Picture verification method and device, electronic equipment and computer readable storage medium
A technology for image verification and image verification, which is applied in the field of verification codes, can solve the problems of being unable to effectively block malicious machine traffic, verification codes being easily cracked by machines, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
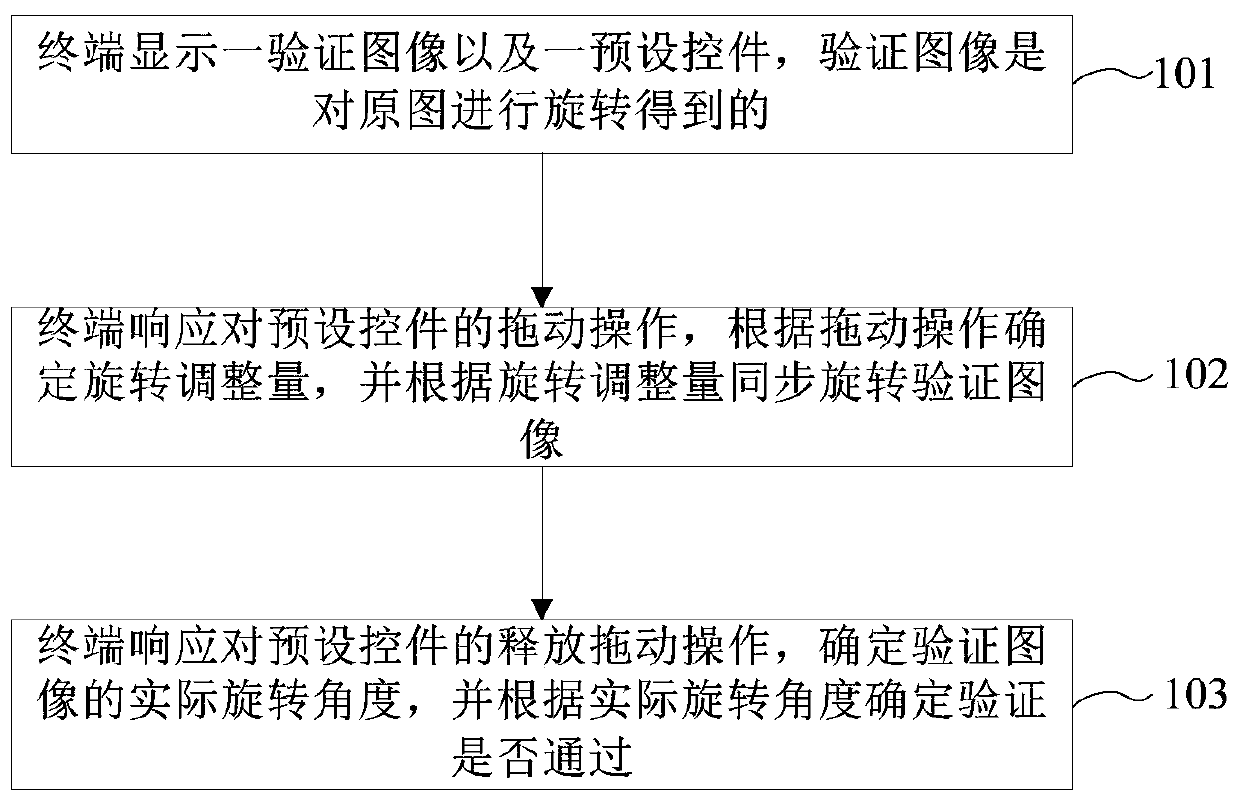
[0044] At present, when a terminal uses some Internet applications, it needs to input a correct verification code before it can use the services provided by the Internet applications. By identifying whether the verification code is correct or not, it is judged whether the user operating the terminal is a real user, thereby blocking malicious machine traffic. Therefore, the input mechanism and identification mechanism of the verification code determine whether the scheme of inputting the verification code can effectively block the flow of malicious machines.
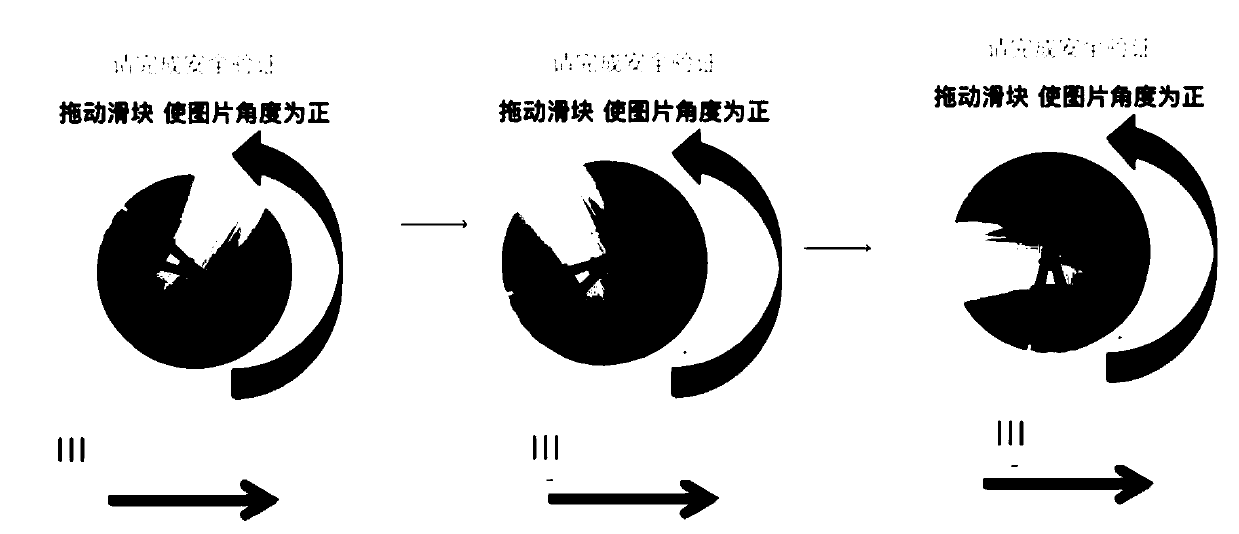
[0045] In the solution provided by the embodiment of the present invention, the rotated image is used as the verification code, and the user needs to operate the terminal to rotate the verification code so that it conforms to the orientation of the terminal, for example, the image is in the forward direction. The rotated image is used as the verification code, so that the verification code itself does not include the veri...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com