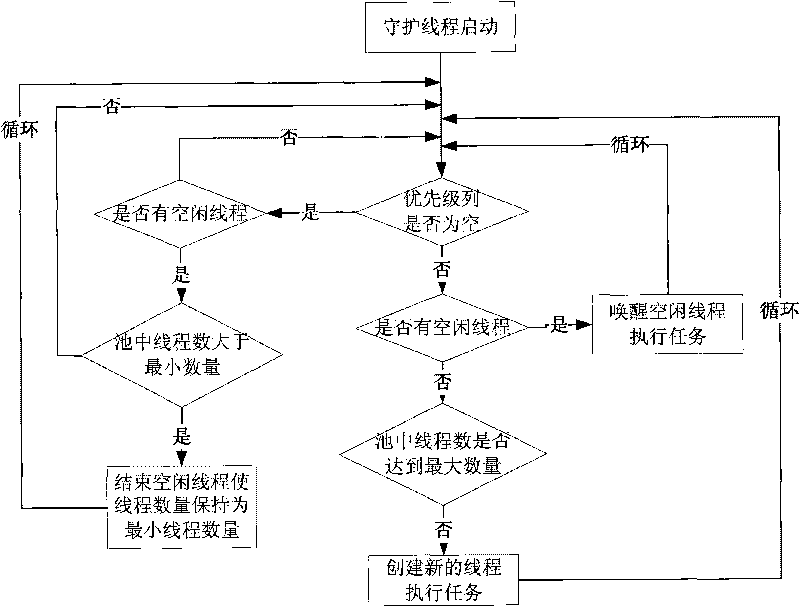
Method for scheduling satellite data product production tasks in parallel based on multithread
ActiveCN101739293ASolve scheduling problemsIncrease the number of tasksResource allocationSatellite dataIdle time
The invention discloses a method for scheduling satellite data product production tasks in parallel based on multithread. The method comprises the following steps: setting priorities for tasks to be scheduled for executing and realizing a uniformed interface; adding the tasks into a priority queue according to an order of the priorities from high to low; setting the maximum number and the minimal number of the tasks of a thread pool, and the longest idle time of a thread; and starting a daemon thread in the thread pool and a plurality of task threads to execute the tasks, wherein the daemon thread regulates the number of the task threads dynamically according to the situation of task amount. The method can utilize system resource rationally, aims at the data product production of a satellite ground application system, and solves the difficult points of complicated product production processes, long task executing time, large task amount, high real time and parallelism degree for scheduling the tasks and the like.
Owner:SPACE STAR TECH CO LTD
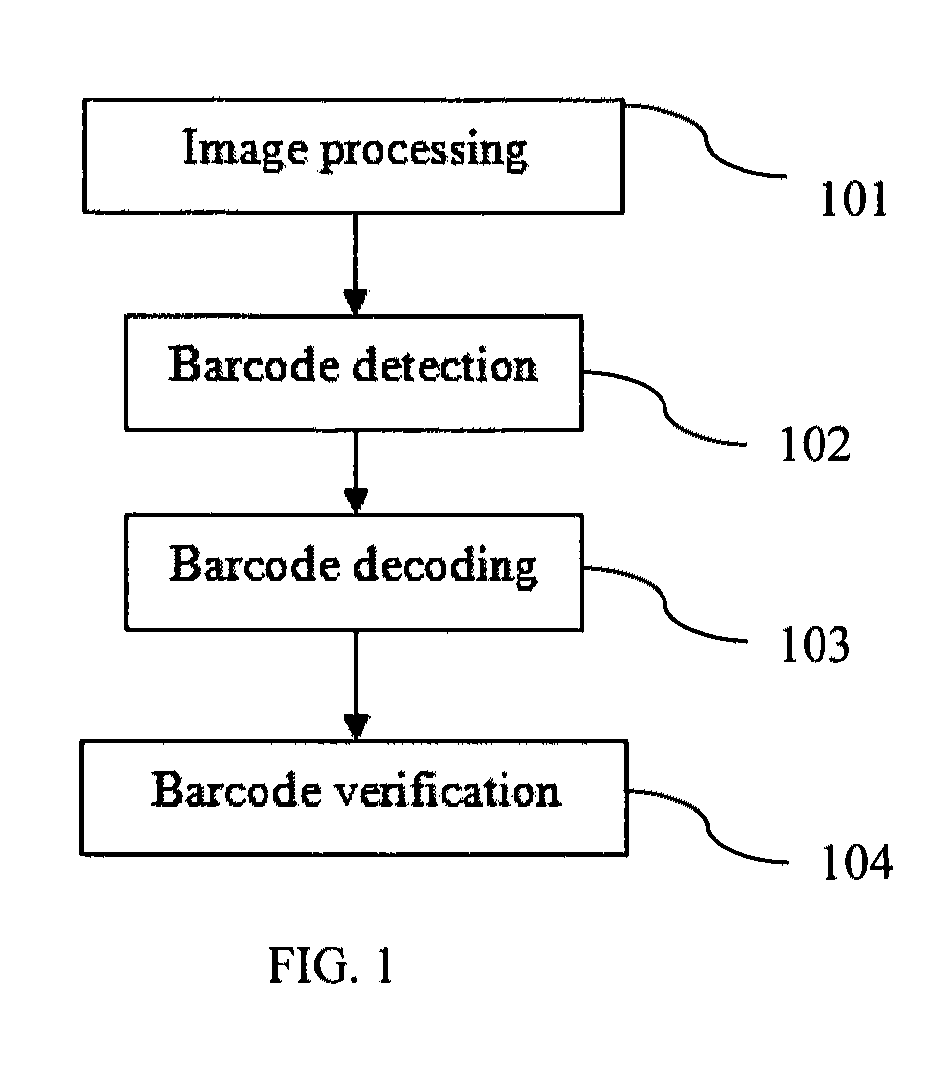
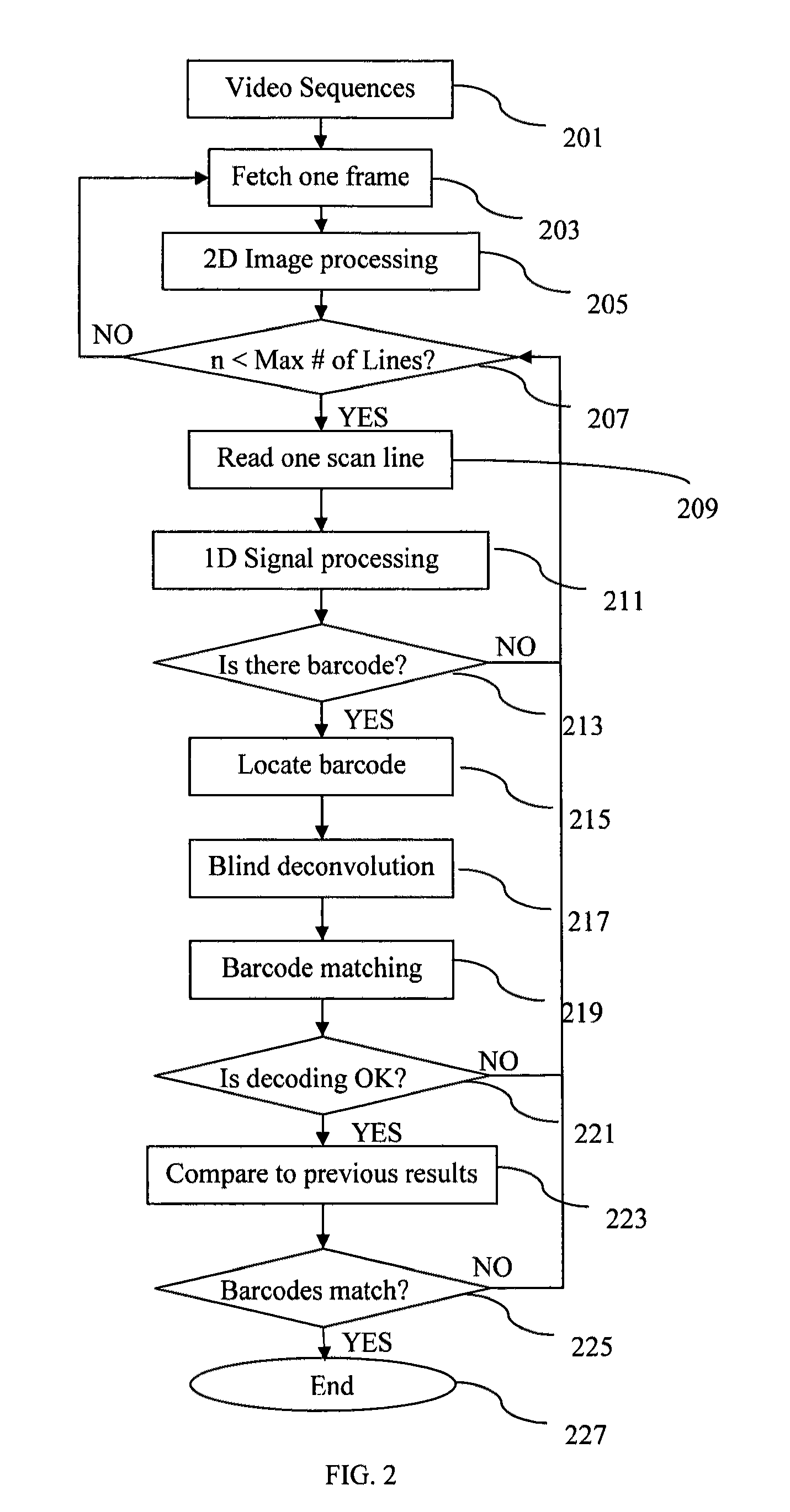
Real-time barcode recognition using general cameras
ActiveUS20120091204A1Reduce computing costEasy to measureSensing record carriersVerifying markings correctnessPattern recognitionPoint spread
A method, apparatus, and system for decoding and recognizing barcode information by using a general camera such as one in a mobile device is disclosed. The invention uses a set of compact point spread functions (PSF) with a squared-shape distribution to restore blurred barcode image for quick and efficient decoding and recognition. Image pre-processing methods are applied to reduce noise and normalize pixel grayscale. On each normalized image, the invention checks if the image contains barcode lines. If there is a barcode, the invention tries to identify the beginning and ending positions of the barcode. The invention selectively decodes multiple scan lines across the barcode and match against predefined barcode models. The best matched barcodes are saved in the history buffer.
Owner:SHI JIAZHENG +1
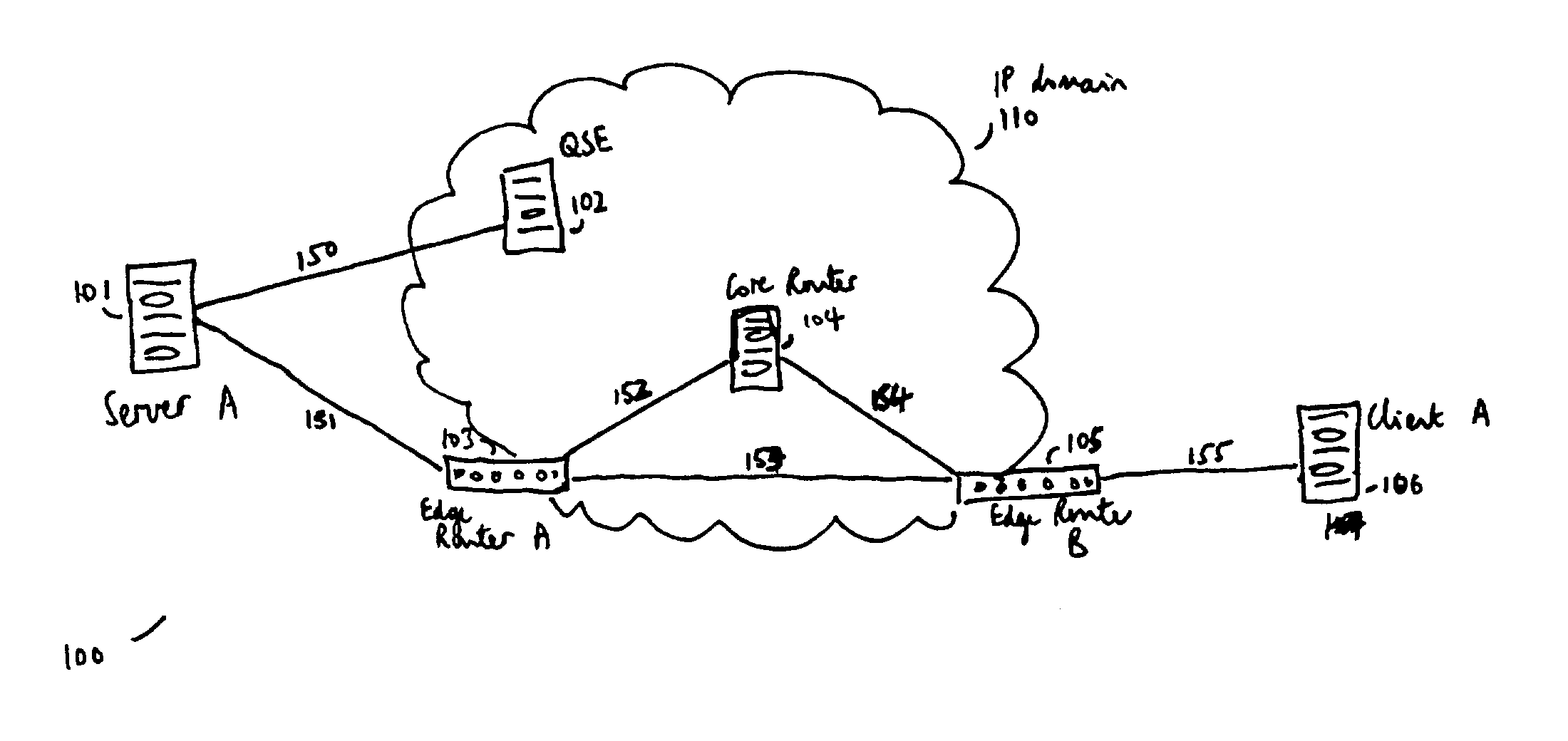
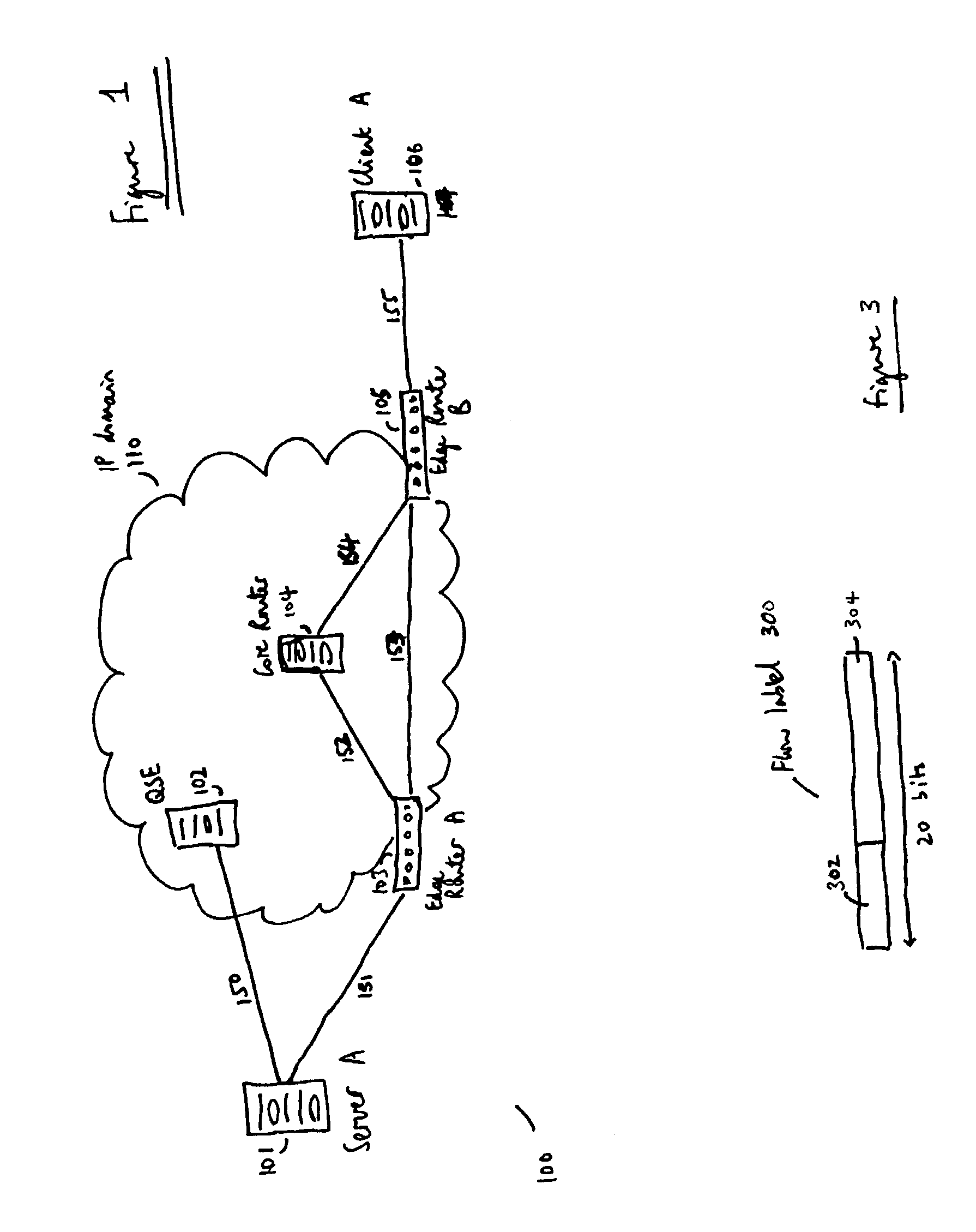
Flow labels
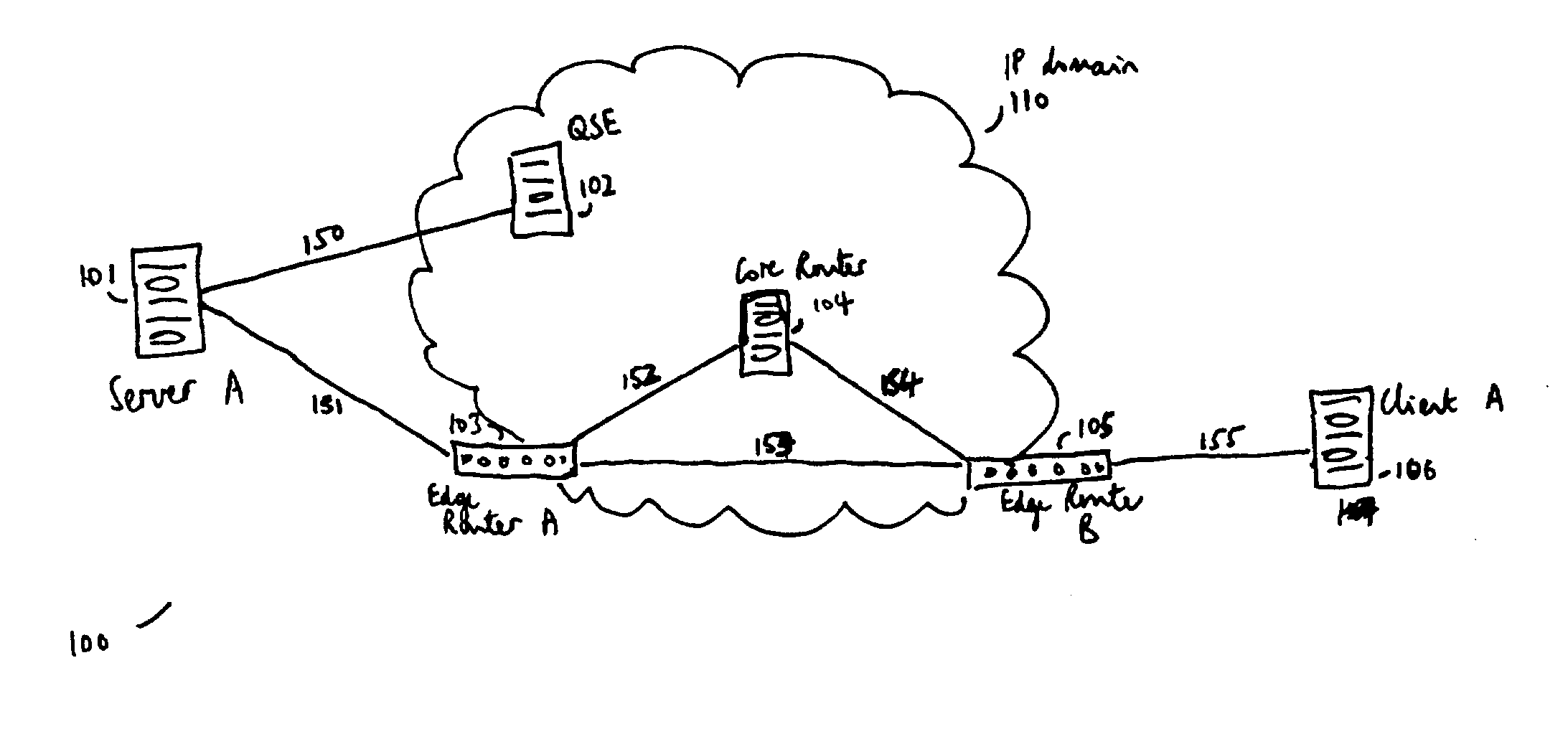
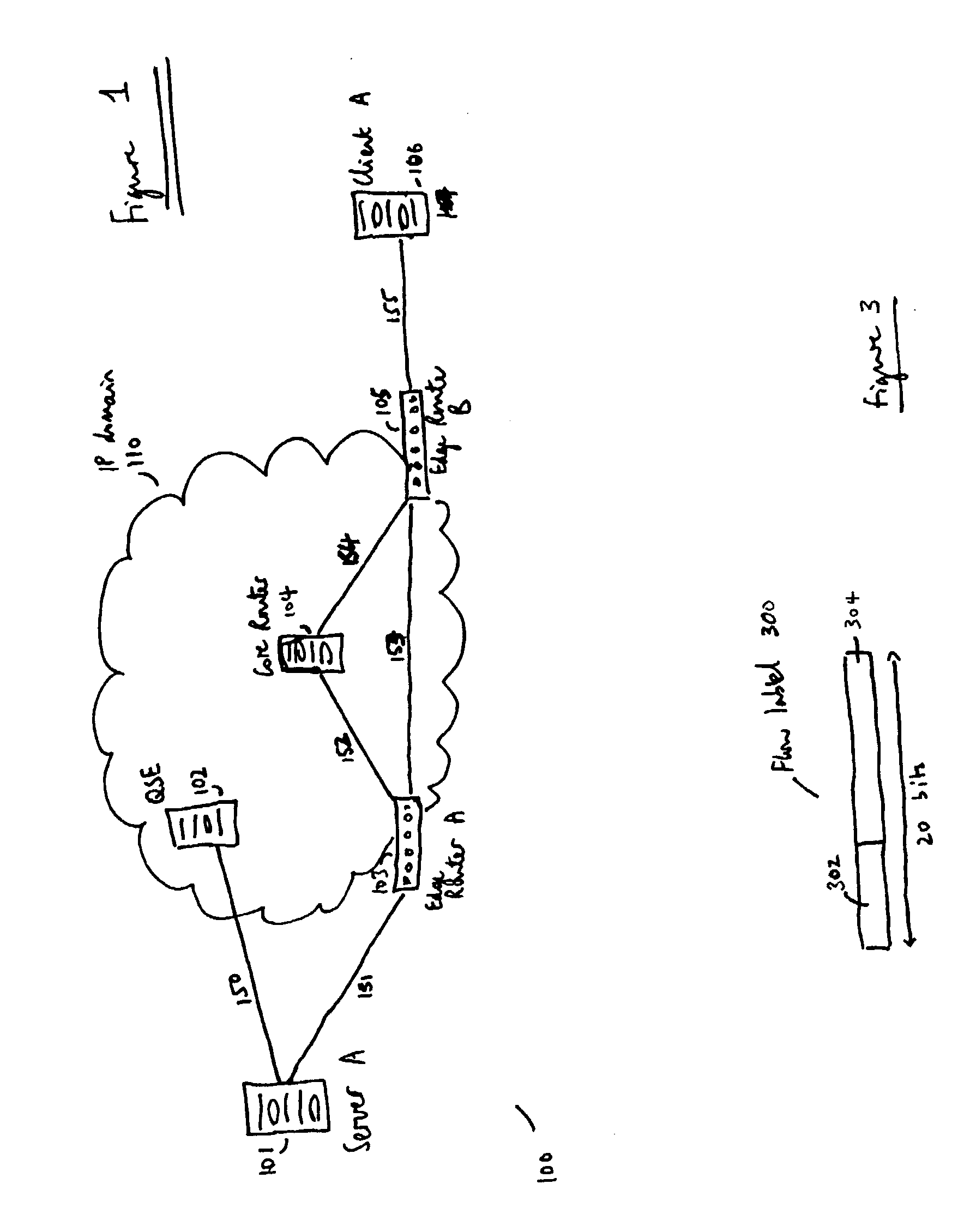
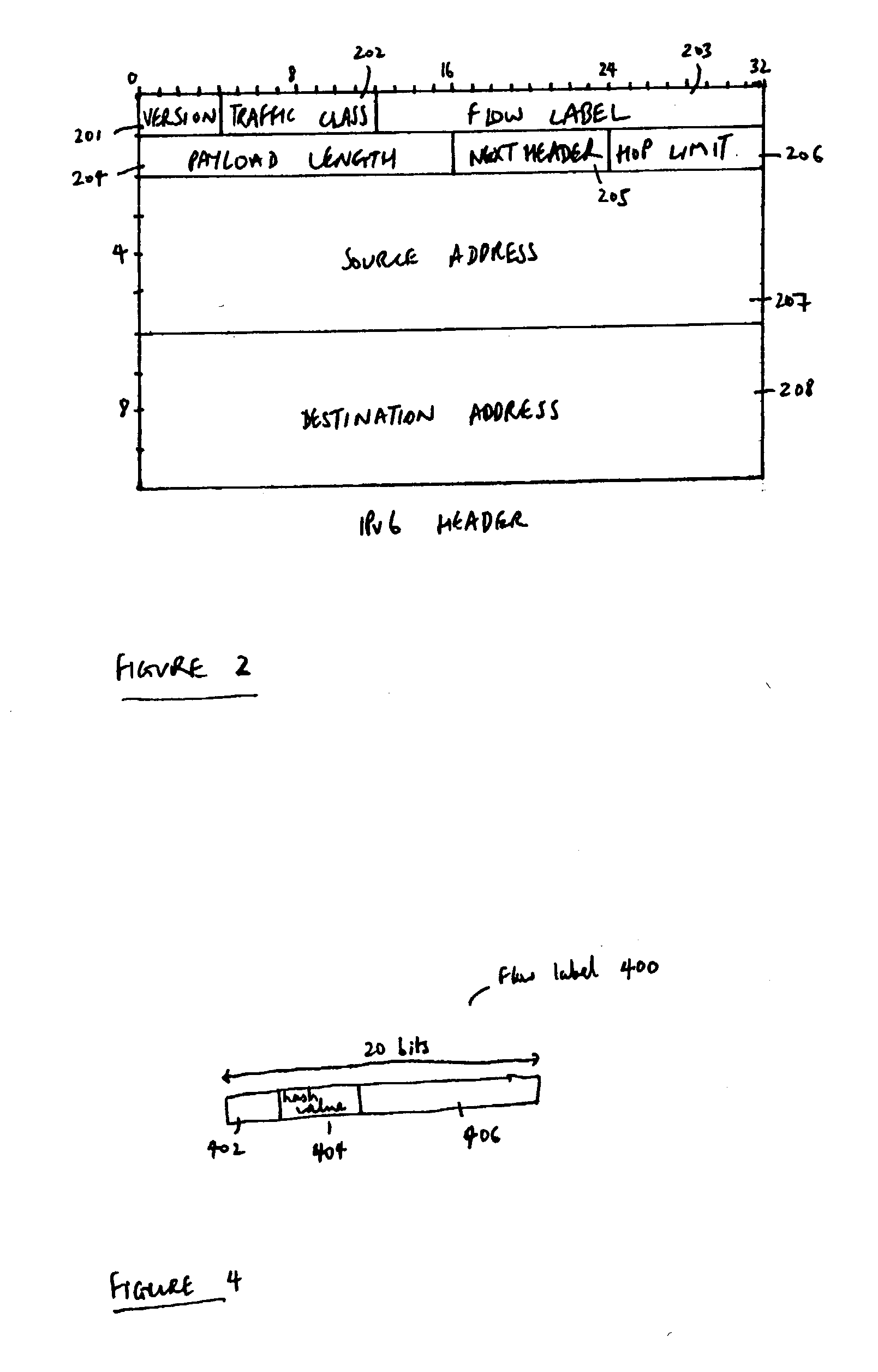
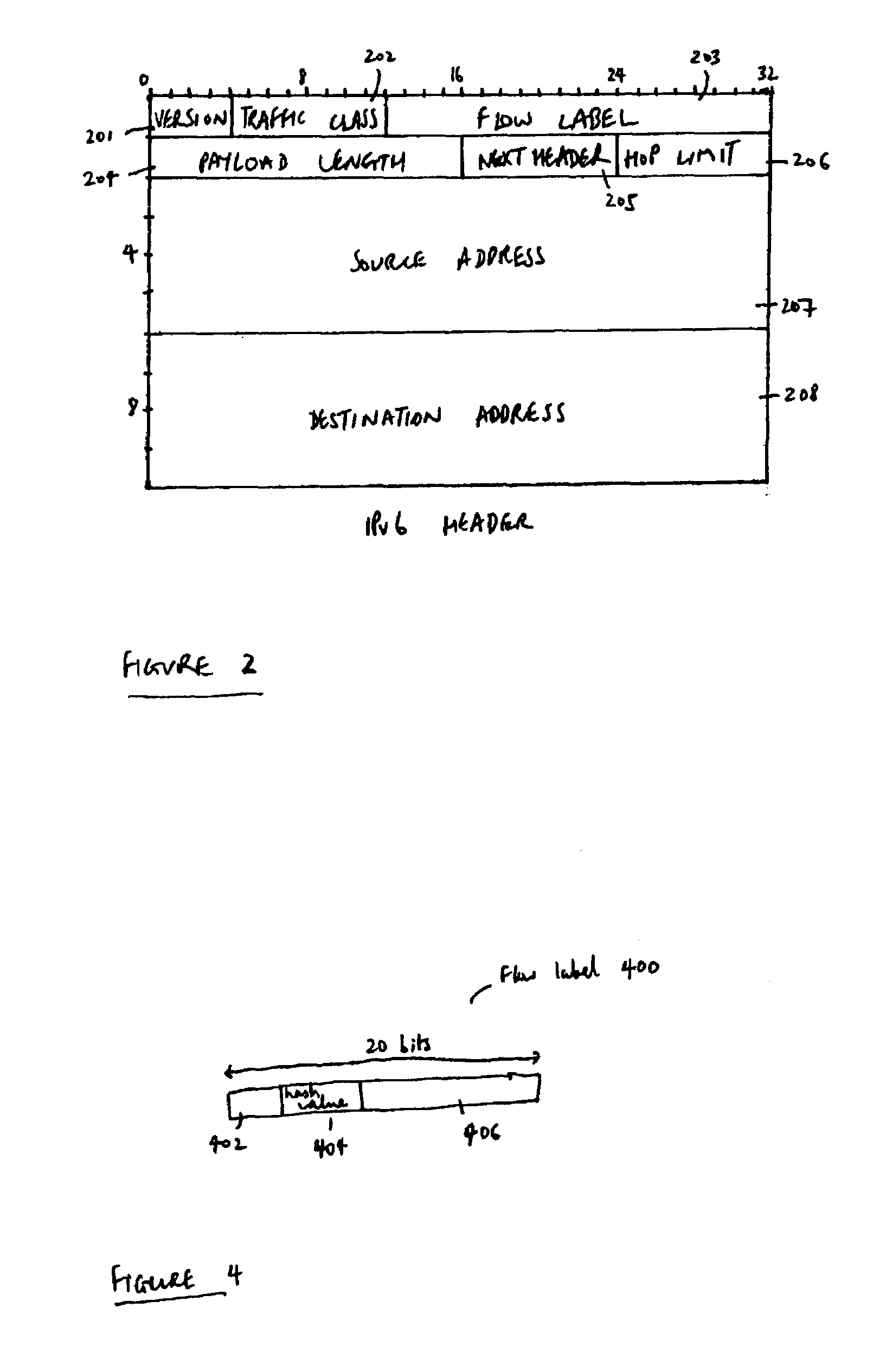
ActiveUS20040125797A1Easy to useValid verificationData switching by path configurationNetwork data managementQuality of serviceData stream
There is disclosed a system for monitoring a packet data flow, comprising: a data flow source element including: determining means adapted to determine a quality of service identifier for the data flow; first generating means adapted to generate an encoded value in dependence on the quality of service identifier; allocating means adapted to allocate the quality of service identifier and the encoded value to the flow label for each data packet of the data flow; and transmitting means for forwarding data packets including flow labels to a routing domain; and a routing domain interface element including: receiving means for receiving data packets from the data flow source; second generating means adapted to generate a further encoded value in dependence on the quality of service identifier in a flow label of a data packet; comparing means adapted to compare the further encoded value to the encoded value in the flow label; and routing means adapted to selectively route the data packets in dependence on the comparing step.
