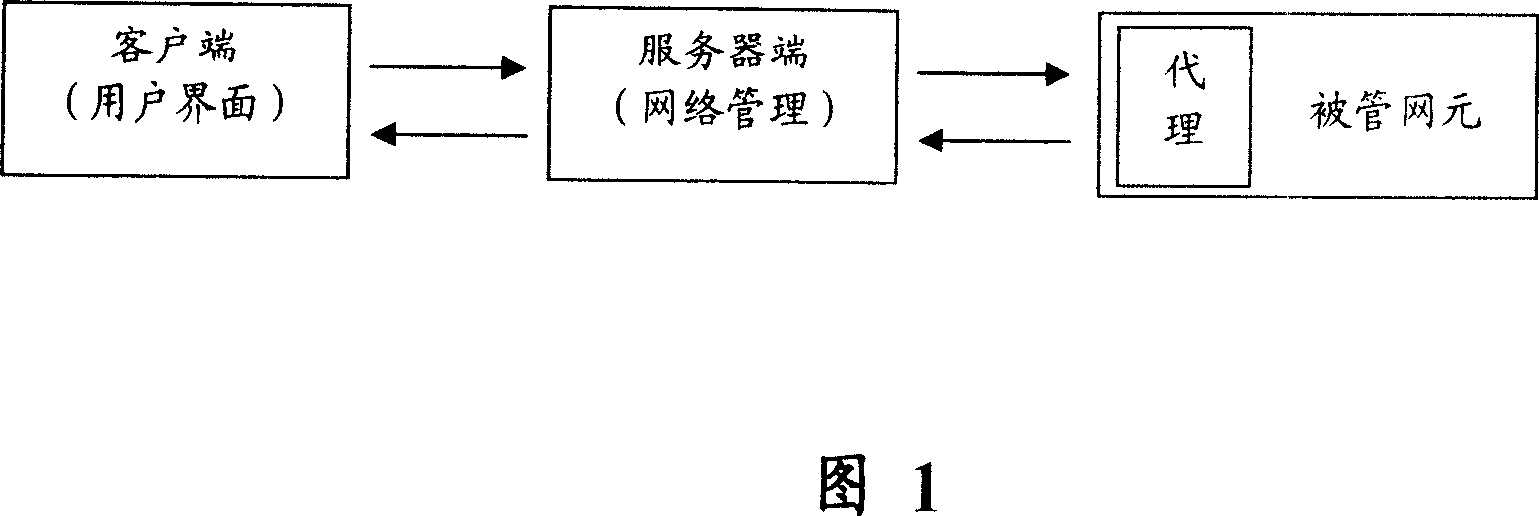
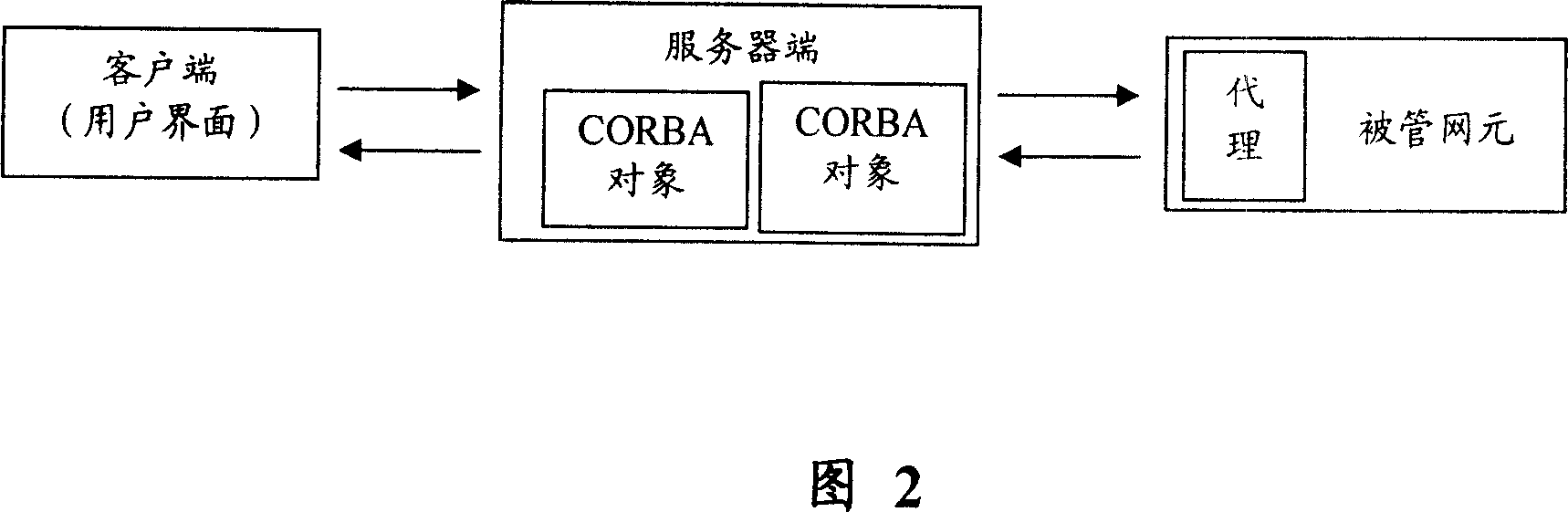
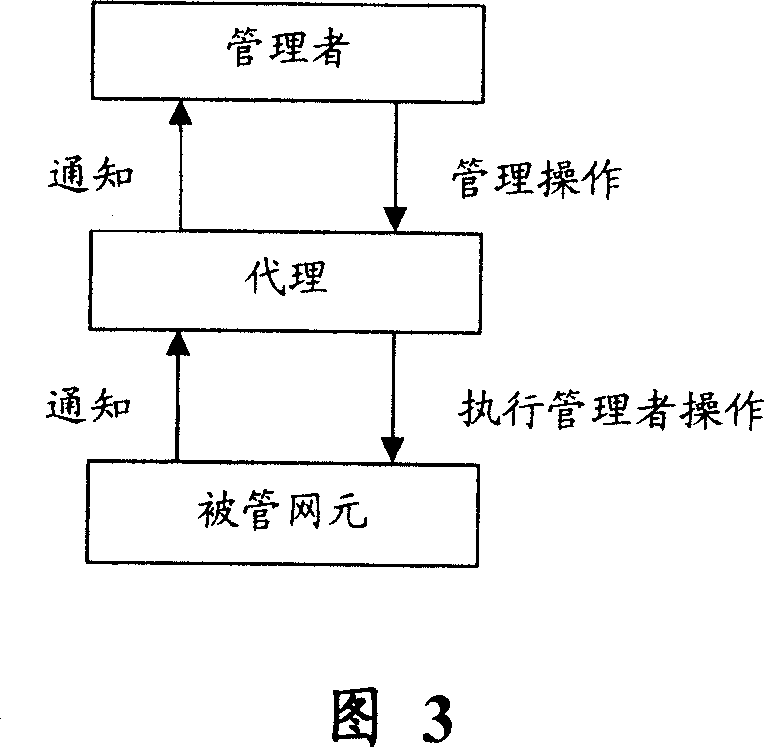
Patents
Literature
153results about How to "Avoid single point of failure problems" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method for realizing distributed virtual networks applicable to cloud platform
InactiveCN104468746AAvoid single point of failure problemsDoes not affect the normal provision of network servicesNetworks interconnectionComputer moduleVirtual switch
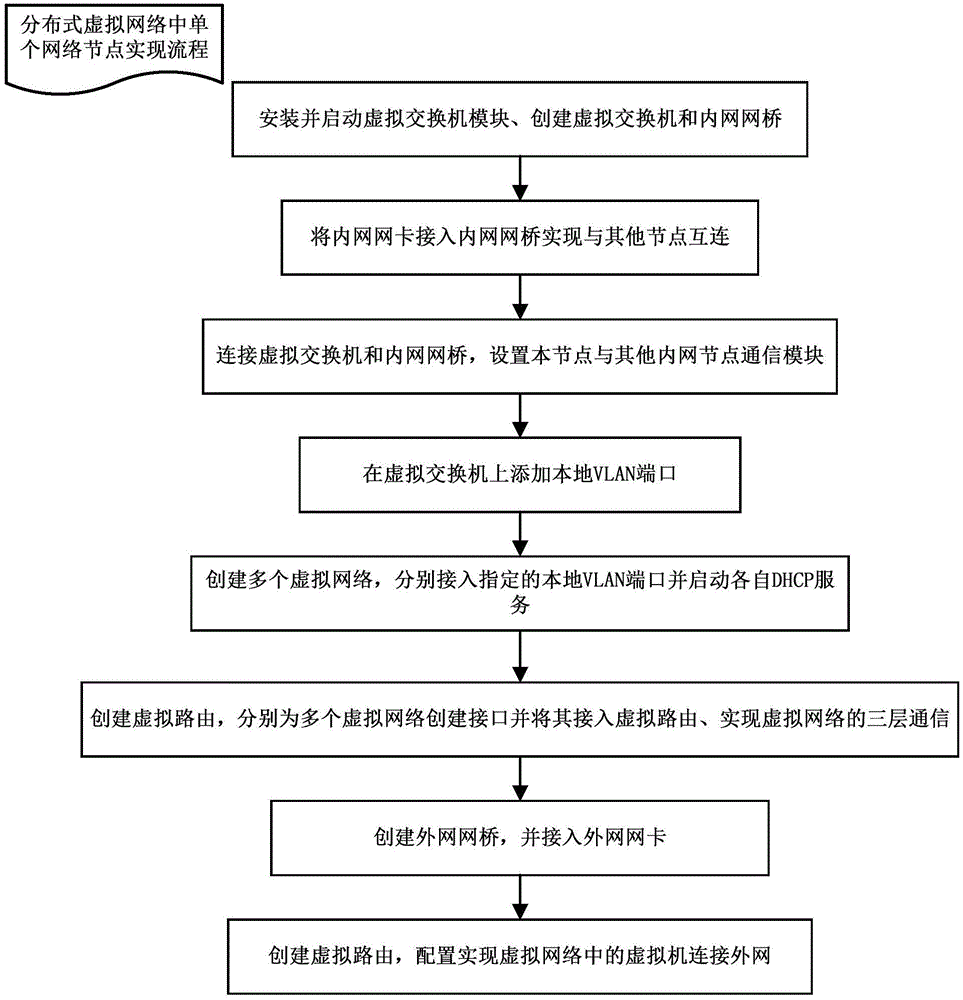
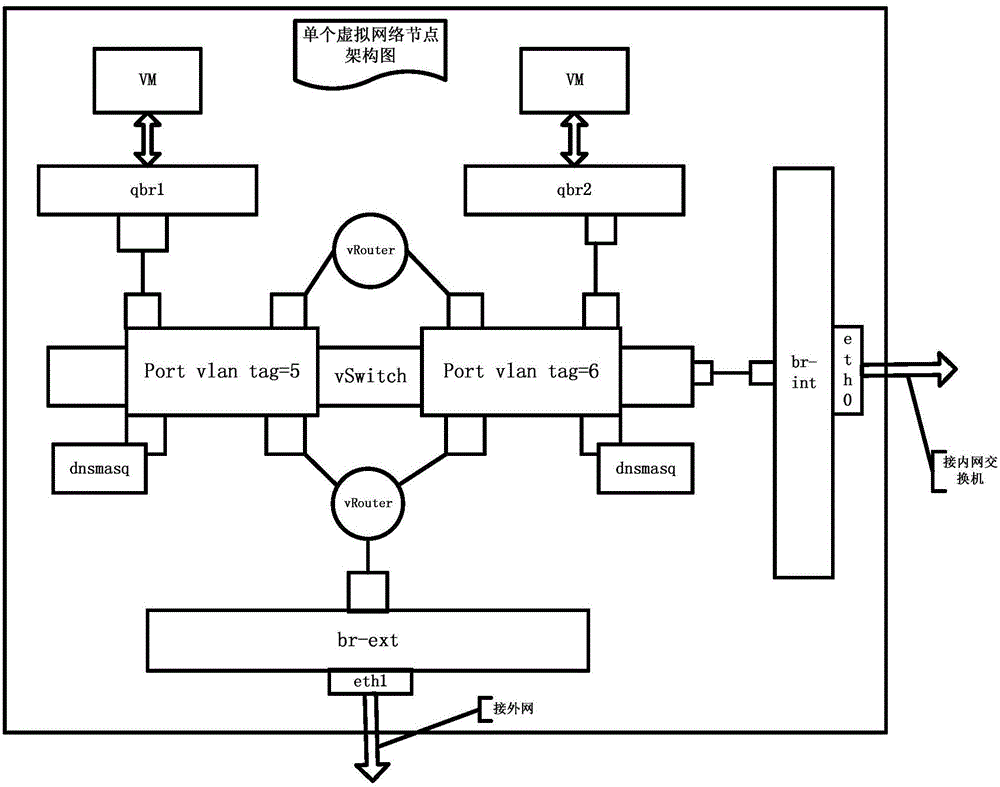
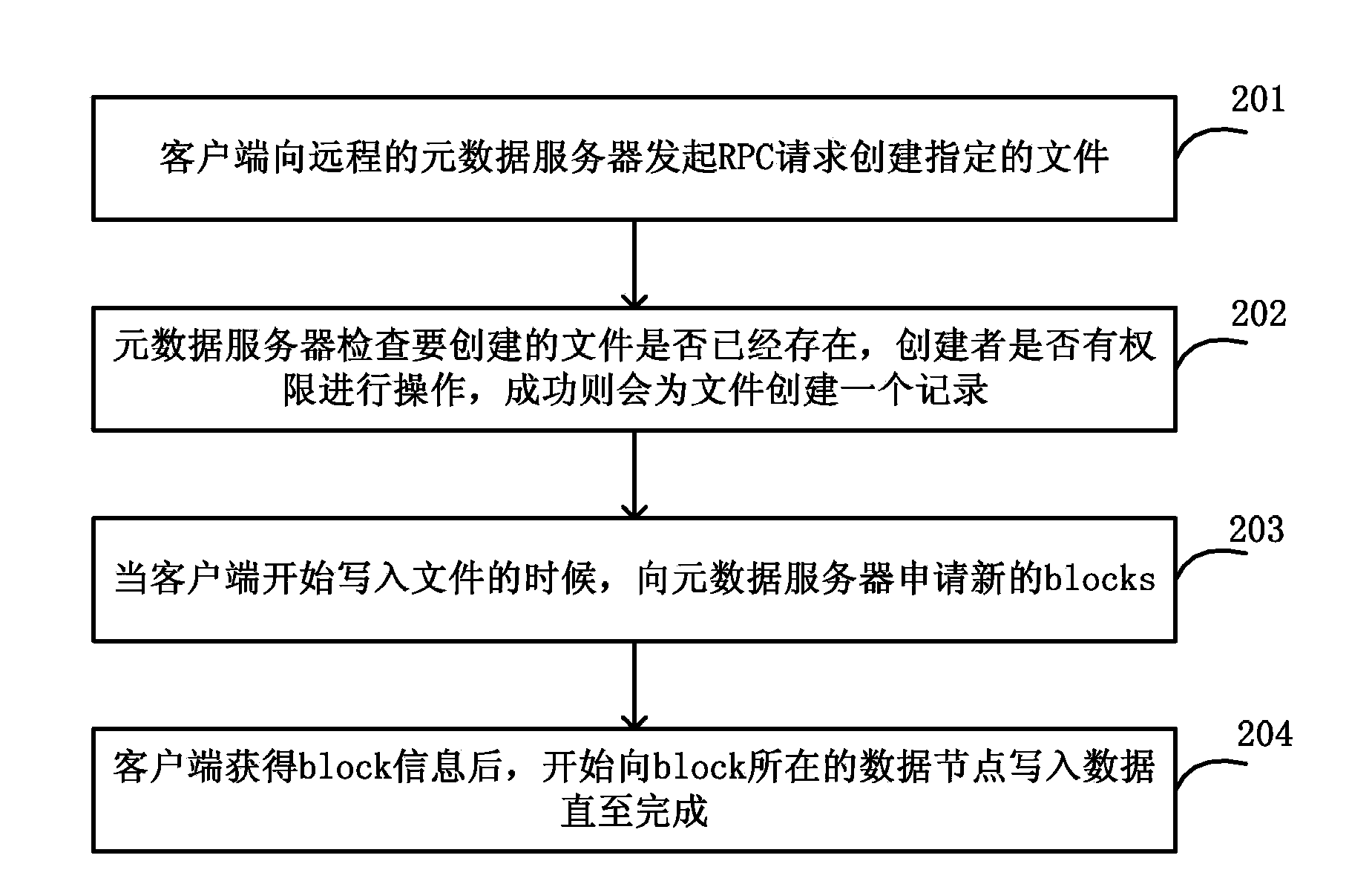
The invention relates to the technical field of cloud computing management, in particular to a method for distributed virtual networks applicable to a cloud platform. According to the method, any number of physical nodes are selected as network nodes of the cloud platform, and the network nodes establish and provide virtual network service; establishment of the network nodes includes the steps that (1), a virtual switch module is installed and started, and a virtual switch and an intranet network bridge are established; (2), an intranet network card is connected into the intranet network bridge; (3), the virtual switch and the intranet network bridge are connected, and a communication module for the node and other intranet nodes is set; (4), local VLAN ports are added; (5), the multiple virtual networks are established; (6), a virtual route is established; (7), an extranet network bridge is established, and an extranet network card is connected in; (8), a virtual route is established. Single-point failures of centralized network service of the cloud platform can be avoided, load balance of the network service nodes is achieved, the virtual networks can be managed flexibly and conveniently, and the method can be used for realizing the distributed virtual networks.
Owner:G CLOUD TECH
A multi-tenant virtual network isolating method
ActiveCN104394130AAvoid single point of failure problemsImprove reliabilityTransmissionCloud computingPhysical interface
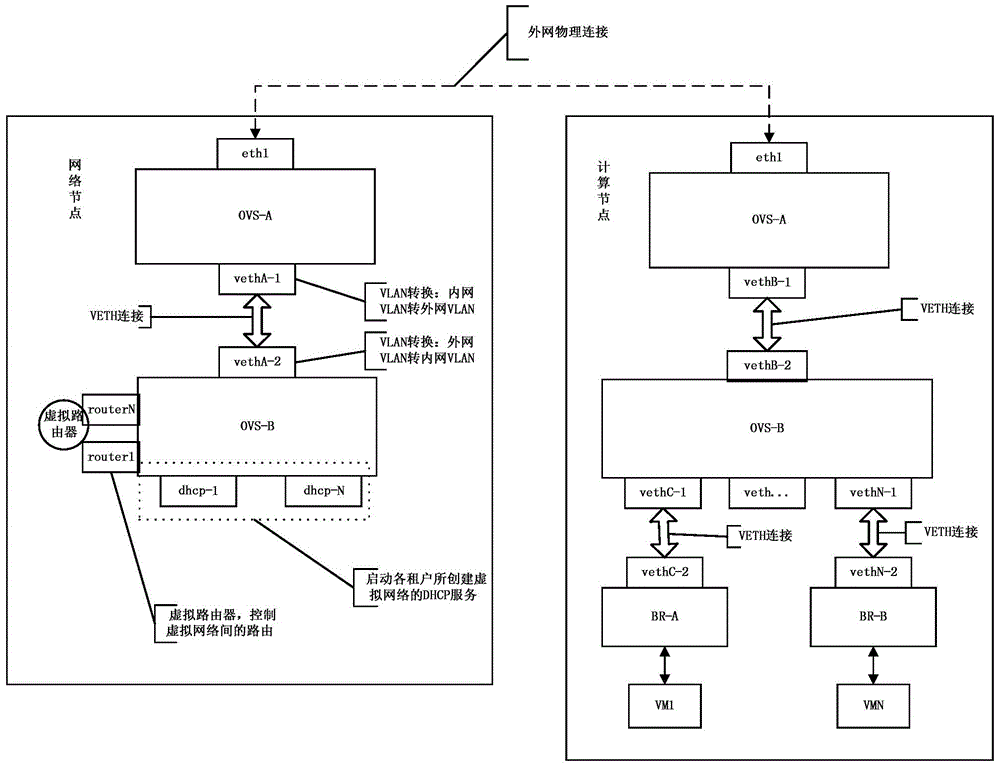
The invention relates to the technical field of cloud computing and particularly to a highly-flexible multi-tenant virtual network isolating method. In the invention, the method comprises: firstly creating two virtual switches OVS-A and OVS-B in an initialized process; then adding a physical interface eth1 connecting to an external network to the OVS-A; and then creating a VETH device to connect the OVS-A with the OVS-B. A process of creating a private network and starting a virtual machine comprises: (1) adding an internal port dhcp-N and setting an internal network VLAN-N; (2) creating private network space netns-N; (3) accessing the dhcp-N port to the netns-N; (4) setting an internal and external network VLAN converting rule at both ends of the VETH device connected to OVS-A and OVS-B of the network node and the computing node; (5) creating a linux network bridge at the computing node; (6) creating a VETH device to connect to the BR-N with the OVS-B; and (7) the virtual machine bridging to BR-N to be started and obtaining an IP through the dhcp service started at the step (3). The invention provides the highly flexible multi-tenant virtual network isolating method.
Owner:G CLOUD TECH
Client terminal updating method, server, client terminal of network management system
InactiveCN101141303AImprove performanceAvoid single point of failure problemsUser identity/authority verificationData switching networksSoftware engineeringNetwork management
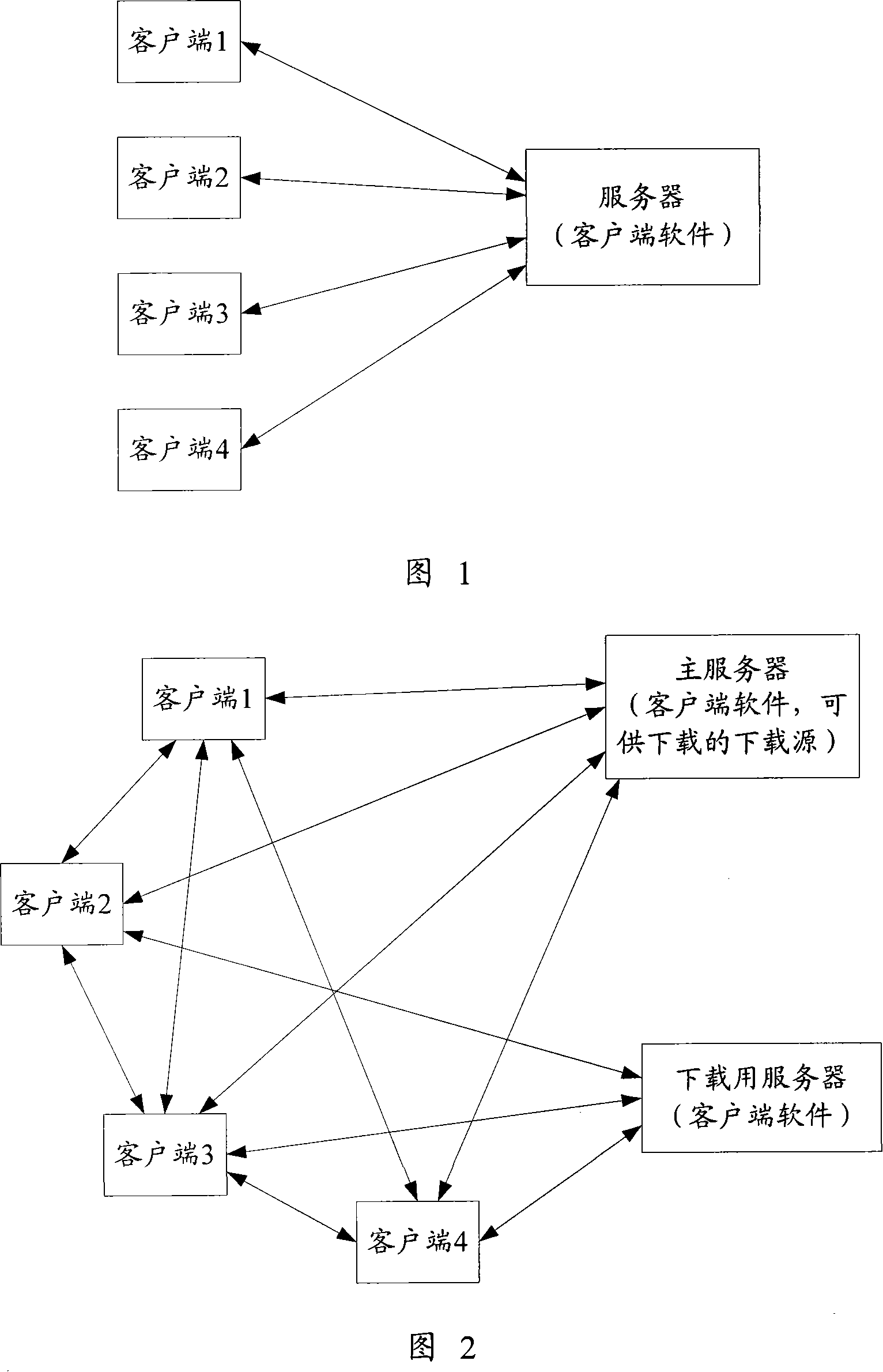
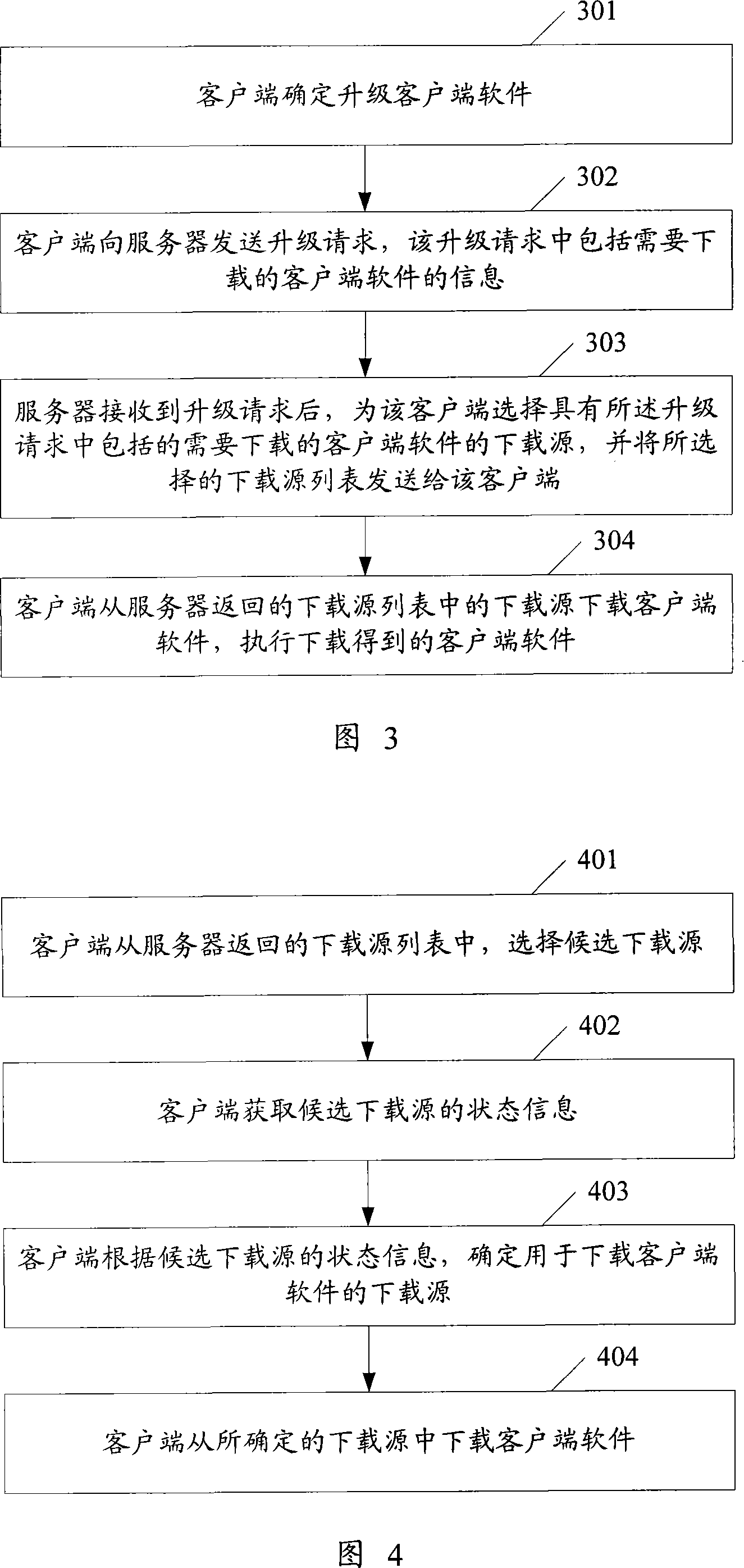
The utility model discloses a client updating method for the network management system. The server receives the updating request from the client. Such updating request comprises the information concerning the client software to be downloaded; the server chooses the download source which is subject to the required client software as per the available download source listed files. Such download source is from the available download source; the server sends the required download source list to the client, so that the client can choose the download source from the download source list to download the client software and execute the client software. Also, the utility model discloses a server and a client which are suitable to the network management system. Based on the method, the server and the client as disclosed by the utility model, the single point failure can be avoided as updating the client.
