Device and method based on pixel encryption
An image device and pixel technology, applied in the field of information security, can solve problems such as inability to prevent shooting, and achieve the effect of enhancing confidentiality and high stability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
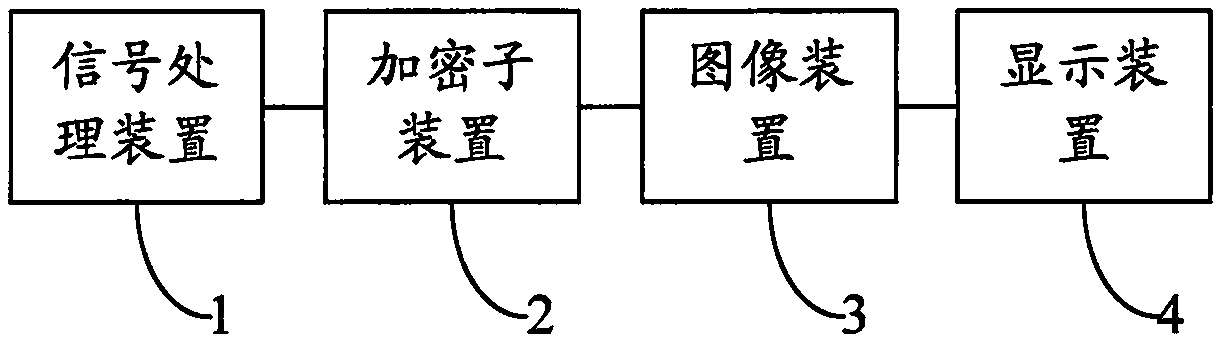
[0043] figure 1 It is a structural diagram of a device based on pixel encryption according to Embodiment 1 of the present invention. see figure 1 , this embodiment provides a device based on pixel encryption, which includes: a signal processing device 1 , an encryption sub-device 2 , an image device 3 and a display device 4 .
[0044] The output end of the signal processing device 1 is electrically connected to the input end of the encryption sub-device 2 . The signal processing device 1 is used to decompose the pixels of the file to be encrypted to obtain the processed file, and is also used to collect the specific content of the file to be encrypted, and send the processed file to the encryption sub-device 2 . The signal processing device 1 adopts a SiI9011 chip. Files to be encrypted include but are not limited to text, pictures and videos.
[0045] The output end of the encryption sub-device 2 is electrically connected with the input end of the imaging device 3 . The ...
Embodiment 2
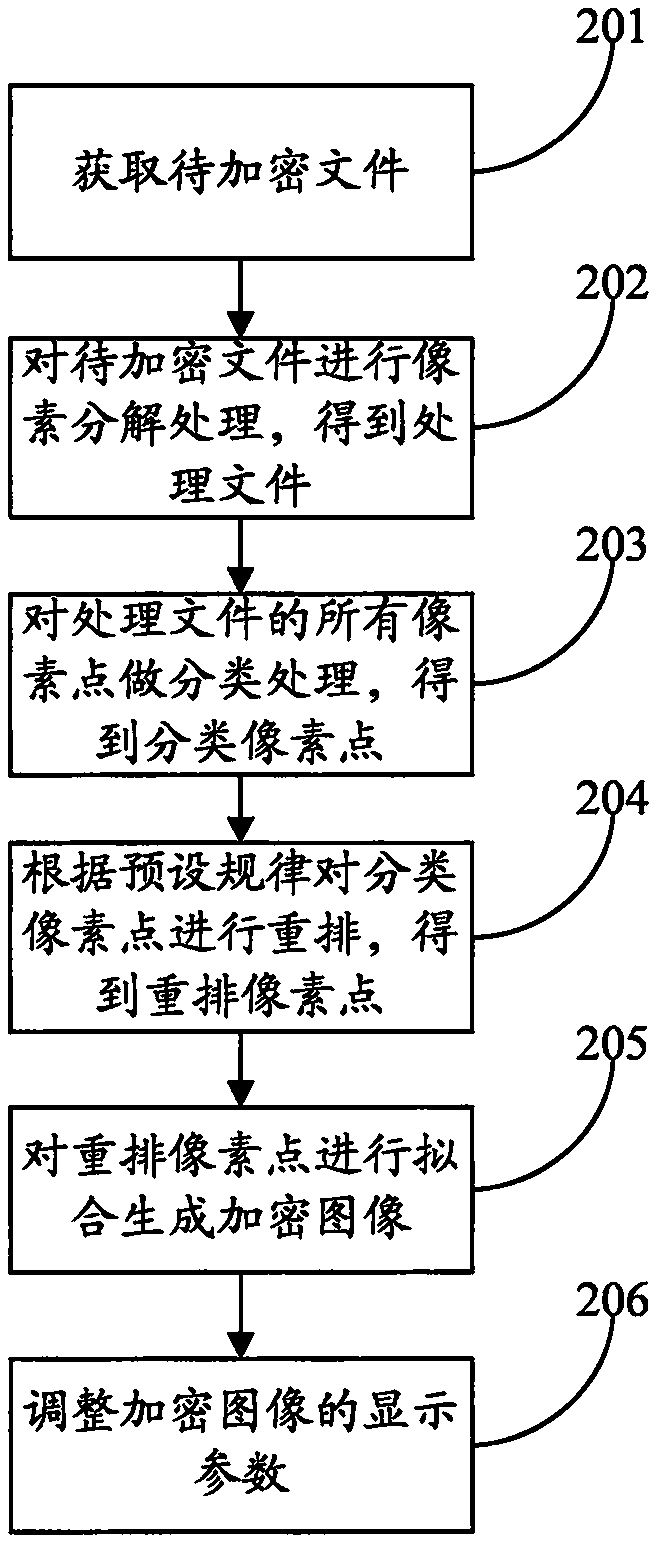
[0055] figure 2 It is a flow chart of the pixel-based encryption method according to Embodiment 2 of the present invention. see figure 2 , this embodiment 2 provides a method based on pixel encryption, which includes:
[0056] Step 201, obtain the file to be encrypted. Files to be encrypted include but are not limited to text, pictures and videos.
[0057] Step 202, performing pixel decomposition processing on the file to be encrypted to obtain the processed file. It specifically includes: acquiring a display image of the file to be encrypted, and splitting pixels of the display image.
[0058] Step 203, perform classification processing on all pixels of the processed file to obtain classified pixels. Specifically include:
[0059]Divide pixels with the same RGB value in all pixels of the processed file into one category. RGB represents the colors of the three channels of red (red, R), green (green, G), and blue (blue, B). The RGB color mode is a color standard in the...
Embodiment 3
[0065] This embodiment provides a pixel encryption system. The pixel encryption system includes: a signal processing device, an encryption sub-device and an image device.
[0066] The signal source transmits the file to be encrypted to the signal processing device. Files to be encrypted include text, pictures, and videos.
[0067] The signal processing device receives and collects the file to be encrypted, copies the original RGB value of the file to be encrypted, decomposes the original pixels of each frame of the image in the file to be encrypted to obtain a processed file, and transmits the processed file to the encryption sub-device.
[0068] The signal source and the signal processing device are connected through a high-definition multimedia interface (High Definition Multimedia Interface, HDMI). The signal processing device is electrically connected with the encryption sub-device.
[0069] The encryption sub-device encrypts the processing file, generates an encrypted ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com