Owner:MIND FUSION LLC
Energy perception routing algorithm used for wireless sensing network
InactiveCN102149160ASolve the problem of "resource blind spot"Solve the "resource blind spot" problemNetwork topologiesHigh level techniquesRest energyWireless mesh network
The invention relates to an energy perception routing algorithm used for a wireless sensing network, which comprises the steps as follows: 1, a two-tier clustering mechanism based on a cellular network structure is realized for a wireless sensing network; 2, cluster heads are dynamically selected according to the rest energy of nodes and the central distance from the nodes to a cell to form a backbone network which processes and forwards data, wherein the nodes not serving as the cluster headers and not implementing data transmission enter a dormant state; and the nodes serving as the cluster headers manage the nodes in the clusters; and 3, a limited flooding mechanism is used for establishing routing taking a convergent node as a final target node; a routing table is established between the cluster headers according to the minimum path overhead between the clusters and the rest energy of the cluster headers; and optimal routing can be established for the nodes in the whole wireless sensing network only through one broadcasting by reasonably adjusting the parameters. The energy perception routing algorithm used for the wireless sensing network can improve the lifecycle of the whole wireless sensing network, thus satisfying the application of the wireless sensing networks sensitive to energy.
Owner:NINGBO POLYTECHNIC
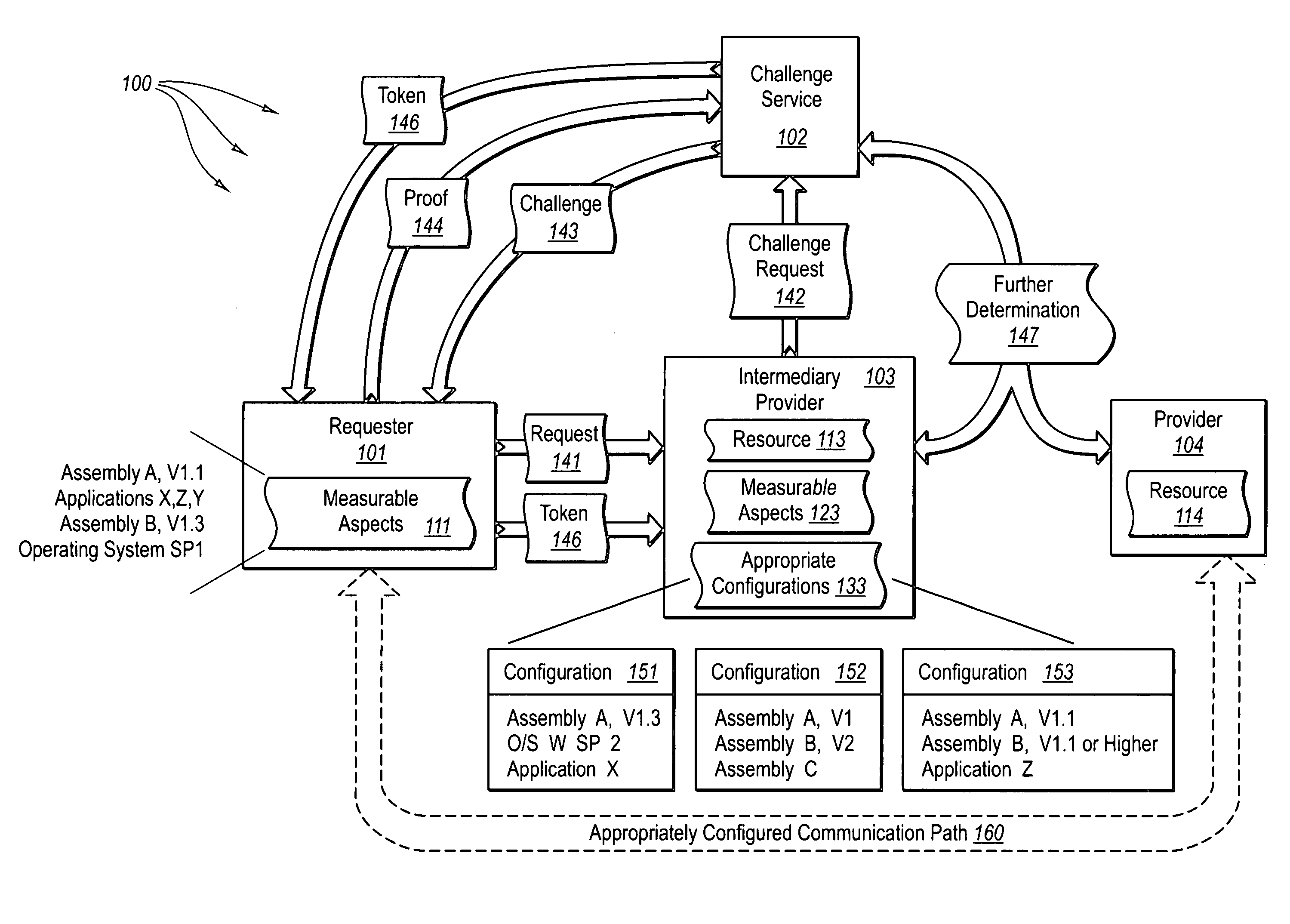
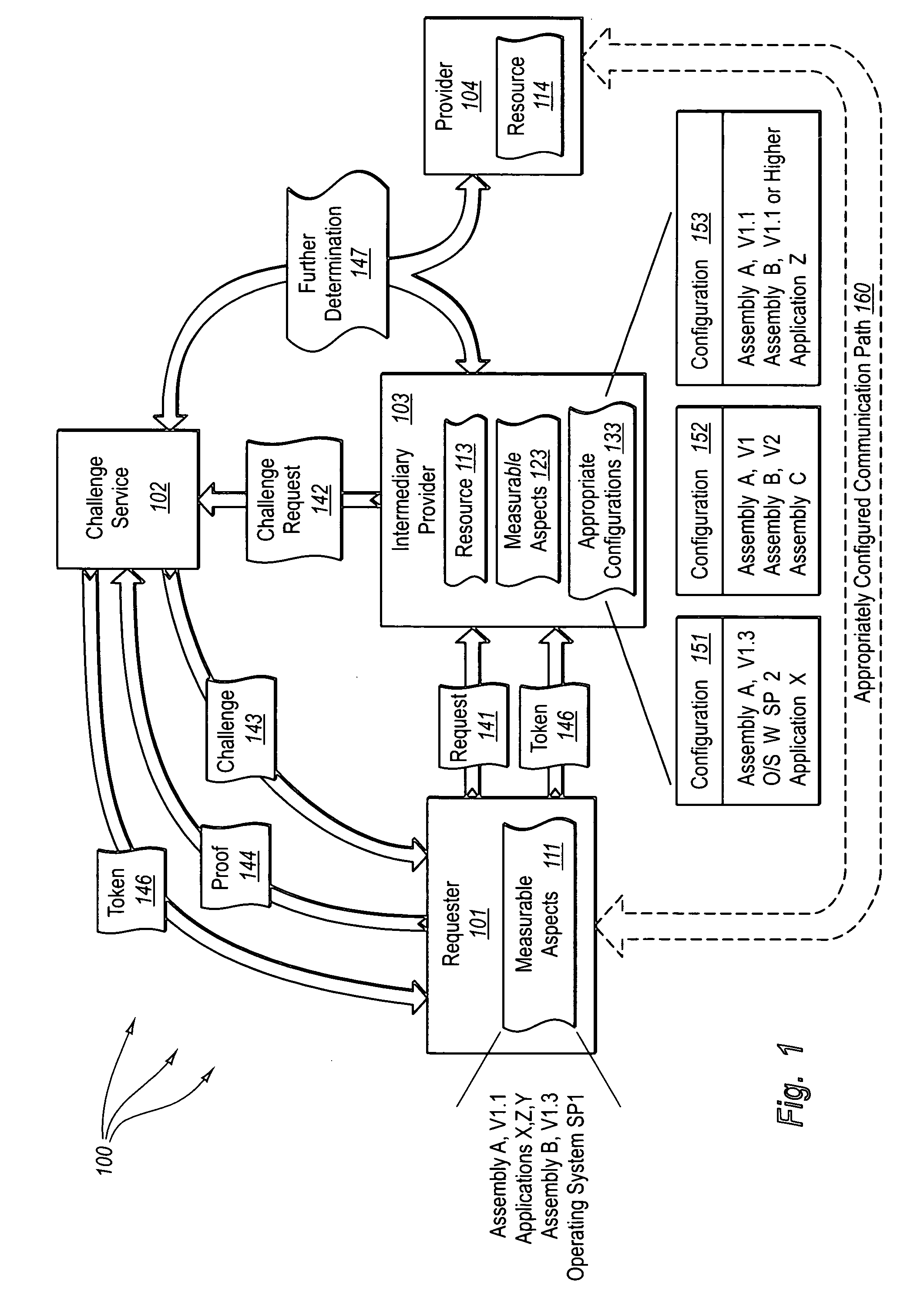
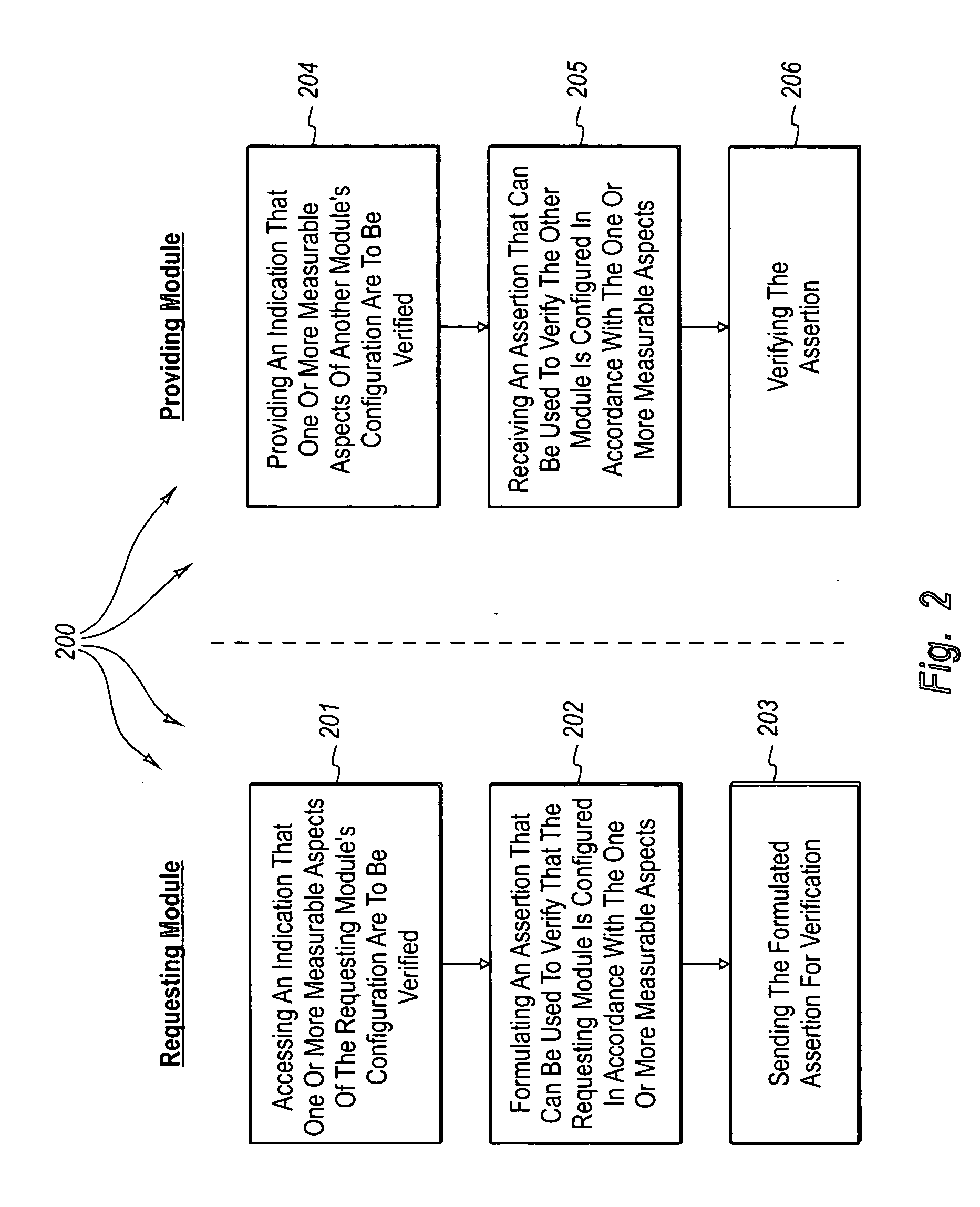
Bi-directionally verifying measurable aspects associated with modules, pre-computing solutions to configuration challenges, and using configuration challenges along with other authentication mechanisms
InactiveUS20050235150A1Efficiently validatedValid verificationUser identity/authority verificationDigital data authenticationComputing systemsVerified computing
The present invention extends to validating measurable aspects of computing system. A provider causes a challenge to be issued to the requester, the challenge requesting proof that the requester is appropriately configured to access the resource. The requester accesses information that indicates how the requester is to prove an appropriate configuration for accessing the resource. The requester formulates and sends proof that one or more measurable aspects of the requester's configuration are appropriate. The provider receives proof that one or more measurable aspects of the requester's configuration are appropriate and authorizes the requester to access the resource. Proof of one more measurable aspects of a requester can be used along with other types of authentication to authorize a requester to access a resource of a provider. Solutions to challenges can be pre-computed and stored in a location accessible to a provider.