Owner:HUAWEI TECH CO LTD
Streaming media buffering proxy server system based on cluster
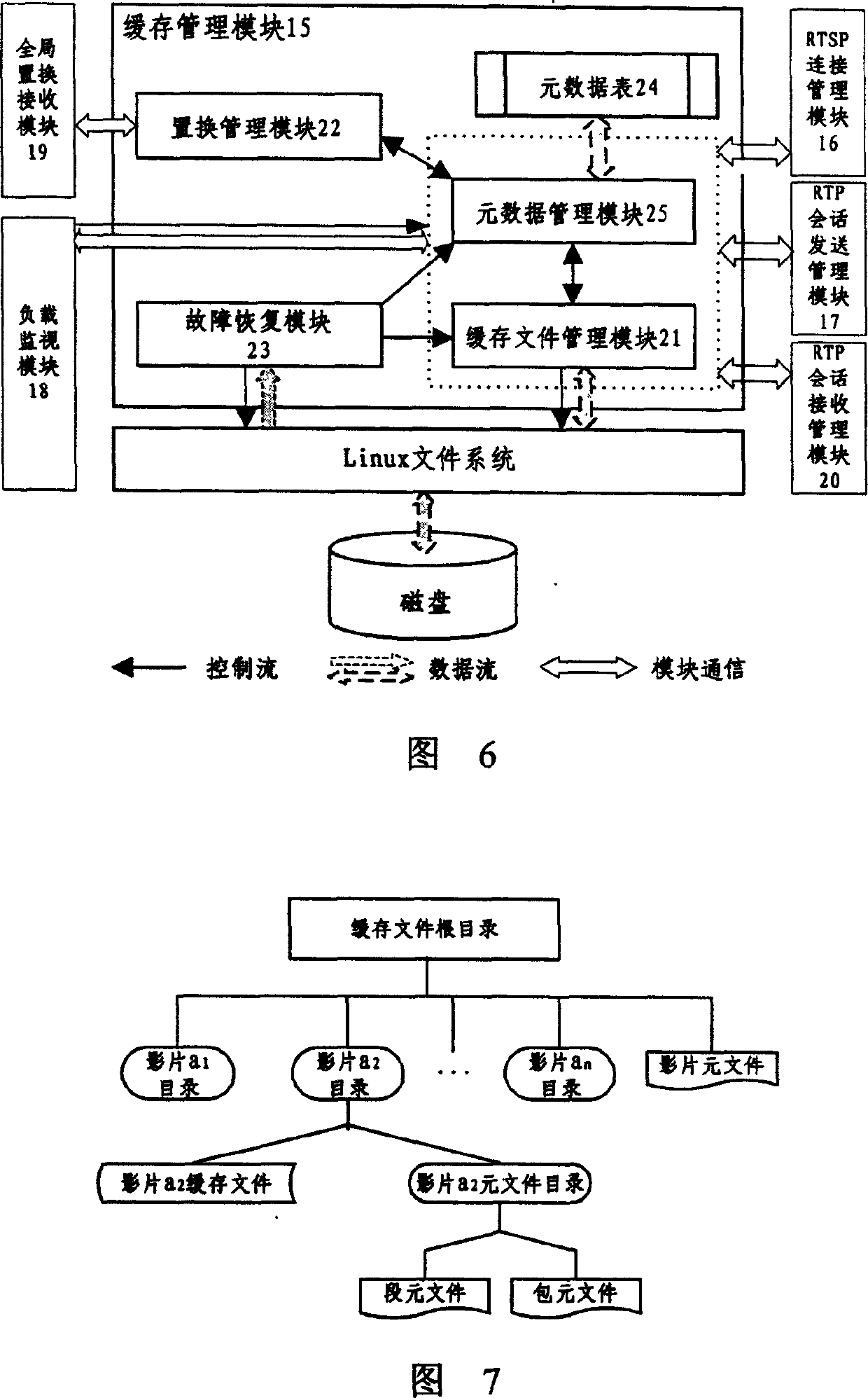
InactiveCN1595905AHigh scalability and fault toleranceImprove throughputStore-and-forward switching systemsTwo-way working systemsCluster basedLinux kernel
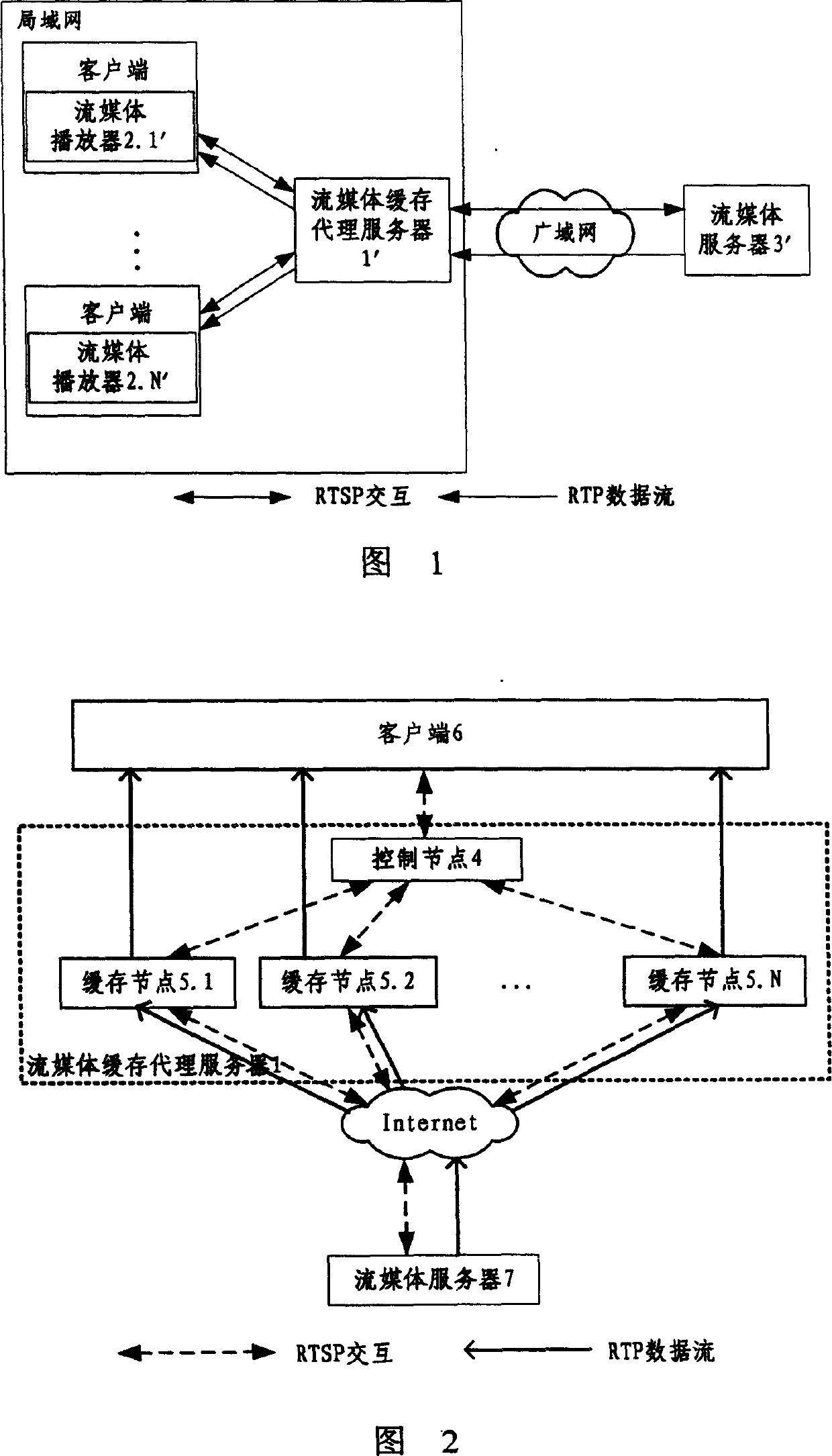
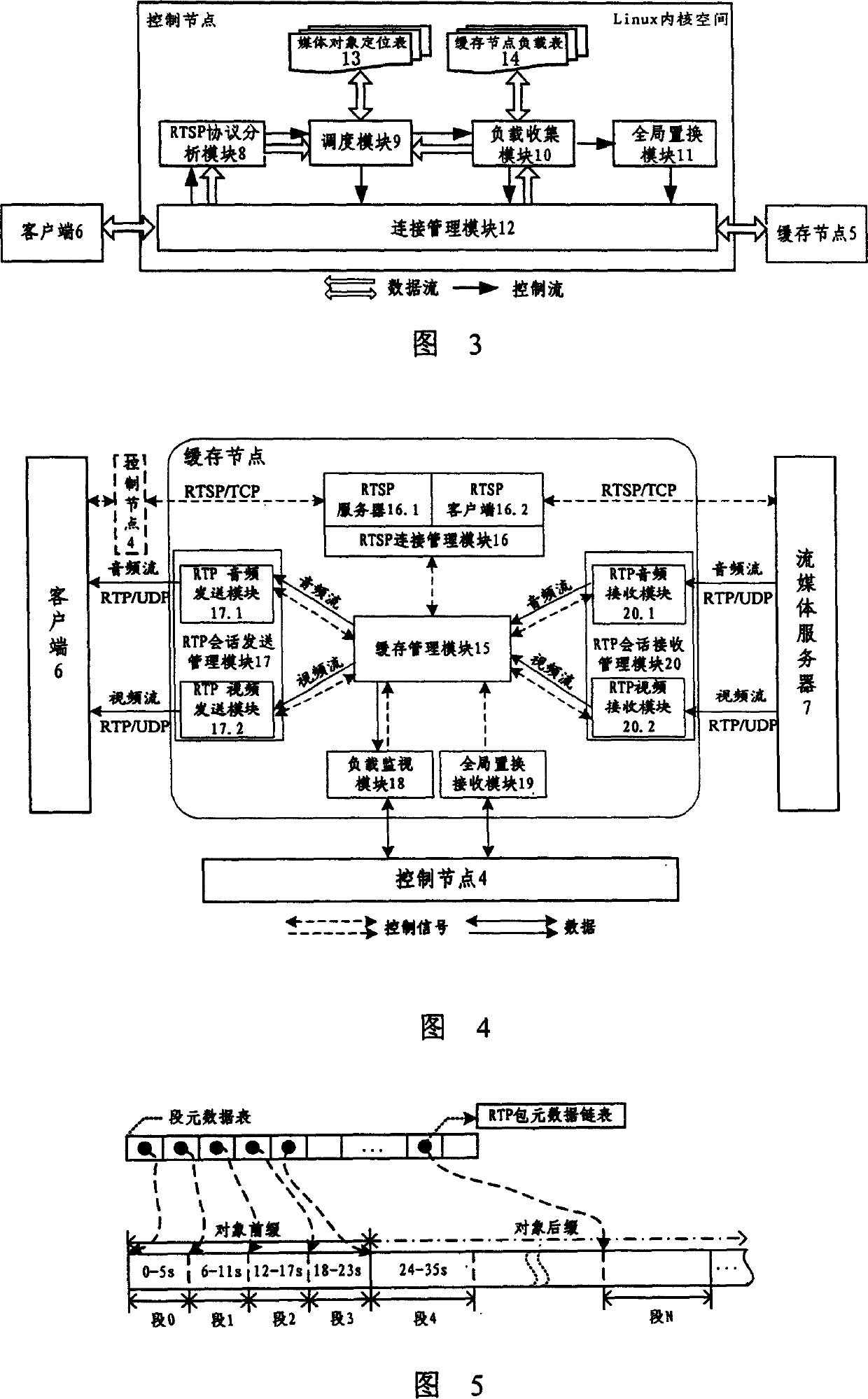
The invention discloses a group flow media buffer proxy server system including a control joint and a buffer joint. The control joint is realized in the Linux kernel layer, including connection managing model, dispatching model, load collecting model and global substituting model. The buffer joint includes RTSP connection managing model, RTP meeting managing model, buffer managing model, load supervising model and global substituting model. The system uses the merits of the group system, upgrades the buffer space management and efficiency; the system realizes a buffer managing tactics based on the combination of prefix and suffix of logic segment, the tactics synthesizes the buffer technology and prefix buffer technology, upgrades the buffer managing efficiency greatly.
Owner:HUAZHONG UNIV OF SCI & TECH
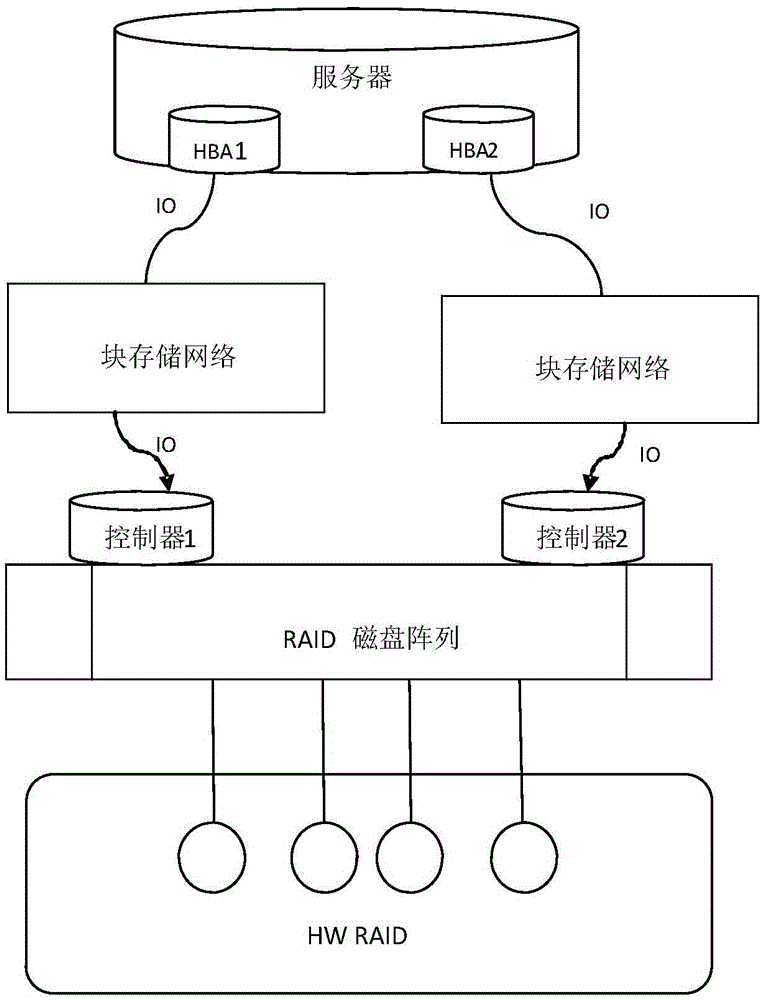
Distributed storage method and system of block device
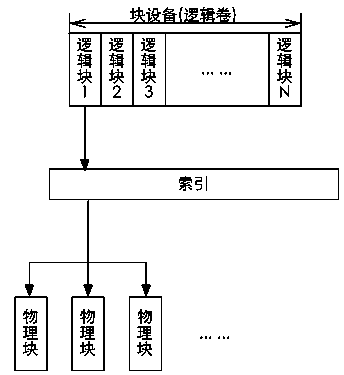
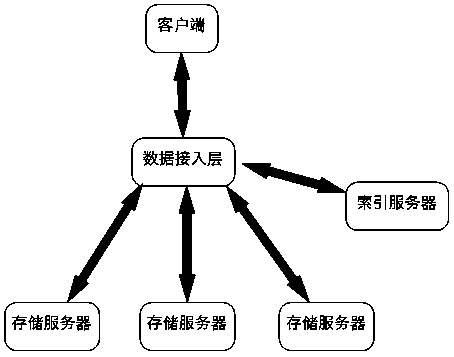
ActiveCN103870202AHighly reliable dataAvoid single point of failure problemsInput/output to record carriersProtocol processingIndexing Service
The invention is applicable to the storage field, particularly relates to distributed storage systems and discloses a distributed storage method and system of a block device. The method comprises defining the storage space of the block device as a logical volume and segmenting the logical volume into N logical blocks in a fixed size; actually storing the logical blocks in a plurality of physical storages, and associating the mapping relations of the logical blocks and a plurality of corresponding physical storage addresses through indexing. The system comprises a data access layer, an index server and a storage server, wherein the data access layer processes a read-write request of the block device on the basis of an iSCSI (Internet small computer system interface) protocol; after analyzing the protocol, the data access layer obtains the actual physical storage position of the logical block involved in the request from the index server; after receiving the request, the index server queries associated indexes to find a corresponding storage server and feeds information back to the data access layer; after receiving information fed back by the index server, the data access layer accesses the storage server to complete subsequent data reading and writing tasks.
Owner:UCLOUD TECH CO LTD
Network management system and method
InactiveCN1968283AImprove scalabilityImprove processing powerTransmissionSystem safetyNetwork management
The invention relates to a network manage system, which comprises user terminal for sending service request to corn module, and receiving feedback result; corn module for receiving the request and receiving the information reported from network unit; managed network unit for responding the service request of corn module and reporting order information to the corn module; the corm module comprises web service layer module, service manage layer module, service processing layer module, data storage layer module, access layer module which are interlayer managed. The invention also provides a relative manage method. The invention can improve system safety and flexibility without block.
Owner:HUAWEI TECH CO LTD
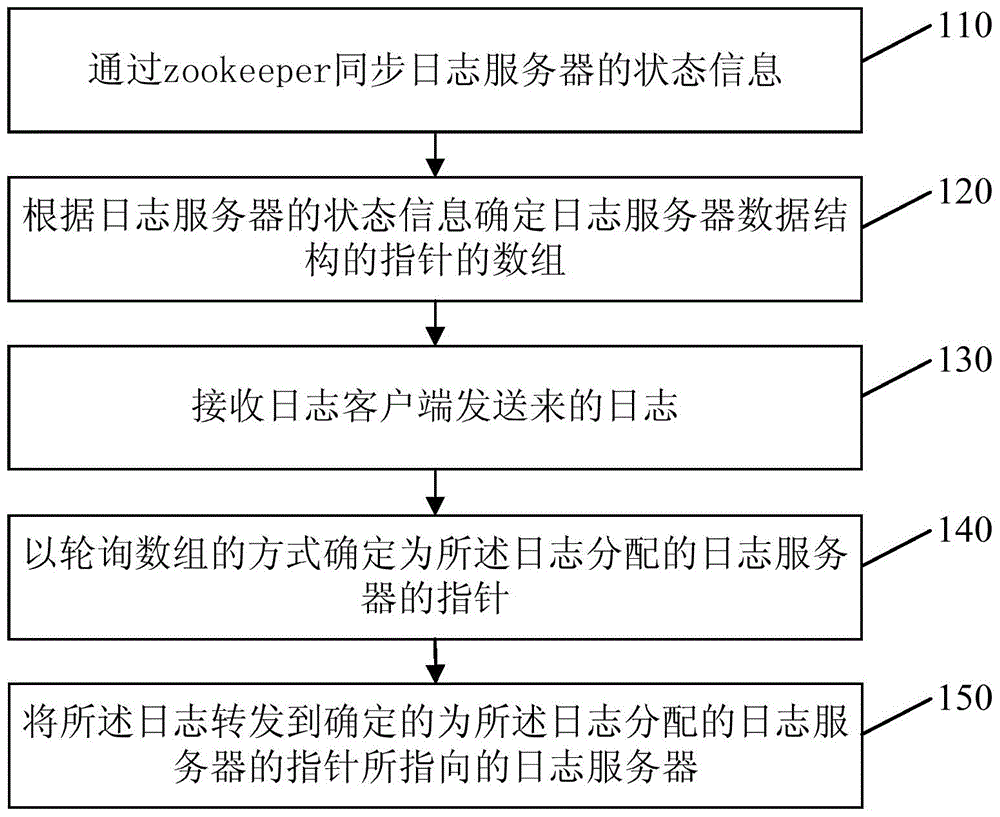
Method and device for log collection cluster load balance
ActiveCN104023083ALoad balancingAvoid single point of failure problemsTransmissionSingle point of failureData structure
The invention discloses a method and a device for log collection cluster load balance. The method comprises the following steps: synchronizing state information of a log server through zookeeper, confirming data of a pointer of a log server data structure according to the state information of the log server, receiving a log transmitted from a log client, confirming the pointer of the log server distributed by the log in a data group polling mode, and forwarding the log to a confirmed server to which the pointer of the log server distributed by the log points. Communication between a log collection server and a log server is achieved through zookeeper, as the zookeeper is a cluster, the problem of single point of failure is avoided, the log server is allocated for the received log according to the state information of the log server so as to store the log, and load balance is achieved.
