Patents
Literature
4350 results about "Personal security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
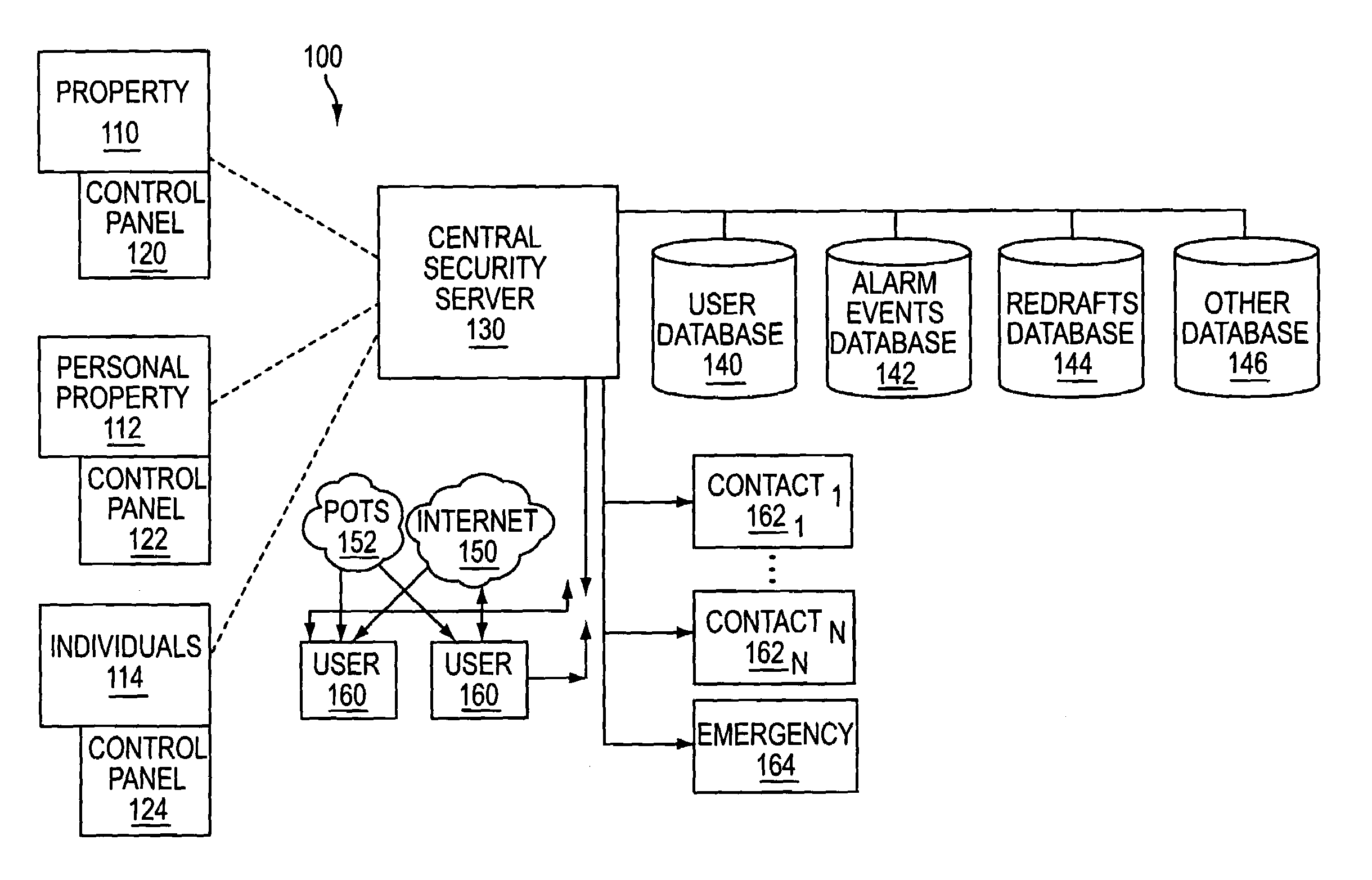
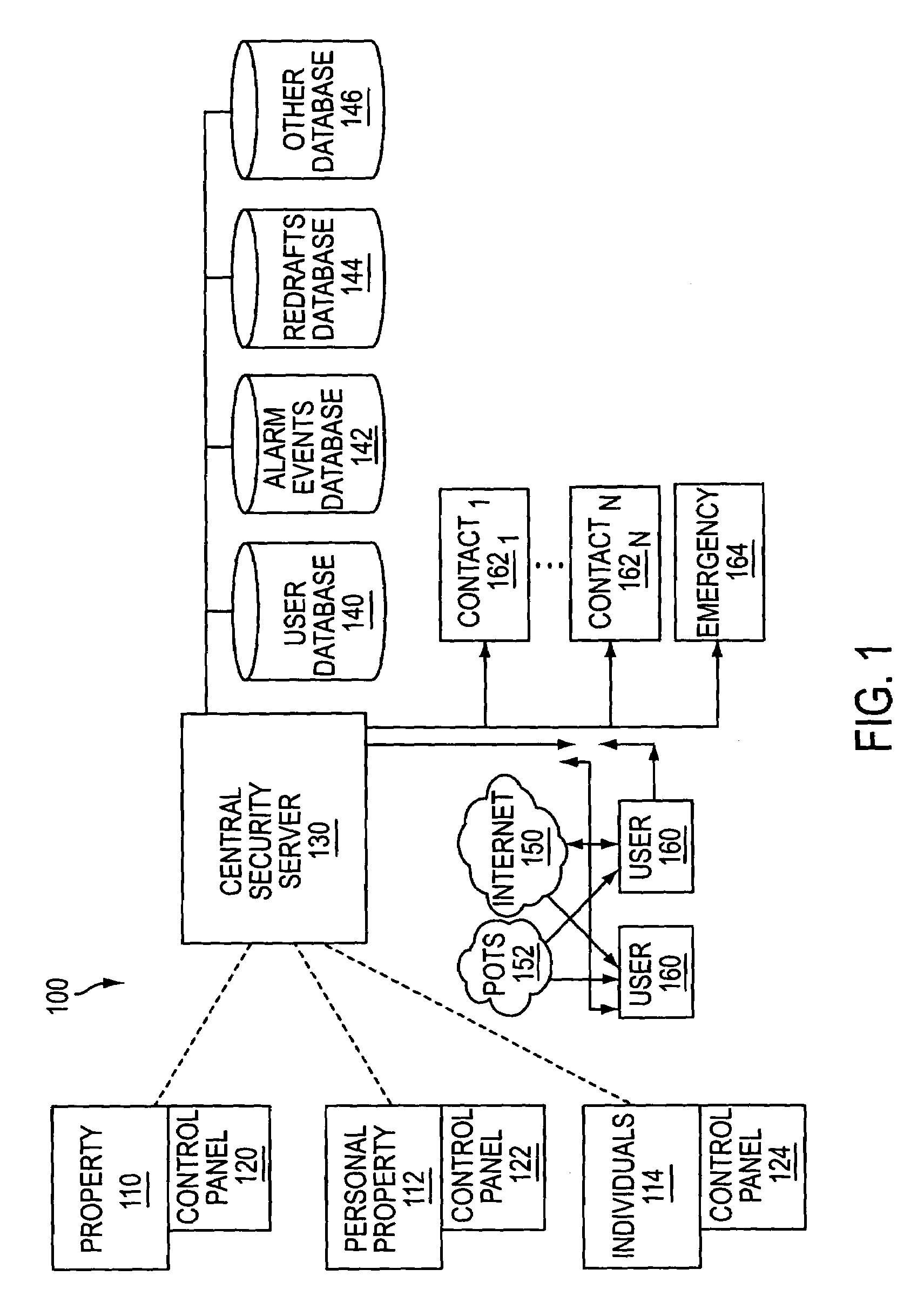
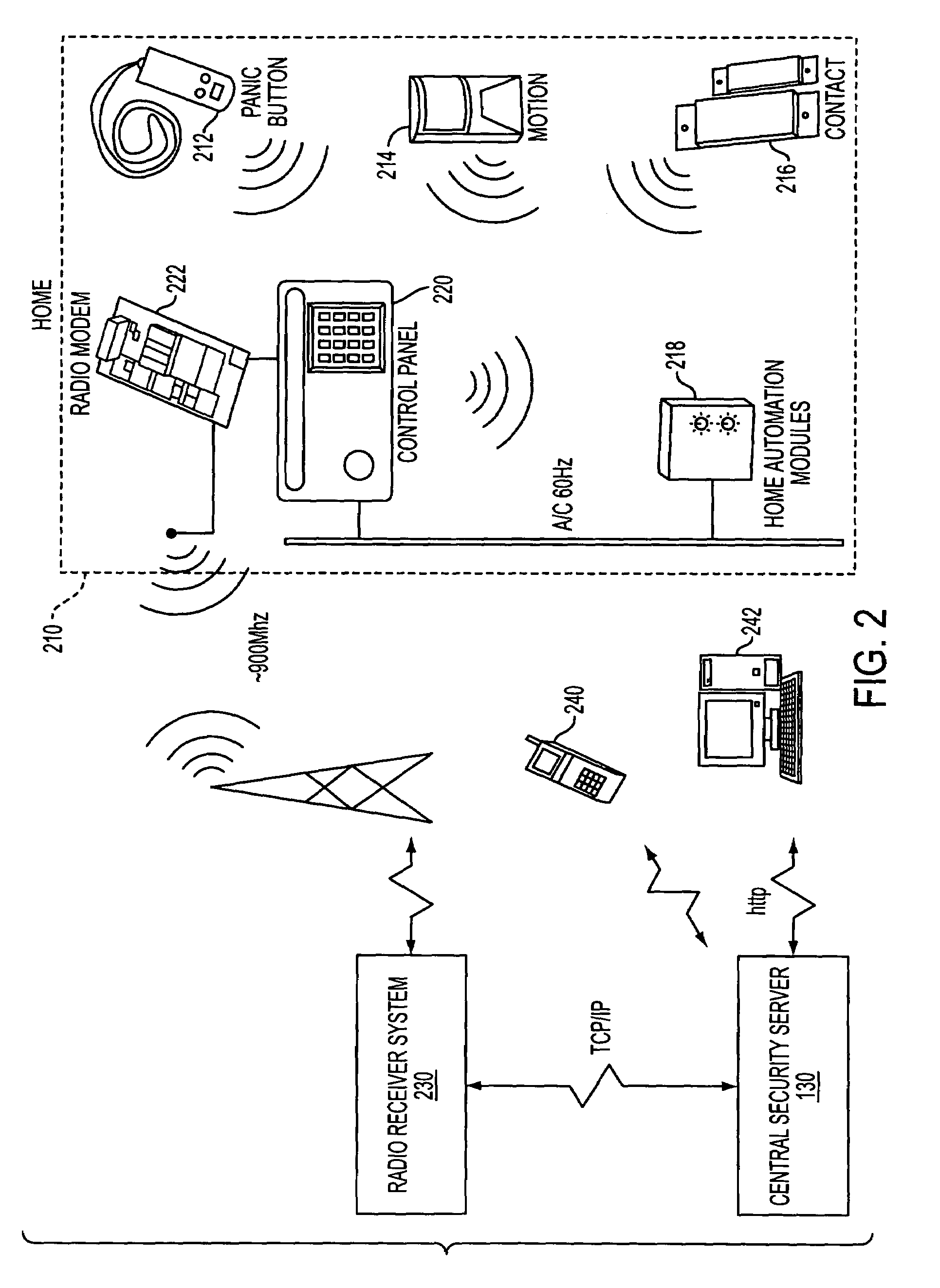
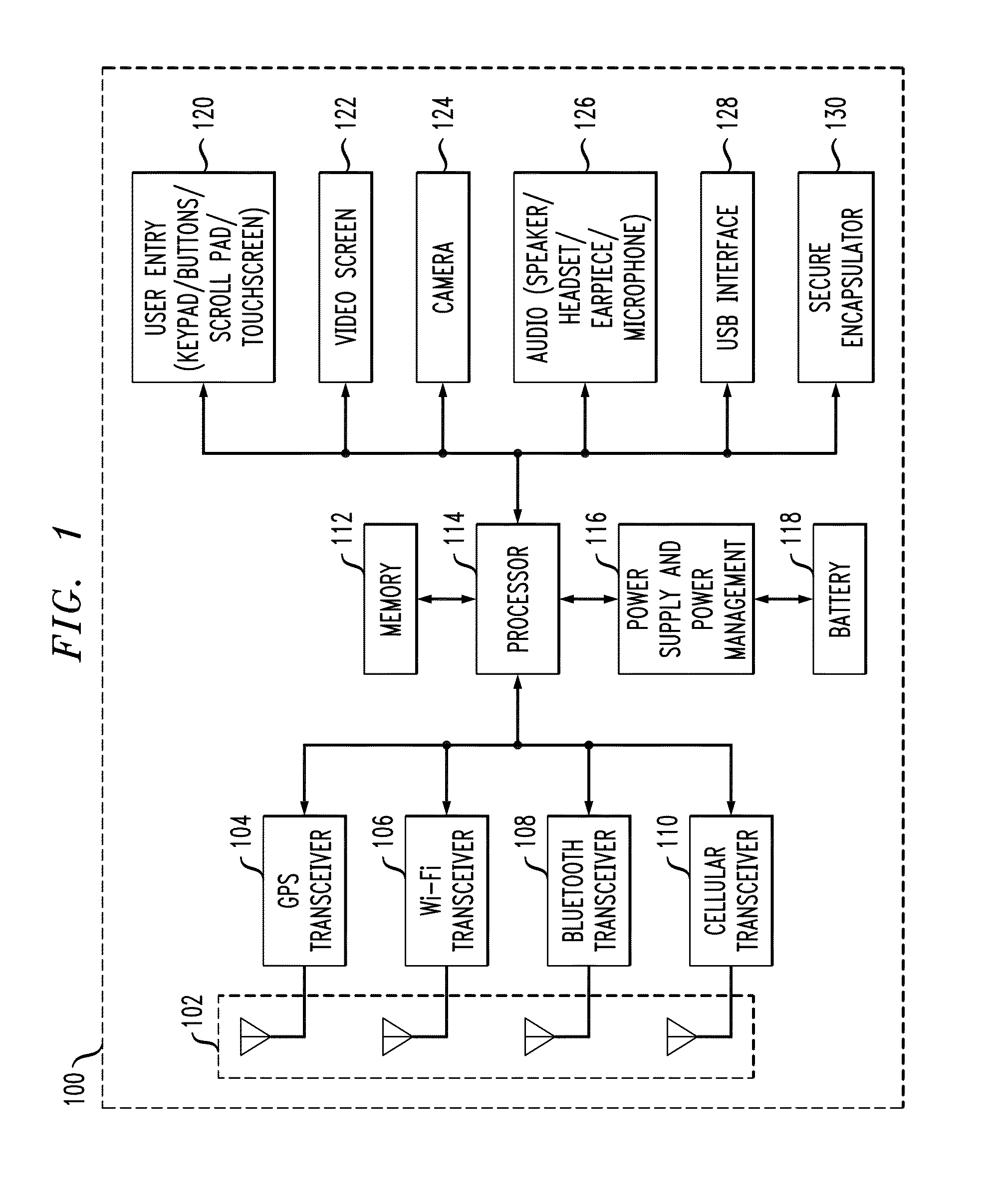
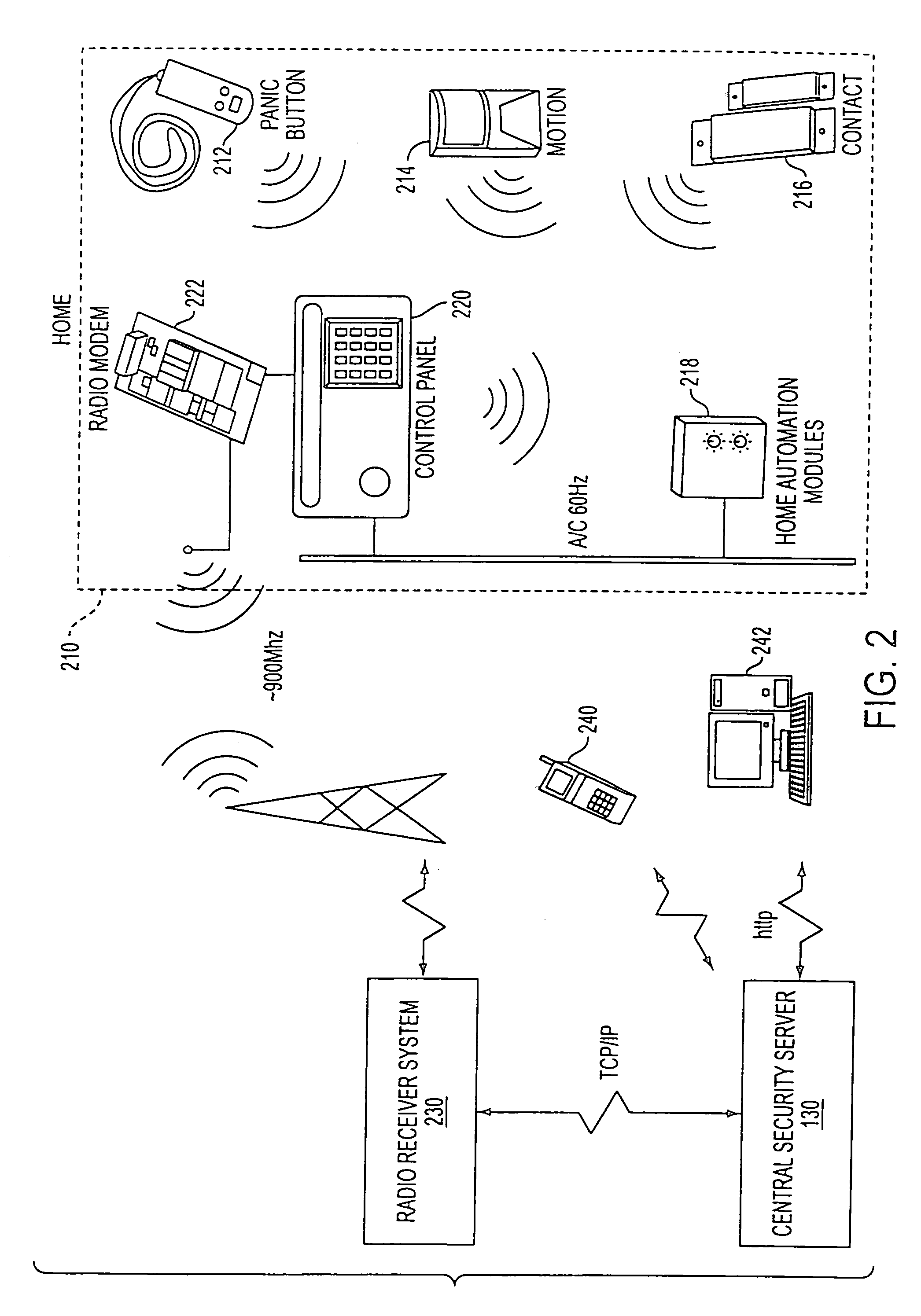
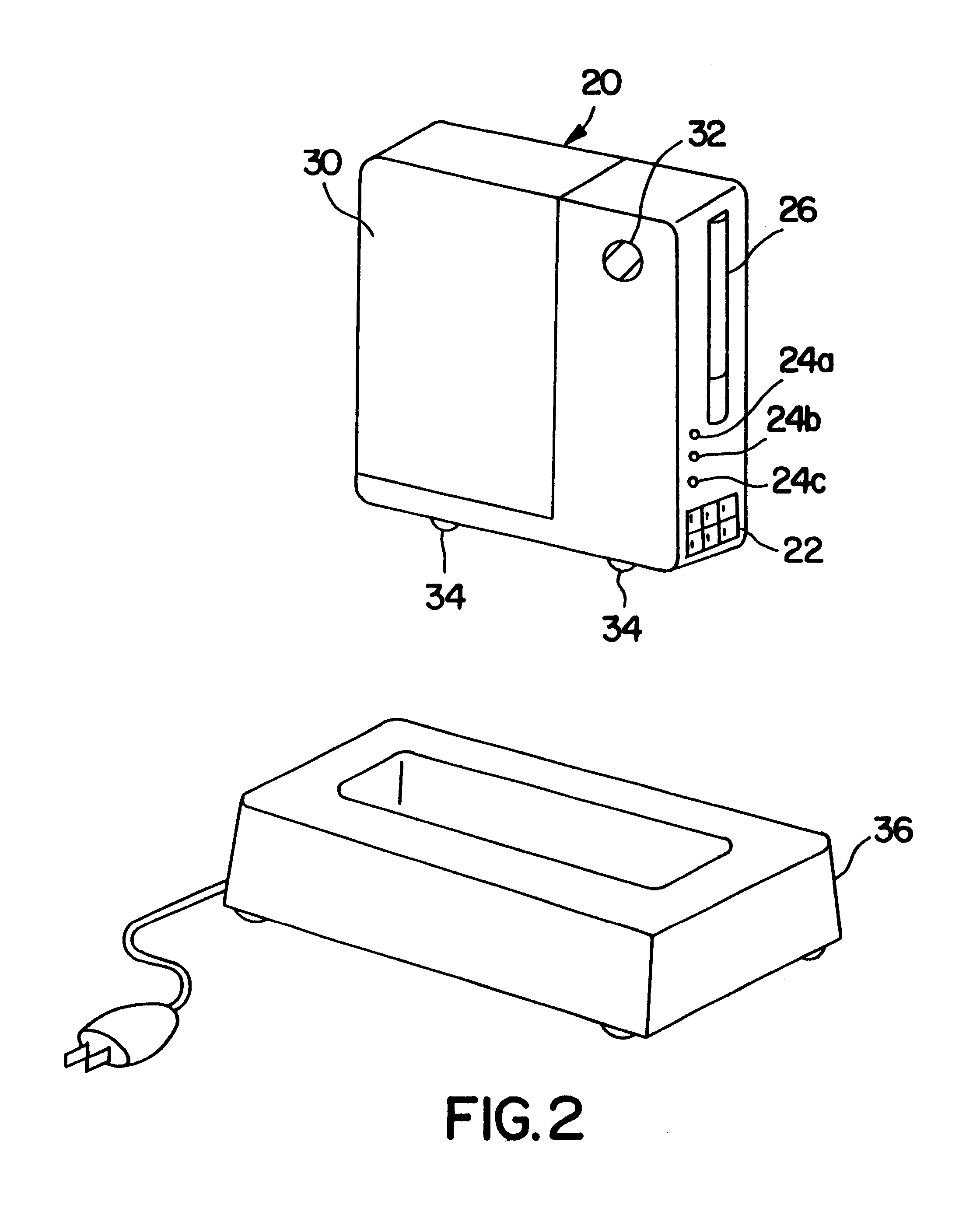
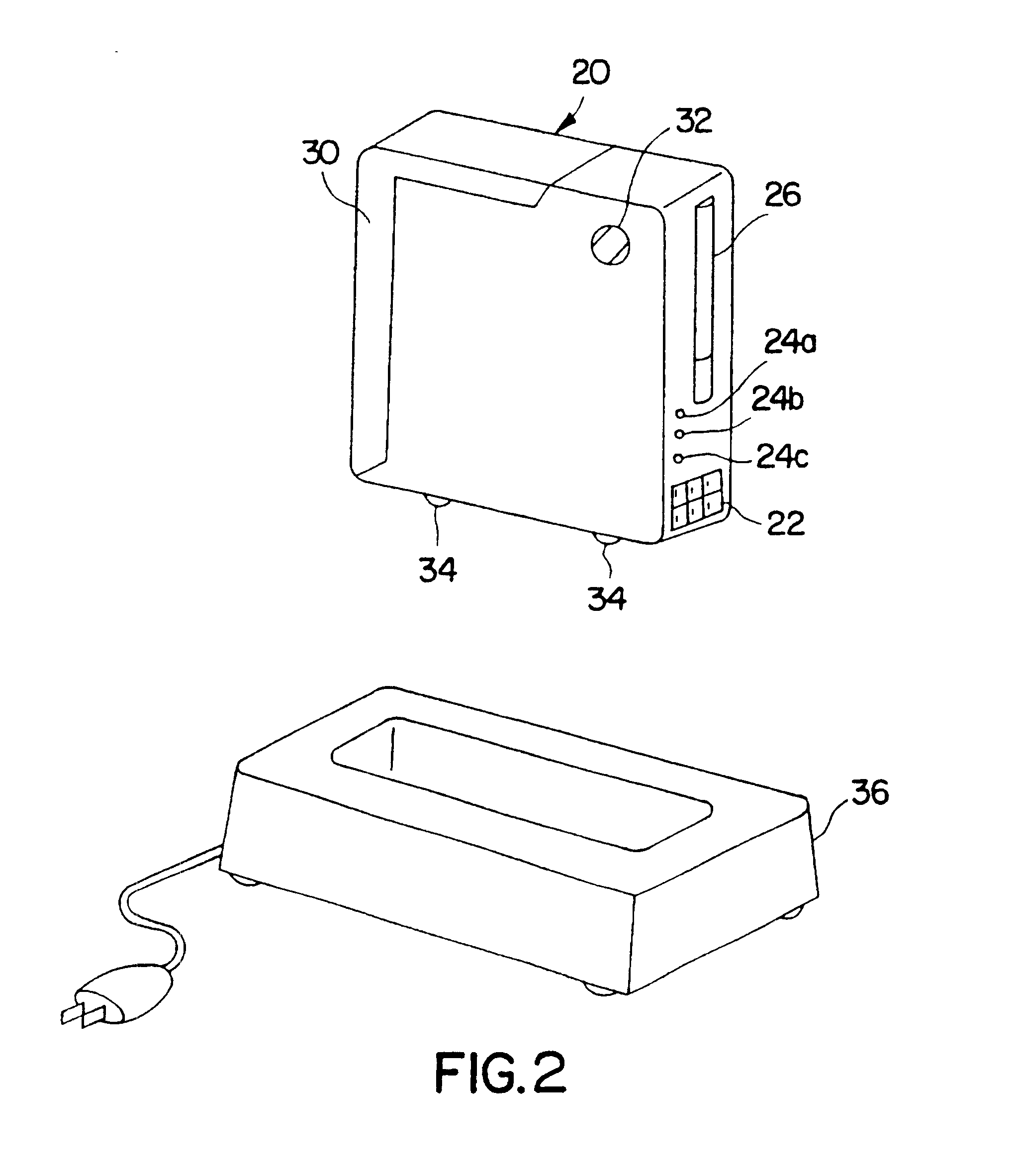
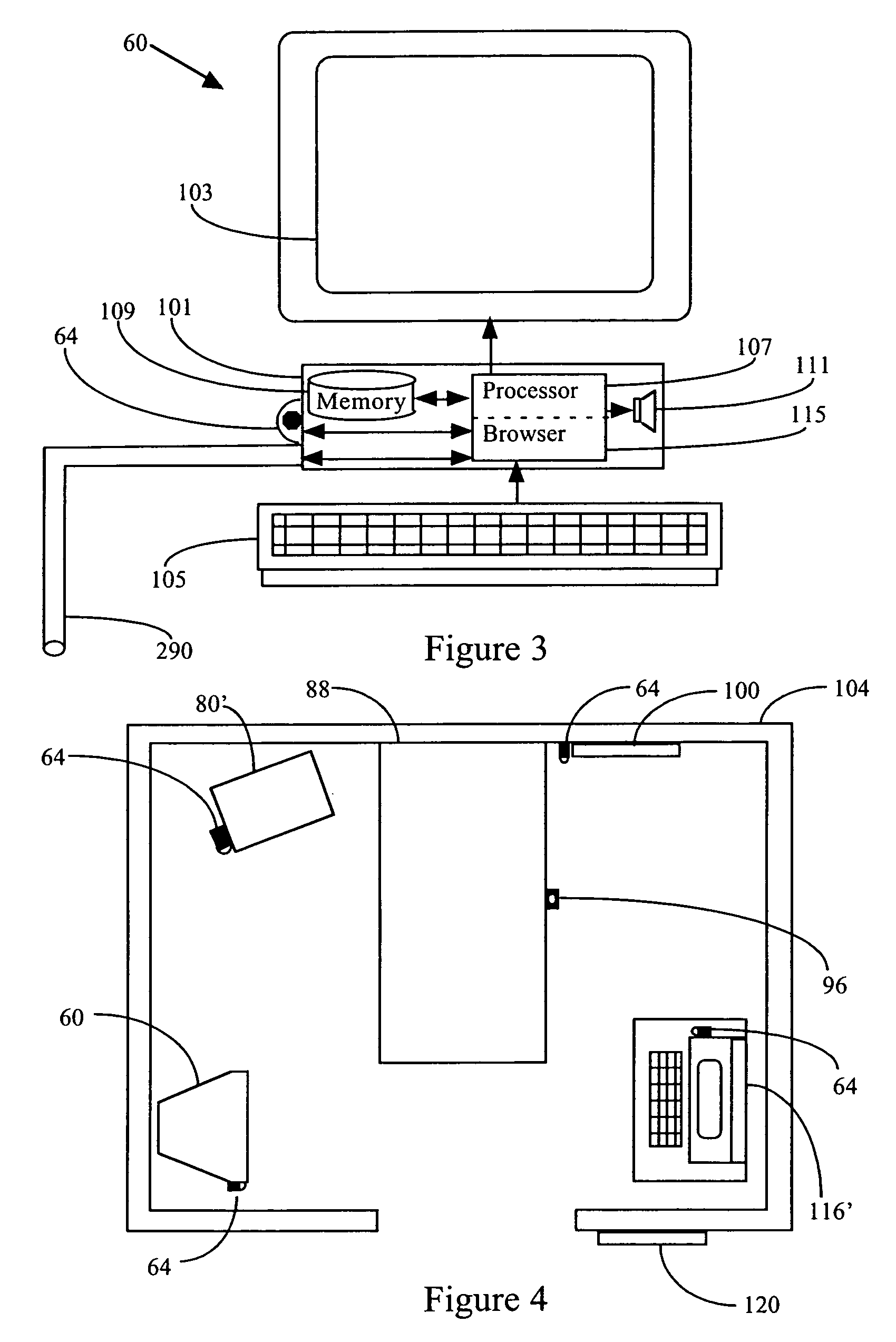
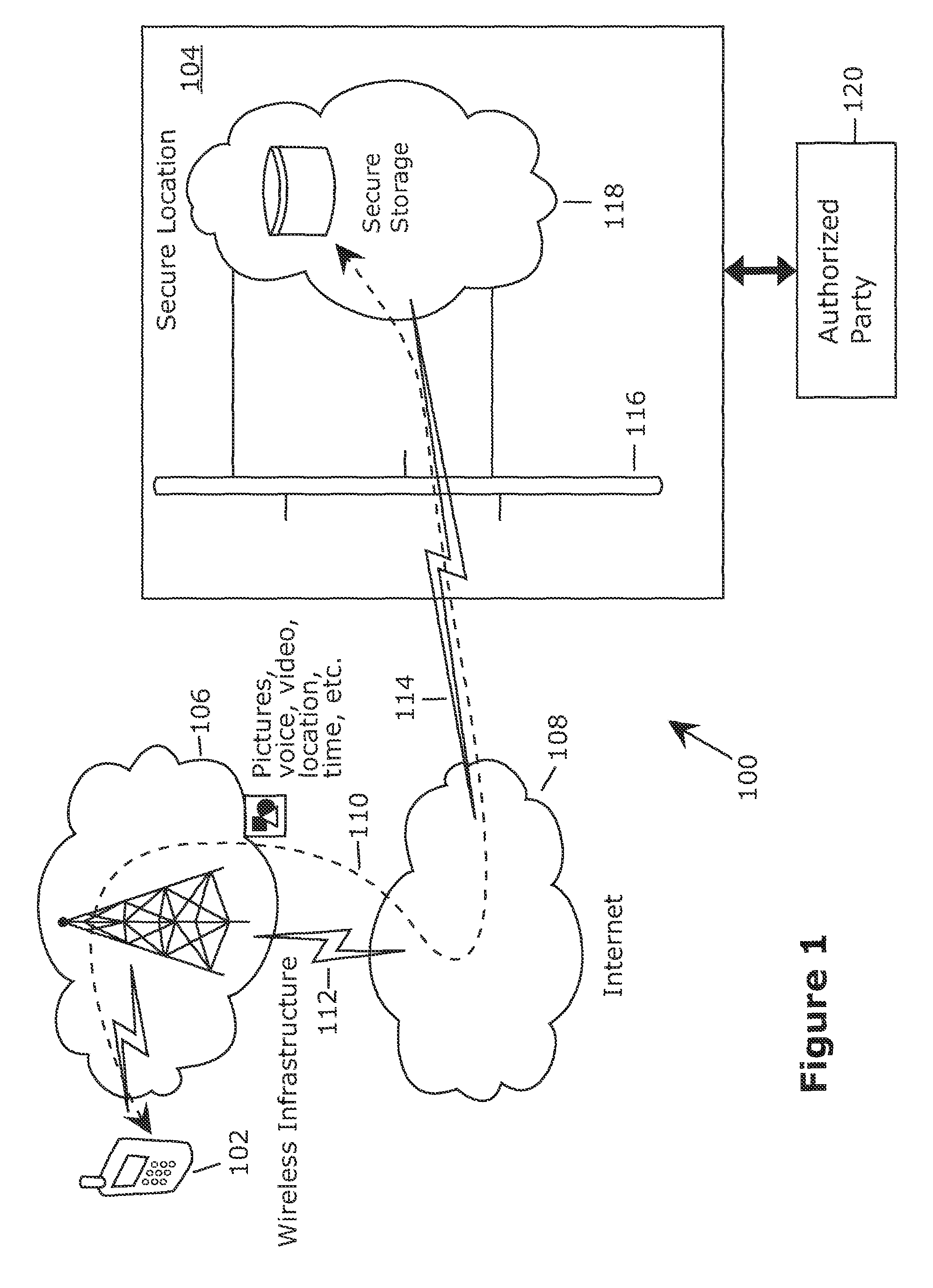
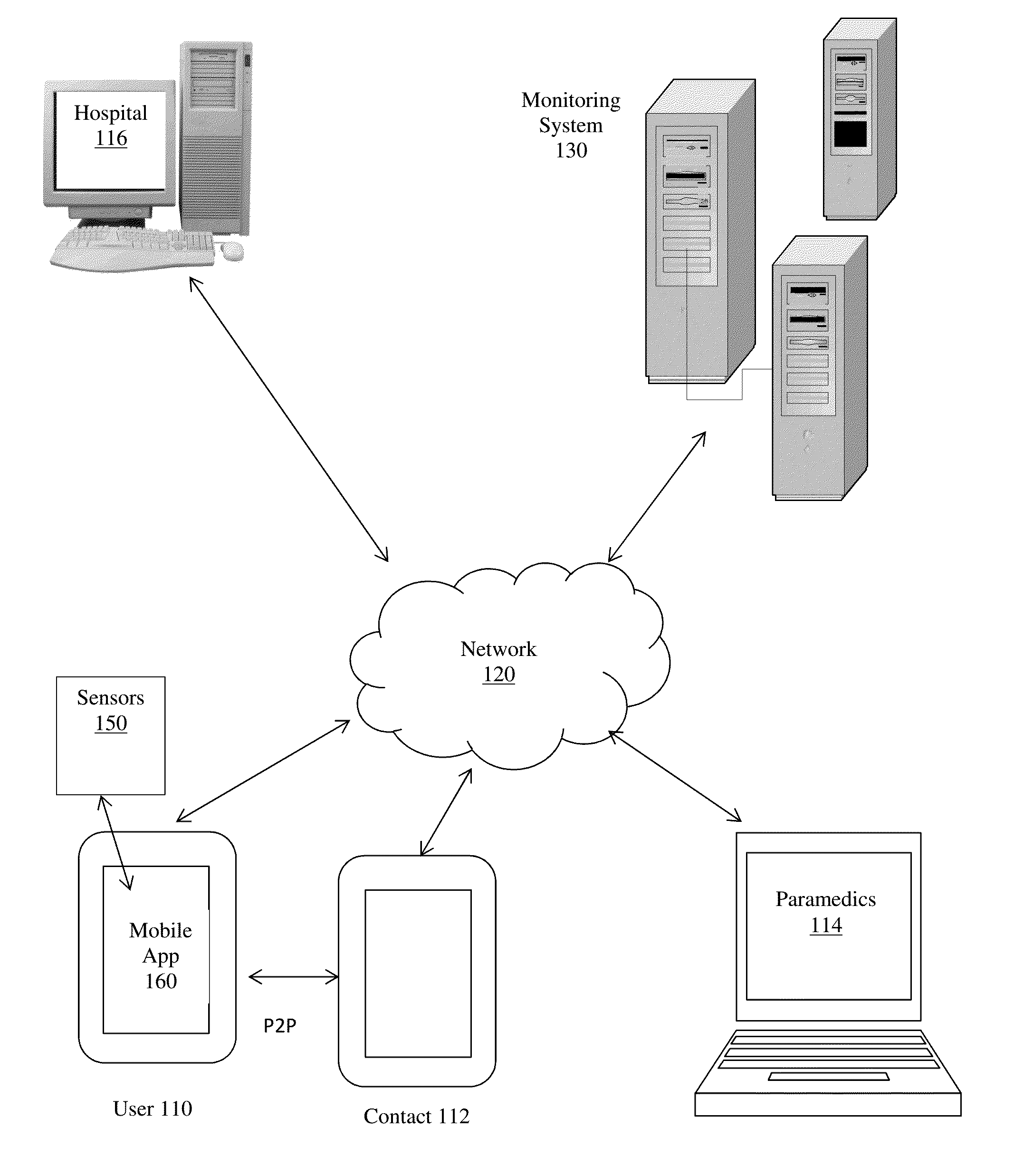
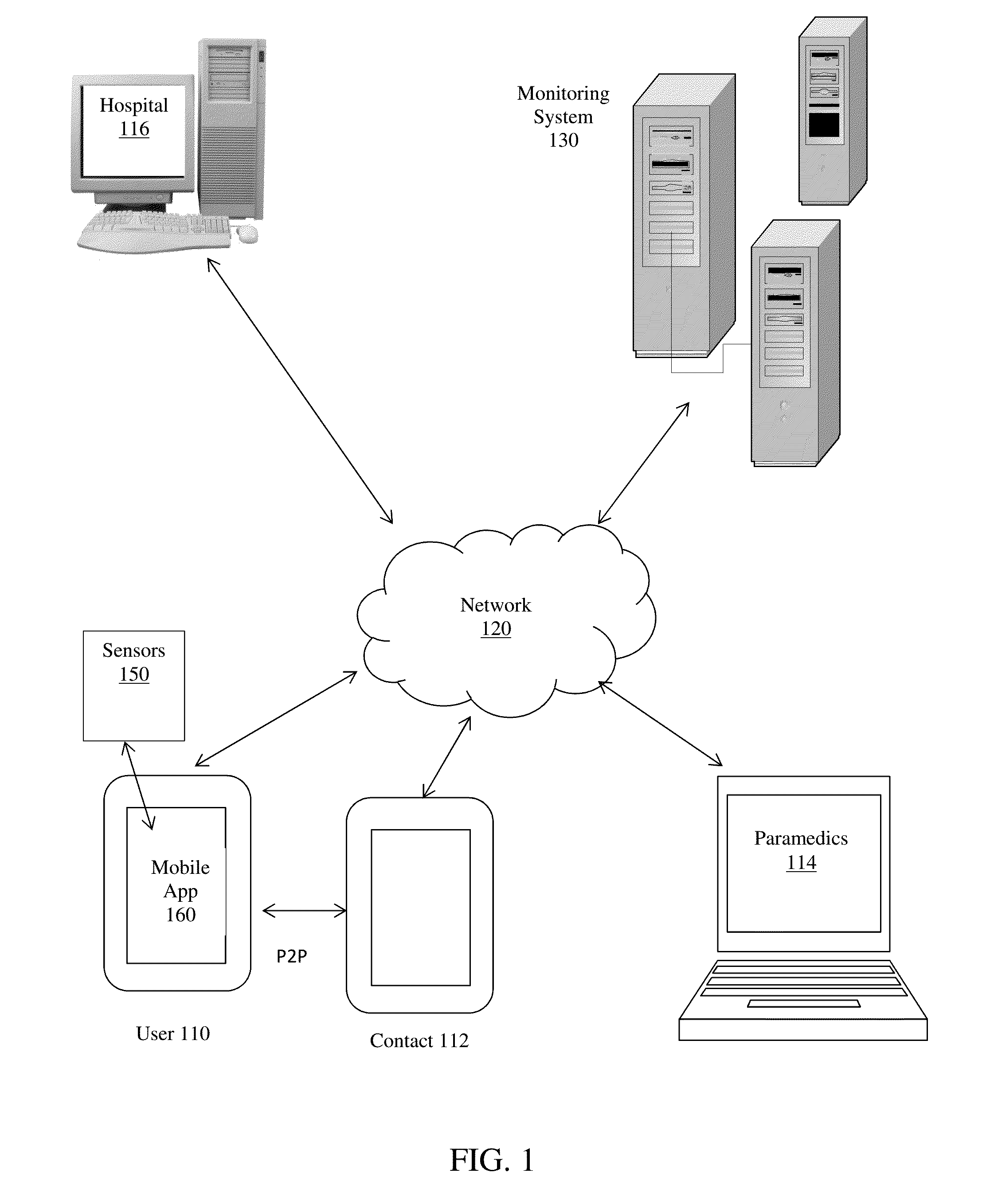
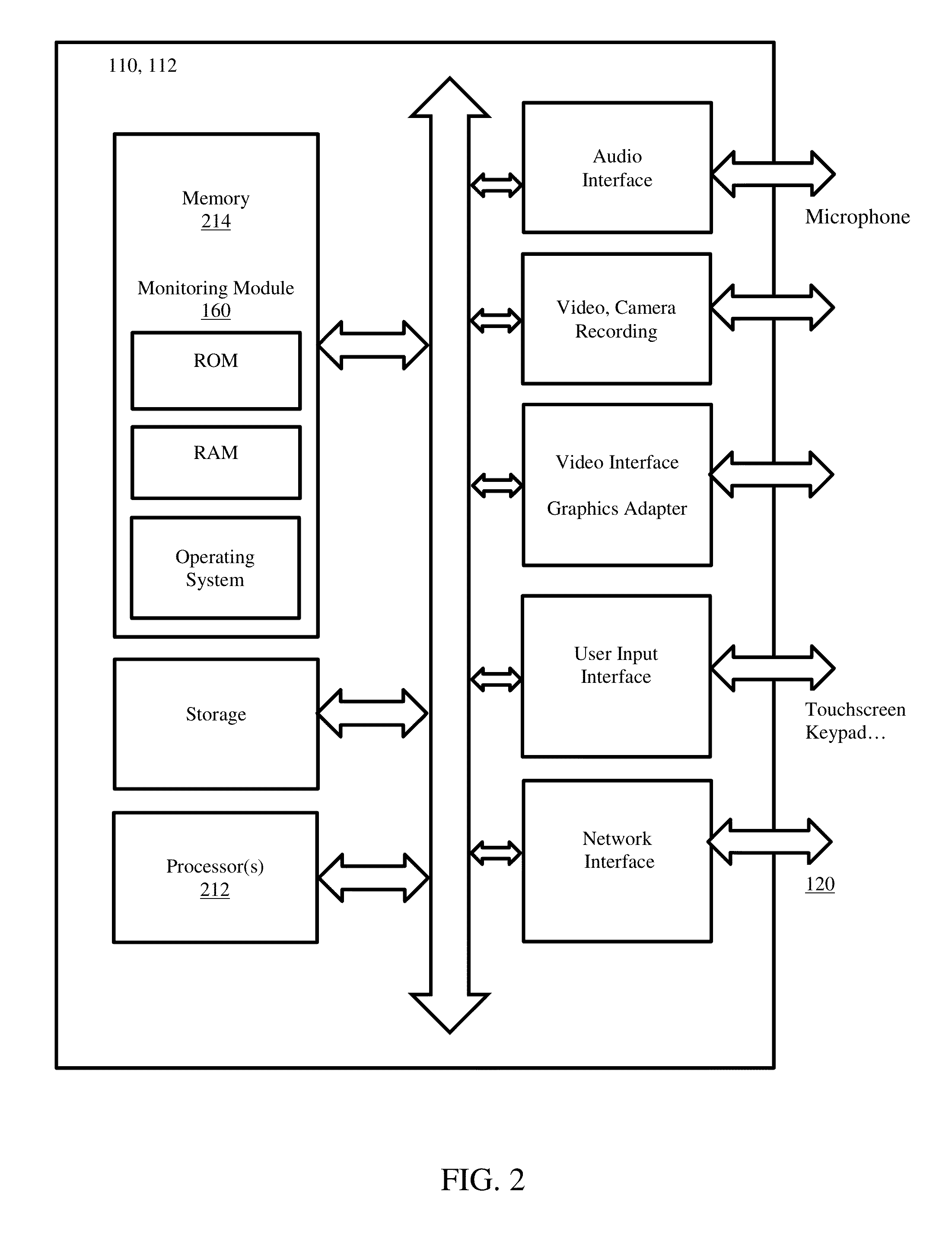
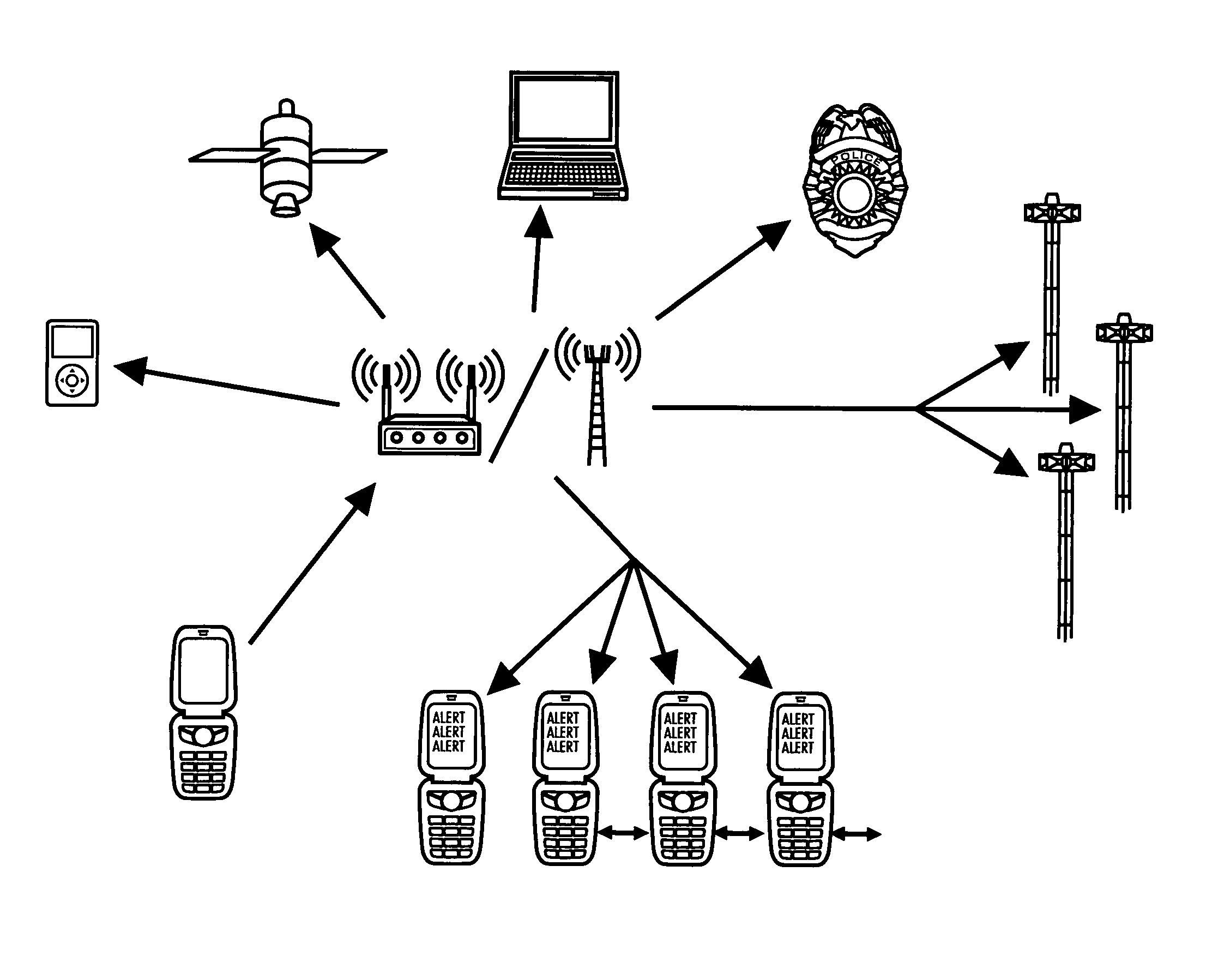
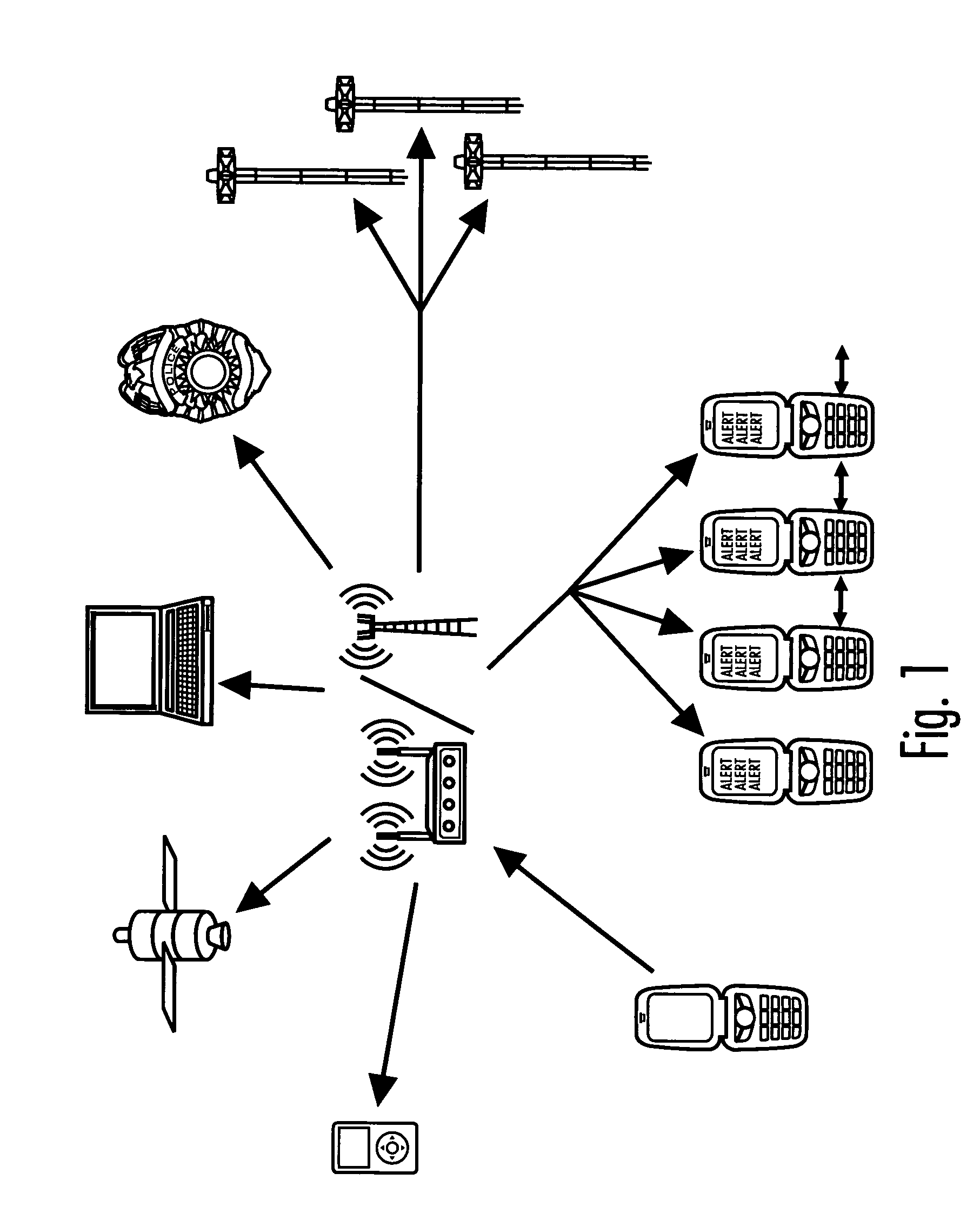
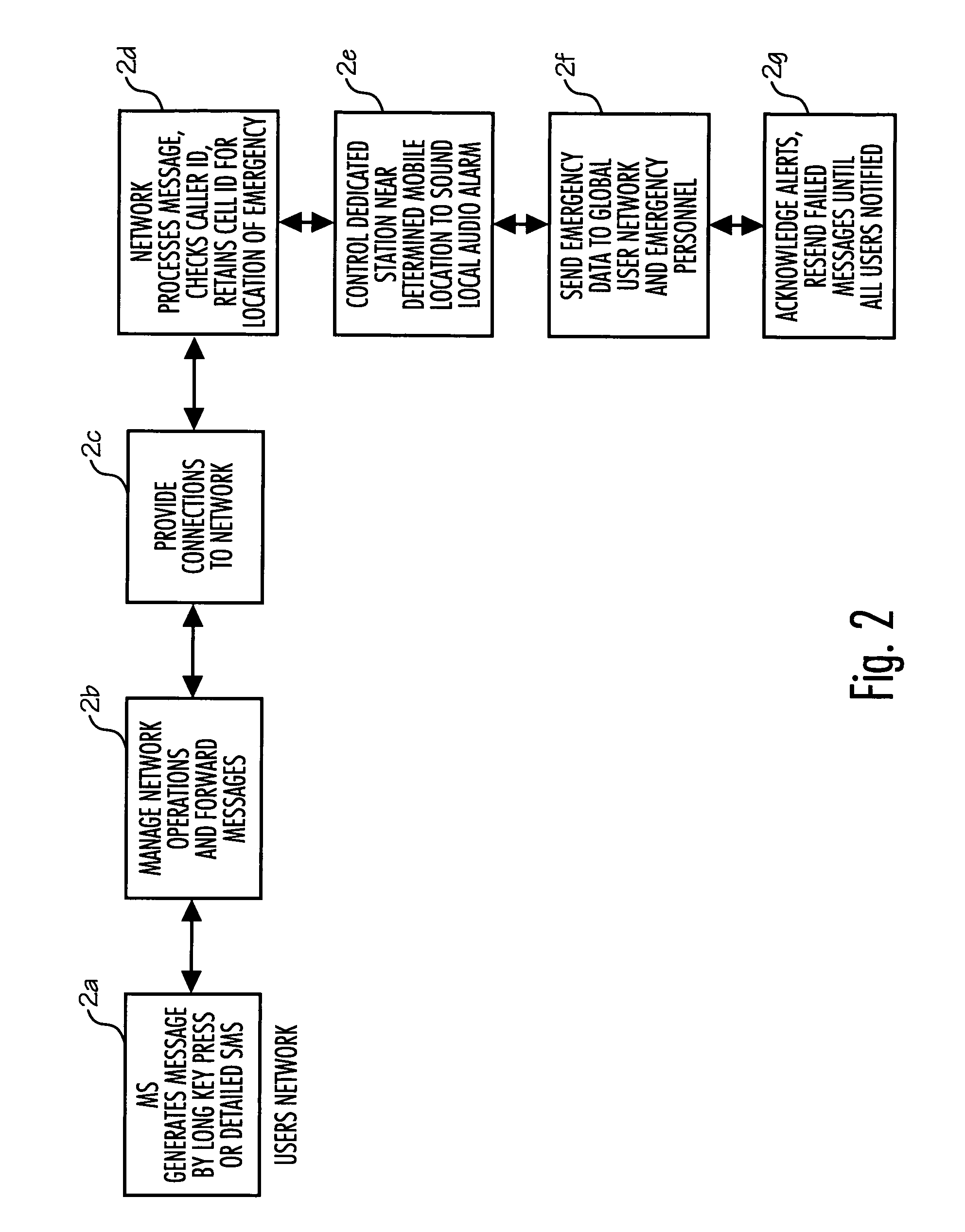
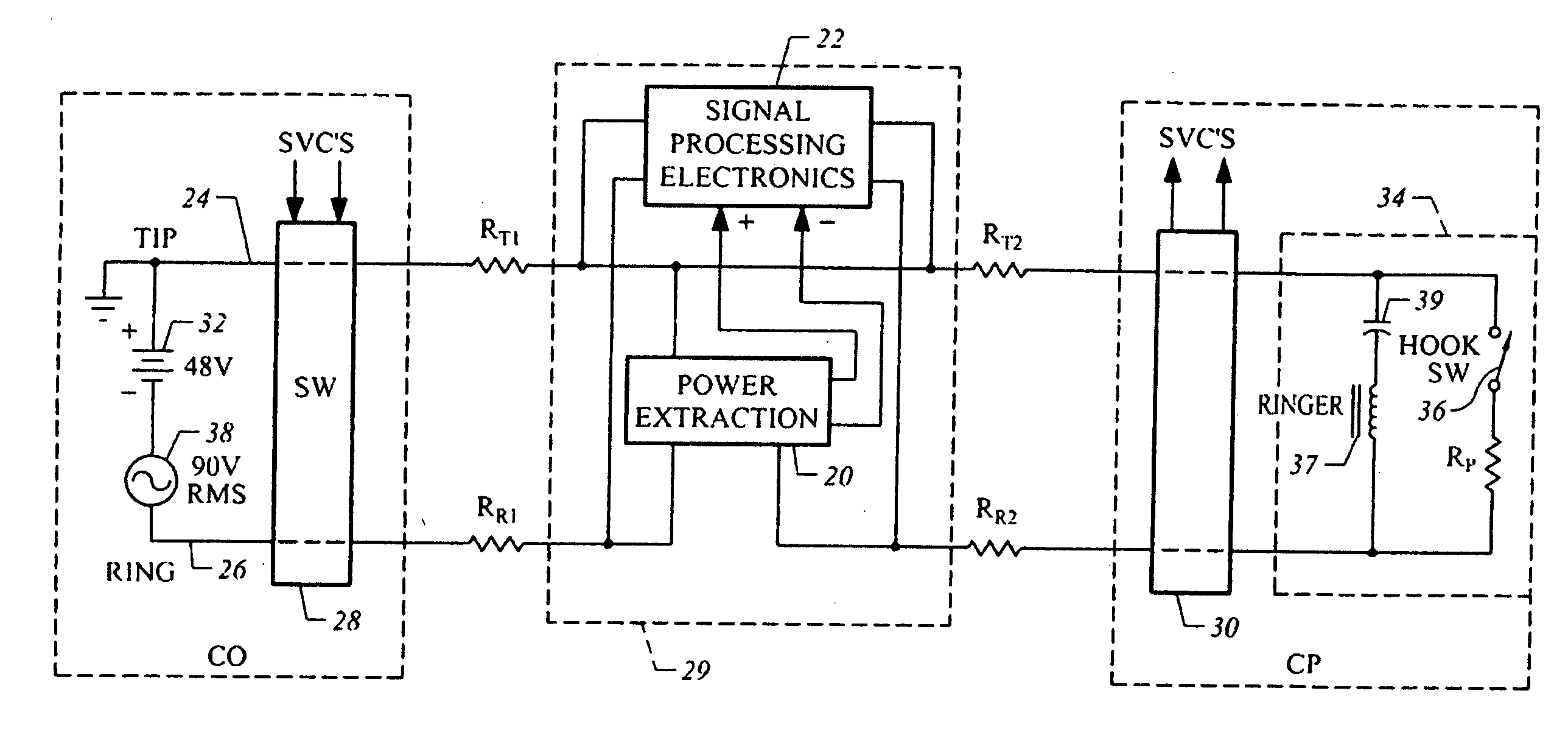
System and method for connecting security systems to a wireless device
InactiveUS7113090B1Electric signal transmission systemsMultiple keys/algorithms usagePersonalizationMonitoring system
The present invention provides a personal security network where an individual's system or systems of security devices may be connected to a central security network. The central security network of the present invention may monitor a system's status and alert the individual when an alert situation occurs. The present invention provides a security network where a user may set up personalized alarms and alert services; identify various methods of contact; order at which to be contacted; individuals and entities to be contacted; type of situations to be alerted of and other relevant security and other information. The present invention may further provide a personalized web interface where authorized individuals may view current and historical security device status. A user may generate personalized reports based on aggregated historical data based on various user-defined factors. The reports may be displayed to the user in various formats, such as maps, graphs, statistics, and others.
Owner:ALARM COM INC
Personal safety mobile notification system
ActiveUS20130183924A1Well formedBiocideHydroxy compound active ingredientsGlobal Positioning SystemMobile device
In described embodiments, a system establishes a perimeter around an area, and mobile devices within the established perimeter communicate with a server that provides and collects personal and asset safety information. The provided information might enable users associated with the mobile devices to plan actions or take routes based on a given criteria, such as a safest route, through display on the mobile device. The collected information from the mobile device might be location, emergency event, environmental factors, sensor information and the like, which might then be communicated to users and / or administrators of the system. Location information, such as through global positioning system (GPS), might provide tracking of mobile devices and users or assets associated with each mobile device. GPS functionality associates latitude, longitude and elevation (X-Y-Z coordinate axis) data with the collected and provided information.