Owner:MICROSOFT TECH LICENSING LLC
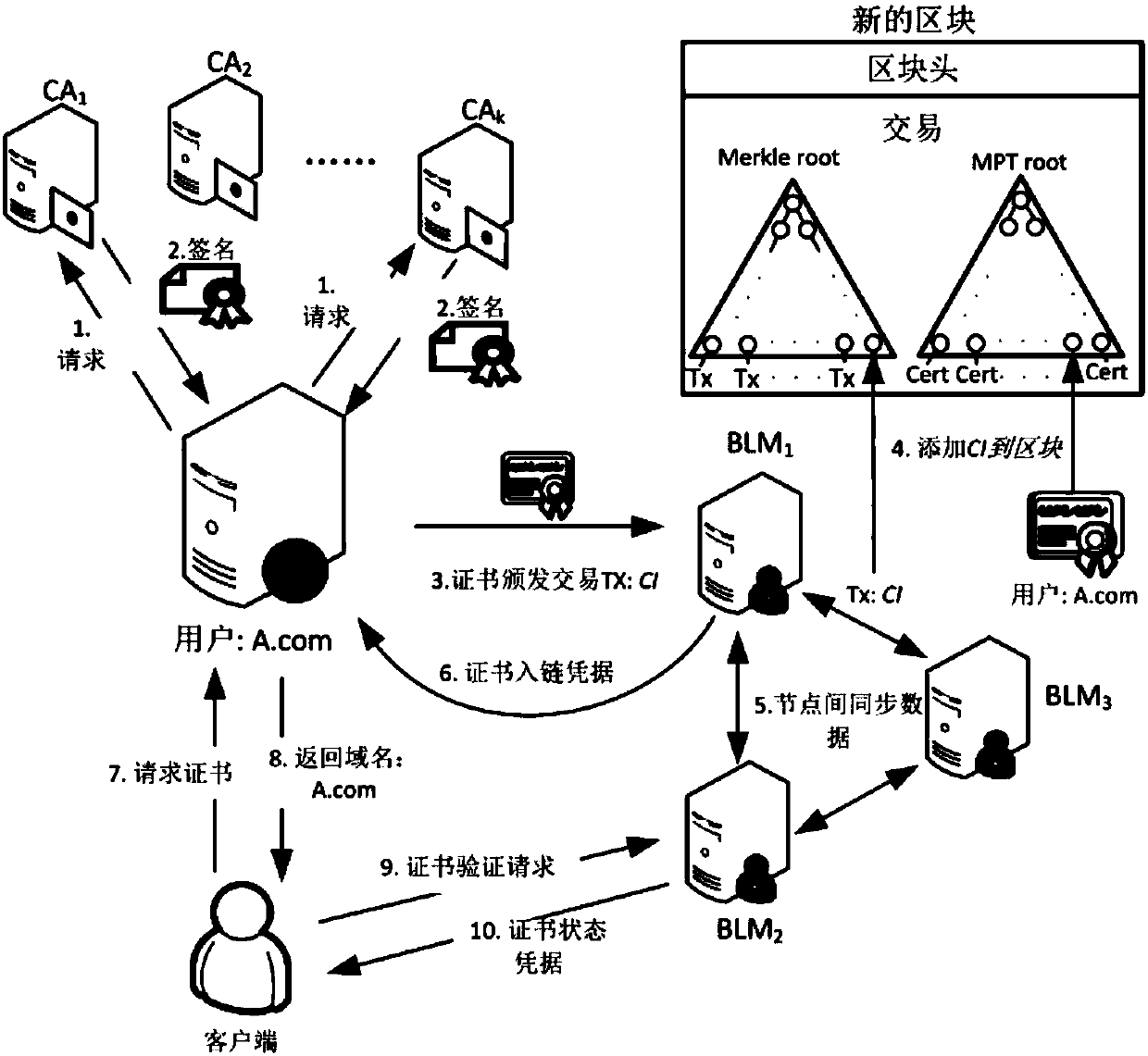
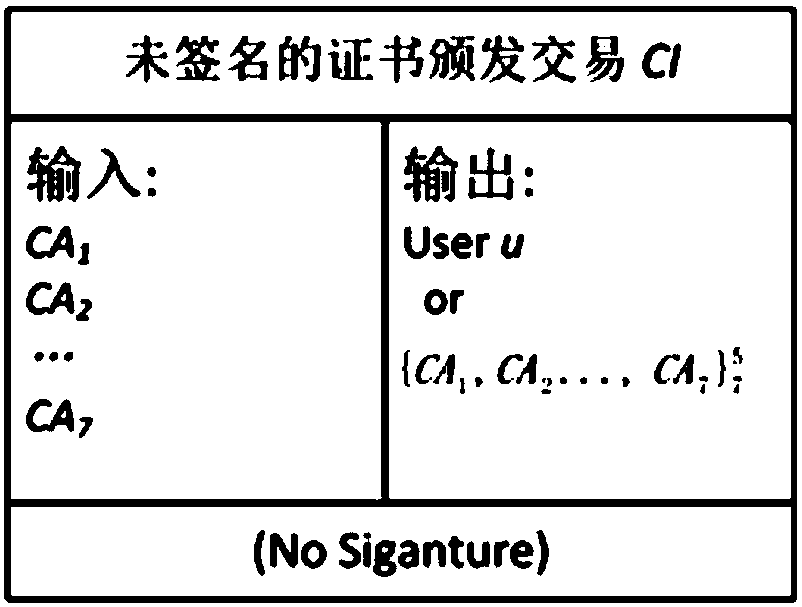
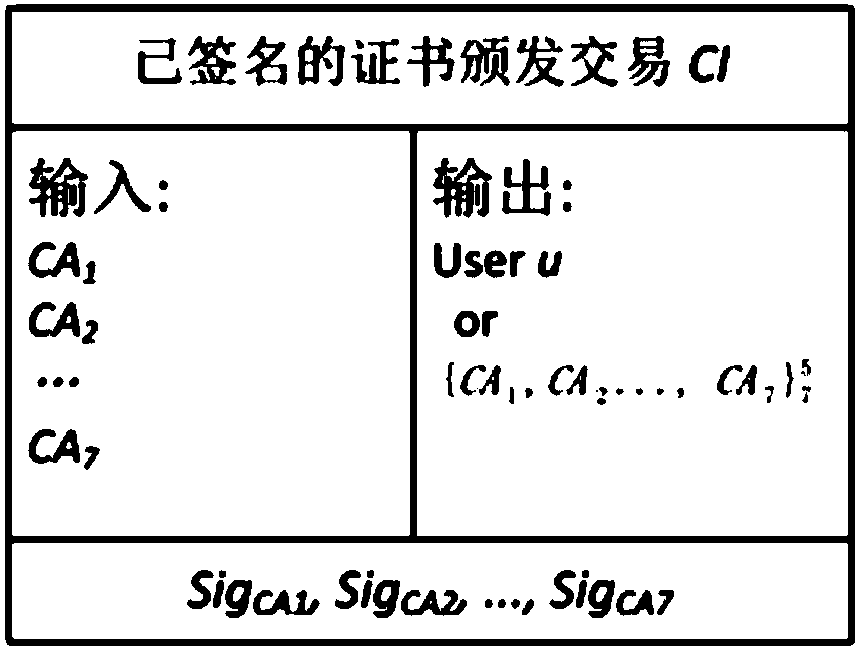
Public key infrastructure system based on block chain, and certificate management method thereof
ActiveCN107769925ASafe and efficient managementImprove efficiencyUser identity/authority verificationDomain nameE infrastructure
The invention relates to a public key infrastructure system based on a block chain, and a certificate management method thereof. The public key infrastructure system comprises a user u, a plurality ofCAs, a plurality of block chain maintainers BLM, a block chain and a client, the user u sends a signature request to the plurality of CAs, the plurality of CAs separately perform signature and feed back the same to the user u; the user u merges the signatures in a singed certificate issue affair and sends the same to the block chain maintainers BLM; the block chain maintainers BLM verify and store the signatures in candidate blocks of the block chain, and send proves of existence of the singed certificate issue affair CI-signed to the user u; and the client requests a certificate from the user u, the user u replies the domain name and the block chain maintainers BLM, and the client sends a query and verification request to the block chain maintainers BLM to query the state of the certificate and make response. By adoption of the public key infrastructure system, simple, convenient and efficient management of the certificates are achieved, and the problem of single point fault of CA can be avoided.
Owner:SHANDONG UNIV
Multifunctional tribology performance test system
InactiveCN102628747AReal performance testPerformance testing is completeMachine bearings testingEngineeringTribology
The invention discloses a multifunctional tribology performance test system, which comprises a test cabin body, a bearing sleeve, a test shaft, a shaft sleeve, a test shaft driving device, a loading device and a comprehensive performance test unit. An installation space of a piece to be tested is arranged between the shaft sleeve and the bearing sleeve. Two ends of the test cabin body are respectively in rotation sealing fit with the test shaft, and a lubricant inlet and a lubricant outlet are arranged on the test cabin body. The comprehensive performance test unit comprises a computer, a torque rotating speed detection device, a loading force detection device, a lubricant temperature detection device, a liquid film thickness detection device and a lubricant flow detection device. The multifunctional tribology performance test system can simultaneously conduct radial and axial loading, simulates actual complex working conditions of the piece to be tested truly, achieves tests of tribology comprehensive performance such as rotating speed, torque, temperature rise, friction characteristic, test loading force, production validation (PV) value, dynamic rigidity and dynamic damping, and is capable of really and comprehensively testing and verifying the comprehensive performance of the piece to be tested.
Owner:重庆奔腾智能装备技术有限公司
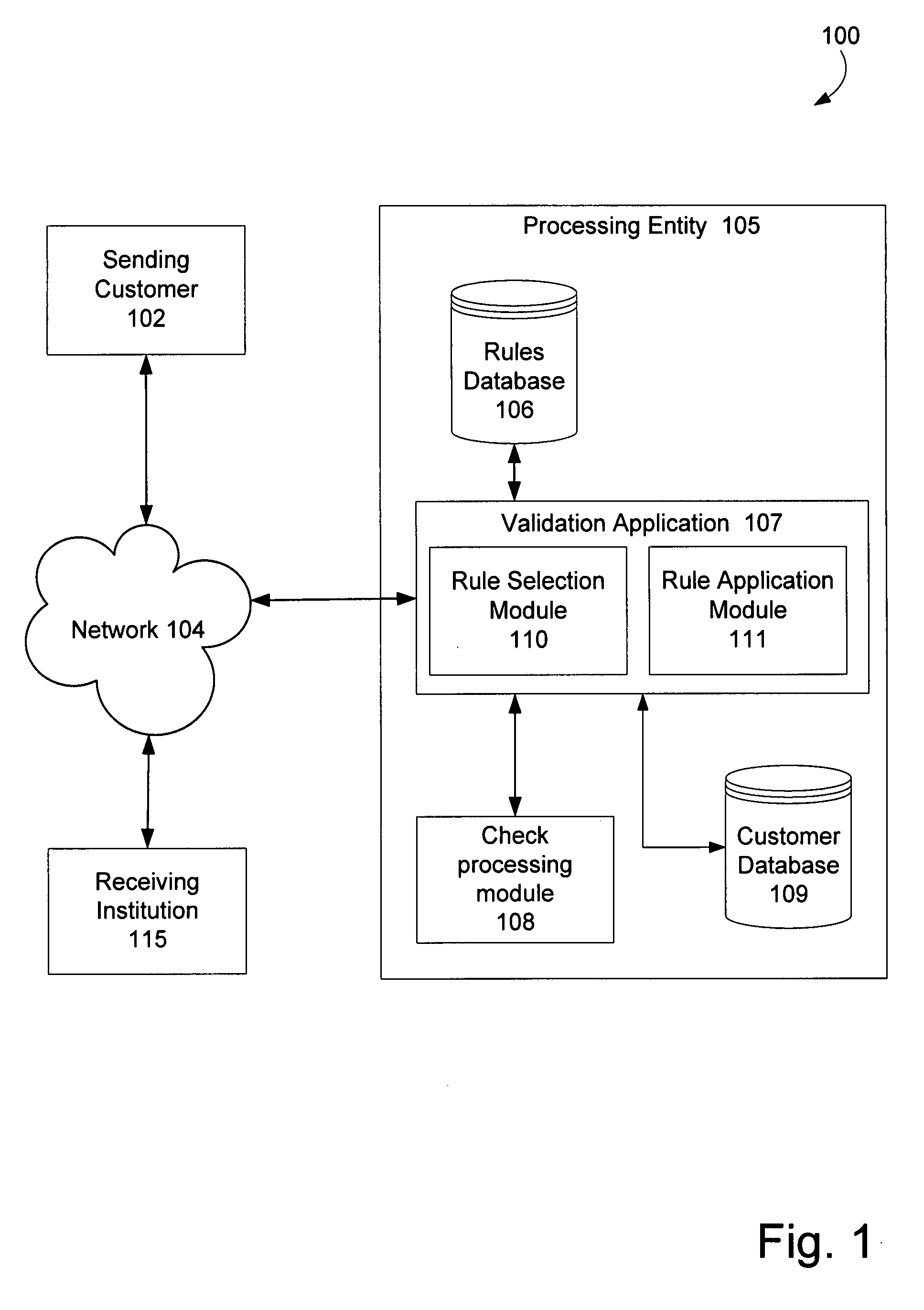
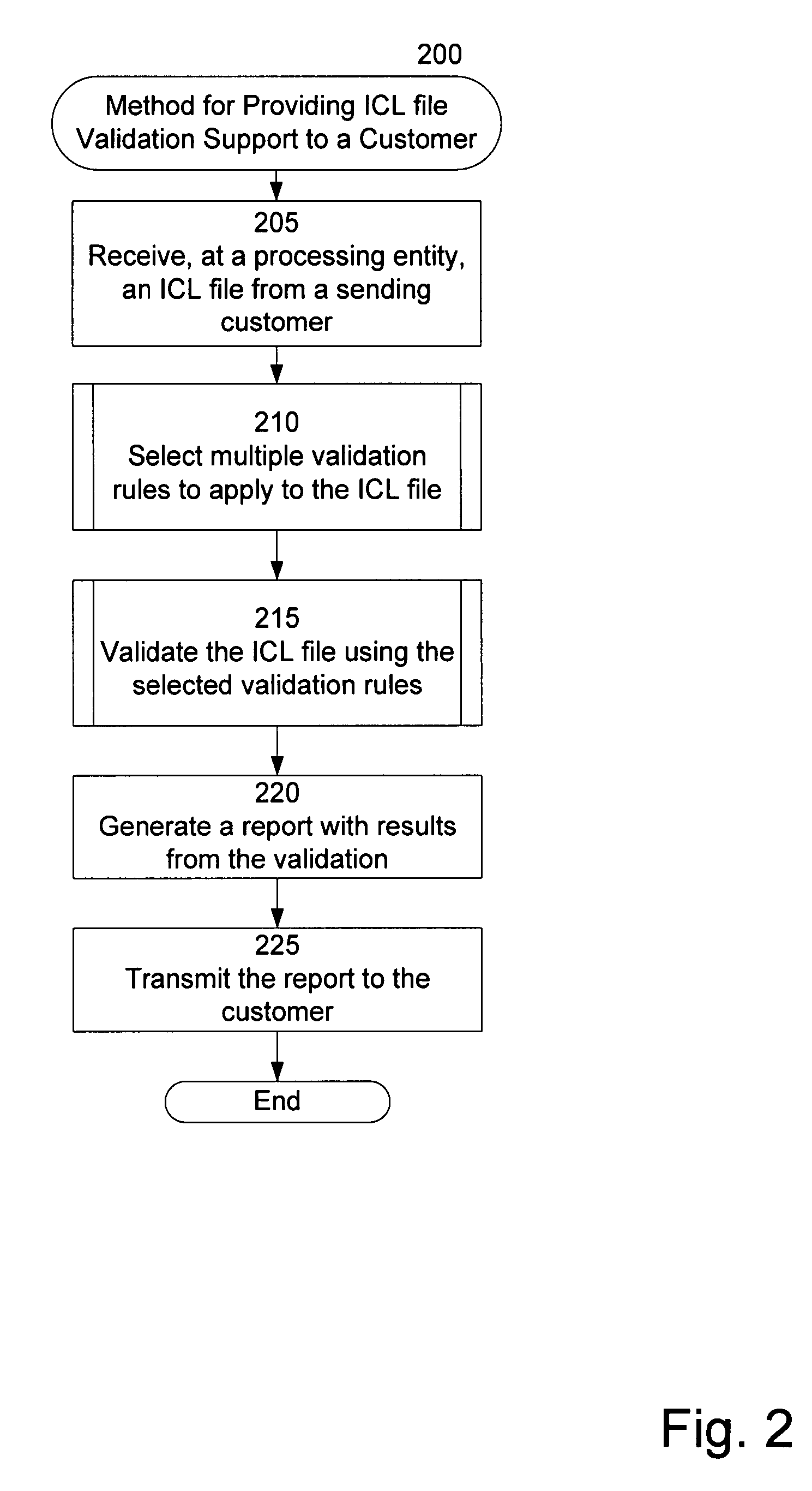
Electronic image cash letter validation
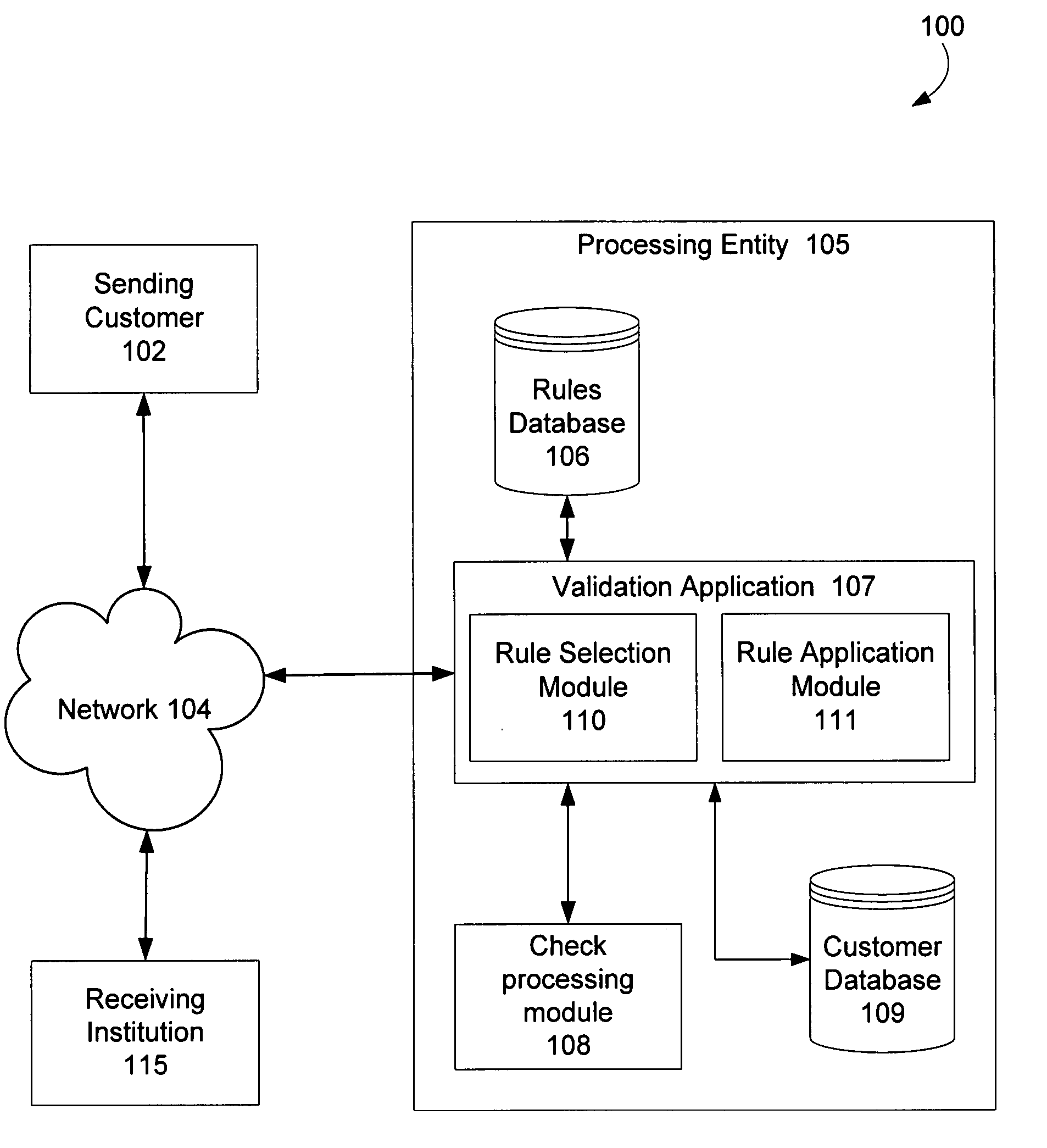
ActiveUS20080006687A1Valid verificationPrevent improper validation rejectionComplete banking machinesFinancePaymentCheque
Validating image cash letter (“ICL”) files using appropriate validation standards for each ICL file and, where appropriate, allowing successfully validated elements of an ICL file containing one or more unsuccessfully validated elements to be processed for payment and / or presentment. A processing entity can receive an ICL file with multiple ICLs that each includes multiple bundles of electronic check items from a customer. The processing entity can validate the ICL file using multiple validation rules selected based on a file type of the ICL file, data content of the ICL file, and / or an identity of a bank associated with the ICL file. The processing entity can transmit a report of the validation results to the customer. The processing entity can select certain successfully validated elements of the ICL file for check presentment and / or payment processing.
Owner:FEDERAL RESERVE BANK OF DALLAS +4
Flow labels
ActiveUS7266121B2Easy to useValid verificationError preventionTransmission systemsQuality of serviceData stream
There is disclosed a system for monitoring a packet data flow, comprising: a data flow source element including: determining means adapted to determine a quality of service identifier for the data flow; first generating means adapted to generate an encoded value in dependence on the quality of service identifier; allocating means adapted to allocate the quality of service identifier and the encoded value to the flow label for each data packet of the data flow; and transmitting means for forwarding data packets including flow labels to a routing domain; and a routing domain interface element including: receiving means for receiving data packets from the data flow source; second generating means adapted to generate a further encoded value in dependence on the quality of service identifier in a flow label of a data packet; comparing means adapted to compare the further encoded value to the encoded value in the flow label; and routing means adapted to selectively route the data packets in dependence on the comparing step.