Owner:GUANGDONG EFLYCLOUD COMPUTING CO LTD
Application QoS (Quality of Service) management system based on cloud service bus and operation method thereof
InactiveCN103002034AImprove efficiencyImprove operational efficiencyData switching networksQuality of serviceUser needs
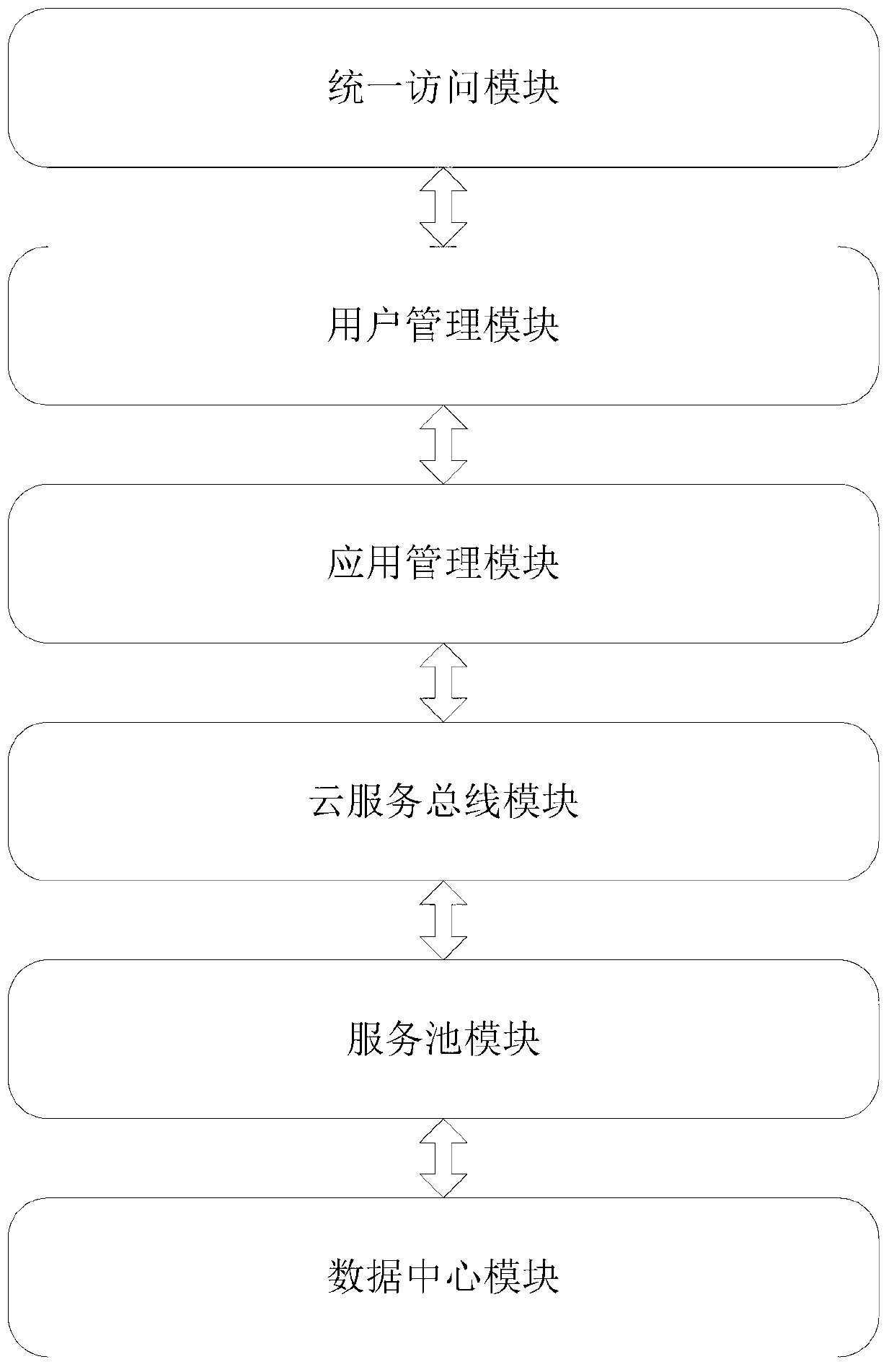
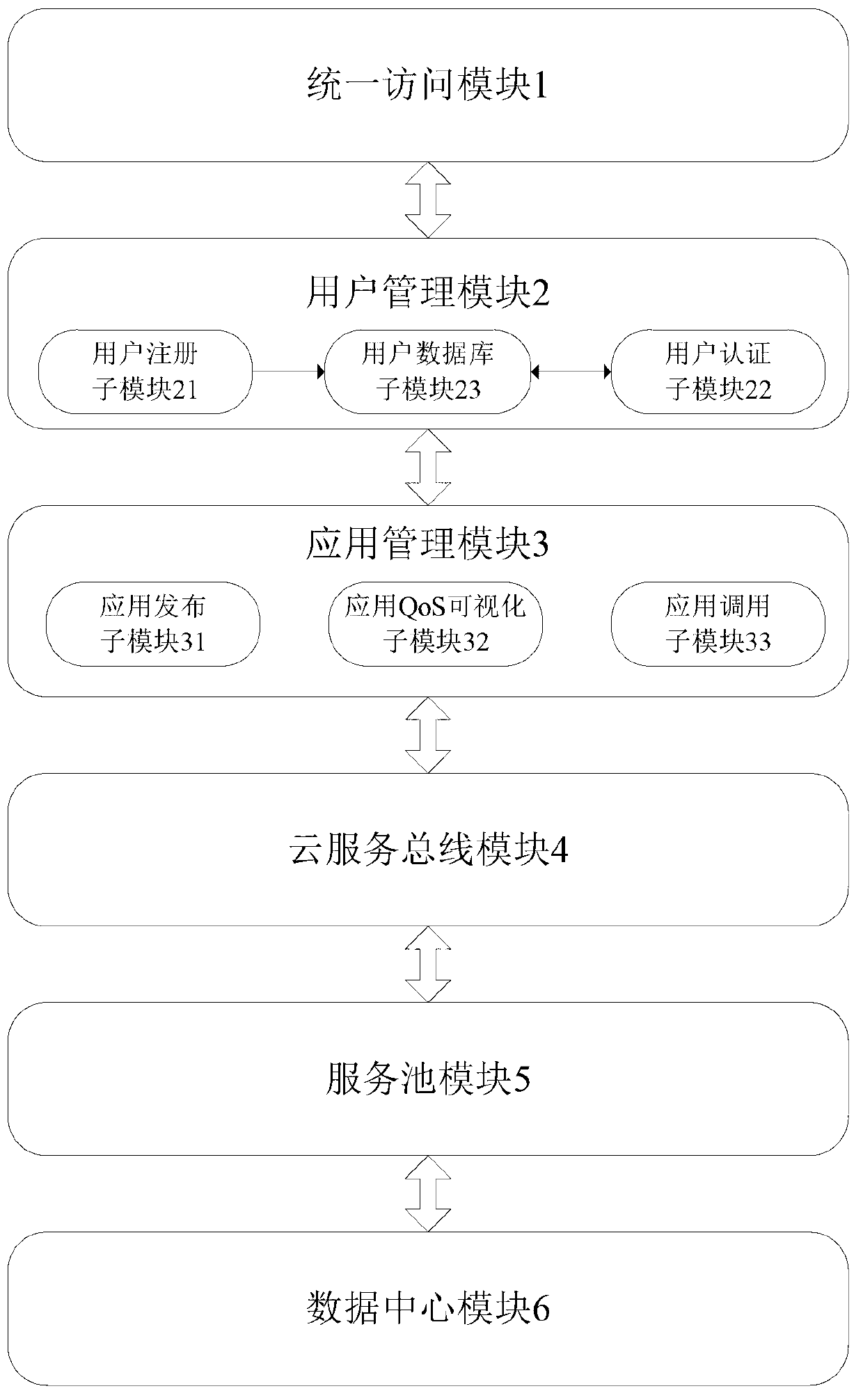
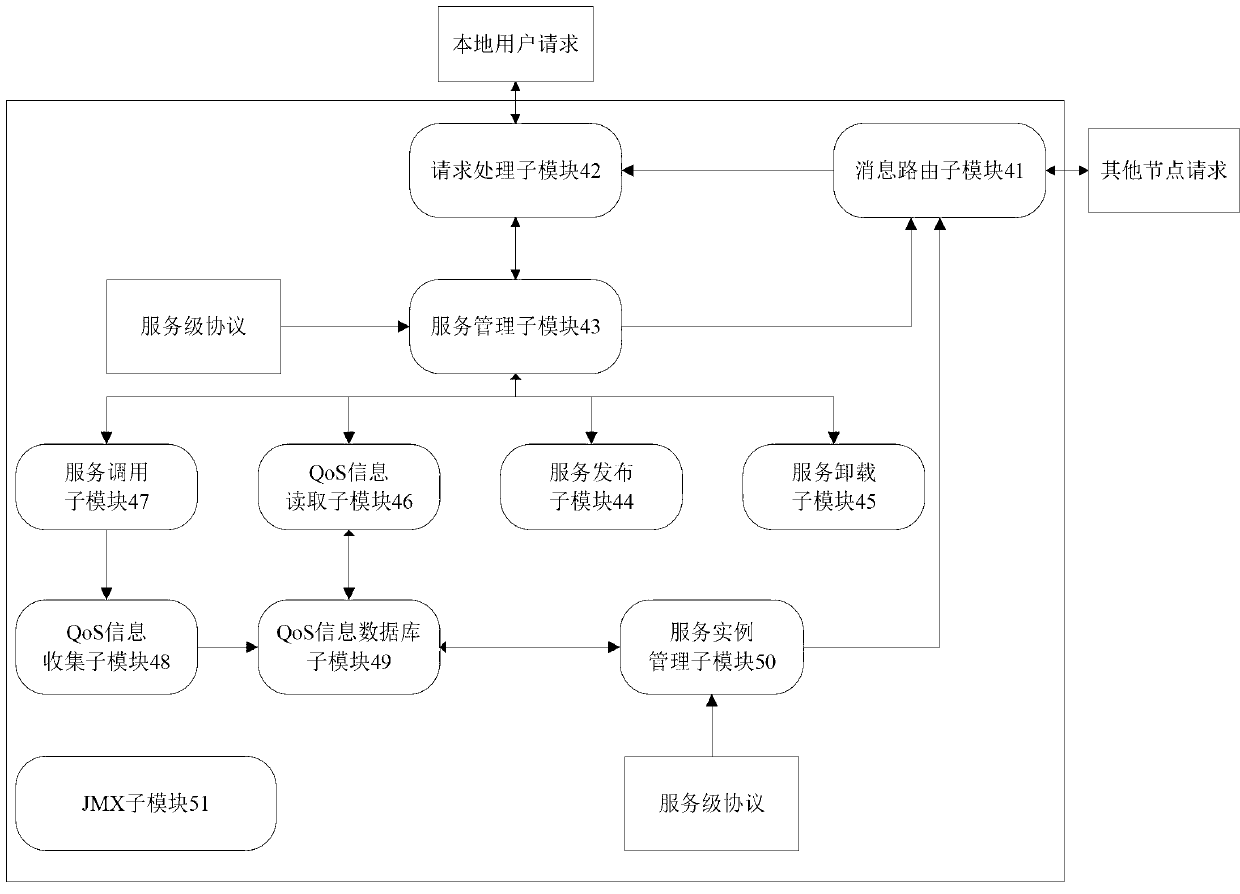
The invention discloses an application QoS (Quality of Service) management system based on cloud service bus, which comprises a user access module, a user management module, an application management module, a cloud service bus module, a service pool module and a data center module, wherein the user access module is used for providing a unified access interface for a user; the user management module is used for providing user authentication function; if the ID (identification) authentication of the user is successful, the user information is transmitted to the application management module, or, the user management module reminds the user to register; the application management module is used for providing a unified application management interface for the user according to the user information transmitted by the user management module so that the user selects application distribution, application call or application QoS visualization function; and a user request is transmitted to the cloud service bus module after the user selects corresponding function. According to user demand and application access condition, the number of service instances corresponding to the applications is dynamically increased and decreased, and the resource utilization rate is improved while the application QoS is ensured.
Owner:HUAZHONG UNIV OF SCI & TECH
Clout competing platform
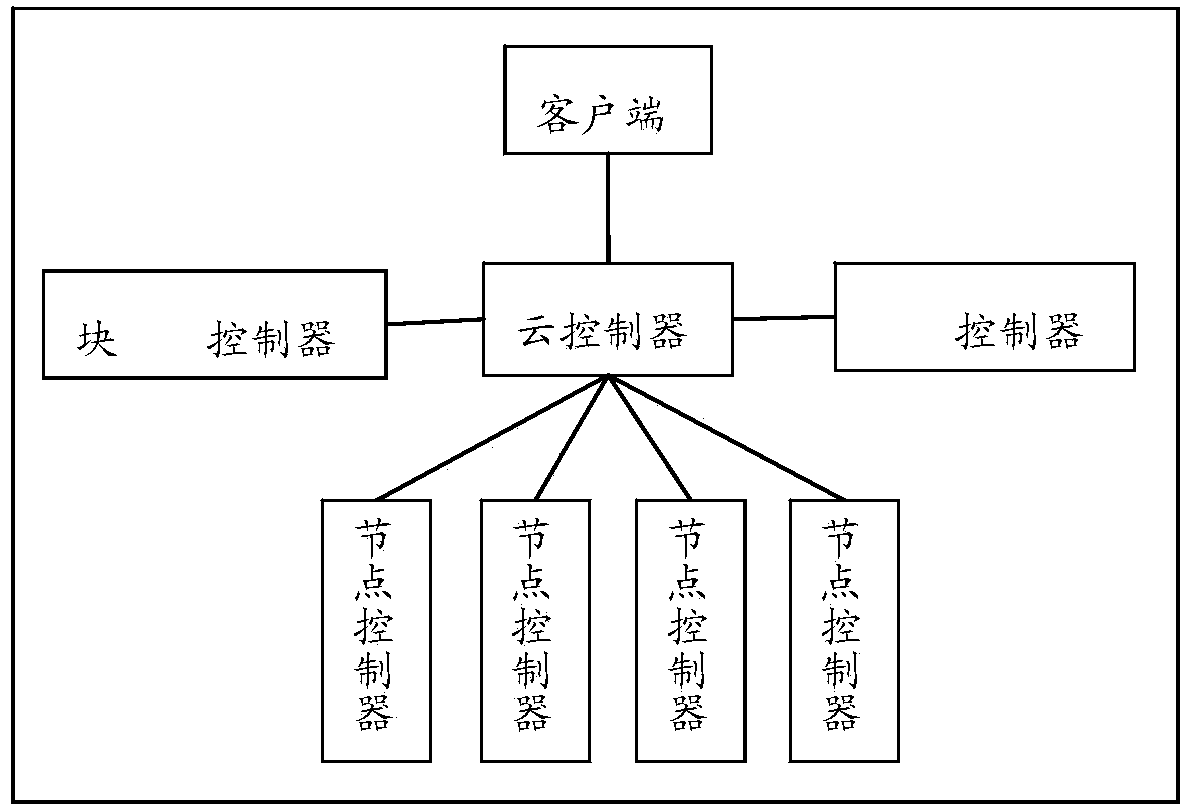
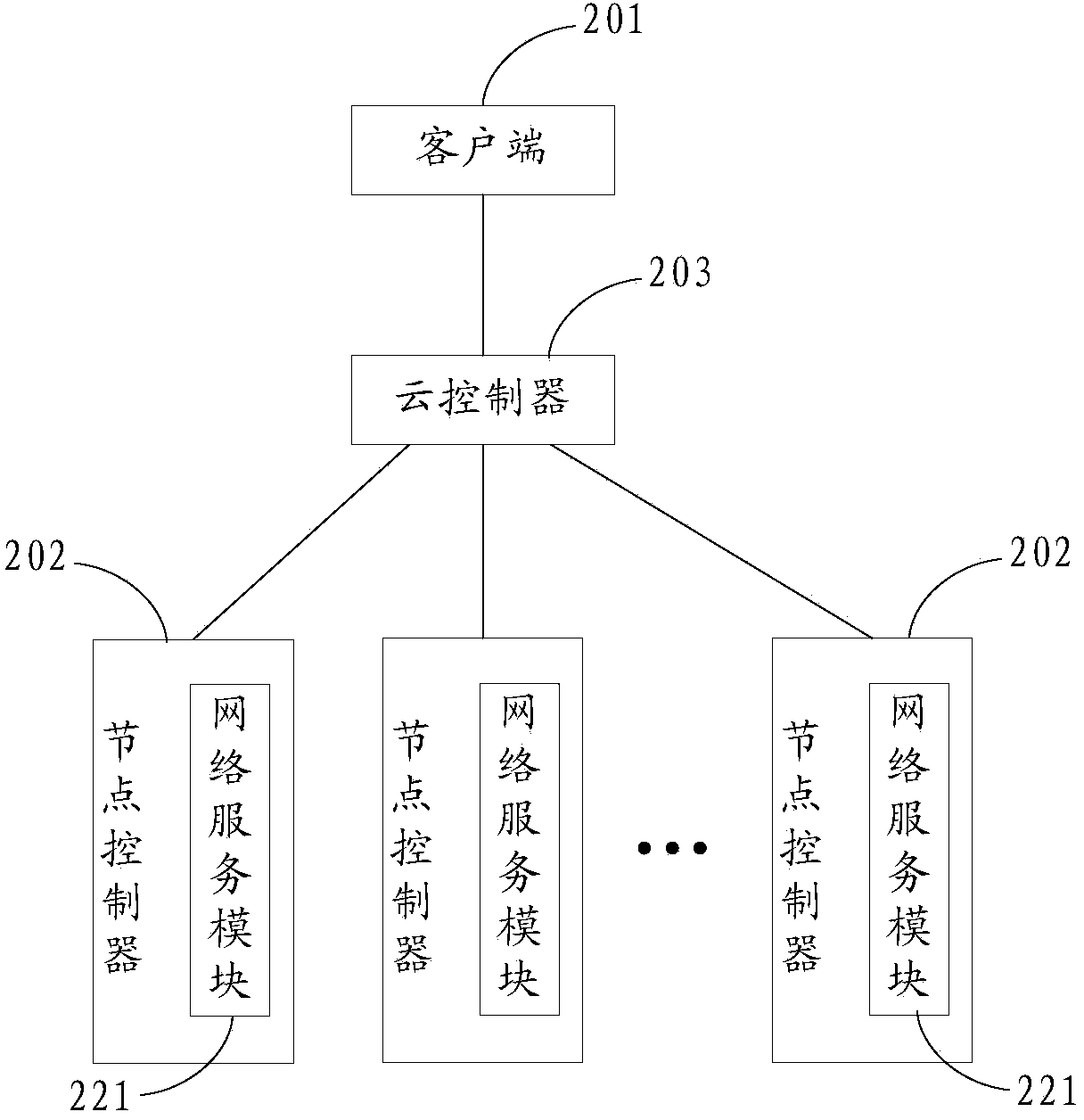
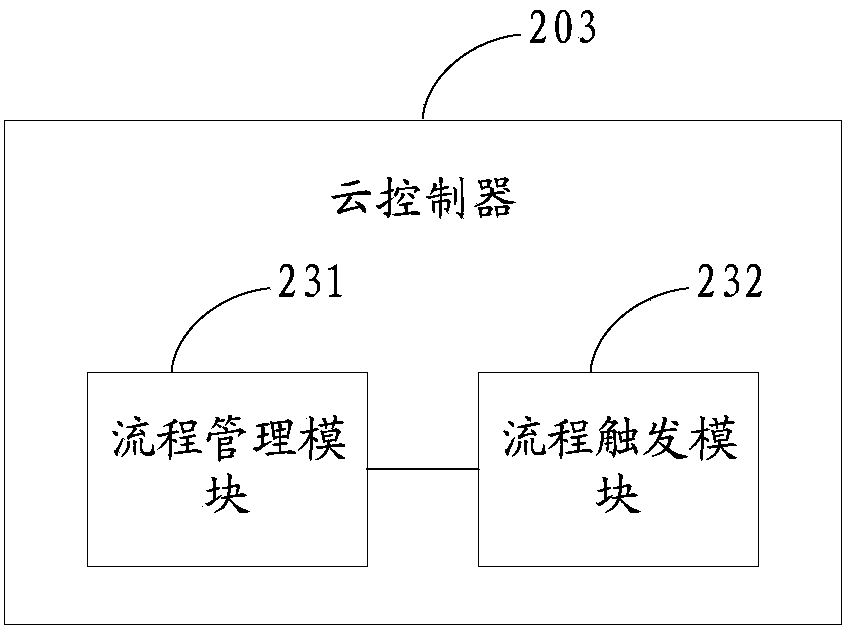
InactiveCN103458055AAvoid single point of failure problemsImprove user experienceData switching networksClient-sideSingle point
The invention discloses a cloud competing platform. The cloud competing platform comprises a client-side used for acquiring user service requests, and at least on node controller. At least on virtual machine embodiment runs on a node corresponding to each node controller. Each node controller comprises a network service module and a cloud controller, wherein the network service module is used for managing a virtual network corresponding to the virtual machine embodiment corresponding to the node controller to which the network service module belongs, and the cloud controller is respectively connected with the client-side and the node controller, is used for receiving user service request sent by the client-side, and calls the virtual machine embodiment corresponding to a corresponding node controller according to the user service requests to provide service. According to the cloud competing platform, the network service module is arranged in one node controller, and when the network service module fails, virtual embodiments on other node controllers can still conduct cloud controller calling and provide service for users, so that the problem of single-point failure in a cluster controller in the prior art is avoided, and user experience is improved.
Owner:INST OF SOFTWARE APPL TECH GUANGZHOU & CHINESE ACAD OF SCI
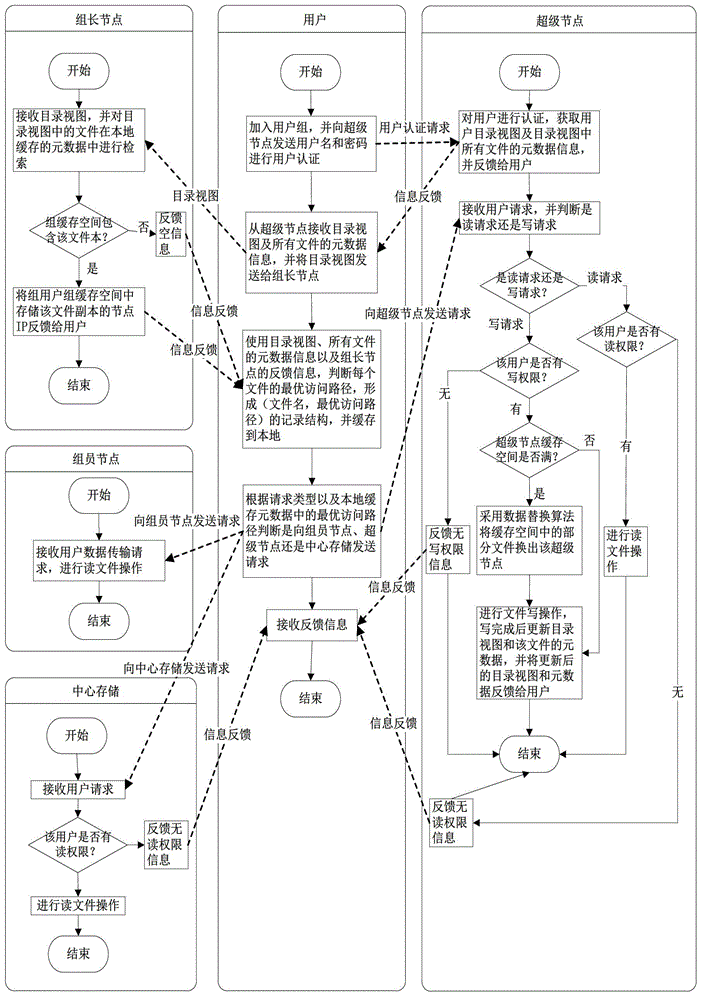
Hybrid cloud storage system and method based on multi-level cache
ActiveCN103338242AReduce network latencyImprove access bandwidthTransmissionSpecial data processing applicationsUser authenticationIp address
The invention discloses a hybrid cloud storage method based on multi-level cache. The method comprises the following steps: a user joins a user group for login according to the local area network where the user is, and sends a user name and a password for user authentication to a super node of the region where the user group is, the super node achieves authentication of the user according to the received user name and password, the user receives a catalog view returned from the super node and metadata information of all files and sends the catalog view to a group leader node of the user group, the group leader node judges whether the buffer memory space of the group contains files in the catalog view according to the received catalog view, and if yes, feeds the IP address of the node in which the files are saved in the buffer memory space of the group to the user, and the user determines the optimal access path of each file in the catalog view according to the received feedback information. The hybrid cloud storage method allows the user to access data from the user group cache and the super node layer cache which have lower network delay, thereby lowering the network delay of the user data access.
Owner:HUAZHONG UNIV OF SCI & TECH
Internet of Things data access control method and system based on block chain and IBE algorithm
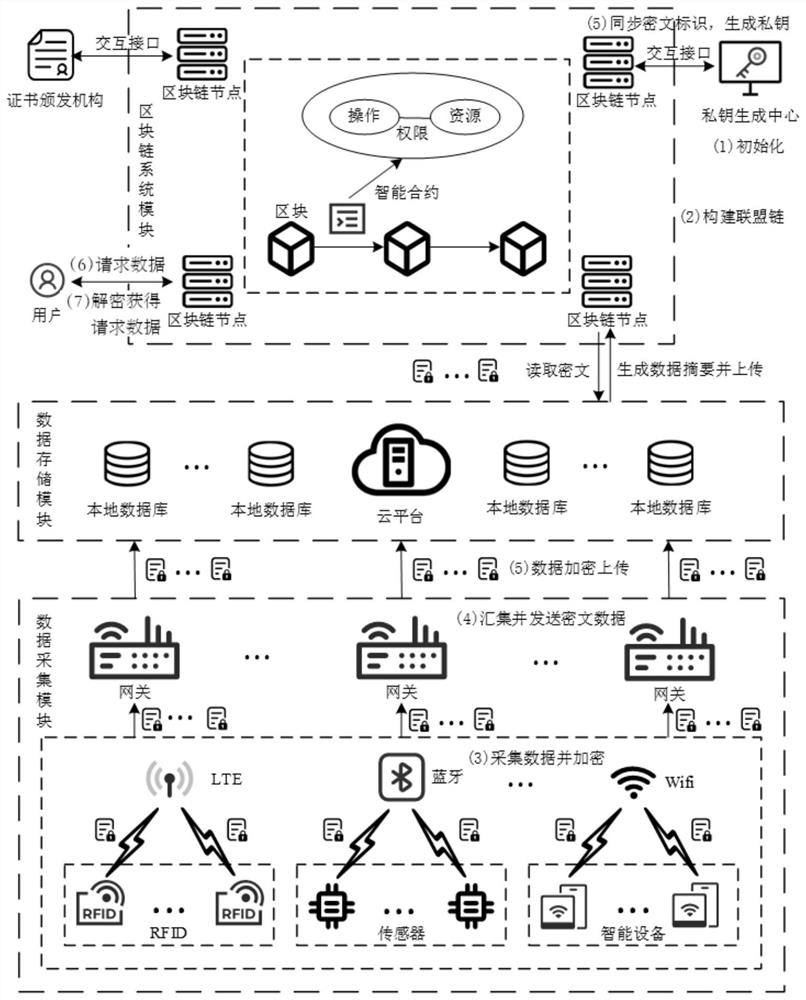
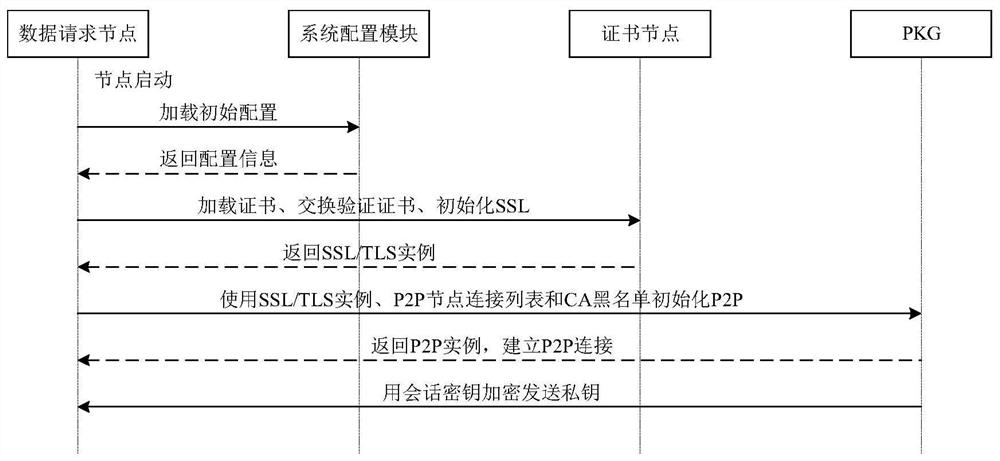
ActiveCN113783836AAvoid single point of failure problemsEffectively prevent node replication attacksKey distribution for secure communicationUser identity/authority verificationIot gatewayAlgorithm
The invention discloses an Internet of Things data access control method and system based on a block chain and an IBE algorithm. A private key generation center PKG carries out system initialization, and constructs an alliance chain; Internet of Things equipment acquires data, encrypts the data to obtain a ciphertext, and sends the ciphertext to the Internet of Things gateway; the Internet of Things gateway sends the ciphertext to an Internet of Things system cloud platform or a local database for storage; a hash value corresponding to the ciphertext is generated, and the ciphertext identifier and a key value pair corresponding to the hash value are stored in the block chain; the PKG generates a private key; a data requester initiates a data request transaction on a block chain, an access control contract deployed on the block chain verifies validity of a data request, the PKG establishes a secure connection with the data requester to share a private key after verification is passed, and the data requester decrypts encrypted data by applying an IBE decryption algorithm to obtain request data. According to the invention, safe and credible fine-grained access control in an Internet of Things environment can be realized, and confidentiality, integrity and availability are satisfied.