Owner:LIQUID RARITY EXCHANGE LLC
System and method for connecting security systems to a wireless device
InactiveUS6965313B1Not be preventElectric signal transmission systemsMultiple keys/algorithms usagePersonalizationMonitoring system
The present invention provides a personal security network where an individual's system or systems of security devices may be connected to a central security network. The central security network of the present invention may monitor a system's status and alert the individual when an alert situation occurs. The present invention provides a security network where a user may set up personalized alarms and alert services; identify various methods of contact; order at which to be contacted; individuals and entities to be contacted; type of situations to be alerted of and other relevant security and other information. The present invention may further provide a personalized web interface where authorized individuals may view current and historical security device status. A user may generate personalized reports based on aggregated historical data based on various user-defined factors. The reports may be displayed to the user in various formats, such as maps, graphs, statistics, and others.
Owner:ALARM COM INC
System and method to authenticate users to computer systems
InactiveUS20050091338A1Facilitates rapid secondary logLimited accessDigital data processing detailsDrug and medicationsTelecommunications linkTransceiver
A system utilizing a personal security device to provide access to a computer terminal where the personal security device includes circuitry and transceiver components for transmitting identification information and exchanging other digital information with a computer terminal and other compatible devices and the personal security device establishes a communication link with a computer terminal to allow a user to logon to the terminal so that when a user leaves the computer terminal, the communication link is terminated, causing the computer terminal to lock the keyboard, blank the monitor, and / or logoff the user if the communication link is not restored within a sufficient time period and also allowing the personal security device to facilitate subsequent computer access within a time range by providing time related access codes to the terminal that can be used to reestablish computer terminal access.
Owner:DLH TECH LLC
System and methods for maintaining and distributing personal security devices
InactiveUS7111172B1Key distribution for secure communicationPublic key for secure communicationInternet privacyClient-side
This invention relates to methods and apparatus for securely accessing and providing information including the use of a personal security device on a client where the client is subject to compromise.
