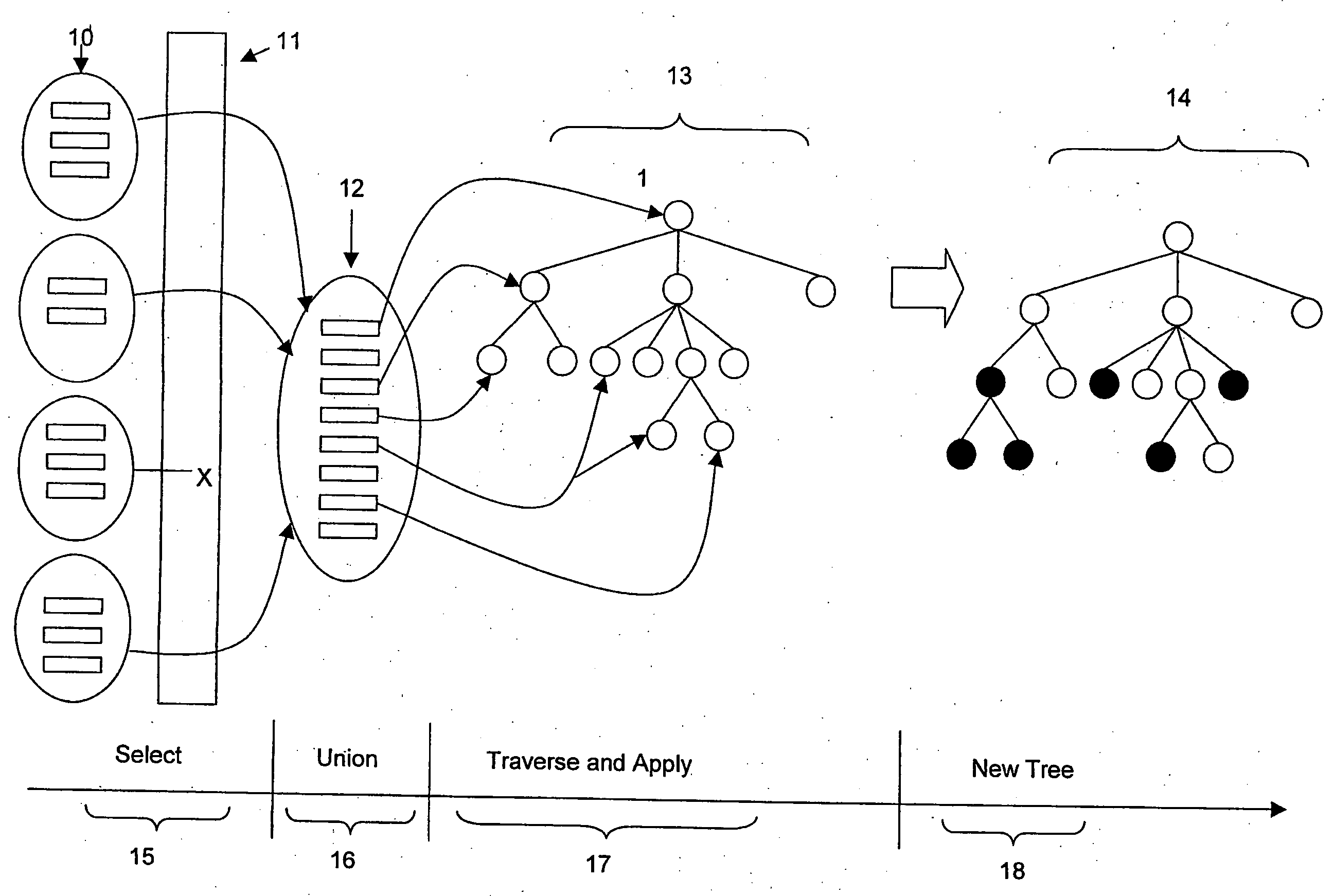
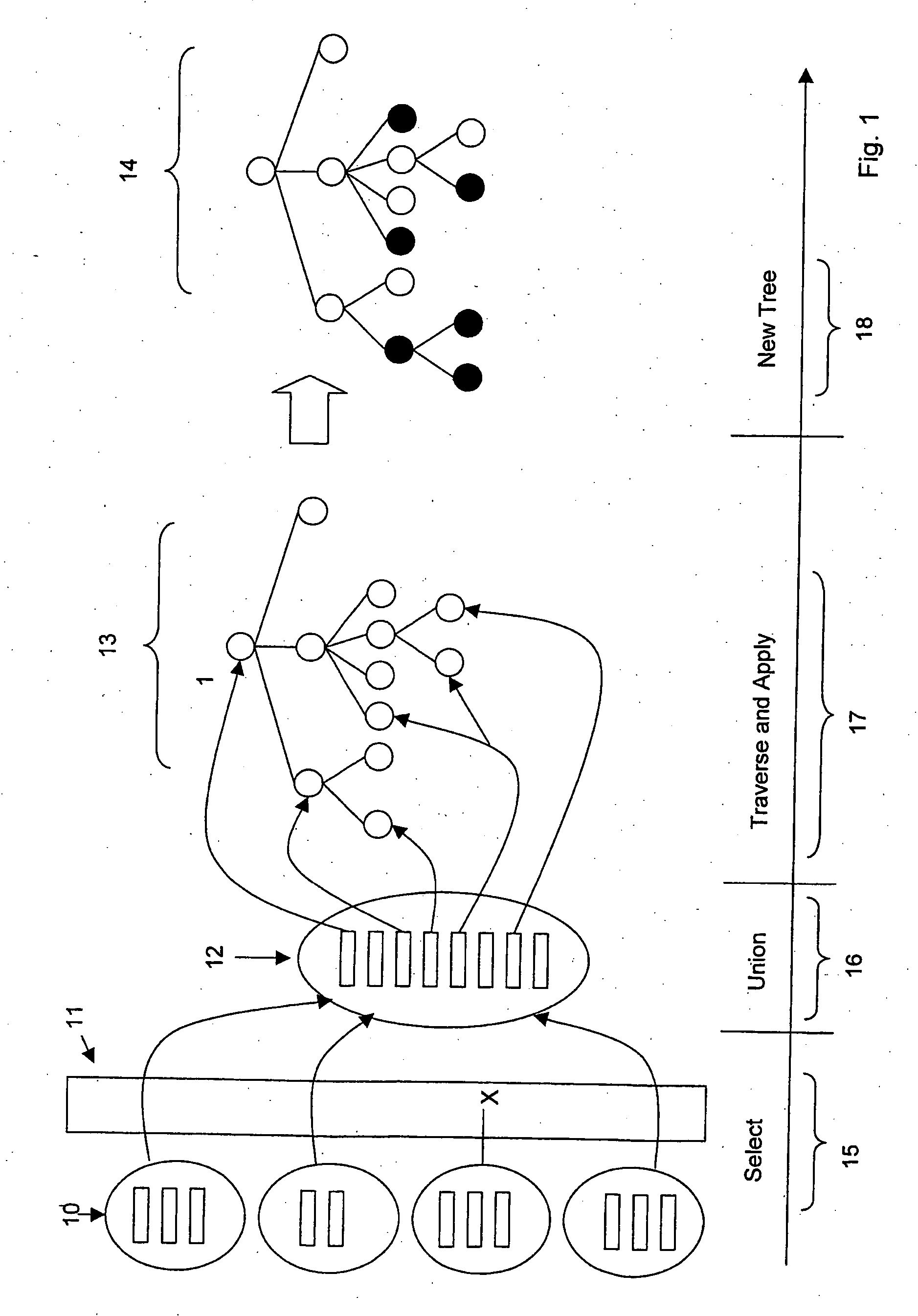
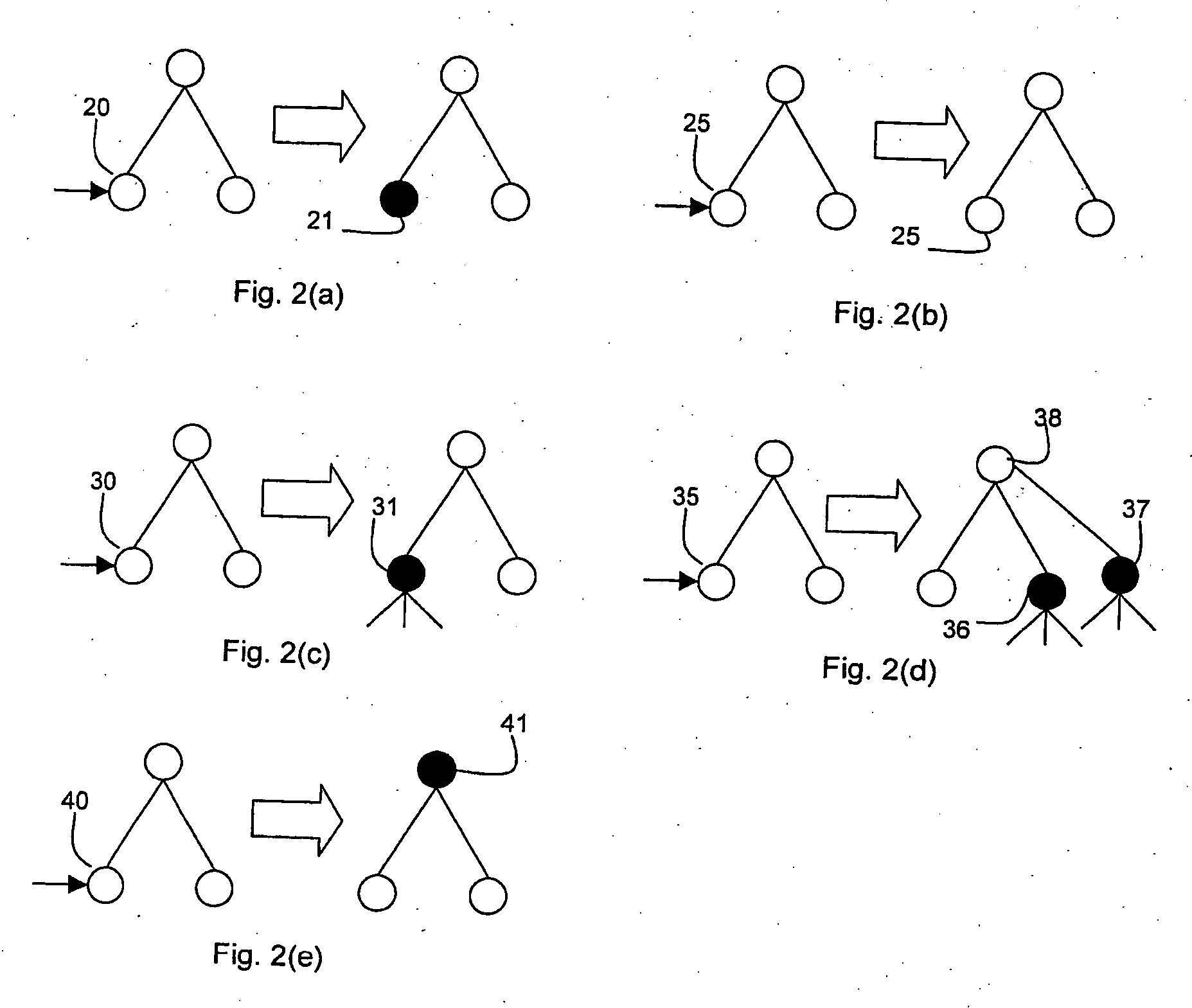
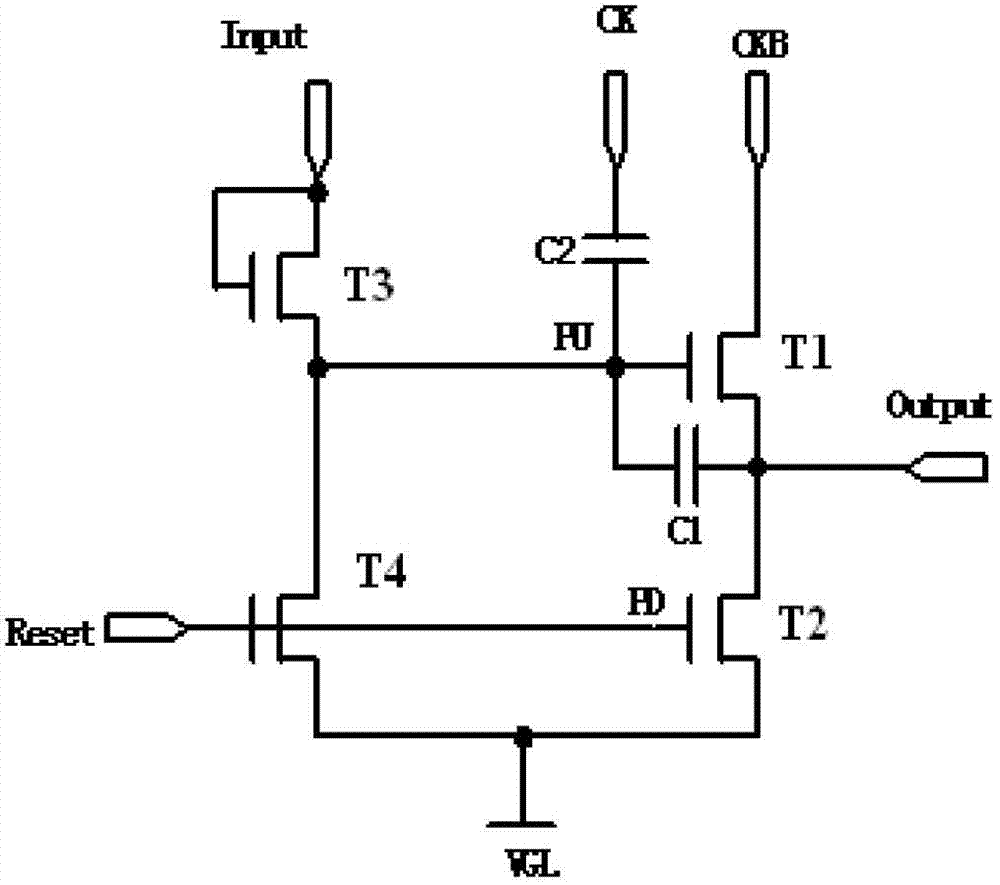
Patents
Literature
266 results about "Node level" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
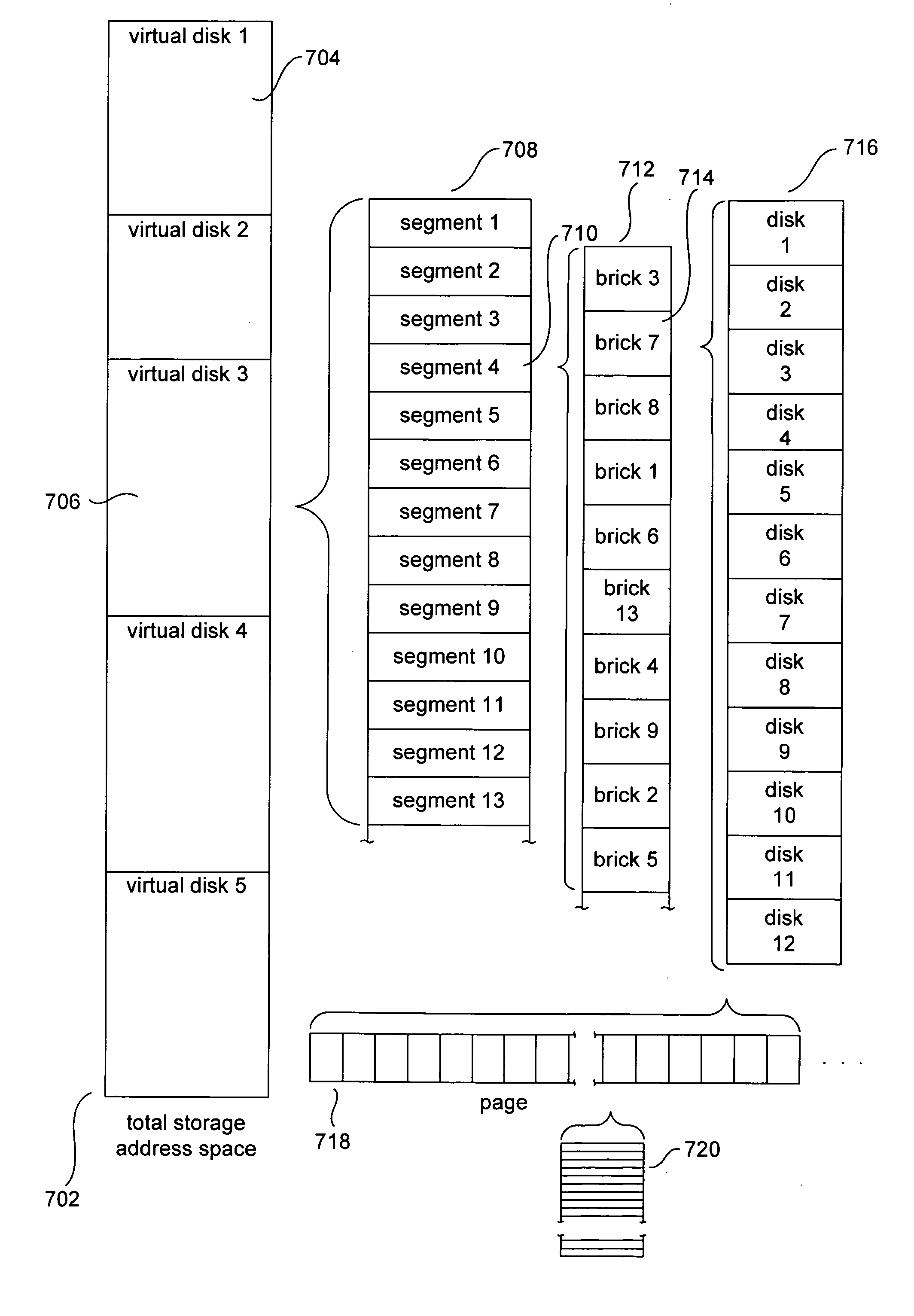
Methods and systems for hierarchical management of distributed data
Various method and system embodiments of the present invention are directed to hierarchical control logic within each component data-storage system of a distributed data-storage system composed of networked component data-storage systems over which virtual disks, optionally replicated as virtual-disk images, composed of data segments in turn composed of data blocks, are distributed at the granularity of segments. Each data segment is distributed according to a configuration. The hierarchical control logic includes, in one embodiment of the present invention, a top-level coordinator, a virtual-disk-image-level coordinator, a segment-configuration-node-level coordinator, a configuration-group-level coordinator, and a configuration-level coordinator.
Owner:HEWLETT PACKARD DEV CO LP
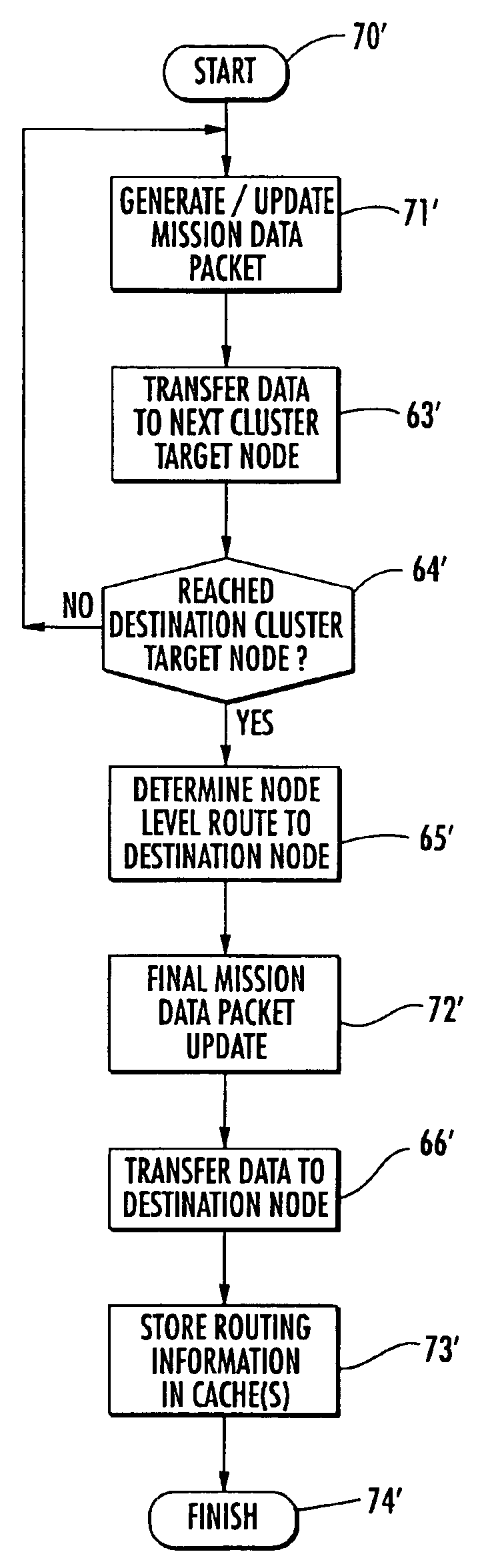
Hierarchical mobile ad-hoc network and methods for performing reactive routing therein using dynamic source routing (DSR)
InactiveUS6870846B2Use to determineError preventionFrequency-division multiplex detailsWireless ad hoc networkSelf-organizing network
A method is provided for sending data in a wireless ad-hoc network including a plurality of nodes grouped into clusters of nodes and a plurality of wireless links connecting the plurality of nodes, where each cluster node has a designated cluster leader node. The method may include sending a cluster-level route request from a source node of a source cluster to a cluster leader node of the source cluster, and determining a cluster-level route between the source cluster and a destination cluster including a destination node responsive to the cluster-level route request and using a plurality of the cluster leader nodes. Furthermore, at least one cluster target node may be designated in a cluster along the cluster-level route, and a node-level route determined from the source node to the destination node including the at least one cluster target node. In addition, the method may also include generating a mission data packet for transferring the data.
Owner:STINGRAY IP SOLUTIONS LLC
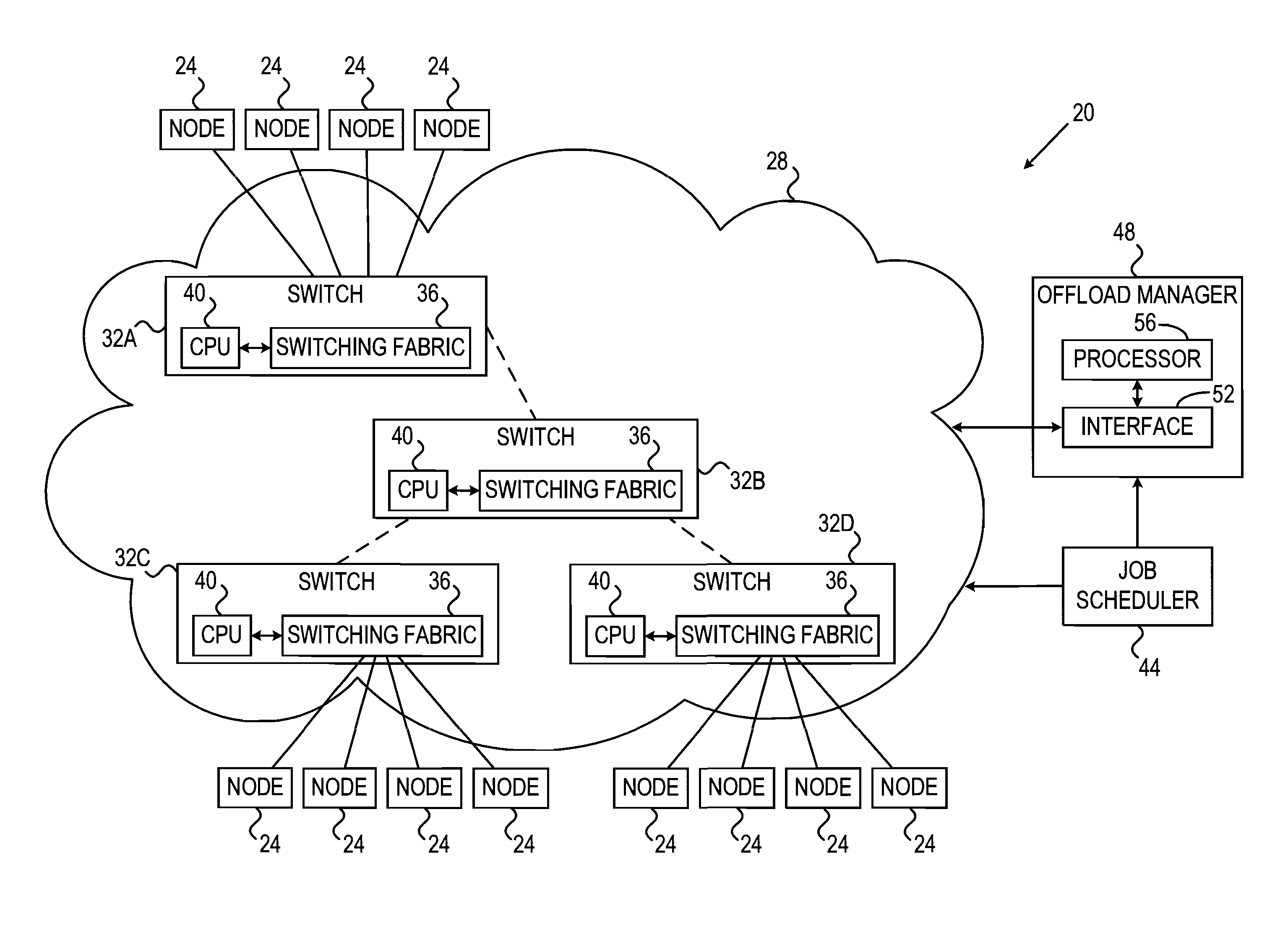
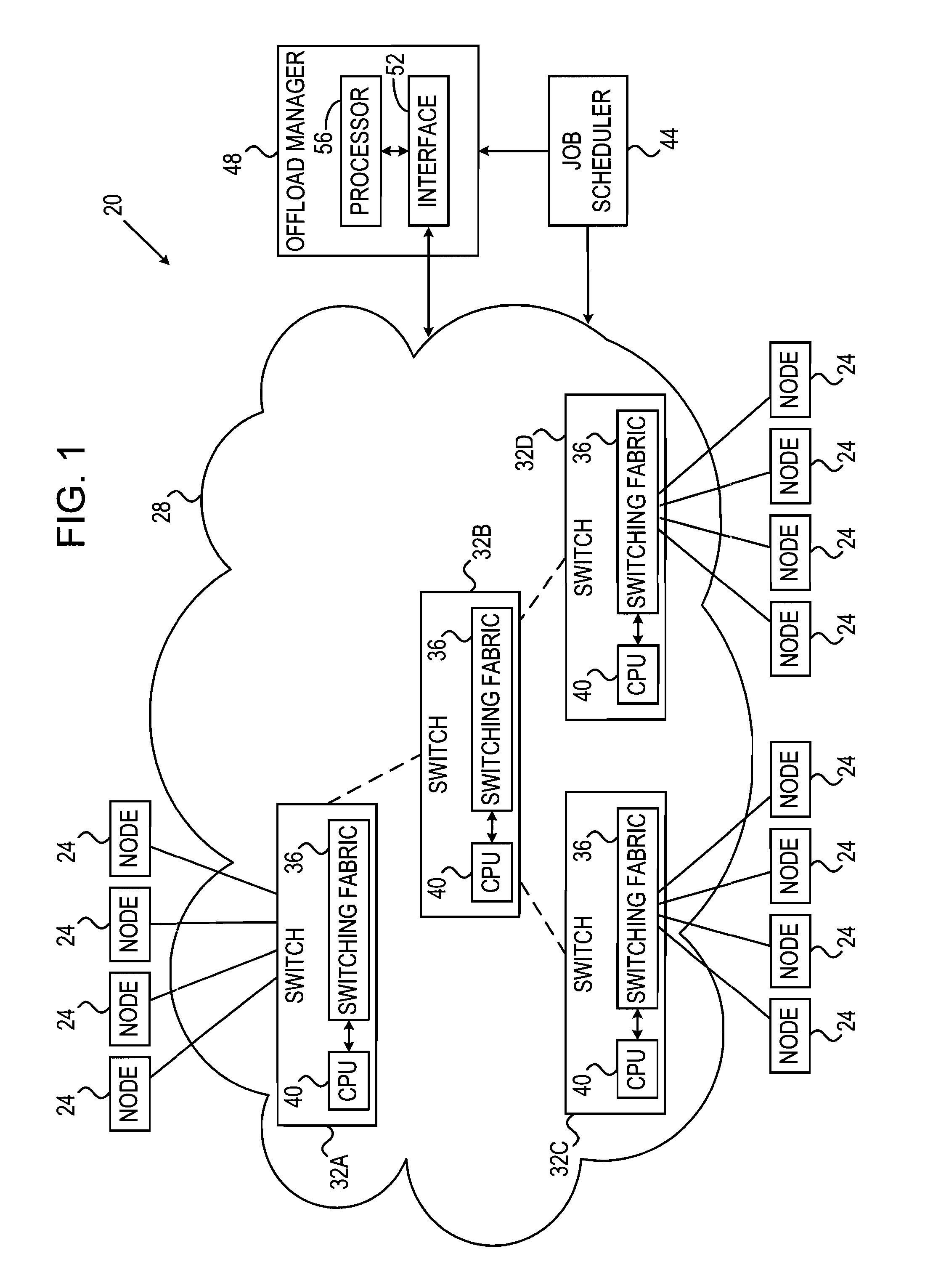
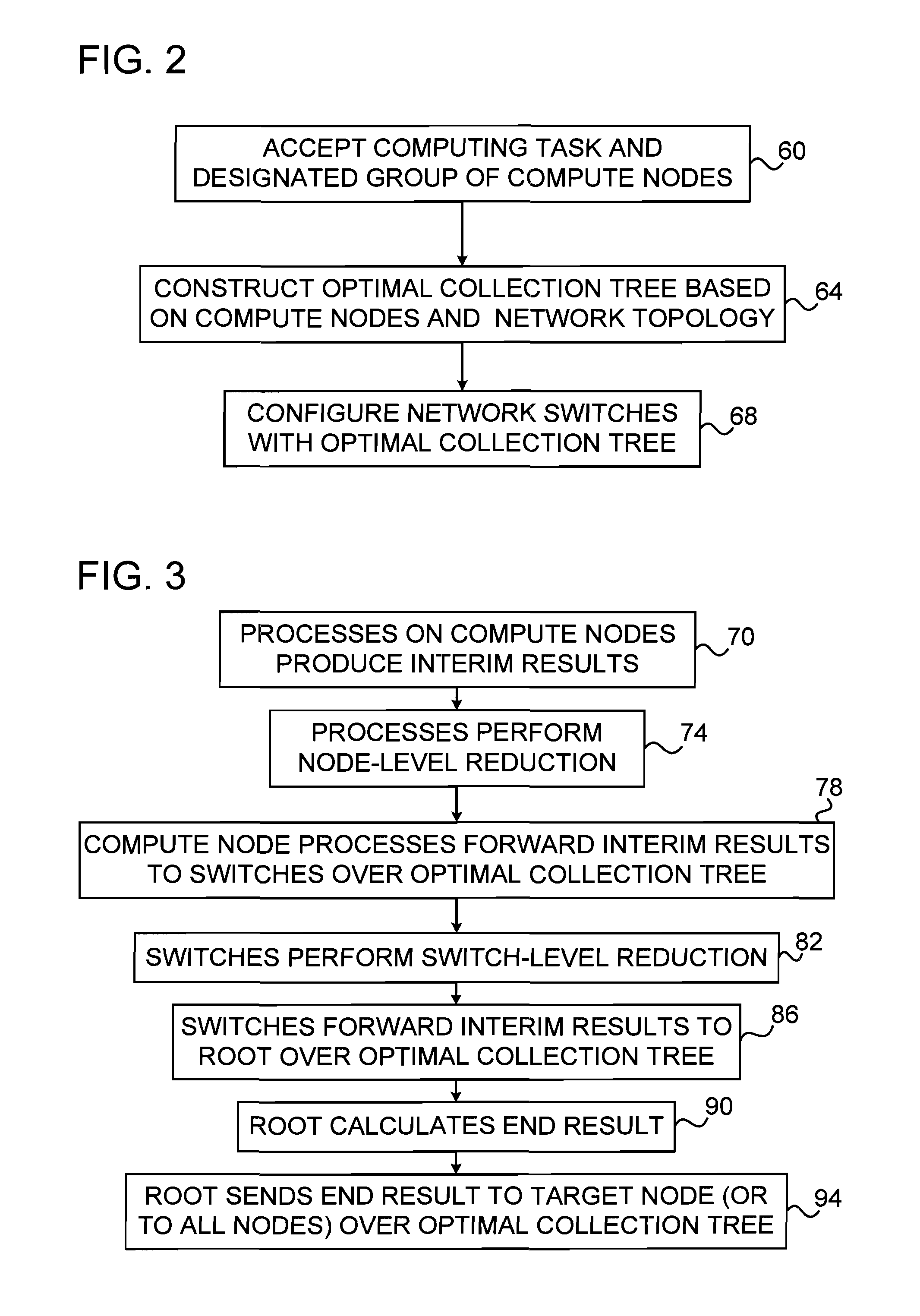
Topology-Aware Fabric-Based Offloading of Collective Functions
ActiveUS20110113083A1Multiple digital computer combinationsTransmissionInterconnectionNetwork switch
A computing method includes accepting a notification of a computing task for execution by a group of compute nodes interconnected by a communication network, which has a given interconnection topology and includes network switching elements. A set of preferred paths, which connect the compute nodes in the group via at least a subset of the network switching elements to one or more root switching elements, are identified in the communication network based on the given interconnection topology and on a criterion derived from the computing task. The network switching elements in the subset are configured to forward node-level results of the computing task produced by the compute nodes in the group to the root switching elements over the preferred paths, so as to cause the root switching elements to calculate and output an end result of the computing task based on the node-level results.