Owner:CRYSTAL MOUNTAIN COMM LLC
Recording processing method and device based on business information, and computer device
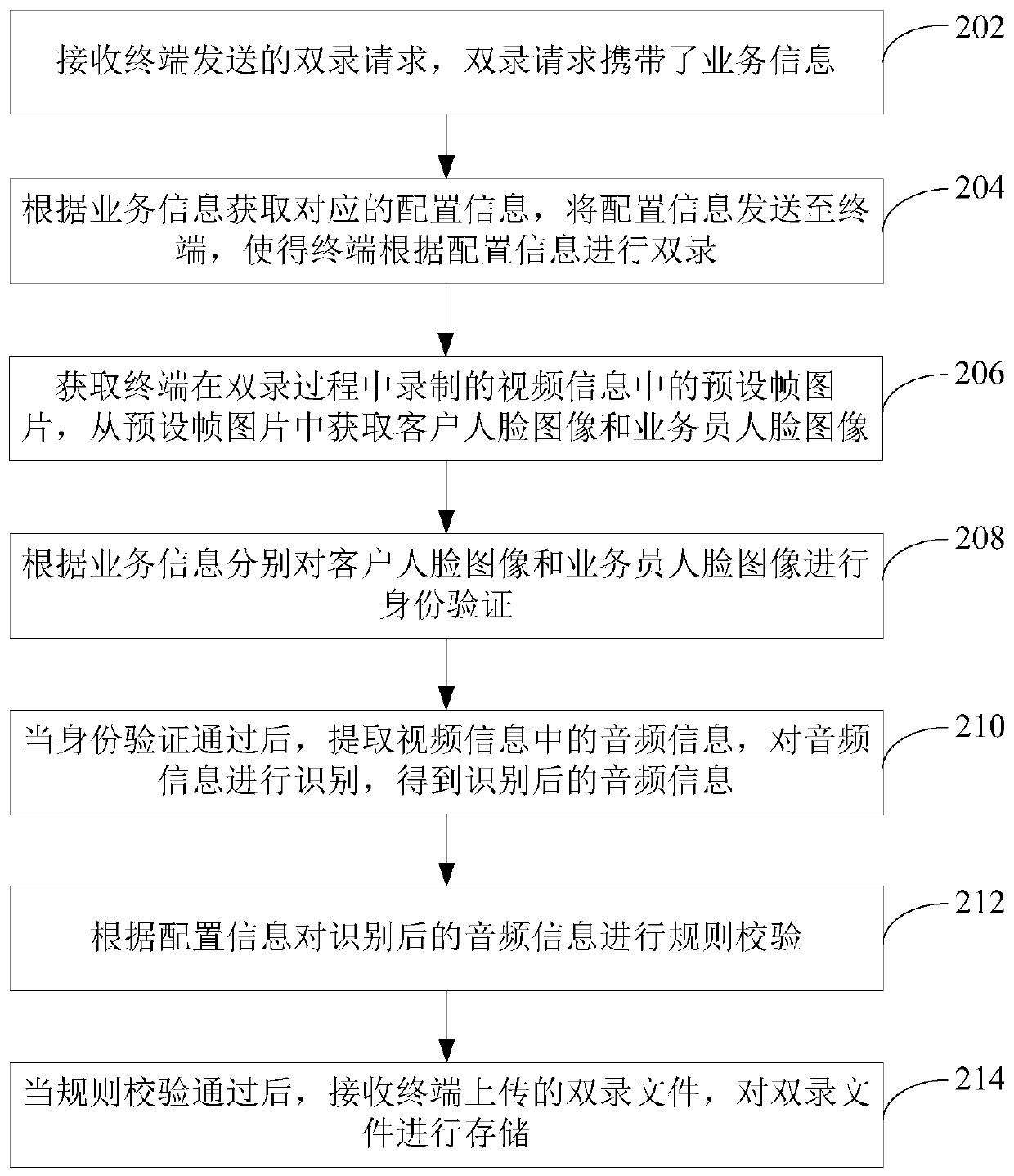
ActiveCN109783338AImprove verification efficiencyValid verificationHardware monitoringCharacter and pattern recognitionService informationAuthentication
The invention relates to a recording processing method and device based on business information of biological recognition and a computer device. The method comprises the steps of receiving a double-recording request sent by a terminal, obtaining corresponding configuration information according to service information carried by the double-recording request, and sending the configuration information to the terminal; Obtaining a preset frame picture in the video information recorded by the terminal in the double-recording process, and obtaining a client face image and a salesman face image fromthe preset frame picture; Respectively carrying out identity verification on the client face image and the salesman face image according to the service information; After the identity verification ispassed, extracting audio information in the video information, and identifying the audio information to obtain identified audio information; Performing rule verification on the identified audio information according to the configuration information; And after the rule verification is passed, receiving the double-record file uploaded by the terminal and storing the double-record file. By adopting the method, the data in the recording process can be effectively processed so as to effectively improve the double-recording verification efficiency.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
Delegating certificate validation
ActiveUS7395428B2Valid verificationSufficient informationUser identity/authority verificationCertificate signing requestComputerized system
The principles of the present invention provide for delegating certificate validation. A client computer system sends a certificate validation request to a server computer system over a trusted link. The certificate validation request includes at least enough certificate information for a certificate authority to identify a digital certificate that binds a sending entity to a private key. The server computer system checks a validation path to determine if the digital certificate is valid and at least one certificate revocation list to determine if the certificate has been compromised. The server computer system sends a certificate status indication to the client computer system over the trusted link. Accordingly, the resources of the server computer system, instead of the client computer system, are utilized to validate a digital certificate. Further, digital certificate validation can be delegated to a server computer system that attempts to pre-validate a digital certificate.
Owner:MICROSOFT TECH LICENSING LLC
Alliance blockchain underlying encryption method capable of resisting quantum attacks
ActiveCN108768652AIncrease vitalityValid verificationPublic key for secure communicationUser identity/authority verificationVitalityQuantum computer
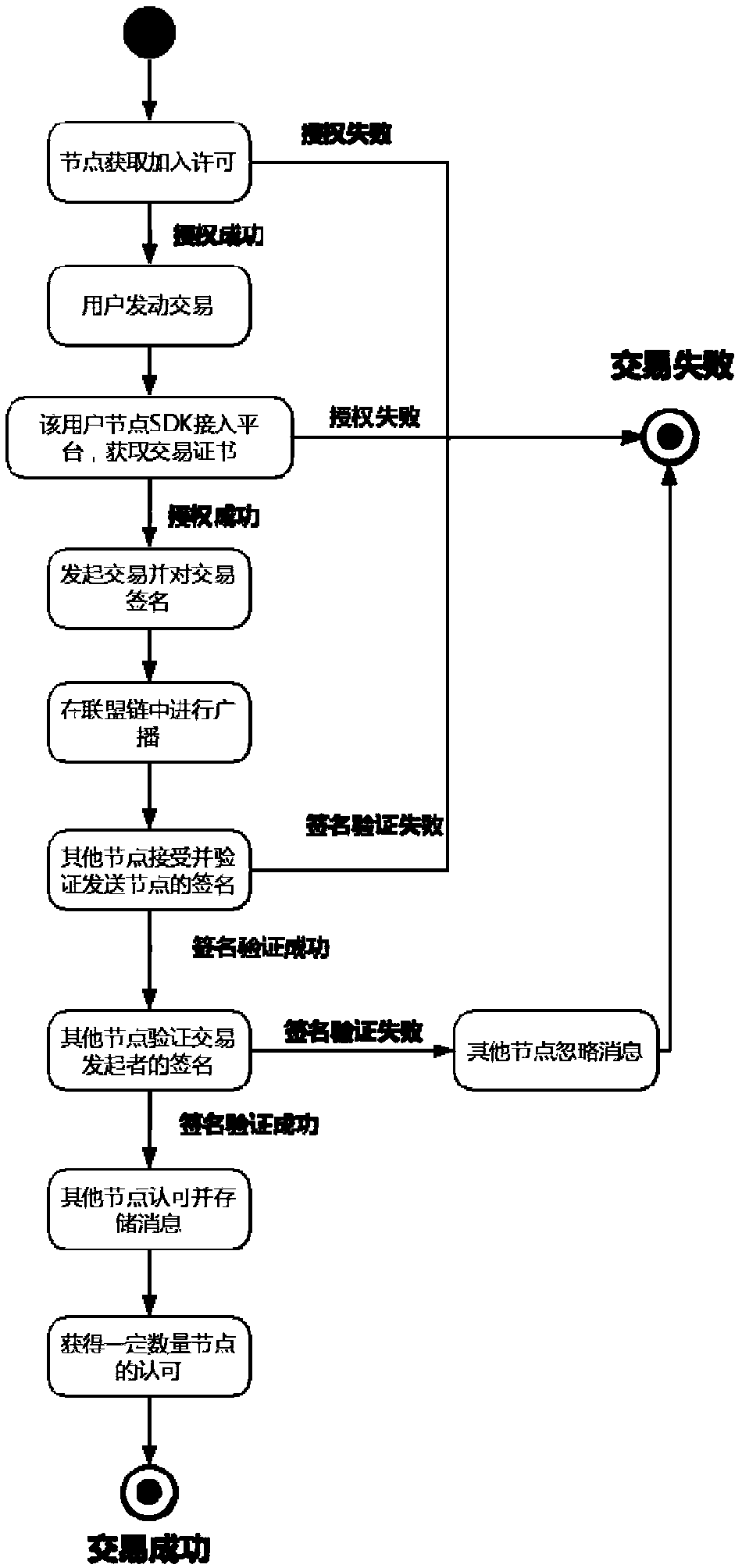
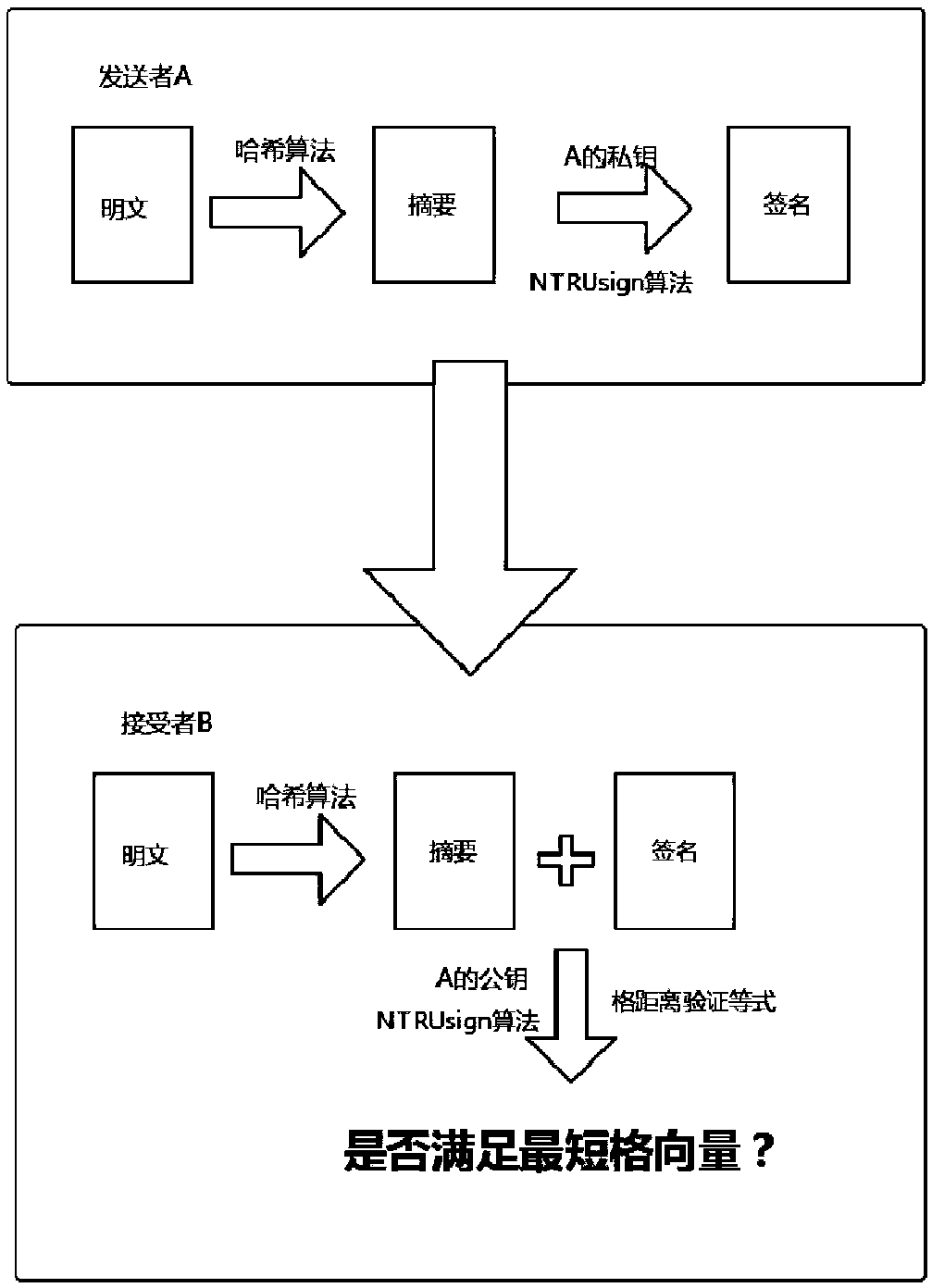
The invention discloses an alliance blockchain underlying encryption method capable of resisting quantum attacks. According to the method, a set of identity and message verification process is adopted, in the links that may be broken by hackers through quantum computing or other means, such as the link of issuing digital certificates, the link that nodes access a transaction platform, the link that the nodes perform transactions, and the link that the transaction contents are transmitted between the nodes, an NTRUsign algorithm that resists the quantum attacks is adopted to generate signaturesor verify the signatures, the verification of the identity and information security can be strengthened, so that the alliance chain can resist the attacks of quantum computing on the whole, and the alliance chain can still have strong vitality in the future quantum computing era.
Owner:HANGZHOU QULIAN TECH CO LTD
Circuit structure and method for realizing USB interface functional verification test on the basis of FPGA module
ActiveCN102087624AConvenient verificationValid verificationDetecting faulty computer hardwareWork performanceComputer module
The invention relates to a circuit structure for realizing a universal serial bus (USB) interface functional verification test on the basis of a field programmable gate array (FPGA) module. The circuit module comprises an FPGA module and an advanced reduced instruction set computer (RISC) machine (ARM) chip, wherein a USB host control program is loaded in the FPGA module; the FPGA module is connected with USB equipment to be tested through a low voltage differential signaling (LVDS) signal interface and is also connected with the ARM chip; and the ARM chip is connected with a test computer. The invention also relates to a method for performing the USB interface functional verification test by using the circuit structure. By adopting the circuit structure and the method for realizing the USB interface functional verification test on the basis of the FPGA module, the test computer is communicated with the USB equipment to finish the processes of identification and enumeration with the USB equipment, and the ARM chip resolves a command sent by the test computer and controls a command which is sent to the test computer by the USB equipment, so that not only a USB interface can be verified more comprehensively, conveniently and effectively, but also the structure is simple and practical, the operation process is quick and convenient, the working performance is stable and reliable, and the application range is wide.
Owner:SPREADTRUM COMM (SHANGHAI) CO LTD
Personal identification method and apparatus for biometrical identification
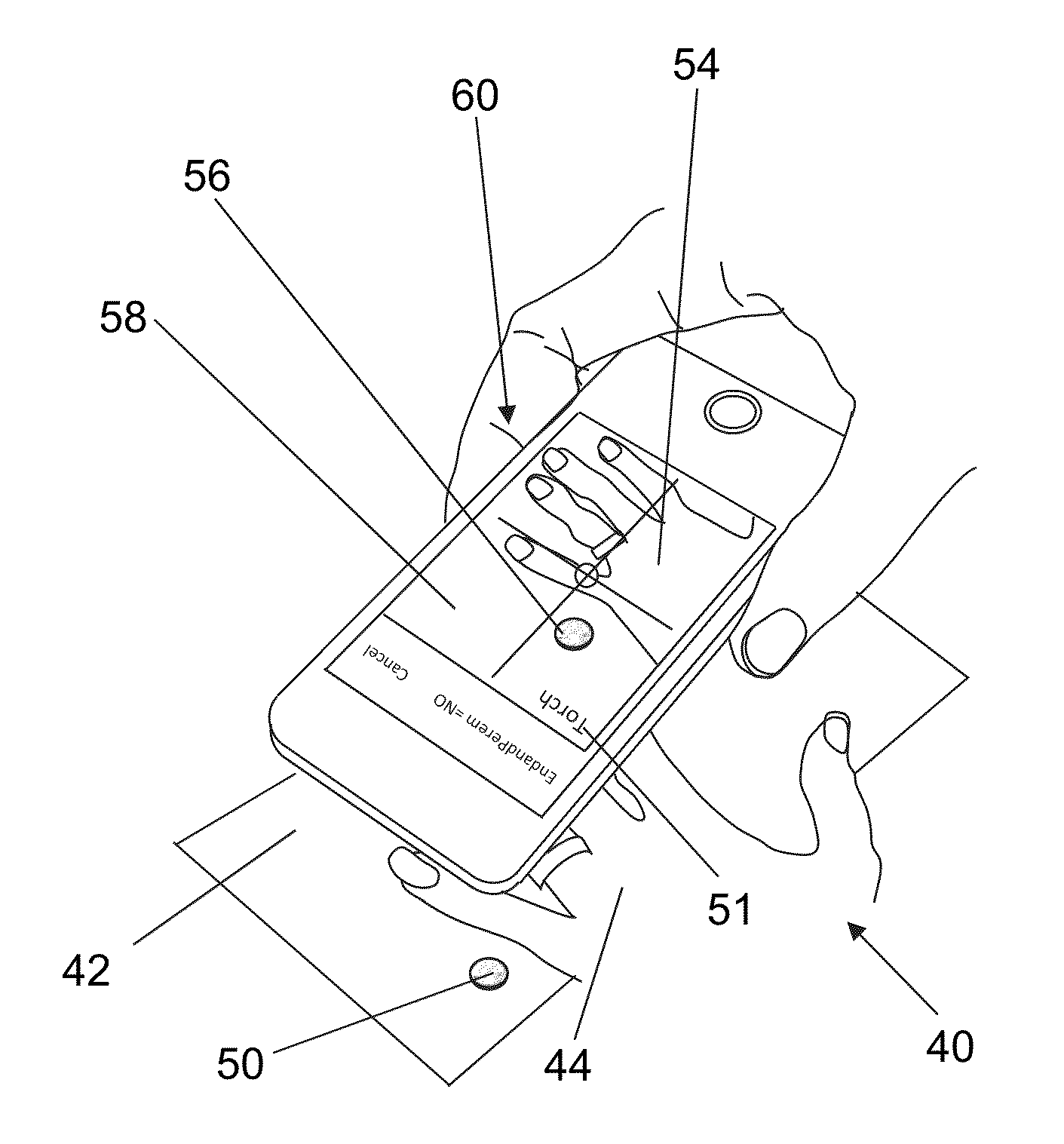
ActiveUS20160267340A1Valid verificationTransmission easilyBiometric pattern recognitionMatching and classificationWeb siteIdentity theft
Identification systems comprising methods and apparatus, including computer programs encoded on a computer storage medium on digital and mobile devices, for determining a person's identity based on biometric characteristics of a person's hand or face using dimensions of a full-scale object from within at least one image of the person's hand or face. The method and apparatus of the present invention may be used to protect against identity theft in performing financial transactions, and to prevent unauthorized access to computer systems, mobile devices, web sites, and any premises either in banks, businesses and other organizations dealing with confidential information.
Owner:JENSEN BETTINA
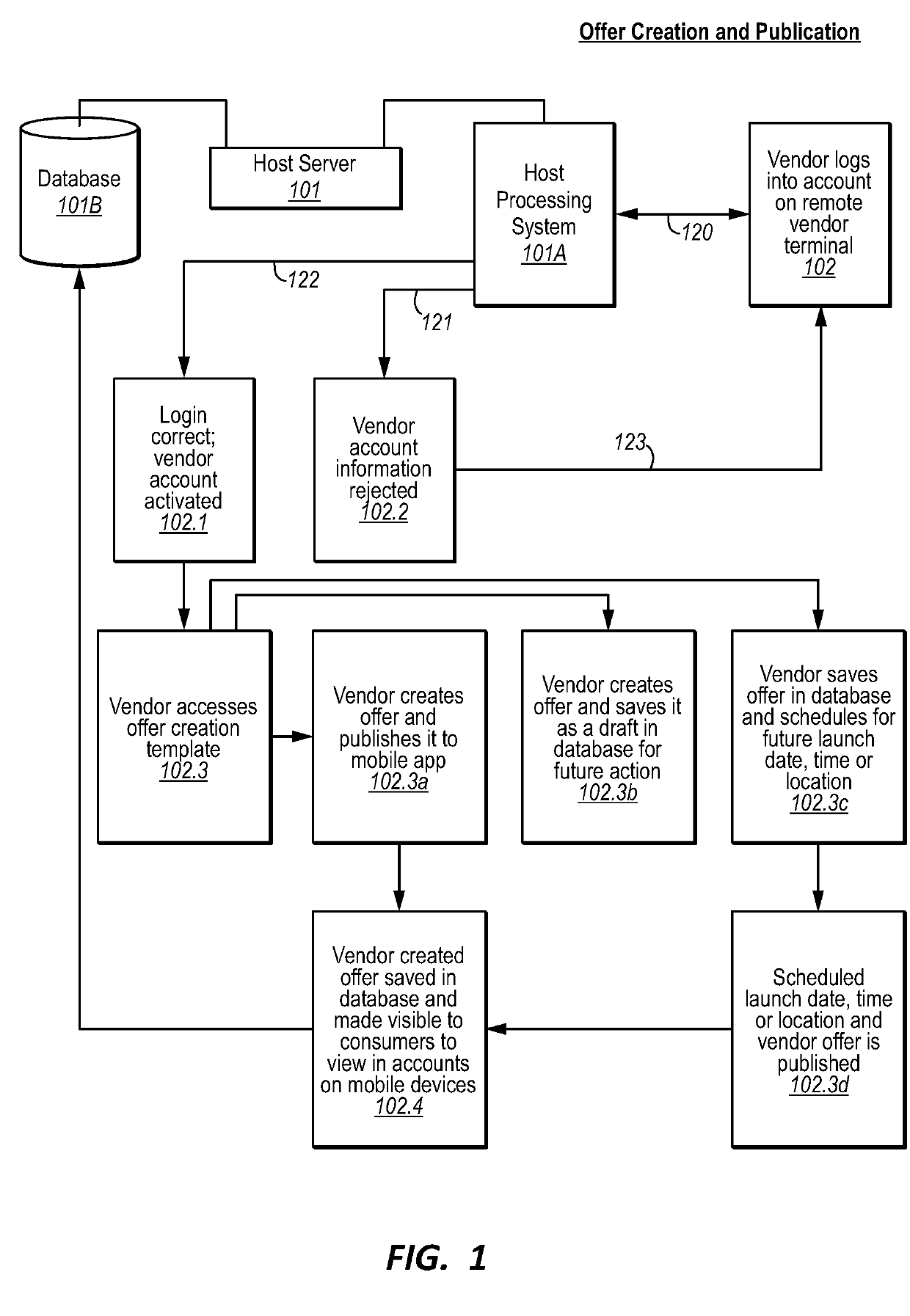
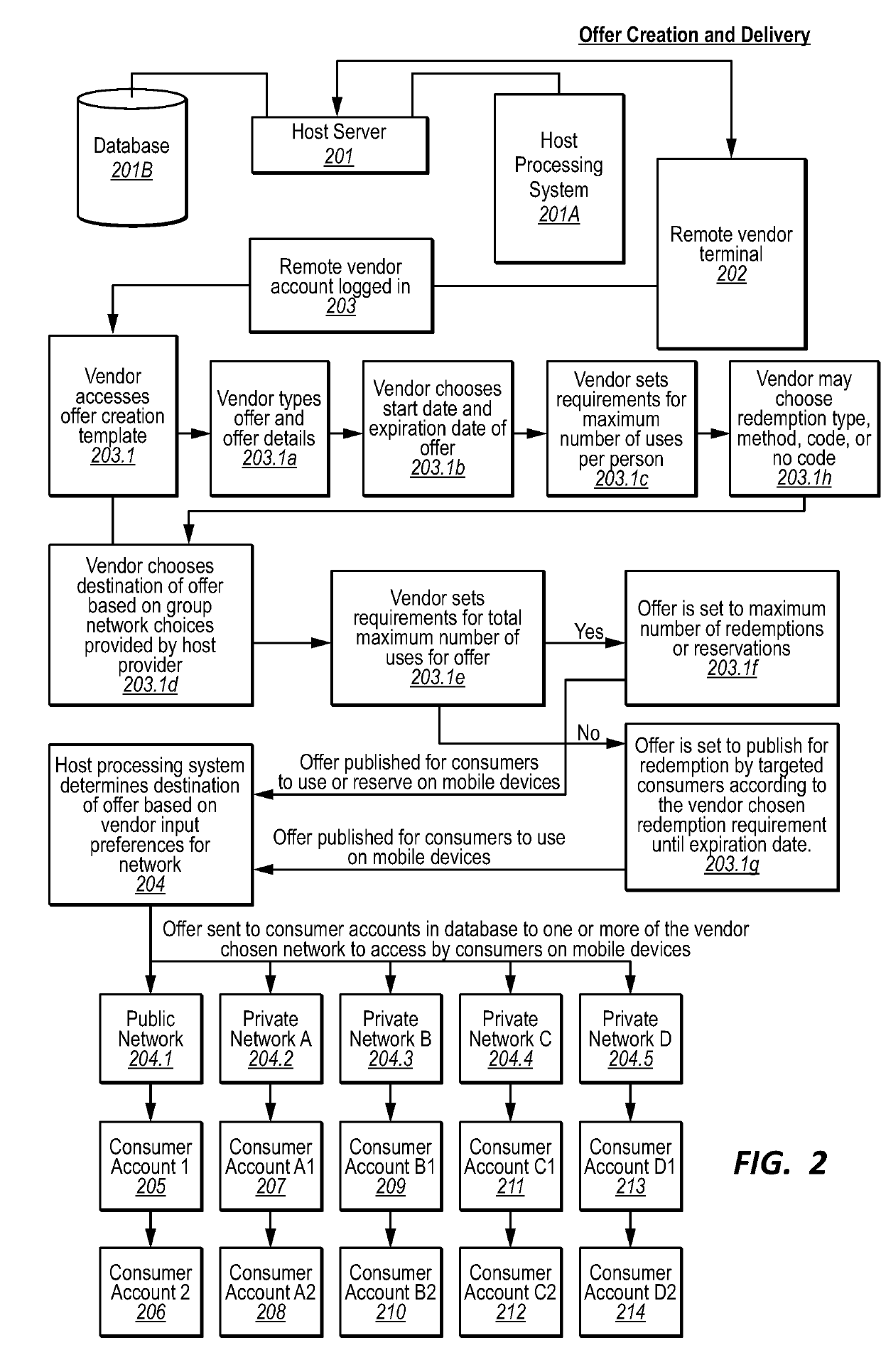
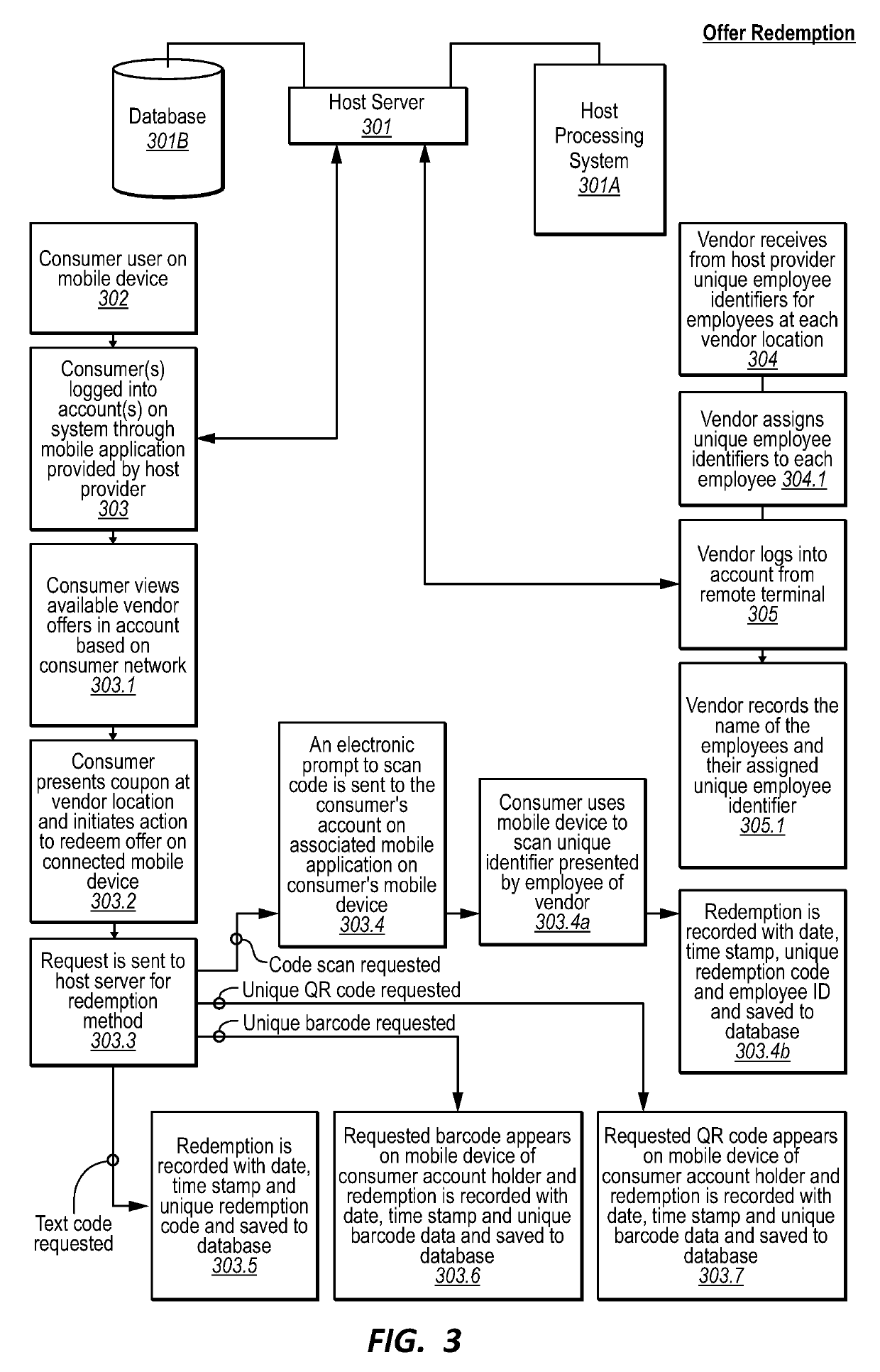
Methods and systems for creating, publishing, and redeeming incentive marketing offers
InactiveUS20190228428A1Efficient targetingValid verificationMarketingElectronic computerData science
Methods and systems for managing electronic computer-based incentive marketing campaigns are provided. In particular, one embodiment comprises a method that validates redemption of an offer based on a location of a consumer computing device correlating to a vendor location. Another embodiment comprises a method that provides an offer to a consumer computing device based on a response from a consumer account to a survey. Another embodiment comprises a method that distributes and validates redemption of an offer based on a consumer account being associated with a network to which the offer is to be distributed. A further embodiment comprises a method that denies a request to redeem an offer until a pre-determined period of time has elapsed. One or more other embodiments comprise methods and systems that improve the creation, publication, distribution, validation, redemption, and overall management of digital incentive marketing offers.