Owner:EMC IP HLDG CO LLC
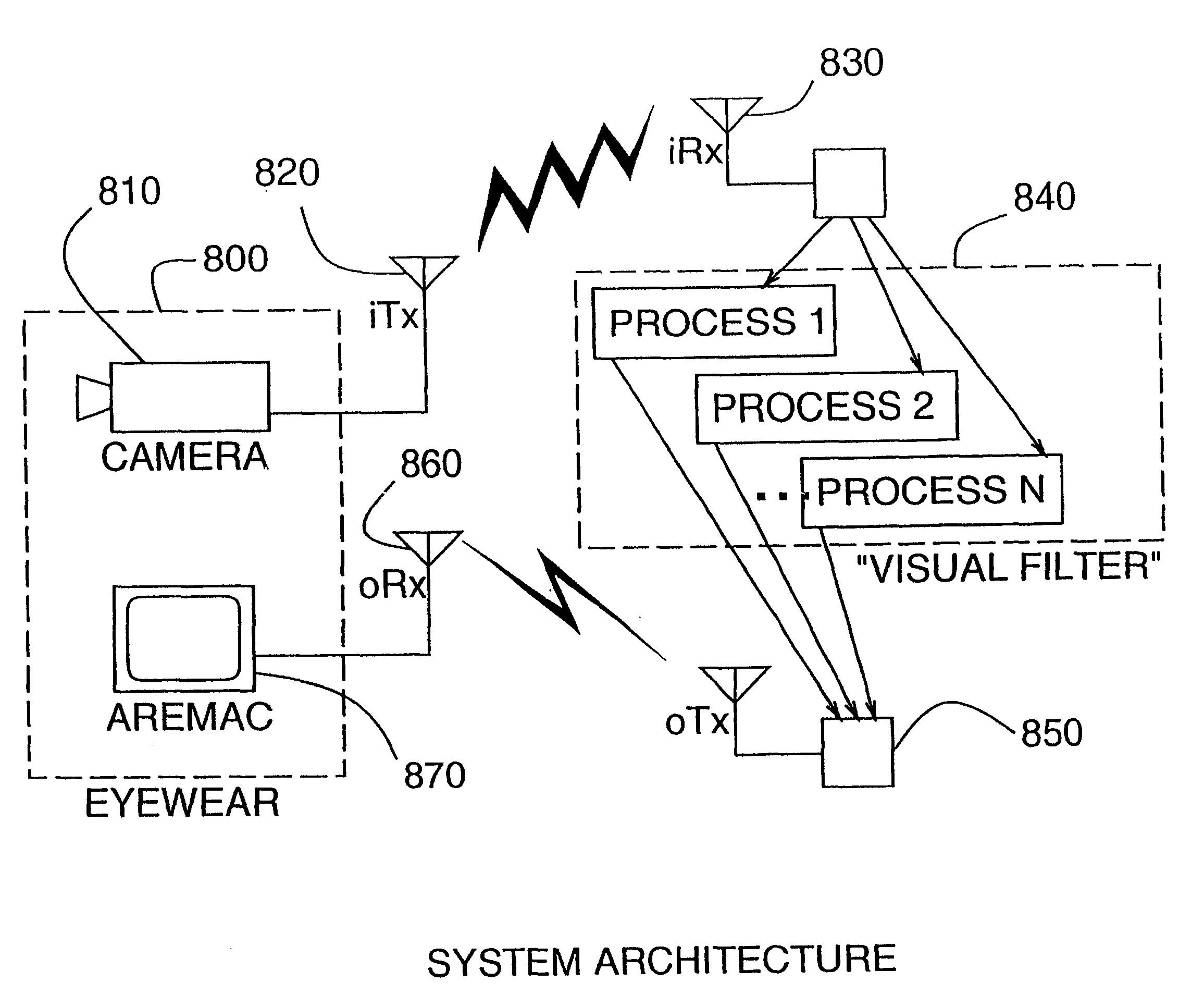
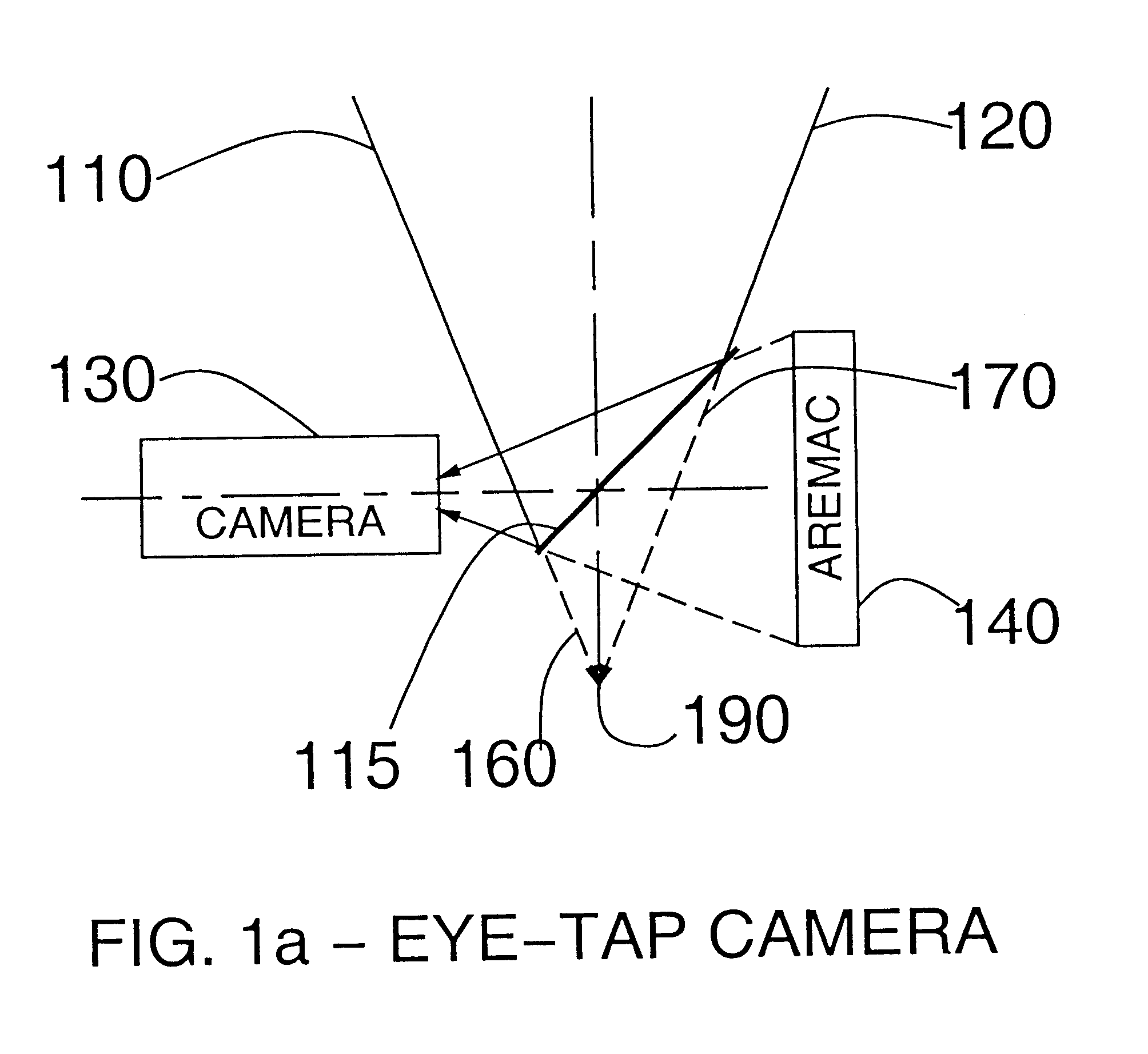
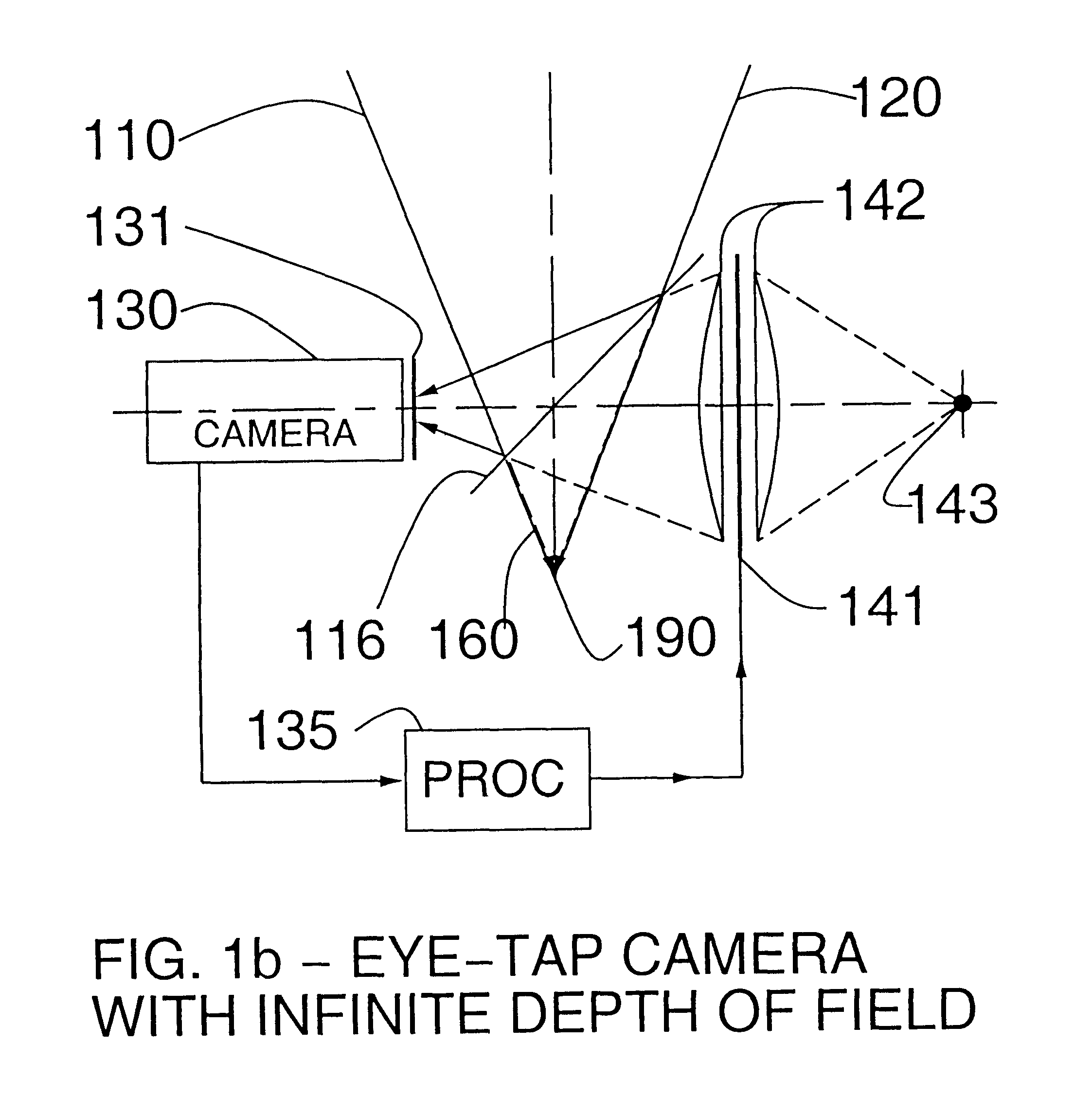
Eye-tap for electronic newsgathering, documentary video, photojournalism, and personal safety
InactiveUS6614408B1Augment and diminishEasy to catchTelevision system detailsCathode-ray tube indicatorsCommunications mediaComputer science
A novel system for a new kind of electronic news gathering and videography is described. In particular, a camera that captures light passing through the center of a lens of an eye of the user is described. Such an electronic newsgathering system allows the eye itself to, in effect, function as a camera. In wearable embodiments of the invention, a journalist wearing the apparatus becomes, after adaptation, an entity that seeks, without conscious thought or effort, an optimal point of vantage and camera orientation. Moreover, the journalist can easily become part of a human intelligence network, and draw upon the intellectual resources and technical photographic skills of a large community. Because of the journalist's ability to constantly see the world through the apparatus of the invention, which may also function as an image enhancement device, the apparatus behaves as a true extension of the journalist's mind and body, giving rise to a new genre of documentary video. In this way, it functions as a seamless communications medium that uses a reality-based user-interface.
Owner:MANN W STEPHEN G
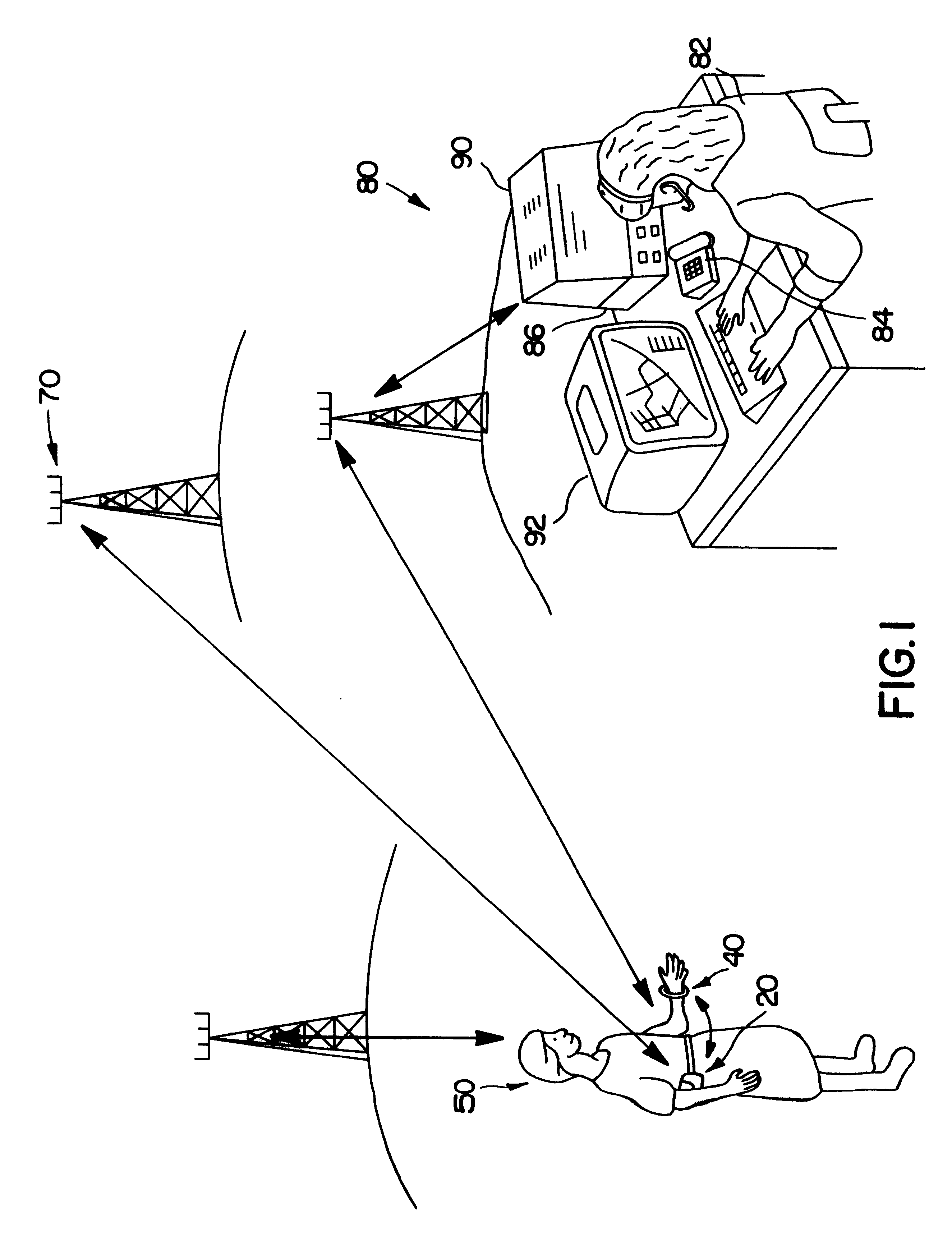
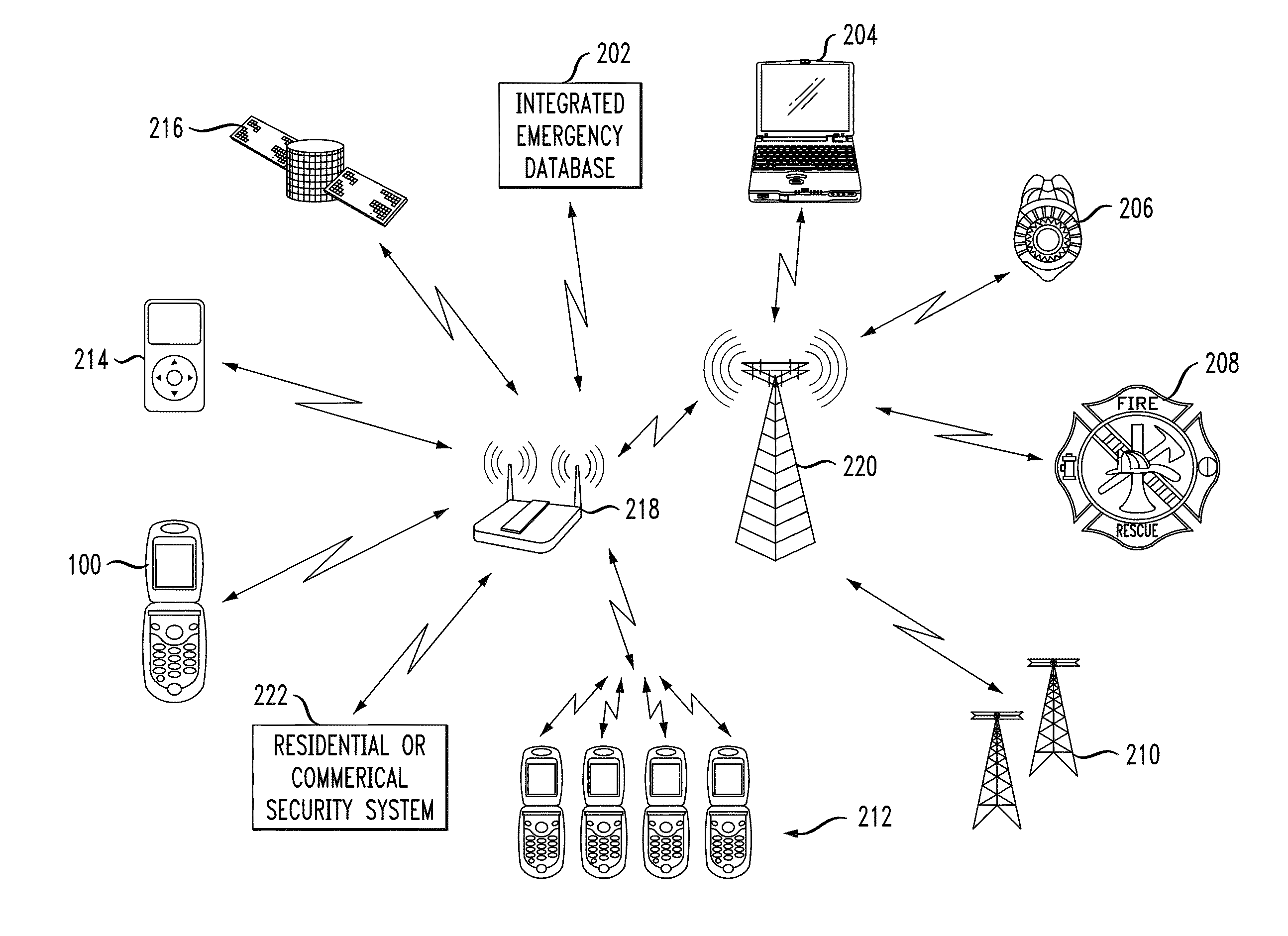
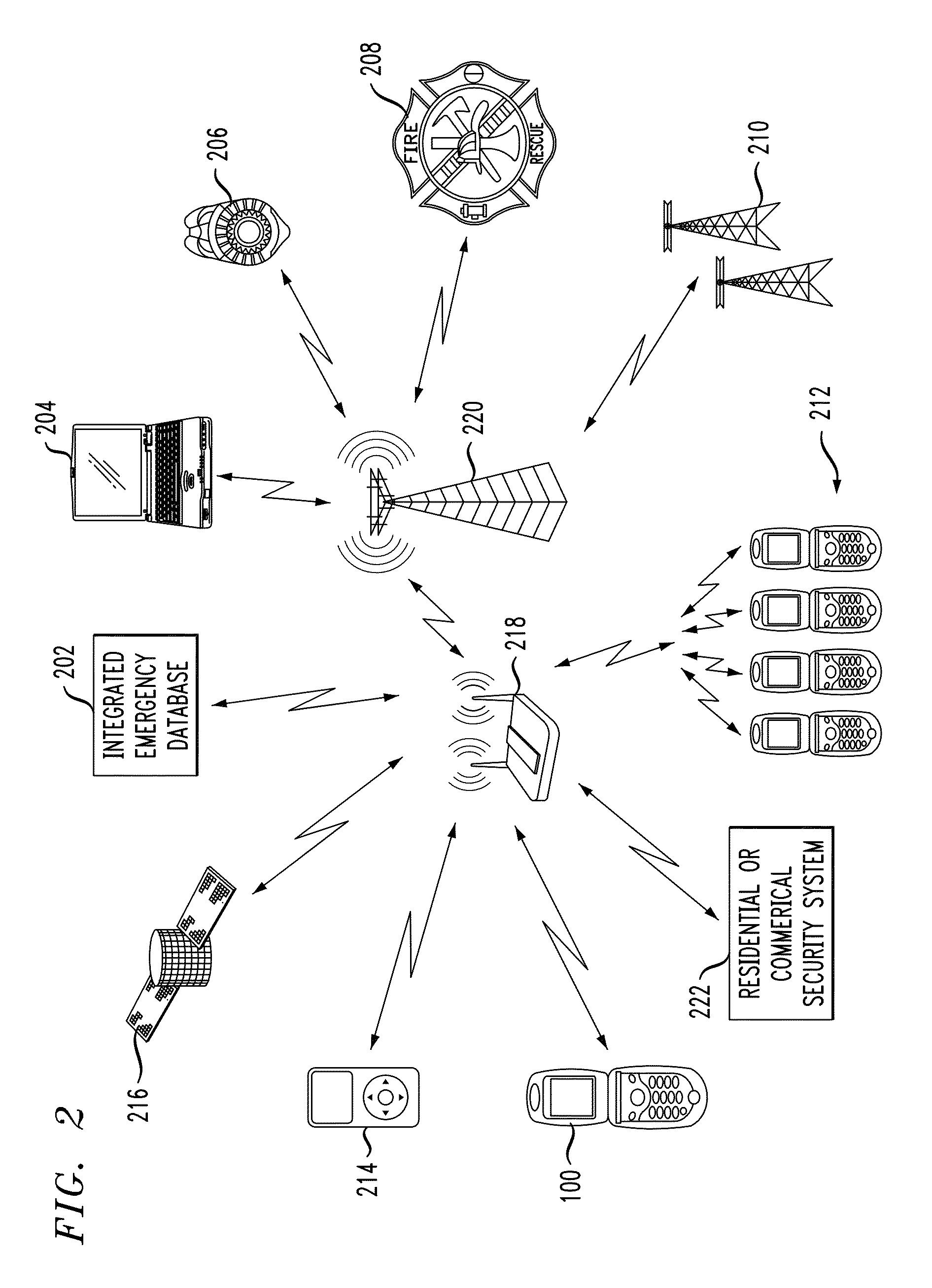
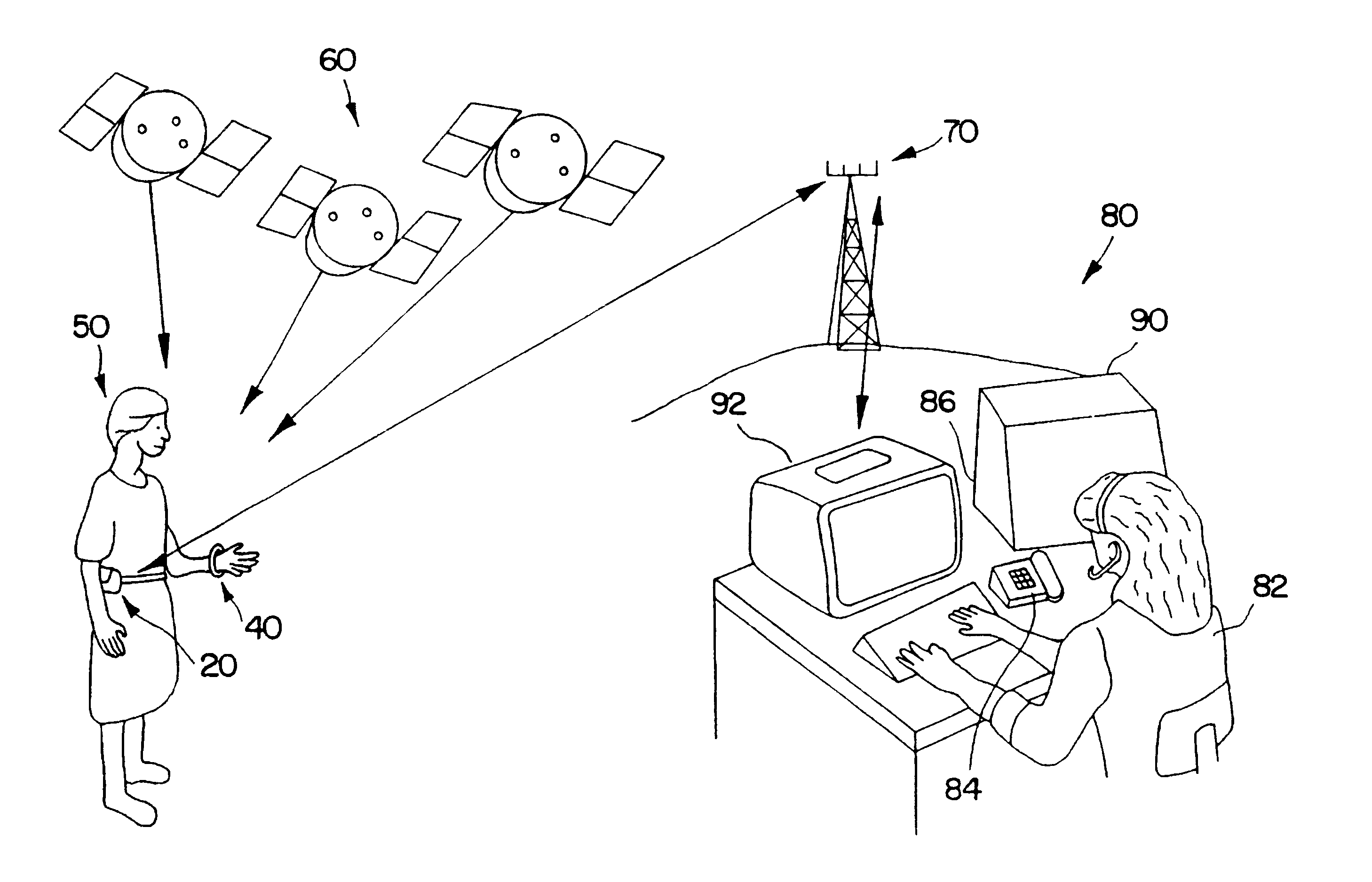
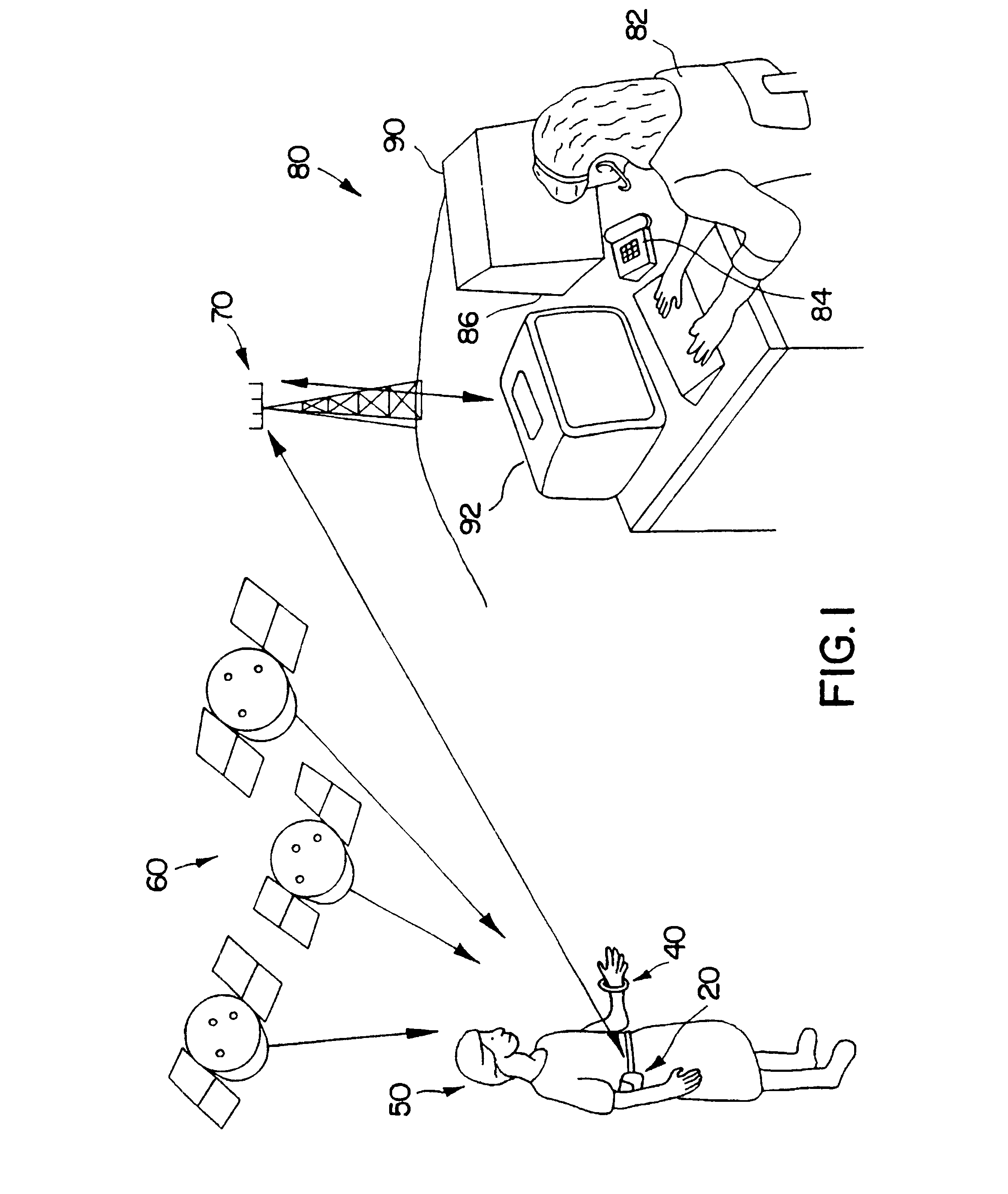
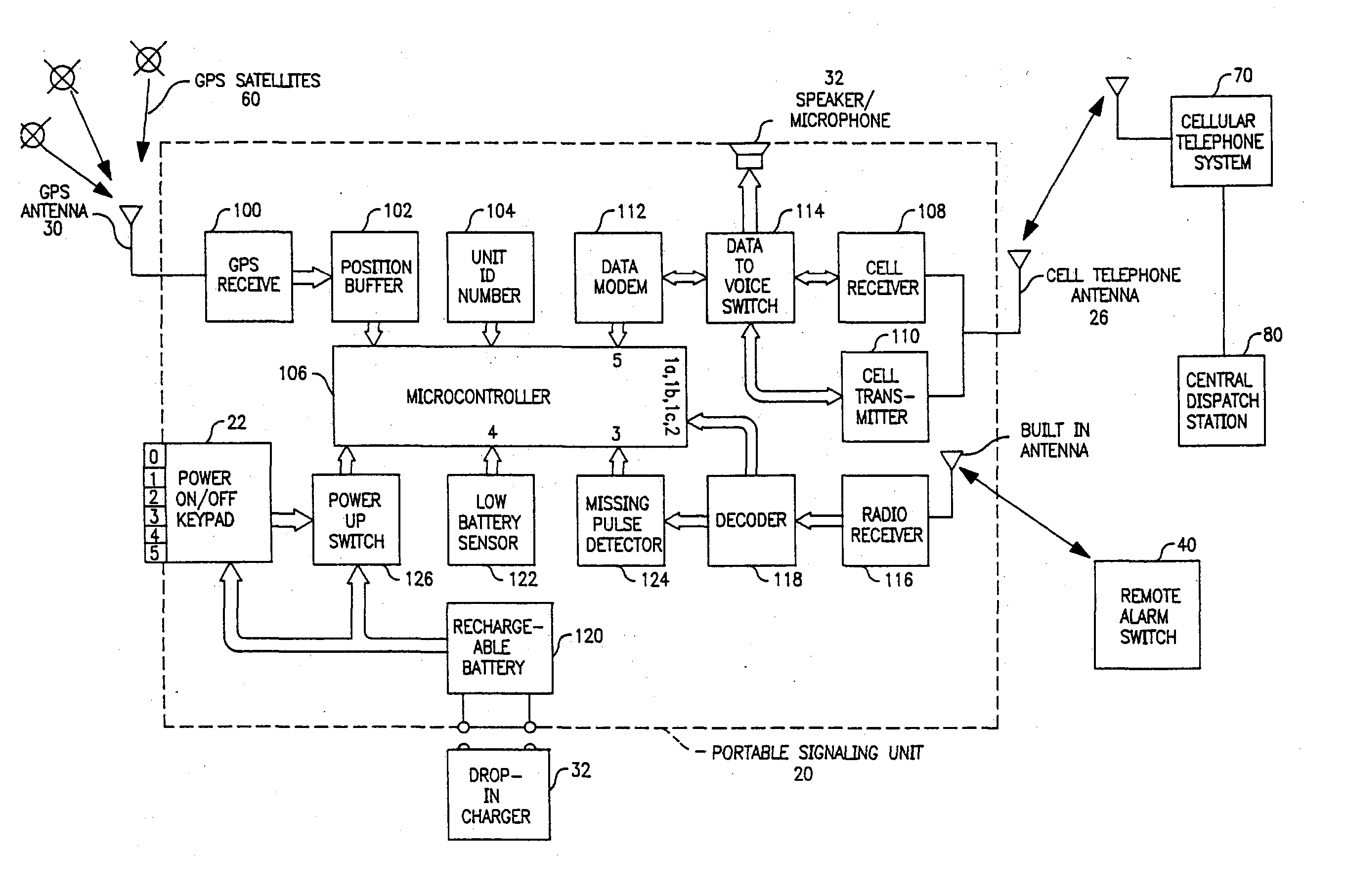
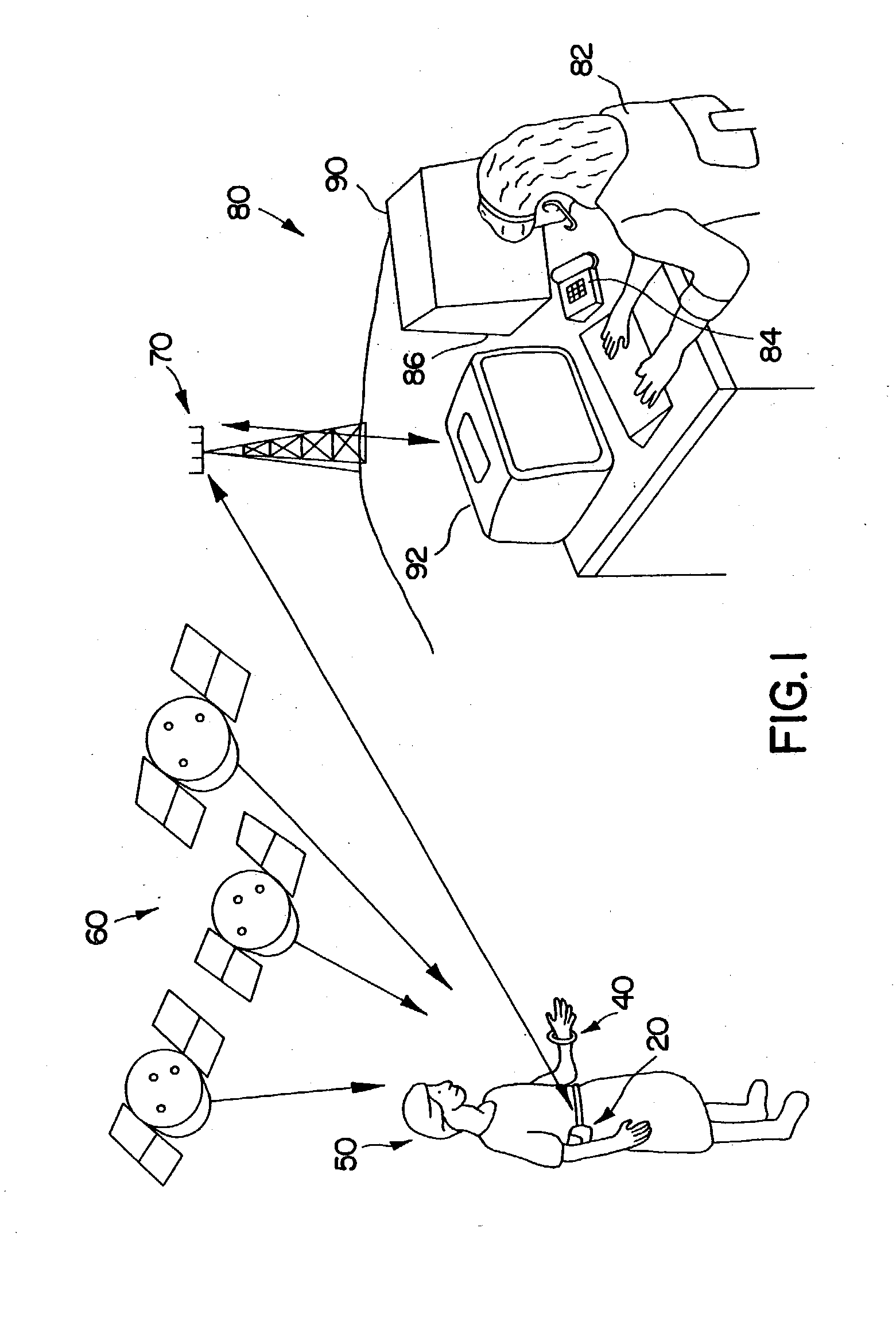
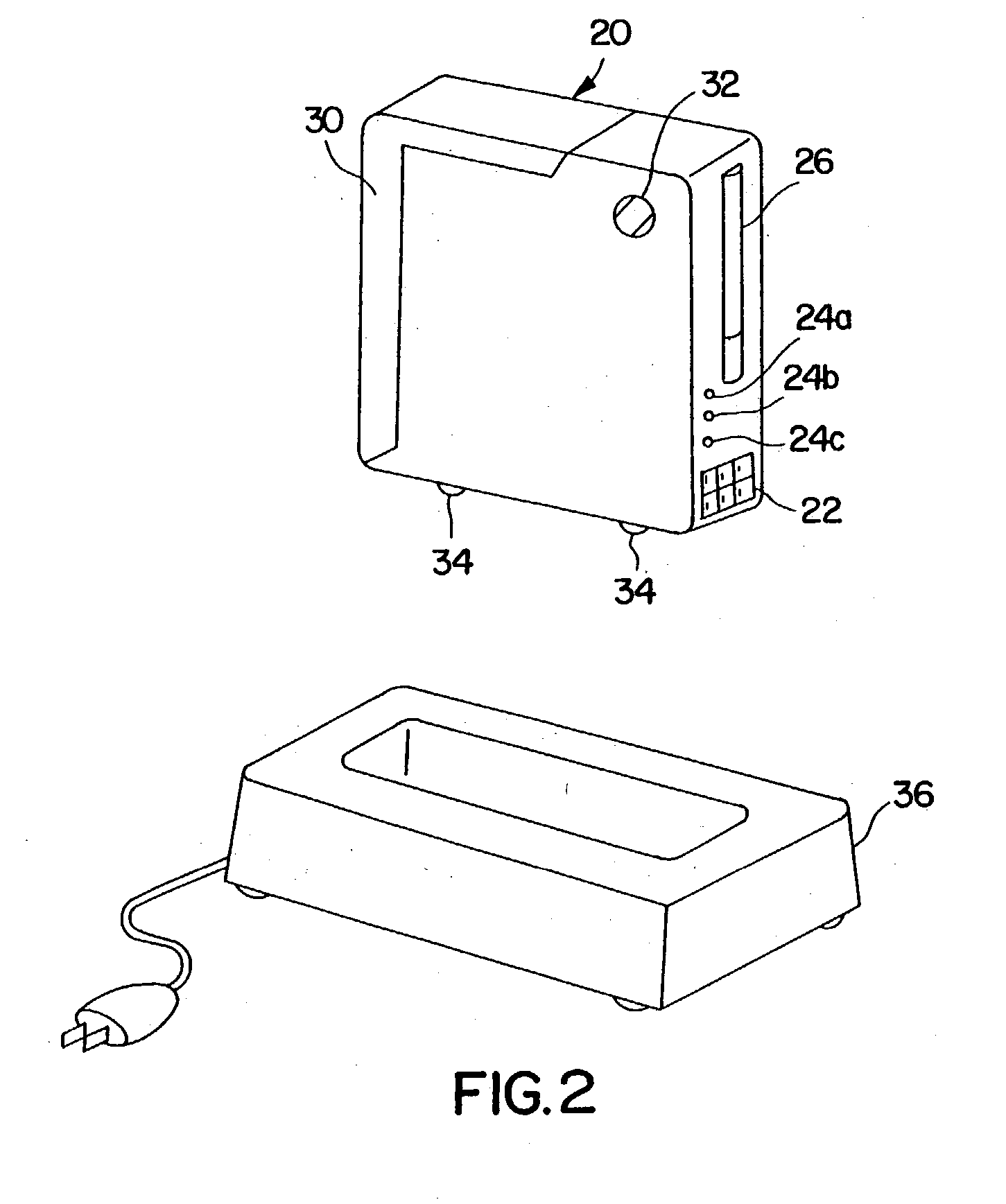
Personal security and tracking system
InactiveUS6239700B1Efficient schedulingDirection finders using radio wavesFrequency-division multiplex detailsTransceiverCommunications system
Wireless communication system for location of a person and identification of a distress condition of the person comprising portable transceivers (20) carried by persons, each having an associated alarm switch (40), the transceiver activatable locally and / or via a remote network and the alarm switch operable locally to activate the transceiver.
