Program code verification method and device
A technology of program code and code, which is applied in the field of program code review methods and devices, can solve problems such as safety problems of dangerous function systems, and achieve the effects of shortening time, improving efficiency, and improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
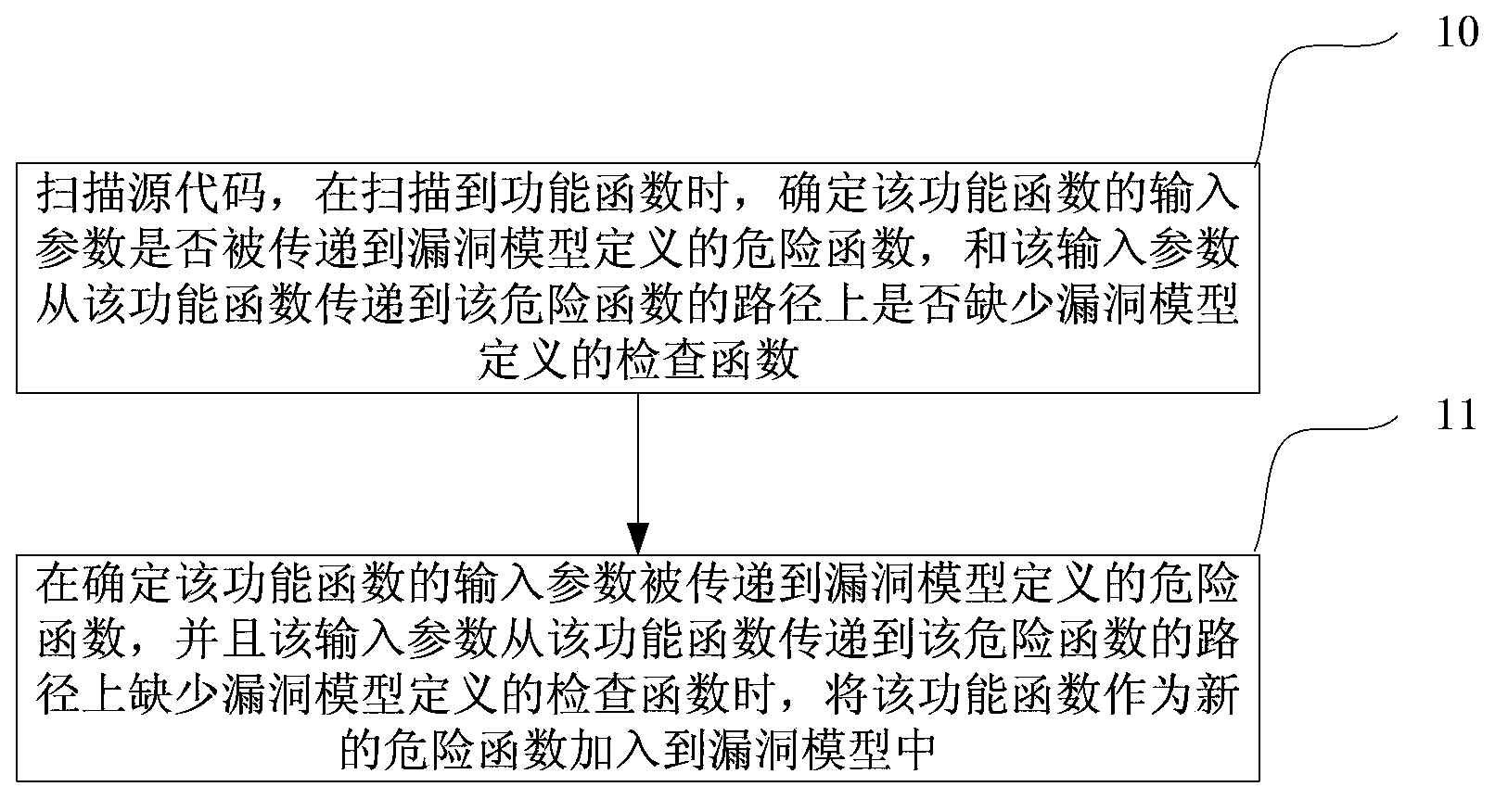
[0069] see figure 1 , the present embodiment provides a program code review method, including the following steps:
[0070] Step 10: Scan the source code of the program, and when a functional function is scanned, determine whether the input parameter of the functional function is passed to the dangerous function defined by the vulnerability model, and whether the input parameter is passed from the functional function to the dangerous function Whether the check function defined by the vulnerability model is missing on the path;
[0071]Here, it is determined whether the check function defined by the vulnerability model is missing on the path where the input parameter of the functional function is passed from the functional function to the dangerous function. The specific implementation method may be: the path of passing the input parameter from the functional function to the dangerous function Each function on the path is compared with the check function defined by the vulnera...