Owner:MELLANOX TECHNOLOGIES LTD
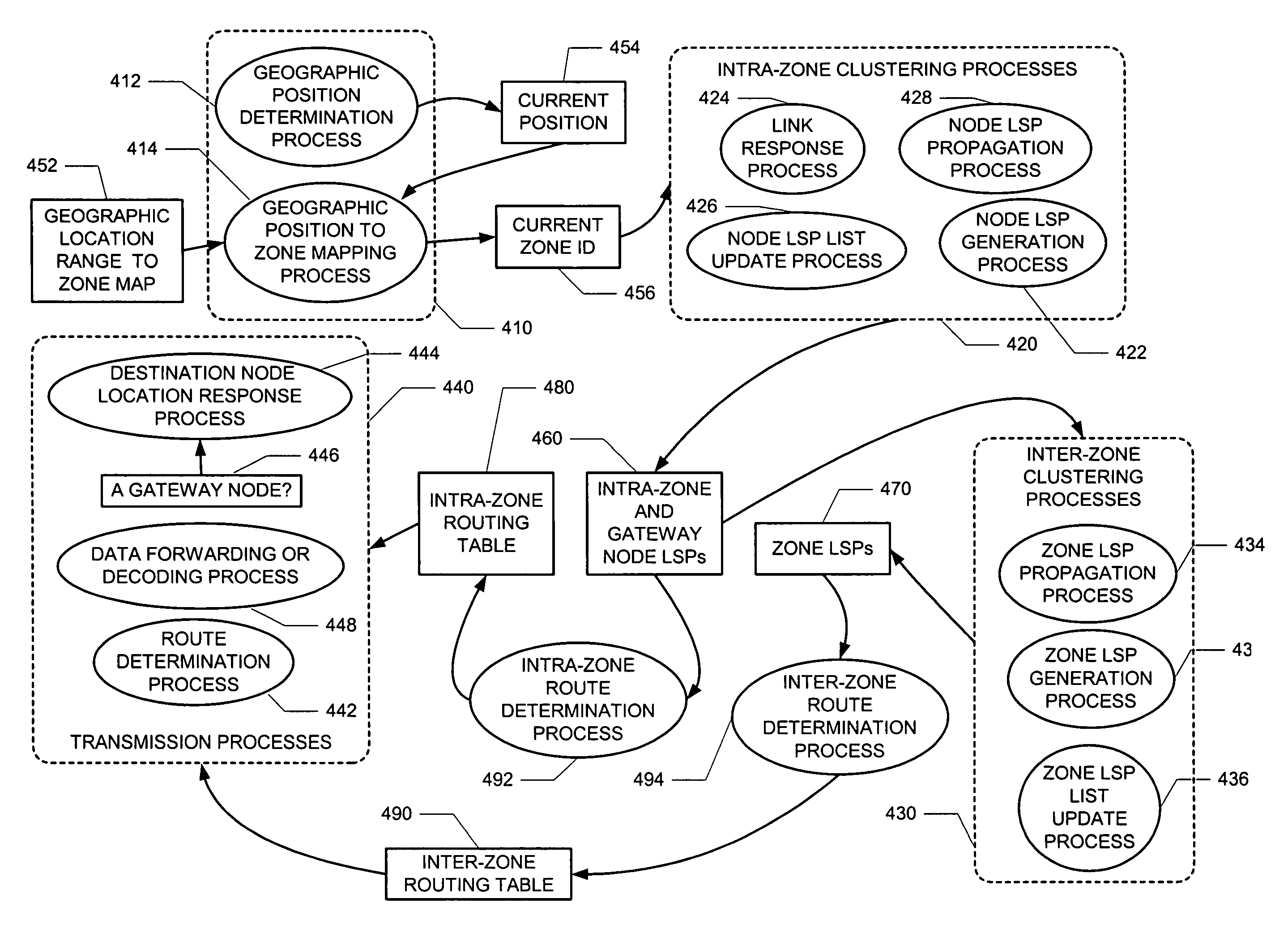
Methods and apparatus for routing in a mobile ad hoc network
InactiveUS6980524B1Telephonic communicationData switching by path configurationOverlap zoneLink-state routing protocol
A “peer-to-peer” hierarchical routing protocol—also referred to as Zone-based Hierarchical Link State Routing protocol (or “ZHLS”)—which incorporates location information into a novel “peer-to-peer” hierarchical routing approach. The network may be divided into non-overlapping zones. Aggregating nodes into zones conceals the detail of the network topology. Initially, each node knows its own position and therefore zone ID through a position determination unit, such as a Global Positioning System (GPS). After the network is established, each node knows the low level (node level) topology about node connectivity within its zone and the high level (zone level) topology about zone connectivity of the whole network. A packet may be forwarded by specifying the hierarchical address—zone ID and node ID—of a destination node in the packet header.
Owner:POLYTECHNIC INST OF NEW YORK
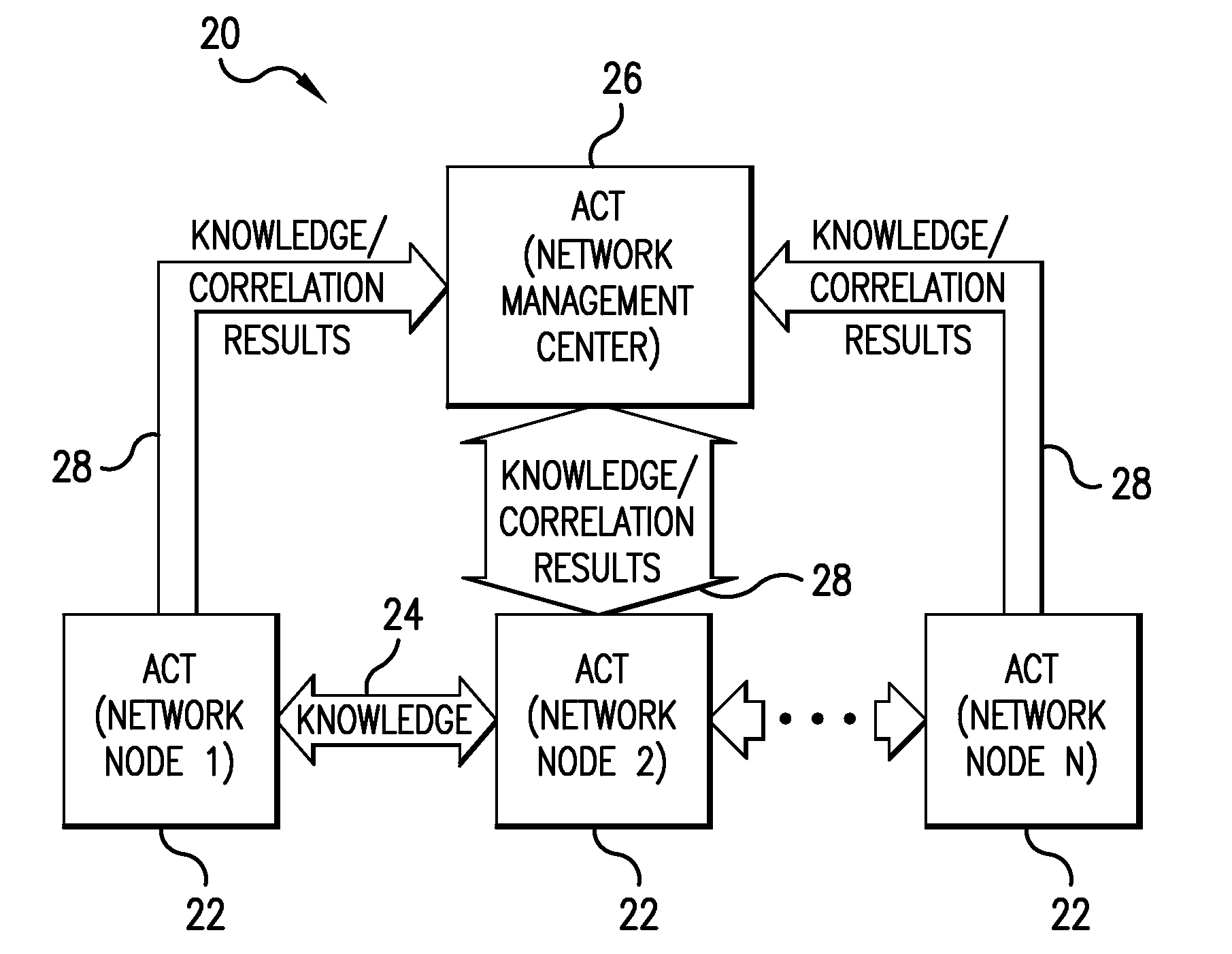
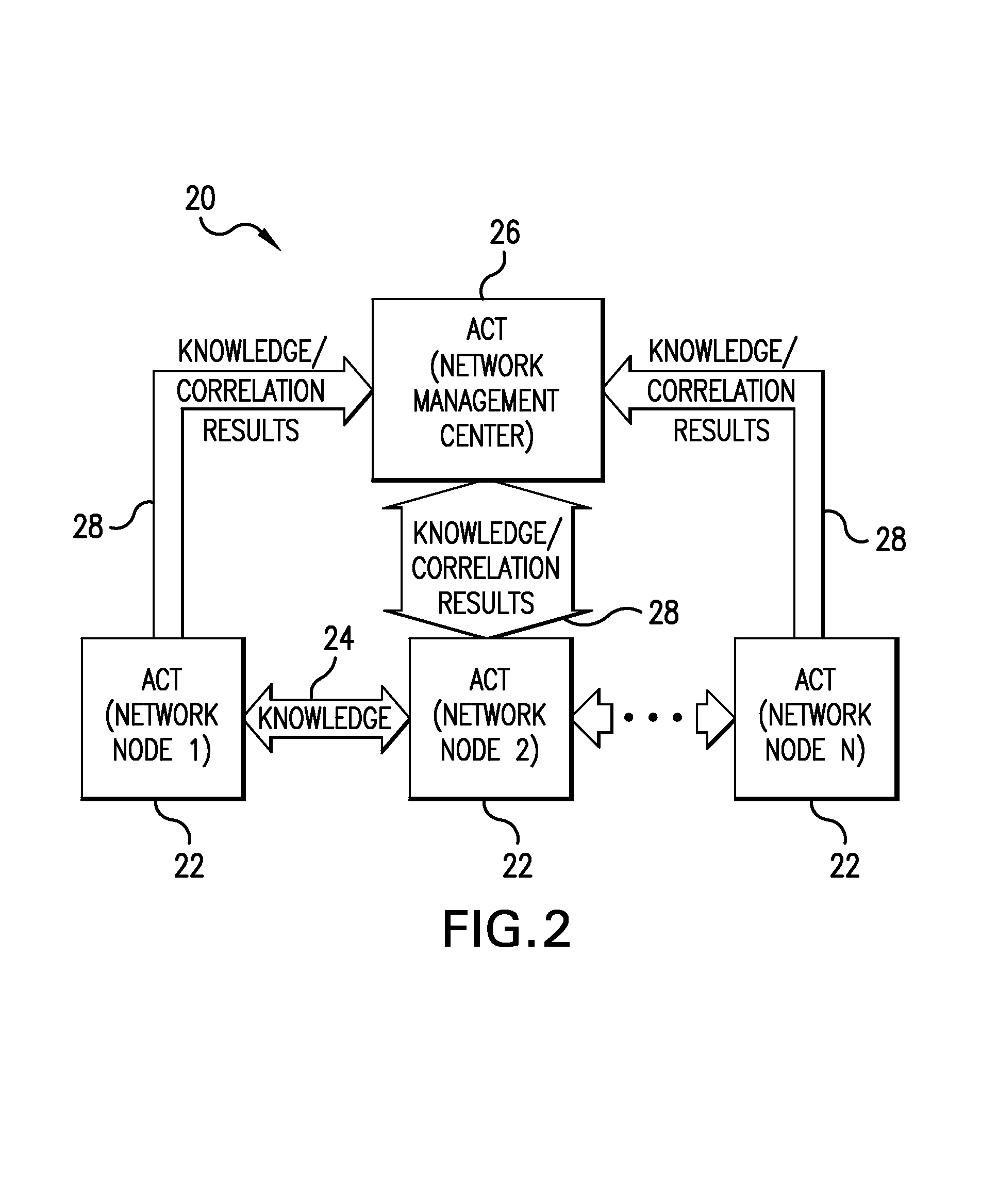
System and method for fault diagnosis using distributed alarm correlation
ActiveUS7257744B2Error detection/correctionDigital computer detailsAlarm correlationReal-time computing
A system and method for diagnosing faults in a communication network using a distributed alarm correlation system. The alarm correlation system may include node-level alarm correlation tools (ACTs) located at nodes in the network to provide node-level alarm correlation producing node-level correlation results. The node-level ACTs may share diagnostic knowledge with other node-level alarm correlation tools at other nodes. Each of the node-level ACTs may also share the diagnostic knowledge and the node-level correlation results with a higher-level ACT. The higher-level ACT may provide higher-level alarm correlation to produce higher-level correlation results.
Owner:SUBCOM LLC
Failure detection and fault tolerance method and failure detection and fault tolerance system for real-time cloud platform
ActiveCN103716182ANo loss of stateComprehensive detection effectData switching networksFault toleranceReal time services
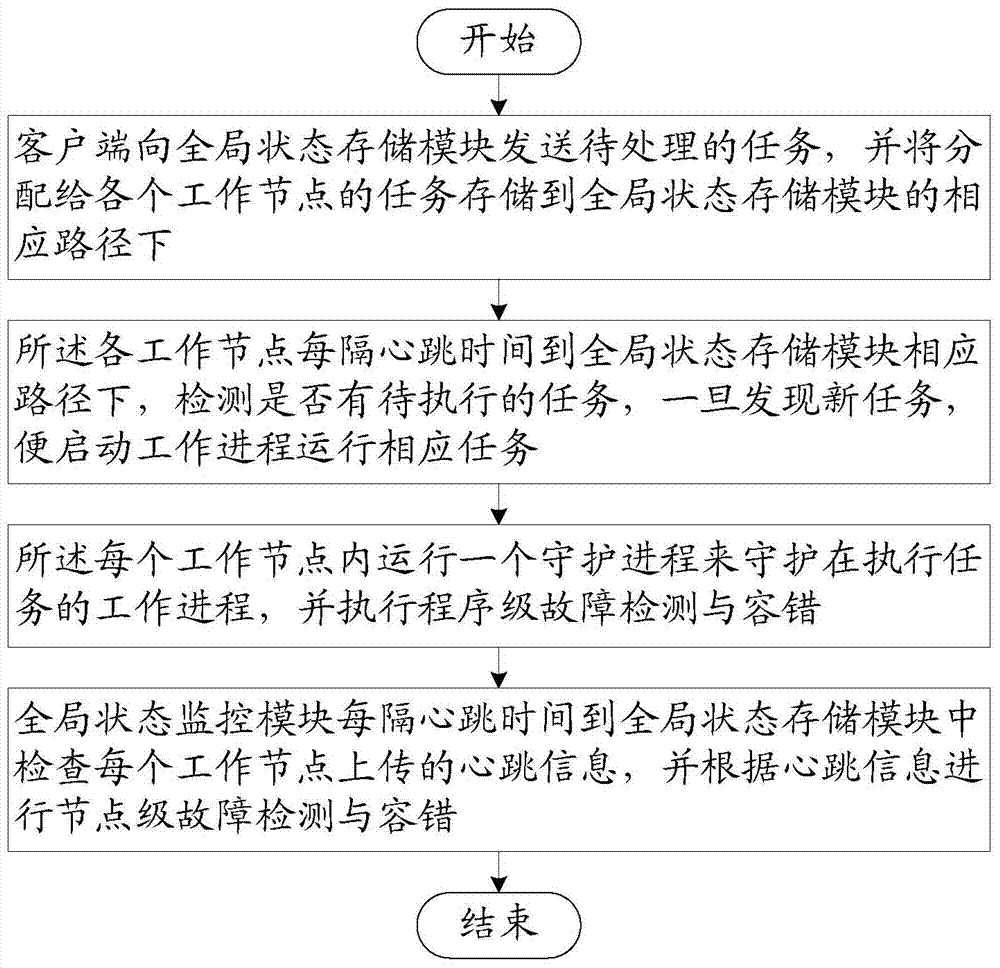
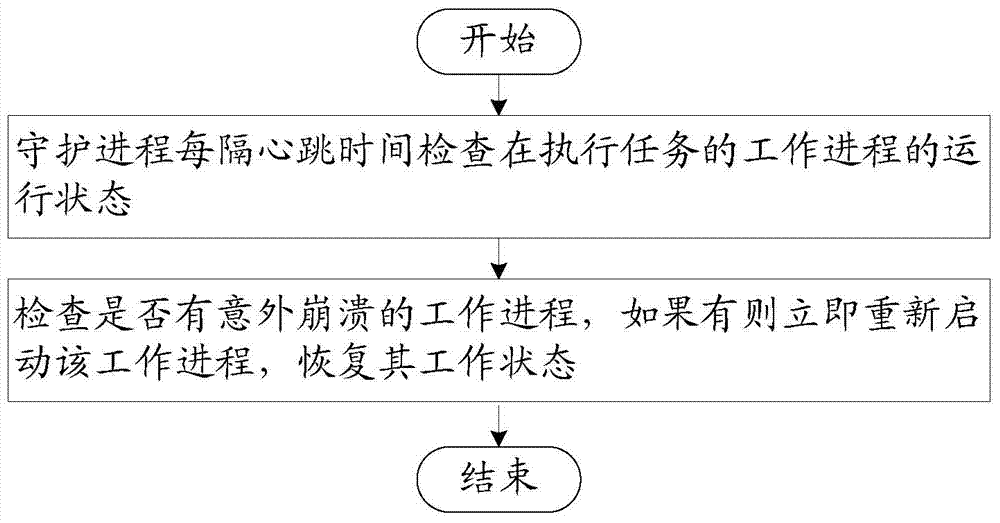
The invention relates to a failure detection and fault tolerance method and a failure detection and fault tolerance system for a real-time cloud platform. The system comprises a client used for sending a command, summiting a task and storing tasks assigned to working nodes in corresponding paths, a global state monitoring module used for monitoring the operation state of the working nodes, carrying out node-level failure detection and fault tolerance according to heartbeat information uploaded by the working nodes and performing migration of a task in a failure node, a global state storage module used for storing the working state and heartbeat information of the global state monitoring module and the working nodes, and working nodes used for performing a task, running a daemon process to guard a work process and performing program-level failure detection and fault tolerance. State information of a whole cluster is all stored in a Zookeeper system, a stateless architecture of the nodes is realized, a node failure does not cause state loss, the system has a perfect failure detection and fault tolerance mechanism, multilevel fault tolerance is realized, and uninterrupted operation of real-time services is guaranteed.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
System and Method for Implementing NUMA-Aware Reader-Writer Locks
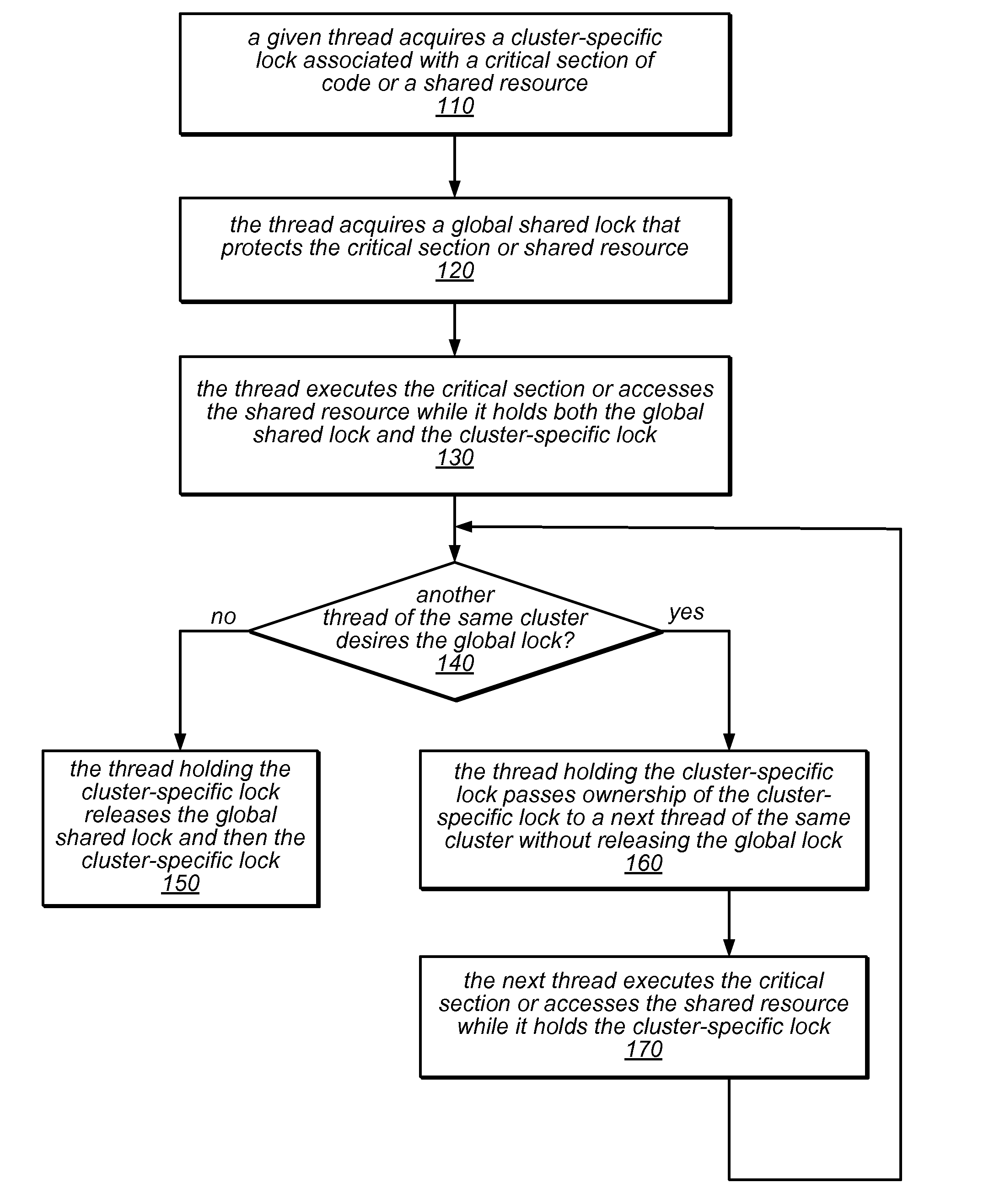
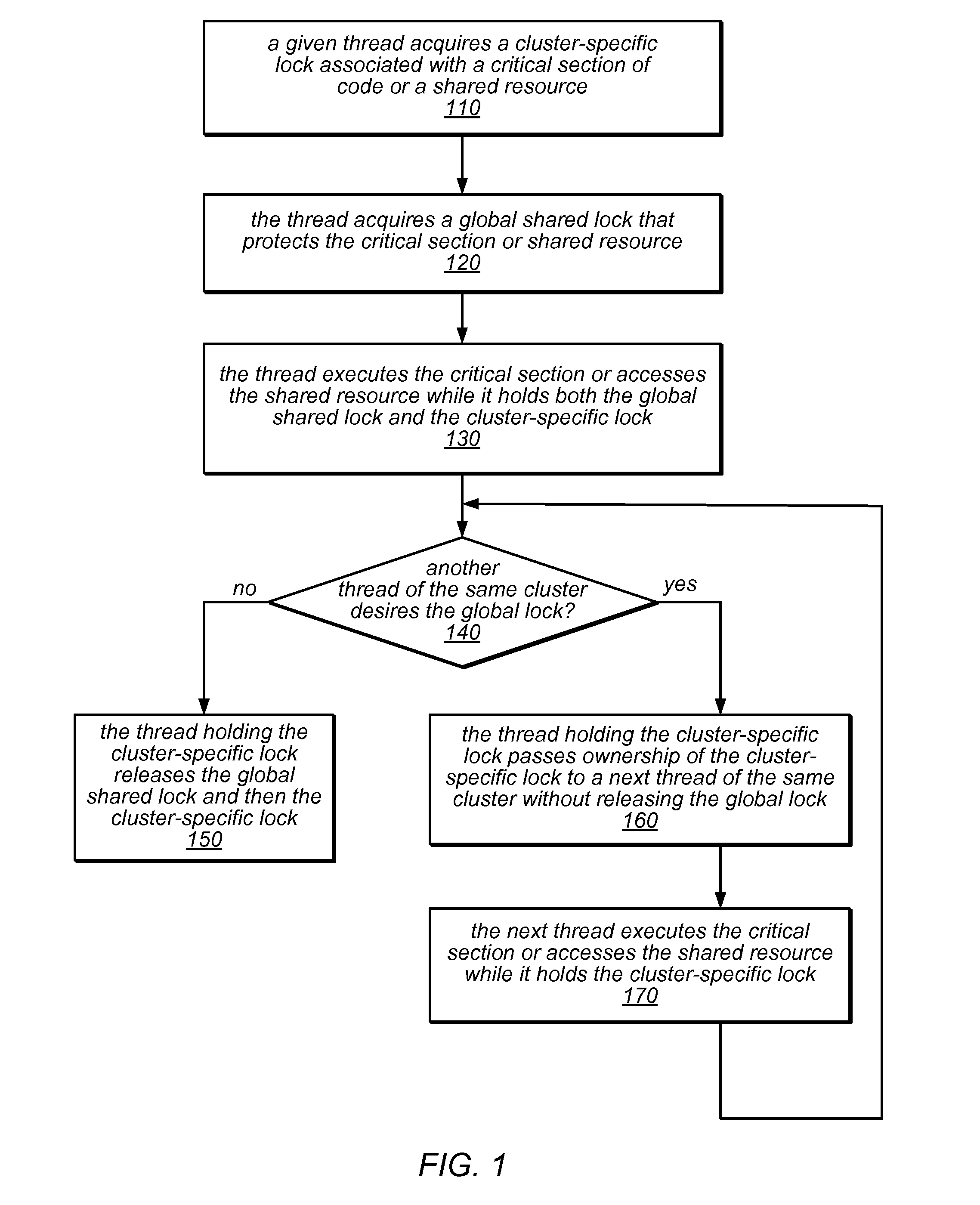
ActiveUS20130290967A1Reduce probabilityReduce traffic problemsMultiprogramming arrangementsMemory systemsCritical sectionParallel computing
NUMA-aware reader-writer locks may leverage lock cohorting techniques to band together writer requests from a single NUMA node. The locks may relax the order in which the lock schedules the execution of critical sections of code by reader threads and writer threads, allowing lock ownership to remain resident on a single NUMA node for long periods, while also taking advantage of parallelism between reader threads. Threads may contend on node-level structures to get permission to acquire a globally shared reader-writer lock. Writer threads may follow a lock cohorting strategy of passing ownership of the lock in write mode from one thread to a cohort writer thread without releasing the shared lock, while reader threads from multiple NUMA nodes may simultaneously acquire the shared lock in read mode. The reader-writer lock may follow a writer-preference policy, a reader-preference policy or a hybrid policy.
Owner:ORACLE INT CORP
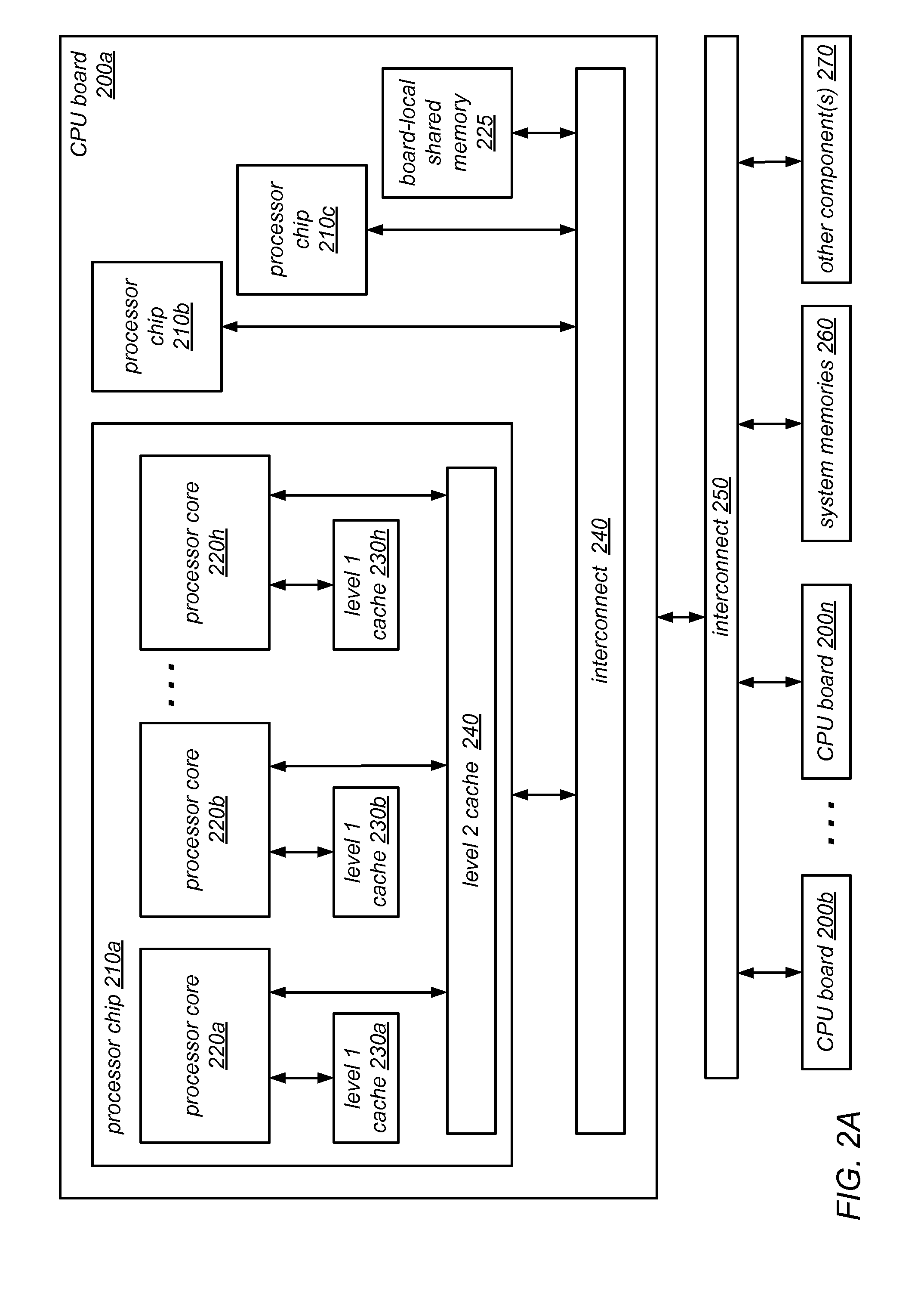
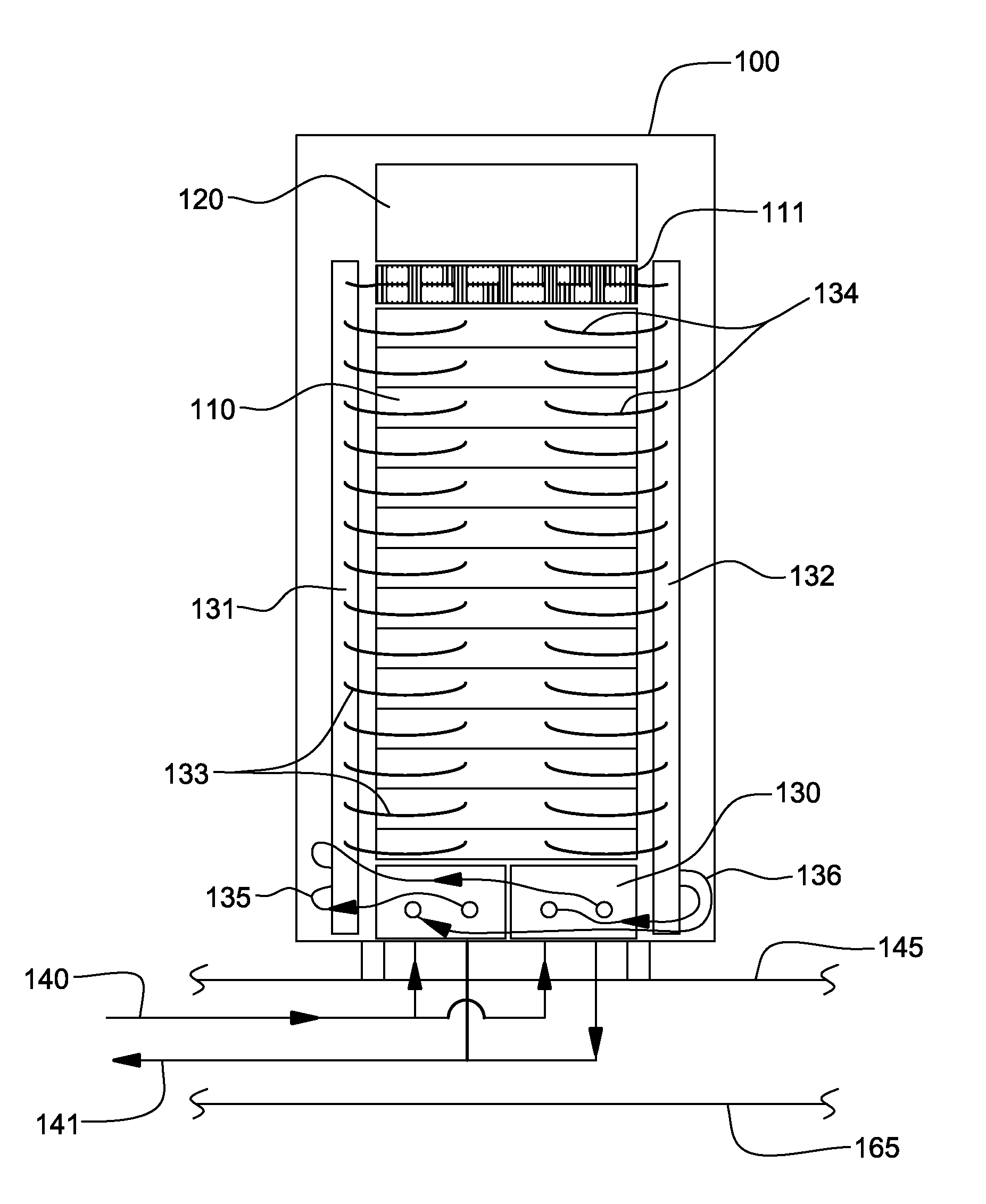
Frame level partial cooling boost for drawer and/or node level processors
InactiveUS6970355B2Small dimensionAvoid the needDomestic cooling apparatusSemiconductor/solid-state device detailsSystems designEngineering
A hybrid cooling system is provided which is particularly useful for cooling electronic circuit components disposed on circuit boards arranged in a plurality of drawers within a cabinet or frame. Air cooling is provided locally with a supplementary, auxiliary, or secondary cooling system being provided at more distant frame level locations. This configuration permits optimal sizing of the respective hybrid cooling system components without negatively impacting the coefficient of performance (COP). Hybrid heat sinks are employed to accommodate the hybrid cooling system design.
