Tamper-proof encryption implementation method and device in batch data uploading process
A technology of batch data and implementation method, which is applied in the field of data upload, can solve the problems of inability to ensure authenticity, data monitoring, interception and tampering, etc., and achieve the effect of ensuring non-repudiation, safeguarding interests, and preventing leaks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
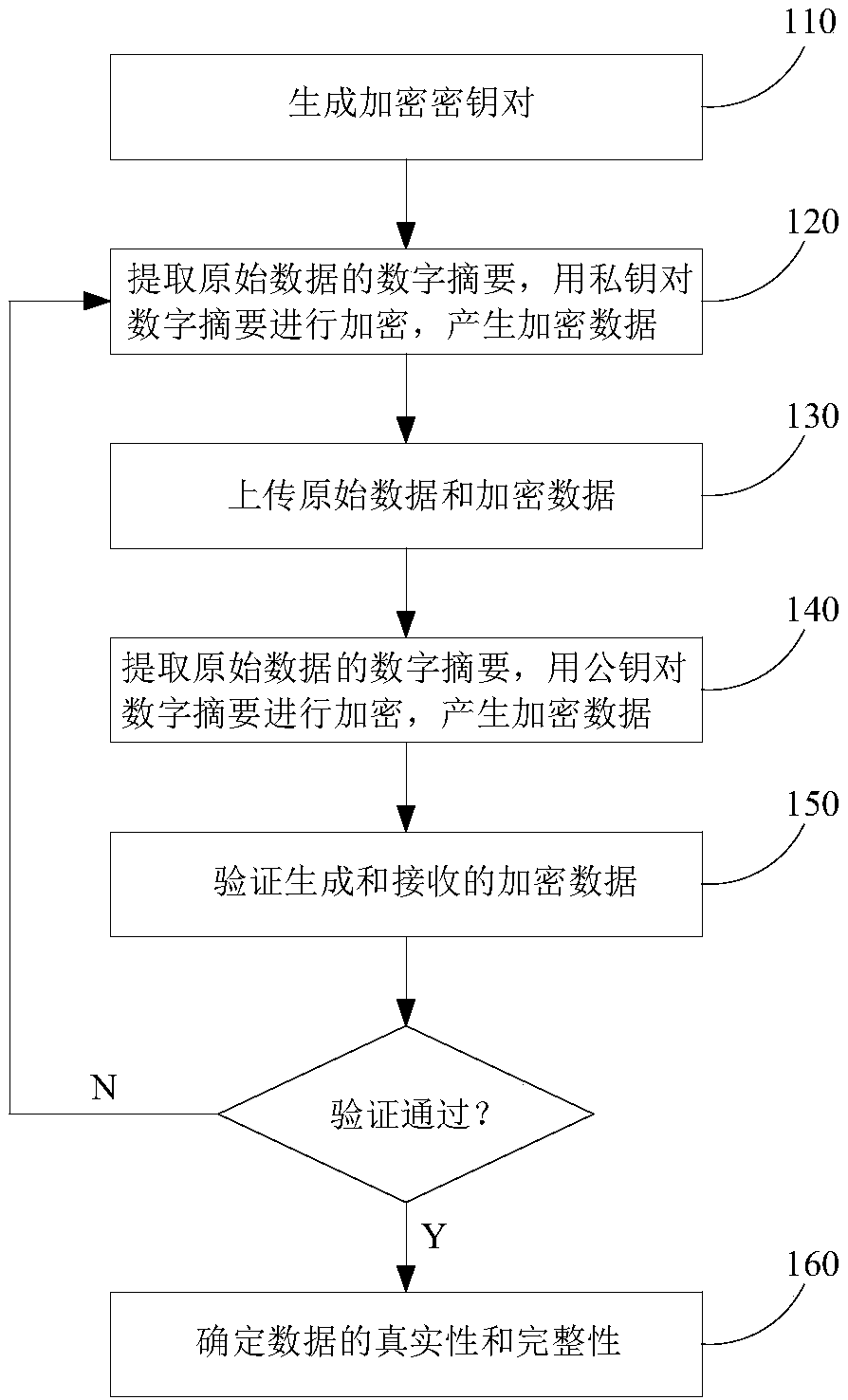
[0055] A tamper-proof encryption implementation method in batch data upload, which is used to ensure the authenticity and non-repudiation of data, please refer to figure 1 As shown, it includes the following steps:
[0056]110. Use the 3DES algorithm (Triple Data Encryption Algorithm triple data encryption algorithm, which is a general name for block ciphers) to generate a key pair; the key pair can be provided by a third-party security platform for digital signatures, effectively protecting the interests of both parties in data transmission. The length of the key pair should be sufficiently secure, for example, a 1024-bit key pair can be used. The key pair includes a private key and a public key corresponding to the private key, the private key is given to a data sending terminal, and the public key is given to a data receiving terminal.
[0057] 120. The sending terminal uses the SHA256 algorithm (Secure Hash Algorithm secure hash algorithm, which is a family of cryptograph...