Owner:NANJING UNIV OF POSTS & TELECOMM
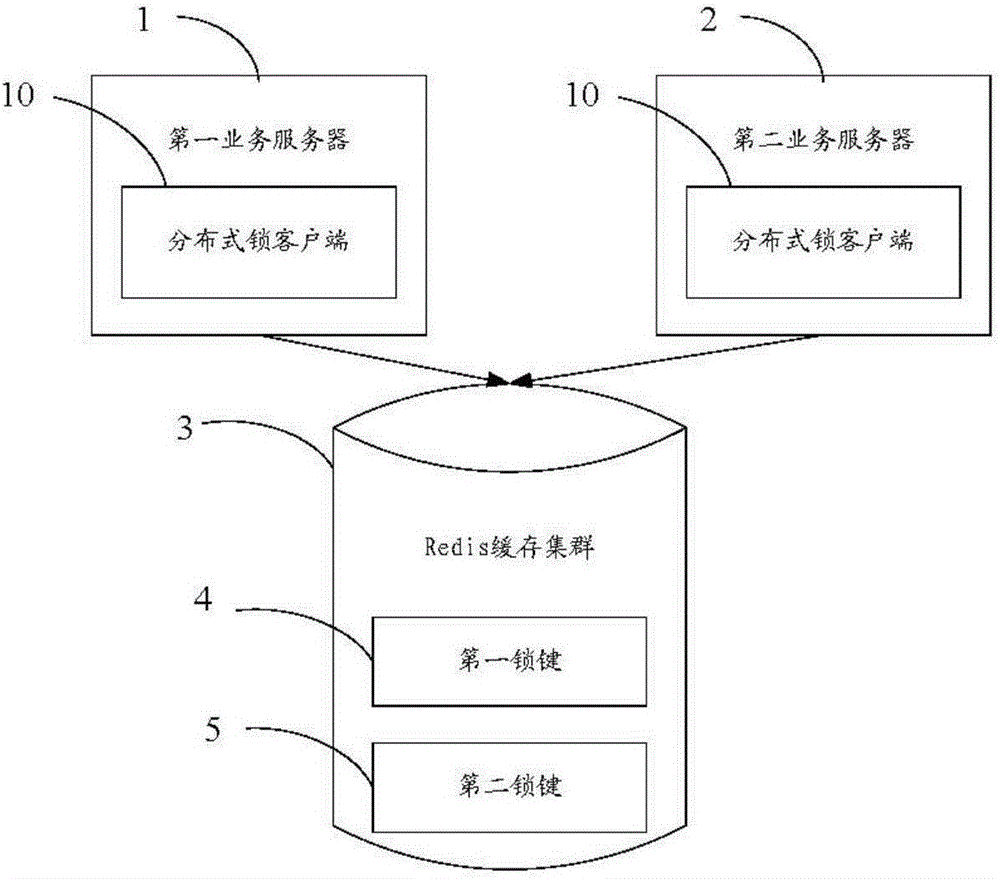
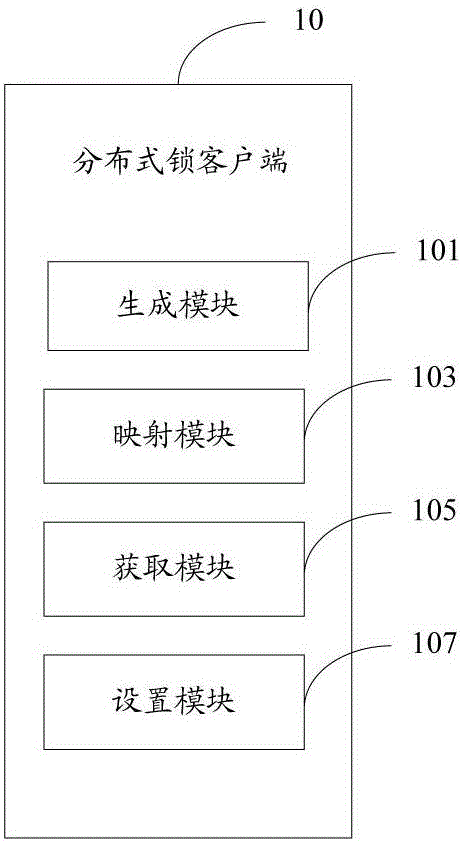
Distributed lock client and control method
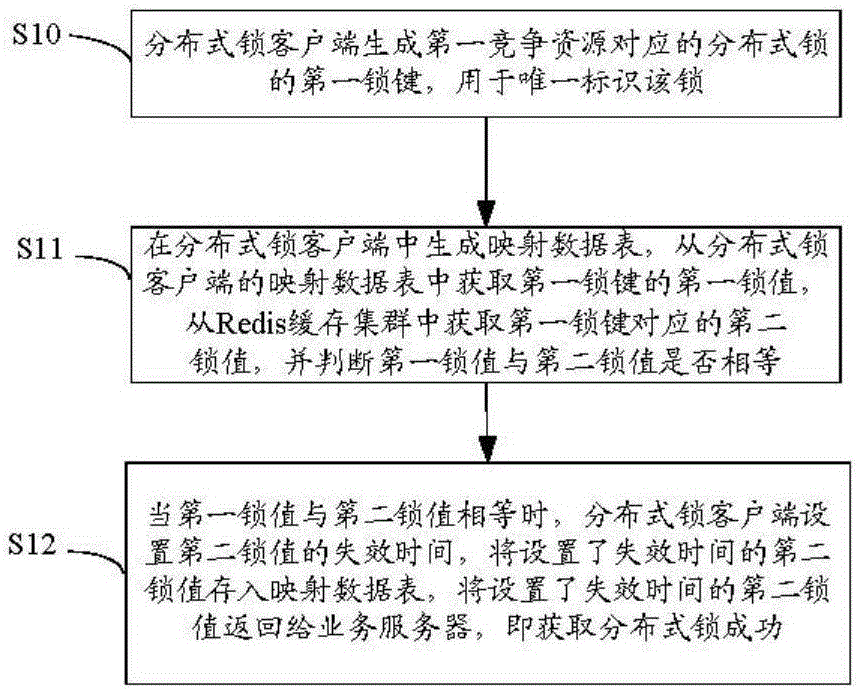
ActiveCN106354565AEasy to handleAvoid single point of failure problemsResource allocationTransmissionComputer moduleInternet business
The invention provides a distributed lock client. The distributed lock client comprises a generation module, a mapping module, an acquisition module and a setting module, wherein the generation module generates a first lock key of a distributed lock corresponding to a first competition resource, and the first lock key is used for uniquely identifying the distributed lock corresponding to the first competition resource; the mapping module generates a mapping data table, and the mapping data table comprises multiple lock keys and lock values corresponding to the multiple lock keys; the acquisition module acquires a first lock value corresponding to the first lock key from the mapping data table and a second lock value corresponding to the first lock key from a Redis buffer cluster and judging whether the first lock value is equal to the second lock value; when the first lock value is equal to the second lock value, the setting module sets the failure time of the second lock value, stores the second lock value with the failure time set in the mapping data table and returns the second lock value to a service server. The invention further provides a control method. By means of the distributed lock client and the control method, the handling performance of the distributed lock is greatly improved, and the handling capacity of the server distributed framework of the internet serve is improved.
Owner:NUBIA TECHNOLOGY CO LTD
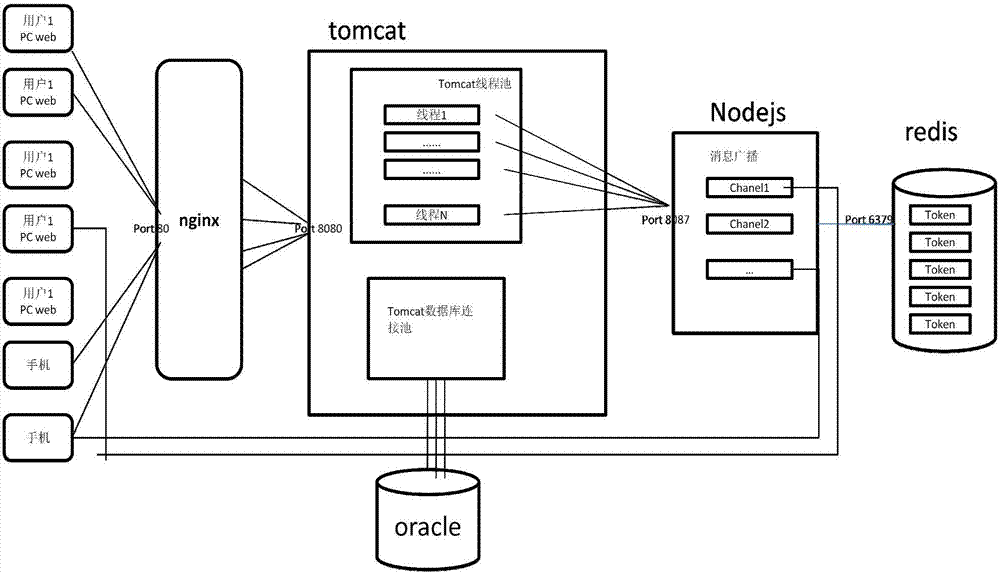
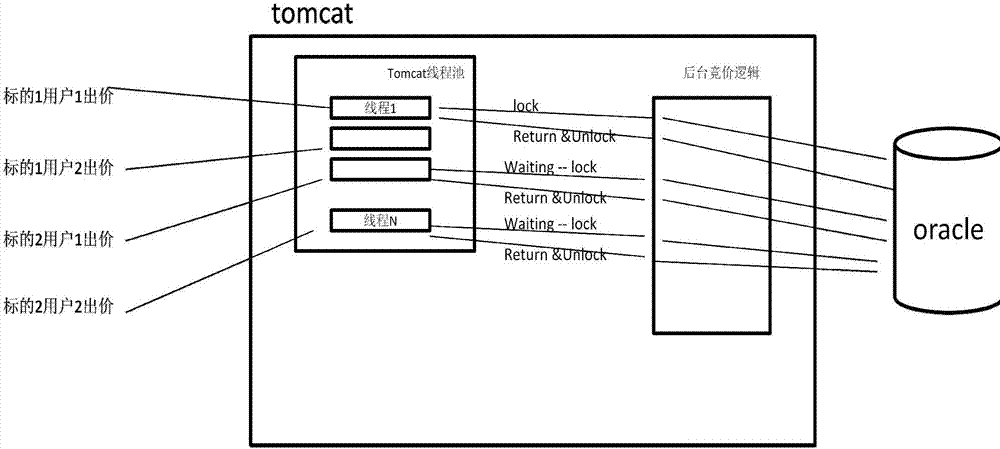
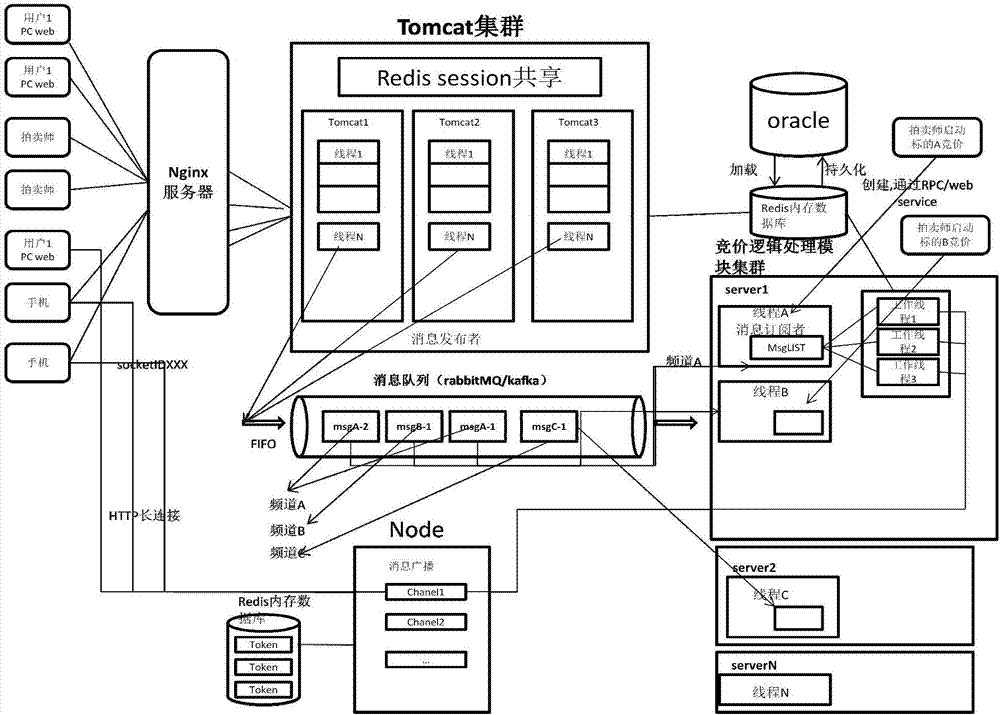
Auction bidding system based on distributed non-blocking asynchronous message processing mode and operation method thereof
ActiveCN107093138ARelieve pressureTroubleshoot out-of-sync issuesInterprogram communicationCommerceMessage queueComputer module
The invention relates to an auction bidding system based on a distributed non-blocking asynchronous message processing mode and an operation method thereof. The auction bidding system comprises an nginx server, a node server, a Tomcat cluster, a message queue, a bidding logic processing module cluster, and an Oracle database. A user initiates a request through a user terminal, and sends the request to the Tomcat cluster through the nginx server. The Tomcat cluster converts the request into a message, saves the message to the message queue, and gives a feedback to the user for response, wherein the feedback is used to remind the user that the request has been received and is being processed. The bidding logic processing module cluster processes the message in the message queue, and notifies the user of the processing result through the node server.
Owner:山东佳联电子商务有限公司
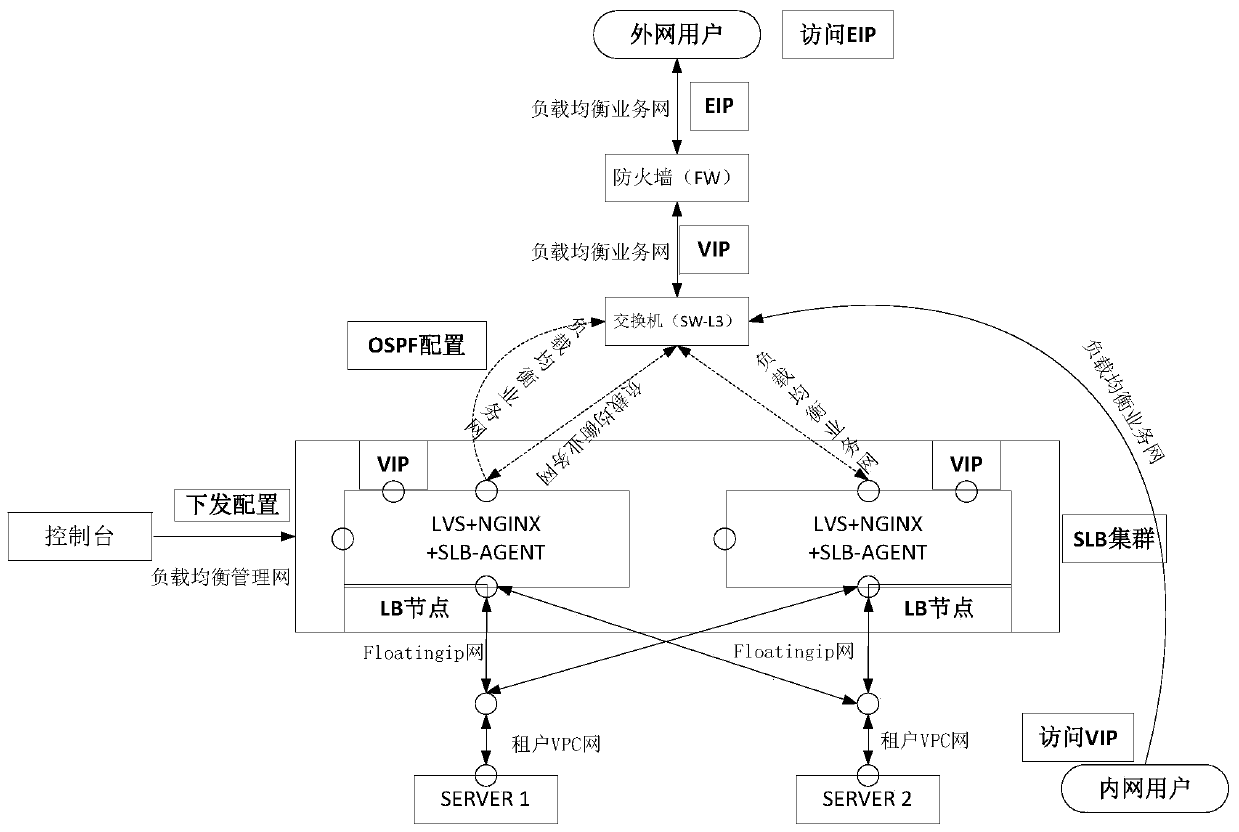
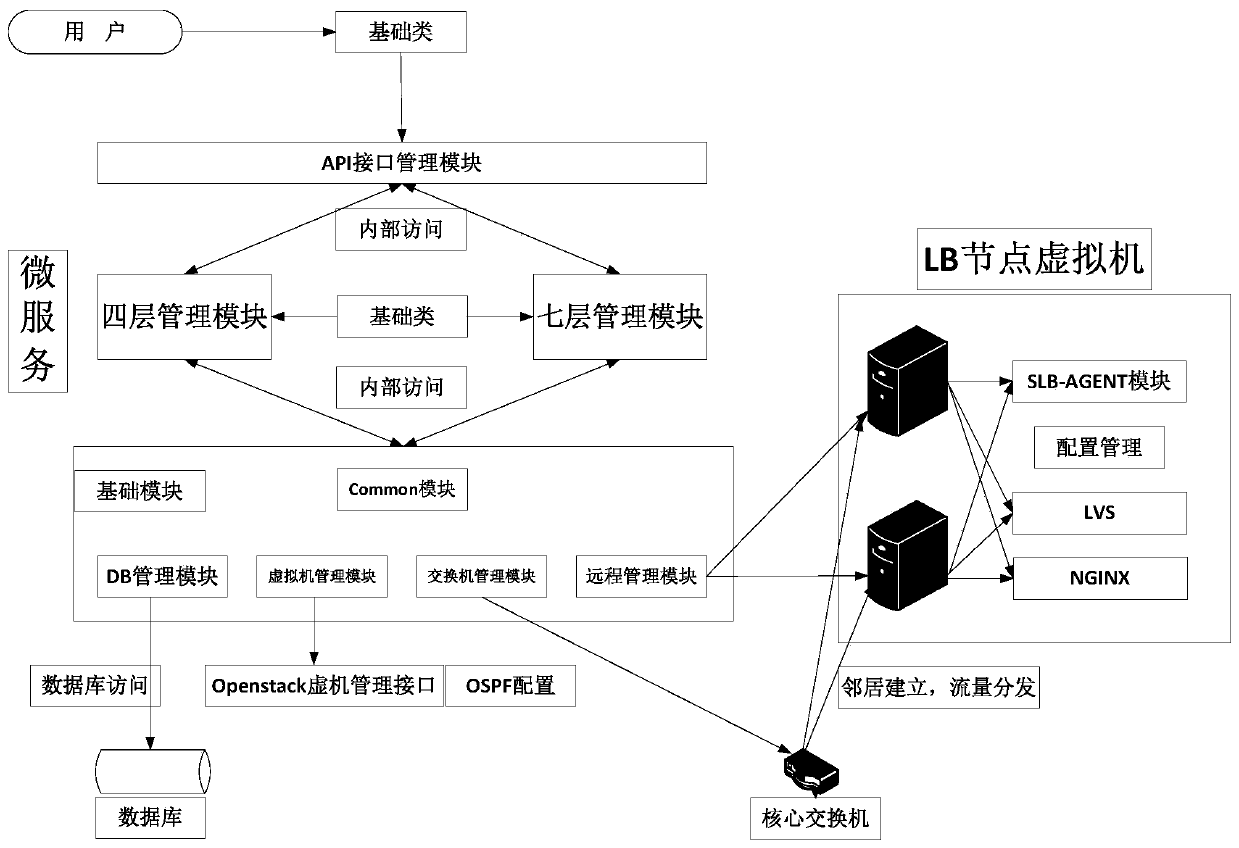
Multi-live load balancing method and system applied to openstack cloud platform
PendingCN111274027AImplement multi-active modeReduce demandResource allocationSoftware simulation/interpretation/emulationResource utilizationSingle point of failure
The invention discloses a multi-live load balancing method and system applied to an openstack cloud platform, and belongs to the field of cloud computing pass. The technical problem to be solved by the invention is how to meet the requirements of four-layer and seven-layer flow load balancing, avoide a single-point fault of the load balancing node, achieve the maximum utilization rate of the loadbalancing node performance, and improve the resource utilization rate of the physical server on the cloud platform; the adopted technical scheme is as follows: the method comprises the following steps: open-source LVS and NGINX are used for carrying out load balancing on four-layer flow and seven-layer flow respectively; through cooperation of an open source quagga virtual router of an ospf protocol and a physical switch supporting the ospf protocol, multi-path selection is carried out; a multi-active mode is realized, and communication with a virtual machine in a tenant vpc is performed through an external network shared by tenants on an openstack platform, so that cross-vpc load balancing is realized. The system adopts a micro-service software architecture and comprises a UI layer, a back-end micro-service layer, an atomic micro-service layer and a far-end SLB-AGENT layer.