Owner:IBM CORP
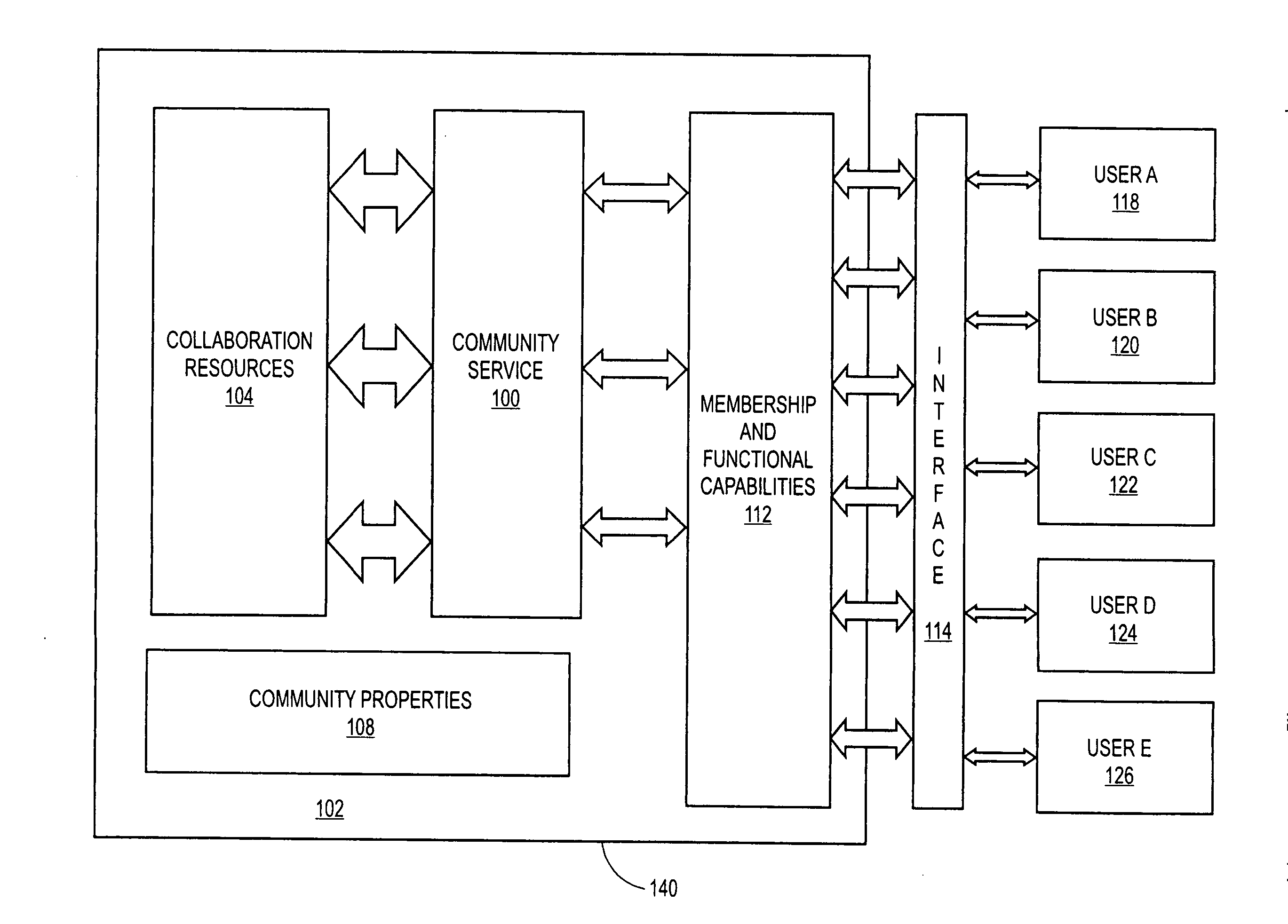
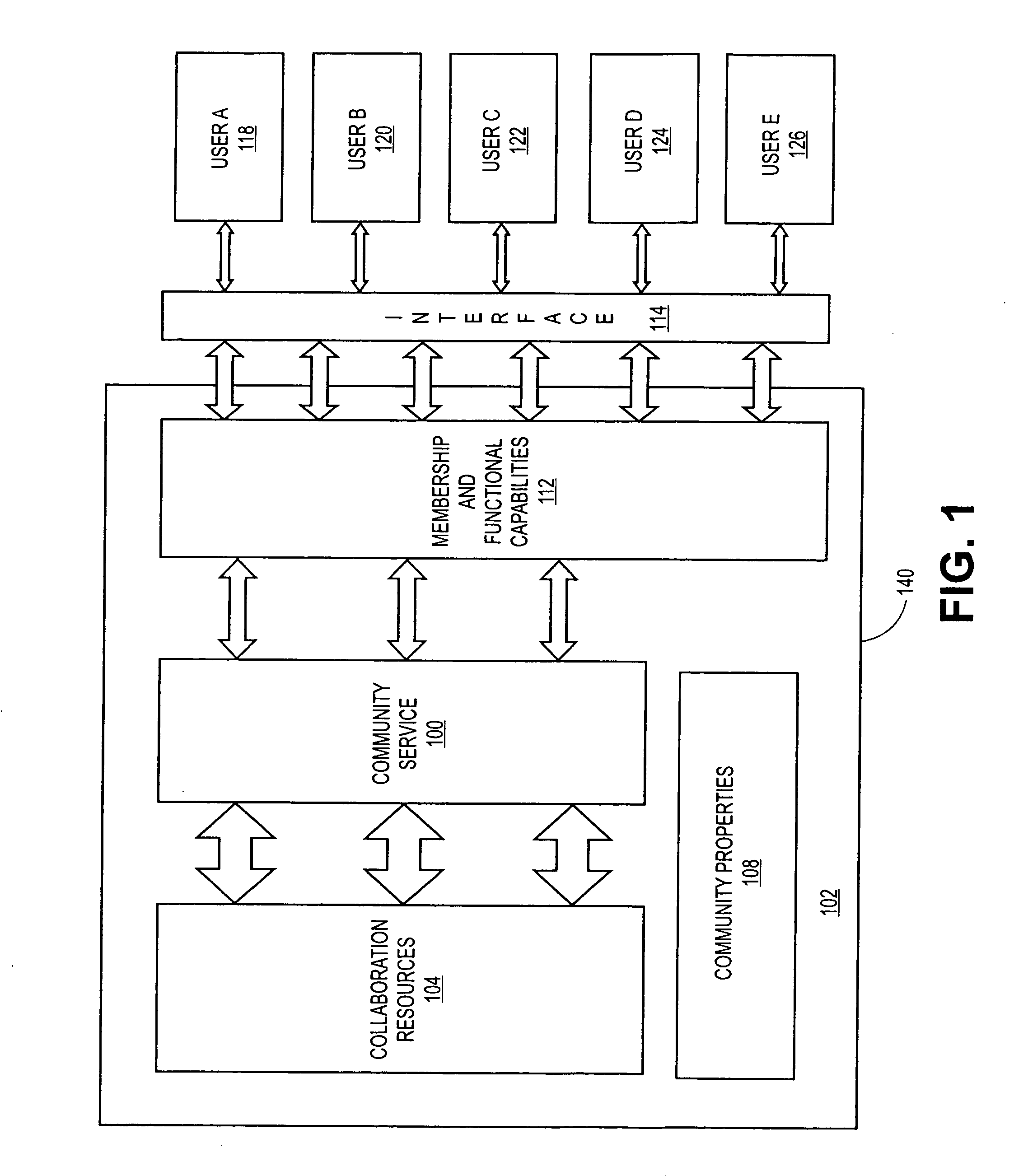
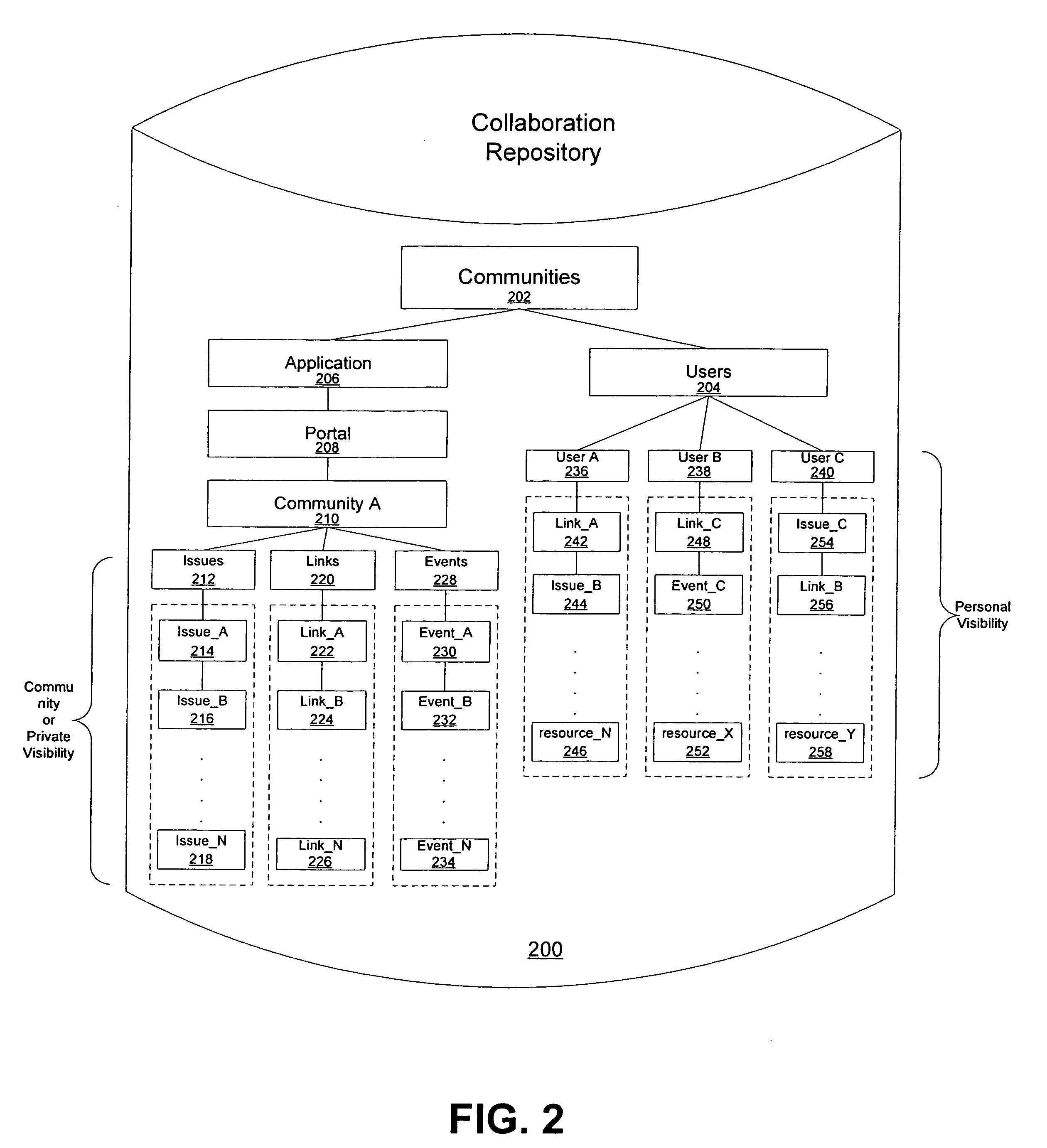
System and method for providing security in a communities framework
ActiveUS20070113187A1Provide securityAvoid accessDigital data processing detailsUser identity/authority verificationCollaborative computingSecurity policy
Systems and methods are disclosed for providing security for a communities framework in a collaborative computing environment. A community can be provided for maintaining user membership during collaboration. The community can contain various collaboration resources, community services and members having access to the resources and services. A first layer of security can be implemented via membership and functional capabilities. Members can be assigned to various membership capabilities and these membership capabilities can be mapped to functional capabilities in order to control access to the resources by the various members. A second layer of security can be implemented via entitlements and security policies applied to the content repository. Entitlements can be applied at a node level of a content repository. Each node can be evaluated when operations are requested for it.
Owner:ORACLE INT CORP
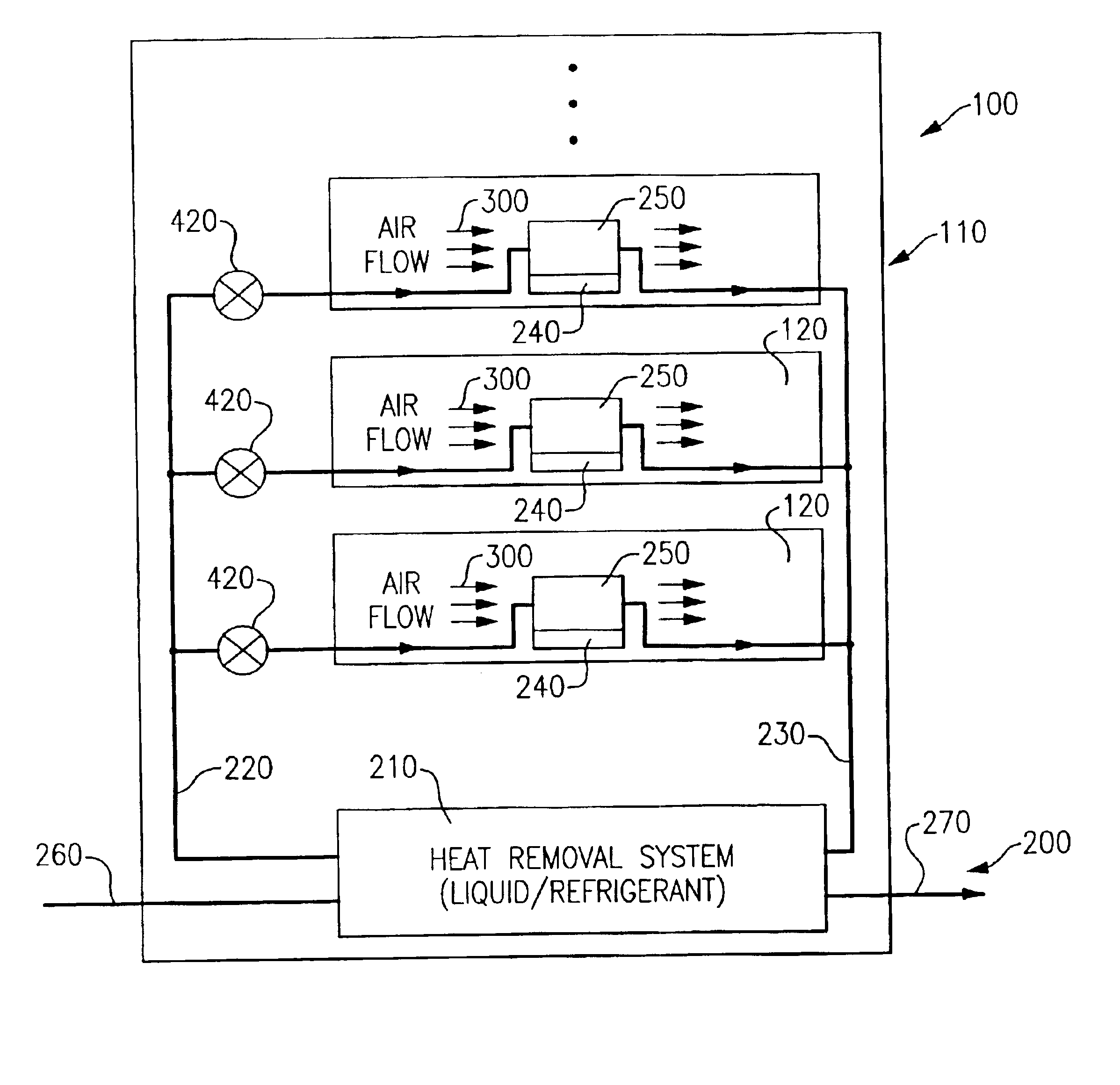
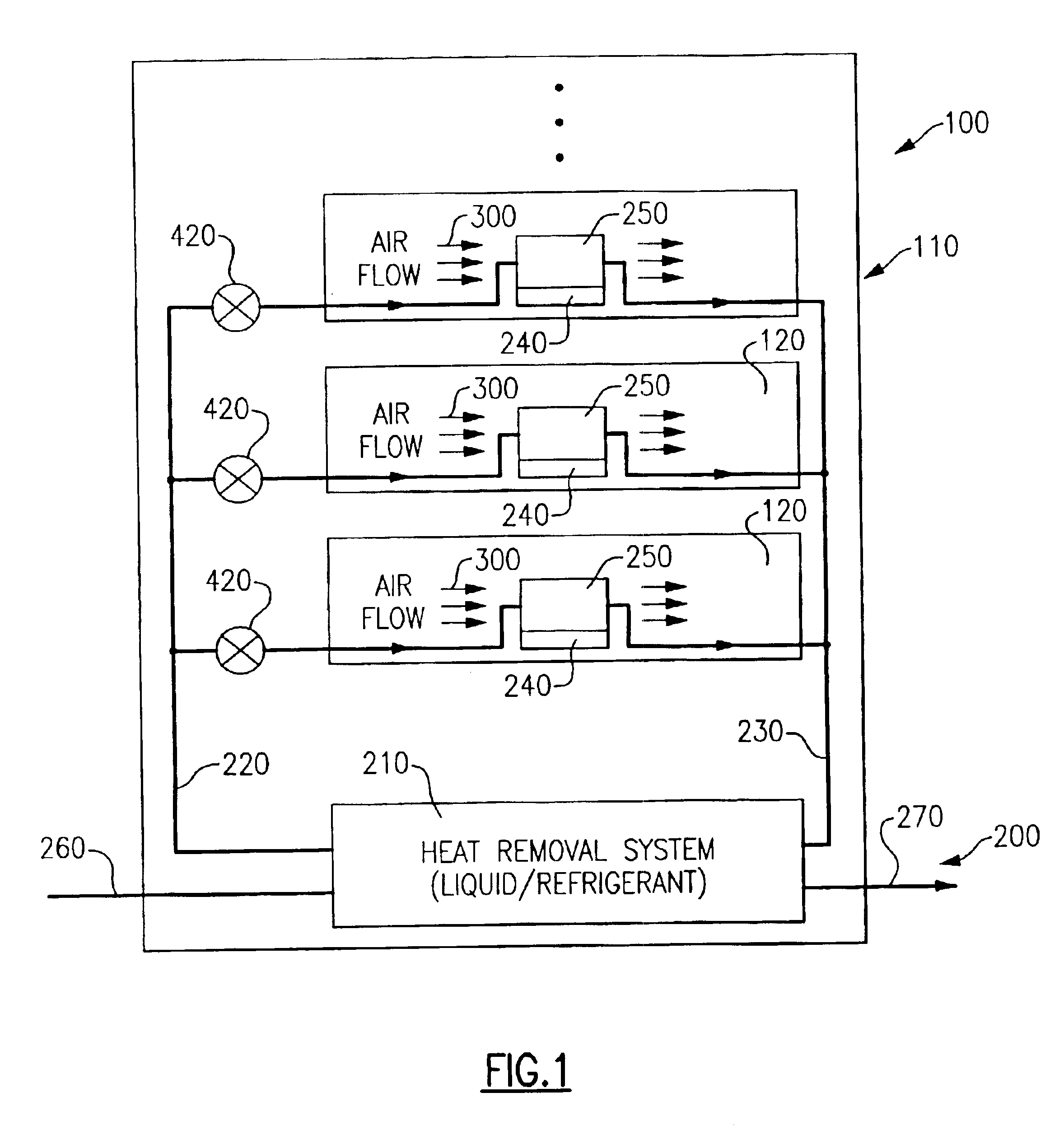
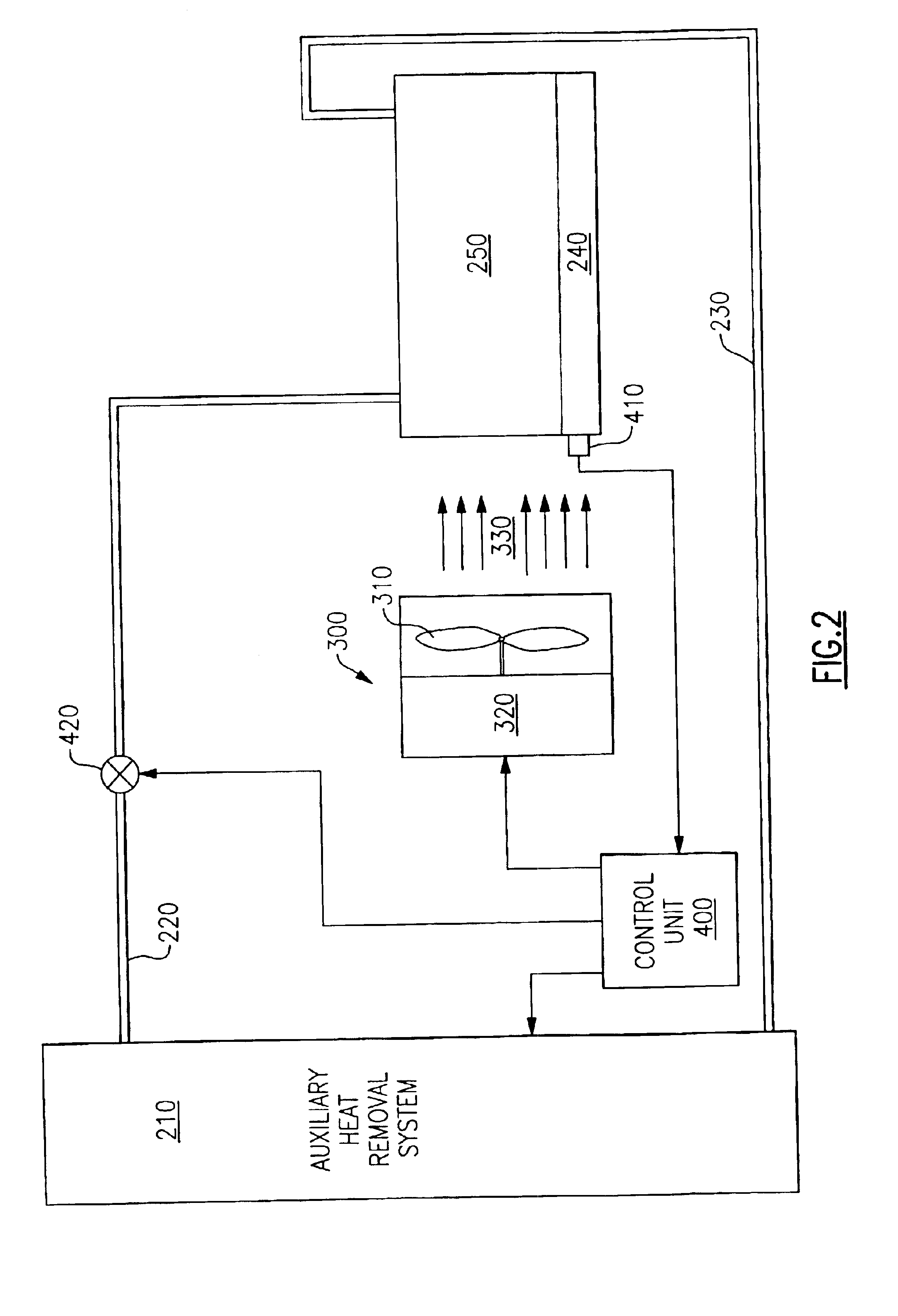
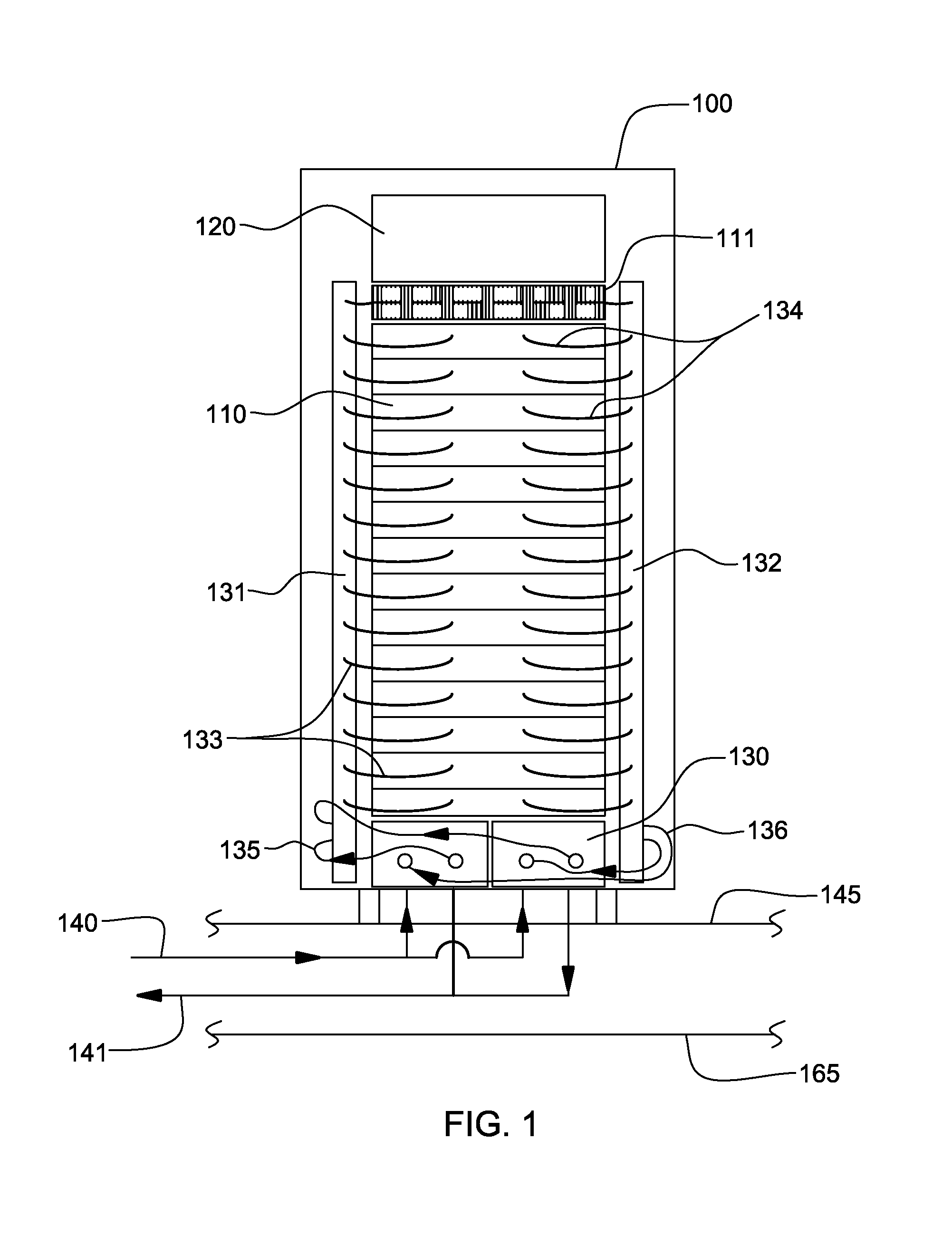
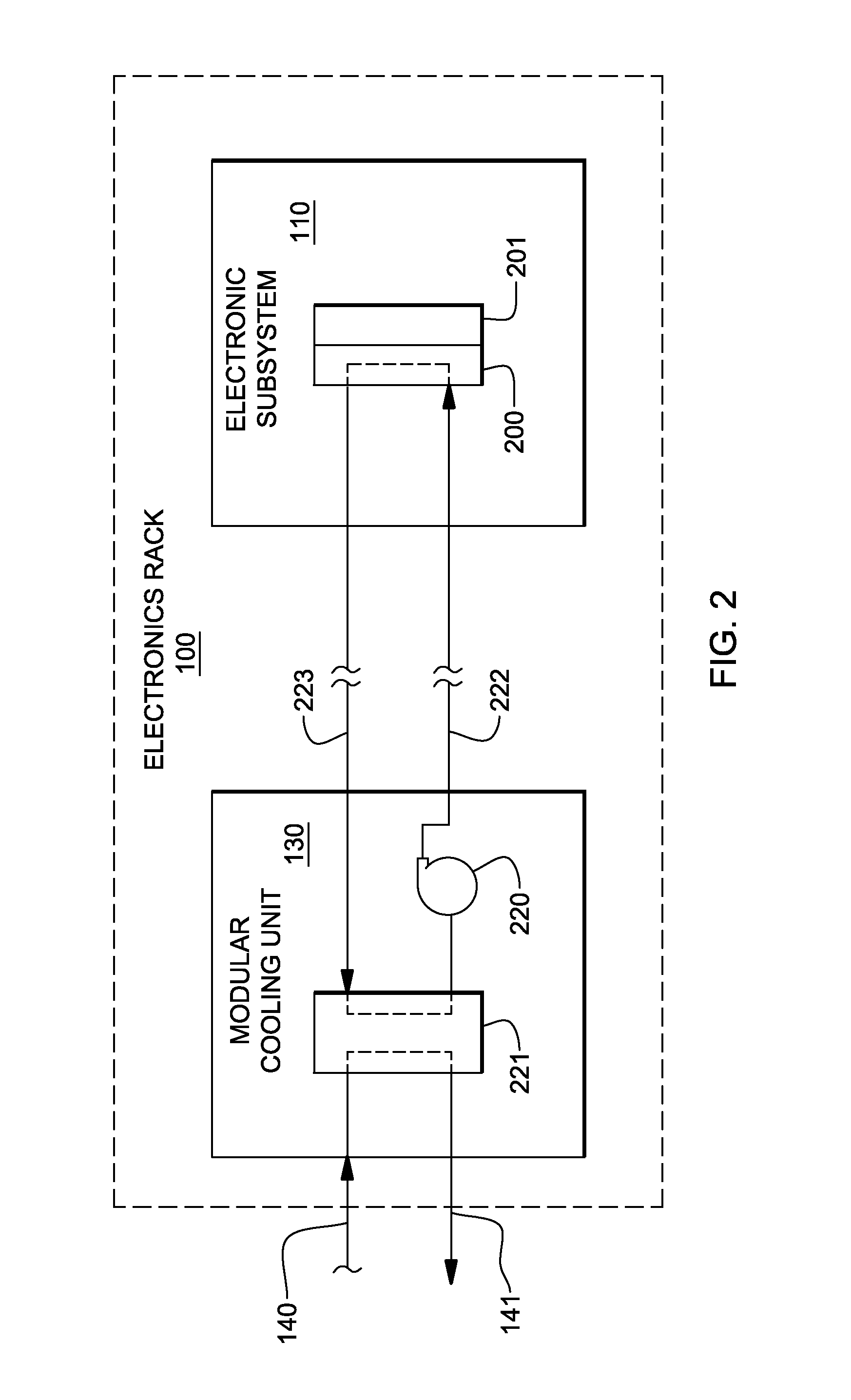
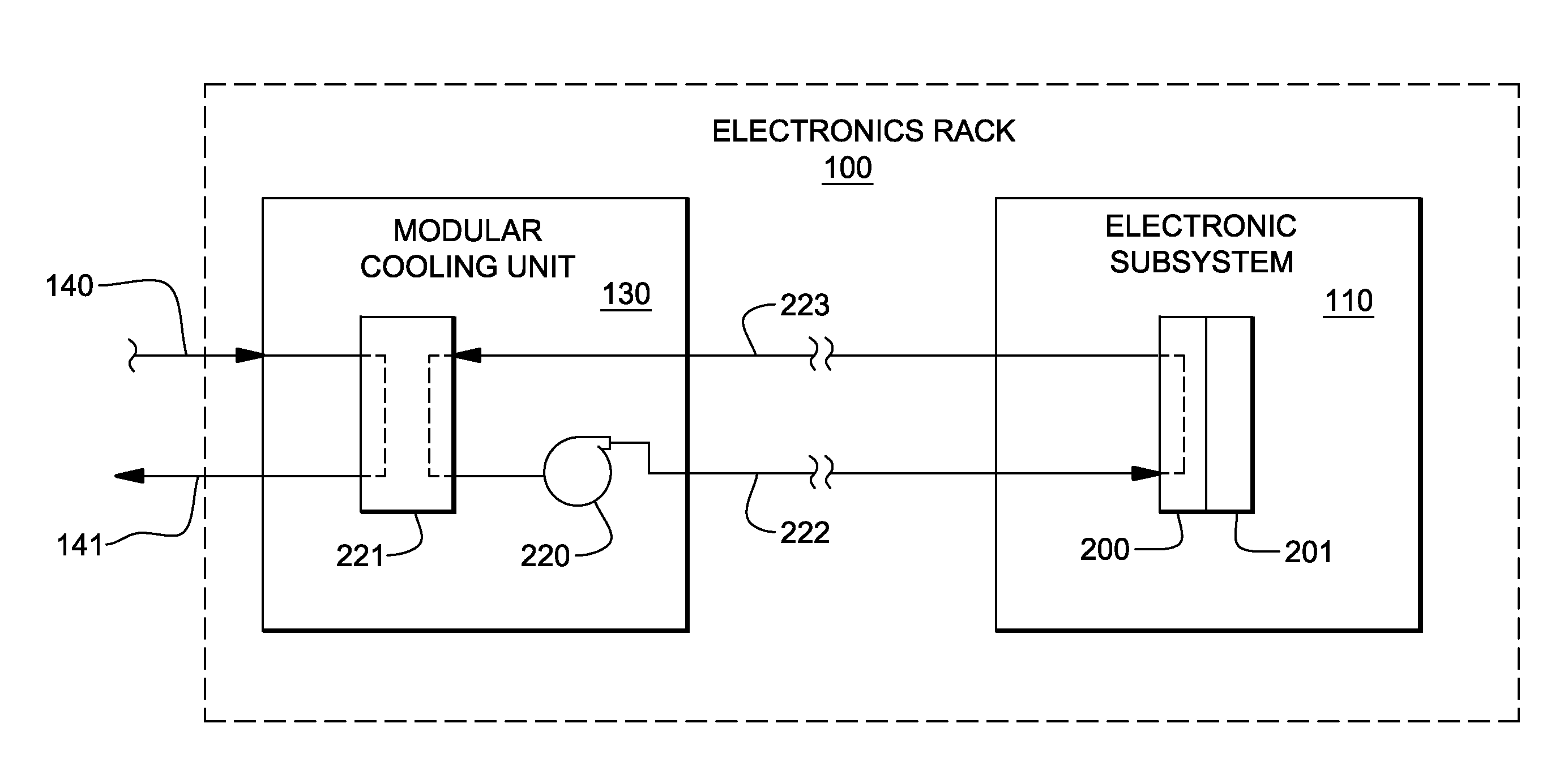
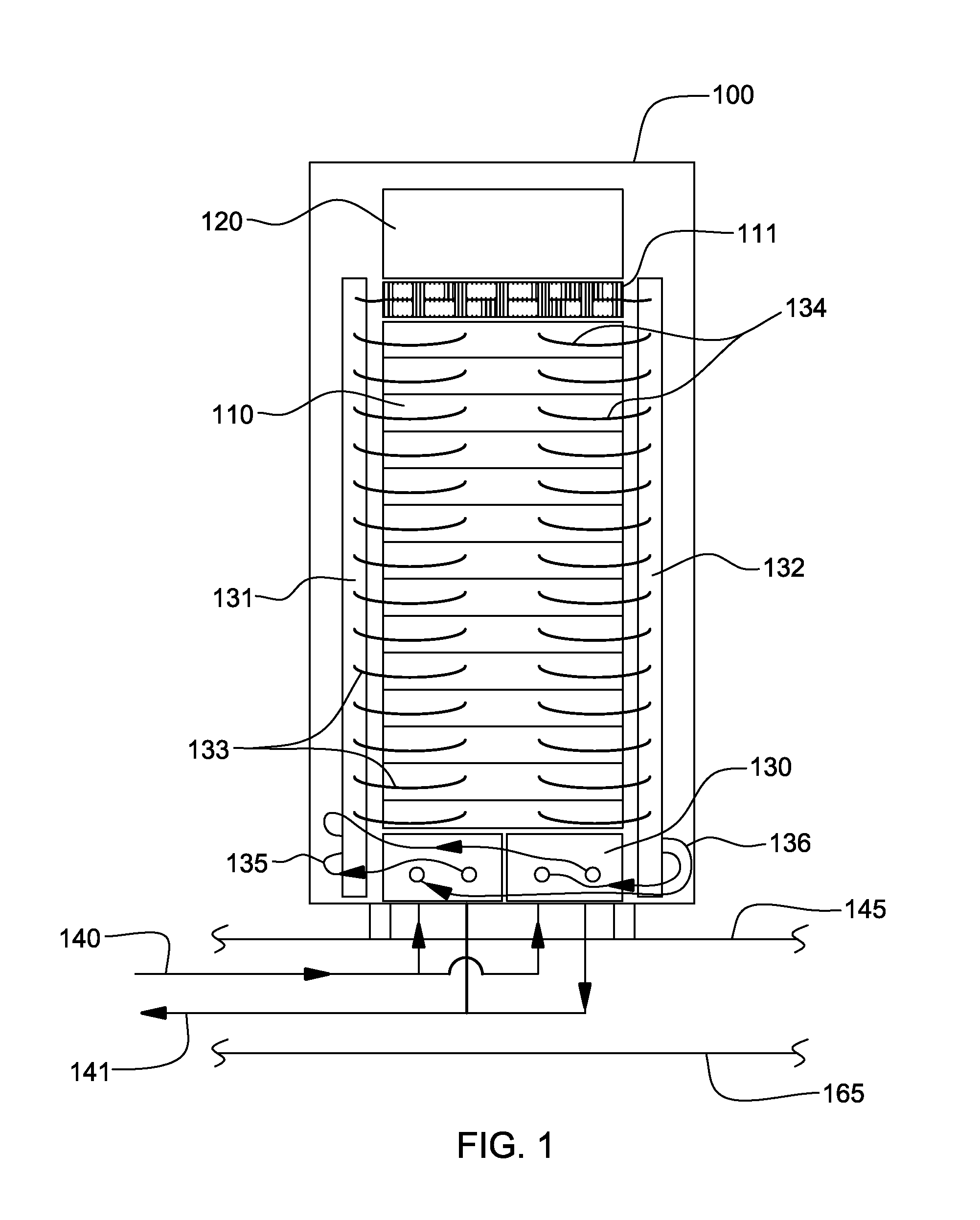
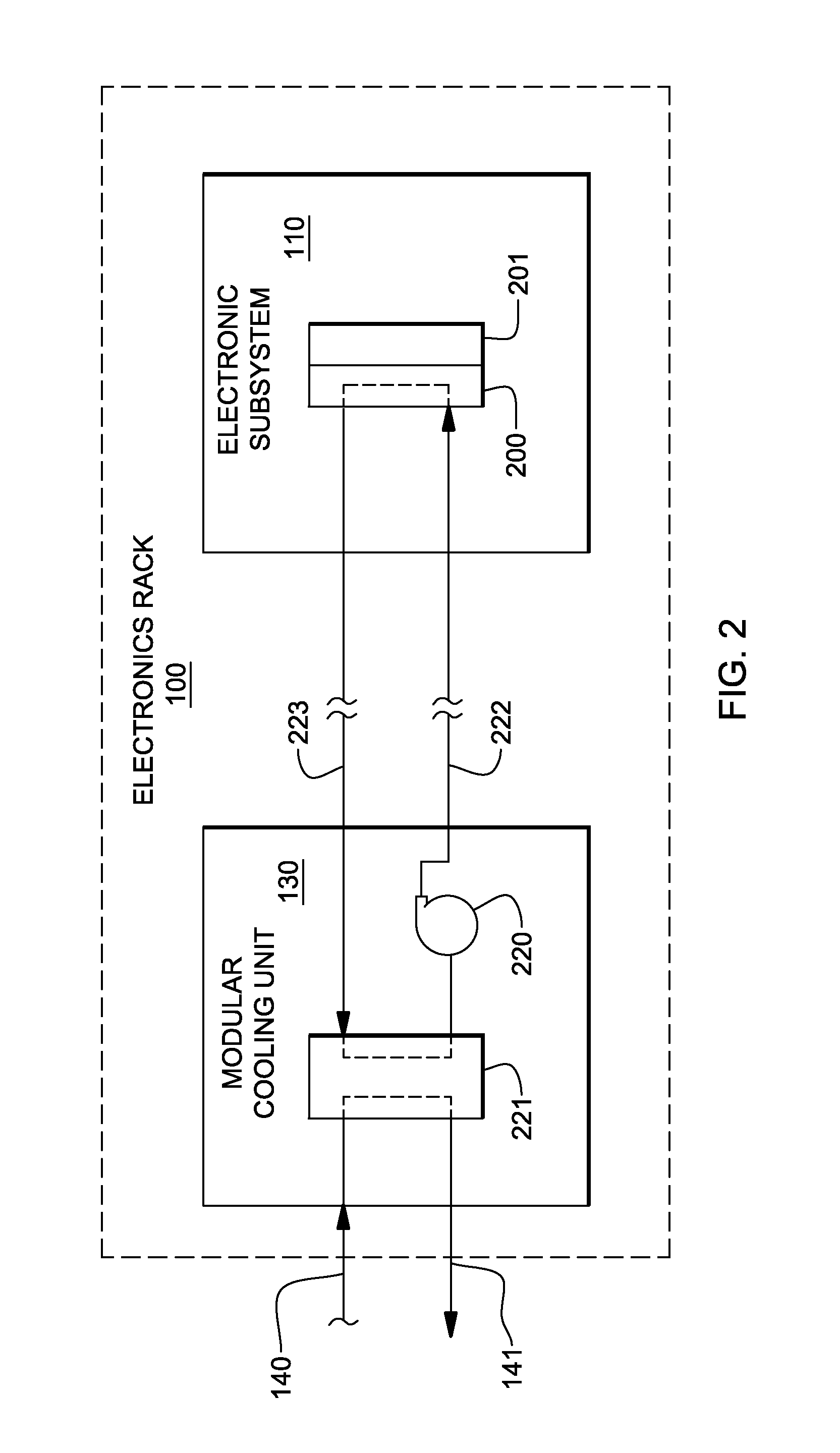
Valve controlled, node-level vapor condensation for two-phase heat sink(s)
ActiveUS20130027884A1Easy to condenseEasy extractionDigital data processing detailsIndirect heat exchangersSteam condensationAutomatic control
A cooling apparatus and method are provided for cooling one or more electronic components of an electronic subsystem of an electronics rack. The cooling apparatus includes a heat sink, which is configured to couple to an electronic component, and which includes a coolant-carrying channel for coolant to flow therethrough. The coolant provides two-phase cooling to the electronic component, and is discharged from the heat sink as coolant exhaust which comprises coolant vapor to be condensed. The cooling apparatus further includes a node-level condensation module, associated with the electronic subsystem, and coupled in fluid communication with the heat sink to receive the coolant exhaust from the heat sink. The condensation module is liquid-cooled, and facilitates condensing of the coolant vapor in the coolant exhaust. A controller automatically controls the liquid-cooling of the heat sink and / or the liquid-cooling of the node-level condensation module.