Owner:RPX CORP
Personal safety mobile notification system
In described embodiments, a system establishes a perimeter around an area, and mobile devices within the established perimeter communicate with a server that provides and collects personal and asset safety information. The provided information might enable users associated with the mobile devices to plan actions or take routes based on a given criteria, such as a safest route, through display on the mobile device. The collected information from the mobile device might be location, emergency event, environmental factors, sensor information and the like, which might then be communicated to users and / or administrators of the system. Location information, such as through global positioning system (GPS), might provide tracking of mobile devices and users or assets associated with each mobile device. GPS functionality associates latitude, longitude and elevation (X-Y-Z coordinate axis) data with the collected and provided information.
Owner:LIQUID RARITY EXCHANGE LLC
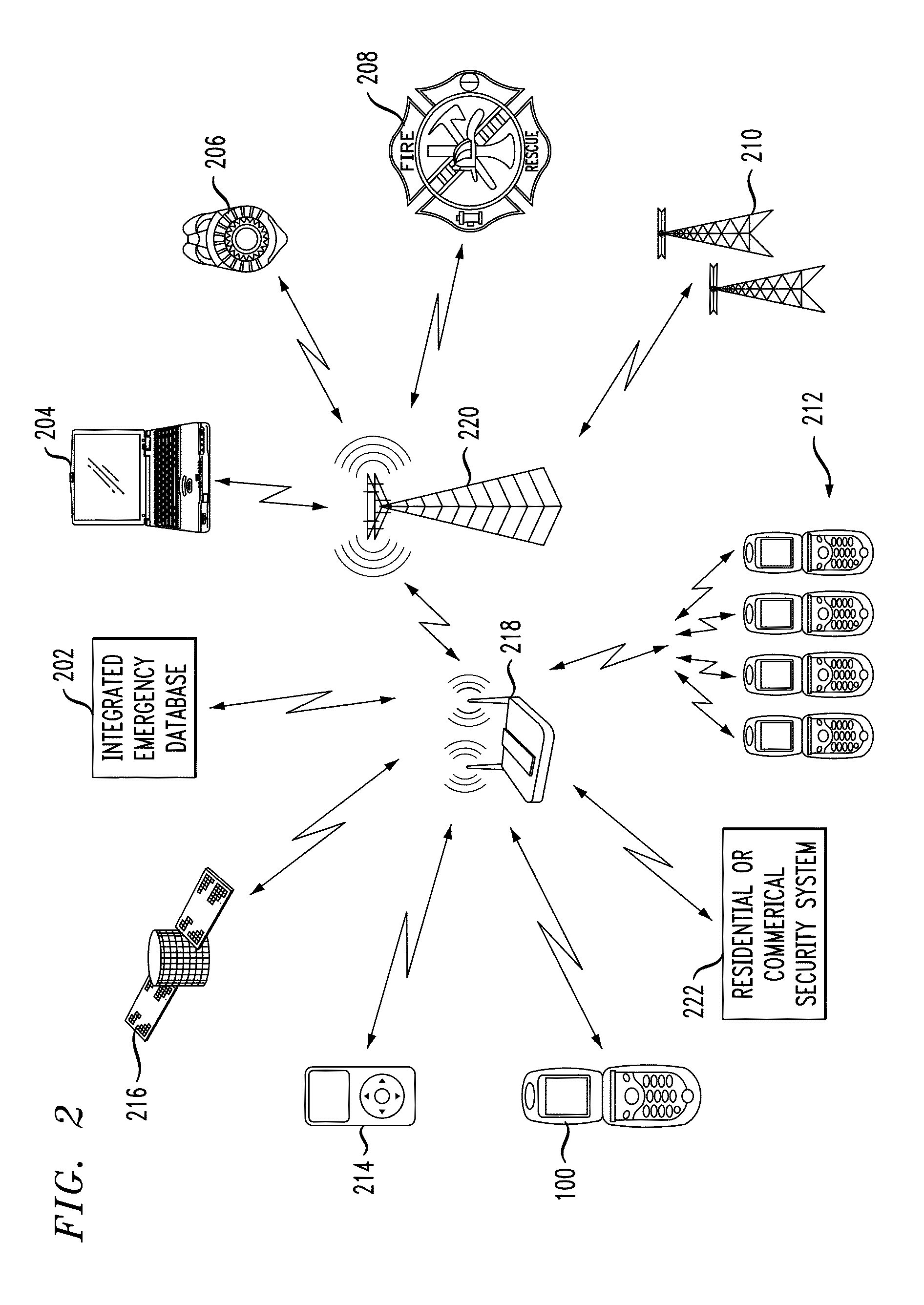
Method and system for providing location dependent and personal identification information to a public safety answering point
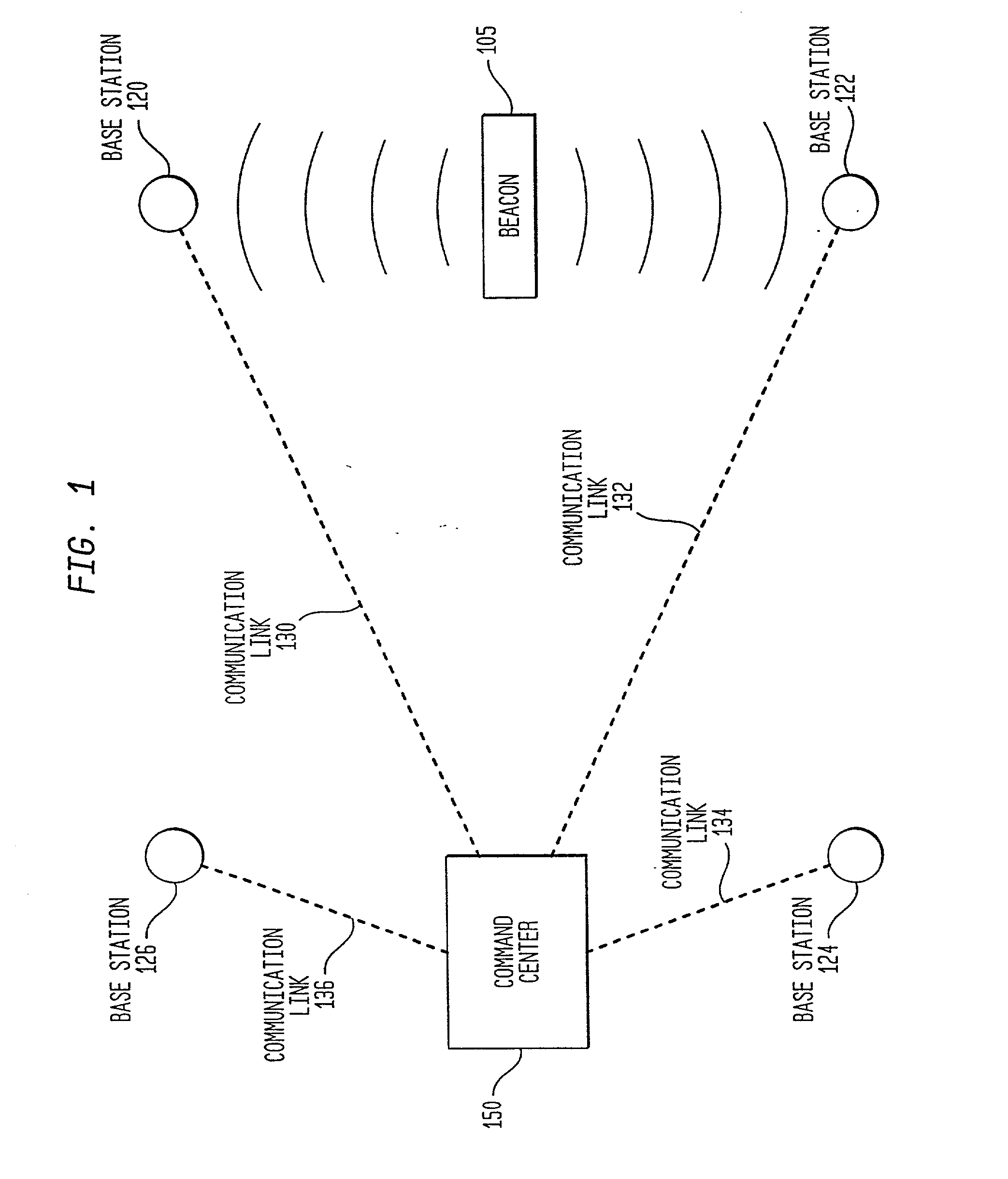
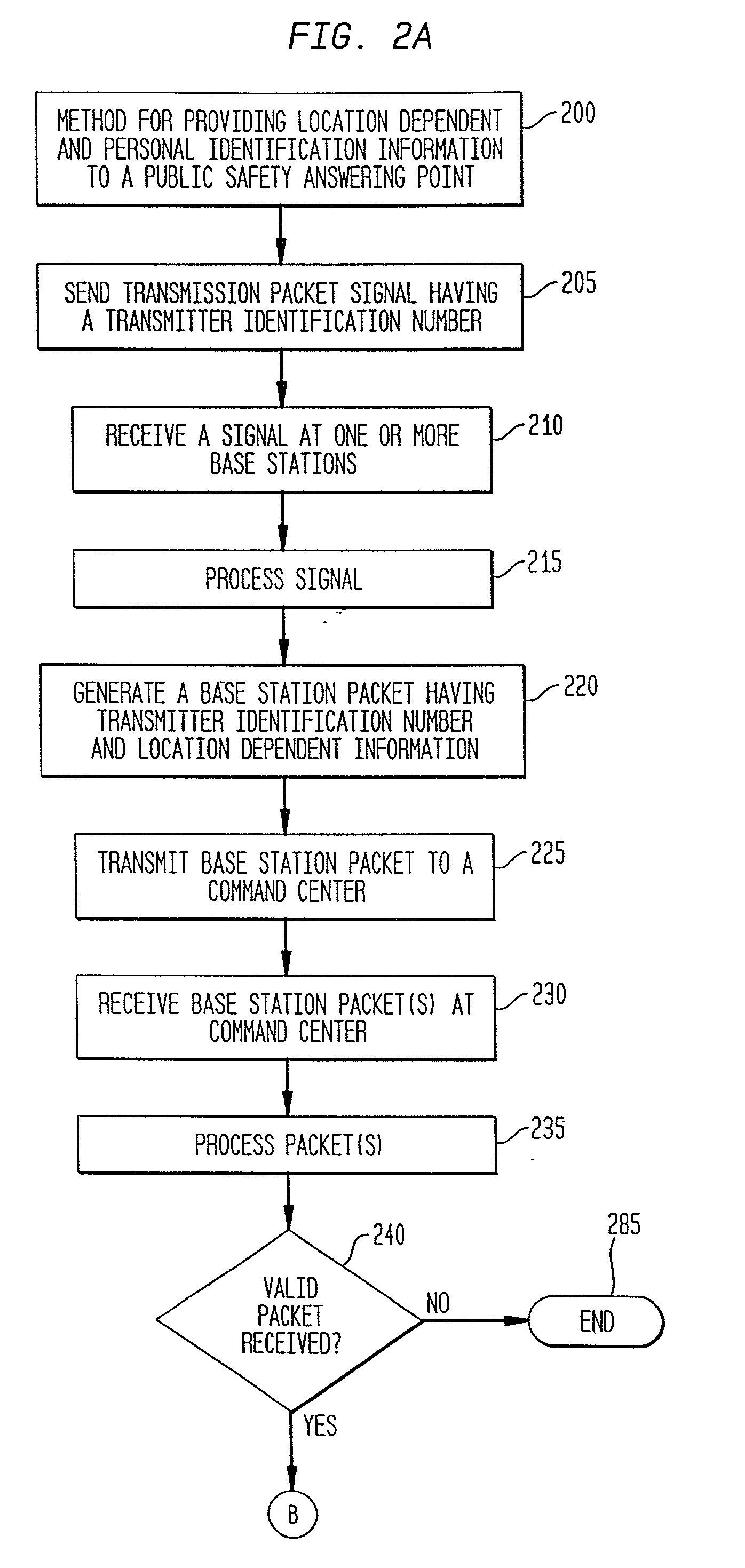
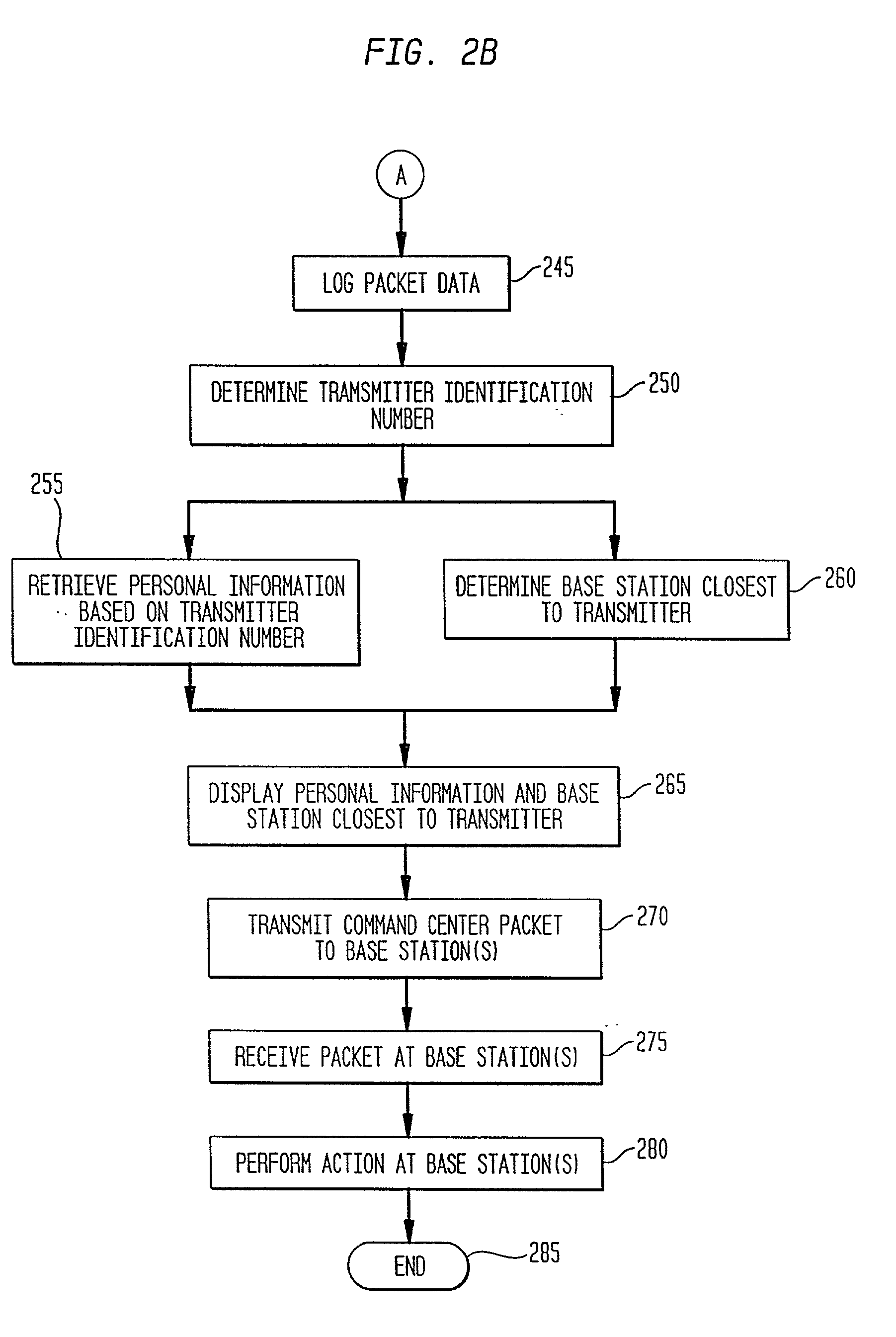
InactiveUS20010034223A1Emergency connection handlingTelephonic communicationNetwork packetSignal processing
A method and system are provided for sending location dependent and personal identification information to a public safety answering point. Base stations for receiving a transmission packet signal having a transmitter identification number are located throughout an area where personal security coverage is desired. Whenever a personal security transmitter is activated, it is received by one or more base stations. Each base station has a signal receiving unit for receiving a transmission packet signal and a signal processing unit for processing a transmission packet signal and generating a base station packet. Base station packets contain both a transmitter identification number and location information about the activated transmitter. After a base station packet is generated, it is sent to a command center for processing. If a valid base station packet is received at a command center, information contained in the base station packet is used to determine the closest base station to the activated transmitter and to retrieve personal identification information about the person to whom the transmitter was issued. This location and personal identification information is then displayed at the command center or public safety answering point.
Owner:MARYLAND UNIV OF COLLEGE PARK
Personal security and tracking system
InactiveUS6624754B1Efficient schedulingFrequency-division multiplex detailsTelephonic communicationGeolocationEngineering
The personal security and tracking system that enables an individual in distress to initiate an alarm to alert appropriate personnel combined with a locating and tracking system that enables the alerted personnel to monitor the location of the individual in distress. The system comprises a portable signaling unit includes a locating system and a manual trigger switch to provide the priority alarm levels. The central processing station receiving signals from the portable signaling unit to process and analyze the signal of interpreting the geographical location and the priority alarm signal.
Owner:RPX CORP
System and method to authenticate users to computer systems
InactiveUS7941534B2Facilitates rapid secondary logLimited accessDigital data processing detailsDrug and medicationsTransceiverTelecommunications link
Owner:DLH TECH LLC
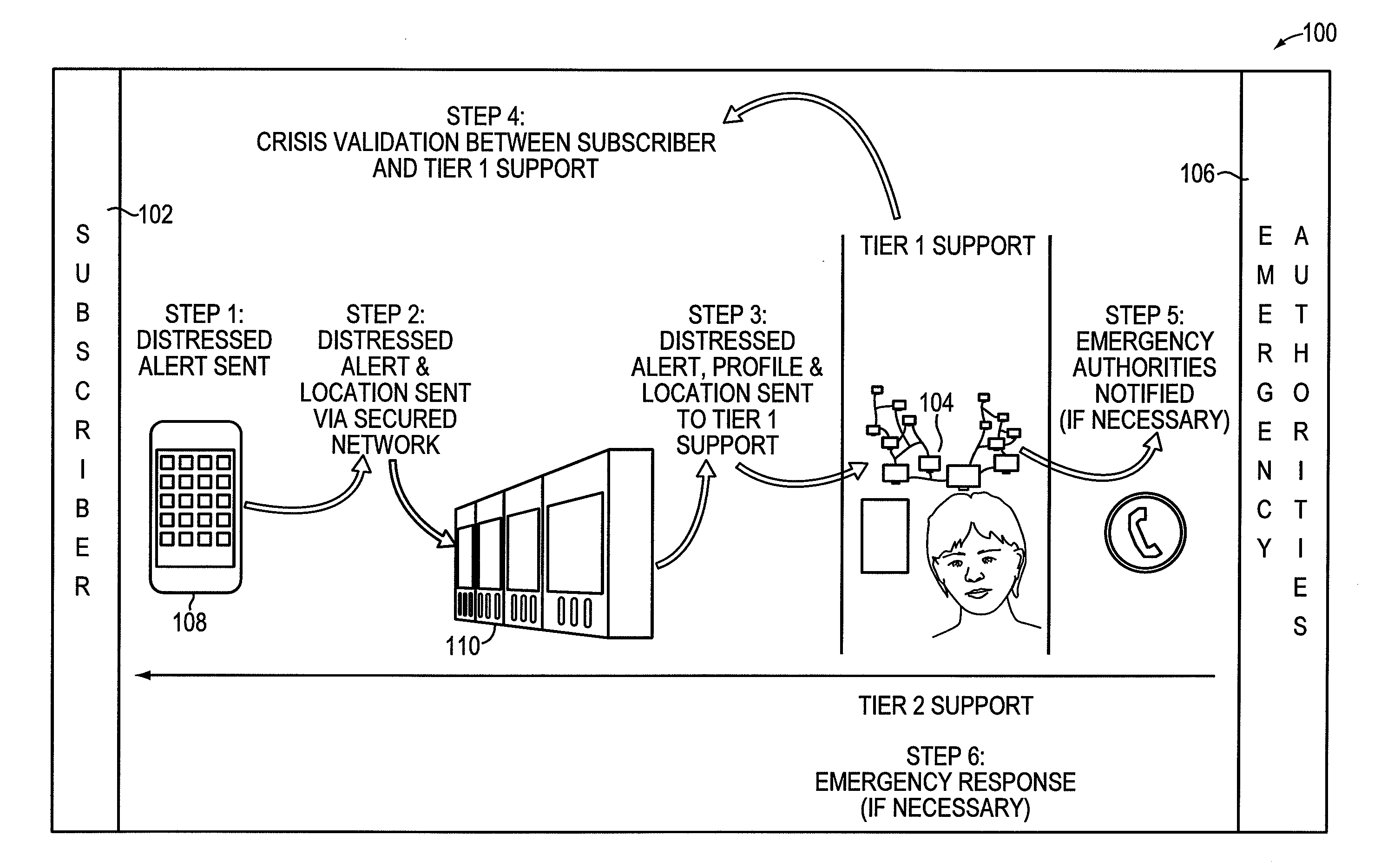
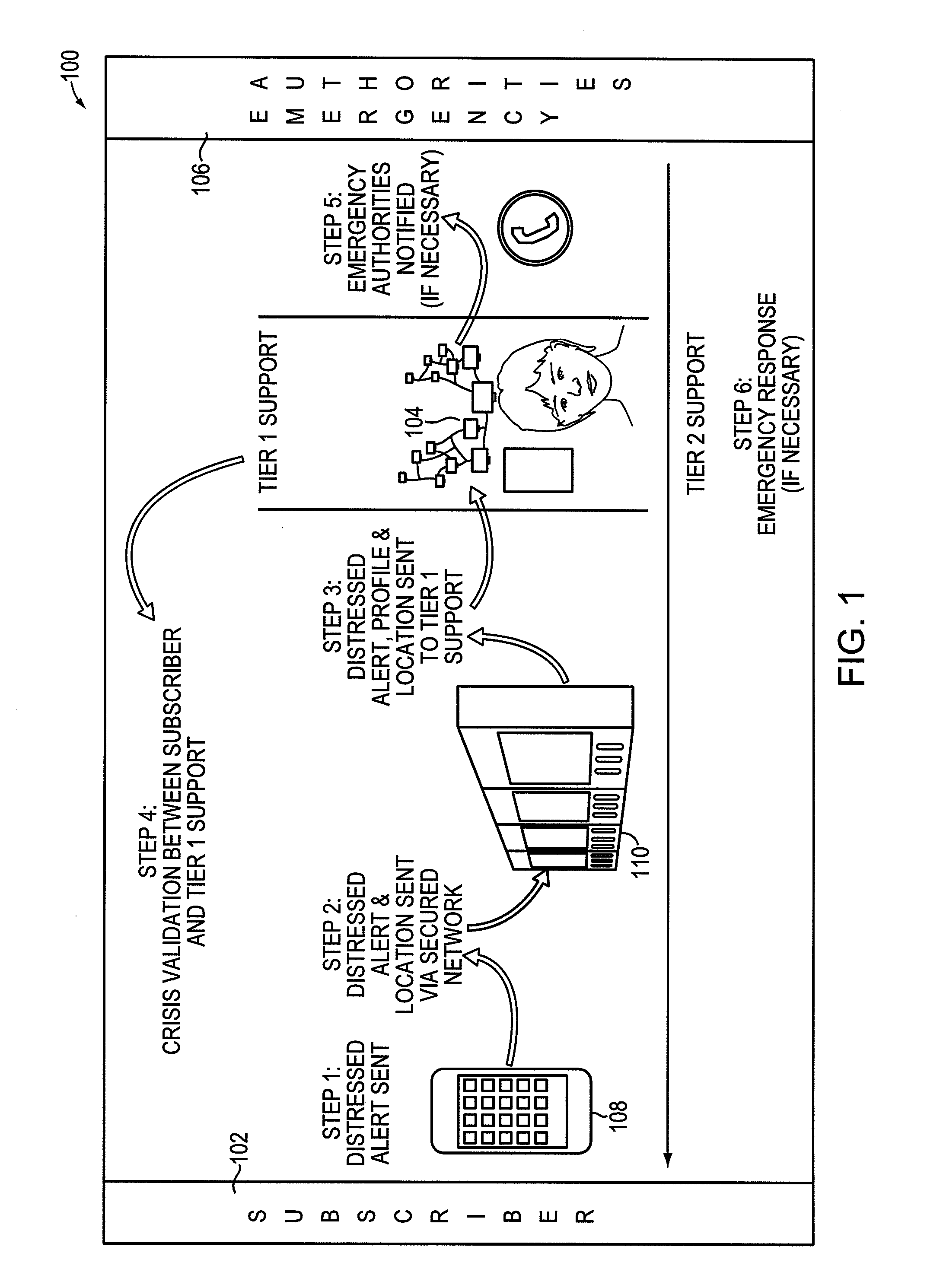
Personal safety application for mobile device and method
InactiveUS20120329420A1Emergency connection handlingSubstation equipmentThird partyTelecommunications link
A method of notifying an intermediary located remote from a user of an emergency service requested by the user associated with a mobile communication device includes receiving, at the intermediary, an alarm signal generated by a user interaction with a safety application on the mobile communication device. Upon receipt, an audio communication link or a video communication link is activated between the mobile communication device and the intermediary based on the user's interaction with the safety application. Information, such as static personal user information and dynamic location information of the mobile communication device, is presented to the intermediary. The intermediary may then contact a third party based on a communication between the user and the intermediary and a location of the mobile communication device.