Owner:BRUNER DAVID WAYNE +2
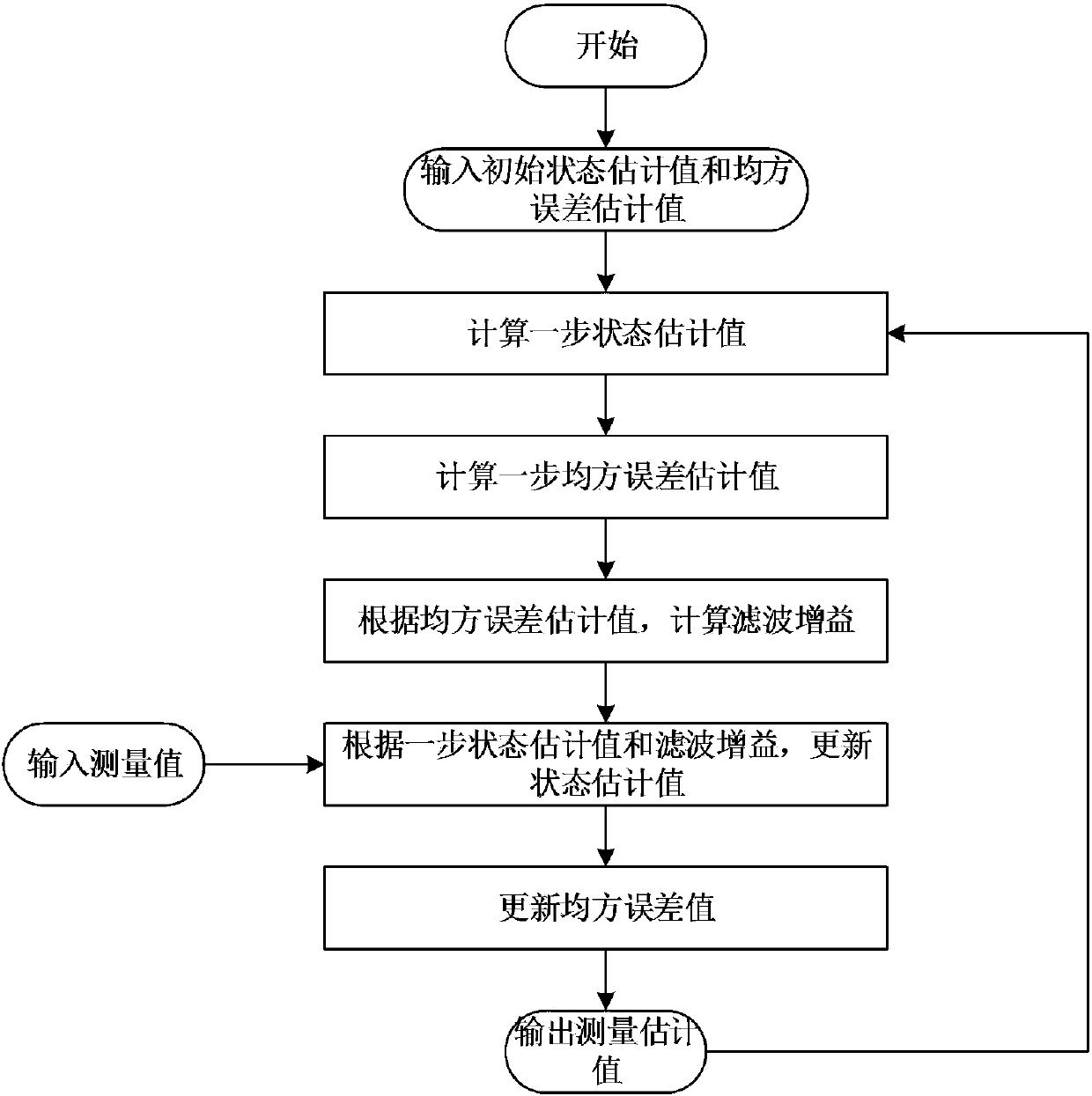
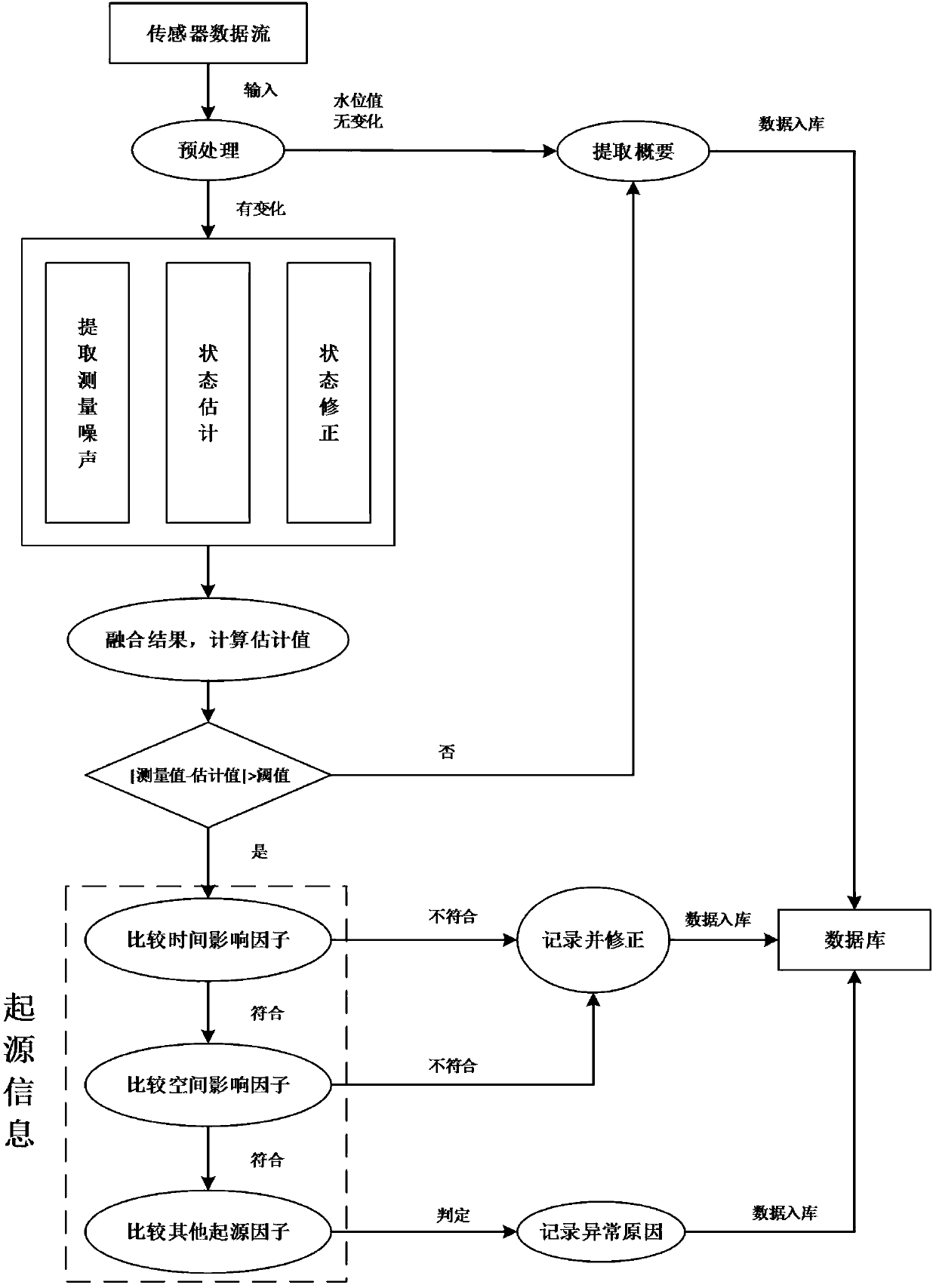
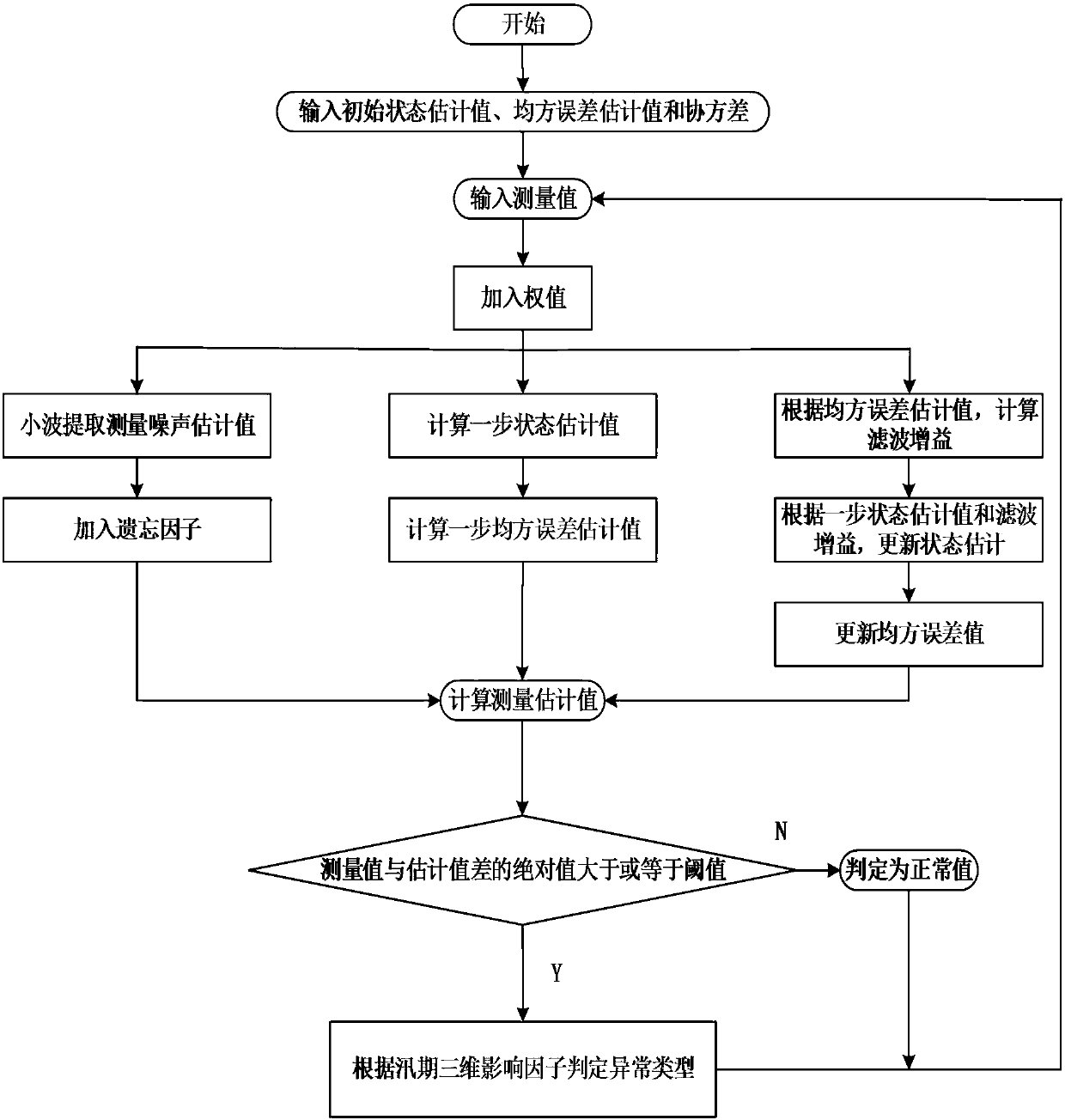
Data flow abnormality detection method based on parallel Kalman algorithm
InactiveCN106709250AImprove efficiencyVerification is feasibleSpecial data processing applicationsInformaticsData streamParallel algorithm
The invention discloses a data flow abnormality detection method based on a parallel Kalman algorithm. The data flow abnormality detection method comprises the following steps that 1, measurement data of a sensor in a period of time is acquired; 2, the measurement data is compared with a measurement value in a previous period of time, once a change is generated, an estimation value is calculated through the Kalman algorithm according to the measurement value, an absolute value of a difference between the estimation value and the measurement value is compared with a specified threshold value, and if the absolute value is not smaller than the threshold value, the absolute value is judged to be an abnormal value, and the next step is conducted; 3, the generation reasons of the abnormal value are judged by considering a time influence factor, a space influence factor and other factors such as the flood period, the weather and the human factors which influence abnormality detection and recorded, and information is stored in a database. According to the data flow abnormality detection method, the time influence factor, the space influence factor and the other provenance information influence factor are taken into account; an algorithm task is decomposed and processed in parallel in order to improve the algorithm efficiency, and the detection precision is improved.
Owner:HOHAI UNIV
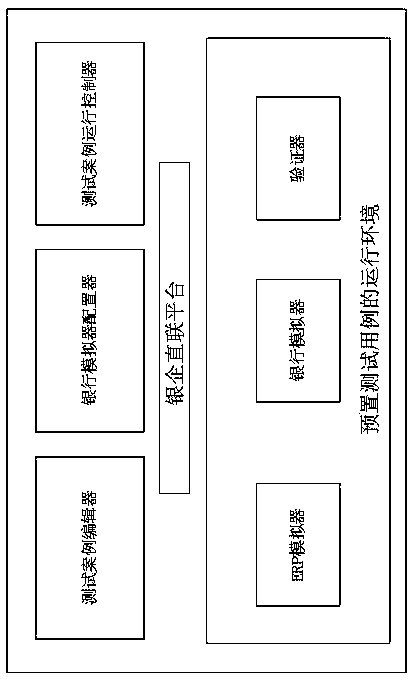
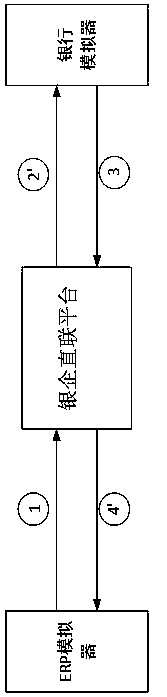
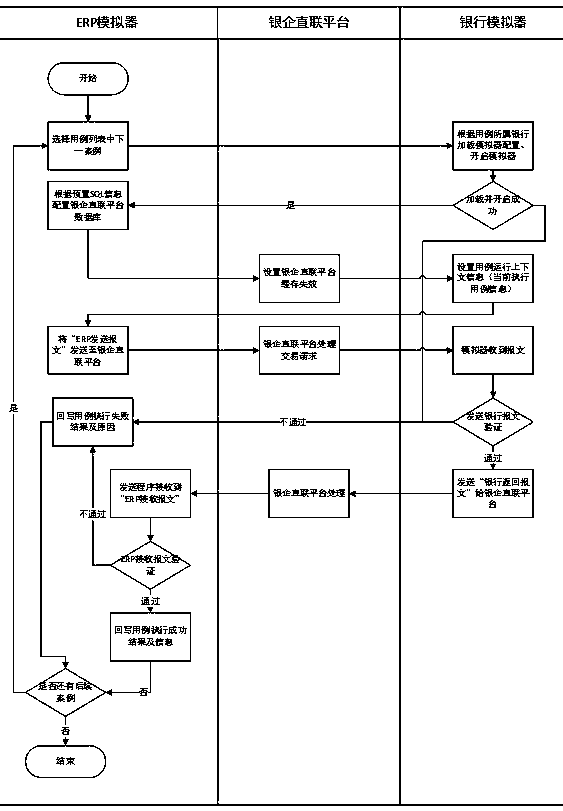
Real business-based financial transaction test system and method
InactiveCN108614777ARealize simulationEffectively detect defectsFinanceSoftware testing/debuggingFinancial transactionFinancial trading
The invention discloses a real business-based financial transaction test system and method, belongs to the field of financial transaction simulation and test, and aims at carrying out modification byusing systems of ERP manufacturers so as to obtain effective and sufficient verification without influencing fund security of enterprise users. An adopted technical scheme is the real business-based financial transaction test system which comprises an ERP simulator, a bank simulator, a bank-enterprise direct connection platform, a verifier, a test case editor, a bank simulation configuration unitand a test case operation controller. The invention furthermore discloses the real business-based financial transaction test method.
