Container-based malicious code detection sandbox system and detection method
A malicious code detection and container technology, which is applied in the field of information security, can solve the problems of slow startup speed of virtual machines, large system resource consumption, and insufficient practicability, achieving both security and operating efficiency, low system resource consumption, and improved practicality. sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Example Embodiment
[0041] The present invention will be described in detail below with reference to the drawings and through specific embodiments. The following embodiments are for explaining the present invention, and the present invention is not limited to the following embodiments.
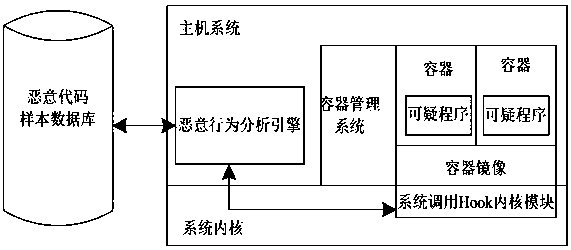
[0042] Such as figure 1 As shown, a container-based malicious code detection sandbox system provided by an embodiment of the present invention includes a host system, a malicious behavior analysis engine, a container management system, and several containers;
[0043] The host system is used to manage and run the container, intercept and filter system calls during the running of the container, and send system call operation information to the malicious behavior analysis engine;
[0044] Malicious behavior analysis engine, used to receive the container system call information intercepted by the host system, and perform malicious behavior analysis to generate an analysis report;
[0045] The container management system runs...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com