Owner:IBM CORP
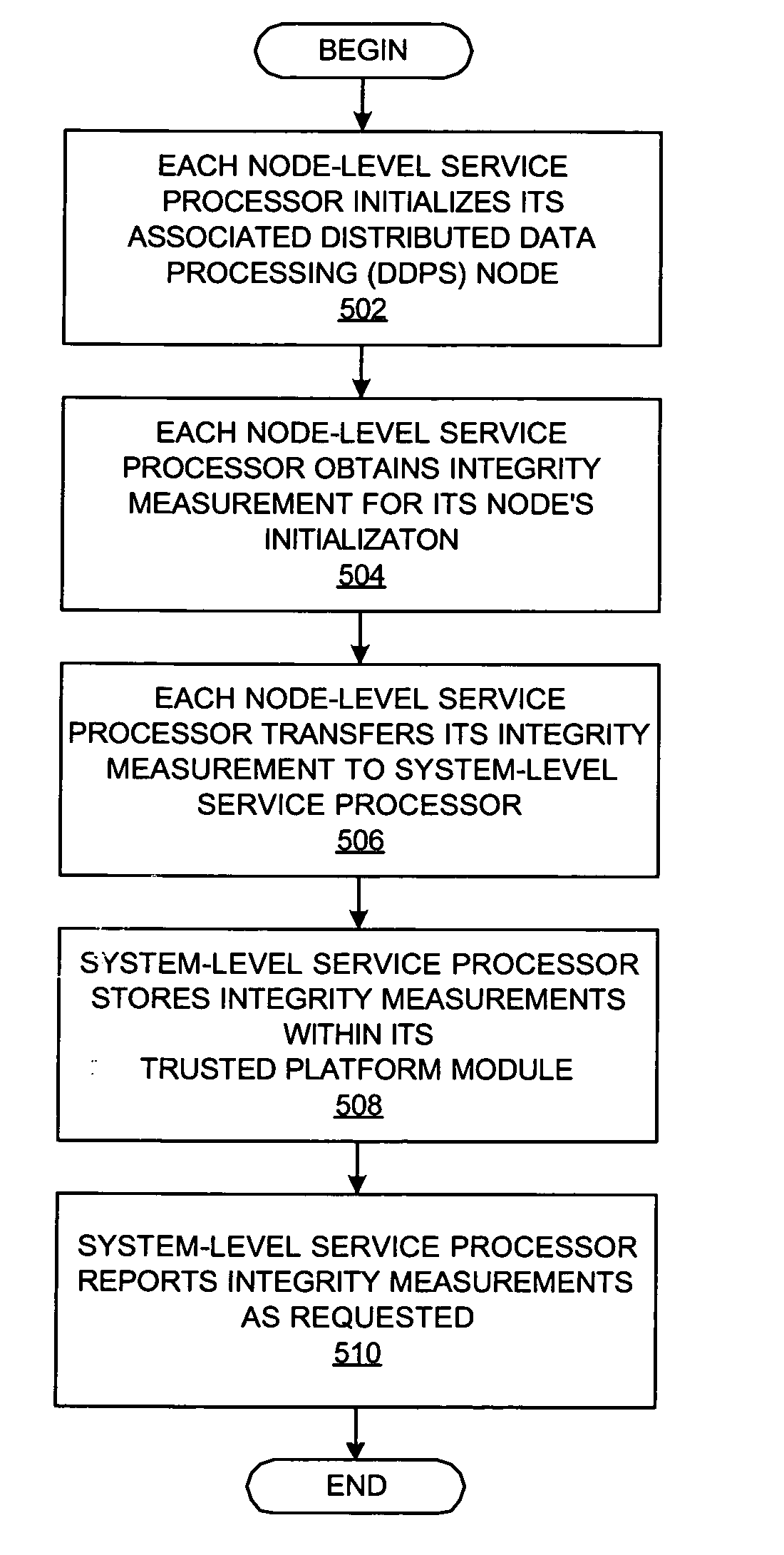
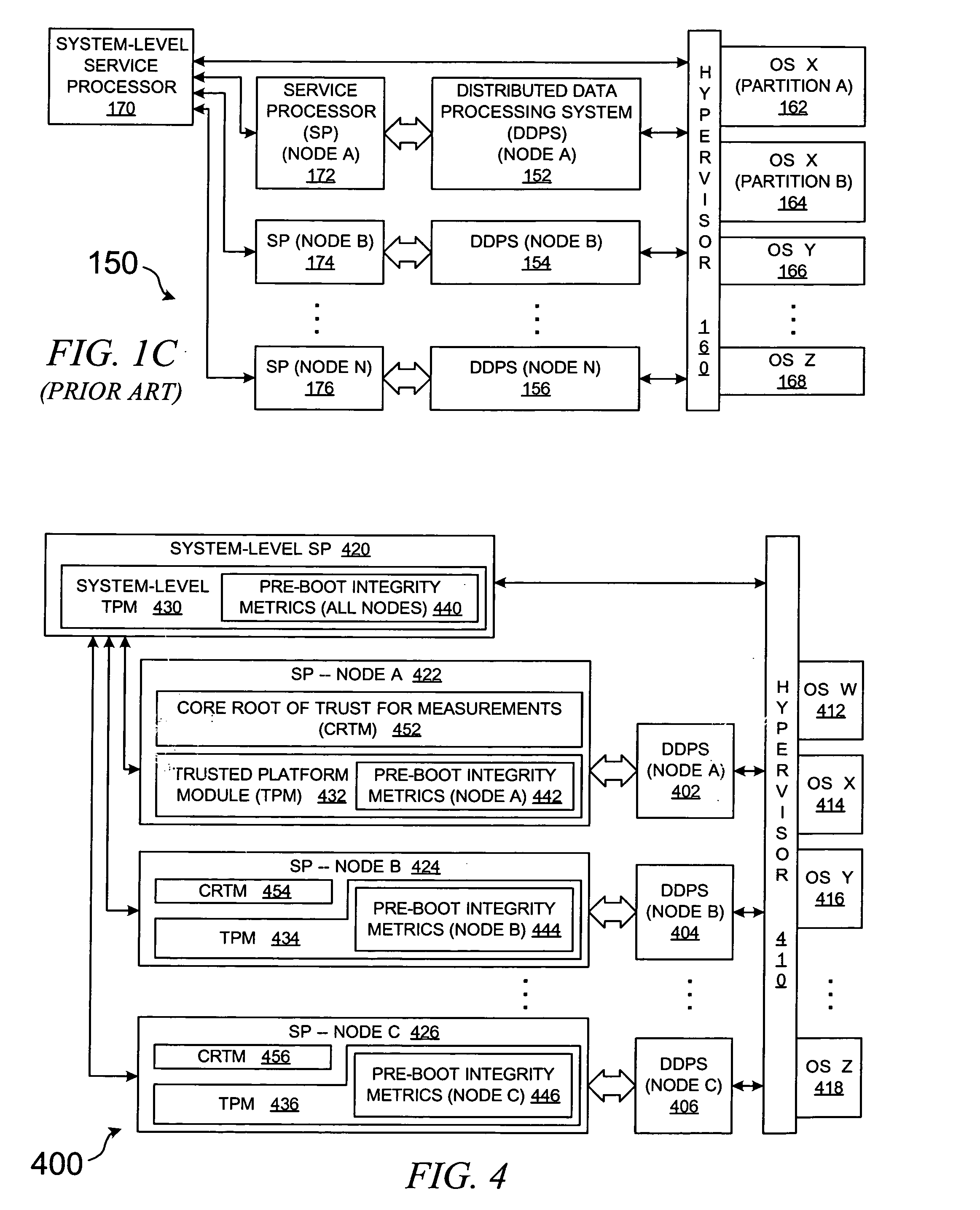
Method and system for hierarchical platform boot measurements in a trusted computing environment
InactiveUS20050246525A1Memory loss protectionError detection/correctionData processing systemOperational system
An architecture for a distributed data processing system comprises a system-level service processor along with one or more node-level service processors; each are uniquely associated with a node, and each is extended to comprise any components that are necessary for operating the nodes as trusted platforms, such as a TPM and a CRTM in accordance with the security model of the Trusted Computing Group. These node-level service processors then inter-operate with the system-level service processor, which also contains any components that are necessary for operating the system as a whole as a trusted platform. A TPM within the system-level service processor aggregates integrity metrics that are gathered by the node-level service processors, thereafter reporting integrity metrics as requested, e.g., to a hypervisor, thereby allowing a large distributed data processing system to be validated as a trusted computing environment while allowing its highly parallelized initialization process to proceed.
Owner:IBM CORP
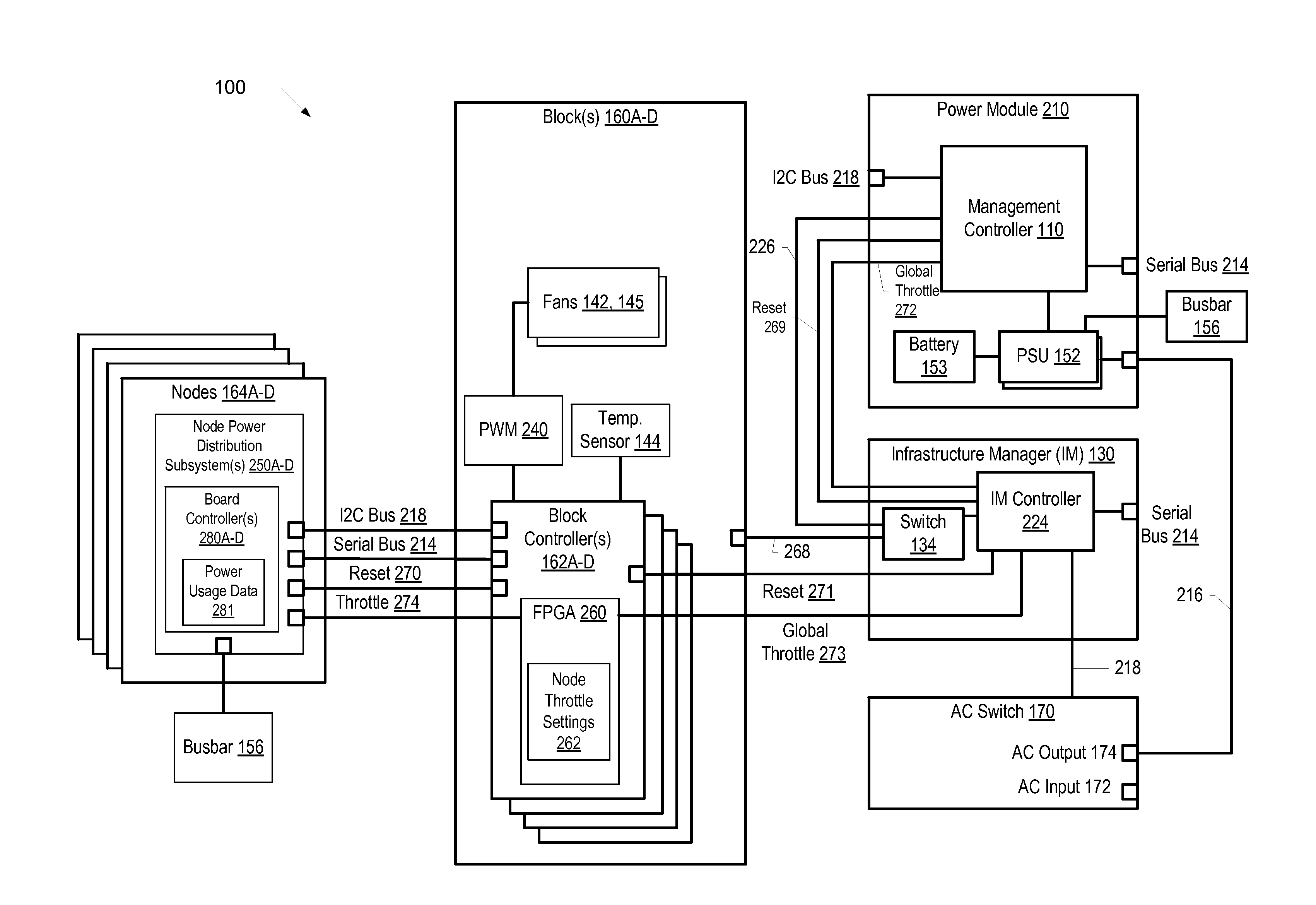
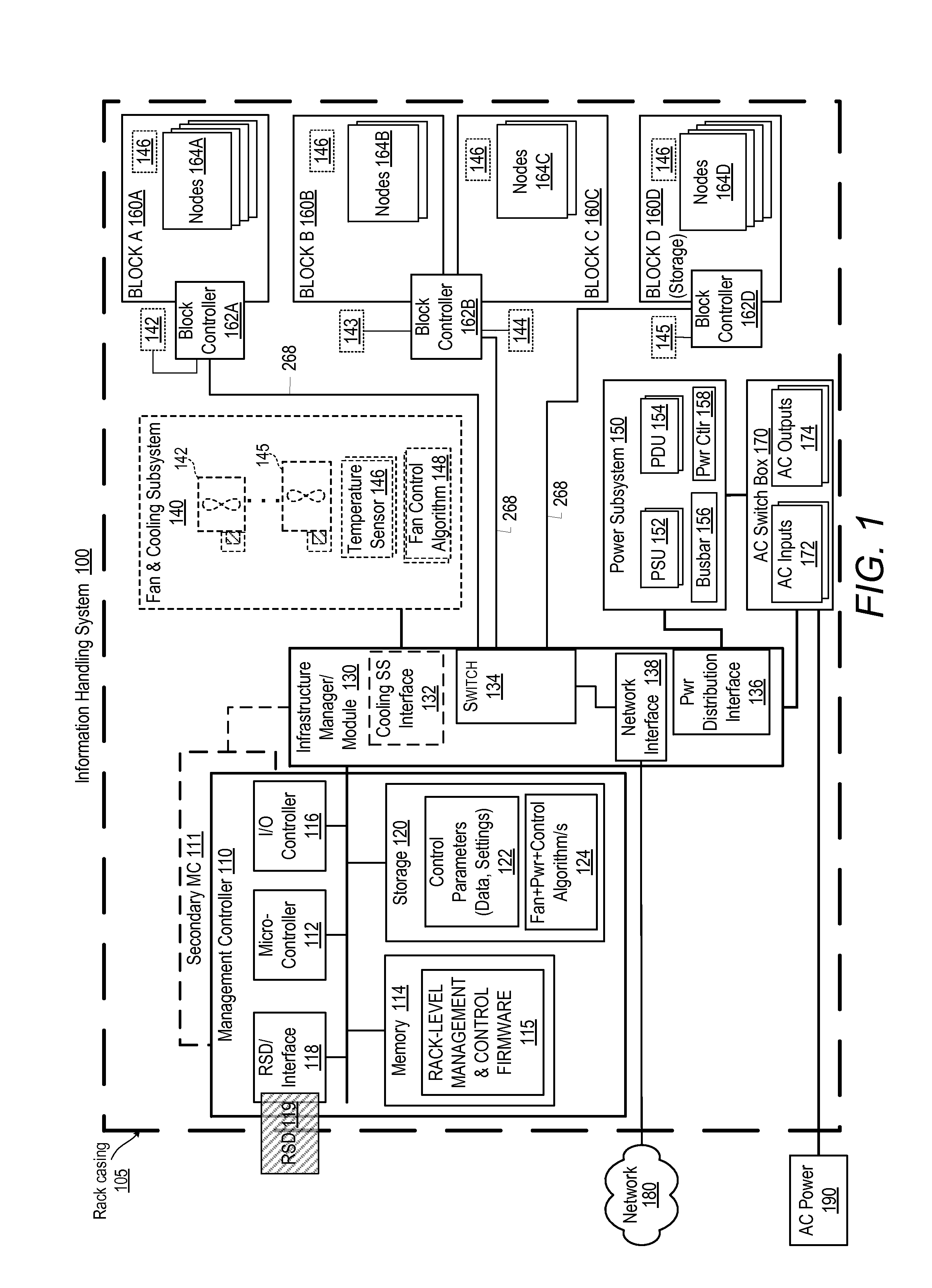
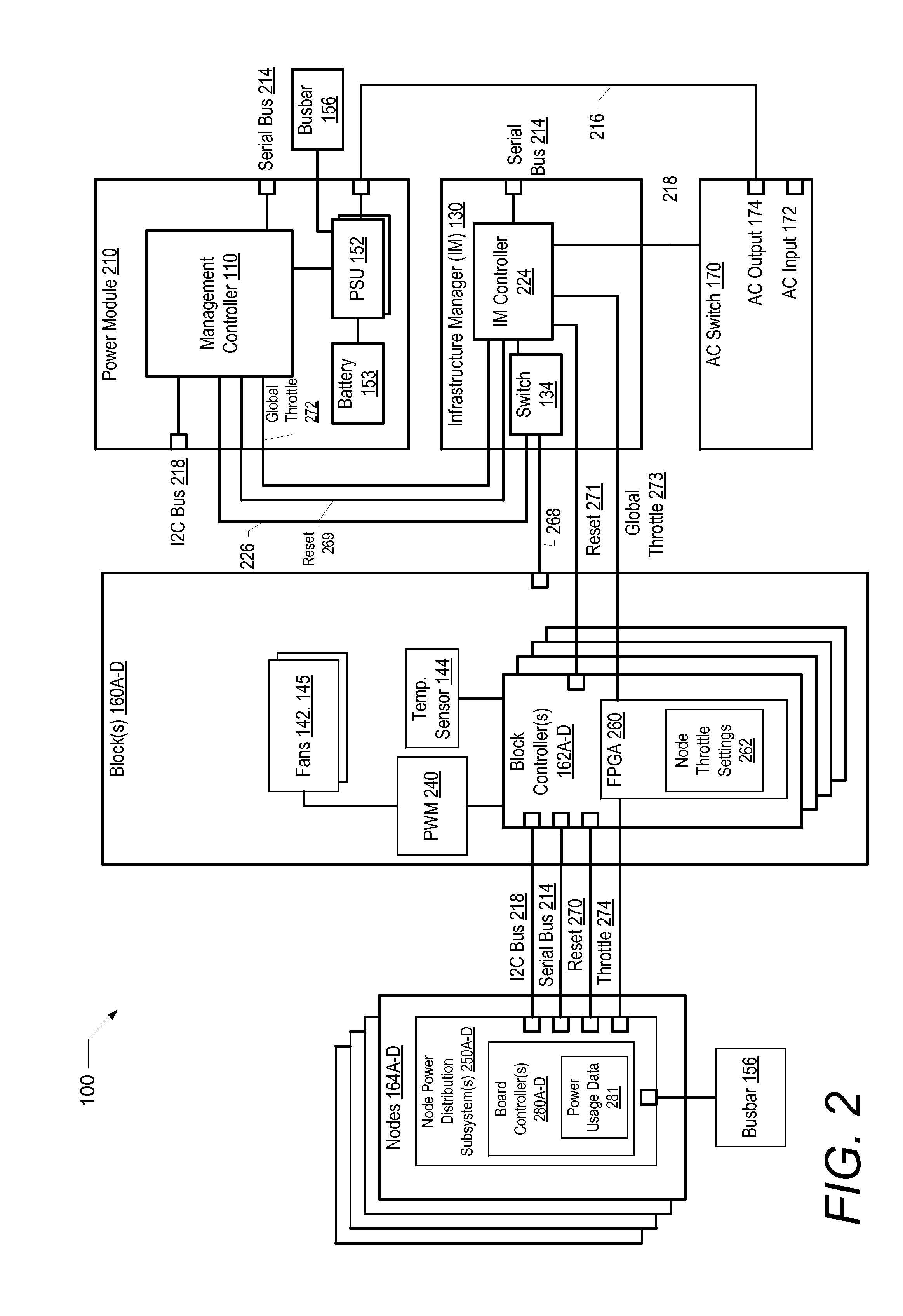
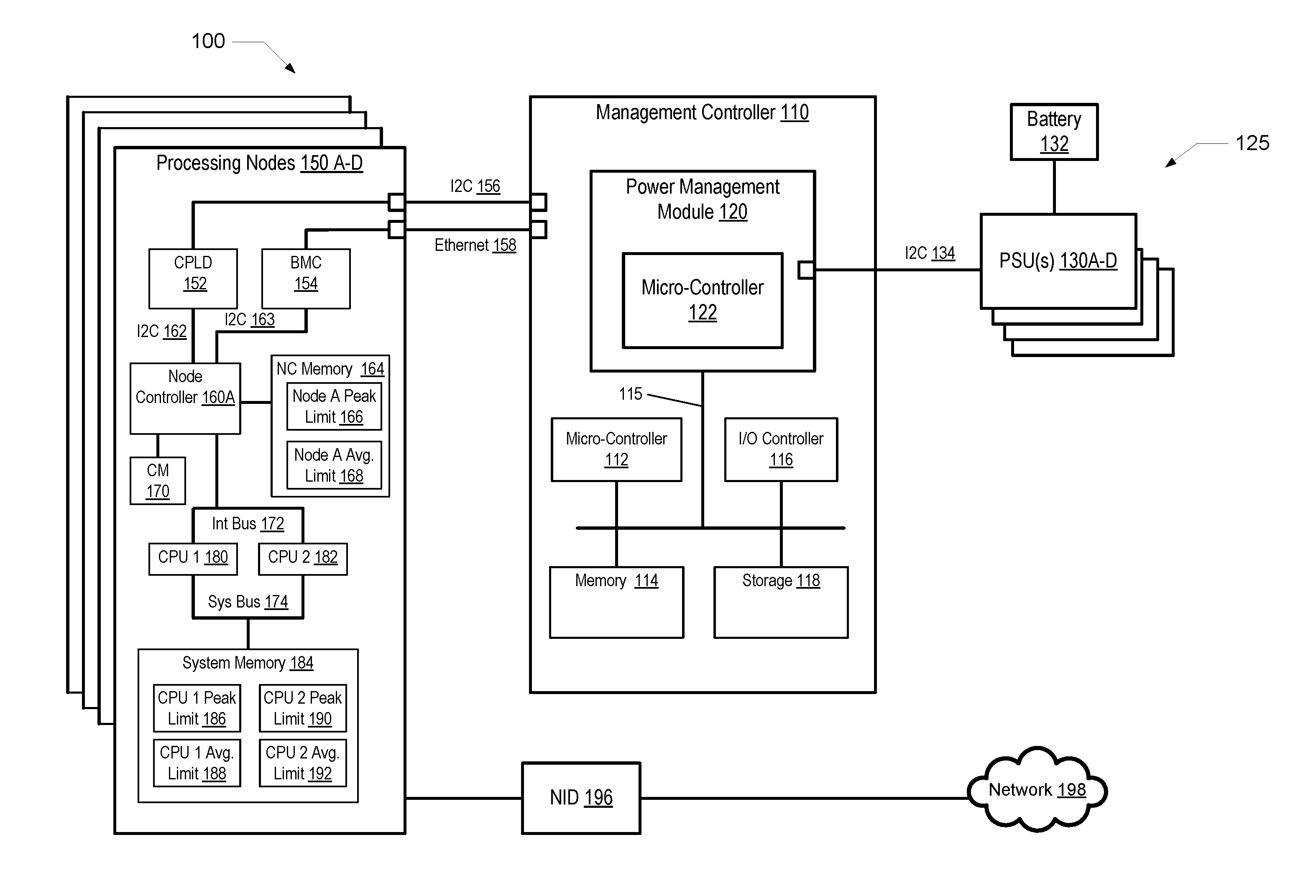
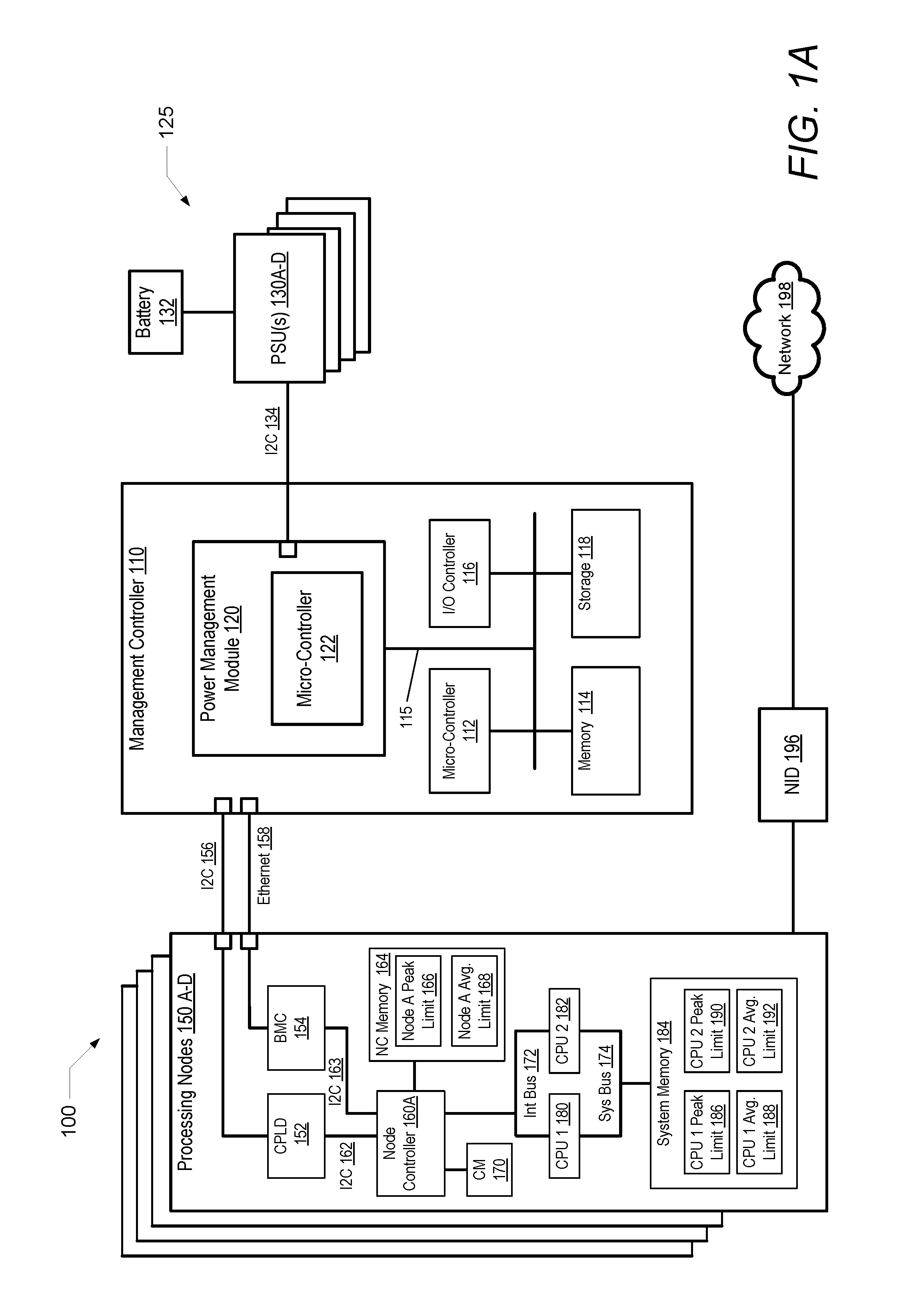
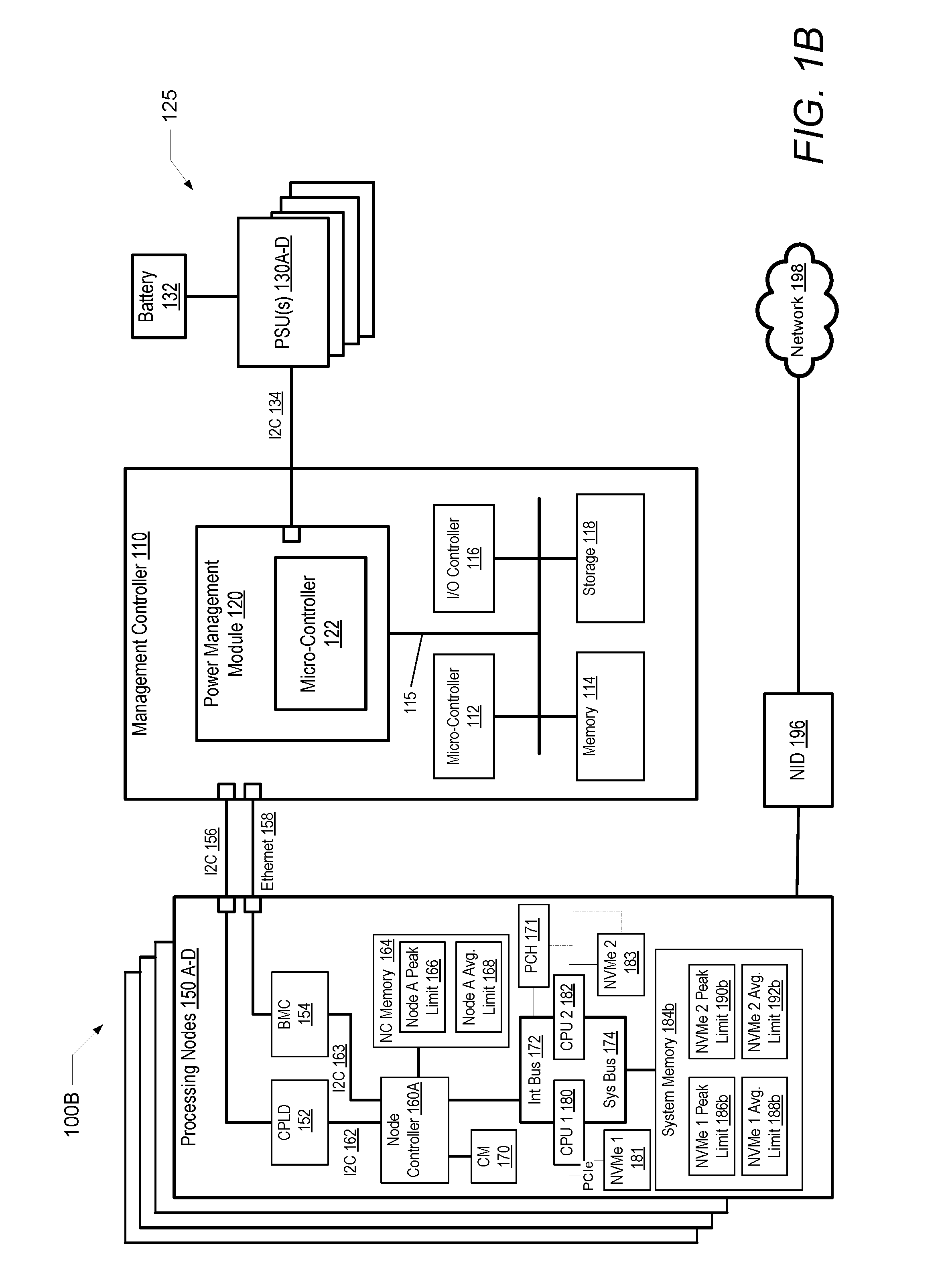
Predictive power capping and power allocation to computing nodes in a rack-based information handling system
ActiveUS20150177814A1Volume/mass flow measurementPower supply for data processingPower usagePower budget
A computer-implemented method enables rack-level predictive power capping and power budget allocation to processing nodes in a rack-based IHS. A rack-level management controller receives node-level power-usage data and settings from several block controllers, including current power consumption and an initial power budget for each node. A power consumption profile is generated based on the power-usage data for each node. A total available system power of the IHS is identified. A system power cap is determined based on the power consumption profiles and the total available system power. A current power budget is determined for each node based on an analysis of at least one of the power consumption profile, the initial power budget, the current power consumption, the system power cap, and the total available system power. A power subsystem regulates power budgeted and supplied to each node based on the power consumption profiles and the system power cap.