Owner:SHANDONG INSPUR GENESOFT INFORMATION TECH CO LTD
Anti-fake method combining tracing code with random encryption password
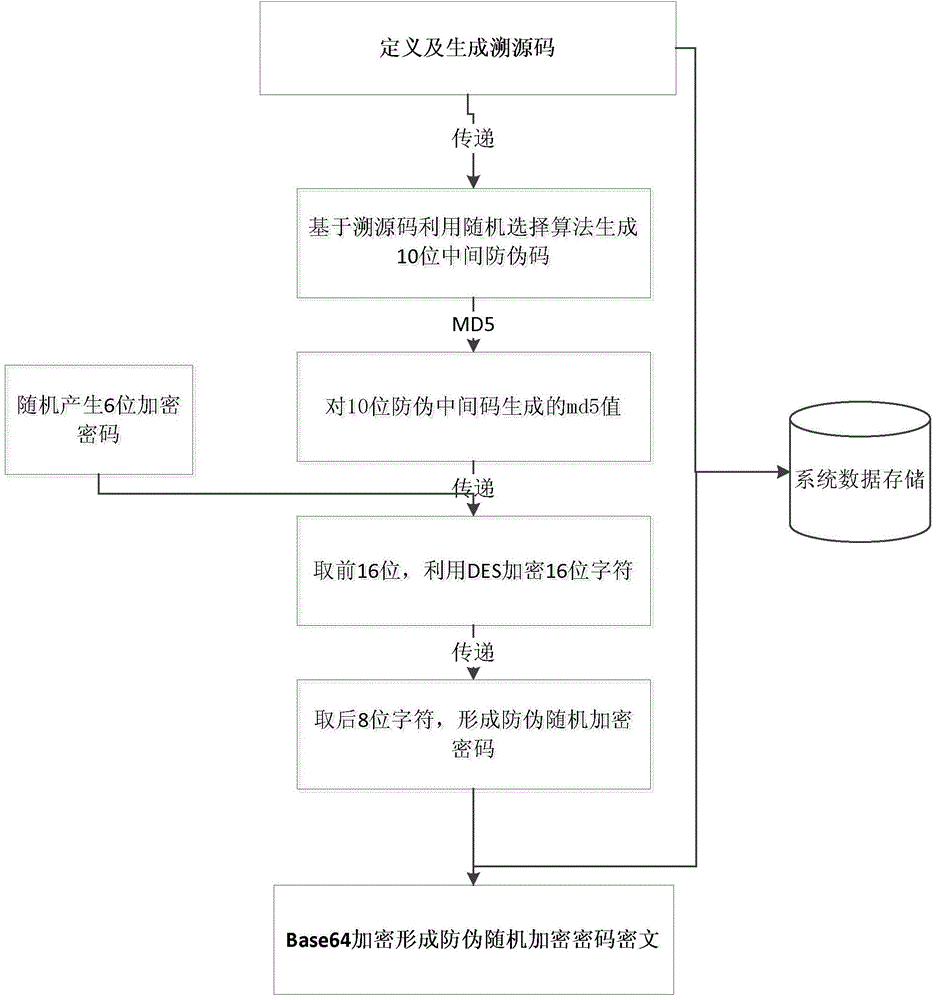
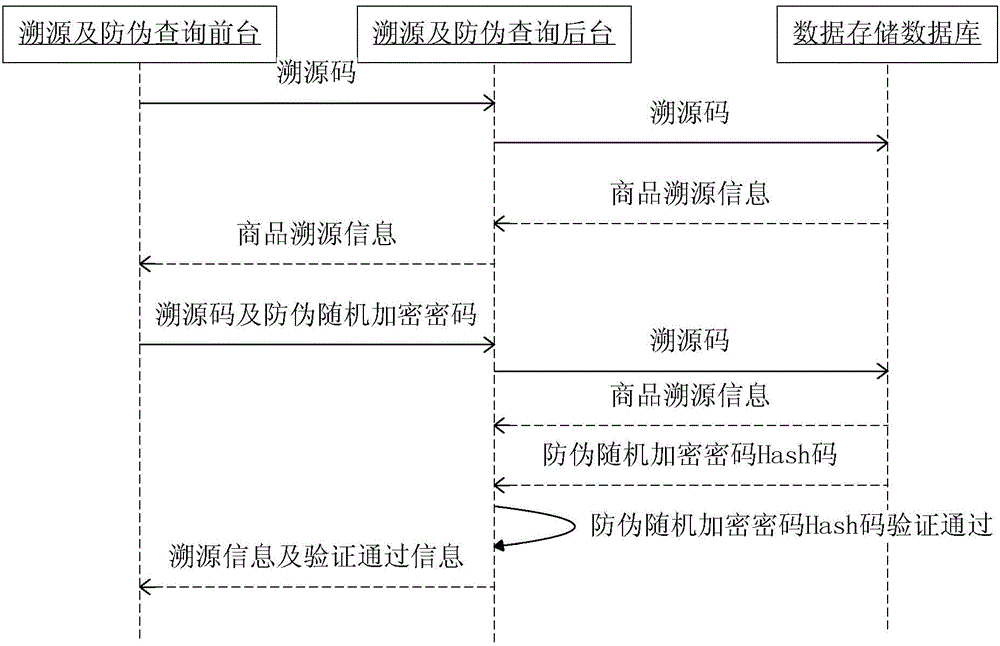
ActiveCN104574090ARealize multiple anti-counterfeitingTo achieve the effect of cross-validationStampsCommerceArray data structurePassword
The invention discloses an anti-fake method combining a tracing code with a random encryption password. The method comprises the following steps: (1) an anti-fake verification server generates the tracing code for a designated product; (2) an intermediate code is generated on the basis of the tracing code, and informative abstract of the intermediate code is encrypted to generate the anti-fake encryption password; (3) a byte array comprising the tracing code and the anti-fake encryption password is encrypted, and an anti-fake verification code is formed and stored; (4) the tracing code is arranged in an open space of the designated product, and the anti-fake encryption password is hidden in the designated product; (5) a consumer obtains the tracing code and the anti-fake encryption password from the designated product, sends the tracing code and the anti-fake encryption password to the anti-fake verification server to generate an anti-fake verification code and compares the obtained anti-fake verification code with the corresponding stored anti-fake verification code, if the two codes are consistent, the anti-fake verification is passed, and otherwise, it is prompted that the anti-fake verification fails. The anti-fake method improves the anti-fake safety and reliability and effectively combines a tracing function with an anti-fake authentication function.
Owner:无锡中科方德软件有限公司
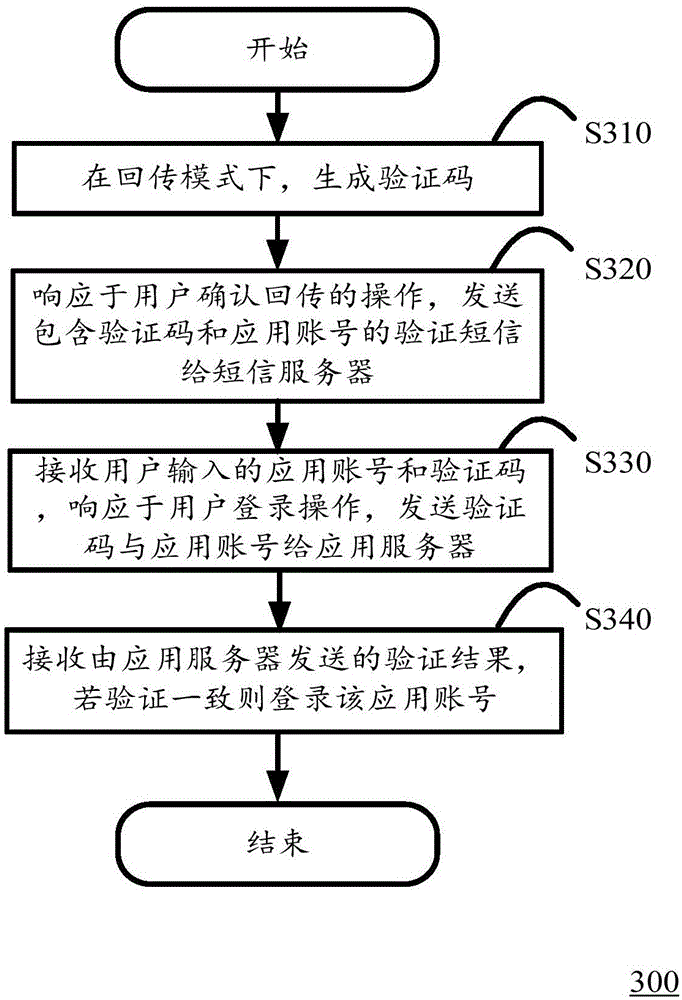
Information verification method, device and system
The invention discloses an information verification method, and the method is executed in a mobile terminal. The mobile terminal can be connected with an application server and a short message server through a network. The method comprises the steps: generating a verification code at a return mode; responding to an operation that a user confirms the return, carrying out the call of a short message interface, transmitting a verification short message containing the verification code and an application account number to the short message server, and transmitting the verification short message to the application server through the short message server; receiving an application account number and a verification code, which are inputted by a user, responding to logging-in operation of the user, and transmitting the verification code and the application account number to the application server, so as to bring convenience to the application server for verification, wherein the application server completes the verification through comparing the verification code corresponding to the application account number transmitted by the short message server with the verification code corresponding to the application account number transmitted by the mobile terminal and judging whether the verification code corresponding to the application account number transmitted by the short message server is consistent with the verification code corresponding to the application account number transmitted by the mobile terminal or not. The method also comprises a step: receiving verification results transmitted by the application server, and logging into the account number if the verification is consistent.
Owner:广州密码科技有限公司
System and method for handling permits for user authentication tokens
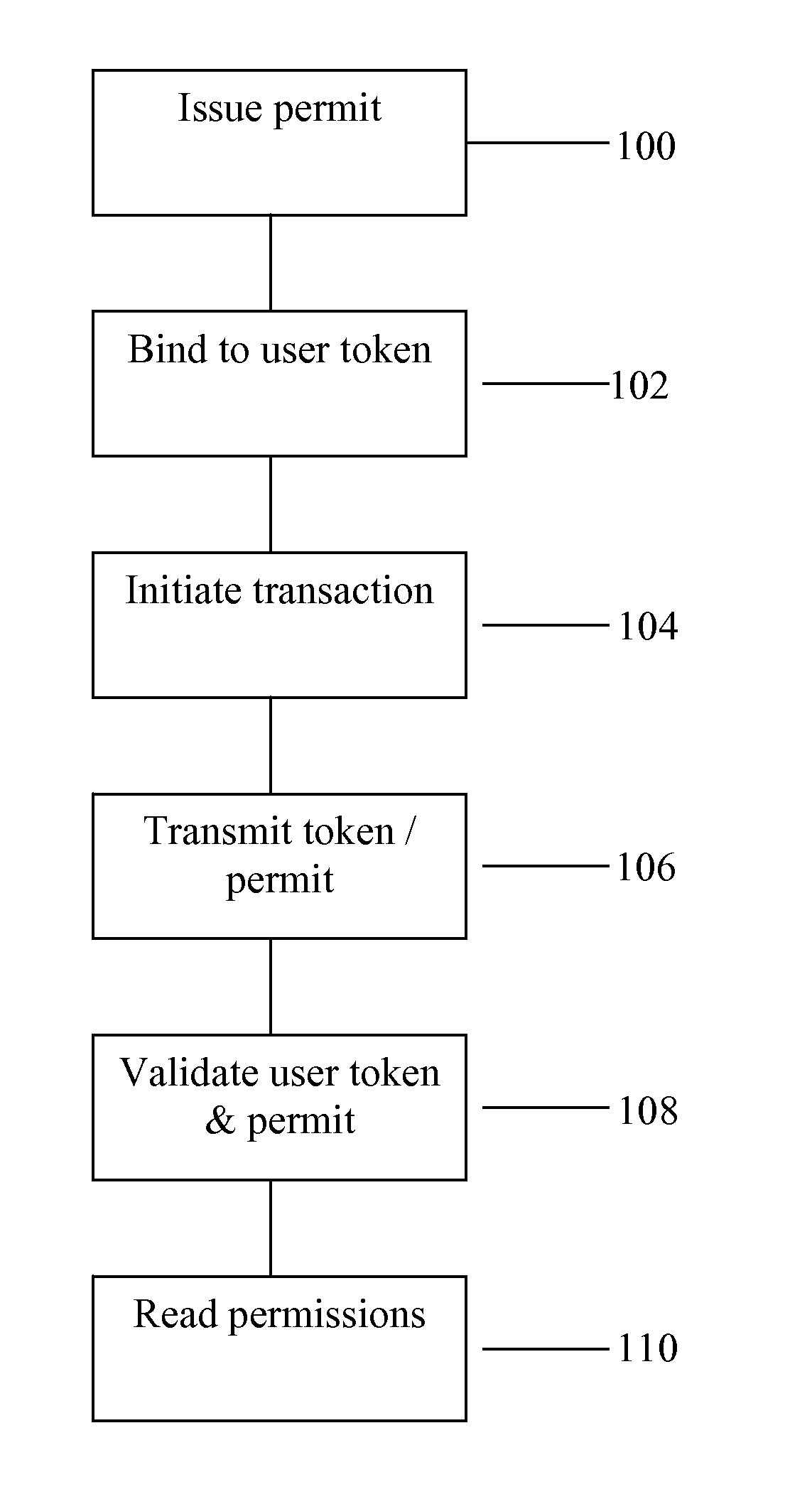
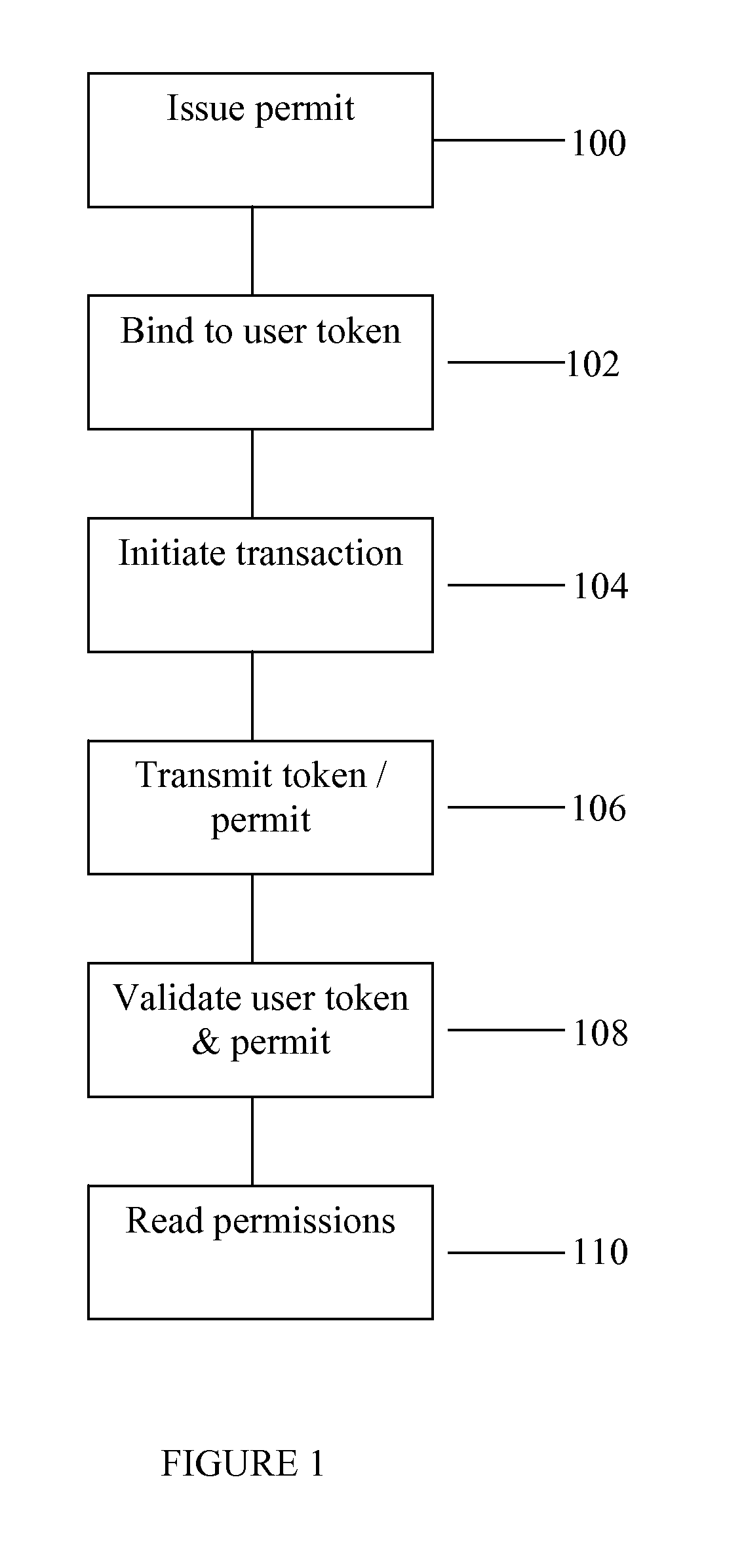
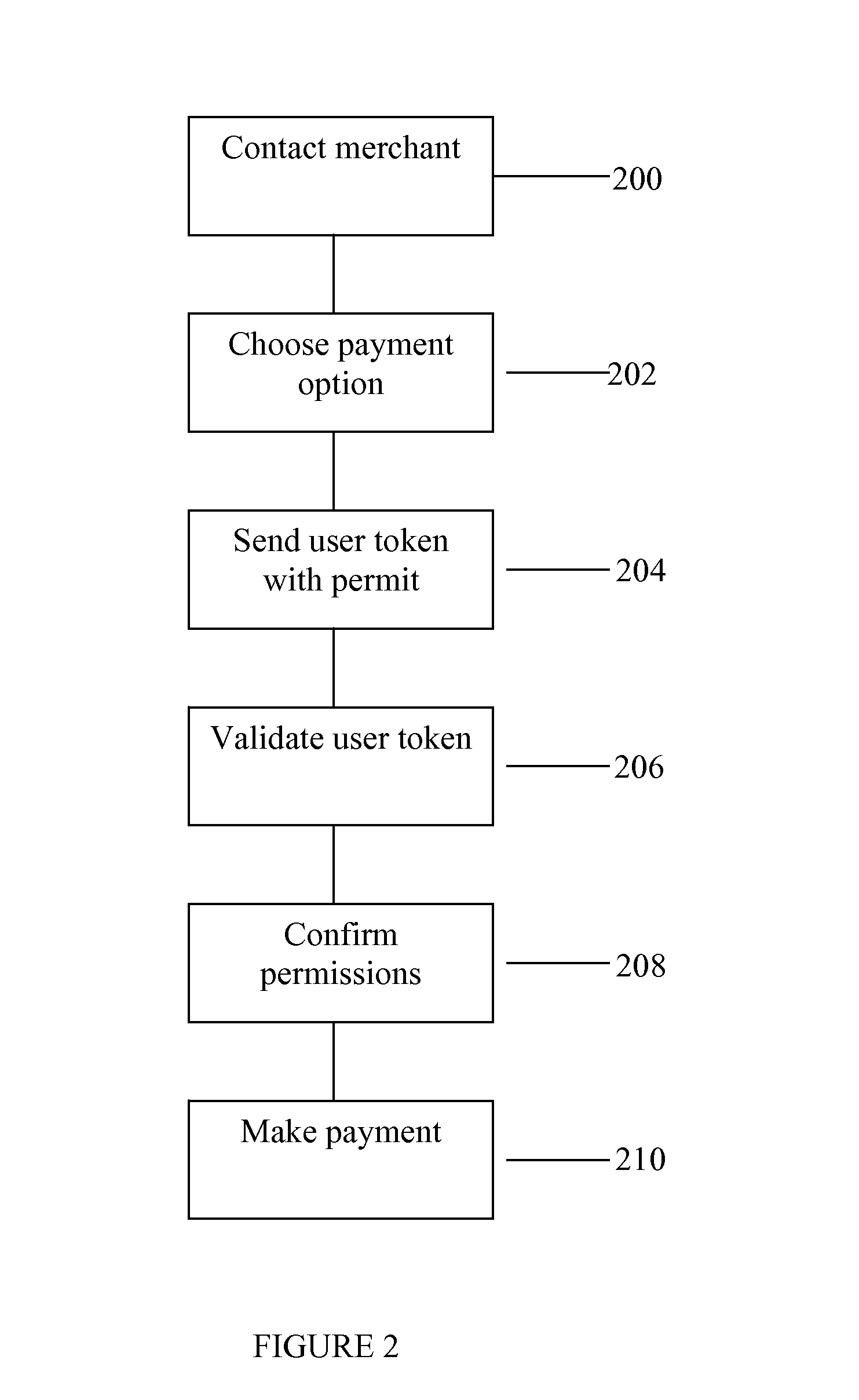
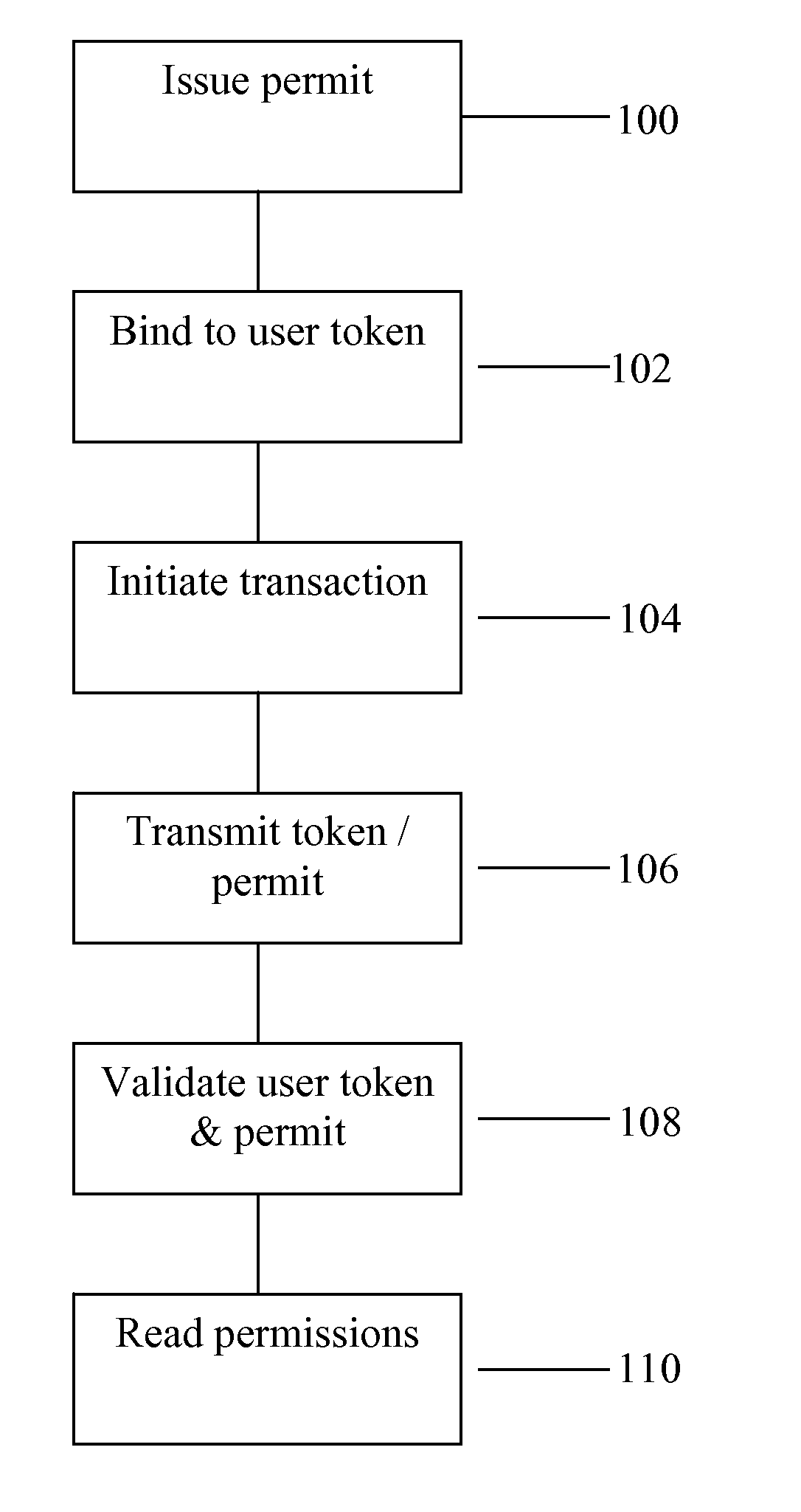
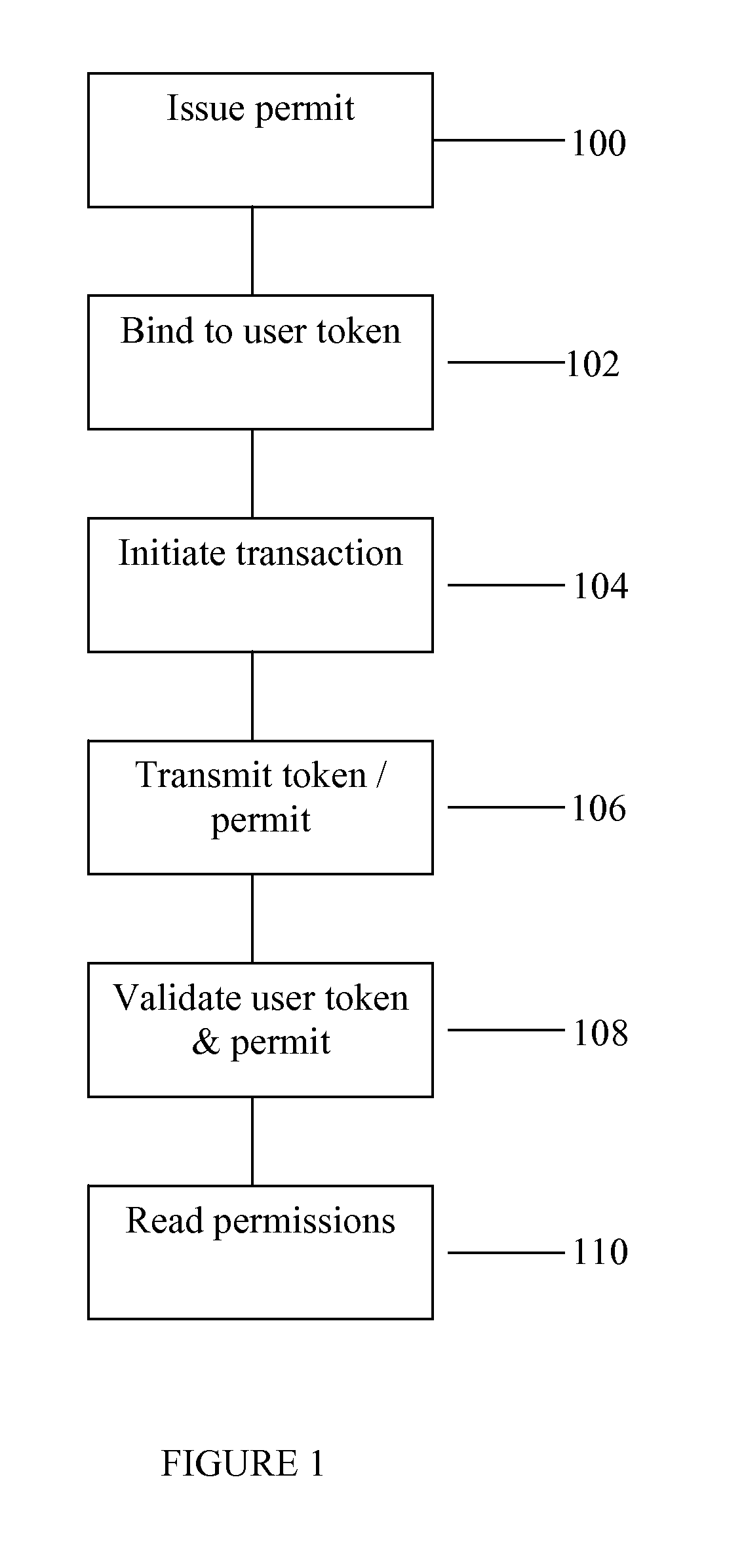
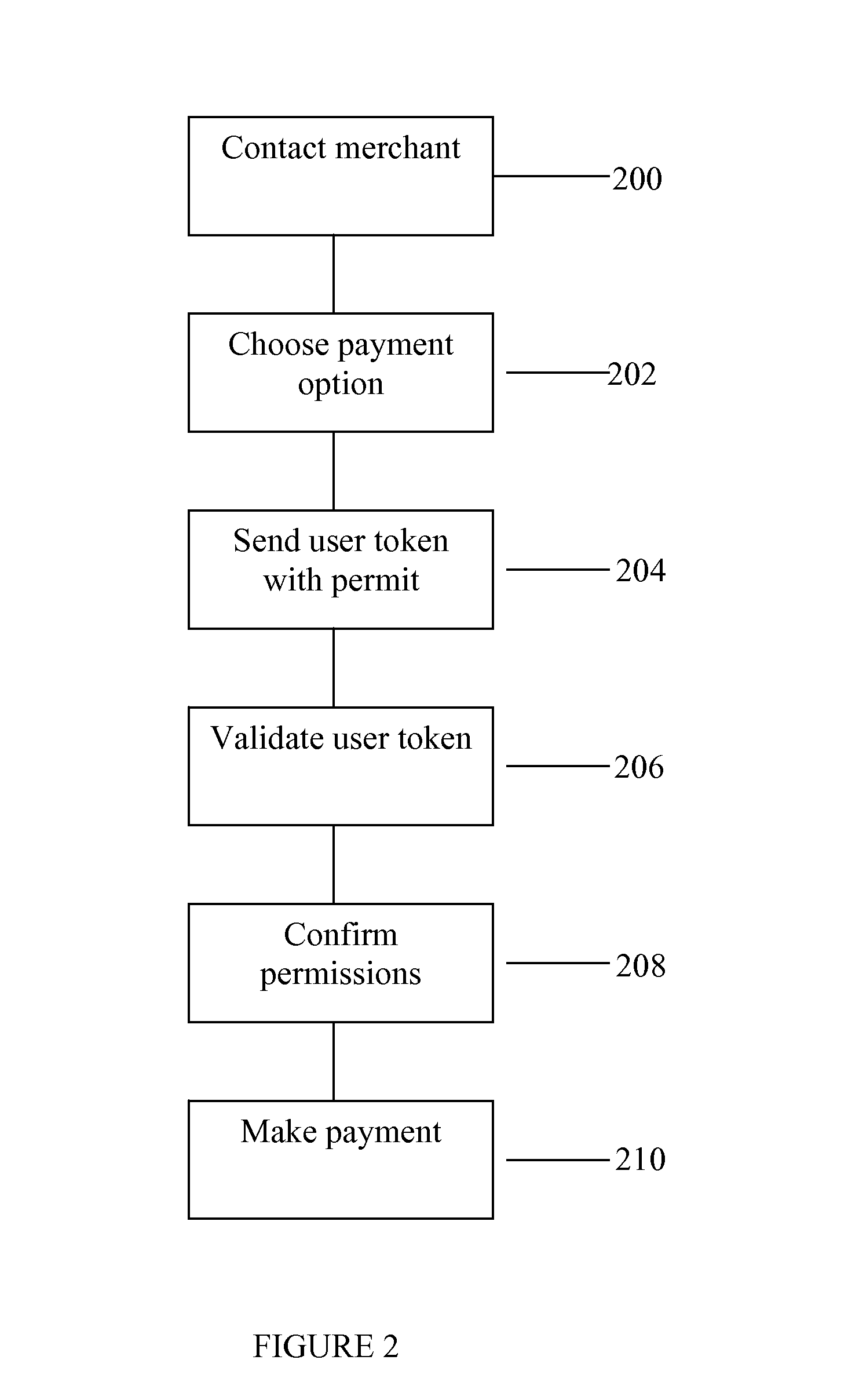
ActiveUS8549602B2Valid verificationDigital data processing detailsUser identity/authority verificationDigital signatureInternet privacy
The invention consists of a method of handling permits, comprising the steps of: (a) providing a user with a user permit linked to a user authentication token, the user permit defining permissions granted to the user and the user token containing identity authentication information for the user; (b) presenting the user token to a gatekeeper to confirm the user's identity; (c) validating the user permit based on the permit issuer's digital signature; and, (d) granting the user access based on said permissions within the user permit.
