Providing application visibility for micro-segmentation of a network deployment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044]In the following detailed description of the invention, numerous details, examples, and embodiments of the invention are set forth and described. However, it should be understood that the invention is not limited to the embodiments set forth and that the invention may be practiced without some of the specific details and examples discussed.
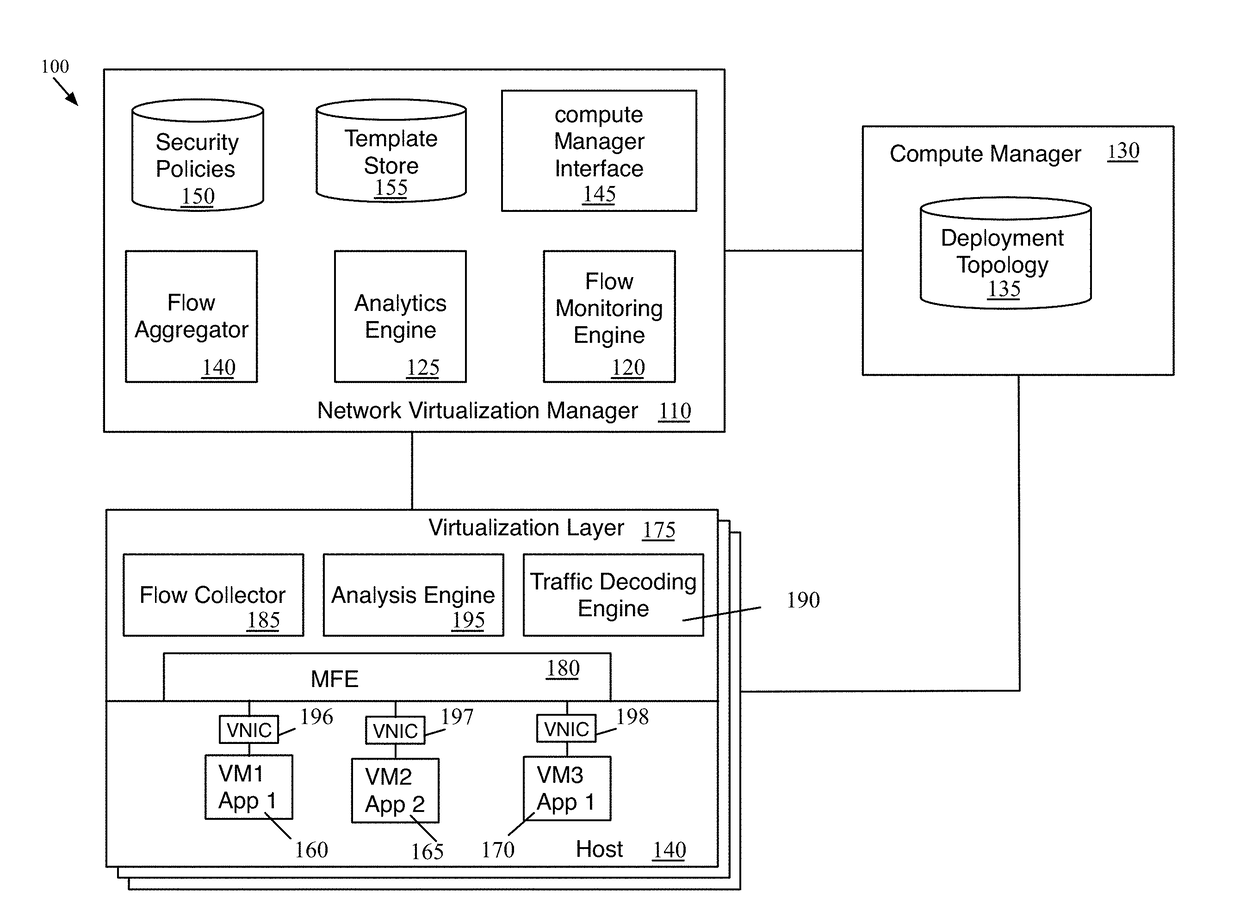
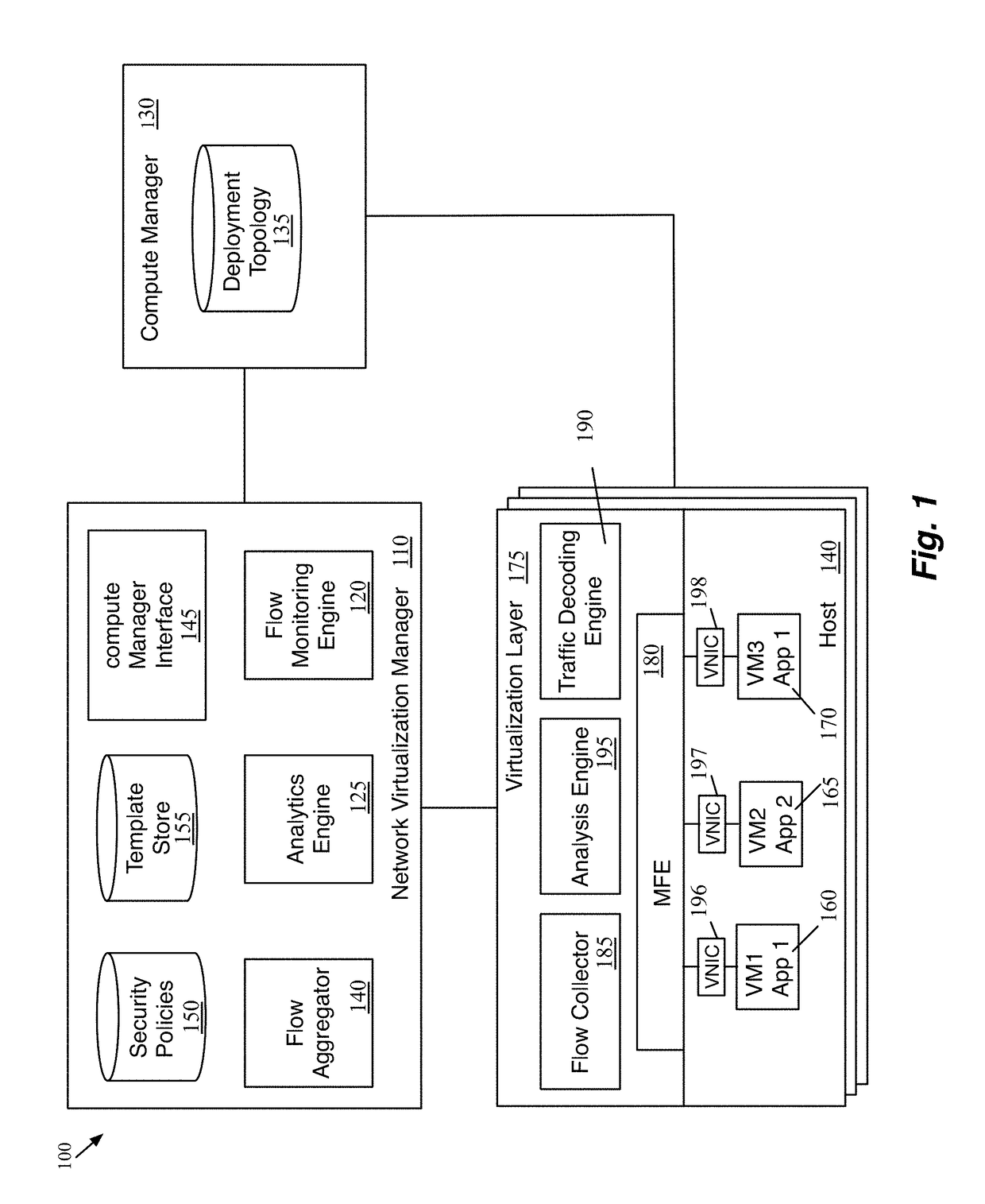
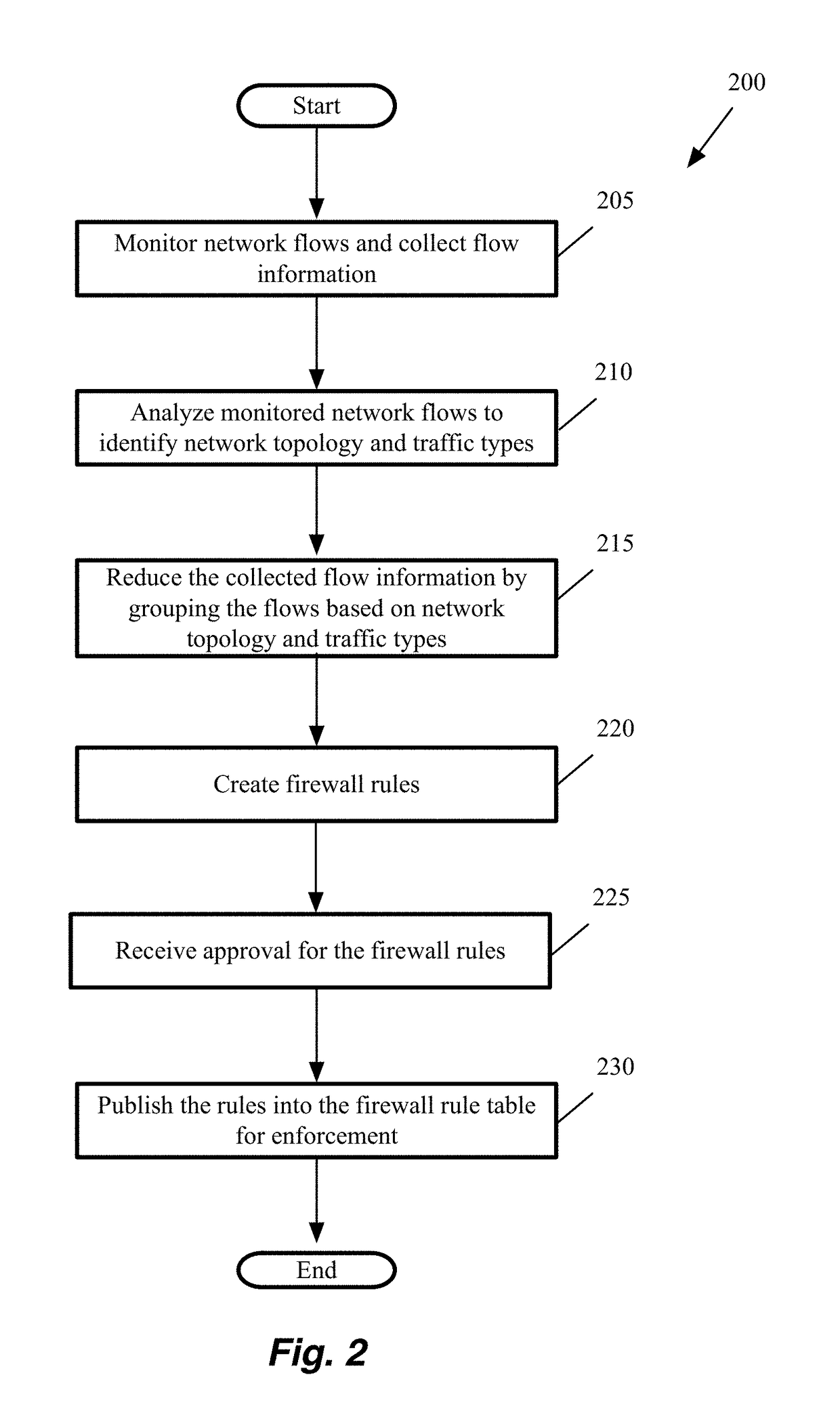
[0045]Some embodiments provide a method of defining micro-segmentation or security policies using a zero trust model for new and existing applications in a datacenter. In a zero trust model, a network is divided into small (or micro) segments and security is applied at the boundaries of each micro-segment. The method analyzes packet traffic generated by the virtual machines that implement these applications. The method receives a selection of a set of seed nodes (for instance through a user interface) and performs flow collection, flow analysis and security policies definition for the seeds in parallel.
[0046]Some embodiments perform flow mon...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com