Availability computing method of data published based on differential privacy
A computing method and differential privacy technology, applied in the field of information security, can solve the problems of data providers or users computing availability difficulties, publishers not being able to disclose original data to data providers, forged availability, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] Below in conjunction with specific embodiment, further illustrate the present invention, should be understood that these embodiments are only used to illustrate the present invention and are not intended to limit the scope of the present invention, after having read the present invention, those skilled in the art will understand various equivalent forms of the present invention All modifications fall within the scope defined by the appended claims of the present application.
[0017] 1. Basic knowledge
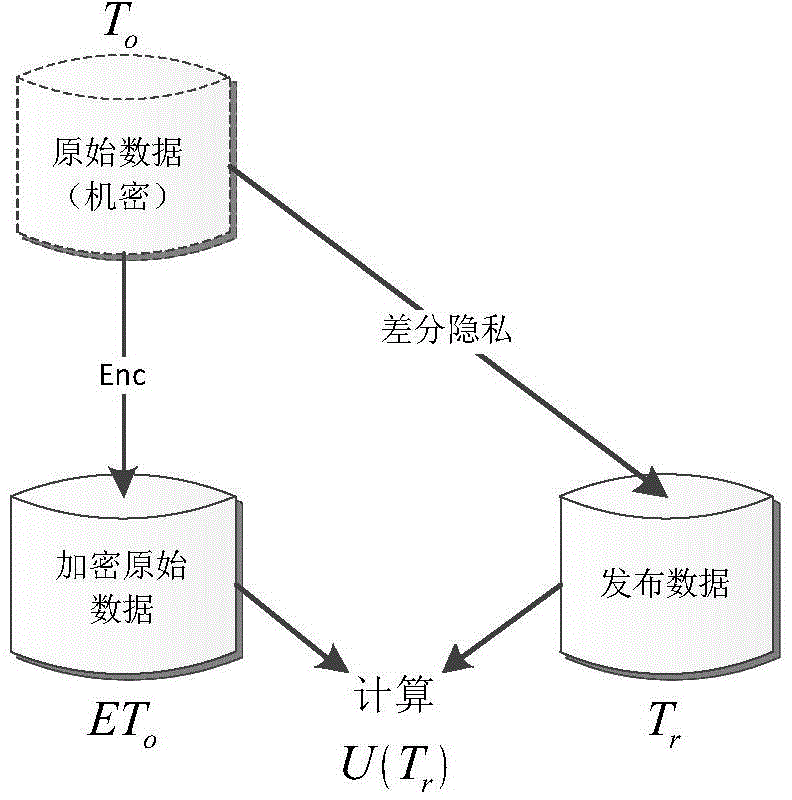
[0018] 1.1 Differential privacy protection data release
[0019] The differential privacy model aims to protect sensitive information by making the results of two queries with at most one different record indistinguishable. The definition of differential privacy is given as follows:
[0020] Definition 1. The method M: R(D)→R(T) is ε-differentially private if and only if for any and for each pair of D, only differ on one record
[0021] Pr[M(D)∈R(T)]≤e ε ·Pr[M(D...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com