Owner:MYFORCE
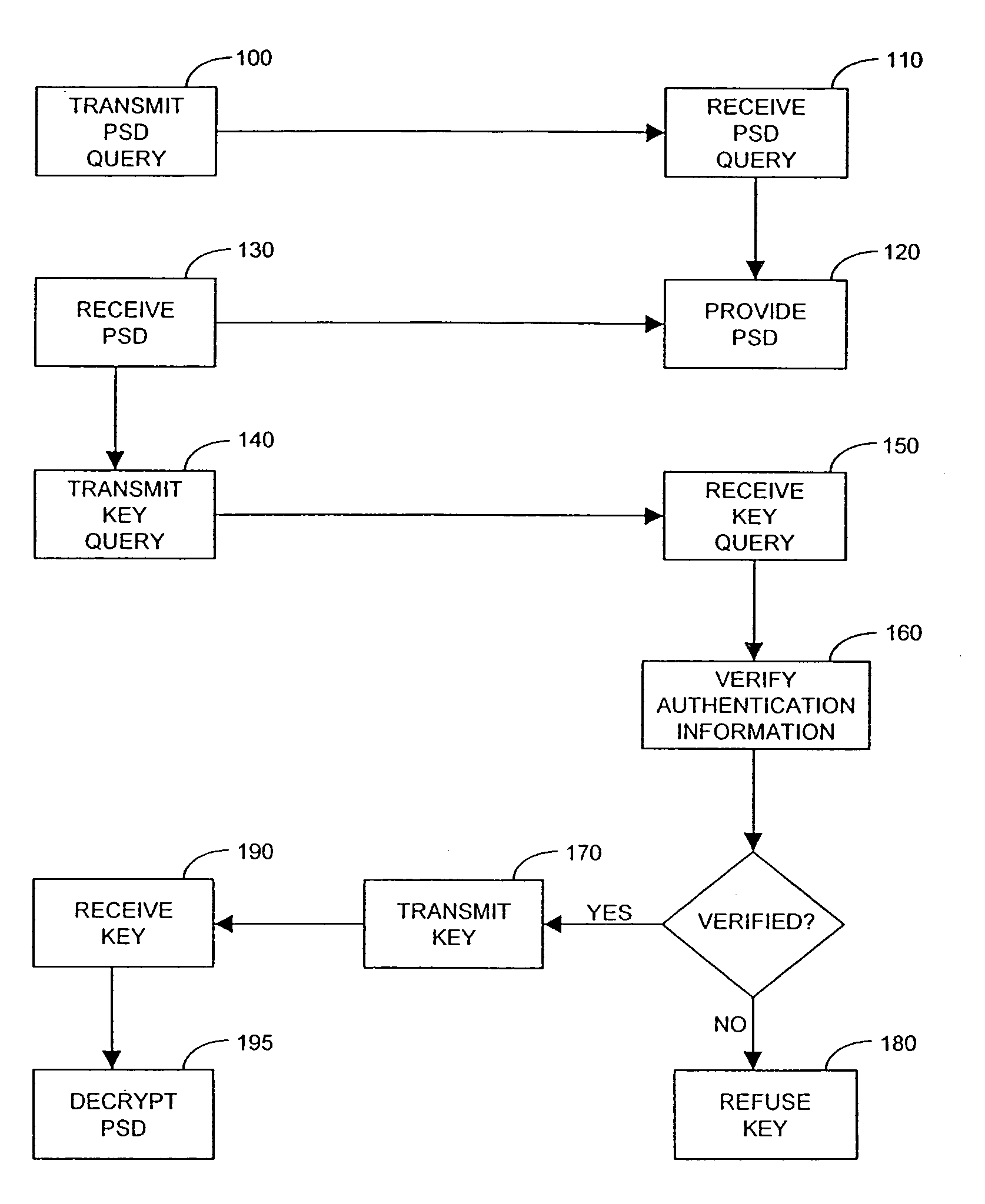
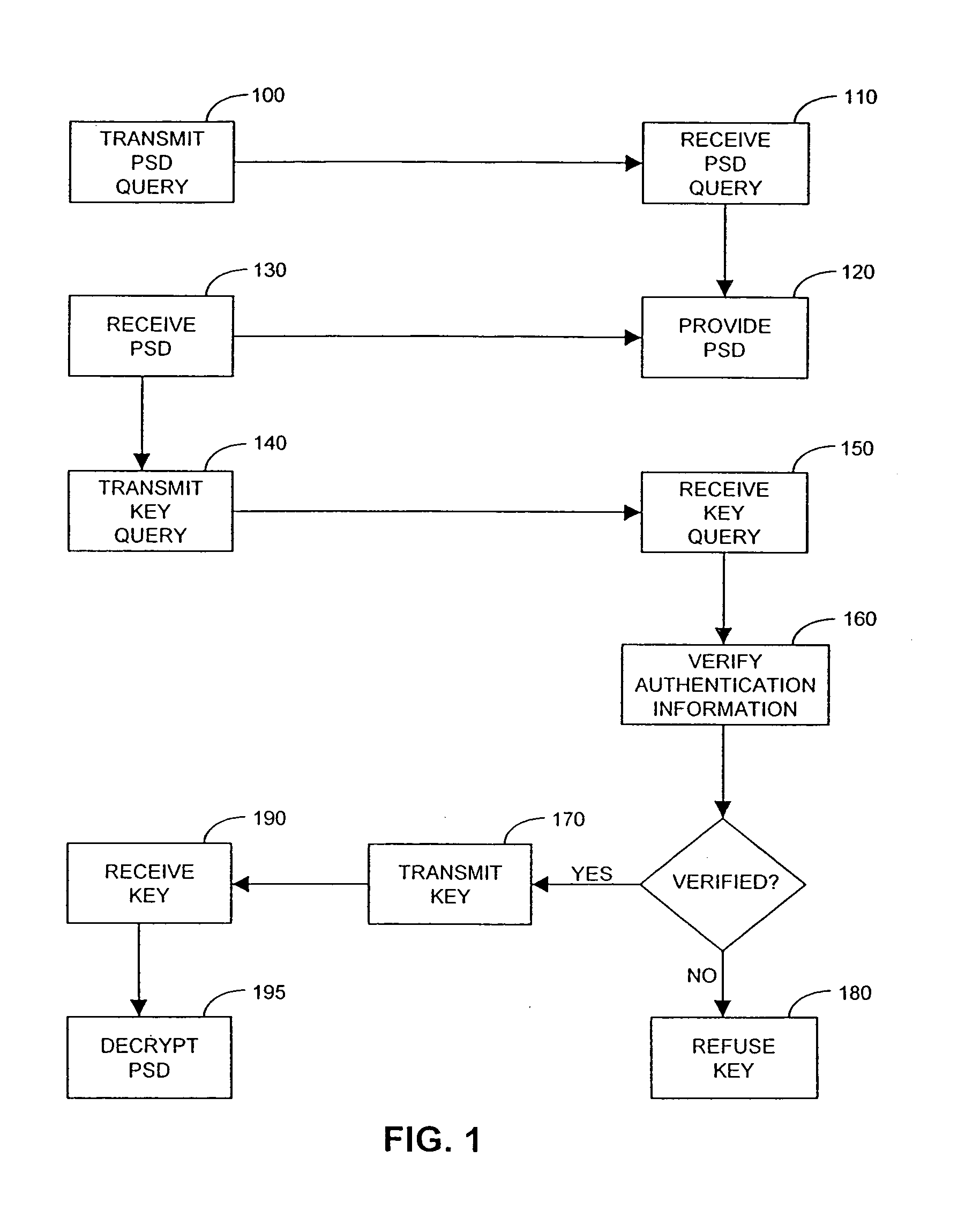
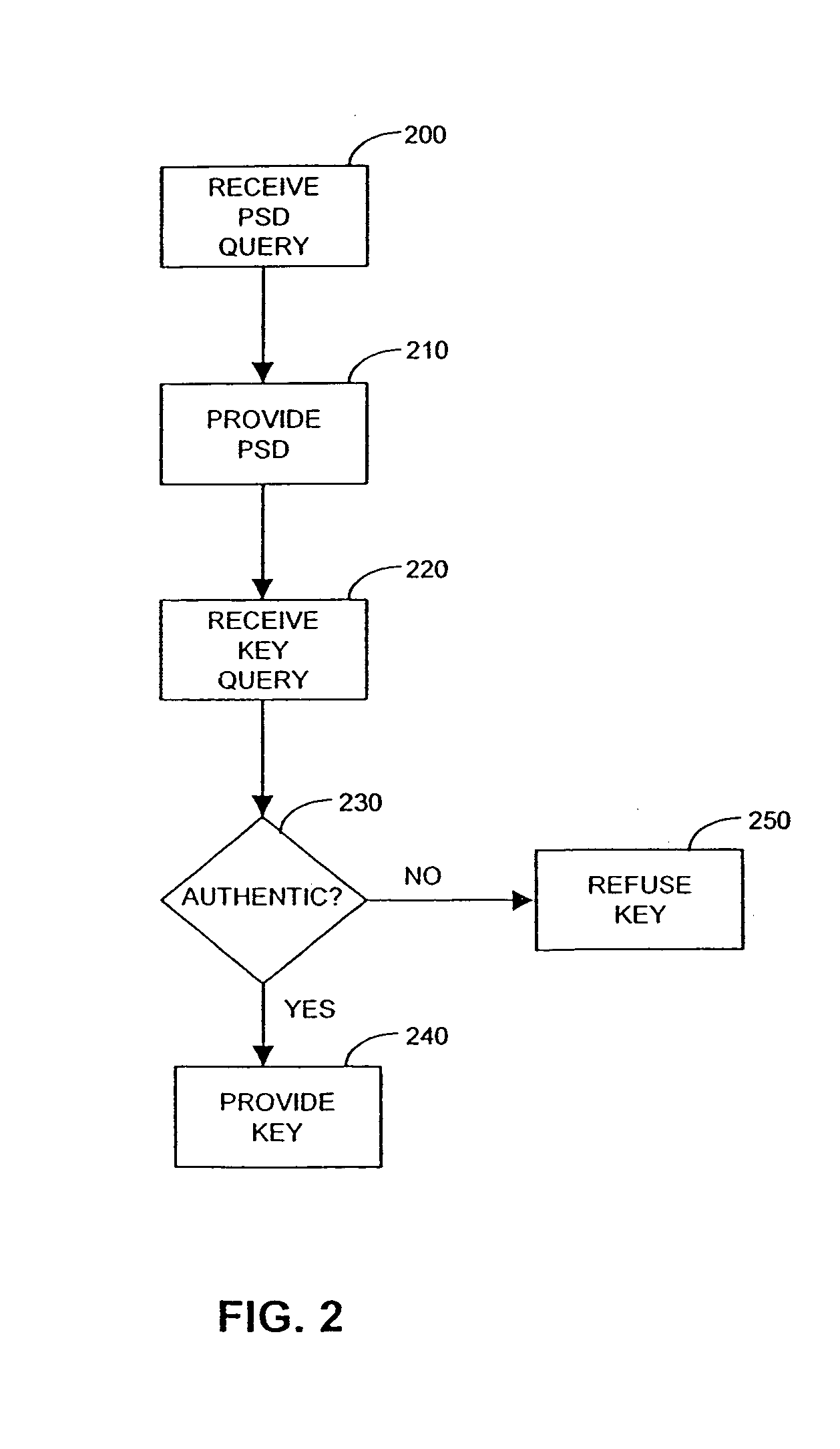
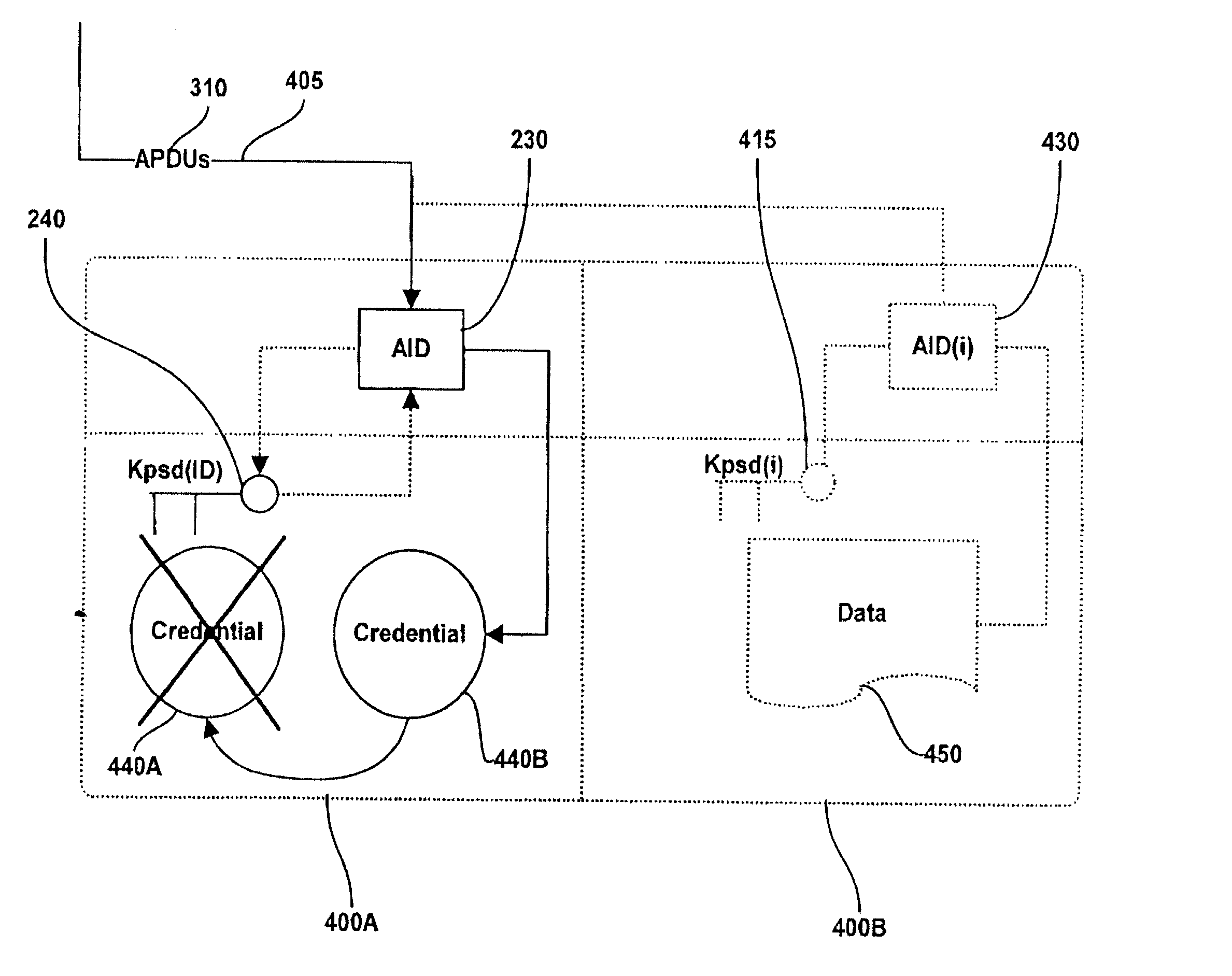
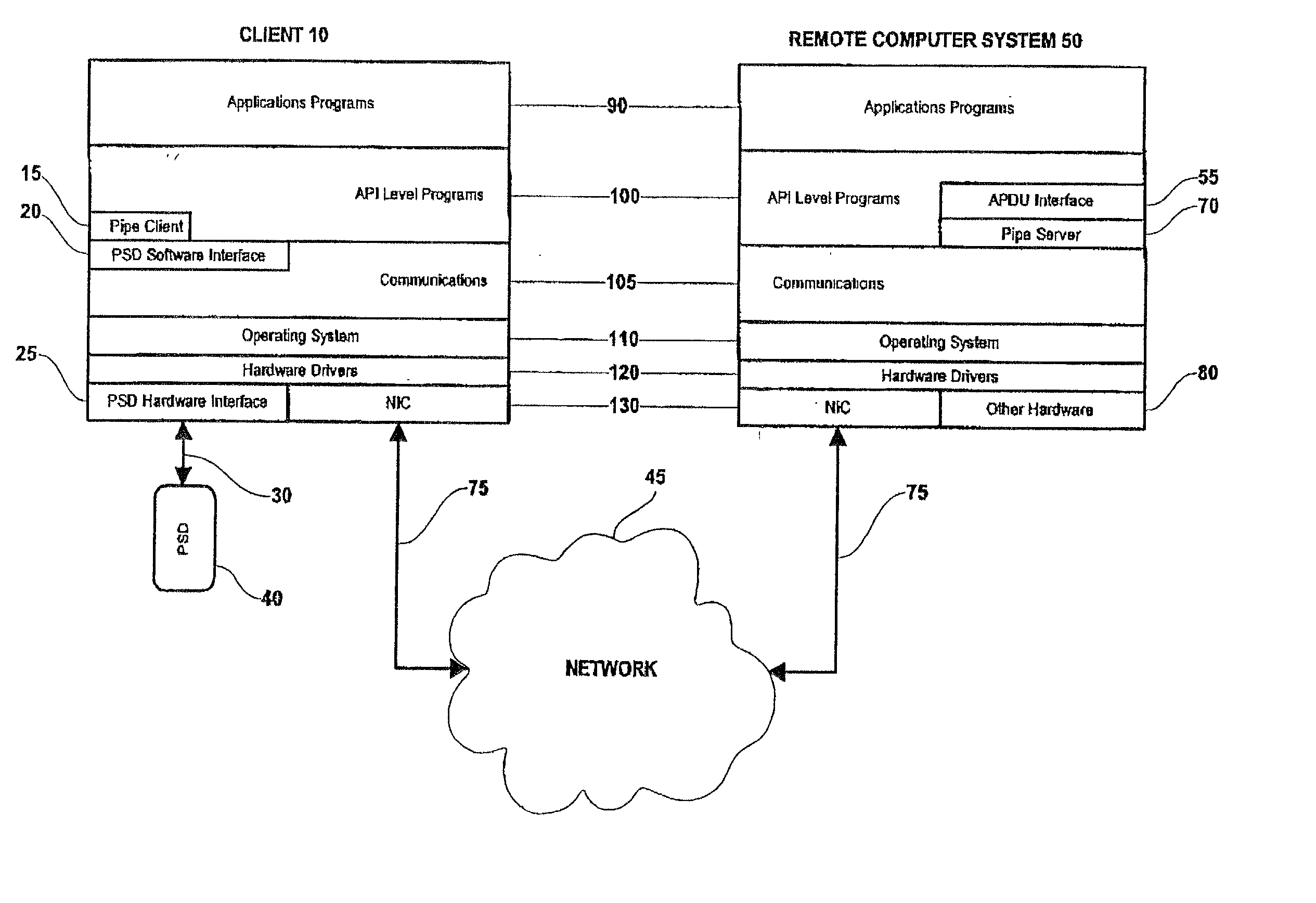
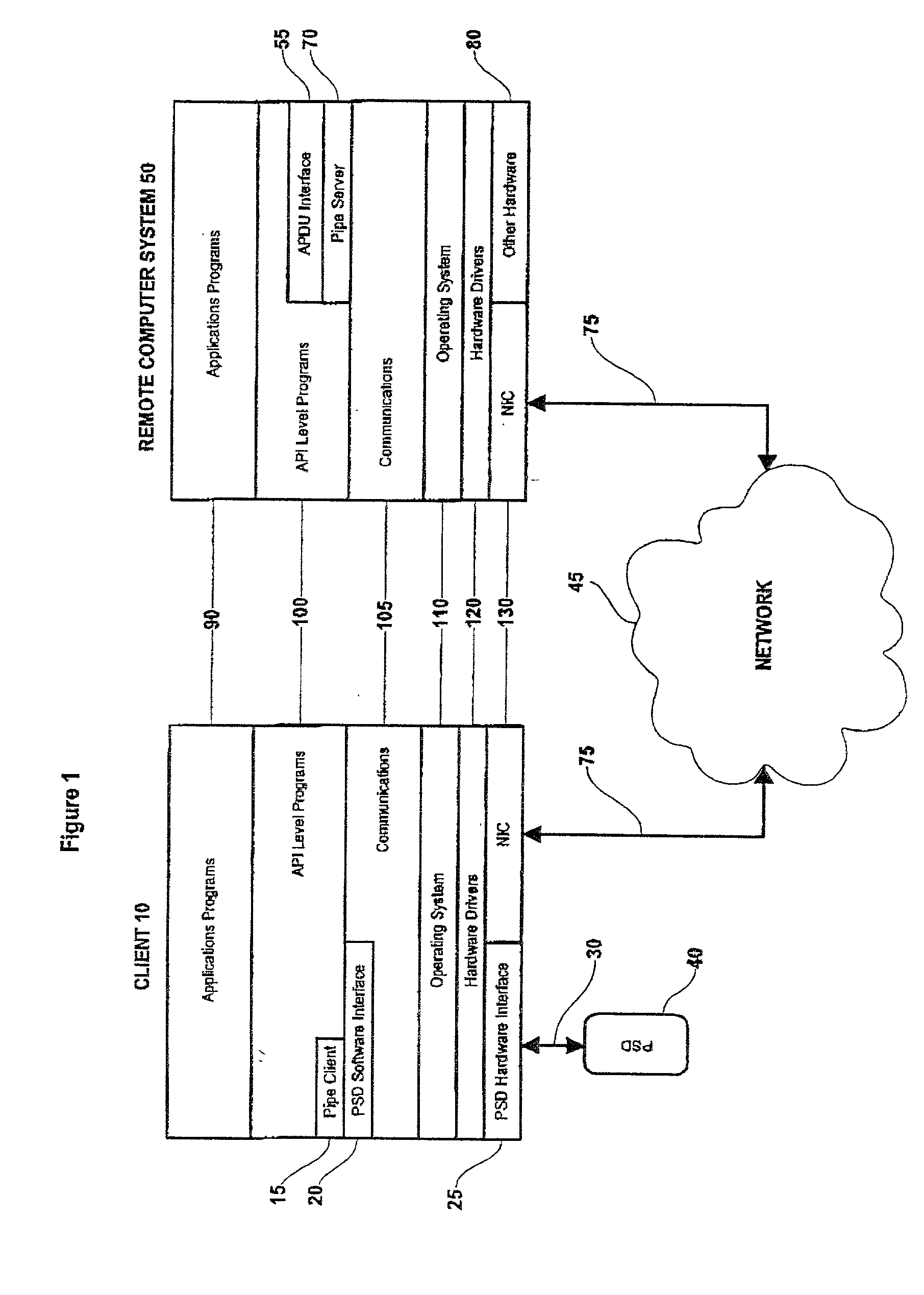
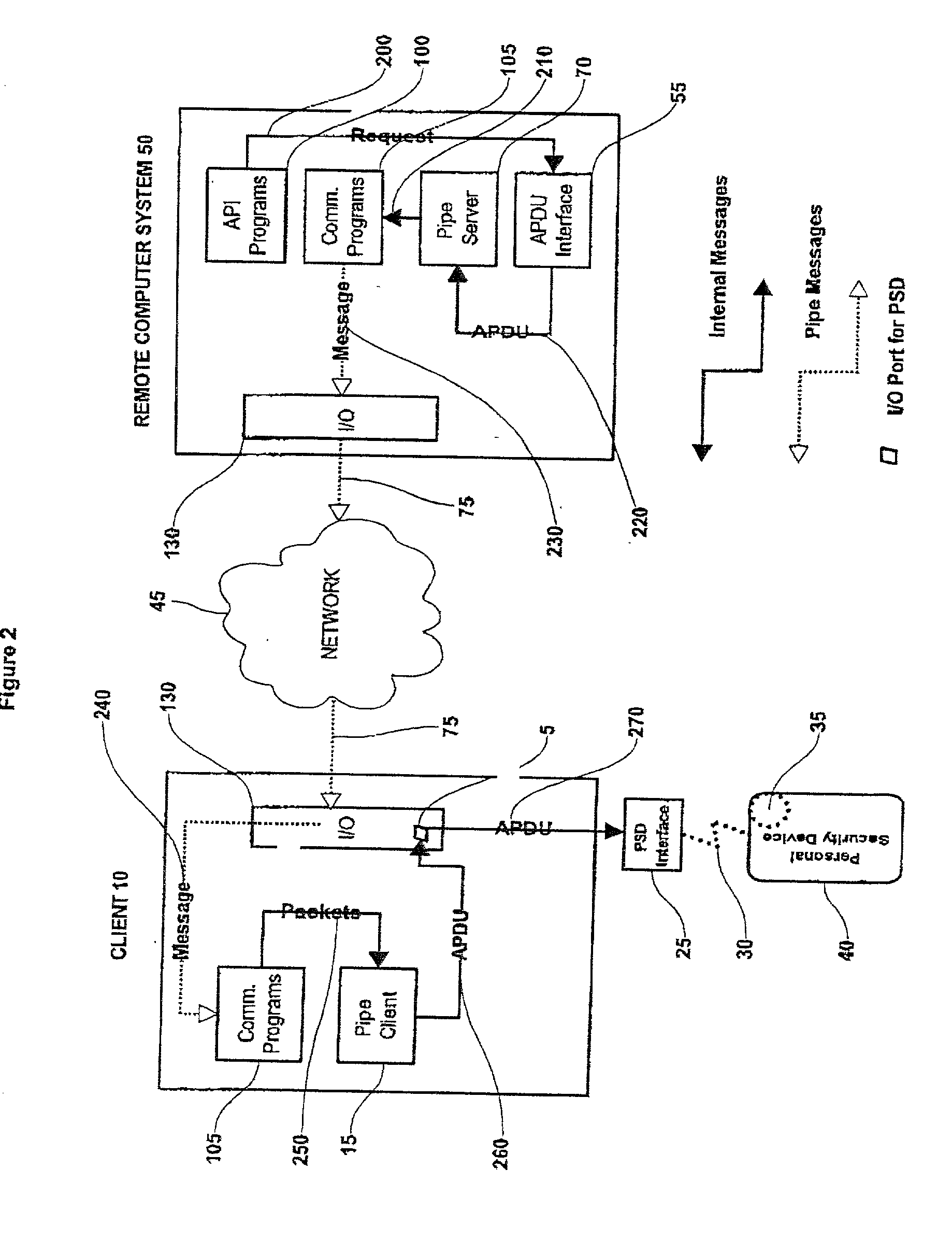
Method and system for performing post issuance configuration and data changes to a personal security device using a communications pipe
InactiveUS20030167399A1User identity/authority verificationUnauthorized memory use protectionHardware security moduleDigital credential
This invention provides a mechanism for performing secure configuration and data changes between a PSD and a hardware security module (HSM) using a communications pipe established between said PSD and said HSM. The data changes and configuration changes include but are not limited to installing, updating, replacing, deleting digital certificates, cryptographic keys, applets, other digital credentials, attributes of installed objects, or other stored proprietary information.
Owner:ACTIVCARD
Personal safety system, method, and apparatus
ActiveUS9177455B2Alarms using portable personal devicesVisible signalling systemsTransport systemComputer vision
Owner:PERPCAST
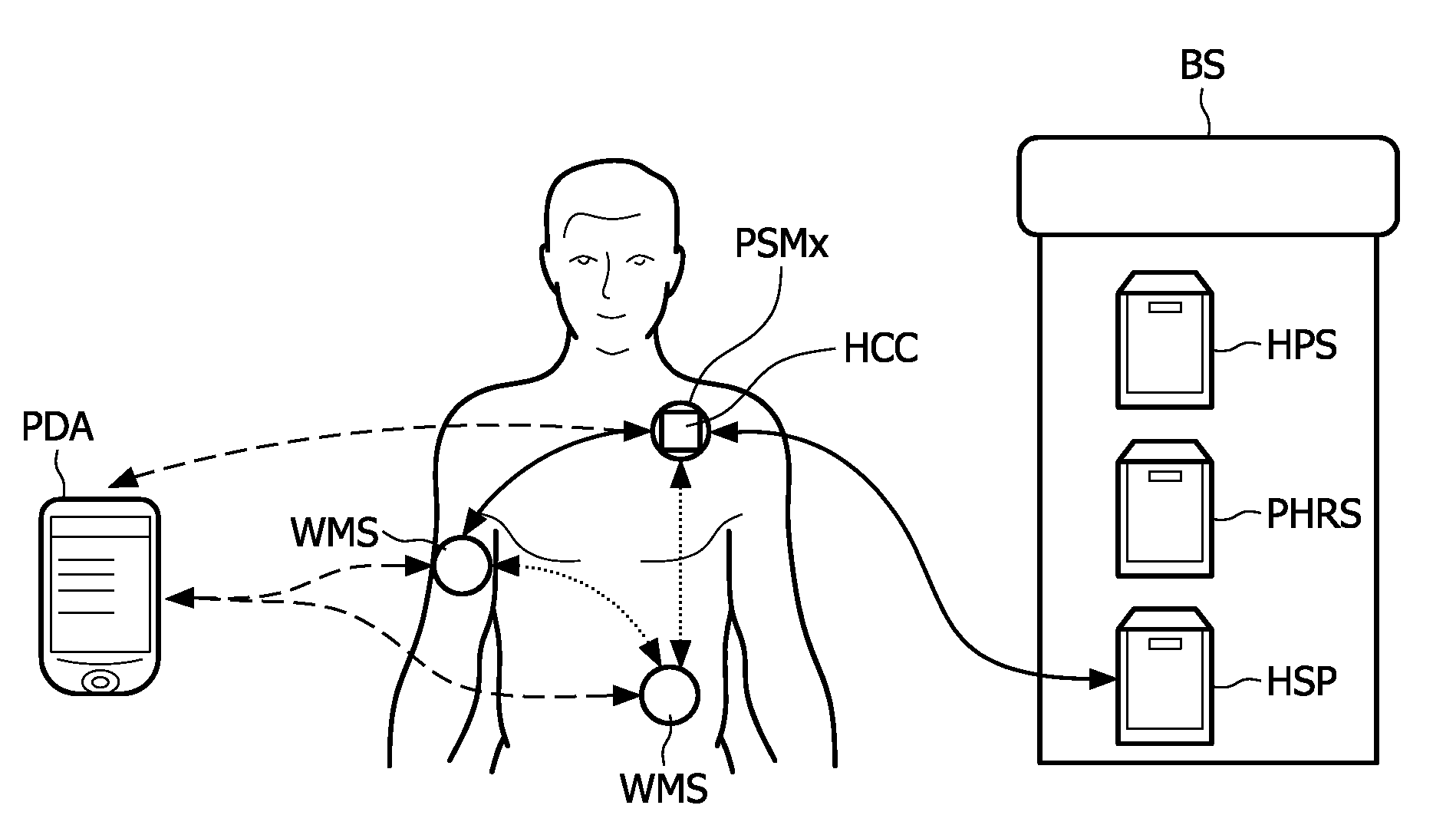
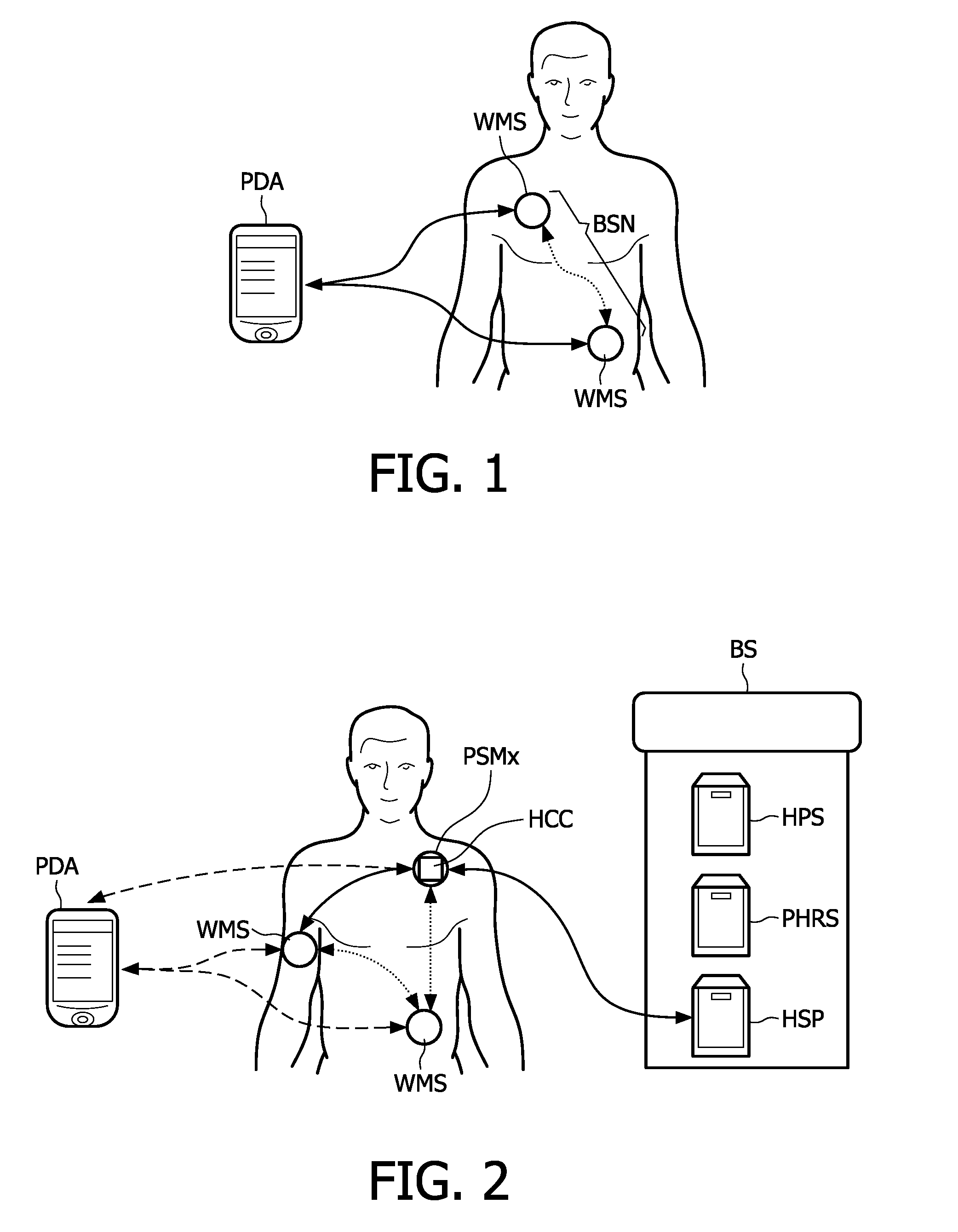
Personal security manager for ubiquitous patient monitoring
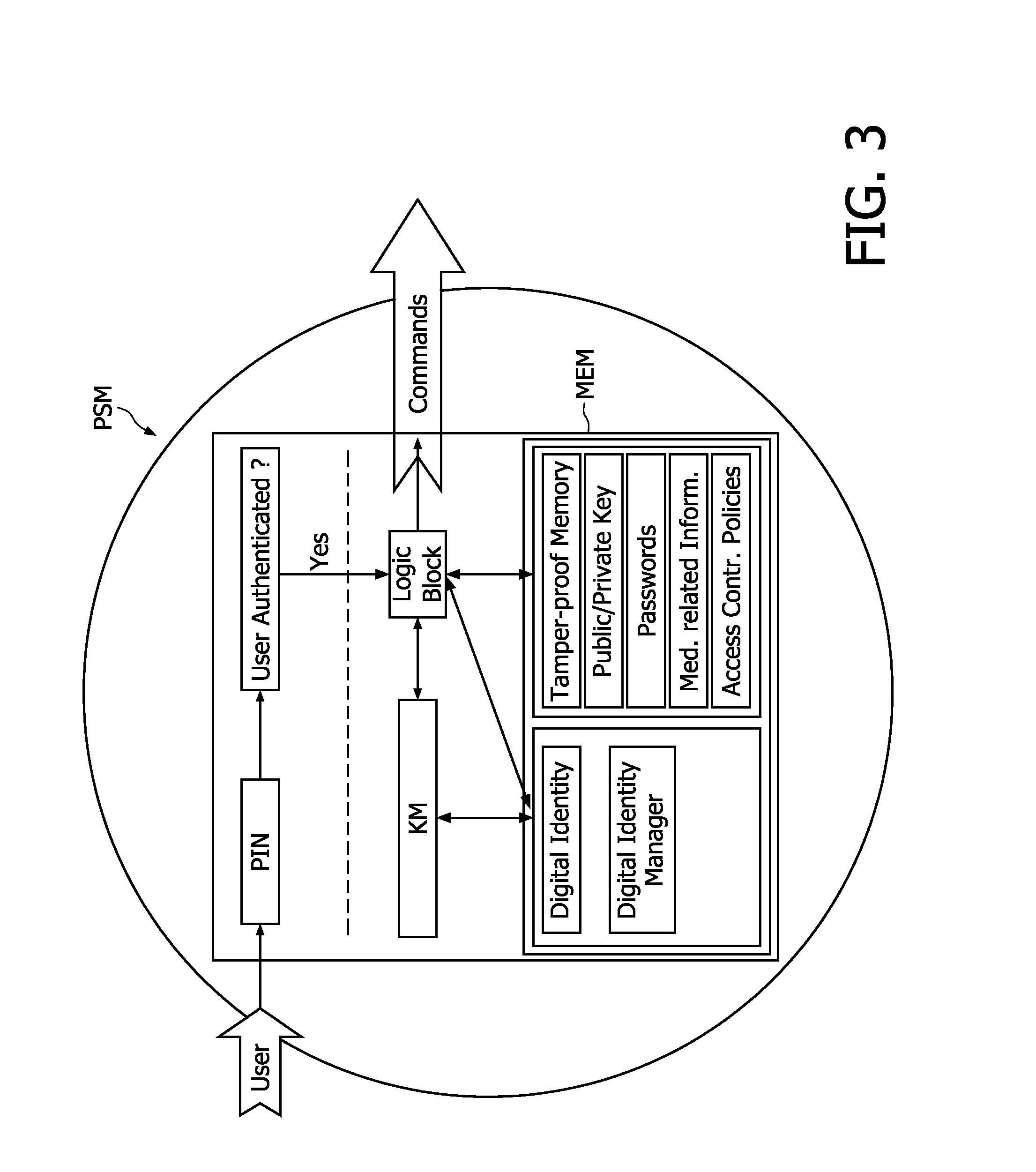
ActiveUS20110145894A1Effective and secure accessEffective access controlDigital data processing detailsDigital data protectionSecure communicationPersonal security
The present invention relates to a system and corresponding method for a secure end-to-end patient healthcare system which includes wireless medical sensors adapted to be attached to a patient's body and in communication with each other forming a body sensor network within a wireless medical sensor network including one or more body sensor networks; λ-secure keying means incorporated into each wireless medical sensor for enabling secure communications between the wireless medical sensors, and a personal security manager within the body sensor network and in communication with the wireless medical sensors within the body sensor network, the personal security manager providing secure communications with backend services and providing security relationships within the body sensor network by means of the λ-secure keying means, wherein the λ-secure keying means are such that a coalition of no more than λ compromised wireless medical sensors conceals a pairwise key between any two non-compromised wireless medical sensors and provides protection against node compromise until λ+1 wireless medical sensors have been compromised.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
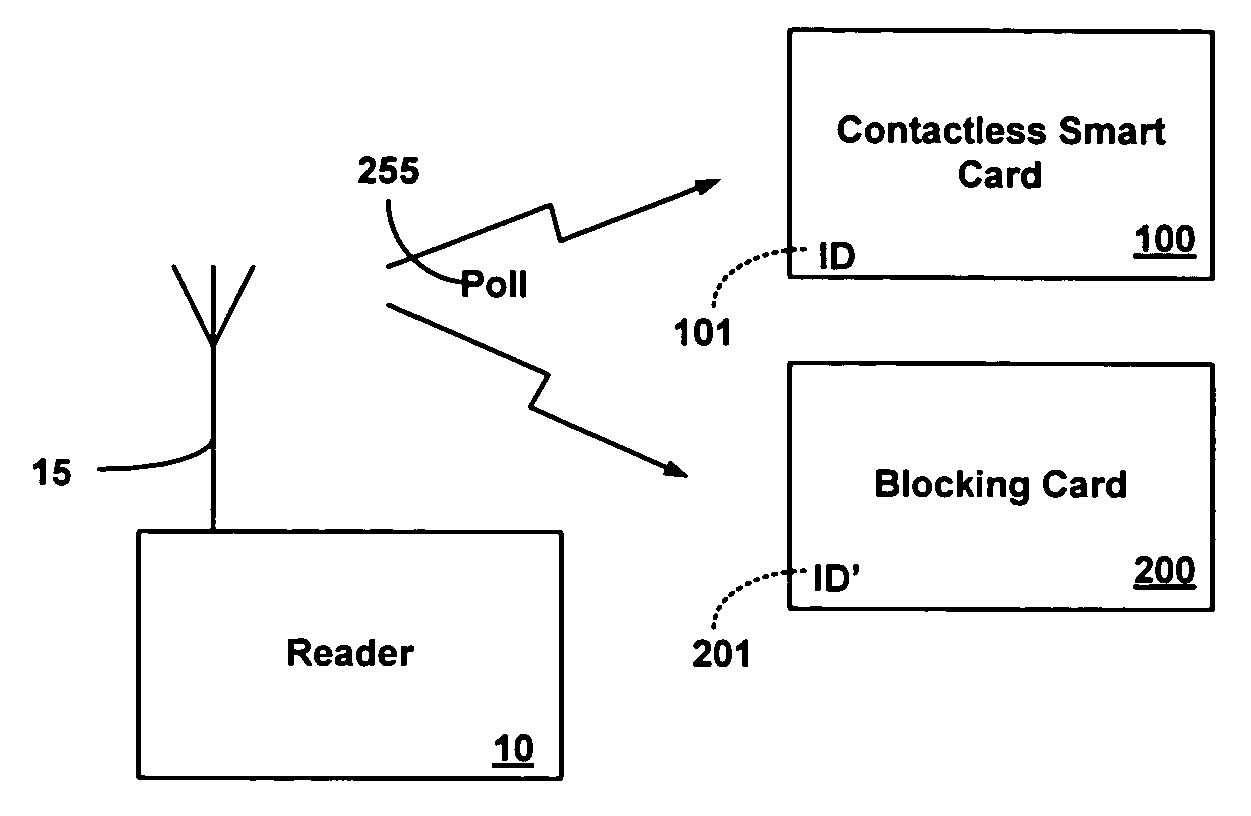
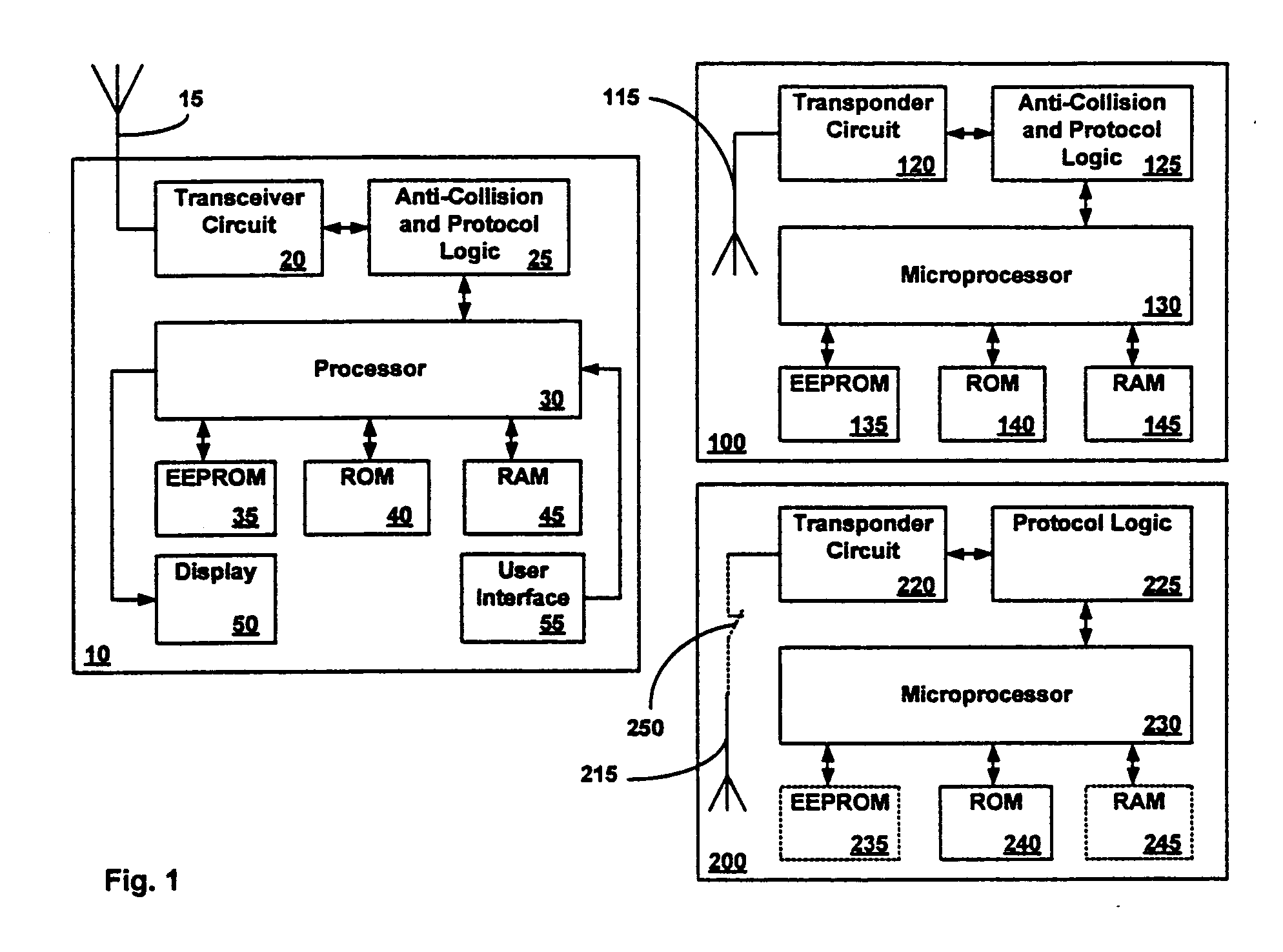
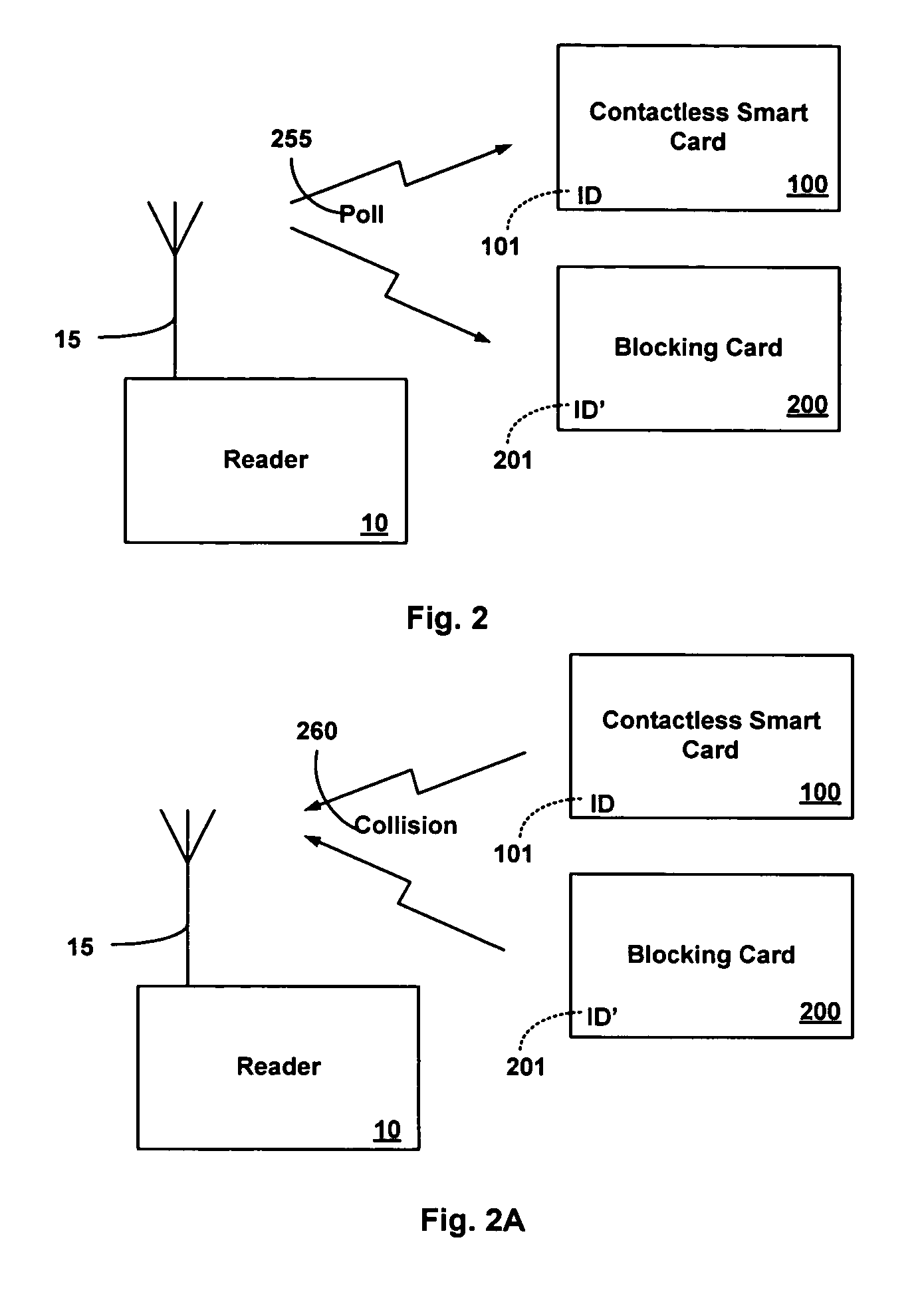
Blocking contactless personal security device
A blocking Personal Security Device (PSD) is disclosed which is intended to protect the privacy of one or more contactless PSDs present within a common RF field generated by a contactless PSDs RF reader. The blocking PSD is programmed to exploit an anti-collision protocol used by the RF reader. The blocking PSD prevents the RF reader from accessing a contactless PSD within the common RF field by ignoring wait time commands and repeatedly responding to the RF reader's interrogations.