Owner:IQVIA INC
System and method for handling permits for user authentication tokens
ActiveUS20080127321A1Efficiently validateValid verificationDigital data processing detailsUser identity/authority verificationUser authenticationInternet privacy
The invention consists of a method of handling permits, comprising the steps of: (a) providing a user with a user permit linked to a user authentication token, the user permit defining permissions granted to the user and the user token containing identity authentication information for the user; (b) presenting the user token to a gatekeeper to confirm the user's identity; (c) validating the user permit based on the permit issuer's digital signature; and, (d) granting the user access based on said permissions within the user permit.
Owner:IQVIA INC
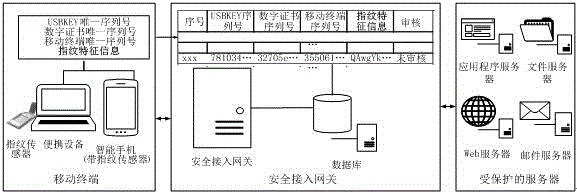
Mobile terminal safety access authentication method in combination with fingerprint
ActiveCN106488452APrevent unauthorized accessEnsure safetyDigital data authenticationSecurity arrangementIdentity recognitionInformation access
The invention provides a mobile terminal safety access authentication method in combination with fingerprint. The method comprises the four steps of establishing an encryption channel, user registering, user information checking and user business accessing. A client collects terminal feature information which comprises a USBKEY sequence number, a digital certificate sequence number, a mobile terminal sequence number and user fingerprint feature information, and the terminal feature information is uploaded to a safety access gateway through the encryption channel; the safety access gateway verifies the integrity and validity of the terminal information, and decides whether the terminal can access a protected server according to a verification result. The fingerprint recognition technology is combined with the traditional identity recognition mode, so that the medium for marking the identity is directly related to the natural person, the identity recognition and the recognized person are really corresponding to each other, the security level of the mobile terminal information access is effectively improved, and the convenient mobile technology can be facilitated to play effect in the information application.
Owner:JIANGSU ELECTRIC POWER CO +1
Picture verification method and device, electronic equipment and computer readable storage medium
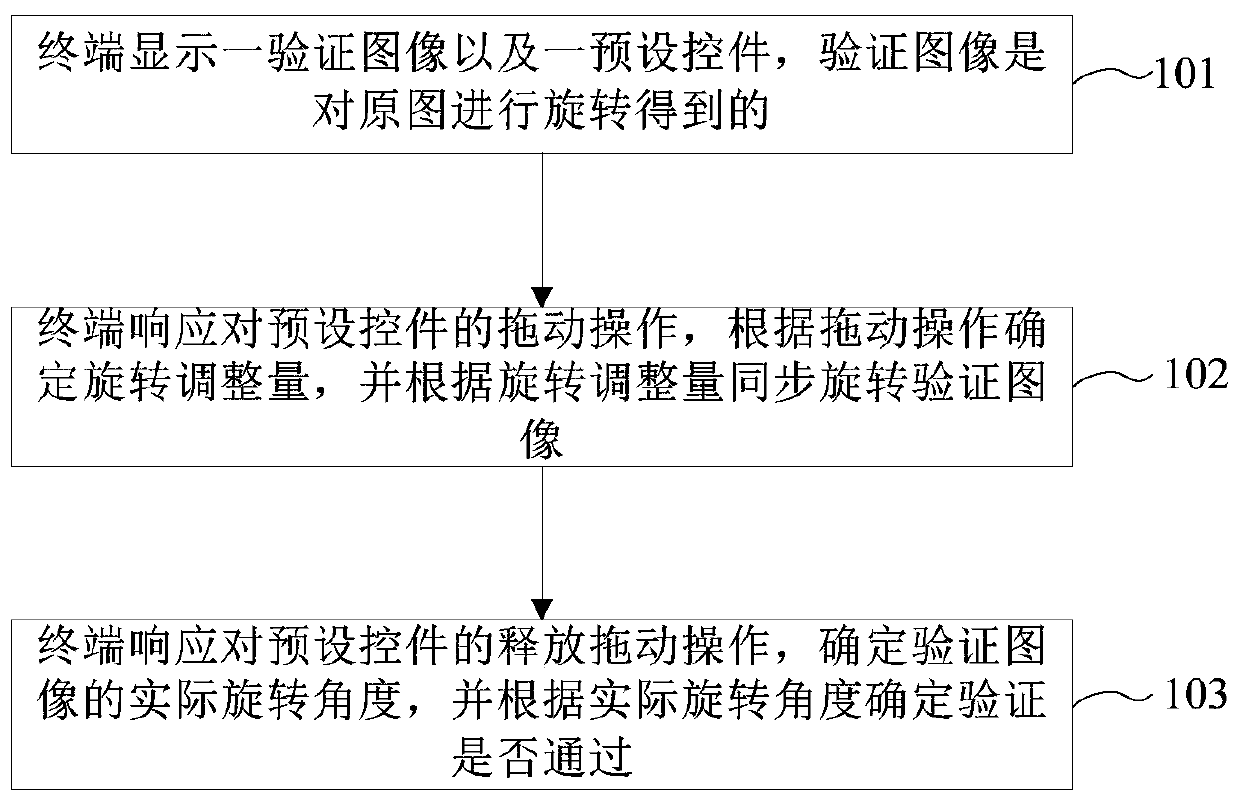
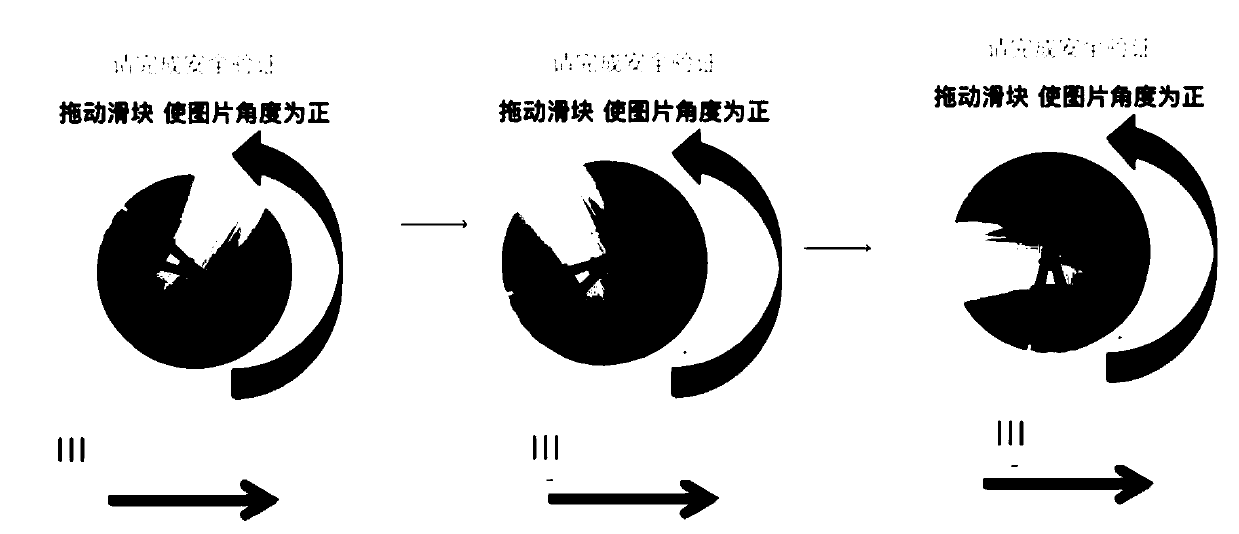
PendingCN110308847AValid verificationEfficient identificationDigital data authenticationInput/output processes for data processingValidation methodsImage identification
The invention provides a picture verification method and device, electronic equipment and a computer readable storage medium. The picture verification method comprises the steps that a terminal displays a verification image and a preset control; the terminal responds to dragging operation on the preset control, determines a rotation adjustment amount according to the dragging operation, and synchronizes the rotation verification image according to the rotation adjustment amount; and the terminal responds to a release dragging operation on the preset control, determines an actual rotation angleof the verification image, and determines whether the verification is passed or not according to the actual rotation angle. According to the scheme provided by the invention, the rotated image is used as the verification code, and verification can be realized in a mode of rotating the verification image by a user. As the verification code does not comprise the verification result, the verification result corresponding to the verification code cannot be directly determined in an image recognition mode. When a verification result is input, the rotation mode has various possibilities, so that the machine cannot be cracked by multiple attempts, and malicious machine flow can be effectively identified by the mode.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
Equipment for continuously producing adhesive non-woven fabric web
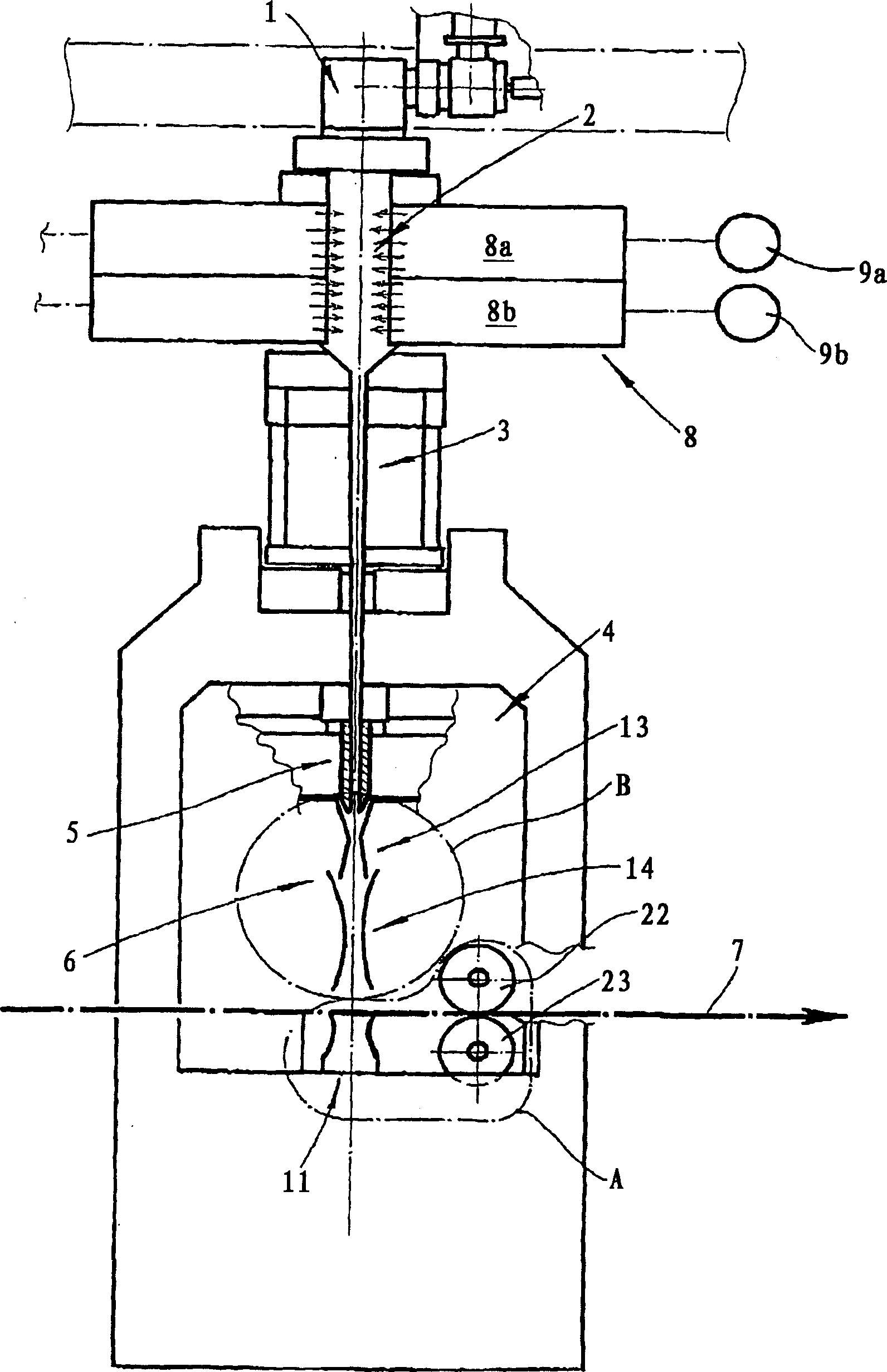
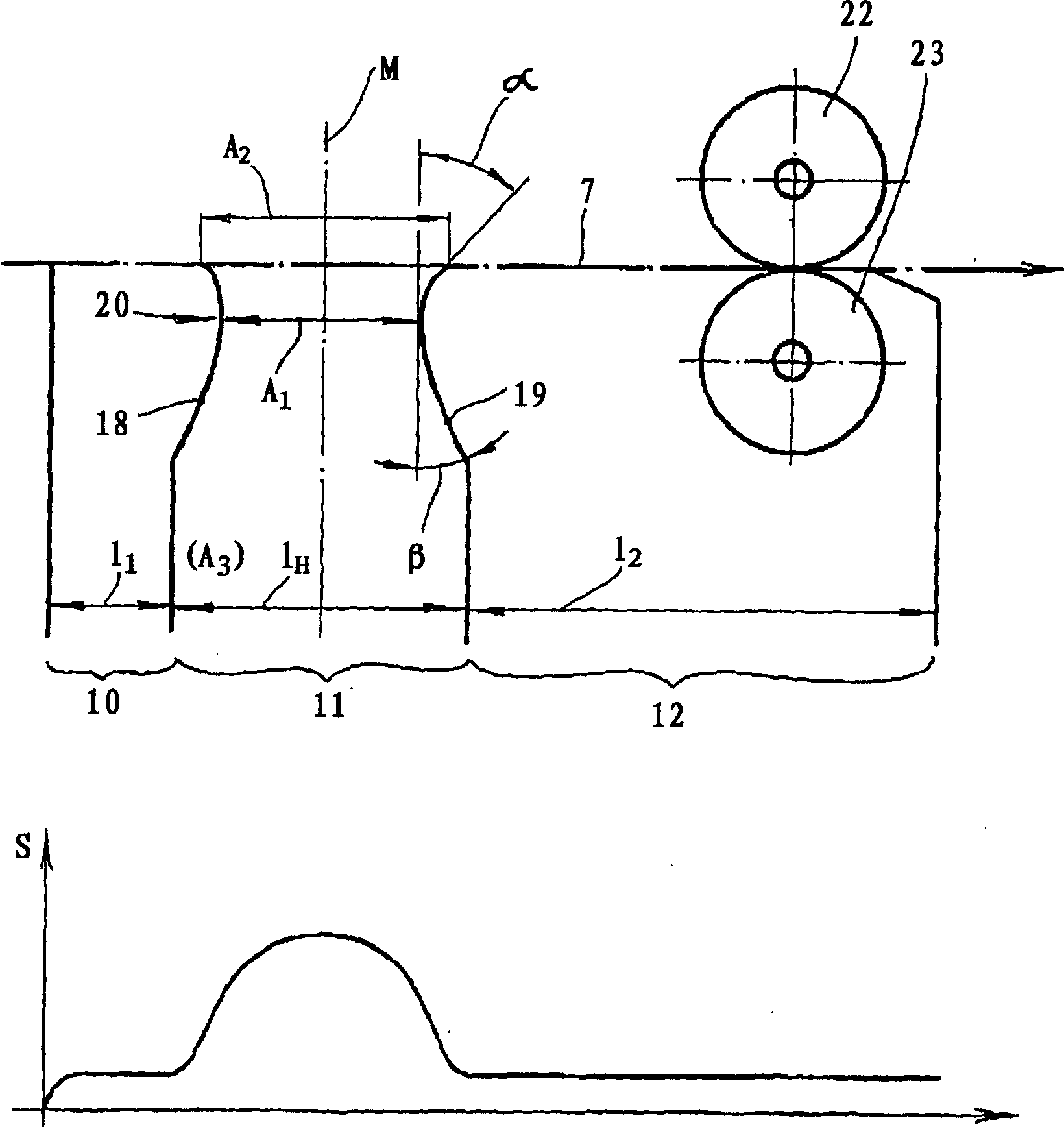
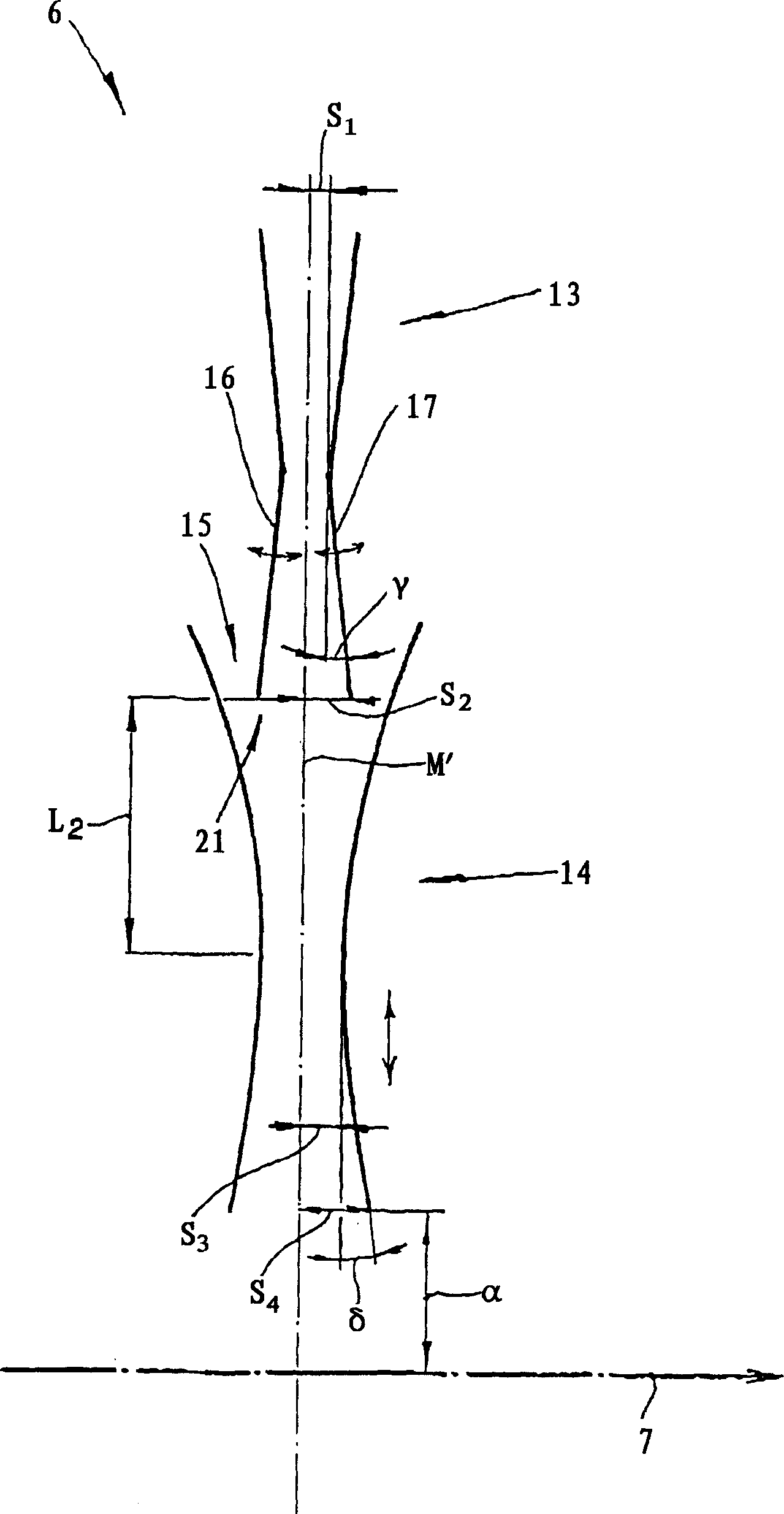
InactiveCN1441105AEffective delivery reliabilityFunction increaseMelt spinning methodsNon-woven fabricsThermoplasticWoven fabric
A spun-bond web production apparatus comprises a spinneret for producing descending thermoplastic synthetic resin filaments; receiving device for receiving filaments; continuously movable collecting foraminous belt; and at least two mutually independently controllable suction zones beneath the belt for drawing air and including a primary suction zone at which a greater part of the filaments are drawn onto the belt. A spun-bond web production apparatus comprises a spinneret (1) for producing descending thermoplastic synthetic resin filaments; receiving device below the spinneret and receiving filaments for aerodynamically stretching the filaments; continuously movable collecting foraminous belt (7) displaceable longitudinally in a web-producing direction below the receiving device to produce a spun-bond web; and at least two mutually independently controllable suction zones (11) beneath the belt for drawing air through and in succession in the web-producing direction, and including a primary suction zone at which a greater part of the filaments are drawn onto the belt and at least one other suction zone.