Owner:山东汇贸电子口岸有限公司
A system management method and apparatus
ActiveCN109471770AAvoid single point of failure problemsReal-time monitoring of computing nodesHardware monitoringSystems managementComplex programmable logic device
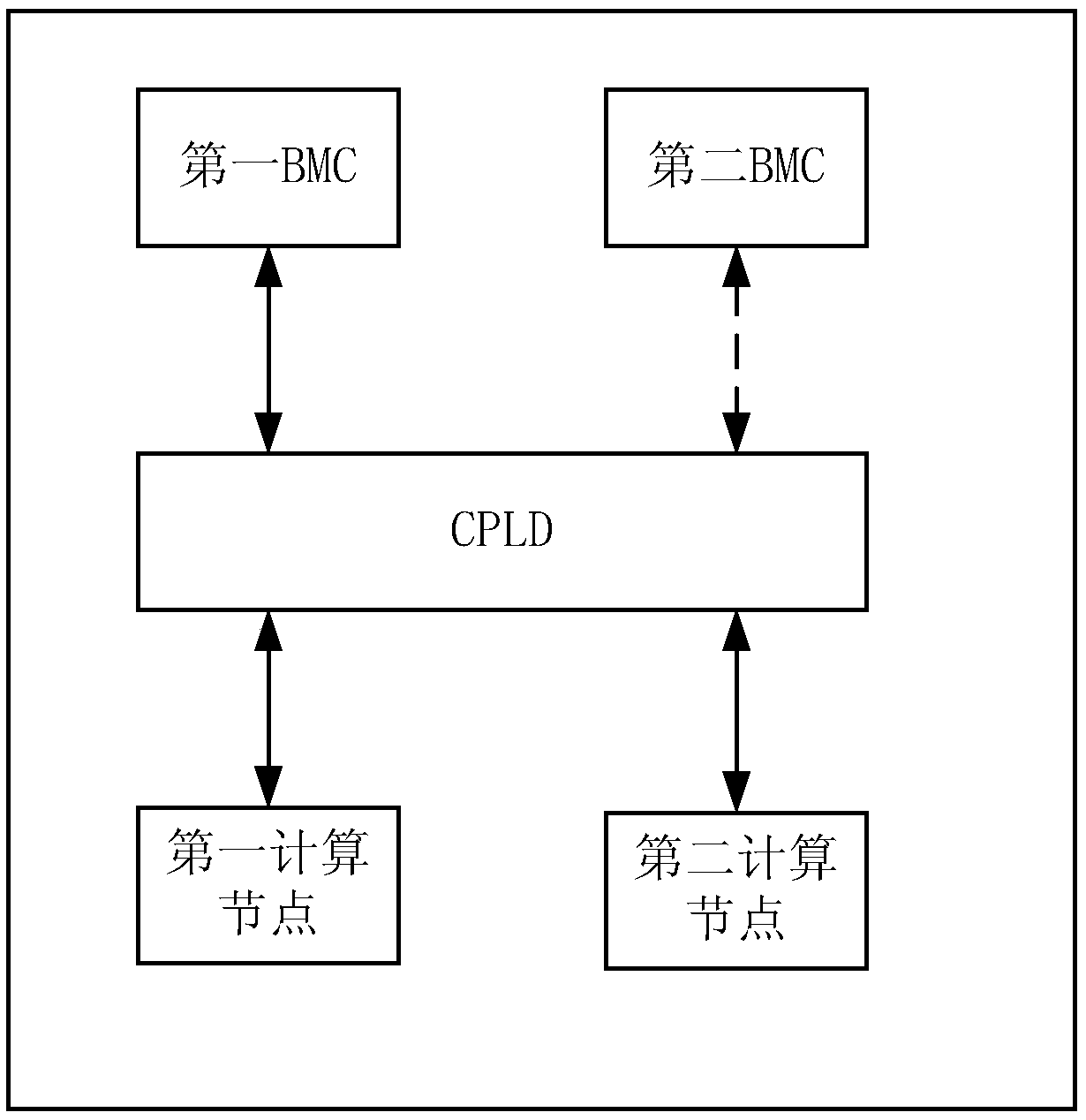
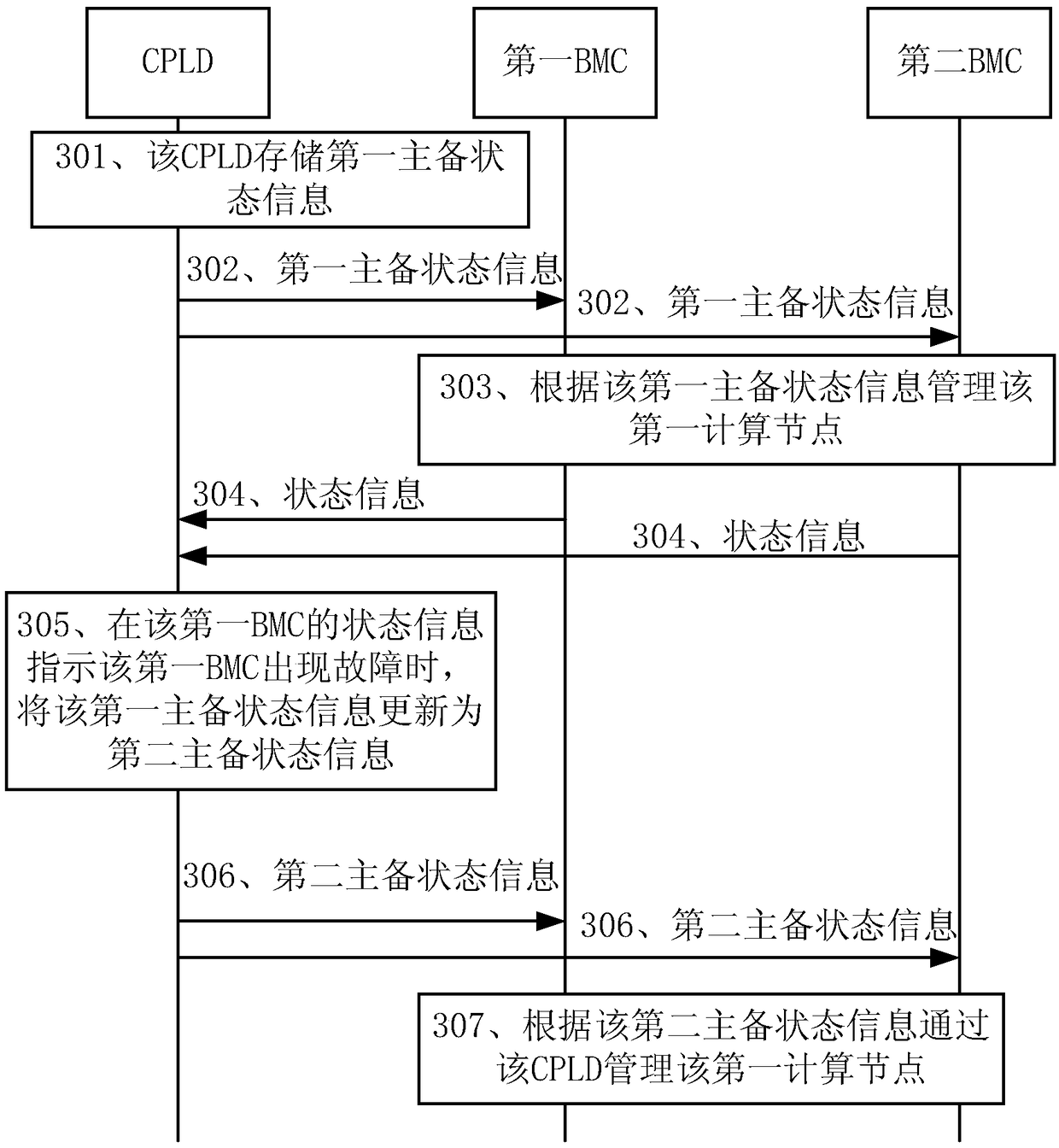
DETAILED DESCRIPTION embodiment of that present application disclose a system management method, The server includes a complex programmable logic device (CPLD), a first substrate management controller(BMC), a second BMC and a first computing node. The CPLD stores first master / backup state information indicating that the first BMC is a master BMC and the second BMC is a backup BMC. The first BMC and the second BMC manage a first computing node according to the first master / standby state information; The CPLD monitors the first BMC and the second BMC in real time; When the first BMC is abnormal, the CPLD updates the first master / standby state information to the second master / standby state information, the second master / standby state information is used to indicate that the first BMC is a backup BMC and the second BMC is a master BMC; The first BMC and the second BMC manage the first computing node according to the second master / standby state information. As that serv arranges the primary and the standby BMC, the management compute node of the standby BMC can be switched immediately when the primary BMC is abnormal, and the problem of a single point of failure of the BMC is solved.
Owner:XFUSION DIGITAL TECH CO LTD
Method, device and system for having access to information through metadata
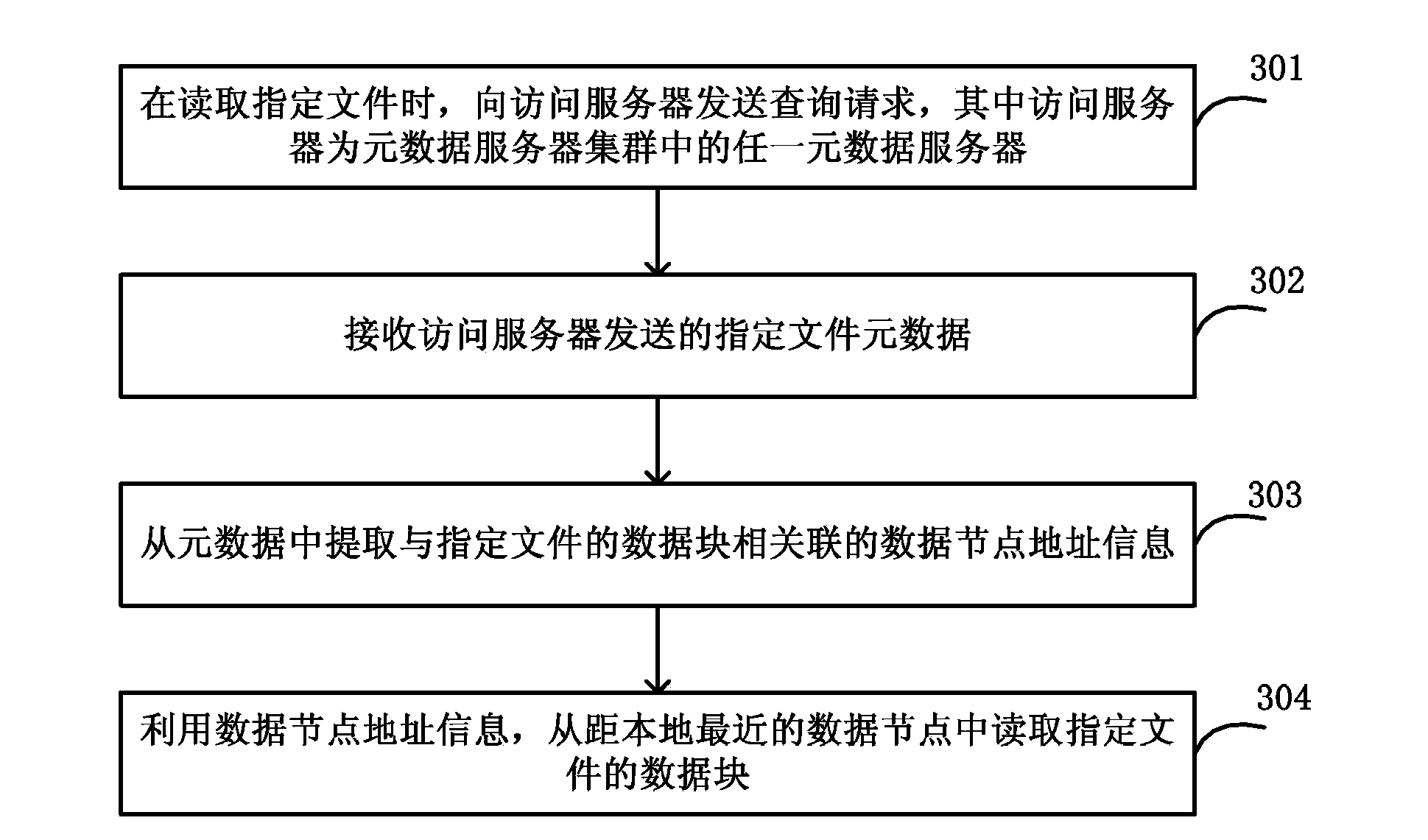
InactiveCN104144150AAvoid performance bottlenecksAvoid single point of failure problemsData switching networksSpecial data processing applicationsDistributed File SystemData node
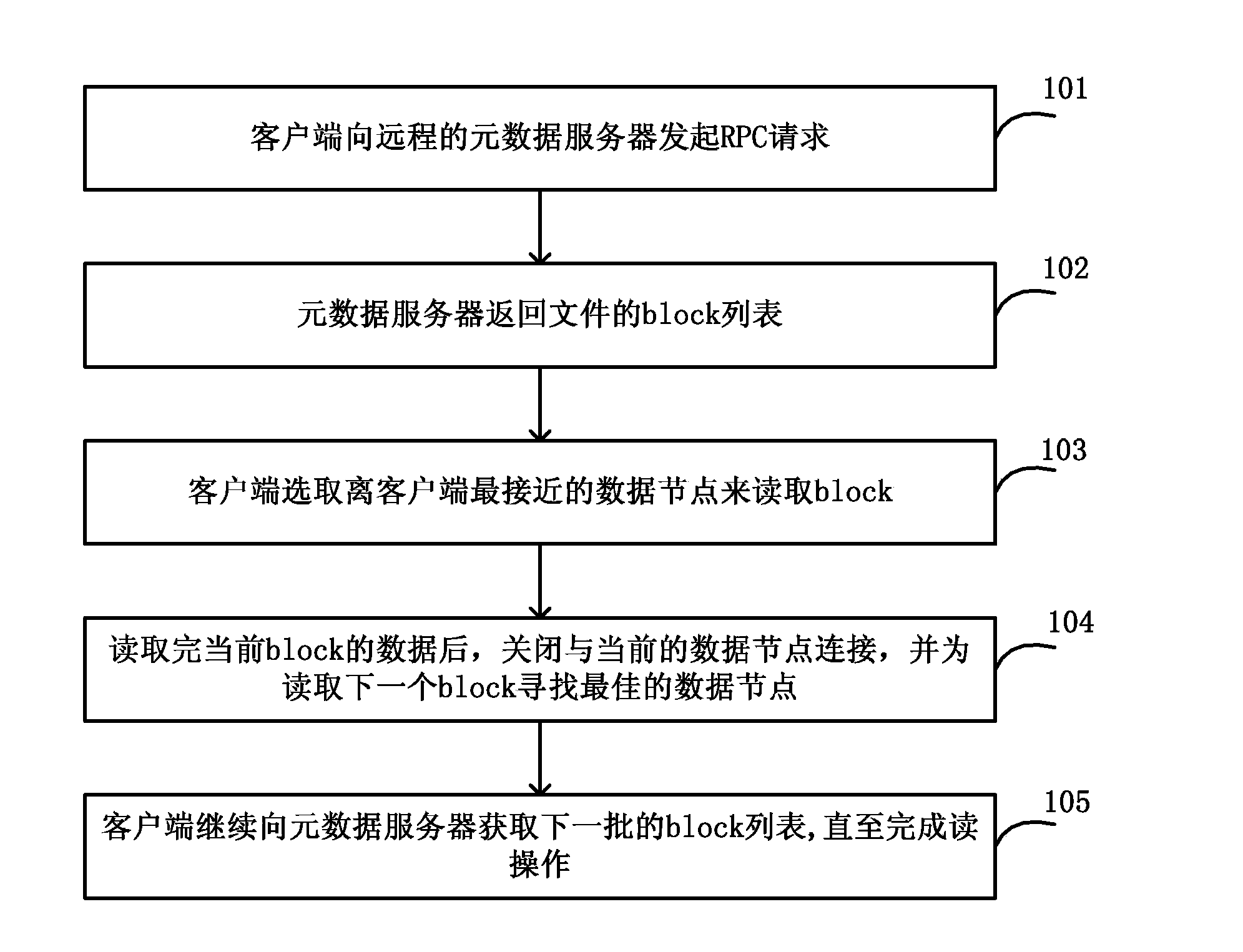
The invention discloses a method, device and system for having access to information through metadata. The method for having access to information through the metadata comprises the steps that an inquiry request is sent to an access server, wherein the access server is any metadata server in a metadata server cluster; after the access server receives the inquiry request, whether metadata of an assigned file exist locally or not is judged, if the metadata of the assigned file exist locally, the metadata of the assigned file are obtained from the local, and if not, the metadata of the assigned file are obtained from a corresponding metadata server with the assigned file metadata; the assigned file metadata sent by the access server are obtained, and data blocks of the assigned file are read from a data node closest to the local according to the data node address information of the metadata. The single metadata server is expanded into the metadata server cluster, and therefore the single-point fault problem is effectively avoided, and the performance bottleneck of existing distributed file system metadata servers is broken.
Owner:CHINA TELECOM CORP LTD
Network flow control method and computing node
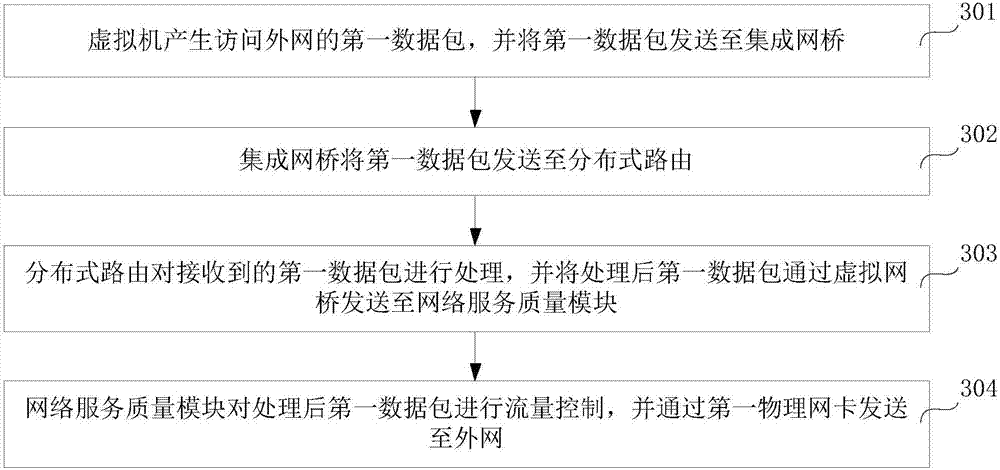
ActiveCN107547439AEasy to controlAvoid single point of failure problemsNetworks interconnectionTraffic capacitySingle point of failure
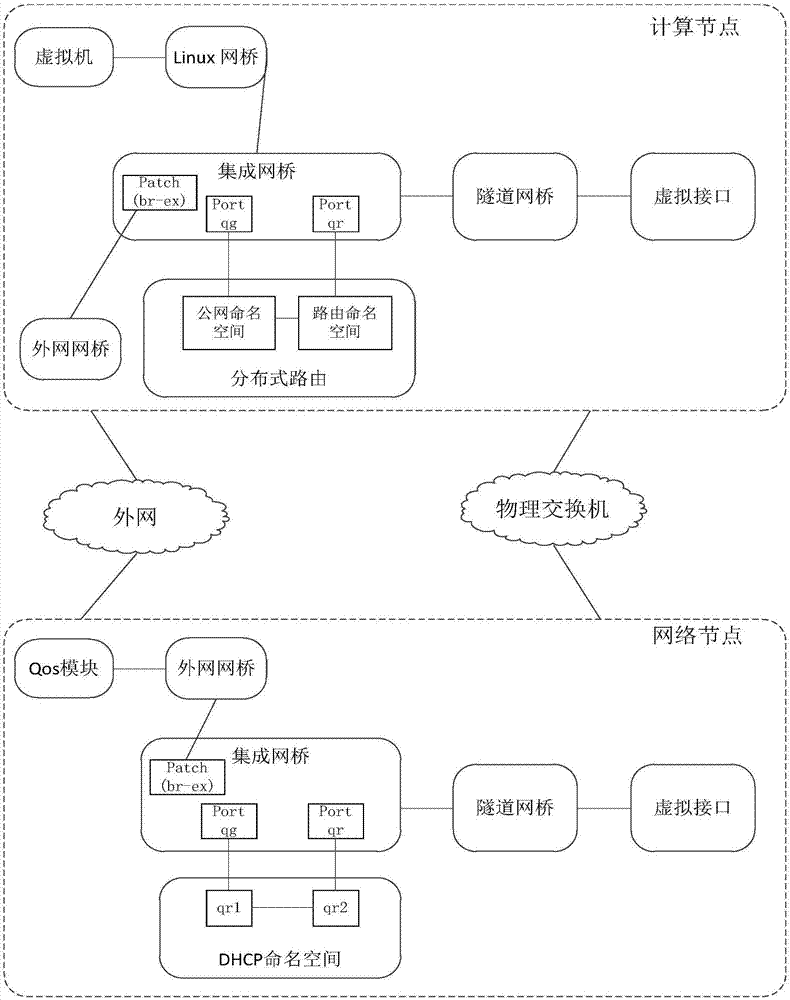
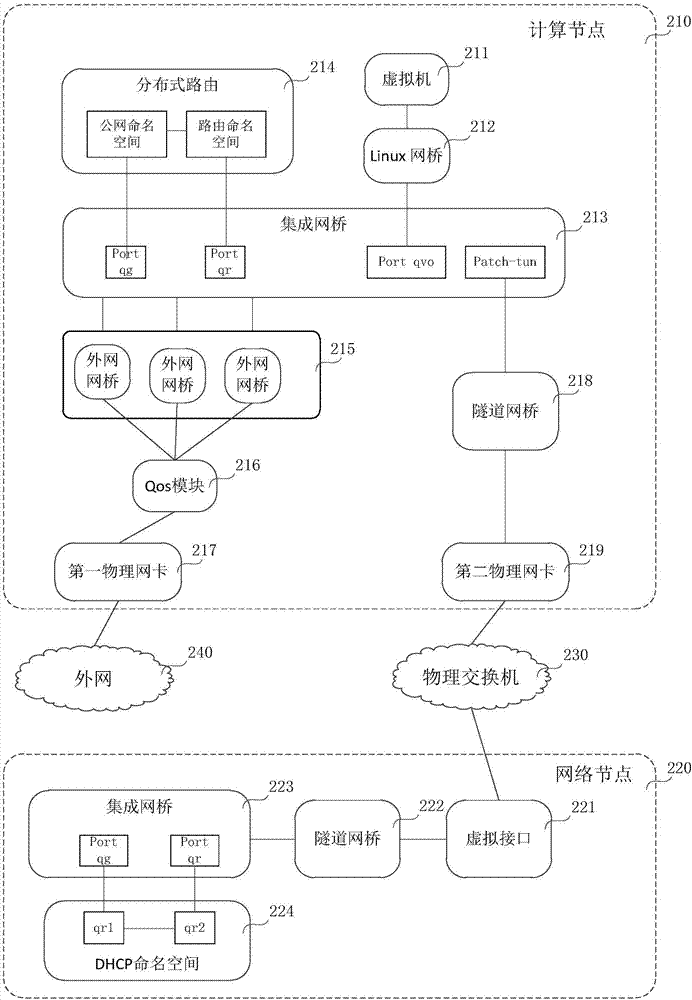
The embodiment of the invention relates to the field of cloud computing network virtualization technology and particularly relates to a network flow control method and a computing node. A virtual machine generates a first data packet accessing an external network and sends the first data packet to an integrated network bridge; the integrated network bridge sends the first data packet to a distributed routing; the distributed routing processes the received first data packet and sends the processed first data packet to a network service quality module via an external network bridge; and the network service quality module performs flow control on the processed first data packet and sends the processed first data packet to the external network via a first physical network card. Therefore, thecomputing node can control the network flow of the virtual machine, and the single point failure problem caused by the over high load of the network node can also be avoided. The delay of the first data packet to arrive at the external network from the virtual machine can also be shortened, and thus the network service quality of the virtual machine is ensured.
Owner:CHINA UNIONPAY
Method and device for implementing distributed lock based on a network, and medium
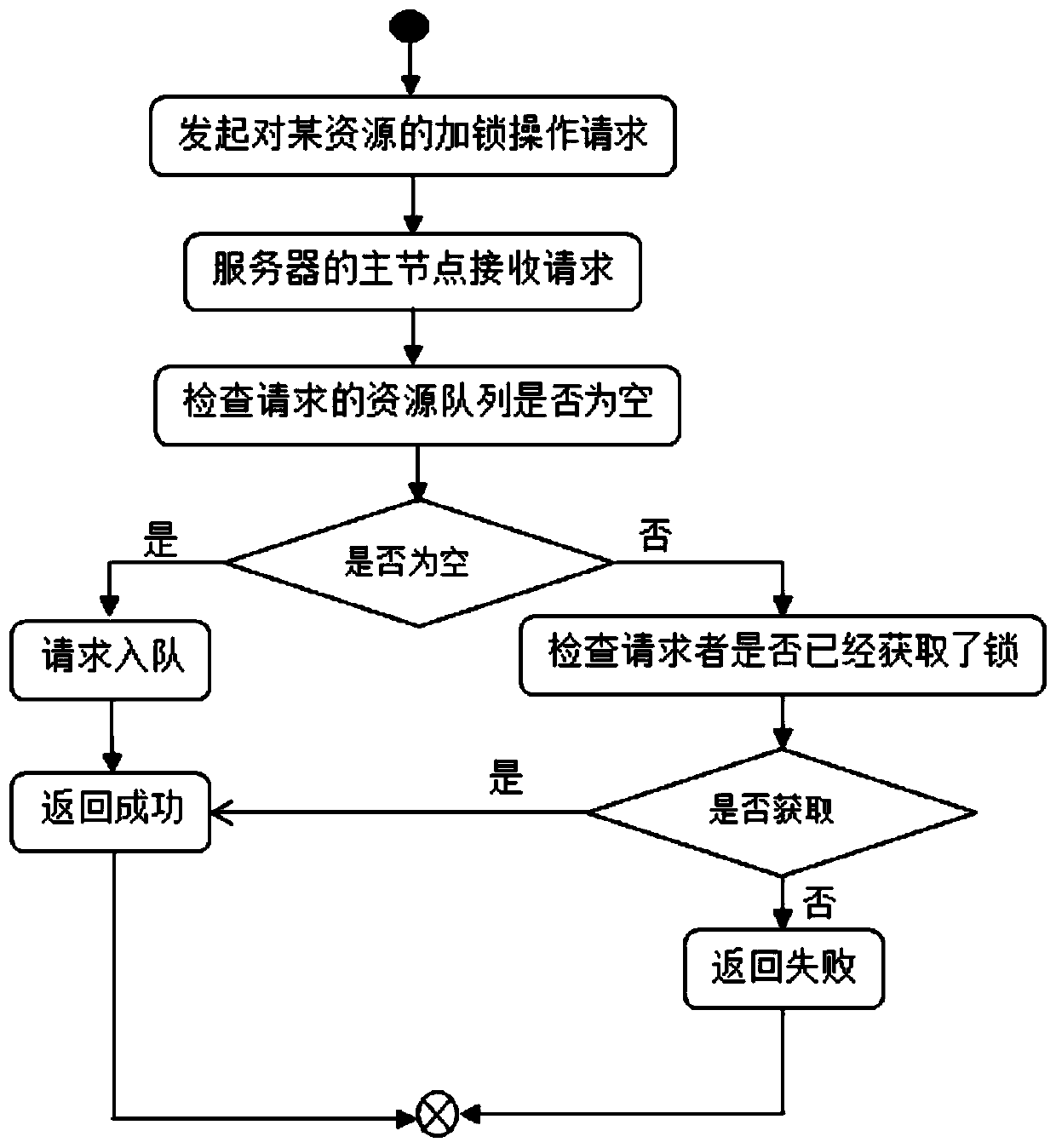
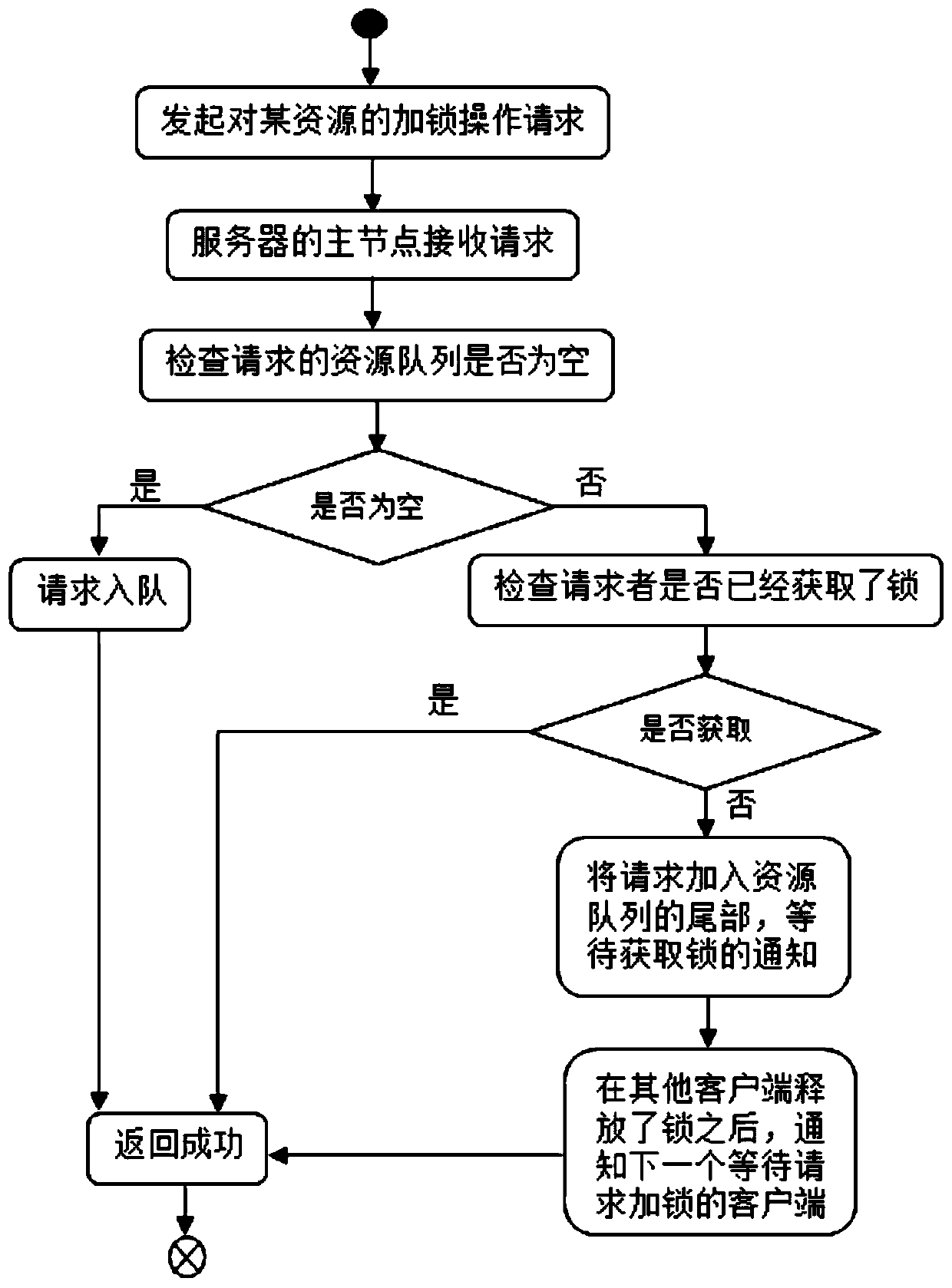
InactiveCN109753364AEffective accessSolve the reentrancy problemProgram synchronisationInterprogram communicationClient-sideThird party
The invention provides a method and a device for implementing a distributed lock based on a network, and a medium. The method comprises the following steps: firstly, receiving a locking operation request of a distributed lock sent by at least one client, adding at least one client into a client queue for sequencing, sequencing on the basis of time or priority, then obtaining a current client whichfirstly performs a locking operation request, and judging whether the locking request of the current client is a synchronous locking request or an asynchronous locking request; different locking strategies are used according to different locking requests, so that the locking request corresponding to the current client side meeting the conditions obtains the distributed lock and accesses the resource information, and if the conditions are not met, locking failure information is returned. According to the content of the invention, effective access of shared resources is realized, and the problem of reentrancy of the distributed lock, the problem of single-point failure of the distributed lock service and dependence of the distributed lock service on third-party software are solved.