Owner:ACTIVIDENTITY
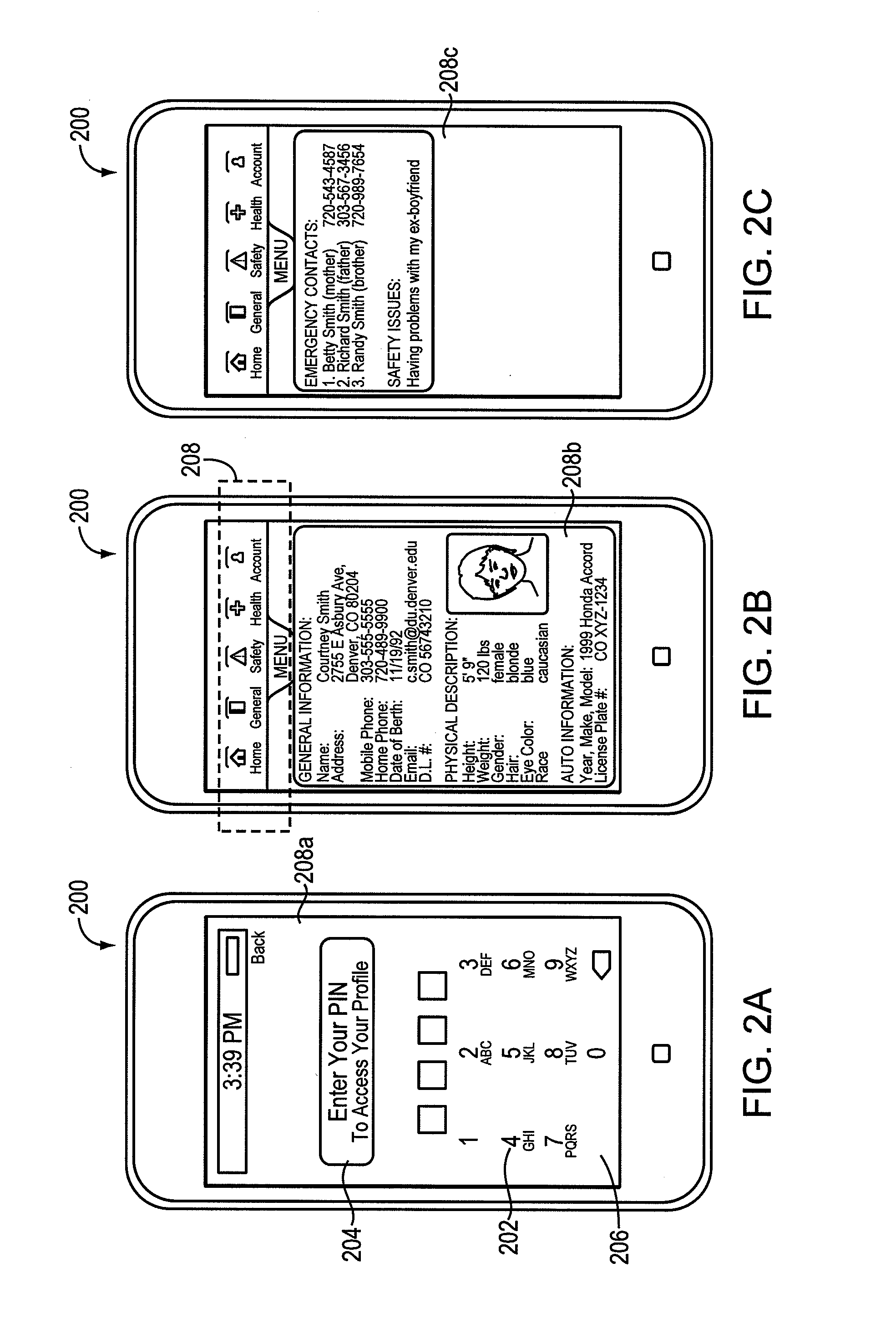
Computerized method and system for global health, personal safety and emergency response
A computerized system and method for intuitively detecting a user's need for emergency help, preventive care and medical interventions and also for coordinating care for user's loved ones and pets when user experiences an emergency or has passed away. Detection is done via labs and life signs equipment and sensors, self-initiated request for monitoring or the system's periodically polling user through an alert, a telephone call, a notification, a text message or other appropriate means to find out if they are in danger. Polling and automated monitoring may also be triggered by real-time medical data electronically or wirelessly transmitted to the system. If user fails to respond, the system automatedly calls either user's contacts (by listed priority) to notify them of a potential emergency, or emergency responders directly depending on severity of the emergency and communicates to them critical information as well as a code to access user's medical record(s).
Owner:VINCENT MELISSA
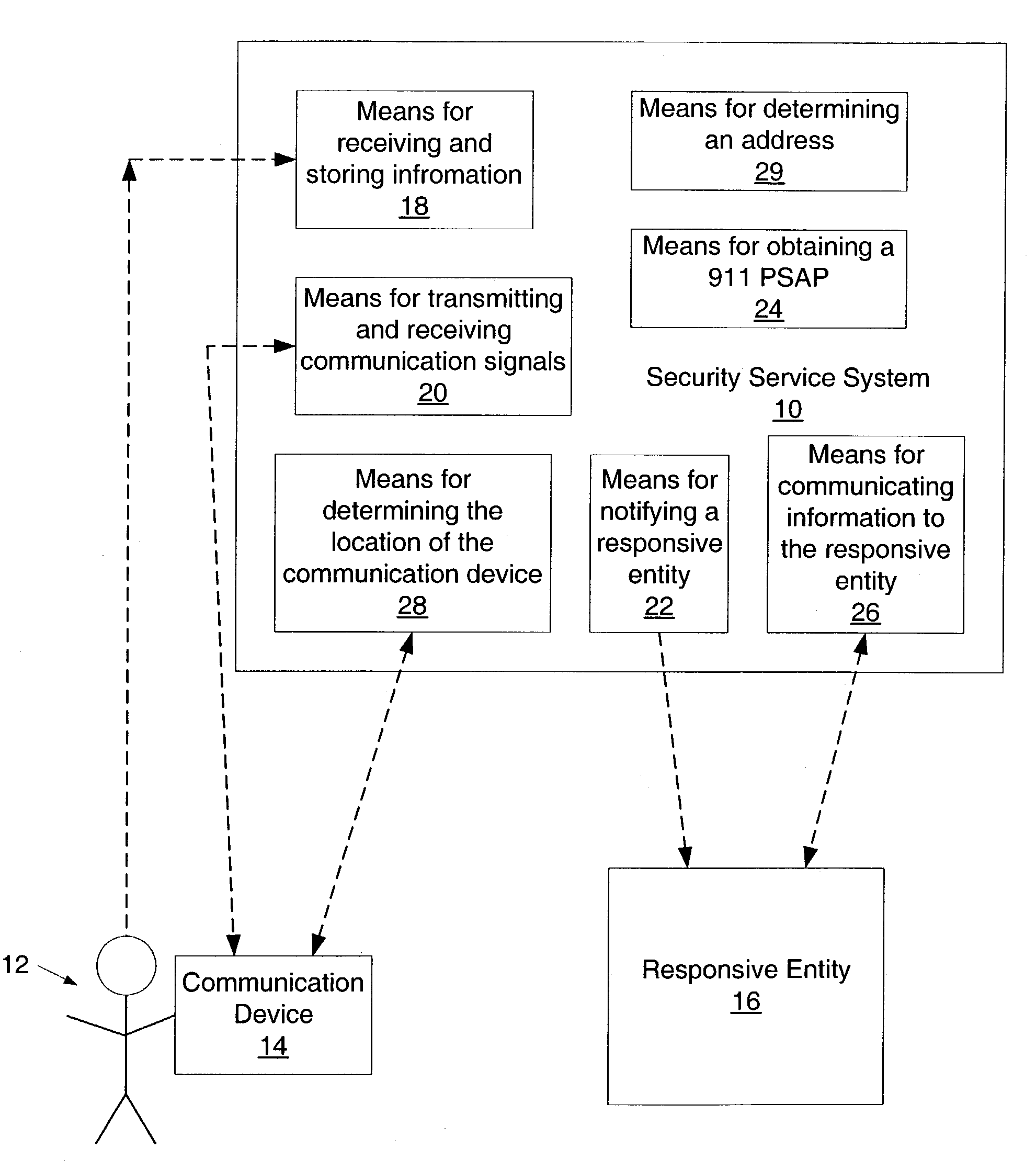
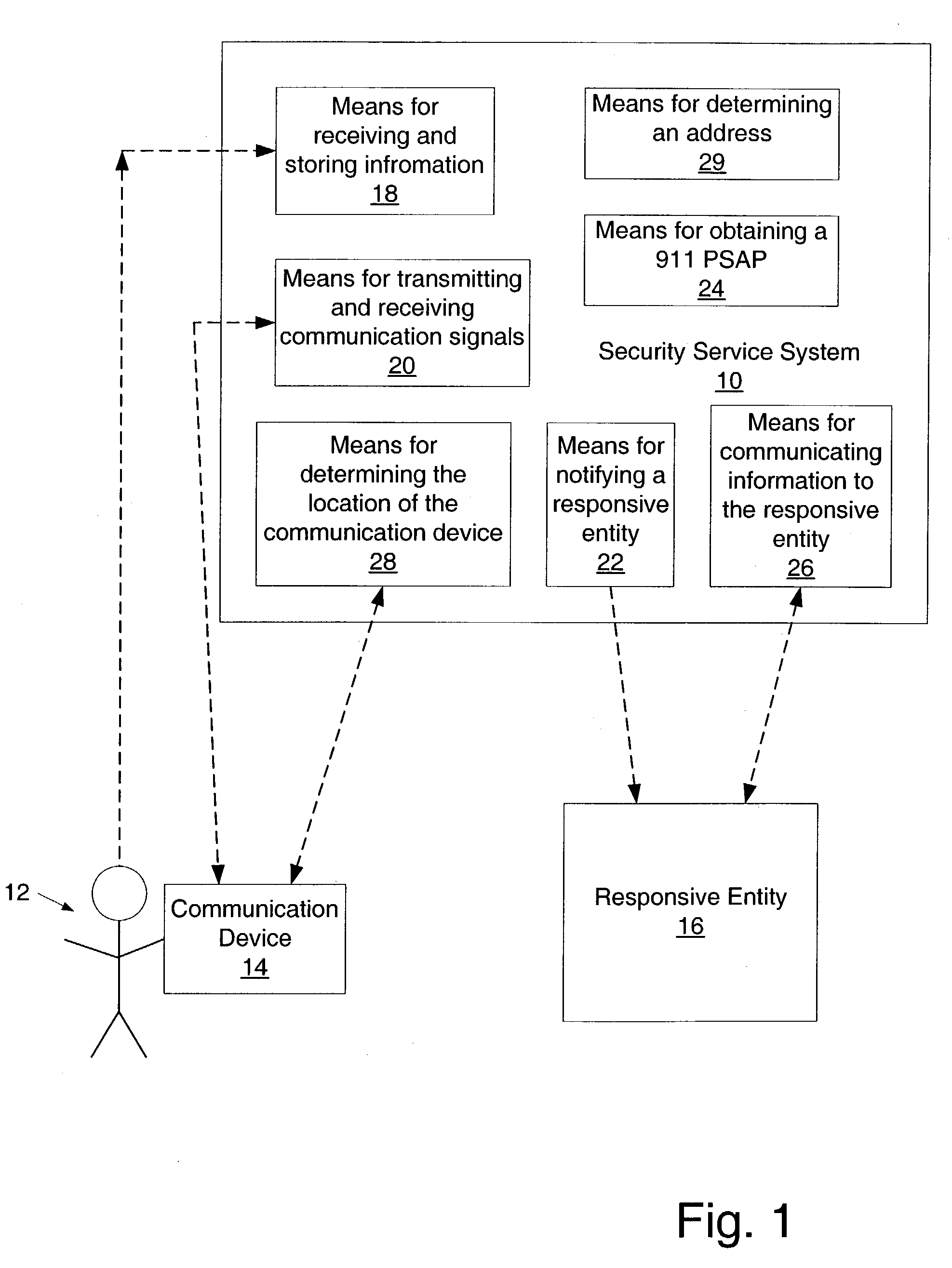
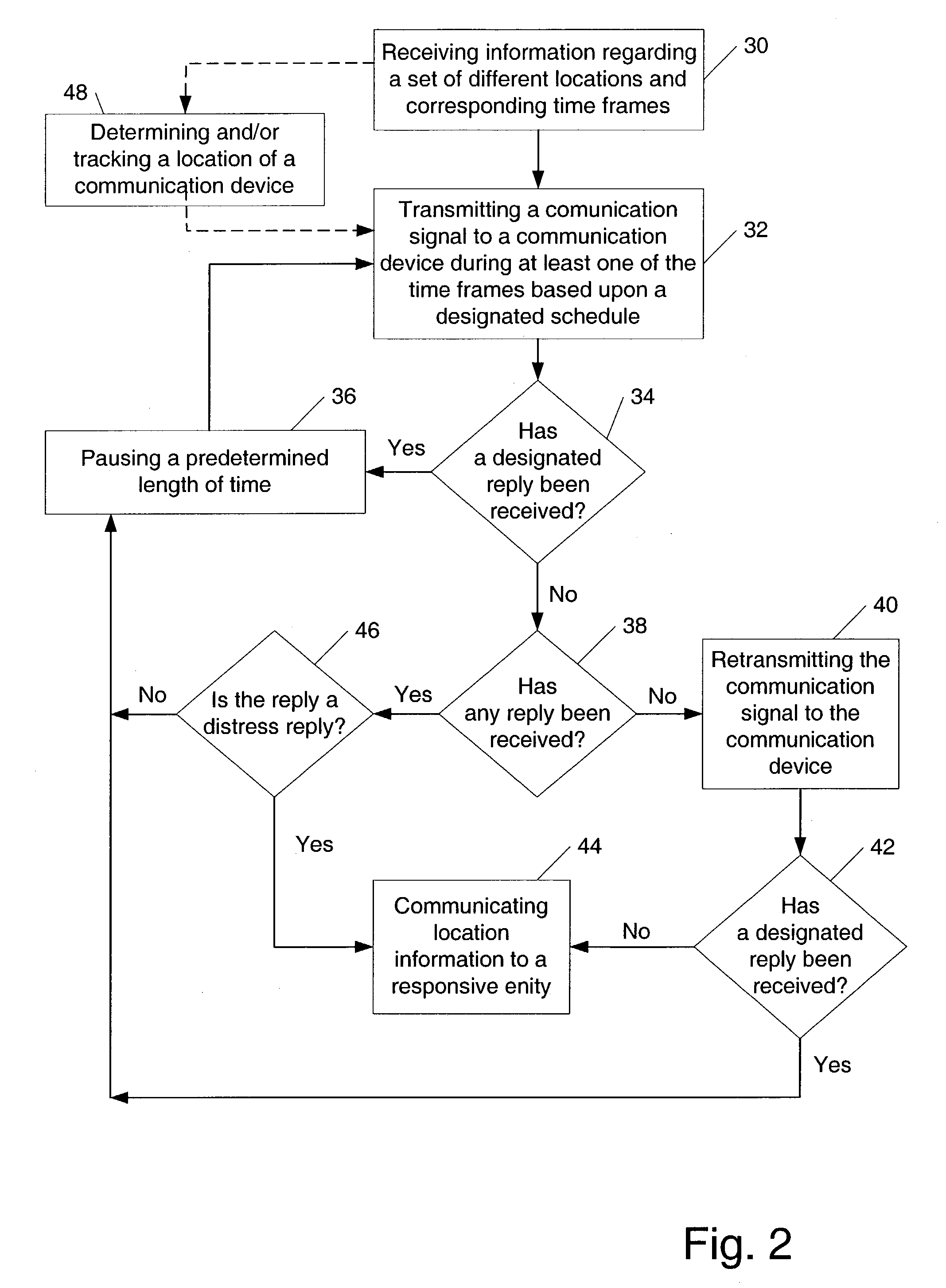
Portable personal security system
A system which is adapted to provide a personal security system to a mobile individual is presented. In addition, a method for providing a security system to a mobile individual is presented as well as a method of using such a security system. In general, the method of providing a personal security system to a mobile individual using the system described herein may include receiving information regarding a set of different locations and corresponding time frames. In addition, the method may include transmitting a communication signal to a communication device during at least one of the time frames based upon a designated schedule. Subsequently, the method may include determining a subsequent course of action based upon whether a designated reply has been received in response to the transmitted communication. In some cases, the method may include notifying a responsive entity of location information upon failing to receive the designated reply.
Owner:RESOURCE CONSORTIUM LTD LLC +1
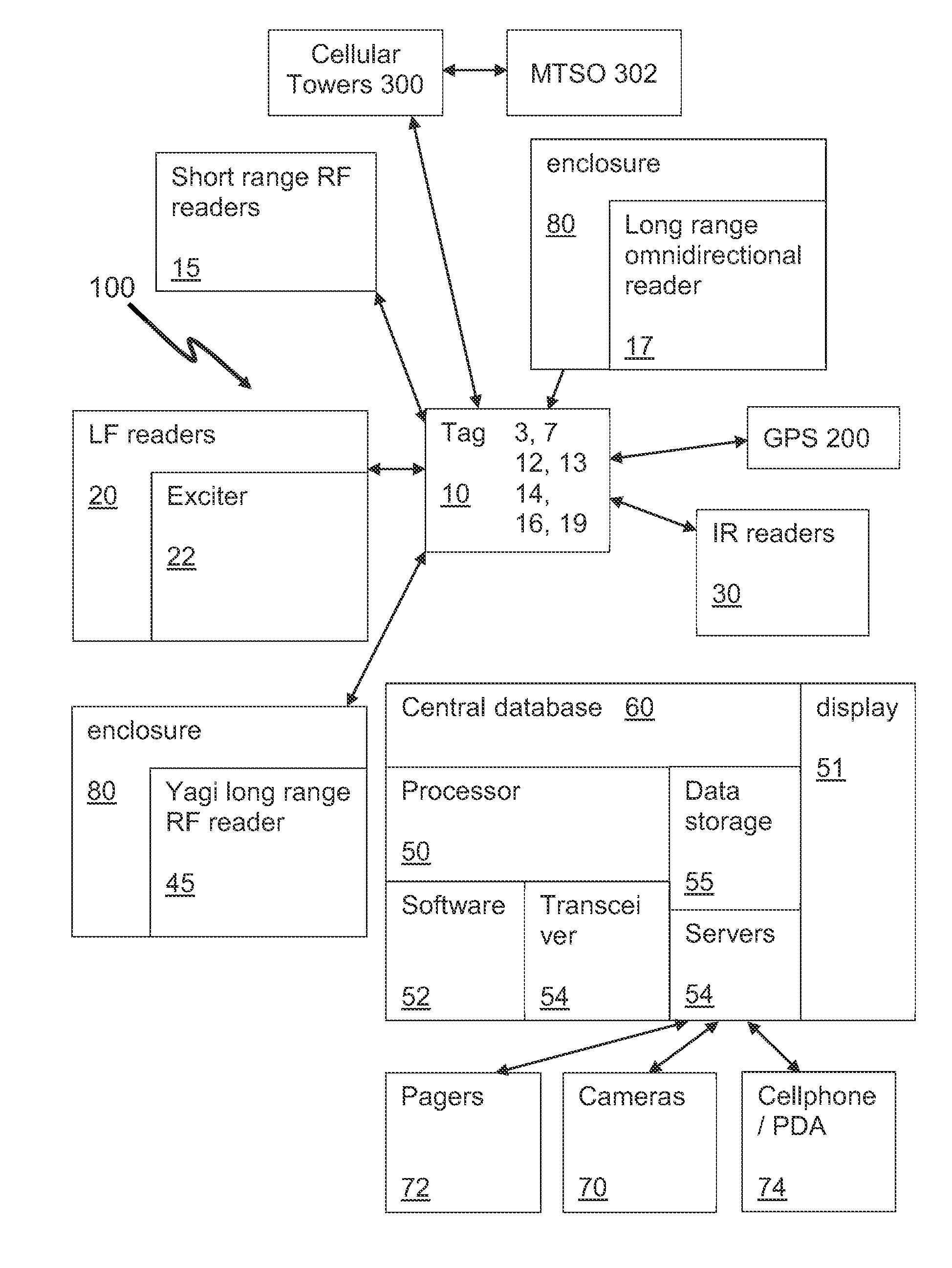
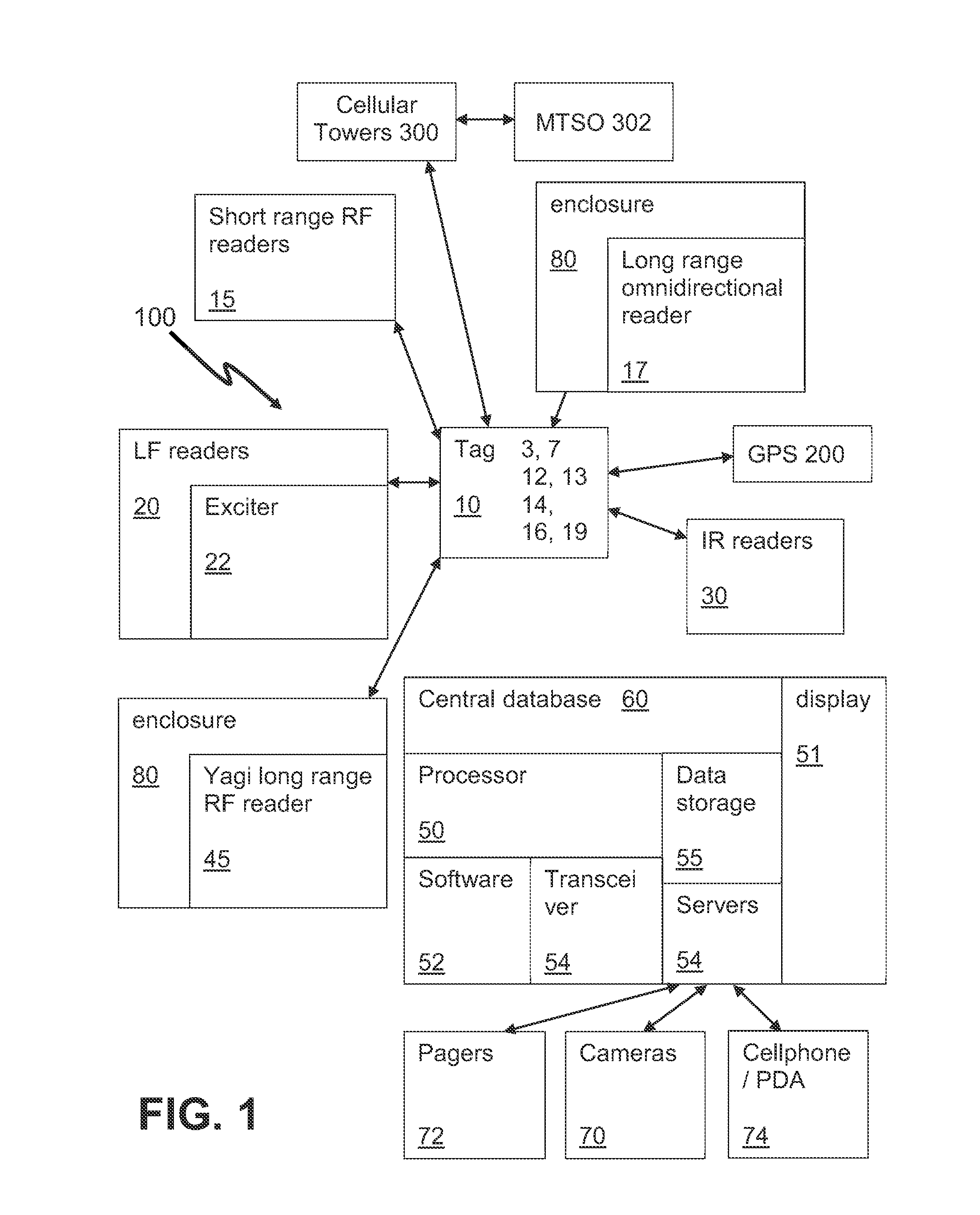
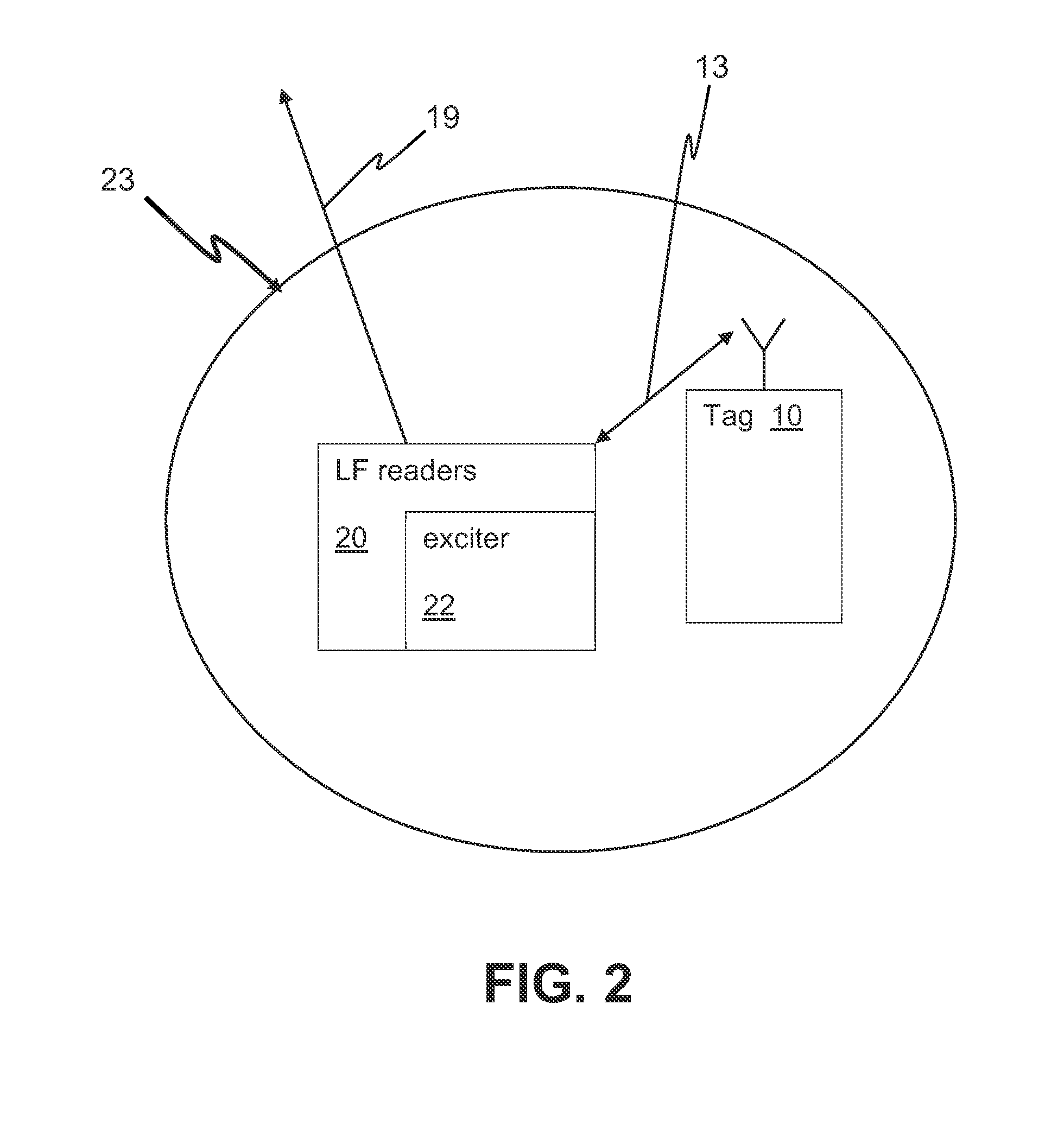
Indoor/Outdoor Personal Security System
InactiveUS20140206307A1Provide securityEmergency connection handlingTelephonic communicationTriangulationCentral database
A security system uses tags that are able to receive time signals sent from the GPS satellites or the broadcasting radio signals from the cell towers and transmit the identification and location information or signals to the central database and server for triangulation / trilateration periodically or in the event of an emergency. A security system uses tags that are able to transmit RF signals to readers located around a college campus. The tags may transmit signals periodically or in the event of an emergency. Certain locations use LF readers with exciters that trigger a signal from the tag. The security system may provide quick identification and location of individuals in danger.