Owner:莱芬豪舍有限责任两合公司机器制造厂
System and method for verifying E-mail password
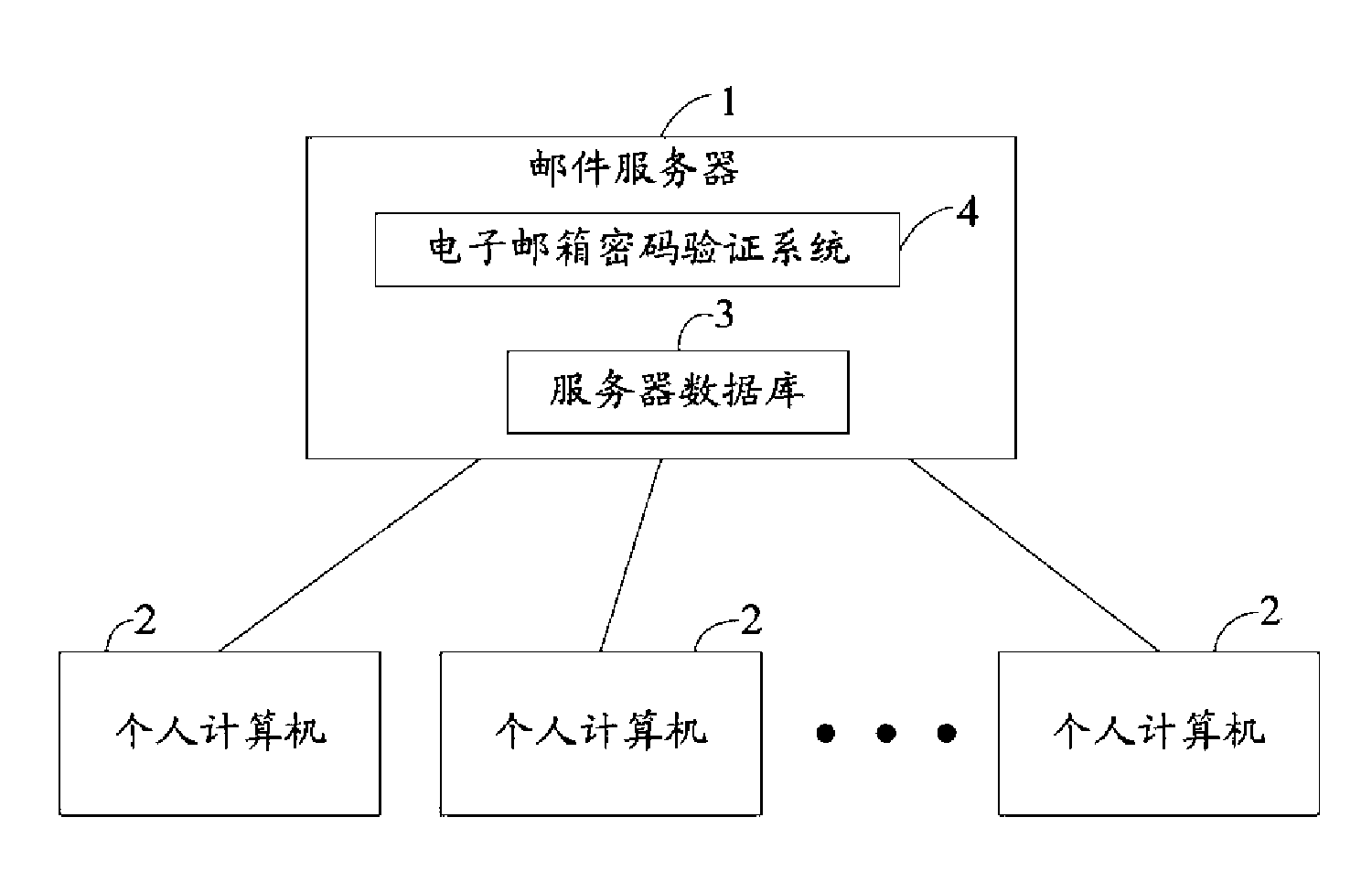
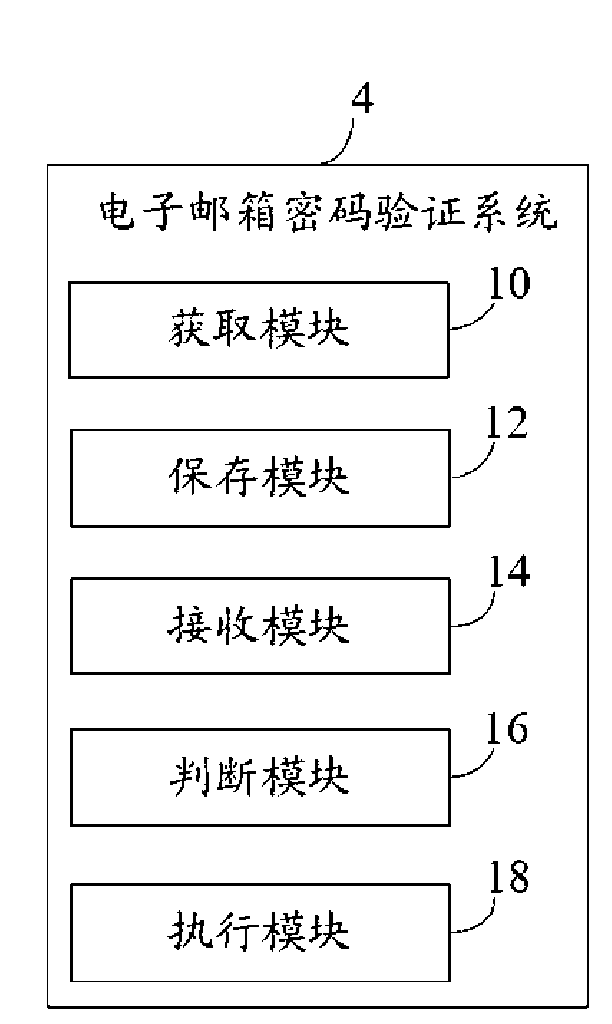
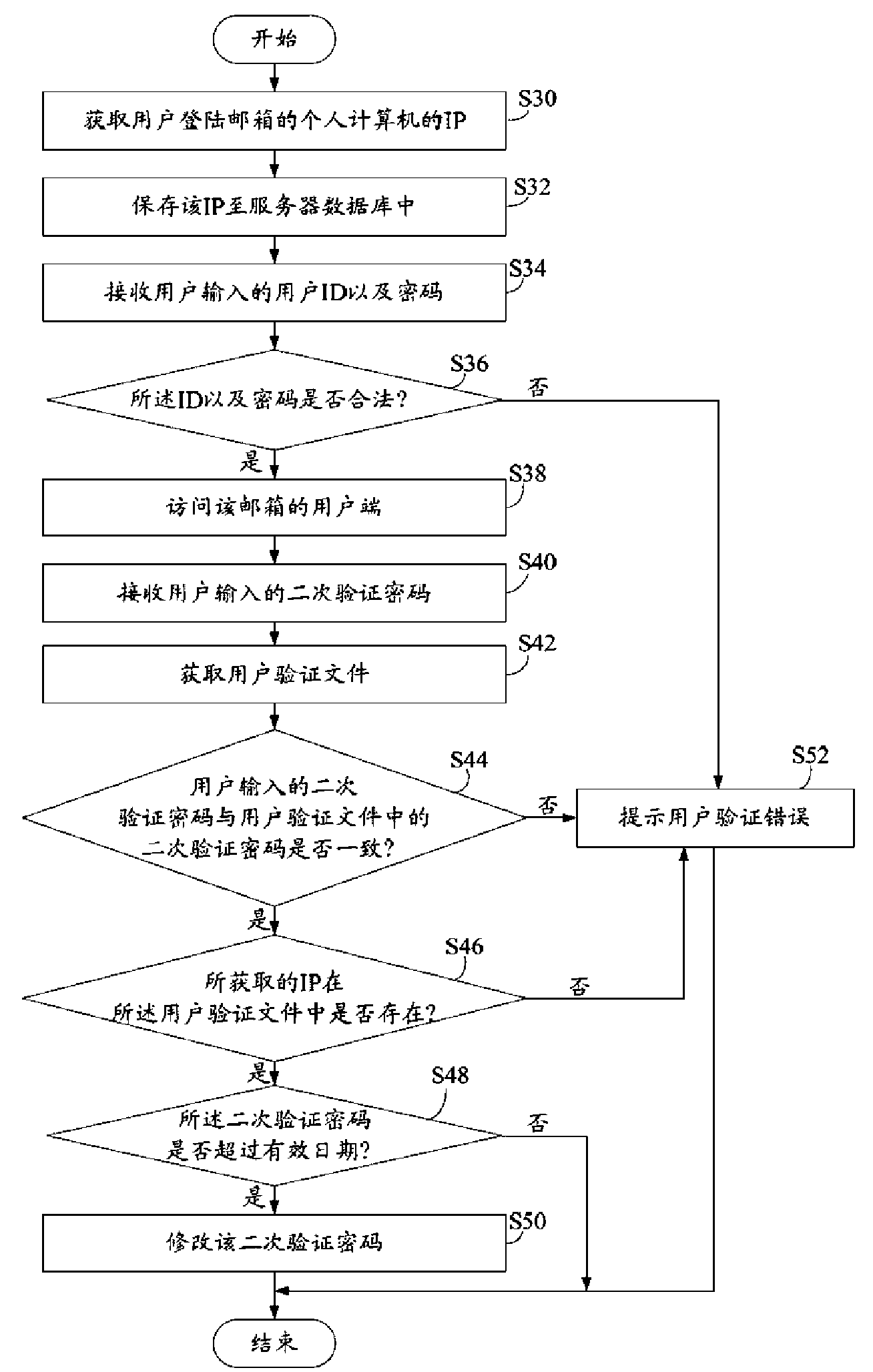
InactiveCN101594350AAvoid lossValid verificationUser identity/authority verificationComputer security arrangementsUser verificationPassword
The invention provides a method for verifying an E-mail password, which comprises the following steps: receiving ID and a password input by a user; judging whether the received ID and the password are legal; promoting the user that the password is verified to be wrong when the ID and the password are illegal, and logging out; or if the ID and the password are illegal, accessing a user end of an E-mail; receiving a secondary verification password input by the user; acquiring a user verification file from a server database; when the secondary verification password input by the user accords with a secondary verification password of the user verification file, accessing the E-mail; or the secondary verification password input by the user does not accord with the secondary verification password in the user verification file, promoting the user that the password is verified to be wrong. In addition, the invention also provides a system for verifying the E-mail password.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
Method used for detecting display panel
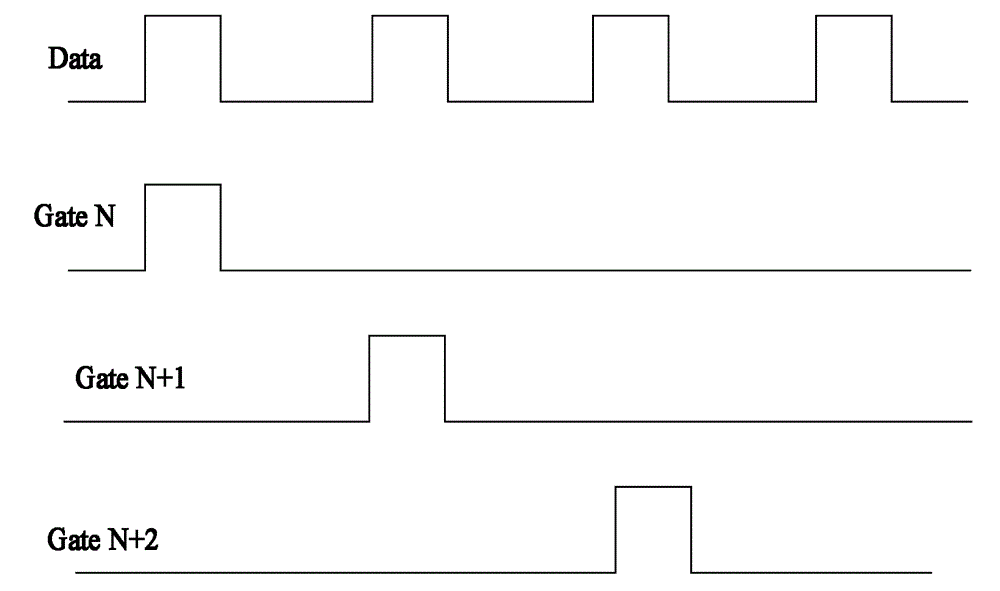
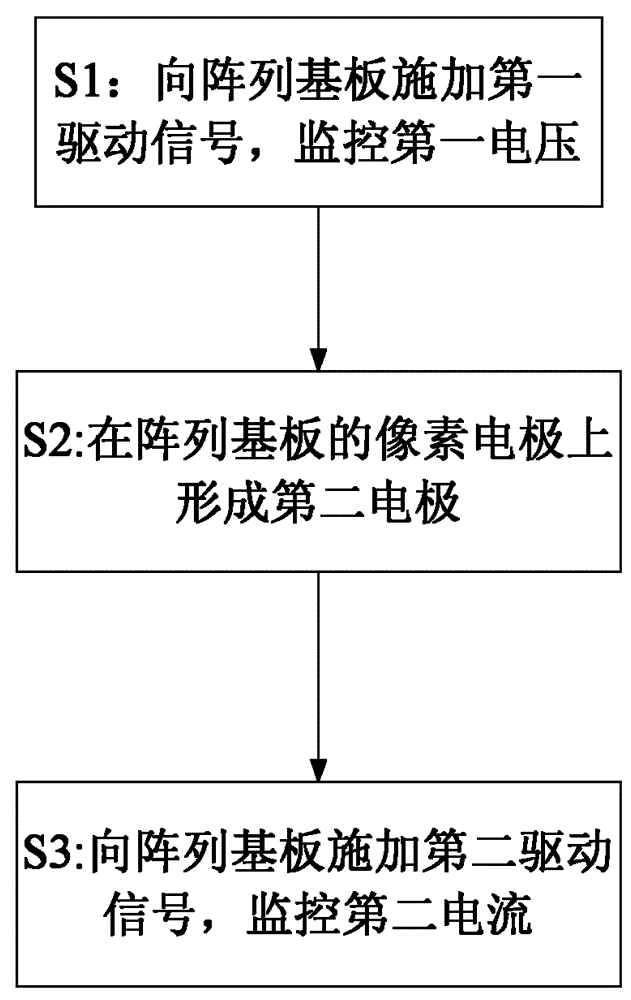
ActiveCN104809970AImprove reliabilityEfficient use ofSemiconductor/solid-state device testing/measurementStatic indicating devicesElectricityPower flow
The invention discloses a method used for detecting a display panel. The display panel comprises an array substrate used for driving an electroluminescent device, wherein the array substrate comprises pixel electrodes arranged in an array and a pixel switch array used for driving the pixel electrodes. The method comprises the following steps: S1) applying a first driving signal to the manufactured array substrate, and monitoring first voltage on the pixel arrays; S2) forming a second electrode on each pixel electrode of the array substrate; S3) applying a second driving signal to the array substrate on which the second electrode is formed, and monitoring second current which flows the second electrode, wherein each pixel electrode is one of the cathode and the anode of the electroluminescent device, and each second electrode is the other one of the cathode and the anode of the electroluminescent device. According to the method, an organic luminescent layer does not need to be manufactured, and therefore, the cost of the whole detection process is greatly lowered. Meanwhile, interference brought by new defects which may be introduced in the manufacture of the organic luminescent layer is eliminated, a detection process of the display panel is simplified, detection complexity is lowered, and the method is favorable for improving detection efficiency.
Owner:BOE TECH GRP CO LTD
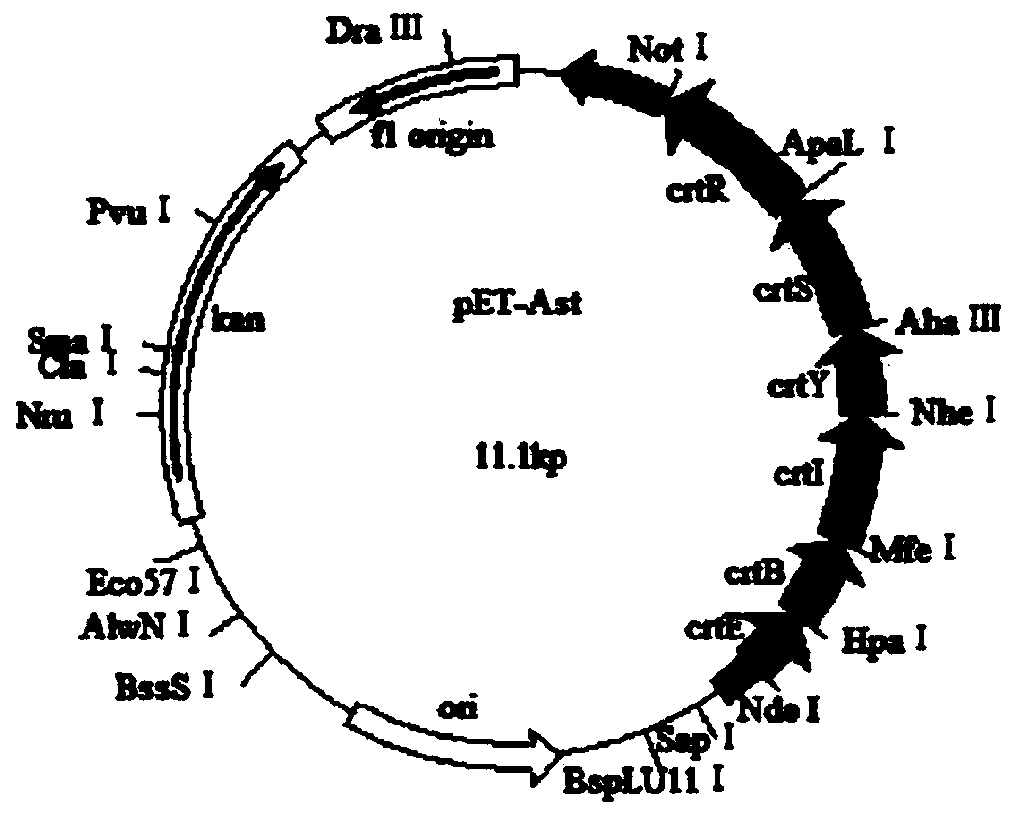
Astaxanthin synthetic gene recombinant plasmid as well as preparation method and application of astaxanthin synthetic gene recombinant plasmid
InactiveCN103805623ARealize accumulationBuild accuratelyMicrobiological testing/measurementVector-based foreign material introductionAstaxanthinBetaxanthins
The invention discloses an astaxanthin synthetic gene recombinant expression plasmid pET-Ast with a base sequence as shown in SEQ ID NO: 1. The invention also discloses a preparation method of the recombinant expression plasmid pET-Ast, an application of the recombinant plasmid pET-Ast to the detection of astaxanthin synthetase activity of a target receptor, and an application method. After the astaxanthin synthetic gene recombinant expression plasmid pET-Ast provided by the invention is introduced to an Escherichia coli BL21 strain, the accumulation of astaxanthin in a cell body of Escherichia coli is successfully realized, so that an astaxanthin production strain can be accurately and rapidly established. The preparation method of the astaxanthin synthetic gene recombinant expression plasmid pET-Ast is simple and convenient, easy to operate and low in cost. By using the method disclosed by the invention, a gene sequence to be detected in the target receptor can be replaced with a related gene sequence in the recombinant expression plasmid pET-Ast through digestion and connection, and then, the function of a gene to be detected in the target receptor can be simply and effectively detected and verified through detecting whether the astaxanthin is accumulated in a host cell body.
Owner:HEBEI UNIVERSITY
Comprehensive testing platform for high-resolution jogging target imaging system
The invention discloses a comprehensive testing platform for a high-resolution jogging target imaging system. The platform comprises a microwave darkroom; a target model; a target movement platform which is located on a platform substrate of the microwave darkroom, and is used for bearing the target model and driving the target model to move and to rotate on the target movement model; an antenna system which is used for receiving and transmitting electromagnetic waves, is located on a side surface of a moving track of the target movement platform, and moves towards the target model; a microwave assembly which is used for carrying out the echo amplitude and phase measurement of the target model and collecting the imaging data; and a controller which is used for controlling the target movement platform and the antenna system. The platform provided by the invention can truly simulate the spatial movement posture of a load, and the high-resolution imaging system carries out the measurement of the target, and completes the strip-type two-dimensional imaging measurement of a jogging target. The platform can achieve the effective verification and / or testing of and ISAR mechanism.
Owner:BEIJING INST OF ENVIRONMENTAL FEATURES
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com