CP-ABE access control scheme based on block chain
A CP-ABE, access control technology, applied in the field of access control based on attribute encryption, can solve problems such as hidden dangers, reduce workload, ensure openness and transparency, and solve the problem of single point of failure.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
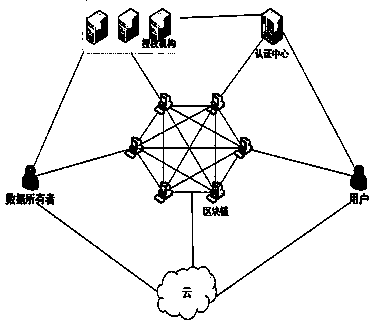
[0023] Such as figure 1 The shown architecture demonstrates the overall flow of the invention:
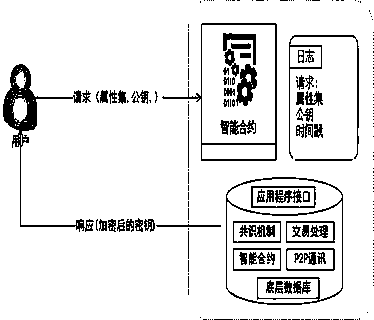
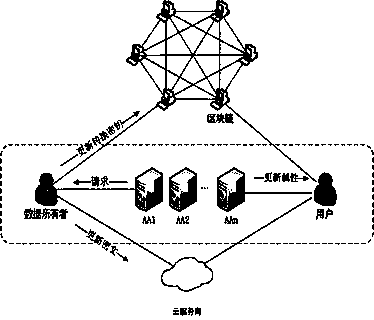
[0024] Step 1: The newly added attribute authority should initiate a registration request to the blockchain, send its subject, valid time and public key through the smart contract, and the certification center will issue an identity certificate after passing the certification.
[0025] Step 2: The data owner requests an encryption key from the AA in this domain, and the AA returns an encryption key after the request is passed;
[0026] Step 3: The data owner encrypts the data file with an encryption key. After encrypting the plaintext, the data owner selects an RSA key pair, encrypts the ciphertext again with the public key, and uploads the ciphertext to the cloud service provider. Publish the private key to the blockcha...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com