Multi-party safety calculation method and device, and electronic equipment
A computing method and security technology, applied in the field of distributed computing, can solve problems such as incorrectness, leakage of private data, implementation of malicious algorithms, etc., and achieve the effect of facilitating auditing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
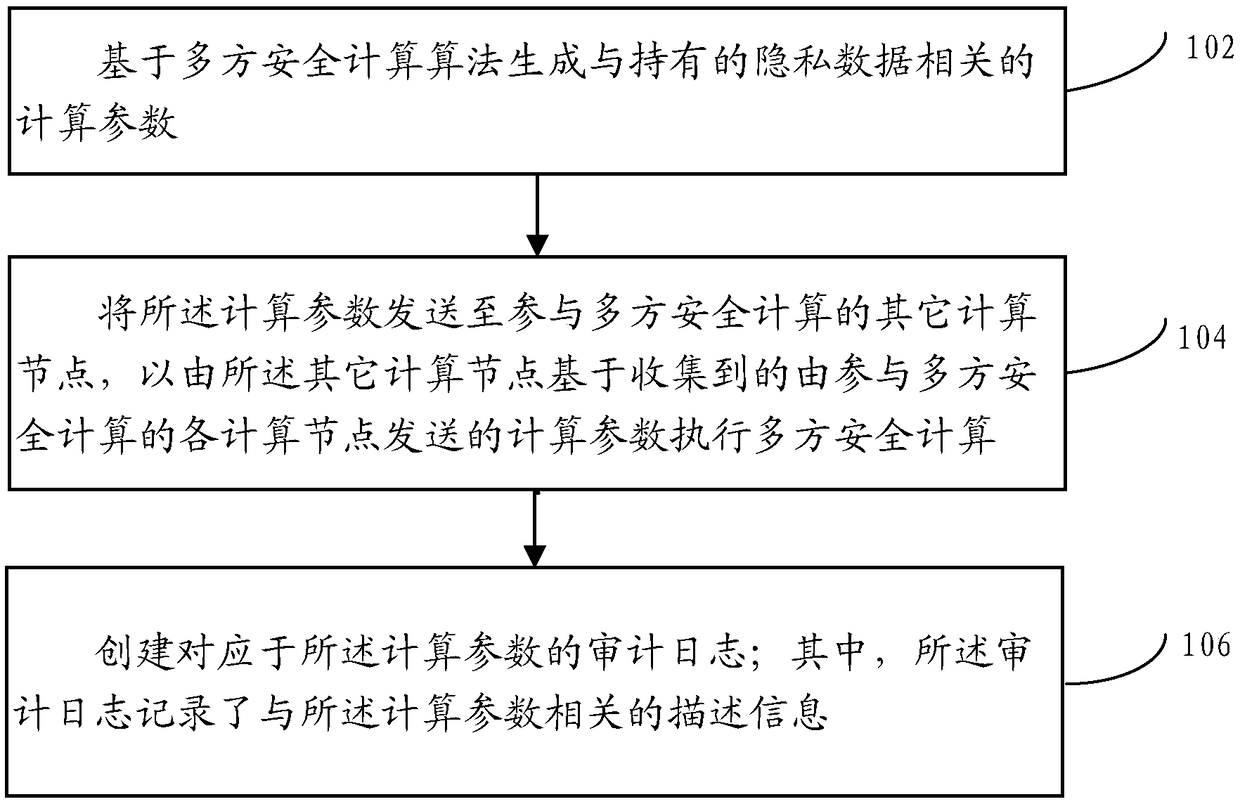
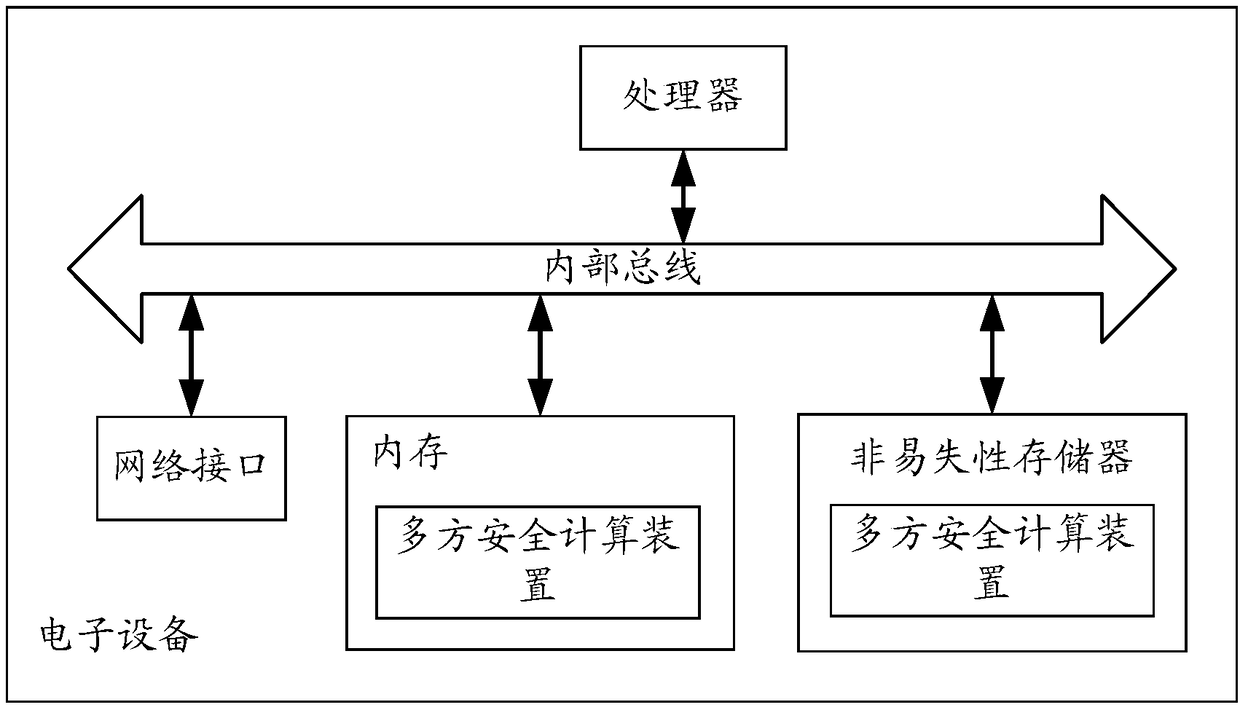
[0062] In practical applications, for the purpose of privacy protection, multi-party secure computing algorithms are usually black-box algorithms, and the data transmission behavior between computing nodes equipped with multi-party secure computing algorithms is very opaque;
[0063] For example, between computing nodes equipped with multi-party secure computing algorithms such as secret sharing, homomorphic encryption, and obfuscated circuits, interactive messages carrying a large amount of ciphertext and / or random numbers are usually transmitted, even for users of multi-party secure computing algorithms It is also difficult to understand the specific meaning of the ciphertext and / or random numbers carried in the above interaction messages.
[0064] Therefore, for the provider of the multi-party secure computing algorithm, in order to prove that the multi-party secure computing algorithm it provides is transparent and credible, it has to share the source code of the multi-part...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com