Owner:北京明朝万达科技股份有限公司
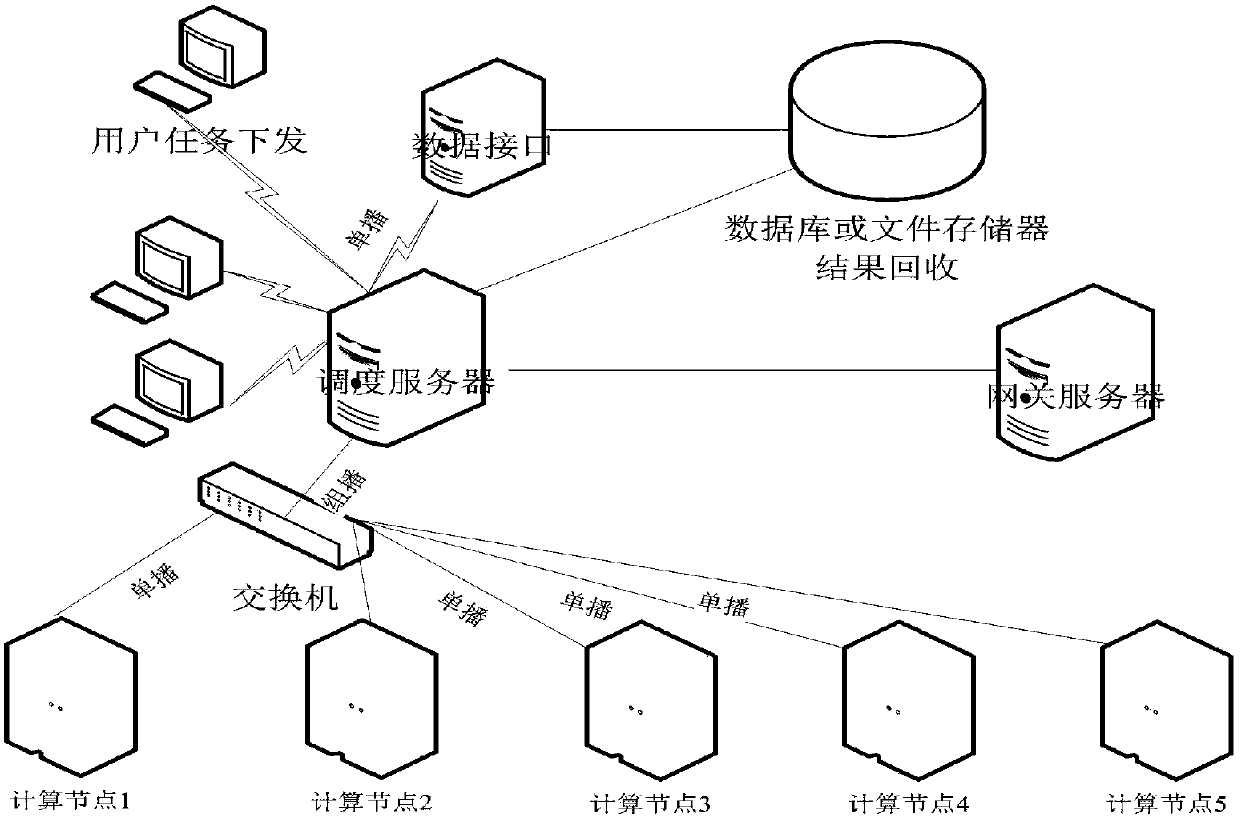
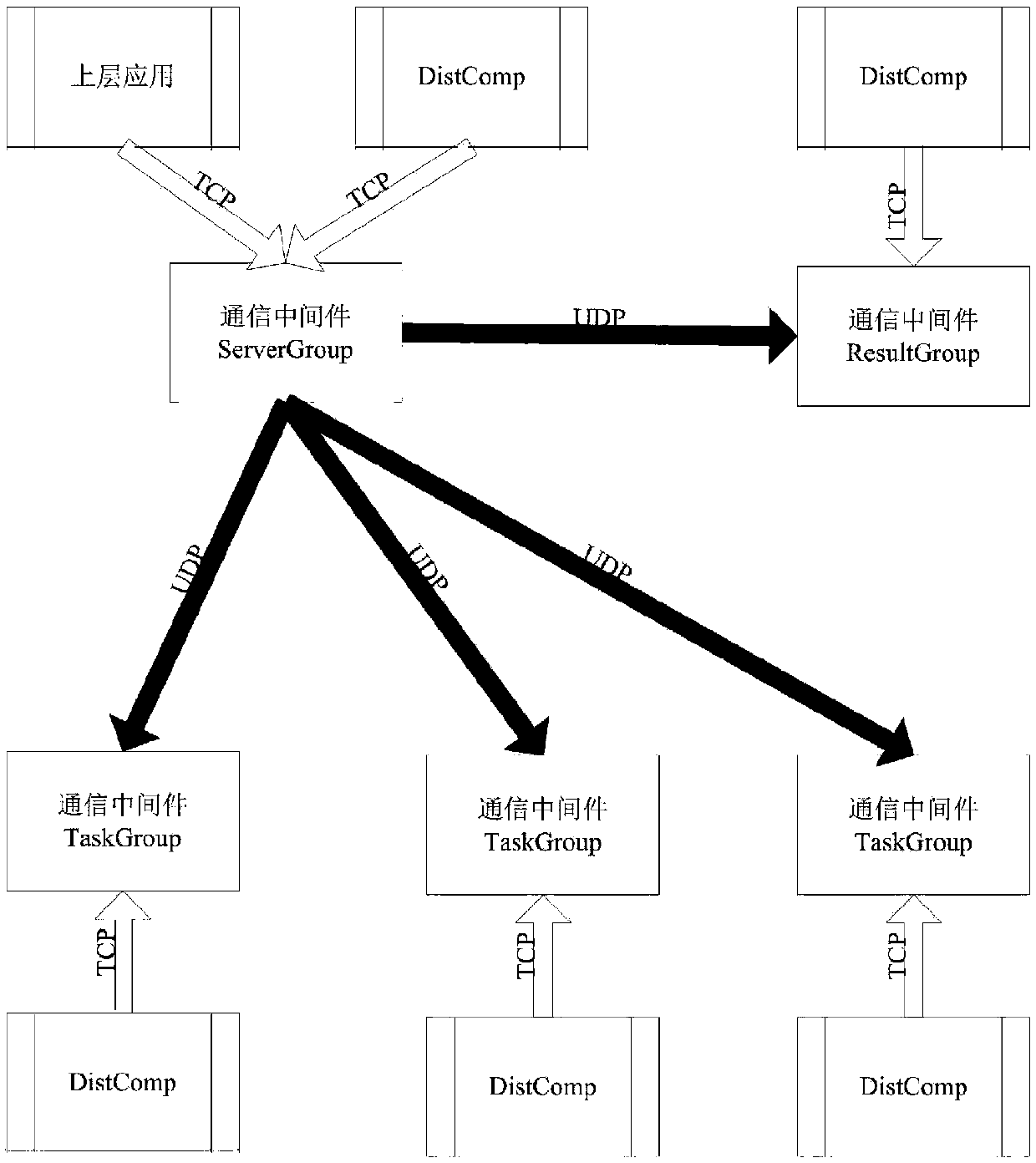
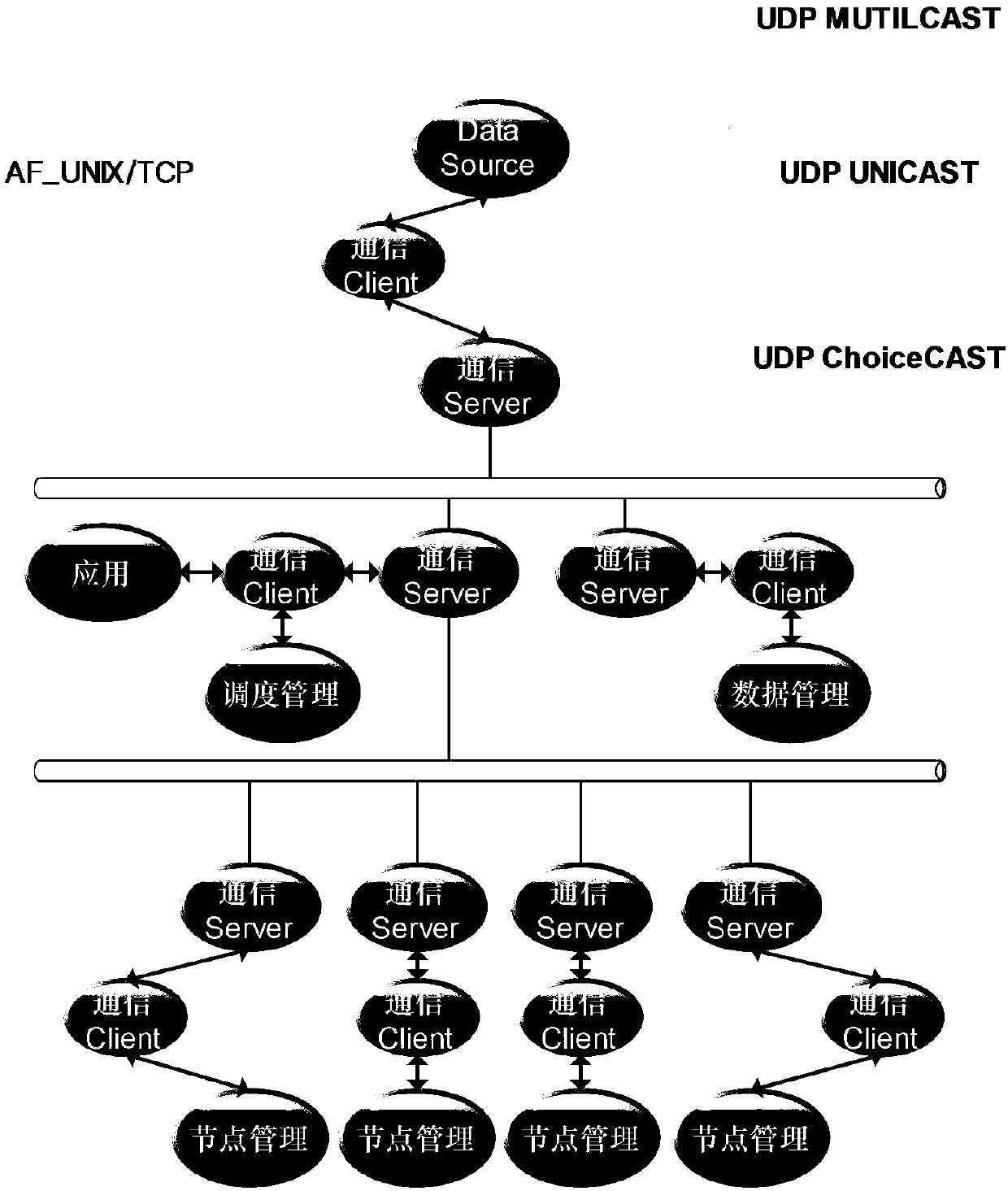
A distributed parallel computing platform based on online simulation and a method thereof
PendingCN109815002AGood effectStrong business guaranteeProgram initiation/switchingResource allocationService guaranteeElectric power system
The invention relates to a distributed parallel computing platform based on online simulation and a method thereof. The distributed parallel computing platform is composed of a plurality of high-performance servers and is divided into nodes with different functions, each type of nodes complete different functions, and the whole online simulation distributed parallel computing platform is composedof a gateway server, a scheduling server, a data server and a computing server. The platform adopts a TCP and a UDP communication mode based on reliable protocol communication to realize data and filetransmission in the whole platform, and adopts a multicast technology to complete command and file issuing among node servers. According to the invention, a distributed parallel computing platform established by adopting a multicast technology and a multi-core technology provides powerful service guarantee for the periodic computation of the online mode of the power system, and the system is stable in operation.
Owner:CHINA ELECTRIC POWER RES INST +2
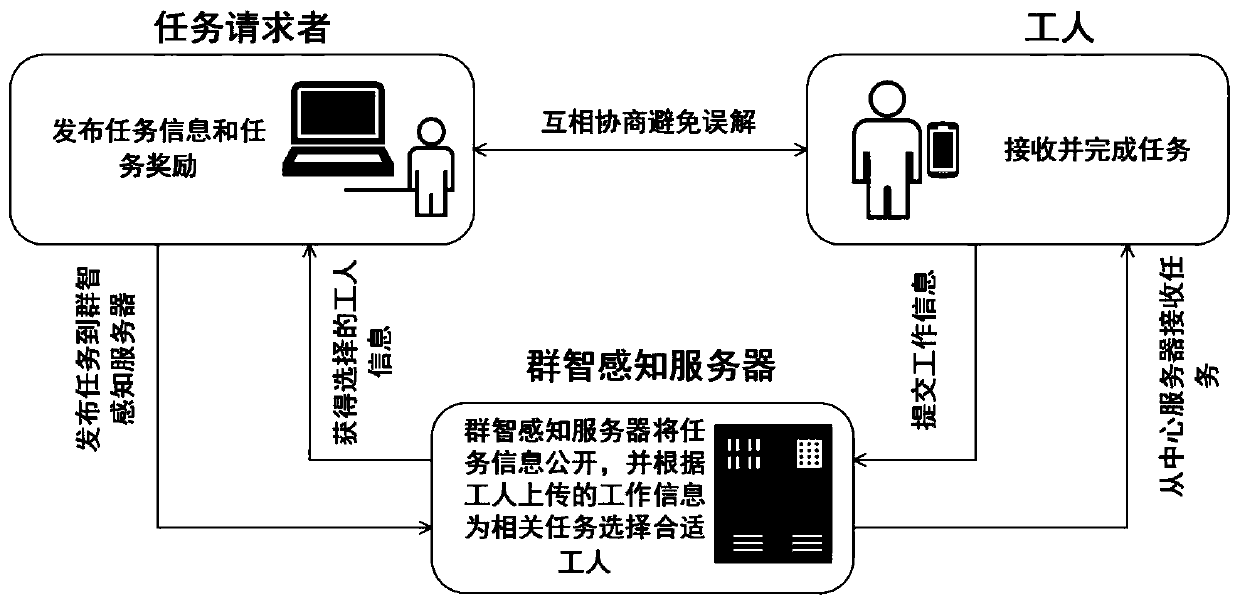
Method and system for mobile crowd sensing, server and storage medium
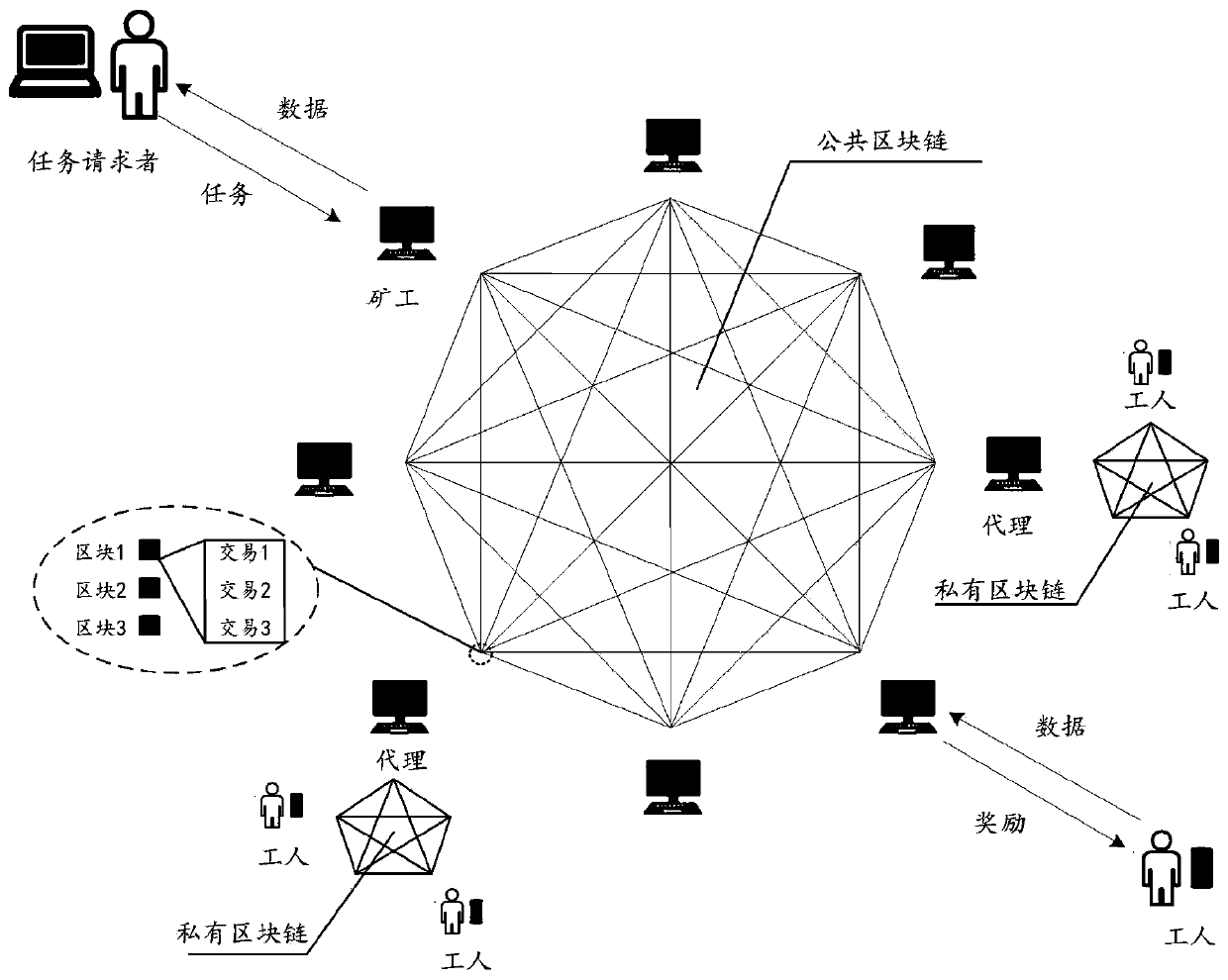
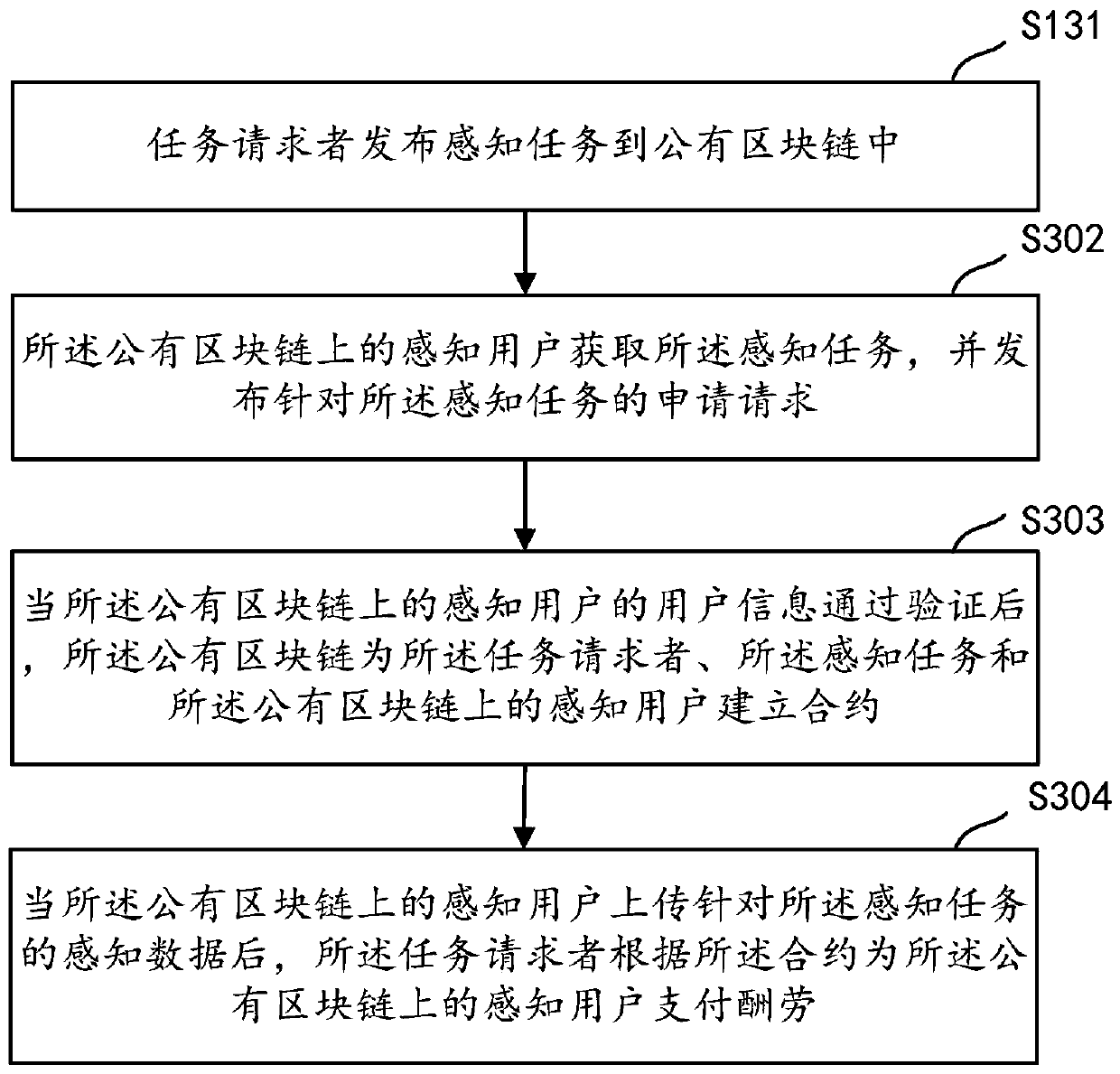
ActiveCN111177778AAvoid Privacy LeakageAvoid data lossDigital data protectionSensing dataUser privacy
The invention relates to the technical field of computers, and concretely relates to a method and a system for mobile crowd sensing, a server and a storage medium. The method comprises the following steps: a task requester publishes a sensing task to a public block chain; a sensing user on the public block chain acquires the sensing task and issues an application request for the sensing task; after the user information of the sensing user on the public block chain passes the verification, the public block chain establishes a contract for the task requester, the sensing task and the sensing user on the public block chain; and after the sensing user on the public block chain uploads sensing data for the sensing task, the task requester pays a reward for the sensing user on the public block chain according to the contract. The technical problems of user privacy leakage and data loss in the prior art are solved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Crowd sensing worker selection mechanism and system based on blockchain position privacy protection
The invention relates to a crowd sensing worker selection mechanism and system based on blockchain position privacy protection, and the system comprises a client and a distributed system. The client is connected with the distributed system; wherein the distributed system comprises a blockchain. The crowd sensing worker selection mechanism comprises the following steps: S11, performing user registration; S12, releasing task information; s13, the blockchain publishing information; S14, submitting work information; S15, selecting calculation by a worker; s16, signing and selecting by workers; s17, judging whether all the workers sign a contract or not; and S18, publishing a contract signing result. Sub-region optimization and global optimization technologies are sequentially used for worker coverage in a worker selection mechanism, and a more accurate calculation result is obtained; a greedy strategy is used for selecting results, and it is guaranteed that the result obtained in each stepis an optimal solution.
