Detection object-based software vulnerability model detection method
A detection object and model detection technology, applied in software testing/debugging, etc., can solve problems such as repetitive work, affecting detection speed, and low accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
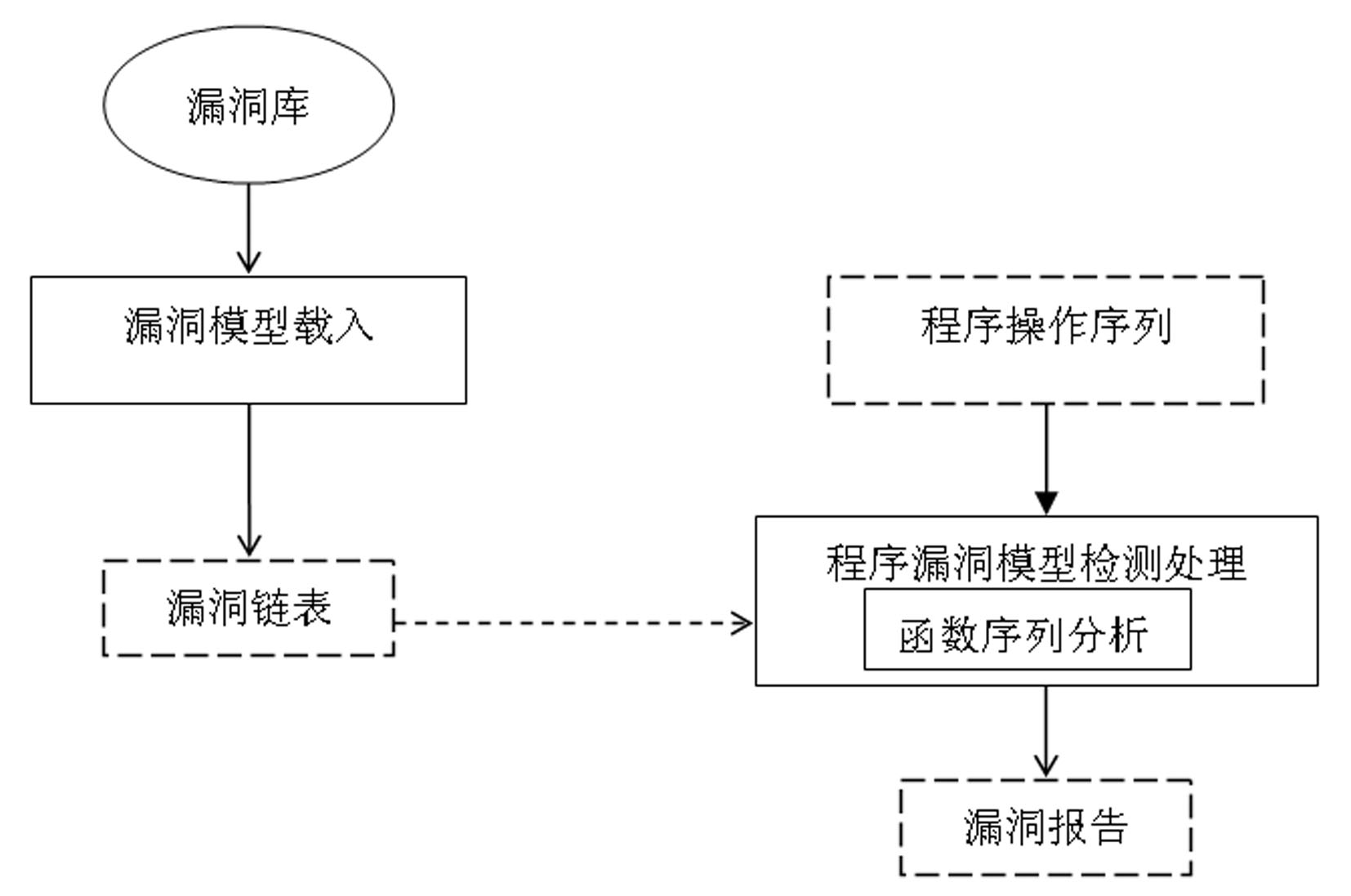
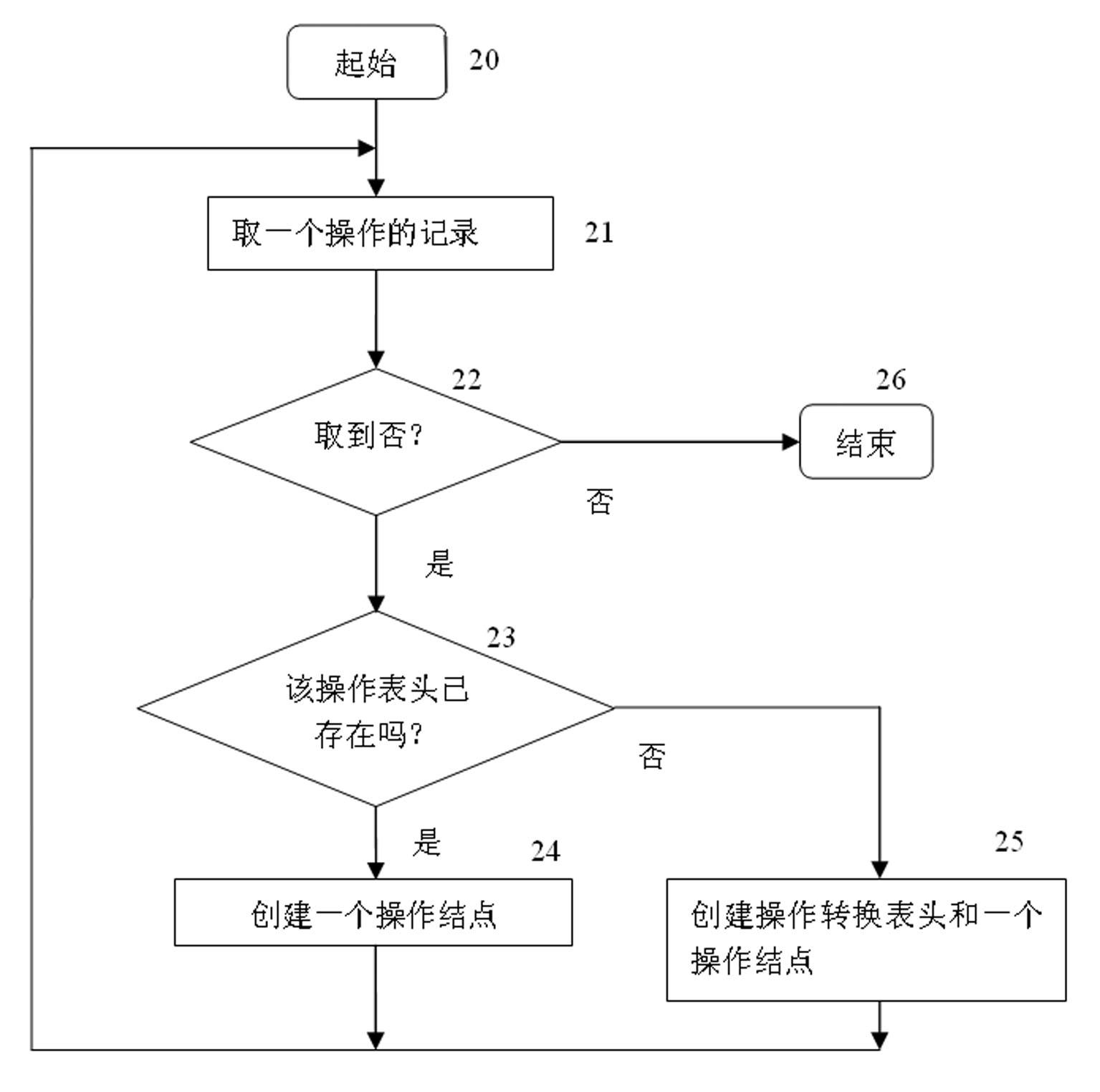
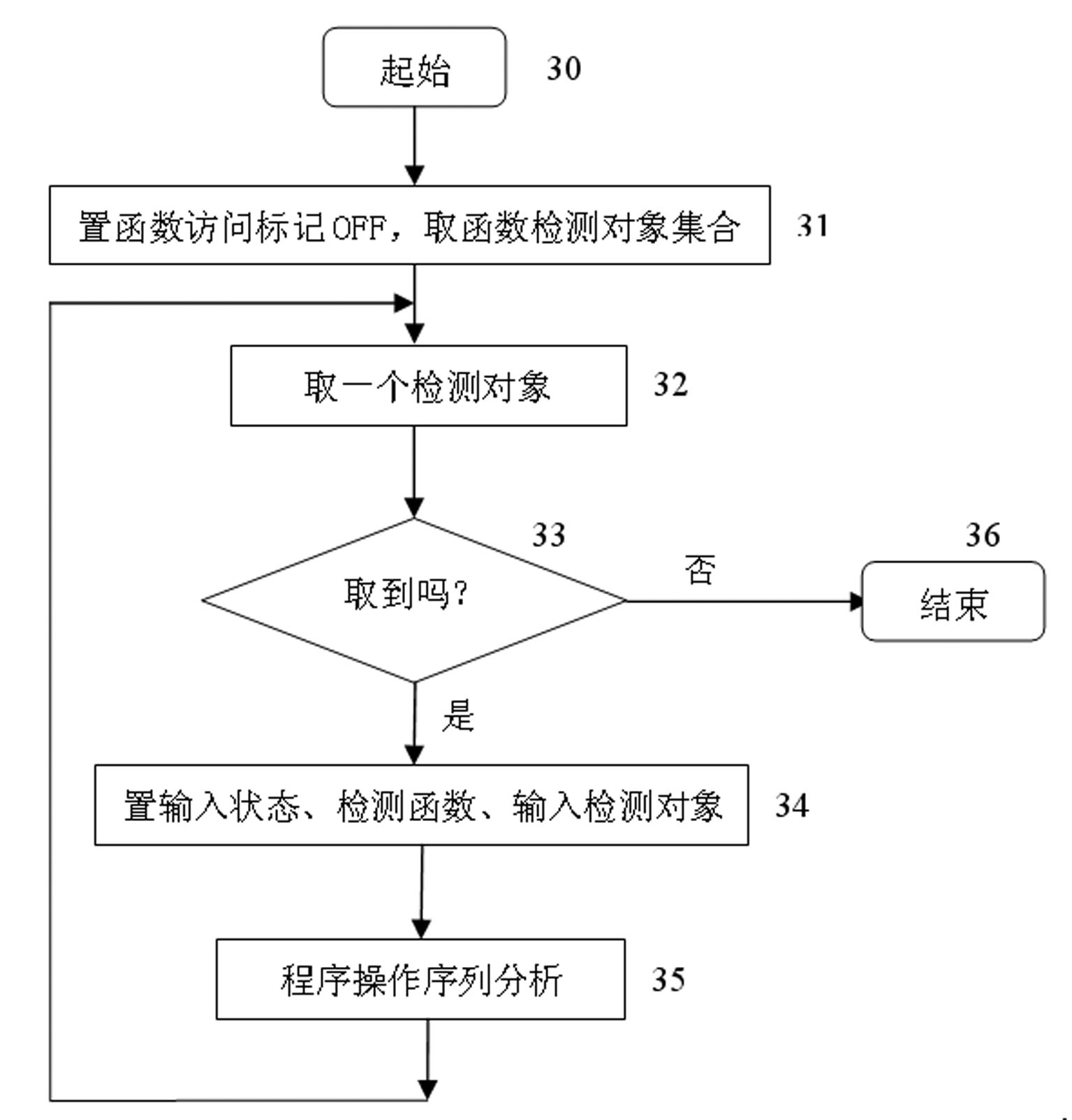
[0019] The working process of the inventive method is as Figure 1-Figure 5 shown.
[0020] figure 1 Shown is the overall structure and working principle of this method implementation. The purpose of this method is to analyze and detect the program to be detected according to the operations involved in the vulnerability model, and report the discovered vulnerabilities. In order to improve the processing speed, the vulnerability model needs to be loaded into the memory from the database, so that it can be used as a reference when analyzing the program. During the vulnerability model detection process, the model detection work is carried out step by step according to the vulnerability-related operations in units of functions. Vulnerability model detection starts from the main function, and performs state detection and reports the existence of vulnerabilities according to the model detection results of vulnerability-related operations and step-by-step functions.
[0021] f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com