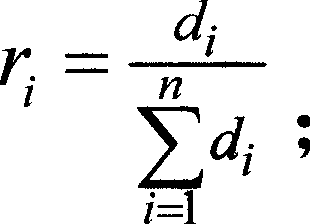Fuzzy risk evaluation system and method for computer information security
A technology of risk assessment system and information system, which is applied in the computer information security fuzzy risk assessment system and the field of information security risk assessment, can solve the problems of lack of security assessment framework, assessment criteria and indicators are difficult to quantify, etc., to improve objectivity and fairness, reduce The effect of subjective factors
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
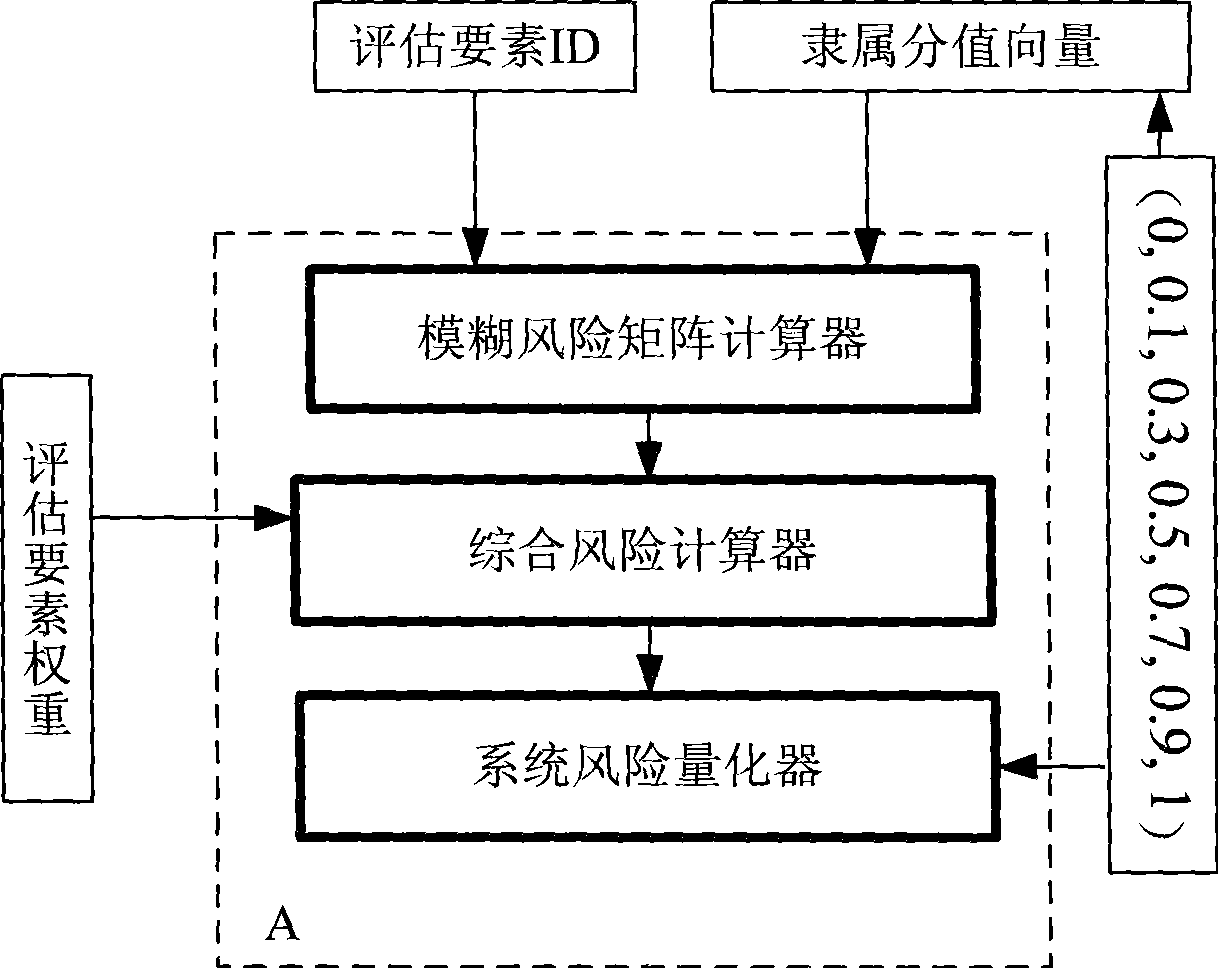
[0022] A computer information system fuzzy risk assessment system (such as figure 2 ), there is a fuzzy risk matrix calculator, which calculates the degree of membership of the fuzzy level of the evaluation element according to the user's risk judgment on the evaluation element, and it has the following inputs:
[0023] 1) Evaluation element identification (ID),
[0024] 2) The discriminant vector (d 1 , d 2 ,...,d n ). d i Indicates the estimated score (0≤d i ≤10), for each evaluation element, its output is an evaluation element fuzzy level membership vector. If there are k evaluation elements, a k×n fuzzy matrix is obtained, which is denoted as the fuzzy risk matrix R.
[0025] If the risk level standard set by the user is a 7-point level {0, 0.1, 0.3, 0.5, 0.7, 0.9, 1}, the implementation of the main components is as follows:
[0026] 1. Implementation of the fuzzy risk matrix calculator:
[0027] Let the risk level vector input by the user be {d 1 , d 2 ,...,...
Embodiment 2
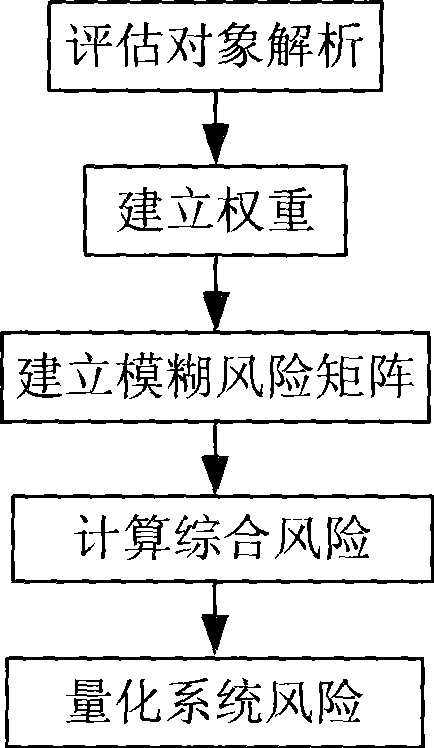
[0037] Such as figure 1 As shown, a specific evaluation process is as follows:
[0038] 1. Establish risk level standards.
[0039] First define a 7-point risk level as shown in Table 1:
[0040] Table 1: Risk Level Criteria
[0041] grade factor
Grade symbol
No describe
0 S 1 Ignorable. The occurrence of a risk event has little impact on the system
0.1
S 2
small. Influential but small. Once a risk event occurs, at most
10% loss of value. 0.3 S 3 slightly obvious. A change in the system can be felt, but not serious.
[0042] Once a risk event occurs, at most 30% of the value will be lost.
0.5
S 4
medium. can cause damage to system reputation, or to system resources or
The reduction of service trust requires the payment of maintenance fees for important resources.
Once a risk event occurs, it can cause a 50% value loss.
0.7
S 5 serious. Can ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com