Network vulnerability evaluation method
A vulnerability and network technology, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve the problem of difficulty in ensuring the accuracy of vulnerability assessment, and achieve the effect of improving accuracy and avoiding serious consequences.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
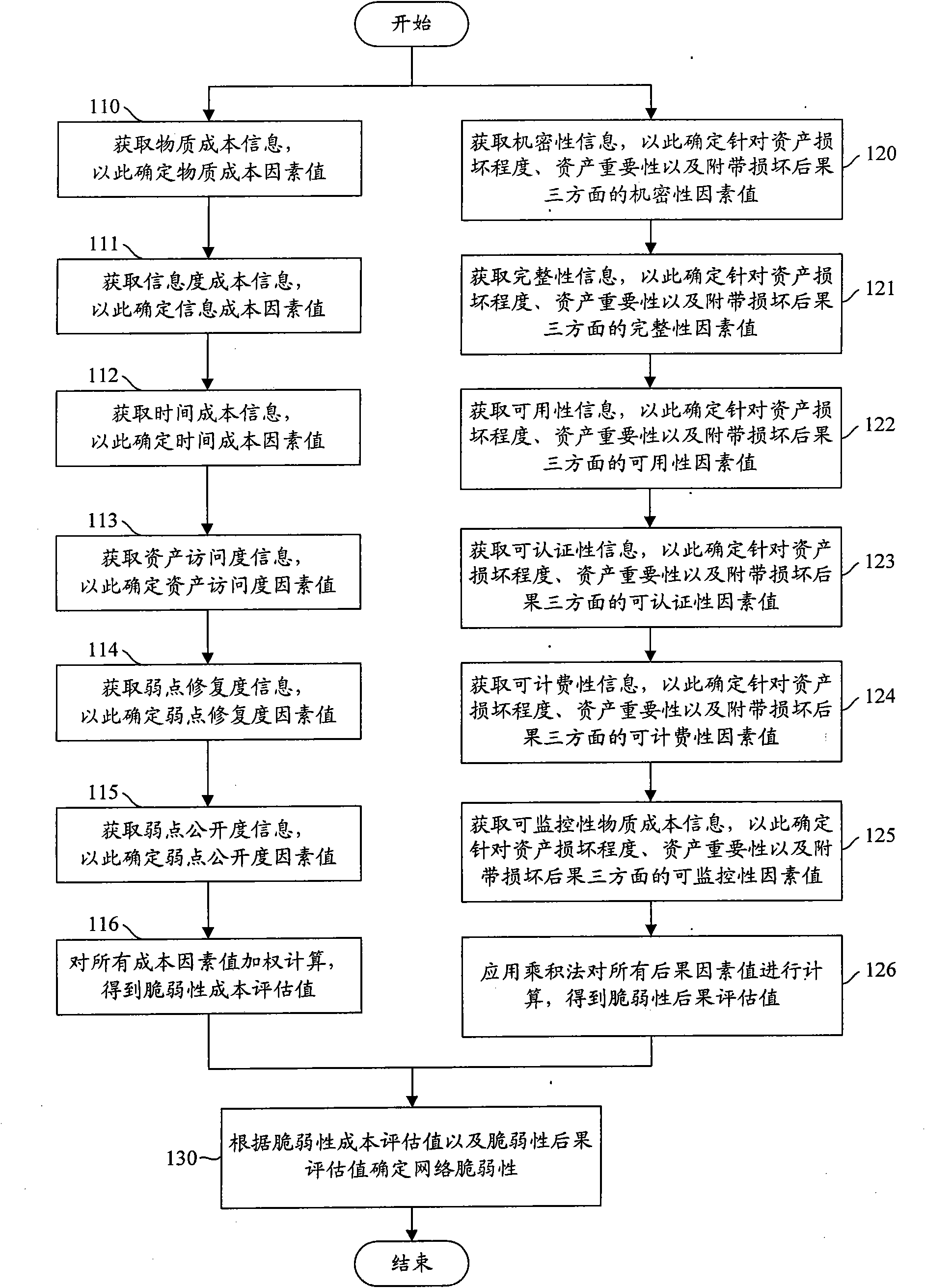
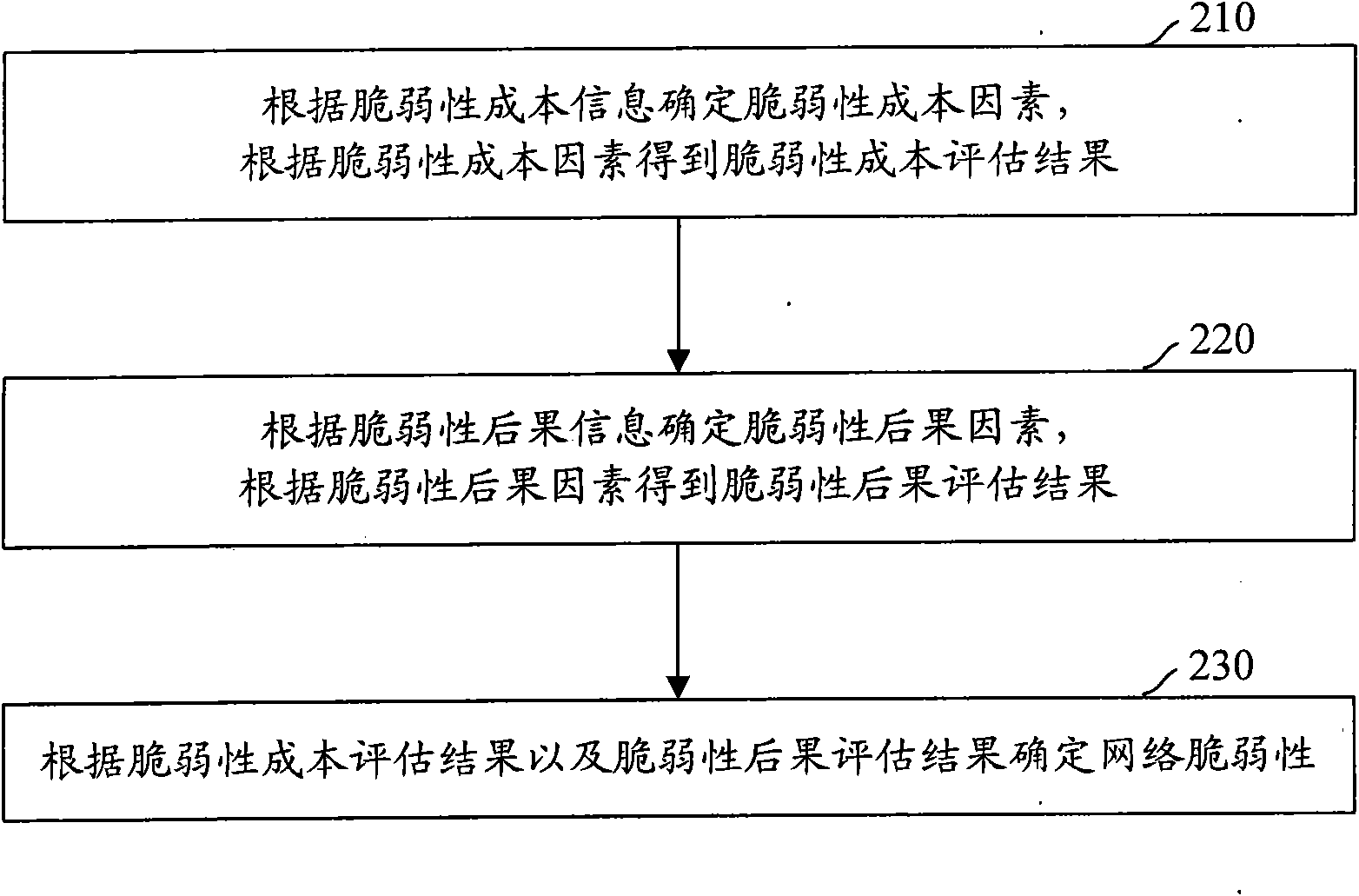
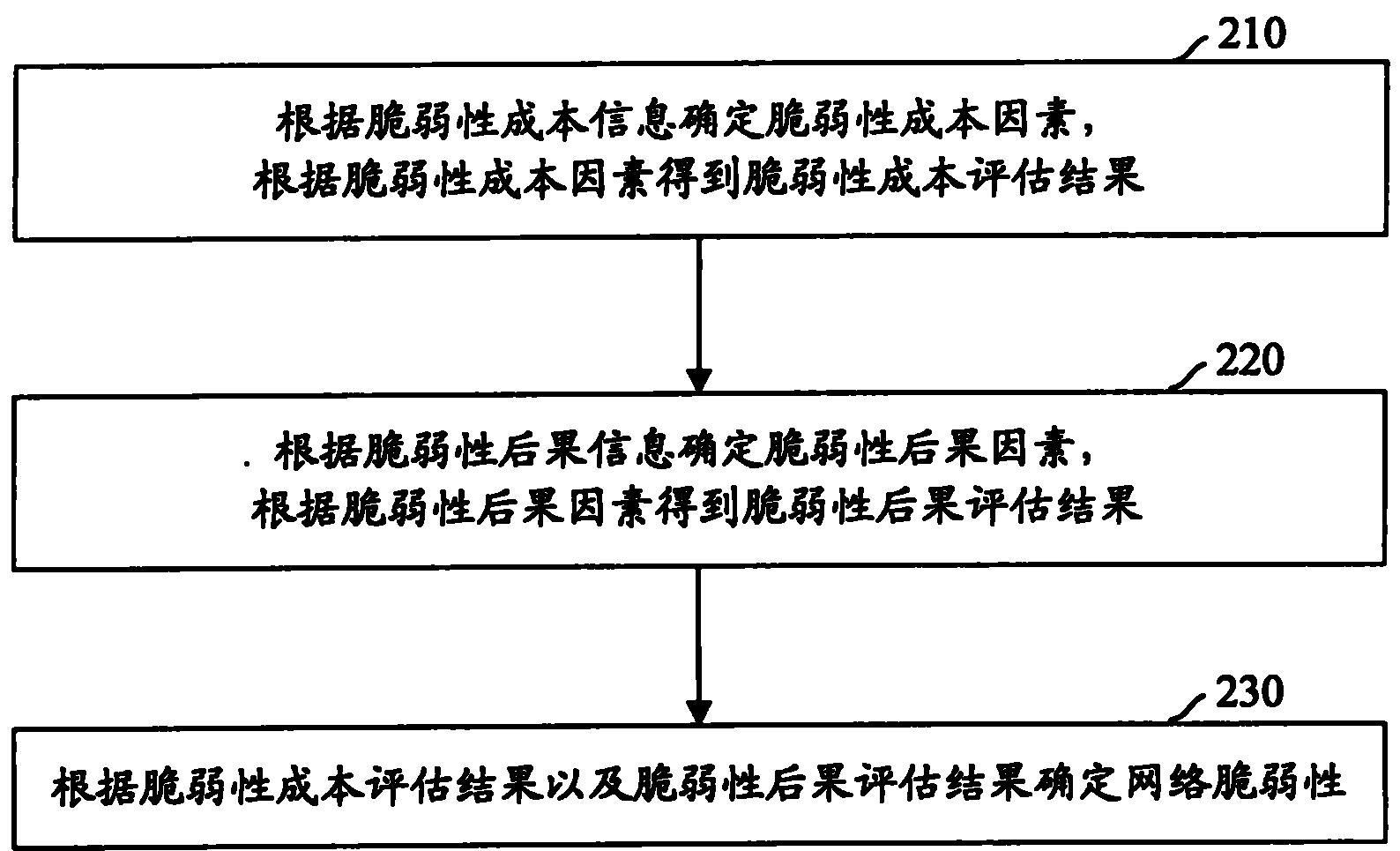
[0040] Generally speaking, the network vulnerability assessment method provided by the present invention includes: determining the vulnerability cost factors according to the vulnerability cost information, obtaining the vulnerability cost assessment results according to the vulnerability cost factors; determining the vulnerability consequence factors according to the vulnerability consequence information , get the vulnerability consequence assessment result according to the vulnerability consequence factor; determine the network vulnerability according to the vulnerability cost assessment result and the vulnerability consequence assessment result.
[0041] Regarding the factors to be considered when conducting network assessments, we can focus on considering the material cost and time cost of exploiting vulnerabilities, which do not seem to be directly related to the vulnerability, but actually affect the exploitability of the vulnerability. In addition, although no one has cl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com