Differential privacy protection method based on microaggregation anonymity
A differential privacy and clustering technology, applied in the field of data anonymity and differential privacy protection, can solve the problems of unreasonable way of data set anonymization, no data privacy and usability analysis, only considering accuracy and clustering usability, etc. , to achieve the effect of enhancing security, reducing information loss, and ensuring availability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
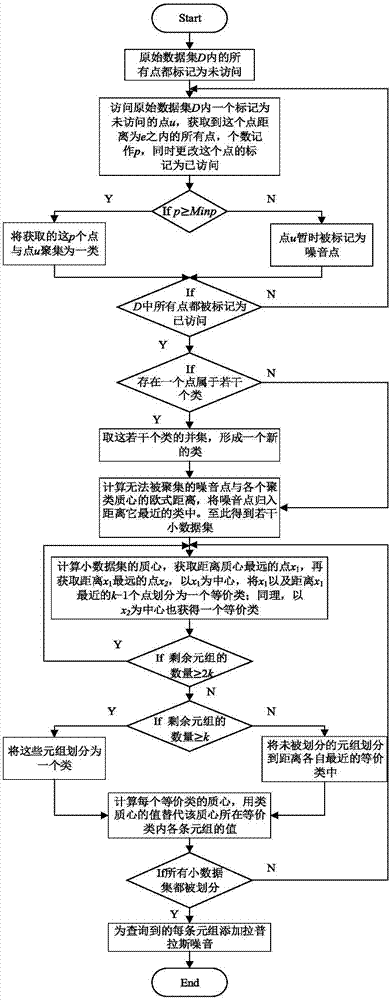
[0028] The present invention mainly proposes a differential privacy protection method based on micro-aggregation anonymity. The following is the concept of micro-aggregation and differential privacy protection used in the method of the present invention.
[0029] Definition 1 Micro-aggregation: Use some method to divide the original data set into several equivalence classes according to the degree of similarity, and the number of records in each equivalence class is at least k, and then use the class centroid to replace each record in the class.
[0030] According to Definition 1, it is easy to know that the smaller the value of k, the smaller the offset of the class centroid relative to each record value in the class, so the amount of information loss after anonymization is less. For example, Table 1 is an original data table, identifier={name}, quasi-identifier QI={age, zip code}, sensitive attribute S={salary}. Use the micro-aggregation method to process Table 1, and remove...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com