Owner:BEIJING UNIV OF POSTS & TELECOMM
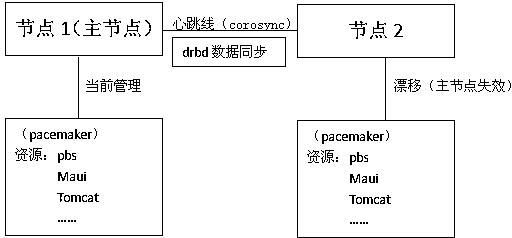
Double-computer reinforcing method for high-performance job scheduling management node
InactiveCN103942128AAvoid single point of failure problemsGuaranteed reliabilityHardware monitoringRedundant hardware error correctionOperation schedulingSingle point of failure
The invention discloses a double-computer reinforcing method for a high-performance job scheduling management node. The method is mainly applied in the field of high-performance calculation and is used for achieving dual reinforcement of a node level and a resource level by means of installation and configuration of Pacemaker, corosync and drbd software in terms of the job scheduling management node. According to the method, on one hand, a single-point fault problem of single-computer deployment is avoided, and on the other hand, job system resource monitoring can be achieved through the pacemaker software, and storage of a job scheduling system can be configured on two computers through the drbd software; compared with a heartbeat+NFS mode, namely an NFS shares storage of the job scheduling system, the method has dual redundant advantages, effectively guarantees operation reliability of the system and can effectively make up for defects of the traditional method.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Distributed management method and system for metadata of large-scale storage system
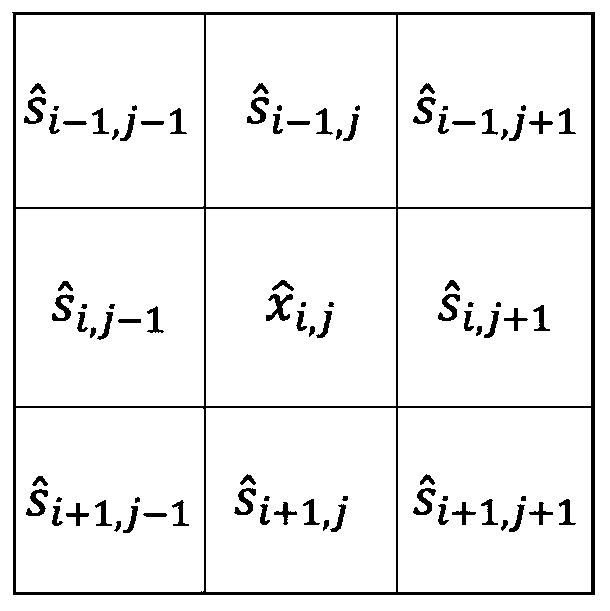
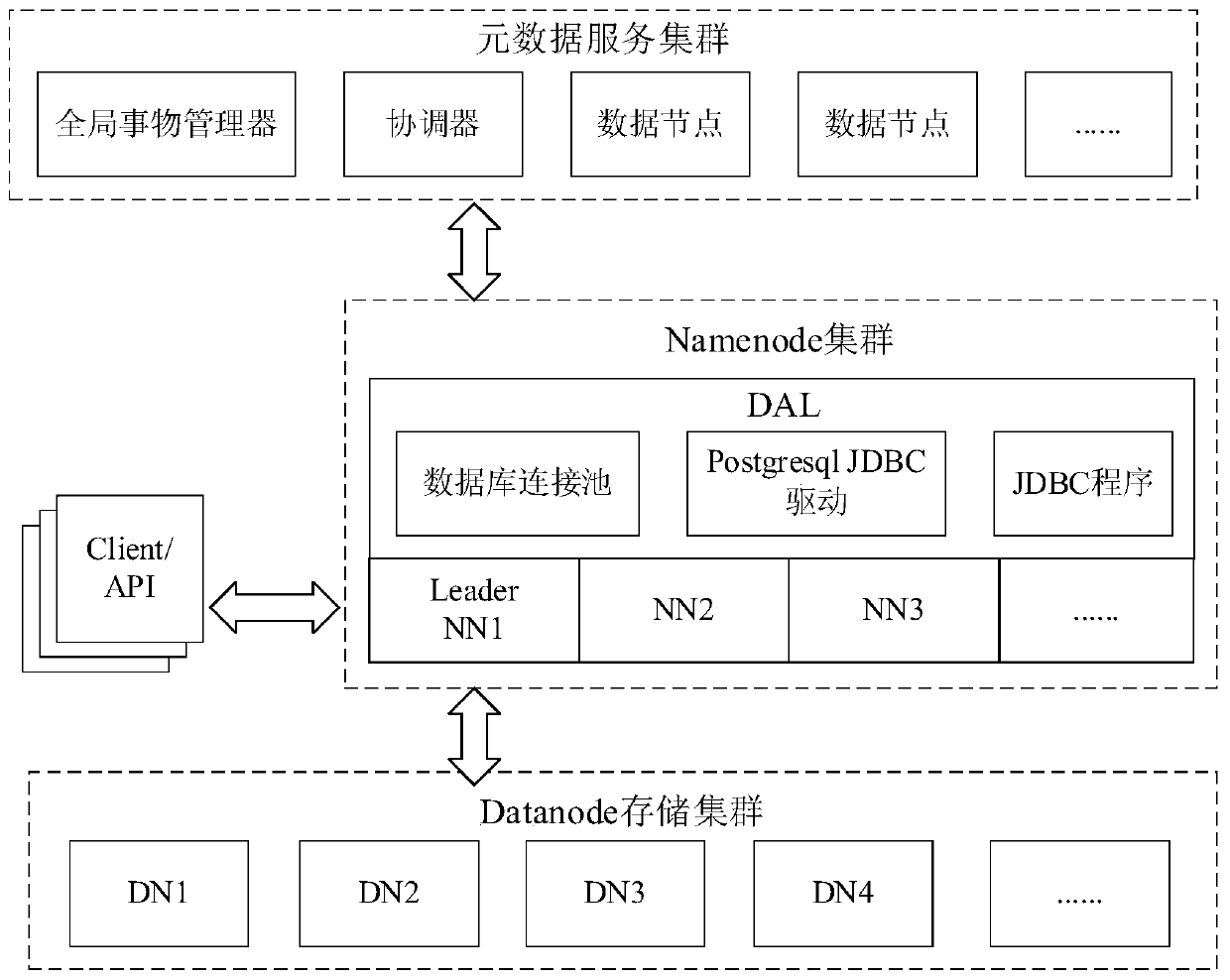
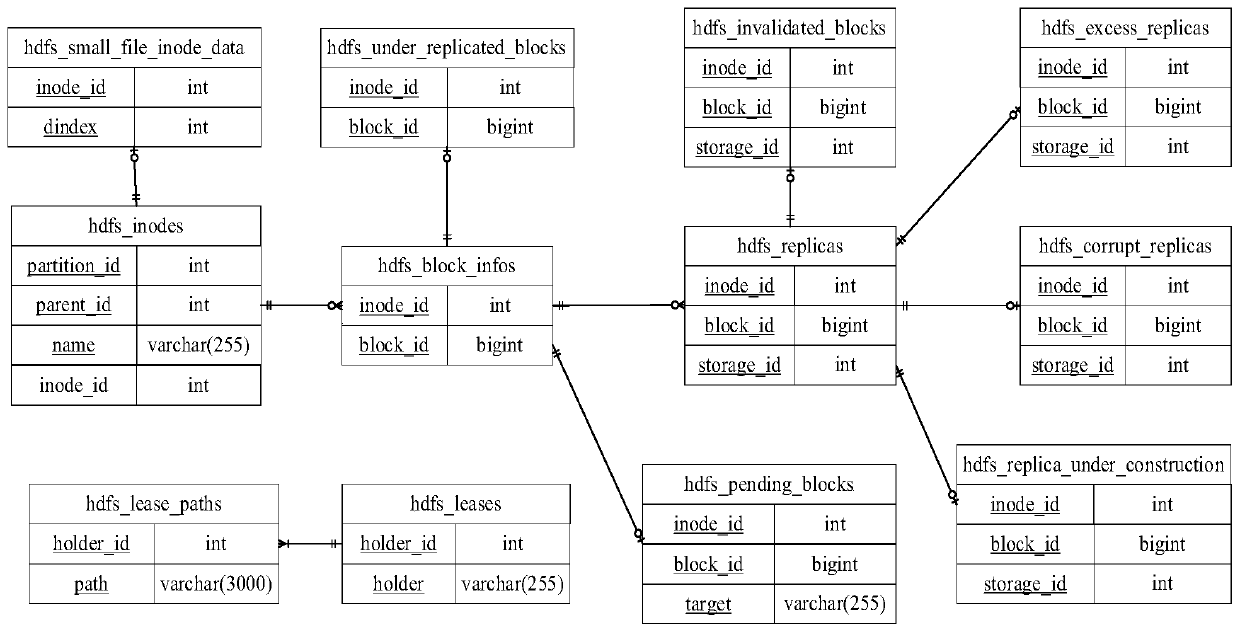
ActiveCN110287150AIncrease storage spaceImprove scalabilityFile access structuresFile/folder operationsInodeDistributed database
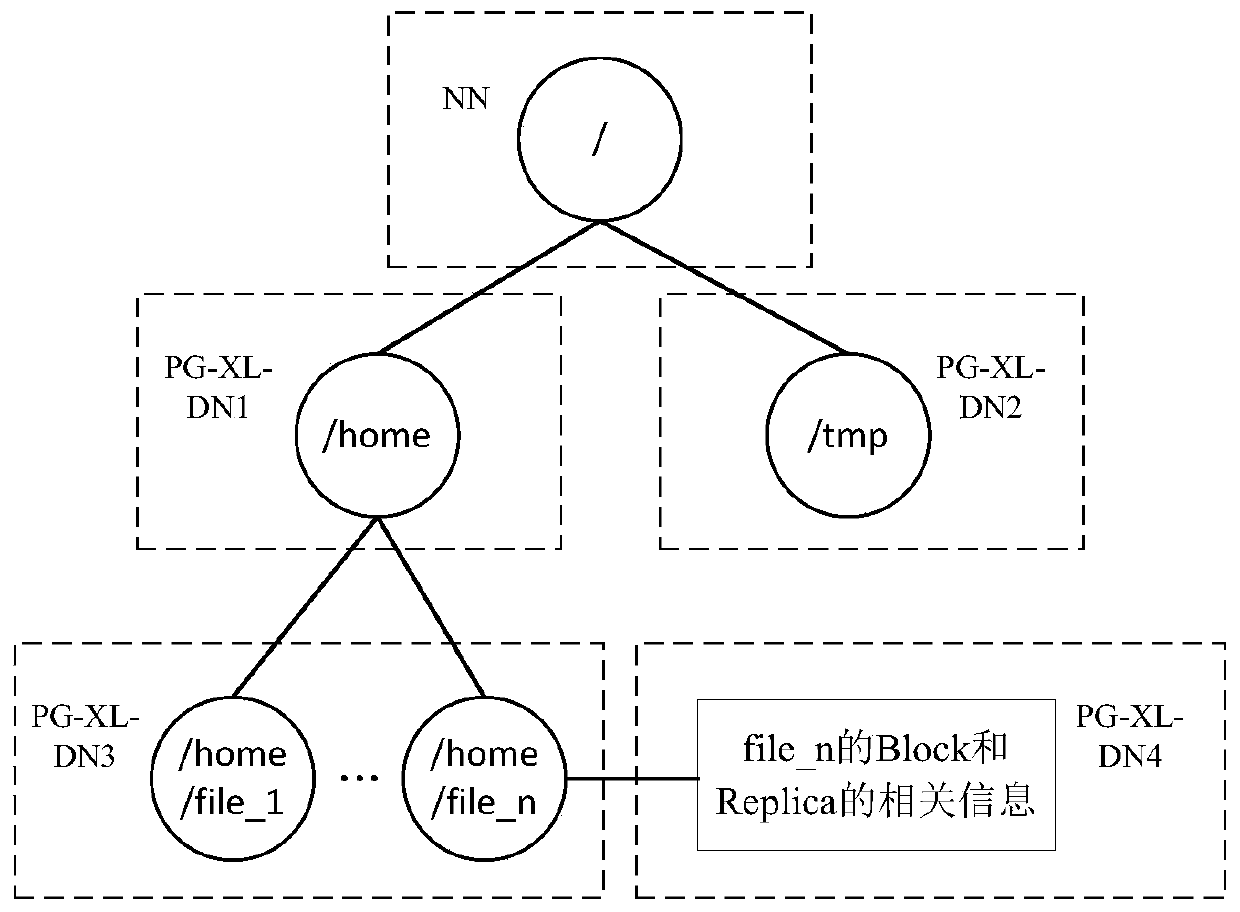
The invention discloses a distributed management method and system for metadata of a large-scale storage system. According to the method, metadata, stored in a NameNode memory, of an HDFS is abstracted into a structure of a two-dimensional table, and the structure of the two-dimensional table is stored in a distributed database in the form of the two-dimensional table; and the abstracted two-dimensional tables are associated with each other through an inode _ id. The Namenode becomes a bridge for the client to access the metadata, the client is firstly connected with the Namenode, the Namenode is used for operating the metadata in the distributed database, and the metadata is returned to the client. The single-point fault problem of the HDFS is solved.
Owner:INST OF INFORMATION ENG CAS
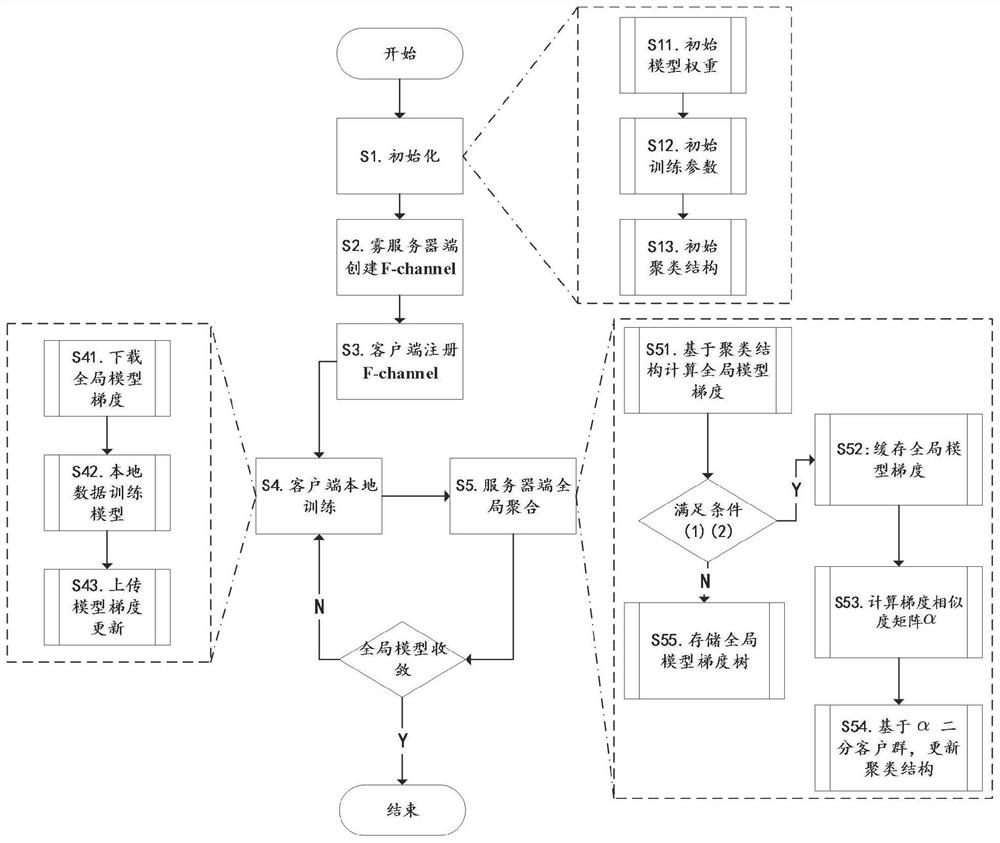
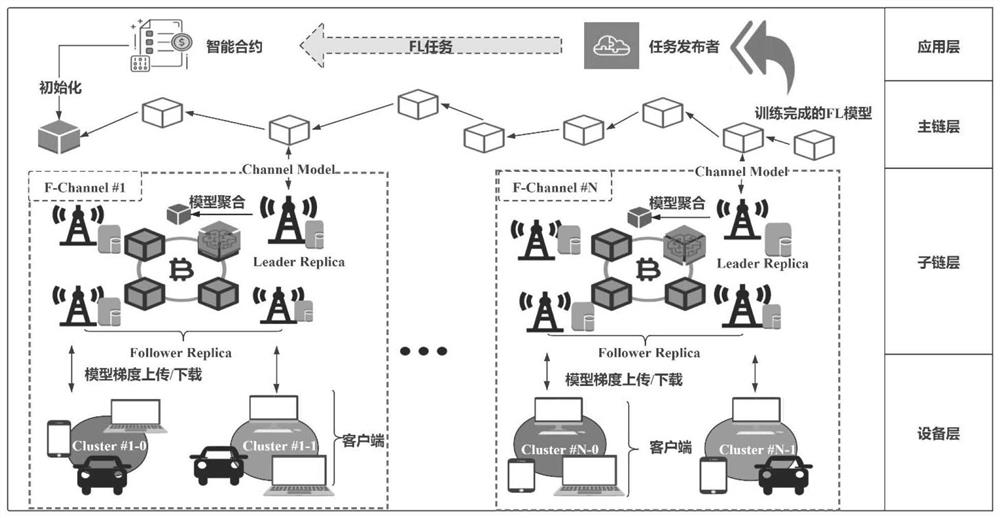
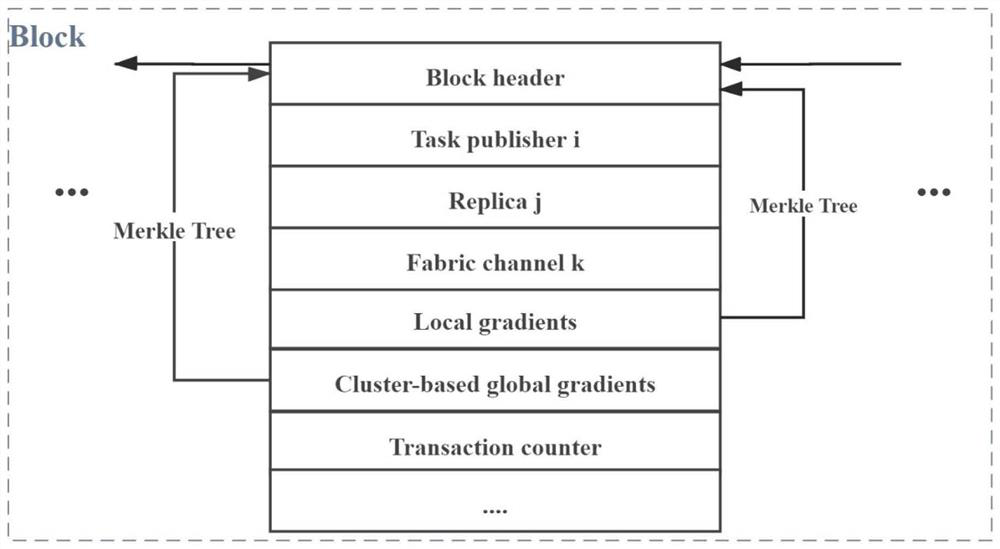
Federal learning method based on fog calculation
ActiveCN113379066AImprove efficiencyImprove securityDatabase distribution/replicationCharacter and pattern recognitionAttackLearning methods
The invention relates to a federal learning method based on fog calculation, and belongs to the technical field of mobile communication. An operator located at the cloud serves as a publisher of a federated learning task, a fog node located at the edge serves as a block chain consensus node to provide safe coordination service for federated learning, and meanwhile, Internet of Things equipment such as a smart phone and a tablet personal computer serve as a client of federated learning. Through the security verification service provided by the block chain and a given clustering federated learning method, the federated learning can effectively improve the federated learning efficiency and stability. In order to solve a single-point fault problem and a model hostile attack problem existing in federated learning, a client collaborative learning mode based on a block chain is provided, in order to reduce extra time delay generated by introduction of a block chain technology, a block chain consensus mode maintained by a fog node is PBFT, a block chain network is divided into a plurality of sub-networks, and consensus verification is carried out based on different federated learning tasks in each sub-network to reduce consensus time delay.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
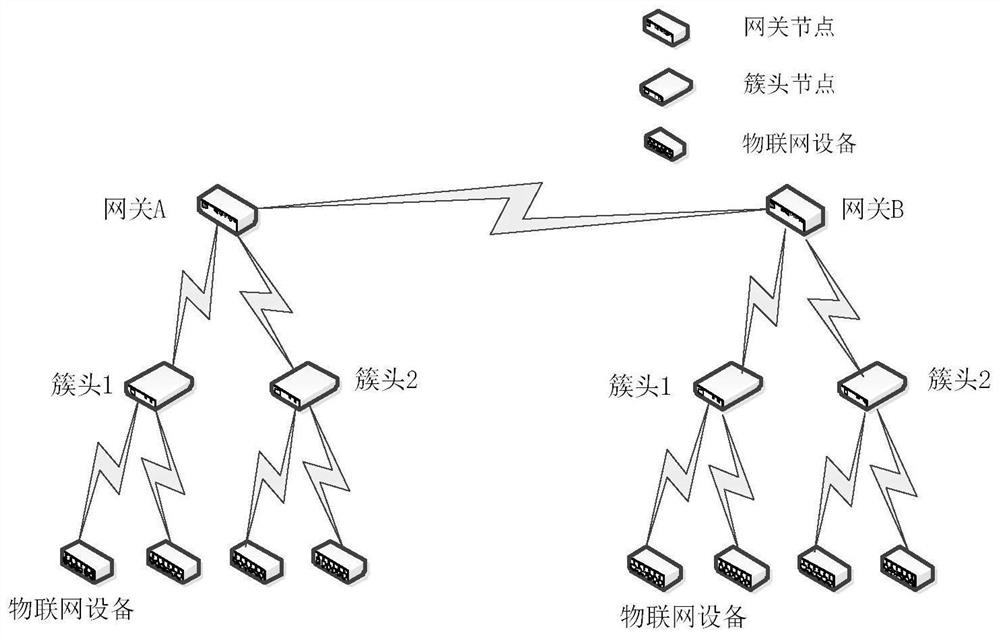
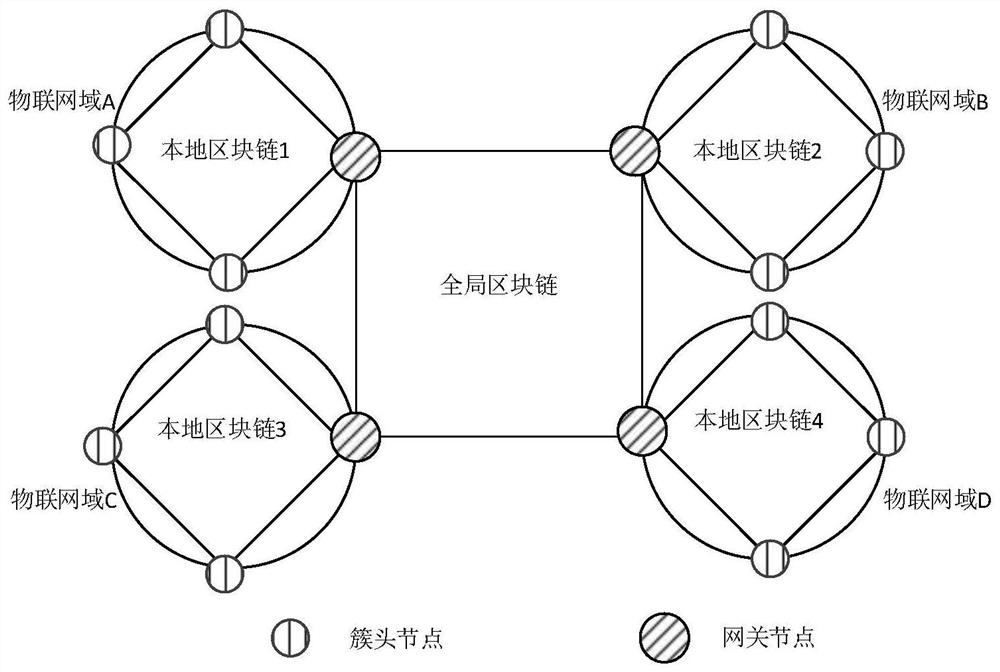
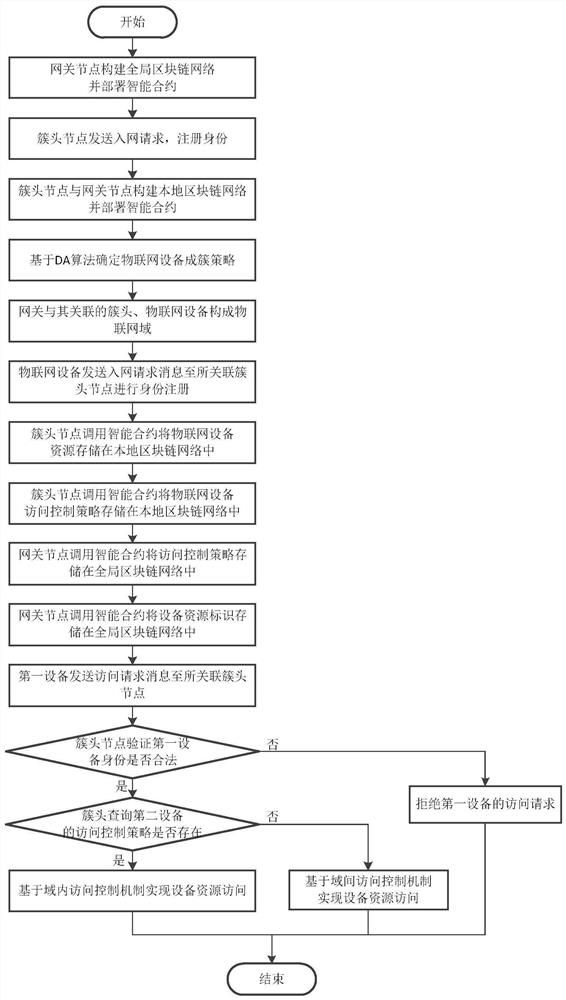
Internet of Things equipment resource access control method based on hierarchical blockchain
The invention relates to an Internet of Things equipment resource access control method based on a hierarchical blockchain, and belongs to the field of Internet of Things equipment resource access control. The method comprises the following steps: constructing global and local blockchain networks and deploying a smart contract; determining an Internet of Things equipment clustering policy by using a DA algorithm; formulating, by the Internet of Things equipment, an access control policy, generating an access control message and sending the access control message to a cluster head node; calling, by the cluster head node, the smart contract to store the access control policy in the local blockchain network; forwarding, by the cluster head node, the access control message to a gateway node; and calling, by the gateway node, the smart contract to store the access control policy in the global blockchain network; sending, by the cluster head node, an equipment resource identifier message to the gateway node; calling, by the gateway node, the smart contract to store the equipment resource identifier in the global blockchain network; and performing, by the cluster head node, identity authentication on the first Internet of Things equipment so as to select the intra-domain / inter-domain access control machine to realize equipment resource access.
