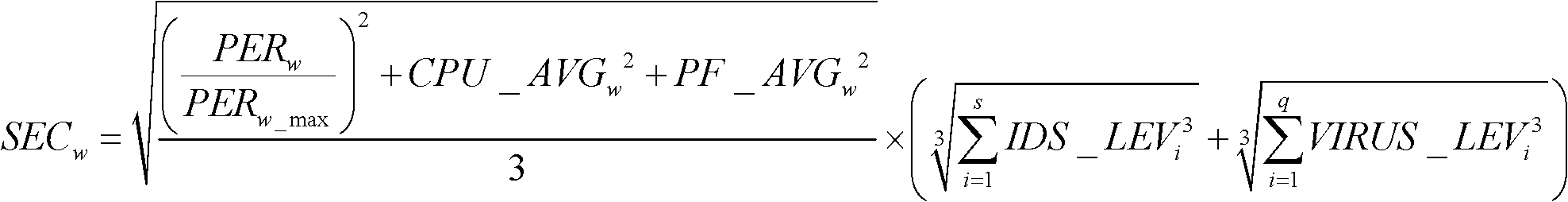Network security situation evaluation method
A situation assessment and network security technology, applied in the field of network security, can solve the problems of unreasonable design of network security situation assessment algorithm, difficult network security management command, decision-making, single data source, etc., and achieve comprehensive network security situation assessment results. The evaluation results are intuitive and practical, and the evaluation results are accurate.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
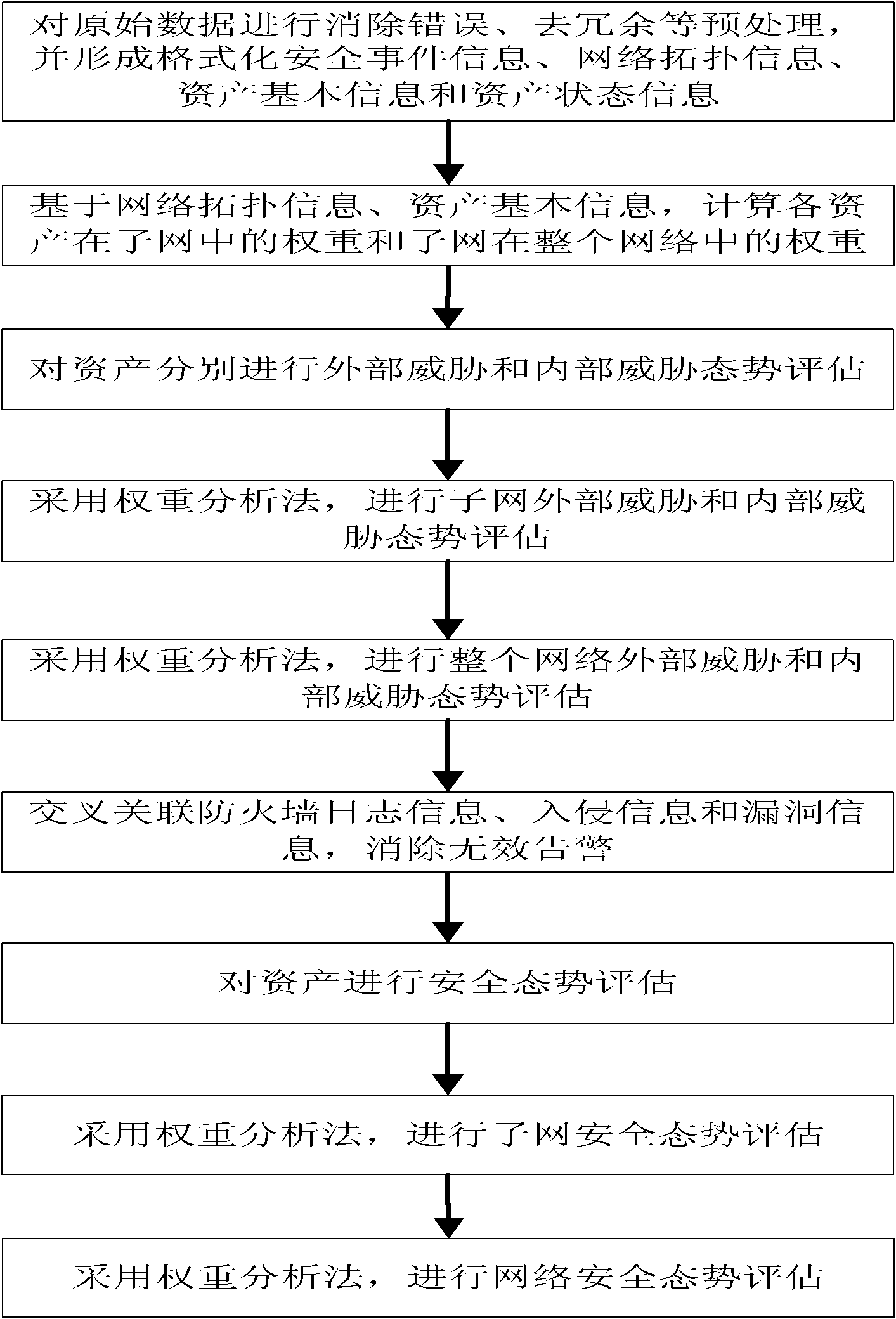
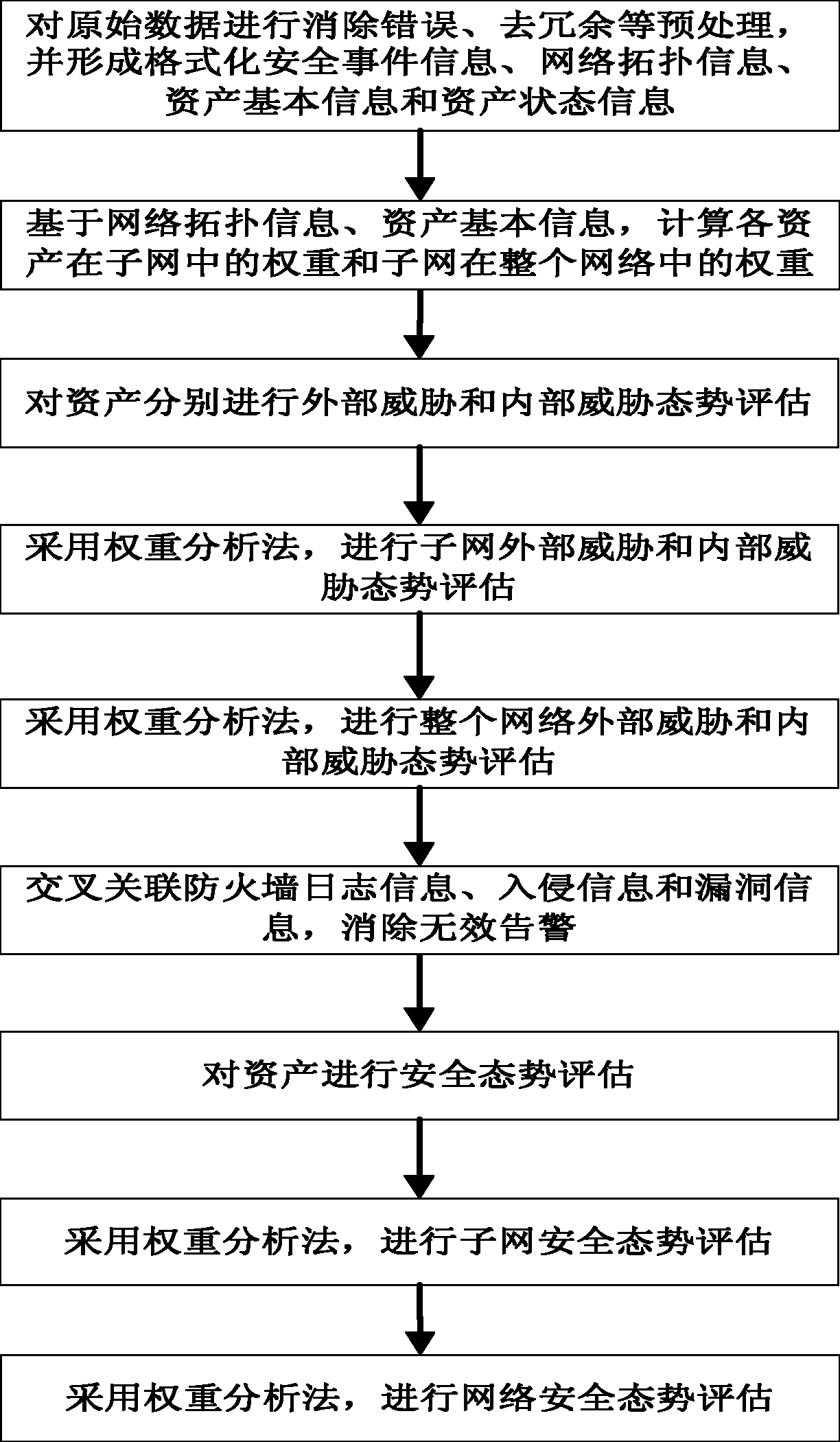
[0053] The preferred embodiments will be described in detail below in conjunction with the flow charts. It should be emphasized that the following descriptions are only illustrative, not intended to limit the scope of the present invention and its application.
[0054] Step 1: Preprocess the raw data, eliminate duplicate information and error information, and generate formatted security event information, network topology information, basic asset information, and asset status information.
[0055] Data sources used for network security situation assessment include firewalls, intrusion detection systems, antivirus software, vulnerability scanning systems, topology discovery tools, performance collection tools, etc. After removing redundancy and eliminating error information, it is formatted to form security event information, network topology information, basic asset information, and asset status information.
[0056] Security event information is mainly divided into firewall l...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com