Owner:MAURER MICHAEL +5
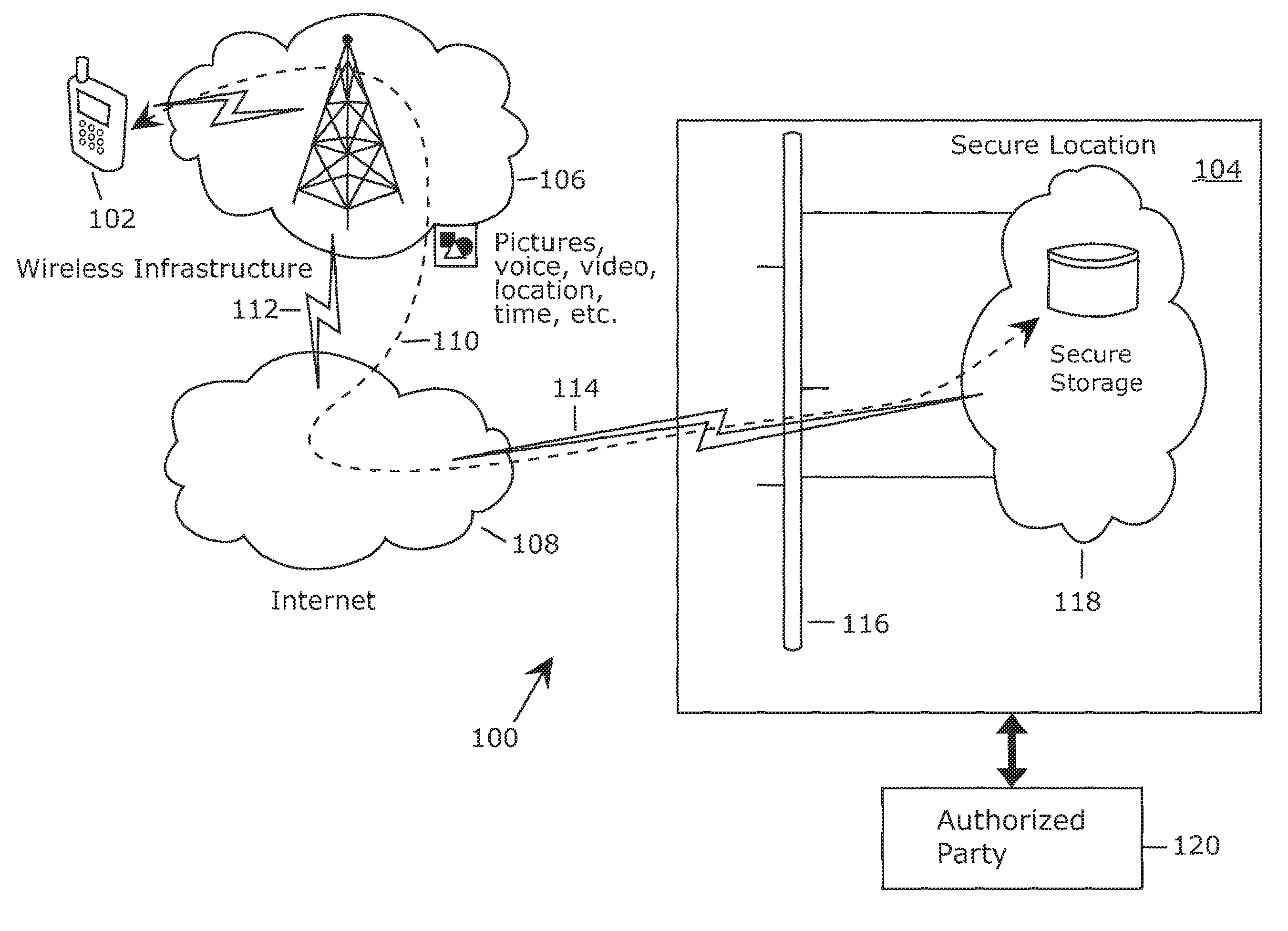
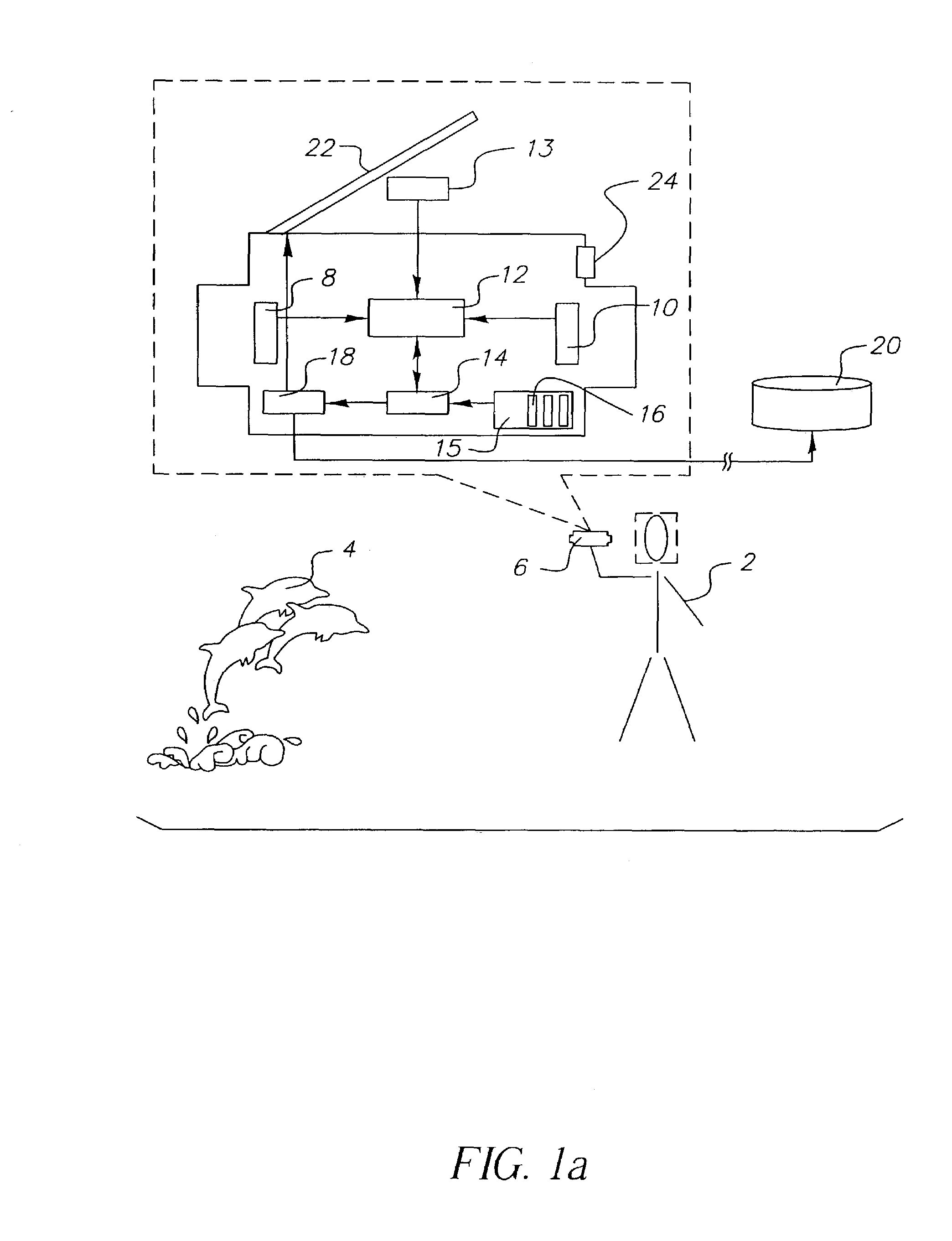
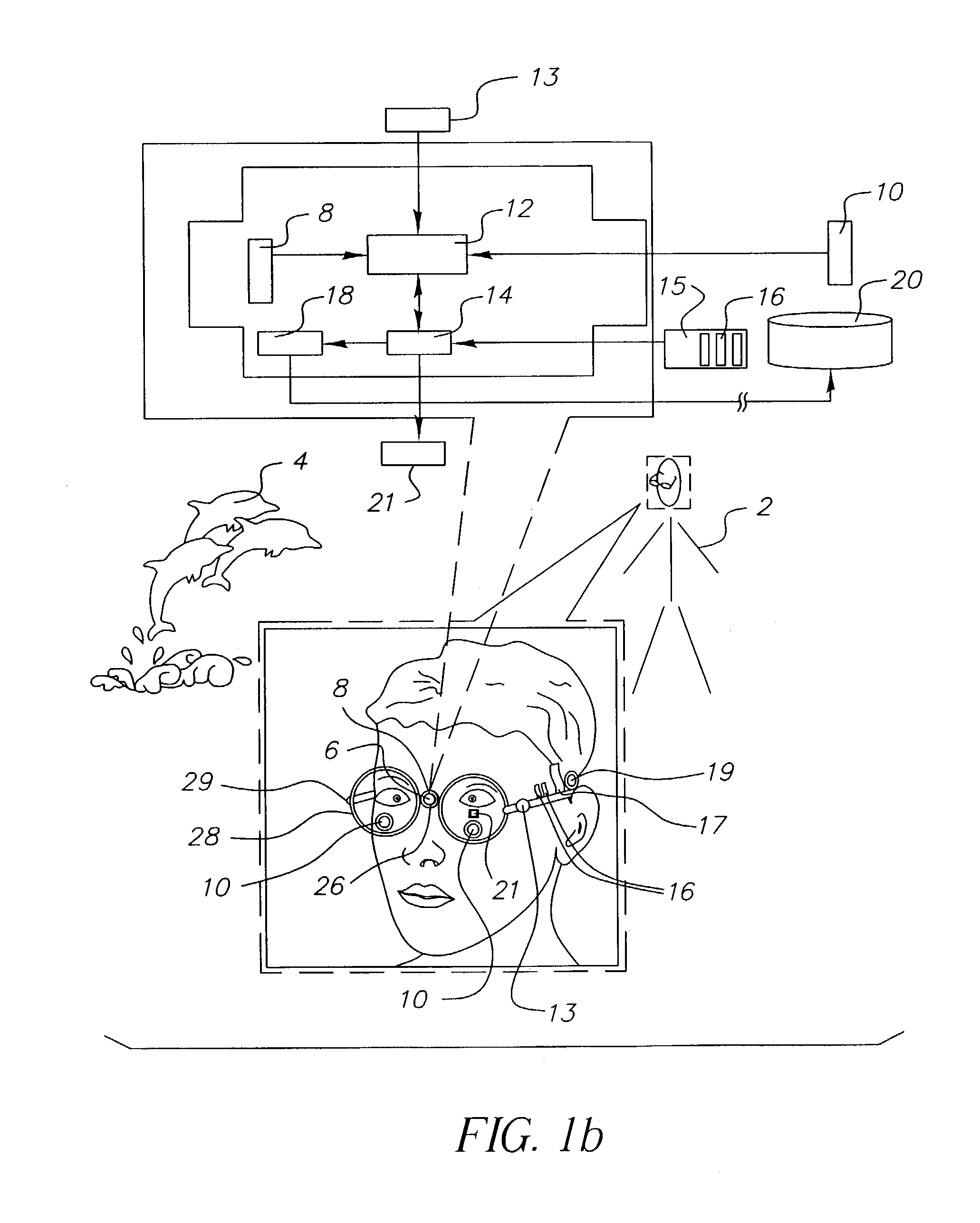
Imaging method and system for health monitoring and personal security
An image capture method is provided. In accordance with the method, an image of the scene is captured and affective information is collected a capture. The scene image and affective information are transmitted to an image receiver. An imaging system is also provided having an image capture system adapted to capture an image of a scene and a memory which stores the captured image. A set of sensors is adapted to collect affective signals from the user at capture. A processor is adapted to determine affective information based upon the affective signals and to associate affective information with the captured image. A transmitter sends the scene image and the affective information to a receiver.
Owner:MONUMENT PEAK VENTURES LLC
Personal safety mobile notification system
ActiveUS8013734B2Devices with voice recognitionDevices with GPS signal receiverControl systemNetwork control
Described embodiments provide a method of alarm notification. An alert mode of a mobile device is activated based on an emergency situation in an area. The mobile device transmits an indication of the emergency situation to a communication network control system. The communication network control system confirms the indication of the emergency situation to the mobile device and notifies emergency personnel of the indication of the emergency situation. The communication network control system transmits an indication of the emergency situation to one or more additional mobile devices in the area.
Owner:LIQUID RARITY EXCHANGE LLC
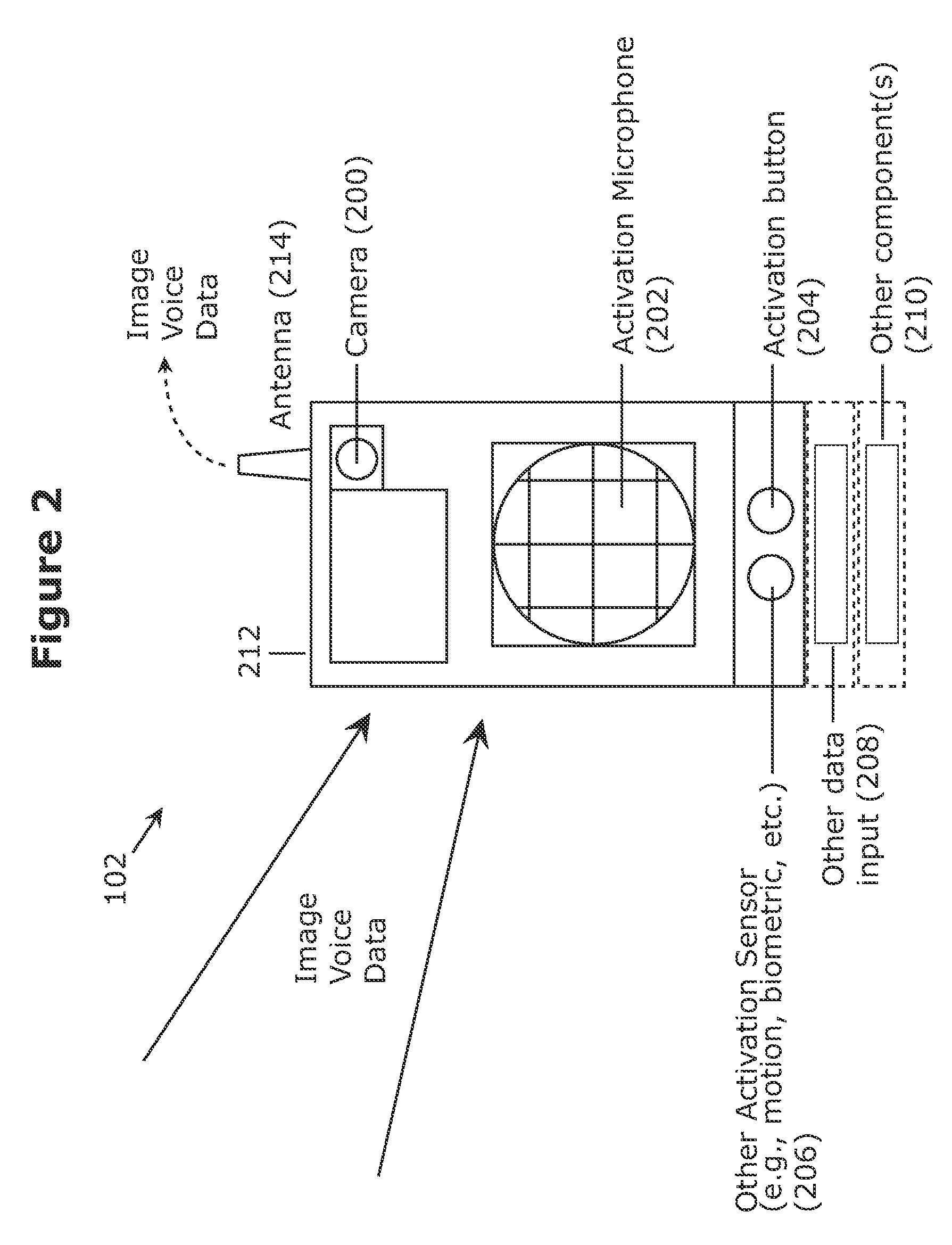
Personal security feature for a regular camera phone
InactiveUS20100087161A1Color television detailsClosed circuit television systemsCamera phoneWireless transmission
A mobile communications device includes a camera and an LED flash. The camera is configured to photograph a series of images in rapid shoot mode. The user photographs the series of images of an assailant in response to recognizing imminent danger of an attack. A predetermined event, such as a user pressing a camera button or hot key on the mobile communications device three times in rapid succession or pressing a combination of buttons, begins the series of photographs. The photographs are automatically transmitted wirelessly to a central repository for later use. The predetermined event also initiates a call to an emergency call center and / or an audible alarm.
Owner:SONY ERICSSON MOBILE COMM AB
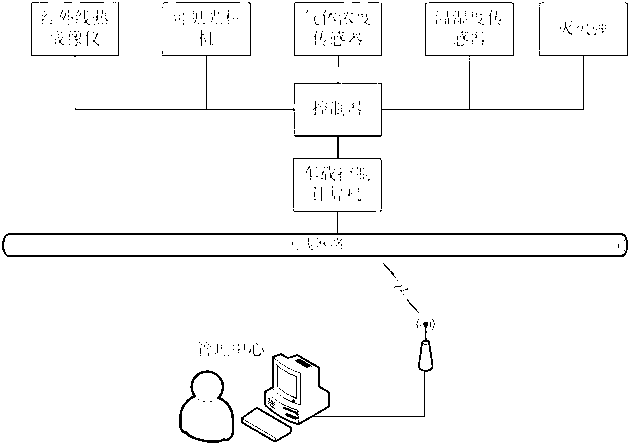
Construction tunnel safety protection method based on wireless sensor network and a monitoring system thereof
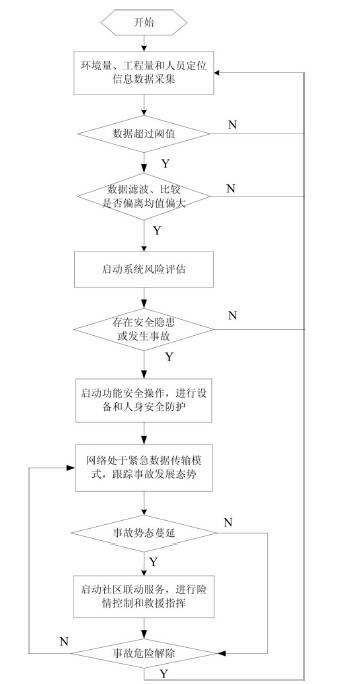
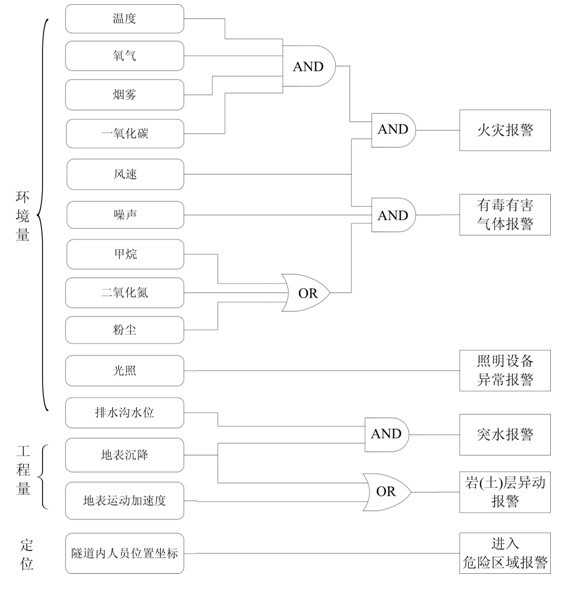
InactiveCN102042030AOvercome problemsChange the situation of "only monitoring but not monitoring"Mining devicesNetwork topologiesSecurity systemServer
The invention belongs to the field of construction safety monitoring and wireless communication and discloses a construction tunnel safety protection method based on a wireless sensor network and a monitoring system thereof. The method is as follows: by acquiring environment, work amount and locating data of personnel in a tunnel, realizing alarming services of six types of dangerous situations and corresponding safety protection means, calling a protection plan to take protection measures on key parts of the system when emergent (dangerous) events occur, and with the purpose of guaranteeing personal safety, releasing a control command. The system comprises a wireless sensor network based on industrial wireless communication standard WIA-PA, a positioning network and a mobile network. If the dangerous situation develops further, the system exchanges data with a remote mobile server by a 3G network, leads a community security system into the range of a construction tunnel safety protection system, and provides united rescue of communities and disaster control services. The invention is used for tunnel construction safety monitoring, and a computer or 3G mobile equipment can obtain construction site information at any time; and the installation of the WIA-PA wireless network is flexible, and the formed safety protection system and sensing early-warning network make contribution to solving the problem of tunnel safety construction fundamentally.
Owner:HUAZHONG UNIV OF SCI & TECH
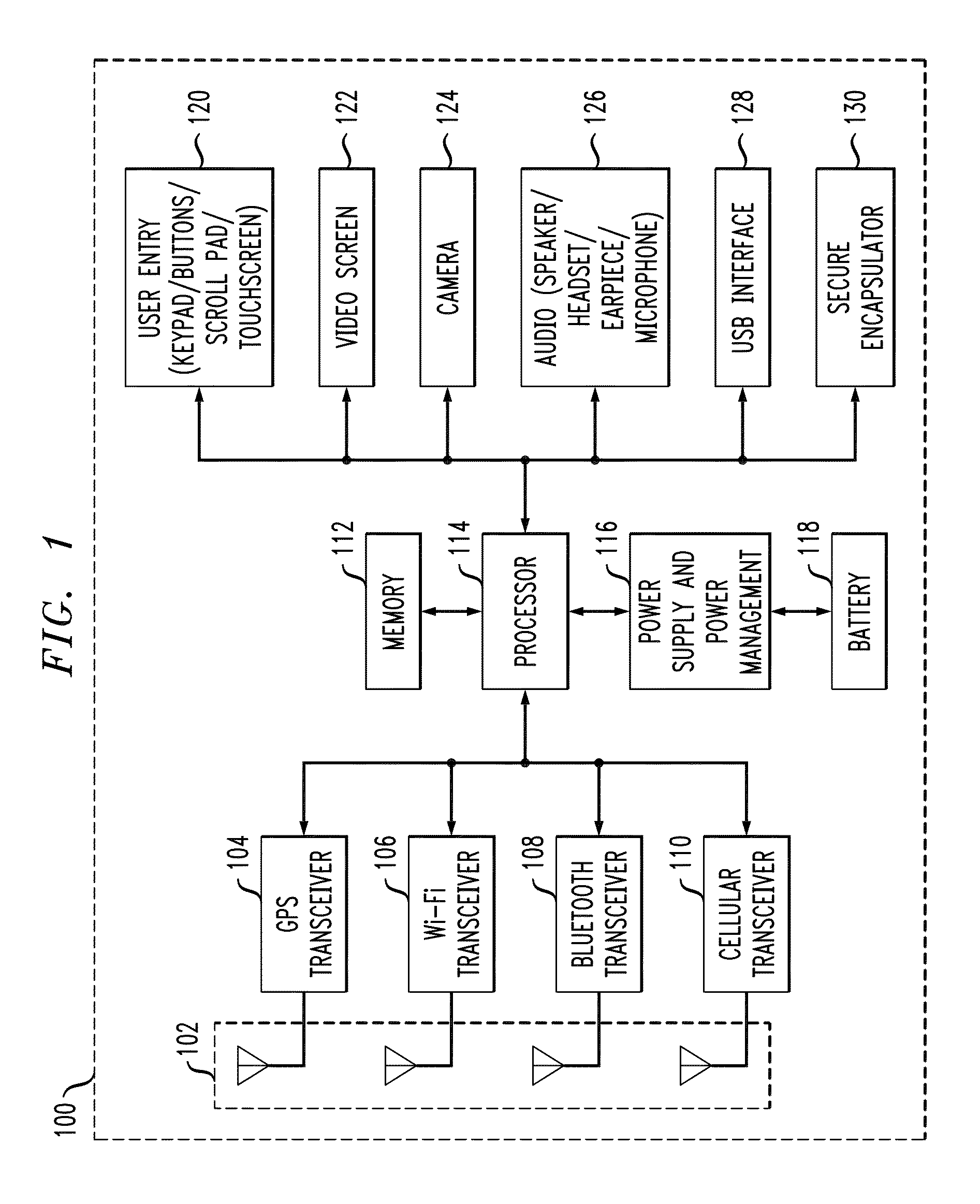
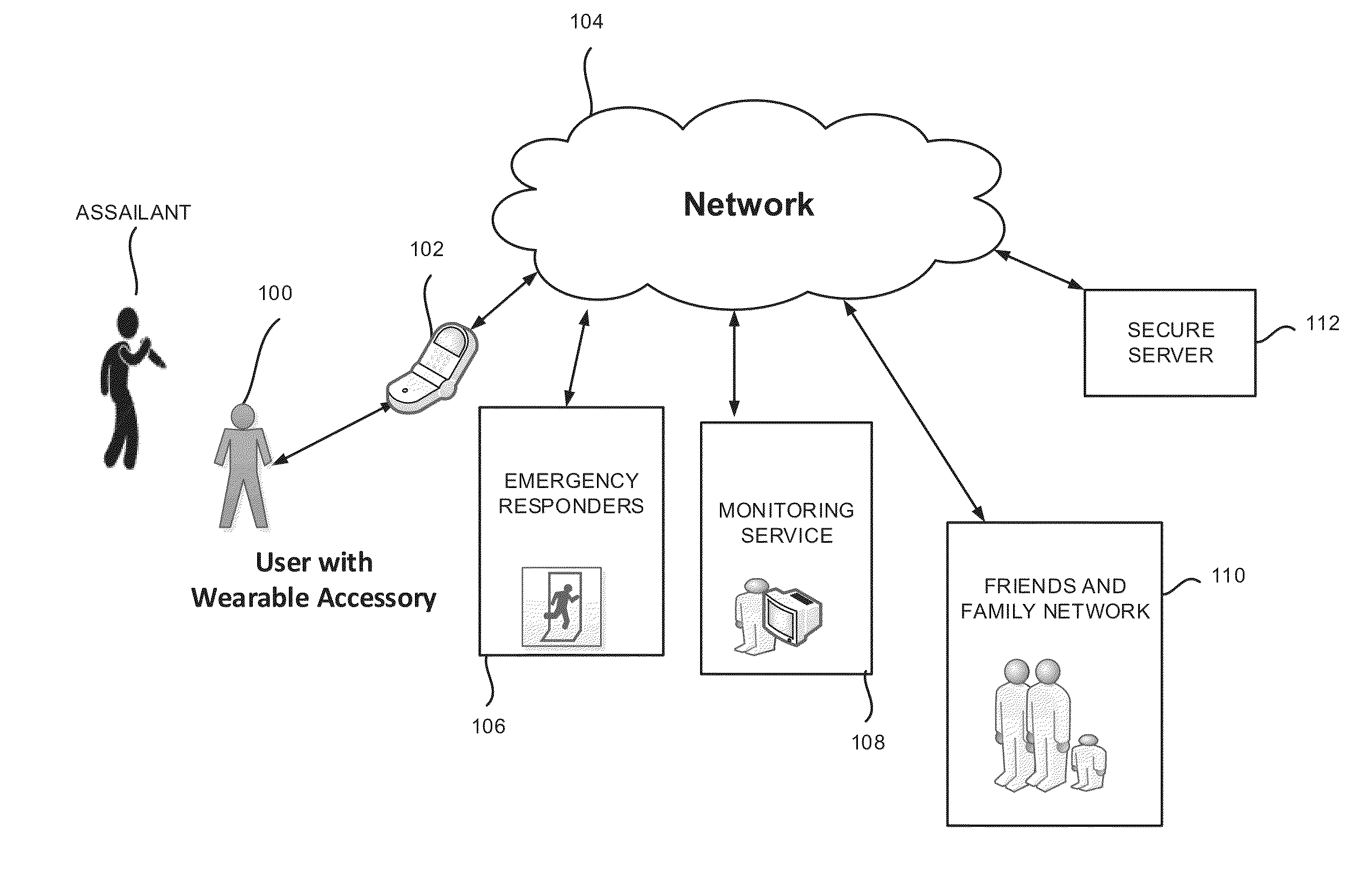
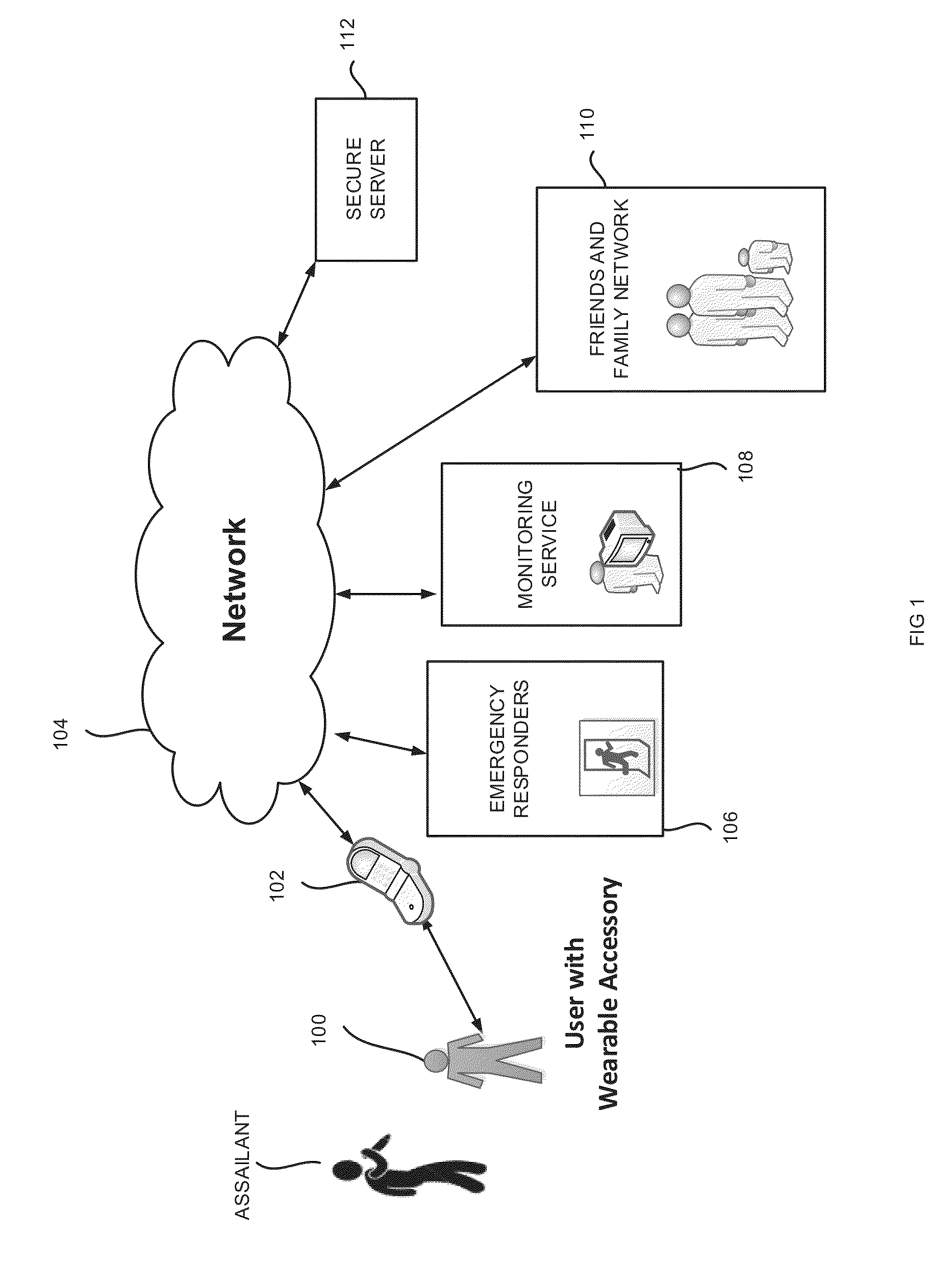
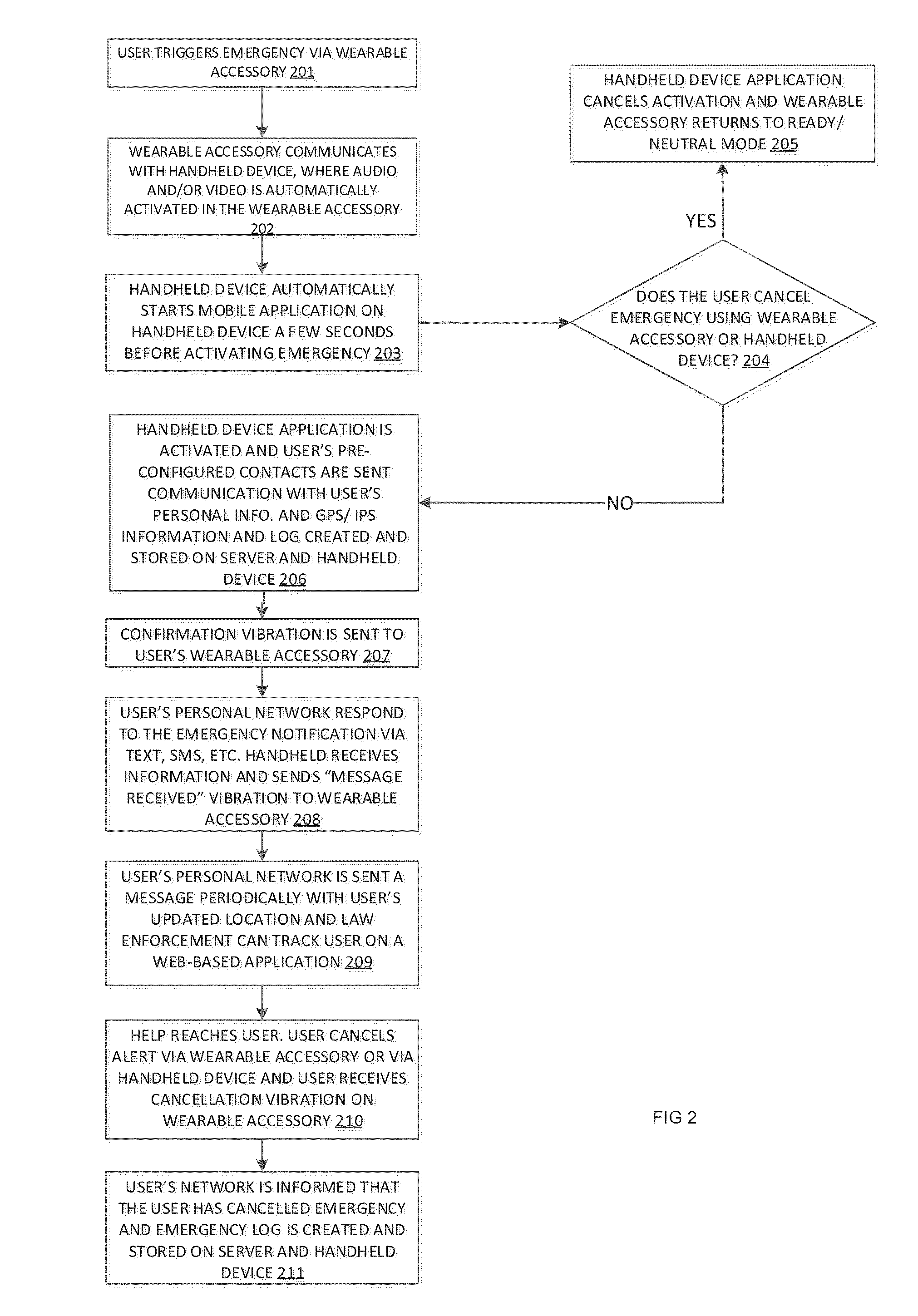
Personal safety device, system and a method
InactiveUS20150065082A1Speed up the processInput/output for user-computer interactionTelevision system detailsBiological activationHand held devices
The present invention relates to a wearable accessory including a detachable / removable circuitry housing, a vibration generation means for producing a vibration, the vibration generation means housed within the housing, at least one switch for allowing a user of the wearable accessory to cause activation of the vibration generation means, the switch housed within the housing, a module for communicating with at least one handheld device using a communication protocol, an image capturing device including a microphone for receiving audio and video signals at the wearable accessory, a USB port for charging the wearable accessory, a multiple-bit microprocessor is configured and coupled for controlling functions of the wearable accessory, the microprocessor housed within the housing and a storage means for storing data representative of the signals, the storage means coupled with the microprocessor.