Owner:DELL PROD LP
Document transformation
InactiveUS20040268249A1Digital data processing detailsSpecial data processing applicationsUser deviceDocument transformation
In a server a source document is represented as a source document object model (13). For delivery of the source document to a user device such as a mobile phone the server dynamically selects transformation maps (10) and merges them to provide a compound map (12). The maps (10) are selected according to characteristics of the delivery channel and of the user device. The source DOM (13) is then transformed into a target DOM (14) in a single pass. Each node of the source DOM (13) self-transforms using the map rules. At the node level the transformation may change node attributes and / or node-to-node relationships.
Owner:MOBILEAWARE TECH
Shift register unit, shift register and display device
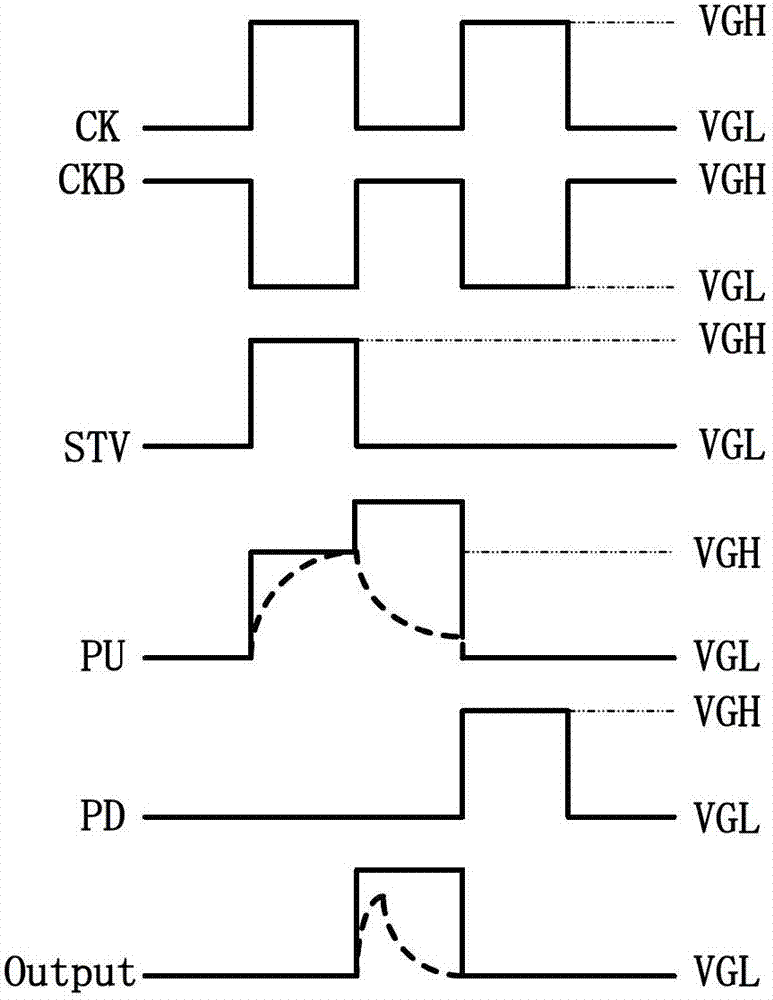
ActiveCN102819998AGuaranteed to workPrevent drop downStatic indicating devicesDigital storageShift registerComputer module
The invention provides a shift register unit, a shift register and a display device. The shift register unit comprises a first output control module, a second output control module, a hierarchical output module, and a pull-up node level keeping capacitor, wherein the hierarchical output module is respectively connected with a pull-up node, a pull-down node, a carry signal output end and a drive signal output end, and is used for keeping a high level of a drive signal at the evaluation stage and for keeping a low level at the reset stage, the pre-charging state and the non-work stage by hierarchically outputting the carry signal and the drive signal; and the pull-up node level keeping capacitor is connected between a first low-level output end and the source of a first thin film transistor (TFT) included in the first output control module, and is used for keeping a high level of the pull-up node at the evaluation stage through the first output control module so as to keep high level of the drive signal. The shift register unit provided by the invention can suppress the influence of leakage current of a depletion-type TFT on the shift register.
Owner:BOE TECH GRP CO LTD +1
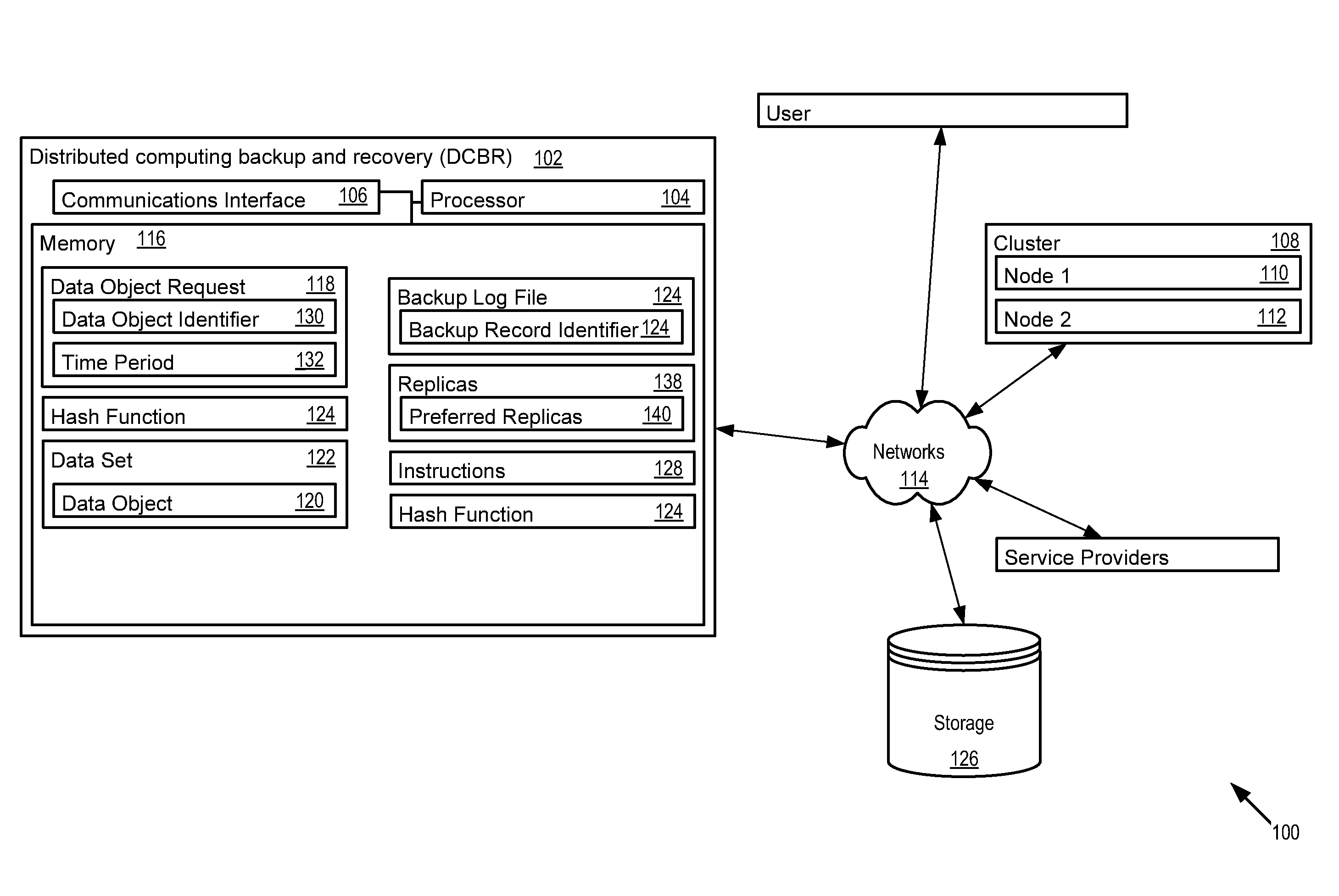
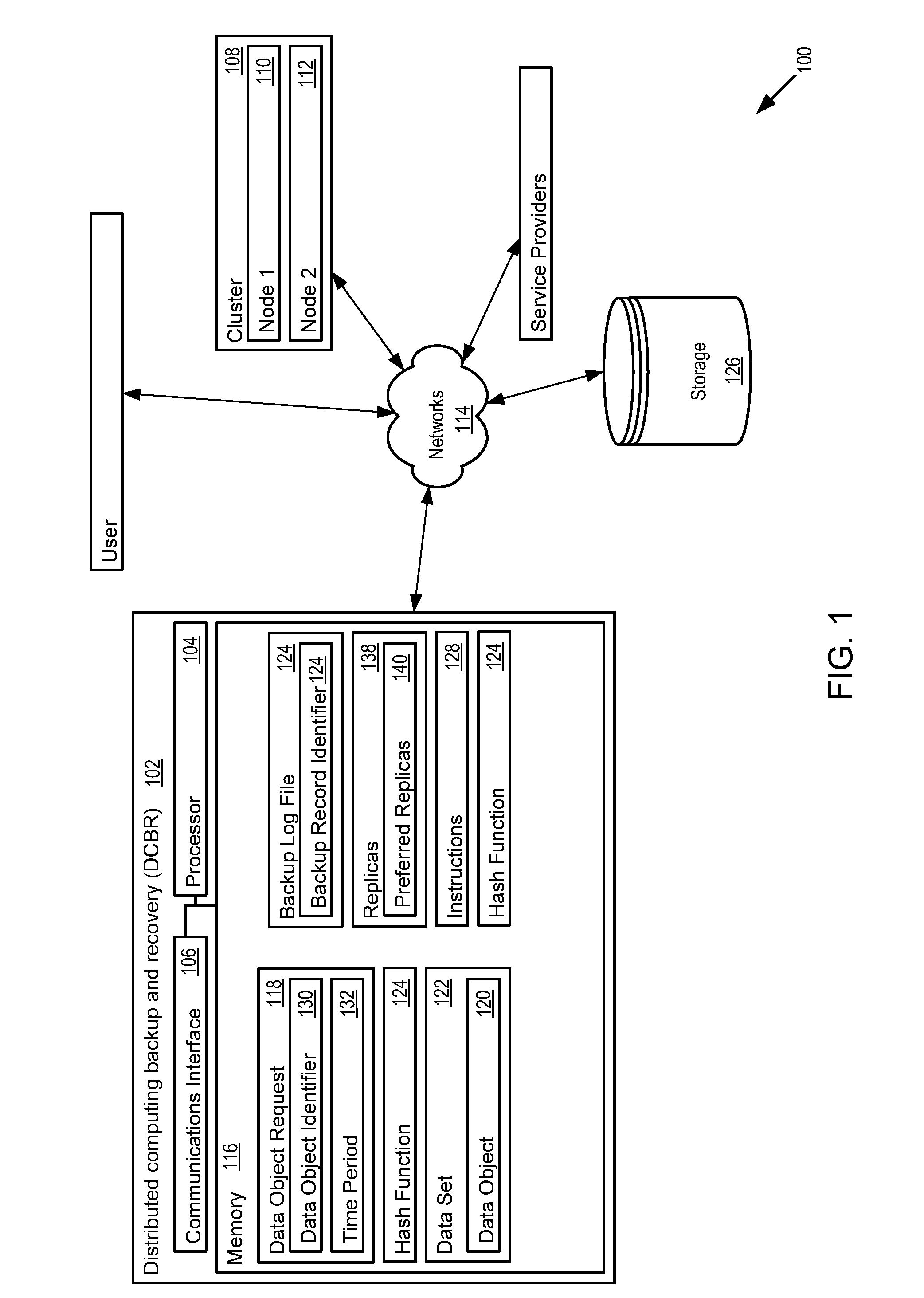
Distributed computing backup and recovery system
The distributed computing backup and recovery (DCBR) system and method provide backup and recovery for distributed computing models (e.g., NoSQL). The DCBR system extends the protections from server node-level failure and introduces persistence in time so that the evolving data set may be stored and recovered to a past point in time. The DCBR system, instead of performing backup and recovery for an entire dataset, may be configured to apply to a subset of data. Instead of keeping or recovering snapshots of the entire dataset which requires the entire cluster, the DCBR system identifies the particular nodes and / or archive files where the dataset resides so that backup or recovery may be done with a much smaller number of nodes.
Owner:ACCENTURE GLOBAL SERVICES LTD
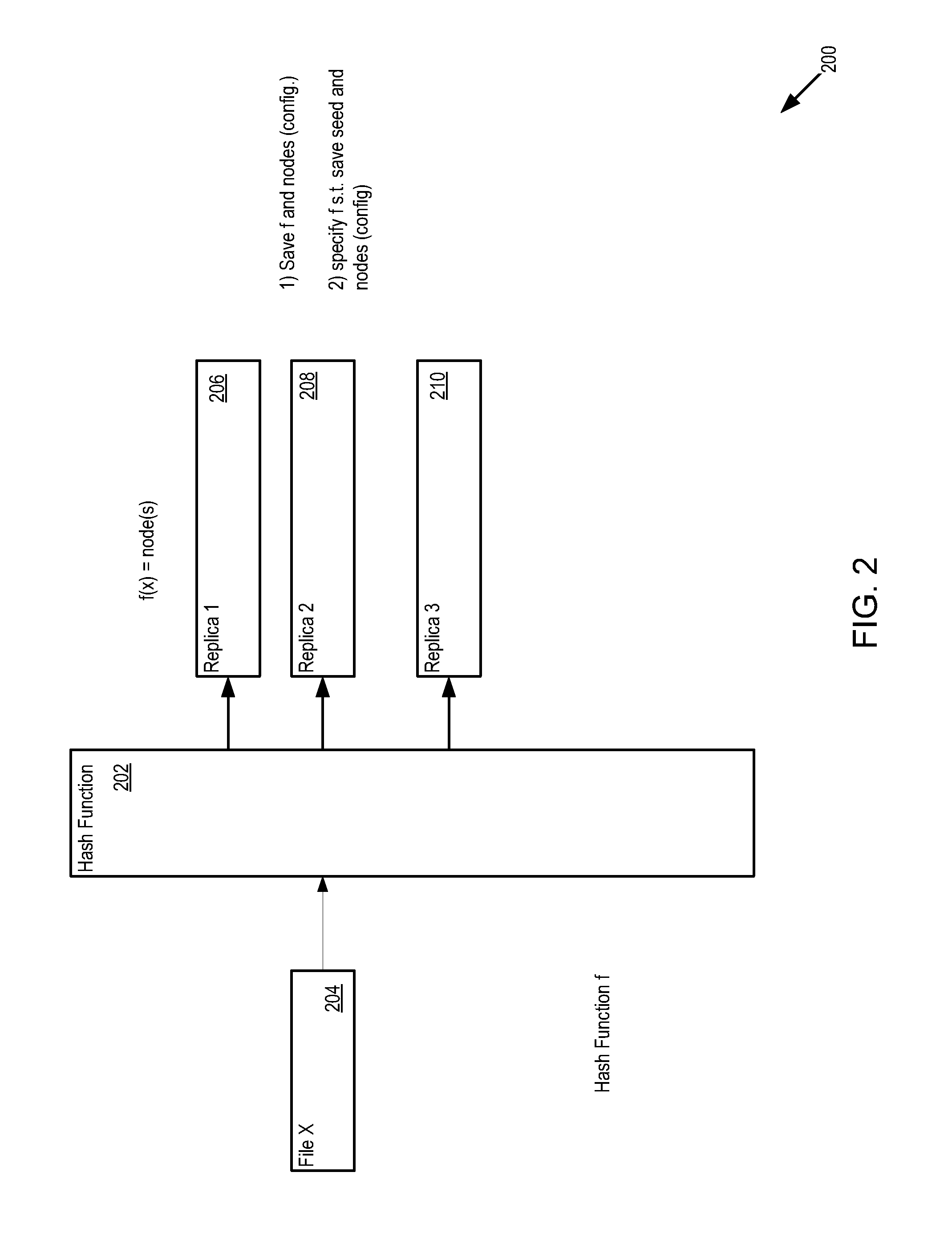
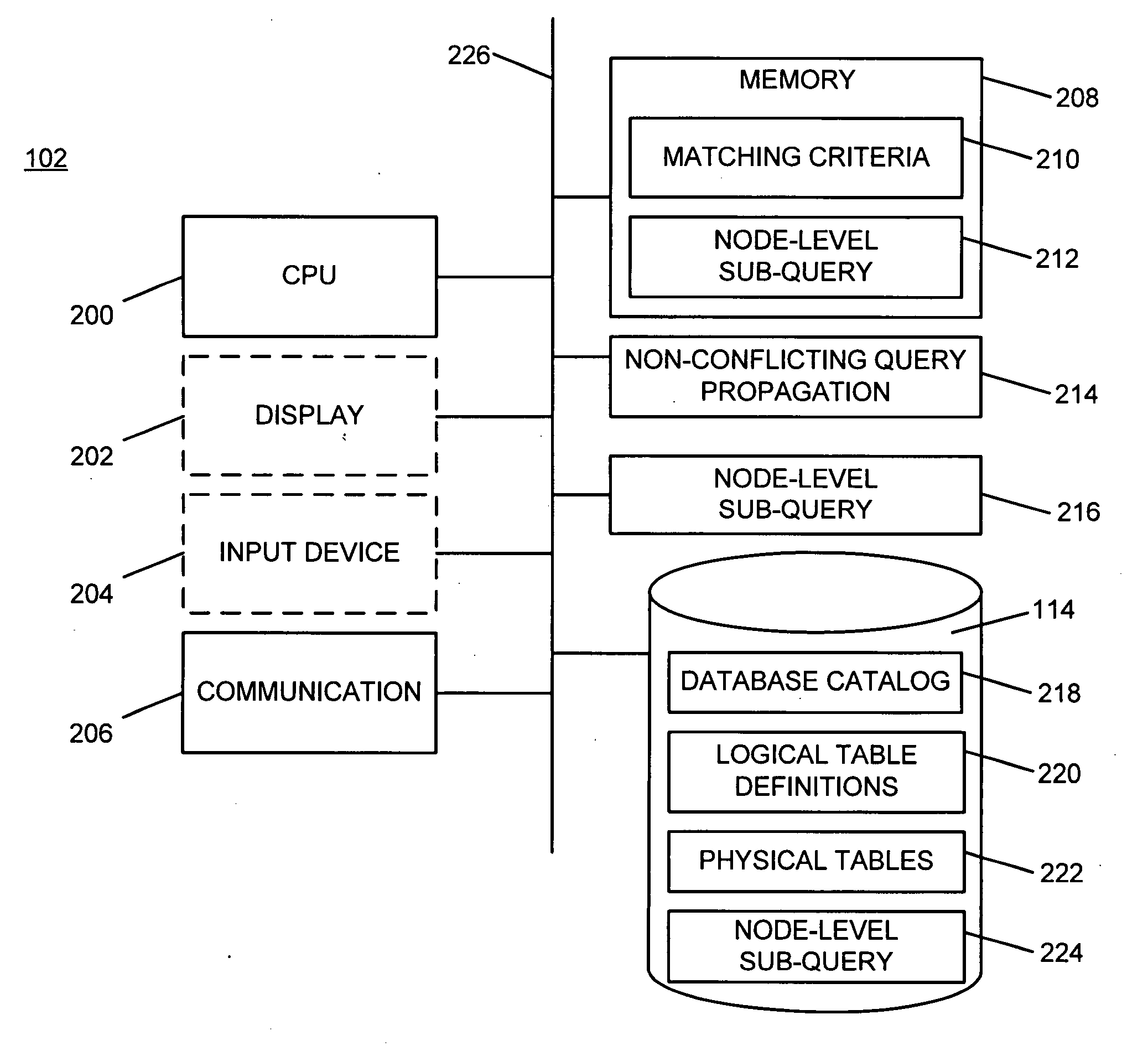
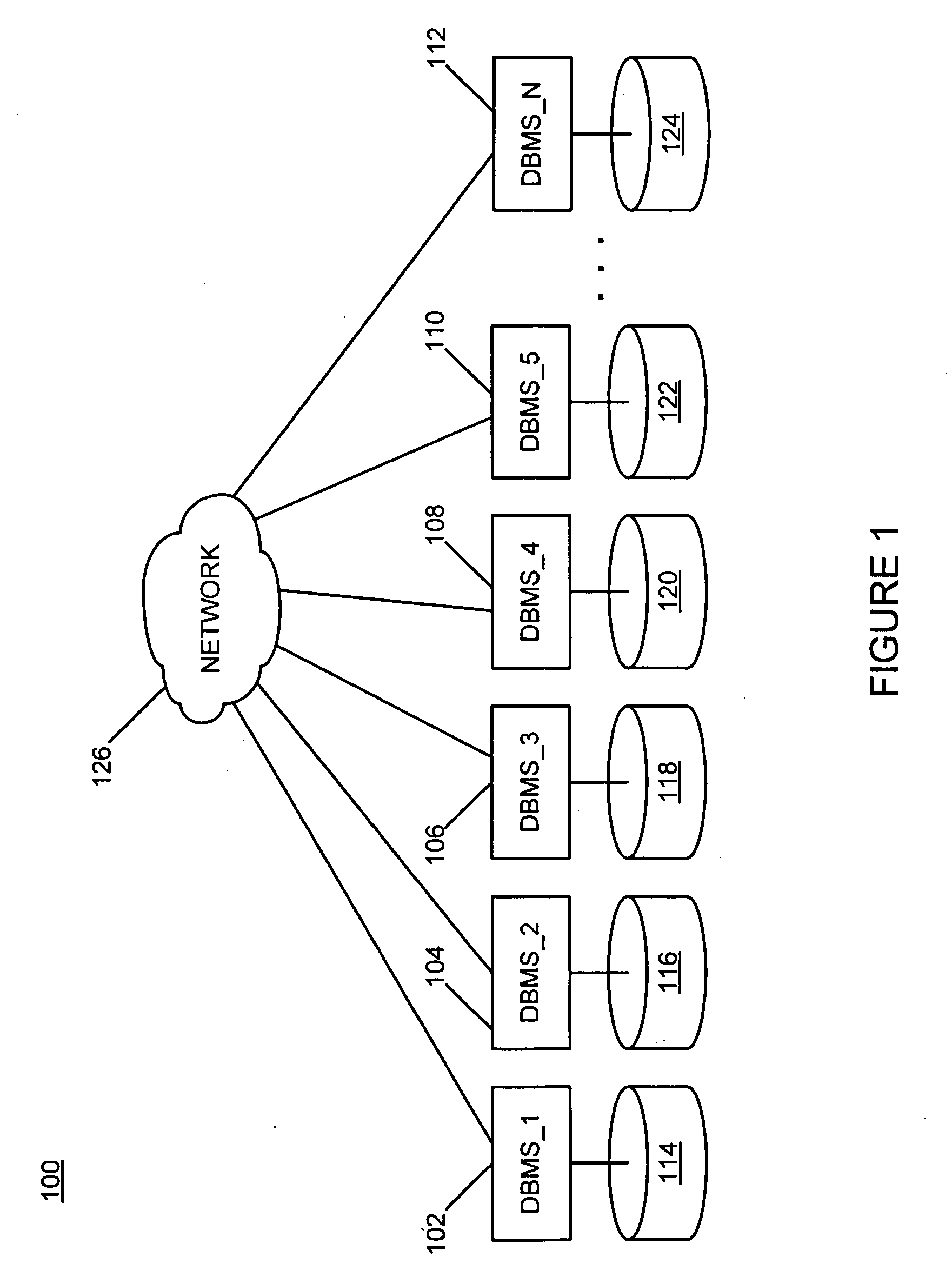
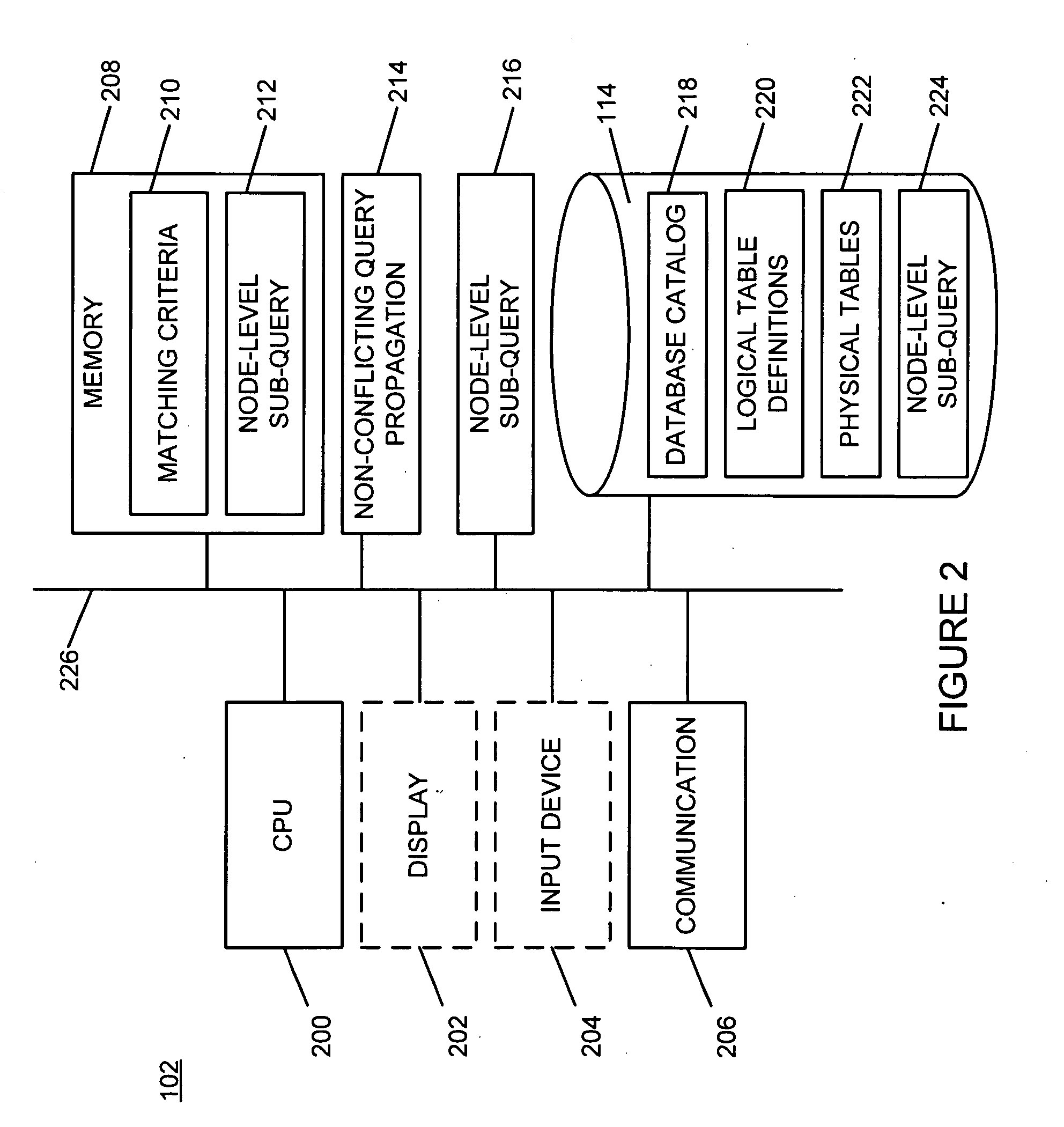
Node-level sub-queries in distributed databases
InactiveUS20100094851A1Digital data information retrievalDigital data processing detailsLogical queryDistributed database
A database query is received that includes a logical query indicator at a distributed database node within a distributed network of databases. The logical query indicator includes at least one physical database query and at least one database node identifier that allows at least one distributed database node to identify at least one physical database to execute the physical database query against. It is determined that the at least one database node identifier matches a local node identifier. The at least one physical database query is executed against at least one local physical database table. A local query response is formed including data retrieved from the at least one local physical database table. The database query is responded to with at least the local query response. This abstract is not to be considered limiting, since other embodiments may deviate from the features described in this abstract.
