Computer document operational safety audit system
A technology of operation security and computer, which is applied in the field of computer document operation security audit system, can solve problems such as the decline of competitiveness, failure of enterprise investment, and weak security management of terminal equipment, so as to improve effectiveness, ensure safety and integrity, and facilitate Effect of Intranet Security Analysis
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] Below in conjunction with accompanying drawing and embodiment the present invention is described in detail:
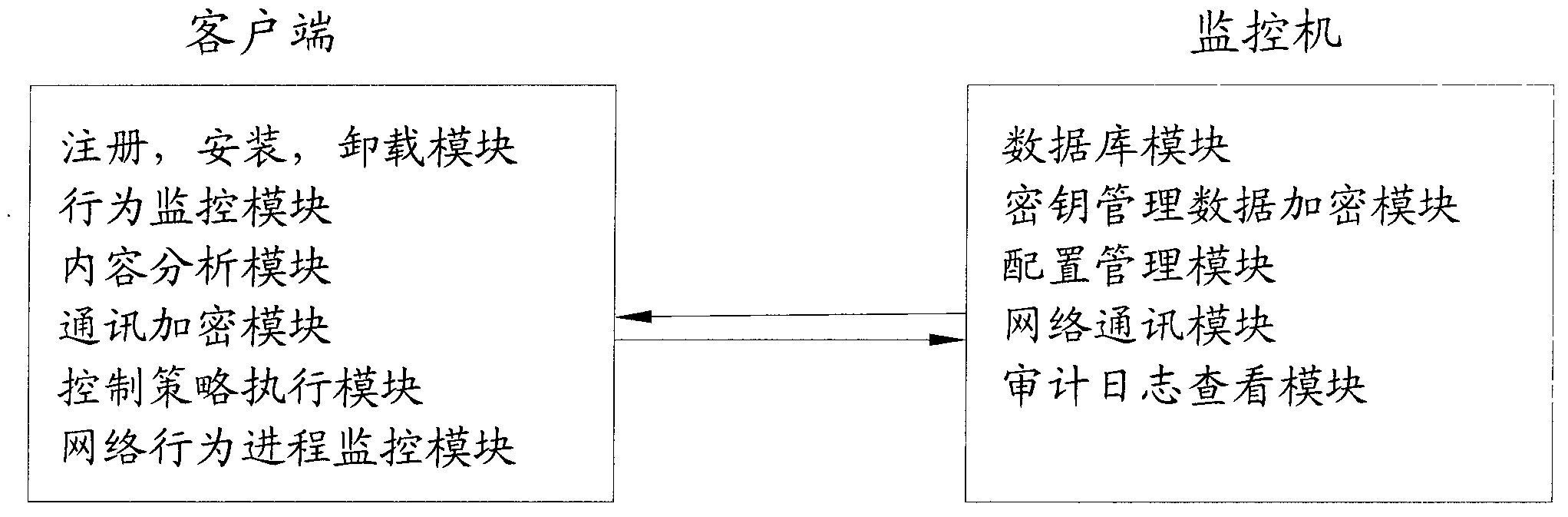
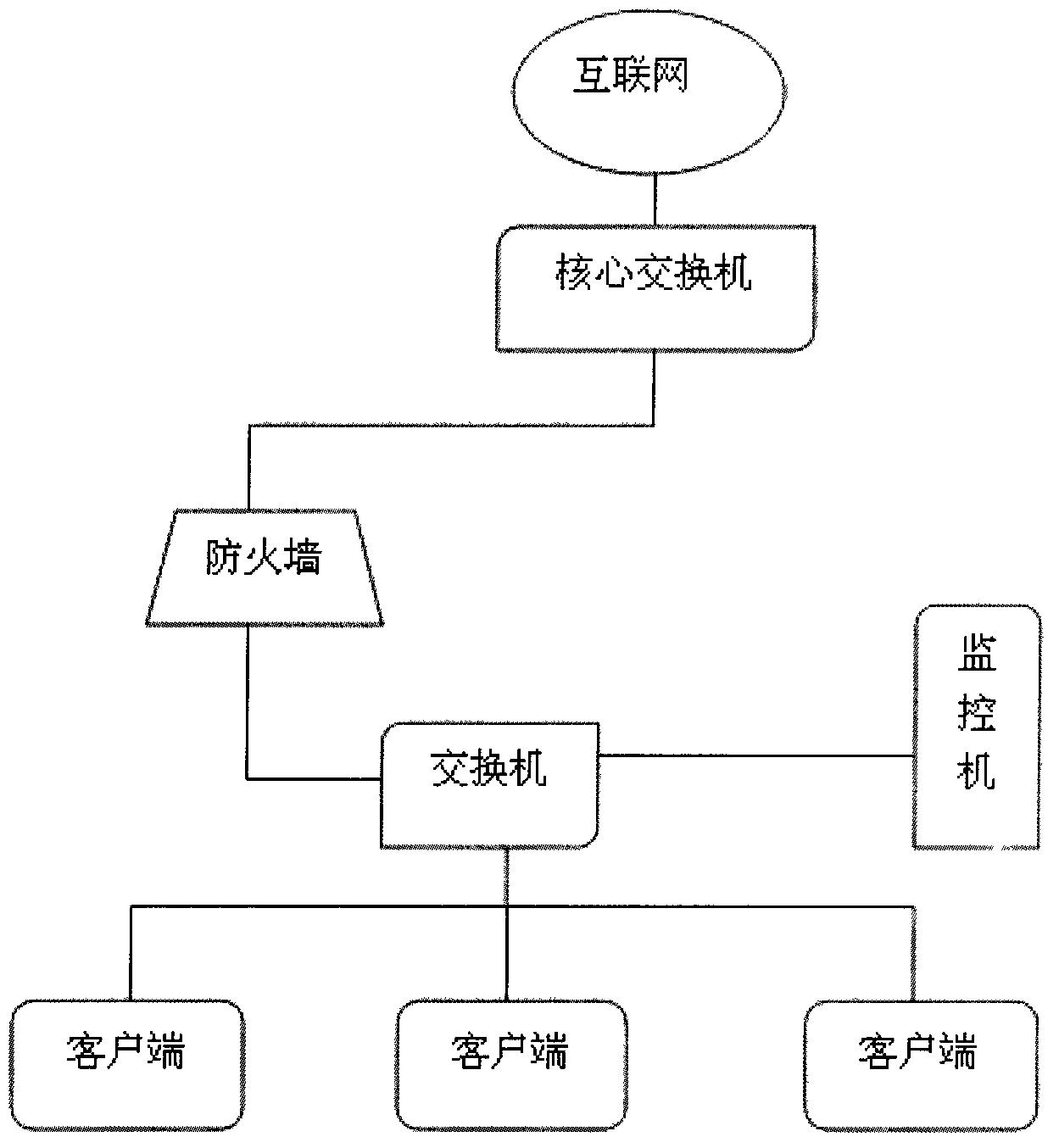
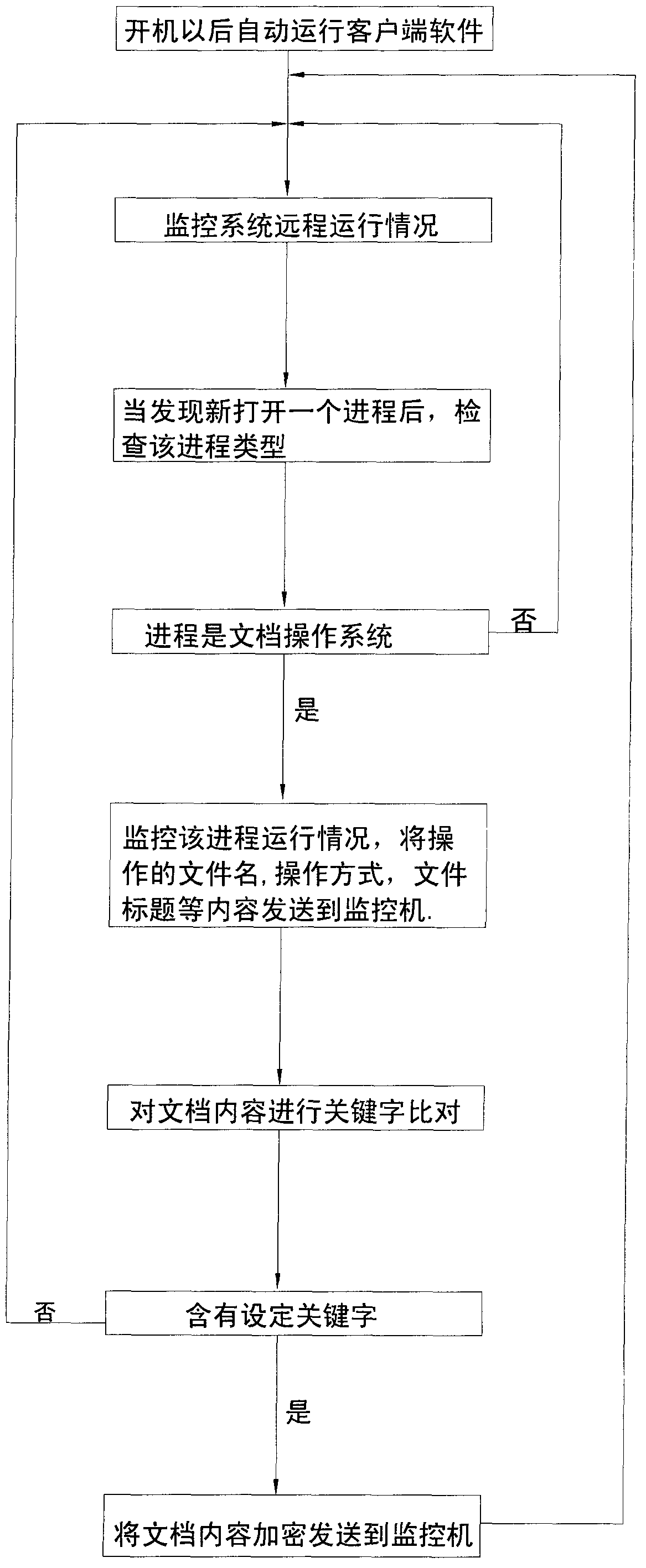
[0027] Such as figure 1 , figure 2 As shown, it includes a monitoring machine and client software, the monitoring machine includes a network communication module for network communication between the monitoring machine and the client; a database operation module is used for real-time recording of document operations sent by the client software Logs, documents suspected of violating regulations, and software and hardware asset information; key management and data encryption modules, which are used to encrypt confidential files and log information transmitted with special protocols, and manage passwords; monitoring machine server configuration management modules are used to define The control strategy for the client includes the control strategy of disabling the U disk, disabling the wireless network, and locking the IP, and sending it to all target clients; the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com