Owner:CHINA MOBILE M2M
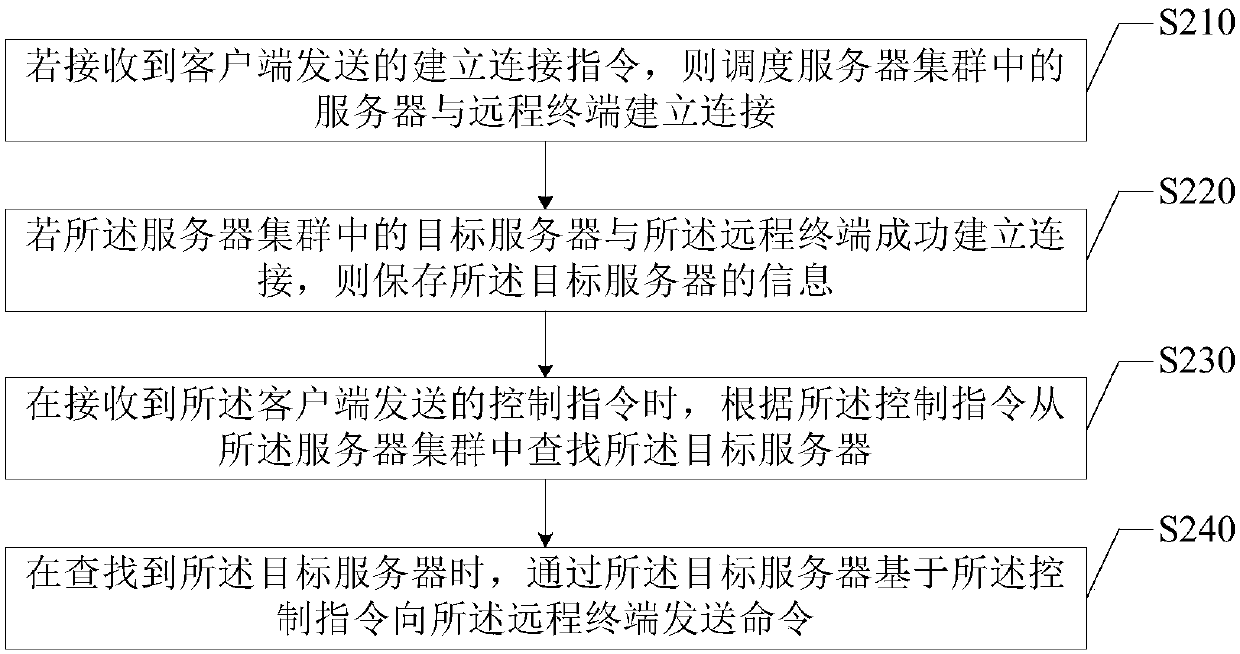
Control method, control device, electronic equipment and storage medium
ActiveCN109936587AAvoid single point of failureAvoid single point of failure problemsTransmissionSingle pointSingle point of failure
The embodiment of the invention provides a control method, a control device, electronic equipment and a storage medium, and relates to the technical field of computers. The method comprises the following steps: if a connection establishment instruction sent by a client is received, scheduling servers in a server cluster to establish connection with a remote terminal; if the target server in the server cluster is successfully connected with the remote terminal, storing the information of the target server; when a control instruction sent by a client is received, searching a target server from aserver cluster according to the control instruction; And when the target server is found, sending a command to the remote terminal based on the control instruction through the target server. According to the technical scheme provided by the embodiment of the invention, remote control on the remote terminal can be realized, and meanwhile, the problem of single-point faults of a control system canbe avoided.
Owner:BEIJING JINGDONG QIANSHITECHNOLOGY CO LTD
CP-ABE access control scheme based on block chain
PendingCN111079191ASolve the single point of failure problemReduce workloadDigital data protectionTransmissionAttribute authorityAuthorization
The invention discloses a blockchain combined access control architecture based on attribute encryption. Aiming at attribute encryption based on a ciphertext strategy in a multi-authorization-center scene, the work of the authorization centers is executed by a block chain, a trust relationship between the attribute authorization centers is constructed by utilizing an intelligent contract, a key management mechanism is established, and attribute authorization, key management and attribute revocation are completed by the intelligent contract. According to the scheme, the access control process based on attribute encryption is public, transparent, more flexible and safer.
Owner:INNER MONGOLIA UNIVERSITY
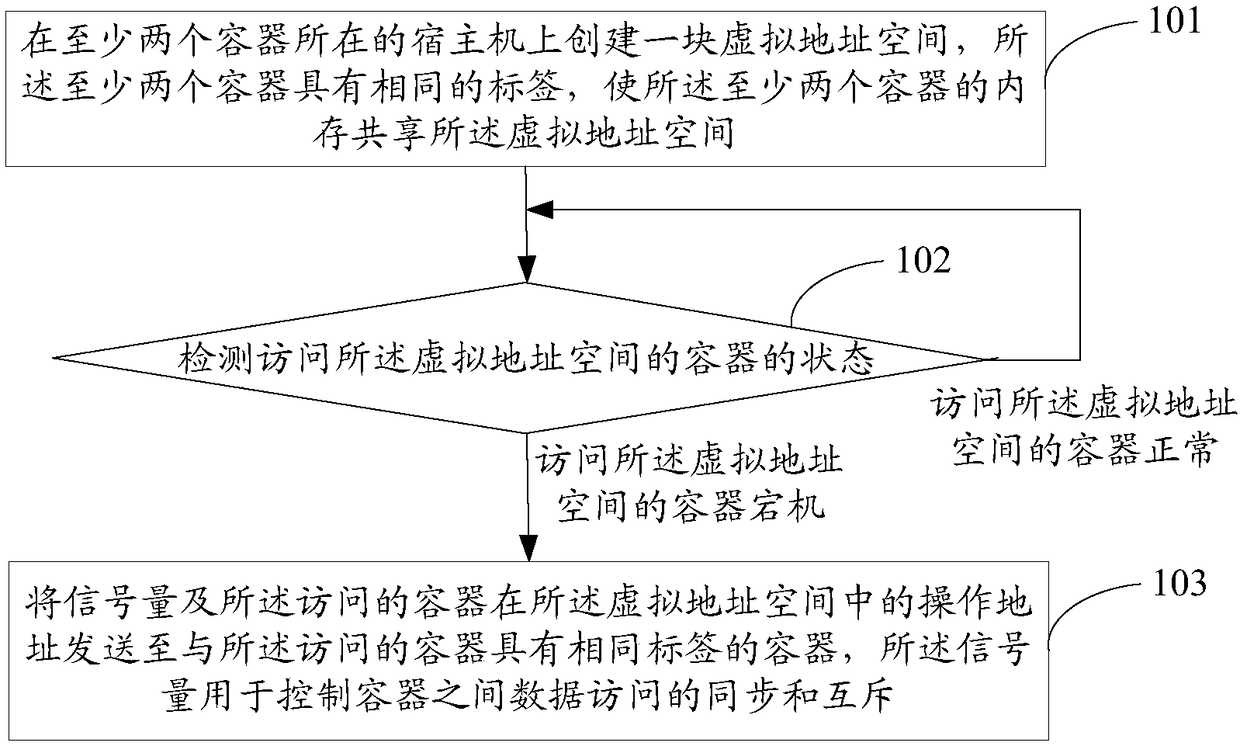
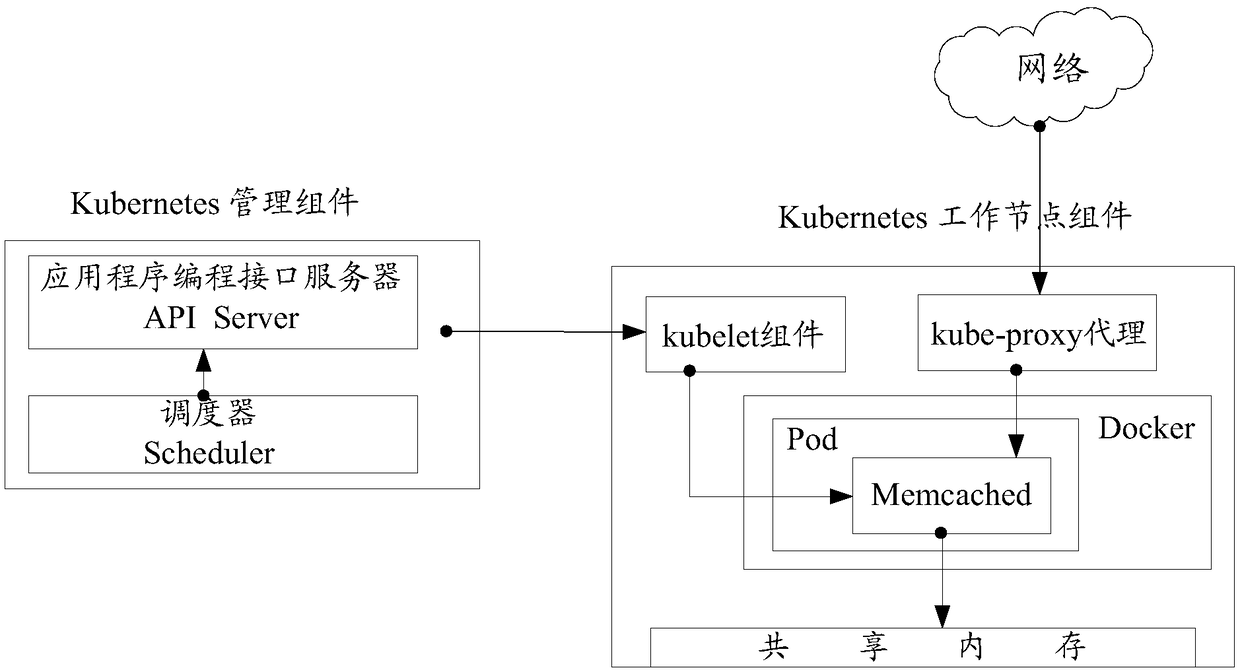
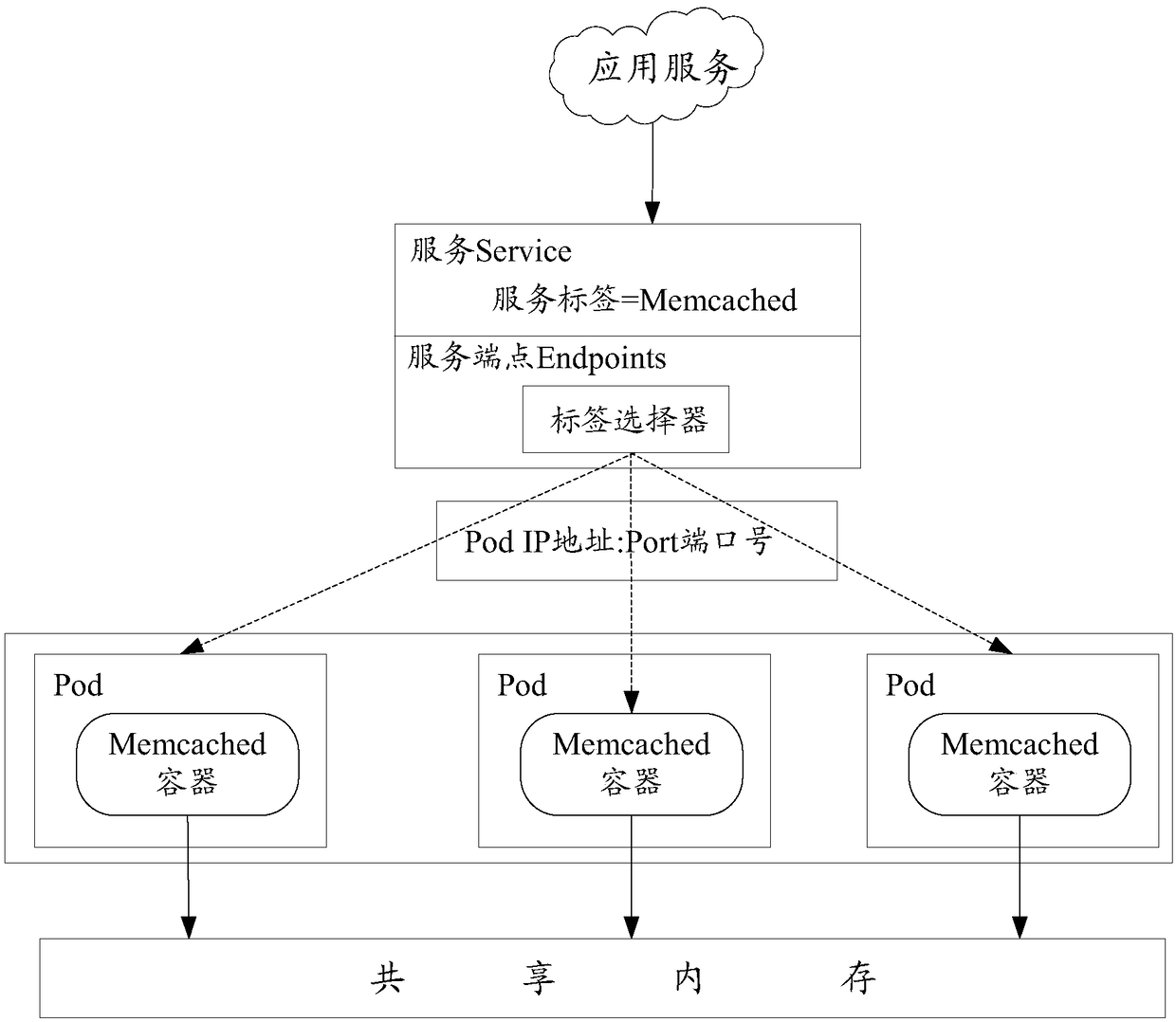
Memory sharing method, container management platform, and computer-readable storage medium
ActiveCN109213571AReduce multiple copiesSolve single point of failureInterprogram communicationSoftware simulation/interpretation/emulationSingle pointMemory sharing
The invention discloses a memory sharing method, a container management platform and a computer-readable storage medium. The method comprises the following steps: a virtual address space is created ona host machine where at least two containers are located; the at least two containers have the same label, so that the memory of the at least two containers shares the virtual address space; detecting a state of a container accessing the virtual address space; when an accessed container is down, a semaphore for controlling synchronization and mutual exclusion of data accesses between the containers and an operational address of the accessed container in the virtual address space are sent to a container having the same label as the accessed container. The semaphore is used to control synchronization and mutual exclusion of data accesses between the containers. By detecting a state of a container that accesses a virtual address space, when the access container is down, the semaphore and itsoperation address are sent to other containers. On the premise of reducing the front-end multiple distributions, the shared memory among multiple Memcached server nodes is realized, thus solving theproblem of single point failure of Memcached cluster.
Owner:BEIJING BAIWU TECH CO LTD
Multipath data traffic load equalizing method
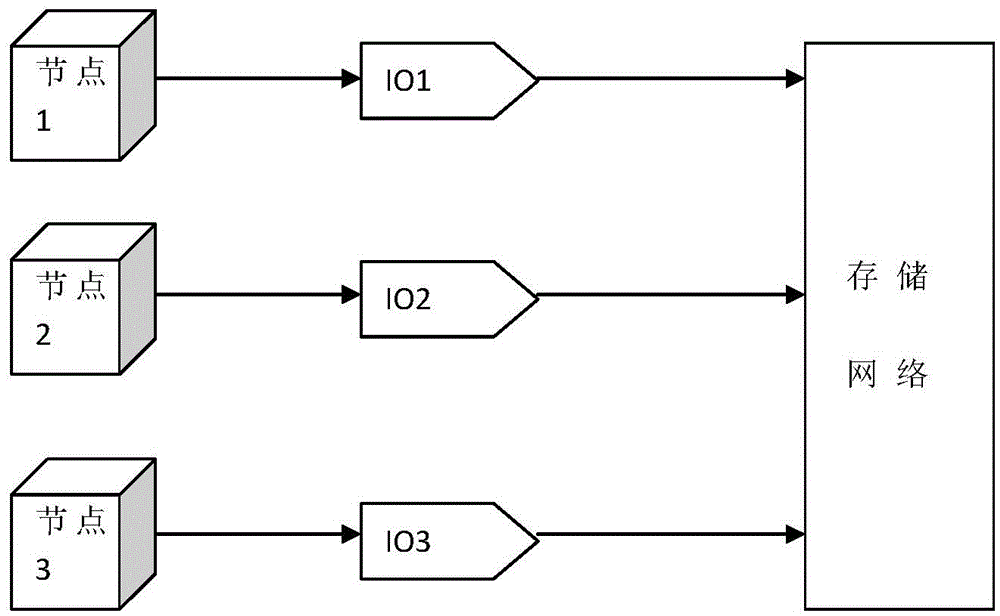
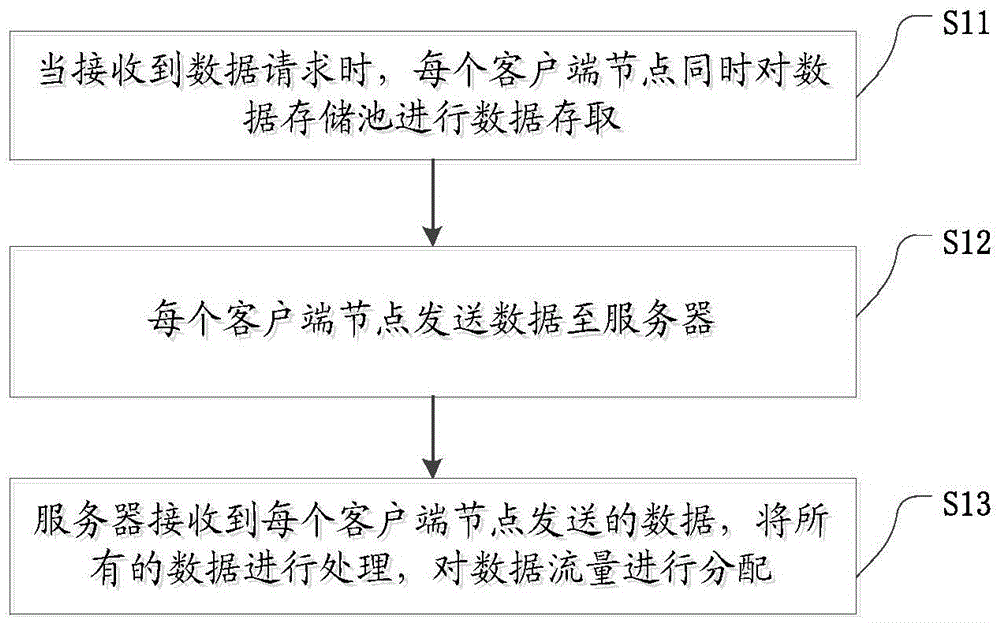
InactiveCN105553872AReal-time monitoring and managementImprove Data Management EfficiencyData switching networksTraffic capacityData access
The invention discloses a multipath data traffic load equalizing method. The method comprises: when a data request is received, carrying out data access to every data storage pool at the same time by every client node; sending data to a server by every client node; receiving the data sent by every client node by the server, processing all data, and distributing data traffic. According to the method, the high efficiency data access is realized.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
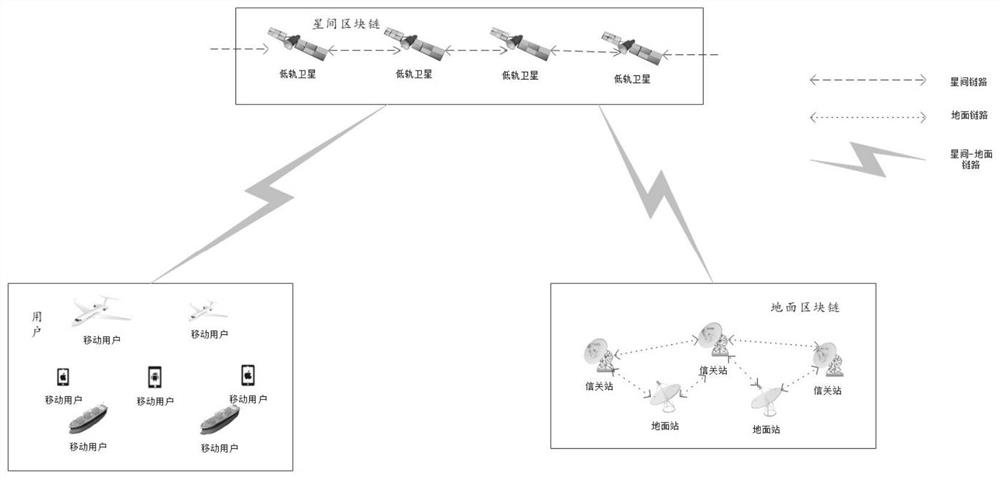
Spatial information network access control system and authentication method based on blockchain
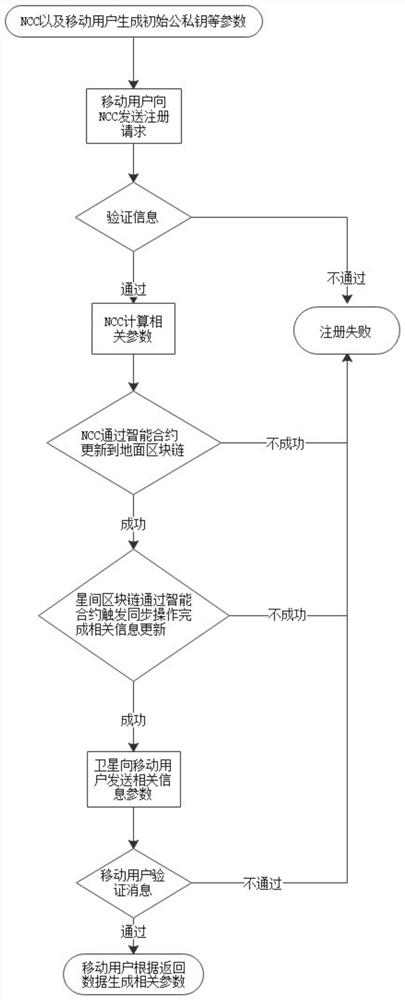
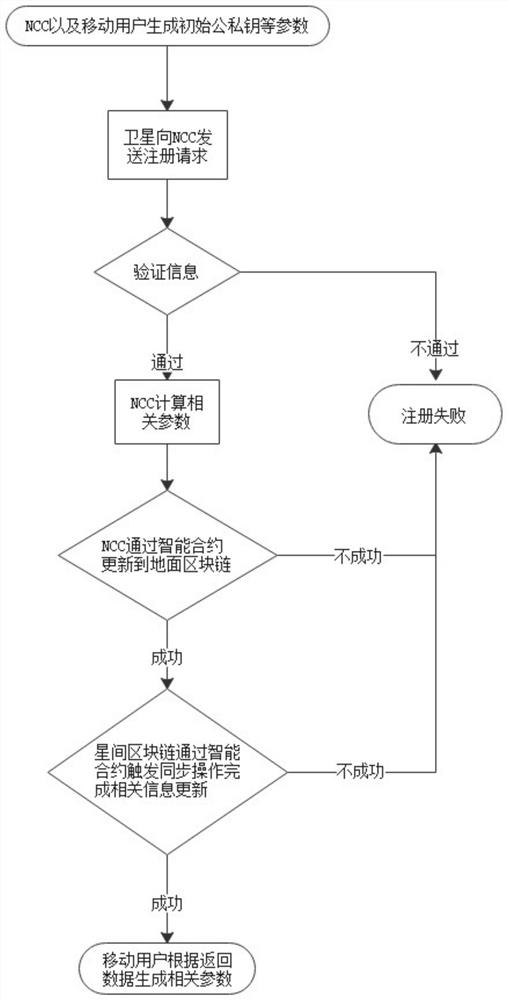
ActiveCN112564775AFast authenticationImprove integrityRadio transmissionSecurity arrangementData integrityStation
The invention provides a spatial information network access control system and authentication method based on a blockchain, the spatial information network access control system based on the blockchain comprises a ground blockchain module, an inter-satellite blockchain module and a client, wherein the ground blockchain module comprises ground stations and a gateway station; each ground station andthe gateway station are provided with a link; the inter-satellite blockchain module comprises a low-orbit satellite; and the client comprises each mobile user. The invention further provides a spatial information network access control authentication method based on the blockchain. The method comprises a related parameter initialization and registration process, an access authentication and authority management control process and a transfer process based on the blockchain. According to the invention, rapid authentication and access permission confirmation of the user equipment can be satisfied, the data integrity and security in the whole process are further enhanced by introducing the blockchain, the problem of single-point failure existing in network control NCC in an actual scene is solved, and access control and operation traceability functions are provided.
Owner:JIANGSU FUTURE NETWORKS INNOVATION +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com