Owner:IBM CORP
Method of supporting access network handover operation of user equipment in wireless communication system and apparatus for the same
Provided method includes receiving, from the source AN, a handover request requesting a handover of an AN of the user equipment, wherein the user equipment is configured with a per node level tunnel for connection to a target user plane function node, and wherein the per node level tunnel is a common connection tunnel which is generated in the node unit for all traffics between the target AN and the target user plane function node, determining whether a service provision through the per node level tunnel is possible, determining whether generation of a new per node level tunnel for the user equipment is necessary when it is determined that service provision is impossible, and generating the new per node level tunnel for the user equipment based on a result of the determination or changing the tunnel model of the user equipment to a different tunnel model.
Owner:LG ELECTRONICS INC
Ranking method for web page and web site
InactiveCN1996299AReflect qualityReflect the importanceSpecial data processing applicationsWeb siteWeb page
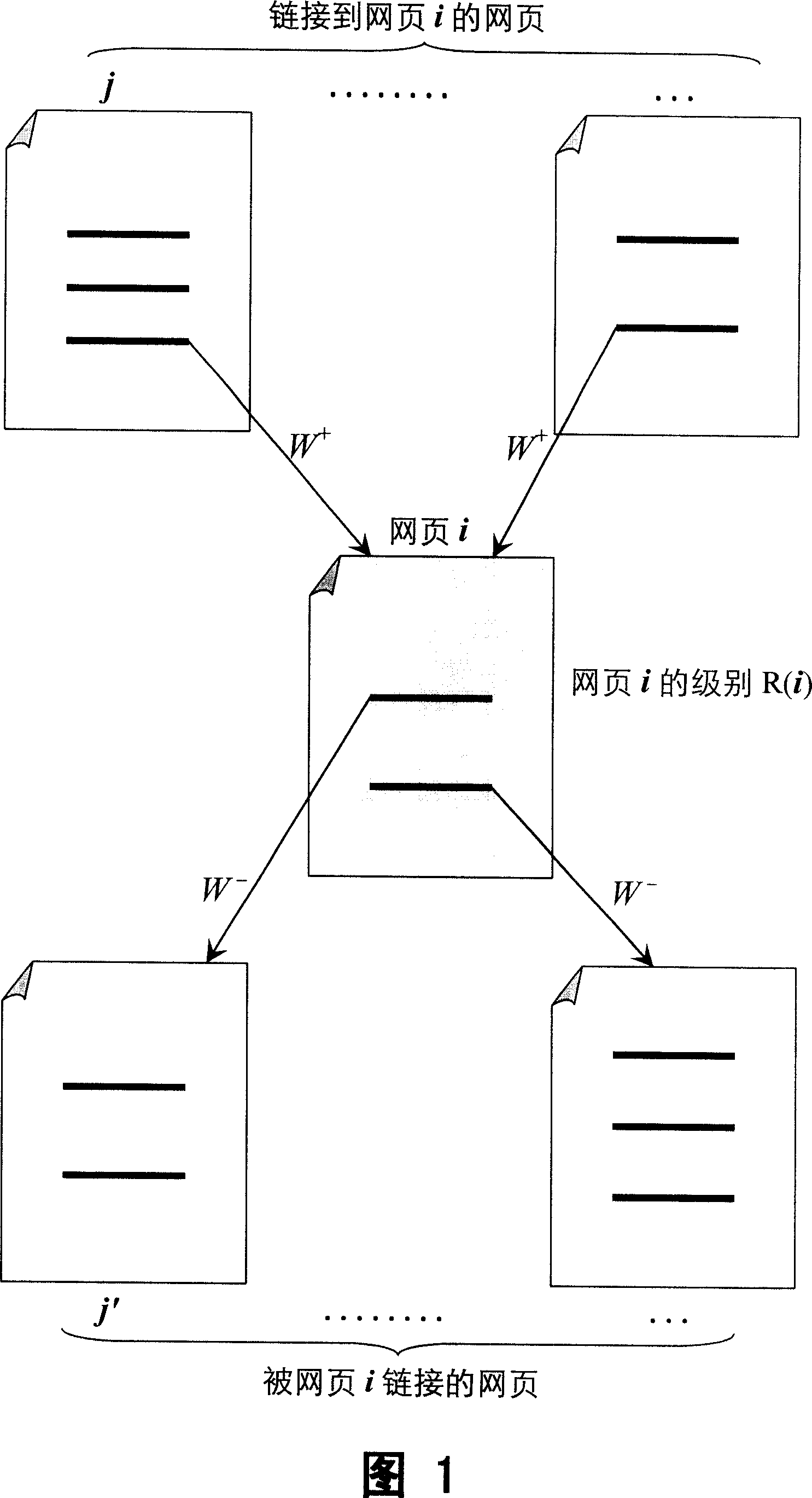
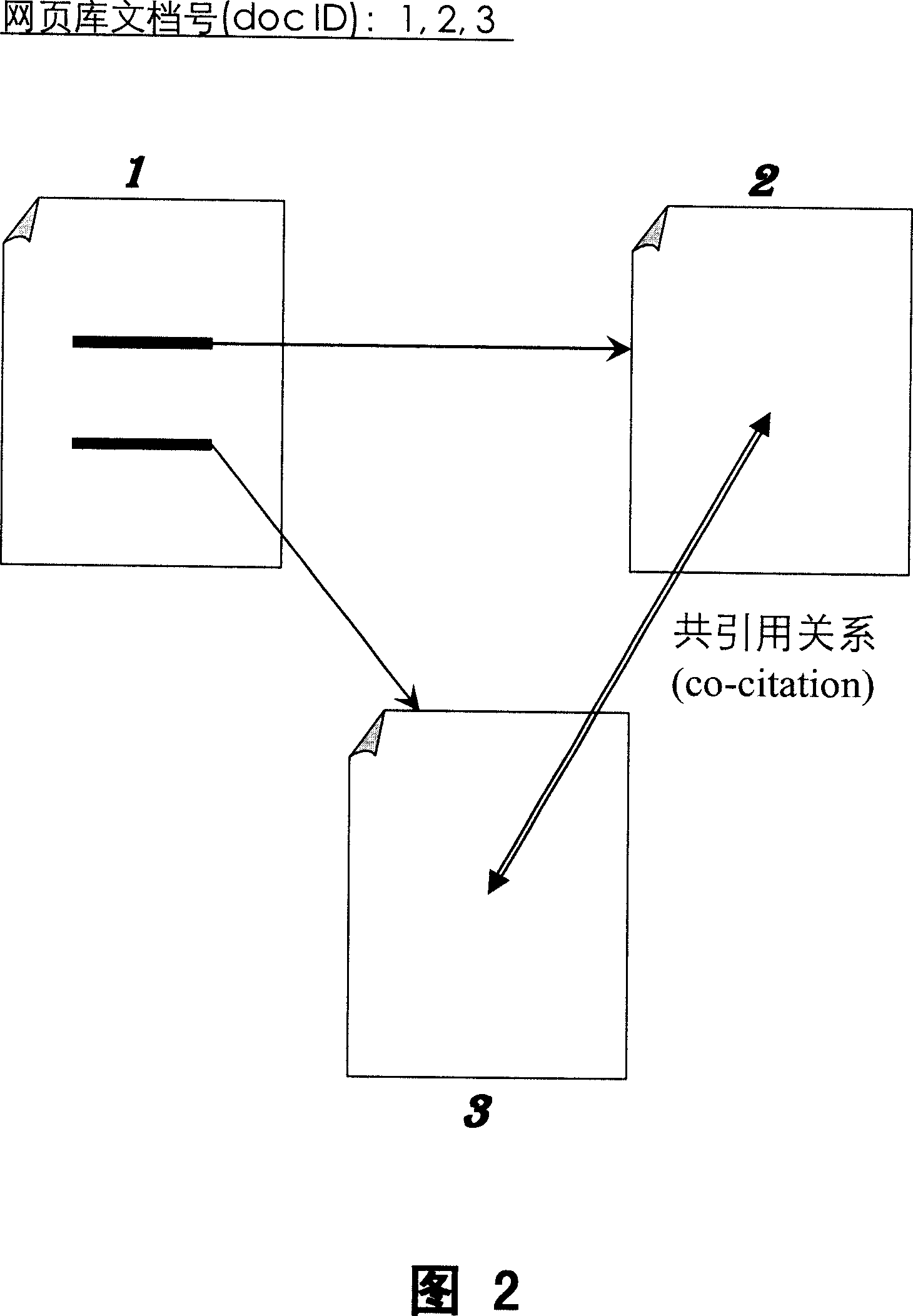
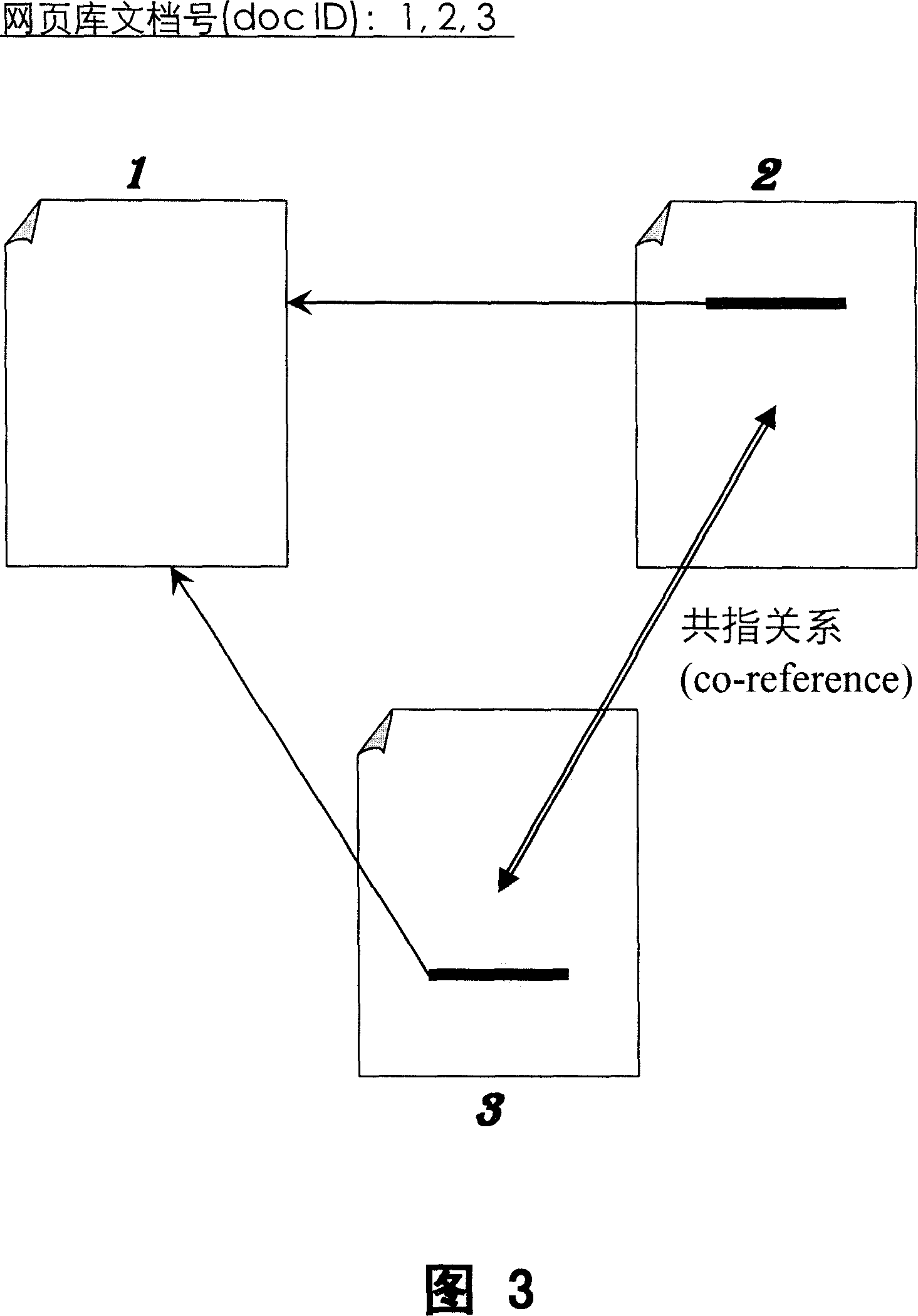
The invention relates to a network node evaluating method, with multi chains relations of the nodes recursively deciding the level of each webpage. The level of each node is the sum of entry chain positive weight and weighting of the source node, or the sum of negative weighting and the target node level, or the sum its commonly quoted relationship weight and the common quotation relationship node level, or the sum of common index relationship weight and the level of the common index relationship node, or further sum of the four kinds of the weighting sum. Network node can be webpage, or super webpage representing the chain relationship of all the said web pages. The evaluating result of this invention can provide even more holistic and accurate reflection of the quality, importance and authority of the nodes, with good stability, and better effect of anti plagiary. It can provide better technical result for sequencing the result of the webpage searching, website classification, and search result sequence.
Owner:孙斌
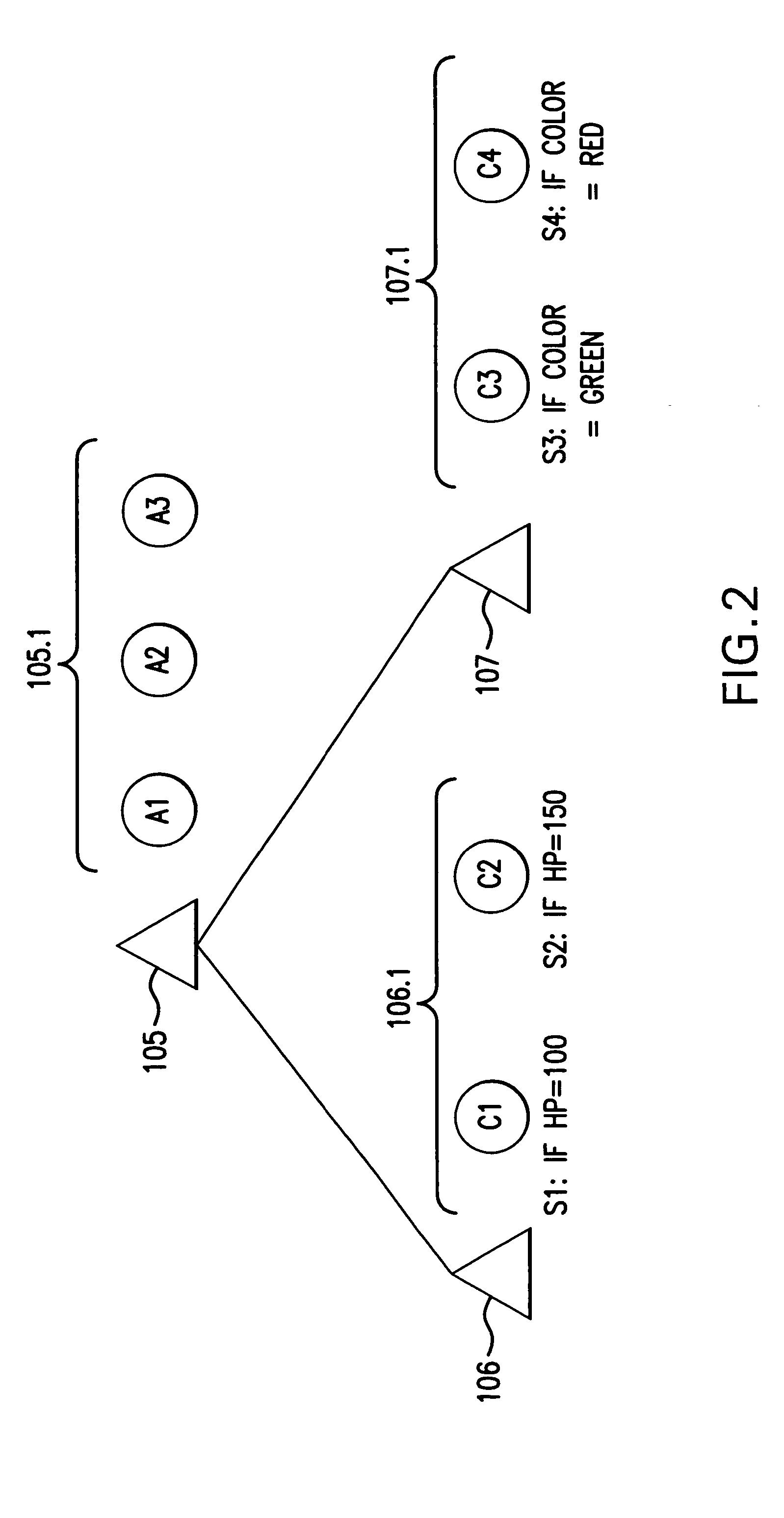
Method and system for automatically generating selection conditions in a product configuration system
InactiveUS6983187B2Computer aided designSpecial data processing applicationsComputer scienceNode level
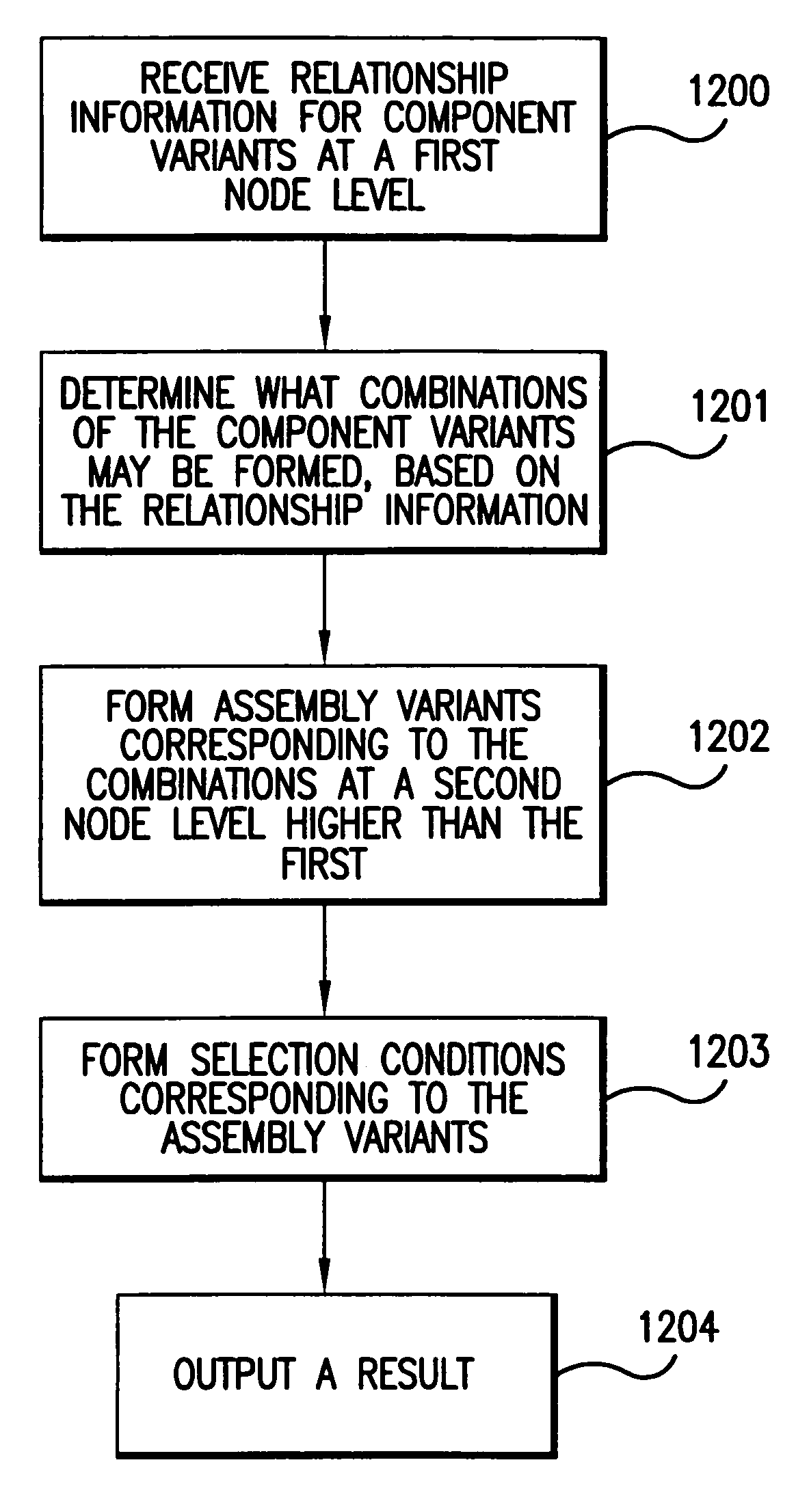
This disclosure relates to a method and system for automatically generating selection conditions associated with component variants represented in a hierarchical node structure in a product configuration system. The selection conditions relate to a determination of when component variants are to be included in a configurable product. The method and system may involve receiving relationship information for component variants at a first node level of the node structure, and determining what combinations may be formed from the component variants based on the relationship information. The method and system may further involve forming assembly variants corresponding to the combinations, at a second node level higher than the first node level, and forming selection conditions corresponding to the assembly variants based on selection conditions corresponding to the component variants.
Owner:SAP AG
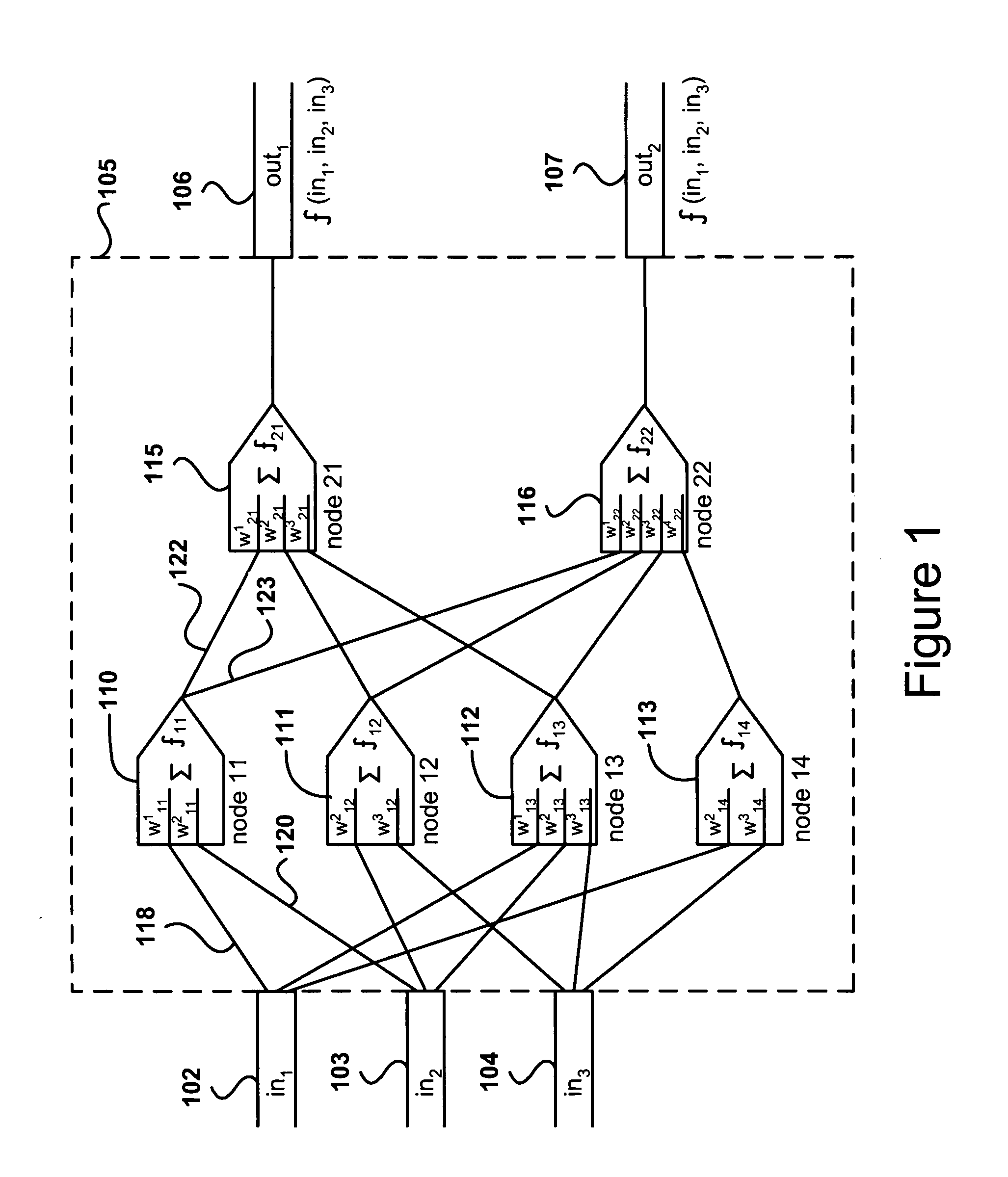
Molecular-junction-nanowire-crossbar-based neural network
InactiveUS7359888B2Easy to getTransistorSemiconductor/solid-state device detailsNanowireCross connection
A method for configuring nanoscale neural network circuits using molecular-junction-nanowire crossbars, and nanoscale neural networks produced by this method. Summing of weighted inputs within a neural-network node is implemented using variable-resistance resistors selectively configured at molecular-junction-nanowire-crossbar junctions. Thresholding functions for neural network nodes are implemented using pFET and nFET components selectively configured at molecular-junction-nanowire-crossbar junctions to provide an inverter. The output of one level of neural network nodes is directed, through selectively configured connections, to the resistor elements of a second level of neural network nodes via circuits created in the molecular-junction-nanowire crossbar. An arbitrary number of inputs, outputs, neural network node levels, nodes, weighting functions, and thresholding functions for any desired neural network are readily obtained by the methods of the present invention.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Dynamic peak power limiting to processing nodes in an information handling system
ActiveUS20170031431A1Limited peak power consumptionVolume/mass flow measurementPower supply for data processingPower capabilityPower usage
A computer-implemented method dynamically limits peak power consumption in processing nodes of an IHS. A power management micro-controller receives processing node-level power-usage and workload data from several node controllers, including current power consumption and a current workload, for each processing node within the IHS. A total available system power of the IHS is identified including a peak power output capacity and a sustained output power capacity. At least one node peak power threshold is determined based on the power-usage and workload data for each of the processing nodes. The node controllers are triggered to determine and set a device peak power limit for each of several variable performance devices within each of the processing nodes based on the node peak power threshold, wherein each of the variable performance devices dynamically adjusts a value of a corresponding device performance metric based on the device peak power limit.