Owner:SEHGAL AKHIL
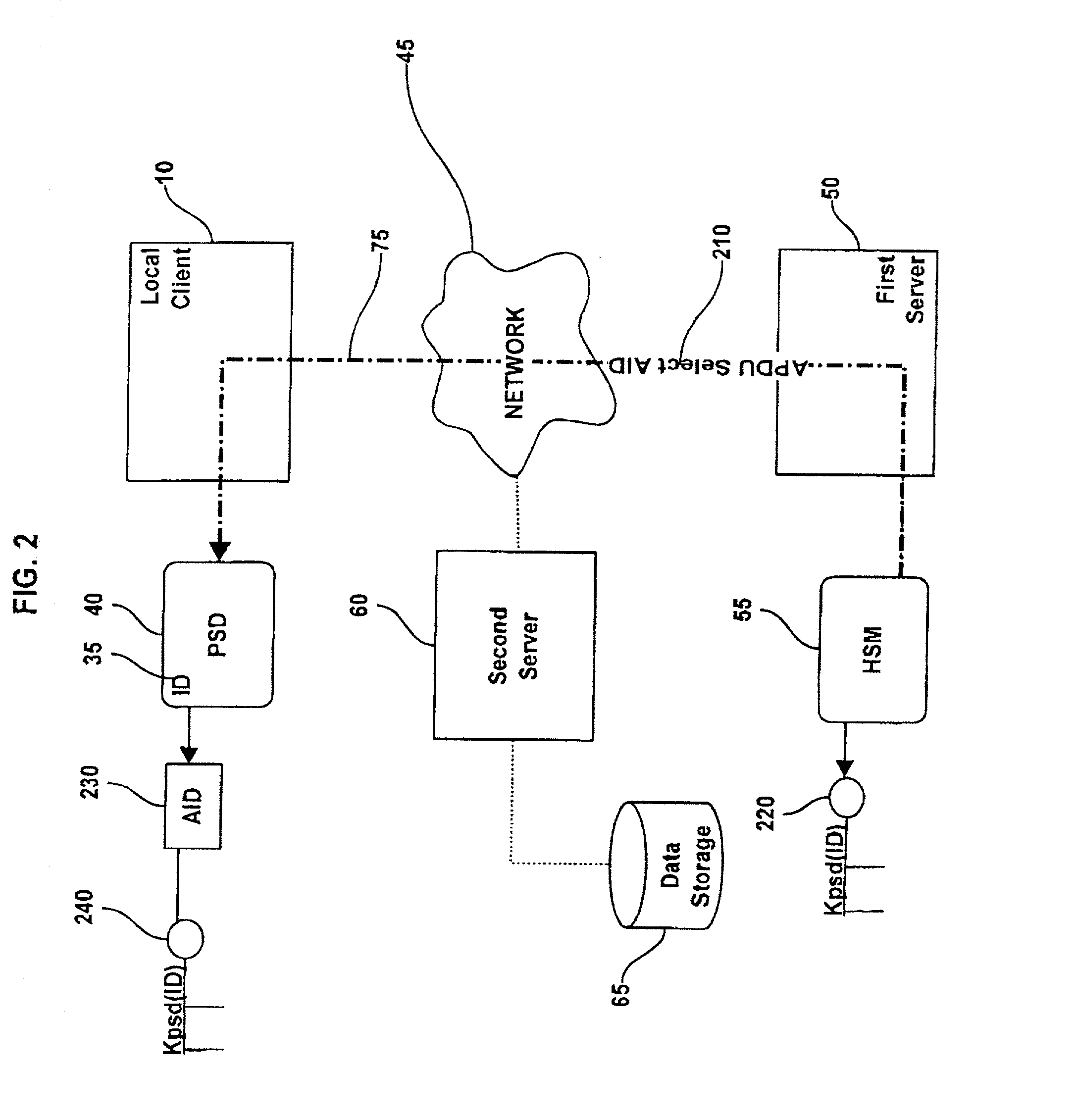
Method and system for establishing a remote connection to a personal security device
InactiveUS20020162021A1Easy maintenanceLess susceptibleDigital data processing detailsComputer security arrangementsSecret codeClient-side
System and method for establishing a remote connection over a network with a personal security device connected to a local client without using a local APDU interface or local cryptography.
Owner:ACTIVCARD
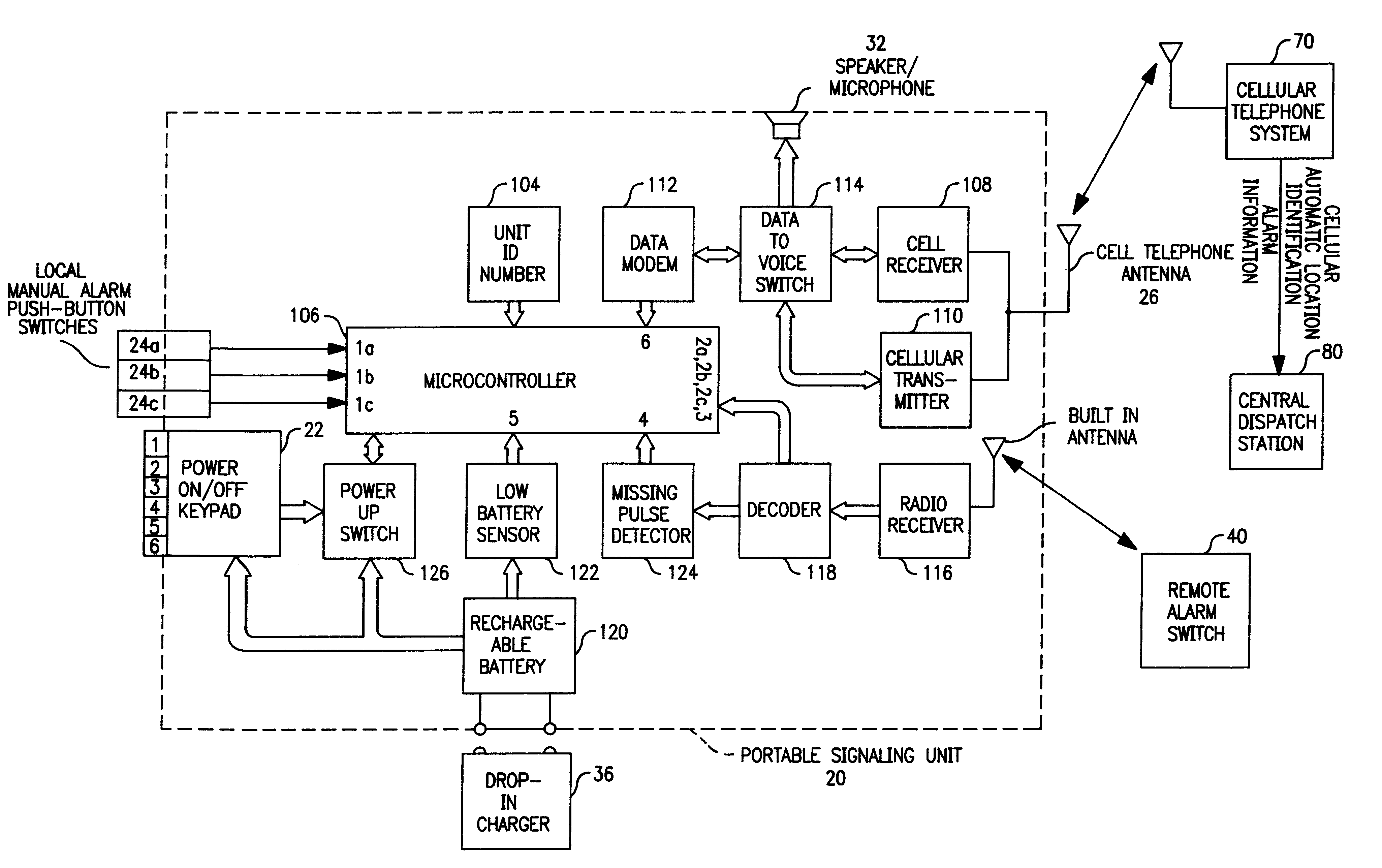
Personal security and tracking system
InactiveUS20040014478A1Efficient schedulingUnauthorised/fraudulent call preventionEavesdropping prevention circuitsCommunications systemSignaling system
A signaling system is provided for rendering an alarm for an individual in distress combined with a locating and tracking system to thus alert and direct appropriate personnel to the needs of the individual in distress and to monitor the location of that individual. The system comprises a portable signaling unit, a remote alarm switch device, a central dispatch station, and makes use of a wireless communication system. The portable signaling unit and the remote alarm switch may be adapted to be worn at different locations on the person's body. The remote alarm switch way be concealed in the form of a wristband or in the form of any other object such as a broach, pendant, or keychain.
Owner:HOFFMAN RESOURCES
Disguised personal security system in a mobile communications device
InactiveUS20050083195A1Promote resultsImprove scalabilityConcealed burglar systemsTelephonic communicationEngineeringOperation mode
The disguised personal security system in a mobile communications device (MCD) has two modes of operations: audible and silent. Depend on the situation, the user may activate an audible alarm to fend off the perpetrator or in hostile situation, secretly contacts an emergency monitoring service (EMS). The system may be activated manually or automatically. When activated, the MCD contacts an EMS and transmit its location coordinates. The EMS then transmits an acknowledgement signal and activates a “hyper-state” microphone to monitor the user's environment and dispatches the corresponding assistance or authorities. The disguised personal security system is seamlessly integrated into a mobile communication device so that close scrutiny of the device will not be able to distinguish it as a personal security system. The system includes hidden setup menus that accessible by the secret key sequence.
Owner:PHAM LUC H +1
Personal security system
InactiveUS20160071399A1Improve securityImprove protectionSubstation equipmentSpeech recognitionPersonalizationDriver/operator
A personal security system that continually monitors audio from any microphone accessible from a computer or mobile phone for keys, identifies keys emitted by a user and if found, issues an alert. May also monitor movement to aid in event detection. Audio monitoring may search for keys in a personalized manner to minimize false positives and may work on low power devices in the background to continually provide security, even if a computer is locked. May transmit alerts via a data network, or voice network. The alerts may be sent to users, devices, security or medical entities to provide personal safety and security. May also be utilized for persons unable to physically manipulate their phone or computer, during or after an assault, or medical emergency. May also be utilized to improve safety when moving between locations, to improve the safety of a driver or a passenger of a vehicle.
Owner:ON GUARD
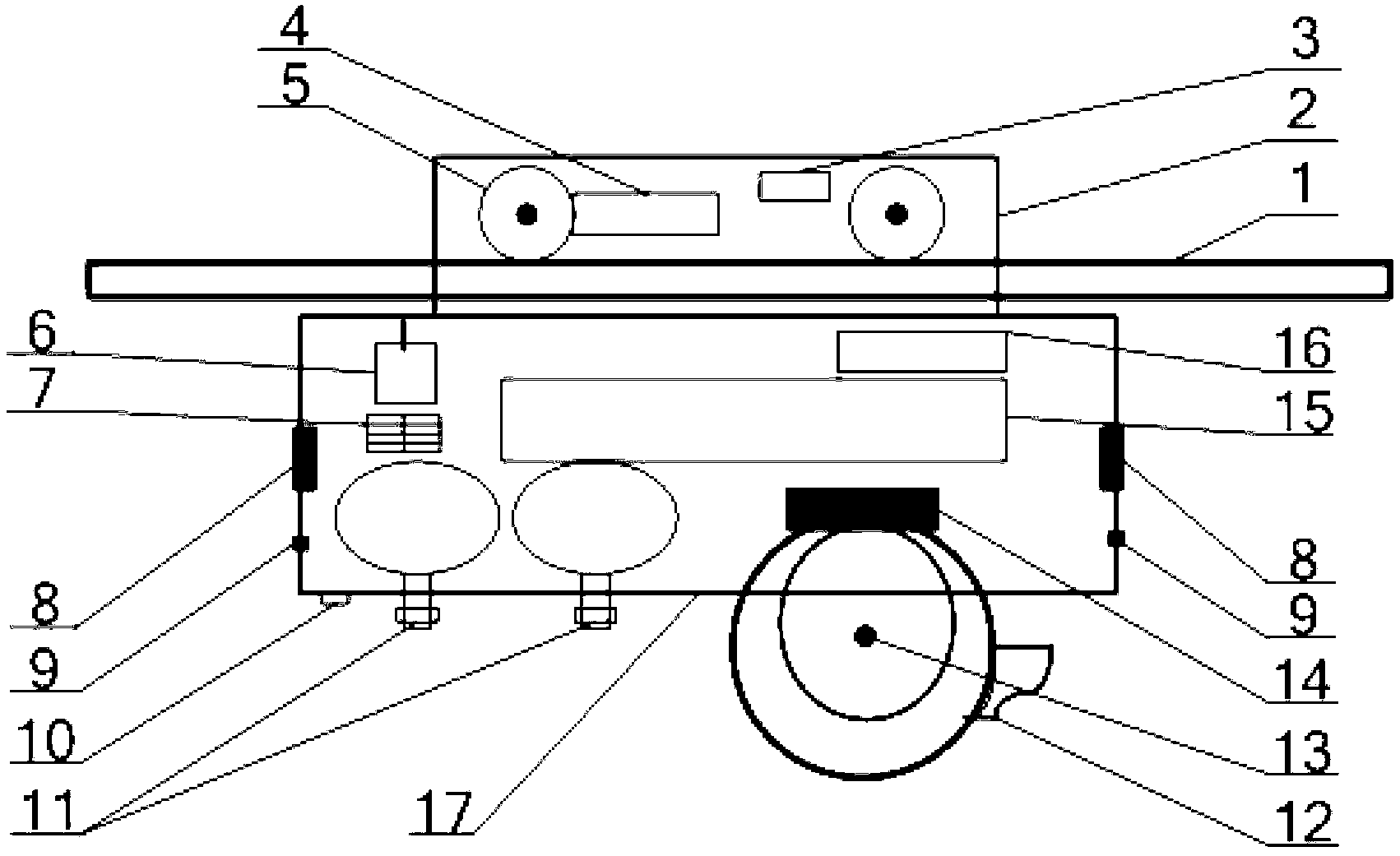
Suspended type intelligent fire-fighting robot
The invention discloses a suspended type intelligent fire-fighting robot. The suspended type intelligent fire-fighting robot is characterized in that a rotating shaft of a driving motor is connected with travelling wheels; the travelling wheels are put on rails and are used for driving the fire-fighting robot to move; an audio transceiver is used for carrying out audio broadcasting and voice talkback; an ultrasonic radar is used for detecting obstacles; a visible light camera and an infrared ray thermal imager are both mounted on a visible light / thermal imagery double-vision cradle head and can freely rotate; the audio transceiver, the ultrasonic radar, a sensor, fire extinguishing bullets, the visible light camera and the infrared ray thermal imager are respectively and correspondingly connected with a controller; the controller is in communication connection with a vehicle-mounted computer; the vehicle-mounted computer is in remote communication connection with a management center through a wireless network. The robot can be used for carrying out polling on each polling site in a tunnel instead of workers and has the advantages that the polling is automatic and real-time, the personal security is protected, the warning and the fire extinguishing processing are timely carried out, the monitoring and the real-time communication are remotely carried out, and the data can be saved and played back so as to carry out analysis and summary.
Owner:成都慧拓自动控制技术有限公司
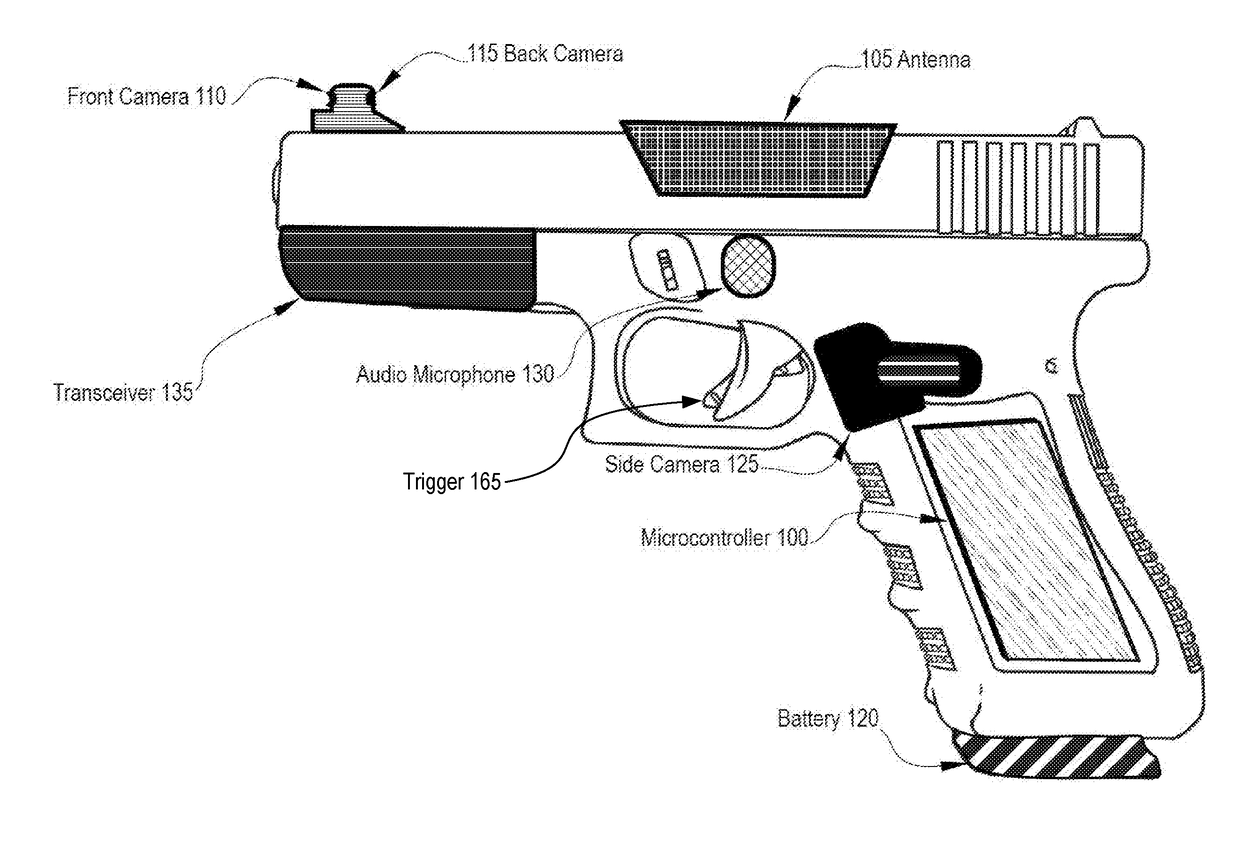
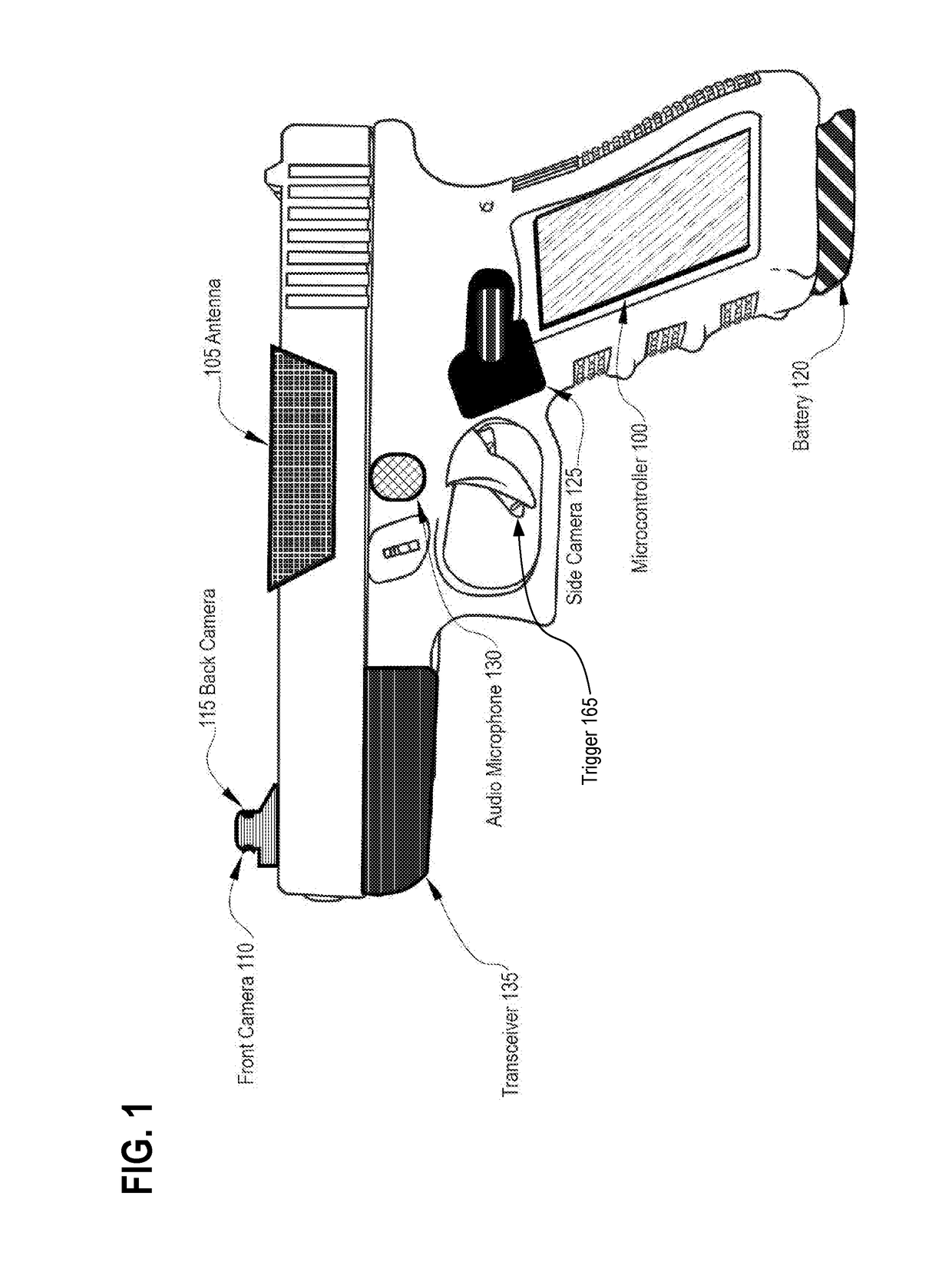
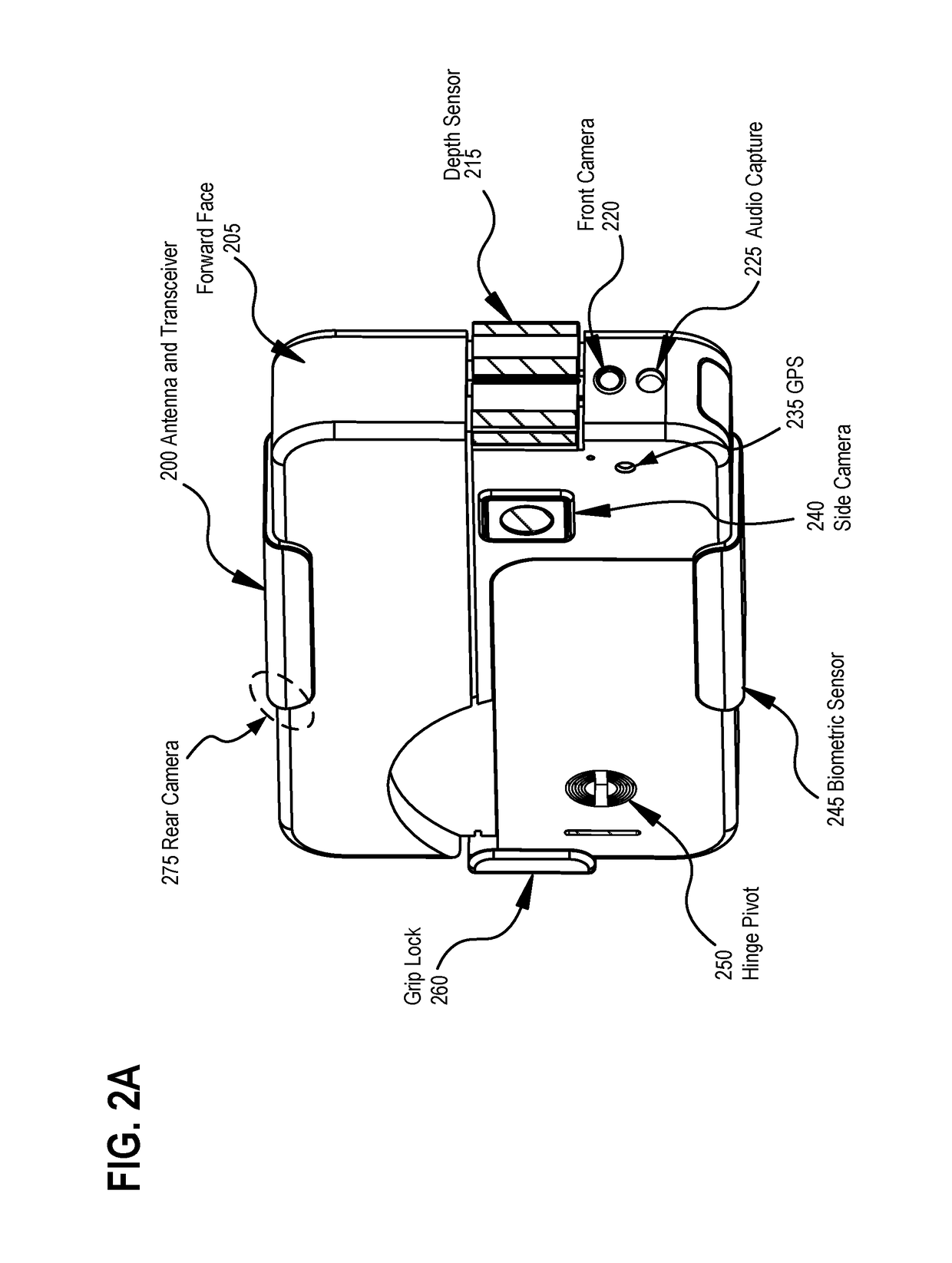
Systems, methods, and apparatuses for implementing video shooting guns and personal safety management applications
In accordance with disclosed embodiments, there are provided systems, methods, and apparatuses for implementing video shooting guns and personal safety management applications. An exemplary personal safety device may include, for example, a processor and a memory to execute instructions; a rechargeable battery to electrically power the personal safety device; a front facing video camera to capture video data of a scene anterior to a front face of the personal safety device; a rear facing video camera to capture video data of a scene posterior to a rear of the personal safety device; an audio capture device to capture audio data from an environment within which the personal safety device is to operate; a trigger to initiate recording of the front facing video camera, the rear facing video camera, and the audio capture device when triggered by an operator of the personal safety device; and a transceiver to transmit the recorded video data from the front and rear cameras and the captured audio data to a remote location over a network. According to another embodiment, a holster operates in conjunction with a body camera to activate audio and video capture and streaming upon removal of a firearm from the holster. Other related embodiments are disclosed.
Owner:SENSLYTICS CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com