Embodiment 2
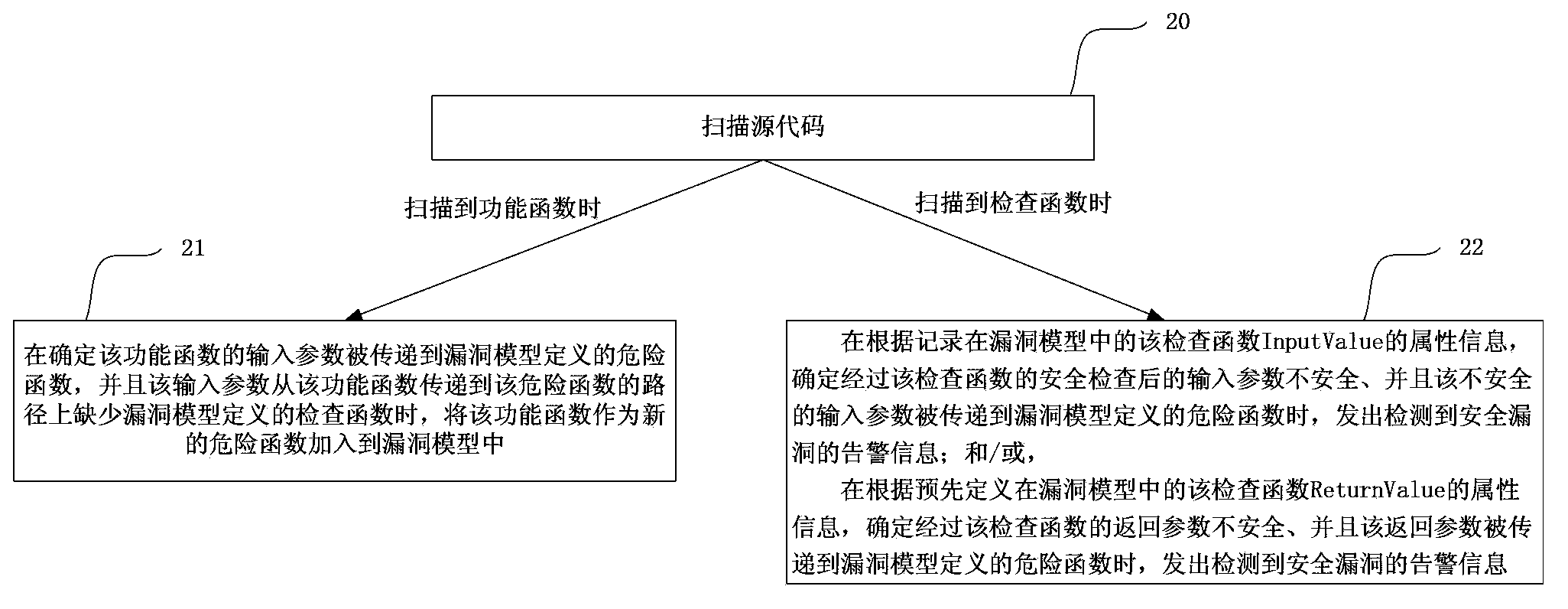
[0080] see figure 2 , the present embodiment provides a program code review method, including the following steps:
[0081] Step 20: Scan the source code of the program. When a functional function is scanned, go to step 21. When a checking function is scanned, go to step 22;
[0082] Step 21: Determine whether the input parameter of the functional function is passed to the dangerous function defined by the vulnerability model, and whether the input parameter lacks the inspection function defined by the vulnerability model on the path passed from the functional function to the dangerous function; When the input parameter of the function is passed to the dangerous function defined by the vulnerability model, and the path from the functional function to the dangerous function lacks the inspection function defined by the vulnerability model, the functional function is added as a new dangerous function to in the vulnerability model and determine that a security vulnerability has ...
Embodiment 3
[0103] This embodiment provides a program code review method, including the following steps:
[0104] Step 30: read the source function defined by the superclass in the vulnerability model, find the function of the subclass of the superclass in the source code, and determine the found function as the starting point of code scanning; and / or,
[0105] Read the source function defined by the interface in the vulnerability model, find the function of the class that uses the interface in the source code, and determine the found function as the starting point of code scanning;
[0106] Step 31: Start scanning the source code of the program from the determined starting point.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com