Owner:DELL PROD LP
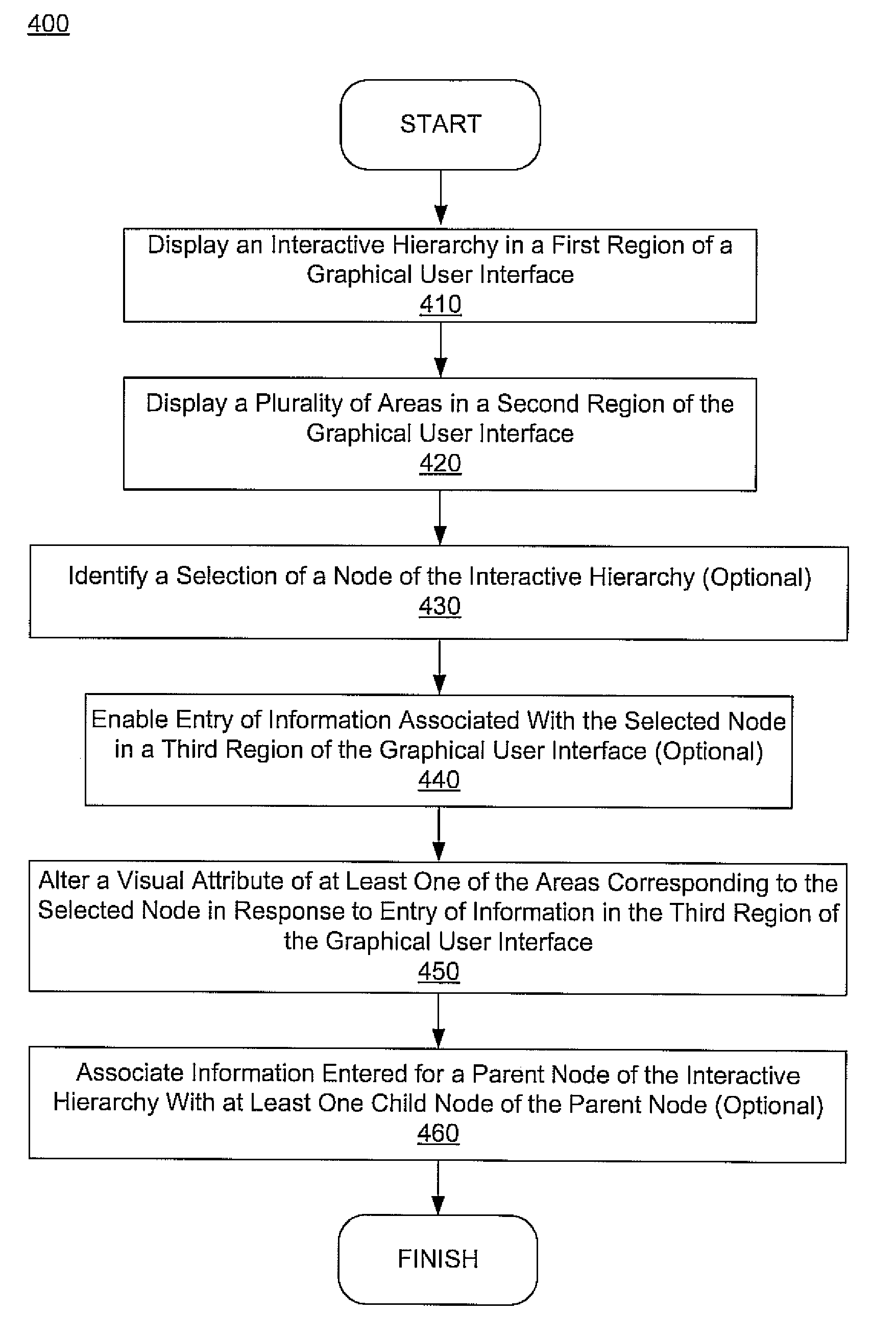
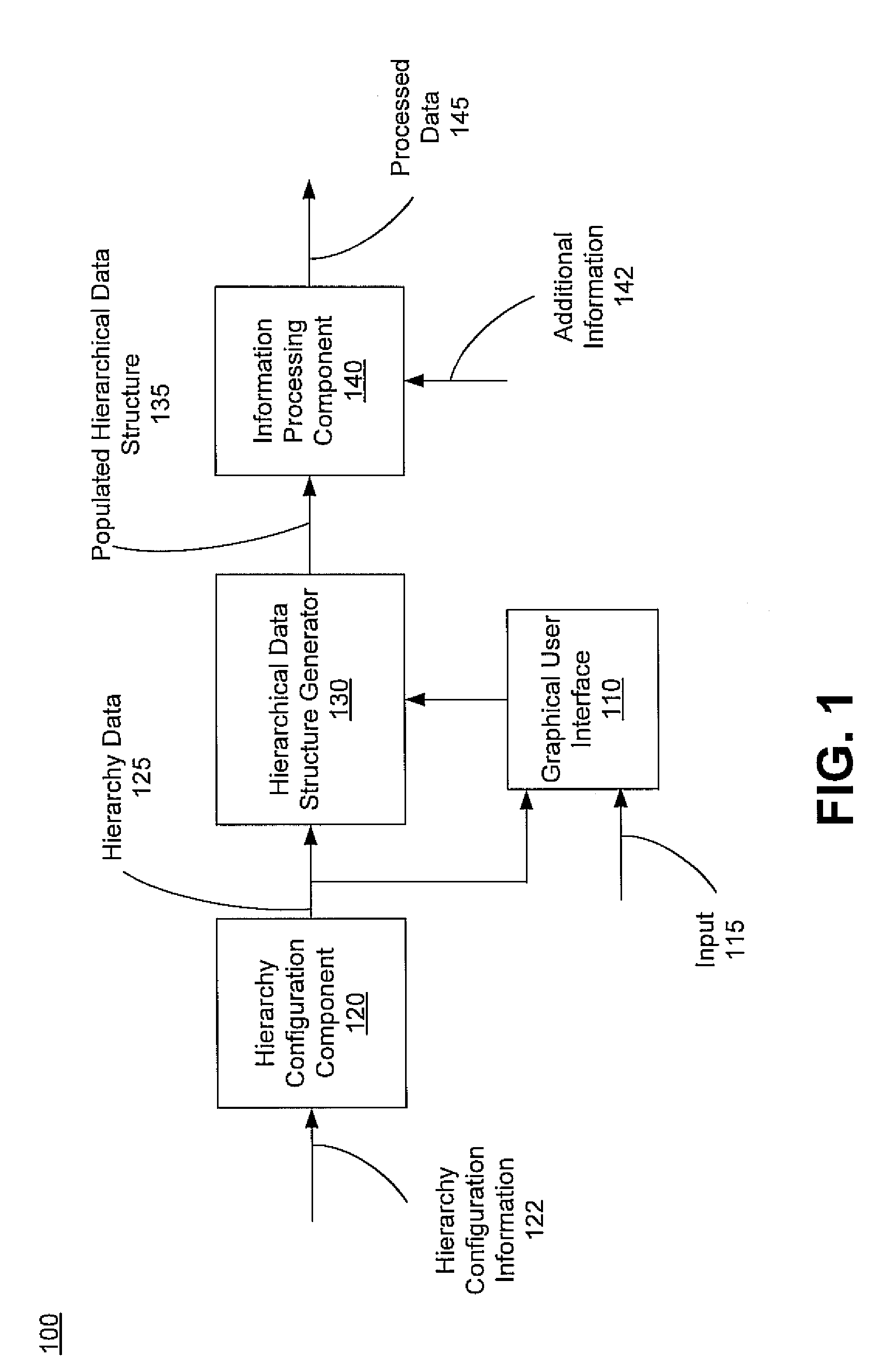
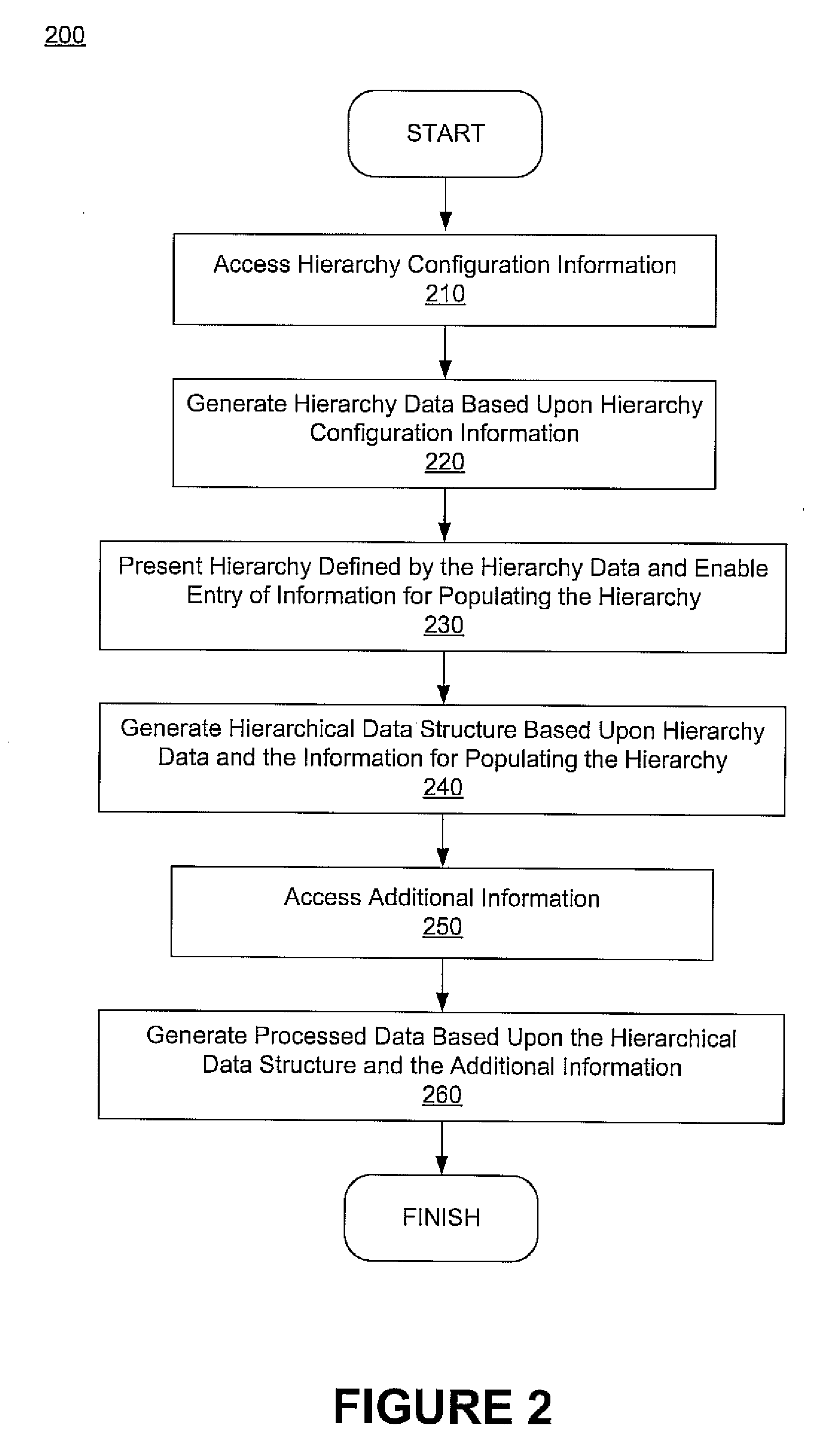
Method, system, and graphical user interface for presenting an interactive hierarchy and indicating entry of information therein
ActiveUS20090276733A1Easy and efficient managementImproving sense-of-taskFinanceNatural language data processingGraphicsGraphical user interface
A method, computer system, and graphical user interface for presenting an interactive hierarchy and indicating entry of information therein is disclosed. An interactive hierarchy is used to organize information using nodes arranged in multiple levels, where the interactive hierarchy may also be used to select a node to operate on. The interactive hierarchy may provide sense-of-place by depicting the organization of the nodes and indicating which node a user is operating on. An indicator is also provided which indicates whether one or more types of information have been entered for a given node, level of nodes, etc., thereby providing sense-of-task by enabling a user to determine which types of information have already been entered, which types of information have yet to be entered, etc. Further, a task indicator may be provided for stepping users through various information entry and / or management tasks, thereby further improving sense-of-task.
Owner:ORACLE INT CORP
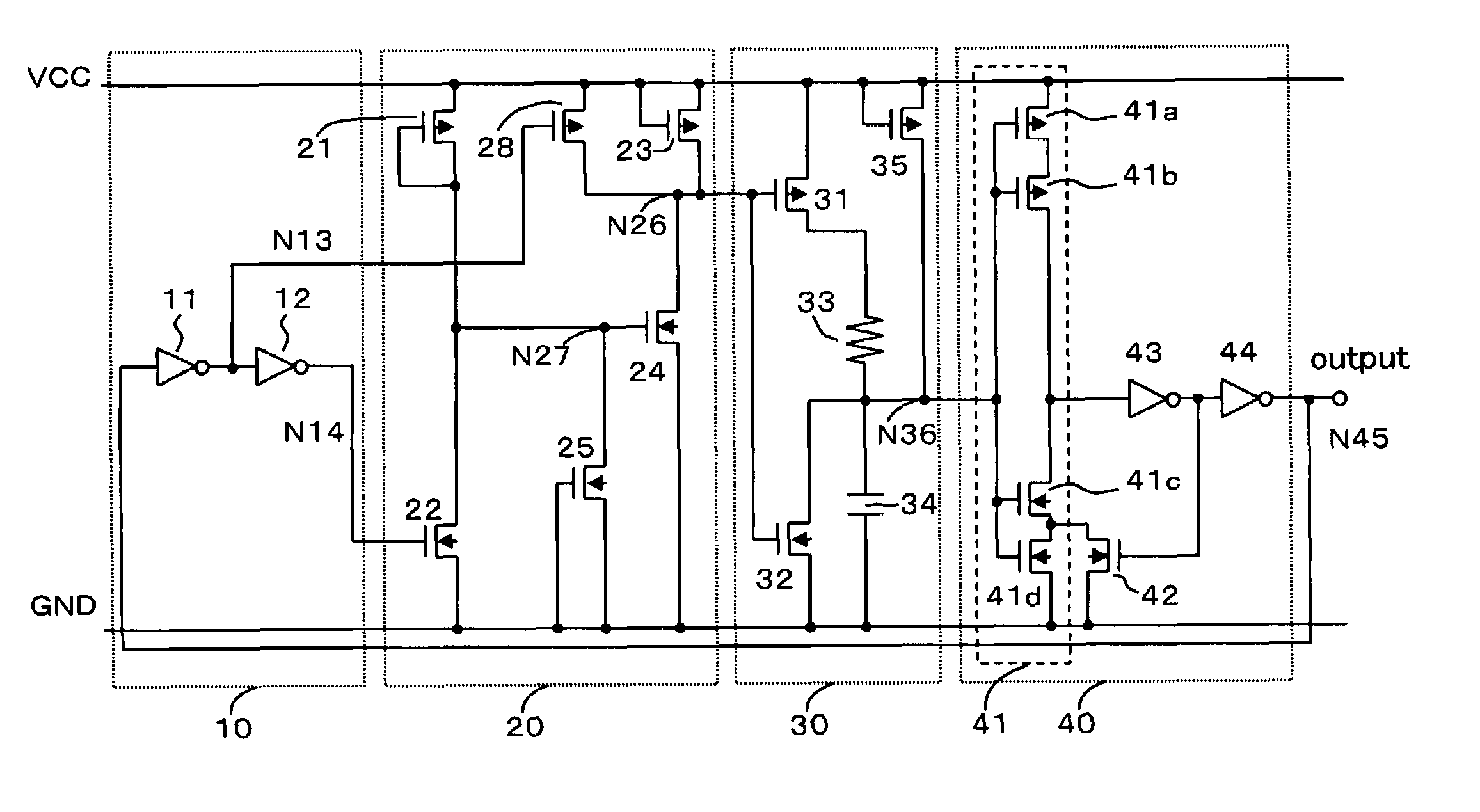
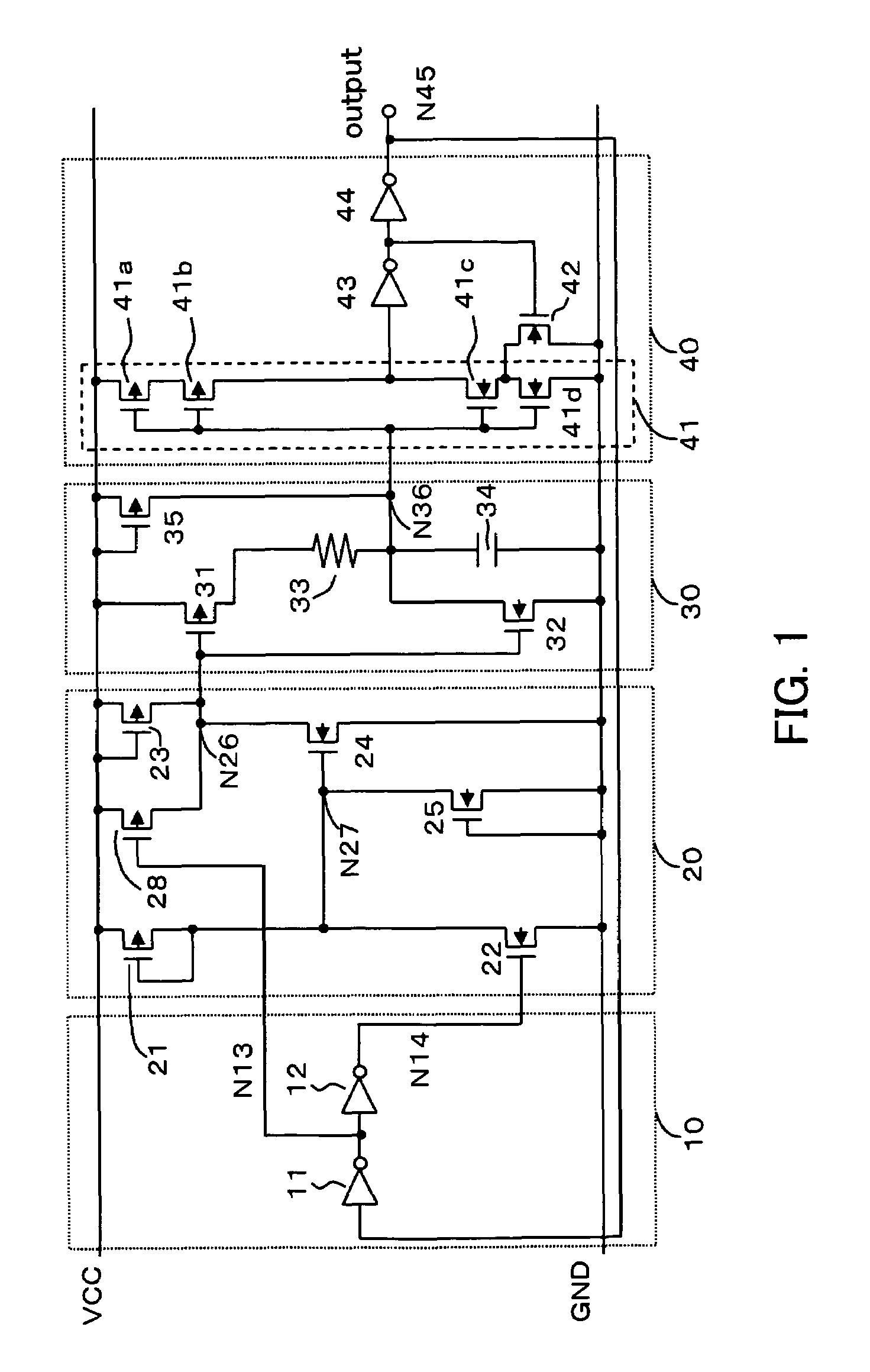
Power-on reset circuit
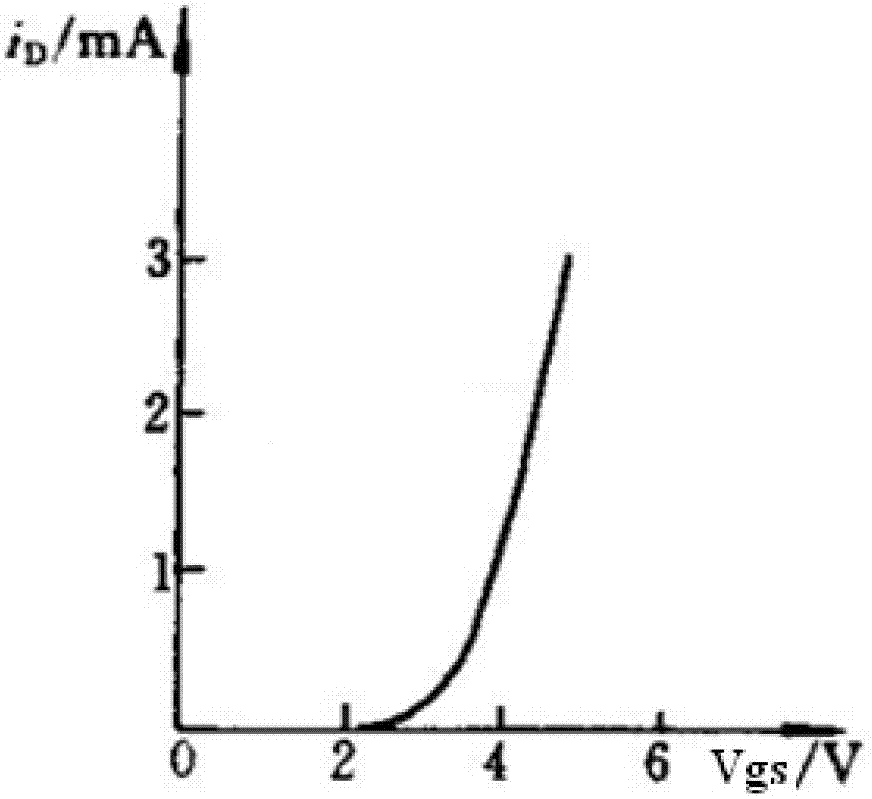
InactiveUS6972602B2Reduce the valueHysteresis characteristicPulse automatic controlElectronic switchingPower-on resetElectricity
A power-on reset circuit comprises a power supply voltage detection circuit that detects a rise of a power supply voltage and that changes a logic level of a first internal node; a capacitor charge / discharge circuit that charges and discharges a capacitor according to the first internal node level and that in an event that the power supply voltage is reduced, discharges the capacitor to follow the event; and a reset pulse generation circuit that before the power supply voltage rises higher than the predetermined voltage, outputs a first output voltage to an output node and that after the power supply voltage has risen higher than the predetermined voltage, outputs a second output voltage to the output node upon detecting that a charge level of the capacitor has become higher than a charge level detection voltage.
Owner:SHARP KK
Cache policy based on match of content popularity and node level
ActiveCN106101223ASmall acquisition delayReduce invalid cacheTransmissionDistributed computingContent popularity
The invention provides a cache policy based on match of content popularity and a node level. The cache policy is applied to a content center wireless network and realizes the match of the content popularity and the node level. Firstly, the cache performance of each node on a forwarding path is evaluated, the cache performance of the node is comprehensively evaluated from three parameters, namely the hops of the node from a user, the betweenness centrality and the replacement rate, wherein a gray correlation method is selected to assess and classify the nodes at the same time. Then, based on the matching probability of the content popularity and the node level, the node makes a cache decision on the content. By adopting the method, the cache space in the content center network is effectively utilized, so that the cache redundancy is reduced.
Owner:BEIJING UNIV OF POSTS & TELECOMM +1
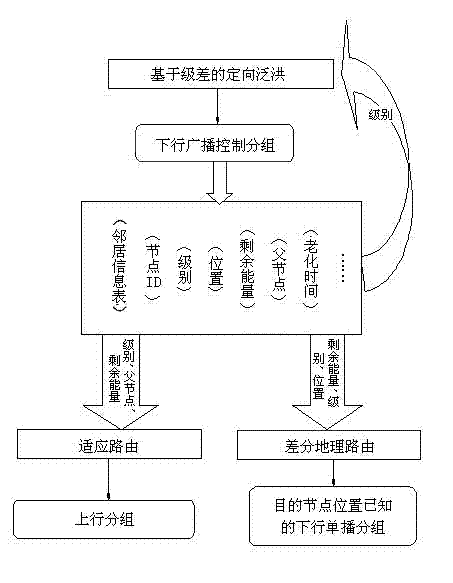
Method for adaptively routing underwater sensor network on basis of difference
InactiveCN102868974ACutting costsLower latencyPower managementEnergy efficient ICTPathPingEngineering
The invention generally relates to the technical field of network communication, and particularly relates to a method for routing an underwater sensor network. The method for routing comprises the following constituent parts: (1) node grade definition; (2) node grade information acquiring and updating processes; (3) neighbor node information recording; (4) directional flooding mechanism based on grade difference; (5) adaptive routing step based on the grade difference, node density and residual energy; and (6) differential geographical routing step based on the grade difference and distance. The method has the following advantages that the best next hop adaptive routing is determined on the basis of the neighbor table information to reduce redundant paths, so that the energy efficiency is improved to a great extent; and the adaptive routing adopts immediate routing, so that the inhibition time of the conventional underwater UWSN (underwater wireless sensor network) routing to a received package is avoided, and the time delay from terminal to terminal is reduced. A great deal of simulation experiments prove that through an underwater sensor network adaptive routing protocol based on the difference, the energy consumption can be reduced to a great extent, the time delay from terminal to terminal is reduced, the node utilization equity is improved, and the whole network life time is prolonged.
Owner:QINGHAI NORMAL UNIV +1
Valve controlled, node-level vapor condensation for two-phase heat sink(s)
InactiveUS20130077247A1Digital data processing detailsModifications using liquid coolingAutomatic controlNuclear engineering
A cooling apparatus and method are provided for cooling one or more electronic components of an electronic subsystem of an electronics rack. The cooling apparatus includes a heat sink, which is configured to couple to an electronic component, and which includes a coolant-carrying channel for coolant to flow therethrough. The coolant provides two-phase cooling to the electronic component, and is discharged from the heat sink as coolant exhaust which comprises coolant vapor to be condensed. The cooling apparatus further includes a node-level condensation module, associated with the electronic subsystem, and coupled in fluid communication with the heat sink to receive the coolant exhaust from the heat sink. The condensation module is liquid-cooled, and facilitates condensing of the coolant vapor in the coolant exhaust. A controller automatically controls the liquid-cooling of the heat sink and / or the liquid-cooling of the node-level condensation module.
Owner:INT BUSINESS MASCH CORP
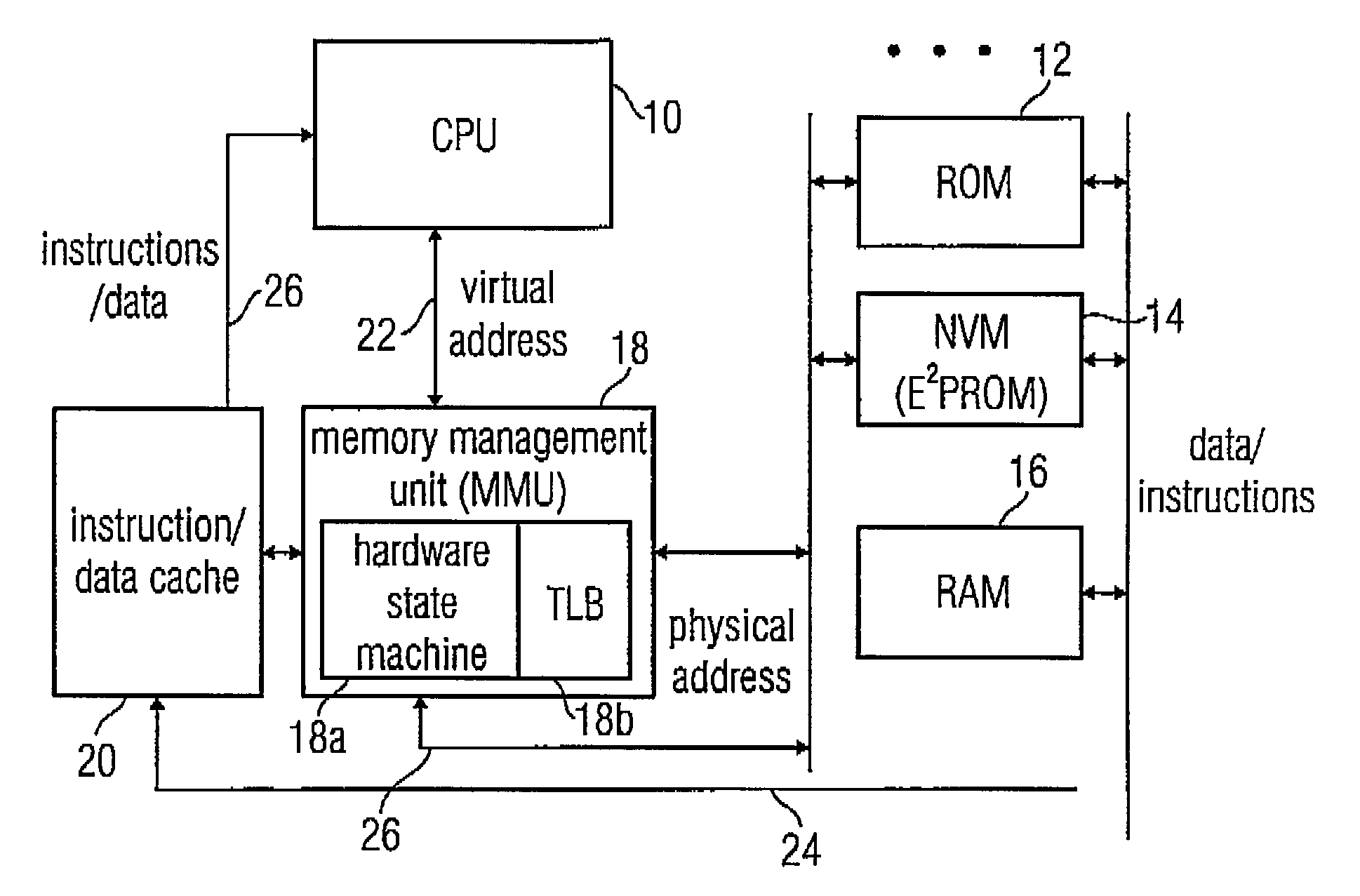
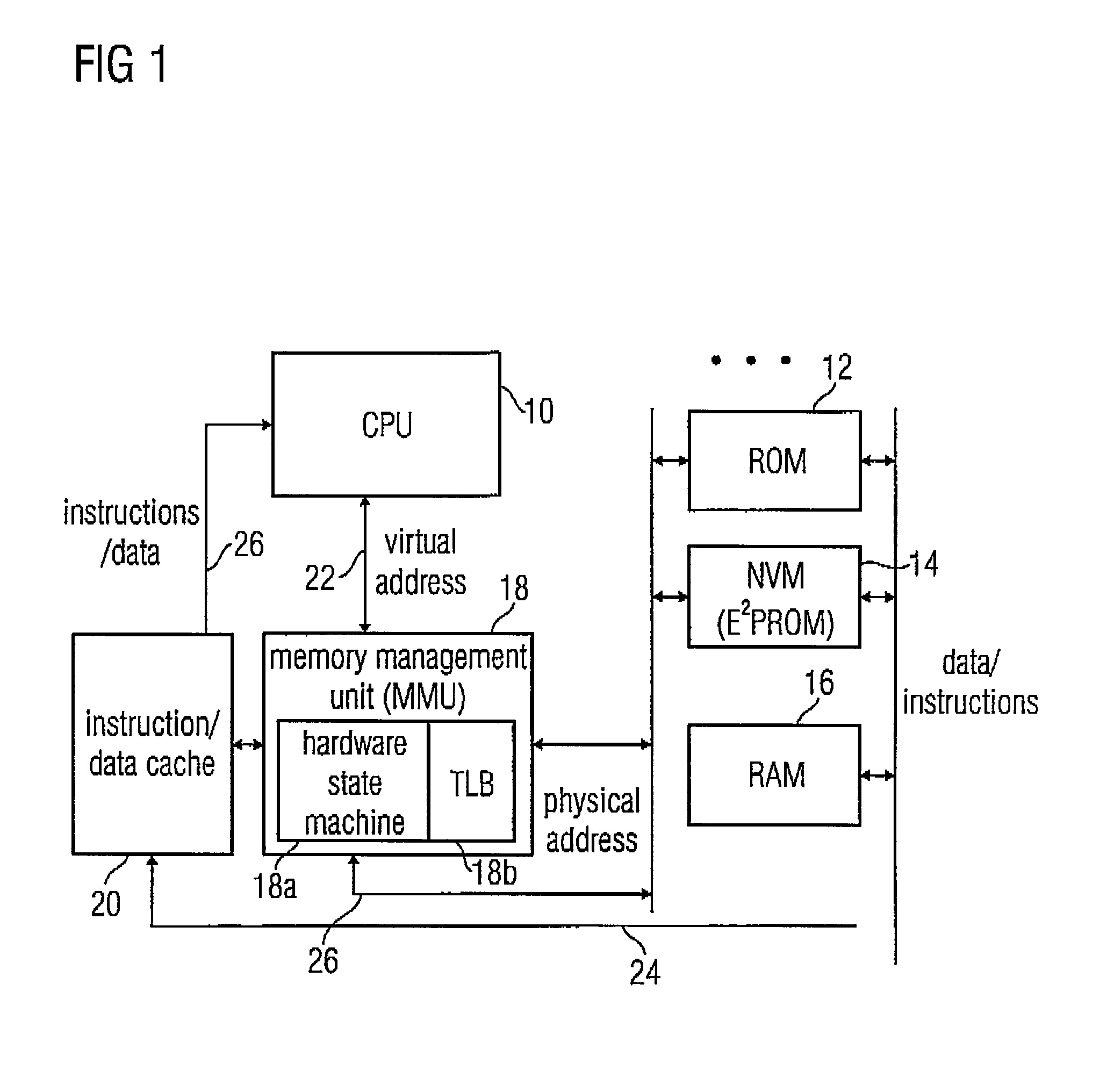
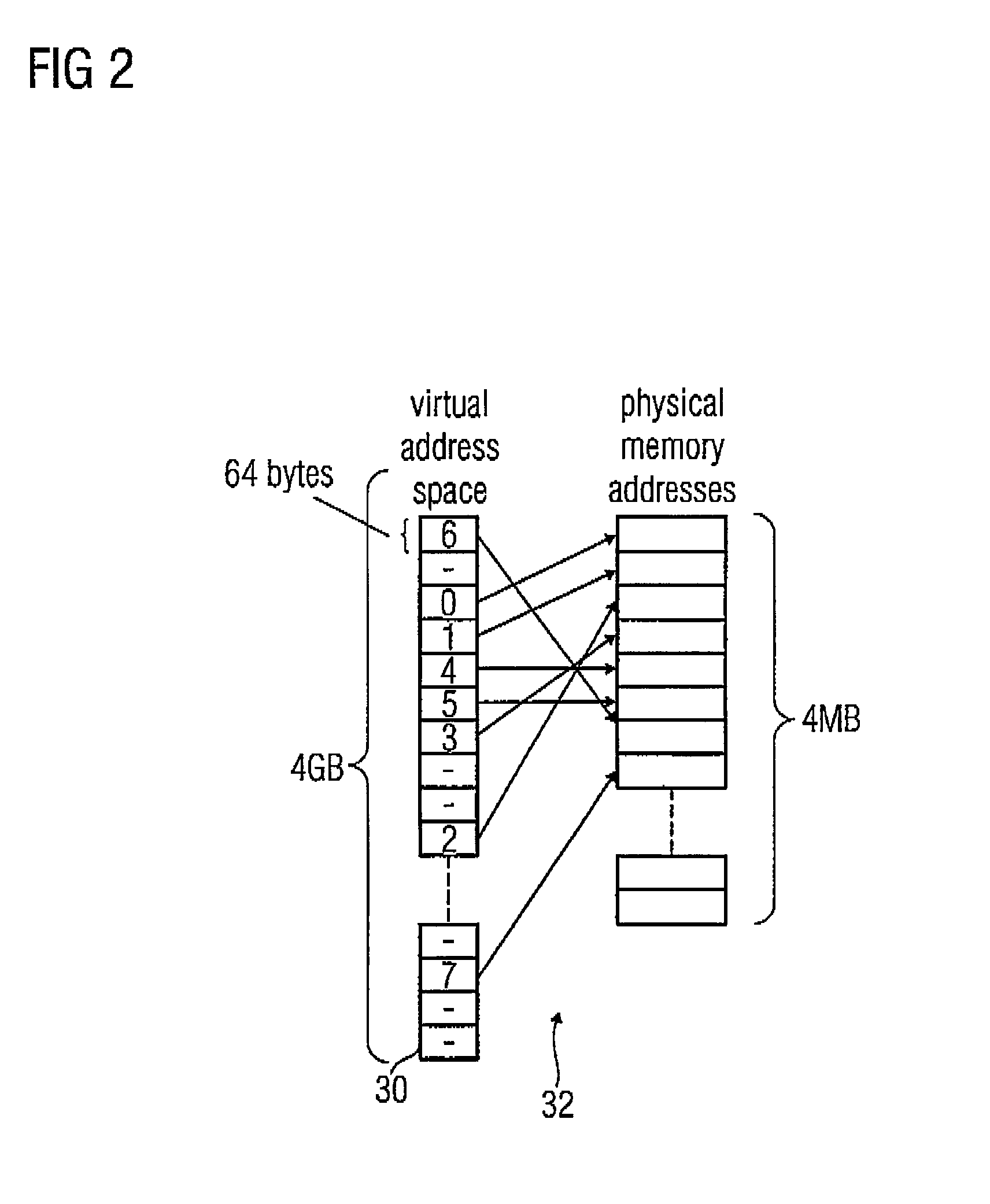
Apparatus and method for determining a physical address from a virtual address by using a hierarchical mapping regulation with compressed nodes
InactiveUS7124275B2Less physical memory spaceImprove securityMemory architecture accessing/allocationMemory systemsOperating systemVirtual address space
A method for determining a physical address from a virtual address, wherein a mapping regulation between the virtual address and the physical address is implemented as hierarchical tree structure with compressed nodes. First, a compression indicator included in the mapping regulation is read, and a portion of the virtual address associated with the considered node level is read. Using the compression indicator and the portion of the virtual address, an entry in the node list of the considered node is determined. The determined entry is read, whereupon the physical address can be determined directly, if the considered node level has been the hierarchically lowest node level. If higher node levels to be processed are present, the previous steps in determining the physical address for compressed nodes of lower hierarchy level are repeated until the hierarchically lowest node level is reached.