Embodiment 2
[0064] Embodiment 2 provides a device for implementing tamper-proof encryption in batch data upload, which is the virtual device of Embodiment 1 above, which includes:
[0065] A key pair generating unit, configured to generate a key pair using the 3DES algorithm; the key pair includes a private key and a public key corresponding to the private key, the private key is given to the data sending terminal, and the public key is given to Data receiving terminal;
[0066] The first encrypted data generation unit is used for the sending terminal to use the SHA256 algorithm to extract the first digital abstract from the original data to be sent, and then use the private key to encrypt the first digital abstract with the RSA algorithm to generate the first encrypted data;
[0067] a sending unit, configured for the sending terminal to upload the original data and the first encrypted data to be received by the receiving terminal;
[0068] The second encrypted data generation unit is u...
Embodiment 3
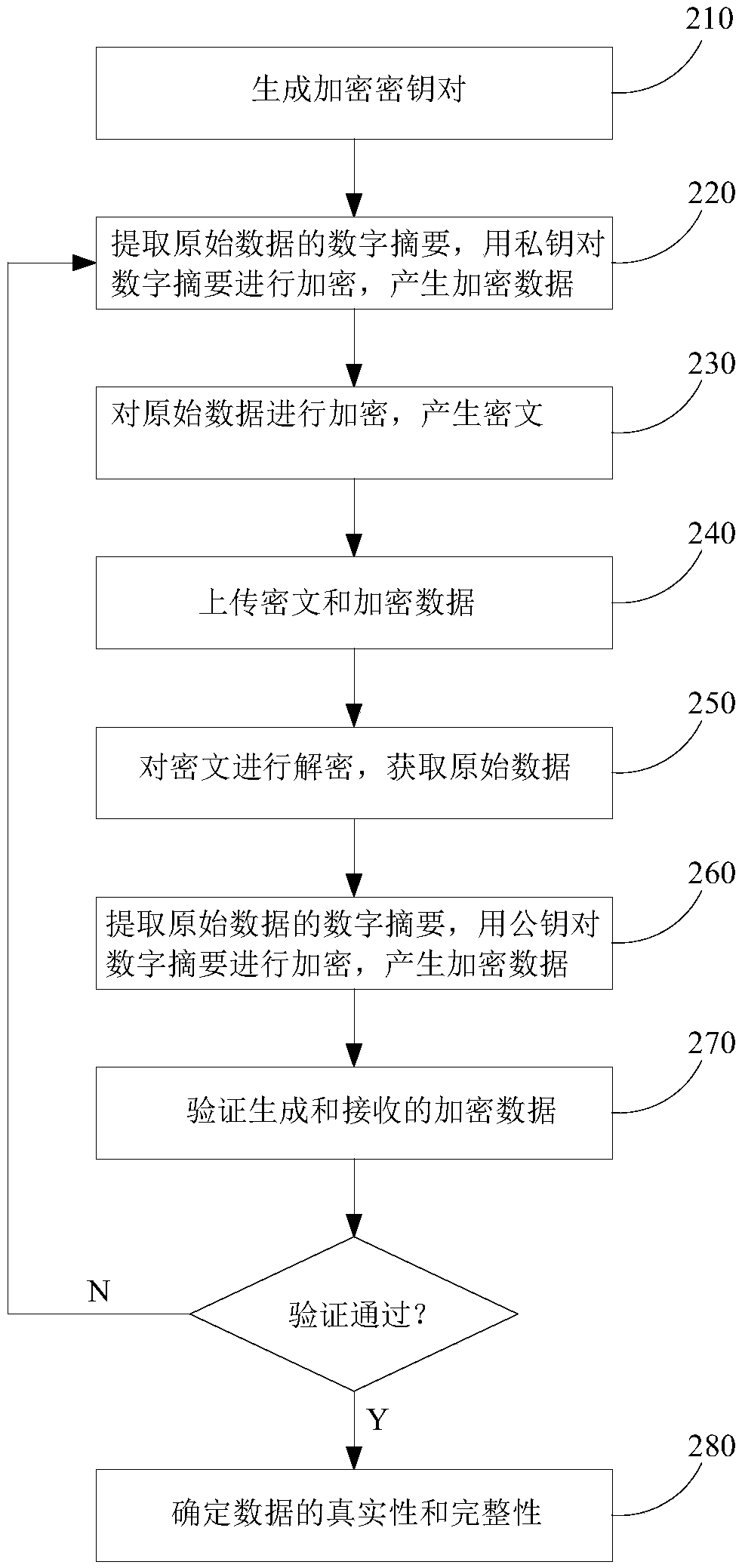
[0072] Embodiment 3 is an improvement based on the embodiment. It encrypts the original data to be sent first, even if the transmitted data is intercepted, it will not lead to data leakage, and more effectively prevents data from being intercepted and resulting in leakage The occurrence of risk. Please refer to figure 2 As shown, it includes the following steps:
[0073] 210. Use the 3DES algorithm to generate a key pair; the key pair is two pairs, and the key pair includes a first private key, a second private key, and a first public key corresponding to the first private key, and A second public key corresponding to the second private key. The key pair can be provided by a third-party security platform and used for digital signatures to effectively protect the interests of both parties in data transmission. The length of the key pair should be sufficiently secure, for example, a 1024-bit key pair can be used. The first private key and the second private key are assigned...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com