Owner:INFINEON TECH AG
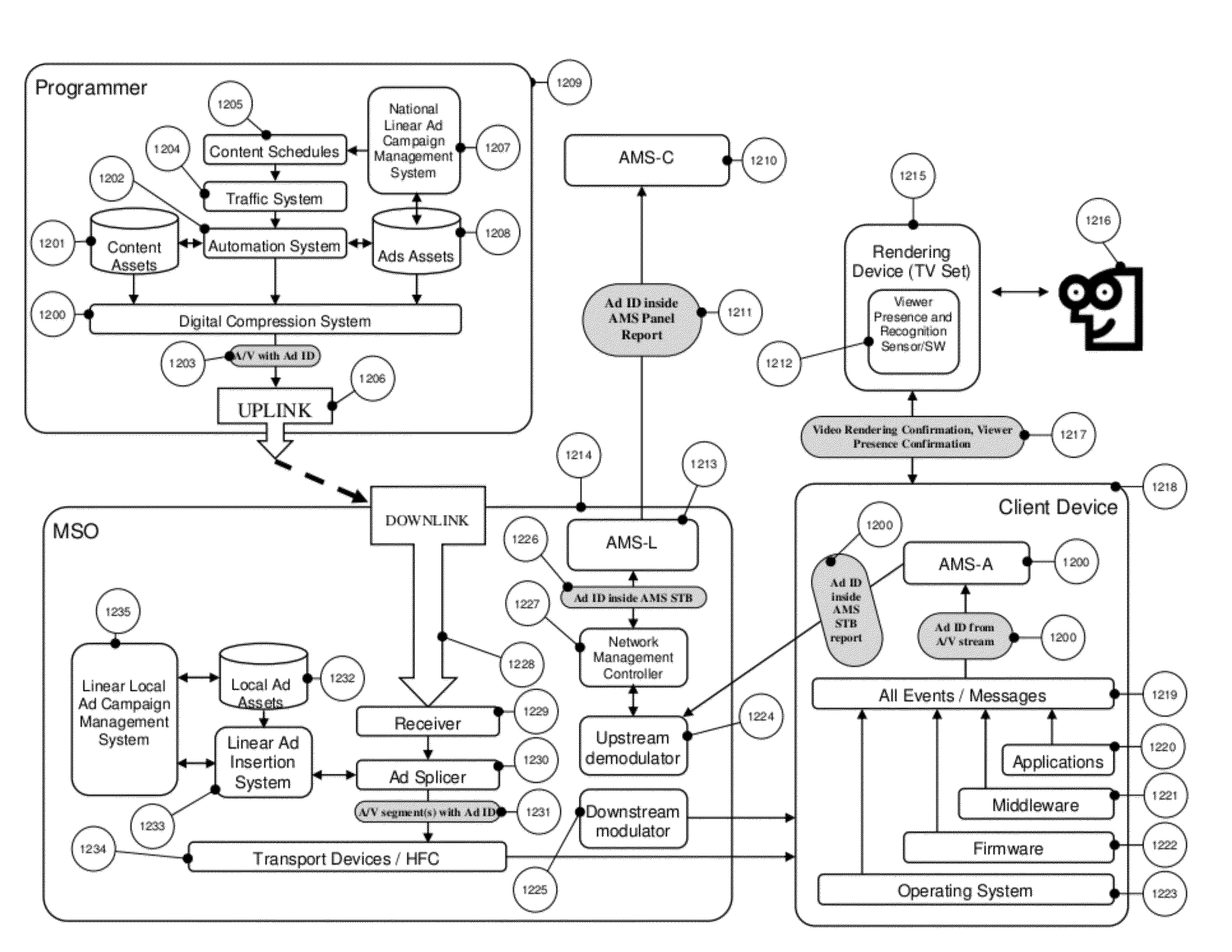
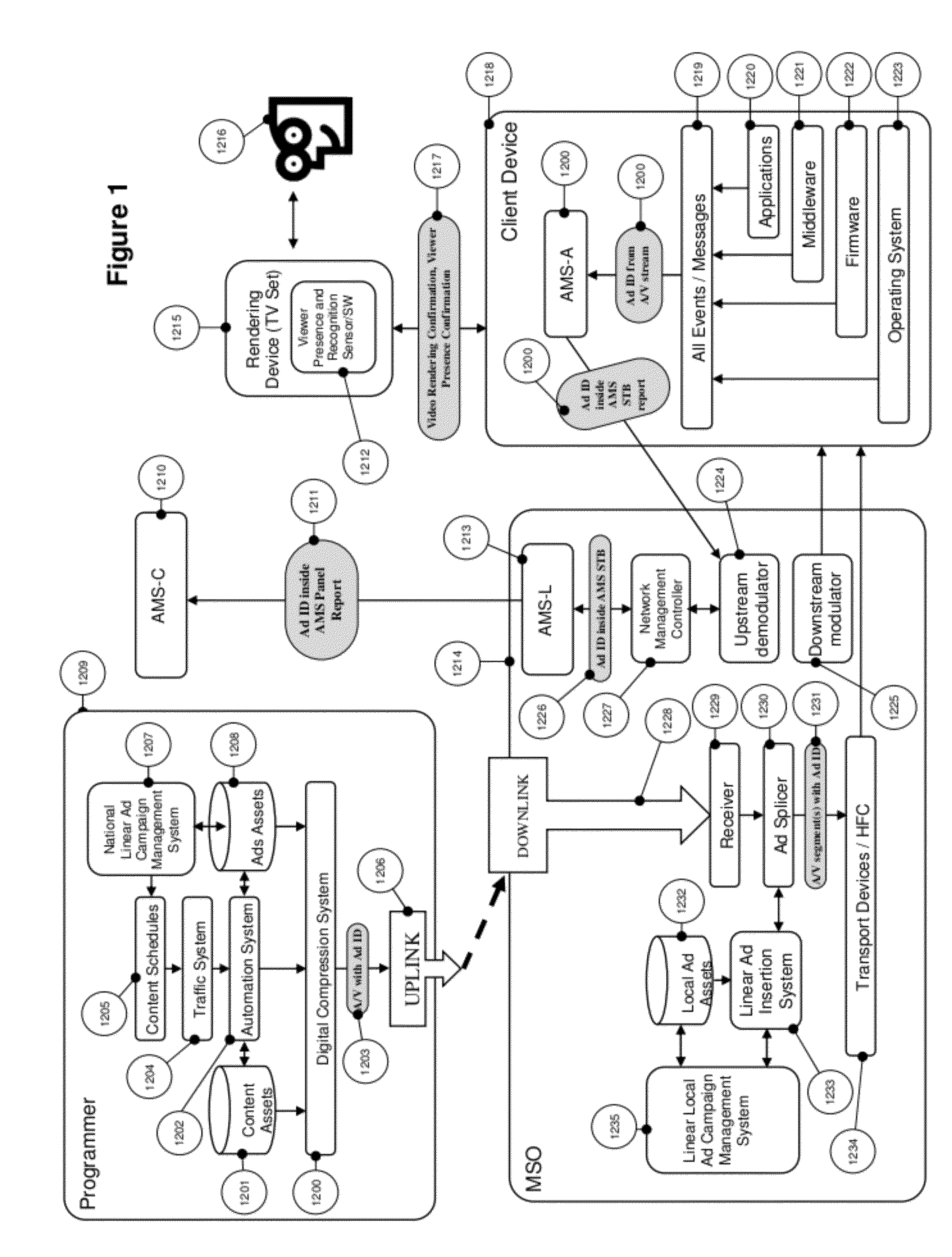
System and method for scalable, high accuracy, sensor and id based audience measurement system based on distributed computing architecture
ActiveUS20120297409A1Method is newEnhancing ad viewershipAnalogue secracy/subscription systemsBroadcast services for monitoring/identification/recognitionDisplay deviceComputer science
Dynamic television audience measurement systems (AMS) and methods are disclosed. The system comprises a central level AMS sub-system, a local node level AMS sub-system, a plurality of client level AMS sub-systems, and a plurality of display devices, each monitored by a client level AMS sub-system. The central level AMS sub-system receives panel definitions from panel requestors and transmits the panel definitions to and receives a merged viewership report from the local node level AMS sub-system. The local node level AMS sub-system receives panel definitions from and transmits the merged viewership report to the central level AMS sub-system, transmits the panel definitions to and receives viewership reports from the plurality of client level AMS sub-systems, and merges the viewership reports into the merged viewership report. Each client level AMS sub-systems receives panel definitions from and transmits the viewership report to the local node level AMS sub-system and compiles the viewership report.
Owner:WEBTUNER CORP
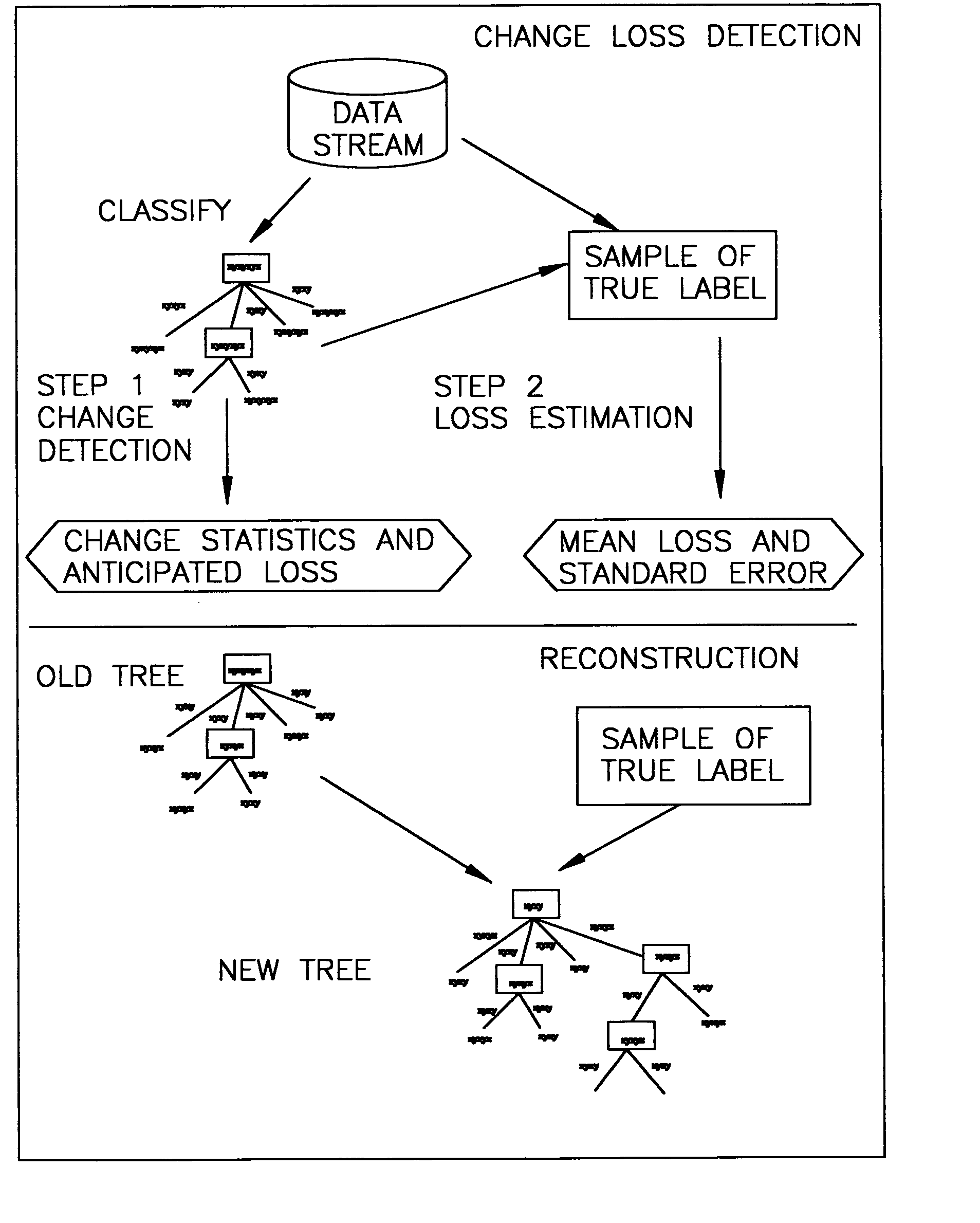
System and method for continuous diagnosis of data streams
InactiveUS20060010093A1Data processing applicationsMultimedia data retrievalDiagnostic dataData stream
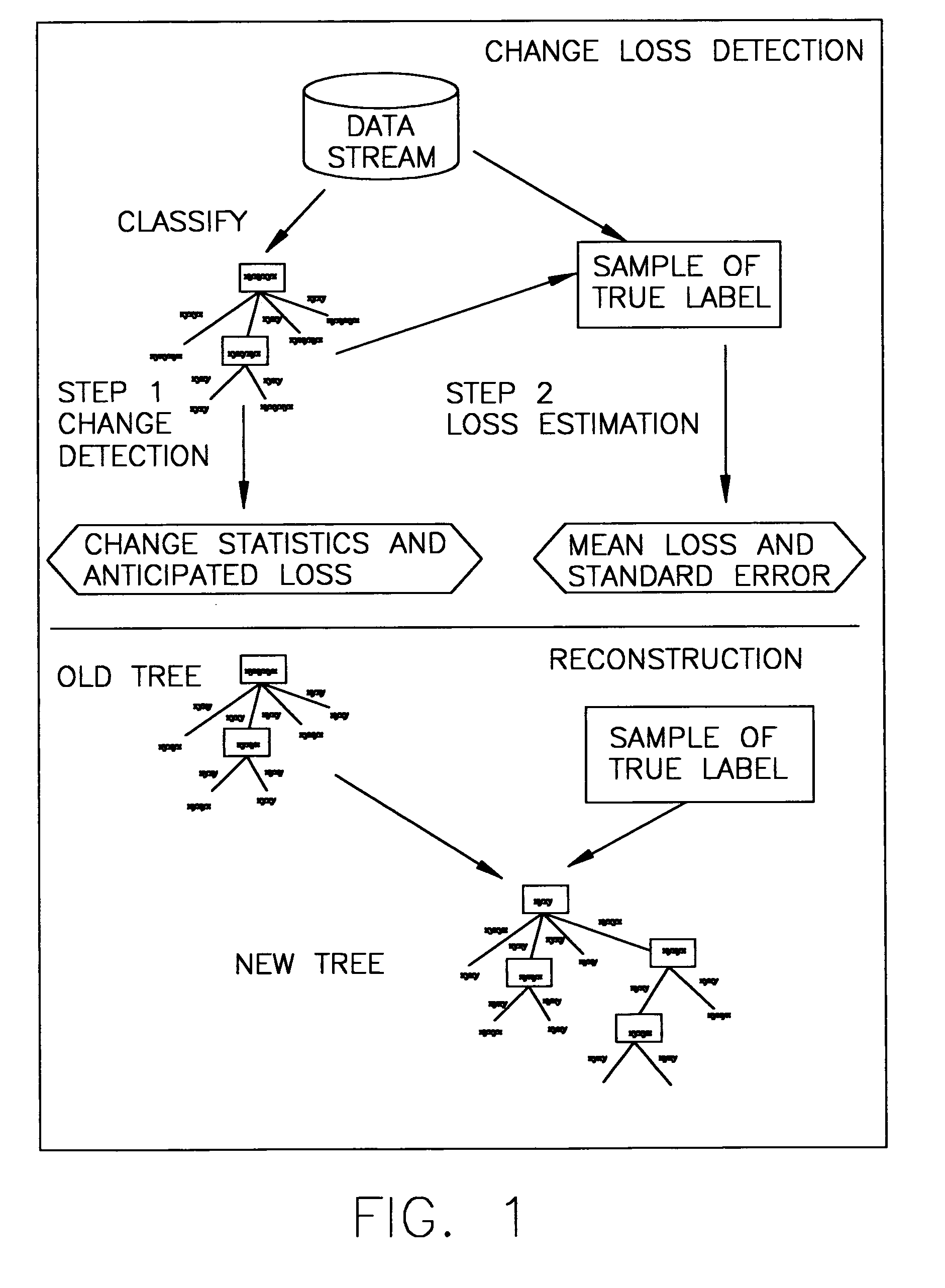
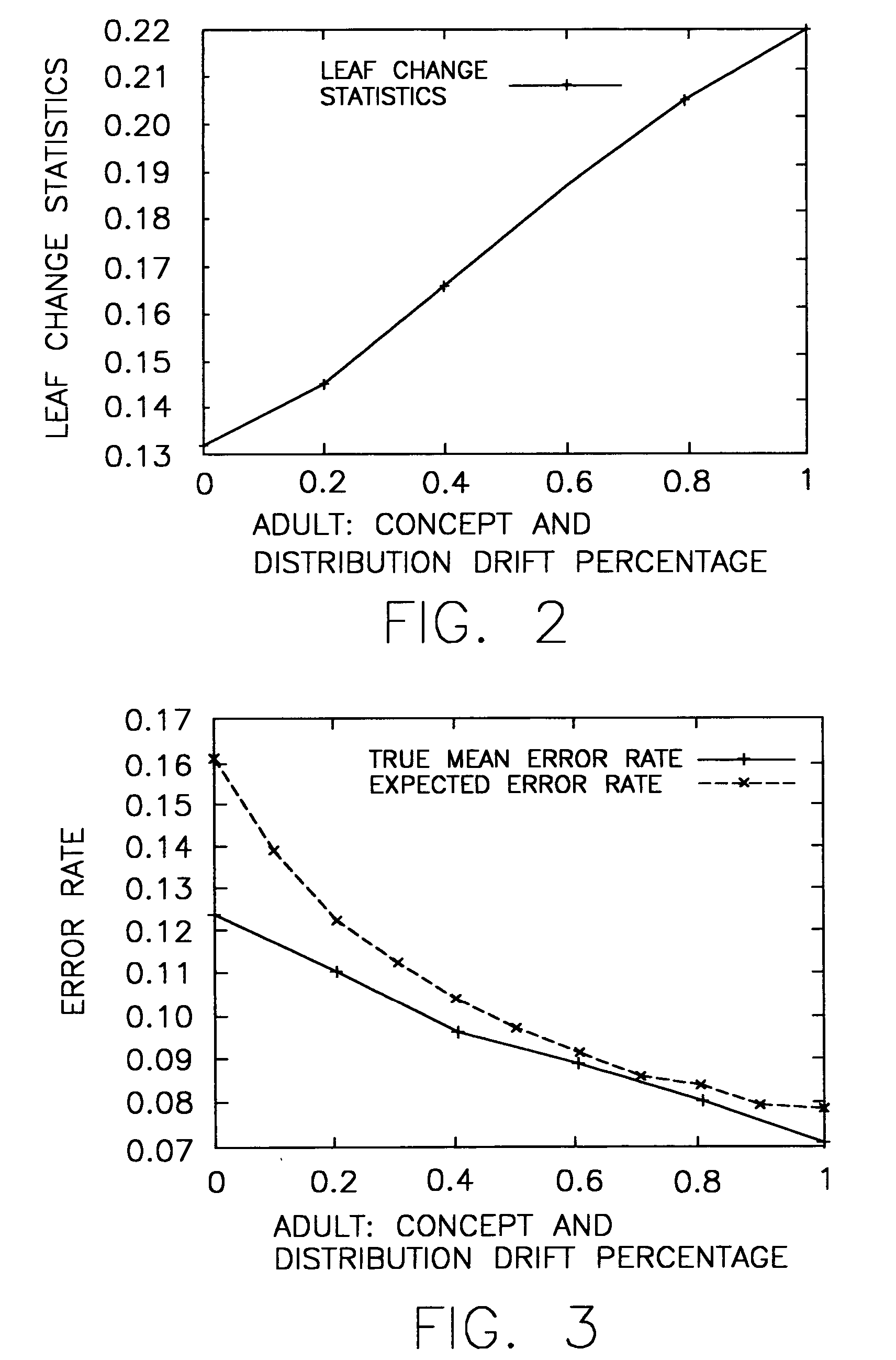
In connection with the mining of time-evolving data streams, a general framework that mines changes and reconstructs models from a data stream with unlabeled instances or a limited number of labeled instances. In particular, there are defined herein statistical profiling methods that extend a classification tree in order to guess the percentage of drifts in the data stream without any labelled data. Exact error can be estimated by actively sampling a small number of true labels. If the estimated error is significantly higher than empirical expectations, there preferably re-sampled a small number of true labels to reconstruct the decision tree from the leaf node level.
Owner:IBM CORP
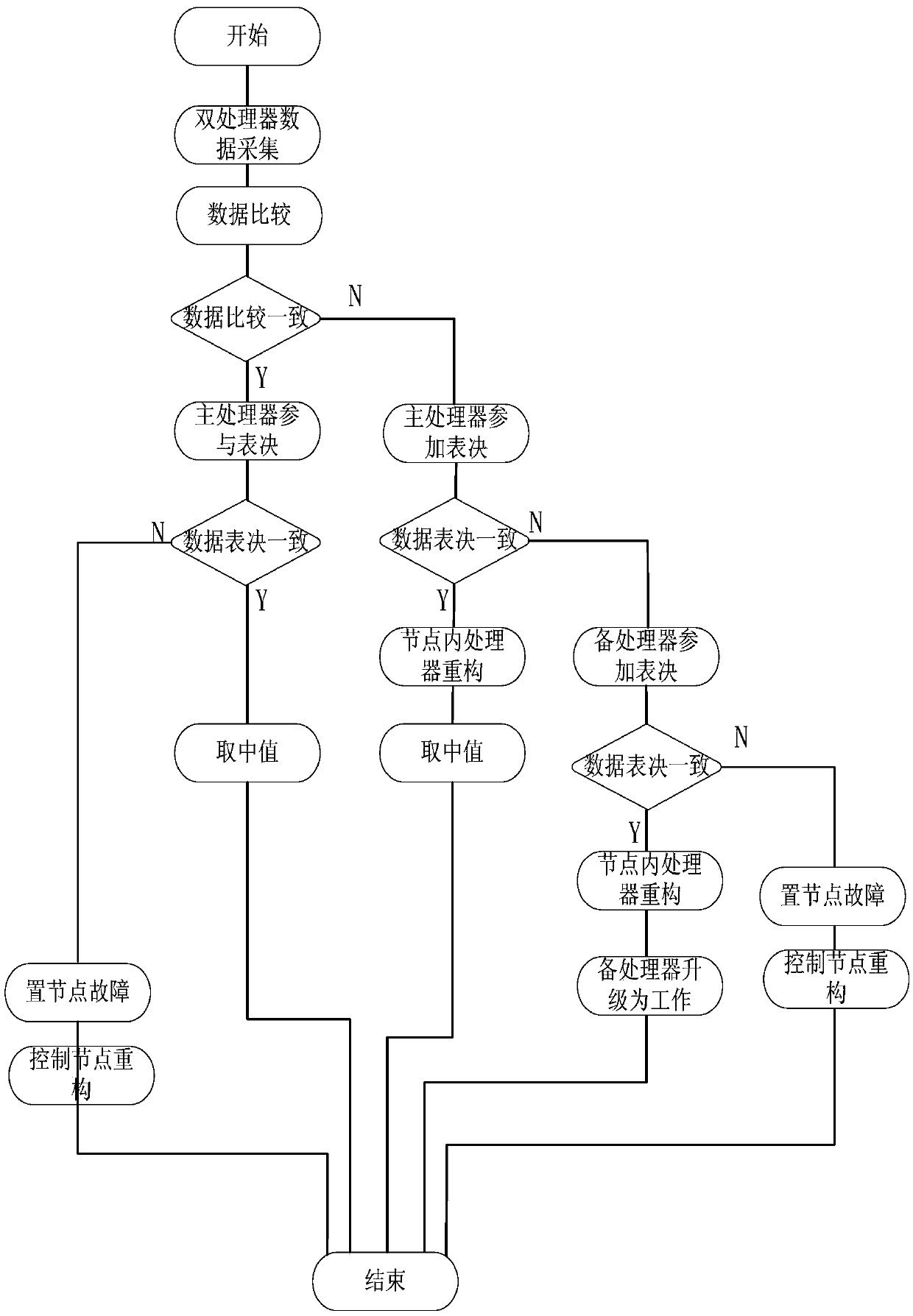
Redundancy management method for improving availability of monitoring pair based fault tolerant system
ActiveCN105550053AEnsure credibleMitigation margin downgradeHardware monitoringReliability/availability analysisFault toleranceComputerized system
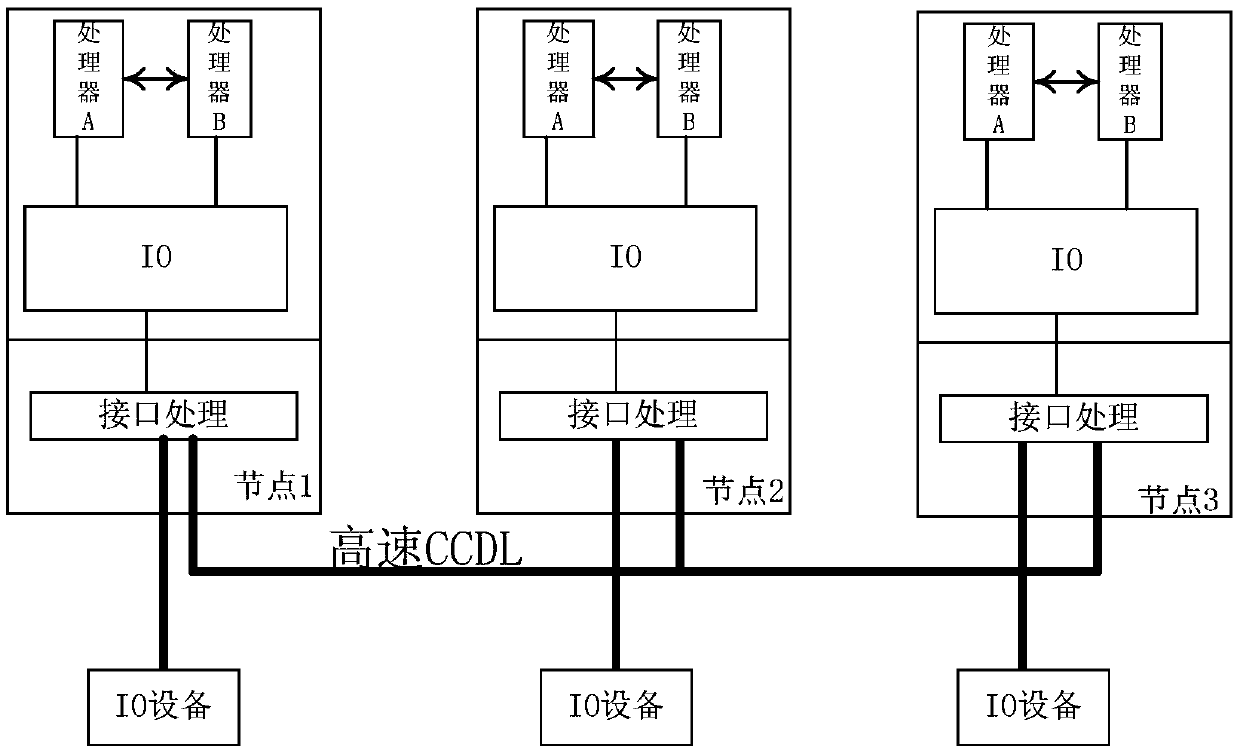
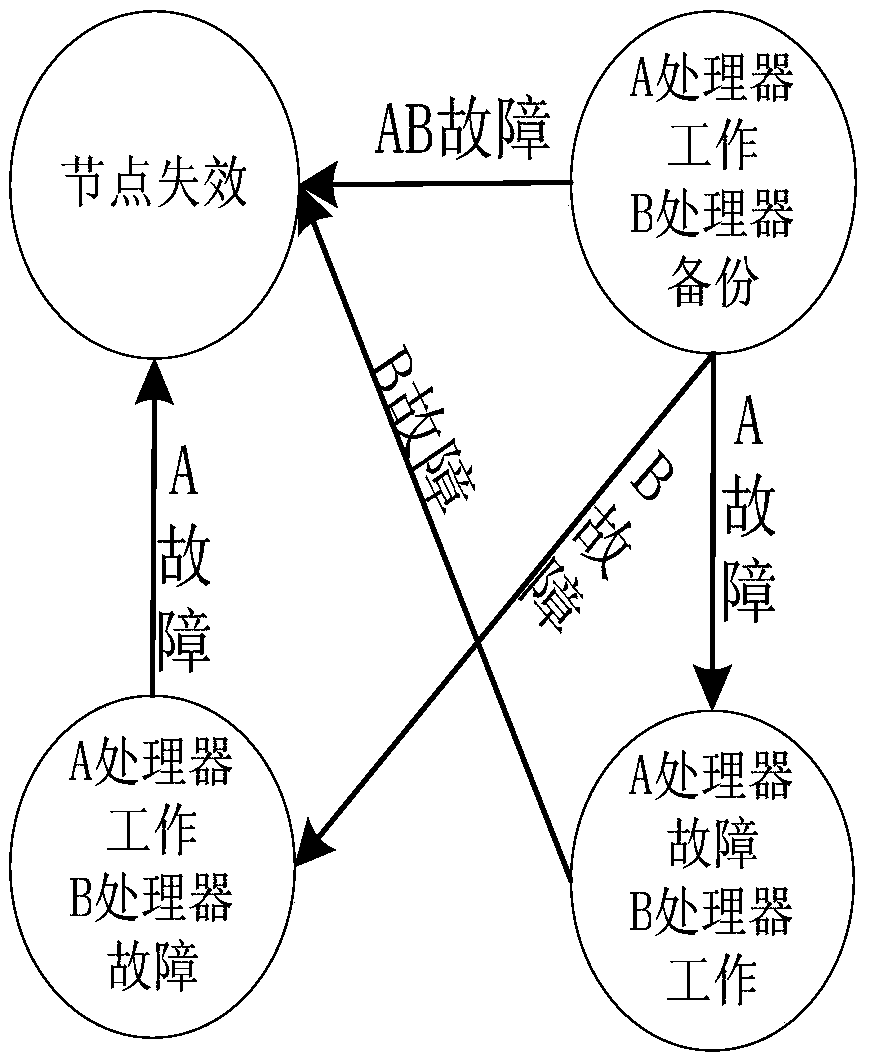
The invention discloses a redundancy management method for improving the availability of a monitoring pair based fault tolerant system. The method comprises the steps of intra-node voting and monitoring and node-level voting and monitoring. During the intra-node voting and monitoring, a controller A and a controller B are consistent by comparison and data of the controller A are selected to enter the node-level voting and monitoring. During the node-level voting and monitoring, a mid-value is selected as a reference value of monitoring from values of three signals of three nodes, and if a difference between other two non mid-value signals and a mid-value signal is within a threshold range, then the non mid-value signals are normal, otherwise, the non mid-value signals are faulted. According to the redundancy management method, the redundancy management of a monitoring pair based three-node or two-node fault tolerant computer is realized; the credibility of system data of a fault tolerant computer system can be ensured; and compared with fault silence based monitoring pair fault tolerance, the redundancy degradation of the system is slowed down, and a backup controller can be reconfigured to be a main controller when a fault occurs once in a node through a software and hardware combination mode, so that the system is ensured not to be degraded.
Owner:XIAN AVIATION COMPUTING TECH RES INST OF AVIATION IND CORP OF CHINA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com